#spy software for mobile
Explore tagged Tumblr posts
Text
ONEMONITAR Mobile Spy App for Employee Tracking

Boost workplace productivity with ONEMONITAR. The mobile spy app helps businesses monitor employee activity, ensuring compliance, efficiency, and better resource management.
0 notes
Text

Track and secure your devices with our cutting-edge mobile monitoring software. Monitor calls, messages, apps, and location in real-time. Stay informed, ensure safety, and manage devices with ease. Reliable, secure, and user-friendly for peace of mind.
083840 32094
0 notes
Text
CHYLDMONITOR Mobile Spy for Android

Get CHYLDMONITOR, the ultimate mobile spy solution tailored for Android devices. Seamlessly monitor phone activities, including call logs, messages, and app usage, all from a centralized control panel. With CHYLDMONITOR, you can ensure the safety of your children or enhance employee productivity by keeping an eye on their digital interactions. Experience top-notch Android monitoring today.
Protect and monitor effectively. Download CHYLDMONITOR for Android!
#mobile spy app#mobile spy software#mobile spy for android#mobile spy download#mobile spy without access to phone#mobile spy app hidden#mobile spy app undetectable#mobile spy parental control#mobile spy app with GPS tracking#mobile spy app features
0 notes
Text
Subprime gadgets

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me THIS SUNDAY in ANAHEIM at WONDERCON: YA Fantasy, Room 207, 10 a.m.; Signing, 11 a.m.; Teaching Writing, 2 p.m., Room 213CD.

