#AND A BYTE? LIKE A COMPUTE-
Explore tagged Tumblr posts
Photo



Happy RTDLDX release day, everyone! To celebrate, have some Underworld Friends AU and their respective collectibles!
Plus, bonus Papi:

His taste in friends may be bad, but his needs are simple and he’s an absolute delight.
(I HOPE THIS GOES WITHOUT SAYING, BUT PLEASE NO-ONE PUT RTDLDX SPOILERS ON THIS POST, BTW. I HAVE NOT PLAYED THE EPILOGUE YET.)
#kirby#magolor#sectonia#haltmann kirby#max profitt haltmann#papi kirby#magolor's is obviously just based on the collectible revealed on the official twitter even if i don't know its name#then haltmann's and sectonia's are the puns of all time#GET IT? GET IT? A SHARD OF A REFLECTION? LIKE A MIRROR?#AND A BYTE? LIKE A COMPUTE-#also for the record this does not contain any spoilers for rtdldx#ive barely scratched the surface of the game#i probably got the name of magolors collectable wrong even
46 notes
·
View notes
Text
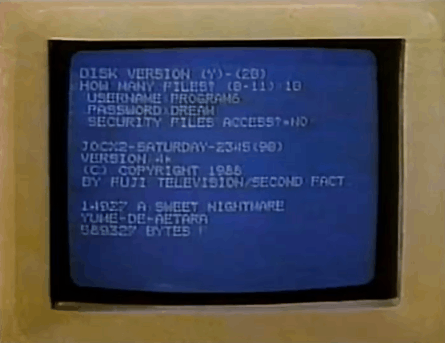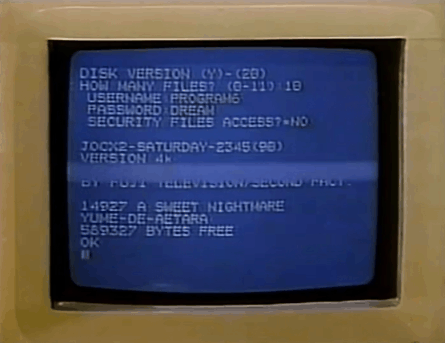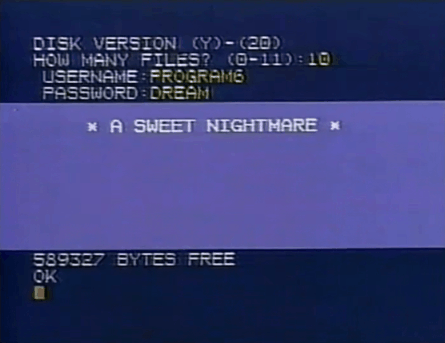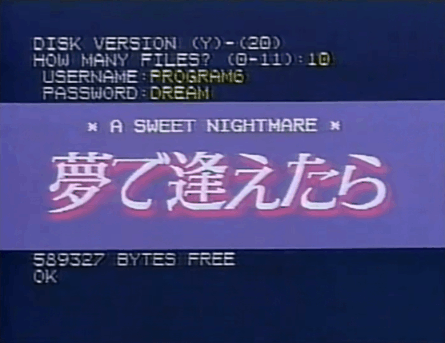
#animated gif#animated gifs#gif#gifs#old advertisements#old ads#retro#vhs#computers#80's#old tech#old computers#tech#80s#589327 bytes free#sweet nightmare#why does it just display her password like that
161 notes
·
View notes
Text


Local bat demon drives hell BATTY!!!!
#byte's bites#good omens#good omens oc#Haven't got a name yet but they work mostly through the internet!!#ADORES computer viruses they keep them on tamagotchis like they're their darling little pets#probably came into existence around like? 200 years-ish ago#give or take#They haven't been on Earth before but they saw Crowley wearing sunglasses from a distance ONCE and was like: I need a pair. NOW.#LOVES the 2010's that was their favorite decade ever#bribes their coworkers to get them human memorabilia#Also they change up their looks a lot as a little treat!!
45 notes
·
View notes
Text

This USB shit is easy (has spent the past six hours struggling to perform the pictured "RDY?" "ACK" exchange)
#I gave up on the plt-kbd for the time being#it does NOT work like how I thought it did#so I've skipped ahead to the TI-92+#my thoughts#programming#computers#calculators#still not totally sure what those 0x0C 0x10 bytes mean#more reading of documentation required methinks
2 notes
·
View notes
Text


