#the servers are down for maintenance which means I make random posts
Explore tagged Tumblr posts
Text
Discord Chat dump post: Khonsu, power armor and some very obvious metaphors
So yesterday I decided to be very cringe in a Discord server again (because it was a day ending in -y) and went on a 40-minute long tangent about cryptic OC lore - specifically how the power armor of a (Chaos) Astartes can double as a metaphor for their mental state, levels of intimacy and personal autonomy/agency. Reposting it here to create a more permanent copy of my thoughts.
Minor CWs: brief discussion or mentions of disability, body horror, injury, toxic relationships, nudity and patient care in a purely fictional context
---
[00:16]girl help
[00:17]OC thoughts again
[00:19]Astartes power armor as a metaphor for intimacy (remaining guarded/opening up), but also for the meaning/purpose of life (being a person vs. being a war machine), and how both of these things play into Khonsu's unique state and way of life
[00:22]because the Rubric'd parts (their right shoulder and arm) are sealed tight, but there's nothing beneath them and they are animated not by exerting your will directly at your body, but by channeling it into a spell (which can be potentially hijacked), and the rest is slowly succumbing to mutation, which manifests not only through physical deformation of limbs or random eyes popping up, but also through the afflicted flesh overgrowing and trying to permanently merge with the armor
[00:25]also, the armor serves as crucial protection - the moment you remove it you're going to be not only, y'know, exposed to blades and bullets, but also extremely vulnerable because you're missing a whole limb, your other arm and one leg are kind of fucked, and also the side-effect of the whole "flesh merging with armor" thing is that if you remove the armor, you're ripping out chunks of your body with it, it hurts like a bitch and takes a moment to heal up
[00:26]if you remove the armor, you're going to be hurt, weakened and left extra vulnerable
[00:28]but if you keep wearing it, well, a quarter of it is only under your control until someone more powerful comes along and phases you out, and the rest is trying to become one with it against your will, taking away your autonomy and destroying the body you've made to be as close as you could to a personal ideal
[00:30]you're risking losing your humanity, but your humanity also kind of sucks in some ways
[00:33]and this extends to Su's psychology: if they stay guarded and closed off, they will grow more dour and insensitive, they will harden towards others but also marinate in their own suffering until it makes them go insane or breaks them into an indifferent, obedient puppet, both of which will basically kill off their "self" (either in the sense of "destroying what's left of their personal values and code of conduct" or "destroying what's left of their autonomy and free will")
[00:33]but if they let the guard down, well
[00:35]there's a lot of bad shit to handle in there, and not everyone will be able or willing to put up with it, it also exposes them to hurt, opens up avenues for abuse/exploitation and leaves them weakened because opening up means dredging up, if not reliving all the pent-up emotions and walled-off memories, and that's a lot of pain to bear
[00:36]and I have an idea for a scene that's like
[00:37]Su and Freyr are growing close to one another, not yet lovers but close confidants, maybe even genuine friends at this point (if you're willing to ignore the five kinds of power imbalance between them, never said this was a healthy relationship)
[00:39]and Su feels safe enough aboard their new voidship to make use of some downtime and strip out of their armor so they can a) get it through some much-overdue maintenance and repair, b) maybe also shower or something, biomancy can only take you so far
[00:41]they don't let anyone know about what they're about to do though, they want to pull through this alone and maybe get back in the armor by the time anyone will start looking for them
[00:45]predictably this doesn't really work out because while Su makes use of the private arming chambers adjacent to their private quarters that can be only accessed with their permission, Freyr lives there too and has a permanent pass
[00:46]at that point he's either actively socializing with the rest of the warband or trying to get back into the daily training routine, but the Power of Plot compels him to come back early and find the passage to the arming chambers
[00:47]and also Su
[00:47]naked, in pain and still bleeding on the floor
[00:48]and to Su's equal surprise and horror, he decides to help a mangled-up, disabled Sorcerer get up, tend to the wounds a bit, then get a proper bath
[00:51]he's actually so supportive it encourages Su to stay out of the armor a little longer, maybe walk around a little, lay down on a comfy bed (!) with fresh sheets (!!), try on some light casual clothes (!!!), y'know, experience something approaching normal life after centuries of the utterly deprecating CSM grind
[00:56]tl;dr Freyr is a catalyst for Su embracing their humanity by demonstrating his own and providing them with a safe space to be vulnerable (but it also backfires in the long run because he's the only kind of psychological support and social safety net Su has, so if he's gone - things will go downhill rapidly)
[01:05]I'm done being cringe BTW please kick me out of here or something
#ylthinocrambles#oc: khonsu#just strongarm me into actually writing shit instead of doing out-of-context OC dumping on servers#because nobody will read it either way :')#but at least my cringe will be contained on AO3 or something
3 notes
·
View notes
Text
there is no bottom to the pit that is my hatred of syrcus tower. I would rather heal orbonne or puppets bunker with all brand new party members than endure the mindless tedium of that teal hell one more time
#if I ever catch someone at ilvl cheesing I will show up on their lawn#and play the hamster dance full blast under their window on a boombox at 4am#no one should be exposed to amon and his dumb hat on a daily basis that's just cruel#god it is so boring#where is dun scaith in roulette? and copied factory? and aglaia?#I love healing those#I'm bitter because I actually did get orbonne with a fairly inexperienced group today and it was just so fun?#but 9/10 times it's syrcus tower#I hope you find a way to die even more dead than you are amon#choke on your hat#ffxiv#ffxivmp#mp#the servers are down for maintenance which means I make random posts
5 notes
·
View notes
Text
Broken NPC
Oh look I'm posting something This is a fic related to the NPC!Wels AU that @justletmeplayminecraft created! It takes place before this fic here so make sure you read that one too!
Read it on AO3!
A broken NPC has no place in its original server. There only seem to be two options: be deleted, or escape.
"Alright WelsKnight_9357, you must be the infamous singing knight everyone's been talking about on the forums."
"I am?"
The coder in front of the NPC looked up from his panels, eyes wide in surprise as if he hadn't expected the NPC to respond.
"Uhm, yeah." He responded, shaking his head and looking back down at the panels. "Hm, yeah your entire code is jumbled. That's odd, did someone hack you? Why would they bother to hack one random NPC? And make them sing for that matter? How long have you even been like this?"
"I started singing before I was moved to this route." The NPC answered, earning another surprised look from the coder. "I estimate seven months."
"You're… aware of all this? Wait, you can understand passage of time? For that matter, how are you talking outside of your script? Actually, why is that surprising you're literally singing, which I did not program in."
"Is singing bad?"
"Uh, well, I mean, no not really."
"Then what is the problem?"
"The problem is that you're clearly busted beyond any sort of quick fix."
"I am?"
The coder sighed, hitting a button on his panels. The NPC felt something click in the back of its head and travel down to the soles of its feet. "Follow me."
The coder began walking away and the NPC followed after, free from its set path finding. It let its eyes wander across the greenery and the decorations of the area it had been set up at, having only the chance to look at it from a distance. It thought they looked a lot nicer up close. It caught the coder giving it confused and skeptical glances from his place ahead of it as it was led into a tree, the decorative coding facade falling away as the coder opened up a way into a large room with swirling blue and purple walls encased in a dark material.
"What are those?" It asked. It hasn’t seen anything like them in the world.
"Those are world and hub portals. Players can leave the server through them."
The NPC watched as the coder's words were demonstrated, various players standing in the transparent swirls and disappearing without a trace. "Are we going through one?"
"No, we have a maintenance room in this hub. That's why we're here."
"Maintenance?"
"Yeah, you need a hard reset. We can scrap all your old code and replace it. Add a firewall or something, too, to prevent this from happening again."
"Will I still be able to sing?"
The coder sighed, stopping and turning to look at the NPC with a tired expression. "No. You won't be able to sing anymore. Or do this." He gestured at it.
"Do what?"
"Ask all these questions."
A few beats passed, the NPC looking down at the ground as it thought about the coder's words. "I do not want to stop singing. I like singing."
The coder's eyes widened before hardening. "Let me ask you this. What are you?"
"I am the NPC WelsKnight_9357."
"Exactly. You're an NPC. You can't want anything. You can't like anything. You're not sentient. You're just complicated pieces of coding made to execute simple routines, repeat basic dialogue, and complete designed motor tasks to make actual players' experiences on the server more enjoyable."
The NPC's brows furrowed, thinking back to all the players that had gathered around it when it would sing its made up songs. How they would clap for it for some reason, and laugh at the rhymes it made, and return with another player in tow and gesture to it excitedly.
"I thought the players enjoyed my singing."
"That doesn't matter because it isn't a part of the design. It's not a part of your design."
"But you said I am supposed to make players' experiences more enjoyable."
"By doing as you're supposed to and nothing else." He pinched the bridge of his nose. "How else can I say this? You are not real. Nothing you do or say matters because you cannot, and should not be able to, make decisions for yourself. You should not be singing. You should not be interacting with players outside of your script. You should not be asking questions. You should not be aware you do anything at all."
"But… I am."