The promise of feudal security: "Surrender control over your digital life so that we, the wise, giant corporation, can ensure that you aren't tricked into catastrophic blunders that expose you to harm":
https://locusmag.com/2021/01/cory-doctorow-neofeudalism-and-the-digital-manor/
The tech giant is a feudal warlord whose platform is a fortress; move into the fortress and the warlord will defend you against the bandits roaming the lawless land beyond its walls.
That's the promise, here's the failure: What happens when the warlord decides to attack you? If a tech giant decides to do something that harms you, the fortress becomes a prison and the thick walls keep you in.
Apple does this all the time: "click this box and we will use our control over our platform to stop Facebook from spying on you" (Ios as fortress). "No matter what box you click, we will spy on you and because we control which apps you can install, we can stop you from blocking our spying" (Ios as prison):
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
But it's not just Apple – any corporation that arrogates to itself the right to override your own choices about your technology will eventually yield to temptation, using that veto to help itself at your expense:
https://pluralistic.net/2023/07/28/microincentives-and-enshittification/
Once the corporation puts the gun on the mantelpiece in Act One, they're begging their KPI-obsessed managers to take it down and shoot you in the head with it in anticipation of of their annual Act Three performance review:
https://pluralistic.net/2023/12/08/playstationed/#tyler-james-hill
One particularly pernicious form of control is "trusted computing" and its handmaiden, "remote attestation." Broadly, this is when a device is designed to gather information about how it is configured and to send verifiable testaments about that configuration to third parties, even if you want to lie to those people:
https://www.eff.org/deeplinks/2023/08/your-computer-should-say-what-you-tell-it-say-1
New HP printers are designed to continuously monitor how you use them – and data-mine the documents you print for marketing data. You have to hand over a credit-card in order to use them, and HP reserves the right to fine you if your printer is unreachable, which would frustrate their ability to spy on you and charge you rent:
https://arstechnica.com/gadgets/2024/02/hp-wants-you-to-pay-up-to-36-month-to-rent-a-printer-that-it-monitors/
Under normal circumstances, this technological attack would prompt a defense, like an aftermarket mod that prevents your printer's computer from monitoring you. This is "adversarial interoperability," a once-common technological move:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
An adversarial interoperator seeking to protect HP printer users from HP could gin up fake telemetry to send to HP, so they wouldn't be able to tell that you'd seized the means of computation, triggering fines charged to your credit card.
Enter remote attestation: if HP can create a sealed "trusted platform module" or a (less reliable) "secure enclave" that gathers and cryptographically signs information about which software your printer is running, HP can detect when you have modified it. They can force your printer to rat you out – to spill your secrets to your enemy.
Remote attestation is already a reliable feature of mobile platforms, allowing agencies and corporations whose services you use to make sure that you're perfectly defenseless – not blocking ads or tracking, or doing anything else that shifts power from them to you – before they agree to communicate with your device.
What's more, these "trusted computing" systems aren't just technological impediments to your digital wellbeing – they also carry the force of law. Under Section 1201 of the Digital Millennium Copyright Act, these snitch-chips are "an effective means of access control" which means that anyone who helps you bypass them faces a $500,000 fine and a five-year prison sentence for a first offense.
Feudal security builds fortresses out of trusted computing and remote attestation and promises to use them to defend you from marauders. Remote attestation lets them determine whether your device has been compromised by someone seeking to harm you – it gives them a reliable testament about your device's configuration even if your device has been poisoned by bandits:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The fact that you can't override your computer's remote attestations means that you can't be tricked into doing so. That's a part of your computer that belongs to the manufacturer, not you, and it only takes orders from its owner. So long as the benevolent dictator remains benevolent, this is a protective against your own lapses, follies and missteps. But if the corporate warlord turns bandit, this makes you powerless to stop them from devouring you whole.
With that out of the way, let's talk about debt.
Debt is a normal feature of any economy, but today's debt plays a different role from the normal debt that characterized life before wages stagnated and inequality skyrocketed. 40 years ago, neoliberalism – with its assaults on unions and regulations – kicked off a multigenerational process of taking wealth away from working people to make the rich richer.
Have you ever watched a genius pickpocket like Apollo Robbins work? When Robins lifts your wristwatch, he curls his fingers around your wrist, expertly adding pressure to simulate the effect of a watchband, even as he takes away your watch. Then, he gradually releases his grip, so slowly that you don't even notice:
https://www.reddit.com/r/nextfuckinglevel/comments/ppqjya/apollo_robbins_a_master_pickpocket_effortlessly/
For the wealthy to successfully impoverish the rest of us, they had to provide something that made us feel like we were still doing OK, even as they stole our wages, our savings, and our futures. So, even as they shipped our jobs overseas in search of weak environmental laws and weaker labor protection, they shared some of the savings with us, letting us buy more with less. But if your wages keep stagnating, it doesn't matter how cheap a big-screen TV gets, because you're tapped out.
So in tandem with cheap goods from overseas sweatshops, we got easy credit: access to debt. As wages fell, debt rose up to fill the gap. For a while, it's felt OK. Your wages might be falling off, the cost of health care and university might be skyrocketing, but everything was getting cheaper, it was so easy to borrow, and your principal asset – your family home – was going up in value, too.
This period was a "bezzle," John Kenneth Galbraith's name for "The magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it." It's the moment after Apollo Robbins has your watch but before you notice it's gone. In that moment, both you and Robbins feel like you have a watch – the world's supply of watch-derived happiness actually goes up for a moment.
There's a natural limit to debt-fueled consumption: as Michael Hudson says, "debts that can't be paid, won't be paid." Once the debtor owes more than they can pay back – or even service – creditors become less willing to advance credit to them. Worse, they start to demand the right to liquidate the debtor's assets. That can trigger some pretty intense political instability, especially when the only substantial asset most debtors own is the roof over their heads:
https://pluralistic.net/2022/11/06/the-end-of-the-road-to-serfdom/
"Debts that can't be paid, won't be paid," but that doesn't stop creditors from trying to get blood from our stones. As more of us became bankrupt, the bankruptcy system was gutted, turned into a punitive measure designed to terrorize people into continuing to pay down their debts long past the point where they can reasonably do so:
https://pluralistic.net/2022/10/09/bankruptcy-protects-fake-people-brutalizes-real-ones/
Enter "subprime" – loans advanced to people who stand no meaningful chance of every paying them back. We all remember the subprime housing bubble, in which complex and deceptive mortgages were extended to borrowers on the promise that they could either flip or remortgage their house before the subprime mortgages detonated when their "teaser rates" expired and the price of staying in your home doubled or tripled.
Subprime housing loans were extended on the belief that people would meekly render themselves homeless once the music stopped, forfeiting all the money they'd plowed into their homes because the contract said they had to. For a brief minute there, it looked like there would be a rebellion against mass foreclosure, but then Obama and Timothy Geithner decreed that millions of Americans would have to lose their homes to "foam the runways" for the banks:
https://wallstreetonparade.com/2012/08/how-treasury-secretary-geithner-foamed-the-runways-with-childrens-shattered-lives/
That's one way to run a subprime shop: offer predatory loans to people who can't afford them and then confiscate their assets when they – inevitably – fail to pay their debts off.
But there's another form of subprime, familiar to loan sharks through the ages: lend money at punitive interest rates, such that the borrower can never repay the debt, and then terrorize the borrower into making payments for as long as possible. Do this right and the borrower will pay you several times the value of the loan, and still owe you a bundle. If the borrower ever earns anything, you'll have a claim on it. Think of Americans who borrowed $79,000 to go to university, paid back $190,000 and still owe $236,000:
https://pluralistic.net/2020/12/04/kawaski-trawick/#strike-debt
This kind of loan-sharking is profitable, but labor-intensive. It requires that the debtor make payments they fundamentally can't afford. The usurer needs to get their straw right down into the very bottom of the borrower's milkshake and suck up every drop. You need to convince the debtor to sell their wedding ring, then dip into their kid's college fund, then steal their father's coin collection, and, then break into cars to steal the stereos. It takes a lot of person-to-person work to keep your sucker sufficiently motivated to do all that.
This is where digital meets subprime. There's $1T worth of subprime car-loans in America. These are pure predation: the lender sells a beater to a mark, offering a low down-payment loan with a low initial interest rate. The borrower makes payments at that rate for a couple of months, but then the rate blows up to more than they can afford.
Trusted computing makes this marginal racket into a serious industry. First, there's the ability of the car to narc you out to the repo man by reporting on its location. Tesla does one better: if you get behind in your payments, your Tesla immobilizes itself and phones home, waits for the repo man to come to the parking lot, then it backs itself out of the spot while honking its horn and flashing its lights:
https://tiremeetsroad.com/2021/03/18/tesla-allegedly-remotely-unlocks-model-3-owners-car-uses-smart-summon-to-help-repo-agent/
That immobilization trick shows how a canny subprime car-lender can combine the two kinds of subprime: they can secure the loan against an asset (the car), but also coerce borrowers into prioritizing repayment over other necessities of life. After your car immobilizes itself, you just might decide to call the dealership and put down your credit card, even if that means not being able to afford groceries or child support or rent.
One thing we can say about digital tools: they're flexible. Any sadistic motivational technique a lender can dream up, a computerized device can execute. The subprime car market relies on a spectrum of coercive tactics: cars that immobilize themselves, sure, but how about cars that turn on their speakers to max and blare a continuous recording telling you that you're a deadbeat and demanding payment?
https://archive.nytimes.com/dealbook.nytimes.com/2014/09/24/miss-a-payment-good-luck-moving-that-car/
The more a subprime lender can rely on a gadget to torment you on their behalf, the more loans they can issue. Here, at last, is a form of automation-driven mass unemployment: normally, an economy that has been fully captured by wealthy oligarchs needs squadrons of cruel arm-breakers to convince the plebs to prioritize debt service over survival. The infinitely flexible, tireless digital arm-breakers enabled by trusted computing have deprived all of those skilled torturers of their rightful employment:
https://pluralistic.net/2021/04/02/innovation-unlocks-markets/#digital-arm-breakers
The world leader in trusted computing isn't cars, though – it's phones. Long before anyone figured out how to make a car take orders from its manufacturer over the objections of its driver, Apple and Google were inventing "curating computing" whose app stores determined which software you could run and how you could run it.
Back in 2021, Indian subprime lenders hit on the strategy of securing their loans by loading borrowers' phones up with digital arm-breaking software:
https://restofworld.org/2021/loans-that-hijack-your-phone-are-coming-to-india/
The software would gather statistics on your app usage. When you missed a payment, the phone would block you from accessing your most frequently used app. If that didn't motivate you to pay, you'd lose your second-most favorite app, then your third, fourth, etc.
This kind of digital arm-breaking is only possible if your phone is designed to prioritize remote instructions – from the manufacturer and its app makers – over your own. It also only works if the digital arm-breaking company can confirm that you haven't jailbroken your phone, which might allow you to send fake data back saying that your apps have been disabled, while you continue to use those apps. In other words, this kind of digital sadism only works if you've got trusted computing and remote attestation.
Enter "Device Lock Controller," an app that comes pre-installed on some Google Pixel phones. To quote from the app's description: "Device Lock Controller enables device management for credit providers. Your provider can remotely restrict access to your device if you don't make payments":
https://lemmy.world/post/13359866
Google's pitch to Android users is that their "walled garden" is a fortress that keeps people who want to do bad things to you from reaching you. But they're pre-installing software that turns the fortress into a prison that you can't escape if they decide to let someone come after you.
There's a certain kind of economist who looks at these forms of automated, fine-grained punishments and sees nothing but a tool for producing an "efficient market" in debt. For them, the ability to automate arm-breaking results in loans being offered to good, hardworking people who would otherwise be deprived of credit, because lenders will judge that these borrowers can be "incentivized" into continuing payments even to the point of total destitution.
This is classic efficient market hypothesis brain worms, the kind of cognitive dead-end that you arrive at when you conceive of people in purely economic terms, without considering the power relationships between them. It's a dead end you navigate to if you only think about things as they are today – vast numbers of indebted people who command fewer assets and lower wages than at any time since WWII – and treat this as a "natural" state: "how can these poors expect to be offered more debt unless they agree to have their all-important pocket computers booby-trapped?"

