#this was 107+ layer btw
Explore tagged Tumblr posts
Text
So you may be aware that recently i got into quite the pokemon ranger (guardian sign) brainrot

Always loved this game and always loved the idea of being a ranger and i also talked recently about how it fitted like a puzzle piece in what i already made of my character story that i made after having played PLA
#i never loved being able to draw so much#this was 107+ layer btw#i hate procreate#csp is much more easy to use for me but the ipad is also easier than graphic tablet#digital art#oc#self insert#pokemon#pokemon ranger#pokemon ranger guardian signs#pokemon ranger guardian signs fanart#pokemon ranger fanart#pokemon fanart#nashi Emilie#nashi emilie art#nashi's art#tiziri art
5 notes
·
View notes
Text
on hua cheng's morality and self esteem
on my first read of the book, i was actually convinced that hua cheng was this amoral asshole but that's just what he WANTS you to think. hua cheng actually cares a lot about ghost city (founded to combat the injustice of ghost persecution btw), he just downplays his achievements in front of xie lian because he doesn't want to 'trick' him into liking him. he also sees any accomplishments as a direct result of dianxia's influence so it would be wrong to take credit for them. perhaps hundreds of years of playing the part of the terrible calamity skewed his perception of himself even further.
in his introduction in heaven, they say how he would "Sometimes... carry out a massacre in cold blood, and sometimes he would do odd acts of kindness" (page 157, book 1) which makes me wonder what heaven defines as "cold blood." he visibly dislikes the man who bet his daughter's life and mentions killing several tyrants. in creating e'ming, he nearly destroyed himself in order to save those mortals. on the casino in ghost city, "If I don’t control a place like this, then someone else will. I’d rather that person be me." (page 107, book 2.) he has a very strong sense of justice that he hides under 3 million layers of arrogance.
xie lian gets the ability to tell if he is lying early in the book and sees him for who he really is. they're very similar in that they have this drive to do good in the world but think about it and go about it in very different ways. hua cheng even mentions that it doesn't matter how you go about saving the common people, and that xie lian over-complicates what is right and wrong and should do what he wants... but he wouldn't turn that logic on himself :/
anyway

**this is my reading btw if anybody wants to have a discussion im 100% down
#this started out as a joke about how i sometimes have very coherent analysis about him and sometimes i can only go hrgrhrghrgr#but i have too many thoughts about him. plus i'm working on a characterization reference guide and reread books 1 and 2 yesterday#so my head's full of textual evidence✨#on your first read of an mxtx book you fall for the parts the characters are playing. on the second read you get knocked out#from how well put together and connected everything is. and on the third read your third eye opens#tgcf#i speak#hua cheng#xie lian#hualian#tgcf meta#meta#tgcf analysis
340 notes
·
View notes
Text
Let's talk about Chapter 107- Part Deux (Ex Machina)
Man. Man.
Follow up post from this. Might as well keep this as a series because I guess verbal diarrhoea is a coping mechanism for me. Thoughts and predictions again. Spoilers below


So it appears that yes, Hiyori is 100% dead now since we saw her memories through Yato (broke my fucking heart btw) and we're going down the shinki route.
Yato didn't want to name her. He had no choice. He had just watched the love of his life be murdered right in front of him and was about to see her be transformed into his Father's monstrous puppet. Naming her there and then before Father got the chance to was the only way to save her. This is the most brutal fucking chapter in the entire series I swear to GOD. (Though I think most of us can agree that from the small glimpse of Hakki we have so far, she looks gorgeous. That sakura design.. 🥺)
But seriously I'm hoping and praying that Hiyori is somehow going to retain her memories and either bypass the GGS or be pretty much immune to it. Like I said before, she's a special case. Because she already had ties to the Far Shore and to multiple gods, she might get a sort of get out of jail free card here. Plus it would just interrupt the flow of the finale to a really weird extent if she lost all of her memories. It'd be too jarring and weird imo. Perhaps she initially has all of them but then over time her Near Shore memories will eventually fade away.
(Reiterating what I said in the previous post. I have no idea how this is going to affect other shinkis with her being around in regards to the GGS. Or even if her existence will be allowed by Amaterasu. It's not like Ammy can wipe everyone's memories of Hiyori to safeguard them. But hey)
Also the fact that his shinkis are literally Snow White? Lol.
Lets say she retains her memories. Will she still be called Hiyori or will she have to go by Shirone even if hearing her name won't break her? Maybe it'll be a closely guarded secret by her and Yato. Having her name on a part of her body that can't be seen (like over her heart for instance because thematics) means it's hidden from view from anyone else, therefore nobody can use that name against her (KAZUMA. 👀) An extra layer of protection for her. It'll be her and Yato's (and probably Yukine's too) secret.
Speaking of Yukine, I'm guessing he's going to be out of action for this final final fight. With Hiyori slicing the Koto No Ha in half like an absolute boss ass bitch, it's likely that The Nation will collapse and everyone will return to their regular forms. Yukine will probably be in a bad shape and unfit to fight let alone even transform into Sekki. Meaning it's going to be Yato and Hiyori Vs Father working together as one. The Deux Ex Machina has appeared and she is pissed.

(Literally though, first thing she does as a weapon is take a slice at Father and the brush. I didn't even realise she'd cut his fingers til the second read through. Looks like she might have even got his neck too? Dare I say...? Slay?)
So yeah. I'm hoping that because of her original ties to Yato and the Far Shore, her memories may not be lost. The two of them will team up to take down Father as possibly the most powerful shinki we've seen so far. Nobody has been able to make a dent in the Koto No Ha until now. Which is possibly why this is why the story is going this way. Yato has tried and failed to take down Father multiple times. He couldn't use Yukine for his final confrontation for obvious reasons so he went on a search to find a suitable and powerful enough shinki to take his place, and that ended up being Kazuma. Obviously didn't work out as intended though.
Funny how maybe the person he's needed to take down Father all along is Hiyori. Father might have ended up winning in the end but by killing her, he's essentially doomed himself.
#noragami spoilers#give me power of love bullshit I wanna see these two kick ass together in harmony#BE OK. LIVE. REMEMBER. KILL.#noragami
15 notes
·
View notes
Text
I reached the image limit of the last post so im making another post
Anyway, TLDR, i try to get the password given any hash, but after some math i kinda failed.
Also for lure, "sukimtnqocjr" is also the correct password.
The related codes are here:

So we have this simple_hash function. We have the hash (DE gave us in the source code), and we wanna find a password (i.e., a list of integers) that works for this hash.
tbh as long as they don't obfuscate their code you don't have to do this, just change every password hash to a known password hash and you can unlock any file. BUT let's just say you want the original password with brute force, or DE actually obfuscated their code...
This function is not really easy to reverse, mostly because it's not linear. You see, javascript does left shift in singed 32bit integer, and that screws with the linearity.
But it does look linear, isn't it? Let's look at another version of this code:

That looks so linear... but only when you operate in Z/2^32Z.
Assume a simpler case: let's say we have a password of length 4: [x_3, x_2, x_1, x_0]. If we define
m := 2^6 + 2^16 - 1 = 65599
n := 2^32
we know the hash of simple_hash_v2 (h) will be:

We just have to somehow solve all x, given h, m and n.
Do note that all x are small, like smaller than K := 256 (because ASCII). For small numbers we have something to use in cryptography: lattices, shortest vector problem (SVP), and Lenstra-Lenstra-Lovász (LLL) Algorithm. (I absolutely hate this but this direction seems good.)
Skipping all the explanation on how lattices, SVP and LLL works, note that for the below given lattice B, there is a small vector v in this lattice, and we can very possibly find it with LLL:

We do need the password length to make this matrix, but we can just brute force all lengths or try a huge length and say some x at the front are 0.
Let's experiment with this. Given password "khra" = [107, 104, 114, 97], we expect [-97, 107, 104, 114, 256] in the lattice.

Well, that's weird. Do note that the answer is in there: adding the 2nd and 3rd row give us the correct answer. As long as you have a lattice that fits some condition below, that lattice can be a correct password (It might not be the password DE sets but that just means we have collision):
The first element is negative
Every element has magnitute less than K
The final element is K
But you can see the problem: our vector may not be so small that LLL can find it easily...
Trying the actual password "khrajahuxata" and the appropriate lattice matrix:

That is absolutely terrible. We can't even linear combine the rows to get what we want. This only gets worse when our password length is longer.
I'm not that good with cryptography so maybe this lattice is just shitty and I can't find a better one. Or it's just not appropriate to use LLL when you have a ton of unknowns. I don't know. I spent hours on this instead of doing actual work I'm supposed to do. Anyway don't brute force the password.
btw the z3 solver took 2 hours for this input

I mean, it's the wrong result, sure, but it's the correct hash so the page won't even complain about this.
You can try the password "sukimtnqocjr" and you can see that it actually works on the page. That's a cool hash collision. Just kidding that just means this hash is too weak. Don't use linear-like hashes okay at least add like one nonlinear layer like how AES does.
HOLY FUCK
www.doctorentrati.com
also im playing with it rn so spoiler below. expect editing
fuck i feel like im playing ctf

manually delete the is-hidden class works
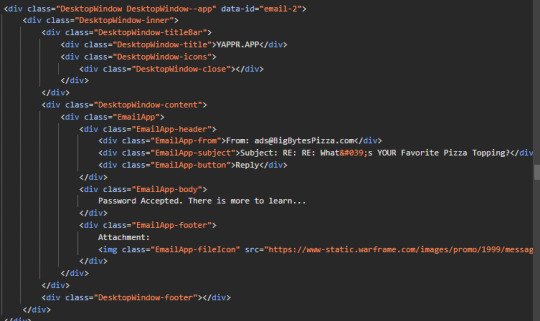
OH NO... why don't you encrypt the content with the password...
I mean you can check the password by comparing it with hash and use the real password to encrypt and decrypt the thing... your javascript code is indeed obfuscated, if you change something in the encryption algorithm to make it not trivial to solve the password (e.g., change AES's subByte table) then I would rather actually solve this than de-obfuscate the code.
just don't show everything when people inspect the website okay
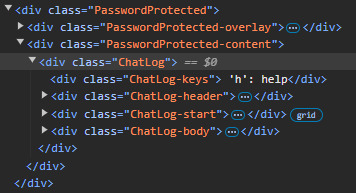
yes very protected
---https://www.reddit.com/r/Warframe/comments/1gc4zwc/arg_thread_reference_post_to_everything_use_this/
oh nevermind they still kinda did that
also wtf i definitely can't figure most of these out
someone said it's only possible to unlock the first file and i can kinda see that
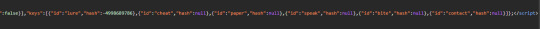
so they do use a hash to do the password thing (which is standard), aaaand the rest of the hash is null so the files are not meant to be solved for now
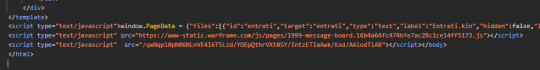
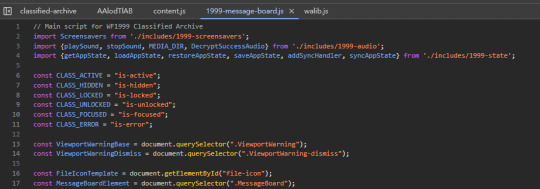
oh no... i looked at the wrong file, this is not obfuscated and is the main logic. Now I don't know what the file "/qwNqpl0pN06NLnVE4I6T5Lzd/YOEpQthrVXt0SY/IntzETIaAwk/Kxd/AAlodTlAB" does.
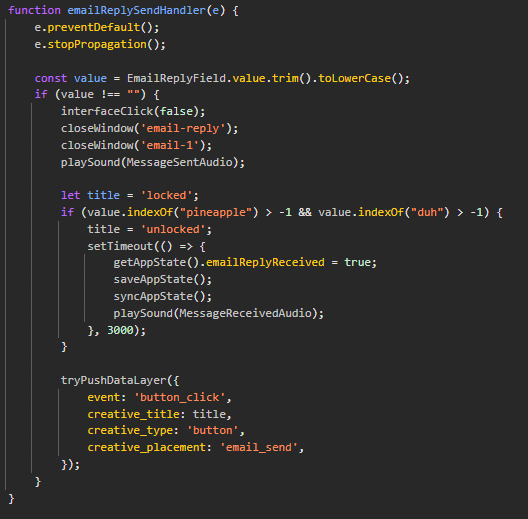
That's why you should obfuscate the code guys the correct email reply is literally written in there
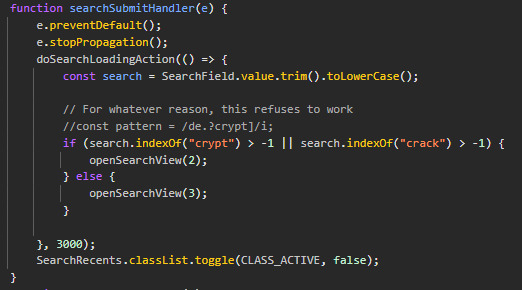
i guess you don't need to use the hint in ascloid just type "crypt" and it still works
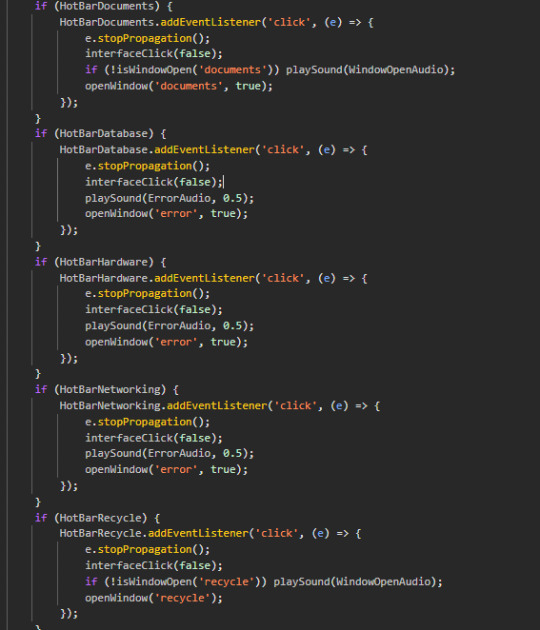
seems like the rest of the hotbar literally does nothing. you can't unlock it or anything, i guess it's for the later versions of the ARG
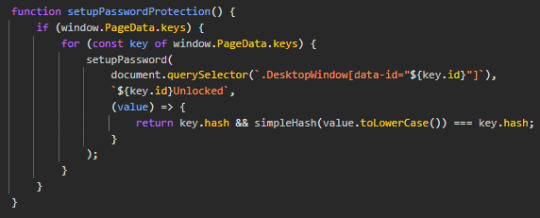