thoughts?
#🍀#my art#dont like the pink on the sleeves so im gonna change that but#hes supposed to be like. a computer virus that infects ppls computers and tries to get ppl to love him#also hes got a little cat like thing based on a computer mouse named byte
8 notes
·
View notes
Text
He is not even 1kb in size
#a couple bytes….#everyone in that movie is soooo small#except maybe Calhoun I imagine her game is like a couple GB lmfao#vanellope too#or maybe not I have no scale for how large newer arcade games are#what would happen if somebody ripped those files though. and put them on a computer. are you like cloning the characters and then#trapping them inside a computer#you see I’ve already began to think too much about this#wreck it ralph#turbo#🐛VIRUS OFFERINGS
6 notes
·
View notes
Text
The scale of a mesh usually shouldn't affect performance. Most issues are caused usually by textures, high vertice counts, expensive shaders, etc. The scale *can* make existing issues worse tho
A misconfigured script could also be the culprit but I haven't really looked into what the issue was so 🤷♂️
Fun fact: We know the size of the Pokémon world because Scarlet and Violet has framerate issues
#this seems a bit ill-informed#in most computer graphics libraries the scale of models usually dont matter#the magnitude of the number that represents the positions of vertices are always going to be the same size#you allocate the same amount of bytes to a 3d vector point everywhere#so the time it takes to finish rendering 1 model for a frame should overall be the same#however this is not said for the number of vertices#since now you have more triangles lighting etc to compute#textures are also another factor in this#im more lenient to believe that this is caused by an expensive shader being run#or a misplaced script in the ocean that handles the physics and extends it beyond what the character needs#regardless if the ocean isnt in sight it shouldnt be computed#my takeaway is that rendering something large isnt necessarily a culprit#but rather it can be something else which is made worse by the size of a model#you can likely render a 4 vertex plane whose sides are thrice the diameter of the sun and youd be ok.
58K notes
·
View notes
Text


watched that stupid ass habbin hodtel show. fell in love with the stupid screen-faced zetto clone
#my art#self insert#↑THIS thing eats fiber optic cables 4 fun#chewing on vox rn. just personally#hazb¡n is that special kind of shitty where it compels me to like. save the good parts and remake the rest entirely#anyways. this is Byte he has every disease and could easily snap vox's brain in half but doesn't bc haha pretty computer guy♡♥︎♡♥︎
1 note
·
View note
Text
there is an academic text I've been trying to get my hands on, and I tracked down an ebook copy held by the national library, but due to legal restrictions it's only available for viewing on a library computer on their premises. like the only way I can read this research is to go to the national central library, book a computer desk, and scroll through it on a pc monitor for hours on end.
this digital copyright shit is so stupid, it makes me SO fucking mad. it costs nobody anything to let readers access this shit from home. it's a bunch of bits and bytes, the ebook file already exists. but publishers (and I include universities in this) are so brain rotten and craven that they will block any attempt to make information more accessible just in case there's a chance they'd miss out on one person with a really specific research interest paying them like £17 to look at a word document in a more comfortable chair.
24K notes
·
View notes
Text
China hacked Verizon, AT&T and Lumen using the FBI’s backdoor

On OCTOBER 23 at 7PM, I'll be in DECATUR, presenting my novel THE BEZZLE at EAGLE EYE BOOKS.

