#Cybersecurity breaches
Explore tagged Tumblr posts
Link
Cybersecurity breaches cost businesses monetary loss and mental stress. Learn data breach prevention tips and save your business from becoming another target.
Read more: https://www.tntra.io/blog/data-breach-prevention/
#Data Breach Prevention#Cybersecurity breaches#data breach prevention tips#Cybersecurity Breaches Data#Cybersecurity
0 notes
Text

"In their statement on Friday, NPD warned that the “the information that was suspected of being breached contained name, email address, phone number, social security number, and mailing address(es).” It recommended the public to take a number of steps to safeguard their identities, including freezing their credit and putting fraud alerts on their files at big credit bureaus.
The breach came to public awareness after a class-action lawsuit was filed August 1 in U.S. District Court in Florida, which was first reported by Bloomberg Law.
National Public Data did not share how many people were at risk, but hackers, who have been identified as part of the hacking group USDoD, have been offering, for sale, what they claimed were billions of NPD records since April, though the Washington Post reported that “security researchers who looked at the trove said some of the claims were exaggerated.”"
source 1
source 2
source 3
free database created by Pentester to see if your information has been leaked
#destiel meme news#destiel meme#news#united states#us news#cybersecurity#data breach#hacking#tech industry#cyber security#identity theft#social security#national public data
227 notes
·
View notes
Text
One of western Canada’s largest rental property companies is warning tenants about a cyber security breach it says was discovered earlier this year. In a letter to tenants on Aug. 19, also published on its website, Mainstreet Equity Corporation says on it discovered a third party had gained access to a portion of its IT infrastructure on May 21. “Upon discovering this, we immediately undertook countermeasures to prevent any further unauthorized activity,” the company said.
Continue Reading
Tagging: @newsfromstolenland
#data breach#cybersecurity#landlords#personal information#western canada#cdnpoli#canadian politics#canadian news#canada
77 notes
·
View notes
Text
The reason I care about being in Cybersecurity runs much deeper to me than income.
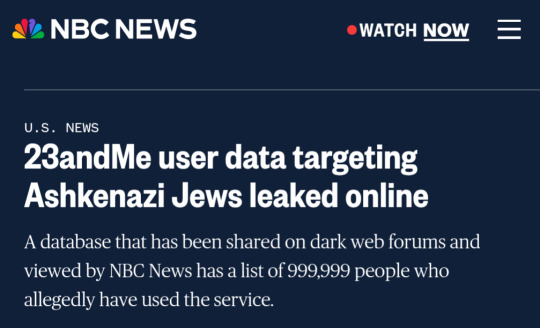
I remember being 11 years old on YouTube and suddenly my video was bombarded with hundreds of antisemitic insults and threats. I knew I wasn't safe online.
If you are from Jewish descent please look into your OPSEC as soon as possible. The online interactions and influence isn't worth your safety. Form a community through decentralized and encrypted platforms to keep yourselves safe, please.
20 notes
·
View notes
Text
Secure Your Laravel App: Fix Insufficient Transport Layer Security (TLS)
Introduction
Transport Layer Security (TLS) is vital for ensuring secure communication between clients and servers over the Internet. Insufficient TLS configurations can leave your Laravel web applications exposed to various cyber threats, like Man-in-the-Middle (MitM) attacks. In this blog post, we’ll explain the risks associated with insufficient TLS security in Laravel and provide a detailed guide on how to configure your Laravel application for optimal security.

