#which is then undermined by the cost and the new entry level expectation of a degree
Explore tagged Tumblr posts
Text
I absolutely think you're right that vocational training has become less common (to the extent where certain trades are in high demand because there are so few trained in them) and there has been this major push toward university education. University has been framed as essential for economic and social mobility, and has acted as a legitimate barrier for advancement for a lot of people, which is an issue. A person shouldn't need to go to university to have autonomy, respect, and mobility at their job. And like you said -- a lot of jobs ask for a degree that really don't need one and don't make sense to require one, which is compounding the issue.
I definitely see it in Australia, and in Canada (but less where I was from, admittedly, which had a greater trades focus than most places), this push for everyone to get a university education, regardless of whether that really makes sense for their wants and circumstances or the job requirements. And I've seen it put a lot of pressure on universities themselves to teach vocational skills and act more like job training than universities are largely equipped to. It's a weird predicament and it does mean you get a ton of students who are in school because they have to be, not because they have a strong intrinsic motivation.
And while I think education is great and having an educated population is a good thing, it sort of simultaneously means that the education they're getting isn't maybe what they were seeking or won't give them the hard skills they need, and yet isn't necessarily translating to the actual development of soft skills like critical thinking and communication etc, not as much as a university education was in theory designed to promise.
The way I often describe it is that in a fair society, everyone should have an opportunity to go to university and it should be free/inexpensive to do so, but no one should feel obligated to in order to have a decent life.
I've taught the same couple classes for a few years, and each term the percent/volume of questions about the assignments has gone up, based on the same (or more!) starting info in the outlines and rubrics. Students are so focused on getting The Right Answer and doing things Right that they don't trust their own judgement and ask a ton of questions to make sure they're doing things right or want an excruciating level of detail.
And honestly? It's exhausting and a little frustrating.
I want students to succeed and feel confident in themselves, but I also don't want to be holding the hand of whole ass adults and telling them which specific passages in the textbook are the most critical to focus on and that yes they're on the right track with that analysis or that it's fine to interpret as they've done or that yes when we say apply the concepts from class those are the concepts we mean and yes when we say make a critical judgment we do expect you to apply critical thinking and evidence and that's exactly what it says in the assignment outline and -
I know it comes from a place of anxiety and it's how they're trained so I don't put this frustration back on the student but as an educator, it feels like a certain amount of bullshit to be teaching graduate level classes with the same degree of hand holding I would have sought as a student in *maybe* my first term of uni but realistically only sought early to midway through high school, if that.
The kids (and many of the adults) aren't all right, y'all. And the burn out and burden this places on everyone else in the system is just as much of a problem.
#i genuinely feel like post secondary education is in this growing pain / transition / existential crisis#promulgated by the corporatization if education and by capitalism#and by propping education up as a class barrier and using it as a promsie of upward social mobility#which is then undermined by the cost and the new entry level expectation of a degree#you need a degree to do basic data entry yet meanwhile most tech companies don't ask for one bc your skills (not studies) are your asset#anyway i have a lot of thoughts about where these issues are from and how they're spiralling still#but tbh i would honestly love to see a stronger return and emphasis to vocational schools and training#i think it suits so many learners and is so societally undervalued#but i digress#phyn rambles#education systems#thank queue for coming
21 notes
·
View notes
Text
Ninth House, Leigh Bardugo

Rating: Mixed Review Genre: Fantasy, Mystery, Dark Academia Representation: -Bi/pan protagonist -Jewish protagonist -Latina mixed race protagonist Trigger warnings: Sexual assault (in scene), rape (in scene), CSA (in scene), graphic violence, murder, drug use, drug abuse, drugging of another person, overdose, domestic abuse, medical abuse, violence by dogs Note: Not YA
Why is it that every time I read Leigh Bardugo, I love the book with a passion...except for one thing that makes me want to tear my hair out?
Here’s what seriously impressed me about Ninth House, Bardugo’s entry into New Adult. The pacing was phenomenal. The measured, perfectly timed revelations of information had me finding excuses to listen to the audiobook - taking extra neighborhood walks, doing extra loads of laundry - because I was so hooked. Then, there’s the worldbuilding. Bardugo managed to walk a delicate line, successfully suspending disbelief while still asserting that eight Yale secret societies do secret magic rituals to the benefit of the oligarchical capitalist machine (we all kind of suspected this was the case, right?). But the best part of the book, the part that had me recommending Ninth House in more than one group chat, was, of all things, the point-of-view jumps.
Rarely are point-of-view switches the star of the show, but I was so excited to see a genuinely original, intrinsic-to-the-heart-of-the-whole-novel use of that technical tool. The point of view jumps crank the volume up on the theme of the whole book. We start with the main character, Galaxy “Alex” Stern; she is the point-of-view character for the present semester during which the principal action of the novel takes place. Her upperclassman and mentor Daniel Arlington (or “Darlington”) is the point-of-view character for the semester before - all because something happened to Darlington. Alex is telling people he’s doing a “semester in Spain,” and all the reader knows is that her explanation isn’t strictly true. The point-of-view jumps being so strict (there is never an Alex perspective chapter during last semester, and never a Darlington perspective in the present) serves to separate the two characters from each other with a really incredible emotional effectiveness. The heart of the novel, for me as a reader, was yearning for these two to be reunited - and all because Bardugo holds the two character points-of-view separate across an unbreachable temporal divide. It’s a powerfully effective technique.
But let’s backtrack. Alex is a 20-year-old high school dropout from the west coast. As the story progresses, we learn that Alex can see ghosts, which is why, despite never finishing high school or getting her GED - or even applying - Alex is a freshman at Yale - contingent on her joining the secret society called “Lethe House” as apprentice (“Dante”) to the current leader of the society, Darlington (the “Virgil”). Lethe House is the governing body of the eight Yale secret societies that practice the magic that keeps the elite in power. These secret societies make books sell, make T.V. anchors charming and compelling, and open portals to other parts of the world - when they aren’t throwing over the top Halloween parties with magic designed to alter one’s perception of reality.
Darlington, by contrast to Alex, seems to belong at Yale. He’s from an old family, and he’s preppy and well-read. Most of all, he loves Lethe House and its history of keeping the secret societies from harming people in their pursuit of magic and power. That is, until he disappears just in time for Alex, only half-trained, to investigate the murder of a girl on campus.
The first three quarters of the novel are fantastic for the reasons stated above. Bardugo’s approach to mystery writing is effective. We have half a dozen suspects, most of whom, as elite ivy league magicians, are at least guilty of some misdeed. Having all your red herrings end up somewhat culpable anyway is a good way to keep your mystery difficult to solve until the end. We were off to a good start.
Unfortunately, in the end, Bardugo made the all-too-common choice to value “surprise” over the most compelling, satisfying solution. So while the reader doesn’t see the ending coming, that is at the steep cost of the ending not being justified by the rest of the book. Bardugo even has to invent new rules of magic off the cuff to justify the ending. When the rest of the book so painstakingly developed the rules of magic in a way that made sense and never felt overly expository, undoing all that effort feels like a monumental waste. And for what did Bardugo undermine all her hard work? A mystery that the reader won’t have all the clues to solve? It’s really okay - in fact, good - if the reader can puzzle out your story. It means your story has symmetry, internal logic, or perhaps, some sort of message.
This is what had me tearing my hair out. I know exactly how I would have written the ending of Ninth House to be the perfect conclusion to a stunning book. I know exactly what the message should have been. Is it somewhat ridiculous to say that Bardugo misinterpreted the message of her own book? Perhaps. But given the out-of-left-field-ending, the theme of the book ends up being a rather cheaply bought “No matter how traumatized you are, you can be a girlboss” instead of the message that the very structure of the novel itself was pointing to since page one: one of companionship, trust, and restoration (frankly, a better message for a novel with a main character who suffers so much loss and trauma. But, sure, “girl power” is a theme...I guess...)
Here’s what I mean by the structure of the novel itself pointing to a different theme. (Spoiler warning for the rest of this paragraph). Because the point-of-view switches in the first two thirds of the novel were used by Bardugo like two magnets being held apart, the only way to create a feeling of resolution was, so to speak, putting the magnets back together: getting Darlington back into the “present.” The degree of disconnect between reader expectations and the reality of the book is comparable to picking up a romance novel only to have the two leads decide to just be friends at the end. Bardugo set expectations - akin to genre expectations - but unfortunately Bardugo kneecapped her first book in the service of the sequel.
And then there’s the trauma. Alex’s backstory wouldn’t be the same without some level of trauma; it’s an important part of her character arc. Even the explicit presence of sexual assault on the page was justified in the case of Alex’s backstory - and I think that is rarely true. But when it came to a side character’s explicit in-scene rape, which was used as a clue in the broader murder mystery rather than treated as a crime in its own right, that tipped me over into feeling the trauma in Ninth House was more excessive than necessary for character development. The resolution to that side character’s rape is oddly cartoonish - like an over-the-top prank rather than justice - and again, the only reason the rape happens to the character is to give Alex more information she needs to solve the plot. Maybe that wouldn’t bother some readers, but for me, a book has to bend over backwards to justify showing me a character being raped. Bardugo does well earlier in the book when depicting Alex’s assault; the assault is the explanation for why Alex doesn’t view magic with the same childish excitement as the rest of Yale, and it’s part of what holds her apart from the entitled secret societies. It needed to be in the book. Everything else was gratuitous.
That said, there’s one thing still to address in this roller coaster of a review, and that is: wait, is this a queer book? I had gone into it assuming that it would be, mostly because all my queer friends were reading it. And the answer is….kind of? Knowing Bardugo’s history with putting queer characters in her books, I’m going to assume she wasn’t baiting when she had Alex claim to have loved a girl in her backstory. Which, in the context of the rest of the novel, would make Alex bi or pan. As a book that a lot of queer fans of Bardugo’s YA have read, or will read, it feels appropriate to review it here.
This was a mixed review from start to finish, but to finish up: if you are thinking about reading Ninth House, go for it! There is so much to like about this book. Take to heart that if you read and liked Bardugo’s handling of sexual assault in her YA titles, you should be prepared to be surprised by Ninth House. It is not the same. I would not have called her handling of sexual assault in Six of Crows, for instance, restrained - but compared to Ninth House, it absolutely is. Despite my strongly worded feelings about the ending, Bardugo left room to redeem herself in the sequel (which, if you ask me, is why the ending was so bad in the first place...). I for one will definitely be reading the sequel the second it comes out.
#leigh bardugo#ninth house#fantasy#mystery#dark academia#not ya#mixed review#bi#reviews only#protagonist of color#jewish protagonist
31 notes
·
View notes
Text
Headlines
Climate change makes freak Siberian heat 600 times likelier (AP) This year’s freak Siberian heat wave is producing climate change’s most flagrant footprint of extreme weather, a new flash study says. International scientists released a study Wednesday that found the greenhouse effect multiplied the chance of the region’s prolonged heat by at least 600 times, and maybe tens of thousands of times. In the study, which has not yet gone through peer review, the team looked at Siberia from January to June, including a day that hit 100 degrees (38 degrees Celsius) for a new Arctic record.
Mail delays likely as new postal boss pushes cost-cutting (AP) Mail deliveries could be delayed by a day or more under cost-cutting efforts being imposed by the new postmaster general. The plan eliminates overtime for hundreds of thousands of postal workers and says employees must adopt a “different mindset” to ensure the Postal Service’s survival during the coronavirus pandemic. Late trips will no longer be authorized. If postal distribution centers are running late, “they will keep the mail for the next day,″ Postal Service leaders say in a document obtained by The Associated Press. “One aspect of these changes that may be difficult for employees is that—temporarily—we may see mail left behind or mail on the workroom floor or docks,″ another document says. The changes come a month after Postmaster General Louis DeJoy, a major donor to President Donald Trump, took over the sprawling mail service. In a memo titled “PMG Expectations and Plan,″ the agency said the changes are aimed at “making the USPS fundamentally solvent which we are not at this time.″ Postal Service officials, bracing for steep losses from the nationwide shutdown caused by the virus, have warned they will run out of money by the end of September without help from Congress. The service reported a $4.5 billion loss for the quarter ending in March, before the full effects of the shutdown sank in.
Twitter Hack Exposes Frailty of the Digital Public Square (Foreign Policy) Twitter accounts belonging to high-profile business leaders and politicians were hacked yesterday in the biggest security breach in the website’s 14-year history. Fortunately, the goal of the hackers was more con artist than saboteur. Accounts belonging to business leaders such as Jeff Bezos and Bill Gates as well as Democratic presidential candidate Joe Biden and former U.S. President Barack Obama all posted a version of the same message: A call to donate money to a cryptocurrency account in return for your money back twice over. Despite the millions of followers these accounts have, the scam seems to have convinced very few of them. Only about $120,000 in bitcoin has been deposited to the hacker’s accounts, according to Reuters. Although the refrain “Twitter is not real life” is often used as a putdown toward the social media-addled masses, the website can have an outsized grip on reality. In 2013, a hacker took control of the Associated Press Twitter account and wrote a hoax tweet describing explosions at the White House. The tweet was quickly deleted, but not before tricking high-frequency trading algorithms—sending the U.S. stock market into a flash crash.
Barbados wants you to work from its beaches during the pandemic (NYT) In the first half of 2020, governments around the world imposed entry restrictions or strict quarantine procedures; flight traffic fell to its lowest level in decades. Many are confined not just to their countries, but also to their homes, as offices were shut down along with travel. But even as the pandemic continues to rage, the government of Barbados, a country in the eastern Caribbean, is sending a very different message: Come here, not just for a holiday, but for up to a year. Bring your laptop. Soak up the sun, the sea, the sand—and forget about the coronavirus. Dubbed the “Barbados Welcome Stamp” and launching this week, the program will allow visitors to stay on the Caribbean island visa-free for up to one year. The aim is to attract remote workers, with a bill to be introduced in Parliament by the government that will remove the local income taxes that normally kick in after six months. The program has unsurprisingly sparked global interest. Considered from a cramped apartment in London or New York, working remotely on a beach has an appeal even to those who know little about Barbados. Barbados is not the only country trying to open up to laptop-toting foreigners. Estonia is to launch its own long-awaited “Digital Nomad” visa program in the coming months, and countries including Georgia, Germany and Costa Rica already have visa programs geared toward freelancers.
A fight over nude swimming marks return of pre-coronavirus banalities in Europe (Washington Post) LYCHEN, Germany—There is perhaps no better sign that people are eager to move on from the coronavirus than the fact that this German lake district town is embroiled in a heated debate about nude swimming, and it has drawn national attention. The local council’s ban on naked swimming—and other activities such as naked yoga—has returned the town to the banalities of pre-coronavirus summers and earned it a spot on the national public broadcaster’s nightly newscast, where it received more airtime than the United States’ spiraling coronavirus outbreak that day. Nude swimming has long been socially acceptable in other parts of eastern Germany and in Lychen, a town of about 3,000 people nestled between glassy lakes. “Whoever wants to swim naked swims naked. And those who don’t, do not,” said vacation home landlord Martin Hansen, 60, who opposes the ban. But in May, after it became apparent that the first wave of the coronavirus had largely bypassed the region, the Lychen town council turned its attention from social distancing restrictions to bathing rules. To some council members, naked fellow residents swimming, doing yoga and playing volleyball had been a growing annoyance. The mayor and council moved to ban all nude activity at popular public bathing spots. The outrage that followed included an anonymous letter to the mayor, threatening to poison the town’s lakes if nudist swimming rights were infringed upon. The police announced an investigation. TV crews and newspaper journalists descended on Lychen. Mayor Karola Gundlach declined an interview request from The Washington Post, citing the excessive media coverage and adding, “It does not help if people from around the world send me emails and tell me or the town what to do, what is right and wrong.”
Minorities under attack as PM pushes ‘tolerant’ Pakistan (AP) It’s been a tough month for religious minorities in Pakistan, and observers warn of even tougher times ahead as Prime Minister Imran Khan vacillates between trying to forge a pluralistic nation and his conservative Islamic beliefs. A Christian was gunned down because he rented in a Muslim neighborhood in northwest Peshawar, not far from the border with Afghanistan. Another Christian, pastor Haroon Sadiq Cheeda, his wife and 12-year-old son were beaten by their Muslim neighbors in eastern Punjab and told to leave their village. The attackers screamed “you are infidels.” An opposition politician was charged this week with blasphemy after declaring all religions were equal. A senior political figure, allied with the government and backed by Islamic extremists, stopped construction of a Hindu temple in the capital Islamabad. Analysts and activists blame an increase in attacks on an indecisive Khan. They say he preaches a vision of a tolerant Pakistan where its religious minorities thrive as equals among an overwhelming Muslim majority. They say that at the same time he cedes power to extreme Islamic clerics, bowing to their demands and turning to them for the final say, even on matters of state.
India virus cases surge nearly 32,700, beach state shut anew (AP) India’s virus cases surged another 32,695 as of Thursday, taking the nation closer to 1 million and forcing a new lockdown in the popular western beach state of Goa two weeks after it was reopened to tourists. The new confirmed cases took the national total to 968,876. The Health Ministry also reported a record number of 606 deaths in the past 24 hours, taking total fatalities up to 24,915. About a dozen states, including Maharashtra, Tamil Nadu, West Bengal and Assam, have put high-risk areas under lockdowns, only allowing essential food supplies and health services. Goa state’s top elected official, Pramod Sawant, announced a three-day lockdown and a night curfew in the popular backpacking tourist destination, beginning Thursday night. He said people were flouting social distancing norms. Nearly 40,000 people were fined 100 rupees ($1.3) each in the past two weeks for not wearing masks.
Flooding in Bangladesh (Foreign Policy) As much as one-third of Bangladesh is now underwater after the country’s heaviest rainfall in a decade, according to Al Jazeera. As we reported last week, the floods began in part because of the overflowing of the Brahmaputra River. In the neighboring Indian state of Assam, at least 50 people have been killed as a result of the flooding.
Mysterious Fires Scorch Iran (Foreign Policy) Iran, already ravaged by U.S. sanctions and the coronavirus pandemic, now faces another scourge: A wave of mysterious fires torching the country, including a blaze that burned seven ships in Bushehr, a major port city, on Wednesday. The fires include a July 2 explosion at an underground fuel enrichment plant in Natanz that the New York Times reported was part of a covert effort to undermine the Iranian nuclear program. The incidents have sparked fears in Iran that the United States and Israel are increasing sabotage operations directed at Tehran. No deaths were reported from Wednesday’s fire. Officials in Iran have blamed some of the fires on sabotage, but others appear to have been caused by accidents, equipment failures, and inclement weather, the Times reported. The fires may raise fears of military miscalculation between the United States and Iran. The blazes come as the United States failed to convince allies on the U.N. Security Council to extend an arms embargo against Iran set to expire in October, as Foreign Policy reported. The Trump administration faces opposition from allies in its efforts to continue its so-called “maximum pressure” campaign—a definitive effort to scupper the 2015 nuclear deal. A website close to Iran’s Supreme National Security Council, Nournews, said this month that an attack on Natanz could cross a “red line” and lead to “fundamental changes” in the Middle East.
China becomes first economy to grow since virus pandemic (AP) China became the first major economy to grow since the start of the coronavirus pandemic, recording an unexpectedly strong 3.2% expansion in the latest quarter after anti-virus lockdowns were lifted and factories and stores reopened. Growth reported Thursday for the three months ending in June was a dramatic improvement over the previous quarter’s 6.8% contraction —China’s worst performance since at least the mid-1960s. But it still was the weakest positive figure since China started reporting quarterly growth in the early 1990s. China, where the coronavirus pandemic began in December, was the first economy to shut down and the first to start the drawn-out process of recovery in March after the ruling Communist Party declared the disease under control.
Taiwan holds military drills against potential China threat (AP) Taiwan’s military fired missiles from the air and the island’s shore facing China on Thursday in a live-fire exercise to demonstrate its ability to defend against any Chinese invasion. Assault helicopters launched missiles and fighter jets dropped bombs on targets at sea, while tanks and missile trucks fired from a beach to deter a simulated invading force. The drill was part of a five-day annual exercise that ends Friday. China regards Taiwan as a breakaway province that is part of its territory. The self-governing island of 24 million people lies 160 kilometers (100 miles) off China’s southeast coast across the Taiwan Strait.
