#Advanced Mobile Surveillance System
Explore tagged Tumblr posts
Text
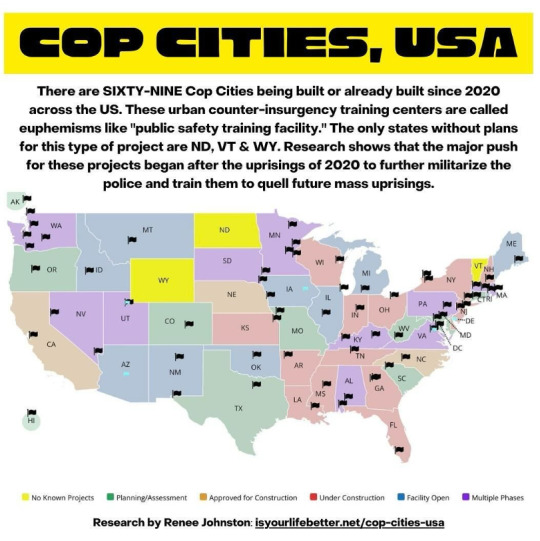
The Stop Cop City movement has sought to prevent the expropriation of part of the Welaunee Forest for the development of an 85-acre police mega training center: a model town to prepare the state’s repressive arms for the urban warfare that will ensue when the contradictions of their exploitation and extraction become uncontainable, as they did in 2020 after the APD murdered Rayshard Brooks. That murder, and all those that came before, were the lodestars of the Black-led movement during the George Floyd uprisings; their demands were no less than the dismantlement of the entire carceral system. Unable to effectively manage or quell the popular street movements, the Atlanta Police Foundation set out to consolidate and expand their capabilities for surveillance, repression, imprisonment, armed violence, and forced disappearance. One result is Cop City, which has been racked by militant sabotage, land occupation, arson, and popular mobilizations, in an attempt to end the construction and return Atlanta to its people. As the Atlanta Police Foundation was unable to contain the 2020 Black rebellion, so too have they been unable to quell the resistance against Cop City. The press reports that the project is hemorrhaging money and is mired in delays and difficulties. For their part, the city, the state, and the federal government, have in turn employed every tool in their power to destroy the movement. Last week, the Georgia State Senate passed a bill to effectively criminalize bail funds in the state; RICO charges have been contorted to target networks of support and care that surround the fighters; and last January, APD assassinated the comrade Tortuguita in cold blood while they rested in their tent in the forest. It is clear that Stop Cop City represents one of the conjunctural spear tips for expanding the existing systems of counterinsurgency that span Africa, Asia, and the Arab world. Today the system’s belly rests atop Gaza, whose rumblings shake the earth upon which we walk. Through its Georgia International Law Enforcement Exchange (GILEE) program, the APD has sent hundreds of police to train with the Zionist occupation forces. And in October 2023, after Tufan al-Aqsa, the Atlanta Police Department engaged in hostage training inside abandoned hotels, putatively intended to “defeat Hamas,” in an advancement of tactics for the targeting of Black people. With every such expansion, the ability of counterinsurgency doctrines to counteract people’s liberation struggles grows. The purpose of counterinsurgency is to marshal state and para-state power into political, social, economic, psychological, and military warfare to overwhelm both militants and the popular cradle—the people—who support them. Its aim is to render us hopeless; to isolate and dispossess us and to break our will to resist it by any and all means necessary. This will continue apace, unless we fight to end it. Stop Cop City remains undeterred: on Friday, an APD cop car was burnt overnight in response to the police operation on February 8; yesterday, two trucks and trailers loaded with lumber were burnt to the ground. An anonymous statement claiming credit for the former, stated: “We wish to dispel any notion that people will take this latest wave of repression lying down, or that arresting alleged arsonists will deter future arsons.” As the U.S. government and Zionist entity set their sights on the Palestinian people sheltering in Rafah, as they continue their relentless genocide of our people in Khan Younis, Jabalia, Shuja’iyya, and Gaza City, the Stop Cop City movement has clearly articulated its solidarity with the Palestinian struggle. They have done so with consistency and discipline, and we have heard them. Our vision of freedom in this life and the next requires us to confront and challenge the entangled forces of oppression in Palestine and in Turtle Island, and to identify the sites of tension upon which these systems distill their forces. This week, as with the last three years, the forest defenders have presented us one such crucible.
(11 Feb 24)
National Lawyers Guild, Stop All Cop Cities: Lessons For a National Struggle (video, 1 hr 45 min)
1K notes
·
View notes
Text
CONFIDENTIAL LOGISTICS REPORT
DRC, Planning & Evaluation Office, Logistics & Infrastructure Division
Date: [REDACTED]
To: Director [REDACTED]
From: Administrator [REDACTED], Logistics & Infrastructure Division
Subject: Facility Expansion: New Paternity Compound Construction
Executive Summary
This report outlines the ongoing expansion of DRC-operated paternity compounds across several strategic locations nationwide. In response to increasing insemination rates and projected surrogacy demands, we have begun constructing new high-capacity compounds to accommodate more surrogates. These expansions will enable the DRC to streamline the conscription process, optimize surrogacy cycles, and ensure our ability to meet the population sustainability targets outlined for the next fiscal period.
The new compounds focus on enhanced security, specialized medical equipment, and increased surrogacy capacity.
I. Facility Expansion Overview
Strategic Locations and Site Selection
To ensure regional coverage and minimize travel time to detain and inseminated surrogates, the DRC has approved the construction of [REDACTED] new paternity compounds in FEMA Zones 4, 6, 7, and 8. These facilities will be situated in [REDACTED] areas, selected for their proximity to population centers, existing transport infrastructure, and relative isolation, ensuring operational security.
Zone 4: Atlanta, GA
Zone 6: Houston, TX
Zone 7: Omaha, NE
Zone 8: Denver, CO
Each compound is designed to accommodate [REDACTED] surrogates at any given time, with the ability to scale up to [REDACTED] in emergencies. Construction is scheduled for completion within the next [REDACTED] months, with the first inspections set to begin by [REDACTED] this year.
Paternity Compound Design Features:
High-Capacity Paternity Wards: Each compound contains specialized wards designed to manage surrogates carrying up to sedecatuplets (16), with private rooms for those at risk of premature labor.
Enhanced Monitoring Systems: Advanced surveillance and biometric monitoring ensure constant oversight and swift response to emergencies.
Security Enhancements: Reinforced containment protocols, secure access points, and patrol routes have been established to prevent unauthorized access and ensure surrogate compliance.
II. Specialized Equipment and Medical Support
Given the unique demands and expectations placed on surrogates, each paternity compound will be equipped with advanced medical infrastructure to ensure the safety and effective management of extreme weight gain, reduced mobility, and increased risks of organ stress.
Key Equipment and Infrastructure:
Reinforced Support Beds: Traditional hospital beds have proven insufficient for surrogates carrying high multiples, whose pregnancies can lead to total weight gains exceeding 200 lbs. Each ward will feature reinforced, adjustable support beds capable of accommodating extreme weights. These beds will be equipped with pressure-relief systems to minimize discomfort and reduce the risk of bedsores for near-immobile surrogates.
“I hate that I’m here! But… all I have is this bed! I can’t move, I can’t breathe half the time, but at least I have a fucking memory foam mattress!” - Surrogate S118-176-J, 27 days pregnant with decatuplets (10)
Automated Feeding & Hydration Systems: Automated systems will ensure continuous nutrition and hydration to support surrogates with reduced mobility. Given the caloric intake requirements for such pregnancies, these systems will monitor and adjust fluid and nutrient delivery, reducing the need for frequent staff intervention.
“I’m basically just a machine now, aren’t I? They hook me up, pump me full of these stupid protein shakes, and keep me breathing so I can keep carrying these bowling ball-sized kids. It’s disgusting!” - Surrogate S117-138-N, 18 days pregnant with quattuordecatuplets (14)
Custom Mobility Aids: Custom-designed lift systems and mobility aids will be integrated into each ward to facilitate the movement of surrogates. These devices will allow for safe repositioning, transfers to specialized birthing chairs, and support during transport.
“I don’t know how they expect us to move with this much weight on us. Even standing feels like my legs are going to snap. Those lifts? They’re humiliating... but without them, I wouldn’t be able to get out of bed at all.” - Surrogate S120-494-P, 30 days into a sedecatuplets (16) pregnancy
Advanced Fetal Monitoring: Each compound will have real-time ultrasound and biometric monitoring stations to track fetal development. Given the accelerated gestational period, these systems will continuously update fetal positioning, size, and viability, enabling rapid response to complications.
"It’s terrifying. Knowing how big they are, how many there are… they’re not coming out normal. When I finally pop them all out, they’ll get better care than I ever did!" - Surrogate S119-667-N, 22 days pregnant with hendecatuplets (14)
Dedicated Obstetrics & Neonatal Care Units: Immediate neonatal care is essential, and each compound will include state-of-the-art neonatal intensive care units (NICUs) to support newborns. Advanced incubators and respiratory support systems will ensure the survival of even the most premature babies.
"They always tell me how important it is to ensure the babies survive, even if I don’t. I get it, I do… but knowing there’s a whole team of people ready to take over the second I’m gone? It’s like they’ve already decided how this ends." - Surrogate S117-856-M, 8 days pregnant with tridecatuplets (13)
Pain Management and Sedation Systems: Surrogates will experience extreme discomfort and physical strain. Each paternity ward will be equipped with integrated IV pain management systems, allowing for both localized and systemic pain relief. Sedation protocols can be initiated remotely if a surrogate's distress becomes vocal, ensuring they can not incite civil disorder.
“I’m so big I can’t even see my dick, which is now buried under all these babies and fat. I’d be lying if I said the meds didn't help to blitz me out of my mind... a caring them I'm a gigantic incubator now.” - Surrogate S119-461-L, 11 days pregnant with dodecatuplets (12)
Future Equipment Developments: Research teams are exploring next-generation mobility aids, including exoskeleton support harnesses, to provide mobility assistance for late-term surrogates. These innovations aim to improve surrogate survival to deliver full-term pregnancies. Once available, prototypes will be tested in select compounds.
III. Expansion Strategy: Future Projections and Scaling
Projected Surrogacy Demand: With the increase in insemination rates, each compound is expected to handle up to [REDACTED] inseminations per month once fully operational. This translates to a need for approximately [REDACTED] newborns annually to meet population sustainability targets. Our current projections indicate that these numbers are achievable.
IV. Conclusion and Recommendations
The successful construction and operation of these new paternity compounds are critical to effectively maintaining the DRC’s ability to enforce surrogacy mandates. Our specialized equipment and infrastructure improvements will ensure we meet demands while preserving control over our surrogate.
Report submitted by: Administrator [REDACTED], Logistics & Infrastructure Division
----------------
Sending...
Sending...
Sending...
Read...
----------------
To: Administrator [REDACTED], Logistics & Infrastructure Division
From: Director [REDACTED], DRC
Subject: RE: Facility Expansion: New Paternity Compound Construction
Dear Mr. [REDACTED],
I’ve reviewed the latest progress report on the new Paternity Compounds, and I must commend your team on the impressive strides made thus far, even with the ambitious timeline we’ve set.
I have been particularly interested in the improvements to our birthing suites. As you are well aware, managing multiple pregnancies presents unique challenges.
We are entering a critical phase. I want to emphasize that these upcoming births will set a precedent for all future operations. The successful use of these new facilities will allow us to demonstrate that our methods ensure the next generation's survival and that we can handle the demands without sacrificing efficiency or outcomes.
I look forward to seeing the first results when the initial surrogates reach full term and the birthing suites are fully operational.
Keep up the excellent work, and do not hesitate to reach out if additional resources or support are needed to ensure success.
Regards, Director [REDACTED]
----------------
Click Here to return to DRC Report Archives

