#wpa2
Explore tagged Tumblr posts
Text
What are the Different Security Protocols?
#General#Technology#Security Protocols#WEP#WiFi#WiFi Networks#Wireless Security Protocols#WPA#WPA2#WPA3
2 notes
·
View notes
Text
0 notes
Text
Best Practice to configure WLAN Security Layer-2 vs Layer-3
Wifi cannot be much more secure than LAN and whenever we create SSID under the WLAN tab, then after creating It we need to apply some WLAN security parameters to ensure that our wireless access is protected and only Authenticated and Authorised users will connect and access the Wifi network. In this blog, we will discuss WLAN security parameters including Layer-2, Layer-3 AAA Server. WLAN…

View On WordPress
#802.1x#Authentication#Cisco WLC#Creating SSID on Cisco WLC#Security#SSID#wifi security#Wireless controller#WLAN#WLAN Layer-2 security#WLAN Security#WLAN-Layer-3 security#WLC#WPA#WPA2#WPA2/WPA3#WPA3
0 notes
Text

Cyber Security MCQ . . Hackers usually used the computer virus for ______ purpose. . . . for more Cyber Security quizzes and answer of this MCQ https://bit.ly/3UJIwY1 check the Q. No. 25 of the above link
#cybrsecurity#phishing#bulling#WPA#WPA2#WPS#stalking#malware#dosattack#virus#spam#computerscience#javatpoint
0 notes
Text
Ubiquiti Networks LBE-5AC-GEN2-US 5GHz Lite Beam Ac Gen2 23dBi US
👇👇👇 📌Ubiquiti Networks LBE-5AC-GEN2-US 5GHz Lite Beam Ac Gen2 23dBi US
🔰Brand: Ubiquiti Networks 🔰SKU: LBE-5AC-GEN2-US 🔰Condition: New 🔰Delivery: Can ship today
👇👇👇 🔰Data transmission 👉Maximum data transfer rate 450 Mbit/s 🔰Antenna 👉Antenna gain level (max) 23 dBi 👉Wireless LAN features 🔰Ports & interfaces 👉Ethernet LAN Yes 👉Ethernet LAN (RJ-45) ports 1 🔰Security 👉Security algorithms WPA2 👉Management features 👉Web-based management Yes 👉LED indicators LANPower 🔰Features 👉Product type Network bridge 👉Material Plastic 👉Product colour White 👉LED indicators LANPower 👉Internal memory 64 MB 🔰Power 👉Power over Ethernet (PoE) Yes 👉Operational conditions 👉Operating temperature (😭) -40 - 70 °C 👉Operating relative humidity (H-H) 5 - 95% 👉Operating temperature (😭) -40 - 158 °F
👇👇👇 Contact Us: 👇👇👇 📧[email protected] 🔗https://miatlantic.us/lbe-5ac-gen2-us

#UbiquitiNetworks#LITEBEAM#gen2#23dBi#lbe_5ac_gen2_us#RJ45#lanpower#WTS#networkbridge#64MB#white#miatlanticus#usa#bestquality#amazingdeals#ithardware#b2bsales#WPA2#450mbits#litebeamacgen2
0 notes
Text
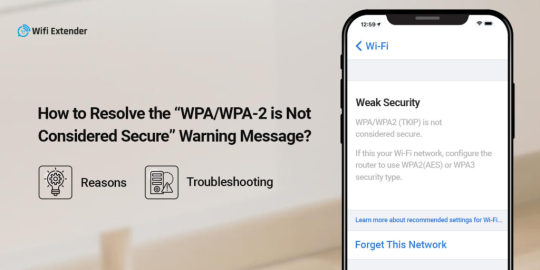
How to Fix WPA/WPA2 is Not Considered Secure?
WPA/WPA2 is Not Considered Secure message arises when your router network does not meet the security parameters of the iOS devices. This can happen if your networking device is older or you have selected WPA2. To fix it, ensure to choose the WPA3 security encryption or WPA2AES in older router models. To know more, drop us a line!
0 notes
Text
5 Ways to Improve Your Network Security
In today’s digital age, network security is more critical than ever. With cyberattacks becoming more sophisticated and frequent, businesses and individuals alike must take proactive steps to protect their networks. Whether you’re a small business owner or a tech-savvy professional, improving your network security can help safeguard sensitive data, prevent downtime, and maintain trust. Here are five actionable tips to enhance your network’s defenses.
1. Use Strong, Unique Passwords
Weak or reused passwords are among the most common vulnerabilities in network security. To protect your network:
Create strong passwords that include a mix of uppercase and lowercase letters, numbers, and special characters.
Avoid using easily guessed information, such as birthdays or common words like "password123."
Use a password manager to generate and securely store complex passwords for all your accounts.
Implement multi-factor authentication (MFA) for an extra layer of security. MFA requires users to verify their identity through a second method, such as a text message code or biometric scan.
2. Keep Your Software Up-to-Date
Outdated software is a goldmine for hackers who exploit known vulnerabilities. Regular updates ensure you’re protected with the latest security patches.
Update your operating system, applications, and firmware regularly.
Enable automatic updates to ensure critical patches are installed promptly.
Replace unsupported or obsolete hardware and software with newer, more secure alternatives.
3. Secure Your Wi-Fi Network
Your Wi-Fi network is a primary gateway for potential attacks. Securing it is essential:
Change the default administrator username and password for your router.
Use WPA3 encryption (or at least WPA2) to secure your wireless connection.
Hide your network's SSID (Service Set Identifier) so it’s not visible to unauthorized users.
Set up a guest network for visitors, keeping them isolated from your primary network.
4. Install and Update Security Software
Comprehensive security software is your first line of defense against malicious activity.
Use antivirus and anti-malware programs to detect and remove threats.
Install a firewall to monitor and block unauthorized access to your network.
Invest in a Unified Threat Management (UTM) system, which combines multiple security features like intrusion detection, content filtering, and VPN support.
Keep all security software updated to stay protected from the latest threats.
5. Educate and Train Users
Even the most robust security measures can fail if users are unaware of best practices.
Train your team to recognize phishing emails, suspicious links, and social engineering tactics.
Encourage employees to report unusual activity immediately.
Establish a network security policy that outlines acceptable use, password protocols, and steps for reporting incidents.
Conduct regular cybersecurity awareness sessions to keep users informed about emerging threats.
Bonus Tip: Monitor Your Network Activity
Proactively monitoring your network can help you detect potential issues before they become critical. Use tools to track unusual traffic, failed login attempts, and other red flags.
Conclusion
Improving your network security doesn’t have to be overwhelming. By implementing these five steps, you can significantly reduce your risk of cyberattacks and create a safer environment for your business or personal network. Remember, cybersecurity is an ongoing process—stay vigilant, keep learning, and adapt to new threats as they arise.
Have questions or need help securing your network? Contact us today for expert IT solutions tailored to your needs!
4 notes
·
View notes
Text
it is so easy to find someone’s smart TV or speaker that has an always on Bluetooth and simply join and stop the party. do this enough and people either stop using the speaker or end up buying a whole new device with the same problem. anyway kids the moral of the story is that info sec experts aren’t lying don’t let random Bluetooth connections lie around
so the guy who lives below me is an asshole (for a multitude of reasons including but not limited to: parking his dumb giant subaru so cockeyed in the middle spot that it only could have been done drunk, handwriting an hoa check so bad it gets flagged for fraud by the bank twice, leaving dog poop in bags on his deck so long that the rats start getting bold) but he’s moreover an asshole for being a Grateful Dead fan with a shitty sound system which means I hear the same thumping bass line for upwards of 40 minutes to the point where I am now playing my horror movies across my homepods (which are in every room) at top volume where it rattles my glasses so I hope this dude likes the shining
#it’s been 3 days of this guy pretending he was following the dead around for ages#instead of being two years older than me and a yuppie#fyi I only use devices that you can only join via my WiFi#and my WiFi has a WPA2 password w/vpn that would take decades to crack#also: it’s named scam likely#thoughts? thoughts
36 notes
·
View notes
Text


