#AdObjectives
Explore tagged Tumblr posts
Text
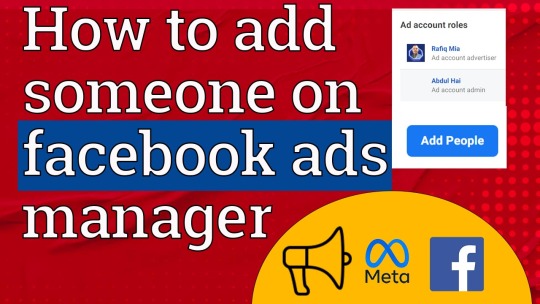
To add people to Facebook Ads Manager, follow these steps:
1. **Access Ads Manager**: Go to Facebook Ads Manager by visiting facebook ads manager and logging in with your Facebook account credentials. If you don't have an Ads Manager account set up yet, you'll need to create one.
2. **Navigate to Settings**: Once you're in Ads Manager, look for the settings icon (gear icon) in the upper-right corner and click on it. This will take you to the "Ad Account Settings" page.
3. **Navigate to Ad Account Roles**: On the "Ad Account Settings" page, find and click on "Ad Account Roles" in the left-hand menu. This is where you can manage who has access to your ad account.
4. **Click on Add People**: In the "Ad Account Roles" section, you'll see a list of people who currently have access to the ad account. To add someone new, click on the "Add People" button.
5. **Enter Email Address or Name**: In the pop-up window, you can add people by entering their email address associated with their Facebook account or by typing their name. As you type, Facebook will suggest matching profiles.
6. **Select Role**: After selecting the person you want to add, choose their role from the dropdown menu. There are different roles with varying levels of access, such as Admin, Advertiser, or Analyst. Choose the appropriate role based on the level of access you want to grant them.
7. **Click Add**: Once you've selected the person and their role, click the "Add" button to add them to your ad account.
8. **Confirm and Adjust Settings (if necessary)**: After adding someone, you may want to review the settings for their role to ensure they have the appropriate level of access. You can adjust these settings by clicking on the pencil icon next to their name in the "Ad Account Roles" section.
9. **Notify the Person (optional)**: You can choose to notify the person via email that they've been added to the ad account. This can be helpful for letting them know they have access and what level of access they've been granted.
#SocialAdvertising#DigitalStrategy#AdPerformance#AdOptimization#AudienceInsights#CampaignManagement#MarketingMetrics#ContentStrategy#FacebookBusiness#AdBudget#AdAnalytics#FacebookStrategy#FacebookMarketingTips#FacebookAdsManager#FacebookPixel#AdTargeting#FacebookAudience#AdObjectives#FacebookROI#AdPlacement#Rafiqmia#Fundasdigitalmarketing
0 notes
Text
Facebook Marketing For Small Business
Facebook marketing for small business is using Facebook's platform to promote products or services, engage with followers, and increase brand awareness, leads, and sales.
https://iosandweb.net/blog/facebook-marketing-for-small-business/

#facebookads#boostingposts#socialmediaadvertising#digitalmarketing#targetedadvertising#socialmediamarketing#onlineadvertising#AdObjectives#paidsocial#audiencetargeting
1 note
·
View note
Photo
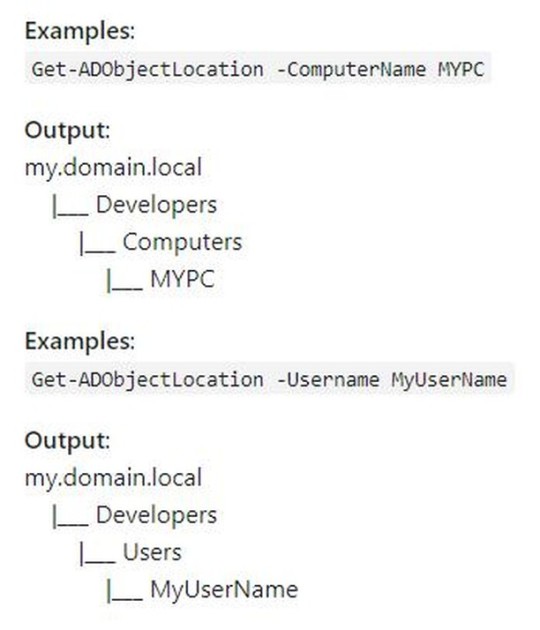
The quickest way to find out where in Active Directory a user or computer is located (OU location)! . . I created a small PowerShell function to do this for me. It can create a simple visual map for you to point out the exact location of the AD object. https://buff.ly/2sOHeRa #powershell #activedirectory #azureAD #Azure #scripting #automation #script #adobject (at Brampton, Ontario) https://www.instagram.com/p/BtEQirqgQ__/?utm_source=ig_tumblr_share&igshid=e27km4pywe3o
0 notes
Text
HTB - Cascade

So it’s been a while. Had a few real life events occur which distracted me from things and also made a silly nooby mistake that cost me some time but here we are. :)
Cascade was honestly a great machine in my opinion- I feel I’m now nearly there with knowing the basics of AD enum and it really brought home the damage that focusing on one objective can do.
Took me a stupidly long time to find the password of r.thompson as I was mistakenly focusing on finding the credentials of s.smith (I noticed he was a remote management user and thus likely to be a target.) But after that point things were pretty obvious (except decrypting arksvc’s password- spent sometime screwing aorund with ROT13 and all sorts. xD)

Another domain controller and no web server... *cracks fingers in preparation for noob feels* Obviously our foothold is going to arise from SMB, AD and potentially Kerberos enumeration.
My enum tool performed a scan using enum4linux which returned nothing but possible users:

There’s a large variety of possibilities here... The correct next step is to narrow that list down. Personally, I did this via the execution of getadusers: this reveals the last time the user logged on and thus gives us the knowledge of which user accounts are the most presently active:

There are 4 highly likely users here: arksvc, s.smith, r.thompson and util. Previous execution of nmap’s ldap-search script led me to believe the target would be s.smith as this revealed him to be a remote management user; getnpusers revealed that no one had doesn’t require preauth set while kerbrute proved fruitless.
After several frustrated hours, I was looking through the results of ldap-search again which revealed some crucial information I had missed due to being too focused on s.smith: r.thompson had a property named cascadeLegacyPwd with a base64 encoded value. -.-

A simple base64 decode later and I had a foothold... Finally; from here things seemed to be a bit easier!
With r.thompson’s credentials, I had access to the Data SMB share and the I.T files within (revealed with a simple smbclient -L and also via the results in ldap-search)
Some basic enum revealed an email sent by s.smith that would be relevant later and a VNC install reg file within \\10.10.10.182\Data\IT\Temp\s.smith\. This file held the hashed value of s.smith’s password.
A tool named vncpwd cracked this for me easily enough (or decrypted, simply saying hashed as passwords are commonly hashed rather than encrypted,) giving us access to Audit$ and winrm.
Audit held some interesting files- four DLLs related to SQLite, a DLL named CascCrypto, an exe named CascAudit and a db file. It’s likely these files were going to hold some critical information; to avoid being too single minded again, I first enumerated the system through winrm to ensure I wasn’t jumping down a rabbit hole (I wasn’t.)
Confident that the files within Audit$ were the way forward, I proceeded to uploaded the relevant DLLs and exe to Cascade and examined the contents of the db file- this held a base64 encoded password for arksvc and some information on deleted users; decoding the string proved fruitless this time, suggesting there was further encryption or hashing in place.
Running the exe with the relevant db file argument resulted in the addition of two rows to the DeletedUserAudit table within the db. Curious, I spent sometime attempting to view this information via LDAP queries as Steve but he seemed to lack the necessary privileges for this (nothing was returned despite there obviously being deleted users.)
Get-ADObject -filter 'isDeleted -eq $true' -includeDeletedObjects -Properties *
Fair enough; I recall seeing a file named ArkSvc within the Data share that referred to an AD recycle bin... Best to try this out again once we have ark’s credentials! We also now have the users flag which is always nice. :)
I tried using the strings command on CascAudit but this didn’t produce anything directly usable so I first decided to explore if there’s anything easily detectable going on with the string. As encryption and hashing aren’t really my areas, I wasted several hours seeing if I could produce any relevant text from the base64 string- ROT13, hashcat against MD4, MD5 and others, it goes on...
After a while I grew suspicious that the answer was in the exe and DLL- CascCrypto... The string was obviously encrypted and the details on the in-use algorithm were probably within those files.
I first used radare2 on CascAudit.exe to see if there was anything juicy that strings missed. This revealed the key c4scadek3y654321, the IV 1tdyjCbY1Ix49842 and the in-use algorithm AES but with the key being the only obvious string I didn’t immediately think to try the IV. Time to get my reverse engineer shit together...
Setting up dnSpy was a nightmare for me for reasons I can’t fathom- my host OS is Ubuntu but dnSpy is able to be run by WINE; not for me! I had dotnet40 installed via winetricks and everything too!
*sigh* Hello Windows, my old enemy... I downloaded an ISO image of Windows 7 x64 and successfully set up dnSpy here.
5 minutes later I had all the information I needed from the C# representation of the assembly code of the exe... Now time to decrypt, revealing the password of w3lc0meFr31nd.
Login... Now I’m ark; from my enum as Steve I was aware the path to root lay within ark’s AD Recycle Bin privileges and sure enough, the LDAP query that previously returned nothing returned another cascadeLegacyPwd; this time for TempAdmin.
From the email found within Data, I had an awareness that this password was also the password of administrator... A serving of baCT3r1aN00dles later and we have root.

