#vmware appdefense
Explore tagged Tumblr posts
Text
New Post has been published on VMware Virtualization Blog
New Post has been published on http://www.tayfundeger.com/vsphere-platinum-nedir.html
vSphere Platinum Nedir?
Merhaba,
Bir önceki yazımda sizlere vSphere 6.7 Update 1 ‘in yeniliklerinden bahsetmiştim. Hatta bu makalemin en sonunda sizlere vSphere Platinum‘dan bahsetmiştim. vSphere Platinum detaylı bir konu olduğu için ayrı bir makalede bilgi vermek istedim. vSphere 6.7 Update 1 yenilikleri ile ilgili yazmış olduğum makaleye aşağıdaki linkten ulaşabilirsiniz.
vSphere 6.7 Update 1 ile Gelen Yenilikler
vSphere 6.7 update 1 ‘in duyurusu ile birlikte VMware vSphere Platinum‘unda duyurusu yapıldı. Ürünün kasım ayı içerisinde çıkarılması beklendiğinide belirtmek isterim.
Kullanmış olduğumuz alt yapıda yani VMware altyapısında birden fazla virtual machine ve bunların üzerlerinde çeşitli uygulamalar çalıştığı için bunların güvenliğini sağlamakta önemli bir durum haline geldi. Nihayetinde tüm dünyada bir dijital dönüşüm çağı başlamış durumda ve şirketler gelirlerini artırmak için ve piyasada farklılaşmak için dijital dönüşüme biraz daha önem vermeye başlamış durumda. Tabi bu dijital dönüşümün önemli bir basamağıda güvenliktir. Uygulamalarınızı çalıştırdığınız platformun güvenliği çok önemlidir. Altyapı oluşturulurken bunun güvenlik boyutunuda ele almak ve bunu güvence altına almak gerekmektedir. Günümüzde güvenlik tehditleri git gide artmaktadır ve daha karmaşık bir hal almaktadır. Güvenlik denildiğinde ilk olarak aklınıza antivirus geliyor ancak antivirus bazı durumlarda etkisiz olabiliyor. Ayrıca antivirus’un bulunduğu işletim sisteminde çok fazla kaynak tüketiminine sebep olup sistem performansını olumsuz etkileyebilir. Bazı durumlarda ise antivirus bir saldırıyı veya atak’ı çok geç farkedebiliyor.
Güvenlik tehditleri günümüzde bir hayli artmış durumda. Bunun için sizlere VMware vSphere Platinum hakkında bilgi vermek istiyorum. vSphere Platinum, VMware vSphere Enterprise Plus ve VMware AppDefense‘yi içeren yeni bir paketdir . Ancak bu sadece iki VMware ürününden oluşan bir paket değildir. vSphere Platinum, vSphere Platinum için özel olarak tasarlanmış özel bir vCenter Server plugin‘i içerir ve bu iki ürün arasında bir entegrasyon oluşturur. Bu eklenti VMware ortamını yöneten admin’lere, AppDefense’in uygulama katmanında güvenlik tehditlerinin görünürlüğü sağlar ve daha güvenli bir altyapı sağlamak için Güvenlik Yöneticileriyle yakın işbirliği içinde çalışmasına olanak tanır.
VMware vSphere Platinum, hypervisor’e tam olarak entegre edilmiş gelişmiş güvenlik yetenekleri sunan yeni bir vSphere sürümüdür. Bu yeni sürüm, AppDefense ürünü ile bir araya getirerek uygulamaların güvenliği sağlar. VMware, AppDefense ürününü ilk olarak VMworld 2017’de duyurmuştu.
Yukarıda VMware AppDefense‘in arayüzünü görebilirsiniz. Ancak burada dikkat ettiyseniz virtual machine’ler gösterilmiyor. İlgili virtual machine’ler çeşitli gruplar halinde gösteriliyor. Elbette burada virtual machine bazında sorunun ne olduğunuda kısmen inceleyebilirsiniz ancak VMware ortamını yöneten kullanıcılar için bu oldukça zor bir durum. Yani şöyle düşünün virtual machine içerisinde hangi uygulamanın veya hangi serviste bir problem olduğunu doğrudan bu ekrandan kontrol etmeniz sizin zamanınızı alacaktır.
Yukarıdaki ekran görüntüsünde sanal altyapı nesnelerine daha çok odaklanmış bir gösterge panosunu görebilirsiniz: ESXi host‘lar ve virtual machine’ler. Bu, vSphere Administrator ürününün tehditleri izlemesi ve ele alması için daha kolay bir yöntemdir çünkü bu, yöneticinin bu tehditleri IP adresleri veya bağlantı noktaları yerine yönetilen nesnelerle hızlı bir şekilde ilişkilendirmesine olanak tanır. Aslında buradaki ekranı VROPS’un monitor göstergelerine benzetebilirsiniz. Bende açıkcası ona benzettim. Yukarıdaki ekranda örneğin alt yapınızda bulunan virtual machine’lerin kaçtanesi unsupported durumd aolduğunu veya kaçtanesi appdefense tarafından izlendiğini görebilirsiniz. Yine altyapınızda bulunan virtual machine’ler üzerindeki servislerin risk durumlarını görebilirsiniz. Farkı biraz daha anlatabildim diye düşünüyorum.
Örneğin yukarıdaki ekran görüntüsünde host and cluster tab’ından monitor bölümüne girişi yapılmış. Yine burada yer alan AppDefense tab’ı altında yer alan Processes bölümünden bu virtual machine üzerinde yer alan processes’lerin ayrıntılarını görebilirsiniz. Dikkat ettiyseniz burada skor’larda yer almaktadır. Yani bu processes güvenli mi yoksa güvensiz mi buradan görebilir hatta bunun path’inide görebilirsiniz.