Japan “extremely concerned” as 136 COVID cases reported on U.S. bases (CBS News) The biggest coronavirus outbreak within the U.S. military anywhere in the world continues to grow. U.S. Forces Japan confirmed Wednesday another 36 infections among troops on the Japanese island of Okinawa, bringing the total to at least 136 since the U.S. military reported its first cases there last week. Until then, all of Okinawa had seen only 148 confirmed cases of COVID-19 since February, with Japanese authorities managing to contain the spread of the virus that causes the disease. In a sign of the growing tension between Japanese officials and the U.S. military in Okinawa, Defense Minister Taro Kono has pointed to “several problems” with the U.S. response to the pandemic. He notably avoided giving specifics when pressed by reporters earlier this week. “Okinawa residents are extremely anxious” about the spread of infection at U.S. military bases, said Okinawa governor Denny Tamaki, who flew to Tokyo Wednesday for a meeting with Defense Minister Kono to air his island’s grievances.
3 notes
·
View notes
Text
Is AI Democratization a Real Thing?
In the last decades, we’ve seen tremendous advancements in Artificial Intelligence (AI) and related fields. It is viewed not only as a ground-breaking technology, but as a step forward to the future having the means to change our society. We expect AI to use hardware and software to see and hear patterns, make predictions, learn and improve, and take action with this intelligence. Some enthusiasts believe that AI can be a tool that will guide us to a better world showing how to achieve more. In this context, new questions have been raised of power and pervasiveness of such technologies. However, many IT companies claim that AI will democratize AI and will make it available “for every person and every organization”, open to developers and researchers around the world. But does AI really democratize our world? And is it only a positive development?
What does AI democratization mean?
When we say that something is democratized, we imply that all people can access it and benefit from it. In enterprise IT, to democratize AI means to make it accessible for every organization or even to every person within the organization. Such dissemination of AI is indeed beneficial in many respects:
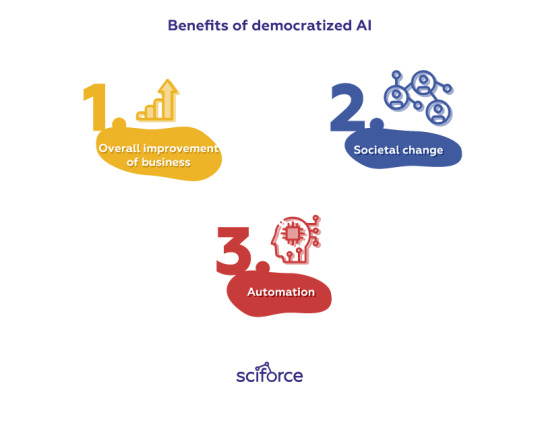
Benefits of democratized AI
Overall improvement of business — AI currently encompasses cloud suites, NLP-based virtual assistants to run business, improve customer’s experience and increase stats;
Societal change — as the awareness and the usage of AI grows, it gains more power to address global issues, like fighting climate change, tracking police work to avoid unfair targeting, or developing new standards in healthcare;
Automation — Gartner predicts that many of these tools will be automated, offering a completely new level of self-service that will free up companies’ potential.
What do we see today?
It is true that many companies, first of all tech startups and market giants, deploy artificial intelligence of some kind: machine learning does their predictions, natural language processing is improving their communication with clients, and sophisticated deep learning algorithms detect anomalies in their processes. However, many companies do not have the resources to build AI of their own and have to rely on cloud technologies to fill the gaps. For companies that are not tech-savvy, AI often feels complicated or overwhelming and it can be downright expensive, especially when engaging data science.
In this context, big tech firms end up way ahead of the curve, other enterprises can hardly catch them up, or even benefit from AI. To understand whether true AI democratization is achievable, let’s discuss what aspects of the market and inherent characteristics of AI add to inequality and what measures are taken to make AI available for everyone:
Data is the King
Data is the key to successful AI-driven intelligence and the more data we create, fuelling the so-called new “data economy”, the smarter products and services we can develop. Data seems to be an increasingly important asset and often the only significant advantage over the competition and as a result it is vigorously kept private. Undeniably, having access to all data produced by your devices or every trace of your digital presence and being able to cross-correlate them across different platforms, services and people give an enormous power. To understand the scale, we can think of the monopolizing presence of IT giants like Facebook or Google in our daily digital life. This is completely rightful and strategically sound, but unfortunately completely in contrast with the AI democratization process.
We are promised that the monopolizing effect is mitigated by new algorithms that offer insightful predictions even with limited datasets. However, best results are still achieved with gigantic amounts of data, so to make AI available to everyone, we first need to make data available to every interested party via open and shared datasets. AI democratization can not work if we do not democratize data first.
At the same time, access to data is only the first step towards AI democratization, since it is not the amount of data that wins the competition, but the ability to use it.
Technical Illiteracy
In many cases, we do not think of the amount of digital data we produce in the world where every “like” on Facebook counts. At the enterprise-level, companies that are not technically savvy, are easily misled by complicated Ai solutions. Major AI companies intentionally take advantage of the common illiteracy in AI by oversimplifying and even undermining more serious AI democratization approaches. Similarly to data ownership, concerns are raised on the dangerous monopolization of AI technologies by only a few organizations.
Network Effect
An extension of such monopolization is the “network effect”, a social and economic phenomenon where an increased number of users improves the value of a good or service in turn attracting more participants and triggering a virtuous cycle. This effect makes the situation even more unequal, as the tech giants gather most of the participants, their data and, as a result, intelligence — just think of Google and Baidu that detain ~86% the entire market share.

AI Talents
As big companies have more resources, they open up their doors to the best scientists, creating advanced labs for AI research with infinite resources. This has led to great advancements and speed-up in AI research. At the same time, tech giants tend to open up their AI research labs, giving the researchers the freedom to collaborate with other institutions or make everything open-source.
Does it add to democratization of AI? From the inspirational point of view, yes, since everyone now can download the sample code and try to use it in any project.
However, in reality the results are not always reproducible, and what tech giants achieve is free improvement and testing of their open-source tools.
Cloud
Most companies who successfully deploy AI have to invest heavily on the tech side. The enterprises that have more limited resources or that have no wish to engage in the full circle of AI research and development can get more affordable cloud solutions. The cheaper cloud tech gets, more AI tools can exist offering immediate solutions. Besides, as clouds make AI more accessible, more people can specialize in it, decreasing salary costs to companies for these data-specific jobs.

As we can see, democratization in reality is a myth as the access to AI is limited, on the one hand, by the resources and knowledge a company has and, on the other hand, by the amount of data and technology tech giants are eager to share. However, the lack of accessibility is not necessarily totally bad. Data quality is often uncertain, to say the least. When relying on a combination of entry-level AI specialists typical for smaller companies and automated or self-service AI tools, companies may be relying on data that is poor and produces unstable solutions. Results from poor data can ripple across the business, with unanticipated outcomes not evident until it’s too late.
Another problem we may face as AI democratizes is the bureaucracy inherent to many enterprises that will prevent companies and employees from acting quickly. Yet, it is the only way that intelligence can actually make a difference — if it is applied at the right time, which often arrives faster than a board can enact a decision.
To sum up, AI is indeed our future, and we’ll see the technology getting more accessible to everyone. However, like in human democracy, we’ll need a system of checks and balances to ensure that the AI-driven world remains afloat.
1 note
·
View note
Photo

"Confronting the Cybersecurity Challenge" - Keynote Address by Glenn S. Gerstell, NSA General Counsel
2017 Law, Ethics and National Security Conference at Duke Law School
February 25, 2017
Good morning, and thank you for having me at this impressive conference. I'm happy to be back here at Duke. I've had the pleasure of visiting the school on several occasions, including for recruiting for my former law firm as well as attending a wedding of a good friend at the Duke University Chapel. And back at NSA, we are delighted to have two fantastic members of your class of 2012 with us in the Office of General Counsel and we are looking forward to having another recent graduate join us this fall.
Yesterday, you heard from many experts on the topic of cybersecurity, which is a timely theme for this conference. Right now, that topic is at the forefront of American minds: there has been a proliferation of high-profile intrusions against U.S. companies, and malicious cyber activity will forever be associated with the 2016 election cycle. While I can't say I have the same qualifications as some of yesterday's exceptional speakers, I would like to talk to you today from my vantage point of not only a lawyer who spent many years in the private sector counseling companies around the world, especially in the telecom and technology sectors, but also -- and more importantly for today's purposes -- as the General Counsel for the past year and a half of the National Security Agency.
Now, many of you may be wondering why the General Counsel of NSA has decided to speak to you today at all -- indeed, for its first few decades the Agency's very existence was officially denied so there was no question that anyone on behalf of the Agency would ever speak in public. Fortunately that's all changed. But you might be expecting me to talk about surveillance rather than cybersecurity. After all, in the wake of the Snowden disclosures, most people associate NSA with spying. Foreign surveillance -- or "signals intelligence" to use the precise term -- is, however, only half of our work. The other half, which is increasingly significant, is information assurance. In common terms, information assurance involves protecting and perhaps defending information and information systems. Our specific charge is to protect and defend national security systems, which include all classified networks along with those unclassified networks that involve intelligence activities or equipment that is critical to military or intelligence missions. So that includes all of the Department of Defense's networks around the world, and such specialized networks as the President's nuclear command communications system. This aspect of our mission, though somewhat unheralded, is of critical importance.
NSA is uniquely positioned to make key contributions to the nation's cybersecurity because, through its two missions of foreign surveillance and information assurance, it lives on the cutting edge of the global information space. Those twin missions complement each other in a way that enhances the agency's ability to detect and prevent cyber threats. NSA employs experts in signals intelligence, information security, and computer network defense and exploitation, and as a result of this expertise, NSA has end-to-end insights into malicious cyber activity, internet infrastructure and networks, the activities of hostile foreign powers, and cyber best practices. Although significant cybersecurity expertise resides elsewhere in the federal government, NSA is often regarded as possessing the leading collection of information security talent in the U.S. government based on the sheer breadth and depth of our focus on the subject.
So this morning I want to use that platform - informed by our twin missions - to explore new strategies for the organizational structure that underpins U.S. cybersecurity. I know that everyone here is a disciple of national security law, and as a result, this audience is more cognizant than most about the cyber threats we face today. But I will spend a few minutes just to make sure we all have a clear picture of the current scope of the threat, how we are currently postured to address that threat, and where gaps remain in that approach. I would then like to explore with you some thoughts on how our federal government should organize itself to address those gaps.
You hardly need me to point out the ever-increasing dependency on connected technologies in our everyday lives. In fact, I bet about quarter of you have already checked your cell phones since Major General Dunlap introduced me...maybe even half if my skills as a speaker leave something to be desired. The increasing interconnectedness of our networks and devices enhances convenience in an astounding way -- it's nice to know that I can use my smartphone to order an Uber car around the world and also adjust the water temperature of my home spa -- but along with that convenience -- for individuals as well as businesses and governments and other organizations -- comes heightened vulnerability. The vulnerability can take many forms. It wasn't that long ago that cybersecurity simply meant deleting emails from a Nigerian prince who needed your help in making a bank deposit. Beyond basic email hygiene, there are threats to an entire network - true, the network owner can take extra precautions to secure the network, but that security can be undermined by the one user who connects to it with an infected device or downloads a spearfishing email. Network threats by definition can be as serious as the criticality of the infrastructure or equipment controlled by the network or the sensitivity of the information conveyed by the network.
A great deal of time and attention has already been spent assessing today's cyber threat. Study after study has echoed the gravity of our country's cybersecurity vulnerability. Experts agree that the threat is so grave because barriers to entry are extremely low while potential rewards are great, and the risk of getting caught for mischief is low. Malicious cyber tools are cheap and widely available on the internet. One lone actor with few resources now has the power to wreak havoc on a network anonymously. Cyber crimes are notoriously hard to track, and attribution can be challenging at best. These same studies typically put malicious cyber activity into one of three categories: cyber crime, in which criminals are seeking money outright...or something of value to resell, such as credit card numbers, tax IDs, and social security numbers, or they hold corporate data for ransom. Another category is cyber espionage. This category typically involves nation states, and it includes both political espionage and espionage for commercial gain, like the theft of trade secrets for economic advantage. And third, there's just general cyber mischief. This category includes hacktivists, those who use cyber vulnerabilities to spread propaganda, like ISIL, and those who seek to disrupt services or sites, like the recent DDOS attacks facilitated by Internet of Things botnets on the website of cybersecurity journalist Brian Krebs and on Dyn, a domain name service provider, that took down popular sites like Twitter, Spotify, and Reddit. And it's only a matter of time before this category also includes the deletion or alteration of data -- just think of the havoc that can create, especially in the case of the latter, where the malicious action might not be apparent.
So we know the nature of the threat -- and to give some sense of the scope of it, it's no exaggeration to say that cyber vulnerability is one of the biggest strategic threats to the United States. I was alarmed when at the first annual threat assessment I had the privilege of attending before the Congressional intelligence oversight committees, the Director of National Intelligence placed cyber threats ahead of terrorism. There are 23 victims of malicious cyber activity per second according to a 2016 report from Norton, and the Center for Strategic and International Studies recently estimated that such activity costs our national economy $140 billion each year. By comparison in just economic terms - and I don't mean to suggest they are really equivalent - the Institute for Economics and Peace, which publishes a yearly Global Terrorism Index, estimated that the global economic impact of terrorism was about $90 billion in 2015. And in case you were worried about the stock market bubble, the Chair of the SEC last year said that the gravest threat to the American financial system was cyber. The threat is so grave, in fact, that former CIA director and Secretary of Defense Leon Panetta described our nation's cybersecurity weaknesses as amounting to a pre-9/ 11 moment.
But surely we're doing something about it? Although the Bush Administration took steps to address cybersecurity policy on a national level, for example through the issuance of National Security Presidential Directive 54 in 2008, the issue remained somewhat obscure -- and indeed a year later the topic wasn't even mentioned in President Obama's inaugural speech. Over the ensuing eight years, however, as the topic rose in national prominence, the Obama administration took significant steps to implement a whole-of-government approach to dealing with the multi-faceted cybersecurity threat, , including through issuance of PPD-41 and Executive Order 13636. The first laid out the framework for the US government's response to significant cyber incidents; the second provided a risk-based approach for managing cybersecurity threats. Executive Order 13694, also issued by President Obama, enabled sanctions against malicious cyber actors. He used this new Executive Order to issue sanctions against various nation state cyber actors, including against North Korea after the Sony hack and, most recently, against Russia for its cyber interference in the U.S. election. The Administration also authorized high profile prosecutions of nation state-sponsored cyber actors. For example, the government indicted five Chinese military hackers for espionage against U.S. nuclear, metal, and solar companies, and it also brought charges against seven Iranians working for the Islamic Revolutionary Guard Corps who carried out intrusions against the U.S. financial sector and a dam in New York.
In addition to these Executive Branch efforts, and after much debate, at the end of 2015, Congress passed the Cybersecurity Information Sharing Act, or CISA, which is designed to improve cybersecurity in the U.S. through enhanced sharing of threat information between the public and private sector. Unfortunately, I don't think anyone believes that CISA by itself is adequate to the task. The statute's slow development was perhaps an indication that at the time CISA was being debated, the full scope of the cyber threat had not yet sunk in for all parties to the conversation and also, perhaps, that concerns about government surveillance remained high in the wake of the Snowden disclosures.
To further advance the discussion, the last Administration created a Commission on Enhancing National Cybersecurity, which recently issued its report containing some useful recommendations to enhance the government's cybersecurity efforts. Others, including think tanks, commissions, commercial companies, and professors, have also studied the problem and contributed proposals. To date, however, political will has not yet coalesced around one preferred approach, and the US government's response to cybersecurity challenges remains largely reactive.
Perhaps that is because, as many critics have noted, cybersecurity roles and responsibilities are unclear. Currently, cybersecurity responsibilities are shared across several federal departments, agencies, and congressional committees. To start off with, there are no fewer than six Federal cybersecurity centers – the National Cybersecurity and Communications Integration Center (NCCIC) run by DHS, the National Cyber Investigative Joint Task Force (NCIJTF) led by the FBI, the Cyber Threat Intelligence Integration Center (CTIIC) housed within the Office of the Director of National Intelligence, the Department of Defense's Cyber Crime Center, US Cyber Command's Joint Operations Center, and NSA's own Cybersecurity Threat Operations Center (NTOC). NSA itself sits at one extreme of the operational model, with NSA being responsible for securing national security systems. That means, for example, that NSA is authorized to review and approve all standards, techniques, systems, and equipment related to national security systems. NSA also gathers foreign cyber threat intelligence and works to determine attribution of malicious cyber intrusions. But even for national security systems, however, there is no end-to-end solution. Within the Department of Defense, in which NSA is housed, there are procedures in place for enforcing network security standards and best practices for national security systems. For national security systems outside DoD, however, those procedures are less robust because the network owners – namely the other federal agencies -- have more autonomy and varied resources.
Contrast that operational model with the more advisory model that is used to protect the "dot gov" domain, which is overseen by the Department of Homeland Security. That department is responsible at least in principle for securing the remaining entirety of the federal government's networks along with critical infrastructure, although in reality each government agency has a major share of that responsibility. The National Institute of Standards and Technology, or NIST, which is organized under the Department of Commerce, develops the mandatory standards and guidelines for federal agencies' information systems. DHS is also principally responsible for communicating and coordinating in the cyber arena with the private sector, but nowhere in the federal government is there any meaningful authority to regulate, police or defend the private sector's cyber domain. Such authority as there is, is dispersed among not only DHS, but also various federal cyber centers that have been established, such as the Cyber Threat Intelligence Integration Center, and such disparate agencies as the Federal Trade Commission -- which has an important role in, for example, seeing that private entities safeguard consumer information from cyber data breaches -- to the Securities and Exchange Commission, which among other things regulates cyber protection for our nation's securities exchanges and registered stock brokers. And let's not forget the role of the Secret Service, which has a key role in combating cyber crime involving our banking system.
I could go on, but you get the idea -- cyber responsibilities are scattered across the federal government. To be sure, there are understandable reasons why it evolved this way and some good reasons for continuing a multifaceted approach at least in part. With the multiplicity of agencies involved, it's no surprise that simply coordinating incident response is a major undertaking. PPD-41 lays out a framework that assigns responsibilities for federal cyber response among FBI, DHS, and the Office of the Director of National Intelligence, but as you might expect, no one really thinks this is an optimal solution. And on Capitol Hill, while Congress has been active in holding many informative hearings over the past few years on aspects of the cyber threat, almost any Member of Congress (not to mention many outside commentators) would bemoan the fact that jurisdiction over cyber is spread among many committees and subcommittees - leading some Senators and Representatives within the past year to push for the establishment of a single committee to oversee cybersecurity.
In short, we can all agree that glaring gaps remain in our nation's cybersecurity posture. Former Secretary of Commerce Penny Pritzker correctly pointed out that "Even though the Internet is now ubiquitous in our lives, cyber remains the only domain where we ask private companies to defend themselves against Russia, China, Iran, and other nation states." For physical threats to the health and safety of our citizens, we do not ask each person to stand up their own personal Army, Navy, or National Guard - and for good reason. If dozens of Target or Home Depot stores were physically attacked, all at once, across the United States, the government would not stand by and hope that their own contracted security guards both repelled the threat and then healed the victims. Indeed, we are finding out seemingly every day that we are vulnerable to cyber intrusions in ways that we didn't expect. The recent reports about hacks of political institutions with an intent to influence the Presidential election reminded us that just because a network does not fit within the definition of a national security system or fall within the sectors designated as critical infrastructure does not mean that it isn't a vital component of a fundamental American institution.
In addition, under the current structure, the private sector in general continues to have little to no incentive to concentrate resources on cybersecurity. Admittedly, there are companies in some sectors, such as finance, where the value of the product or service is intrinsically network-based, which do regularly share cybersecurity information and have sophisticated cybersecurity efforts. For the most part, however, private companies are incentivized to rush new products to store shelves in an effort to capture market share, and generate profits for shareholders. Delaying a product's release in order to assess and upgrade its cybersecurity can cost a company dearly, particularly if its competitors have not taken similar care. Many companies are even reluctant to share too much information because of concerns about protecting trade secrets and perceived antitrust collusion. It's by no means clear that the average consumer picks products and services based on a solid understanding of the comparative cyber risks present. That may be attributable to a lack of consumer education, or a conscious choice to weight other factors in product selection higher or industry's unwillingness or inability to address the risks - or all of these factors and others as well. But no matter what, it's incontrovertible that we do not yet have fully developed standards or practices in place that cause private companies in general to ensure the products they are selling are secure.
