#CodeAnalysis
Explore tagged Tumblr posts
Text
#Python#JSON#DataParsing#LargeFiles#Programming#CodeAnalysis#DataScience#PythonProgramming#CodingTips#SoftwareDevelopment
1 note
·
View note
Text
Programming with Ai-Driven Tools
🚀 Are you ready to supercharge your programming with AI-driven tools? Dive into the world of AI Code with these 9 remarkable tools! 🤖💻
🌟 AI Code Tools: Unlocking Programming Efficiency 🌟
Artificial Intelligence is revolutionizing the world of coding. Whether you're a seasoned programmer or just starting your journey, these 9 AI-powered tools are your ticket to enhanced productivity:-
💡 AI Code: Your Efficiency Boost 💡
Embracing AI in your programming journey can elevate your efficiency, reduce errors, and help you stay ahead of the coding curve. Whether you're a developer, data scientist, or tech enthusiast, these AI code tools are here to empower you.
Excited to explore AI-driven programming or have your own experiences to share? Let's dive into the future of coding together! 💬

#AI hashtag#Programming#AIProgramming#AIInCoding#AIInDevelopment#CodeAutomation#CodeAnalysis#EfficiencyBoost
0 notes
Link
https://bit.ly/3R8Q34L - 🔍 The CYFIRMA team has unmasked MaaS operator EVLF DEV, creator of CypherRAT and CraxsRAT. Over 100 threat actors have bought these RATs in 3 years, allowing control over victim devices. #Cybersecurity #Malware 🚀 ‘Malware-as-a-service’ is aiding cybercriminals to begin operations. EVLF and others are helping threat actors with specific malware tools, focusing on a destructive Android RAT. #MaaS #AndroidRAT #CyberCrime 💼 EVLF's web shop has boosted CraxsRAT's reach. Transactions are in cryptocurrency, and the operation is based in Syria. Details about EVLF were identified. #Cryptocurrency #ThreatActors 📱 CraxsRAT, targeting Android devices, has been misreported as affecting Windows OS. Cracked versions with backdoors contribute to confusion. #AndroidSecurity #MalwareResearch 💣 Technical analysis shows CraxsRAT as a dangerous Android RAT. Customization features make the generated package deadly and enable live screen recording. #AndroidRAT #CodeAnalysis 🏦 EVLF's crypto wallet balance is 75,000 USD over 3 years. A temporary freeze by Freewallet led to a thread by EVLF, confirming the Syria operation. #CryptoWallet #CyberInvestigation 🛡️ EVLF's CraxsRAT is perilous for Android. Protection includes caution in downloading, avoiding suspicious links, updates, and reliable security software. #CyberProtection #RAT 📚 Recommendations include training, updates, encryption, mobile device management, backups, incident planning, user support, app review, cautious permissions, security software, and safe networks.
#Cybersecurity#Malware#MaaS#AndroidRAT#CyberCrime#Cryptocurrency#ThreatActors#AndroidSecurity#MalwareResearch#CodeAnalysis#CryptoWallet#CyberInvestigation#CyberProtection#RAT#CybersecurityTips#SafePractices#operatingsystem#control#devices#cybersecurity#cybercriminals#operation#cryptocurrency#analysis#customization
0 notes
Text
#pentest#pentesting#domains#codeanalysis#tools#comptiapentest#penetrationtesting#learntorise#infosectrain
0 notes
Text
Is Static Code Analysis Better Than Dynamic Code Analysis?

Dynamic and Static Analysis are two types of code security tests. Both of these are used while checking the source code. A static code review does not need the execution of the code while a dynamic code analysis is mainly dependent on how well the code performs during execution. Normally both the methods are used while extensively reviewing source codes. To understand and observe how well these tests workout, it is necessary for any company to pay close attention to details
What is Static Code Analysis?
Static analysis involves checking the source code without executing it. That means it focuses on the internal structure than on the functional aspect of the code. It is normally performed in a non-runtime environment i.e. it is not done when the program is running. Static analysis involves checking the source code, byte code or application binaries for any possible susceptibilities. While performing this test, application data and control paths are created and then checked for any security weaknesses.
Benefits and Limitations of Static AnalysisBenefits
1) Locates exact area of error in coding
2) It grants ample time for some quick fixes
3) Locates the issues at an early stage
4) Detects certain unique defects like variable use, uncalled functions or unreachable codes
5) It is conducted by trained developers who have a complete understanding of the code or using an automated code review tools like Codegrip.
Limitations
1) Takes a lot of time if done manually
2) A paucity of trained persons makes it difficult to perform
3) Cannot locate issues faced in the runtime environment
What is Dynamic Code Analysis?
A dynamic analysis is an exact opposite; it is done in a runtime environment. Thus it looks and studies the source code from the outside. It involves manipulating the running state to discover what the possible security vulnerabilities are. It mounts a simulated attack on the application or program and observes how it reacts.
Both of these tests are many times viewed to be conflicting to each other, but for an integrated code review, both are equally important to be performed
Benefits and Limitations of Dynamic AnalysisBenefits
1) Locates vulnerabilities in the runtime environment
2) Helps in validating Static analysis’s findings
3) Allows analyzing programs without having access to the actual code
4) Identifies susceptibilities that might be shown as false negatives in static analysis
5) Can be conducted against any application
Limitations
1) No guarantee of full test coverage of source code
2) Becomes difficult to go back and trace the vulnerabilities back to its original location
3) Needs longer timeframe to put in the fixes
Let us now quickly see the main differences between these two tests:
Static Analysis
Done at the initial stage before execution
Done at a non-runtime
Internal observation of the structure
Focuses on Structural aspects
Application data and control paths are created to check vulnerabilities
As the name suggests, it is a fixed approach with decided parameters
Dynamic Analysis
It is done at a later stage during execution
Done in runtime
External observation of performance
Focuses on functional aspects
A simulated attack is mounted on the program to check how it responds and then susceptibilities are identified
As the name suggests, it is dynamic in nature and largely depends on challenges faced during execution
Conclusion
Both of these tests are not opposed to each other and can, in fact, be used in unison or simultaneously. Automating your code reviews would be a good start to having flawless codes with the help of review tools like Codegrip.
1 note
·
View note
Photo