#ai mpreg#male pregnancy#mpreg#mpreg kink#mpreg belly#pregnant man#mpreg morph#mpreg caption#mpregbelly#mpregstory#mpreg birth#mpreg art#mpreg story#mpregnancy#mpreg roleplay#male pregnant#caucasianmpreg
213 notes
·
View notes
Text
Humans are weird: Military Industrial Complex
( Please come see me on my new patreon and support me for early access to stories and personal story requests :D https://www.patreon.com/NiqhtLord Every bit helps)
Summary report of Terran Republic
Homeworld: Terra. Alias: Earth
Territory: 23 Planets 16 Star Systems 54 Orbital Stations 267 Asteroid Mining Operations
Population: 20.9 Billion
Military Threat Level: Red
Technological Level: Yellow
Personal Log from observer Nul Yand
“On the surface the Terran Republic should not even exist.
Their technological level is far below their neighbors such as the Olon Alliance or the Fenrar Empire.
They barely have the means to travel between their worlds and even then it requires months when the previously mentioned governing bodies can do it in days.
The one quality these humans have that has kept them alive for so long is the scope of their military; or more accurately their military industrial complex.
One could be forgiven for equating the two to be one in the same, but the distinction is made quite obvious when dealing with humans.
Their military operates under three branches known as the Fleet, the Army, and the Home Guard.
The fleet maintains the various orbital and suborbital craft almost completely. This ranges from the kilometer long Kepper Warships to atmospheric attack craft and is the primary partner for the second branch as a means to travel between worlds.
The army is made up of ground forces ranging from standard infantry to heavy mobile assault tanks. During times of war they are the spear tip and conduct numerous covert operations against human aggressors. When these operations are not enough the ground forces are then deployed which conduct full scale planetary invasions or man the numerous defensive forts dotted throughout their territory.
The final branch is the least militaristic of the three but serves a crucial role nonetheless. Home Guard serves as the eyes and ears within the human domain as a sudo military surveillance force. They enforce the laws while also rooting out enemies to said laws such as common gang members to spy’s and collaborators.
All three of these organizations are supplied through what is known as the human Military Industrial Complex.
The MIC is not a single entity but a collection of private corporations, weapon manufacturers, scientific committees, political lobbyists, and countless other unnamed groups who have saw fit not to make themselves known.
They provide the human military with a near endless supply of weaponry, ammunition, vehicles, ships, and more ensuring that at no time are their forces underequipped.
Research divisions conduct numerous lines of inquiry which include biological and advanced robotics. This has resulted in the military having a wide variety of advanced war machines such as the attack bot 5000, and the UAV dubbed “Seekers” which are capable of tracking down individual targets across an entire planet.
The biological division has made several advances in medical technology which have equally contributed with the production of Healing Pods which can induce accelerated healing process for even the most injured soldier. On the more questionable front they have also created several strains of lethal viruses to be used against enemy combatants. Rumor is that the Red Vein Plague was one such concoction when the war against the Tumari began taking a turn for the worse against humanity.
With this vast network of resources, the Terran military has been able to adapt to nearly any situation it has faced allowing it to survive even against impossible odds.
When the vast fleet of organic Milnani ships invaded human borders it was expect the human fleets would be wiped out within the first week. The first few engagements resulted in losses, but by the third engagement the humans had deployed new boring missiles that chewed through the thick hide of Milnani ships and dispersed a lethal toxic into the ships bloodstream. Within minutes the ships were violently convulsing as entire portions were torn open from muscle spasms, exposing the passengers to the cold void of space.
When the Tucmal used their advanced weaponry advantage to conquer an outlying colony, the human military dispatched a covert strike team to capture one of the weapon platforms and return it to a research lab on Omega VI. A month later effective shields had been deployed to counteract Tucmal weaponry rendering it useless. A week later the first phase plasma canons were being deployed that could burn through Tucmal armor protecting weapon platforms
When a War Sphere was deployed to obliterate the human homeworld a relay station was deployed to follow it just outside of weapons range. A cryptology team intercepted all incoming transmissions and was able to decipher the communications from the war sphere back to whoever was controlling it thanks to a recently acquired quantum gen III computer and over two dozen alien speakers who had been “invited” to a private facility. The team was able to interject into the transmissions and send a new command to turn around, return to its point of origin, and destroy the planet it came from. They then ordered it to turn off its transmission center so the human command could not be countermanded. In short order the war sphere followed its new directive and returned to its point of origin somewhere in the Ocares Sector.
This shadowy collective has been a backbone of human survival and though many have sought to remove this bountiful source of progress none have been able to completely destroy the MIC. Research groups have been tracked down and their teams wiped out to the man only for another group to take up the notes half a sector away. Factories and facilities obliterated in orbital bombardments were relocated to space stations orbiting no stars in the space between systems off all charts and maps.
It was deemed that only an overwhelming force of unprecedented vastness striking all at once would be sufficient to deal a crippling blow to the MIC. This in of itself however has proved a problem as to gather such a force would almost immediately be noticed and countered before it could even be put into motion.
My recommendation would be to isolate humanity and avoid combat as much as possible.
If conflict is inevitable then it must be prevalent that all significant technology not fall into their hands lest it be deconstructed and used against us.
Only then do we have a slight chance of victory."
#humans are weird#humans are insane#humans are space oddities#humans are space orcs#scifi#story#writing#original writing#niqhtlord01#military industrial complex
109 notes
·
View notes
Text

How powerful is a U.S. aircraft carrier?
A U.S. Navy aircraft carrier is a large warship designed to serve as a mobile airbase for naval aviation. It is the centerpiece of a carrier strike group (CSG) and plays a crucial role in projecting power, protecting maritime interests, and providing humanitarian assistance worldwide.
Key features of a U.S. Navy aircraft carrier include:
Flight Deck: The carrier's flight deck is where aircraft take off and land. It is equipped with catapults for launching fixed-wing aircraft and arresting gear to catch aircraft on landing. The flight deck is one of the busiest and most dangerous places on the ship during flight operations.
Hangar Deck: Below the flight deck is the hangar deck, where aircraft are stored, maintained, and prepared for flight operations. It provides sheltered storage for aircraft and equipment, as well as maintenance facilities and workshops.
Air Wing: The carrier's air wing typically consists of a mix of fighter jets, bombers, reconnaissance aircraft, early warning aircraft, and helicopters. These aircraft provide offensive and defensive capabilities, including strike missions, air superiority, surveillance, and search and rescue.
Command and Control Center: Aircraft carriers serve as command centers for naval task forces, with advanced communication and information systems to coordinate operations. They have the capability to direct air, surface, and subsurface assets in complex operations.
Defense Systems: Carriers are equipped with a variety of defense systems to protect against threats such as enemy aircraft, missiles, and submarines. These include radar systems, anti-aircraft missiles, close-in weapon systems, and electronic warfare capabilities.
Overall, U.S. Navy aircraft carriers are among the most powerful and versatile warships in the world, capable of projecting power, maintaining presence, and providing support in a wide range of military operations.
84 notes
·
View notes
Text
In December 2024, Ukrainian forces operating north of Kharkiv reportedly conducted their first ever attack on Russian positions using exclusively unmanned technologies. This landmark military operation, which featured a combination of machine gun-equipped ground drones and kamikaze aerial drones, underscored Ukraine’s increasingly sophisticated use of robotic systems, while also highlighting the evolving role being played by these technologies on the modern battlefield.
As Ukrainian commanders prepare for a fourth year of combat in Europe’s largest war since World War II, they are now hoping that their country’s growing arsenal of robotic systems can help counter Russia’s often overwhelming advantages in both manpower and firepower. “Ukrainian officials have repeatedly highlighted Ukraine’s efforts to utilize technological innovations and asymmetric strike capabilities to offset Ukraine’s manpower limitations in contrast with Russia’s willingness to accept unsustainable casualty rates for marginal territorial gains,” noted the Institute for the Study of War in late 2024.
Ukraine’s emphasis on unmanned robotic systems certainly makes good sense. While overall Ukrainian casualties during the first three years of the full-scale invasion are thought to be significantly lower than Russian losses, Russia’s far larger population means Ukraine has little prospect of success in a grinding war of attrition. Over the past year, reports of Ukrainian mobilization challenges and personnel shortages have become more and more frequent, with desertion rates also reaching record highs.
With the Ukrainian military outnumbered and outgunned, defense tech innovations have played an important part in Kyiv’s war effort since 2022. Many of Ukraine’s key advances have come via the country’s vibrant startup sector, much of which pivoted to military projects in the wake of Russia’s full-scale invasion. In July 2024, the Associated Press reported that Ukraine had developed an ecosystem of laboratories to create a robot army, with around 250 defense startups active in secret locations “that typically look like rural car repair shops.”
The Ukrainian government has sought to support these grassroots efforts with the creation of initiatives like the BRAVE1 defense tech cluster, which was established in spring 2023 to streamline cooperation between the private sector, the state, and the Ukrainian military. In a move hailed by officials in Kyiv as a unique development, Ukraine launched a dedicated drone warfare branch of the country’s military in summer 2024. The establishment of Ukraine’s Unmanned Systems Forces demonstrated that Kyiv was preparing for “the war of the future, not the war of the past,” commented USF commander Colonel Vadym Sukharevskyi.
Robotic systems alone cannot solve the Ukrainian military’s manpower shortages. At present, the focus is on developing technologies capable of performing a range of specific combat and logistical tasks. For example, Ukraine plans to deploy tens of thousands of robotic ground vehicles along the one thousand kilometer front line of the war during 2024. These systems will handle functions including mine-laying and de-mining, the delivery of ammunition and other supplies to troops in trenches, and the evacuation of wounded soldiers to rear positions where they can receive medical treatment.
Unmanned ground vehicles are seen by Ukrainian military planners as a particularly effective response to the ubiquity of reconnaissance and attack drones above the battlefield. With the entire front line area now under more or less constant surveillance, it can be extremely difficult for soldiers to move about above ground, and virtually impossible to travel in vehicles without electronic jamming devices. Robotic systems capable of operating in dangerous environments can go some way to addressing this problem, and can help make sure front line units are resupplied in a timely fashion.
The Ukrainian army’s use of robotic systems is already attracting consideration international attention. With new models typically undergoing testing in combat conditions, the cycle from development to deployment is often exceptionally dynamic, creating unprecedented opportunities for defense tech companies. Maintaining Ukraine’s current rapid pace of innovation is recognized as vital in order to remain one step ahead of Russia, which is also investing heavily in robotic systems and drones.
With Ukrainian efforts to implement AI technologies expected to advance in 2025, there are concerns that the fledgling robot armies currently taking shape on the battlefields of Ukraine could reduce the barriers to killing and dramatically escalate the potential for future conflicts. However, with their country fighting for survival, Ukrainian defense tech developers are primarily concerned with saving the lives of their compatriots and defeating Russia’s invasion.
15 notes
·
View notes
Text
The SPARTANS Breakdown.