My purpose in reviewing the nature of the cyber threat is not to browbeat you with the severity of the problem, which I am sure you accept, but instead to implore you to join me in the conviction that the time to act is now. The incessant and rapid pace of technological development in the cyber arena continues to outstrip our ability to organize ourselves to address cyber threats before they become major cyber incidents. Some of the factors that might have contributed to our slow or tepid response to the threat -- ranging from lack of awareness to an unrealistic hope that somehow a public-private partnership would miraculously evolve to address the problem - have dissipated. We don't need to study or admire the problem any longer. Presidential elections have often served as the springboard for national initiatives and the new President has already signaled a strong awareness of the threat and an intention to do something about it. Moreover, interest in cybersecurity is high in the wake of the Russian malicious cyber activities, and the public is now more familiar with the role of intelligence agencies in protecting the national security. A major undertaking for the new Administration and Congress will be to take a hard look at the nation's cybersecurity and formulate a long term approach in an attempt to prevent a cyber equivalent of 9/ 11 -- one that simultaneously addresses both organizational obstacles and the underlying legal framework.
So let's turn to what should be done. As I've already alluded to, there has been no dearth of strategies proposed to address the cyber threat on a national level. They range from a recent Center for Strategic and International Studies report (advocating for making cybersecurity an independent operational component at DHS while also strengthening other key agencies), to GWU's Center for Cyber and Homeland Security (recommending the development of a framework that would allow technologically advanced private entities to engage in level of proactive cybersecurity measures that fall between traditional passive defense and offense). Separately, the Presidential Commission on Enhancing National Cybersecurity recommended, among other things, improving public/private partnerships and increasing use of the current Cybersecurity Framework laid out in Executive Order 13636. Meanwhile, Representative Michael McCaul, the Chairman of the House Homeland Security Committee, has been working to pass a bill that would codify certain cybersecurity authorities at DHS's National Protection and Programs Directorate, which would be renamed the Cybersecurity and Infrastructure Protection Agency.
As you can see, much attention has been paid to the nation's cybersecurity, but a consensus has not yet developed regarding the preferred approach. What's revealing, however, is that virtually all of these studies seek to advance two overarching goals: integration and agility. Any new approach to cybersecurity must be integrated, in that it must include major national-level structures in which all divisions of government know their roles in clearly defined, non-duplicative assignments appropriate to the particular expertise and position of the government entity. Integration isn't merely a governmental imperative. A national coordinated solution by definition must involve both the public and private sectors, and equally must take full advantage of the intelligence and insights generated by our national security apparatus. Most importantly, it must coalesce around a national will -- the creation and sustaining of that should be the work of not only the executive and legislative branches but also corporate America and academia.
A new framework must also be agile. From my position at NSA, I've witnessed the challenges in sharing classified threat indicators within government and across the private sector, and I've also seen firsthand that the process for determining who can act and what approach should be taken in response to a cyber threat is slow and cumbersome, involving formal requests for assistance, several layers of approval, and time-consuming fiscal considerations. It is akin to calling county water officials when your house is on fire, who must ask for assistance from the fire department, which must then receive approval from the mayor and money from the city treasury before a truck can be dispatched. By the time this administrative legwork is complete, our cyber house has been reduced to cinders. It is essential that our cybersecurity framework be equipped with both the resources and the authority to anticipate, protect against, and respond to cyber threats with the speed that will make a difference.
So how do we accomplish this? One obvious and affirmative strategy, and the one that I think may have the most potential for achieving real gains, would be to unify the government's cybersecurity activities by establishing a new lead department or agency for cybersecurity. Easily said perhaps -- but exactly how would one go about doing it? Well, much as we did two centuries ago, we can again look to our neighbors across the pond for ideas. The United Kingdom faces the same cyber threats we do, but for a variety of reasons one could speculate on (perhaps having to do with their size, institutional strengths and political culture), they sometimes are able to achieve solutions more quickly than can our arguably more fractious democracy. The UK within the past few months has selected a new integrated model, by creating the National Cybersecurity Centre or NCSC. Like the U.S., the UK had various entities, all with disparate responsibilities for cybersecurity. Their new center brought together and replaced four different entities. The NCSC is intended to act as a bridge between industry and government, providing a unified source of advice, guidance, and support on cybersecurity and management of cyber incidents. In other words, the NCSC model is intended to address both prevention and remediation of cyber threats and incidents by pulling together under one roof the full range of critical cybersecurity functions, including research, advice and guidance, and incident response and management. I am not necessarily proposing this precise model as the solution; after all, the UK has, as I noted a moment ago, a different culture, it is smaller, and the actual details of its legal system are quite unlike ours despite being obviously erected upon similar concepts. It is still useful, however, to examine the ground that they've started to break to determine whether there is anything that we can and should import.
The understanding that victims of cyber attacks were receiving conflicting advice and views depending on the government agency to which they turned was a major rationale for the UK to establish a unified cyber center -- but what really kick-started the UK to action was that the realization that relatively unsophisticated cyber intrusions, such as the attack against TalkTalk, a UK telecom provider, by a teenage boy, were turning into national level events because of a lack of basic cyber hygiene and because the government was not appropriately transparent about cyber threats and intrusions. Increased information sharing alone, however, was not the answer; UK experts decided that a more interventional approach was required in order to create consistency and coherency.
The UK carefully considered whether to organize the NCSC inside or outside the intelligence community. Much like in the U.S., there was apprehension in the UK after the Snowden disclosures about the role of its intelligence apparatus. Ultimately, however, the UK elected to stand up the NCSC as an agency wholly within the Government Communications Headquarters, which is the UK's version of NSA. This was done because, as I mentioned previously with respect to NSA, GCHQ already had the technical expertise and the intelligence insights that would be needed by the new organization. In order to overcome the public's apprehension, the NCSC committed itself to transparency: it publishes comprehensive data on cyber threats and, whenever possible, includes supporting evidence. Its facility is largely unsecured, so that it can bring in subject matter and technical experts from the private sector to teach NCSC personnel about their industries.
In conjunction with the establishment of the NCSC, the UK also rolled out its comprehensive National Cyber Security Strategy, which sets out the UK's approach to tackling and managing cyber threats to the country. It advocates for developing an innovative cyber security industry and provides for an active, nationwide cyber defense program. As an example, they've begun deploying a web check service, which scans for web vulnerabilities or misconfigurations in the websites of all public sector organizations in the UK. Website owners are provided a tailored report about any issues identified. Overall, the UK has committed to investing over $2 billion over the next five years to transform their cybersecurity posture.
Naturally, there are drawbacks to a model such as the NCSC. For example, concentrating cybersecurity responsibilities in one lead agency misses an opportunity to marry cyber expertise with the unique insights and understanding of requirements possessed by each agency in their own fields. In addition, as we've seen with the Department of Homeland Security, there are always bureaucratic and political issues associated with standing up a new national organization. The potential advantages of this approach, however, seem for the UK to outweigh the disadvantages.
Could we do the same thing here? At least on its face, this could satisfy the two principles I suggested a minute ago -- namely, integration and agility. Most importantly, through unification, the cyber protection mission would be informed by the foreign intelligence mission that uncovers malicious cyber activity from nation states and political groups adverse to us. The benefits of that proximity are precisely what led NSA, in an internal reorganization last year, to combine its information assurance teams with the signals intelligence ones in a combined operations directorate. And in a slightly different but still highly relevant context, the decision to co-locate and partially integrate the new US Cyber Command with NSA was a critical factor in seeking efficiency and synergy for the new organization. If we were to follow the UK model, cyber security would be the principal mission for a newly-created organization, rather than a secondary or tertiary support function, as it currently is for many federal agencies, and it stands to reason that that focus would yield better outcomes. Unifying cybersecurity responsibilities in one organization would enable the federal government to eliminate redundancies and to concentrate and streamline cybersecurity resources and expertise -- both of which can be hard to come by in an era where the cost of purchasing and updating equipment and retaining cyber talent creates challenges to the implementation of cyber best practices. And manifestly, housing the cyber threat discovery, protection, defense, and remediation capabilities in one entity would afford the agility and timeliness that is critical to an effective cyber strategy. In short, I think the case for such a unified, central approach is fairly compelling.
Even if we all concurred that such an approach was the right one, there would still be many details to be worked out. One key question would be how to sufficiently empower the new organization so that it could effectively defend the various networks of many federal entities -- which would include the power to, in some sense, police those networks, setting and enforcing standards, perhaps even shutting them down if needed -- while at the same time letting each entity have some authority and responsibility for its own unique operations. A unified and nationally prioritized budgetary authority would clearly be a critical component of such an approach. Similarly, Congress would need to embrace this approach on multiple levels, including centralizing to some significant extent the jurisdiction over cyber matters that is now accorded to many committees and subcommittees. The very process of deciding what we are going to do, however, will require us to face these questions head on. This exercise will be valuable in forcing us to decide how cyber responsibilities will be shared across the government, how the public and private sectors should work together, how to enforce compliance with standards, and how to respond to malicious cyber actors.
If this nationally unified approach were adopted, I am not necessarily proposing that such an organization fall within NSA. Although that is certainly worth exploring, we recognize that there are very real concerns about the scope of government surveillance and the potential use of "zero-day vulnerabilities" or cyber vulnerabilities that could be discovered by the government -- but at a minimum, NSA should have a special relationship with any new cybersecurity organization. It would make no sense to deny such a new organization the insights and warnings about cyber threats developed by NSA through its foreign intelligence mission. That would fly in the face of the very need for integration and agility. Whether that relationship takes the form of, for example, some deeper partnership between NSA and truly integrated cybercenter in a new Cabinet-level Department of Cyber, or housed, say, within the existing DHS, is something that the executive and legislative branches will have to sort out.
I want to make clear that by advocating that we avail ourselves of the infrastructure already paid for with taxpayer dollars and of the expertise and position of NSA, I am not, however, suggesting that NSA be granted additional surveillance authorities. We recognize that -- while increased communications monitoring might be an inevitable byproduct of confronting the cyber threat -- it's equally true that monitoring and implementing other technological approaches are fraught with understandable concern about government intrusion. Undoubtedly, there are portions of the population with unanswered questions (or worse) about us, but just because that perception exists does not mean folks like me are doomed to silence. Instead, I feel like we owe it to ourselves and to the public to enter the debate on topics like cybersecurity. The cybersecurity threat is grave, and we've got the unique expertise needed to help safeguard the nation against those threats. It's important to share some of our knowledge, developed over many years, in order to foster a vital public debate about the right way to address threats to our national security, and part of that debate includes an honest discussion about the pros and cons of locating a lead cyber agency or department within the intelligence community.
We at NSA feel duty bound to discuss these types of issues, and we'd like to do so transparently and openly to help reach a consensus as to the best approach. I hope that I've done that here today. Thank you for listening, and since I just spoke so highly about fostering discussion, I'd like to open up the floor for a few questions in the time remaining.
via NSA.gov
3 notes
·
View notes
Text
Y’know, today I feel like talking about Disgaea, specifically my problems with Disgaea 5: Alliance of Vengeance.
Spoilers for Disgaea 1, 2, 5, and Makai Kingdom, I guess.
So, first off, let’s talk about...
The Narrative.
Disgaea 5 tells the tale of edgelord Squall Leonhart wannabe Killia, a former asshole who got redeemed by falling in love with the daughter of the only demon to ever give him a proper ass-thrashing, who spent his time teaching Killia how to find inner peace blah blah blah it’s actually pretty bland. Killia speaks in a constant monotone, half-heartedly tries to get his rapidly accumulating party of Overlord-level demon pals to leave him the hell alone, and is generally just really goddamn boring. It’s not to say this kind of character can’t be interesting--in fact, I name-dropped Squall earlier, and until Final Fantasy VIII went completely off the rails in the second disc he was a legitimately nuanced character and I was interested in seeing where he went. Here’s the problem with all that, though:
The Disgaea series is a parody.
Now, full disclaimer--I’ve only played Disgaea 1, 2, 5, and Makai Kingdom. I have Disgaea 3 and 4, but I haven’t been able to secure a PS3 to play them on yet, so I’m leaving those out of the discussion (though from what I’m aware those are parodies as well.) However, of the four games I have played, Disgaea 5 stands out as being the only one of them to really take itself seriously.
Well, 2 did as well to a certain extent, but other than the looming issue of “we’re trying to off your evil dad, Rozalin,” Disgaea 2 takes itself about as seriously as Disgaea 1 did, and Disgaea 1 is a farce.
A beautiful, glorious, hilarious, one hundred percent intentional farce.
Laharl is a ridiculous creature. He’s petty, narcissistic, and childish, and while there are serious story beats (Etna being blackmailed, that asshole Angel stealing Flonne’s protective pendant, etc) Laharl never stops mocking his foes, his friends, and the genre itself. Disgaea 1, in short, is taking the piss, parodying the most ridiculous parts of anime and JRPGs (and, hell, American raygun gothic) with delightful glee...which is why, when things turn deadly fucking serious in the final chapter, it’s so goddamn heart-wrenching and effective. That slow burn of Laharl growing to care about Flonne enough that he tears the Heavenly Host several new assholes to try to save her from their judgment (and, even in the best ending, has to talk himself down from murdering the head angel in cold blood because she wouldn’t have wanted him to take revenge for her sake) is one of the most effective tonal twists in the history of media, in my opinion: all of a sudden, it’s not funny anymore.
While Disgaea 1 lampooned the genre as a whole, Disgaea 2 takes a different tack, and lampoons common anime/JRPG character archetypes. The hot-blooded, idiotically honorable melee fighter; the spoiled rich brat of a princess; the annoyingly perverted goblin of a third wheel (and, ugh, I wish that archetype would die already), the plucky little kids who are the least innocent characters in the whole crew other than the aforementioned perv goblin, on and on and on. The goal may be serious, but the characters are almost as silly as they were in Disgaea 1, and I actually think 2 manages an even better balance of humor and compelling storytelling than 1, because not only is the romance between Adell and Rozalin natural, enjoyable, and endearing, the dramatic beats come along without undermining the sheer silliness of our protagonists until it can have the most impact. There’s a moment in one of the later chapters where Laharl from the first game appears without warning, pissed off, heavily geared, and more than a thousand levels your superior.
(Yes, I said a THOUSAND levels. For those of you in the audience who aren’t familiar with the series, the level cap is 9999, and you can reset a character to level 1, storing attained levels for bonus stats. I’ll be talking about the grind later, don’t you worry.)
The encounter with Laharl accomplishes several things over the course of the two fights with him: it delivers a joyful reunion with the protagonist of the first game, which turns to terror when you see his stats, which turns to horror as you send your team into the meat grinder to die helplessly...and then it shows us that something is frighteningly wrong with Rozalin as she is seemingly possessed and tears this impossible foe apart effortlessly. From there the story really kicks into high gear, and like Disgaea 1, transitions into a deadly serious final assault on Zenon’s stronghold, but unlike Disgaea 1 it’s not a shocking swerve in tone--the story’s been building to this over time, gradually reconstructing the genre it gleefully tore to pieces over the previous game and a half.
Makai Kingdom is a very different affair, and can actually be most closely contrasted with Disgaea 5. In the Disgaeaverse, an “Overlord” is a very powerful demon who rules a pocket dimension called a “Netherworld.” Laharl’s an Overlord, for example. Makai Kingdom deals with a set of protagonists on a whole other level of power; these are the Overlords that other Overlords view as gods, and they essentially sit around on their asses playing card games and throwing popcorn at their TV.
I think you can see where I’m going with this.
Makai Kingdom is a return to Disgaea 1′s attitude--relentless silliness, mockery of itself, with a sharp turn at the end. Whether it accomplishes this goal as well as Disgaea 1 isn’t all that relevant, but it is something we can compare to Disgaea 5.
Disgaea 5 starts off similarly--hideously powerful Overlord-level demons gather together, but the characters are...not exactly dour, but played straight, I guess. There’s no parody, no lampooning; it’s very stock JRPG comedy (and “comedy”), with dramatic tension, a serious approach to its story and antagonists, and predictable story beats obvious to anyone who’s ever seen a mediocre anime or played a mediocre JRPG. Hell, the main villain’s name is Void Dark, and not a single character makes fun of that! There are some interesting designs, and I actually think Majorita is a compelling villain for Usalia, who I likewise enjoy immensely, but the story abandons almost everything that made the previous games’ plots entertaining. Topple an empire, murder some baddies, get your homes back, save your dead love from the creepy brother with the incestuous undertones. That’s it. That’s all. As a story structure, it works just fine, and as evidenced by my love for the rest of the series I absolutely think challenging established conventions is a good thing, but it doesn’t do so successfully enough that it stands out as a worthy entry in the series. Where it does shine is in improvements to gameplay quality-of-life and beautiful animation, which brings me to...
The Gameplay.
Disgaea 5 improves the UI, adds all sorts of neat little quirks to character customization, and improves game control substantially. It adds extra ways to gain stat points (like I said before, character levels cap at 9999 and can be stored for stat bonuses--this game also allows you to train stats for stat points via minigames) and is just generally more in-depth than its predecessors...at the cost of being stupidly easy to grind out.
Yes, I think an easier grind is a bad thing. Let me explain: I have over ten thousand hours in Disgaea 2 alone over the last twelve years. I picked the first two games up when Disgaea 2 was brand new, and have beaten the game dozens of times in the intervening span. Most recently, about five years ago, I created a save file on the PSP port of the game, and I spend idle trips or the time I’m falling asleep grinding it out as kind of an idle game.
Literally everything you do in a Disgaea game gets you experience for something. Weapon mastery, skill exp, character exp, you name it. Hell, you can run randomized dungeons inside your items to level those up, too. It’s incredibly satisfying and makes for a constant sense of progression--even if you don’t level up in a fight you’ve still gotten experience points for the skills and weapons you’ve used, making it stronger, more effective, etc. My personal goal is to, eventually, have one of every character class maxed out on stored levels and every skill and weapon proficiency in the game, which is a deliberately impossible task because it’s just so much fun to chase it forever.
Here’s the other thing: the Disgaea series, due to the ludicrous level cap, is known for its absurdly deep pool of ever-stronger bonus bosses, stretching, yes, all the way up to the level cap. The hunt for those is likewise extremely satisfying, and takes quite a while, especially since the campaign usually caps out at around levels 70-90.
With all this in mind, imagine my dismay when I realized I was blowing through skill and weapon exp and hitting the caps on everything in a tiny percentage of the time I was expecting. To be fair, there is a “Cheat Shop” NPC who can adjust the EXP you gain up and down, which is neat, but I have to crank it down to literally single-digit percentages of normal to get the same amount of chase-time out of it. This is not to say that the game should be inaccessibly grindy; in fact, Disgaea 1 and 2 aren’t. The story campaigns in those games are perfectly completable with the normal skill progression and a small but admittedly grindy amount of extra leveling in unlocked areas. It’s all the extreme bonus content that’s gated behind the postgame grind, and the huge ceiling on skill levels and weapon proficiencies means you’re constantly rising in power and challenging new heights. I think that’s a fantastic reward for being dedicated to the game! And Disgaea 5 in its default state takes that away. I had a character capped out on all proficiencies, subclasses, and aptitudes within my first hundred hours of the game.
It was...disappointing, I guess. All around, mostly; for every step forward it took, it also took a step back. Ultimately, the story takes a backseat to my points about the grind, because the campaign in any Disgaeaverse game is literally about 2% of the game’s content. Disgaea 5 took my grind from me, and that’s why I’m salty enough to have just spent an hour typing up a book report on its failings, I guess.
46 notes
·
View notes
Text
A rambling diatribe on retro-gaming elitism
There’s a lot to be annoyed about in the world today - obviously - especially with the various types of mess we’re all living with in every country in the world.
But a particular, and specific annoyance in the retrogaming hobby/lifestyle/environment/zeitgeist, is the hive-mind attitude from an increasing number of the most vocal (and seemingly most affluent) participants that this is, or should be, an extremely expensive hobby/lifestyle/etc/etc.
It’s impossible not to notice an underlying, deeply unpleasant, atmosphere of elitism in many of the communities I visit. An attitude of ‘you’re not doing it right’ directed at anyone who doesn’t have their Neo Geo AES hooked up to a 20” PVM via OSSC. (I have no idea if that example makes sense, nor do I care.)
This is the kind of arms-race attitude that fought to keep PC gaming an exclusive club for decades, and it has gradually seeped into retro gaming's language and ecosystem almost undetected.