The coder turned around again, shoulders slumping forward in defeat. "Maybe I should just completely scrap you. Your design is out of date anyways; coding is several years old. And you're clearly broken. This isn't worth the headache."
The coder began walking but the NPC didn't follow. It stood there, processing the words the coder just mumbled. Scrap? As in delete? Was he going to delete it? Just because it wanted to sing?
You're an NPC. You can't want anything.
That can't be right. If it really were an NPC then it shouldn't feel this way. It shouldn't feel dread crawling up its spine at the idea of being deleted. It shouldn't feel sorrow at the idea of never singing again. If it were an NPC, it must be really broken if it was acting this way. Maybe it would be better if it were scrapped, if it were completely erased from existence before it could get more confused about who and what it was.
Movement caught its eye and it watched as a player walked into a blue portal, the swirls and particles enveloping them until they completely disappeared.
If it were an NPC… then it shouldn't want to run through that portal and get away as fast as possible.
Maybe it wasn't an NPC.
Maybe they weren’t an NPC.
They heard a call from behind them as they made a dash for the blue swirls, shutting their eyes tight as the feeling of the portal covered them. It tickled their nose and made their eyes itch, and slowly but surely they felt as their coding was sifted through and pulled through the portal.
Almost pulled through, anyways.
The NPC(?) screamed as it felt like their coding was being ripped in two. A searing feeling coursed through them that they had never felt before made them fall to their knees, gripping their arms as they stared at the ground unseeing.
Voices weren't registered around them, but they felt a hand land on their arm and slide up the armor, making contact with the portal.
And just like that, the pain numbed and the broken NPC was gone.
#i will probably rewrite this later#npc!wels#npc wels#hermitcraft#hermitcraft fics#welsknight#broken npc#sky writes#surprising i know
45 notes
·
View notes
Text
The Sims 4 Nifty Knitting: Plopsy Retail Deep Dive
SimGuruConnor has released a forum post detailing the “Plopsy” online retail marketplace feature from The Sims 4 Nifty Knitting Stuff!
Welcome back to another Nifty Knitting Deep Dive! This is part 4 of our ongoing series where we take a peek behind the curtain (of yarn?) to discuss in depth upcoming gameplay features, and have a little Q&A with members of the development team. Today, let’s talk about Plopsy!

Plopsy is an online arts and crafts marketplace to buy and sell goods. It’s sort of an amalgamation of real life online stores, but the themes should feel familiar. For a pack centered around knitting, this felt like a really good add. Afterall, there are only so many times you can gift your significant other a sweater…and yet so many sweaters to knit!
The flow for Plopsy is relatively straightforward – once you’ve crafted an object the List on Plopsy interaction becomes available. Listing an item on Plopsy costs a small fee, and will remain listed on Plopsy for several days. You can keep track of your listed items in your inventory, where you will see the current duration of the item and if there are any interested buyers.
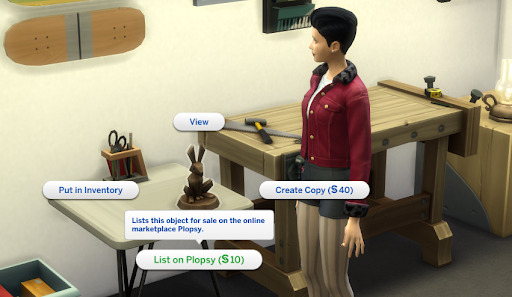
(it’s that easy!)
If someone is interested in buying your item, you’ll be notified with a message. If you agree to the buyer’s offer, you can use the Ship on Plopsy action to ship the object in the mail. You’ll be paid immediately and get a thank you message from the buyer when they receive your package. Alternatively, you can ignore a buyer’s offer and relist the object for sale again.

(Ship it!)
Plopsy offers a higher payout than selling things the old fashioned way, at the cost of some general maintenance and patience. The goal is to offer a better selling experience for both the stay-at-home crafting professional and the fairweather crafting hobbyist. Plopsy isn’t tied down to a career or a gig, so anyone is free to try it!

(adsbygoogle = window.adsbygoogle || []).push({}); Sims can also purchase things on Plopsy through their phones or computers. This storefront will rotate in random crafted items throughout the day, so even non-crafty Sims have a chance at some cool stuff (including the new knitted clothing!).
We plan for Plopsy to be available for things like paintings, woodworking statues, potions, knitted items, flower arrangements, and more. Hoping to wrap future arts and crafts under Plopsy too!
Without further ado here’s Rick Rodgers, engineer extraordinaire here on our Stuff Pack team, here to talk a bit about coding, UI, and all the bits between.
Conor: Can you tell us what it means to be Gameplay Engineer on The Sims 4?
Rick: To understand what a GPE is (we always say GPE), you need to understand a bit about how The Sims 4 works. The Sims 4 uses a client-server architecture, which means it is essentially composed of two separate programs that talk to each other. The first program we call “the client”, and it is responsible for displaying the game to the player. It handles things like graphics, audio, and the user interface (it’s relatively important!). The second program we call “the server” and it manages what we call gameplay systems like autonomy, interactions, relationships, aspirations, skills, and careers. The server keeps track of those systems and condenses them down into operations the client understands, like “play this animation on this object” or maybe “put this cat on top of this vacuum”. As a GPE, my job is to build (and fix) the gameplay systems on the server and make sure designers have the options they need to create features using them. (Disclaimer: I am simplifying a bit)
Conor: You also work on UI Engineering. How is it different from Gameplay Engineering? How is it the same?
Rick: To me, gameplay engineering is about solving abstract problems like “where and how should a Sim put down the object they are holding?” while UI engineering is usually about solving much more concrete problems like, “What do we do if the Russian word for Tiny Home is too long for this button?”. UI engineering can be really satisfying because the changes we make are usually immediately visible. There is also something fun about changing-up the interface of the game that we stare at all day long. At the end of the day though, code is code. I like to work on both because it means I get to implement the gameplay and UI components of a single feature.
Conor: Is there one thing in Nifty Knitting that you’re really excited to be working on?
Rick: Plopsy – I think partly because the idea of selling things I make at home has always appealed to me in real life. Also, Plopsy breaks some of the assumptions we had previously made about how we would use the crafting system, and it’s been fun to find and solve the problems that have come up.
Conor: What is your favorite feature you have ever worked on in The Sims 4?
Rick: Can I pick two? Favorite feature to make: I had a lot of fun adding Freelancer Careers to the game. We had done something similar to Freelancer with the Acting Career in The Sims 4 Get Famous, and we wanted to figure out a way to use some of the things we liked about the Acting Career to make other careers. When we added another Freelancer Career for Fashion Photography in The Sims 4 Moschino Stuff Pack, I felt like my baby was all grown up. Favorite feature to play: I really enjoyed working on the Murphy Bed in The Sims 4 Tiny Living Stuff Pack. It’s convenient design, but sometimes prickly exterior, make it the perfect combination of sensible and a little nefarious. You might say I identify with it a bit. I didn’t hook-up the object itself, that was our design team. But I worked on it because we needed gameplay support in code for a bed that was also a loveseat. We had never made anything like that before.
Conor: Thanks Rick!
That’s all I have for this week, Simmers, but never fear, we have one more design deep dive to share with you. I saved the best, and my personal favorite, for last. So be sure to join us next time for the Knitting Deep Dive!
Until then….
~ SimGuruConor
14 notes
·
View notes
Video
youtube
Transcript:
PRESENTER: Our next speaker is Cory Doctorow, who is a sci-fi novelist who works at the Electronic Frontier Foundation, and is affiliated with MIT Media Lab and Open University.
Please welcome Cory.
[MUSIC]
CORY: Thank you very much... hi. So there's a little formality first as a member a good standing of the order of after-dinner and conference speakers of England and Wales... I am required as the last speaker before lunch to make a joke about being the last speaker before lunch. This is that joke.
[LAUGHTER]
Thank you.
So, I work for Electronic Frontier Foundation and I've met some of you in the halls here, and when I mentioned I work with EFF, they say “Oh, you guys have been around for a long time,” and it's true, like not just Internet time, not like “This is Zcash's second birthday, so we're the doddering old men of cryptocurrency,” Oh long time, like we've been around for a quarter century, a legitimate long time.
And I want to talk about our origin story, but the key victories that we scored really early on a quarter century ago that really are the reason you guys— and you folks are in this room today...
I want to talk about the Crypto Wars... not those Crypto Wars, these Crypto Wars.
So, back in the late 90s the NSA classed cryptography as a munition, and imposed strict limits on civilian access to strong crypto, and there were people as you heard Primavera speak about who called themselves cypherpunks crypto-anarchists, who said that this was bad policy it was a governmental overreach and it needed to be changed... and they tried a whole bunch of different tactics to try and convince the government that this policy was not good policy.
So they talked about how it was ineffective, right, they said you can ban civilian access to strong cryptography and only allow access to to weak crypto, the 50 bit version of DES and that will not be sufficient to protect people. They they made this as a technical argument, they said like “Look, we believe that you could brute force DES with consumer equipment,” and the court said, “Well... who are gonna believe you, or the NSA? Because the NSA, they hire all the PhD mathematicians that graduate from the Big Ten schools, and they tell us that DES-50 is good enough for anyone, so why should we believe you?”