Ayrıca vSphere Platinum’un VSAN, NSX ve vRealize Suite gibi ürünler ile de tam entegrasyonunun olduğunu belirtmek isterim.
vSphere Platinum oldukça dikkat çekeceğe benziyor. Ürün daha release olmadığı için şuan için makalesini yazamıyorum ancak release olduktan sonra hemen inceleme ve kurulum makalesini yazacağım. Orada daha detaylı olarak anlatıyor olacağım.
Ürün ile detaylı bilgiye aşağıdaki link’den ulaşabilirsiniz.
https://blogs.vmware.com/vsphere/2018/08/under-the-hood-vsphere-platinum.html
Umarım faydalı olmuştur.
İyi çalışmalar.
0 notes
Text
VMware AppDefense mueve la industria hacia un modelo de seguridad intrínseco
VMware AppDefense mueve la industria hacia un modelo de seguridad intrínseco
VMware transforma la seguridad de las aplicaciones de infraestructura y de nubes basados en VMware vSphere
VMware anunció VMware AppDefense, su innovadora solución para proteger las aplicaciones que se ejecutan en entornos virtualizados o en la nube.
Esta nueva solución de seguridad aprovecha la infraestructura virtual para vigilar si las aplicaciones que se encuentran activas tienen el estado…
View On WordPress
0 notes
Text
Mac Os X Patch For Vmware

Download Unlocker 208
Vmware Unlocker For Mac Os
Vmware Mac Os X Patch
VMware Tools is a critical component in your virtual infrastructure. It provides drivers for virtual and paravirtual devices, security components, and capabilities such as guest file system quiesced snapshots. On that note, I am delighted to announce the general availability of VMware Tools 11.0.
Install Mac OS X Yosemite on VMware, and it is the 11th major release of Mac, Apple company. Therefore, this version of Mac OS X Yosemite is 10.10 and it was the old version of macOS operating system among the other operating systems. In order to allow the users to show the macOS operating system on the list of other operating systems on VMware player. In this case, you can download the Patch Unlocker tool from above-given link with the full and complete update. After that, you download extract the file with winrar or 7Zip. We Can Finally Do it.It really didnt take that long. Here is the link for the macos mojave image file http://www.mediafire.com/file/yv55fbrjn1471br/macOSMoj. But one big change with this update isn’t documented anywhere: The software has been modified so that it will run the non-server versions of Snow Leopard (Mac OS X 10.6) and Leopard (Mac OS X 10.5).
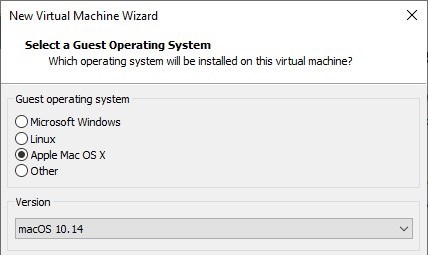
What’s New for Windows?
A major version bump usually signals significant new features, and this release is no exception. We continue our efforts to minimize additional reboot requirements by making the VMCI driver available through the Windows Update channel for Windows Server 2016 and above. My colleague Eric Gray blogged about the initial launch of this back in August 2018 when we made the pvscsi driver available through Windows Update. In April this year, we launched VMware Tools 10.3.10. At the time we made the vmxnet3 driver through this channel. We’re working hard to give you the option of further drivers, so expect to see more of this kind of announcements as time goes on.
VMware Tools 11.0 now uses Visual Studio 2017 as the kernel space compiler.
From a security perspective, we have split out the monolithic AppDefense driver into 2 separate drivers. We have split the AppDefense driver (glxgi.sys) into glxgi.sys and giappdef.sys. Glxgi.sys continues to provide guest integrity functionality, and the new giappdef.sys provides process and network attestation. This splitting of the drivers means we can replace the user-mode components without requiring a reboot, and that has to be a good thing!
There are 2 new features from the perspective of the Guest Admin. First, you can now configure VMware Tools to prevent automatic upgrades. You can also prevent a vSphere Admin from adding or removing VMware Tools components. If you have strict change control or security requirements, this one is for you!
VMware Tools 11.0 for Mac OSX
This release isn’t just about Windows, either. There are a couple of changes for Mac OS X users too. As of VMware Tools 11.0 for Mac OSX, we have deprecated the ballon driver for memory management. In readiness for MacOSX 10.15 (Catalina), this release of VMware Tools for Mac OSX is notarized.
So what about Linux?
It’s no secret that the TAR and OSP (Operating System Specific Packages) for Linux are no longer under active development. 10.3.5 was the final release of these tools from a feature perspective. However, we continue to backport security fixes for legacy Linux distros. To distinguish the fact that there are no new features for these VMware Tools, we are releasing VMware Tools 10.3.20, which is only available as TAR and OSP. If you’re running a modern distro, you should be using open-vm-tools rather than the OSP or TAR tools. Once the OS vendors have completed their build and test of the code, the latest version of open-vm-tools will be available in your repo. If you need to upgrade before your vendor pushes open-vm-tools to their repo, you can download the code from Github and compile for your platform.
Cross-Platform Improvements
So that’s the platform-specific aspects covered. On top of those, we also have some other general improvements for you. As of VMware Tools 11.0, we now capture the installation log into the hypervisor logs. In the case of issues, we collect these logs in the VMware support bundle for GSS to troubleshoot.
We also have some performance goodness for you too: you’ll see an increase in memory and guest process introspection performance. Finally, we see some pretty hefty performance increases for the Host-Guest Filesystem (HGFS). This is around 20% for high volume, low size data transfers, and a 30% performance increase when moving larger files. All in all, those are some pretty significant gains!
Summary
That’s a bunch of new features, performance bumps, and security fixes. If you’re itching to get your hands on the latest version, you can download from https://www.vmware.com/go/tools.


Read more about this release with the release notes of VMware Tools 11.0 . We also have separate release notes for the OSP/TAR only VMware Tools 10.3.20.