So, Cascade was a really enjoyable machine to me- I’ve got my head around AD enumeration a bit more and I’ve learned an important lesson about not focusing on one goal: sometimes the route in isn’t what you think. :)
#hackthebox#ctf#hacking#reverse engineering#dotnet#windows 7#virtualbox#active directory#offensive security#enumeration#nmap#ldap#smb#ad#rpc#kerberos#OSCP prep
2 notes
·
View notes
Text
Cách đổi tên user trong Active Directory
Bạn có thể đổi tên tài khoản người dùng trong Active Directory theo một số cách khác nhau. Ví dụ như sử dụng giao diện đồ họa của AD hoặc lệnh PowerShell.
Cách đổi tên Domain User sử dụng Active Directory
Cách đơn giản nhất để đổi tên người dùng AD là sử dụng Active Directory Users and Computers (ADUC). - Mở bảng ADUC bằng cách chạy lệnh dsa.msc trong CMD; - Tích chọn tùy chọn sau trong menu: View > Advanced Features; - Dùng Active Directory tìm user bạn muốn đổi tên; - Mở bảng user properties rồi nhấn vào tab Object. Tên đầy đủ của người dùng được hiển thị trong trường Canonical name of object. Đây là tên được hiển thị trong bảng điều khiển ADUC và các công cụ Windows và AD khác;

- Để đổi tên user, bạn nhấn phải chuột vào tên người dùng rồi chọn Rename;

- Trong cửa sổ mở ra, bạn có thể thay đổi Full Name (Tên chính tắc của đối tượng), First name, Last name, Display Name, cũng như các thuộc tính userPrincipalName và userlogonname (samAccountName / pre-Windows 2000); - Nhập tên người dùng bạn muốn đổi và nhấn Ok để áp dụng.

Bạn cũng có thể đổi tên người dùng bằng cách chỉnh sửa thủ công các thuộc tính thích hợp trong tab Attribute Editor trong cửa sổ properties của người dùng.

Cách đổi tên User bằng PowerShell?
Bạn có thể sử dụng lệnh trong PowerShell để đổi tên người dùng trong AD. Các lệnh cơ bản là Rename-ADObject và Set-ADUser. - Rename-ADObject — cho phép bạn thay đổi giá trị của các thuộc tính: cn, DifferentName, name; - Set-ADUser — cho phép bạn thay đổi samAccountName, UPN, given name, surname và other names của người dùng. Nếu bạn muốn đổi tên người dùng sử dụng Rename-ADObject, bạn phải chỉ định DistinguishedName của nó. Ví dụ: Rename-ADObject –identity “CN=Nguyen Van A,OU=Office,OU=User,OU=Sales,DC=blogcntt,DC=com” -NewName "Nguyen Van A" Mẹo: Bạn có thể thêm tham số whatIf vào một lệnh để lấy thông tin về hoạt động mà lệnh đó sẽ thực hiện. Để làm cho lệnh dễ dàng hơn, bạn có thể lấy thông tin của người dùng theo tên hoặc samAccountName bằng lệnh Get-ADUser: Get-Aduser a.nv | Rename-ADObject -NewName "b.nv" Liệt kê các thuộc tính có sẵn và giá trị của chúng: Get-ADUser "Nguyen Van A" | fl *name*

Bạn có thể thay đổi những cài đặt người dùng khác bằng lệnh Set-ADUser. Ví dụ: Get-ADUser b.nv | Set-ADUser –displayname “Nguyen Van B” –SamAccountName b.nv –Surname “B”

Bạn có thể sử dụng lệnh dsmove.exe để đổi tên người dùng. Cú pháp này được sử dụng: dsmove "" -newname "" Ví dụ, Đổi tên của "Nguyễn Van A" thành "Nguyen Van B": dsmove.exe "CN=Nguyen Van A,CN=Office,DC=Users,DC=Sales" -NewName "Nguyen Van B" Read the full article
0 notes
Text
PowerShell Enable Active Directory Recycle Bin

PowerShell Enable Active Directory Recycle Bin, work in Windows Server 2012/2012R2/2016/2019. 1. Enabling Recycle Bin (Windows Server 2008 R2): To enable recycle bin: Open Powershell on the PDC (Primary Domain Controller). NOTE: To confirm which server is the primary DC, run the below command: Get-ADForest | fl Make sure that the server you are using is the SchemaMaster or else the command will not work. Check that the ForestMode shows up as Windows2008R2Forest. If not, run Import-Module ActiveDirectory, then run following command: Set-ADForestMode –Identity -ForestMode Windows2008R2Forest enable it using Active Directory Domains and Trusts by right-clicking on the top level item and selecting Raise forest functional level. Please note that this option needs replication if one or more DCs exist, therefore running the PowerShell command yields faster results.Once enabled run the following command in PowerShell: Enable-ADOptionalFeature –Identity ‘CN=Recycle Bin Feature,CN=Optional Features,CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=domain’ –Scope ForestOrConfigurationSet –Target ‘ ’ By default, the deleted object lifetime and tombstone lifetime in AD are set to 60 days. If this is not enough, you can modify the value by running the below commands (below example sets them to 1 year): Set-ADObject -Identity “CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=domain” –Partition “CN=Configuration,DC=contoso,DC=com” –Replace:@{“tombstoneLifetime” = 365} Set-ADObject -Identity “CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=domain” –Partition “CN=Configuration,DC=domain” –Replace:@{“msDS-DeletedObjectLifetime” = 365} 2. How to restore an object (Windows Server 2008/2008R2): First, search for the object using one of the following commands using PowerShell. Don't forget to run the command: Import-Module ActiveDirectory Search for all objects: get-adobject -filter ‘IsDeleted -eq $True’ -IncludeDeletedObjects -properties IsDeleted,LastKnownParent | Format-List Name,IsDeleted,LastKnownParent,DistinguishedName Search for a particular user: Get-ADObject -Filter {displayName -eq "Name"} -IncludeDeletedObjects (where Name is the display name of the user) Once the user or object is found, restore it using the following command: Get-ADObject -Filter {displayName -eq "Name"} -IncludeDeletedObjects | Restore-ADObject This will restore it to its last OU location 3. Enabling Recycle Bin (Windows Server 2012/2012R2/2016/2019) In this versions enabled by default. Confirm that the forest functional level is at least Windows2008R2. Once completed: Open Active Directory Administrative Center Right-click on the domain name and select Enable Active Directory Recycle Bin Being that this option changes the collection structure for AD, a prompt will show that this action is irreversible. Press Ok Wait for the change to apply Done 4. How to restore an object (Windows Server 2012/2012R2/2016/2019): To restore an object: Open Active Directory Administrative Center;Click on the domain name folder and open the Deleted Objects folder from the list;Find the object and select Restore. This will automatically restore it to the location from where the object was deleted;To restore the object in another folder or OU, select Restore To;Done Read the full article
0 notes
Text
SCORCH : Active Directory Cleanup with Orchestrator
Active Directory Cleanup Runbook Automation