And so we did this — we built this thing called the DES cracker it's a quarter-million-dollar specialized piece of equipment that could crack the entire key space of DES in two hours, right, so we said, “Like, look... here's your technical proof. We can blow through the security that you're proposing to lock down the entire US financial, political, legal and personal systems with for a quarter million dollars,” and they said, “Well, maybe that's true but we can't afford to have the criminals go dark, right, they're gonna hide behind crypto and they won't be able to— we won't be able to spy on them.”
So in the face of all those of all that resistance, we finally came up with a winning argument. We went to court on behalf of a guy named Daniel J. Bernstein. You probably heard of DJB he's a cryptographer, he's cryptographer whose name is all over all the ciphers you use now, but back then DJB was a grad student at the University of California, Berkeley, and he had written a cipher that was stronger than DES-50, and he was posting it to USENET.
And we went to the Ninth Circuit and we said we believe that the First Amendment of the US Constitution, which guarantees the right to free speech, protects DJB's right to publish source code: that code is a form of expressive speech, as we understand under expressive speech in the U.S. Constitutional Framework. And this worked, right?
Making technical arguments didn't work, making economic arguments didn't work, making law-enforcement arguments didn't work. Recourse of the Constitution worked. We won in the Ninth Circuit, we won at the Appellate Division, and the reason you folks can do ciphers that are stronger than DES-50 (which these days you can break with a Raspberry Pi), the reason you can do that, is because we won this case.
[APPLAUSE]
Thank you.
[MORE APPLAUSE, CHEERING]
So I'm not saying not to suck up to you, right. I'm saying that because it's an important note, in terms of tactical diversity, and trying to achieve strategic goals, right. It turns out that making recourse to the Constitution is a really important tactical arrow to have in your quiver. And it's not that the Constitution is perfect, and it's certainly not true that the U.S. always up holds the Constitution, all right. All countries fall short of their goals, the goals that the U.S. fall short of are better than the goals that many other countries fall short of, The U.S. still fall short of those goals, and the Constitution is not perfect and you folks... you might be more comfortable thinking about deploying math and code as your tactic, but I want to talk to you about the full suite of tactics that we use to affect change in the world.
And this is a framework that we owe to this guy Lawrence Lessig. Larry is the founder of Creative Commons and has done a lot of other important stuff with cyber-law and now works on corruption— that's a connection I'm going to come back to— and and Larry says that there are four forces that regulate our world: four tactical avenues we can pursue. There's code, that's what's technically possible, right? Making things like Deep Crack.
There's markets, what's profitable, right? Founding businesses that create stakeholders for strong security turned out to be a really important piece to continuing to advance the crypto agenda, because there were people who would show up and argue for more access to crypto not because they believed in the U.S. Constitution but because their shareholders demanded that they do that as part of their ongoing funding, right?
There's norms, what's socially acceptable moving from the discussion of crypto as a thing that exists in the realm of math and policy, and to a thing that is part of what makes people good people in the world — to convince them that, for example, allowing sensitive communications to go in the clear is a risk that you put not just on yourself, but on the counter-parties to your communication. I mean I think we will eventually arrive at a place where sending sensitive data and the clear we'll be the kind of technical equivalent of inviting people to a party where you close the door and chain-smoke, right it's your selfish laziness putting them at risk.
And then there's law, what's legal. Now the rule of law is absolutely essential to the creation and maintenance of good cipher systems because there is no key length, there is no cipher system, that puts you beyond the reach of law, right. You can't audit every motherboard and every server in the cloud that you rely on, for a little backdoor chip the size of a grain of rice, that's tapped right into the motherboard control system. You can't make all your friends adopt good operational security: this is a bit of the rules used by the deep packet inspection system deployed by the NSA, this was published in German newspaper by after it was leaked to them. The deep packet inspection rules that the NSA was using to decide who would get long-term retention of their communications and who wouldn't... They involved looking for people who had ever searched for how to install Tor, or Tails, or Qubes, so if you would ever figured out how to keep a secret, the NSA then started storing everything you ever sent, in case you ever communicated with someone who wasn't using crypto, and through that conveyed some of the things that was happening inside your black box conversations.
Right, you can't make everybody you will ever communicate with use good crypto, and so if the state is willing to exercise illegitimate authority you will eventually be found out by them. You can't audit the ciphers that that every piece of your tool chain uses, including pieces that you don't control that are out of your hands, and in the hands of third parties. One of the things we learned from the Snowden leaks was that the NSA had sabotaged the random number generator in a NIST standard, in order to weaken it so that they could backdoor it and read it. And so long as the rule of law is not being obeyed, so long as you have spy agencies that are unaccountable running around sabotaging crypto standards, that we have every reason to believe otherwise are solid and sound, you can never achieve real security.
This turns out to be part of a much larger thing called BullRun in the US and EdgeHill in the UK that the NSA and MI5 were jointly doing to sabotage the entire crypto tool chain from hardware, to software, to standards, to random number generators.
OPSEC is not gonna save you, because security favors attackers. If you want to be secure from a state you have to be perfect. You don't just have to be perfect when you're writing code, and checking it in, you have to be perfect all the time. You have to never make a single mistake. Not when you're at a conference that you've travelled across the ocean to, and you're horribly jet-lagged. Not when your baby has woken you up at 3:00 in the morning, not when you're a little bit drunk. You have to make zero mistakes. In order for the state to penetrate your operational security, they have to find one mistake that you've made, and they get to cycle a new shift in every eight hours to watch you.
They get to have someone spell off the person who's starting to get screen burn in on their eyes and has to invert the screen, because they can no longer focus on the letters. They just send someone else to sit down at that console and watch you. So your operational security is not going to save you.
Over time the probability that you will make a mistake approaches 1. So crypto is not a tool that you can use to build a parallel world of code that immunizes you from an illegitimate powerful state. Superior technology does not make inferior laws irrelevant.
But technology and in particular privacy and cryptographic technology, they're not useless. Just because you're OPSEC won't protect you forever, it doesn't mean that it won't protect you for just long enough. Crypto and privacy tools, they can open a space in which, for a limited time, before you make that first mistake, you can be sheltered from that all-seeing eye.
And in that space you can have discussions that you're not ready to have in public yet. Not just discussions where you reveal that your employer has been spying on everyone in the world, but all of the discussions that have brought us to where we are today. You know, it's remarkable to think that, within our lifetimes, within living memory, it was illegal in much of the world to be gay, and now most of those territories gay people can get married. It was illegal to smoke marijuana and now in the country I'm from — Canada — marijuana is legal, right.
[APPLAUSE]
In every province of the country.
[MORE APPLAUSE]
Right, it was illegal to practice so-called interracial marriage, right. There are people who are the products of those marriages who were illegal. So how in our lifetimes did we go from these regimes where these activities were prohibited, to ones in which they are embraced and considered normal?
Well it was because people who had a secret that they weren't ready to talk about in public yet, could have a space that was semi-public. Where they could choose their allies, they could find people who they thought they could trust, with a secret, and they could whisper the true nature of their hearts to them, and they could recruit them into an ever-growing alliance of people who would stand up for them, and their principles.
They could whisper the love that dare not speak its name, until they were ready to shout it from the hills and that's how we got here. If we eliminate privacy and cryptography, if we eliminate the ability to have these semi-public conversations, we won't arrive at a place in which social progress continues anyway, we'll arrive at a place that we much like the hundreds of years that preceded the legalization of these activities that are now considered normal, where people that you love went to their graves with secrets in their hearts that they never confess to you, great aches that you had unknowingly committed— had contributed to because you never knew their true selves.
So we need good tech policy, and we're not getting it. In fact we're getting bad technology policy that's getting worse by the day.
So you may remember that in over the last two years we discovered that hospitals are computers that we put sick people into, and when we take the computers out of the hospitals they cease to be places where you can treat sick people. And that's because of an epidemic of ransomware there's been a lot of focus on the bad IT policies of the hospitals and the hospitals had some bad IT policies, you shouldn't be running Windows XP, there's no excuse for it and so on.
But ransomware had been around for a long time and it hadn't taken down hospitals all over the world, right. The way that ransomware ended up taking down hospitals all over the world if somebody took some off-the-shelf ransomware and married it to a thing called Deep Blue�� or EternalBlue, rather. And EternalBlue was an NSA exploit. They had discovered a vulnerability in Windows XP, and rather than taking it to Microsoft and saying, “You guys had better patch this, because it's a really bad 0-day,” they had just kept it secret in their back pocket against the day that they had an adversary they wanted to use it against... except, before that could happen someone leaked their cyber-weapon.
And then dum-dums took the cyber weapon and married it to this old piece of ransomware, and started to steal hospitals. Now, why do I call these people dum-dums? Because the ransom they were asking for was 300 dollars. They didn't even know that they had stolen hospitals, they were just opportunistically stealing anything that was connected to an XP box, and then asking for 300 dollars — in crypto currency — in order to unlock it, right.