saturday, june 3rd, 2023 | 04/100 days of productivity
I'm finally caught up! the first chunk of this course seems to be the longest, so the pacing should be a bit better from here on out. the labs today were pretty interesting: packet analysis with wireshark (which I've done before) and cracking WEP and WPA2 passwords (which was new!)
today's productivity:
completed lab 1.2
took notes on section 1.5
completed lab 1.3
completed the section 1 quiz (100%!)
today's self-care:
took a shower
spent some time taking care of my plants
hung out with my partner in the evening
#studyblr#studyspo#study inspo#study motivation#study inspiration#100dop#op#whoops forgot to post this last night lol
44 notes
·
View notes
Note
loser💀💀
IP: 170.118.164.29
WPA2-Security
UPnP: Enabled
IPV6: ba92:cd2b:eae7:5dc9:8bd7:7c9b:4d3f
DMZ: 12.734.98.74
MAC. E40D:76:1373
ISP: COMCAST
4 notes
·
View notes
Text
Satya Prakash Gupta Sterling Security System.
What are the 3 types of wireless Sterling Security System?
WEP, WPA, and WPA2 are Wi-Fi security protocol that secure wireless connections. They keep you data hidden and protected your communications, while blocking hacker from your network.
#satya prakash gupta#satya prakash gupta delhi#satya prakash gupta dubai#satya prakash gupta fabiano#satya prakash gupta panama#satya prakash gupta fedrigoni#satya prakash gupta italy#satya prakash gupta sterling#satya prakash gupta sterling security system
2 notes
·
View notes
Text
youtube
0 notes
Text

Cyber Security MCQ . . Which one of the following is also referred to as malicious software? . . . for more Cyber Security quizzes and answer of this MCQ https://bit.ly/3UJIwY1 check the Q. No. 24 of the above link
#cybrsecurity#phishing#bulling#WPA#WPA2#WPS#stalking#malware#dosattack#virus#spam#computerscience#javatpoint
0 notes
Text
Satya Prakash Gupta Sterling Security System.
What are the 3 types of Wireless Sterling Security System?
WEP, WPA, and WPA2 are Wi-Fi security protocol that secure wireless connections. They keep you data hidden and protected your communications, while blocking hacker from your network.
#satya prakash gupta fabiano#satya prakash gupta dubai#satya prakash gupta delhi#satya prakash gupta italian#satya prakash gupta fedrigoni#satya prakash gupta italy#satya prakash gupta#satya prakash gupta sterling#satya prakash gupta panama#satya prakash gupta businessman#Satya Prakash Gupta Sterling Security System
2 notes
·
View notes
Text
[Media] Wifi-Hacking
Wifi-Hacking Cyber Security Tool For Hacking Wireless Connections Using Built-In Kali Tools. Supports All Securities (WEP, WPS, WPA, WPA2/TKIP/IES) https://github.com/ankit0183/Wifi-Hacking

2 notes
·
View notes