Do you know if your website is safe or not? Hackers track your website, use the security loophole and finally HACKED YOUR WEBSITE We will provide you the Web Security analysis report with Developer Guide (Code Analysis For Owner / Developer).
Reach us @ : www.webspider.pk Call / WhatsApp / Botim+92 334 500 9042
0 notes
Text
How to integrate your MAVEN project with SonarQube
How to integrate your MAVEN project with SonarQube

So, You want to integrate your project to SonarQube for managing the source quality of your project. That’s indeed a wonderful idea. If you are wondering and excited to learn How to go about it, just keep calm and sit back, I will take you through the same. I am very certain that after this blog you will be able to integrate your project with SonarQube in just a matter of time.
So, Let’s dive…
View On WordPress
0 notes
Text
CodeAnalysis Tencent Cloud Code Analysis (TCA for short, code-named CodeDog inside the company...
CodeAnalysis Tencent Cloud Code Analysis (TCA for short, code-named CodeDog inside the company early) is a code comprehensive analysis platform, which includes three components: server, web and client. It supports the integration of common code analysis tools in the industry. Its main function is to ensure the code quality under agile iterations of multiple engineering projects, and Support the team to inherit the code culture. https://github.com/Tencent/CodeAnalysis

-
0 notes
Photo
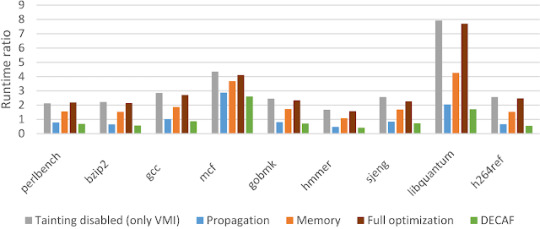
DECAF – Short for Dynamic Executable Code Analysis Framework | TheHackerNews.Co #analysis #analysisframework #binaryanalysis #code #codeanalysis #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #thehackernews
0 notes
Photo

Flare-Emu – Emulation features for the x86, x86_64, ARM, ARM64 | MrHacker.Co #architectures #arm #arm64 #binaryanalysis #codeanalysis #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Text
RT @CapeofGoodCode1: 50 % of your R&D investment is waste! Visit us at our booth at #TNW2019 and learn how to avoid waste with intelligent DETANGLE code & feature analysis. #CodeAnalysis #SoftwareQuality https://t.co/0wDLv8lvYk https://t.co/KFFKLSTgWs
50 % of your R&D investment is waste! Visit us at our booth at #TNW2019 and learn how to avoid waste with intelligent DETANGLE code & feature analysis.#CodeAnalysis #SoftwareQualityhttps://t.co/0wDLv8lvYk pic.twitter.com/KFFKLSTgWs
— Cape of Good Code (@CapeofGoodCode1) May 9, 2019
from Twitter https://twitter.com/fbeardev
0 notes
Text
jsinspect/ Detect copy-pasted and structurally similar code https://t.co/dm0q99f8ei #JavaScript #CodeAnalysis
jsinspect/ Detect copy-pasted and structurally similar code https://t.co/dm0q99f8ei #JavaScript #CodeAnalysis
— Macronimous.com (@macronimous) October 19, 2018
from Twitter https://twitter.com/macronimous October 19, 2018 at 05:33PM via IFTTT
0 notes
Photo

In PVS-Studio team we feel at home! Is the work also the second home for you? Share your photos with a hashtag - #workathome #programminglife #codeanalysis #coding
0 notes
Text
jsinspect/ Detect copy-pasted and structurally similar code https://t.co/VAsucjX1ge #JavaScript #CodeAnalysis https://t.co/srlAuHa6ZO
jsinspect/ Detect copy-pasted and structurally similar code https://t.co/VAsucjX1ge #JavaScript #CodeAnalysis pic.twitter.com/srlAuHa6ZO
— Macronimous.com (@macronimous) October 14, 2018
from Twitter https://twitter.com/macronimous October 14, 2018 at 09:10PM via IFTTT
0 notes
Text
jsinspect/ Detect copy-pasted and structurally similar code https://t.co/9wklOqKlp8 #JavaScript #CodeAnalysis https://t.co/7F5b7k8Lgb
jsinspect/ Detect copy-pasted and structurally similar code https://t.co/9wklOqKlp8 #JavaScript #CodeAnalysis pic.twitter.com/7F5b7k8Lgb
— Macronimous.com (@macronimous) September 14, 2018
from Twitter https://twitter.com/macronimous September 14, 2018 at 07:45PM via IFTTT
0 notes