#should i tag this at mitm???
Explore tagged Tumblr posts
Text
so. there are two frankie muniz hairstyles i would like to discuss.
my man has had some... questionable choices in the past. but i have one that i cant decide if it ate or not, and one that i KNOW ate

so. this one. i cant tell if he ate this up. i really cannot make up my mind as to whether or not i love or hate it.

THIS ONE. THIS ONE FUCKS SO HARD. AND IT WAS ONLY TEMPORARY. FOR LIKE A COUPLE MONTHS. AND IT BREAKS MY HEART THAT FRANKIE MUNIZ DOESN'T REALIZE HE EATS UP LONG HAIR.
#if you disagree with me on the last one your tastes are atrocious#i know its 6:30am. im losing my fucking mind.#oh my god. the fact. that frankie doesnt grow his hair out longer. pisses me the fuck off.#especially now that he's older with a beard. do you realize how fucking awesome he would look if he grew it back out to that second length#im not crazy i just think about this hairstyle at least once a day#frankie muniz#should i tag this at mitm???#i will.#mitm#malcolm in the middle#ramble#rambles
12 notes
·
View notes
Text

for @trans-francis
#francis wilkerson#mitm#trans francis#moodboards#headcanon#i guess i should tag it as hc shshdhd idk
83 notes
·
View notes
Text
Speeddemon storyline
Again, not much was actually written... the format of this one reads way more like a discussion at times, because that was how a lot of this was developed and... I don’t really wanna fix any more of this stuff.
Again, DO NOT TAG AS GIO/MIS!!
Pompeii:
Giorno snatches the keys right out of Fugo’s hand and jumps in the driver seat, "hurry up get in let’s go!!" So Fugo & Abbacchio are like 'ok... at least he treats things with urgency'
The trip is horrific, and Giorno almost drives right through the park. The 「MITM」 fight happens as it did in canon, with maybe a little dry heaving stumbling around from Fugo & Abbacchio.
Abbacchio realizes he can’t drive on the way back, he’s lost too much blood and a whole hand, And Fugo...
Fugo tries, he really does. He tries so hard to get Giorno to let him drive. But... well. He’s scary. He’s a literal demon in the car.
Abbacchio: "HE ALMOST KILLED US!"
Bruno: “Giorno? That's ridiculous.”
Fugo’s almost crying because he never thought he could meet a more dangerous driver than him, and that was terrifying, but he doesn’t say anything because he’s still shaking from everything that happened in... 2 hours?
They almost crashed into a few cars on the way, almost drove right into the ruins, Giorno infected himself on purpose, he almost crashed into a few more cars on the way back, etc.
To Florence (the train):
Van scene? They all get thrown onto each other like sardines.
BIG TIME THERES NOT EVEN A SECOND TO REALIZE IF SOMEONES TOUCHING TRISH, EVERYONES ON THE GROUND IN SECONDS
ABBACCHIOS SCREAMING BECAUSE GODAMNIT HIS HAND
BRUNO HAS BIG CONCERNS BECAUSE WHERE THE HELL WAS THIS SIDE OF THE BOY!?
Narancia’s probably having fun
GIORNO ACTUALLY PASSES WHERE THEY HAD TO GO AND NOBODY REALIZES IT FOR LIKE A WHOLE 3 MILES, BUT SUDDENLY THE VAN WHIPS THE FUCK AROUND AND ALMOST TIPS OVER, ALMOST CRASHING INTO SEVERAL OTHER CARS AND ZOOMS BACK
AND THERES NO SUCH THING AS SLOWING DOWN TO GIORNO, THOSE WORDS DONT EXIST
HE ONLY EVER SLAMS ON THE BRAKES
Bruno believes Fugo and Abbacchio now.
After Florence:
"Do you feel that, Coco Jumbo," Giorno laughs. He's speaking to the turtle, seemingly forgotten that everyone's inside, "this speed, the rush! Nothing can catch you! Nobody can reach me!" And that’s... odd. That’s not the kind of thing they’d expect to hear.
Not from him; someone who didn’t seem to care who was in his way, (probably) willing to run over anyone.
And when someone (let’s say Mista) gets out of the turtle to say something, Giorno panics. He’s freaking out, because nobody was supposed to be able to catch up, he was safe as long as he was moving, moving, moving, moving, but someone was here somebody caught up and-
"Dude, hey, hey, relax! I was just going to say, we should stop for some food! There's no enemy here!"