The simple joy of rekindling one's nostalgia for Super Mario World, or re-experiencing the simple fun of games lost with the arcades, is being obfuscated by a collective need to quantify, update, and monetise every aspect of vintage computer entertainment.
It’s the kind of environment where you might expect the gateway drug of emulation to be met with the utmost scorn, but instead the self appointed guardians of retro (You can have that for your quiz team/band name, BTW) have positioned emulation behind a paywall of Retron 5s, Mega SGs, and (only the latest and most expensive) Everdrives. Any excited newcomer asking about the best controller to play retro games on their laptop is quickly overwhelmed with talks of latency, resolutions, and refresh rates.
If it wasn’t bad enough that forced exclusivity exists, it actually appears to be having it’s desired effect.
You can see it both in the way questions are asked and in the tone of the responses. You can see it in the photos of someones latest, expensive, haul and the other even more expensive stuff in the background - almost, but not quite, out of focus.
People don’t ask where they can find a cheap CRT, they ask if their $100 Trinitron is ‘good enough’. A joyous celebration of a bargain buy, or a long lost attic discovery, will be met with derision and disbelief, the underlying accusation that unless you can afford the inflated eBay prices for a barely average Sega Saturn game, then you aren’t worthy to own it.
Which brings me neatly to the event that triggered this rambling blog entry.
There was someone on a Discord server I’ve been frequenting who stated, blankly, without malice, that “all the good Saturn games are 100+ dollars”.
Why would they think this? Simply because it’s what the gatekeepers want them, you, and everyone else to think.
These are the people who, when a collective question is asked, wouldn’t dream of recommending any of the dozens of fantastic, better even, Saturn games you could buy for the price of Burning Rangers.
It’s this sub-group who don’t want you enjoying Sonic the Hedgehog for free when they’ve invested $200 in a Mega SG. The only way their post-purchase rationalisation can cope is by attacking the perceived difference in quality, by claiming they seek a ‘purer’ experience, and by attempting to undermine the simple pleasure of just playing old games by insinuating that someone with a secondhand NES Mini isn’t doing it right.
Now I just want to be clear that I’m not claiming to be some kind of saint who never judges anyone else's choices, nor am I saying that there aren’t benefits to some modern retro products, but the weaponised affluence I’m seeing increasingly around retro gaming communities is something else entirely.
Admission 1: I strongly believe that by downloading a thousand roms and picking one to play for five minutes before switching to another, then another, then another... your assessment of them will lack a psychological bond of choice, expectation, and - yes - sometimes investment that adds to the whole experience of a game.
But this is no less true of a pack of illegal roms than it is of someone with thousands in disposable income spending a tenth of that on a game they’ll probably never play.
Cost, value, and investment are relative terms. The kind of ‘bond’ I’m trying to describe between a player and a game can be gained through the investment of time, the effort of research, and the expectation of finding out for oneself if that game from your childhood holds up 20 years later.
Admission 2: I think games from the previous century should be played on a CRT television whenever possible. Pixels look better with real scanlines - it’s an incontrovertible fact - and the colour depth offered by that massive, humming monstrosity wedged into the corner is really something lost to the ages.
But it’s not a prerequisite of fun. And it’s especially not necessary to find the most expensive, most instagrammable, most egregiously hyped PVM to enjoy a game of Super Mariokart with your kids.
When I say: "I think these games should be played on a CRT", I mean ANY CRT. I’m typing this in a room with 6 of the things, two of them were free, and the whole collection has been compiled for the total cash investment of £26.
As someone born over 4 decades ago I’ll let you into a secret: The geometry has always been rubbish, the hum has always been loud, the picture has always flickered and no one ever cared about resolution or refresh rate or input lag when playing Tornado Low Level on their ZX Spectrum in 1984.
It’s entirely possible to argue a convincing case that you’ll get a more enjoyable retro experience from a wonky Bush portable TV than from any professional quality display equipment. And beyond that, if you can’t find a tube telly or don’t have room for one, use an LCD - it’s better than nothing, and the filters some emulators have these days are great.
It comes down this:
If you’re lucky enough, or have worked hard enough, to have the disposable income necessary to buy $400 RGB Scart cables and a professional monitor the size of a family car - and that’s genuinely what you want for your retro gaming experience - That’s cool. You don’t need anyone's approval or respect, you’re doing what you want to do the way you want to do it - and that’s a life lesson for everyone right there. But it’s your way, and nothing more than that.
This nonsense of idolising only the most expensive elements of this hobby has to change and we, the members of these communities, are the only people in a place to do that.
So the next time you see an excited new Dreamcast owner looking for game suggestions, mention the best ones first, not the most expensive.
When you come across a reddit picture of someone's game collection don’t immediately look for the over-priced ‘rare’ game they haven’t got, look for the ones you have in common and can have a conversation about.
And if you ever, ever, see someone being criticised for playing roms, or using composite cables, or playing on a flat screen TV, or any of that postering gibberish - step into that conversation and ask what games they love? What happy memories do they have? What is it about retro games brings them joy?
Because this is the real value of games.
They bring us experiences and memories to savour forever, they engage with us in a different way to that of films and music - and that difference should be cherished.
Games exist to bring us pleasure. Sometimes that pleasure is tinged with fear, and sometimes it’s truly dark and doesn’t feel like pleasure at all. Sometimes the pleasure comes from intellectual stimulation, sometimes from mindless entertainment.
But whatever form it takes, this pleasure, this… fun… cannot be tempered by technology, and it must never be attributed to any scale of monetary investment.
The simplicity of Retro Games is joyous, they are heartbreaking, they are brilliant and they must never be withheld from those who measure value in the size of their smile, by those who measure it in the size of their wallet.
You better get the aspect ratio right though, or I will hunt you down!
0 notes
Text
Reason behind leaked exam papers in South Africa.
How can a country expect its educational system to breed innovative citizens, people who are going to take this country to greater heights when teachers are still underpaid. Passion fades with time when no motivator is present. We cannot run away from the fact that everyone is motivated by money to be even more dedicated in what they do. We can deceive ourselves and believe those claiming they are doing something because of passion and not money, take away their salary and see how long they will last in that job
Since when quality came at a low cost? Since when the nest service is from something that is poorly managed? Low investment yields less returns. The department claims to increase salaries forgetting that there is inflation, salaries increase with inflation which still does not make a difference at all. I propose a minimum of R22000 for entry level teachers after deduction of tax. These people are new to the working industry and they are expected to pitch early with what? Public transport? They are expected to rent nearer to the school or buy a house. Is the environment conducive? Will they be able to reach their optimum level and deliver as expected while leaving in a yard where there is loud noises daily and Intoxicated people doing as they please? Are they supposed to rent in back rooms? What of their dignity as teachers? Why are they belittled this much in this country. They have expenses like groceries and they are expected to look decent and presentable and are supposed to be people the learners look up to yet they are paid peanuts.
What of the extra hours they put in outside the schooling hours they are paid for? MPs earn a lot of money just from discussing without reaching a solution. We have countries like Switzerland and Germany paying teachers salaries that they deserve and they have the innovative graduates to show for it. Brain drain is ruling in this country of ours. Brain drain is a problem described as the process in which a country loses its most educated and talented workers to other countries through migration. Negative effects include loss of tax revenues by the home country, and a loss of key health and education service professionals. Quality teachers flee to countries with better pay. A teacher cannot even open an investec bank account and that says a lot about the level of undermining teachers face.
Teachers resort to ill means in order to make extra cash on the side. Teachers appointed as examiners are in the forefront of these shenanigans, every year we sit and watch the grade 12 results being announced seeing decimal increases in pass rates then told the perfomancr is “ getting better”, a few days later stories of leaked papers surface. You cannot tell me no one has ever asked themselves how does this happen, traffic cops settle for bribes because they are underpaid, teachers are no exception. Teachers appointed as examiners exchange exam papers for money because of the hunger the government puts them under. Organisms including humans always prefer where the grass is greener.
I plead for change.
0 notes
Text
Vote Like The Affordable Care Act Depends On It (It Does)

Health care is on the ballot this year, in more ways than voters may realize.
Full of the Affordable Care Act remains a very real possibility if Republicans get through the midterm elections with their congressional majorities intact. But even if the law stays on the books, its future will depend heavily on who wields power at the state level ― as governors, insurance commissioners and members of state legislatures.
These officials have always had a lot to say about the ACA’s implementation, although they rarely get the attention they deserve. Now they have even more influence, thanks to the ways that President Donald Trump and his allies have battered the law over the last 18 months.
The most recent change came from Washington early this month, when the Trump administration made it easier for people to buy that leaves out key benefits like mental health and prescriptions and isn’t available to people with pre-existing conditions. The plans hare tantalizingly low premiums, but they can expose beneficiaries to crushing medical costs ― all while driving up the price of more comprehensive coverage.
Short-term policies won’t be available everywhere, because states can restrict or even prohibit them. Some have done so already. But whether more follow will hinge, in part, on who is making the decisions come 2019.
The current state of play for health care is a reminder of one way that the GOP’s war on “Obamacare” has made headway ― by giving states more control so that access to health care in places like Georgia looks more and more different than it does in California.
It wasn’t supposed to be this way, at least not exactly. The idea of the ACA was to make sure all Americans, in all states, could get health insurance, partly by creating new, subsidized market of regulated private plans and partly by offering Medicaid to all Americans living below or just above the poverty line.
But a 2012 Supreme Court decision made it easy for state officials to reject the Medicaid expansion and GOP leaders in 17 states have done just that, even though the federal government picks up nearly all of the expansion’s cost. (It’s 18 states if you include Maine Gov. Paul LePage, who refuses to carry out an expansion the state’s voters approved by ballot initiative.) Republican officials in a similar, overlapping list of states have done their best to the private insurance reforms.
Access to health care in places like Georgia looks more and more different than it does in California.
In Florida, a lieutenant to Rick Scott, the governor now running for U.S. Senate, blocked enrollment counselors from holding events in state buildings. In Georgia, insurance commissioner came right out and said he and his colleagues were doing “everything in our power to be an obstructionist.” In Iowa and Tennessee, state officials made it easy for people to stay out of the newly reformed markets ― and enroll, instead, in plans that don’t comply with the ACA’s standards for benefits and open enrollment.
That last part is important because it has directly undermined how the new system is supposed to work. Insurers need healthy people paying into the system so that there’s enough money to cover the high medical bills of the people with serious health problems.
The ACA includes provisions to make that happen, including tax credits (which make insurance cheaper) and the individual mandate (which penalizes people who don’t get comprehensive coverage). But in states where officials have not done their part, enrollment among healthy people has lagged and insurers have jacked up premiums in response ― making coverage flat-out unaffordable for some of the people who don’t qualify for tax assistance.
Things are likely to get worse, thanks to what Republicans in Washington have done since Trump took over. They have passed a tax cut that effectively . They have for enrollment outreach. Now, with this latest regulatory change, they have made it easier for people to purchase ― and then hold onto ― short-term plans that don’t comply with the ACA’s standards.

Bloomberg via Getty Images
Republican governors like Florida's Rick Scott did everything they could to undermine the Affordable Care Act. If Democrats take their positions in November, it could make a big difference in how the law's reforms play out.
People struggling with high premiums today will discover short-term plans are a lot cheaper ― and many who opt for that coverage will be just fine. But the buyers who get serious medical problems will face crippling medical bills and in many cases, they won’t know about this exposure until it is too late, because the companies and brokers who sell these plans are notorious for hiding limits and exclusions in the fine print.
“I’m concerned that people will buy these policies, show up at the hospital for a condition they did not expect, and discover they are not covered,” , director of Alaska’s insurance division, told HuffPost. She added that her office intended to look “very, very closely” at applications from insurers seeking to market these plans.
Officials in different parts of the country have already taken or are considering such action, as a recent survey published by the demonstrated. Massachusetts, New York and New Jersey have more or less prohibited short-term plans altogether. Maryland, Vermont and Hawaii have limited them severely.
Other states, including Colorado and Oregon, have their own, somewhat less stringent restrictions in place, while California, Illinois and Washington are in the process of considering new ones, according to research by Sarah Lueck of the Center on Budget and Policy Priorities. In states like Alaska and Pennsylvania, which don’t have strong rules in place, state officials are vowing to use what authority they have to monitor advertising material and stop brokers from selling these policies under false pretenses.
It is by no means coincidental that the list of states acting aggressively to regulate short-term plans overlaps heavily with the list of states that have tried all along to make the ACA’s private insurance reforms work and were the first to expand Medicaid, as well.
Medicaid expansion initiatives are on the ballot in three deeply conservative states: Idaho, Nebraska and Utah.
Nor is it a coincidence that the officials saying nice things about the Trump administration regulations come from places that have been most hostile to the ACA all along ― places like Alabama, whose commissioner Jim Ridling admitted the new policies offer less financial protection but defended them as covering “people up to what they can afford.”
Opinions on the Trump regulations and how to treat them tend to correlate with party identification, although the relationship isn’t perfect and the differences among officials aren’t just about partisanship anyway. They reflect some real philosophical divides over how health insurance should work and what role government should play in managing it.
One view supports the basic impulse of universal health care that everybody should have access to relatively generous coverage regardless of income or pre-existing conditions, even if that requires more regulation, government spending and taxes. The other view holds that less government is always preferable to more and that ultimately, people will be better off shopping for whatever coverage insurers see fit to offer on their own.

Center on Budget and Policy Priorities
The latter view dominates in the South, the Plains and parts of the Midwest, which explains why those tend to be the states with the most dysfunctional markets and highest numbers of uninsured residents.
But that could change in November. Democratic gubernatorial candidates have a real shot of replacing Republicans in Florida, Georgia, Michigan and Wisconsin. Georgia is particularly interesting because it is one of the states that elect insurance commissioners directly and a Democrat could take that seat, too.
Democrats in Florida and Georgia are running on Medicaid expansion, which will not be easy to pull off quickly if, as seems likely, Republicans are still in charge of their state legislatures. But voter initiatives to expand Medicaid are on the ballot in three other, deeply conservative states: Idaho, Nebraska and Utah. Put it all together and it’s no exaggeration to say that November’s elections could mean gaining or losing health care access for hundreds of thousands of Americans ― and maybe even millions.
Source
https://www.huffingtonpost.com/entry/obamacare-state-junk-insurance_us_5b6e03a1e4b0ae32af98249c
0 notes
Text
Review - John Wick: Chapter 2

Back in 2014, I walked into a theater that was half full with reasonable expectations for Keanu Reeves long awaited return to action films. Me and everyone else in that half-capacity theater had a blast. I walked out of that theater having seen one of the most pleasurable action films perhaps this century. John Wick became a litmus test for whether or not I could trust somebody. If they don’t like John Wick, I don’t trust them. I dressed as John Wick for Halloween that year. One time a friend finally watched it and I got two texts from him in response that read “DUDE JOHN WICK” and “HOLY SHIT.” The list of what that film meant to me goes on and on. With that said, Chapter 2 is not only one of the best action sequels I’ve ever seen, it’s possibly one of the best sequels I’ve ever seen, period.
Perhaps the greatest achievement of Chapter 2, which any great sequel should do, is that it completely validates its existence despite the first film not really asking for a sequel. When you finish John Wick, you don’t sit there during the credits going “Can’t wait for the sequel! So many questions!” yet still when you finish Chapter 2 you nod your head approvingly, acknowledging that yes, we actually did need this. It keeps the core tenet of the original, which is that you should not fuck with this guy. It’s as the tagline on one of the poster says, “Never stab the devil in the back.” Chapter 2 finds most of its narrative thrust by expanding on a cautionary line from Winston to Wick in the first film: “If you dip so much as a pinky back into this pond, you may well find something reaches out and drags you back into its depths.” Santino D’Antonio (Riccardo Scamarcio), a member of the most powerful family in Italy comes to Wick to demand a return on a favor he is owed. By the rules of their trade, Wick must honor this request or die. Thrust back into the world he wanted to leave behind, Wick has a target on his back. Chapter 2 manages to to expand on what happened in the original for new material without undermining anything that happened previously.
Not many films attain the level of action opera. The only other one this decade was The Raid 2. I haven’t quite written down the rules of entry for the classification of action opera, but if you’ve seen The Raid 2 or John Wick: Chapter 2 hopefully you understand what I’m getting at. It’s just another level of action filmmaking, where you’re watching it at its grandest and most theatrical. Take John Woo for example, if you’ve seen The Killer or Hard Boiled, that guy knows how to make an action opera. The action in Chapter 2 is bigger, more expansive and theatrical, yet doesn’t lose the key pleasure of the first, which is watching Reeves demolish scores of baddies unassisted. The operatic nature of the film is immediately felt. The opening sequence is created by answering one question left unanswered from the first: where did his car go? He never got it back in the first film. In a giddily coked up turn from Peter Stormare, he plays the brother of Viggo Tarasov who’s in the unlucky position of having something of Wick’s. It doesn’t have much impact on the plot to follow, but it’s a wonderful, delirious sequence to reintroduce Wick to us. John Wick is a pure force of nature. We spent the first film getting to know this character and how badass he is, now we get an entire film that knows we already know that, and all it has to do is continue to display his ultimate levels of badassery.
It doesn’t tiredly rehash plot points of the original, instead taking the opportunity to flesh out the underworld that Wick has reentered and can’t escape from. It’s terrific world building, there’s a good amount of expository construction about how this world functions that happens visually, or in how characters insinuate things in dialogue. There’s so many bizarre little oddities to absorb about this world. The sommelier at the Rome Continental doesn’t recommend wines, but guns, in a great stunt performance from Peter Serafinowicz. To put out a hit, you contact a building full of women in pink blouses, all with the same tattoo sleeve on their right arms, and they connect calls using old-timey phone line connectors, then enter the hit info on a computer that is older than me. The introduction of an amulet known as a marker is integral to the plot. It’s a blood oath of sorts that must be honored at all costs.
Keanu Reeves is 52 years old and is out here with the dexterity and athleticism of an NBA power forward, doing physically grueling stunt work while making it look like ballet. Meanwhile, I am 24 years old, and this morning I woke up with my back really sore because I guess I slept on it wrong. Keanu Reeves is one of the last movie stars, along with Tom Cruise, who can do the most insane stunts themselves. They don’t need a double. There’s a trustworthiness to their presence, you can trust everything you’re seeing. The second shot of the film nods to one of the greatest stunt artists of all time, Buster Keaton, subtly relating that the filmmakers understand that stunts work at their best when their star is actually performing them. Keanu Reeves was already in my mind one of the great action stars, but Chapter 2 puts him in the Hall of Fame discussion.
Scamarcio turns in a wonderful villain as Santino, a sniveling sleazy presence. Common plays another assassin hunting John Wick and rises to the challenge of the stunt work and fight choreography. They have an epic extended couple of fight scenes, and they really beat the shit out of each other, it’s incredible to watch the sheer athleticism on display. Here’s hoping he comes back for Chapter 3. Ruby Rose also delivers a terrific character, a mute assassin also hunting Wick, and she too pulls off the physicality required extremely well. Side characters from the first make welcome appearances (I greatly appreciated another exchange with Jimmy), while other characters like Winston (Ian McShane) get a larger role. The legends Laurence Fishburne and Franco Nero contribute great turns that further flesh out this world, with Fishburne getting the juicy line “SOMEBODY GET THIS MAN A GUN.”
It’s just Chad Stahelski directing this time around, but the spirit of collaboration between himself and David Leitch is still felt. Stahelski’s past as a stunt coordinator and double is essential once again to why the film succeeds. The action is as good as it gets, filming them in long and extended takes, avoiding the noise and fuzz of hand-held action in clean camera movements. Stahelski knows how to make this look good, and with an actor like Reeves, he doesn’t have to hide anything in cuts. How Wick weaves his way through battle is like watching the greatest ballet act, he pulls off the feat of making heavily rehearsed action sequences look and feel in the moment, like they’re a product of this character’s expertise and skill. Chapter 2’s action had me sweating. Each sequence and showdown continually gets more impressive. Every single action scene feels like a highlight, you could put nearly every scene in this film down for the best action scene of the year. This film never runs out of tricks and showmanship to wow you with. There’s a sequence late in the film that takes place in an extended maze of mirrors that should have been impossible to film. It just should have been impossible to orchestrate so much mayhem while trying to hide the camera from reflection. You’ll need a cigarette after watching it.