So this is not good technology policy: the NSA believes in a doctrine called NOBUS — No One But US... is smart enough to discover this exploit. Now, first of all we know that's not true, we know that the NSA, from the crypto wars, we know that the NSA does not have a monopoly on smart mathematicians, right. These were the people who said DES-50 were strong enough for anyone— they were wrong about that, they're wrong about this. But even if you believe that the NSA would never, that the exploits they discovered would never be independently rediscovered, it's pretty obvious that that doesn't mean that they won't be leaked. And once they're leaked you can never get that toothpaste back in the tube.
Now since the the Enlightenment, for 500 years now, we've understood what good knowledge creation and technology policy looks like. So let me give you a little history lesson, before the Enlightenment we had a thing that looked a lot like science through which we did knowledge creation.
It was called alchemy, and what alchemists did is a lot like scientists: you observe two phenomenon in the universe you hypothesize a causal relationship — this is making that happen — you design an experiment to test your causal relationship, you write down what you think you've learned — and here's where science and alchemy part ways — because alchemists don't tell people what they think they've learned. And so they are able to kid themselves, that the reason that their results seem a little off is because, maybe they made a little mistake when they were writing them down, and not because their hypothesis was wrong, which is how every alchemist discovers for himself the hardest way possible that you should not drink mercury, right.
[LAUGHTER]
So for five hundred years alchemy produces no dividends, and then alchemists do something that is legitimately miraculous. They convert the base metal of superstition into the precious metal of knowledge... by publishing. By telling other people what they think they know, they know, not to just their friends, will go easy on them, but their enemies, right. Who if they can't find a single mistake in their work, they know that their work is good. And so as a first principle whenever you're doing something important, everyone should be able to criticize it, otherwise you never know that it works.
So you would hope that that's how we would operate in the information security realm. But that's not how we're operating. In 1998 Congress passed this law of the Digital Millennium Copyright Act. They then went to the European Union in 2001 and arm-twisted them into passing the European Union Copyright Directive, and both of these laws have a rule in them that says that you're not allowed to break Digital Rights Management. You're not allowed to bypass a system that restricts access to a copyrighted work. And in the early days this was primarily used to stop people from making region-free DVD players, right. But now everything's got a copyrighted work in it because everything's got a system in a chip in it that cost 22 cents and has 50,000 lines of code, including the entire Linux kernel and usually an instance of BusyBox running with the default root password of admin admin, right.
And because that's a copyrighted work, anyone who manufactures a device where they could make more money if they could prescribe how you use that device can just add a one-molecule thick layer of DRM in front of that copyrighted work, and then because in order to reconfigure the device you have to remove the DRM, they can make removing DRM and thus using your own property in ways that benefit you into a felony, punishable by a five-year prison sentence and a $500,000 fine. And so there's this enormous temptation to add DRM to everything and we're seeing it in everything: pacemakers, voting machines, car engine parts, tractors, implanted defibrillators, hearing aids, there's a new continuous loop, or closed loop artificial pancreas from Johnson & Johnson, it's a continuous glucose monitor married to an insulin pump with some machine learning intelligence, to figure out what dose you need from moment-to-moment, and it uses proprietary insulin cartridges, that have a layer of DRM in them to make sure that to stay alive, you only feed your internal organ the material that the manufacturer has approved so that they can charge you in extreme markup.
So that's bad, that's the reason we're seeing DRM everywhere, but the effect of that is what it does to security research, because under this rule, merely disclosing defects in security that might help people bypass DRM, also exposes you to legal jeopardy, right. So this is where it starts to get scary, because as microcontrollers are permeating everything we use, as hospitals are turning into computers we put sick people into, we are making it harder for critics of those devices to explain the dumb mistakes of the people who made them have made— We're all drinking mercury.
And this is going everywhere, particularly it's going into your browser. So several years ago the W3C was approached by Netflix and a few of the other big entertainment companies to add DRM to HTML5, because it was no longer technically simple to put DRM in browsers, because the way they were changing the APIs. And the W3C said that they would do it, and there's it's a long complicated story why they went into it, but I, personally, and the EFF, we had a lot of very spirited discussions with the W3C leadership over this, and we warned them that we thought that the companies that wanted to add DRM to their browsers didn't want to just protect their copyright. We thought that they would use this to stop people from disclosing defects in browsers, because they wanted to be able to not just control their copyright but ensure that there wasn't a way to get around this copyright control system.
And they said “Oh no, never! These companies are good actors, we know them, they pay their membership dues, they would never abuse this process to come after security researchers who are making good-faith, honest, responsible, disclosures—,” Whatever, you add your adjective for a disclosure that's made in a way that doesn't make you sad, right... there are all these different ways of talking about security disclosures...
And we said, “All right, let's find out. Let's make membership in the W3C and participation in this DRM community committee contingent on promising only to use the DMCA to attack people who infringe copyright, and never to attack people who make security disclosures,” and the entire cryptocurrency community who were— and blockchain community who are in the W3C working groups, they backed us on this. In fact it was the most controversial standards vote in W3C history, the only one that ever went to a vote, the only one that was ever appealed, it was the only one that was ever published without unanimous support, was published with 58% support, and not one of the major browser vendors, not one of the big entertainment companies signed on to a promise not to sue security researchers who reveal defects and browsers.
So let's talk a little about security economics and browsers. So security obviously it's not a binary, it's a continuum. We want to be secure from some attack you heard someone talk about threat modeling earlier... so, like, you got a bank vault. You know that, given enough time, and a plasma torch your adversary can cut through that bank vault. But you don't worry about that because your bank vault is not meant to secure your money forever, it's meant to secure your money until a security guard walks by on their patrol and calls the police, right. Your bank vault is integrated with the rule of law it is a technical countermeasure that is backstopped by the rule of law, and without the rule of law your bank vault will eventually be cut open by someone with a plasma cutter.
So security economics means factoring in the expected return on a breach into the design of the system, right. If you have a system that's protecting 500 dollars in assets you want to make sure that it will cost at least 501 dollars to defeat it, and you assume that you have a rational actor on the other side who's not going to out of your breach $1.00 in the hole, right. You assume that they're not going to be dum-dums.
So, there's a way that this frequently goes wrong, a way that you get contact shifts that change these security economics calculus. And that's when the value of the thing that you're protecting suddenly goes up a lot, and the security measures that you're using to protect it don't. And all of a sudden your 500 dollar security measure or 501 dollar security measure isn't protecting 500 dollars worth of stuff... it turns out that it's protecting 5 million dollars worth of stuff and the next thing you know there's some dude with a plasma cutter hanging around your vault.
So this challenge is especially keen in the realm of information security, because information security is tied to computers, and computers are everywhere. And because computers are becoming— whoops— because computers are becoming integrated into every facet of our life faster than we can even keep track of it, every day there's a new value that can be realized by an attacker who finds a defect in computers that can be widely exploited. And so every day the cost that you should be spending to secure your computers is going up, and we're not keeping up. In fact computers on average are becoming less secure, because the value that you get when you attack computers is becoming higher, and so the expected adversary behavior is getting better resourced, and more dedicated.
So this is where crypto currency does in fact start to come into the story. It used to be that if you found a defect in widely used consumer computing hardware, you could expect to realize a few hundred or a best a few thousand dollars. But in a world where intrinsically hard to secure computers are being asked to protect exponentially growing crypto currency pools... well, you know how that works right?
You've seen crypto-jacking attacks, you've seen all the exchanges go down, you understand what happens when the value of the asset being protected shoots up very suddenly: it becomes extremely hard to protect. So you would expect that in that world where everything we do is being protected by computers that are intrinsically hard to protect, and where we need to keep adding more resource to protect them, that states would take as their watchword making crypto as easy to implement as possible, making security as easy as possible to achieve. But the reverse is happening. Instead what's happening is states are starting to insist that we're gonna have to sacrifice some of our security to achieve other policy goals.
So this guy used to be Prime Minister of Australia — he's not anymore — wait six months the current Prime Minister of Australia will also not be Prime Minister of Australia anymore — this guy, Malcolm Turnbull— yeah, sorry, did I just get his name wrong? I just blew up his name... what is his name? God, he went so quickly, Malcolm Turnbull, it is Malcolm Turnbull, right there on the slide, I almost called him Malcolm Gladwell.
[LAUGHTER]
So he gave this speech where he was explaining why he was going to make it the law that everybody had to backdoor their crypto for him, and you know all these cryptographers had shown up and they said, "The laws of math say that we can't do that, we can't make you a thing that's secure enough to protect the government, and its secrets, but insecure enough that the government can break into it,” and he said — and I'm not going to do the accent — he said: “The laws of Australia prevail in Australia, I can assure you of that the laws of mathematics are very commendable but the only law that applies in Australia is—” read it with me— “the law of Australia.”
I mean this may be the stupidest technology thing ever said in the history of really dumb technology utterances... but he almost got there, and he's not alone, right. The FBI has joined him in this call, you know, Canada's joined them in this call, like if you ever needed proof that that merely having good pecs and good hair doesn't qualify you to have good technology policy, the government of Justin Trudeau and it's technology policy has demonstrated this forever, right.