And he realizes he summoned [Gold Experience], and its strength was crushing the wheel in his hands, and the gas pedal creaked dangerously under his heel from the pressure he was putting on it. He loosens his grip and lifts his foot, breaths heavy with the echoes of his fear, "r-right, its... safe..."
And Mista’s staring, he knows that’s not right. But Giorno wasn’t ready, clearly - and Mista didn’t want to lose an arm because he pried too soon. But he didn't forget it, and found himself watching Giorno a lot more. Watching for signs of whatever the hell set him off, trying to see if there was something they could do. This was the new guy, the youngest of them as well as probably the strongest & most confident, but he seemed like he was almost in worse shape than they were when they joined
Giorno doesn’t notice, but the others do. It’s in the way Mista sits in the passenger seat with almost no hesitation, and how he stares so closely at Giorno when he’s driving. Well, they don’t really notice that, but Mista brings it up.
"Do you notice that Giorno looks... free?" Nobody knows what the hell that’s supposed to mean, except Bruno, who agrees but doesn’t expand on it.
"Do you think Giorno...," he starts at some other time, but stops himself.
Abbacchio fills in, "is a lunatic? Yes."
"No - I mean, he’s a little crazy, but I mean- do you think he-," Mista hesitates, and finishes quietly, "he’s running from something?"
That strikes a nerve.
Because they’ve all been running from something. The past, the future, themselves, or others – they’ve all been running.
Venezia:
Thanks to Ghiaccio and that chase on Liberty Bridge, Mista figures out exactly what made Giorno panic so badly
Whereas Mista just startled him before in that truck, Giorno knew there was nobody around on that bridge.
When Ghiaccio shows up, Giorno knows it’s because he caught up
He was only caught when he stopped before, he was always safe when he moved. For the first time in his life, someone caught up when he was running;
Because he’s not fast enough, and if one person can catch up then there are hundreds of others, and he can never be safe again.
Mista figures this out because Giorno’s saying it out loud; "I’m not fast enough", "they’ll catch me", etc.
And he realizes Giorno is running from everything.
He was probably even trying to run from them, emotionally.
Now I’m not sure what kind of speech Mista could/would give, but I imagine there’d be something there about... Not how running away doesn’t solve anything, that’s not what he needs. Something like...
"It’s easier to run away when the thing chasing you can only walk."
Or of course, "if you get rid of what’s chasing you, you don’t need to run."
So Giorno realizes there’s one thing he’s always done when he’s running that he hasn’t done now
Stop.
So he slams on the brake and summons [Gold Experience] to stop the car from up front. Ghiaccio was not prepared for this, and he slams right into the car, skidding across the icy top and sliding ahead on the bridge, probably for a good mile.
And now it’s time to run again.
[Gold Experience] hits the car from behind to get it moving while Giorno hits the gas, and Ghiaccio is definitely hit.
Mista’s stomach is in absolute knots, he feels it in his throat, but he cheers anyways because hell yea, and that light of freedom is back and Giorno’s laughing, when seconds ago he was approaching a near total breakdown
Of course Ghiaccio’s not done, but they bought time, time to get ahead and thaw the car, time to get several miles closer to the goal and a plan
Which is when Giorno drives the car into the canal.
(Not before making a pigeon and sending it ahead to steal the disc, as well as just filling the car with leafy plants)
So they kind of just... huddle down and wait. No way Ghiaccio would see the bubbles & ripples and think it wasn’t them, and Giorno was sure he’d freeze the water to be sure they’d drown. With the plants they’d have oxygen for a few hours, and the pigeon (having been made from one of Trish's hairpins, stolen of course) would return to the turtle with the disk in no time (he hoped), so they just had to wait.
Of course, this wouldn’t be Golden Wind if something didn’t go wrong. So there’s a splinter in the glass the two are worried about, and they watch with growing fear as it steadily stretches across the windshield, water streaming in, until the break is too big for the glass to stand.
This is where they don’t have time to think of alternatives, and they have to swim out asap. There’s no telling where Ghiaccio’s waiting, or really where they even are, so they just have to hope for the best and get to the surface
And the surface is, of course, frozen over. So they have to estimate where they are by light - or rather, by shadows, because their best chance of going unseen is to break out under the bridge.
Which... Ghiaccio’s smart, he’s figured that out too. But he doesn’t know their stands, so he’s waiting right above, waiting to hear the telltale smash.
But they don’t actually break through; it’d take too much energy, be too loud, and the rest of the ice would be too unstable. Giorno, Mista, and [Gold Experience] are just kind of... pushing against it
Eventually it starts splintering and cracks open, and they can get their heads out at least to breathe - at the same time Ghiaccio’s starting to rant about secrets, or girls, or... something, they aren’t really paying attention
They’re both getting ridiculously numb, but the ice seems like it won’t hold their weight, so they can’t get out of the water too quickly - they actually have to push their way through, cringing and holding their breath at every sound.