State-affiliated Chinese hackers penetrated AT&T, Verizon, Lumen and others; they entered their networks and spent months intercepting US traffic – from individuals, firms, government officials, etc – and they did it all without having to exploit any code vulnerabilities. Instead, they used the back door that the FBI requires every carrier to furnish:
https://www.wsj.com/tech/cybersecurity/u-s-wiretap-systems-targeted-in-china-linked-hack-327fc63b?st=C5ywbp&reflink=desktopwebshare_permalink
In 1994, Bill Clinton signed CALEA into law. The Communications Assistance for Law Enforcement Act requires every US telecommunications network to be designed around facilitating access to law-enforcement wiretaps. Prior to CALEA, telecoms operators were often at pains to design their networks to resist infiltration and interception. Even if a telco didn't go that far, they were at the very least indifferent to the needs of law enforcement, and attuned instead to building efficient, robust networks.
Predictably, CALEA met stiff opposition from powerful telecoms companies as it worked its way through Congress, but the Clinton administration bought them off with hundreds of millions of dollars in subsidies to acquire wiretap-facilitation technologies. Immediately, a new industry sprang into being; companies that promised to help the carriers hack themselves, punching back doors into their networks. The pioneers of this dirty business were overwhelmingly founded by ex-Israeli signals intelligence personnel, though they often poached senior American military and intelligence officials to serve as the face of their operations and liase with their former colleagues in law enforcement and intelligence.
Telcos weren't the only opponents of CALEA, of course. Security experts – those who weren't hoping to cash in on government pork, anyways – warned that there was no way to make a back door that was only useful to the "good guys" but would keep the "bad guys" out.
These experts were – then as now – dismissed as neurotic worriers who simultaneously failed to understand the need to facilitate mass surveillance in order to keep the nation safe, and who lacked appropriate faith in American ingenuity. If we can put a man on the moon, surely we can build a security system that selectively fails when a cop needs it to, but stands up to every crook, bully, corporate snoop and foreign government. In other words: "We have faith in you! NERD HARDER!"
NERD HARDER! has been the answer ever since CALEA – and related Clinton-era initiatives, like the failed Clipper Chip program, which would have put a spy chip in every computer, and, eventually, every phone and gadget:
https://en.wikipedia.org/wiki/Clipper_chip
America may have invented NERD HARDER! but plenty of other countries have taken up the cause. The all-time champion is former Australian Prime Minister Malcolm Turnbull, who, when informed that the laws of mathematics dictate that it is impossible to make an encryption scheme that only protects good secrets and not bad ones, replied, "The laws of mathematics are very commendable, but the only law that applies in Australia is the law of Australia":
https://www.zdnet.com/article/the-laws-of-australia-will-trump-the-laws-of-mathematics-turnbull/
CALEA forced a redesign of the foundational, physical layer of the internet. Thankfully, encryption at the protocol layer – in the programs we use – partially counters this deliberately introduced brittleness in the security of all our communications. CALEA can be used to intercept your communications, but mostly what an attacker gets is "metadata" ("so-and-so sent a message of X bytes to such and such") because the data is scrambled and they can't unscramble it, because cryptography actually works, unlike back doors. Of course, that's why governments in the EU, the US, the UK and all over the world are still trying to ban working encryption, insisting that the back doors they'll install will only let the good guys in:
https://pluralistic.net/2023/03/05/theyre-still-trying-to-ban-cryptography/
Any back door can be exploited by your adversaries. The Chinese sponsored hacking group know as Salt Typhoon intercepted the communications of hundreds of millions of American residents, businesses, and institutions. From that position, they could do NSA-style metadata-analysis, malware injection, and interception of unencrypted traffic. And they didn't have to hack anything, because the US government insists that all networking gear ship pre-hacked so that cops can get into it.
This isn't even the first time that CALEA back doors have been exploited by a hostile foreign power as a matter of geopolitical skullduggery. In 2004-2005, Greece's telecommunications were under mass surveillance by US spy agencies who wiretapped Greek officials, all the way up to the Prime Minister, in order to mess with the Greek Olympic bid:
https://en.wikipedia.org/wiki/Greek_wiretapping_case_2004%E2%80%9305
This is a wild story in so many ways. For one thing, CALEA isn't law in Greece! You can totally sell working, secure networking gear in Greece, and in many other countries around the world where they have not passed a stupid CALEA-style law. However the US telecoms market is so fucking huge that all the manufacturers build CALEA back doors into their gear, no matter where it's destined for. So the US has effectively exported this deliberate insecurity to the whole planet – and used it to screw around with Olympic bids, the most penny-ante bullshit imaginable.
Now Chinese-sponsored hackers with cool names like "Salt Typhoon" are traipsing around inside US telecoms infrastructure, using the back doors the FBI insisted would be safe.

Tor Books as just published two new, free LITTLE BROTHER stories: VIGILANT, about creepy surveillance in distance education; and SPILL, about oil pipelines and indigenous landback.


If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/10/07/foreseeable-outcomes/#calea