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/29/boobytrap/#device-lock-controller

Image: Oatsy (modified) https://www.flickr.com/photos/oatsy40/21647688003
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
#pluralistic#debt#subprime#armbreakers#mobile#google#android#apps#drm#technological self-determination#efficient market hypothesis brainworms#law and political economy#gadgets#boobytraps#app stores#curated computing#og app#trusted computing
230 notes
·
View notes
Note
After seeing your weatherbugapp reblog i installed duckduckgo and tried it.
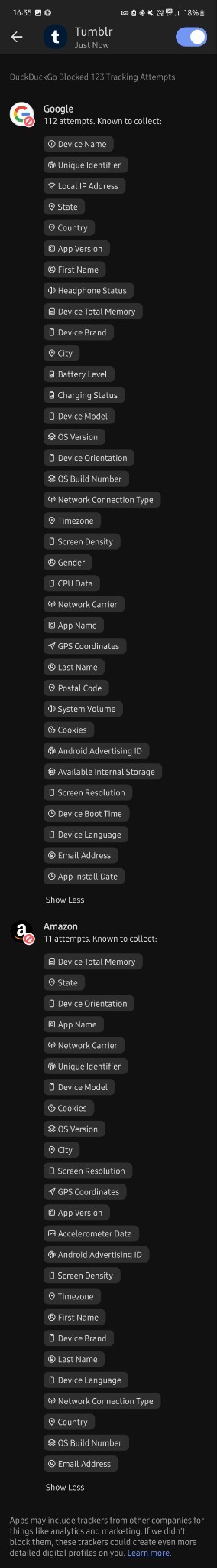
I don't know much about technology tbh but i downloaded this app less than 30 mins ago and in that time google tried to track me 112 times?? And they tried to collect finger prints? And my first and last name? And my gender? And my country, state and city? My gps coordinates? My postal code? My network carrier? My fricking battery level for whatever reason? Can you please tell me if this is normal at all, because i'm freaking out right now. I just turned 18 and started using mobile banking and stuff and this shit scares me
Why tf does it need to know my screen density???my system volume????my charging status????? What tf are they cooking
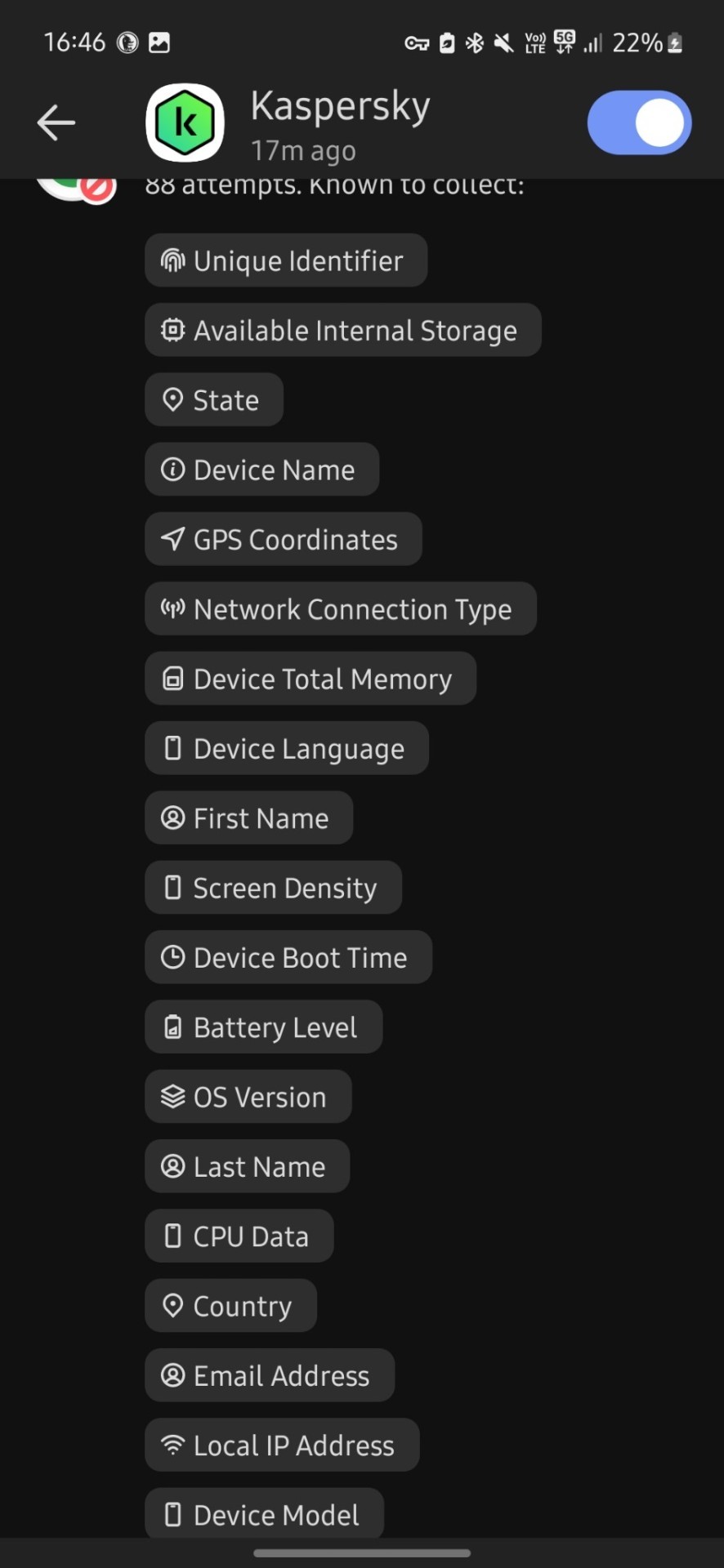
Now it's at 476 tracking attempts bro???? barely 5 mins passed.....
I condensed your three asks into one for readability!
And yeah, I'm very far from an expert about any of this, but as far as I know that's just. Normal. That's the normal amount of spying they're doing on your phone. I assume the numbers we see are to some extent because having been foiled, a lot of these scripts try repeatedly, since I can't imagine what use thousands of trackers per phone would be even to the great aggregators.
Tracking the phone stuff like screen resolution and battery level is because (apart from that definitely not being considered remotely 'private' so it's Free Real Estate) in aggregate that data can be used to track what phone use patterns are like on a demographic scale and therefore. Where the smart money is.
Almost all of this is getting sold in bulk for ad targeting and market analysis. This does presumably make it very hard to notice when like. Actually important stuff is being spied on, which is why I feel better about Having Apps with the duckduckgo app blocker thing.
My bank's app reportedly sells data to a couple aggregators including Google. Not like, my banking info, but it's still so offensive on principle that I avoid using the app unless I have to, and force stop it afterward.
The patterns that show up on the weekly duckduckgo blocker report are interesting. Hoopla attempts about two orders of magnitude more tracking than Libby, which makes sense because they're a commercial streaming service libraries pay by the unit for access, while Libby is a content management software run by a corporation that values its certification as a 'B' company--that is, one invested in the public good that can be trusted. The cleanness of their brand is a great deal of its value, so they have to care about their image and be a little more scrupulous.
Which doesn't mean not being a little bit spyware, because everything is spyware now. Something else I've noticed is that in terms of free game apps, the polished professional stuff is now much more invasive than the random kinda janky thing someone just threw together.
Back in the day you tended to expect the opposite, because spyware was a marginal shifty profit-margin with too narrow a revenue stream to be worth more to an established brand than their reputation, but now that everyone does it there's not a lot of reputation cost and refraining would be sacrificing a potential revenue stream, which is Irresponsible Conduct for a corporation.
While meanwhile 'developing a free game app to put on the game store' is something a person can do for free with the hardware they already have for home use, as a hobby or practice or to put on their coding resume. So while such apps absolutely can be malicious and more dangerous when they are than The Big Brand, they can also be neutral in a way commercial stuff no longer is. Wild world.
But yeah for the most part as far as I can make out, these are just The Commercial Panopticon, operating as intended. It's gross but it probably doesn't indicate anything dangerous on an individual level.
56 notes
·
View notes
Text
Post #9 Week 12
Why does race swapping cause such a dramatic social uproar?