This is an equal opportunity madness that every developed state in the world is at least dabbling in. And we have ended up not just in a world where fighting crime means eliminating good security. It's dumber than that, right. We've ended up in a world where making sure people watch TV the right way means sacrificing on security.
Now the European Union they just actually had a chance to fix this because that copyright directive that the U.S. forced them to pass in 2001, that has this stupid rule in it that they borrowed from the DMCA... it just came up for its first major revision in 17 years. The new copyright directive is currently nearly finalized — it's in its very last stage — and rather than fixing this glaring problem with security in the 21st century, what they did was they added this thing called article 13, so article 13 is a rule that says if you operate a platform where people can convey a copyrighted work to the public so like if you have a code repository, or if you have Twitter, or if you have YouTube, or if you have SoundCloud, or if you have any other way that people can make a copyrighted work available, if you host Minecraft skins, you are required to operate a crowd-sourced database of all the copyrighted works that people care to add to it and claim so anyone can upload anything to it and say, “This copyright belongs to me,” and if a user tries to post something that appears in the database you are obliged by law to censor it. And there are no penalties for adding things to the database that don't belong to you. You don't even have to affirmatively identify yourself. And the companies are not allowed to strike you off from that database of allegedly copyrighted works, even if they repeatedly catch you chaffing the database with garbage that doesn't belong to you — the works of William Shakespeare, all of Wikipedia, the source code for some key piece of blockchain infrastructure, which now can't be posted to a WordPress blog and discussed, until someone at Automattic takes their tweezers and goes through the database, and pulls out these garbage entries, whereupon a bot can re-insert them into the database one nanosecond later. So this is what they did, instead of fixing anti-circumvention rules to make the Internet safe for security.
So, I mentioned this is in its very last phase of discussion and it like it was a fix, and then the Italian government changed over, and they flipped positions, and we're actually maybe going to get to kill this... but only if you help? If you're a European, please go tosaveyourinternet.eu and send a letter to your MEPs, this is really important. Because this won't be fixed for another 17 years, if this passes... saveyourinternet.eu.
So when we ask ourselves why are governments so incapable making good technology policy, the standard account says it's just too complicated for them to understand, right. How could we expect these old decrepit irrelevant white dudes to ever figure out how the Internet works, right, if it's to technological, you're too old, right.
But sorting out complicated technical questions, that's what governments do. I mean I work on the Internet, and so I think it's more complicated than other people's stuff, but you know, when I'm being really rigorously honest, I have to admit that it's not more complicated than public health, or sanitation, or building roads, and you know we don't build roads in a way that is as stupid as we have built the Internet.
And that's because the Internet is much more hotly contested, because every realm of endeavour intersects with the Internet. And so there are lots of powerful interests engaged in trying to tilt Internet policy to their advantage, right.
The TV executives, and media executives who push for article 13, you know, they're not doing it because there are moustache-twirling villains, they're just doing it because they want to line their pockets, and they don't care what cost that imposes on the rest of us. Bad policy, bad tech policy, it's not bad because making good policy is hard, it's bad because making bad policy has a business model.
Now tech did not cause the corruption that distorts our policy outcomes, but it is being supercharged by the same phenomenon that is distorting our policy outcomes, and that's what happened with Ronald Reagan, Margaret Thatcher and their cohorts who came to power the same year the Apple ][+ shipped, and among the first things they did in office was dismantle our antitrust protections, and allowed companies to do all kinds of things that would have been radioactively illegal in the decades previous, like buying all their competitors, like engaging in illegal tying, like using long term contracts, and their supply chain to force their competitors out, like doing any one of a host of things that might have landed them in front of an antitrust regulator and broken up into smaller pieces the way AT&T had been.
And as that happened we ended up in a period in which inequality mounted and mounted and mounted and 40 years later, we've never lived in a more unequal world. We have surpassed the state of inequality of 18th century France, which for many years was the gold standard for just how unequal a society can get before people start chopping off other people's heads. And unequal states are not well-regulated ones. Unequal states are states in which the peccadilloes, cherished delusions and personal priorities of a small number of rich people who are no smarter than us start to take on out-size policy dimensions. Where the preferences and whims of a few plutocrats become law.
[APPLAUSE]
So, in a plutocracy policy only gets to be evidence-based when it doesn't piss off a rich person and we cannot afford distorted technology policy, we are at a breaking point. Our security and our privacy and our centralization debt is approaching rupture. We are about to default on all of those debts, and we won't like what the bankruptcy looks like when that arrives.
Which brings me back to cryptocurrency, and the bubble that's going on around us, the bubbles they're not fueled by people who have an ethical interest in decentralization, or who worry about overreaching state power, those bubbles right all the frothy money that's in there, not the coders who are writing it or the or the principled people who think about it, but all the money that's just sloshing through it, and making your tokens so volatile that the security economics are impossible, that money is being driven by looters who are firmly entrenched in authoritarian states, the same authoritarian states that people are interested in decentralization say we want to get rid of.
They're the ones who are buying cyber-weapons to help them spy on their own populations, to figure out who is fomenting revolution, so they can round them up, and torture them and arrest them, so that they can be left to loot their national treasuries in peace, and spin the money out through financial secrecy havens like the ones that we learned about in the Panama Papers, and the Paradise Papers.
And abetting the oligarchic accumulation of wealth, that is not going to create the kinds of states that produce the sound policy that we need to make our browsers secure. It will produce states whose policy is a funhouse mirror reflection of the worst ideas of the sociopaths who have looted their national wealth and install themselves as modern feudal lords.
Your cryptography will not save you from those states. They will have the power of coercive force and the unblinking eye of 24/7 surveillance contractors. The internet, the universal network where universal computing endpoints can send and receive cryptographically secure messages, is not a tool that will save us from coercive states, but it is a tool that will give us a temporary shelter within them, a space that even the most totalitarian of regimes will not be able to immediately penetrate, where reformers and revolutionaries can organize, mobilize, and fight back where we can demand free fair and open societies, with broadly shared prosperity, across enough hands, that we can arrive at consensuses that reflect best evidence, and not the whims of a few. Where power is decentralized... and incidentally having good responsive states will not just produce good policy when it comes to crypto. All of our policy failures can be attributed to a small moneyed group of people who wield outsize power to make their bottom line more important than our shared prosperity.
Whether that's the people who've spent years expensively sowing doubt about whether or not cigarettes would give us cancer or the people who today are assuring us that the existential threat that the human species is facing is a conspiracy among climate scientists, who are only in it for the money.
So you're here because you write code and you may not be interested in politics, but politics is interested in you. The rule of law needs to be your Alpha and Omega, because after all, all the Constitution is is a form of consensus, right. It's the original consensus-seeking mechanism. Using the rule of law to defend your technology, it's the most Internet thing in the world!
Let's go back to Bernstein. When we went to Bernstein and argued this, case we essentially went on an Internet message board and made better arguments than the other people. And we convinced the people who were listening that our arguments were right. This is how you folks resolve all of your problems, right? Proof of concept, running code, good arguments and you win the rule— you win the battle of the day.
So making change with words — that's what everybody does whether we're writing code, or writing law, and I'm not saying you guys need to stop writing code, but you really need to apply yourself to the legal dimension too.
Thank you
[APPLAUSE]
Thank you.
So we're gonna ask some questions now. I like to call alternately on people who identify as women or non-binary, and people identify who as male or non-binary, and we can wait a moment if there's a woman or non-binary person who wants to come forward first.
There's some there's a mic down there and then there's a rover with a mic, just stick up your hand.
There, any hands up there, is someone have their hand up, is that what that person was shouting and audibly from the back?
No? All right are there any people identify as men are non-binary you'd like to ask the first question? There's someone there, if there's a runner with a mic maybe? Or if you want to come down to this microphone.
Someone's coming now.
AUDIENCE MEMBER: As someone who spent a lot of time involved the Internet I'm sure you've read the book “The Sovereign Individual”, and I recently read this book and it talked a lot about how the Internet will increase the sovereignty of individuals and also how cryptocurrencies will. And it predicted a massive increase in inequality, as a direct result of Internet. Could you comment on that?
CORY: Yeah, I've read the book, so I'm not gonna comment directly on the book, but I think it's true that if you view yourself as separate from the destinies of the people around you, that it will produce inequality. I think that that's like empirically wrong, right, like, if there's one thing we've learned about the limits of individual sovereignty it's that you know you have a shared microbial destiny.
You know I speak as a person who left London in the midst of a measles epidemic and landed in California right after they stamped it out, by telling people that you had to vaccinate your kids or they couldn't come to school anymore. We do have shared destinies. We don't have individual sovereignty, and even if you are the greatest. And you know, anyone who's ever run a business knows this, right. You could have a coder who's a hundred X coder who produces a hundred times more lines of code than everybody else in the business. But if that coder can't maintain the product on their own and if they're a colossal asshole that no one else can work, with then that coder is a liability, not an asset, right.
Because you need to be able to work with more than one person, in order to attain superhuman objectives, which is to say more than one person can do. And everything interesting is super-human, right. The limits on what an individual can do are pretty strong. And so yeah, I think that that's true, I think that that the kind of policy bent towards selfishness, kind of self-evidently produces more selfish outcomes, but not better ones, right. Not ones that reflect a kind of a shared prosperity and growth. Thank you.