we do have the hash... i wonder if we can z3 brute force other passwords...
okay that's it. i mean i didn't really solve anything, other people already solved this. i think i have the most fun looking through the source code... which doesn't take much time compared with the time i took looking for the password the legitimate way and failed miserably
also please obfuscated your code DE i mean if this is a proper ARG we shouldn't able to cheat like this. at least not that simply

okay... i guess brute force with z3 is harder than i thought. i don't know how much time solving "khrajahuxata" would take and i'm already limiting my search space in lowercase letters only
27 notes
·
View notes
Text
Paint Them Pink-Jordan Parrish
Valentine’s Collection:#8
Teen Wolf Imagine:#107
Word Count: 1,530
Warnings: None that I can think of?
Summary: Jordan schedules a pamper session for Y/N and himself.
A/n: I thought I was never going to get this done but here it is! (I really enjoyed writing for Jordan btw)
tagging @joeynihil again because... Parrish


Masterlist
Coming Soon
Last Imagine
It had been a long few months in Beacon Hills, though that’s how it always felt. As if time was dragging on and on and there was never more than a moment to breathe. It was exhausting. Parrish, a deputy and a hellhound, found himself constantly on the move. He was either on the job or fighting supernatural creatures, sometimes both, and that left very little time for his girlfriend.
Jordan had been dating Y/N, a 24-year-old teacher’s aid and banshee, for a few years. They lived together and spent as much time together as they could but most of their time together was interrupted by one thing or another.
But not tonight. Parrish decided that nothing was going to interrupt them tonight, and they were going to relax - really relax - for the first time in months.
When Y/N walked into their home after work a bit later than usual she found all the lights off and candles set up all around the living room. Jordan pulled away from lighting the last candle and turned around to greet her wearing nothing but his bathrobe.
“What’s all of this?”
“You and I are going to relax and have some fun. I brought out all your face masks so we can choose some of them to do and nail polish so I can paint your nails, and I’ve been watching videos online about how to give a massage and I might just show you what I’ve learned.”
“You happened to come across a lot of porn didn’t you?”
Jordan sighed. “So much porn.”
Y/N laughed and kissed his cheek. “Well, when do we get started?”
“Right now, go get your robe on and meet me back out here.”
“Just my robe?” She asked.
“Just your robe.” He assured.
“Then, I’ll be right back.” She pecked Jordan quickly on the lips before striding over to the bedroom.
A few minutes later Y/N came back into the living room makeup removed from her face, hair pulled back into a bun and wearing a plush white bathrobe that matched Jordans, a Christmas present from her mother with their names embroidered in gold on the left side.
“Hey hot stuff.” Jordan smiled, wrapping Y/N in a hug.
Y/N laughed and hit Jordan slightly on the chest. “I was literally just out here.”
“Yeah, and then you went away, now you’re back and you look good.” Jordan explained holding her closer.
“You’re such a dork.”
“But I’m a dork who loves you.”
“And I love you.” She smiled before kissing him softly then pulling away completely.
“So mask time?” Jordan asked moving back toward the couch.
“Mask time, what one do you want to use?” Y/N asked looking at the colored tubes on the coffee table.
“I don’t know, what are you using?”
“Probably the Chocolate and Strawberry clay mask. I love how it smells.” She replied, picking up the pink tube and reading the back.
“What do you think I should use?”
“Probably the anti-stress one. You are a stressed out hellhound plus it will soothe your skin. You’ll love it.” She explained with a smile.
“Anti-stress it is.” Jordan smiled, snatching the blue container off the table.
“I’ll do yours first.” Y/N said taking the tube from his hands and squeezing some onto her fingers and placing her hand to Jordan’s forehead.
His face scrunched up as she rubbed the mask over his skin. “Oh, that’s cold.”
Y/N eyed you but continued to apply the mask with a straight face. “Try not to move your face too much, it will make the clay dry weird on your face.”
“You look so serious.” Jordan laughed, making a face.
“What did I say about moving your face?” She questioned with a laugh, dabbing more mask onto his nose.
“Sorry.” Jordan straightened out his face, watching the woman before him spread an even layer of substance all over his face, smiling when she had finally completed her job.
“I’ll do yours.” He offered, taking the pink tube from Y/N’s lap.
“You don’t have to.” She assured, trying to reach for the tube her boyfriend was now squeezing in his hands.
“I want to.” He stated, turning to Y/N with his fingers coated in the pink substance.
She sighed. “Alright.”
“Okay, so how do I do this?”
“You looked up how to give a massage but you didn’t think to look up how to apply a face mask?” She asked with a chuckle.
“It didn’t come to mind.”
“Step one, put some on your fingers, you’ve already completed step one. Step two, spread it around on my face. Try not to get it in my eyes, nose, or mouth.”
“I think I can manage that.” Jordan then went to work spreading an even coat over her face.
Y/N smiled slightly as she watched a straight faced Jordan concentrate on the task before him. “Now who’s serious.” She noted with a laugh.
“I’m trying not to blind you.”He laughed, his fingers running under her eyes before pulling away from her face completely. “There I think you’re good.”
“Good. We leave them on until they’re completely dry then we wash them off.” Y/N explained placing the masks back onto the table.
“Can I kiss you while this is on?”
“I don’t see why not.”
“Good.” Jordan smiled and quickly leaned into kiss her on the lips. They were both careful not to ruin their masks.
After pulling away from the kiss the two sat and talked about their day, Y/N’s feet resting in Jordan’s lap as they laughed together. But it wasn’t long before they were washing the masks from their faces laughing and nudging each other from in front of the bathroom mirror. Though they soon returned to the couch, back to their original positions.
“Nails?” Jordan asked.
Y/N thought a moment before nodding her head. “Nails.”
��What color do you want?”
“Pink.”
“There are 10 different shades of pink over here.”
“Close your eyes and pick.” She replied. Jordan reached from a pale pink with sparkles. “Not that one.” He then reached for a pink that looked much more like a red. “No not that one either.” Then he picked up a medium pink that she was sure had to be from years ago.“Or that one.” This time he picked up a hot pink that reminded her of summer. “Oh, that one, I like that one.”
Jordan chuckled slightly and began to shake the nail polish. “Why didn’t you just ask for this one then?”
“I wasn’t sure what one I wanted until you picked it up.” She explained.
“I love you, but you’re kind of annoying sometimes.”
“I love you too.” She leaned forward and pressed a quick kiss to his lips.
Jordan smiled and began to paint her nails, dragging the lacquer covered brush over her nails slowly and paying careful attention of any that got onto her fingers. He was completely silent the entire time, not looking up once. Y/N watched him admiringly until he finished each finger, blew on them for a moment then moved onto her toes.
He was as careful with her toes as he had been with her fingers. Long and delicate strokes over each nail until it was covered in the color that reminded her so much of summer.
“Done.”
“Yay! Can I do yours now?”
“Yeah but you have to paint them with that clear stuff, no painted nails at work. Unfortunately it’s hard to be a professional deputy when you have pink fingernails.” Jordan explained with a furred brow and slight pout.
Y/N took Jordan’s hand in her’s and began coating his nails in the clear shining liquid.
“Can I do your toes too?” She asked with a sweet smile.
Jordan pretended to think for a moment before nodding his head. “Yes.”
“The top coat still?”
Jordan shook his head and pointed to the color he had just used on her. “No, paint them pink.”
“I thought they had to be clear, for work.”
“My hands yeah, but our toes can match. So paint them pink.”
She smiled and reached for the small bottle. “Pink it is.”
Y/N picked up the color that Jordan had just used on her and began to paint his toes in the bright color that was quickly becoming her favorite. When she was finished she blew on them lightly and moved back to rest her legs over Jordan’s.
The two sat talking as their nails dried. When the paint was finally firm to the touch, Jordan began to rub at Y/N’s calves and ankles.
“So, do you want me to try out that massage stuff I learned?”
“I think I’ll pass.” Y/N said, taking her legs from his lap and standing up beside the couch.
“Don’t you want to relax a bit more?” He asked, trying to convince her. He had worked hard on learning these skills and he kind of wanted to show off.
“Yeah, but I have another method in mind.” Y/N said with a smile, then dropped her robe.
@imaginesandsmutforusfreaks @girlwiththebow
#jordan parrish#jordan parrish imagine#jordan parrish imagines#jordan parrish one shot#jordan parrish one shots jordan parrish fanfic#jordan parrish fanfiction#jordan parrishxreader#teen wolf#teen wolf imagine
270 notes
·
View notes
Link
(Via: Hacker News)
G. Graefe and P. A. Larson. B-tree indexes and CPU caches. In Proceedings 17th International Conference on Data Engineering, pages 349–358, 2001.
S. Richter, V. Alvarez, and J. Dittrich. A seven-dimensional analysis of hashing methods and its implications on query processing. Proc. VLDB Endow., 9(3):96–107, Nov. 2015.
B. Fan, D. G. Andersen, M. Kaminsky, and M. D. Mitzenmacher. Cuckoo filter: Practically better than bloom. In Proceedings of the 10th ACM International on Conference on Emerging Networking Experiments and Technologies, CoNEXT ’14, pages 75–88, New York, NY, USA, 2014. ACM.
K. Alexiou, D. Kossmann, and P.-A. Larson. Adaptive range filters for cold data: Avoiding trips to siberia. Proc. VLDB Endow., 6(14):1714–1725, Sept. 2013.
M. Abadi, P. Barham, J. Chen, Z. Chen, A. Davis, J. Dean, M. Devin, S. Ghemawat, G. Irving, M. Isard, et al. Tensorflow: A system for large-scale machine learning. In OSDI, volume 16, pages 265–283, 2016.
A. Crotty, A. Galakatos, K. Dursun, T. Kraska, C. Binnig, U. Çetintemel, and S. Zdonik. An architecture for compiling udf-centric workflows. PVLDB, 8(12):1466–1477, 2015.
N. Shazeer, A. Mirhoseini, K. Maziarz, A. Davis, Q. Le, G. Hinton, and J. Dean. Outrageously large neural networks: The sparsely-gated mixture-of-experts layer. arXiv preprint arXiv:1701.06538, 2017.
N. Shazeer, A. Mirhoseini, K. Maziarz, A. Davis, Q. Le, G. Hinton, and J. Dean. Outrageously large neural networks: The sparsely-gated mixture-of-experts layer. arXiv preprint arXiv:1701.06538, 2017.
Y. Wu, M. Schuster, Z. Chen, Q. V. Le, M. Norouzi, W. Macherey, M. Krikun, Y. Cao, Q. Gao, K. Macherey, et al. Google’s neural machine translation system: Bridging the gap between human and machine translation. arXiv preprint arXiv:1609.08144, 2016.
C. Kim, J. Chhugani, N. Satish, E. Sedlar, A. D. Nguyen, T. Kaldewey, V. W. Lee, S. A. Brandt, and P. Dubey. Fast: Fast architecture sensitive tree search on modern cpus and gpus. In Proceedings of the 2010 ACM SIGMOD International Conference on Management of Data, SIGMOD ’10, pages 339–350, New York, NY, USA, 2010. ACM.
E. R. Sparks, A. Talwalkar, D. Haas, M. J. Franklin, M. I. Jordan, and T. Kraska. Automating model search for large scale machine learning. In Proceedings of the Sixth ACM Symposium on Cloud Computing, SoCC 2015, Kohala Coast, Hawaii, USA, August 27-29, 2015, pages 368–380, 2015.
F. Chang, J. Dean, S. Ghemawat, W. C. Hsieh, D. A. Wallach, M. Burrows, T. Chandra, A. Fikes, and R. Gruber. Bigtable: A distributed storage system for structured data (awarded best paper!). In 7th Symposium on Operating Systems Design and Implementation (OSDI ’06), November 6-8, Seattle, WA, USA, pages 205–218, 2006.