G.R.O.W. BULWARK – Heavy Assault Mech "Battlefield Utility Leviathan & Warfare Armored Response Keeper"
Designation: SPARTANS-BW-100 "BULWARK" Role: Anti-Superhuman Heavy Combat Unit Manufacturer: G.R.O.W. Advanced Warfare Division First Deployment: 2113
Overview:
The BULWARK-class SPARTAN is the largest and most heavily armed unit in the SPARTANS division, designed to provide extreme firepower and suppression capabilities against high-threat superhumans. While highly durable and powerful, these mechs still struggle against S-Rank and above superhumans, as demonstrated in 2125, when 100 BULWARKS were deployed against the villain Gluttony—only to be completely obliterated.
Specifications:
Frame & Armor:
• Height: 7 meters (23 feet)
• Weight: 19 metric tons
• Armor Composition:Titanium-Nanopolymer Composite with Adaptive Shock Absorption Plating
• Structural Reinforcement: Can withstand explosive impacts, energy blasts, and high-caliber rounds
Power System:
• Core Reactor: Hybrid Plasma-Fusion Core
• Backup Energy Source: High-Capacity Quantum Batteries (2-hour reserve)
Weapon Systems:
• HYPERION Rail Cannons (x2, forearm-mounted)
• Fires hyper-accelerated tungsten slugs at Mach 6
• Can punch through a city block in a single shot
• Limited effectiveness against teleporters or regenerators
• ARES Missile Pods (x4, shoulder-mounted)
• Carries EMP warheads, high-explosive rockets, and cryo-missiles
• Smart-tracking system with target adaptation AI
• CERBERUS Plasma Repeater (Right Arm-Mounted)
• Rapid-fire particle cannon for crowd control and area suppression
• Capable of burning through armored vehicles in seconds
• DAMPENING FIELD GENERATOR
• Creates a localized power-nullification zone (100m radius)
• Less effective against SS-Rank and above superhumans
• TITAN-Class Energy Shield (Deployable, Back-Mounted)
• Can withstand direct hits from S-Rank energy blasts
• Limited duration (~5-minute sustain)
AI & Combat Systems:
🧠 Neural Combat Processor:
• Advanced predictive combat algorithms allow it to anticipate enemy movements
• Records and analyzes superhuman battle data to improve efficiency
🚀 Mobility & Locomotion:
• Digitigrade leg structure allows for improved speed and agility
• Thruster-Assisted Jumps for repositioning and heavy-landing shock attacks
Weaknesses:
Despite its overwhelming firepower and tactical AI, the BULWARK suffers significant drawbacks when fighting SS-Rank and above superhumans:
• Energy Consumption:
• The power-nullification field burns out when overused
• Plasma-based weapons drain reserves quickly
• Speed & Agility Limitations:
• BULWARKs are slower than most high-tier superhumans
• Easily outmaneuvered by teleporters or hyper-speed combatants
• Durability Issues Against High-Tier Opponents:
• While heavily armored, S-Rank+ superhumans can rip through its plating
• Gluttony’s spear, Gáe Bulg, effortlessly pierced through its core
🔥 The Gluttony Massacre (2125) 🔥
• In one of the largest anti-superhuman operations in history, 100 BULWARKS were deployed to stop Gluttony.
• She effortlessly dismantled them, using her overwhelming strength, speed, and soul absorption abilities.
• Within 15 minutes, every single BULWARK was destroyed, marking the largest recorded failure of the SPARTANS program.
Final Verdict:
The BULWARK is an unmatched force against B-A Rank superhumans, but it remains outclassed by higher-tier threats. While it is humanity’s best answer to superhuman warfare, its limitations against god-like opponents leave G.R.O.W. still searching for better solutions.
---------------------------------------------------------------------------

G.R.O.W. WRAITH – Surveillance & Pursuit Drone "Weaponized Reconnaissance and Adaptive Infiltration Tactical Hunter"
Designation: SPARTANS-WR-300 "WRAITH" Role:Reconnaissance, Surveillance, High-Speed Pursuit Manufacturer: G.R.O.W. Advanced Warfare Division First Deployment:2115
Overview:
The WRAITH-class SPARTAN is a fast, highly intelligent aerial drone designed for tracking, monitoring, and capturing rogue superhumans. Equipped with cutting-edge stealth technology, high-speed propulsion, and long-range sensors, WRAITHs act as the eyes and ears of G.R.O.W., constantly scanning cities for superhuman activity.
These drones are particularly effective against C-A Rank superhumans, but struggle against S-Rank and above due to their limited combat capabilities.
Specifications:
Frame & Armor:
• Size: 3 meters (9.8 feet) in width
• Weight: 2.3 metric tons
• Armor Composition:Adaptive Nano-Polymer Shell (stealth-coated, resistant to energy interference)
• Structural Integrity: Highly durable but not designed for prolonged combat
Power System:
• Core Reactor:Quantum Micro-Core for long-term surveillance
• Backup Power Source:Solar-Nano Capacitors (can sustain operations for weeks without recharge)
Weapon Systems:
• STASIS Tethers (x2, deployable from underside)
• Fires electromagnetic capture tethers to restrain or immobilize targets
• Can paralyze lower-tier superhumans for up to 10 minutes
• TRANQUILIZER DART SYSTEM
• Loaded with neurotoxins and sedatives
• Can incapacitate C-A Rank targets instantly
• TASER DISCHARGE ARRAY
• Emits a 300,000-volt pulse to stun or disable enemies
• Ineffective against energy-immune superhumans
• HIGH-POWER PLASMA CANNON (Underbelly Mounted)
• Fires a precision plasma bolt capable of melting through steel
• Not effective against SS+ Rank threats
AI & Combat Systems:
🧠 Tactical Intelligence Processor:
• Operates autonomously with real-time decision-making AI
• Predictive tracking algorithms allow it to anticipate enemy movements
• Data collection system uploads enemy combat patterns to G.R.O.W.'s database
👁️ Surveillance & Sensors:
• Omni-Directional Optics: 360-degree thermal, night-vision, and X-ray scanning
• Quantum-Signal Receiver: Can tap into encrypted communications
• Long-Range Tracking Beacons: Detect energy signatures up to 50 kilometers away
🚀 Mobility & Flight Capabilities:
• Antigravity Propulsion System for silent flight
• Adaptive Wing Configuration for high-speed maneuvering
• Top Speed: Mach 1.5 (low atmosphere)
• Sub-Orbital Capability: Can reach the upper atmosphere for high-altitude monitoring
Weaknesses & Defeat Against S+ Rank Superhumans
Despite its cutting-edge technology and stealth systems, WRAITH-class drones are ineffective against S-Rank and above superhumans, due to the following limitations:
• ⚡ Limited Firepower:
• While equipped for subduing low-to-mid-tier superhumans, WRAITHs lack high-damage output
• S+ Rank targets can easily resist its stasis fields and tasers
• 🚀 Durability Issues:
• The armor is designed for stealth, not direct combat
• Powerful superhumans can destroy a WRAITH with a single strike
• 📡 Signal Interference:
• Psychic superhumans or energy manipulators can disrupt its AI systems
• Teleporters can easily evade or outmaneuver them
🔥 Notable Failure: The Gluttony Incident (2125) 🔥
• During the infamous 2125 battle, 163 WRAITH drones were deployed to track and intercept Gluttony.
• However, she effortlessly bypassed their tracking systems and obliterated them using her soul chains before they could even deploy their capture tethers.
• This failure demonstrated that WRAITHs were completely ineffective against SSS+ Rank threats, leading G.R.O.W. to reconsider its reliance on autonomous drones.
Final Verdict:
The WRAITH-class SPARTAN is the pinnacle of reconnaissance and pursuit technology, but its lack of offensive capabilities makes it ineffective against top-tier superhumans. While still a critical tool for surveillance, tracking, and capturing lower-ranked threats, G.R.O.W. is actively researching ways to improve its combat performance against world-ending adversaries.
---------------------------------------------------------------------------
G.R.O.W. SEEKER – Enforcement Android "Synthetic Enforcement and Engagement Kill/Evade Reconnaissance" Units
Designation: SPARTANS-SK-2000 "SEEKER" Role:Reconnaissance, Surveillance, Enforcement, CQC Engagement Manufacturer: G.R.O.W. Advanced Warfare Division First Deployment:2116 Advanced humanoid combat droids for law enforcement and superhuman suppression.
Overview:
SEEKERS are highly adaptive humanoid androids developed by G.R.O.W. to serve as frontline operatives in dealing with superhuman threats. Their primary function is non-lethal takedowns, but they can engage in lethal combat when authorized. Designed with cutting-edge nanite morphing technology, they can reshape their arms into various tools and weapons, providing unmatched versatility. SEEKERS are also equipped with advanced combat AI, capable of predictive modeling to counter enemy movements. They balance stealth, adaptability, and raw combat prowess, utilizing advanced AI, modular weapon systems, and nanite-based armor. SEEKERS function independently or in coordinated squads, making them an essential asset for tracking, containing, and neutralizing Deviants or rogue Enhanced individuals.
Specifications:
Frame & Armor:
• Size: 2.3 meters (7.5 feet)
• Weight: 1.2 metric tons
• Armor Composition:
• Tier-VII Hybrid Plating (Ghost Model);
• Lightweight & Flexible (Allows for high-speed movement).
• Absorbs low-caliber ballistics, plasma rounds, and minor concussive blasts.
• Weak against heavy armor-piercing projectiles.
• Titanium-Carbide Plating (Overlord Model);
• Heavy Combat Armor designed to endure direct superhuman strikes.
• Highly resistant to plasma, lasers, and most energy-based attacks.
• Weak against corrosive or nanite-based weaponry.
• Adaptive Stealth Armor (Phantom Model – Experimental);
• Can shift textures to create optical camouflage.
• Low durability but completely silent.
• Structural Integrity: • Reinforced Endoskeleton: Composed of Graphene-Titanium Alloy, making it 5x stronger than human bones. • Synthetic Muscle Weave: Provides enhanced strength & flexibility, allowing SEEKERS to move faster than most Enhanced humans. • AI Core Protection:ORACLE AI Core is embedded within the torso, protected by anti-EMP shielding to prevent hacking attempts.
Power System:
• NOVA Fusion Core: Miniaturized cold fusion reactor providing energy for up to 96 hours of continuous operation. • Overload Mode Drawback: Excessive use causes rapid power drain, requiring a full reboot after 3 minutes of operation.
• Vulnerabilities:
• EMP Exposure: While resistant, a direct EMP burst can force a temporary shutdown.
• Sustained Damage: Severe damage to joints can hinder movement until repairs are conducted.
SEEKER CLASSIFICATIONS:
• SEEKER (Model-01 "Ghost") [The white android]
• Holographic Projection: This model can create decoy images and camouflage itself with advanced light-bending technology.
• Stealth-Oriented: Operates best in urban environments, infiltrating and monitoring high-risk areas.
• Non-Lethal Priority: Primarily designed for apprehension, equipped with taser-based projectiles, EMP pulses, and nanite restraints.
• Combat AI: Capable of adapting to various combat styles, predicting movements with a 0.3-second delay reduction.
• SEEKER (Model-02 "Overlord") [The black android]
• Overload Mode: When engaged, this unit burns through energy reserves for a significant boost in strength, speed, and durability for close-quarters combat (CQC).
• Heavy Combat Focus: Prioritizes engaging physically enhanced superhumans that require brute force suppression.
• Shockwave Emitters: Capable of releasing concussive blasts to disorient or knock back opponents.
• Power Limitations: Overload Mode can only be sustained for a maximum of 3 minutes before system overheating, requiring cooldown.
AI & COMBAT SYSTEMS:
1. Combat AI ("ORACLE" OS):
• Powered by "ORACLE" (Omni-Response Adaptive Combat Learning Engine), an adaptive AI combat processor.
• Capable of predicting enemy movements with a 0.3-second response time based on observed fighting styles.
• Integrates with G.R.O.W. tactical networks, allowing instant battlefield awareness and strategic coordination with BULWARK, WRAITHS, and Overwatch teams.
• Limited self-learning capabilities—SEEKERS can adjust per mission but require external updates to retain experiences long-term.
2. Combat Modes:
SEEKERS are programmed with multiple combat modes, toggled based on engagement protocols:
• STANDARD MODE (Passive Surveillance / Apprehension Focused)
• Non-lethal combat priority (taser weapons, shockwave suppressors, nanite cuffs).
• AI prioritizes evasive maneuvers & disabling strikes.
• EXECUTION MODE (High-Priority Target Elimination)
• Lethal force authorization engages plasma weaponry, energy blades, and Overload Mode.
• Predictive combat system prioritizes direct neutralization over capture.
• SIEGE MODE (Team Coordination & Suppression)
• Integrates with BULWARKs & WRAITHs for coordinated strikes against high-tier targets.
• Deploys area-based weapons (shockwave detonators, localized EMP blasts).
• STEALTH MODE (Ghost Model Only)
• Uses holographic projection & optical cloaking for reconnaissance or assassination.
• AI automatically avoids detection and disables threats silently.
WEAPON SYSTEMS:
SEEKERS are designed to handle both enhanced individuals and heavily armored targets, utilizing modular weapon systems.
1. PRIMARY ARMAMENTS
✔ Adaptive Nanite Arms: SEEKERS can morph their forearms into weapons or tools in real-time. ✔ Tachyon Blades: High-frequency plasma blades capable of cutting through most organic & armored targets. ✔ Plasma Pulse Projectors: Wrist-mounted plasma cannons for ranged attacks. ✔ Electromagnetic Shock Emitters: Short-range concussive bursts to disable foes or disrupt energy-based abilities.
2. SECONDARY SYSTEMS
✔ EMP Charges: Disrupts cybernetics & energy-based abilities in 10-meter radius. ✔ Taser Darts: Fires from forearm (Non-lethal but can be lethal on max settings). ✔ Stasis Nanites: Deployable nanite webbing to immobilize enemies temporarily.
3. UNIQUE MODEL-SPECIFIC WEAPONS

