#BYOD
Explore tagged Tumblr posts
Text
D&d Player Recruitment:
Looking for 2 new players for the group. We run long hours and have fun. Must be 18+, Fur Friendly, No Kink Shaming, Friendly (don't be a dick), Able to roll with the punches as a game plays, Team Player. Current group is chaotic, the DM is chaotic and doesn't hold back with descriptions or consequences and the game can be NSFW and graphic at times if/when it calls for it.
Game info: D&D 3.5e
Runs every Saturday noon to midnight
Uses discord for voice
Roll20 for gameboard
Myth-weavers for character sheets
The game will be set in a Victorian era with low magic (with dinosaurs). You wake up with no memory of your past and a foreboding feeling of what may be coming, and a guilt of what you may have done.
You'll be attempting to avoid the plot without knowing your past. Derail things, start a store, spend 5 hours helping an elderly man pick potatoes, but beware of the quest giver over at the inn. You will not know you class or abilities starting out. As you hit milestones you will level up and uncover more info on your abilities and class.
Summary - Avoid the plot, Amnesia, set in Victorian era low magic setting (with dinosaurs), Theme of Redemption
Varients - individual milestone and Cliche Variant to invoke cliches
DM will need character arch type (ie mage, caster, niche melee type) for the general character DM'll be making you so that DM can ensure you are playing something you'll like. You will not know your name at the start, other players will get randomly get assigned to pick races and names for other players. This will be uncovered as time goes on you start knowing not much more than you do now.
Message me if interested
Disclaimer:
There are two small children in the house, so noise levels may very dependent on the brand of chaos they choose to display.
#recruitment#dnd#d20#dungeons and dragons#geek#nerd#d5#3.5 edition#dragons#weekend#Saturdays#players#byod
6 notes
·
View notes
Text
Water Testing and Analysis Market

🚀 𝗧𝗵𝗲 𝗙𝘂𝘁𝘂𝗿𝗲 𝗼𝗳 𝗠𝗼𝗯𝗶𝗹𝗲 𝗖𝗼𝗻𝘁𝗲𝗻𝘁 𝗠𝗮𝗻𝗮𝗴𝗲𝗺𝗲𝗻𝘁 (𝗠𝗖𝗠) 𝗶𝘀 𝗛𝗲𝗿𝗲! 🚀
The Mobile Content Management Market size is forecast to reach US$21.324 billion by 2030, growing at a CAGR of 22.5% from 2024 to 2030.
𝐃𝐨𝐰𝐧𝐥𝐨𝐚𝐝 𝐑𝐞𝐩𝐨𝐫𝐭 𝐒𝐚𝐦𝐩𝐥𝐞: https://tinyurl.com/56rr5yex
In a world driven by #digital #transformation, Mobile Content #Management has #become the cornerstone of #secure and #efficient content distribution. 🌐
#MobileContentManagement#MCM#DigitalTransformation#BYOD#CloudSolutions#DataSecurity#RemoteWork#AIInBusiness#FutureOfWork
0 notes
Text

Learn how to configure Cisco ISE for seamless BYOD onboarding. Our step-by-step guide ensures secure and efficient device management, enhancing your network's flexibility and security. https://www.dclessons.com/configuring-ise-for-byod-onboarding
0 notes
Text

In this blog post, we’ll look at two common mobility strategies that hotels have implemented: BYOD and Choose Your Own Device (CYOD) by following along here you will gain an understanding of how these technologies can be used most effectively in hotels. Read More...
#business phones#voip technology#pbx system#hotel phone system#voip phone#hotel hospitality#phonesuite direct#phonesuite dealers#voip advantages#pbx communications#Mobility Device#BYOD#hotel industry#Cloud Telephony#Cloud Calling#VoIP Protocol#SIP Protocol#Call booking#Pms integration#Call center#integration#Communications#Hotel reservation#Cloud VoIP
0 notes
Text
India Foxtrot Echo - IndiGo’s foray into premiumization of services?
In September 2019, a sudden set of tweets (it was still twitter then) announced the launch of In-Flight entertainment in IndiGo. Most looked at the advertisements or press releases and took to social media excitedly. A look at the details and one realised it was a deal with Sonyliv where the airline had a partnership. A discounted seven day pricing allowed you to download anything (before the…

View On WordPress
0 notes
Text
Here are Five BYOD Principles to Consider from a Highly Respected Source