D. G. Severance and G. M. Lohman. Differential files: Their application to the maintenance of large data bases. In Proceedings of the 1976 ACM SIGMOD International Conference on Management of Data, SIGMOD ’76, pages 43–43, New York, NY, USA, 1976. ACM.
F. Chang, J. Dean, S. Ghemawat, W. C. Hsieh, D. A. Wallach, M. Burrows, T. Chandra, A. Fikes, and R. Gruber. Bigtable: A distributed storage system for structured data (awarded best paper!). In 7th Symposium on Operating Systems Design and Implementation (OSDI ’06), November 6-8, Seattle, WA, USA, pages 205–218, 2006.
G. E. Hinton, O. Vinyals, and J. Dean. Distilling the knowledge in a neural network. CoRR, abs/1503.02531, 2015.
J. G. Cleary. Compact hash tables using bidirectional linear probing. IEEE Trans. Computers, 33(9):828–834, 1984.
M. Turcanik and M. Javurek. Hash function generation by neural network. In 2016 New Trends in Signal Processing (NTSP), pages 1–5, Oct 2016.
J. Wang, H. T. Shen, J. Song, and J. Ji. Hashing for similarity search: A survey. CoRR, abs/1408.2927, 2014.
J. Guo and J. Li. CNN based hashing for image retrieval. CoRR, abs/1509.01354, 2015.
F. Chang, J. Dean, S. Ghemawat, W. C. Hsieh, D. A. Wallach, M. Burrows, T. Chandra, A. Fikes, and R. Gruber. Bigtable: A distributed storage system for structured data (awarded best paper!). In 7th Symposium on Operating Systems Design and Implementation (OSDI ’06), November 6-8, Seattle, WA, USA, pages 205–218, 2006.
M. Mitzenmacher. Compressed bloom filters. In Proceedings of the Twentieth Annual ACM Symposium on Principles of Distributed Computing, PODC 2001, Newport, Rhode Island, USA, August 26-29, 2001, pages 144–150, 2001.
I. Goodfellow, J. Pouget-Abadie, M. Mirza, B. Xu, D. Warde-Farley, S. Ozair, A. Courville, and Y. Bengio. Generative adversarial nets. In Advances in neural information processing systems, pages 2672–2680, 2014.
I. Sutskever, O. Vinyals, and Q. V. Le. Sequence to sequence learning with neural networks. In Advances in neural information processing systems, pages 3104–3112, 2014.
A. Graves. Generating sequences with recurrent neural networks. arXiv preprint arXiv:1308.0850, 2013.
K. Cho, B. van Merrienboer, Ç. Gülçehre, D. Bahdanau, F. Bougares, H. Schwenk, and Y. Bengio. Learning phrase representations using RNN encoder-decoder for statistical machine translation. In Proceedings of the 2014 Conference on Empirical Methods in Natural Language Processing, EMNLP 2014, October 25-29, 2014, Doha, Qatar, A meeting of SIGDAT, a Special Interest Group of the ACL, pages 1724–1734, 2014.
S. Abu-Nimeh, D. Nappa, X. Wang, and S. Nair. A comparison of machine learning techniques for phishing detection. In Proceedings of the anti-phishing working groups 2nd annual eCrime researchers summit, pages 60–69. ACM, 2007.
R. B. Basnet, S. Mukkamala, and A. H. Sung. Detection of phishing attacks: A machine learning approach. Soft Computing Applications in Industry, 226:373–383, 2008.
G. Graefe and P. A. Larson. B-tree indexes and CPU caches. In Proceedings 17th International Conference on Data Engineering, pages 349–358, 2001.
R. Bayer and E. McCreight. Organization and maintenance of large ordered indices. In Proceedings of the 1970 ACM SIGFIDET (Now SIGMOD) Workshop on Data Description, Access and Control, SIGFIDET ’70, pages 107–141, New York, NY, USA, 1970. ACM.
T. J. Lehman and M. J. Carey. A study of index structures for main memory database management systems. In Proceedings of the 12th International Conference on Very Large Data Bases, VLDB ’86, pages 294–303, San Francisco, CA, USA, 1986. Morgan Kaufmann Publishers Inc.
R. Bayer. Symmetric binary b-trees: Data structure and maintenance algorithms. Acta Inf., 1(4):290–306, Dec. 1972.
J. Boyar and K. S. Larsen. Efficient rebalancing of chromatic search trees. Journal of Computer and System Sciences, 49(3):667 – 682, 1994. 30th IEEE Conference on Foundations of Computer Science.
J. Rao and K. A. Ross. Making b+- trees cache conscious in main memory. In Proceedings of the 2000 ACM SIGMOD International Conference on Management of Data, SIGMOD ’00, pages 475–486, New York, NY, USA, 2000. ACM.
C. Kim, J. Chhugani, N. Satish, E. Sedlar, A. D. Nguyen, T. Kaldewey, V. W. Lee, S. A. Brandt, and P. Dubey. Fast: Fast architecture sensitive tree search on modern cpus and gpus. In Proceedings of the 2010 ACM SIGMOD International Conference on Management of Data, SIGMOD ’10, pages 339–350, New York, NY, USA, 2010. ACM.
C. Kim, J. Chhugani, N. Satish, E. Sedlar, A. D. Nguyen, T. Kaldewey, V. W. Lee, S. A. Brandt, and P. Dubey. Fast: Fast architecture sensitive tree search on modern cpus and gpus. In Proceedings of the 2010 ACM SIGMOD International Conference on Management of Data, SIGMOD ’10, pages 339–350, New York, NY, USA, 2010. ACM.
A. Shahvarani and H.-A. Jacobsen. A hybrid b+-tree as solution for in-memory indexing on cpu-gpu heterogeneous computing platforms. In Proceedings of the 2016 International Conference on Management of Data, SIGMOD ’16, pages 1523–1538, New York, NY, USA, 2016. ACM.
K. Kaczmarski. B + -Tree Optimized for GPGPU.
M. Böhm, B. Schlegel, P. B. Volk, U. Fischer, D. Habich, and W. Lehner. Efficient in-memory indexing with generalized prefix trees. In Datenbanksysteme für Business, Technologie und Web (BTW), 14. Fachtagung des GI-Fachbereichs ”Datenbanken und Informationssysteme” (DBIS), 2.-4.3.2011 in Kaiserslautern, Germany, pages 227–246, 2011.
T. Kissinger, B. Schlegel, D. Habich, and W. Lehner. Kiss-tree: Smart latch-free in-memory indexing on modern architectures. In Proceedings of the Eighth International Workshop on Data Management on New Hardware, DaMoN ’12, pages 16–23, New York, NY, USA, 2012. ACM.
E. Fredkin. Trie memory. Commun. ACM, 3(9):490–499, Sept. 1960.
V. Leis, A. Kemper, and T. Neumann. The adaptive radix tree: Artful indexing for main-memory databases. In Proceedings of the 2013 IEEE International Conference on Data Engineering (ICDE 2013), ICDE ’13, pages 38–49, Washington, DC, USA, 2013. IEEE Computer Society.
G. Graefe and P. A. Larson. B-tree indexes and CPU caches. In Proceedings 17th International Conference on Data Engineering, pages 349–358, 2001.
J. Goldstein, R. Ramakrishnan, and U. Shaft. Compressing Relations and Indexes. In ICDE, pages 370–379, 1998.
T. Neumann and G. Weikum. RDF-3X: A RISC-style Engine for RDF. Proc. VLDB Endow., pages 647–659, 2008.
H. Zhang, D. G. Andersen, A. Pavlo, M. Kaminsky, L. Ma, and R. Shen. Reducing the storage overhead of main-memory OLTP databases with hybrid indexes. In Proceedings of the 2016 International Conference on Management of Data, SIGMOD Conference 2016, San Francisco, CA, USA, June 26 - July 01, 2016, pages 1567–1581, 2016.
A. Galakatos, M. Markovitch, C. Binnig, R. Fonseca, and T. Kraska. A-tree: A bounded approximate index structure. under submission, 2017.
M. Athanassoulis and A. Ailamaki. BF-tree: Approximate Tree Indexing. In VLDB, pages 1881–1892, 2014.
G. Graefe. B-tree indexes, interpolation search, and skew. In Proceedings of the 2Nd International Workshop on Data Management on New Hardware, DaMoN ’06, New York, NY, USA, 2006. ACM.
G. Graefe. B-tree indexes, interpolation search, and skew. In Proceedings of the 2Nd International Workshop on Data Management on New Hardware, DaMoN ’06, New York, NY, USA, 2006. ACM.
J. Yu and M. Sarwat. Two Birds, One Stone: A Fast, Yet Lightweight, Indexing Scheme for Modern Database Systems. In VLDB, pages 385–396, 2016.
M. Stonebraker and L. A. Rowe. The Design of POSTGRES. In SIGMOD, pages 340–355, 1986.
G. Moerkotte. Small Materialized Aggregates: A Light Weight Index Structure for Data Warehousing. In VLDB, pages 476–487, 1998.
W. Litwin. Readings in database systems. chapter Linear Hashing: A New Tool for File and Table Addressing., pages 570–581. Morgan Kaufmann Publishers Inc., San Francisco, CA, USA, 1988.
J. Wang, H. T. Shen, J. Song, and J. Ji. Hashing for similarity search: A survey. CoRR, abs/1408.2927, 2014.
J. Wang, W. Liu, S. Kumar, and S. F. Chang. Learning to hash for indexing big data;a survey. Proceedings of the IEEE, 104(1):34–57, Jan 2016.
S. Richter, V. Alvarez, and J. Dittrich. A seven-dimensional analysis of hashing methods and its implications on query processing. Proc. VLDB Endow., 9(3):96–107, Nov. 2015.
M. Turcanik and M. Javurek. Hash function generation by neural network. In 2016 New Trends in Signal Processing (NTSP), pages 1–5, Oct 2016.
J. Wang, H. T. Shen, J. Song, and J. Ji. Hashing for similarity search: A survey. CoRR, abs/1408.2927, 2014.
J. Guo and J. Li. CNN based hashing for image retrieval. CoRR, abs/1509.01354, 2015.
J. Wang, H. T. Shen, J. Song, and J. Ji. Hashing for similarity search: A survey. CoRR, abs/1408.2927, 2014.
K. Weinberger, A. Dasgupta, J. Langford, A. Smola, and J. Attenberg. Feature hashing for large scale multitask learning. In Proceedings of the 26th Annual International Conference on Machine Learning, ICML ’09, pages 1113–1120, New York, NY, USA, 2009. ACM.
M. Turcanik and M. Javurek. Hash function generation by neural network. In 2016 New Trends in Signal Processing (NTSP), pages 1–5, Oct 2016.
B. Fan, D. G. Andersen, M. Kaminsky, and M. D. Mitzenmacher. Cuckoo filter: Practically better than bloom. In Proceedings of the 10th ACM International on Conference on Emerging Networking Experiments and Technologies, CoNEXT ’14, pages 75–88, New York, NY, USA, 2014. ACM.
K. Alexiou, D. Kossmann, and P.-A. Larson. Adaptive range filters for cold data: Avoiding trips to siberia. Proc. VLDB Endow., 6(14):1714–1725, Sept. 2013.
R. Grossi and G. Ottaviano. The wavelet trie: Maintaining an indexed sequence of strings in compressed space. In Proceedings of the 31st ACM SIGMOD-SIGACT-SIGAI Symposium on Principles of Database Systems, PODS ’12, pages 203–214, New York, NY, USA, 2012. ACM.
R. Grossi, A. Gupta, and J. S. Vitter. High-order entropy-compressed text indexes. In Proceedings of the Fourteenth Annual ACM-SIAM Symposium on Discrete Algorithms, SODA ’03, pages 841–850, Philadelphia, PA, USA, 2003. Society for Industrial and Applied Mathematics.
M. Magdon-Ismail and A. F. Atiya. Neural networks for density estimation. In M. J. Kearns, S. A. Solla, and D. A. Cohn, editors, Advances in Neural Information Processing Systems 11, pages 522–528. MIT Press, 1999.
J. C. Huang and B. J. Frey. Cumulative distribution networks and the derivative-sum-product algorithm: Models and inference for cumulative distribution functions on graphs. J. Mach. Learn. Res., 12:301–348, Feb. 2011.
D. J. Miller and H. S. Uyar. A mixture of experts classifier with learning based on both labelled and unlabelled data. In Advances in Neural Information Processing Systems 9, NIPS, Denver, CO, USA, December 2-5, 1996, pages 571–577, 1996.
N. Shazeer, A. Mirhoseini, K. Maziarz, A. Davis, Q. Le, G. Hinton, and J. Dean. Outrageously large neural networks: The sparsely-gated mixture-of-experts layer. arXiv preprint arXiv:1701.06538, 2017.
C. Kim, J. Chhugani, N. Satish, E. Sedlar, A. D. Nguyen, T. Kaldewey, V. W. Lee, S. A. Brandt, and P. Dubey. Fast: Fast architecture sensitive tree search on modern cpus and gpus. In Proceedings of the 2010 ACM SIGMOD International Conference on Management of Data, SIGMOD ’10, pages 339–350, New York, NY, USA, 2010. ACM.
C. Kim, J. Chhugani, N. Satish, E. Sedlar, A. D. Nguyen, T. Kaldewey, V. W. Lee, S. A. Brandt, and P. Dubey. Fast: Fast architecture sensitive tree search on modern cpus and gpus. In Proceedings of the 2010 ACM SIGMOD International Conference on Management of Data, SIGMOD ’10, pages 339–350, New York, NY, USA, 2010. ACM.
0 notes
Text
continuing where i left off
wrath layer fic chapter 2 reaction:
once again, author's notes reaction. i found the details tag from a tumblr post once and decided id stash the info away until i could use it somewhere. and that turns out to be here
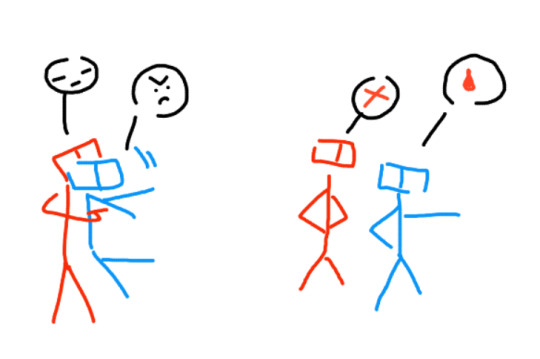
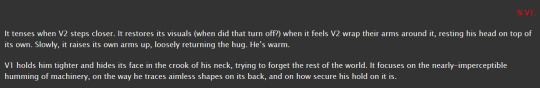
yeah. feral little guy who wants to kill and murder but stopped by the guy who isnt feral