Image: Kris Duda, modified https://www.flickr.com/photos/ahorcado/5433669707/
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
#pluralistic#calea#lawful interception#backdoors#keys under doormats#cold war 2.0#foreseeable outcomes#jerry berman#greece#olympics#snowden
403 notes
·
View notes
Note
I actually know fics about this! Not about her being Domino's general though I would HAPPILY read that fic, but Jocasta Jones and the Librarian Clones turns out to have been partially inspired by this post (she ends up with a squad and they are on their way to becoming excellent librarians!!) and General Jocasta is in a similar vein where basically Obi-Wan gets put in charge of organizing the war and goes to the people who spend their lives organizing things aka the librarians for help (this one is complete!). So on the off-chance there's librarians/archivists/museum folks who like Star Wars following me, check them out they're fun!
But in terms of Domino Squad becoming Librarians/Archivists/their favorite assistants:
The Commanders have a Chat populate SOLELY by Commanders and the Captains they invite in and it is as secure as they can make it. Which is pretty damn secure.
And they're well into an informational conversation read gossip session about their latest Jedi shenanigans.
Cody: I found Obi-Wan stress baking. It wouldn't be that wierd if I knew where he got the ingreditates we haven't gone shopping in months?
Bly: that's nothing General Kolar joined us a few days ago and he and Aalya have been competeing over who can flip the most tanks in a battle
Rex: Hah that's nothing!
CT-1409: it really is.
Wolffe: whom the fuck?
CT-1409: It was Crafts' Day yesterday. 25 Jedi cadets who are still working on their Force levetating.
Rex: Who are you and how did you get into this chat?
CT-1409: With paint. Apparently glitter has been banned from the Archives for the past 147 years due to The Glitter Incident, its use by jedi cadets is restricted to particular rooms in the temple. It was wonderful. It was also Very Messy.
COdy: Rex, Keelie, who is this?
Rex: You think all CTs know each other Commander? Really??
CT-1409: Truely sir
Fox: Echo.
CT-1409: yes sir!
Fox: Echo what are you doing in our chat?
CT-1409: SIr Sargent Byte said I should work on the offensive side of cyber security sir.
Wolffe: Fox who the fuck is this
Fox: hush. So you decided to do this?
CT1409: I have been told to hush sir
Fox: Do I need to come over there you little shit?
CT-1409: Commander Thorn dared me sir.
Fox: I'm beginning to understand why Byte laughed when someone said you're the one with impulse control
CT-1409: That would be Cutup and Hevy sir
Fox: guys this is Echo. He's part of Domino squad they got assigned to the archives a while back, we've run into each other a couple times
Bly: and you decided, on a dare, to hack into our hyper-secured chat to test your slicing skills
CT-2010: He did sir
several people are typing...
What if Shaak Ti, in stopping the Kaminoans from decommissioning clones, asks around if anybody has place and purpose for some non-combatant clones. And Jocasta Nu goes "A bunch of keen young men with eidetic memories? Don't mind if I do" and that is how the Jedi temple library has the most amazing librarians in the galaxy
Okay but -
Domino fails their final test, but Shaak manages to stop them from being decommissioned or sent to work sanitation by roping Jocasta into snatching them up for that reason. All the members of Domino kind of collectively groan and complain but ship out anyway, and they’re pretty sure it’s all going to be this terrible, boring slog through ancient books with some stuffy librarian Jedi -
Right up until Jocasta gets word of a cache of Jedi holocrons on a frontline planet, packs up her five new assistants and her lightsaber, and leads them on the most greuling, dangerous, ridiculous mission through active battlefields and Separatist camps that absolutely no one believes happened when they tell their vode later. Which is absolutely fine, because Domino now knows they have the most badass general in the whole galaxy, bar none.
#libraries and archives have a lot of tech needs#so if any of the dominos happen to be good with tech or cyber security they will be the librarians new favorite people#doubly so if they spend time after the war designing user friendly systems for LAMs#lets say it's echo and droidbait that do this#fives specializes in wrangling the kids becasue he has the same amount of energy and he can do the funny voices in story time#cutup makes kids laugh and also helps wrangle them he's good at explaining to baby jedi why they need to be careful#levitating stuff around the shelves with their sharp corners and the fragile computer screens#meanwhile hevy's eyeball deep in the kind of monotonous labeling/detail work people fob off on you#when you're either the assistant or good with details just cause he likes the nitty gritty stuff#all of them work the front desk and shelving and extra help with kids/research/finding stuff whenever needed#they are not allowed to do exhibits yet#they're still trying to figure out how to do on-combat displays and reports and exhibits don't work if you write like its a report#the Corries knows them cause either they've run into the Corries escorting younglings places or checking out coruscant#or a couple have gone to the temple for some reason or other at some point#not sure how Fox specifically knows them yet but he assigned Byte to help them work on software stuff#he knows them enough to know they're little chits and consideres them crazy enough to manage baby jedi#he's keeping them away from quinaln he fears the chaos and doesn't want them stealing his jedi#clone wars#domino squad#domino squad lives#jocasta nu#jedi archives#jedi#clone troopers#jedi librarians and archivists#clone commanders#arc trooper echo#arc trooper fives#clone trooper hevy#clone trooper droidbait
4K notes
·
View notes
Note
Strange question, but I'm curious. Do you have a least favourite computer?
Ohhhh, good one. I'm going to make some enemies for these, I'm sure.
Least favorite vintage computer:
Apple I
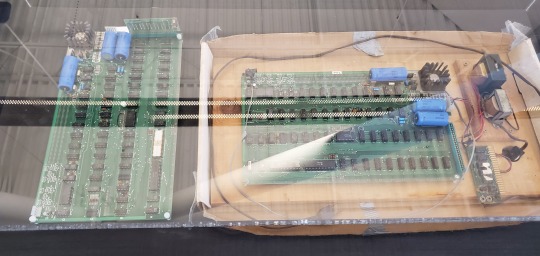
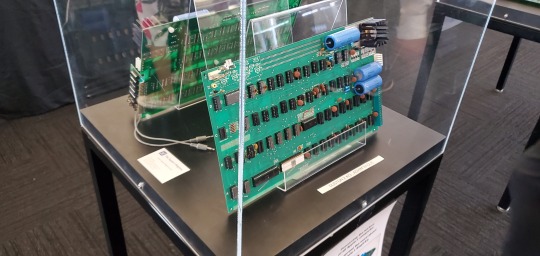