Giorno sees the pigeon on the rather distant statue and knows the disc must be inside - disappointed that it isn’t handled, but glad the pigeon blended in well enough that the statue was never investigated. But the trash was, it seemed, and whatever image Mista thought of made him grin.
It was enough of a distraction from the cold that they were able to drag themselves onto the bank, but the next problem was an even bigger obstacle. How could they get to Ghiaccio and take him out, or get to the disc and grab it, before being seen...?
Giorno considers the ice itself. He couldn’t make anything that'd actually help in this cold - the water they’d just escaped was already freezing over - but a distraction... And nothing was better to get an enemy's attention than to make them think they were making a break for it.
So Giorno makes 2 winter bass - big enough to make a lot of noise, but not so big that they’d be immediately caught - and drops them in the most fragile area of reforming ice, sending them on their way. Their backs bump the solid ice a few times as they go around, and Ghiaccio makes a noise like a squawk and jumps up, following what he believes are the two targets
They both get up. Giorno signals for Mista to stay down, but Mista grabs his arm, "hey, relax a little, let me. I need a success somewhere; you're hogging all the glory." He smiled, to show he’s kidding but intends to do this, and though he doesn’t get it, Giorno smiles back slightly.
Mista’s weird boots don’t have the slight heels Giorno's shoes do, so it really was for the best as he trudges his way to the statue. After a second, he grabs his gun and starts trying to chip the stone away, grabbing the pieces as they fall, and watching where Ghiaccio ran off.
Eventually, when he sees the corner of the case, he fumbles, nearly cursing aloud when the pieces of stone hit the ground with echoing clacks
He ends up panicking, yanking the disk out, and scrambled back to the bridge
And then they both realize they have no idea what to do next
Giorno gives the disk to Trish's hairclip pigeon and sends it off, but they still have a big threat to handle. Neither of them can tell how much of their shaking is from the cold, and how much is the anxiety
Giorno ends up grabbing Mista’s hand, hoping it would ground him, and Mista realizes just how scared Giorno actually is. How scared he probably always is, when they're not moving at insane speeds.
And he can't let that fear be any more justified.
"We'll get out of this," he whispers, "we'll get this guy, get back to our friends, and we'll be moving again, little buddy."
#speeddemon giorno#giorno giovanna#giorno#jojo giorno#jjba giorno#lets see if putting all the writing in just one long post works better#jojo#jojo's bizarre adventure#jojo au#jjba#jjba au#bruno#jjba bruno#jojo bruno#bruno bucciarati#leone abbacchio#jojo abbacchio#jjba abbacchio#jojo mista#jjba mista#guido mista#part 5#part 5 golden wind#part 5 vento aureo#jojo man in the mirror#jjba man in the mirror#jojo white album#jjba white album#jojo ghiaccio#jjba ghiaccio
3 notes
·
View notes
Text
Week 4
++ if something is “broken” a property can be violated faster than brute force ++
Bits of Security and brute force
Bits of work represents how much security a particular system has / how much protection it has against a brute force attack / how hard it is to brute force. An attacker would have to perform operations to break it
1 bit = 2 options
2^10 ~ 1,000 2^20 ~ 1 million 2^30 ~ 1 billion
Eg/ if we have a 10 digit password – a-z, A-Z, 0-9 only then
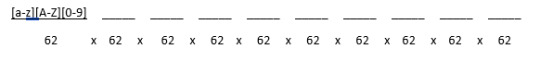
62 options for each digit = 62^10 options
2^6 ~ 64, so we have (2^6)^10 = 2^60 -> 60 bits of work to brute force this password
But the average time it would take to brute force, is half the total time i.e. so 59 bits of work
Brute forcing is really slow, definitely not an efficient way to crack something. With 256 bits of work is probably enough to not be cracked. We can be smarter about how we decrypt things, especially when we know they’re in English. See index of coincidence post for more on English letter frequency distribution.
Since most English-speaking people use English words in their passwords, and communicate in English, we can greatly reduce the amount of work it takes to crack an encrypted message/password thanks to the lack of entropy within the English language.