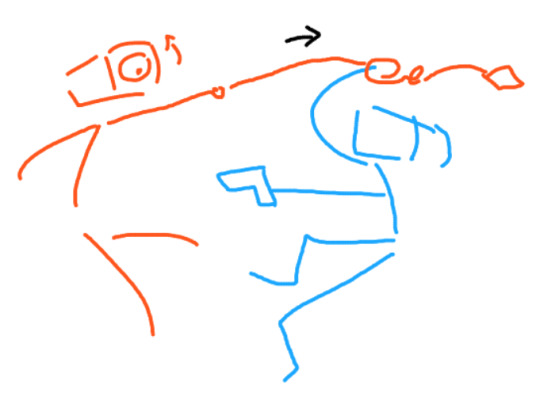
everything is gayer from v2's pov, who has already realized his feelings and trying so hard and failing at getting rid of his crush on this stupid blue fuck
and then i have little thoughts on the little v1-sentry interaction. it's there i guess. v1 the undersocialized little guy who only knows how to kill panicking because if not kill, then what do?? the fact that there's a Lot of people didnt help
oh the v1 trauma scene. im dreading a little at rereading this, i dont think it was good >-<
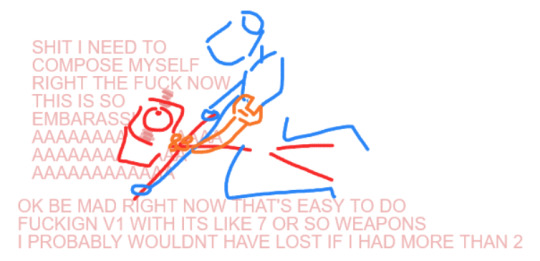
first, from current v1's pov, who has forgotten what has happened. this reads fine honestly