Not for any technical reasons, or anything about its history. I happen to like and respect Steve Wozniak, and everything he did in the service of computing in the 1970s. His ROM monitor known as WOZMON is only 256 bytes so it can fit into a first generation 1702A EPROM, which is damned impressive. I use the newer EWOZMON regular basis on other 6502 machines.
The Apple I exemplifies a computer that no longer exists as a computer. Rather, it's become the legendary trading card for the ultrawealthy techbro types who seek to commodify the history of the home computer revolution that they didn't bother to study. It's been reduced to no more than a static display piece, and a cornerstone of revisionist history, ignoring the larger picture.
An Apple I is considered too monetarily valuable to risk applying power to or fixing, "gotta leave it original!" with failed, leaky capacitors, doing nothing. Well if you can't use it, it ceases to be a computer because it isn't computing anything. They had almost a dozen of them at VCF West XIV, most of which were under plexiglass with a hired guard to keep an eye on them because the high price they fetch. Only one was powered up at a time under the watchful gaze of experts, handling things with museum gloves. Unlike other exhibits, these were not available to be touched or interacted with (which defeats the whole reason people enjoy vintage computer festivals).
Assuming you look beyond the hype, and get your hands on a working Apple I? It turns out to be quite underpowered and limited -- which makes sense, Woz was optimizing the shit outta his part count and budget! I wish I had his skills. It was a major technical achievement to get it to do that much with so little. It's a TV Typewriter (RIP Don Lancaster) bolted to a minimal 6502. If i had one at my disposal in the 1970s, I'd probably do like the contemporary hackers did and modify it as my budget and skills allowed. But it's 2024 and an Apple I -- you aren't allowed to do that. No, if I had an Apple I, I could sell it and buy a house with that money.
If it weren't for all that, I think I'd probably just be indifferent to it, or maybe even like it for what it is.
Least favorite general computer:
eMachines eTower 600is

What a piece of shit. I had one when it was new, running Windows ME and it was hot garbage. I could not stand this underpowered excuse for a computer after a few months when the new computer sheen wore off. Floppy drive died too soon. Didn't come with the advertised 64MB of RAM (who puts 33MB of RAM in a computer?). Hard drive was only 10GB, kept filling it up. It was filled with bloatware, the keyboard was cheap garbage. I don't begrudge my parents for buying it, they didn't know any better and I was too young to have any say in the matter. That said, it endured the shortest tenure of any computer in my house to date.
Never obsolete my ass.
605 notes
·
View notes
Text
The Girl in IT - Masterlist (Under Rework!)
A Boss! Joel Miller x IT Specialist F! Reader AU

Click here for The LIST
Series Rating: E (18+, MDNI)
Series Summary: When an IT specialist who feels behind in life stumbles upon a sexual bucket list on her boss's computer one night, what will she do once she finds out that it was written about her?
Series Warnings & Tags: No Outbreak! Joel Miller, Smut, Joel's Sexual Bucket List, Boss x Employee Relationship, Virgin Reader, All the Fluff, All of the Yearning, Mishaps, Awkward Sex, a small-ish Age Gap, Joel is a Forward and Healthy Communicator, Roleplay, Meddling Millers, Tess is a Boss, Sugar Daddy Lite, Daddy Kink, Smut, SO MUCH SMUT, Age Gap, Overstimulation, Squirting, Older Man/Younger woman, So much dirty talk, DD/lg (kinda? they're both into it), Virgin Reader, Loss of Virginity, PIV Sex (finally!!!!), Breeding Kink, Breeding kink, More tags to be added as series progresses
Chapter List:
The Night Shift - 5.6K
Off to the Races - 3.6K
Vroom Vroom - 6K
Gooey - 6.4K
Pony - 3.5K
The Adults are Talking - 5.3K / Deleted Scene - Sweet Revenge - 1.3K
The All Hands Meeting - 4.4K
The Panic! in the Breakroom (Christine's Version) - 8.2K
Fools Rush In - 3.9K (Undergoing Rework)
Looks Like We Made It - 4.1K (Undergoing Rework)
Love, Joel - From Joel's Eyes
The Tornado Watch - 2K
Who Wants to be a Millionaire? - Coming Soon!
To Build a Home
IT Ticket - Byte-Sized Microfics / Drabbles (1K words or less):
Print Job
I Fell
Moodboards:
Frank's Wedding Pinterest Board for Joel & Sugar, Honolulu, Hawaii 2024
I would choose you in every lifetime.
The Girl in IT Vibes
Behind The Scenes & Extras!
Behind the Music!
Joel's Headcanons!
Sugar's Headcanons!
Minor Character Headcanons!
NSFW Alphabet (18+)
Sugar's Style! - After Joel's Neiman Marcus Birthday Spree!
Joel and Sugar Fanart! - by the lovely @desuidesu
The Girl in IT meets The Office - Fanart by the lovely @babyispunk
Recreated Slack Visuals - Fanart by the lovely @babyispunk
Meet Cute NYC - 1.3K (A glimpse at the future!)
#pedro pascal#joel miller fanfiction#joel miller x you#joel miller#joel miller x reader#pedro pascal fanfiction#joel miller x female reader#joel miller fanfic#joel miller smut#joel the last of us#joel tlou#joel miller imagine#joel miller fic#the last of us fic#the last of us fanfic#the last of us#pedro pascal characters#pedro pascal fandom#pedro pascal characters fanfiction#joel miller tlou#tlou fanfiction#the last of us hbo#tlou hbo#tlou
905 notes
·
View notes
Text

♬♪ .. living,retro computer id pack﹙for anonymous ﹚♯ predominantly androgynous.