6 runbooks – 5 are functional workbooks and 1st runbook calls the rest in sequence.
Download the Powershell Scripts – ad cleanup runbook ps
Runbook 1 – AD Cleanup
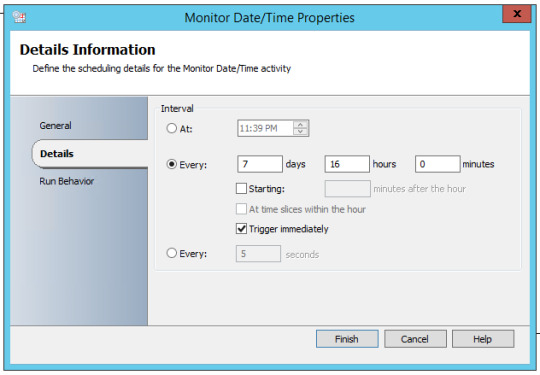
The Master Runbook ��� which triggers every 7 days 16 hours – call the 5 runbooks and they a ‘wait for completion’ before starting the next runbook.

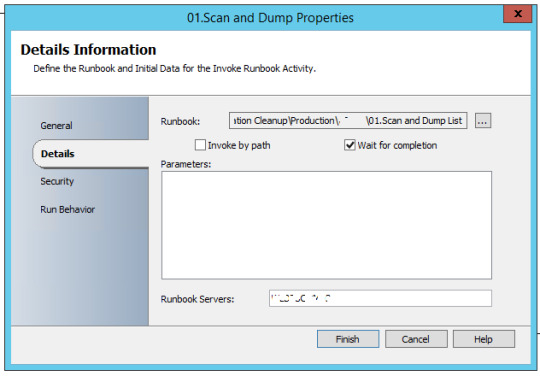

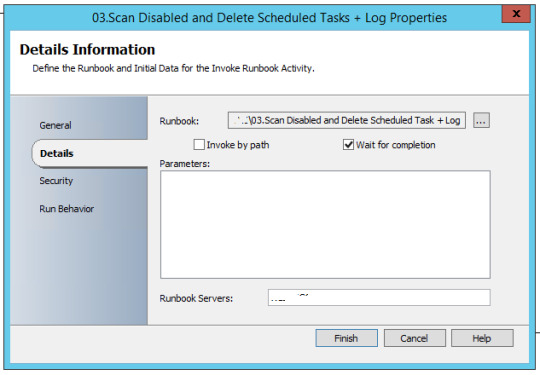

Runbook 2 – Scan and Dump List
Powershell script which scans Active Directory [admin rights not required], check machines which are inactive for 180 days and machine should not be disabled – Operating System = WinXP, Win7 or Win10.

C:\windows\System32\WindowsPowerShell\v1.0\powershell.exe {import-module activedirectory
$DaysInactive = 180
$time = (Get-Date).Adddays(-($DaysInactive))
$result=@()
$result2=@()
#————————————————————————————————————————–
Get-ADComputer -Filter {(Modified -lt $time) -and (useraccountcontrol -ne “4098”)} -Properties * |
select Name,OperatingSystem | foreach {if (($_.OperatingSystem -like “Windows 7*”) -or($_.OperatingSystem -like “Windows 10*”) -or ($_.OperatingSystem -like “Windows 8*”) -or ($_.OperatingSystem -like “Windows xp*”)) {$result+=$_.Name}}
$result | set-content C:\SourceSoftware\runbook-output\adcleaner\output\ad-cleaner.csv}
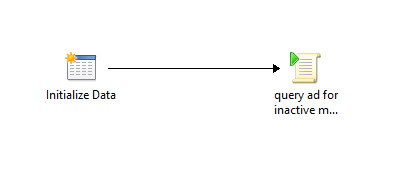
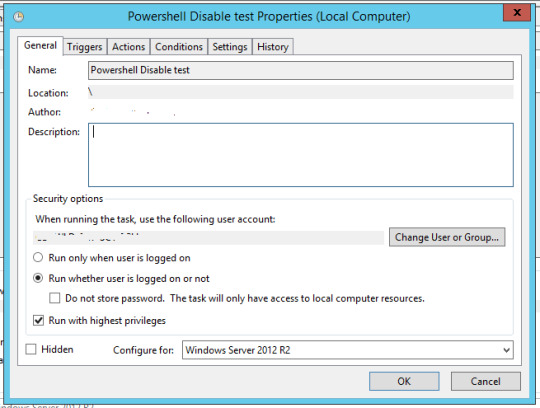
Runbook 3 – Scan and Disable Scheduled Task
Powershell script to Disable machines in AD [requires Admin rights] found in earlier Runbook



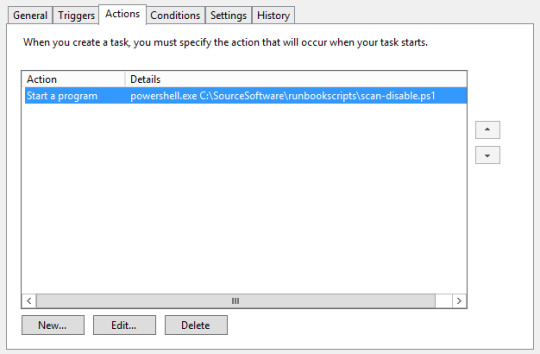
#Setting search parameters and creating array
import-module activedirectory
$DaysInactive = 180
$time = (Get-Date).Adddays(-($DaysInactive))
$result=@()
#————————————————————————————————————————–
#Searching for computers that fit the parameters
Get-ADComputer -Filter {(LastLogonDate -lt $time) -and (Enabled -eq “True”)} -Properties * -ErrorAction SilentlyContinue |
select Name,OperatingSystem,comment,CN,LastLogonDate,DistinguishedName | foreach {if (($_.OperatingSystem -like “Windows 7*”) -or($_.OperatingSystem -like “Windows 10*”) -or ($_.OperatingSystem -like “Windows 8*”) -or ($_.OperatingSystem -like “Windows xp*”)) {$result+=$_}}
#Disabling computers
#$result|Foreach-Object {Disable-ADAccount -Identity $_.DistinguishedName -recursive -ErrorAction SilentlyContinue}
foreach ($_ in $result)
{If ($_ -ne $Null)
{Disable-AdAccount -Identity $_.DistinguishedName}}
#————————————————————————————————-
Runbook 4 – Scan Disabled and Delete Scheduled Task + Log
Powershell Script to scan for machines inactive for 360 days and disabled, then delete them [required AD Admin rights]
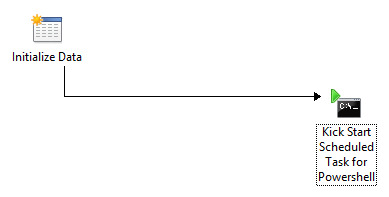




#Setting search parameters and creating array
import-module activedirectory
$DaysInactive = 360
$time = (Get-Date).Adddays(-($DaysInactive))
$result=@()
#Searching for computers that fit the parameters
#————————————————————————————————————————–
Get-ADComputer -Filter {(LastLogonDate -lt $time) -and (Enabled -eq “False”)} -Properties * -ErrorAction SilentlyContinue |
select Name,OperatingSystem,comment,DistinguishedName | foreach {if (($_.OperatingSystem -like “Windows 7*”) -or($_.OperatingSystem -like “Windows 10*”) -or ($_.OperatingSystem -like “Windows 8*”) -or ($_.OperatingSystem -like “Windows xp*”)) {$result+=$_}}
#Write Output to Log
#————————————————————————————————————————–
$result | set-content \\SERVER01\runbook-output\adcleaner\output\ad-disable.csv
#————————————————————————————————————————–
#Delete Function
#————————————————————————————————————————–
foreach ($_ in $result)
{If ($_ -ne $Null)
{Remove-ADObject -Identity $_.DistinguishedName -recursive -Confirm:$false}}
#————————————————————————————————————————–
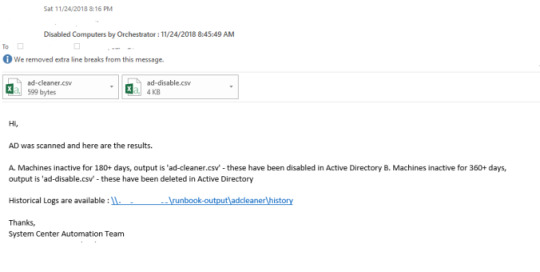
Runbook 5 – Mail Routine
Send mail with output files to recipients, with subject of today’s date