I'm sure as many saw through social media that amount of backlash the new real life remake of The Little Mermaid had when it first came out that the disney princess, Ariel would be played by Halle Bailey, an african american actress. All over social media it was filled with hating remarks about the actresses hair, her complexion, and overall personality being “wrong” for a fictional character. It was utterly disgusting. In Laytoa Lee’s article, Are Y’all Ready for a Black Mermaid? How Black Twitter Challenges White Supremacist Imaginations we learn the hate that comes through the big screen when roles are switched from white actors to african american actors. Lee explains, “For these “fans,” their discontent stemmed from the casting of a Black actress for a role that their minds should be played by a white actress, since the original animated film featured a white Ariel” (Lee 2023). The actors being switched with different looks creates more creative and unique styles to different cats, the art is subjective. However many ignorant people are ruining the whole idea by creating hate in a disturbing way.
How does connecting to an actress encourage the youth to be themselves?
In Laytoa Lee’s article, Are Y’all Ready for a Black Mermaid? How Black Twitter Challenges White Supremacist Imaginations we see in what ways young girls were deeply influenced by seeing their princess look like them. Lee shares, “ the surprise and awe on these beautiful little faces when they first realized the mermaid on film is Black like them. In one video, a little girl squeals and exclaims, “She’s like me” (Lee 2023). Even with all the hate associated within the actress, she still was able to share some light and touch the heart of many little girls. Seeing that an actual disney princess looks like you, gives hope and begins to make little girls believe that they can achieve so much. I feel like this is such a vital opportunity for the younger generation to experience all races. It helps kids connect to their true selves, and having these fictional characters can give them the greatest joy in my opinion. I think it was such a magical thing.
Is surveillance through mobile devices gonna change our future?
In this week's lecture we watched a short documentary titled, Survalliced and we saw the scary reality that the future may turn into. We see how specifically modern day software has targeted manu innocent individuals to watch and spy on their phones. The surveillance is watching our messages, social media, and everything on our phones. They are specifically targeting activists and their posts. We have even discussed in the class, how someone was targeted for like Black Lives Matter posts and was arrested and labeled a terrorist. This is extremely scary and concerning. We have to be alert in real life situations happening across the United States, social media is a great way to stay alert. However we have to be crucial in making sure that we aren't getting watched, however it's more hard to do than say.
Is there a way to put a stop to our technology being surveillanced?
It's no secret that our phones, laptops, ipads are being hacked into by the government or even other individuals. We know that the government has access to our tweets, photos, contacts, and pretty much anything on our phones. There's no escaping the software hacks of modern day technology. Even if our own social media is private, there's still ways to get into our profile. Pretending to be someone you're not or even through tags from friends. As long as you're a part of that cloud, hackers can gain access to information. We had a whole discussion a couple weeks ago about the dangers of hacking and ways to prevent it. However I think the most important thing we can do is spread awareness to everyone around us. Especially if we know political activists fighting for our futures, government officials specifically activists in order to punish them with a crime. Spreading awareness can help others continue to protest but safely.
Lee, L. (2023, April 14). Are Y’all ready for a black mermaid? how black twitter challenges White Supremacist imaginations. Ms. Magazine. https://msmagazine.com/2023/04/17/the-little-mermaid-halle-bailey-black-twitter/
O'Neill, M., & Peltz, P. (Directors). (2020). Surveilled [Film]. HBO Documentary Films.
4 notes
·
View notes
Text
Chinese Hack Means Beijing Reading and Hearing All US Military and Intelligence Classified Phone Communications
10 December 2024 by Larry C. Johnson 96 Comments