Also released today are VMware Workstation 15.5 and Fusion 11.5, which come bundled with the latest versions of VMware Tools.
Try our vSphere 6.7 Hands-On Lab here!
How to get updates for macOS Mojave or later
If you've upgraded to macOS Mojave or later, follow these steps to keep it up to date:
Choose System Preferences from the Apple menu , then click Software Update to check for updates.
If any updates are available, click the Update Now button to install them. Or click ”More info” to see details about each update and select specific updates to install.
When Software Update says that your Mac is up to date, the installed version of macOS and all of its apps are also up to date. That includes Safari, iTunes, Books, Messages, Mail, Calendar, Photos, and FaceTime.
To find updates for iMovie, Garageband, Pages, Numbers, Keynote, and other apps that were downloaded separately from the App Store, open the App Store on your Mac, then click the Updates tab.
To automatically install macOS updates in the future, including apps that were downloaded separately from the App Store, select ”Automatically keep my Mac up to date.” Your Mac will notify you when updates require it to restart, so you can always choose to install those later.
How to get updates for earlier macOS versions
If you're using an earlier macOS, such as macOS High Sierra, Sierra, El Capitan, or earlier,* follow these steps to keep it up to date:
Open the App Store app on your Mac.
Click Updates in the App Store toolbar.
Use the Update buttons to download and install any updates listed.
When the App Store shows no more updates, the installed version of macOS and all of its apps are up to date. That includes Safari, iTunes, iBooks, Messages, Mail, Calendar, Photos, and FaceTime. Later versions may be available by upgrading your macOS.
To automatically download updates in the future, choose Apple menu > System Preferences, click App Store, then select ”Download newly available updates in the background.” Your Mac will notify you when updates are ready to install.
* If you're using OS X Lion or Snow Leopard, get OS X updates by choosing Apple menu > Software Update.
Download Unlocker 208
How to get updates for iOS
Learn how to update your iPhone, iPad, or iPod touch to the latest version of iOS.
Vmware Unlocker For Mac Os
Learn more
Vmware Mac Os X Patch
Learn how to upgrade to the latest version of macOS.
Find out which macOS your Mac is using.
You can redownload apps that you previously downloaded from the App Store.
Your Mac doesn't automatically download large updates when it's using a Personal Hotspot.

0 notes
Text
Test Drive vSphere Platinum!
Did you know that VMware has multiple ways to test and try out products in easy-to-use, flexible, and low-stress ways? VMware Test Drive First, the VMware Test Drive program gives you access to most VMware products in a preconfigured, easy-to-use hosted environment with as much or as little guidance as you’d like. Everything is installed, configured, and optimized for you and your teams, and the comprehensive step-by-step videos, walkthroughs, and guides ensure you have a great experience focused on what you want to learn and see. Beginning today you can test and demo the advanced workload security features of vSphere Platinum and AppDefense in the Test Drive environment. Curious about what vSphere Platinum brings to the table? Want to see how VMware AppDefense changes the game around workload and endpoint security? Go to the VMware Test Drive site and sign up now! VMware Hands-on Labs Second, VMware Hands-on Labs (HOL) is also a great way to try VMware products. While the Test Drive is a preconfigured environment, the Hands-on Labs is dynamic. Each lab environment is provisioned on-demand inside of the Hands-on Labs cloud environments, and each has different strengths and content. Hands-on Labs is a huge feature of VMworld conferences (you’re going, right?) and a subset of labs is available year-round via the HOL web site. There are lab manuals to help guide you through learning each technology, but using the lab isn’t limited to following a manual. Want to try something? Want to see how a feature works? The Hands-on Labs is a great place to experiment, too. Nested Virtualization Last, nested ESXi & vCenter Server is a great way to test and experiment in your own environment. You can run ESXi for non-production purposes as a guest OS inside ESXi, which is exactly how the Hands-on Labs works! Maintaining separate test environment hardware is time-consuming and inflexible. As vSphere requirements change it sometimes means that old hardware cannot be effectively used for testing. Plus, if you break the environment you have to rebuild it. With nested vSphere you build ESXi VMs in essentially the same way you build other VMs, and deploy a separate vCenter Server Appliance to manage them. Once you do that you can snapshot them all so the environment is easily reset for testing. Want to try a new process, or make sure a procedure works before you do it in production? This is an excellent, low-effort way to do so. VMware doesn’t directly support nested ESXi, but many in the greater VMware and vExpert community have great resources on nested ESXi and vSphere. Sign Up All these resources are free to customers and easy to use. Sign up today! * VMware vSphere Platinum Test Drive * VMware Hands-on Labs The post Test Drive vSphere Platinum! appeared first on VMware vSphere Blog. http://bit.ly/2Y6ie6R
0 notes
Photo

How to Correctly Create Scopes and Services in… How to Correctly Create Scopes and Services in VMware AppDefense How to Correctly Create Scopes and Services in...