and now with the memory. the last line in the center is part of v1 realizing that its stuck in a loop and deleting the memory. so far with how i've written it, v1 does Not fare well when realizing it failed an order/task/anything. it does better at not marking things as failure now but it still handles it poorly
current idea that im not 100% sure will make it into the series is that memory deletion does not mean deletion of like, feelings. the stress is Still There. which. you know. if v1 suddenly finds itself in a loop where it keeps deleting its memories, and thereby placing it back into the exact same situation each deletion, the stress just continues building up and. yeah
not sure how i feel about the fact that, so far, my pre-canon characterization of v1 and v2 is that v1 is the most anxious thing that loves to kill ever, and v2 is like...there. v2 going "wow, its so easy being an unfeeling machine" [proceeds to not even realize he is experiencing feelings]. v2 is very stressed when he learns that he has feelings like everyone else. deals poorly with having them. v1 is just always stressed the fuck out though. i guess it's like a cheetah or something
word of the author means nothing btw if its not in the series. everything can change at any time i just like talking about my current plans
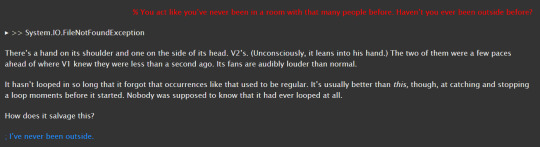
v1's reaction to conflict like this! it doesn't want to talk about that at all and gets angry if you try. the anger comes from something like fear though
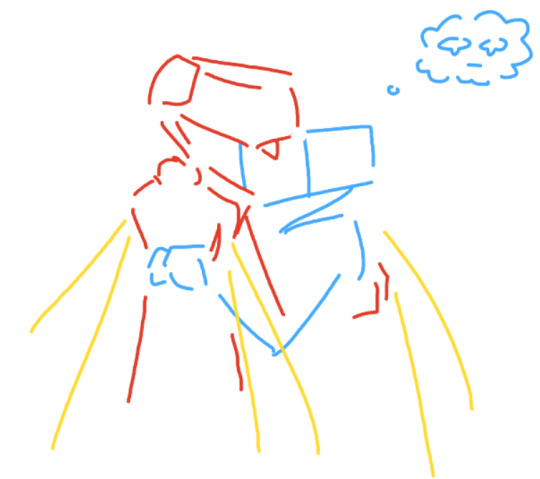
ok the drawing scene! i struggled with explaining the concept behind it a little. i looked up an image of a lighthouse and mentally broke stuff down into shapes and then tried to describe that as best as i could
if i have to be completely honest, the idea of robots being Very Good at just tracing art and doing realistic art, but struggle more with the abstract stuff comes from this fic. i havent finished reading it nor do i really remember a lot of stuff anymore these days but that was 1 of the scenes that stuck out to me. another scene that sticks out to me is the part where sun tries to describe his favourite colour, but its a very specific colour, guy probably has the hex code for it and all, and tries really hard to recreate that exact colour. its cool i need to reread if i ever get the time. 107 chapters got hands