names ⇢ lovebytes,calware,malakai,halware,atari,AM,wheatley,chip,malwaria,micah,mickey,hal,zip,zap,tessa,tecca,emoticon﹙emoticonnie﹚,bailey,sean,cursor,pascal,cache,java﹙javascript﹚,data,click﹙clicky,clickie,clicker﹚,myspace,wirehead,whirr,solitaire,paige,peyton﹙payton﹚,electronica,talia﹙digitalia﹚,fax,circe,programatha,juno,will
pronouns ⇢ it its,bit byte,beep boop,click clack,key keys keyboard,whirr whirrs,pix pixel pixelated,CPU CPUs,compute computer,route router,win windows,sentient sentience,wire wires wired,err error,pro program programmed,soft software,hard hardware,cir circuit circuitboard,click scroll,404 404s,404 page not found,^_^ ^_^s,:-) :-D,o_o >_>,🔌 🔌s,💻 💻s,🖥 🖥s,⌨ ⌨s,🖱 🖱s,💽 💽s,💾 💾s,💿 💿s,📀 📀s,🔇 🔊
titles ⇢ the man﹙woman,girl,boy,gal,guy,being,thing﹚in the machine,the one behind your screen﹙The one behind your LCD screen﹚,_ who is running on flash﹙can be replaced with any software﹚,_ technological form,_ wires,__ with a circuitboard in place of _ brain,ms. paint,__ plugged into the wall,your mechanical﹙technological,electronic﹚best friend
ids ⇢ Aiwarix,Vietechxic,Digitalbeing,Technobodiment,8bitgender,Technoperspeque,Girlvirtual,Nonbinaryvirtual,Boyvirtual,Virualors,Oldcomputic,Win10gender,Byteic,Aithing,Dynirusic,Digirealgender
users ⇢ Lovebytez,﹙name﹚-﹙4-digit number﹚,0100000101001101,7653r70¹,hi-040405,computers-cant-byte,machinery-and-me,35784m5¹,circuitboard4brains,malwaria,b-i-n-a-r-y,c-i-r-c-u-i-t,https-﹙name﹚-dot-com,thinking-in-1s-and-0s,1s-and-0s-and-1s,benevolentware,wifiwifey,pluginbestfriend,pluginplaything
¹ Combining random numbers and letters can be used to make more usernames like this.