The Subject of the mail would be appended with current date and time
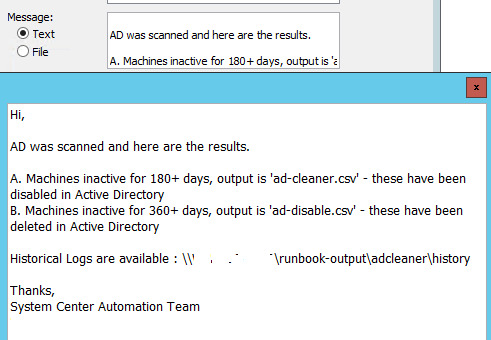

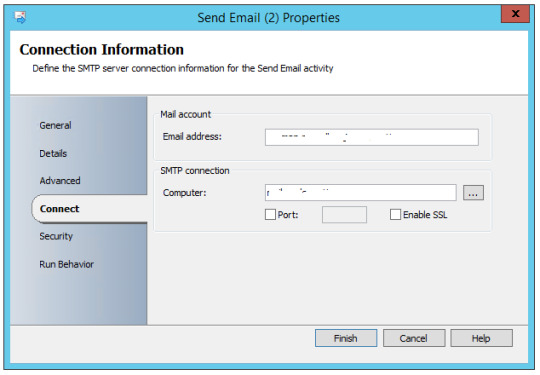
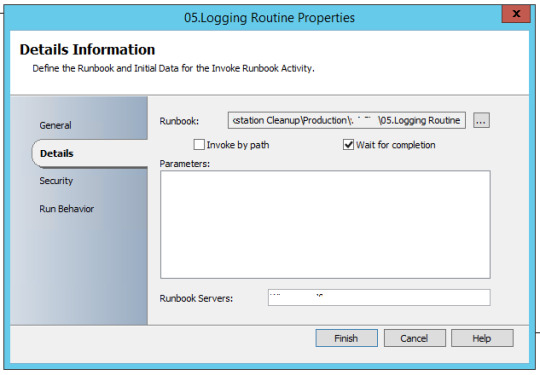
Runbook 6 – Logging Routine
Moving current logs to history folders and appending with date of file transfer in name.

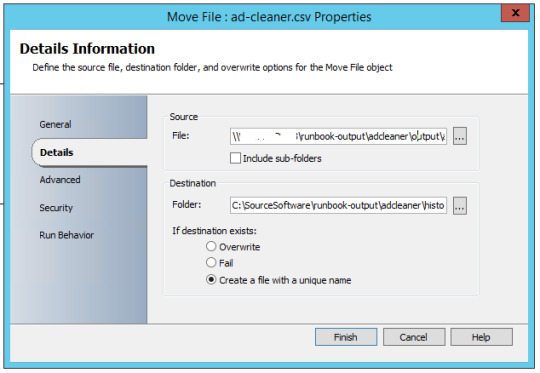




sample automated email
from WordPress http://bit.ly/2Hpa6tj via IFTTT
0 notes
Text
Powershell: Exporting Active Directory Contacts
Powershell: Exporting Active Directory Contacts
Some time ago, I needed to have a list of all Contacts registered in Active Directory. Knowing that there are a lot of them (numbering at least eighty), getting the data manually was not a viable alternative, particularly knowing that the same objective can be achieved through Powershell. I eventually came up with a solution. To make following it logically easier, I’m going to include commentary…
View On WordPress
0 notes
Text
Find Unresolvable ForeignSecurityPrincipals in ActiveDirectory
Active Directory is a complex service. It is even more complex when dealing with multiple forests. I have had to manage many multi-forest domains over the years. People are always asking for reports on group membership for audit or access verification. There are some good tools to do that with, but there are issues with many of them when dealing with multi-forest environments. One of these problems is group membership in foreign domains.
When you add an object from a foreign domain into a group it creates an object called a ForeignSecurityPrinciple. The object is basically just a SID that can be used in the local domain along with some information that helps AD construct information about the FSP for tools to display. When the object functions correctly most tools will perform as expected. You can generate your reports or run your scripts without any issues.
These objects help us get the job done, except when they do not. A problem that occurs many times is that you try to query a group with PowerShell or some tool and the tool returns unexpected results. If you dig into it you will generally find that the tool is looking for a constructed property that cannot be built and AD returns an error which causes unexpected results. The properties of the FSPs are pulled from the foreign domain by AD and returned to the tool. If someone deleted the referenced object the query is null and thus the property cannot be returned leading to our error condition.
If you come across a multi-forest domain you will learn something you didn't know frequently. One of these things is that FSPs with constructed properties will crash your tools and scripts that always worked for you in the past. There is hope though. This simple script can ferret out those pesky and undesired orphaned objects. You can send the results to a script to delete them or you can simply pipe the out for review. I will say that I prefer group membership to be clean and this script has helped me keep it that way.
<# Get-DeletedFsps.ps1 -Domains @("prod.contoso.com", "nonprod.contoso.com" Results: CN=S-1-5-21-0000000000-0000000000-000000000-20229,CN=ForeignSecurityPrincipals,DC=prod,DC=contoso,DC=com CN=S-1-5-21-0000000000-0000000000-000000000-87540,CN=ForeignSecurityPrincipals,DC=prod,DC=contoso,DC=com CN=S-1-5-21-0000000000-0000000000-000000000-21712,CN=ForeignSecurityPrincipals,DC=nonprod,DC=contoso,DC=com CN=S-1-5-21-0000000000-0000000000-000000000-87541,CN=ForeignSecurityPrincipals,DC=nonprod,DC=contoso,DC=com #> Param( [Parameter(Position=0,Mandatory=$true)][Array]$Domains=@()) # Result set creation $Unmapped = @() # Cycle through domains ForEach ($Domain In $Domains) { # Build the path to FSPs $Dn = "CN=ForeignSecurityPrincipals" ForEach($DomainPart In $Domain.Split('.')) { $Dn += ",DC=$DomainPart" } # Obtain the list of FSPs $ForSecPri = Get-ADObject -SearchBase $Dn -Server $Domain -LdapFilter "(objectClass=foreignSecurityPrincipal)" # Resolve FSPs and if we cannot add them to the result set ForEach($Object In $ForSecPri) { Try { (New-Object System.Security.Principal.SecurityIdentifier($Object.Name)).Translate([System.Security.Principal.NTAccount]) | Out-Null } Catch [System.Security.Principal.IdentityNotMappedException] { $Unmapped += $Object.DistinguishedName } } } # Return the results for post processing Return $Unmapped
1 note
·
View note
Text
👍To add people to Facebook Ads Ma👌
To add people to Facebook Ads Manager, follow these steps:
1. **Access Ads Manager**: Go to Facebook Ads Manager by visiting facebook ads manager and logging in with your Facebook account credentials. If you don't have an Ads Manager account set up yet, you'll need to create one.
2. **Navigate to Settings**: Once you're in Ads Manager, look for the settings icon (gear icon) in the upper-right corner and click on it. This will take you to the "Ad Account Settings" page.
3. **Navigate to Ad Account Roles**: On the "Ad Account Settings" page, find and click on "Ad Account Roles" in the left-hand menu. This is where you can manage who has access to your ad account.
4. **Click on Add People**: In the "Ad Account Roles" section, you'll see a list of people who currently have access to the ad account. To add someone new, click on the "Add People" button.
5. **Enter Email Address or Name**: In the pop-up window, you can add people by entering their email address associated with their Facebook account or by typing their name. As you type, Facebook will suggest matching profiles.
6. **Select Role**: After selecting the person you want to add, choose their role from the dropdown menu. There are different roles with varying levels of access, such as Admin, Advertiser, or Analyst. Choose the appropriate role based on the level of access you want to grant them.
7. **Click Add**: Once you've selected the person and their role, click the "Add" button to add them to your ad account.
8. **Confirm and Adjust Settings (if necessary)**: After adding someone, you may want to review the settings for their role to ensure they have the appropriate level of access. You can adjust these settings by clicking on the pencil icon next to their name in the "Ad Account Roles" section.
9. **Notify the Person (optional)**: You can choose to notify the person via email that they've been added to the ad account. This can be helpful for letting them know they have access and what level of access they've been granted.
#SocialAdvertising
#DigitalStrategy
#AdPerformance
#AdOptimization
#AudienceInsights
#CampaignManagement
#MarketingMetrics
#ContentStrategy
#FacebookBusiness
#AdBudget
#AdAnalytics
#FacebookStrategy
#FacebookMarketingTips
#FacebookAdsManager
#FacebookPixel
#AdTargeting
#FacebookAudience
#AdObjectives
#FacebookROI
#AdPlacement #Rafiqmia #Fundasdigitalmarketing
That's it! The person you added will now have access to your Facebook ad account according to the role you assigned to them.
#SocialAdvertising#DigitalStrategy#AdPerformance#AdOptimization#AudienceInsights#CampaignManagement#MarketingMetrics#ContentStrategy#FacebookBusiness#AdBudget#AdAnalytics#FacebookStrategy#FacebookMarketingTips#FacebookAdsManager#FacebookPixel#AdTargeting#FacebookAudience#AdObjectives#FacebookROI#AdPlacement#Rafiqmia#Fundasdigitalmarketing
0 notes
Text
Difference Between Facebook Ads and Boosting a Post
Facebook Ads provide more customization options and specific targeting, with different objectives like website traffic or lead generation. Boosting a post is a quick and easy way to increase post reach, but with limited targeting options and objective mainly focused on engagement.
https://iosandweb.net/blog/facebook-ads-vs-boosting-a-post-whats-the-difference/