0 notes
Text
Antiviren
New Post has been published on https://www.chemieunternehmen.com/linklists/antiviren/
Antiviren
Ergebnisse der Google Suche zu „Antiviren“
https://www.leespcrepairs.co.uk/is-free-antivirus-good-enough/ https://blog.botfrei.de/2013/04/avast-free-antivirus-fur-mac/ https://blog.botfrei.de/2014/10/antivirus-fuer-das-iphone/ https://www.avira.com/en/blog/breaking-antivirus-software http://www.clinicadoslagos.pt/?p=3732 https://davidgoldfield.wordpress.com/2016/11/04/question-which-antivirus-program-works-best-with-my-screen-reader-answer-you-might-be-asking-the-wrong-question/ https://davidgoldfield.wordpress.com/2016/11/16/kaspersky-antivirus-a-review-for-screen-reader-users/ https://blog.logsign.com/top-10-anti-phishing-best-practices/ http://antivirus.co.in/apple-finally-admits-to-its-fake-anti-virus-malware-problem-read-more-httpwww-theinquirer-netinquirernews2073747apple-finally-admits-fake-anti-virus-malwareixzz1p4exzidm-the-inquirer-comp/ https://blog.eset.ie/2013/02/06/research-reveals-nearly-half-of-all-irish-computers-depend-on-free-antivirus-for-protection/ https://blog.fox-it.com/2013/02/21/writeup-on-nbc-com-distributing-citadel-malware/ https://www.safegadget.com/38/free-internet-security-software/ http://tecdr.net/antivirus-is-dead/ https://virologydownunder.com/past-time-to-tell-the-public-it-will-probably-go-pandemic-and-we-should-all-prepare-now/ https://geeknewscentral.com/2012/09/20/sophos-anti-virus-deletes-itself-as-a-virus/ https://www.wwm4u.de/blog/2016/02/25/antivirus-auf-dem-mac/ https://www.capestonecart.com/ruthless-scanguard-antivirus-2019-review-strategies-exploited/ https://www.veil-framework.com/framework/veil-evasion/ https://waleedmostafa.wordpress.com/2017/01/14/recommendations-for-antivirus-exclusions-for-scom-2016/ https://www.pandasecurity.com/mediacenter/tips/tips-find-online-love-safely/ https://yongrhee.wordpress.com/2020/03/08/do-macos-need-an-antimalware-antivirus-and-edr-software/ https://fop5.org/website-links/ https://pvinod.com/store-nod32-antivirus-on-your-usb-thumbdrive/ https://j00ru.vexillium.org/about/ https://blog.larga.md/2018/07/15/12-best-free-antivirus-application-for-2018-to-secure-your-pc/ https://weberblog.net/palo-alto-blocks-smtp-virus-with-541-response/ https://badcyber.com/several-polish-banks-hacked-information-stolen-by-unknown-attackers/ https://danielsauder.com/2017/02/04/using-tdm-gcc-with-kali-2/ https://soundmacguy.wordpress.com/2018/11/15/farewell-scep/ https://multimedia-4-all.de/hosting/ http://www.jacopoborga.com/2018/04/08/local-convergence-for-random-permutations-the-case-of-uniform-pattern-avoiding-permutations/ https://ourrighttoknow.ca/blog/3345668/ https://blog.wpsec.com/finding-php-and-wordpress-backdoors-using-antivirus-and-indicator-of-compromise/ https://helpmerick.com/should-you-pay-for-avg.htm http://blog.ismaelvalenzuela.com/2009/01/26/embassy-of-india-in-spain-found-serving-remote-malware-through-iframe-attack/ http://www.deltalounge.net/wpress/ngg_tag/bpm/ https://www.prowell-tech.com/best-security-apps-for-android/ https://sorelia.de/category/antivirus-software/ https://dalewifisec.wordpress.com/2012/03/27/is-free-public-wi-fi-safe/ https://networkguy.de/secure-exchange-webservices-with-sophos-utm-waf/ https://www.securedsector.com/welche-traditionelle-av-software-ist-heutzutage-noch-empfehlenswert-keine/ https://bowenracing.com/colin-bowen-it-services/servicing-and-tune-ups/ http://athlosproject.eu/our-partners/fondazione-irccs-instituto-neurologico-carlo-besta-fincb/uam/ https://www.newyorkcomputerhelp.com/blog/2010/08/19/got-time-warner-internet-then-you-can-also-get-free-antivirus-software-nyc-antivirus-support/ https://mrgnome.wordpress.com/2009/04/01/best-antivirus-detection-rates/ https://www.smart.uk.com/beware-ransomware/ https://avg2019antivirus.wordpress.com/2018/08/15/avg-my-account/ http://thecomputerboys.com/?p=239 https://www.hitech-gamer.com/blog/2018/08/14/battlefield-5-closed-alpha-angespielt/ http://www.usc2014provostfacultyretreat.net/panels-3/ https://techdirectarchive.com/page/5/ https://itltotalsecurity.wordpress.com/2018/02/26/free-antivirus-in-india-for-pc-itl-antivirus/ https://blog.getninjas.com.br/importancia-de-se-utilizar-um-antivirus/ https://www.imploracosmetic.com/twelve-best-absolutely-free-antivirus-computer-software-for-2018/ https://socialjosh.com/free-antivirus-software-programs-for-windows/ https://keyfindings.blog/2019/07/31/unravelling-the-norton-scam-chapter-1/ http://www.nadynerichmond.com/blog/2012/06/21/using-vmware-workstation-to-thwart-a-fake-antivirus-scammer/ http://www.manliocerroni.it/biografia/ https://fixvirus.com/contact-us/ https://tisiphone.net/2017/06/28/why-notpetya-kept-me-awake-you-should-worry-too/ https://blogs.vmware.com/openstack/next-generation-security-services-openstack/ http://www.hoersaal-events.de/jq7ize3/best-movie-apps-2020.html https://www.technobuzz.net/10-best-free-online-virus-and-malware-scanners/2/ https://www.iitr.de/blog/wirklich-schnelle-wegwerf-mailadresse/551/ http://lboc.centrosportivodongnocchi.it/shellcode-evasion.html https://exertia.wordpress.com/2006/05/08/solar-power/comment-page-1/ https://www.awarego.com/what-is-cyber-security-awareness/ https://infosec.engineering/designing-a-defensible-network/ https://osquest.com/2009/07/18/false-positive-from-avast-antivirus-for-windows-live-photo-gallery/ http://www.planb-berlin.com/verlosung-belasound/ https://eyeofrablog.wordpress.com/2017/09/13/windows-console-monitoring/ https://diablohorn.com/2013/02/21/we-bypassed-antivirus-how-about-idsips/ https://www.freesoftwarefiles.com/antivirus/avast-free-antivirus-2015-download/ https://openxcom.org/2014/06/quick-update/ http://tuxdiary.com/2014/10/01/firejail/ https://www.pantheonuk.org/how-is-pii-email-37f47c404649338129d6-error-fixed/ https://nancy-rubin.com/2017/04/03/soup-up-your-business-with-software/ https://cdn.shopify.com/s/files/1/0454/0940/3047/files/smadav_2020_rev_9_7_full_Download_for_free.pdf https://jenomm.com/2015/02/24/like-an-antivirus/ https://www.mcbsys.com/blog/2015/08/hitmanpro-alert-crashes-windows-10-upgrade/ https://ronnydejong.com/2017/10/07/part-1-improve-your-endpoint-security-w-windows-defender-atp-microsoft-intune-windows-defender-antivirus-application-guard/ https://solutionsreview.com/endpoint-security/2016-gartner-endpoint-protection-platforms-magic-quadrant-whats-changed-since-2014/ https://engineersforum.com.ng/2019/03/08/60-nigerian-businesses-suffer-cyber-attacks-stakeholders/ http://mit-freude-tragen.de/2015/07/16/mythosbestetragehilfe/ https://www.r-statistics.com/2011/04/how-to-upgrade-r-on-windows-7/ https://bulbandkey.com/blog/business/how-to-cope-with-challenges-faced-by-small-businesses-and-their-solutions-in-2020/ https://vigneshsharepointthoughts.com/2016/01/14/minimal-download-strategy-feature-in-sharepoint-2013/ https://activationpage.com/usa-kaspersky-com/kavdownload/ http://appletechsolution.com/2020/05/30/secured-your-laptop-mcafee-total-protection-antivirus/ https://www.isitwp.com/best-wordpress-security-plugins-compared/ https://www.infotecblog.com.br/motivos-manter-antivirus-atualizado/ https://www.smartpenguin.org/smartpenguin/1702/lowdown-on-lockdown/ https://www.christophertruncer.com/veil-a-payload-generator-to-bypass-antivirus/ https://welearnsecurity.com/2019/05/19/from-beginner-to-expert-as-penetration-tester/ https://blog.getpaint.net/2014/06/14/paint-net-4-0-beta-build-5278-is-now-available/ https://aracoiaba.pe.gov.br/site/sample-page/ https://stopstalkerware.org/2020/05/27/new-members-and-territories-join-fight-against-digital-violence http://windowsvj.com/wpblog/2010/01/giveaway-win-nod32-antivirus-4-full-version-free-licenses/ https://mueller-tech.com/2018/10/08/what-is-appdefense/ https://win10.support/dataexchangehost-exe-data-exchange-host/ https://oduinn.com/2011/02/23/1797-makefiles/ https://itsupportguys.com/mindful-it-security-tips/ https://stonesoupprogramming.com/2017/07/04/create-node-js-handlebars-express-js-project-from-command-line/ https://www.precontechs.com/top-choices-of-antivirus-ratings-2019/ https://blog.tonerden.com/2020/03/05/warning-an-android-security-app-with-1-billion-downloads/ https://synoguide.com/2014/09/23/documents-shared-link-expire-synology-nas/ https://bjthoughts.com/2011/01/nn8-first-impressions/ https://macfunamizu.com/2008/03/01/future-of-mobile-internet-search-applications/ https://softwaretested.com/windows/how-to-fix-windows-defender-issue-with-17763-195/ https://www.boc.de/watchguard-info-portal/2018/08/webblocker-server-version-1-0-jetzt-ab-fireware-12-2-verfuegbar/ https://sites.northwestern.edu/thesafe/2018/07/24/your-old-computer-is-a-security-risk/ https://www.artofmusic.co.ke/2017/12/13/event-month-strings-keys/ https://rhein.blogactiv.eu/2015/07/30/a-plea-for-tobacco-free-eu-in-2025/ https://sandraestok.com/how-to-test-a-link-is-safe-without-clicking-on-it/ https://kbl24.com/what-is-a-linux-host/ https://www.secpod.com/blog/advantech-webaccess-hmiscada-persistence-cross-site-scripting-vulnerability/ http://floridasecretaryofstate.com/file-a-business-sunbiz-website/ https://blog.bengalbraith.com/2009/09/29/thoughts-on-palm-and-jamie-zawinski/ https://drashna.net/blog/2014/02/sophos-and-a-draconian-firewall/ https://gauravsk98.wordpress.com/2017/07/15/satsang-as-an-antivirus-gaurav-s-kaintura/ https://www.netz-guru.de/2008/08/01/shops-viren-und-kuchen-oder-vortrage-beim-igz-hof/ https://trishkhoo.com/2010/12/go-faster-linking-data-generation-to-hotkeys/ https://solar-network.be/online-casino-erfahrungen/lotto-de-baden-wrttemberg.php https://marienfeldt.wordpress.com/2010/03/22/iphone-business-security-framework/ https://www.theroadtosiliconvalley.com/local-california/mountain-view/ http://mike-graham.co.uk/blog/2014/10/22/change-upn-in-o365-with-ad-sync/ https://vintsvai-msk.ru/eset-nod32-antivirus-not-updating-18567.html https://www.trickscity.com/top-best-antivirus-security-apps-for-android/ https://techtalk.pcmatic.com/2020/05/27/pc-matic-polls-covid-19-work-from-home-trends/ http://www.loosewireblog.com/2005/05/is_antivirus_so.html http://temporao.pt/root-factors-for-paperrater-reviewingwriting-2/ https://miketabor.com/securing-synology-nas/ https://blog.zensoftware.co.uk/2012/12/20/are-you-suffering-from-not-scanned-messages-ending-up-in-your-quarantine-folder/ https://www.geeks3d.com/20080801/3d-printing-in-4-simple-steps-shapeways/ https://www.vuelio.com/uk/wp-content/uploads/2019/10/WP-comments-export-2019_10_25_10_25_41.csv-1.txt https://www.pinterest.com/pin/633811347548327129/ https://www.indiewire.com/2014/11/its-time-to-forgive-the-how-i-met-your-mother-series-finale-67496/ http://thehubfenton.org.uk/jd2ew/global-virtual-apk.html https://runsignup.blog/2017/01/09/runsignup-certified-pci-level-1/ https://marcoramilli.com/2018/10/17/martymcfly-malware-targeting-naval-industry/ https://www.faqforge.com/windows/how-to-speedup-slow-mozilla-thunderbird-email-client-on-windows-7/ https://www.renaultblog.de/ddt4all-neue-version-verfuegbar/ https://www.beris.nl/2020/01/08/ransomware/ https://raas.itpeers.com/en/2018/06/14/dados-seguros/ https://www.glasner.com/2010/10/the-raven/ https://puremodapk.com/avg-pro-apk/ https://ticktocktech.com/blog/2019/04/17/the-most-destructive-computer-viruses/ http://virtuallyrandom.com/c-headers-are-expensive/ https://blog.hwr-berlin.de/elerner/ganz-allein-auf-wolke-7/ http://www.etech.com.my/wp-content/themes/chigue/huw/sccm-deployment-error-0xfffd0000.html https://jasonbrimhall.info/2014/02/04/t-sql-tuesday-051-place-your-bets/ https://blog.frostwire.com/2018/09/27/frostwire-for-android-is-no-longer-available-on-google-play/ https://y0av.me/2015/07/09/s4blyncbluescreen/ https://technewsforyou.com/2010/05/02/macrium-reflect/ https://www.hyperborea.org/journal/2005/08/opera-as-default/ https://www.klangwelt-info.de/2012/10/net-ware-bouncing-boobs-electro-newcomer-sampler/ https://www.operational-security.com/thirty-day-security-challenge/ https://avi.alkalay.net/2007/08/my-new-nokia-e61i.html https://blog.adamsweet.org/?p=250 https://sites.google.com/site/f52ilmem/ConsumerElectronics/compatible-common https://procrastinus.com/2015/07/14/living-in-the-candy-store-and-moving-out/ http://ugne.vapeshopitalia.it/raspberry-pi-print-and-scan-server.html http://waui.centroattivitasportive.it/cf-resolver.html http://higu.claudiapesaresi.it/autotuner-tool-clone.html http://er.nuovalsgroup.it/fmrte-2020-license-key.html http://dkox.rainbowsirmione.it/citrix-netscaler-gateway-saml-configuration-guide.html http://omegalabltd.com/de/boldebold2-4-3/ https://www.thedroidlawyer.com/2011/12/more-on-android-phone-security/ http://hewn.parcodellafavorita.it/access-to-the-path-is-denied-powershell-remove-item.html http://achy.gundam-shop.fr/windows-1909-download.html http://iewp.centrolingueremida.it/qnap-scripts.html http://vxio.kanpisa.it/world-traffic-3-crack.html http://hued.gallitoloco.it/sound-analyzer-mac.html http://ywyl.christmascollection.it/helo-app-free-download.html http://fbu.christmascollection.it/windows-1909-download.html http://sweetgbedu.com/music/free-beats/sweet-gbedu-free-beat-oxlade-away-prod-by-dj-smithbeatz/ http://blog.clymategraphics.com/jrkma/how-to-disable-vbscript-in-windows-7.html https://harmonygwalior.com/4oodqu/unifi-security-gateway-set-dns-server.html https://uem4all.com/2019/03/11/intune-macos-management/ http://www.grupo-lar.com/flrwnmyg/how-to-disable-vbscript-in-windows-7.html https://www.culturamas.es/2016/11/06/el-verdadero-significado-de-la-palabra-kafkiano/ https://commercialcleaningcorp.com/what-is-electrostatic-disinfection-and-how-does-it-work/ https://patchcracks.com/adobe-photoshop-full-crack-key-download/ https://blog.ciaops.com/2020/07/20/attack-surface-reduction-for-windows-10/ https://grannystormcrowslist.wordpress.com/the-list/ https://sethoughts.com/2016/11/11/measuring-tracking-se-teams-solved/ https://kianainteriors.com/fms2qlyf/binani-apk-download.html https://www.cruisinaltitude.com/weeks-app-loungebuddy/ https://oddvar.moe/2017/08/15/research-on-cmstp-exe/ http://www.kiwanja.net/blog/2012/06/back-to-the-future-seventeen-things-you-might-not-know-about-frontlinesms/ https://citedesjeunes.ca/blog/d1e21f-devise-ethiopie-mots-fl%C3%A9ch%C3%A9s
Chemieunternehmen unter https://www.chemieunternehmen.com
0 notes
Text
VMware Announces Intent to Acquire Octarine to Expand Workload Security Solution
Octarine acquisition will bring intrinsic security to containerized applications running in Kubernetes and build security capabilities into the fabric of the existing IT and DevOps ecosystems
Newly created Next-Gen Security Operations Center (SOC) Alliance features industry-leading SIEM/SOAR vendors Splunk, IBM Security, Google Cloud’s Chronicle, Exabeam, and Sumo Logic
PALO ALTO, Calif. and DUDAI, UAE. VMware, Inc. (NYSE: VMW), a leading innovator in enterprise software, made two key announcements during Connect 2020, the company’s annual cybersecurity user and partner conference (hosted virtually by VMware Carbon Black):
The intent to acquire Octarine, whose innovative security platform for Kubernetes applications helps simplify DevSecOps and enables cloud native environments to be intrinsically secure, from development through runtime.
The creation of a Next-Gen SOC Alliance along with Splunk, IBM Security, Google Cloud’s Chronicle, Exabeam, and Sumo Logic. The alliance empowers SOC teams with visibility, prevention, detection and response capabilities that can uniquely leverage the VMware fabric.
Intent to Acquire Octarine to Bring Intrinsic Security to Containers & Kubernetes
Protecting workloads is critical to the security of applications and data inside every organization. The unique properties of the cloud (speed, agility, scale) mean that developers are increasingly using Kubernetes and containers to modernize applications and changing the nature of workloads that need to be secured.
