#purchase order software open source
Explore tagged Tumblr posts
Text
I bought an 8bitdo Retro mechanical keyboard!

(Picture not mine, source from PC World.)
I wanted a plastic keyboard, I really do not actually use the knob on a Keychron board I have, it still comes in a scooped keycap profile, and it has a companion numpad with a calculator built in. Win/win/win!
This keyboard comes in four designs (not colorways, full designs) themed after the NES, the Famicom, the IBM Model M, and the Commodore 64 keyboard. The NES keycaps have multiple different fonts on them, the Famicom keycaps have Japanese sublegends, the Model M keycaps have a mock stepped Caps Lock key, and the Commodore 64 keycaps are an apparently off-the-shelf SA set from one of many, many, many keycap companies floating around China (I recognize their font and profile shape from Akko ASA keycaps and numerous other scooped profile keycap sets you can have cheaply off of Aliexpress and Amazon. Do check those out, genuinely, you'd struggle to find a bad scooped keycap set these days and I love scooped profiles over Cherry and OEM.)
The build quality of the actual keyboard itself is good, feels like a very similar plastic blend to what 8bitdo uses for its controllers like their Pro 2. Stabilizers are smooth and don't rattle, the legends on the keycaps are reasonably sharp and in NES-appropriate font, the keycaps themselves are MDA profile (I would prefer SA, but beggars can't be choosers) and are somewhat thin but still good quality, dye-sublimated PBT, no warp on the spacebar. Arrow keys are a separate color from the two tones that make up the main keycap set and made to resemble a d-pad. The keyboard itself is somewhat light, but my perception is skewed from using a metal keyboard for a long time, and this is after all a plastic shell, top-mounted keyboard. Even so I think I'll probably end up cracking open the keyboard and putting in some liquid silicone as noise-dampening and additional weight.
Two knobs control both wireless functionality and computer software volume, the wireless knob is heavy with only three options while the volume one is light with many individual steps. The volume knob can be somewhat unresponsive on individual steps. Bluetooth is very responsive and wants to pair with my computer the moment it's flicked over to, and 2.4ghz wireless comes with a receiver that slots into the back of the keyboard magnetically for storage. A power light on the right of the keyboard mimics the NES power light and pulses while charging, is steady while using wireless or when fully charged and connected over USB.
The underlying PCB is south-facing hotswap sockets (who the hell cares their orientation, this only matters for lighting, which this keyboard doesn't have). By default the keyboard comes with Kailh box whites, a very light clicky switch. I yanked them out immediately and put Boba U4T tactiles in because they're the king of all switches. They thunk nicely in this chassis, the Kailh whites weren't slouches either, they did pick a good stock choice for switch without resorting to Gateron or Outemu blue horseshit.
The NES version of the keyboard came with a two-button macro pad that hooks over TRRS cable (you recognize it as a 3.5mm jack or headphone cable) to one of four ports on the top-right of the keyboard. These are essentially just two keyboard switches with giant keycaps on a separate board and the buttons are populated by Gateron greens. The switches are nowhere close to heavy enough to approximate a button, and I gave them Kailh box navies. Still not enough, but better.
These keyboards also come wiiiiiith a companion number pad!

(Picture credit the 8bitdo store.)
While I don't actually have this one in hand just yet I do have it on order. It looks like it'll be about the same build quality as the main keyboard, and it caught my eye for four reasons and ended up making me purchase the full set as a result:
The numpad has a built in calculator.
Same aesthetic choices as the main keyboard (NES, Famicom, IBM Model M, Commodore 64)
Magnetically attaches to the right side of the keyboard to transform it into a more era appropriate full-size.
Far and away the cheapest wireless mechanical numpad with calculator on the market, sitting at $45.
An important note though is that the Famicom and NES keypads don't attach to their respective keyboards, simply because their respective keyboards don't have magnets inside the sides of the chassis to allow for it. I have some cheap button magnets laying around that I'll use for this purpose and probably see if they're strong enough to be placed on the inside of the board and allow for the numpad to connect to it. I also imagine there's going to be a repop or v2 of this keyboard in the future that has this done already, seeing as the Commodore 64 version of the board and I believe the Model M version of the board already have that.
I'll reblog this and give some actual definitive thoughts on the numpad once it's in my hands.