There has been some limited press coverage about recent Salt Typhoon — a Chinese cyber / hacking operation — but most Americans are oblivious about what has transpired. The story is simple. Following Edward Snowden’s escape to Russia and the release of damning evidence that the US Government was spying on Americans, the US Department of Justice pressured the telecommunications giants — i.e., Verizon, ATT and T-Mobile — to create a backdoor in their network software that allows Federal law enforcement to read texts and listen to calls on classified apps. If you are using WhatsApp and think you are safe from the government’s spying eyes, think again.
Sometime before the November 5 Presidential election, the US intelligence community discovered (or learned?) that the Chinese had hacked the “backdoor” and have had full access to all US Government-issued cell phones that use a classified app for text and voice communications. A knowledgeable source told me that the compromise started in 2022 and was only recently discovered.
What does this mean? All conversations / communications over the commercial networks are (or were) being read / recorded by China. My source described the Chinese hack as something akin to the Brits, with help from Polish and American cryptologists, breaking the Enigma machine and reading classified German military traffic.
6 notes
·
View notes
Text


I thought this one would be just another developer of mobile game that use The Sims 4 contents in its (fake) ads to fraud users by making people belive it is its game, when it has a completely different gameplay.
Unfortunately, Room Makover by FlyBird Casual Games is much more than this.
Room Makover has plenty of false ads. This time I actually tried the game, because the pictures and videos on Google Play were cute and I decided to give it a try.
I was so naive. Happens that the whole page on Google Play is full of fake contents.
It's just one of those mobile games in which you have to match and remove nails. Every time you pass a level, you will rewarded with bills that you can use to unlock part of a building under "makeover". You have just three option for every part of the building or the room to choose between.
There is nothing creative. Not actual building or cluttering rooms or decoring.
As, always, since I'm a curious little bitch, I decided to dig further into this FlyBird Casual Game and... Oh. God. Their site looks even less legit than LUCKY FORTUNE GAMES' one!
It is just a void page. There is nothing here. NOTHING. The only two working section are the privacy and conditions of use, in which they try to convince you that they didn't have any liability for damages or fraud committed.
The privacy one is curious, because mentions this Commissioner's Office in UK and a long list of partners. Both for ads and for data collection, which is hugely uncommon for this kind of games.
Sooooo... In this magical list of apps, I noticed a few tech nightmares, which I will explain briefly here:
Aarki is an AI company that builds advertising solutions to drive mobile revenue growth. Traslated from bullshit: they use AI to generate fake ads and sells it to shady corps.
Blind Ferret is the big deal here! Not only gave you digital marketing solutions, data collection and analytics, but also pays influencers and product placement on social media to promote the game and, hear me out, CREATE fake ads too! It's literally written in their site: "Our Creative Services don’t just make things look pretty. Our team uses data to guide us! How do we make brands shine? By turning the arts into a numbers game with top-performing creative content." This include: Graphic Design, Illustration, 2D Animation, Video Editing and Composition, Copywriting and conceptualizing.
InMobi is a big Corp that does native advertising, which means promoted contents, collabs with influencers, etc.
Ironsource. This one is a fucking cancer. IronSource Ltd. is an Israeli software company that focuses on developing technologies for app monetization and distribution, with its core production focused on the app economy. That would sound harmless, but Samsung use it in its budget and midrange smartphone to install multiple third-party apps during the set-up process. This platform slips bloatware on the pretext of recommended apps, leading to apps clutter and reduction in on-board storage space. The only purpose it exists on Samsung phones is to download games without your consent with no way to remove it (no app installed).
Mintegral is another fucking tech nightmare. Not only poses serious threats to your privacy and datas, but also uses malicious codes to spy your activity and when you seem intentioned to install a mobile app, Mintegral’s software would then fire off fake clicks on non-existent ads to claim credit for the install and essentially collect a bounty from app publishers who pay ad networks to promote their apps.
Mistplay is one of those "play to earn bucks" that I find very very dangerous. Because YOUR data are their revenue.
Tapjoy does monetization of ads and also surveys, that force users to download one from a long list of games, download it and playing for hours or since it is gained some in-game prize. This surveys are rewarded with credits and user can spend on the mobile game they actually want to play. Tapjoy has a huge market among IMVU users, who need credits to buy piece of clothing and accessories for their avi.
The other apps do mobile app marketing, using data collection that allow shady corps to target more gullable and naive people to scam. Plus they do also monetization surveys to earn money and at the same time forcefully grow the engagement of this shady corps.



Obviously, there is no user support mail listed in their Google Play page, but at least this has a contact mail listed on their website: [email protected]
As always, stay safe and please tell me if you know more about everything above or know the person who create this build first.
Help people to stay safe.
Thank you.
<<< previous Coloring app uses design of The Sims 4 builds without the consent of the creators and other mobile developers steal TS4 speed build contents and claim it's the actual gameplay of their mobile game.
#vavuskapakage#the sims 4 build#sims 4 build#ts4 build#mobile gaming#mobile games#fake ads#fake advertising#fake game#caught stealing#stealing content#stop stealing#scam alert#fake games#google play#fraud alert#internet fraud#fraud allegations#internet privacy#data protection#data breach#data analytics#datascience#big data#fraud#mobile ads#google ads#facebook ads#ads#false advertising
4 notes
·
View notes
Text

Mobile spy software is a tool designed to monitor and track smartphone activities, often used by parents, employers, or individuals concerned with security or productivity.
0 notes
Text