The aesthetic of this world is always striking, a heightened reality made from shadows and neon lights. It would be enough if the fight scenes were just as good as they are, but the fact that the whole filmmaking process is as driven and ambitious really goes the distance. I didn’t realize until Chapter 2 just how great and understated the score from Tyler Bates and Joel J. Richard is. They use the same score from the original, only a few new compositions are added. It’s a pulse-pounding work that relies on muffled guitar riffs and electronic machinations, yet there’s a 4-note synth melody that finds its way through each time, like Wick’s own dwindling humanity.
Even though I would watch another 10 chapters, there’s comfort in knowing that they plan to only make 3, and the final chapter is set up terrifically. Chapter 2 ends on an incredible note, with the most dangerous character in these films running for his life with no sanctuary. John Wick joins the annals of the greatest action heroes on screen, up there with the John McClanes, the Rambos, the Bullitts. We get many films with great action heroes, but so rarely do we get great action films driven by character. John Wick and Keanu Reeves are two of the greatest gifts to action films, and to cinema in general. I’m just so happy to be alive while these films exist. At the end of each year, I like to do an action hero power rankings, and Reeves is far and away the top seed right now for 2017.
#Reviews#John Wick: Chapter 2#Keanu Reeves#Chad Stahelski#David Leitch#Common#Riccardo Scamarcio#Laurence Fishburne#Ian McShane#John Leguizamo#Tyler Bates#Joel J. Richard#Dan Laustsen#John Wick#Ruby Rose#Peter Stormare#Peter Serafinowicz#Lance Reddick
1 note
·
View note
Text
Career Pathing: How to Engage and Retain Talent with Technology
The business industry is changing on a global scale. In the race for higher ROIs, increased productivity, and lower costs, companies face significant challenges. This highly competitive environment keeps them on the toes 24/7.
The main issue is that almost all aspects of business operations now require modern, up-to-date approaches. Constantly rising customer expectations pose new demands, and mean that businesses must develop sustainable and purpose-driven HR brand.
Technological advancement is crucial to maintain sufficient business capacity and reduce costs. The changing nature of talent management also increases the stress on businesses.
Each new problem requires a unique solution. While this is partially true, there is one aspect which affects everything: your employees. They are essentially the engine of a business machine. However, you shouldn’t consider this engine to be a panacea. After all, business success is a cumulative notion.
Talent Market and Its Modern Challenges
In the era of automation, in which machines are replacing humans, the most serious problem is a shortage of talent. In fact, according to a ManpowerGroup’s Talent Shortage survey, the USA has been suffering from the effects of this talent shortage for the past decade. Almost every seventh employer struggled to fill jobs over this period.
The reasons for this can be different. High turnover rates, a poor HR brand, and considerable competition for skillful labor market representatives are just a few of them. All this makes HR executives search for working and preferably cheap methods to help them hire, engage, and retain employees.
The first step for recruitment and career path management is determining employees’ needs. Many people mainly focus on financial aspects – bonuses, reward systems, and higher salaries. This is undeniably important, yet overestimated. As the statistics from Gallup show, these financial incentives are relevant for only 12% of employees.
What are the real reasons why people reconsider their current occupations? Relying on data from Achievers, 43% claim career advancement, and 19% cite lack of recognition as the factors which caused them to move on. This illustrates that businesses must focus on promising career pathing and motivation. The latter has already been around for some time. Let’s take a closer look at career path meaning and how to make use of this concept.
Career Pathing Is the New Black in HR Realm
Considering that a good career path is important for almost 50% of employees, opportunities for growth within a company are becoming the new priorities for HR culture. Basically, career pathing means working out a structured worker development program. This helps employees to visualize their potential career growth within a company. Usually, it also includes any necessary competencies and milestones.
Such an approach has two main benefits for HR practices:
Enhanced Loyalty — The principle is simple: once you can clearly see the personal benefits of staying, you are willing to stay and work harder. This way, the working routine means more to employees than just an exchange of time for money.
Increased Motivation — If a person knows what exactly he/she needs to do to take another step up the professional ladder, he now has the motivation to work for it. What can be stronger than an inner eagerness to achieve more?
The approach is even more effective when you support your employees emotionally. This isn’t just limited to empathy. A company works out career pathways, taking into consideration individual preferences, sets of competencies and skills, experience, etc. This forms the basis for a custom plan. Once it’s ready, career path advice is then given. It’s not a one-time event. To retain and engage talent, an HR leader should constantly help, guide, and support an employee.
How to Work Out and Implement a Career Path Program
Businesspeople planning on a glass wall
The career path program doesn’t just benefit employees. Being a strategic approach, it has to fulfill particular goals. This is the first stage. You need to determine weak points.
These could be, for example, low productivity or high turnover rates. After that, you can adjust the program according to your needs. The current HR goals are the baseline, which literally shapes your ability to retain talent management.
Speaking about the process of the program development itself, it’s rather straightforward and involves four steps.
1. Plan Career Roadmaps
A roadmap for a particular job visualizes the journey from an entry-level position to an executive role. It encompasses both vertical and horizontal prospects and determines role changes. The cornerstone is basically a graph that illustrates opportunities within a certain area. For example, a regular HR officer will know that his career path choices will revolve around recruitment and training or the compensations and benefits sphere. However, the ultimate position to aim for is a job as an HR director.
2. Work Out Position Profiles
A position profile is a set of responsibilities, skills, and competencies necessary for a particular position. Such specifications outline the key vectors for further program development. They clarify the suitability of the candidate for a role.
This kind of method is efficient when it comes to recruiting as well. It clearly sets out exactly who you are looking for. Therefore, it contributes to quality hiring.
3. Set the Standards
Performance standards help to determine whether the skills and knowledge of applicants match the job requirements. In other words, if a person meets the standards, he will be able to carry out the job effectively. If s/he doesn’t meet these standards, you’d better look for another candidate or provide training.
The standards should include not only the required areas of competence but also all the necessary parameters. It’s a challenging task to come up with good standards. Many skills (especially soft skills) are hard to evaluate. What is more, unified parameters might not fit all individuals. You can rely on top performers as a benchmark. They have the practical experience and can share it, if necessary.
4. Determine Required Training
Each role is unique. The higher the position, the more qualified you have to be to attain it. It’s common practice to assign a training course. Even if an employee is competent enough, he hasn’t faced the role before (since you hire internally). This means that there is still space for him to improve.
As you can see, the process is rather straightforward. Nonetheless, working out the career path program manually poses many risks. These can vary from poor alignment of data to inconsistency in planning. This is where you can rely on software.
Technologies Is Key for Effective HR Activities
New technologies have never left the spotlight. In fact, one technological advancement directly triggers another. It’s an everlasting process, where automation powers automation. Some will say that there are still areas in which traditional methods are effective. Indeed, Fortuna Visual Group claims that traditional banner ads are still effective.
While this is true, the realm of HR is already on another level. Even its very roots – recruiting – are changing. For example, Sarah Johnston from Briefcase Coach claims that she uses LinkedIn to optimize hiring. She uses online keyword analytic tools, resulting in a 30-40% increase in LinkedIn search appearances.
The real power of automation in HR is down to corporate software that aggregates piles of data. It’s undeniable that advanced software deals with it faster and more effectively. Here are some problems which new technologies can solve:
1. Poor Data Management
Data-driven approaches to management have already proved their worth. Deep analytics delivers better results. It helps to determine weak spots. Businesses don’t need to spend precious time and resources on manually figuring out where a problem lies.
A platform that stores all the data together boasts many useful features. It includes analytics, which can be visualized in the form of diagrams and graphs. This saves time: thus, humans have more time to focus on more meaningful tasks.
What Are the Benefits for HR? The first and most significant benefit is more effective management. The platforms allow for the monitoring of personal progress and career development plans – you can also supervise the productivity of a whole department and even an entire enterprise.
This leads to data-driven development plans. You can spot any areas for improvement and work out changes. This helps to prevent many problems. One of them is a professional burnout. Excessive hard work and perfectionism can easily sabotage the entire career.
The system helps to track the number of working hours and reward or grant a vacation when a person works too much. If the platform has an integrated career pathing program, you can assign the required training. While the software is responsible for monitoring, communicating changes to employees is still a human duty.
Another advantage is that the software provides feedback on performance. According to a CareerBuilder survey, the vast majority of respondents – 81% – claim that this will improve their experience with an employer if done regularly.
2. Anticipating Weak Spots
Every mechanism has its strengths and weaknesses. It’s only reasonable to assess them in advance. Otherwise, a business might stumble upon a loophole, which could then undermine the whole operation.
Technologies are excellent when it comes to evaluation and assessment. You can create an employee’s profile with all the data. It includes their knowledge, skills, experience, etc.
Conduct a career path test to determine these things. After that, you can easily compare the results with the position requirements. It’s vital to remember that there is no ideal candidate. Everyone has weak spots. It’s an HR manager’s duty to spot them.
Since all the data is in one place, you can conduct regular check-ups. These could, for instance, be quick tests of employees’ competence. Another benchmark is performance. Once it falls, it’s time to set up training or consider another candidate for a position. All in all, you can identify the aspects to nurture easier and faster.
Business doesn’t always need an enterprise-level integrated solution. Technology can be implemented in more specific ways. For example, if your team doesn’t show the desired product, it’s time to consider investing in a productivity tracker. Some platforms have outstanding functions which help to maintain efficiency within a team.
3. Prospecting Career Mobility
Some researches show that employers fill their positions easier when hunting talent from other companies. This may sound ridiculous, as it’s always more efficient to utilize the existing resources. Some don’t see this as an option due to inner resistance to such practices. Others don’t have enough data to carry out an assessment. In fact, almost half claim that there are no established processes to identify and move employees around within an organization.
While companies are bound to hire new employees, employees who want to change their career paths are bound to leave: they sometimes leave even if they don’t want to.
Retain talent technology can help both. With detailed information and employee profiles, the software can spot those who will fit certain jobs. This means that if you have an unfilled position, you can launch an algorithm to find those who match the appropriate criteria.
As for the employees, they can determine which occupation is the most suitable for them, based on their set of skills and knowledge.
Such a data-driven approach allows you to keep a loyal worker and potentially identify a role in which he may perform better. Basically, it’s a win-win situation. In this context, you could consider technologies to retain talent best practices.
What Are the Benefits for Business?
Business measures every investment in terms of potential benefits – simply put, ROI. This isn’t always directly related to finance. Increased productivity, higher engagement, and employee satisfaction are the initial advantages. If you think about it from a wider perspective, all these aspects impact the business operations, and consequently, the profit. Let’s get into a detailed analysis of what business gains from implementing technologies in HR:
Reduced turnover rates — The software provides everything you need to fill any positions from the internal workforce. This is cheaper and more efficient. When hiring an outsider, a company has to spend time and money on training and development. And even after all that, a person may not fit in with your corporate culture.
Higher engagement — Career pathing powered by technologies outlines the way to the desired position. Milestones and rigid requirements keep your employees motivated and engaged. After all, every employee needs a goal to achieve.
More effective collaboration — Since you know the strengths and weaknesses of your employees, you can set up a more effective team. The principle is simple. The skills of one member must balance out the shortcomings of another.
Data-driven analytics and decision-making — Whether you are hiring, firing, or forming a team, a data-driven approach is a sign of quality. It means that your decisions have a solid foundation. Therefore, the risk of making a mistake is lower.
New technologies are, therefore, extremely effective tools in the world of HR. However, it’s vital to remember that the software alone won’t lead you to success. Humans must still do their part. Please leave your ideas in comments on how to retain and engage productive talent in our digitalized world.
The post Career Pathing: How to Engage and Retain Talent with Technology appeared first on CareerMetis.com.
Career Pathing: How to Engage and Retain Talent with Technology published first on https://skillsireweb.tumblr.com/
0 notes
Text
Audience Segmentation with Predictive Audiences | AI for All
We talk a lot about marketing challenges and, oftentimes, those challenges relate to marketers of certain maturities, industries, strategies, etc. But what is one universal challenge for all marketers? Audience segmentation. With our Predictive Audiences capability coming soon, Marketo Engage is transforming this fundamental piece of marketing in the most powerful way – through artificial intelligence. Predictive Audiences will be included in our Prime and Ultimate packages and available as an add-on for our Select package.
Audience Segmentation: The Great Balancing Act
Every marketer faces a similar dilemma with each program: reaching the most engaged and relevant audience and maximizing conversion without fatiguing the recipients and driving opt-outs. It’s critical to hit conversion goals but losing an audience member’s ear forever is hugely impactful and can take months or even years to repair.
But how can you reduce send lists while also reaching or even exceeding your goals?
With Predictive Audiences, you can confidently and intelligently target and engage the right people for your event and email campaigns to reach and exceed your goals without fatiguing your audience.
AI in B2B Marketing Today
Artificial Intelligence: still one of the buzziest buzzwords in the marketplace today. You hear about it all the time, but how has it affected your everyday marketing workflows? Do you feel like you have the opportunity to leverage AI in an effective and powerful way? Do you even have access to any AI today?
In fact, 66% of marketers want their AI applications to help them identify the right accounts and individuals to target, while only 18% of B2B marketers report having adopted AI-driven personalization according to “The State of Artificial Intelligence in B2B Marketing,” Demand Metric, 2019.
These contrasting statistics can largely be attributed to some of the barriers to entry of existing AI solutions such as difficult onboarding and implementation as well as high costs and the perception of steep learning curves. Without AI, marketers can still find innovative ways to strike the balance we talked about, but those ways are often resource-intensive, require constant tweaking, and produce little confidence that those efforts will pay off.
AI should be made available to everyone and should be easy to use and to adopt. This belief led us to develop Predictive Audiences, which makes AI available to everyone and part of everyday workflows! It also takes the manual effort and guesswork out of the equation – bringing a new level of efficiency to audience segmentation and targeting.
Let’s take a look at some of the ways you will be able to use Predictive Audiences and how it transforms everyday marketing fundamentals for all marketers and revenue strategies.
1. Maximizing Registrations and Attendance for Events
Crafting an invite list for live events and webinars is often more art than science. For those avid event marketers out there, you know the classic workflow:
Try to match an audience to the event topic based on marketing knowledge or just reuse an invite list
Hit send
Go into the event fairly blind on how many registrants will actually attend
Cross your fingers and host the event
With Predictive Audiences, we are infusing artificial intelligence into your existing workflow to give you the confidence and efficiency to reach the right audience for your events:
Use AI-powered by Adobe Sensei to build a highly targeted audience using Likelihood to Register and Likelihood to Attend Predictive Filters
Send your invites with confidence
Receive alerts when a goal is predicted to miss
Receive intelligent recommendations on how and what to adjust
Hit and exceed event goals
And, better yet, this is all embedded in your existing workflows – just drag these Predictive Filters into your Smart Lists and Smart Campaigns along with the multitude of other audience segmentation triggers and filters that Marketo Engage has to offer. And, voila! You have drastically increased conversions while reducing your overall send list.
2. Minimizing Opt-Outs
So, the first benefit we mentioned was all about reaching and exceeding your event goals while only inviting those who are most likely to register and/or attend. But that’s only part of the equation.
What if you could identify and suppress those users who are likely to unsubscribe? I can’t stress this enough – with a few simple clicks, you could leverage artificial intelligence powered by Adobe Sensei in existing workflows to maintain the health of your database and significantly reduce unsubscribe rates.
Don’t let this feature’s ease-of-use undermine how groundbreaking it is. This feature gives you the confidence to continue to engage customers while managing unsubscribes in a way that has never been possible before. In addition, you can use the Likelihood to Unsubscribe Predictive Filter to create and update a list of marketing suspended contacts to avoid engaging with those users across your instance. By not engaging those who are fatigued, you can drastically increase the lifetime value of each audience member by keeping them engaged at the right level and frequency.
3. Replicating Success from One Program to the Next
Oftentimes, the events you’re hosting are a part of a series. For example, you may be planning to create a new, ongoing webinar series that is designed to onboard new users to your product. Instead of just rolling it out and hoping for the best, you decide to pilot it with a small subset of users. And the pilot was a great success!
Instead of spending hours looking for similarities amongst the attendees to see why it was successful to then replicate for the rest of the series, Predictive Audiences will find a lookalike audience based on a Smart List or Smart Campaign. Once again, within your existing audience segmentation and targeting workflow within Marketo Engage, you can easily add an additional filter to find similar audience members to those in a defined Smart List or Smart Campaign. With this feature, you can significantly reduce time to value for your program creation, bringing new levels of efficiency to your marketing workflows.
4. Optimize In-Flight with Intelligent Recommendations
We are making set-it-and-forget-it event programs a thing of the past. Even if you are closely monitoring registration for your event program, you never really know with any confidence where you will land in terms of registration, and you certainly have little to no insight into what attendance to expect.
Predictive Audiences lets you: 1) track progress towards your goals in real-time 2) predict outcomes and 3) provide intelligent recommendations based on similar, historical programs and your unique goals. You can even track the likelihood of individual members to register and attend your event. No longer are the days of seeing your event program falling short of your goals with no idea what to do to improve it. Optimize in-flight efficiently and with confidence to accelerate buyers through the funnel and accelerate pipeline.
Artificial Intelligence for All
With Predictive Audiences, you can leverage the power of artificial intelligence in an accessible, fundamental, and easy-to-use way to drive results with little to no onboarding or implementation efforts required. In conjunction with Predictive Content and Account Profiling, Marketo Engage offers AI-powered tools for content, ABM, and now spans across foundational, everyday marketing workflows through Audience Segmentation with Predictive Audiences.
Stay tuned for more as we gear up to launch this exciting capability soon.
The post Audience Segmentation with Predictive Audiences | AI for All appeared first on Marketo Marketing Blog - Best Practices and Thought Leadership.
from Marketo Marketing Blog https://adobe.ly/2NfyTjr via IFTTT
0 notes
Text
Links 3/18/19
Patient readers, we just this instant switched on the codes for a new advertising vendor. A very much unintended and unexpected side effect is that some of you may be seeing video and other pop-ups. We were very clear in that these types of ads were not allowed. We are working to make them go away as fast as we can, because we know how much you hate them (and we do too)! –lambert
Update by Yves: The site seems to load faster with the new ads (the ads were what would slow down loading times), so once we get the popups sorted out (which thank God are appearing only on the landing page and so aren’t interfering with reading articles), this should be a net plus to readers once we get past transition issues.
Stonehenge-like monuments were home to giant pig feasts. Now, we know who was on the guest list Science
What’s the cost (in fish) between 1.5 and 3 degrees of warming? Anthropocene
Home Of Strategic Command And Some Of The USAF’s Most Prized Aircraft Is Flooding (Updated) The Drive
Radical plan to artificially cool Earth’s climate could be safe, study finds Grist
Fire Breaks Out At a Houston-Area Petrochemicals Terminal Bloomberg. Second in a week. Video:
The heat is deforming this metal storage tank. Some of the first responders are worried it will collapse. pic.twitter.com/Y3ZsjJ96zj
— Respectable Lawyer (@RespectableLaw) March 18, 2019
Leave the oil in the ground, and this doesn’t happen…
The Fed has exacerbated America’s new housing bubble FT
Churches are opening their doors to businesses in order to survive CBS
Some county treasurers have flouted Iowa gift law for years Bleeding Heartland
Corporations Are Co-Opting Right-To-Repair Wired
Brexit
What will it take to push May’s Brexit deal over the line FT. The arithmetic: “To overturn her 149-vote deficit, she would have to win over at least 75 MPs. The most plausible route starts with the DUP’s 10 MPs. If they backed her deal, then some 50 of the nearly 70 Tory Eurosceptics who voted against it last week may change sides. Then Mrs May would need a further 15 Labour MPs, in addition to the five Labour and former Labour MPs who backed her last week.”
Northern Ireland’s farmers urge DUP to back Brexit deal FT
Around 40 Tory Rebels Told Theresa May: We’ll Vote For Your Brexit Deal If You Quit Buzzfeed
Labour likely to back public vote on UK PM’s deal, says Corbyn Reuters
Brexit by July 1 unless UK votes in EU election: Document Politico
The Irish Backstop: Nothing has changed? It has actually (PDF) Lord Bew and Lord Trimble, Policy Exchange. Bew is a Professor of Irish Politics. Trimble is a former First Minister of Northern Ireland and a winner of the Nobel Peace Prize. Well worth the clickthrough to read the entire PDF. Here is the final paragraph:
All of this suggests that a backstop that functions for more than a short period of time – and the DUP has indicated in Parliament that it could live with a short backstop – is likely to be an extremely unstable affair. If it does not negotiate a trade deal with the UK in the next year or so, the EU is also likely to become increasingly aware that the Protocol will give it nothing but grief as it gets sucked into the Northern Ireland quagmire. In this quagmire, the UK Government (which has the support of the majority of the population in Northern Ireland and which pays the subvention which subsidises the entire society), holds most of the cards.