Navigating the complexities of Bring Your Own Device (BYOD) policies requires careful consideration of key principles. The Sedona Conference® Commentary on BYOD outlines five essential guidelines for organizations. From assessing business needs to safeguarding sensitive data, these principles underscore proactive management. Addressing BYOD concerns preemptively is crucial—check out the article below for insights into ensuring your organization's BYOD practices are both secure and compliant.
The entire article is here: https://forensicdiscovery.expert/here-are-five-byod-principles-to-consider-from-a-highly-respected-source/
#BYOD#DataSecurity#PolicyImplementation#SedonaConference#TechCompliance#digital forensics#forensic discovery#digital evidence#ediscovery
0 notes
Text
Secure Your Data on the Go: A Guide to Responsible Remote Wiping on Mobile Devices

#DataSecurityExpert#MobileDeviceManagement#BusinessContinuity#CybersecurityAwareness#ITProTip#EmployeeTechGuide#BYODPolicy#RemoteWorkSolutions#RemoteWipe#MobileSecurity#DataProtection#LostPhone#StolenPhone#TechTips#SecurityGuide#Cybersecurity#BYOD#BusinessTech
0 notes
Text
The idea of Bring Your Own Device (BYOD) has become increasingly prevalent in today's work environment. Employees are accessing company networks and carrying out work-related operations using their own smartphones, tablets, and computers.
0 notes
Text
WhatsApp, Slack, Teams, and other messaging platforms face constant security risks - Help Net Security
42% of businesses report employees with BYOD devices in business settings that use tools like WhatsApp have led to new security incidents, according to SafeGuard Cyber. Messaging platforms like WhatsApp, Telegram, Slack, and Teams face constant threats, emphasizing the need for robust protection. 66% of threat indicators are found in transient messages associated with these cloud-based…

View On WordPress
0 notes
Text
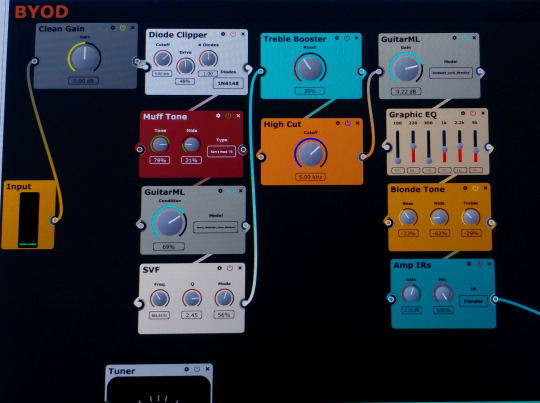
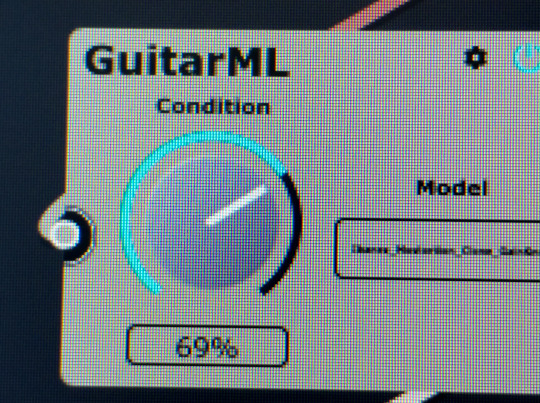

Most every creative process begins with inspiration.
Sometimes the lack of which is, ironically, inspiration enough, lol.
Clever folks, new tech, and accessibility are wear the robes of the muse time and time again.
Thus enter ChowDSP and GuitarML.
I cannot stress enough the coolness-factor of ChowDSP’s BYOD and the GuitarML module/tone library!
Needless to say, the upcoming release is using these HEAVILY!
If you’re a musician, producer, engineer etc., please give a look and listen to what these cats have on offer.
And support if you can!
#guitar#recording#software#guitarml#chow#chowdsp#BYOD#bringyourowndistortion#guitarpedals#guitarfx#guitareffects#recordingstudio#newmusic#mathrock#bigmuff#new music#guitar pedals#guitar effects#bring your own distortion#recording studio
0 notes
Text
BYOD (Bring Your Own Device), CYOD (Choose Your Own Device), COBO (Corporate-Owned, Business-Only), and COSU (Corporate-Owned, Single-Use) are revolutionizing the way we work. 🌐
With BYOD and CYOD, you have the freedom to work on your preferred devices, making productivity a breeze. COBO ensures top-notch security for company-owned devices, while COSU optimizes single-use devices for specific tasks.
Say hello to a new era of flexibility, security, and efficiency! 🙌🔒💼
0 notes
Text