CORY: Hi.
AUDIENCE MEMBER: Hi. I have had the pleasure of seeing you keynote both decentralized web summits, and the ideas you bring to these talks always really stay with me longer than anything else.
CORY: Thank you.
AUDIENCE MEMBER: With what you've talked about here this is honestly one of the most intimidating and terrifying topics, and I'm wondering what what are some ways besides staying informed and trying not to get burned out by it all what are some ways that people can make a difference?
CORY: So, I recently moved back from London to California as I mentioned and one of the things that that means is I have to drive now, I'm a really shitty driver, and in particular, I'm a really shitty parker, and so when I have to park, I do a lot of this, and then a lot of this, and then a lot of this, and then a lot of this, and what I'm doing is I'm like, moving as far as I can to gain one inch of available space, and then— or centimeter, and then moving into that centimeter available space, because that opens up a new space that I can move into, and then I'd open and then I move as far as I can, and I open up a new space.
We do this in computing all the time right we call it hill climbing we don't know how to get from A to Z, but we do know how to get from A to B, right? We can we know where the higher point of whatever it is we're seeking is: stability, or, you know density, or interestingness, or whatever, and so we move one step towards the objective. And from there we get a new vantage point and it exposes new avenues of freedom that we can take.
I don't know how we get from A to Z— I don't know how we get to a better world and I actually believe that because the first casualty of every battle is the plan of attack, that by the time we figured out the terrain, that it would have been obliterated by the adversaries who don't want us to go there. And so instead I think we need heuristics, and that heuristic is to see where your freedom of motion is at any moment, and take it.
Now Larry Lessig, he's got this framework, the Four Forces: Code, Law, Norms, and Markets. My guess is that most the people in this room are doing a lot with Norms and Markets, right, that's kind of where this conference sits in that little 2×2, and as a result you may be blind to some of the code, and some of the law, and norm issues that are available to you, right.
That it might be that jumping on EFF's mailing list if you're European getting on the EDRI mailing list, or if the mailing list for the individual digital rights groups in your own countries like Netspolitik in Germany or the Quadrature du Net in France, or Open Rights Group in the UK, or Bits of Freedom in the Netherlands, and so on... getting on those lists and at the right moment calling your MEP, calling your MP, or even better yet, like actually going down when they're when they're holding surgeries, when they're holding constituency meetings, they don't hear from a lot of people who are technologically clued in, right. Like, they only get the other side of this, and you know I've been in a lot of these policy forums and often times the way that the other side prevails it's just by making it up, right.
Like one of the things we saw in this filter debate like we had computer scientists who were telling MEPs, you know the 70 most eminent computer scientists in the world, right, that a bunch of Turing Prize winners Vint Cerf, and Tim Berners-Lee said, like, these filters don't exist, and we don't know how to make them. And they were like “Oh, we've got these other experts who say we know how to do it,” and they they had been told for years that the only reason nerds hadn't built those filters as they weren't nerding hard enough, right?
And if they actually hear from their own constituents people who run small businesses that are part of this big frothy industry that everybody wants their national economies to participate in, who show up at their lawmakers' offices and say, “This really is catastrophic, it's catastrophic to my business, it's catastrophic to the Internet,” they listen to that, right?
It makes— it moves the needle, and, you know, you heard earlier someone say are we at pitch now, well I should pitch right, I work for Electronic Frontier Foundation, we're a non-profit, the majority of our money comes from individual donors, it's why we can pursue issues that are not necessarily on the radar of the Big Foundations or Big Corporate donors. We're not beholden to anyone, and it's people like you, right, who keep us in business.
And you know I don't draw money from EFF, I'm an MIT Media Lab research affiliate, and they give EFF a grant that pays for my work, so the money we give to the EFF doesn't land in my pocket, but I've been involved with them now for 15 years, and I've never seen an organization squeeze a dollar more, so I really think it's worth your while. EFF.org, thank you.
[APPLAUSE]
Oh— someone over here, yes, hi.
That mic is off—
[TAPPING NOISE FROM MIC]
Oh, there you go.
AUDIENCE MEMBER: Thank you very much, really appreciate the speech, it was very inspiring...
CORY: Thank you.
AUDIENCE MEMBER: Um, I think... maybe not sure how many other people feel this way, but one thing that's been hard to me about politics in general, especially in the age of social media is, you know, there's a lot of it at spreads messages of fear and anger and hatred, and sometimes it feels like when you want to say something, and you want to spread a certain voice, or just spread a certain message, that there's this fear of getting swept up in all these messages, and ideas and things that aren't necessarily... you're not necessarily aware of your own biases, and things like that... how does one stay sane, and fight for, you know, the right fight?
CORY: God... I, you know, I wish I knew. I, like, I'll freely admit to you, I've had more sleepless nights in the last two years than in all the years before it. I mean, even during the movement to end nuclear proliferation, that was a big part of in the 80s, when I thought we were all going to die in a mushroom cloud, I wasn't as worried as I am now.
It's tough, I mean, for me like just in terms of like personal... psychological OPSEC? I've turned off everything that non-consensually shoves Donald Trump headlines into my eyeballs? You know, that we talk a lot about how like engagement metrics distort the way applications are designed, but you know I really came to understand that that was happening about a year and a half ago, so, for example they changed the default Android search bar? So that when you tapped in it showed you trending searches... Well, like nobody has ever gone to a search engine to find out what other people are searching for, right? And the trending searches were inevitably “Trump threatens nuclear Armageddon”.
So the last thing I would do before walking my daughter to school every morning, is I would go to the Weather App and I would tap in it to see the weather, and it's news, and it's weather, and headlines. And the only headlines you can't turn off are “Top Headlines”, and they're trending, you know, they're all “Trump Threatens Nuclear Armageddon,” right?
So I realized, after a month of this, that what had been, really, the most calming grounding 10 minutes, 15 minutes of my day, where I would walk with my daughter to school, we talked about stuff, and it was really quiet — we live in a leafy street — I just spend that whole time worrying about dying, right?
And so, I had to figure out how to like go through and turn all that stuff off, now what I do is I block out times to think about headlines. So I go and I look at the news for a couple hours, every day, and I write about it. I write BoingBoing, right? I write a blog about it, not necessarily because my opinions are such great opinions, but because being synthetic and thoughtful about it means that it's not just buffeting me, right? It becomes a reflective, rather than a reflexive exercise. But I don't know, right? I mean, I think that— and I don't think it's just the tech. I think we are living in a moment of great psychic trauma. We are living in a, you know, the reason the IPCC report was terrifying, was not because of the shrill headlines. The IPCC report was terrifying because it is objectively terrifying, right.
And so... how do you make things that are, I don't know how you make things that are objectively terrifying not terrifying. I think the best we can hope for is to operate while we are terrified, with as much calm and aplomb and thoughtfulness as is possible.
[APPLAUSE]
How are we for time, do you want me off? I know my clock's run out, or can I take one more question? Stage manager? One more or... la— one more, all right and then we'll ring us off, yeah.
AUDIENCE MEMBER: Yeahhhh, hi—
CORY: Better be good, though...
AUDIENCE: Okay, I'm ready I work for the Media Lab too, so my question Cory, thank you for your talk, I think, a lot of people in the cryptocurrency world think about the current systems that we exist in and we're trying to exit those systems to some extent, and create parallel financial, you know, political institutions, what have you, versus expressing voice within the current system... How do you balance, exit versus voice, in the current system?
CORY: Well you know in a techno— in a, and, I said before, that, like, a constitutional argument is just an Internet flame war by another means, right? So, when you're arguing about a commit, and a pull request one of the things you do is you do proof of concept, right? You show that the thing that you're patching is real and can be exploited, or you show that you're, you run unit tests, to show that your patch performs well.
Those parallel exercises are useful as proof of concepts and as unit tests, right? They're prototypes that we can fold back into a wider world. And I think that, it— the thing I worry about, is not that technologists will build technology... I want technologists to build technology. It's that, they will think that the job stops when you've built the proof-of-concept. That's where the job starts, right? When you can prove that you've written a better algorithm, you then have to convince the other stakeholders in the project that it's worth the actual, like, non-zero cost of patching to make that, to make that work, right? Of going through the whole source tree and finding all the dependencies on the things that you're pulling out and gracefully replacing them, because, you know, when you run a big data center, you can't just start patching stuff, you've gotta— you've gotta tool chain that you have to preserve, right?
And so that's— that's, where the job starts, right? Build your proof-of-concept, build us a parallel financial system, build us a whatever, so that we can figure out how to integrate it into a much wider, more pluralistic world, not so that we can separate and sea-stead on our little, you know, world, over there. As you know, like, it doesn't matter how great your ear—
[APPLAUSE]
Thank you, doesn't matter how great your, your, your bunker is, right? Like you can't shoot germs, right? Like if your solution allows the rest of the world to fall into chaos, and no one's taking care of the sanitation system, you will still shit yourself to death of cholera, in your bunker, because, like, you can't shoot germs, right? So we need pluralistic solutions that work for all of us!