Additionally, we’ll show you how to check and resolve potential TLS issues using our free Website Security Scanner tool.
What is Insufficient Transport Layer Security?
Insufficient Transport Layer Security occurs when a website fails to use strong encryption protocols like TLS 1.2 or higher, or when it doesn't properly configure SSL certificates. This exposes web applications to data interception, tampering, and attacks. A properly configured TLS ensures that all data transmitted between the server and client is encrypted and secure.
Common Issues in Laravel with Insufficient TLS Security
Some common causes of insufficient TLS in Laravel include:
Outdated SSL Certificates: Using deprecated SSL/TLS protocols (like SSL 3.0 or TLS 1.0) that are no longer considered secure.
Improper SSL/TLS Configuration: Misconfiguration of the web server or Laravel app that doesn’t force HTTPS or downgrade protection.
Weak Cipher Suites: Servers using weak ciphers, making it easier for attackers to break the encryption.
Lack of HTTP Strict Transport Security (HSTS): Without HSTS, an attacker can force the browser to use an insecure HTTP connection instead of HTTPS.
How to Fix Insufficient TLS in Laravel
Upgrade Your Laravel App’s TLS Protocol To enforce TLS 1.2 or higher, you'll need to configure your server to support these protocols. Here’s how you can configure your server to prioritize stronger encryption:
In Apache: Modify the ssl.conf file:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
In Nginx: Edit your nginx.conf file:
ssl_protocols TLSv1.2 TLSv1.3;
These configurations will ensure that your server uses only secure versions of TLS.
2. Force HTTPS in Laravel Laravel provides an easy way to force HTTPS by modifying the .env file and the config/app.php file:
In .env file:
APP_URL=https://yourdomain.com
In config/app.php file:
'url' => env('APP_URL', 'https://yourdomain.com'),
This will ensure that all requests are redirected to HTTPS, preventing insecure HTTP access.
3. Enable HTTP Strict Transport Security (HSTS) HTTP Strict Transport Security is a web security policy mechanism that helps to protect websites against Man-in-the-Middle (MitM) attacks by forcing clients to communicate over HTTPS. Here's how to add HSTS headers to your Laravel app:
In Apache: Add the following line to your ssl.conf or .htaccess file:
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
In Nginx: Add the following line to your nginx.conf file:
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;
4. Use Strong Cipher Suites Weak cipher suites allow attackers to break the encryption. You can configure your server to use strong ciphers:
In Apache:
SSLCipherSuite HIGH:!aNULL:!MD5:!3DES
In Nginx:
ssl_ciphers 'ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256';
5. Use a Valid SSL/TLS Certificate Ensure that your website uses a valid SSL/TLS certificate from a trusted Certificate Authority (CA). You can get a free SSL certificate from Let's Encrypt.
How to Check TLS Configuration with Our Free Tool
Before and after implementing the changes, it’s essential to check the security status of your website. You can use our free Website Security Checker Tool to evaluate your website’s TLS configuration.
Go to https://free.pentesttesting.com.
Enter your website URL to start the scan.
Review the vulnerability assessment report for TLS issues.
Screenshot of the Free Tool
Here’s a screenshot of the free Website Security Checker tool in action:

Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of a Vulnerability Assessment Report
After running the scan to check website vulnerability, you’ll receive a detailed report highlighting any security vulnerabilities, including issues related to TLS. Here’s an example of the vulnerability assessment report:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
Ensuring sufficient Transport Layer Security in your Laravel app is crucial to protecting sensitive data and preventing attacks. By following the steps outlined in this blog, you can fix any TLS issues and enhance the security of your web application.
Don’t forget to check your website using our free Website Security Checker tool to identify any existing TLS vulnerabilities and other security flaws.
Need help? Contact us at Pentest Testing Corp for professional vulnerability assessments and penetration testing services to secure your website further.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#tls
4 notes
·
View notes
Text
sorry for the ping, but since most of us deal with zip files here, I thought this was important.
PSA: If you use 7-zip, please check which version you are using.
24.07 and earlier are no longer secure and have a serious vulnerability so be sure to update to 24.08 (released 11-Aug-2024) if you have not updated or downloaded it recently.
Note that 7-zip does not auto-update, and should never be downloaded from anywhere except for from the Developers own website: https://7-zip.org/
https://cybersecuritynews.com/7-zip-vulnerability-arbitrary-code/,

#7zip#zip files#software#security#alert#alerta#virus#breach#fyi#psa#safety#computer#android#apple#apps#application#app#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#cybersecurity#cyber security
3 notes
·
View notes
Text
Are AI-Powered Traffic Cameras Watching You Drive?
New Post has been published on https://thedigitalinsider.com/are-ai-powered-traffic-cameras-watching-you-drive/
Are AI-Powered Traffic Cameras Watching You Drive?