ivan aivazovsky! i wanted one of his wave paintings specifically because the first time i saw it, i went WOAH and so i knew i had to use one of his paintings for my yaouri fic. and then the part where their conversation drifts away from the drawing topic is because i ran out of things to say and also i needed them to move onto the next thing i wanted them to do
oh, the voice thing is next! v2's voice is perfectly fine by the time of the 7-3 fic, but in the 4-4 fic, it was fucked up. i needed a reason as to why v2 would restore his voice and the answer is v1 just likes it. v1 likes to listen to him a lot. it also likes to make him shut up but like lovingly
oh, from one of the glitched text, i transcribed "play nice" as "pʰle͡j na͡js" partly from that 1 time i took a linguistics course and they made me transcribe those sounds as e͡j etc instead of whatever online dictionaries transcribe it as, and then that just stuck with me. i also had a moment while transcribing "play" as like hey wait a minute! air releases when i pronounce the p in play, so i should add the symbol for that
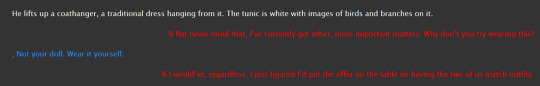
i have that outfit in my closet! no pictures but i know exactly what it looks like. sadly have been unable to find an image that looks like my dress online
i have also had a scene where once v2 finally dresses up v1, his pet name for it is just doll. like. yeah. i havent found an excuse to get v2 to do that though
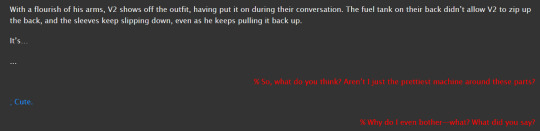