Thank you
[APPLAUSE]
Thank you, all right, thanks everyone.
1 note
·
View note
Text
6 questions about redirects for SEO
A redirect happens when someone asks for a specific page but gets sent to a different page. Often, the site owner deleted the page and set up a redirect to send visitors and search engine crawlers to a relevant page. A much better approach then serving them an annoying, user experience breaking 404 message. Redirects play a big part in the lives of site owners, developers, and SEOs. So let’s answer a couple of recurring questions about redirects for SEO.
Optimize your site for search & social media and keep it optimized with Yoast SEO Premium »

$89 - Buy now »
Info 1. Are redirects bad for SEO?
Well, it depends, but in most cases, no. Redirects are not bad for SEO, but — as with so many things — only if you put them in place correctly. A bad implementation might cause all kinds of trouble, from loss of PageRank to loss of traffic. Redirecting pages is a must if you make any changes to your URLs. After all, you don’t want to see all the hard work you put into building an audience and gathering links to go down the drain.
2. Why should I redirect a URL?
By redirecting a changed URL, you send both users and crawlers to a new URL, therefore keeping annoyances to a minimum. Whenever you perform any kind of maintenance on your site you are actually taking stuff out. You could be deleting a post, changing your URL structure or moving your site to a new domain. You have to replace it or visitors will land on those dreaded 404 pages. If you make small changes, like delete an outdated article, you can redirect that old URL with a 301 to a relevant new article or give it a 410 to say that you deleted it. Don’t delete stuff without a plan. And don’t redirect your URLs to random articles that don’t have anything to do with the article you’re deleting.
Bigger projects need a URL migration strategy. Going from HTTP to HTTPS for instance — more on that later on in this article, changing the URL paths, or moving your site to a new domain. In these cases, you should look at all the URLs on your site and map these to their future locations on the new domain. After determining what goes where, you can start redirecting the URLs. Use the change of address tool in Google Search Console to notify Google of the changes.
3. What is a 301 redirect? And a 302 redirect?
Use a 301 redirect to permanently redirect a URL to a new destination. This way, you tell both visitors and search engine crawlers that this URL changed and a new destination is found. This the most common redirect. Don’t use a 301 if you ever want to use that specific URL ever again. If so, you need a 302 redirect.
A 302 redirect is a so-called temporary redirect. This means that you can use this to say this piece of content is temporarily unavailable at this address, but it is going to come back. Need more information on which redirect to pick?
4. What’s an easy way to manage redirects in WordPress?
We might be a bit biased, but we think the redirects manager in our Yoast SEO Premium WordPress plugin is incredible. We know that a lot of people struggle to understand the concept of redirects and the kind of work that goes into adding and managing them. That’s why one of the first things we wanted our WordPress SEO plugin to have was an easy to use redirect tool. I think we succeeded, but don’t take my word for it. Here’s what Lindsay recently said:
#SEO pointer. Overwhelmed by 404 errors in the Google Search Console? Look for patterns and then use regex. And if you have a #WordPress website, get Yoast Premium. The redirect manager rocks! Thanks, @yoast!
— Lindsay Halsey (@lindsay_wpseo) June 27, 2018
The redirects manager can help set up and manage redirect on your WordPress site. It’s an indispensable tool if you want to keep your site fresh and healthy. We made it as easy as possible. Here’s what happens when you delete a post:
Move a post to trash
A message pops up saying that you moved a post to thrash
Choose one of two options given by the redirects manager:
Redirect to another URL
Serve a 410 Content deleted header
If you pick redirect, a modal opens where you can enter the new URL for this particular post
Save and you’re done!
So convenient, right? Here’s an insightful article called What does the redirects manager in Yoast SEO do, that answers that question.
5. What is a redirect checker?
A redirect checker is a tool to determine if a certain URL is redirected and to analyze the path it follows. You can use this information to find bottlenecks, like a redirect chain in which a URL is redirected many times, making it much harder for Google to crawl that URL — and giving users a less than stellar user experience. These chains often happen without you knowing about it: if you delete a page that was already redirected, you add another piece to the chain. So, you need to keep an eye on your redirects and one of the tools to do that is a redirect checker.
You can use one of the SEO suites such as Sitebulb, Ahrefs and Screaming Frog to test your redirects and links. If you only need a quick check, you can also use a simpler tool like httpstatus.io to give you an insight into the life of a URL on your site. Another must-have tool is the Redirect Path extension for Chrome, made by Ayima.
6. Do I need to redirect HTTP to HTTPS?
Whenever you plan to move to the much-preferred HTTPS protocol for your site — you know, the one with the green padlock in the address bar — you must redirect your HTTP traffic to HTTPS. You could get into trouble with Google if you make your site available on both HTTP and HTTPS, so watch out for that. Also, browsers will show a NOT SECURE message when the site is — you guessed it — not secured by a HTTPS connection. Plus, Google prefers HTTPS sites, because these tend to be faster and more secure. Your visitors expect the extra security as well.
So, you need to set up a 301 redirect from HTTP to HTTPS. There are a couple of way of doing this and you must plan this to make sure everything goes like it should. First, the preferred way of doing this is at server level. Find out on what kind of server your site is running (NGINX, Apache, or something else) and find the code needed to add to your server config file or .htaccess file. Most often, your host will have a guide to help you set up a redirect for HTTP to HTTPS on server level. Jimmy, one of our developers also wrote a guide helping you move your website from HTTP to HTTPS.
There are also WordPress plugins that can handle the HTTPS/SSL stuff for your site, but for this specific issue, I wouldn’t rely on a plugin, but manage your redirect at a server level. Don’t forget to let Google know of the changes in Search Console.
Redirects for SEO
There are loads of questions about redirects to answer. If you think about it, the concept of a redirect isn’t too hard to grasp. Getting started with redirects isn’t that hard either. The hard part of working with redirects is managing them. Where are all these redirects leading? What if something breaks? Can you find redirect chains or redirect loops? Can you shorten the paths? You can gain a lot from optimizing your redirects, so you should dive in and fix them. Do you have burning questions about redirects? Let us know in the comments!
Read more: ‘How to properly delete a page from your site’ »
https://ift.tt/2IPOul3
0 notes
Text
6 questions about redirects for SEO
A redirect happens when someone asks for a specific page but gets sent to a different page. Often, the site owner deleted the page and set up a redirect to send visitors and search engine crawlers to a relevant page. A much better approach then serving them an annoying, user experience breaking 404 message. Redirects play a big part in the lives of site owners, developers, and SEOs. So let’s answer a couple of recurring questions about redirects for SEO.
Optimize your site for search & social media and keep it optimized with Yoast SEO Premium »

$89 - Buy now »
Info
1. Are redirects bad for SEO?
Well, it depends, but in most cases, no. Redirects are not bad for SEO, but — as with so many things — only if you put them in place correctly. A bad implementation might cause all kinds of trouble, from loss of PageRank to loss of traffic. Redirecting pages is a must if you make any changes to your URLs. After all, you don’t want to see all the hard work you put into building an audience and gathering links to go down the drain.
2. Why should I redirect a URL?
By redirecting a changed URL, you send both users and crawlers to a new URL, therefore keeping annoyances to a minimum. Whenever you perform any kind of maintenance on your site you are actually taking stuff out. You could be deleting a post, changing your URL structure or moving your site to a new domain. You have to replace it or visitors will land on those dreaded 404 pages. If you make small changes, like delete an outdated article, you can redirect that old URL with a 301 to a relevant new article or give it a 410 to say that you deleted it. Don’t delete stuff without a plan. And don’t redirect your URLs to random articles that don’t have anything to do with the article you’re deleting.
Bigger projects need a URL migration strategy. Going from HTTP to HTTPS for instance — more on that later on in this article, changing the URL paths, or moving your site to a new domain. In these cases, you should look at all the URLs on your site and map these to their future locations on the new domain. After determining what goes where, you can start redirecting the URLs. Use the change of address tool in Google Search Console to notify Google of the changes.
3. What is a 301 redirect? And a 302 redirect?
Use a 301 redirect to permanently redirect a URL to a new destination. This way, you tell both visitors and search engine crawlers that this URL changed and a new destination is found. This the most common redirect. Don’t use a 301 if you ever want to use that specific URL ever again. If so, you need a 302 redirect.
A 302 redirect is a so-called temporary redirect. This means that you can use this to say this piece of content is temporarily unavailable at this address, but it is going to come back. Need more information on which redirect to pick?
4. What’s an easy way to manage redirects in WordPress?
We might be a bit biased, but we think the redirects manager in our Yoast SEO Premium WordPress plugin is incredible. We know that a lot of people struggle to understand the concept of redirects and the kind of work that goes into adding and managing them. That’s why one of the first things we wanted our WordPress SEO plugin to have was an easy to use redirect tool. I think we succeeded, but don’t take my word for it. Here’s what Lindsay recently said:
#SEO pointer. Overwhelmed by 404 errors in the Google Search Console? Look for patterns and then use regex. And if you have a #WordPress website, get Yoast Premium. The redirect manager rocks! Thanks, @yoast!