There are 2^25 possible combinations of English letters in a 5 letter word
There are only 2^13 valid words
Each letter added to a password adds ~ 2.5 bits of work
Patterns and entropy + English language + Claude Shannon
Redundancy in English language -> rules like i before e except after c, q must be followed by u
Grammar, parts of speech, we can’t just make up words and make sense. All these things contribute to English language being redundant. Thanks to redundancy, we can better understand English when everything is not clear. For example
msot poelpe can raed a sneatnce if the frsit and lsat lterets are the smae,
despite other letters being jumbled. Similarly when there is a lot of background noise we can often still discern what is being said, despite not hearing the annunciation of every letter.
An N-gram is used to calculate the entropy of English. We can statistically calculate the randomness of the next letter when we know the previous N-1 letters. As N increases, the entropy approaches H (i.e. we get closer to knowing the true entropy value of English ? )
Calculating the statistics of Fn has a difficulty of O(26^N)
F0 = 4.7 -> this is the maximum entropy value for English letters, where each letter has equal probability.
Fword = 2.62 -> the average word contains 4.5 letters
Since we can read sentences without spaces almost always, spaces become redundant. We exclude this to get a more accurate representation of entropy.
Maximum redundancy is when all letters have the same likelihood
Man in the Middle Attack
2 people think they are communicating privately with each other, when in fact there is an attacker in the middle relaying ( and maybe altering ) messages between the two. The attacker is able to intercept all messages between the two people as well as interject new ones. Attackers may also target information inside devices
These attacks can be done when the two are communicating via unencrypted Wi-Fi and the attacker is within range of the same access point. This is known as Wi-Fi Eavesdropping. The attacker may set up a Wi-Fi connection that appears legitimate (evil twin?) and wait for someone to connect, instantly gaining access to their device. They may also create a fake node to steal the data of anyone who connects
Session hijacking is another form of a MITM attack. Attackers will access the session created between your device and a website when you enter where they can steal your cookies – containing information such as passwords, pre-fill forms (i.e. bank details, addresses, phone numbers, company details – basically all your personal info) and access other accounts with these details.
Email interception -> monitoring communication between parties, gathering important data including transaction details, bank account information, personal details before impersonating an organisation and targeting individuals for example changing the receiving bank details to their own.
Man in the middle attacks highlight the importance of the Integrity and Authentication principles. It is essential that information is tamper-evident so that the receiving party can verify the authenticity of a message / communications.
Replay Attack
Kind of like a MITM attack, an attacker may intercept communications and then delays or resends it fraudulently deceiving the receiver.
Hash Functions
A regular hash function is any function used to convert data of any size down to data of fixed size. The same text will always result in the same hash – i.e. they are deterministic. A hash is quick to compute and very hard to reverse.
A cryptographic hash function is used to secure messages in transmission. It is unlikely that any two messages will have the same hash. In order for a cryptographic hash function to be secure it must fulfil 6 properties:
1. deterministic
2. quick computation
3. pre-image resistant -> infeasible to determine the message before hashing
4. avalanche effect -> small changes to message = big changes to hash
5. collision resistant -> unique inputs should produce unique hashes
6. puzzle friendly -> H(k|x) = Y – it must be infeasible to find x such that concatenating a random point with x produces the hash equal to Y
Collisions
A hash collision is when two distinct sets of data generate the same hash value. They are unavoidable when a very large set of data is mapped to a short string. This is unfortunate as collisions can be exploited by programs that compare hash values, for example password authentication.
Collision Resistance -> Find any 2 messages, m1 and m2 such that H(m1) = H(m2)
Second Pre-Image Attack -> given, H(m1) and m1, find m2 such that H(m1) = H(m2) (m1 != m2)
Pre-Image Attack -> given only H(m1) find m2 such that H(m1) = H(m2)
Message Authentication Codes (MACs)
A MAC is a way of authenticating and providing integrity to a message via a crypto hash – i.e. if you want to ensure the recipient knows that it has come from you, unaltered. It consists of 3 efficient algorithms
- G: key generation algorithm – a key is selected from the key space at random
Both the sender and receiver must share this symmetric key, K
- S: a signing algorithm – returns a tag given the key and the message
- V: verifying algorithm – returns accepted after verifying the authenticity of the message
For an MAC to be secure it should be computationally infeasible to compute a tag of the message without knowledge of the key

Take a message – combine with key – hash the result – send message w MAC – reperform MAC to verify w shared secret.
These are all bad:
MAC = hash ( key | message ) - vulnerable to a length extension attack
MAC = hash ( message | key ) – can still forge messages with collision
MAC = hash ( key | message | key )
We want HMAC:
HMAC = hash ( key | hash ( key | msg ) )
MACs do not provide non-repudiation – i.e. if there is a dispute over the origins of a message it cannot prove the message was sent by the sender.