Politico’s London Playbook calls their report “a ringing endorsement of the tweaks to the backstop agreed by Theresa May in Strasbourg this month.” Readers?
NORMAN LAMONT: History will never understand Tory MPs if they kill off Brexit Daily Mail
Brexit will mark the end of Britain’s role as a great power WaPo. Surely Suez did that?
Macron calls for ‘strong decisions’ after violent Yellow Jacket protests Politico
Among the Gilets Jaunes LRB
Syraqistan
Months after saying US will withdraw, now 1,000 troops in Syria to stay Jerusalem Post but US denies report it is leaving up to 1,000 troops in Syria Channel News Asia. And what about the mercs?
Saudi Crown Prince’s Brutal Drive to Crush Dissent Began Before Khashoggi NYT
A Palestinian Farmer Finds Dead Lambs in His Well. He Knows Who’s to Blame Haaretz
Algeria After Bouteflika Jacobin
North Korea
Investing in resource-rich North Korea seems like a good idea — but businesses find there’s a catch Los Angeles Times
Picking Up the Pieces After Hanoi Richard Haass, Project Syndicate
New Cold War
How ordinary Crimeans helped Russia annex their home Open Democracy
How Russia Gets To Build Its Most Controversial Pipeline Riddle
Trump Transition
The Pentagon’s Bottomless Money Pit Matt Taibbi, Rolling Stone. How are they gonna pay for it?
Government withholds 84-year-old woman’s social security, claims she owes thousands for college WISH-TV
737 Max
Flawed analysis, failed oversight: How Boeing, FAA certified the suspect 737 MAX flight control system Seattle Times
737 MAX disaster pushes Boeing into crisis mode Phys.org
Big Brother Is Watching You Watch
All the Crime, All the Time: How Citizen Works NYT
Global Mass Surveillance And How Facebook’s Private Army Is Militarizing Our Data Forbes
More Than a Data Dump Harpers. Why Julian Assange deserves First Amendment protection.
Democrats in Disarray
Establishment Democrats Are Undermining Medicare for All Truthout. As I kept saying with my midterms worksheets, the liberal Democrat leadership’s #1 priority is to prevent #MedicareForAll, and to that end they shifted the center of gravity of the electeds against it. Now we see this strategy born out in falling sponsorship numbers.
Even a Vacuous Mueller Report Won’t End ‘Russiagate’ Stephen Cohen, The Nation. “[T]he Democrats and their media are now operating on the Liberty Valance principle: When the facts are murky or nonexistent, ‘print the legend‘.”
Venture capitalist Steve Case spreading funding to Middle America with “Rise of the Rest” CBS
Class Warfare
What’s Wrong with Contemporary Capitalism? Angus Deaton, Project Syndicate
Bill McGlashan’s firing exposes hypocrisy in impact investing Felix Salmon, Axios
The College Admissions Ring Tells Us How Much Schoolwork Is Worth New York Magazine
How Parents Are Robbing Their Children of Adulthood NYT
‘Filth, mold, abuse’: report condemns state of California homeless shelters Guardian
Wall Street Has Been Unscathed by MeToo. Until Now. NYT
What the Hell Actually Happens to Money You Put in A Flexible Spending Account? Splinter
‘Super bloom’ shutdown: Lake Elsinore shuts access after crowds descend on poppy fields Los Angeles Times. “Desperate for social media attention, some visitors have trampled through the orange poppy fields, despite official signs warning against doing so.” Thanks, influencers!
Antidote du jour (via):
See yesterdays Links and Antidote du Jour here.
This entry was posted in Guest Post, Links on March 18, 2019 by Lambert Strether.
About Lambert Strether
Readers, I have had a correspondent characterize my views as realistic cynical. Let me briefly explain them. I believe in universal programs that provide concrete material benefits, especially to the working class. Medicare for All is the prime example, but tuition-free college and a Post Office Bank also fall under this heading. So do a Jobs Guarantee and a Debt Jubilee. Clearly, neither liberal Democrats nor conservative Republicans can deliver on such programs, because the two are different flavors of neoliberalism (“Because markets”). I don’t much care about the “ism” that delivers the benefits, although whichever one does have to put common humanity first, as opposed to markets. Could be a second FDR saving capitalism, democratic socialism leashing and collaring it, or communism razing it. I don’t much care, as long as the benefits are delivered. To me, the key issue — and this is why Medicare for All is always first with me — is the tens of thousands of excess “deaths from despair,” as described by the Case-Deaton study, and other recent studies. That enormous body count makes Medicare for All, at the very least, a moral and strategic imperative. And that level of suffering and organic damage makes the concerns of identity politics — even the worthy fight to help the refugees Bush, Obama, and Clinton’s wars created — bright shiny objects by comparison. Hence my frustration with the news flow — currently in my view the swirling intersection of two, separate Shock Doctrine campaigns, one by the Administration, and the other by out-of-power liberals and their allies in the State and in the press — a news flow that constantly forces me to focus on matters that I regard as of secondary importance to the excess deaths. What kind of political economy is it that halts or even reverses the increases in life expectancy that civilized societies have achieved? I am also very hopeful that the continuing destruction of both party establishments will open the space for voices supporting programs similar to those I have listed; let’s call such voices “the left.” Volatility creates opportunity, especially if the Democrat establishment, which puts markets first and opposes all such programs, isn’t allowed to get back into the saddle. Eyes on the prize! I love the tactical level, and secretly love even the horse race, since I’ve been blogging about it daily for fourteen years, but everything I write has this perspective at the back of it.
Post navigation
← Electronic Health Records: Death By A Thousand Clicks Report from the Ground in Paris: The Most Recent Gilets Jaunes Protests →
Source: https://www.nakedcapitalism.com/2019/03/links-3-18-19.html
0 notes
Text
How Ermanno Olmi Found Grace in the Daily Labors of Italians
Ermanno Olmi’s first fictional feature, “Il Posto,” shown at the Venice Film Festival in 1961, was released in the United States two years later with the incongruously noisy title “The Sound of Trumpets.” That name doesn’t entirely come out of nowhere; it echoes a phrase uttered by the mother of the main character, Domenico Cantoni, a young man starting out at the very bottom of a large Milanese firm and hoping to rise to the lower middle. If he stays up too late reading, she warns him, not even trumpets will wake him in time to get to his job.
In Italian, “Il Posto” more or less means “The Job,” but the faint biblical echo (of Jericho, of Judgment Day) in the English version isn’t entirely out of place, even though the film itself is notably quiet and gentle. If there is drudgery in store for Domenico, there is also music and subtle but striking intimations of divine grace.
Olmi, who died last year at 86, was drawn to the contemplation of work, to the rituals and routines of mid-20th-century clerks and welders, late-19th-century tenant farmers and early-16th-century soldiers. The marvelous retrospective that starts Friday at Film at Lincoln Center reveals a career and a sensibility at once wide-ranging and consistent. Olmi’s movies can be lyrical and impishly funny, passionate and scholarly, observant and impassioned. He had a documentary photographer’s eye for the specific and a painterly sense of composition. He retold Bible stories and directed literary adaptations.
The closest thing he made to an action movie, about Giovanni de’ Medici, who served the pope in the Italian Wars of the early 16th century, is called “The Profession of Arms,” and its depiction of early modern warfare includes a lot of meetings and paperwork. (A new digital restoration of this rigorous and ravishing film, shown at Cannes in 2001 and never released here, is a highlight of the 20-title Lincoln Center program.)
What links de’ Medici’s cavalry campaigns with Domenico’s desk-jockeying isn’t only the drudgery and occasional absurdity of the work, nor the often inscrutable nature of the cause it serves. (What does this enormous, highly regimented company actually do? Why is the pope at war with the German emperor? Such questions are above our heroes’ mortal pay grade, and our own).
Domenico, the oldest son of a small-town, working-class family who barely looks old enough to shave, is wary and diffident, equally flummoxed and fascinated by the ways of the adult, urban world. De’ Medici, the scion of an aristocratic line, is charismatic and decisive, a figure of legend among his contemporaries even before his death, at just 28, from a battlefield wound. Both men are oppressed by their responsibilities, and also brought alive by their devotion to duty. It’s not so much the labor itself. De’ Medici slogs through mud and snow in pursuit of his enemies. Domenico aspires to ascend from assistant messenger to junior pencil pusher. No, it’s the way submission to the work’s demands becomes a kind of spiritual discipline.
Olmi turned the prose of toil into poetry. If he is often, and correctly, classified as a next-generation neorealist — partial to nonprofessional actors, documentary techniques and everyday settings — his was a realism especially attentive to the ecstatic dimensions of quotidian experience. Formal religion is part of that experience, and so is politics. These are Italian movies, after all, directed by a man who came of age in the postwar ideological crucible defined by the Communist Party and the Catholic Church. Those institutions didn’t just influence Italians’ voting habits and social mores in the decades between Mussolini and Berlusconi; Marxism and Catholicism were cultural and aesthetic forces as well, integral to the language of Italian cinema in its boom years.
“Il Posto” is a product of that boom, and a landmark of 1960s cinema, latent with the rebellious impatience and irreverent energy that would ripple across every continent. Like the protagonists of “Billy Liar” and “The Graduate,” Domenico, played by the wide-eyed nonprofessional Sandro Panseri, seems imprisoned by a set of social expectations enforced by parents, bosses and the very architecture of his world. The first part of the film follows him through recruitment and what we would now call onboarding. Along with other candidates, he takes a written and physical examination, and then makes his way through a Kafkaesque series of corridors and waiting rooms.
But he is not just a rat in a maze. “Il Posto” is less a study in misery than an examination of a soul’s progress across a plane of existence that combines elements of inferno, purgatory and paradise. Domenico buys a new raincoat. He also meets a young woman named Antonietta (Loredana Detto, Olmi’s future wife), who is part of his entry-level cohort. On the day of the tests, they take advantage of the long lunch break that is a pillar of Italian civilization to drink espresso at a busy coffee bar and wander in a park. They are scolded for running on the grass, a singular moment of transgression in a film marked by good behavior.
Like the peasants in “The Tree of Wooden Clogs,” Olmi’s 1978 masterpiece, which won the Palme d’Or at Cannes, Domenico and Antonietta find pleasure and even something like freedom within their highly constrained circumstances. “Wooden Clogs,” populated by real-life farmers and agricultural laborers rather than actors, has been accused of taking a nostalgic view of the cruelties of feudalism. Its stately pace and sensual images — it’s set in Olmi’s native region of Bergamo in northern Italy — do impart a sense of beauty, and there is a conservative aspect to Olmi’s evocation of family ties and rural folkways.
But there is also a palpable sense of injustice and strong currents of political disaffection. Power in the countryside and in the industrial city is organized in such a way as to undermine the dignity, curtail the pleasure and constrict the freedom of workers. Political action is one response to this situation, but Olmi’s Christian humanism, while hardly apolitical, points him in a different direction, toward the ineradicable dignity of the individual and the startling beauty of creation.
“Il Posto’s” Domenico intuits this, and the magic of Olmi’s realism is that we do, too, and don’t despair for the young man’s prospects. The movie generated a sequel of sorts, a short feature called “The Fiancés” that I saw for the first time at Lincoln Center and that hit me with the force of a revelation. “Il Posto” ends at a company holiday party, with dancing and forced but genuine merriment. Its successor begins with a similar scene, at a blue-collar dance hall where Giovanni, a metal worker, has gone on a date with his girlfriend, Liliana.
They are older than Antonietta and Domenico, and wearier — of their lives and maybe of each other. Work is both their trial and their salvation. Giovanni (Carlo Cabrini) has a chance to help build a new factory in Sicily, an opportunity that offers a boost in income and status at the cost of months of separation from Liliana (Anna Canzi). He finds loneliness, local color, alienation and intermittent satisfaction — an array of unspectacular modern experiences that Olmi renders with an intensity that never feels overstated.
What keeps you engaged isn’t a plot so much as an intellectually and emotionally awakened sense of what it is to be alive. The film reveals itself, in the end, to be a love story of a conventional and also a miraculous kind. It’s the tale of a working man in love, and it’s the testament of a man who loves his work.
“Ermanno Olmi” begins Friday at Film at Lincoln Center. For more information, go to filmlinc.org.
Sahred From Source link Arts
from WordPress http://bit.ly/2R8Hbe6 via IFTTT
0 notes
Text
MÅLSMAN™, Entry Into the Defense Industry and Solutions to Complex Issues by creator and designer, McCalla, Christine Ann
Abstract
The main objective of this article is to present the framework required for a new entrant into a competitive environment, defense, regulated with the expectations of preventing harm to a significant populace, the international community. This framework also presents challenges and barriers present within this competitive environment and strategic solutions regarding their resolutions. There also designs and methodologies such as cost and production management available that when utilized create expectations that expertise can be acquired within the project management process, as well as the attainability of sustainability. There are also correlationships and relationships present that when applied create strategic competitive advantage. This is in addition to the various approaches to complex problems that can be made available through knowledge management. The practical implications are awareness of the competitive requirements is a key expectation to strategic planning and management, particularly for entry to a new and dominant market with international watchdogs present. There is also the matter of cost effective conflict resolutions available through the avoidance of fines and sanctions, as well as full and complete recovery of revenues generated through appropriate knowledge of computations associated with said recovery.
Keywords: defense industry, weaponry, quality assurance, manufacturing, supply chain
Introduction
The decision to capitalize on abilities in the creation intellectual properties such as patents and copyrights of weaponry of defense, offense, and protection, is as significant as the actions taken to retain them into infinity. There are numerous strategic planning decisions to be made including, compliance processes required; regulations and related statutes; and, regulatory agencies to be cognizant of and their roles. There are also the presence of competitors, brand, and reputation management. Product homogeneity does not equal profitability simply on the basis of product differentiation. Accounting and costing methodologies matter and not just for certification processes, but also for sustainability and intellectual property preservation.
Keyword Search
Keyword searches were executed within ProQuest Central database, including searches for scholarly, peer-reviewed articles. The keywords were derived as implications from the assignment. Keyword terms searches were, features and defense industry; weaponry and defense industry; weapons manufacturing and defense industry; defense supply chain; evaluate stages and quality assurance and delivery; evaluate stages and resources and labor and costs. Additional searches were executed within the Statista database for data relevant to the defense industry, using keywords defense dossier; arms export; and defense competitors.
Fully describe the features of the product Schilde (2015) argued the entrepreneurial potential for the entry of defense as a product, in which there has been substantial growth in over the last two decades, the market for private, civilian force (private, civilian national security expertise) has become as a complementary tool to state military force. Schilde (2015) also argued the contracting of civilians for military operations has been a phenomenon institutionalized by the Defense Base Act of 1941 requiring U.S. contractors and subcontractors to report civilian (and foreign) employee casualties to the Department of Labor with acceleration in military personnel from contractor ratio of 50:1 military personnel to contractors in the 1991 Gulf War to 10:1 in Iraq in 2005. Schilde (2015) also addressed the general concern for the reliance on quasi-privatization of military contracting as, the rise in the private market can undermine constitutionalism and democracy by bypassing veto points and formal governmental involvement; and, centralizing power in the branch of government writing the contracts and delegating its foreign policy to private actors. MÅLSMAN™ can execute risk management through participation within the defense industry utilizing Interpol’s commercial infrastructure; being cognizant of the applicable regulations; regulatory bodies; and, the various impacts and consequences.
The product being manufactured is a portfolio / product mix of defense infrastructure under the name brand, MÅLSMAN™ (swedish for guardian, pronounced moolsman). The MÅLSMAN™ product line being sold were selected as complementary to each other, and multipurposed, for sale and service as government contracting services - direct sales, sales and services to other licensed government contractors private security firms, and on a lease basis to emergency search and rescue corporations. For security, compliance, and licensing reasons, these arrangement will be conducted using international law enforcement agency, Interpol.
MÅLSMAN™ defense infrastructure of aircrafts; missiles and missile systems; armored vehicles; and air defense systems, capable of individual product line use or as a comprehensive system. MÅLSMAN™ aircrafts is comprised of sophisticated aircrafts, (Ross, 1990); Villa and Viggiano’s (2012) Sukhoi Su-30MK fighter aircrafts, MI-35 combat helicopters, Mi-17-V multitasking transport, Mi-26 heavy transport helicopters, Su-35 and Su-39 combat aircraft; the An-74 cargo aircraft; the II-76 and Mi28 combat helicopters. MÅLSMAN™ missile and missile systems, manned and unmanned including ballistic missiles and silos, (Ross, 1990); Villa and Viggiano’s (2012) AIM-9M Sidewinder, AIM-120 AMRAAM, Harpoon and Sea Sparrow missile arsenals, Python and Derby missiles, and, smart bombs of various calibers.
MÅLSMAN™ armoured vehicles include battle tanks, armored personnel carriers, and wheeled tank destroyers, (Ross, 1990); and, Villa and Viggiano’s (2012) wheeled or tracked armored troop carriers. MÅLSMAN™ air defense systems, popular products within the armed market and defense industry according to Ross (1990). Villa and Viggiano’s (2012) ground-air Tor-M1 missile system, radars, NASAMS, and 40 8x8 armored Stryker. D'yachuk, Orkin, and Orkin’s (2011) interactive automated system including aircraft carrier multipurpose groups, tactical aviation, and air weaponry, planning, and simulation mathematical models for attacking naval groups. Relevant clearance levels and licenses are required to participate in the purchase, lease, or negotiation of any of these products. There is also strong demand for these product, and it is anticipated that MÅLSMAN™ will gain a significant market share based on the technical expertise of the owner, management team, customer responsiveness, and technological advancement of the products.
Fig 1 - U.S. arms exports 2017, by weapon category (in TIV expressed in million constant 1990 U.S. dollars) (excerpt from Defense spending and arms trade dossier, page 68, SIPRI ID 248561)
Golde and Tishler (2004) argue strong military powers deem as a must-have, state-of-the-art technological know how and economic wherewithal to secure said infrastructures as well as the development of sophisticated weapons systems. Due to constraints related to socio-economic and political systems, few regions are capable of meeting said needs limiting the competitive landscapes to Western Europe and the United States of America, (Golde and Tishler, 2004). Golde and Tishler (2004) also argued that one such constraint is a defense system, with the defense structure also playing signficant roles within the competitive landscape including by nations; economic growth; regional and national race; access to arms import and export; interrelationship and interactions between security and economic conditions; and, the various models of international arms trade. Given the limitation within the competitive landscape, the major threat remaining is espionage given the limited number of actors within the landscape and the size of the client / market share.
Fig 2 - U.S. arms exports 2017, by country (in TIV expressed in million constant 1990 U.S. dollars) / (excerpt from Defense spending and arms trade dossier, page 65, SIPRI ID 248552)
Defense spending and arms trade dossier (fig 2) presents U.S. arms exports value for 2017, showing a substantial market with buyers such as Saudi Arabia, Australia, United Kingdom, Israel, and Iraq being major actors. MÅLSMAN™ products will be sold to these nations and other willing buyers licensed to transact business in this market. Furthermore, the MÅLSMAN™ product line will assist in Bachar’s (2017) Qualitative Military Edge (QME) as defined by Naval Vessel Transfer Act (NVTA) of 2008. This is the ability to counter and defeat any credible conventional military threat through the use of superior military means including weapons, intelligence, surveillance, and reconnaissance capabilities superior to those of such other individual or possible coalition of states or non-state actors, Bachar’s (2017).
Sokolov (2005) argued one feature of MÅLSMAN™ products, making ordinary citizens feel secure and making an impression on potential adversaries through MÅLSMAN’s™ strategic vision of securing life, living, and zest through the defense of country, mankind, and holdings. Sokolov (2005) also argued that countries lagging in the production of advanced weaponry have a substantial weakness and consequently, the government may resort to extraordinary mobilisation measures in order to modernize and increase production of weapons and munitions. Another feature of MÅLSMAN™ products, is to support defense policies and government policies through its product line offering. Sokolov (2005) also presented theory on defence industry complex, categorized as armaments and classified into three groups of varying technological proximity to civilian industry; the first group, most remote from civilian production, would be allocated to specialised military factories: small arms and ammunition, gunpowder, explosives and poison gas, mortar shells, and so on. The second group was closer to civilian industry; it is comprised of field and naval guns, shipbuilding, aviation, tanks, military optics, and radio communications. The third group, comprising electrical equipment, transport and communications equipment, instruments, personal kit and ration stores, was closest to civilian goods and could be allocated to civilian producers without detriment to defence interests (Russell’s, 2011 value chain / demand chain). Given that MÅLSMAN™ product line of aircrafts; missile and missile systems, manned and unmanned; armoured vehicles; and, air defense systems fits into the Sokolov’s (2005) second and third groups, the viability and feasibility of the MÅLSMAN™ product line is assured.