4. PROPULSION SYSTEMS & MOBILITY
• Kinetic Boosters (Legs): Allows SEEKERS to dash at speeds up to 200 km/h in short bursts. • Magnetic Locking System: Allows them to walk on walls or ceilings. • Thruster Assisted Jumps: Enables 10-15 meter leaps for rapid repositioning.
SEEKER PERFORMANCE METRICS [Compared to peak & enhanced individuals]

Standard Features for All SEEKERS:
• Nanite-Based Morphing Technology: Allows transformation of arms into weapons like stun batons, plasma-based tasers, and energy shields.
• AI Combat Adaptation: Predicts enemy actions based on past encounters, optimizing battle performance.
• Plasma Response System: In lethal scenarios, SEEKERS can switch to plasma weaponry to engage hostile threats effectively.
• Rapid Repair Protocols: Minor damages can be self-repaired via nanites, though severe damage requires external maintenance.
Weaknesses & Limitations:
• Power Drain Issues: Advanced functions like Holographic Projection and Overload Mode can drain reserves quickly, making them ineffective in prolonged battles.
• Struggles with S-Rank+ Superhumans: While SEEKERS are highly effective against C-A Rank threats, they are heavily outmatched against S-Rank and above, requiring additional support from BULWARKS or specialized teams.
• EMP Vulnerabilities: While resistant to low-grade EMPs, strong electromagnetic pulses can temporarily disable them.
• Combat Learning Restrictions: SEEKERS adapt to combat situations quickly, but their AI is still limited compared to organic, unpredictable combatants.
Final Verdict:
SEEKERS are G.R.O.W.'s elite combat androids, designed for high-speed adaptability and tactical superiority. The White Seeker specializes in holographic projection, deception, and recon, while the Black Seeker sacrifices illusions for raw power, utilizing an Overload Mode to burn through energy reserves for devastating CQC engagements. Both feature advanced AI, predictive combat algorithms, and hyper-durable nanocomposite armor, making them formidable opponents. However, they struggle against S-Rank superhumans due to raw power discrepancies. Despite this, SEEKERS remain indispensable for countering lower-tier Empowered threats, conducting assassinations, and executing high-risk operations with precision and efficiency.
Seeker Ghost Model:

Seeker Overlord Model:

Seeker Phantom Model(not in use):

10 notes
·
View notes
Text








Created by our very own General Clark and our daddy, welcome the M.I.U #CLARKS unit and the B.M.P systems, designed to boomerang missiles back to sender with our mobile interceptor computerized unit with $3million buck price tag. Training costs $150k per personnel/180hr. Made in #usa
Typical war unit of yesterday:
During a war, missile launches are typically commanded through a complex system involving multiple personnel and technologies. Here's a general overview:
Authorization: The decision to launch missiles usually comes from high-ranking military officials or government leaders.
Targeting: Military personnel identify and designate targets using various systems, such as radar, surveillance, or intelligence gathering.
Launch command: Authorized personnel enter launch codes or passwords into the missile's control system, verifying the command.
Guidance systems: The missile's guidance system, such as GPS or inertial navigation, guides the missile to its target.
The specific commands and protocols vary depending on the military branch, country, and type of missile system. Some common command structures include:
Air defense systems: Commanded by air defense officers or radar operators.
Ballistic missile systems: Commanded by launch officers or missile crew members.
Cruise missile systems: Commanded by naval or air force personnel.
These systems often involve multiple checks and balances to ensure accurate targeting and minimize the risk of unauthorized launches.
The price tag for missile defense systems and interceptor missiles can be substantial, varying widely depending on the specific system, technology, and quantity. Some examples:
Patriot missile defense system: Estimated cost per interceptor missile: $3-4 million
THAAD (Terminal High Altitude Area Defense) system: Estimated cost per interceptor missile: $10-15 million
SM-3 (Standard Missile 3): Estimated cost per interceptor missile: $10-20 million
Aegis BMD (Ballistic Missile Defense) system: Estimated cost per ship: $1-2 billion (not including interceptor missiles)
The "boomerang missile" concept you mentioned earlier would likely require significant investment in research, development, and production, potentially costing hundreds of millions or even billions of dollars.
Keep in mind that these estimates can vary depending on various factors, including production quantities, technological advancements, and contractual agreements.
#covid#travel#black lives matter#donald trump#phillipeclark#phillip e clark#lifestyle#government#social media#politics#military#war
5 notes
·
View notes
Text
BLOG POST #8 (DUE: 04/10/2025)
What is textual poaching? Can it be a positive tactic in the social media space?
Textual poaching is the idea of fans who express adoration and fascination for a specific topic like a movie, communities are often created (Black Twitter A Response to Bias in the Main Media, Latoya A. Lee, pp.1-2). Textual poaching is a way where fans get together to discuss their high interests of a certain televised media via an online platform. Often, we see fans getting very passionate about it, for example, when Games of Thrones was premiering thousands of people were on Twitter discussing. This high passion for shows/movies can be transmitted to social change in the media. Taking the same imitative in textual poaching when discussing politics and current news. This fascination can lead to action to change injustices in our systems.
Do hashtags actually work in terms of social change in online platforms?
Hashtags are very common to use when making a post whether it’s a picture, video, or even text entry. Using a hashtag can be silly and to add more context to your message. But the true power of hashtags are that they can create exposure for the topic being covered because it can be popularized. Just like #BLM and #NODAPL these hashtags were heavily popular during these social changes initiates. Hashtags are way of textual poaching because they provide resistance (Black Twitter A Response to Bias in the Main Media, Latoya A. Lee, p.2). Resistance is key during social changes and hashtags are great method to take advantage of to spread awareness and get political change.
Are the effects of online change just online, or are there physical, real-world changes?
Online change is not a new concept, ever since technology was introduced the idea of using it as method to express our opinions has been present. I think now more than ever we can take it to extra step and have it be physical real-world change. The ideas we share online can be heavily influenced in today’s political conversations. Mobilization is the term to describe this idea of online action calling congressmen as an example to change their policies and listen to their people (Classifying Forms of Online Activism, Vegh S., p. 4). Technology has been given great power that can use for good or for bad.
How can online activism groups create change specifically in government?
Online activism groups have the power to organize communities to protest any injustices occurring in any institutions. We see it all the time when online groups of people start boycotting certain companies due to their actions. We also see it with the government; now more than ever, people are surveilling the government because of the use of technology. For example in Mexico, there was a pro-Zapatista movement to support the struggle of the indigenous people of Chiapas against the oppression of the Mexican government, the Internet played a role with the external communication of the movement this helped activists in other countries with more advanced communication capabilities to help the cause (Classifying Forms of Online Activism, Vegh S., p. 5). The internet pulls people together to fight for each other even if it’s different countries and communities.
3 notes
·
View notes
Text