— Lindsay Halsey (@lindsay_wpseo) June 27, 2018
The redirects manager can help set up and manage redirect on your WordPress site. It’s an indispensable tool if you want to keep your site fresh and healthy. We made it as easy as possible. Here’s what happens when you delete a post:
Move a post to trash
A message pops up saying that you moved a post to thrash
Choose one of two options given by the redirects manager:
Redirect to another URL
Serve a 410 Content deleted header
If you pick redirect, a modal opens where you can enter the new URL for this particular post
Save and you’re done!
So convenient, right? Here’s an insightful article called What does the redirects manager in Yoast SEO do, that answers that question.
5. What is a redirect checker?
A redirect checker is a tool to determine if a certain URL is redirected and to analyze the path it follows. You can use this information to find bottlenecks, like a redirect chain in which a URL is redirected many times, making it much harder for Google to crawl that URL — and giving users a less than stellar user experience. These chains often happen without you knowing about it: if you delete a page that was already redirected, you add another piece to the chain. So, you need to keep an eye on your redirects and one of the tools to do that is a redirect checker.
You can use one of the SEO suites such as Sitebulb, Ahrefs and Screaming Frog to test your redirects and links. If you only need a quick check, you can also use a simpler tool like httpstatus.io to give you an insight into the life of a URL on your site. Another must-have tool is the Redirect Path extension for Chrome, made by Ayima.
6. Do I need to redirect HTTP to HTTPS?
Whenever you plan to move to the much-preferred HTTPS protocol for your site — you know, the one with the green padlock in the address bar — you must redirect your HTTP traffic to HTTPS. You could get into trouble with Google if you make your site available on both HTTP and HTTPS, so watch out for that. Also, browsers will show a NOT SECURE message when the site is — you guessed it — not secured by a HTTPS connection. Plus, Google prefers HTTPS sites, because these tend to be faster and more secure. Your visitors expect the extra security as well.
So, you need to set up a 301 redirect from HTTP to HTTPS. There are a couple of way of doing this and you must plan this to make sure everything goes like it should. First, the preferred way of doing this is at server level. Find out on what kind of server your site is running (NGINX, Apache, or something else) and find the code needed to add to your server config file or .htaccess file. Most often, your host will have a guide to help you set up a redirect for HTTP to HTTPS on server level. Jimmy, one of our developers also wrote a guide helping you move your website from HTTP to HTTPS.
There are also WordPress plugins that can handle the HTTPS/SSL stuff for your site, but for this specific issue, I wouldn’t rely on a plugin, but manage your redirect at a server level. Don’t forget to let Google know of the changes in Search Console.
Redirects for SEO
There are loads of questions about redirects to answer. If you think about it, the concept of a redirect isn’t too hard to grasp. Getting started with redirects isn’t that hard either. The hard part of working with redirects is managing them. Where are all these redirects leading? What if something breaks? Can you find redirect chains or redirect loops? Can you shorten the paths? You can gain a lot from optimizing your redirects, so you should dive in and fix them. Do you have burning questions about redirects? Let us know in the comments!
Read more: ‘How to properly delete a page from your site’ »
The post 6 questions about redirects for SEO appeared first on Yoast.
from Yoast • SEO for everyone https://yoast.com/6-questions-about-redirects-for-seo/
0 notes
Photo

New Post has been published on http://www.lifehacker.guru/how-to-clean-up-and-optimize-your-sluggish-mac/
How to Clean Up and Optimize Your Sluggish Mac
Your Mac is running a little slow these days. It takes forever to boot up. You have to delete something just to download that file attachment from Carla in accounting. Any time you stream a video it seems to lock up for a few seconds. Let’s fix all that.
Update Your System Software
Before we do anything, let’s make sure your Mac is up to date. Click the Apple icon > App Store, then click the Updates tab. Install any software updates you see here, including macOS updates. This might include security updates or small performance improvements for whatever version of macOS you’re running.
Of course, Apple’s operating systems have been free for the last several iterations, so if you want to also update to Mavericks, Yosemite, El Capitan, or Sierra, you can usually do so without any knock on your Mac’s performance. This is completely optional and up to you, but make sure you are at least running the most recent version of whichever operating system you’ve landed on.
Get Rid of Old Apps
Generally speaking, cleaning up your Mac is mostly about deleting all the cruft you’ve accumulated over the years. Personally, I like to start by removing apps and then move onto deleting files. It’s very easy to glance at a list and know whether you still use an app or not.
Open up your Applications folder, then sort the apps by size, with the largest at the top. If you have a huge application installed that you never use, like iMovie or Garageband, get rid of them. Remember, you can always download anything you got from the Mac App Store again. If you purchased software from a developer, make sure you still have the license key somewhere before you delete it, just in case you need it again at some point in the future.
We’re all trained to uninstall Mac apps by dragging an icon into the trash from the Applications folder, but doing so tends to leave random files associated with that app across your system. These orphan files are rarely substantial in size, but it’s clutter nonetheless. Instead, it’s best to use a utility that’ll also track down that orphaned files. I like App Cleaner for this because it’s free and easy to use. Click and drag an application you want to delete into the App Cleaner window, then App Cleaner hunts down and removes any files associated with that application.
Clear Out Your Storage Space
Chances are, once you clear out a bunch of dumb old apps you no longer use, you’ll have a lot more storage space. That’s not the end of the process though. Next up, it’s time to dig around for weird old files you no longer need.
If you’re running macOS Sierra, you can easily find and remove large files using the built-in storage manager. If you’re not on Sierra, I like the $10 hard drive analyzer, DaisyDisk. DaisyDisk analyzes your system, finds massive files, then lets you delete those files right from the app. Launch DaisyDisk and it shows you a graph with all your files based on type. This way, you can track down anything that’s suspiciously large, like some random video you needed one time, then delete it. DaisyDisk is idiot-proof and automatically hides system files. Since you can preview files in the app, it’s pretty hard to remove an important file on accident. Even still, before you do this, make sure you have backups of any important files.
Go through your very large files and delete anything you no longer need. Depending on how you tend to store files or if you have different backups, this might be a few downloads you forgot about, or it might be entire directories of files you no longer need. For example, as you can see in the GIF above, I can follow a trail of storage hogs all the way down to my email application’s hidden attachments folder.
If you don’t want to shell out the $10 for DaisyDisk and you’re not using macOS Sierra, Disk Inventory X is free, but you’ll have to go back and manually locate the large files Disk Inventory X finds in Finder to remove them.
Optimize Your System
Next up, it’s time to clear up all the random cache files, histories, and other junk that’s wasting space and slowing down your system. Historically, we’ve long been fans of OnyX for this task.
When you first open up OnyX, it’s a bit confusing because you’ll see multiple tabs with a lot of different check boxes. Most of us don’t need to worry about the majority of this though. For a quick cleansing and optimization of your Mac, click the Automation tab. The default settings here are pretty safe for everyone, though some people may want to uncheck the box next to Web browser cache and history if you don’t want to lose specific data from your browser. When you’re happy with your selections, click the Execute button. If you prefer a more manual approach, click the Cleaning tab instead of Automation, then select the specific data to purge.
If you don’t like OnyX for whatever reason, CCleaner does a similar thing and is easier to use. They’re both functionally the same, but OnyX has far more options for advanced users and can do everything for free out of the box without any additional purchases.
Clean Up Everything Else
Finally, let’s clear out a few other places the above options might have missed.
Empty your trash: You do empty your trash now and again, right? If not, Ctrl-click the trash can in the dock and select Empty Trash.
Clear out your Downloads folder: Most browsers save every file you download to the appropriately named Downloads folder. You should clear that out sometimes. Open up Finder, then head to username/Downloads. Take a look at all the files in here, delete anything you don’t need, and move everything you do want to keep to a safer place.
Clean up your desktop: Do you have a lot of files on your desktop? First off, you’re a monster. Second, that’s probably slowing down your computer. Clean it up. Find folders for those files to live in and delete files you don’t need.
Remove old disk images: Macs use disk images to install files, which makes for easy installation, but also means that some of us tend to have random disk images all over the place. Open up Finder, click on All My Files, then type “disk manager” into the search box to locate any of those DMG files hidden throughout your Mac.
Clear out old Mail downloads: If you use Apple Mail, attachments and other random files can clog up your hard drive. Open up Spotlight (press Command+Space), then type in “Mail Downloads.” Tap Enter on the folder that pops up. This folder might have hundreds of items. These are all the various attachments Mail has downloaded over the years. Assuming you’re not using a POP email server, which doesn’t retain old copies after they’re downloaded, you can safely delete every file inside this folder and they will remain on email server.
If you’re unwilling or unable to do all this stuff on your own, there’s CleanMyMac, which for $40 does pretty much everything I listed above all in one app. CleanMyMac can fully remove apps, do general performance maintenance, and it’ll track down a variety of large files for easy removal. It works great provided you don’t mind shelling out the $40 for it, but it doesn’t do more than the elbow-grease intensive methods above.
Recommended Stories
How to Make a Bootable macOS Sierra USB Install Drive
Should I Upgrade to macOS Sierra?
In Defense of the Clean Install
©
0 notes