0 notes
Text
Web security on MICROTRANSACTION.ZONE, pt. I
Hi! Simon here. I’m one of the co-founders of MICROTRANSACTION.ZONE. I’m also the one who insisted on branding it “MICROTRANSACTION.ZONE” in all caps, so if you think that’s annoying, you now have someone to point at and go “what a tosspot”.
One of the things I’ve wanted to do with this project for as long as it has existed, is using it as a springboard to talk a bit about various web security technologies and how they’re implemented on the site. This isn’t going to be another site update post—if you don’t think internet security is very interesting, you have my blessing to close this tab and look at some cat videos instead.
This blog post will be the first of several, divided up into sections detailing various kinds of vulnerabilities, and what specifically I’ve done to prevent those vulnerabilities from impacting our site. It’ll probably be easiest to understand if you have some grasp of basic web technologies, but I’ll try not to get too bogged down in irrelevant technical details. All that said, let’s just dive right in.
Man-in-the-middle (MITM)
If you’re on an unencrypted connection (e.g. if you’re visiting a website over HTTP instead of HTTPS), then the data that’s being sent back and forth between you and that website is fully visible to anyone on the same local network as you, to your ISP, and to any number of other machines on the way between you and the server that hosts the website. Not only can they see it, but there are a number of nefarious tactics available that will let them alter the content of the pages you visit - letting a sneaky attacker who’s on the same wi-fi network as you insert a cryptocurrency miner into any unencrypted website you visit, or letting your ISP insert giant notices about copyright infringement on any site you visit that isn’t protected by HTTPS.
HTTPS prevents this by encrypting all traffic travelling between you and the machine where the website is hosted in such a way that it’s useless garbage to anyone except you and them - all the people i mentioned before can still intercept it if they want, but it’s completely worthless to them. However, it’s not enough for a site to simply support HTTPS - it’s equally important to make sure that it actually gets used. By default, any webserver that serves content over HTTPS will still quite happily let visitors browse the site over HTTP unless they manually type “https://...” into their address bar - obviously, we’d rather that didn’t happen. The solution to this is two-pronged - the first part is to automatically redirect everyone to HTTPS if they try to access the site via unencrypted HTTP. The second part is a technology called “HTTP Strict Transport Security”, or “HSTS”.
Even when we automatically redirect a user to HTTPS, there’s still an unencrypted HTTP connection happening while the redirect is taking place. HSTS fixes that. It’s an HTTP header that gets sent to your browser on every page you load over HTTPS, and it basically tells your browser “stay on HTTPS whenever you visit this site for the next little while”. This means that, once you’ve visited our site over HTTPS even once, your browser will automatically redirect itself to HTTPS any time you visit our site for the next month, before it ever even tries to load the page.
We’re going to get the site added to the HSTS preload list in the near future - once that’s done, this automatic redirection will happen even the very first time you visit our site, on every major browser.
Cross Site Scripting (XSS)
XSS (see here for a basic primer) is one of the most dangerous website vulnerabilities out there, in terms of the damage it can do to a user’s own device - a site with an unchecked XSS vulnerability lets an attacker run any JavaScript they want on a visitor’s machine, letting them do anything from using your computer to mine cryptocurrencies, stealing your website cookies, displaying malicious advertisements, replacing the entire page with whatever content an attacker desires, or even (gasp) letting them lie about what tags a game has on our site.
Unfortunately, there is no magic cure-all for XSS. You have to put up a layered defense; even if one of your defensives measures is defeated, you still have several others rendering the attack useless. A short list of some of the things we do on MICROTRANSACTION.ZONE to prevent XSS attacks:
ASP.NET, which our site is built on, has built-in defences against XSS in form input. Unless you manually disable it (we haven’t), it will error out if it detects something that even smells like HTML tags.
We never reflect the user’s input back at them directly. For example, on our search page, we do not write “Your search for [query] returned these results”. That would involve reflecting user input, which is a bad idea wherever you can avoid it.
This is also one of many reason we do not have a comments-section for each game’s page, as well as one of the reasons we manually vet each submission.
All cookies on the site are marked as “HTTP Only”, meaning that they are not accessible to JavaScript (please do not be alarmed over the word “cookies” - the only cookies we give our normal visitors are “RequestVerificationToken” cookies which are used to help prevent CSRF attacks - more on that specific vulnerability later...)