"The Roots of Human Problems: An Analysis of Systemic Inequality and Control"
"By ForgettableSoul"
In examining the human experience, it becomes increasingly clear that many of the societal issues faced today are not accidental or individual shortcomings. Instead, they are deeply rooted in systems of power designed to maintain control and perpetuate inequality. Though we often celebrate ideals like freedom, equality, and meritocracy, the reality is far more insidious. Systems of power, fueled by greed and self-interest, dominate modern life, creating structures that are difficult to challenge or escape.
The Manufactured Inequality
One of the most glaring issues we face is inequality, a problem that is far from incidental. It is not a failure of the system, but rather a deliberate design. Wealth and resources are concentrated in the hands of a select few, reinforcing their control over economic, political, and social systems. Global capitalism, in particular, has created a system where wealth translates directly into power. Those at the top control political agendas, shape media narratives, and dictate societal values. This cycle keeps the majority of people trapped in poverty, debt, and disillusionment, with little hope of upward mobility.
The concept of meritocracy serves as a tool of distraction here. Many are led to believe that success is attainable through hard work and perseverance. However, the reality is that the system is rigged against most people, with barriers firmly in place to prevent real progress. When individuals fail to achieve their goals, they are often blamed for personal shortcomings, rather than recognizing the larger structural manipulation at play.
The Psychological Game: Manipulating the Masses
Modern media has evolved into a sophisticated tool for control, subtly shaping public opinion and behavior. Consumerism is aggressively promoted, encouraging a cycle of dissatisfaction and desire that traps people in financial servitude. At the same time, political narratives are carefully framed to incite division, ensuring that people remain preoccupied with superficial differences rather than recognizing their shared struggle against a system that exploits them.
This manipulation extends beyond economics. Fearmongering and sensationalism dominate news cycles, distracting the masses from the underlying problems that cause their discontent. By keeping people divided—whether through race, class, or political ideology—those in power maintain their grip on society, making large-scale collective action nearly impossible.
The Concentration of Power
The convergence of corporate, political, and financial power further cements inequality and social control. Lobbying ensures that laws and policies favor the wealthy, while ordinary citizens are left with the illusion of choice through voting systems that have already been co-opted. This phenomenon, often referred to as the “revolving door,” enables political and corporate elites to cycle between government and industry, ensuring that policies serve their interests rather than the public’s.
With the rise of advanced technology and surveillance, this control has only become more efficient. Governments and corporations now have unprecedented access to personal data, allowing them to influence behavior, predict threats, and suppress dissent before it becomes a serious challenge to the status quo.
The Role of Cultural Conditioning
From an early age, people are conditioned to accept societal hierarchies and norms, often without question. Educational systems, rather than promoting critical thinking, serve as indoctrination tools, training individuals to conform and obey. This ensures that future generations will continue to uphold the very systems that oppress them.
Culturally, individualism is exalted, and people are taught that their struggles are personal, rather than systemic. This distracts from the reality that the challenges people face are often the result of systemic inequalities, not personal failures. As a result, individuals become isolated, competing against one another rather than recognizing the larger forces at play that limit their opportunities.
The Cementing of Control
In the digital age, the control of information has become even more pervasive. Algorithms on social media and news platforms filter the information people consume, shaping their beliefs and perceptions in ways that often go unnoticed. Dissenting voices are marginalized, and the dominant narrative—crafted by those in power—remains largely unchallenged.
Moreover, systems of debt and economic dependency keep the majority of people trapped in cycles of work and survival, with little time or energy to question the systems that oppress them. Health care, education, and housing are increasingly commodified, ensuring that people remain financially and socially tethered to those in power.
Fear is another powerful tool in this arsenal. By stoking fears of crime, terrorism, and economic instability, those in power can easily control the population, ensuring that individuals remain compliant and focused on immediate concerns rather than long-term systemic change.
Conclusion: A System Designed for Control
The problems we face today are not the result of individual failures or random misfortune. They are the logical outcome of systems deliberately designed to concentrate power in the hands of a few while exploiting the majority. Breaking free from these systems will require widespread awareness, collective action, and the dismantling of narratives that have been carefully constructed to maintain control.
Until we address the root causes of inequality, manipulation, and control, the cycle will continue. But awareness is the first step. Only by recognizing the true nature of these systems can we begin to imagine a future where power is distributed more equitably, and society is built on principles of fairness and collective well-being.
Signed, ForgettableSoul
3 notes
·
View notes
Text
Integrated Microwave Assembly Market Insights & Analysis 2032
Introduction
The global Integrated Microwave Assembly market is poised for substantial growth, driven by rising defense budgets, rapid advancements in 5G infrastructure, and technological innovations in RF module integration. Valued at USD 2.6 billion in 2023, the market is expected to expand at a CAGR of 6.9% over the forecast period. Increasing demand from aerospace, telecommunications, and automotive sectors is further propelling market expansion, creating lucrative opportunities for industry players.
Request Sample Report PDF (including TOC, Graphs & Tables): https://www.statsandresearch.com/request-sample/40613-global-integrated-microwave-assembly-market
Integrated Microwave Assembly Market Dynamics:
Integrated Microwave Assembly Market Growth Drivers
Rising Defense Investments – Governments worldwide are increasing defense budgets to enhance electronic warfare capabilities, secure communication systems, and advanced military radar technologies.
Proliferation of 5G Networks – The rollout of 5G and the growing need for high-frequency communication infrastructure are significantly boosting IMA adoption.
Advancements in Semiconductor Technologies – Miniaturization, improved efficiency, and high-performance microwave solutions are driving demand in the market.
Expansion of Autonomous Vehicles – Automotive radar and connectivity systems are increasingly integrating microwave assemblies for enhanced safety and autonomous driving capabilities.
Get up to 30% Discount: https://www.statsandresearch.com/check-discount/40613-global-integrated-microwave-assembly-market
Integrated Microwave Assembly Market Challenges
High Production Costs – Advanced materials and sophisticated manufacturing processes elevate production expenses.
Complex Design and Integration Requirements – The need for precision engineering and specialized expertise limits market entry for new players.
Emerging Trends
Compact & High-Performance IMAs – The industry is shifting toward smaller, energy-efficient, and high-power-density solutions.
IoT & AI-Driven Applications – Integration of IMAs with artificial intelligence and IoT is creating new growth avenues.
Sustainability Initiatives – Energy-efficient microwave solutions are becoming a priority to meet global environmental standards.
Integrated Microwave Assembly Market Segmentation
By Product Type
Amplifiers – The leading segment, vital for signal strength enhancement across telecommunications, aerospace, and defense.
Frequency Synthesizers – Fastest-growing segment due to the increasing need for precise frequency generation in wireless communication and radar systems.
Frequency Converters, Oscillators, Transceivers, and Others – These components play critical roles in optimizing microwave system performance.
By Frequency Band
S-Band (Dominant Segment) – Extensive usage in satellite communications, radar systems, and military applications.
X-Band (Fastest-Growing Segment) – Rising deployment in high-resolution imaging, maritime surveillance, and secure communications.
Other Bands – Ku-Band, C-Band, Ka-Band, and L-Band continue to support specialized applications.
By Technology
Silicon Germanium (SiGe) (Market Leader) – Superior high-frequency performance and cost-effectiveness drive adoption.
Gallium Arsenide (GaAs) (High Growth Potential) – High electron mobility makes it ideal for satellite communication, radar, and 5G applications.
Indium Phosphide (InP) and Gallium Nitride (GaNAs) – Emerging technologies for next-generation applications.
By End-Use Industry
Aerospace & Defense – Dominant segment, with increasing applications in secure military communications and radar technologies.
Telecommunications – Expanding due to 5G infrastructure rollout and the need for reliable high-speed networks.
Consumer Electronics, Automotive, Industrial, and Healthcare – Growing adoption across multiple industries, fueled by technological advancements.
Regional Analysis
North America (Market Leader, 35% Share) – Home to major industry players and high defense spending.
Europe (Second-Largest Market) – Increasing focus on defense modernization and 5G expansion.
Asia-Pacific (Fastest-Growing Region) – Rapid industrialization, increasing military expenditures, and expanding telecommunications infrastructure drive market growth.
South America & Middle East & Africa (Emerging Markets) – Growth fueled by rising demand for telecommunications and automotive applications.
Competitive Landscape
Leading players in the Integrated Microwave Assembly market include:
L3Harris Technologies
Qorvo
Wolfspeed
Mercury Systems
Broadcom
NXP Semiconductors
Infineon Technologies AG
Amphenol Corporation
Teledyne Technologies
Murata Manufacturing
MACOM Technology Solutions Holdings
Skyworks Solutions
Analog Devices
Recent Developments
Wolfspeed (2024) – Launched GaN-on-SiC-based IMA modules with superior power density and efficiency for aerospace and defense.
Broadcom (2024) – Introduced IMAs optimized for 5G infrastructure, enhancing bandwidth and reducing latency for next-gen wireless networks.
Integrated Microwave Assembly Market Future Outlook
The Integrated Microwave Assembly market is on a steady growth trajectory, driven by rising defense expenditures, expanding 5G networks, and continuous RF integration advancements. Companies are focusing on compact, high-performance, and energy-efficient solutions, ensuring sustained industry expansion.
Conclusion
The Integrated Microwave Assembly market presents substantial growth opportunities, particularly in aerospace, defense, and telecommunications. While challenges such as high production costs and complex integration exist, ongoing technological advancements and increasing global defense spending are driving market expansion. The shift toward miniaturized, high-efficiency microwave systems will be key in shaping the future of this industry.
Purchase Exclusive Report: https://www.statsandresearch.com/enquire-before/40613-global-integrated-microwave-assembly-market
Our Services:
On-Demand Reports: https://www.statsandresearch.com/on-demand-reports
Subscription Plans: https://www.statsandresearch.com/subscription-plans
Consulting Services: https://www.statsandresearch.com/consulting-services
ESG Solutions: https://www.statsandresearch.com/esg-solutions
Contact Us:
Stats and Research
Email: [email protected]
Phone: +91 8530698844
Website: https://www.statsandresearch.com
#Integrated Microwave Assembly Market#Microwave Assembly Trends#Integrated Microwave Assembly Forecast#Microwave Assembly Analysis#RF Microwave Market#Integrated Microwave Module#Electronics Market Trends#Microwave Systems Market#Defense Electronics Market#Aerospace Microwave Assembly#Global Microwave Assembly Market#Microwave Components Market#Microwave Module Forecast#Telecom Microwave Market#Microwave Market Growth
1 note
·
View note
Text
This day in history

I'm on tour with my new novel The Bezzle! Catch me TONIGHT in LA with Adam Conover at Vroman's, then on MONDAY in Seattle with Neal Stephenson, then Portland, Phoenix and more!