Artificial intelligence (AI) is everywhere today. While that’s an exciting prospect to some, it’s an uncomfortable thought for others. Applications like AI-powered traffic cameras are particularly controversial. As their name suggests, they analyze footage of vehicles on the road with machine vision.
They’re typically a law enforcement measure — police may use them to catch distracted drivers or other violations, like a car with no passengers using a carpool lane. However, they can also simply monitor traffic patterns to inform broader smart city operations. In all cases, though, they raise possibilities and questions about ethics in equal measure.
How Common Are AI Traffic Cameras Today?
While the idea of an AI-powered traffic camera is still relatively new, they’re already in use in several places. Nearly half of U.K. police forces have implemented them to enforce seatbelt and texting-while-driving regulations. U.S. law enforcement is starting to follow suit, with North Carolina catching nine times as many phone violations after installing AI cameras.
Fixed cameras aren’t the only use case in action today, either. Some transportation departments have begun experimenting with machine vision systems inside public vehicles like buses. At least four cities in the U.S. have implemented such a solution to detect cars illegally parked in bus lanes.
With so many local governments using this technology, it’s safe to say it will likely grow in the future. Machine learning will become increasingly reliable over time, and early tests could lead to further adoption if they show meaningful improvements.
Rising smart city investments could also drive further expansion. Governments across the globe are betting hard on this technology. China aims to build 500 smart cities, and India plans to test these technologies in at least 100 cities. As that happens, more drivers may encounter AI cameras on their daily commutes.
Benefits of Using AI in Traffic Cameras
AI traffic cameras are growing for a reason. The innovation offers a few critical advantages for public agencies and private citizens.
Safety Improvements
The most obvious upside to these cameras is they can make roads safer. Distracted driving is dangerous — it led to the deaths of 3,308 people in 2022 alone — but it’s hard to catch. Algorithms can recognize drivers on their phones more easily than highway patrol officers can, helping enforce laws prohibiting these reckless behaviors.
Early signs are promising. The U.K. and U.S. police forces that have started using such cameras have seen massive upticks in tickets given to distracted drivers or those not wearing seatbelts. As law enforcement cracks down on such actions, it’ll incentivize people to drive safer to avoid the penalties.
AI can also work faster than other methods, like red light cameras. Because it automates the analysis and ticketing process, it avoids lengthy manual workflows. As a result, the penalty arrives soon after the violation, which makes it a more effective deterrent than a delayed reaction. Automation also means areas with smaller police forces can still enjoy such benefits.
Streamlined Traffic
AI-powered traffic cameras can minimize congestion on busy roads. The areas using them to catch illegally parked cars are a prime example. Enforcing bus lane regulations ensures public vehicles can stop where they should, avoiding delays or disruptions to traffic in other lanes.
Automating tickets for seatbelt and distracted driving violations has a similar effect. Pulling someone over can disrupt other cars on the road, especially in a busy area. By taking a picture of license plates and sending the driver a bill instead, police departments can ensure safer streets without adding to the chaos of everyday traffic.
Non-law-enforcement cameras could take this advantage further. Machine vision systems throughout a city could recognize congestion and update map services accordingly, rerouting people around busy areas to prevent lengthy delays. Considering how the average U.S. driver spent 42 hours in traffic in 2023, any such improvement is a welcome change.
Downsides of AI Traffic Monitoring
While the benefits of AI traffic cameras are worth noting, they’re not a perfect solution. The technology also carries some substantial potential downsides.
False Positives and Errors
The correctness of AI may raise some concerns. While it tends to be more accurate than people in repetitive, data-heavy tasks, it can still make mistakes. Consequently, removing human oversight from the equation could lead to innocent people receiving fines.
A software bug could cause machine vision algorithms to misidentify images. Cybercriminals could make such instances more likely through data poisoning attacks. While people could likely dispute their tickets and clear their name, it would take a long, difficult process to do so, counteracting some of the technology’s efficiency benefits.
False positives are a related concern. Algorithms can produce high false positive rates, leading to more charges against innocent people, which carries racial implications in many contexts. Because data biases can remain hidden until it’s too late, AI in government applications can exacerbate problems with racial or gender discrimination in the legal system.
Privacy Issues
The biggest controversy around AI-powered traffic cameras is a familiar one — privacy. As more cities install these systems, they record pictures of a larger number of drivers. So much data in one place raises big questions about surveillance and the security of sensitive details like license plate numbers and drivers’ faces.
Many AI camera solutions don’t save images unless they determine it’s an instance of a violation. Even so, their operation would mean the solutions could store hundreds — if not thousands — of images of people on the road. Concerns about government surveillance aside, all that information is a tempting target for cybercriminals.
U.S. government agencies suffered 32,211 cybersecurity incidents in 2023 alone. Cybercriminals are already targeting public organizations and critical infrastructure, so it’s understandable why some people may be concerned that such groups would gather even more data on citizens. A data breach in a single AI camera system could affect many who wouldn’t have otherwise consented to giving away their data.
What the Future Could Hold
Given the controversy, it may take a while for automated traffic cameras to become a global standard. Stories of false positives and concerns over cybersecurity issues may delay some projects. Ultimately, though, that’s a good thing — attention to these challenges will lead to necessary development and regulation to ensure the rollout does more good than harm.
Strict data access policies and cybersecurity monitoring will be crucial to justify widespread adoption. Similarly, government organizations using these tools should verify the development of their machine-learning models to check for and prevent problems like bias. Regulations like the recent EU Artificial Intelligence Act have already provided a legislative precedent for such qualifications.
AI Traffic Cameras Bring Both Promise and Controversy
AI-powered traffic cameras may still be new, but they deserve attention. Both the promises and pitfalls of the technology need greater attention as more governments seek to implement them. Higher awareness of the possibilities and challenges surrounding this innovation can foster safer development for a secure and efficient road network in the future.
#2022#2023#adoption#ai#AI-powered#Algorithms#Analysis#applications#artificial#Artificial Intelligence#attention#automation#awareness#betting#Bias#biases#breach#bug#Cameras#Cars#change#chaos#China#cities#critical infrastructure#cybercriminals#cybersecurity#data#data breach#data poisoning
5 notes
·
View notes
Text