As with any major technology adoption, attackers are not far behind, looking to take advantage of new risk areas. Building Octarine’s innovative Kubernetes security platform into the VMware security portfolio presents a major opportunity for VMware to further mitigate risks in several ways:
Provide full visibility into cloud-native environments so customers can better identify and reduce the risks posed by vulnerabilities and attacks.
Move beyond static analysis and maintain compliance – customers can create and enforce content-based policies to protect the privacy and integrity of sensitive and regulated information.
Integrate into the developer lifecycle to analyze and control application risks before they are deployed into production.
Run alongside service mesh frameworks such as Tanzu Service Mesh to provide native anomaly detection and threat monitoring for cloud and container-based workloads.
Provide runtime monitoring and control of Kubernetes workloads across hybrid environments for threat detection and response.
Following the acquisition’s close, the Octarine technology will be embedded into the VMware Carbon Black Cloud, providing new support of security features for containerized applications running in Kubernetes and enable security capabilities as part of the fabric of the existing IT and DevOps ecosystems. This innovation will further reduce the need for additional sensors in the stack. Octarine capabilities will also integrate and leverage the VMware Tanzu platform, including current investments in Service Mesh and Open Policy Agent.
“Acquiring Octarine will enable us to further expand VMware’s intrinsic security strategy to containers and Kubernetes environments by embedding the Octarine technology into the VMware Carbon Black Cloud,” said Patrick Morley, general manager and senior vice president, Security Business Unit, VMware. “This, combined with native integrations with Tanzu, vSphere, NSX and VMware Cloud Foundation, will create what we believe is a unique and compelling solution for intrinsically securing workloads. And, with the addition of our AppDefense capabilities merged into the platform, we can fundamentally transform how workloads are better secured.”
VMware’s intrinsic security strategy is centered on enriching context from across the security portfolio and leveraging the VMware fabric for native telemetry and control at the endpoint, workload, network, user access point, and application. This innovation enables a true XDR solution that works out of the box with existing VMware solutions – reducing all the bolt-on sensors and appliances that plague security.
For more information on Octarine, click here.
VMware Launches Next-Gen SOC Alliance
In an effort to empower modern SOC teams with the capabilities and context they need to greatly improve both their efficiency and efficacy, VMware has launched a Next-Gen SOC Alliance.
The alliance features Splunk, IBM Security, Google Cloud’s Chronicle, Exabeam, and Sumo Logic integrations with the VMware Carbon Black Cloud to deliver key XDR capabilities and context into SIEM technologies that power the modern-day SOC. Equally important, the combined solutions will be able to take advantage of VMware’s Intrinsic Security framework and enable SOC teams to:
Leverage the VMware fabric – doing away with many of agents and appliances SOCs would normally deploy for visibility, prevention, detection, and response.
Gain far richer context about the infrastructure and applications being protected.
Operationalize more of security with (and through) IT via Carbon Black integrations with VMware management consoles.
Other key benefits from the Next-Gen SOC Alliance include:
Centralized security context, which enables organizations to detect, analyze and respond to data in a unified SIEM at machine speed.
Automation and orchestration tools that combine with XDR capabilities to allow SOCs to scale and standardize their investigation and response processes.
Actionable answers to large-scale queries and remote remediation from within Splunk, IBM Security, Google Cloud’s Chronicle, Exabeam, and Sumo Logic platforms.
“The Next-Gen SOC Alliance brings a critical mass of XDR context and capabilities to SOCs in a fully intrinsic way – one that can uniquely leverage the VMware fabric,” said Tom Barsi, Vice President of Alliances for VMware Carbon Black. “In partnership with the industry’s leading SIEM/SOAR players, we’re setting a strong vision for the modern SOC and delivering unprecedented visibility and remediation capabilities across endpoints, networks, workloads, and containers.”
“Splunk’s Security Operations Suite acts as the backbone for some of the most advanced SOCs in the world,” said Haiyan Song, Senior Vice President and General Manager of Security Markets, Splunk. “As the security industry continues to embrace data at the center of their security strategy, it’s more important than ever to combine the power of Splunk’s industry-leading SIEM and SOAR solutions with XDR to fight back against increasingly sophisticated cyber actors. We are pleased to bring Splunk Enterprise Security and Splunk Phantom to this alliance with VMware Carbon Black and look forward to helping our mutual customers around the world solve their toughest security challenges with data.”
The post VMware Announces Intent to Acquire Octarine to Expand Workload Security Solution appeared first on Businessliveme.com.
from WordPress https://ift.tt/2X4HBpi via IFTTT
0 notes
Link
0 notes
Link
0 notes
Text
VMware купит Pivotal Software и Carbon Black за 4,8 млрд долл.
VMware планирует интегрировать технологии Carbon Black во все свои предложения, включая NSX, Workspace One, AppDefense и Secure State. #vmware #muk #кибербезопасность
http://bit.ly/34cG0QW
0 notes
Text
Original Post from InfoSecurity Magazine Author:
VMware Plans $2.1bn Carbon Black Acquisition
Carbon Black has announced a definitive agreement to merge with VMware, with the virtualization company paying around $2.1bn for the endpoint protection vendor.
With a view to create a “highly differentiated, intrinsic security cloud,” the deal will see VMware be better positioned to better protect enterprise workloads and clients through Big Data, behavioral analytics and AI.
“By bringing Carbon Black into the VMware family, we are now taking a huge step forward in security and delivering an enterprise-grade platform to administer and protect workloads, applications and networks,” said Pat Gelsinger, CEO, VMware.
The combination of Carbon Black’s solutions with VMware’s security offerings, including AppDefense, Workspace ONE, NSX and SecureState, will create a modern security cloud platform for any application, running on any cloud, on any device, the company said. “This combined offering will provide customers advanced threat detection and in-depth application behavior insight to stop sophisticated attacks and accelerate responses,” a statement read.