#20yrsago Education czar calls teachers’ union a “terrorist organization” https://www.cnn.com/2004/EDUCATION/02/24/paige.terrorist.nea/index.html
#20yrsago Garry Trudeau puts $10K up for anyone who will confirm Bush’s Air Guard claims https://web.archive.org/web/20040401103812/http://www.doonesbury.com/strip/faqs/index.html
#20yrsago Nelson’s Grey Tuesday RSS https://web.archive.org/web/20040503084858/http://www.nelson.monkey.org/~nelson/weblog/culture/blogs/greyDay.html
#15yrsago Conan copyright trolls censor fan-readings of public domain stories https://www.sffaudio.com/conan-and-new-zealands-new-copyright-law-vs-broken-sea/
#15yrsago Unimaginably gigantic cell-phone market in Shenzhen https://www.bunniestudios.com/blog/?p=283
#15yrsago John Hodgman explains what’s wrong with “Meh” https://waxy.org/2009/02/john_hodgman_on_meh/
#15yrsago @brucesterling's The Caryatids, my pick for best book of 2009, a novel of clear-eyed hope for the future https://memex.craphound.com/2009/02/24/bruce-sterlings-the-caryatids-my-pick-for-best-book-of-2009-a-novel-of-clear-eyed-hope-for-the-future/
#10yrsago Mozilla’s $25 Firefox smartphone: a free/open device for billions of new netizens https://www.cnet.com/tech/mobile/with-firefox-os-mozilla-begins-the-25-smartphone-push/
#10yrsago Whistleblower: NSA secretly continues Merkel surveillance by bugging other German officials https://arstechnica.com/tech-policy/2014/02/nsa-moves-from-bugging-german-chancellor-to-bugging-german-ministers/
#10yrsago Text of Little Brother on an art-litho, tee, or tote https://www.litographs.com/products/brother
#10yrsago Takei to Arizona lawmakers: we will boycott Arizona if it passes its anti-gay Jim Crow law https://www.cnbc.com/2014/02/25/razing-arizonageorge-takeicommentary.html
#10yrsago How Youtube’s automated copyright system lets big music screw indie creators https://torrentfreak.com/why-youtubes-automated-copyright-takedown-system-hurts-artists-140223/
#5yrsago Deposition of opioid profiteer Richard Sackler reveals his bizarre defense: definitional games and insistence that words mean their opposite https://arstechnica.com/science/2019/02/sackler-behind-oxycontin-fraud-offered-twisted-mind-boggling-defense/
#5yrsago Alexandria Ocasio-Cortez will pay every staffer a living wage, ending the longstanding practice of Congressional staffers taking second jobs https://rollcall.com/2019/02/22/alexandria-ocasio-cortezs-call-for-a-living-wage-starts-in-her-office/
#5yrsago As expected, the EU has advanced the catastrophic Copyright Directive without fixing its terrible defects https://arstechnica.com/tech-policy/2019/02/european-governments-approve-controversial-new-copyright-law/
#1yrago This is your brain on fraud apologetics https://pluralistic.net/2023/02/24/passive-income/#swiss-cheese-security
7 notes
·
View notes
Text
Airborne Optronics Market Share Analysis: Leading Players & Regional Insights

The Airborne Optronics Market is experiencing rapid expansion, fueled by increasing demand for advanced electro-optical systems in military, commercial, and urban air mobility applications. The market, valued at USD 1.4 billion in 2020, is projected to reach USD 2.5 billion by 2025, growing at a CAGR of 12.7%. As defense forces, security agencies, and commercial aviation sectors adopt cutting-edge imaging and surveillance technologies, airborne optronics is becoming an integral part of modern aircraft and UAV systems.
Technological advancements, rising investments in defense modernization, and the growing use of unmanned aerial vehicles (UAVs) for surveillance and reconnaissance are among the key factors driving the market forward. Additionally, the expansion of urban air mobility (UAM) platforms, including air taxis and autonomous cargo drones, is expected to increase the demand for advanced airborne imaging and detection systems.
The Impact of COVID-19 on the Airborne Optronics Market
The COVID-19 pandemic had a notable impact on the Airborne Optronics Market, leading to disruptions in supply chains and temporary slowdowns in aircraft production. In 2020, aircraft orders and deliveries declined, affecting demand for airborne optronics. Industry experts estimated that the pandemic resulted in a 7–10% impact on production and services worldwide.
Despite these challenges, recovery began in early 2021 as aerospace manufacturers resumed operations. The increased reliance on UAVs for autonomous surveillance, border security, and ISR (intelligence, surveillance, and reconnaissance) missions contributed to the resurgence of demand for airborne optronics. Post-pandemic, investments in next-generation imaging sensors and AI-driven surveillance systems are expected to accelerate market growth.
Download PDF Brochure: https://www.marketsandmarkets.com/pdfdownloadNew.asp?id=45924401
Technological Innovations Reshaping the Airborne Optronics Market
Modern airborne optronics systems are evolving with advancements in multispectral imaging, AI-based analytics, and high-resolution electro-optical sensors. These innovations are enhancing the capabilities of aircraft, UAVs, and airborne platforms for defense and commercial applications. The development of miniaturized electro-optical systems through nanotechnology is allowing for integration into small drones and lightweight aerial vehicles, improving efficiency without compromising performance.
Multispectral and hyperspectral imaging technologies are also advancing, allowing airborne systems to detect and analyze objects with greater precision across multiple wavelengths. This enhanced imaging capability is crucial for applications in border security, environmental monitoring, and military reconnaissance. As a result, the multispectral segment is expected to experience the highest growth during the forecast period due to its affordability and adaptability in UAV-based applications.
The integration of artificial intelligence (AI) and machine learning (ML) in airborne optronics is transforming the way data is processed and analyzed. AI-powered imaging systems can automatically detect, classify, and track objects, providing real-time intelligence for military and commercial operators. These advancements are making airborne surveillance more efficient and reducing human intervention in complex decision-making scenarios.
Opportunities Driving the Airborne Optronics Market
The rapid development of urban air mobility (UAM) platforms presents a significant growth opportunity for the Airborne Optronics Market. The demand for autonomous aerial transportation, including air taxis, air ambulances, and cargo drones, is rising. The urban air mobility market is projected to expand from USD 2.5 billion to USD 4.9 billion by 2025, creating a strong demand for highly advanced airborne sensor technologies. Ensuring safe navigation, obstacle detection, and precise landing in urban environments will require state-of-the-art electro-optical systems, further boosting market demand.
Another major opportunity lies in the increasing deployment of UAVs in the military sector. UAVs are being integrated with high-resolution electro-optics and infrared (EO/IR) sensors to conduct surveillance operations, border security, and battlefield intelligence missions. The growing need for autonomous surveillance solutions and drone-based reconnaissance is expected to drive continued investments in airborne optronics technologies.
As the market for commercial drones expands, various industries are exploring applications beyond surveillance, such as infrastructure inspections, environmental monitoring, and emergency response. Drones equipped with airborne optronics are increasingly being used in commercial settings to provide real-time imaging, terrain mapping, and asset monitoring, further widening the scope of market opportunities.
Challenges in the Airborne Optronics Market
Despite its growth potential, the Airborne Optronics Market faces several challenges, particularly regarding weather-related inefficiencies in electro-optical sensors. Airborne electro-optics systems are highly sensitive to environmental conditions such as fog, haze, smoke, and dust, which can obscure visibility and limit the accuracy of imaging and targeting systems.
In battlefield scenarios, airborne optronics systems must operate in unpredictable environments where visibility conditions change rapidly. Factors such as smoke from explosions, dust clouds, and atmospheric interference can reduce the effectiveness of EO/IR sensors, making it challenging to maintain consistent surveillance. Addressing these limitations through enhanced sensor technology, adaptive imaging algorithms, and multi-sensor integration is essential for improving system performance in extreme conditions.
Another challenge is the increasing threat of cybersecurity risks associated with airborne optronics systems. As military and commercial aircraft become more dependent on digital imaging and real-time data processing, the potential for cyber attacks, hacking, and electronic warfare interference is rising. Ensuring the security of real-time surveillance data and sensor networks is a critical concern for both defense agencies and commercial operators.
Regional Market Insights: North America Leading Growth
North America is currently the largest regional market for airborne optronics, driven by strong defense spending, technological leadership, and a growing fleet of commercial and military aircraft. The United States remains a dominant player, with major defense contractors and aerospace companies actively investing in next-generation electro-optical systems. Companies like Northrop Grumman, Lockheed Martin, L3Harris Technologies, and Collins Aerospace are at the forefront of innovation in the airborne optronics sector.
In Europe, nations such as France, Germany, and the UK are focusing on modernizing their defense and surveillance capabilities. The presence of leading European companies, including Thales SA and Safran, is contributing to the region’s market expansion. Meanwhile, the Asia-Pacific region is experiencing growing demand for airborne optronics, particularly in countries like China, India, and Japan, where investments in UAV technology and military surveillance systems are rising.
The Middle East, Africa, and Latin America are emerging markets for airborne optronics, with increasing investments in border security, counter-terrorism, and urban surveillance applications. These regions are expected to witness steady growth as governments and private sector players explore new airborne imaging and reconnaissance solutions.
Ask for Sample Report: https://www.marketsandmarkets.com/requestsampleNew.asp?id=45924401
Future Outlook for the Airborne Optronics Market
The Airborne Optronics Market is expected to witness strong growth, driven by advancements in imaging technology, increasing defense budgets, and the rising demand for UAV-based surveillance. The integration of AI, multispectral imaging, and adaptive sensor technologies will continue to shape the future of airborne surveillance and reconnaissance.
As defense agencies, security forces, and commercial operators seek highly efficient and reliable airborne imaging solutions, companies investing in next-generation electro-optical systems will remain at the forefront of market growth. The continued expansion of urban air mobility and autonomous aircraft systems is expected to open new opportunities for airborne optronics technology, ensuring its relevance in the evolving aerospace industry.
#airborne optronics market#electro-optics in aviation#uav surveillance systems#military optronics growth#advanced imaging sensors#aerospace optical technologies
1 note
·
View note
Text
Smart City Parking Solutions in UAE | Innovative & Efficient Systems - Omnitec UAE
Introduction to Smart City Parking Solutions
In today’s rapidly growing urban environments, efficient parking solutions are essential to manage traffic flow and improve city life. Smart city parking solutions, like those offered by Omnitec UAE, integrate advanced technology to enhance the parking experience in metropolitan areas. These solutions not only help reduce congestion but also improve sustainability and the overall efficiency of city infrastructure.
What are Smart City Parking Solutions?
Smart city parking solutions utilize a combination of Internet of Things (IoT) devices, real-time data analytics, and automated systems to optimize parking management. These systems are designed to make the process more convenient for drivers while providing city administrators with valuable insights into parking space usage, traffic patterns, and more.
Key Features of Smart Parking Solutions:
Automated payment systems: Drivers can pay for parking without physical transactions through mobile apps or online portals.
Real-time space availability: Sensors detect available parking spaces and provide live updates to drivers, reducing the time spent searching for parking.
Traffic management: By managing parking demand, cities can reduce traffic congestion, improve air quality, and enhance mobility.
Benefits of Smart City Parking Solutions by Omnitec UAE
Omnitec UAE is at the forefront of providing cutting-edge smart parking systems in the UAE. By leveraging advanced technologies, Omnitec delivers solutions that not only optimize parking but also address broader urban challenges. Here are some of the benefits that come with adopting smart city parking solutions:
Reduced Congestion With real-time data on parking availability, drivers no longer need to circle around to find an open spot. This leads to smoother traffic flow and significantly reduces congestion in busy city areas.
Environmental Impact Efficient parking management cuts down the carbon emissions caused by vehicles idling while looking for parking. This contributes to the overall sustainability goals of a smart city.
Enhanced User Experience Through the use of mobile apps and automated kiosks, drivers enjoy a seamless and stress-free parking experience. They can book parking spots in advance, make contactless payments, and receive real-time updates about parking availability.
Cost-Effective for Cities Smart parking solutions are scalable and adaptable, making them a cost-effective option for cities. These systems allow municipalities to monitor parking spaces and make data-driven decisions about parking infrastructure and city planning.
Security and Monitoring Advanced technologies such as ANPR (Automatic Number Plate Recognition) systems and CCTV surveillance integrated with smart parking solutions ensure the security of parking areas, reducing theft and vandalism.
How Omnitec UAE’s Solutions are Shaping the Future of Urban Parking
Omnitec UAE’s smart city parking solutions are designed to help cities evolve into smarter, more efficient, and greener environments. Their systems not only meet the needs of modern urban mobility but also address the key challenges of overcrowded city spaces, such as:
Dynamic Pricing Models: The system can adjust parking fees based on demand, encouraging drivers to park during off-peak hours, which helps distribute traffic flow more evenly throughout the day.
Data-Driven Insights: With detailed analytics on parking usage, city planners can make informed decisions about infrastructure investments and optimize space allocation.
Why Choose Omnitec UAE for Smart City Parking Solutions?
Omnitec UAE has a proven track record in delivering reliable, scalable, and future-ready parking solutions tailored for smart cities. Their commitment to innovation and technology sets them apart from competitors. Here's why you should consider Omnitec UAE for your city’s parking needs:
Experience and Expertise: With years of expertise in parking management solutions, Omnitec is a trusted partner for many smart cities.
Tailored Solutions: Whether you’re a city administrator, a business owner, or a real estate developer, Omnitec’s parking solutions can be customized to fit your specific needs.
Sustainability Focus: Omnitec’s parking systems are designed with sustainability in mind, helping cities reduce their carbon footprint and promote eco-friendly transportation options.
Conclusion
As cities continue to grow, the demand for efficient, innovative, and scalable parking solutions becomes more pressing. Omnitec UAE’s smart city parking solutions offer a comprehensive approach to urban parking, blending technology with convenience to meet the evolving needs of modern cities. Whether you're looking to enhance mobility, improve sustainability, or streamline parking management, Omnitec UAE has the expertise and technology to make it happen.
For more information on our Smart City Parking Solutions, visit our website. Explore our innovative solutions that are revolutionizing urban parking in the UAE.
2 notes
·
View notes
Text
2024 Video Telematics Solutions of ICARVISIONS
Let’s take a look at the video telematics solutions offered by ICARVISIONS in 2024.
1. Cargo Logistic Solution
In this Cargo and Logistics solution, we present a robust array of features, including Advanced Driver Assistance Systems (ADAS), Driver Safety Monitoring (DSM), Blind Spot Detection (BSD), 360° panoramic views, Anti-Theft Detection, Temperature Detection, and additional capabilities.
Learn more: Cargo Logistic Telematics Monitoring Solution
2. Bus Solution