ago
🔒 In today’s digital world, choosing the Best cybersecurity Company is essential – and that’s why businesses choose Cytrusst. ✅ Safeguard Your Most Critical Systems and Assets Protect what matters most with robust security designed to defend your essential systems and sensitive data. 🚀 Secure Digital Transformation with Our Unique Defensive Approach Accelerate your digital growth without compromising security. Our innovative defense strategies keep you secure every step of the way. 🔍 Compliance & Hacker Mindset We don’t just follow compliance standards; we think like hackers to stay one step ahead, identifying and mitigating vulnerabilities before they’re exploited. 🔒 Endless Solutions on a Single Platform From detection to prevention, access all the tools and resources you need in one seamless platform. 📊 Risk-Based Approach & Dedicated Client Focus We prioritize your unique risks with a tailored approach and a team dedicated to your security. With Cytrusst, you’re not just getting a provider; you’re gaining a proactive, reliable partner focused on keeping your business safe. Don’t settle for less regarding your security – choose the best. Stay One Step Ahead With Cytrusst - The Best Cybersecurity Company To Safeguard Your Digital Assets And Secure Your Future.
2 notes
·
View notes
Text

#coding#itsecurityalert#securityalert#cybersecurity#hacker#hacking#hacks#devlog#linux#security#data breach#technology
4 notes
·
View notes
Text
Passkeys being supported so many places lately are the best thing to happen to authentication in the last 20 years.
If you have a good password manager and save passkeys to it, it’s finally as convenient to sign in as it was back when nothing had multifactor and you just typed your one memorized password into everything.
#btw speaking of password managers#if you’re still using LastPass switch#even after their huge breach which was only even as big an deal as it was because their security is so much worse than the competition#i see so many people using it‚ including IT professionals with cybersecurity responsibilities#seriously go find something better#at my last job i actually did a lot of research on the actual security of password managers and compared a bunch of options#and the two i would recommend based on that research are 1Password and Bitwarden#or for a FOSS option there’s KeePassXC
3 notes
·
View notes
Text
What is Zero Trust Architecture?

Zero Trust Architecture (ZTA) is a security model that operates on the principle "never trust, always verify." Unlike traditional security models that assume everything within a network is trustworthy, ZTA requires verification for every access request, regardless of whether it originates inside or outside the network.
Why is it Important?
In today's digital landscape, cyber threats are becoming increasingly sophisticated. Zero Trust Architecture helps mitigate risks by continuously verifying every user and device, ensuring that only authorized entities can access sensitive information.
How Does It Protect You?
1. Enhanced Security: By requiring strict verification, ZTA minimizes the risk of unauthorized access and data breaches.
2. Reduced Attack Surface: Limiting access to only what is necessary decreases potential entry points for attackers.
3. Real-time Monitoring: Continuous monitoring and verification help detect and respond to threats promptly.
Adopt Zero Trust Architecture with Century Solutions Group to fortify your cybersecurity defenses and protect your business from evolving cyber threats! #ZeroTrust #CyberSecurity #CenturySolutionsGroup
Learn More:https://centurygroup.net/cloud-computing/cyber-security/
3 notes
·
View notes
Text
According to my phone, the password I've used for hundreds of accounts across many websites, since the day I was born, has been leaked in a data breach. If my parents find out, I will probably never be allowed touch anything with an internet connection ever again (this is hardly even an exaggeration). I may be stupid...
2 notes
·
View notes
Text
I know I don't usually talk about this sort of stuff especially since I am an account that posts random photos
However I regret to inform you that the mushroom bot has a deta beech and your data may be compromised
youtube
5 notes
·
View notes
Text
Protect Your Laravel Application from Clickjacking Attacks
In today's digital landscape, protecting your web application from various security threats is crucial. One such threat is Clickjacking, an attack that tricks users into clicking on invisible or disguised elements on a webpage. For developers using the Laravel framework, ensuring your application is safe from clickjacking is essential.