We have a very restrictive Content Security Policy (CSP). Like HSTS, this is another header - one with the purpose of instructing your browser which places it is allowed to load which types of content from. One of the most important features of our CSP is that it blocks inline JavaScript completely - only JavaScript loaded as external files from a specifically whitelisted range of domains may be run. This means that, even if an attacker should find an XSS vulnerability in our site, they would be powerless to exploit it unless they also managed to upload actual JavaScript files to our web host, or to Google or Twitter. In which case, we’d have bigger problems. CSP is supported by basically every major browser, so as long as you’re not running Internet Explorer or Opera Mini, you’re protected by this additional layer of defense.
0 notes
Text
Just How Easy Is Cellphone Hacking?
Simply How 9spyapps Hacking?
Should you share your Linux field with somebody and you are sick of regularly logging in and out, you may be relieved to know that this is not really needed. File and Printer Sharing should only be enabled in the event you plan to share a few of your folders on the community or if you wish to share your domestically connected printer over the community. As soon as the password is handed to the hacker, they're in your account and youre in for a world of hurt. By default Home windows Server 2003 has lowered the need for service accounts in many situations, however they're nonetheless essential for some third-celebration functions. Previously, Walls mentioned, hackers may entry people’s voice mail by calling their cellphone service suppliers to ask to set a brand new voice mail password. You may even get all the deleted messages of the target cell phone. Drive the person to cash with 5 cards, even in the event that they let the time run out. copy9.com will execute. So with mxspy.com to run the BAT recordsdata of this guide’s automated configuration, you need to decide on the tool’s UnLock from the fitting click menu, which offers you 30mins of unlocked time. Any individual who understands the Whatsapp could have Whatsapp set up without any uncertainty into it.
But this implies they have fixed access vs. The fixed elevating of stamp costs causes a vicious circle. Implementing this command validates key identifiers 4, 7, 14 & eighty two, while discounting all other keys. Finally, create a "security key." A safety key gives a better measure of safety by additional encrypting website data in cookies, those temporary textual content information stuffed with login and browsing data. Banks or monetary institutions by no means send varieties embedded in emails which ask you to fill up your private knowledge within the email body itself. It is a deficiency of this sort of hormones that Motives a single’s total physique and intellect in direction of data accelerated growing older. It's because the remainder of your typing will be stored on the onerous drive as a file, which you haven't any access to. As well as, the smoke detector purchase features a remote controller to operate the system and a movement detection function that when activated will trigger the spy digicam to start recording when it senses motion or movement. Nevertheless this intelligent piece of software program goes further recording memos, image and video information, calendar occasions, tasks and browser histories.
This remote-managed robotic enables you to report video with as much secrecy as attainable. The characters in our novels haven't any free will; the characters in our films don't have any free will; the characters in our video video games don't have any free will. Or they will be deleted also on the spy app and thus, no one can learn them? You should utilize smileys, emoticons and MSN style symbols. Chances are you'll set up the software program on as many telephones as you want, but can solely use on one phone at a time. Remotely install black berry cellphone tracking Cheating partner spy cell. Enter your telephone number. Jonathan Wong, a search advert evangelist at Microsoft, obtained a curious message on chat app Line from a Hack Line App pretending to be his friend. The separate chat window remembers its state and site. Get them concerned, allow them to ask questions and reply them as actually and as clearly as attainable.
Under is the topology or infrastructure how MITM work, and the way it can be happen to do hacking a Facebook account. I can imagine deploying the PowerShell-based PSake build software and a PSake construct script containing operations turned construct targets. You can now talk along with your office surroundings proper throughout the hallway or across the globe in an atmosphere that's fully safe, stable and reliable. Right click on the program’s systray icon and choose Configure. One alternative of this is utilizing very specialised industry lingo to come up with the phrase. And you’ll see that this Tag is associated with just one Article. Let's take an thrilling tour across the fortress of Agra to discover its magnificence and history. Altered the timing for choosing random international locations in order that it does not take as lengthy for big maps. Home windows login, preventing the person from having to enter one other password! Calendars depict work and pay time formatted and summarized as hours and minutes for each day, week, month, and year. I figure that if solely the victims or any by-stander had this gadget, then crime charges would go down. It needs to be handled as malicious and removed!
0 notes
Text
TROOPERS 2017 Day #1 Wrap-Up
I’m in Heidelberg (Germany) for the 10th edition of the TROOPERS conference. The regular talks are scheduled on Wednesday and Thursday. The two first days are reserved for some trainings and a pre-conference event called “NGI” for “Next Generation Internet” focusing on two hot topics: IPv6 and IoT. As said on the website: “NGI aims to provide discussion on how to secure these core technologies by bringing together practitioners from this space and some of the smartest researchers of the respective fields”. I initially planned to attend talks from both worlds but I stayed in the “IoT” tracks because many talks were interesting.