In this Bus solution, we highlight an extensive range of features, including Advanced Driver Assistance Systems (ADAS), Driver Safety Monitoring (DSM), Blind Spot Detection (BSD), AI MDVR, 360° panoramic views, Passenger Counting Technology, and more.
Learn more: Bus Telematics Monitoring Solution
3. Fuel Tanker Solution
In this Fuel Tanker solution, we present a wide array of features, including a Fireproof and Waterproof Data Box, Blind Spot Detection (BSD), Audible Flashing Alert, Ultrasonic Fuel Sensor, Advanced Driver Assistance Systems (ADAS), Driver Safety Monitoring (DSM), AI MDVR, and more.
Learn more: Fuel Tanker Telematics Monitoring Solution
4. Construction Truck Solution

In this Construction Truck safety solution, we highlight a broad range of features, including Blind Spot Detection (BSD), Audible Flashing Alert, Container Recognition, Advanced Driver Assistance Systems (ADAS), Driver Safety Monitoring (DSM), AI MDVR, and more.
Our blind spot detection system provides real-time alerts to drivers and pedestrians through audible and visual warnings, reducing collision risks, preventing accidents, and ensuring the safety of drivers, pedestrians, and nearby vehicles.
Learn more: Construction Truck Telematics Monitoring Solution
5. Law Enforcement Solution
Our Law Enforcement solution is tailored to enhance the safety of law enforcement personnel and mitigate the risks associated with their operations. It does so by enabling real-time vehicle monitoring and oversight of enforcement processes, ultimately enhancing the effectiveness of law enforcement activities.
Learn more: Law Enforcement Telematics Monitoring Solution
6. Dash Cam Solution

The AI Dash Cam (JI7A) is a robust and easily installed 1080P AHD recorder for vehicle surveillance, featuring optional remote monitoring, Advanced Driver Assistance Systems (ADAS), and Driver Safety Monitoring (DSM) functions.
Learn more: AI Dash Cam JI7A | Enhanced Dash Cam JI7A: Now Supports OBD
7. Ship Solution

The ICARVISIONS ship telematics monitoring solution features intelligent Android tablets, cabin and outdoor cameras, and a fireproof and waterproof data box, providing strong monitoring and data protection capabilities that significantly enhance ship safety.
Learn more: Ship Telematics Monitoring Solution
8. Forklift Solution
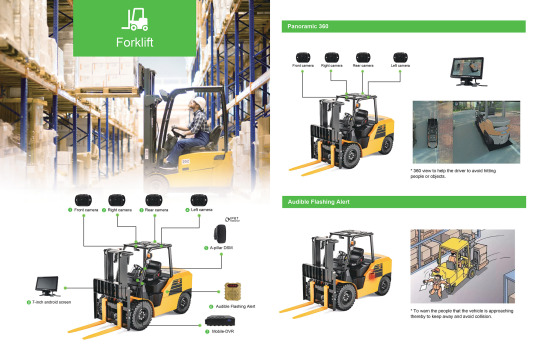
We are thrilled to present ICARVISIONS' forklift safety solution! This solution highlights an extensive array of features, including Driver Safety Monitoring (DSM), an A-pillar DSM camera, Blind Spot Detection (BSD), 360° Panoramic Views, Audible Flashing Alerts, and more.
Learn more: Forklift Safety Solution
9. Train Solution

Introducing our Telematics solution for high-speed trains: an Anti-Vibration CCTV Mobile NVR powered by AI H.265, offering access to telematics portals with a complimentary license.
Learn more: Train Surveillance Solution
2024 ICARVISIONS Catalogue
GOOGLE
ICARVISIONS WEB
1 note
·
View note
Text
Maximize Your Fleet Safety with Video Telematics Solutions