#FacebookAds#boostingposts#socialmediaadvertising#digitalmarketing#targeted advertising#socialmediamarketing#onlineadvertising#paidsocial#AdObjectives#audiencetargeting
0 notes
Link
(Disclaimer: ESL)A while back we had a couple of session with microsoft, one of those focused on DR of Active Directory and another one was on AD health. Here are some of my notes and things learned. Some of them are obvious but might need a reminder and other ones might not be well known:The computers remembers the password last two passwordsWhen rescuing AD, one of the most unsettling things is the thought of having to repair the trust-relationship for all computers that has changed it's password since the backup you are restoring from.Well, it turns out that the machine stores 2 passwords: The one it uses and the one it had before, so restoring to a previous backup should not be a problem. Depending on the age of your backup.Never trust one platformHaving your domaincontrollers on more than one hardware platform (ie. VMWare and Bare Metal or VMWare and Hyper-V) migitiates the risk tremendously. Especially if VMWare auth is down because of that you can't authenticate to AD.Never trust one backup platformUsing both Veeam and Windows Server Backup for your DC's is a great idea. Especially if the Veeam backup got hacked or is corrupt, tapes are corrupt etc. Also, if you are a premier support customer; Microsoft does only support Windows Server Backup.Keep your ADSM (active directory safe mode) passwords properly documented and stored!This is an easy one to forget about, especially if you have inherited an environment. If it's not documented and locked into a safe; change the password and document it properly.Plan for that your DR scenarios might have to take place offlineIn case of a security breach, the network might have to be taken offline. Plan for DR accordingly. And, DC's might have to be kept offline during recovery so that a DC with a larger RID-number on it's objects dosen't overwrite the data that you just restored.Most AD recovery isn't a DR scenario per sayBut a mass deletion in AD is severe enough. Doublecheck that you have the recycle-bin enabled in your domain and develop scripts to quickly mass-restore objects. What we use:# This restores the OU's first, and after that the objects in order. Else it will try to recreate the objects in an OU or object that dosen't exist and fail. # Replace the date with the date that that the mass-deletion took place $FromDate = Get-Date "2018-03-30 13:02:02" $Deleted = Get-ADObject -Filter {(isdeleted -eq $true) -and (WhenChanged -gt $FromDate)} -IncludeDeletedObjects -Properties * | sort lastknownparent -Descending $Deleted | ? {$_.objectclass -eq "organizationalUnit"} | Restore-ADObject $Deleted | ? {$_.objectclass -ne "organizationalUnit"} | Restore-ADObject Use the microsoft tiering model for securing important infrastructureRead more about it here: https://ift.tt/2KJuXYT will hopefully make it so that you don't have to rebuild the entire environment in case of a security breach.Coffee and perhaps something to eat the AD admins best friend.Give AD time to replicate and go and grab a coffee. Being to much in a hurry WILL make things worseDocument your AD in an easy wayUse the "Active directory topology diagrammer" to document your AD and keep it in the same binder as the DR documentation. This will save the one rescuing the AD a lot of headache and even for you since everybody reacts differently during a crisis.Emergency admin accountYou should have an emergency admin account, and it should be monitored for logins and locked in a safe. Password should be changed regularly.Practice DR yearlyWe all know this, but we don't do it because of time. Create a recurring meeting, one or two days a year for practicing to force yourself to make time for it.After practicing this the first time and documenting a routine, the worries AD breaking down is minimal. And the big black hole of worry when it comes to this shrinks.AD is stable, and most DR scenarios isn't because of a failiure of ADMost DR scenarios is because of a security breach. I yet again refer to: https://ift.tt/2KSy1yy DC that you recover to SHOULD be able to handle most of the load for a period of timeWhen recovering AD, at some time, only one DC will be available. And all machines will try to go towards it. When creating or buying a spare machine that AD will be restored to - add a lot of CPU.Write the DR documentation so that it's easy to follow.You might not be around when it happens, you might have been hit by a buss. And the one the company decides to call in panic might not be the one best suited for the job.It's OK since Server 2008 to change IP and DNS of the domaincontrollersThis seems to be the biggest no-no in the AD community. But according to microsoft it's been supported for a while and it seems to be an inherited belief in the sysadmin community. Not to say it isn't risky, it is and some depending systems might not handle it.You want to flush/register DNS tho, and scan through your DNS-records. I've since done this in a test-forest, DMZ-forest and couple of production-forests and never had a problem. This comes in especially handy in environments where you haven't load balanced LDAP/DNS and need to keep the same names/ip of some DC'sHow we did it:Promote a new DC.Demote old DC.Change name of old DC.Remove old DC from domain.Change IP of old DC, turn it off.Change name of new DC to old DC's name.Change IP of new DC to the old DC's IPipconfig /flushdnsipconfig /registerdnsWait until "repadmin /showrepl" is OK, grab a coffee.Change name of the new DC to the old DC's name.ipconfig /flushdnsipconfig /registerdnsWait until "repadmin /showrepl" is OK, grab a coffee.Out of hundreds of systems and thousands of computers and servers, only 3 systems choked when we did this on 5 DC's.GPO's that are backed up with the powershell cmdlets don't store the linked OU'sThis might come as a nasty suprise for some. Use the Get-GPOReport and parse the XML for the links that you store in the same folder as the GPO backup.Write pester tests for testing baseline of your DC'sYou might not remember to put all the roles and configs in, and you might want to test that the networking team has done their jobs. So testing the baseline of your DC's is important. What we currently test with pester after installing a new DC:Can resolve towards our edge DNS serversThat all roles and features needed are installedThat the DFS namespace resolves properlyThat no replication errors are occuringGet-ADUser works aganist the serverThat the server can resolve DNSAV is installed and exclusions are madeThat firewall ports are opened/closedThat the server is in an auto patch groupThat the distribution of DC's in the auto patch groups are even, so that 50% of the dc's don't auto update at the same time.That it can reach other DC'setc.Have your boss in on the DR plans, and agree that he will act as a gatekeeper during a DR scenarioHaving someone holding the door and acting as a information channel during a DR scenario is important. Especially since one error might lead to you having to start over the DR routine from step 1 (An old DC writing over the recovered contents of a new DC for example). A room with a lockable door is preferred.Load balancing the primary DNS and LDAPThis is a great idea. Especially when a lot of stuff is bound directly to the DC's. This will make it easier to restart, replace and remove DC's. F5 for example handles this fine.Moving FSMO roles is easy# If FSMO role holder is online: Move-ADDirectoryServerOperationMasterRole -Identity "Target-DC" -OperationMasterRole SchemaMaster,RIDMaster,InfrastructureMaster,DomainNamingMaster,PDCEmulator # If FSMO role holder is crashed and you need to sieze the roles Move-ADDirectoryServerOperationMasterRole -Identity "Target-DC" -OperationMasterRole SchemaMaster,RIDMaster,InfrastructureMaster,DomainNamingMaster,PDCEmulator -Force It's normal for a demote of a DC to leave some thrash DNS recordsScan your DNS records, either manually or with a script after leftover records from the old DC's and delete them.Schema changes isn't final until next defragmantation of the JET databaseThis occurs once every 12h. even tho it works before that.If you're going to monitor one thing, monitor for JET database errors on the domaincontrollersThis is a