In this post, we'll explore what clickjacking is and how to prevent it in your Laravel application. Plus, we’ll show you how to use our free Website Security Checker tool to assess potential vulnerabilities.
What is Clickjacking?
Clickjacking is a type of attack where malicious users embed your webpage into an invisible iframe on their site. The attacker then tricks the victim into clicking on the iframe, which can lead to unwanted actions like changing settings, submitting forms, or even transferring funds without their knowledge.
For example, a button that looks harmless on the surface might trigger an action you didn’t intend to take when clicked in an iframe. This type of attack can be devastating for your users’ privacy and your application’s security.
Preventing Clickjacking in Laravel
Fortunately, Laravel provides a straightforward way to mitigate the risk of clickjacking. Here's how you can do it:
Step 1: Use HTTP Headers
The best way to prevent clickjacking in your Laravel application is by setting proper HTTP headers. You can do this by adding the X-Frame-Options header to your application's response. This header tells the browser not to allow your webpage to be embedded in an iframe.
In Laravel, you can add this header globally by modifying the app/Http/Middleware/VerifyCsrfToken.php file.
Here’s how you can modify the middleware:
// app/Http/Middleware/VerifyCsrfToken.php namespace App\Http\Middleware; use Closure; use Illuminate\Http\Request; class VerifyCsrfToken { public function handle(Request $request, Closure $next) { // Adding X-Frame-Options header to prevent clickjacking response()->headers->set('X-Frame-Options', 'DENY'); return $next($request); } }
With this code, the header X-Frame-Options: DENY ensures that no website can embed your pages in an iframe. If you want to allow only certain websites to embed your content, you can use SAMEORIGIN instead of DENY.
Step 2: Use Content Security Policy (CSP)
Another robust method to prevent clickjacking attacks is by using a Content Security Policy (CSP). Laravel supports CSP through middleware. By setting a strict policy, you can specify exactly which websites are allowed to load your pages in an iframe.
Here’s an example of how you can configure the CSP in your Laravel application:
// app/Http/Middleware/ContentSecurityPolicy.php namespace App\Http\Middleware; use Closure; use Illuminate\Http\Request; class ContentSecurityPolicy { public function handle(Request $request, Closure $next) { // Setting a strict CSP header response()->headers->set('Content-Security-Policy', "frame-ancestors 'none';"); return $next($request); } }
This ensures that no site can embed your application within an iframe.
Why Use Our Free Website Security Checker?
After implementing these preventive measures, it’s important to test your application’s security. Our free Website Security Scanner tool provides a comprehensive vulnerability assessment for your website, including tests for clickjacking and other security issues.
Here’s a screenshot of our free tool in action:

Screenshot of the free tools webpage where you can access security assessment tools.
Conclusion
Securing your Laravel application against clickjacking attacks is crucial for protecting your users and ensuring your web app remains safe. By following the steps outlined above, you can significantly reduce the risk of such attacks. Additionally, our free Website Security Checker can help you ensure that your site is not vulnerable to clickjacking or any other security issues.
And here’s an example of the vulnerability assessment report generated by our free tool:

An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
By regularly using security tools and following best practices, you can enhance your website’s defenses and maintain a safe browsing environment for your users.
Take Action Today
Start testing your website with our free tool to test website security free and take the first step in protecting your site from clickjacking and other cyber threats.
#Clickjacking#laravel#cyber security#cybersecurity#data security#pentesting#security#the security breach show
3 notes
·
View notes
Text
Massive data breach, please check your email accounts and update your security details!
#data breach#privacy#email#google#telegram#invasion of privacy#cybersecurity#security#internet#pwned#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#alerta#alert#it#i.t.#infotech#information technology
7 notes
·
View notes
Note
I swear to god, every time I go on tumblr, you have reblogged a post that I JUST saw on Pinterest, what are you hiding, what are your secrets.
I installed malware on your computer and phone that monitors your activity on Pinterest and instantly reblogs anything that you see that is also on Tumblr
But probably what it is is that the people I follow tend to reblog already popular posts, and popular posts are a lot more likely to be reposted to other parts of the internet
#ask#anon#my coding ability definitely extends beyond basic programs like the one I use to post postsofbabel stuff and basic Minecraft datapacks#i'm an epic hacker#i am like the one punch man but for breaching cybersecurity
2 notes
·
View notes