(v1 is just laying down on a couch during this scene)
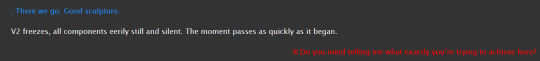
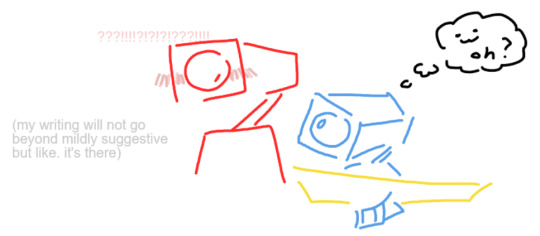
oh yeah i had v1 teasingly call v2 a sculpture but didn't know exactly how to get it to do that. i mean i figured it out but yeah. i dont know if this was a planned thing that never came to fruition or something i made the fuck up just now (memory not the best) but they wouldve played around a bit with the actual sculptures in the room and comparisons wouldve been made
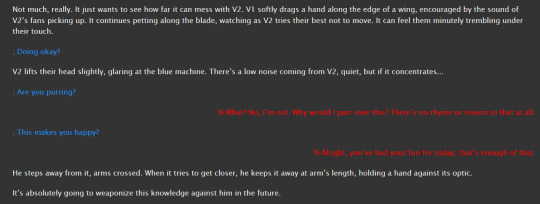

aaand that's the end of the chapter. i dont have any further thoughts on this
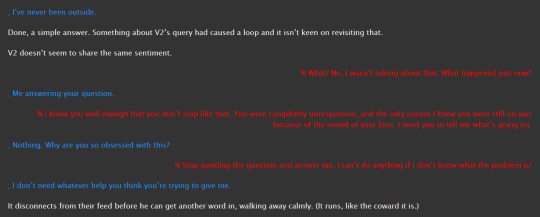
and the below screenshot is the alternate petting scene where v2 overheats. i instead moved the overheating to the next chapter. v2 cannot handle this amount of affection (yet) (he unwillingly gets trained to tolerate more before he gets far too happy about it and ceases to like function for a bit) (thanks v1)
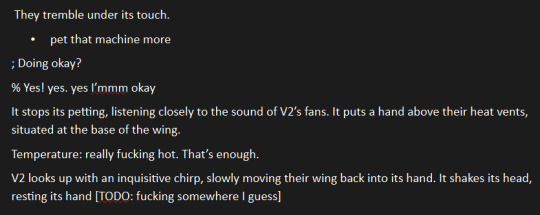
who wants to see me liveblog my reaction to my own fic
17 notes
·
View notes