#✦ ˓ whiskey .#⤷ on the rocks.#id pack#npt#npt pack#npt ideas#npt list#npts#npt suggestions#nputs#nput
832 notes
·
View notes
Text
Byte. He’s a sentient virus that eats viruses on old computers in a dingy computer lab. Kinda like an antivirus but more annoying and will download more viruses onto said computer just for shits and giggles.
694 notes
·
View notes
Text
How to Buy a Computer for Cheaper
Buy refurbished. And I'm going to show you how, and, in general, how to buy a better computer than you currently have. I'm fairly tech-knowledgeable, but not an expert. But this is how I've bought my last three computers for personal use and business (graphics). I'm writing this for people who barely know computers. If you have a techie friend or family member, having them help can do a lot for the stress of buying a new computer.
There are three numbers you want to know from your current computer: hard drive size, RAM, and processor speed (slightly less important, unless you're doing gaming or 3d rendering or something else like that)
We're going to assume you use Windows, because if you use Apple I can't help, sorry.
First is hard drive. This is how much space you have to put files. This is in bytes. These days all hard drives are in gigabytes or terabytes (1000 gigabytes = 1 terabyte). To get your hard drive size, open Windows Explorer, go to This PC (or My Computer if you have a really old OS).
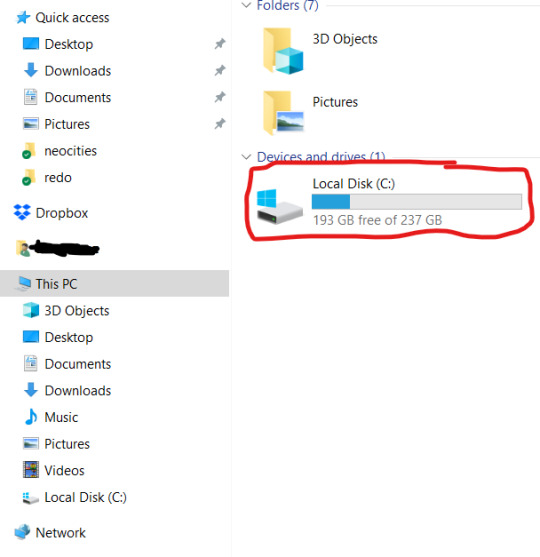
To get more details, you can right-click on the drive. and open Properties. But now you know your hard drive size, 237 GB in this case. (this is rather small, but that's okay for this laptop). If you're planning on storing a lot of videos, big photos, have a lot of applications, etc, you want MINIMUM 500 GB. You can always have external drives as well.
While you've got this open, right-click on This PC (or My Computer). This'll give you a lot of information that can be useful if you're trying to get tech support.
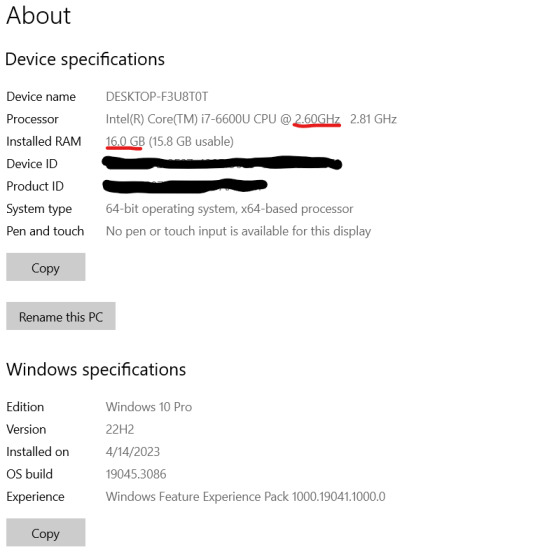
I've underlined in red the two key things. Processor: it can help to know the whole bit (or at least the Intel i# bit) just so you don't buy one that's a bunch older, but processor models are confusing and beyond me. The absolutely important bit is the speed, in gigahertz (GHz). Bigger is faster. The processor speed is how fast your computer can run. In this case the processor is 2.60 GHz, which is just fine for most things.
The other bit is RAM. This is "random-access memory" aka memory, which is easy to confuse for, like how much space you have. No. RAM is basically how fast your computer can open stuff. This laptop has 16 GB RAM. Make sure you note that this is the RAM, because it and the hard drive use the same units.
If you're mostly writing, use spreadsheets, watching streaming, or doing light graphics work 16 GB is fine. If you have a lot of things open at a time or gaming or doing 3d modeling or digital art, get at least 32 GB or it's gonna lag a lot.
In general, if you find your current laptop slow, you want a new one with more RAM and a processor that's at least slightly faster. If you're getting a new computer to use new software, look at the system requirements and exceed them.
I'll show you an example of that. Let's say I wanted to start doing digital art on this computer, using ClipStudio Paint. Generally the easiest way to find the requirements is to search for 'program name system' in your search engine of choice. You can click around their website if you want, but just searching is a lot faster.
That gives me this page
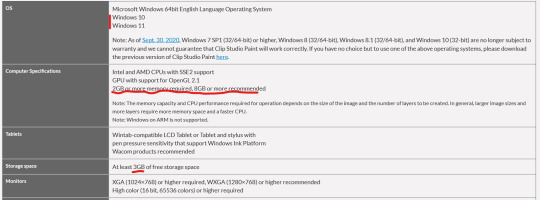
(Clip Studio does not have very heavy requirements).
Under Computer Specs it tells you the processor types and your RAM requirements. You're basically going to be good for the processor, no matter what. That 2 GB minimum of memory is, again, the RAM.
Storage space is how much space on your hard drive it needs.
Actually for comparison, let's look at the current Photoshop requirements.
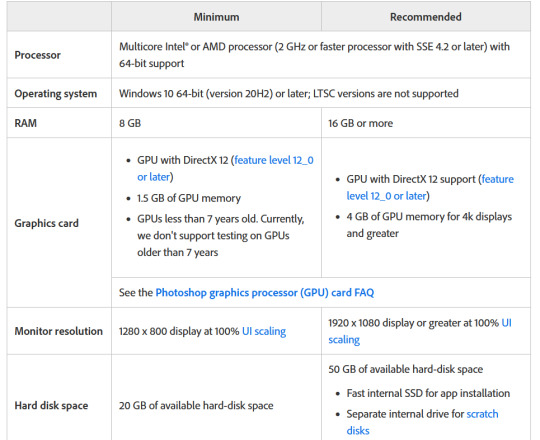
Photoshop wants LOTS of speed and space, greedy bastard that it is. (The Graphics card bit is somewhat beyond my expertise, sorry)
But now you have your three numbers: hard drive space, RAM (memory) and processor (CPU). Now we're going to find a computer that's better and cheaper than buying new!