Oprean (2012) argue that government and states protect substantial resources including the economic; financial; scientific and human resources; and describes features of weaponry, combat techniques, military equipment, new combat methods and procedure, army organisation; and the development of new strategic conceptions and military doctrine of avant-garde. Oprean (2012) presented main features exemplifing the development of all conventional; nuclear; cosmic categories of weaponry and combat technique of mass destruction; intelligent munitions; and, employment of information and cosmic technology in these environments. Given the urgency and dire need for the protection of nations and governments, Oprean’s (2012) features are also features of MÅLSMAN™ product line, summarized as strategic and intelligent defense conceptions and sophisticated weaponry.
Oprean (2012) also described necessary features of defense such as enhancement of armies’ mobility and their capability of deployment; exercising the control on relative distant forces; development of communication means and troops’ movement consisted in enhancement of top control, materialised in a continuous development of information requests towards subordinates; maintainance of heirarchy and structures; opportunity for troops’ response and the risks to which the subordinates are exposed and they assume; reduce the uncertainty of imperative requirement of commanders and staff of operational or strategic headquarters of joint forces; actualize the freedom of action within the battlespace, including the commanders’ initiative and agility of tactical headquarters; and, timely discovery of location and capabilities of all force elements, including individual and weapons. The MÅLSMAN™ product line will be capable of these responses summarized as mobility, deployment, and control features and elements.
Evans (1996) defined a leadership system focused on customers and performance excellence, with leadership practices that promote quality and high performance. Evans (1996) leadership systems attributes are (fig 3), create a strategic vision and clear quality values serving as the basis for all business decisions at all levels with vision and values including the promotion of said vision; setting high expectations; demonstrate personal commitment to quality; integrate quality and values in daily leadership and management; and, sustaining environment for quality excellence.
Fig 3 - Evans’ (1996) leadership system and attributes
Strategic vision
Securing life, living, and zest through the defense of country, mankind, and holdings
Promote vision
Electronic communications, strategic planing and management, meetings, electronic mail (email); online videos, talks, and exhibits
Setting high expectations
Utilize stretch goals - elimination of defects through zero defects management systems; obtain payback in 4.5 years; generate 47% profits after year 6
Demonstrate personal commitment to quality
Apply cross-functional teams using organization tools including calendar, performance measurement metrics, correspondence with clients; quality assurance reviews
Integrate quality and values in daily leadership and management
Achieve cohesion through the use of strategic plans; managers are expected to improve quality management processes; include employees in quality assurance and quality management process through the use of surveys; communicate and reinforce organizational quality values to the entire organization; and, promote quality standards
Sustaining environment for quality excellence
Encourage open-door policy; facilitate collaboration and teamwork; encourage problem solving through group settings
Golde and Tishler (2004) describes security as the difference between the country's stock of weapon systems and its rivals' stock of weapon systems. There is also the efficiency in the usage of weaponry driving the laws of supply and demand, (Golde and Tishler, 2004).
Fig 4 - Golde and Tishler (2004) defense industry framework
Analyze the manufacturing stages of your productIon analyzing the manufacturing stages of MÅLSMAN™ product line
Ross’ (1990) five (5) stages of manufacturing within the defense industry have been previously applied. Bengü and Kara (2010) also provided the product life cycle’s four (4) stages of manufacturing, product idea or concept stage, design and improvement stage, manufacturing stage and logistic support stage. Bengü and Kara (2010) provided four (4) stages of marketing, market introduction (product planning is made and the manufacturing is then introduced. This stage is related to the market environment, economy, style, utility and expected life of the product. Manufacturing increases and production distribution is limited with high marketing costs. Sales increase slowly and deficiencies and defects are corrected); growth (product adapted by buyers, sales increase due to buyer participation, profits increase due to relationship of incomes exceeding costs, manufacturing and product quality increases with increase in product portfolio, brand image constructed with promotional and advertising, difficult for company to choose between percentages of high market share and profitability); mature (longest and most important stage of product life cycle as sales are at its highest amounts. At the end of this stage, sales fall. Manufacturing style is mass production, probable constrictions in manufacturing along with changes in distribution channels. The result is high competition and increasing costs, and declined profitability); and, saturation and decline stages (new product entries observed with accompanying sales increased. For existing products, sales decline with resulting decrease in production. Manufacturing costs are inverted to sales price, with manufacturing costs increasing with price of product decreasing. Distribution channels are straitened, with promotional and advertising costs decreasing). A supply chain must be created through collaboration of designers, suppliers, and customers, including inputs and outputs, value-added services, managing customer needs, and a feedback cycle that connects measurement of customer satisfaction and product and service attributes, (Jambekar and Pelc, 2006).
Ross (1990) defined five (5) stages of manufacturing within the defense industry, prefabricated components imported and assembled in country; actual production of licensed agreement of foreign supplier; complete foreign design weapons under license; modify, redesign, and produce foreign weapons; and, domestically designed arms are produced. Jambekar and Pelc (2006) argued that new technological initiatives should be mapped into three-dimensional space governed by a hierarchy of business units and operations with a cybernetics perspective with fundamental survival functions of transformation, information, measurement and coordination. Jambekar and Pelc (2006) also argued the cycle should begin with the marketing function and extends all the way into service functions (Bengü and Kara, 2010). To successfully execute mass customization, skilled, knowledgeable and autonomous workers, modular processes and products, management coordination and configuration of modules are needed to meet customer specification, (Jambekar and Pelc, 2006).
Bengü and Kara (2010) contributed to the discussion regarding the manufacturing stages using costing concepts methodologies such as activity based costs (ABC), just-in-time (JIT) manufacturing system, product life cycle costing, and total quality costing. Bengü and Kara (2010) also argued that product life cycle costing has been used the Department of Defense of the United States to increase efficiency in armament. It is also a costing methodology aimed at assisting both producers and consumers to forecast and manage costs of a product during its life cycle. Bengü and Kara’s (2010) product life cycle is more than a costing methodology; it is a mechanism to manage costs while also monitoring the relationships of product mix, marketing, sales, branding, profits, and production.
Assess operations concepts and the supply chain process until the product reaches the customer Jambekar and Pelc (2006) argued knowledge management and its related decision metrics managing performance such as defect reduction (fig 3), customer satisfaction, customer retention, and market share resulting in Russell’s (2011) organizational interconnectivity in terms of a supply chain. Russell (2011) assesses operations concepts and the supply chain process until the product reaches the customer as an integration of key business processes up and down the supply chain creating supply chain management, applying resources such as problem solving, innovation, collaboration (underpinning of supplier management - upstream, and customer relationship management - downstream, with information technology being the glue holding the supply chain together, fig 5 and fig 6.
Fig 5 - Russell’s (2011) assessement of MÅLSMAN’s™ operations concepts and the supply chain process until the product reaches the customer as an integration of key business processes
Fig 6 - Russell’s (2011) supply chain definition
Jambekar and Pelc’s (2006) elements of business ecosystem is used to assess operations concept and the supply chain process until the product reaches the customer, (fig 5).
Fig 7 - Jambekar and Pelc’s (2006) elements of MÅLSMAN’s™ business ecosystem being used to assess operations concept and the supply chain process
Enterprise
Large; strong R & D group; mass manufacturing; highly flexible production program, international manufacturing networks (Szwejczewski, Sweeney, and Cousens, 2016); standard and customized products and installations
Comparable competitor
Boeing Company; large size; similar products including homogeneity; similar flexibility including products and customization; location USA
Competitors
Boeing Company
BAE System
Lockheed Martin
Regulations, norms, and mores
Regulating Agencies
Arms-trade watchdog the Stockholm International Peace Research Institute (SIPRI), Reuter (1991)
Standardization Agreement (STANAG), Bojnec (2013)
American National Standards Institute (ANSI), Bojnec (2013)
Bojnec’s (2013) STANAG and ANSI are security and defence standards, and used for similar products and services in defence industry supply and marketing chains. Bojnec’s (2013) STANAG and ANSI prescribe characteristics with which products should comply, as well as ways for testing them.
Naval Vessel Transfer Act (NVTA) of 2008, Bachar (2017)
Arms Export Control Act (AECA), Bachar (2017)
Defense Base Act of 1941
United Nations
The Hague - The Criminal Court
U.S. Department of Defense
Defense threat / conflict groups
Hezbollah, HAMAS, Jihad, al-Aqsa, Martyrs' Brigade, and e Popular Front for the Liberation of Palestine-General Command
Suppliers
Pressure sensors manfacturer/supplier, Jambekar and Pelc (2006)
Temperature sensors manufacturer/supplier, Jambekar and Pelc (2006)
Customized electronic circuit supplier, Jambekar and Pelc (2006)
Precision mechanics supplier, Jambekar and Pelc (2006)
Electronics infrastructure supplier, Jambekar and Pelc (2006)
Computing systems supplier, Jambekar and Pelc (2006)
Engineering products service provider, Jambekar and Pelc (2006)
Electrical accessories supplier, Jambekar and Pelc (2006)
Instrument casing supplier, Jambekar and Pelc (2006)
Complementors
Metal producer
Laboratories and simulation manufacturers and providers
Distribution channels
International representatives
Direct delivery systems
Customers
Nations including Saudi Arabia, Australia, United Kingdom, Israel, and Iraq
United States Department of Defense
Other licensed international agencies
Another methodology to assessing operations concepts and the supply chain process until the product reaches the customer, is Chapman, Bernon, and Haggett’s (2011) selection of appropriate quality management techniques. Chapman, et al’s (2011) techniques are, (1) develop strategies (focus on delivery time variability through appropriate supply chain process designing through the use of process chart/flow chart, histogram, and cause and effect analysis); (2) identify key processes (the order to delivery cycle in defense is similar to commercial / industrial processes, with the focus being the supply chain performance of customer places order, order entry, order processing, transportation, and order received); (3) analyse existing processes (including performance measurements and modification); (4) redesign processes (to achieve appropriate responses and outcomes); and (5) implement new processes (through evaluation of existing processes and address disparaties including the development of acceptable norms in performance).
The operations concepts and supply chain process intersects and interact through the use of Chapman, et al’s (2011), providing simple mechanisms toward easy understanding of current works, methods, and practices; encourage communication and discussion; and, the provision of visual means to inputs from those not initially involved in the documentation process. As an integrated framework, both components provide navigation and clarity for project management, necessary for flexible, mass, and project management manufacturing including customizations particularly in a massive operation such as defense manufacturing.
The function of operations concept and supply chain is to enhance operations through the numerous relationships created and their interdependence including suppliers, customers, and regulators. VanVactor (2011) argues collaboration refers to the cooperative supply chain relationships forged, both formally and informally, directly and indirectly among organizations, supply chain partners, and customers to enhance business operations. VanVactor (2011) also argued that the collaboration of supply chain management and practices are mediators to operations conflicts including effective and profitable business practices.
Another methodology in the assessment of operations concepts and the supply chain process until the product reaches the customer, is VanVactor’s (2011) application of the use of accuracy within the supply chain with the right product delivered to the right customer timely, effectively, and efficiently. There is also the matter of stakeholder involvement where all parties involved within the supply chain operates in a manner creating sustainable operations, including that of collaboration and execution. While the supply chain management focuses on satisfying customer demands, formulating and implementing strategy based on maximizing end-customer business, and managing lines of supply (VanVactor, 2011), it is the operations management that facilitates the routine activities ensuring performance targets are met. One such aptitute would be the balanced scorecard (Balanced Scorecard Institute), where the perspectives of customer, financial, learning and growth / organizational capacity, and internal processes drive organizational continuity (sustainability) enabling coping mechanisms for all levels of the competitive landscape. Ponis, Gayialis, Tatsiopoulos, Panayiotou, Stamatiou, and, Ntalla (2015) aruge supply chains if poorly managed, often leads to increased cost structures which severely deteriorate performance. Operations concept is the navigation that prevents cost-deficient structures and outcomes.
Amanipour, Jamshidvand, and Tabatabaei (2015) argue that the current competitive landscape extends beyond operations in terms of business versus business, to now supply chain versus supply chain. The more efficient the supply chain, the greater the competitive advantage of the organization, in terms of production costs, operations, supply chain management, performance management, branding and brand management, and strategic planning and management. To retain competitive advantage into sustainability, Amanipour, et al, (2015) presents that the supply chain members must learn to seamlessly integrate, grow, and develop business functions beyond traditional quality management practices into supply chain quality management. Supply chain quality management is a systems-based approach to performance improvement that integrates supply chain partners and leverages opportunities created by upstream and downstream linkages with a focus on creating value and achieving satisfaction of intermediate and final customers, (Amanipour, et al, 2015).
To assess operations concepts and the supply chain process until the product reaches the customer, Amanipour, et al’s (2015) Supply Chain Quality Management (SCQM) is used, and defined as a systematically approach by means of elevating supply chain’s quality performance which is achieved by integration of different layers of the chain. The SCQM Activity Clustering (fig 6) is used to illustrate the order in which activities occur until the products reach the customer, (1) quality approaches / business results; (2) supplier relations; (3) customer relations; (4) leadership / human resources; and, (5) management / safety (Amanipour, et al, 2015). The SCQM exceeds the traditional supply chain through the utilization of the application of Amanipour, et al’s (2015) management / safety component completed towards the latter end of the activities, facilitating freedom from deficiencies; quality meaning fitness for use; and the achievement of conformance to requirements.
Fig 8 - Amanipour, et al’s (2015) SCQM Activity Clustering
Bojnec (2013) assesses the operations concepts and the supply chain process until the product reaches the customer in the defense indusry as challenging, based on the issues of, (1) greater cooperation of defence enterprises as part of the defence supply chain to ensure effective defence production at a socially acceptable cost; (2) defence standards make for easier cooperation between defence-civilian enterprises and provide quality control of products (Bojnec’s 2013 ANSI and STANAG; Bachar’s 2017 AECA); (3) defence-civilian cooperation activities in the defence supply chains, public defence procurements, and defence supply networking with foreign industry enterprises must comply with specific norms for security and defence standards for products and services, (Bojnec’s 2013 ANSI and STANAG; Bachar’s 2017 AECA); (4) a specific system of defence standards can enhance security and gate-keeping of the relevant technologies, but can have an adverse effect on the available variety of new such products; (5) defence standards are important to assure quality that can be used for intermediate consumption, production, and sale in arms and ammunition international trade, (Bojnec’s 2013 ANSI and STANAG; Bachar’s 2017 AECA); (6) defence standards simplify product monitoring and servicing as well as preventing illegal production, providing security, compatibility, and access, (Bojnec’s 2013 ANSI and STANAG; Bachar’s 2017 AECA); (7) buyers demand and expect that products and services shall comply with the set defence standards, (Bojnec’s 2013 ANSI and STANAG; Bachar’s 2017 AECA); and, (8) producers expect that defence standards are respected by their sub-suppliers in the defence chains, (Bojnec’s 2013 ANSI and STANAG; Bachar’s 2017 AECA). This assessment results in Yong, et al’s, (2015) competition restriction, as well as barriers of entry to the defense industry.
In assessing operations concepts and the supply chain process until the product reaches the customer, several evaluations occur, (1) the supply chain itself (Fig 6); (2) assessing the operations concepts and supply chain process until the product reaches the customer as an integration of key business processes (Fig 5); (3) evaluation of the elements of how business ecosystem can be used to assess operations concept and the supply chain process (Fig 7); and, inclusion of supply chain quality management (SCQM) Activity Clustering (FIg 8). Present in these visual frameworks listed, integrated and separately, are the processes for operations including enterprising, competitive landscapes, regulations and regulative matters, customer management and elements, risk management, logistics and distribution groups, and the elements of the supply chain as needed.
Finally, the assessment of operations concepts and the supply chain process until the
product reaches the customer is Moon’s (2004) supply chain structure which is the mediated variable between product strategy and supply chain inventory, where the relationship among strategy, structure and performance is highly defined.
Evaluate the various stages in an effort to fine tune them to assure quality product and delivery, including resources, labor and their costs
In evaluating the various stages in an effort to fine tune them to assure quality product and delivery, including resources, labor and their costs, Moon’s (2004) presented three (3) strategies, supply chain structure (SCS) of product with cost leadership strategy (maintaining competitive advantage through lower pricing); SCS of product with differentiation strategy (strategy is based on innovative technologies including design, prestige pricing, and market segmentation); and, interdependence of the supply chain members (in this event, efficiency is driven by monitoring, relationship, and risk of the relationship). One of MÅLSMAN™ competitive advantage will be Moon’s (2004) SCS of product with differentiation strategy (strategy is based on innovative technologies.
Yong, Ahn, Jung, and Park (2015) defense articles are decided not by the market price but rather by the manufacturing costs, with defense production requiring complex production processes and a high level of technology as well as risk. Given that the suppliers and consumers of defense articles are limited, competition is significantly lower than other industries and perfect competition cannot exist, Yong, et al, (2015). However production costs management should not invite risks, as the risk of failure from deficiencies or defects result in national security threats and events, (Templin, 1994). As a result, quality assurance is required.
Yong, et al, (2015) discussed the defense sector as operating significantly different from the commercial sector in numerous ways, (1) supply is driven by the government’s demand for orders for research and development or production of defense articles; (2) as the defense industry is heavily regulated and concerns national security (Templin, 1994), MÅLSMAN™ must address the risk the product presents at all stages including production; (3) government restricts competition as overseas exports are the primary consumers for defense articles; (4) government restricts competition through the assignment of products as defense articles and defense companies; (5) government regulates the defense industry through policies and procedures including investments, capital, and cost recoveries including production in addition to reasonable profits, (Templin, 1994); (6) contract methods are predetermined including fixed price contracts and cost plus contracts. See Yong, et al’s (2015) tables 1, 2, 3, and, 4.
Table 1 - Yong, et al, (2015) Contract amount by type
Russell (2011) presented thesis in assuring quality product and delivery, including resources, labor and their costs through methodologies including, classical logistics (acqusition, storage, and distribution of materials to get the right product to the right customer, at the right time, in the right condition, in the right quantity, at the right cost); lean logistics and lean manufacturing emphasizes flows in which the following are avoid, excessive production runs, poor demand forecasting, faulty inventory data, and erroneous decisions; just-in-time approach eliminates systematic process problems through real-time demand as point of sale data, and more accurate forecasts, and visibility on inventory location.
Table 2 - Yong, et al, (2015) Cost calculation of defense articles
Table 3 - Yong, et al, (2015) Ratios calculation of defense articles
Table 4 - Yong, et al, (2015) Profit calculation of defense articles
Baurina, Nazarova, and Savchenko (2017) argue the relationship between product quality, manufacturing and production costs, and delivery / profitability, with the intersection being accounting methodologies. Baurina, et al (2017) argue that objectives and target performance indicators for developing quality managemetn systems are linked to different outcomes including, achieving acceptable rates of returns and profits while obtaining and returning compliance certification required for export markets; performance and key performance indication measures are required to keep the organization and division operative; accurate financial and accounting records (costing mechanisms) needed to identify the labor input and costs associated with manufacturing and production, as well as the retention of compliance certification; Yong, et al’s (2015) revenue generation and computations (tables 1 - 4) are necessary to provide adequate working capital, including financing, competitive arrangements, contacting and subcontracting with customers, suppliers, and alliances as a matter of proof of sustainability as well as no going concerns; and, strategic planning tools and devices including Balanced Scorecard Institute’s balanced scorecard including the alignment between vision, key performance indicators, and performance measurment systems including the standard perspectives, customer, internal processes, financial, and organizational capacity / learning and growth. Baurina, et al’s (2017) relationship between product quality, manufacturing and production costs, and delivery / profitability, with the intersection being accounting methodologies, is also needed to provide quality assurance in the defense and weapons industries, to ensure that MÅLSMAN™ products is of a high quality with zero defects to meet not only compliance, but quality standards in technical, litigative and liabilities, and organizational reasons so there are no contingencies.