The day started with a keynote by Steve Lord: ”Of Unicorns and replicants”. Steve flagged his keynote as a “positive” talk (usually, we tend to present negative stuff). It started with some facts like “The S in IoT stands for Security” and a recap of the IoT history. This is clearly not a new idea. The first connected device was a Coca-Cola machine that was available via finger in… 1982! Who’s remember this old-fashioned protocol? In 1985, came the first definition of “IoT”: It is the integration of people, processes and technology with connectable devices and sensors to enable remote monitoring status. In 2000, LG presented its very first connected fridge. 2009 was a key year with the explosion of crowdfunding campaigns. Indeed, many projects were born due to the financial participations of many people. It was a nice way to bring ideas to life. In 2015, Vizio smart TV’s started to watch at you. Of course, Steve talked also about the story of St-Jude Medical and their bad pacemakers story. Common IoT problems are: botnets, endpoints, the overreach (probably the biggest problem) and the availability (You remember the outage that affected Amazon a few days ago?). The second part of the keynote was indeed positive and Steve reviewed the differences between 2015 – 2017. In the past, cloud solutions were not so mature, there was communication issues, little open guidance and unrealistic expectations. People learn by mistakes and some companies don’t want to have nightmare stories like others and are investing in security. So, yes, things are going (a little bit) better because more people are addressing security issues.
The first talk was “IoT hacking and Forensic with 0-day” by Moonbeom Park & Soohyun Jin. More and more IoT devices have been involved in security incident cases. Mirai is one of the latest examples. To address this problem, the speakers explained their process based on these following steps: Search for IoT targets, analyze the filesystem or vulnerabilities, attack and exploit, analyze the artefacts, install a RAT and control using a C&C then perform incident response using forensic skills. The example they used was a vacuum robot with a voice recording feature. The first question is just… “why?”. They explained how to compromize the device which was, at the beginning, properly hardened. But, it was possible to attack the protocol used to configure it. Some JSON data was sent in clear text with the wireless configuration details. Once the robot reconfigured to use a rogue access-point, root access on the device was granted. That’s nice but how to control the robot, its camera and microphone? To idea was to turn in into a spying device. They explained how to achieve this and played a nice demo:
So, why do we need IoT forensics? IoT devices can be involved in incidents.Issues? One of the issues is the way data are stored. There is no HD but flash memory. OS remains the first OS used by IoT devices (73% according to the latest IoT developers survey). It is important to be able to extract the filesystem from such devices to understand how they work and to collect logs. Usually, filesystems are based on SquashFS and UBIFS. Tools were presented to access those data directly from Python. Example: the ubi_reader module. Once the filesystem details accessible, the forensic process remains the same.
The next talk was dedicated to SDR (Software Defined Radio) by Matt Knight & Marc Newline from Bastille: “So you want to hack radios?”. The idea behind this talk was to open our eyes on all the connected devices that implement SDR. Why should we care about radio communications? Not that they are often insecure but they are deployed everywhere. They are also built on compromises: big size and costs constraints, weak batteries, the deployment scenarios are challenging and, once in the wild, they are difficult to patch. Matt and Marc explained during the talk how to perform reverse engineering. They are two approaches: hardware & software defined radio. They reviewed pro & con. How to perform reverse engineering a radio signal? Configure yourself as a receiver and try to map symbols. This is a five steps process:
Identify the channel
Identify the modulation
Determine the symbol rate
Synchronize
Extract symbols
In many cases, OSINT is helpful to learn how it works (find online documentation). Many information is publicly available (example: on the FCC website – Just check for the FCC ID on the back of the device to get interesting info). They briefly introduced the RF concept then the reverse engineering workflow. To achieve this, they based the concept on different scenarios:
A Z-Wave home automation protocol
A door bell (capture button info and then replay to make the doorbell ring of course
An HP wireless keyboard/mouse
After the lunch, Vladimir Wolstencroft presented “SIMBox Security: Fraud, Fun & Failure”. This talk was tagged as TLP:RED so no coverage but very nice content! It was one of my best talk for today.
The next one was about the same topic: “Dissecting modern cellular 3G/4G modems” by Harald Welte. This talk is the result of a research conducted by Harald. His company was looking for a new M2M (“Machine to Machine”) solution. They searched interesting devices and started to see what was in the box. Once the good candidate found (the EC2O from Quectel), they started a security review and, guess what, they made nice findings. First, the device contained some Linux code. Based on this, all manufacturers have to respect the GPL and to disclose the modified source code. It takes a long time to get the information from Quectel). By why is Linux installed on this device? For Harald, it just increased the complexity. Here is a proof with the slide explaining how the device is rebooted:
Crazy isn’t it? Another nice finding was the following AT command:
AT+QLINUXCMD=
It allows to send Linux commands to the devices in read/write mode and as root. What else?