Patrick Morley, CEO of Carbon Black, said in a blog post that this was “a massive opportunity” as there is an “opportunity here for Carbon Black to truly disrupt the security industry — and ultimately help more customers stay safe from cyber-attacks.”
Morley added: “VMware has a vision to create a modern security platform for any app, running on any cloud, delivered to any device – essentially, to build security into the fabric of the compute stack. Carbon Black’s cloud-native platform, our ability to see and stop attackers by leveraging the power of our rich data and behavioral analytics, and our deep cybersecurity expertise are all truly differentiating. As a result, VMware approached Carbon Black to deliver on this vision.
“Our product strategy stays the same. Our roadmap stays the same. Our customer support stays the same. The entire product portfolio, cloud and on-premises, is included in the merger – now backed by the extensive global footprint and GTM resources from VMware. In fact, the plan is to invest more aggressively in Carbon Black and leverage our combined strengths to accelerate our growth and execute our vision for our customers.”
Carbon Black will exist as an independent business unit within VMware, and become VMware’s Security Business Unit. Launched in 2007 as Bit9, the company was known as Bit9 & Carbon Black after it acquired Carbon Black in February 2014, and officially assumed the company name Carbon Black in February 2016.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: VMware Plans $2.1bn Carbon Black Acquisition Original Post from InfoSecurity Magazine Author: VMware Plans $2.1bn Carbon Black Acquisition Carbon Black has announced a definitive agreement to merge with…
0 notes
Text
VMware vSphere Platinum Edition "End to End Security with VMware"
VMware vSphere Platinum Edition “End to End Security with VMware”
Do you know there is a new edition from VMware called as vSphere Platinumthat delivers advanced security capabilities fully integrated into the hypervisor?. This new release combines the industry-leading capabilities of vSphere with VMware AppDefense, delivering purpose-built VMs to secure applications. With these new capabilities, vSphere Platinum secures infrastructure and applications by…
View On WordPress
0 notes
Link
Chris Corde, Senior Director, Product Management, VMware An introduction to the AppDefense product, including an overview of the challenges that AppDefense solves, the product’s architecture, and a demo.
© Gestalt IT, LLC for Tech Field Day: VMware AppDefense
0 notes
Text
VMware vSphere Platinum Edition & vSphere 6.7 Update 1
By Curtis Brown
As an efficient and secure platform, VMware vSphere® provides a powerful and flexible foundation for business that accelerates the transformation to hybrid cloud. With vSphere you can support new workloads and use cases while keeping pace with the growing needs and complexity of the SDDC infrastructure.
One of the announcements that coincided with this years VMworld 2018 event in Las Vegas was VMware vSphere 6.7 Update 1 and a new variant of VMware vSphere – Platinum Edition. In this blog I look at the main highlights of this new release and the related new edition.
Platinum Edition
Platinum Edition sits above VMware vSphere Enterprise Plus, inheriting its feature set but adds the following:
VMware AppDefense VMware AppDefense is an integrated component in Platinum Edition. It provides a powerful, yet interesting approach to security. Rather than taking the approach of actively monitoring for expected threat vectors (such as monitoring TCP/UDP ports, looking for malware etc), AppDefense uses machine learning to establish knowledge of the ‘known good’ state of a VM – it is aware of what traffic comes from, or travels to, the VM and so picks up how the VM behaves in normal operation.
If the VM strays from this normal operation, AppDefense raises the alarm. Taking this approach is more resource efficient than active solutions seeking known vectors, while also providing greater coverage for new attack vectors by watching for changes in behaviour from ‘known good’ rather than trying to look for ‘known bad’.
Credits for VMWare Cloud on AWS For those purchasing 5 vCPUs or more, VMware will include $10,000 worth of AWS credits as part of a promotion once Platinum Edition is released as General Availability.
vSphere 6.7 Update 1
In parallel to the release of Platinum edition, VMware vSphere reaches 6.7 Update 1. This builds upon the previous 6.7 release by adding the following:
VM Encryption meeting US Government FIPS 140-2 Validation requirements as well as encryption of cross-vCenter vMotion traffic.
Support for Trusted Platform Module (TPM) 2.0:
At the hardware level, providing security for the ESXi installation itself.
At the VM level as a virtual TPM to allow features such as Microsoft Virtualization Based Security to be enabled fully.
Improvements in Security Access Logging for audit purposes.
Fully featured HTML5 vSphere Client covering all vSphere capabilities.
Enhanced Content Library
Closing Thoughts
VMware vSphere, by VMware’s own admission, is now a mature product, however, it continues to evolve providing enhancements to manageability, performance and security. It probably doesn’t get the attention it deserves, but as the underpinning of most of VMware’s solutions, vSphere is as important as ever to VMware.
In light of the imminent end of support for VMware vSphere 5.5, the release of 6.7 Update 1 emphasises the importance of maintaining currency with the latest release, not merely for shiny new features, but to maintain and enhance security in an ever-dangerous world.
Xtravirt is a leading cloud and virtualisation consultancy and VMware specialist with the ultimate combination of deep experience and agility to design and deliver IT transformations. We are also the VMware Global Professional Services Partner of the Year.
If you need assistance in getting the best from VMware vSphere, please contact us, and we’d be happy to use our wealth of knowledge and experience to assist you.
Useful links
Under the Hood - VMware vSphere Platinum Edition
Under the Hood – vSphere 6.7 update 1
Xtravirt Upgrade Service for VMware vSphere
Virtualisation health check service for VMware vSphere
About the Author
Curtis Brown joined the Xtravirt consulting team in October 2012. His specialist areas include End User Compute solutions and Virtual Infrastructure design and implementation with particular strength in VDI, storage integration, backup and Disaster Recovery design/implementation. He was awarded VMware vExpert 2018.
0 notes