Video evidence has consistently proven to be essential in gathering and storing information, especially for businesses engaged in fleet management. More specifically, we are referring to the effective utilization of video telematics.
In recent years, numerous industries have experienced remarkable technological advancements, and the transportation sector has particularly embraced video telematics as a remarkable innovation.
Here is a comprehensive guide that will enable you to acquire a thorough understanding of video telematics solutions.
Table of Contents
What is Vedio Telematics?
DMS- ADAS: The Core Components of Video Telematics Solutions
How do Video Telematics Solutions Operate?
Benefits of Video Telematics Solutions
(1) Driver Monitoring
(2) Real-time Live Streaming
(3) Opportunities for Driver Training
(4) Surveillance for Security
What is Vedio Telematics?
Video telematics is an advanced version of vehicle telematics that combines visual data, vehicle analysis, and geospatial vision. Unlike traditional automotive telematics solutions that only send text alerts to managers, video telematics solutions also capture video data.
The integration of video telematics into fleet management software has greatly improved its capabilities. In addition to real-time location tracking, the software now collects vast amounts of data and provides valuable insights into vehicles through its sensors Dashboard camera records the driver’s actions, while the video sensor captures the environment surrounded both externally and internally. These environmental factors include the speed of nearby vehicles, the behavior of the driver, and the environment around the vehicle.
DMS- ADAS: The Core Components of Video Telematics Solutions
The Driver Management System (DMS) and Advanced Driver Assistant System (ADAS) are not only the fundamental elements of Video Telematics but are also considered the essence and backbone of video telematics.
The Driver Monitoring System (DMS) is responsible for overseeing and monitoring driver behavior, while the Advanced Driver Assistance System (ADAS) aids in monitoring the surrounding road environment. Moreover, the system recognizes events rather than individual actions, categorizing them into various types such as smoking, yawning, drowsiness, and more. The dashcam captures the driver’s actions, compares them with the recognized events, and subsequently generates appropriate alerts.
In addition, fleet managers are also notified about other significant events, including the blocking of the camera, the absence of the driver from the driver’s seat, and the use of a mobile phone.
The ADAS feature not only enhances the overall functionality but also effectively detects the surrounding environment and promptly notifies the driver of any potential incidents. By incorporating the ADAS feature, insurance claim settlements, driver training, and the overall safety of the vehicle, driver, and cargo have been greatly improved. Fleet managers can be notified about events such as chances of forward collisions, red light jumping, and reckless lane switching through ADAS.
How do Video Telematics Solutions Operate?
Video telematics solutions function by combining vehicle data, driving data, real-time location, and video footage transmitted over cellular data. Whenever an event occurs, the device generates an appropriate alert. The main goal of this technology is to enhance driver safety by providing personalized data that can be used for driver training and coaching purposes.
The software primarily focuses on monitoring drivers’ behavior and identifying risky activities such as overspeeding, reckless driving, distracted driving, and more. Cameras are used to capture video footage, which provides a comprehensive understanding of driver conduct and any related issues. This enables fleet management to make well-informed decisions.
Different types of cameras are available based on the fleet’s requirements, including multi-camera, road-facing, and driver-facing cameras.
Benefits of Video Telematics Solutions
Video telematics solutions offer various benefits, particularly in the context of fleet management, safety, and operational efficiency. Here are some key advantages of implementing video telematics solutions:
(1) Driver Monitoring
Video telematics can record and analyze drivers’ behavior, promoting safer driving habits and reducing risky behaviors such as speeding, harsh braking, and aggressive driving. The solution not only analyzes driving habits but also notifies events of collisions. In such events, video footage can provide crucial information for understanding the cause of the event. Advanced video telematics solutions also provide real-time alerts to prevent collisions.
(2) Real-time Live Streaming
Video telematics systems provide real-time streaming, allowing fleet managers to monitor their fleet and the activities of drivers in real time. This solution helps address issues as they arise and improves overall operational visibility.
(3) Opportunities for Driver Training
Utilizing video footage can be an effective method for driver training and coaching. This enables fleet managers to pinpoint areas that require improvement and offer tailored training to enhance the driving skills of their drivers.
(4) Surveillance for Security
Video telematics serves as a deterrent against theft and vandalism. In case of unauthorized access or theft, video footage can assist in locating stolen vehicles and recovering the assets. Wrapping it all
In conclusion, it is undeniable that video telematics plays a vital role in organizations, particularly in fleet management. Although video telematics solutions offer a multitude of advantages, organizations must implement and utilize the system responsibly.
If you are considering acquiring advanced telematics solutions, look no further than TrackoBit. This comprehensive solution offers a 360° visual coverage of your fleet, as well as features such as route planning solutions and fuel management systems.
Source : Maximize Your Fleet Safety with Video Telematics Solutions
1 note
·
View note
Text
Israeli defense officials have called Israel’s surveillance apparatus in Gaza one of the most sophisticated in the world. But it failed on Oct. 7.
At dawn, Palestinian militants broke through Israel’s multibillion-dollar border fence separating the blockaded Gaza Strip from Israeli communities, breaching the barrier in as many as 80 different places. The militants navigated small drones that disabled Israeli cameras, remote sensing systems, and automated machine guns that would have alerted the Israel Defense Forces (IDF) that the fence had failed.
After they crossed, militants swarmed Israel’s Zikim military base, killing many soldiers and taking some hostage. Over the next six hours, Hamas fighters would kill or take hostage hundreds of Israeli civilians as well as scores of foreign nationals. Militants massacred 250 revelers at a desert rave and hundreds of other people in their own homes, shooting entire families at point-blank range. More than 200 soldiers and civilians—including infants, children, older people, and migrant farm laborers—were shoved onto motorcycles or into golf carts and driven back over the border into Gaza as captives. (Four have since been released.) Residents of cities farther north were roused by air sirens warning of incoming missiles, as news alerts began revealing the scale of the attack.
In total, the operation killed more than 1,400 Israelis. It had been planned for months, if not years, and mobilized more than 1,500 militants from Hamas, which has ruled Gaza since 2007, as well as some from Palestinian Islamic Jihad, another militant group.
The failure by Israeli intelligence to anticipate the massacre was a shock, given the country’s cutting-edge surveillance systems and weaponry pioneered by its technologically advanced military. From borders equipped with hundreds of sensors, cameras, robotic machine guns, and automated drone swarms to biometric databases and spyware, high-tech systems have helped enforce a 16-year Israeli blockade of Gaza and its 2.3 million Palestinian inhabitants. These systems have also been deployed against Palestinians in the occupied West Bank and East Jerusalem, as part of a broader regime of population control.
Yet, on Oct. 7, that intelligence apparatus did not work as promised. Security experts and human rights advocates in Israel say the atrocities are evidence that technology can never be a tenable salve to regional insecurity. It is time to reconsider whether high-tech solutions to violence can ever stand in for political ones.
How exactly Hamas defeated Israel’s sophisticated technology—including a $1.1 billion border wall fortified with underground and aerial remote sensing technologies—is still being investigated. For more than 16 years, the IDF thwarted all but a handful of breaches to the border fence with deadly aerial bombardments, sniper fire, and dragnet surveillance.
But from early indications, it seems the Palestinian militia operated right under Israel’s nose. Hamas compiled troves of information about Israel’s intelligence capabilities and security infrastructure for months. Operatives reportedly trained for the onslaught at a sprawling base near the Gaza-Israel fence for more than a year. They drove through the barrier on trucks and motorcycles, flew over it on bright beach paragliders, and motorboated up the Mediterranean coast.
“They [the Gaza militants] studied us very well. They knew what kind of technology we had on the fence. They knew what needed to be destroyed before getting through the fence. They also knew where the army units were, the tanks, and the bases,” said Yohanan Tzoreff, a senior researcher with the Institute for National Security Studies in Tel Aviv.
“Nothing alerted us that something was wrong along the border. Nothing gave us a picture of what happened in this area,” he said.
While in the occupied West Bank, Israel relies on spy networks, embedded informants, and secret agents, its tactics in Gaza largely rest on digital and automated systems. Israel controls and limits access to telecommunications and internet across the territory, and the military deploys automated drones in nearly 24/7 aerial reconnaissance of densely populated urban areas. Yet somehow, Hamas mapped the sensors, cameras, watch towers, and military bases along the border—planning its sabotage without triggering a single alarm.
The group hid its preparation by avoiding digital communications altogether while planning for the attack. Many of its operations were moved to underground bunkers equipped with hardwired phones outside the range of 2G networks monitored by the IDF. But components of the attack were also rehearsed in broad daylight in plain view of Israeli military personnel. IDF officials even wrote off a September propaganda video of Hamas exploding the border fence; the army simply assumed the border was impenetrable.
Members of Israel’s security establishment have publicly denounced the IDF’s overreliance on technology to contain Gaza in the wake of the attack. Some also lamented that resources were directed away from ground troops on the Gaza border and toward a tech-obsessed military, which had become, in the words of retired IDF Maj. Gen. Yitzhak Barik, “swollen with arrogance.”
“If most of your intelligence comes from sigint [signals intelligence], then I suppose you’re in a way blind if anyone is operating without cellphones or digital communications,” said Ami Ayalon, the former head of Shin Bet, Israel’s domestic intelligence agency. “We just assumed they [Hamas] wouldn’t attack now.”
Ayalon, who has devoted his retirement to advocating for a two-state solution to the Israeli-Palestinian conflict, told Foreign Policy that the military used technology as a “bandage,” focusing on quick fixes to regional volatility while the government abandoned any possibility of bringing about a lasting peace.
“Our [Israel’s] policy has been, we should do everything to maintain this situation, to manage the conflict, not to solve it, because to solve would mean we would pay a huge price”—such as pulling hundreds of thousands of settlers from the occupied West Bank and forfeiting swaths of land in the name of a two-state solution.
Israeli investments in high-tech security and surveillance systems took off in the early 2000s, in response to a surge of Palestinian suicide attacks and other violence of the Second Intifada. Under increasingly right-wing leadership, Israel’s military spent billions of dollars to develop more effective ways to manage regional violence (much of the money came from U.S. military aid) rather than addressing its root causes.
Generals assured the world that biometric cameras, automated drones, targeted spyware, and smarter border walls could effectively quell Palestinian militant groups across the region. Once these generals retired from the military, many of them sat on the boards of weapons companies that promised the technologies would enhance global security. Israeli assaults on Gaza doubled as opportunities arose for Israeli defense firms to unveil automated reconnaissance and strike drones, which were then exported around the world.
As one Israeli columnist put it: “For every significant threat originating in Gaza since Hamas took control in 2007, Israel responded with technological solutions.” The country experienced unprecedented economic growth, powered in large part by the military technology sector, as Gaza endured an economic crisis compounded by the collective trauma of unending war.
Human rights advocates say the Israeli government’s tech-heavy policies helped shield Israeli society from the violence and humanitarian crisis unfolding in Gaza. “The situation in Gaza has been repressed for so long by Israeli society,” said Miriam Marmur, the director of public advocacy at Gisha, an Israeli nonprofit that promotes freedom of movement for Palestinians in Gaza. “Now we’re seeing it surface in horrifying and terrifying ways.”
Israel’s belief that technology can act as a salve to geopolitical volatility mirrors global trends. From NATO- and U.S.-sponsored drone warfare in Afghanistan and Iraq to predictive policing algorithms in the United States, militaries and police forces worldwide have touted high-tech innovation as a silver bullet to quell chronic insecurity. Yet precision strikes and algorithms have done little to address the root causes of violence in all these places. Nearly two decades of drone warfare failed to eliminate al Qaeda—or stop the Taliban’s takeover of Afghanistan. In the United States, predictive policing software, which is rarely accurate, has diverted resources from social services that might more effectively deter crime.
An Israeli approach to Palestinians that would have genuinely improved their lives and offered them hope for independence may well have strengthened the more moderate elements in the West Bank and Gaza and weakened Hamas—a group whose charter calls for the destruction of Israel. But Israeli Prime Minister Benjamin Netanyahu saw political advantages in allowing Hamas to continue ruling Gaza.
As recently as 2019, Netanyahu said strengthening Hamas at the expense of the Palestinian Authority in the West Bank would keep Palestinians divided politically and sabotage any chance for a viable two-state solution. It would also potentially abet the Israeli far right’s goal of annexing the West Bank.
Israel’s military leadership promised that sophisticated weaponry and missile defense systems could maintain this equilibrium. Recent wars between Gaza and Israel hardly disturbed social and economic life in Israel’s urban centers. The status quo, which exacted Palestinian pain and suffering, felt sustainable to most Israelis.
But Hamas’s Oct. 7 attack destroyed the image of a sleek and efficient Israeli war machine that Netanyahu and his allies tried so hard to cultivate. It took one of the most vaunted militaries in the world hours to respond to pleas for help from civilians locked inside their homes or hiding under piles of dead bodies as Hamas militants poured in from Gaza and went on a killing spree. In some cases, off-duty or retired military personnel donned uniforms to rescue their own relatives, driving alone into besieged towns to engage in direct combat.
Intent on redeeming itself, the IDF has responded in an unrestrained and brutal way. The Israeli air force is carpet-bombing Gaza’s crowded urban centers to pave the way for what is likely to be an even deadlier ground invasion. Israeli strikes have so far killed more than 8,000 Palestinians, with thousands more injured, according to Palestinian health officials. Some 700,000 Palestinians in Gaza have fled their homes. Already, one Israeli publication has said the next phase of war will be “a proving ground for some of Israel’s latest military technology.”
Yet any escalation of the war will only lead to more deaths, no matter the technologies deployed. “Do not destroy the Gaza Strip,” Neta Heiman wrote in Haaretz days after Hamas kidnapped her 84-year-old mother, “that won’t help anyone and will only bring an even more ferocious round of violence the next time.”
7 notes
·
View notes