Bengü and Kara (2010) provided several accounting methodologies (costing mechanisms) as, activity based costing (ABC); just-in-time (JIT) manufacturing system; and product life cycle costing. All are capable of managing manufacturing costs, delivering key performance indicators, and revenue generation calculations. However product life cycle costing is most applicable as a defense industry accounting methodology and costing mechanism given its association with the United States Department of Defense and its require to increase armament efficient, Bengü and Kara (2010). Product life cycle costing is capable of analyzing and presenting direct (labor, materials, and overhead), and indirect costs (administrative, design, marketing and selling costs), including performance metrics. It is also capable to monitoring and making adjustments of profitabilities and its performance based on production volumes, and their relationship with marketing and sales expenses, as well as the manufacturing life cycle of the product, product idea or concept stage, design and development stage, manufacturing stage, and after-sales logistic support stage, Bengü and Kara (2010). Bengü and Kara’s (2010) product life cycle accounting methodology and costing mechanism, also capable of generating a marketing product life, market introduction stage; growth stage; mature stage; and, decline stage.
The formation and length of the product life cycle is dependent on speed of technological advances; product acceptance in the market; social and cultural changes and developments; effects of market entry barriers including use of regulations to restrict competition; and, the presence of new consumers, Bengü and Kara (2010). The objective of product life cycle is to determine, analyze, forecast, report and manage all kinds of costs in all life cycle stages of a product, with costs classified into three (3) groups, premanufacturing costs, manufacturing costs (including design and engineering, planning, buying, sales, logistics, and transportation), and post-manufacturing costs, Bengü and Kara (2010).
Bengü and Kara (2010) distinguishes the difference between traditional cost accounting systems and product life cycle as, the traditional cost accounting systems only considers costs related with manufacturing in accordance with the Generally Accepted Accounting Principles (GAAP), whereas product life cycle costing methodology considers costs related with all stages of the product life cycle such as market introduction, growth, mature and decline stages.
Fig 9 - Bengü and Kara (2010) differences between traditional and product life cycle costing methodologies
Compare and contrast your product and plans with a similar product manufactured by a Fortune 500 company
The product for comparison is competitor The Boeing Company, a publicly traded company on NYSE - Nasdaq, who competes in the industry aerospace and defense. The Boeing Company’s product line are similar to MÅLSMAN’s™, defense replacement parts; aircrafts; weapons / missiles and missile systems; armored vehicles; and air defense systems. While The Boeing Company is publicly traded (ticker BA), MÅLSMAN™ has a small number of substantial investors along with substantial revenues garnered from government contracts and owners equity.
Fig 10 -Compare and contrast MÅLSMAN’s™ with competitor The Boeing Company
MÅLSMAN’s™
The Boeing Company
Industry
Defense
industry aerospace and defense
Product line
Aircrafts; missiles and missile systems; armored vehicles; and air defense systems.
Defense replacement parts; aircrafts; weapons; armored vehicles; and air defense systems.
Overall portfolio Commercial Airplanes (BCA); Defense, Space & Security (BDS); Global Services (BGS); Boeing Capital (BCC)
Financing
Privately held; investors
Publicly traded, ticker (BA)
Accounting methodology
Product life cycle reporting; GAAP (new company with funding requirements)
GAAP
# of employees
98,640
140,800
Regulatory agencies
Arms-trade watchdog the Stockholm International Peace Research Institute (SIPRI), Reuter (1991)
United Nations
The Hague - The Criminal Court
U.S. Department of Defense
NASA
Federal Aviation Administration (FAA)
Department of Homeland Security
Regulations
Standardization Agreement (STANAG), Bojnec (2013)
American National Standards Institute (ANSI), Bojnec (2013)
Naval Vessel Transfer Act (NVTA) of 2008, Bachar (2017)
Arms Export Control Act (AECA), Bachar (2017)
Standardization Agreement (STANAG), Bojnec (2013)
American National Standards Institute (ANSI), Bojnec (2013)
Naval Vessel Transfer Act (NVTA) of 2008, Bachar (2017)
Arms Export Control Act (AECA), Bachar (2017)
Competitors
Boeing Company
BAE System
Lockheed Martin
Raytheon
General Dynamics
NEW - MÅLSMAN’s™
Airbus
Embraer
Bombardier, and
Other entrants from Russia, China and Japan
Lockheed Martin Corporation Northrop Grumman Corporation Raytheon Company, General Dynamics Corporation
SpaceX
Non-U.S. companies such as BAE Systems
Sustainability
New company; 7 year contract fundings including profit streams; owners’ equity
No going concerns
Customers
Government contracts
Government contracts
Suppliers
International suppliers
International suppliers
Distribution channels
International representatives
Direct delivery systems
Unknown; multiproduct line creates additional channels
Although a new privately held, MÅLSMAN’s™ financial position is strong with numerous customers including several years government contracts along with substantial owners’ equity. MÅLSMAN™ is expected to demonstrate substantial sustainability although a new company with dominant competitors (Fig 11).
Fig 11 - McCarthy, (2017) The World's Biggest Arms Companies
Conclusion
Entrance into a new industry such as defense presents substantial barriers, financing; regulations; regulatory agencies; technology; and expertise. There is also the matter of sustainability, customer acquistion, supply chain, and other performance management systems. The disciplines of operations management and supply chain management and their numerous structure, supply chain structure, demand management, product life cycle, and understandings, computations, and presentations of the various revenue sources including contracts and its elements does not only make a difference. This is a competitive advantage that can increase working capital, profitability, and the related collaboration required to be considered an allied competitor. An understanding of operations management, supply chain management, supply chain structure, and their relevant frameworks create the edge needed to remain within the competitive landscape, sustainability.
References
Amanipour, H., Jamshidvand, A., & Tabatabaei, M. (2015). An in-depth review and classification of supplier quality management approaches: Following trends in academic, industrial and military literature. Journal of Supply Chain Management Systems, 4(4), 9-23. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/1765137289?accountid=28180
Bachar, A. (2017). JCPOA: IMPLICATIONS AND EFFECTS ON OUR FOREIGN MILITARY SALES PROGRAM. Public Contract Law Journal, 46(4), 873-893. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/1954384783?accountid=28180
Balanced Scorecard Basics. Balanced Scorecard Institute. Retrieved from http://www.balancedscorecard.org/BSC-Basics/About-the-Balanced-Scorecard
Baurina, S. B., Nazarova, E. V., and Savchenko, E. O. (2017). The problem of ensuring industrial products quality in russia. Journal of Business and Retail Management Research, 12(1) Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/1958122791?accountid=28180
Bengü, H., & Kara, E. (2010). Product life cycle costing methodology. Banking and Finance Letters, 2(3), 325-333. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/1014005343?accountid=28180
Boeing Company’s aerospace and defense ranking on Fortune 500 listing. Retrieved from http://fortune.com/fortune500/boeing/
Boeing Company’s listing placement within the Fortune 500 listing. Retrieved from http://www.worldbusinesschicago.com/2017-fortune-500/
Bojnec, S. (2013). Changing role of the Slovenian defence industry. Industrial Management & Data Systems, 113(6), 875-889. doi:http://dx.doi.org.proxy1.ncu.edu/10.1108/IMDS-11-2012-0406
Chapman, P., Bernon, M., & Haggett, P. (2011). Applying selected quality management techniques to diagnose delivery time variability. The International Journal of Quality & Reliability Management, 28(9), 1019-1040. doi:http://dx.doi.org.proxy1.ncu.edu/10.1108/02656711111172568
Defense spending and arms trade dossier. Retrieved from https://www-statista-com.proxy1.ncu.edu/study/12526/defense-spending-and-arms-trade-statista-dossier/
D'yachuk, ,A.K., Orkin, B. D., & Orkin, S. D. (2011). Interactive automated planning system for actions of aviation of different tactical designation against naval objects. Journal of Computer & Systems Sciences International, 50(4), 593-608. doi:http://dx.doi.org.proxy1.ncu.edu/10.1134/S1064230711030087
Erkoyuncu, A. J., Roy, R., Shehab, E., & Kutsch, E. (2014). An innovative uncertainty management framework to support contracting for product-service availability. Journal of Service Management, 25(5), 603-638. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/1660769269?accountid=28180
Evans, J. R. (1996). Leading practices for achieving quality and high performance. Benchmarking for Quality Management & Technology, 3(4), 43. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/217363051?accountid=28180
Golde, S., & Tishler, A. (2004). Security needs, arms exports, and the structure of the defense industry: DETERMINING THE SECURITY LEVEL OF COUNTRIES. The Journal of Conflict Resolution, 48(5), 672-698. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/224557674?accountid=28180
Jambekar, A. B., & Pelc, K. I. (2006). A model of knowledge processes in a manufacturing company. Journal of Manufacturing Technology Management, 17(3), 315-331. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/208180880?accountid=28180
Moon, Seong-Am. (2004). The relationships among manufacturer product strategy, supply chain structure and supply chain inventory. Asia Pacific Journal of Marketing and Logistics, 16(2), 20-45. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/227362010?accountid=28180
Oprean, G. (2012). CONSIDERATIONS ON COMMAND AND CONTROL DURING INDUSTRY AGE AND INFORMATION AGE. Land Forces Academy Review, 17(4), 355-361. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/1270319284?accountid=28180
Ponis, S. T., Gayialis, S. P., Tatsiopoulos, I. P., Panayiotou, N. A., Stamatiou, D. I., & Ntalla, A. C. (2015). An application of AHP in the development process of a supply chain reference model focusing on demand variability. Operational Research, 15(3), 337-357. doi:http://dx.doi.org.proxy1.ncu.edu/10.1007/s12351-014-0163-8
Reuter. (1991, May). Study: Arms cuts aren't increasing world safety. Newsday Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/278369901?accountid=28180
Ross, A. L. (1990). Do-it-yourself weaponry. Bulletin of the Atomic Scientists, 46(4), 20. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/197789677?accountid=28180
Russell, S. H. (2011). Supply chain management: More than integrated logistics. Air Force Journal of Logistics, 35(3), 88-96. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/1430897272?accountid=28180
Schilde, K. (2015). WAR POWERS, PRIVATE ACTORS, AND NATIONAL SECURITY STATE CAPACITY. Boston University Law Review, 95(4), 1369-1386. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/1710788227?accountid=28180
SIPRI. (n.d.). The 20 largest arms-producing and military services companies in the world in 2016, by arms sales (in million U.S. dollars). In Statista - The Statistics Portal. Retrieved May 16, 2018, from https://www-statista-com.proxy1.ncu.edu/statistics/267160/sales-of-the-worlds-largest-arms-producing-and-military-services-companies/.
Sokolov, A. (2005). Before Stalinism: The defense industry of Soviet Russia in the 1920s. Comparative Economic Studies, 47(2), 437-455. doi:http://dx.doi.org.proxy1.ncu.edu/10.1057/palgrave.ces.8100100
Szwejczewski, M., Sweeney, M. T., & Cousens, A. (2016). The strategic management of manufacturing networks. Journal of Manufacturing Technology Management, 27(1), 124-149. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/1757887327?accountid=28180
Templin, C. R. (1994). Defense contracting impediments to supplier productivity and quality improvement. National Contract Management Journal, 25(2), 51. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/223523987?accountid=28180
Thomas, K. T. (2006). Quality management system for defence aeronautical industry. Defence Science Journal, 56(1), 21. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/1414379202?accountid=28180
VanVactor, J. D. (2011). A case study of collaborative communications within healthcare logistics. Leadership in Health Services, 24(1), 51-63. doi:http://dx.doi.org.proxy1.ncu.edu/10.1108/17511871111102526
Villa, R. D., & Viggiano, J. (2012). Trends in south american weapons purchases at the beginning of the new millennium. Revista Brasileira De Politíca Internacional, 55(2) doi:http://dx.doi.org.proxy1.ncu.edu/10.1590/S0034-73292012000200003
Yong, H., Ahn, T., Jung, H., & Park, J. (2015). Costing rule and cost behavior in the korean defense industry *. Seoul Journal of Business, 21(1), 31-57. Retrieved from http://search.proquest.com.proxy1.ncu.edu/docview/1702903546?accountid=28180
0 notes
Text
Huawei, Google, and the tiring politics of tech
The defining question of the 21st century is pretty simple: who owns what? Who owns the telecommunications infrastructure that powers our mobile devices? Who owns the OS that powers those devices? Who owns our data?
Today, we see these intersecting arcs with two prominent tech leaders mired in legal and political processes.
TechCrunch is experimenting with new content forms. This is a rough draft of something new – provide your feedback directly to the author (Danny at [email protected]) if you like or hate something here.
In Canada, we have day three(!) of the bail hearing for Huawei head of finance Meng Wanzhou (孟晚舟), who was arrested at the request of the U.S. last week. And on Capitol Hill today, Sundar Pichai, the CEO of Google, is testifying in front of the House Judiciary Committee, starting a few minutes ago at 10am.
These may be pedestrian proceedings, but they are riven with deep debates over the meaning of ownership. Meng was arrested for supposedly selling equipment to Iran through intermediaries in violation of U.S. sanctions. Huawei is a Chinese company, but uses American intellectual property in its products. Thus, America claims worldwide jurisdiction over the company, since it owns the patents beneath Huawei’s products.
Meanwhile, Pichai is testifying over a number of concerns, including data privacy (i.e. data ownership) and Project Dragonfly, the company’s attempt to re-enter China. He also has to contend with another data breach bug discovered yesterday in Google+. Is Google an American “owned” company (as Pichai will attempt to paint it today), or is it a global company owned by shareholders with obligations to enter China?
These aren’t simple questions, which is why the broader question of ownership will be so important for this century. Despite the win-win attitude of free traders, the reality is that much of technology ownership is monopolistic owing to barriers to entry – there are only a handful of telco equipment manufacturers, public clouds, mobile OSes and search engines out there. Whoever owns that property is going to get rich at the expense of others.
That’s why the US/China trade conflict is an irreconcilable tug-of-war.
For China, a developing country by most metrics even if it has glittering cities like Shanghai, owning that technological wealth is crucial for it to reach the zenith of its growth. It cannot become rich without becoming a technology power, a manufacturing power, and a consumer market capital all at once. And it views with deep suspicion American blocks on wealth transfers. Isn’t this just a way to keep the country down, to replay the century of humiliation all over again?
For the U.S., China’s constant conniving to pilfer American intellectual property undermines U.S. economic hegemony. China does want to steal plans for airplanes, and semiconductors, and other high-tech goods. Of course, it eventually wants to have the human capital and know-how to build these themselves, but first it has to catch up. America, fundamentally, doesn’t want it to catch-up.
As more and more wealth derives from technology, technology = politics becomes the bedrock law.
That’s frankly tiring for someone who just loves great products and wants to see massive technological progress for everyone regardless of nationality. But political symbolism is increasingly a language that Silicon Valley and the tech industry writ large have to understand.
Why Oath keeps Tumblring (now with a price tag)
Last week, I wrote a bit of a screed on why TechCrunch’s parent company, Oath, is struggling so badly:
Oath has a problem:* it needs to grow for Wall Street to be happy and for Verizon not to neuter it, but it has an incredible penchant for making product decisions that basically tell users to fuck off. Oath’s year over year revenues last quarter were down 6.9%, driven by extreme competition from digital ad leaders Google and Facebook.
Now, we know the costs of those product decisions, as well as the greater challenges in the digital advertising market. Verizon announced today that it will write down the value of Oath by $4.6 billion. That will change Oath’s goodwill value from $4.8 billion to $0.2 billion in the fourth quarter. Yikes.
This was a necessary accounting valuation change, and one that recognizes the challenges that Oath faces. As the filing said:
Verizon’s Media business, branded Oath, has experienced increased competitive and market pressures throughout 2018 that have resulted in lower than expected revenues and earnings. These pressures are expected to continue and have resulted in a loss of market positioning to our competitors in the digital advertising business. Oath has also achieved lower than expected benefits from the integration of the Yahoo Inc. and AOL Inc. businesses.
The upside is that Oath still has many, many millions of users every month. It just needs to figure out what to do with all of those eyeballs to build a sustainable business.
Can the West build anything?
Photo by VictorHuang via Getty Images
Seriously, from the Financial Times:
The capital should have been celebrating the opening of the east-west London railway, the biggest construction project in Europe, this week. But Crossrail announced in August that it would not begin operation until autumn 2019 at the earliest.
Even that now seemed “wildly optimistic”, one person close to the project said, given the problems with signals, trains and stations leading to “growing panic” among TfL executives. A number of people close to the project now say it may not be ready until late next year.
Crossrail is one of the most important subway projects in the world, designed to dramatically increase capacity in London’s Underground on the east-west axis. But it is just one of a series of major setbacks in infrastructure costs in the West. Meanwhile in California from Connor Harris at City Journal:
Ten years later, supporters have ample cause to reconsider. CAHSR’s costs have severely escalated: the California High-Speed Rail Authority (CHSRA) now estimates that the train’s core segment alone, from San Francisco to Los Angeles, will cost from $77 billion to $98 billion. Promises that private investors would cover most of the costs have fallen through. Forecasts for the project’s completion date and travel times have also slipped. The fastest trains in the CHSRA’s current business plan have a running time of over three hours, and the first segment of the line—San Jose to Bakersfield, almost 200 miles short of completion—won’t open until 2029.
I want high-speed rail, and I want new subways. I just don’t want new subways that cost billions of dollars per mile, and I don’t want high-speed rail at $100 billion.
The inability of Western countries to build infrastructure within any period of time and within any sort of budget is just mesmerizing. What we are left with is raising the speed limits on subways in New York City from 15 MPH to something a bit more reasonable.
I have talked previously about the need for more startups in this space:
California is home to two very different innovation worlds. For the readers of TechCrunch, there is the familiar excitement of the startup world, with startups working on longevity and age extension, rockets to Mars, and cars that drive themselves. Hundreds of thousands of entrepreneurs, engineers, and product managers are building these futures every day, often on shoestring budgets all in the hope of seeing their solution come to fruition.
Then, there is the “innovation” world of California’s infrastructure. Let’s take the most prominent example, which is the bullet train connecting southern to northern California. The train, first approved in a bond authorized by voters in 2008, is expected to have its first passengers in 2025 — three years after the original target of 2022.
That’s roughly 17 years start to finish, or older than the ages of Facebook (14 years) and the iPhone (10 years) are right now. Given that environmental reviews aren’t even slated to come in until 2020, it seems hard to believe that the route will maintain its current schedule.
Startups, we need your innovation in this space desperately. It’s a trillion dollar market ready for anything that might make these projects move faster, and cost less.
Quick Bites
My quick bites turned into full bites above.
What’s next
I am still obsessing about next-gen semiconductors. If you have thoughts there, give me a ring: [email protected].
Thoughts on Articles
The Increasingly United States – I read this book this weekend. Probably best to just read the reviews for most readers, although if you like modern political science research, this has about all the techniques you can do in American studies these days.
The core thesis is that the notion that “all politics is local” is completely bunk on two dimensions. Voters increasingly vote for candidates at every level of government using the same litmus tests, and they also get their information about politics exclusively from national sources. That basically means city councilors are debating immigration policy (which they have zero control over) rather than trash policy. It also explains the rising polarization in Congress — with less local issues to debate, there are just no opportunities afforded to build coalitions.
The book charts the pathways through which this nationalization takes place, and they will be intimately familiar to most readers (campaign finance changes, national media markets, nationalized policy planning, etc).
The thesis though raises a number of questions. First, how will local issues (zoning, trash pickup, etc.) get the attention they need to make our cities livable and thriving? Second, how can we fund local media so that voters have differentiated visibility into what is happening in their own backyard? These questions aren’t easy to answer, but we must if we want our federal-style system to function the way the founders intended.
The Death of Democracy in Hong Kong by Jeffrey Wasserstrom. A short and emotional look back at the failure of Hong Kong’s Umbrella Movement in 2014 and its ramifications.
Lean In’s Sheryl Sandberg Problem by Nellie Bowles. What does an organization do when the reputation of its founder and major icon turns sour? Lean In is trying to find out. Good if a bit lengthy, but I’m starting to get tired of the constant anti-Sandberg coverage.
Reading docket
What I’m reading (or at least, trying to read)
Huge long list of articles on next-gen semiconductors. More to come shortly.
Inside China’s audacious global propaganda campaign | News | The Guardian
Outgrowing Advertising: Multimodal Business Models as a Product Strategy – Andreessen Horowitz
Via Danny Crichton https://techcrunch.com
0 notes