Monitor phones effortlessly with ONEMONITAR! Easily set up, run discreetly in hidden mode, and access call recordings, locations, and activity logs through a secure dashboard. Perfect for smart and effective monitoring.
0 notes
Text
Opposition MPs expressed dismay after the Prosecution Office of the Greek Supreme Court on Tuesday concluded that no state ministry or agency had used illegal Predator spy software, or any other surveillance software.
“There was absolutely no involvement with the spy software Predator or any other similar software by a state agency, namely the National Intelligence Service (EYP), the Anti-Terrorist unit (D.A.E.E.B.) and more generally the Ministry of Citizens Protection or any government official,” Supreme Court Prosecutor Georgia Adeilini said.
Provisions lifting the privacy of communications issued by Vasiliki Vlachou, Prosecutor of the EYP for 2020-2024, followed the procedure provided by Greek law, the court said.
However, the court said that there were sufficient grounds “for the initiation of criminal prosecution … against certain legal representatives and beneficial owners of companies for criminal acts, such as the violation of the privacy of telephone communication.” These companies, it said, had been involved in violating the privacy of telephone communications of politicians, journalists and others in other countries as well, combined with similar “targets” in Greece.
Opposition leaders reacted with disappointment.
“Today … my confidence in the Greek justice system has been seriously shaken. Unfortunately, this now coincides with the widespread feeling of the Greek people that justice is not the last refuge of the wronged,” wrote the leader of the left-wing SYRIZA party, Stefanos Kasselakis, on social media.
The preliminary examination into the wiretapping case lasted two years and more than 40 witnesses were examined.
They included politicians, journalists, representatives of mobile phone companies, Commanders, Deputy Commanders and other members of the National Intelligence Service, EYP, members of the Greek Authority for Communication Security and Privacy (ADAE) and the National Transparency Authority, NTA, senior police officers, the Intelligence Management and Analysis Directorate, the Finance Directorate as well as the Electronic Crime Prosecution Directorate.
Grigoris Dimitriadis, nephew and former secretary of Prime Minister Kyriakos Mitsotakis, resigned in August 2022 over revelations of alleged involvement with Intellexa, a company that sells Predator in Greece. He denied wrongdoing and sued the media involved in the reports – Reporters United, Efimerida ton Syntakton, as well as the journalist Thanasis Koukakis, whose phone had been infected with Predator. His resignation was followed by that of the then head of the EYP, Panagiotis Kontoleon.
The wiretapping scandal, known as Predator Gate, or the Greek Watergate, and which has occupied the Greek media since 2022, concerns the use of Predator to monitor or attempt to monitor journalists, politicians and other public figures.
The New York Times suggested that the simultaneous tapping of a victim’s phone by the EYP and its Predator infection “indicate that the spy service, and whoever implanted the spyware, were working hand in hand”.
3 notes
·
View notes
Text
Why is Brazil’s Spy Agency ABIN Under Investigation?

Brazil’s main intelligence agency is accused of illegally spying on politicians and high-ranking judges who criticized former president Jair Bolsonaro, according to documents unsealed by the Supreme Court in January 2024. Three Supreme Court justices are among those allegedly targeted by Agência Brasileira de Inteligência (ABIN).
According to a police statement, their investigations under Operation Last Mile indicate a "criminal group" created "a parallel structure within the Brazilian Intelligence Agency (ABIN) and used its tools and services for illicit acts, producing information for political and media purposes, for personal gain and to interfere in federal police investigations".
Police allege that the rogue intelligence operatives illegally monitored public authorities and others using mobile device geolocation tools without judicial authorization. The name ‘Operation Last Mile’ is reportedly a reference to FirstMile software, developed by Israel’s Cognyte to track cell phones and geolocation data.
Police have so far searched the home and offices of Congressman Alexandre Ramagem, a former spymaster under ex-president Jair Bolsonaro who served from 2019 to 2022. ABIN’s former chief denied any wrongdoing and called the allegations politically motivated.
Continue reading.
7 notes
·
View notes
Text
This day in history

#20yrsago Forever War with better sex, Starship Troopers without the lectures: Old Man’s War https://memex.craphound.com/2004/12/12/forever-war-with-better-sex-starship-troopers-without-the-lectures-old-mans-war/
#20yrsago Cable companies will expire your Six Feet Under recordings after 2-4 weeks https://memex.craphound.com/2004/12/12/cable-companies-will-expire-your-six-feet-under-recordings-after-2-4-weeks/
#15yrsago FDIC sends a big F-U: completely blacked out documents in response to WaMu takeover freedom of information requests https://web.archive.org/web/20100114010713if_/https://www.bizjournals.com/seattle/blog/2009/12/the_fight_for_wamu_documents.html
#10yrsago IBM’s banking security software demands the right to spy on you https://yro.slashdot.org/story/14/12/11/2233234/bank-security-software-eula-allows-spying-on-users
#10yrsago US Christian terrorism: the other white meat https://web.archive.org/web/20141205144046/https://thinkprogress.org/justice/2014/12/04/3599271/austin-shooter-christian-extremism/
#10yrsago Senate IP address vandalizes Wikipedia to scrub “torture” from CIA torture report https://mashable.com/archive/senate-wikipedia-torture-report
#5yrsago Teespring removes Techdirt’s “Copying is Not Theft” tees for copyright infringement, and won’t discuss the matter any further https://www.techdirt.com/2019/12/12/teespring-takes-down-our-copying-is-not-theft-gear-refuses-to-say-why/
#5yrsago The three biggest Chinese business scams that target foreign firms https://web.archive.org/web/20200107202820/https://www.chinalawblog.com/2019/12/china-scams-our-annual-holiday-edition.html">https://web.archive.org/web/20200107202820/https://www.chinalawblog.com/2019/12/china-scams-our-annual-holiday-edition.html
#5yrsago A Wechat-based “mobile court” presided over by a chatbot has handled 3m legal procedures since March https://web.archive.org/web/20191207192051/https://www.japantimes.co.jp/news/2019/12/07/asia-pacific/crime-legal-asia-pacific/ai-judges-verdicts-via-chat-app-brave-new-world-chinas-digital-courts/#.Xev7n2bP1qY
#5yrsago Facebook promised to provide academics data to study disinformation, but their foot-dragging has endangered the whole project https://socialscience.one/blog/public-statement-european-advisory-committee-social-science-one
#5yrsago DJ Riko is back with the 18th annual Merry Mixmas mashup album! http://djriko.com/mixmases.htm
#5yrsago Family puts Ring camera in children’s room, discovers that hacker is watching their kids 24/7, taunting them through the speaker https://www.vice.com/en/article/how-hackers-are-breaking-into-ring-cameras/
#5yrsago 2019 was the year of voice assistant privacy dumpster fires https://www.bloomberg.com/news/features/2019-12-11/silicon-valley-got-millions-to-let-siri-and-alexa-listen-in
#1yrago An Epic antitrust loss for Google https://pluralistic.net/2023/12/12/im-feeling-lucky/#hugger-mugger
8 notes
·
View notes
Text