sign of corruption in the AD database. Here's the event ID's: https://ift.tt/2KzF03f DFS-R for SYSVOL and Netlogon replication errorsA restore of those can be quite annoying, but not to hard: https://ift.tt/2KSy2CC be carefull so that you don't overwrite a good share that you were supposed to use. And double check that GPO's are working after a restore, else restore GPO from last known good backup. Otherwise it might cause a mismatch between GPO version in AD and GPO version in SYSVOL.Domain isn't a security bondary, a forest isI yet again, refer to the tiering model: https://ift.tt/2KN7OVm is a good read as well: https://ift.tt/2J0iDOL for NTLMv1 usage and disable itNTLMv1 is roughly 30 years old and an obselete authentication method. What it does is that it from the beginning only supported 7 characters + 1 parity bit like this:[ ][ ][ ][ ][ ][ ][ ][*]This is simple enought to crack, 7 chars is done in no time at all. According to what i found on the internet it's 577 combinations and takes around 10 minutes. Now, afterwards they added support for 14 chars and that should take, but did they make it 14 whole bytes + a parity bit? NO...If they made it like this:[ ][ ][ ][ ][ ][ ][ ][ ][ ][ ][ ][ ][ ][ ][*]The password would in theory take 204 million years for a brute force attack to crack it. But how it works is that it splits the password in two like this:[ ][ ][ ][ ][ ][ ][ ][*] + [ ][ ][ ][ ][ ][ ][ ][*]So it takes in theory 20 minutes instead...On top of that, if your password is lets say, 11 charachters it fills the remaining bytes with 0.[M][Y][P][A][S][S][W][*] + [O][R][D][!][0][0][0][*]Did you notice how it's all caps? That's because the NTLM password is converted to all caps before hashed into the database. NTLMv1 is dumb and should be disabled.If you installed your forest from scratch with with Server 2016, NTLMv1 is disabled by default.If you keep your systems patched, security breaches through software vunerabilities is rareThe most common point of entry is through identity theft. This is why it's even more important to use the microsoft security model when designing security for your AD.Because if the hacker has owned a computer by calling Debbie and asking nicley, and you have been logged on with an account that has Domain Admin rights on that machine; The hacker owns your network.When scanning software for missing patches use a software or script that uses the wsusscn2.cabUse the WSUS offline catalog when scanning for missing patches! A lot of software just contacts your local WSUS and if WSUS dosen't have any patches to offer it assumes that it's good. The truth is that there might be a lot of patches missing on your system, and scanning with the offline WSUS catalog will catch it.Upgrading the forest functional level is best done daytimeA lot of sneaky errors can occur when uppgrading the forest/domain functional level.One of those are that the KRBTGT (Kerberos Ticket Granting Ticket) password is changed. Windows systems tend to follow the change without any problems, but *nix systems talking kerberos might not and you might have to restart them. So if your environment has a lot of important applications running in linux, especially if they are critical; do it during daytime and cooperate with your *nix team.From my experience, this is best suited at 10AM. People have arrived to work, are awake and ain't hungry.Also, do yourself a faviour and upgrade in a test forest with the most critical apps first.As soon as you have one DC up, rerun a full backup using windows backup tooDon't want to have to do all that work again if easily avoidable.Thanks for the input /u/tomasplandEdit: Thanks a lot for the great response! Fixed some spelling and clarified what emergency admin is. via /r/sysadmin
0 notes
Text
Moving a User to a Different OU
Today I will be sharing a simple way to move a user account to a specified OU.
PowerShell:
Get-ADUser USER NAME HERE | Move-ADObject –targetpath ‘PATH HERE: OU=OU NAME HERE,DC=DOMAIN NAME,DC=TOP LEVEL DOMAIN’
Example Scenario:
I will move the account of a temporary worker at DigiCompany.com named Felix Jones with the user name of FJones to the Disabled Users OU.
Get-ADUser FJones | Move-ADObject –targetpath ‘OU=DISABLEDUSERS,DC=DIGICOMPANY,DC=COM’
Although I have tested and previously successfully ran these commands, each organization and environment is different and as such I cannot guarentee that using the information listed above will not cause any disruption or harm. Run any PowerShell commands with caution and only with a full understanding of what each command and switch does. Run only in an environment in which you are authorized to do so and use at your own risk.
#Microsoft#Active Directory#Powershell#System Administration#the IT life#that IT life#Computers#Network Administration
0 notes
Text
Latest Update Free Version of Microsoft 70-410 Exam Study Guides in CertBus
How to pass MCSA 70-410 exam? CertBus gives all candidates the 100% guaranteed MCSA 70-410 Installing and Configuring Windows Server 2012 exam dumps. We help you to face your MCSA 70-410 exam with confidence. Successful candidates share their reviews about our MCSA 70-410 Installing and Configuring Windows Server 2012 dumps. Now CertBus supplies the most effective MCSA 70-410 VCE and PDF dumps. We ensure our MCSA 70-410 exam questions are the most complete and authoritative compared with others, which will ensure your MCSA 70-410 exam pass.
We CertBus has our own expert team. They selected and published the latest 70-410 preparation materials from Microsoft Official Exam-Center: http://ift.tt/2qVZwwH
QUESTION NO:3
You work as a senior administrator at ABC.com. The ABC.com network consists of a single
domain named ABC.com. All servers on the ABC.com network have Windows Server 2012
installed, and all workstations have Windows 8 installed.
You are running a training exercise for junior administrators. You are currently discussing a
Windows PowerShell cmdlet that activates previously de-activated firewall rules.
Which of the following is the cmdlet being discussed?
A. Set-NetFirewallRule
B. Enable-NetFirewallRule
C. Set-NetIPsecRule
D. Enable-NetIPsecRule
Answer: B
Explanation:
QUESTION NO:39
Your network contains a server named Server1 that runs Windows Server 2012 R2.Server1 has the
Hyper-V server role installed.
Server1 hosts four virtual machines named VM1, VM2, VM3, and VM4.
Server1 is configured as shown in the following table.
You install a network monitoring application on VM2.
You need to ensure that all of the traffic sent to VM3 can be captured on VM2.
What should you configure?
A. NUMA topology
B. Resource control
C. Resource metering
D. Virtual Machine Chimney
E. The VLAN ID
F. Processor Compatibility
G. The startup order
H. Automatic Start Action
I. Integration Services
J. Port mirroring
K. Single-root I/O virtualization
Correct Answer: J
Explanation
Explanation/Reference:
Explanation:
With Hyper-V Virtual Switch port mirroring, you can select the switch ports that are monitored as well as
the switch port that receives copies of all the traffic. And since Port mirroring allows the network traffic of a
virtual machine to be monitored by copying the traffic and forwarding it to another virtual machine that is
configured for monitoring, you should configure port mirroring on VM2.
References:
http://ift.tt/1FXnOsp
QUESTION NO:30
Your network contains an Active Directory forest named contoso.com. All domain controllers currently run
Windows Server 2008 R2.
You plan to install a new domain controller named DC4 that runs Windows Server 2012 R2.
The new domain controller will have the following configurations:
Schema master
Global catalog server
Active Directory Federation Services server role
Active Directory Certificate Services server role
You need to identify which configuration can be fulfilled by using the Active Directory Domain Services
Configuration Wizard.
Which configuration should you identify?
A. Enable the global catalog server.
B. Install the DNS Server role.
C. Install the Active Directory Certificate Services role.
D. Transfer the schema master.
Correct Answer: A
Explanation
Explanation/Reference:
QUESTION NO:9
Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2.Server1
and Server2 are part of a workgroup.
On Server1 and Server2, you create a local user account named Admin1.You add the account to the local