The last talk “Hacks & case studies: Cellular communications” was presented by Brian Butterly. Brian’s motto is “to break things you must understand how they work”. The first step, read as much as possible, then build your lab to play with the selected targets. Many IoT devices today use GSM networks to interact with them via SMS or calls. Others also support TCP/IP communications (data). After a brief introduction to mobile network and how to deploy your own. An important message from Brian: Technically, nothing prevents to broadcast valid networks ID’s (but the law does it :-).
It’s important to understand how a device connects to a mobile network:
First, connect to its home network if available
Otherwise, do NOT connect to a list of blacklisted networks
Then connect to the network with the strongest signal.
If you deploy your own mobile network, you can make target devices connect to your network and play MitM. So, what can we test? Brian reviewed different gadgets and how to abuse them / what are their weaknesses.
First case: a small GPS Tracker with an emergency button. The Mini A8 (price: 15€). Just send a SMS with “DW” and the device will reply with a SMS containing the following URL:
http://gpsui.net/smap.php?lac=1&cellid=2&c=262&n=23&v=6890 Battery:70%
This is not a real GPS tracker, it returns the operation (“262” is Germany) and tower cell information. If you send “1111”, it will enable the built-in microphone. When the SOS button is pressed, a message is sent to the “authorized” numbers. The second case was a gate relay (RTU5025 – 40€). It allows opening a door via SMS or call. It’s just a relay in fact. Send “xxxxCC” (xxxx is the pin) to unlock the door. Nothing is sent back if the PIN is wrong. This means that it’s easy to brute force the device. Even better, once you found the PIN, you can send “xxxxPyyyy” to replace the PIN xxxx with a new one yyyy (and lock out the owner!). The next case was the Smanos X300 home alarm system (150€). Can be also controlled by SMS or calls (to arm, disarm and get notifications). Here again, there is a lack of protection and it’s easy to get the number and to fake authorized number to just send a “1” or “0”.
The next step was to check IP communications used by devices like the GPS car tracker (TK105 – 50€). You can change the server using the following message:
adminip 123456 101.202.101.202 9000
And define your own web server to get the device data. More fun, the device has a relay that can be connected to the car oil pump to turn the engine off (if the car is stolen). It also has a microphone and speaker. Of course, all communications occur over HTTP.
The last case was a Siemens module for PLC (CMR 2020). It was not perfect but much better than the other devices. By example, passwords are not only 4 numbers PIN codes but a real alphanumeric password.
Two other examples: a SmartMeter sending UDP packets in clear text with the meter serial number is all packets). And a Solar system control box running Windows CE 6.x. Guest what? The only way to manage the system is via Telnet. Who said that Telnet is dead?
It’s over for today. Stay tuned for more news by tomorrow!
[The post TROOPERS 2017 Day #1 Wrap-Up has been first published on /dev/random]
from Xavier
0 notes
Text
i did not reclaim the mitm tags for a bunch of kpop stans to take over
(/lh)
#IN CASE YOU COULDNT TELL IM JUST KIDDING IM JUST BEING AN ASS LMAO#sometimes i find the most random shit in the mitm tags#im sure the kpop stans are looking through here though and being like#what the fuck sort of weird ass semifandom is this#if you're a kpop stan you should check out malcolm in the middle#they have literally nothing to do with each other but it's a funny show#reminds me of that one time the show was mentioned on wandavision#and i was forced to find out what wandavision was#and all i saw for days was that parody intro they made which was hilarious by the way#if mitm is canon in the mcu universe does that mean mitm is set in the same universe as mcu#dewey could defeat thanos#he has the power#i went way off subject i apologize to any kpop stans reading this
10 notes
·
View notes
Text
well if you guys didn't look at my bio now you definetly know who my second favorite is
0 notes
Text
┏┓
┃┃╱╲ In this
┃╱╱╲╲ house
╱╱╭╮╲╲ we love
▔▏┗┛▕▔ & appreciate
╱▔▔▔▔▔▔▔▔▔▔╲
dewey wilkerson
╱╱┏┳┓╭╮┏┳┓ ╲╲
▔▏┗┻┛┃┃┗┻┛▕▔
#this templete is dead but so am i#i love my son#not mitm#idk if i should tag posts like these asksksls
0 notes