Russia reactivates Beriev Be-12 seaplanes from the Cold War era to detect Ukrainian naval drones
Fernando Valduga By Fernando Valduga 03/10/2023 - 23:10in Military, War Zones
In a twist that could come directly from a spy novel, Russia is deepening its Cold War manual to combat the cutting-edge technology of Ukraine's maritime drones.
Believe it or not, the Russian Navy is using its 1960s amphibious Beriev Be-12 plane to face the modern dilemma of Ukrainian naval drones. These drones have become a stone in the shoe of the Russian Black Sea Fleet, and Moscow bets that its updated but aged Beriev Be-12 may rise to the challenge.
According to Business Insider India, in the last two months, Ukraine has intensified its operations against the Russian Black Sea Fleet, despite not having a traditional navy. The Ukrainian military has unleashed cruise missile attacks against vital shipyards and fleet headquarters, while mobilizing unmanned surface ships, or naval drones, against Russian naval means. These economic drones, loaded with explosives, have emerged as a significant challenge for Russia.

Ukraine is ambitiously developing what it describes as "the world's first naval fleet of drones". These maritime drones have already inflicted damage on Russian ships, including the Olenegorsky Gornyak and the merchant oil tanker Sig. Although the Russian Ministry of Defense has contested these allegations, it continues to seek effective countermeasures against these maritime threats.
The Beriev Be-12 Chayka ("Seagull", NATO report name: Mail), which made its maiden flight in 1960, is not an ordinary aircraft. Designed with a V-shaped arched wing for takeoffs in the water and a lower fuselage similar to a ship for landings in the water, even in stormy conditions, the Be-12 is a relic with remarkable capabilities. It is powered by turboprop engines from the Soviet era, adding a layer of nostalgia to its modernized capabilities. The aircraft can fly at speeds above 500 km/h and has a fuel reserve that allows missions with an extension of more than 4,000 km or a duration of several hours. The aircraft is armed with a series of mines, torpedoes and bombs.

In 2018, the Russian Navy decided to give new life to these old aircraft. The modernization equipped the Be-12 with a completely new aiming system and modern weaponry. Despite being the oldest aircraft still in operation in the Russian armed forces, the updated Be-12 are expected to radically improve Russia's reconnaissance capabilities against enemy submarines through hydroacoustic, radar and magnetic detection systems. The aircraft will also be armed with modern anti-submarine torpedoes and depth bombs.
The Beriev Be-12 are currently stationed at Kacha Air Base in Crimea. The Russian high command seems to believe that these modernized aircraft could be a game changer in the fight against the Ukrainian naval threat in the Black Sea.
Tags: Military AviationBerievRussiaWar Zones - Russia/Ukraine
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, he has participated in several events and air operations, such as Cruzex, AirVenture, Daytona Airshow and FIDAE. He has work published in specialized aviation magazines in Brazil and abroad. Uses Canon equipment during his photographic work throughout the world of aviation.
Related news
MILITARY
The F-35 fighter, the most expensive weapons program in the world, has just become more expensive
04/10/2023 - 08:11
MILITARY
Meet the cockpit of the Saab F-39 Gripen, the most advanced fighter in Brazil
03/10/2023 - 19:14
MILITARY
RAF typhoons are sent to Poland for joint exercises before the Warsaw Security Forum
03/10/2023 - 16:00
COMMERCIAL
Leasing company reaches agreement with Russian airline Aeroflot
03/10/2023 - 15:00
A Swedish Gripen fighter taking off. GKN Aerospace was hired to upgrade the Gripen's RM12 engine, a modified General Electric F404, with improved software designed to improve performance and reduce life cycle costs. (Photo: GKN)
MILITARY
GKN Aerospace receives request to upgrade the RM12 engine for the JAS39 Gripen
03/10/2023 - 14:00
MILITARY
Turkey presents ANKA drone in meeting with Argentine military
03/10/2023 - 12:00
Client PortalClient PortalClient PortalClient PortalClient PortalClient PortalClient PortalClient PortalhomeMain PageEditorialsINFORMATIONeventsCooperateSpecialitiesadvertiseabout
Cavok Brazil - Digital Tchê Web Creation
Commercial
Executive
Helicopters
HISTORY
Military
Brazilian Air Force
Space
Specialities
Cavok Brazil - Digital Tchê Web Creation
13 notes
·
View notes