Learn to configure Cisco Identity Services Engine (ISE) for seamless Bring Your Own Device (BYOD) onboarding, enhancing network security and user experience. Implement robust BYOD policies with ISE for fortified network access control. https://www.dclessons.com/configuring-ise-for-byod-onboarding
0 notes
Link
https://bit.ly/3QJOcmF - 🔐 Network Access Control (NAC) is a vital technology that controls access to network resources based on policies. It identifies, verifies, and assesses device compliance, granting access levels from full access to no access, with continuous monitoring for ongoing compliance. #CyberSecurity #NAC 📈 The Importance of NAC for Organizations: With growing endpoint usage and threat actors, automation provided by NAC reduces time, cost, and broadens potential attack surfaces. Features like Multi-Factor Authentication add an extra layer of security, making it essential for Zero Trust Security. #NetworkSecurity #ZeroTrust 🛠️ Types of NAC: Two essential forms - pre-admission and post-admission - provide a defense-in-depth strategy. Together, they keep threat actors from accessing network resources and discover unnoticed ones. #NetworkProtection 🎯 NAC Capabilities: These include Authentication, Role-Based Access Control, Device Profiling, Endpoint Security Assessment, Policy Enforcement, Quarantine, Remediation, and Integration with other solutions, adding a robust security layer. #NetworkManagement 🏆 Benefits of NAC: Enhancing security, saving costs through automation, streamlining user experience, and providing control, compliance, stronger authentication, are some of the key advantages. #CostSaving #Security 📱 Use Cases: NAC aids in managing BYOD, Network Access for Non-employees, IoT Devices, provides Visibility and Reporting, and helps in Incident Response, ensuring secure network handling across different scenarios. #IoTSecurity #BYOD 🧩 Choosing and Implementing a NAC Solution: Integrating NAC requires consideration of native integration with existing systems, all-in-one solutions, and planning. Steps like gathering information, managing identities, applying permissions, and regular updates are key. #NetworkIntegration In summary, Network Access Control (NAC) is pivotal in today's security landscape, offering protection, compliance, and enhanced user experience. Its implementation must align with the organization's structure and needs for optimal benefits.
#CyberSecurity#NAC#NetworkSecurity#ZeroTrust#NetworkProtection#NetworkManagement#CostSaving#Security#IoTSecurity#BYOD#NetworkIntegration#CyberSecurityAwareness#NetworkControl
0 notes
Text
0 notes
Text
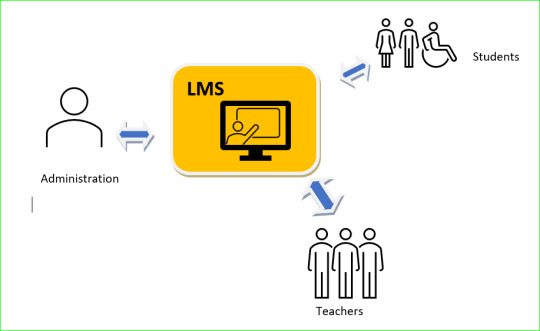
Competence in Digital Pedagogy
Digital environments and tools of a training organization related to teacher work Reflection on: Learning managements systems? Intranet content? Administration tools? School equipment or BYOD? Security issues? Communication platforms? Social media presence? With advancement in technology, the educational systems has been changing from paper work to digital, and the work has been becoming…
View On WordPress
0 notes
Text
BYOD Classrooms
The School of the Future

Introduction:
Technology is becoming increasingly prevalent in our daily lives, with new trends emerging in 2023 that are only expected to grow in the years to come. Schools and other educational institutions have been particularly impacted by this shift, as classrooms are now more interactive and enjoyable thanks to the incorporation of new technologies. It’s exciting to see how technology is transforming the way we learn and interact with one another.
Implementing a “bring your own device” (BYOD) policy is an excellent way to make learning more personalised and provide students with an opportunity to use technology that is familiar to them. With BYOD, students can access online resources, collaborate with peers, and personalise their learning experience in ways that weren’t possible before. Additionally, BYOD can help reduce the financial burden of purchasing individual devices for each student, as well as save time for educators who don’t need to manage multiple devices. By leveraging the power of BYOD, educators can create a more personalised learning environment that allows students to take control of their educational experience.
Discover a Technology Toolbox:
The modern virtual toolbox for an effective teacher includes the best apps and online programs for efficient instruction. We have found some of the most popular options that encourage collaboration among students, teachers, and family members, as well as those that give students more control of the content they learn. Google’s suite of tools is an amazing way to collaborate with others, both near and far. Through Google Drive, anyone can access and share content instantly with others. It’s great that the original file creator can assign permissions to other collaborators and view any changes that are made in real-time. Having this level of collaboration capability makes it much easier for teachers and students to work together on projects, no matter where they are located.
1 note
·
View note