Administrators group. On both servers, Admin1 has the same password.
You log on to Server1 as Admin1.You open Computer Management and vol.connect to Server2. When you
attempt to create a scheduled task, view the event logs, and manage the shared folders, you receive
Access Denied messages.
You need to ensure that you can administer Server2 remotely from Server1 by using Computer
Management.
What should you configure on Server2?
A. From Server Manager, modify the Remote Management setting.
B. From Local Users and Groups, modify the membership of the Remote Management Users group.
C. From Windows Firewall, modify the Windows Management Instrumentation (WMI) firewall rule.
D. From Registry Editor, configure the LocalAccountTokenFilterPolicy registry value.
Correct Answer: D
Explanation
Explanation/Reference:
The LocalAccountTokenFilterPolicy setting affects how administrator credentials are applied to remotely
administer the computer.
References:
http://ift.tt/1msV2V0
QUESTION NO:10
You work as an administrator at ABC.com. The ABC.com network consists of a single domain
named ABC.com. All servers on the ABC.com network have Windows Server 2012 installed.
ABC.com has a server, named ABC-SR13, which is configured as the primary DNS server in the
ABC.com domain. ABC.com has another server, named ABC-SR14, which makes use of ABC-
SR13 for DNS queries.
You want to make sure that running nslookup.exe from ABC-SR14 produces a result that shows
the proper name of the default server.
Which of the following actions should you take?
A. You should consider creating a reverse lookup zone on ABC-SR14.
B. You should consider creating a forward lookup zone on ABC-SR14.
C. You should consider creating a reverse lookup zone on ABC-SR13.
D. You should consider creating a forward lookup zone on ABC-SR13.
Answer: C
Explanation:
QUESTION NO:14
You work as a senior administrator at ABC.com. The ABC.com network consists of a single
domain named ABC.com. All servers on the ABC.com network have Windows Server 2012
installed.
You are running a training exercise for junior administrators. You are currently discussing
connection security rules.
Which of the following is TRUE with regards to connection security rules? (Choose all that apply.)
A. Connection security rules allows for traffic to be secured via IPsec.
B. Connection security rules do not allow the traffic through the firewall.
C. Connection security rules are applied to programs or services.
D. Connection security rules are applied between two computers.
Answer: A,B,D
Explanation:
QUESTION NO:12
You work as a senior administrator at ABC.com. The ABC.com network consists of a single
domain named ABC.com. All servers on the ABC.com network have Windows Server 2012
installed.
You are running a training exercise for junior administrators. You are currently discussing Group
Policy preference.
Which of the following is TRUE with regards to Group Policy preference?
A. It supports applications and operating system features that are not compatible with Group
Policy
B. It does not support item-level targeting.
C. It is the same as Group Policy filtering.
D. It does not cause the application or operating system feature to disable the user interface for
the settings they configure.
Answer: A,D
Explanation:
QUESTION NO:23
You work as an administrator at ABC.com. The ABC.com network consists of a single domain
named ABC.com. All servers in the ABC.com domain, including domain controllers, have Windows
Server 2012 installed.
You have just executed the Uninstall-WindowsFeature Server-Gui-Shell
QUESTION NO:35
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain.
The domain contains two domain controllers named DC1 and DC2 that run Windows Server 2012 R2.
The domain contains a user named User1 and a global security group named Group1.
You need to modify the SAM account name of Group1.
Which cmdlet should you run?
A. Add-AdPrincipalGroupMembership
B. Install-AddsDomainController
C. Install-WindowsFeature
D. Install-AddsDomain
E. Rename AdObject
F. Set AdAccountControl
G. Set-AdGroup
H. Set-User
Correct Answer: E
Explanation
Explanation/Reference:
QUESTION NO:22
Your network contains an Active Directory domain named contoso.com. The domain contains a DHCP
server named Server1 that runs Windows Server 2012 R2.
You create a DHCP scope named Scope1. The scope has a start address of 192.168.1.10, an end
address of 192.168.1.50, and a subnet mask of 255.255.255.192.
You need to ensure that Scope1 has a subnet mask of 255.255.255.0.
What should you do first?
A. From the DHCP console, reconcile Scope1.
B. From the DHCP console, delete Scope1.
C. From the DHCP console, modify the Scope Options of Scope1.
D. From Windows PowerShell, run the Set-DhcpServerv4Scope cmdlet.
Correct Answer: B
Explanation
Explanation/Reference:
The only way to change the subnet mask of a scope is to delete and recreate the scope. SetDhcpServerv4Scope
does not include a parameter for the subnet mask.
CertBus exam braindumps are pass guaranteed. We guarantee your pass for the 70-410 exam successfully with our Microsoft materials. CertBus Installing and Configuring Windows Server 2012 exam PDF and VCE are the latest and most accurate. We have the best Microsoft in our team to make sure CertBus Installing and Configuring Windows Server 2012 exam questions and answers are the most valid. CertBus exam Installing and Configuring Windows Server 2012 exam dumps will help you to be the Microsoft specialist, clear your 70-410 exam and get the final success.
70-410 Latest questions and answers on Google Drive(100% Free Download): http://ift.tt/2qWnasR
70-410 Microsoft exam dumps (100% Pass Guaranteed) from CertBus: http://ift.tt/2qVZwwH [100% Exam Pass Guaranteed]
Why select/choose CertBus?
Millions of interested professionals can touch the destination of success in exams by certbus.com. products which would be available, affordable, updated and of really best quality to overcome the difficulties of any course outlines. Questions and Answers material is updated in highly outclass manner on regular basis and material is released periodically and is available in testing centers with whom we are maintaining our relationship to get latest material.
Brand Certbus Testking Pass4sure Actualtests Others Price $45.99 $124.99 $125.99 $189 $69.99-99.99 Up-to-Date Dumps Free 365 Days Update Real Questions Printable PDF Test Engine One Time Purchase Instant Download Unlimited Install 100% Pass Guarantee 100% Money Back Secure Payment Privacy Protection
Published by CertBus http://ift.tt/2rZy1XA
0 notes
Text
[Latest Version] Free CertBus Microsoft 70-410 PDF Download with 100% Pass Guarantee
Attention please! Here is the shortcut to pass your 70-410 exam! Get yourself well prepared for the Microsoft MCSA 70-410 Installing and Configuring Windows Server 2012 exam is really a hard job. But don’t worry! We CertBus, provides the most update exam PDF and VCEs. With CertBus latest exam Q and As, you’ll pass the MCSA 70-410 Installing and Configuring Windows Server 2012 exam in an easy way
We CertBus has our own expert team. They selected and published the latest 70-410 preparation materials from Microsoft Official Exam-Center: http://ift.tt/2qVZwwH
QUESTION NO:38
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain.
The domain contains two domain controllers named DC1 and DC2 that run Windows Server 2012 R2.
The domain contains a user named User1 and a global security group named Group1.
You reconfigure DC2 as a member server in the domain.
You need to add DC2 as the first domain controller in a new domain in the forest.
Which cmdlet should you run?
A. Add-AdPrincipalGroupMembership
B. Install-AddsDomainController
C. Install-WindowsFeature
D. Install-AddsDomain
E. Rename AdObject
F. Set AdAccountControl
G. Set-AdGroup
H. Set-User
Correct Answer: D
Explanation
Explanation/Reference:
Explanation:
Installs a new Active Directory domain configuration
C:\PS>Install-ADDSDomain -Credential (Get-Credential CORP\EnterpriseAdmin1) -NewDomainName
child – ParentDomainName corp.contoso.com -InstallDNS -CreateDNSDelegation -DomainMode Win2003
– ReplicationSourceDC DC1.corp.contoso.com -SiteName Houston -DatabasePath “D:\NTDS” –
SYSVOLPath “D:\SYSVOL” -LogPath
“E:\Logs” NoRebootOnCompletion
References:
http://ift.tt/2qp7NNp
QUESTION NO:17
Your network contains an Active Directory domain named contoso.com.