We're going to buy ~refurbished~
A refurbished computer is one that was used and then returned and fixed up to sell again. It may have wear on the keyboard or case, but everything inside (aside from the battery) should be like new. (The battery may hold less charge.) A good dealer will note condition. And refurbished means any flaws in the hardware will be fixed. They have gone through individual quality control that new products don't usually.
I've bought four computers refurbished and only had one dud (Windows kept crashing during set-up). The dud has been returned and we're waiting for the new one.
You can buy refurbished computers from the manufacturers (Lenovo, Dell, Apple, etc) or from online computer stores (Best Buy and my favorite Newegg). You want to buy from a reputable store because they'll have warranties offered and a good return policy.
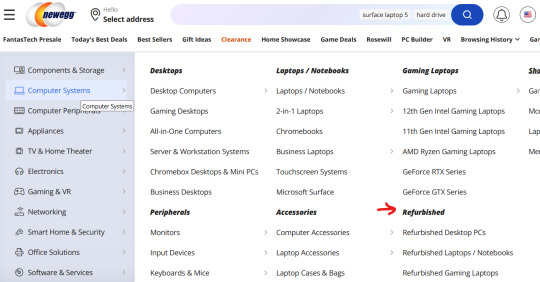
I'm going to show you how to find a refurbished computer on Newegg.
You're going to go to Newegg.com, you're gonna go to computer systems in their menu, and you're gonna find refurbished
Then, down the side there's a ton of checkboxes where you can select your specifications. If there's a brand you prefer, select that (I like Lenovos A LOT - they last a long time and have very few problems, in my experience. Yes, this is a recommendation).
Put in your memory (RAM), put in your hard drive, put in your CPU speed (processor), and any other preferences like monitor size or which version of Windows you want (I don't want Windows 11 any time soon). I generally just do RAM and hard drive and manually check the CPU, but that's a personal preference. Then hit apply and it'll filter down.
I'm going to say right now, if you are getting a laptop and you can afford to get a SSD, do it. SSD is a solid-state drive, vs a normal hard drive (HDD, hard disk-drive). They're less prone to breaking down and they're faster. But they're also more expensive.
Anyway, we have our filtered list of possible laptops. Now what?
Well, now comes the annoying part. Every model of computer can be different - it can have a better or worse display, it can have a crappy keyboard, or whatever. So you find a computer that looks okay, and you then look for reviews.
Here's our first row of results
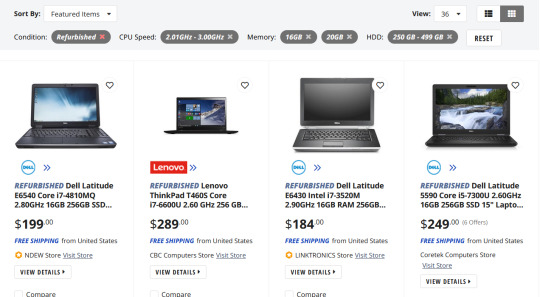
Let's take a look at the Lenovo, because I like Lenovos and I loathe Dells (they're... fine...). That Thinkpad T460S is the part to Google (search for 'Lenovo Thinkpad T460s reviews'). Good websites that I trust include PCMag, LaptopMag.com, and Notebookcheck.com (which is VERY techie about displays). But every reviewer will probably be getting one with different specs than the thing you're looking at.
Here are key things that will be the same across all of them: keyboard (is it comfortable, etc), battery life, how good is the trackpad/nub mouse (nub mice are immensely superior to trackpads imho), weight, how many and what kind of ports does it have (for USB, an external monitor, etc). Monitors can vary depending on the specs, so you'll have to compare those. Mostly you're making sure it doesn't completely suck.
Let's go back to Newegg and look at the specs of that Lenovo. Newegg makes it easy, with tabs for whatever the seller wants to say, the specs, reviews, and Q&A (which is usually empty).
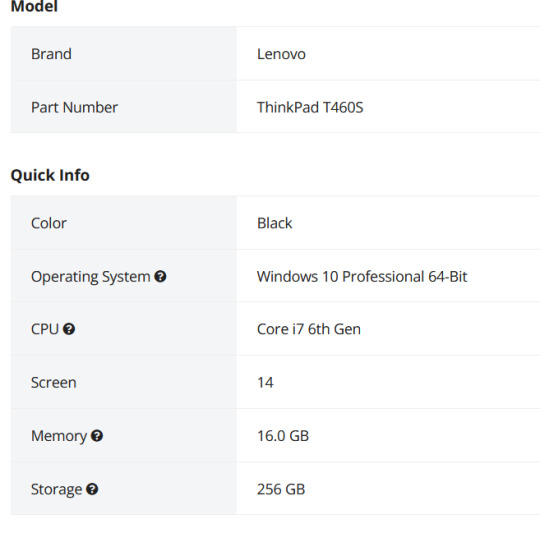
This is the start of the specs. This is actually a lesser model than the laptop we were getting the specs for. It's okay. What I don't like is that the seller gives very little other info, for example on condition. Here's a Dell with much better information - condition and warranty info.
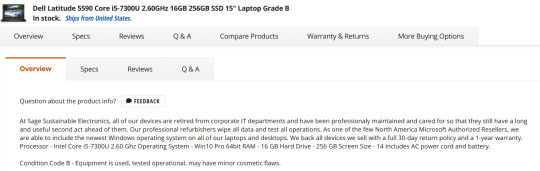
One thing you'll want to do on Newegg is check the seller's reviews. Like on eBay or Etsy, you have to use some judgement. If you worry about that, going to the manufacturer's online outlet in a safer bet, but you won't quite get as good of deals. But they're still pretty damn good as this random computer on Lenovo's outlet shows.
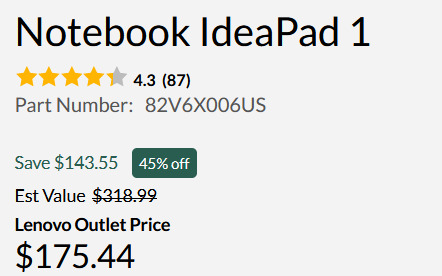
Okay, so I think I've covered everything. I do recommend having a techie friend either help or double check things if you're not especially techie. But this can save you hundreds of dollars or allow you to get a better computer than you were thinking.
992 notes
·
View notes