All client computers run Windows 8.
You deploy a server named Server1 that runs Windows Server 2012 R2.
You install a new client-server application named App1 on Server1 and on the client computers. The client
computers must use TCP port 6444 to connect to App1 on Server1.Server1 publishes the information of
App1 to an intranet server named Server2 by using TCP port 3080.
You need to ensure that all of the client computers can connect to App1. The solution must ensure that the
application can connect to Server2.
Which Windows Firewall rule should you create on Server1?
A. An outbound rule to allow a connection to TCP port 3080
B. An inbound rule to allow a connection to TCP port 3080
C. An outbound rule to allow a connection to TCP port 6444
D. An inbound rule to allow a connection to TCP port 6444
Correct Answer: D
Explanation
Explanation/Reference:
A. Server2 needs inbound on 3080
References:
http://ift.tt/2rOuTdS firewallwithadvanced-
security-in-windows-server-2012.aspx
QUESTION NO:31
You work as an administrator at ABC.com. The ABC.com network consists of a single domain
named ABC.com. All servers on the ABC.com network have Windows Server 2012 installed.
You have been instructed to make sure that a server, named ABC-SR07, is configured to be
managed remotely from ABC-SR01 using Server Manager.
Which of the following is not a valid option to take? (Choose all that apply.)
A. You could access the server manager on ABC-SR01.
B. You could access the server manager on ABC-SR13.
C. You could run the %windir%\system32\Configure-SMRemoting.exe from n elevated command
prompt on ABC-SR13.
D. You could run the Configure-SMRemoting.exe
QUESTION NO:29
You work as an administrator at ABC.com. The ABC.com network consists of a single domain
named ABC.com. All servers on the ABC.com network have Windows Server 2012 installed.
ABC.com has its headquarters in London, and several widespread satellite offices. When
ABC.com releases a new written policy stating that the graphical user interface (GUI) should not
be installed on any servers deployed to ABC.com
QUESTION NO:25
You have a server named Server1 that runs Windows Server 2012 R2.
You promote Server1 to a domain controller.
You need to view the service location (SRV) records that Server1 registers in DNS.
What should you do on Server1?
A. Open the Srv.sys file.
B. Open the Netlogon.dns file.
C. Run ipconfig /displaydns,
D. Run Get-DnsServerDiagnostics.
Correct Answer: B
Explanation
Explanation/Reference:
QUESTION NO:31
Your network contains an Active Directory forest named contoso.com.
The forest contains two domains named contoso.com and child.contoso.com and two sites named Site1
and Site2. The domains and the sites are configured as shown in following table.
When the link between Site1 and Site2 fails, users fail to log on to Site2. You need to identify what
prevents the users in Site2 from logging on to the child.contoso.com domain.
What should you identify?
A. The placement of the global catalog server
B. The placement of the infrastructure master
C. The placement of the domain naming master
D. The placement of the PDC emulator
Correct Answer: D
Explanation
Explanation/Reference:
The exhibit shows that Site2 does not have a PDC emulator. This is important because of the close
interaction between the RID operations master role and the PDC emulator role The PDC emulator
processes password changes from earlier-version clients and other domain controllers on a best-effort
basis; handles password authentication requests involving passwords that have recently changed and not
yet been replicated throughout the domain; and, by default, synchronizes time. If this domain controller
cannot connect to the PDC emulator, this domain controller cannot process authentication requests, it may
not be able to synchronize time, and password updates cannot be replicated to it.
QUESTION NO:37
You work as an administrator at ABC.com. The ABC.com network consists of a single domain
named ABC.com. All servers in the ABC.com domain, including domain controllers, have Windows
Server 2012 installed.
When you recently added new workstations to the ABC.com manually, you found that that the
computer accounts were created in the default container. You want to make sure that the default
container for newly created computers is redirected to a specified, target organizational unit (OU).
Which of the following actions should you take?
A. You should consider making use of the replace.exe command-line tool.
B. You should consider making use of the redircmp.exe command-line tool.
C. You should consider making use of the redirusr.exe command-line tool.
D. You should consider making use of the rexec.exe command-line tool.
Answer: B
Explanation:
QUESTION NO:7
You work as an administrator at ABC.com. The ABC.com network consists of a single domain
named ABC.com. All servers on the ABC.com network have Windows Server 2012 installed.
ABC.com has a server, named ABC-SR13. ABC-SR13 hosts a shared folder, named ABCShare,
which has been shared as ABCShare$.
Which of the following is TRUE with regards to sharing the folder in this manner?
A. It allows all users to view ABCShare when browsing the network.
B. It prevents users from viewing ABCShare when browsing the network.
C. It only allows ABC-SR13
QUESTION NO:39
Your network contains a server named Server1 that runs Windows Server 2012 R2.Server1 has the
Hyper-V server role installed.
Server1 hosts four virtual machines named VM1, VM2, VM3, and VM4.
Server1 is configured as shown in the following table.
You install a network monitoring application on VM2.
You need to ensure that all of the traffic sent to VM3 can be captured on VM2.
What should you configure?
A. NUMA topology
B. Resource control
C. Resource metering
D. Virtual Machine Chimney
E. The VLAN ID
F. Processor Compatibility
G. The startup order
H. Automatic Start Action
I. Integration Services
J. Port mirroring
K. Single-root I/O virtualization
Correct Answer: J
Explanation
Explanation/Reference:
Explanation:
With Hyper-V Virtual Switch port mirroring, you can select the switch ports that are monitored as well as
the switch port that receives copies of all the traffic. And since Port mirroring allows the network traffic of a
virtual machine to be monitored by copying the traffic and forwarding it to another virtual machine that is
configured for monitoring, you should configure port mirroring on VM2.
References:
http://ift.tt/1FXnOsp
QUESTION NO:27
You work as an administrator at ABC.com. The ABC.com network consists of a single domain
named ABC.com. All servers on the ABC.com network have Windows Server 2012 installed.
A server named, ABC-SR13, has a Server Core Installation of Windows Server 2012 installed.
You are instructed to convert ABC-SR13
CertBus exam braindumps are pass guaranteed. We guarantee your pass for the 70-410 exam successfully with our Microsoft materials. CertBus Installing and Configuring Windows Server 2012 exam PDF and VCE are the latest and most accurate. We have the best Microsoft in our team to make sure CertBus Installing and Configuring Windows Server 2012 exam questions and answers are the most valid. CertBus exam Installing and Configuring Windows Server 2012 exam dumps will help you to be the Microsoft specialist, clear your 70-410 exam and get the final success.
70-410 Latest questions and answers on Google Drive(100% Free Download): http://ift.tt/2qWnasR
70-410 Microsoft exam dumps (100% Pass Guaranteed) from CertBus: http://ift.tt/2qVZwwH [100% Exam Pass Guaranteed]
Why select/choose CertBus?
Millions of interested professionals can touch the destination of success in exams by certbus.com. products which would be available, affordable, updated and of really best quality to overcome the difficulties of any course outlines. Questions and Answers material is updated in highly outclass manner on regular basis and material is released periodically and is available in testing centers with whom we are maintaining our relationship to get latest material.
Brand Certbus Testking Pass4sure Actualtests Others Price $45.99 $124.99 $125.99 $189 $69.99-99.99 Up-to-Date Dumps Free 365 Days Update Real Questions Printable PDF Test Engine One Time Purchase Instant Download Unlimited Install 100% Pass Guarantee 100% Money Back Secure Payment Privacy Protection
Published by CertBus http://ift.tt/2rqUWd1
0 notes