As far as the board itself is concerned, I quite like it. The keycap profile is agreeable, the nostalgia pandering targeted me with laser precision, the board sounds quite good acoustically (especially for being a top-mount keyboard!) and it has a volume knob I'll see if I can reprogram some day. While I normally hate TKL layouts, I'm putting up with it because it will eventually be a fullsize with the numpad. Worth $150 total? Don't know, can't answer that for you, it's worth it to me but I very specifically wanted a keyboard themed after an old Nintendo console with no setup required and no chasing down or commissioning GMK keycap sets. I also wanted a calculator numpad.
#look at my flop reviews boy#mechanical keyboards#keyboards#mechanical keyboard#keyboard#tech#gadgets#computers#nintendo#NES#nintendo entertainment system
45 notes
·
View notes
Text
Last year, the White House struck a landmark safety deal with AI developers that saw companies including Google and OpenAI promise to consider what could go wrong when they create software like that behind ChatGPT. Now a former domestic policy adviser to President Biden who helped forge that deal says that AI developers need to step up on another front: protecting their secret formulas from China.
“Because they are behind, they are going to want to take advantage of what we have,” said Susan Rice regarding China. She left the White House last year and spoke on Wednesday during a panel about AI and geopolitics at an event hosted by Stanford University’s Institute for Human-Centered AI. “Whether it’s through purchasing and modifying our best open source models, or stealing our best secrets. We really do need to look at this whole spectrum of how do we stay ahead, and I worry that on the security side, we are lagging.”
The concerns raised by Rice, who was formerly President Obama's national security adviser, are not hypothetical. In March the US Justice Department announced charges against a former Google software engineer for allegedly stealing trade secrets related to the company’s TPU AI chips and planning to use them in China.
Legal experts at the time warned it could be just one of many examples of China trying to unfairly compete in what’s been termed an AI arms race. Government officials and security researchers fear advanced AI systems could be abused to generate deepfakes for convincing disinformation campaigns, or even recipes for potent bioweapons.
There isn’t universal agreement among AI developers and researchers that their code and other components need protecting. Some don’t view today’s models as sophisticated enough to need locking down, and companies like Meta that are developing open source AI models release much of what government officials, such as Rice, would suggest holding tight. Rice acknowledged that stricter security measures could end up setting US companies back by cutting the pool of people working to improve their AI systems.
Interest in—and concern about—securing AI models appears to be picking up. Just last week, the US think tank RAND published a report identifying 38 ways secrets could leak out from AI projects, including bribes, break-ins, and exploitation of technical backdoors.
RAND’s recommendations included that companies should encourage staff to report suspicious behavior by colleagues and allow only a few employees access to the most sensitive material. Its focus was on securing so-called model weights, the values inside an artificial neural network that get tuned during training to imbue it with useful functionality, such as ChatGPT’s ability to respond to questions.
Under a sweeping executive order on AI signed by President Biden last October, the US National Telecommunications and Information Administration is expected to release a similar report this year analyzing the benefits and downsides to keeping weights under wraps. The order already requires companies that are developing advanced AI models to report to the US Commerce Department on the “physical and cybersecurity measures taken to protect those model weights.” And the US is considering export controls to restrict AI sales to China, Reuters reported last month.
Google, in public comments to the NTIA ahead of its report, said it expects “to see increased attempts to disrupt, degrade, deceive, and steal” models. But it added that its secrets are guarded by a “security, safety, and reliability organization consisting of engineers and researchers with world-class expertise” and that it was working on “a framework” that would involve an expert committee to help govern access to models and their weights.
Like Google, OpenAI said in comments to the NTIA that there was a need for both open and closed models, depending on the circumstances. OpenAI, which develops models such as GPT-4 and the services and apps that build on them, like ChatGPT, last week formed its own security committee on its board and this week published details on its blog about the security of the technology it uses to train models. The blog post expressed hope that the transparency would inspire other labs to adopt protective measures. It didn’t specify from whom the secrets needed protecting.
Speaking alongside Rice at Stanford, RAND CEO Jason Matheny echoed her concerns about security gaps. By using export controls to limit China’s access to powerful computer chips, the US has hampered Chinese developers’ ability to develop their own models, Matheny said. He claimed that has increased their need to steal AI software outright. By Matheny’s estimate, spending a few million dollars on a cyberattack that steals AI model weights, which might cost an American company hundreds of billions of dollars to create, is well worth it for China. “It’s really hard, and it’s really important, and we’re not investing enough nationally to get that right,” Matheny said.
China’s embassy in Washington, DC, did not immediately respond to WIRED’s request for comment on theft accusations, but in the past has described such claims as baseless smears by Western officials.
Google has said that it tipped off law enforcement about the incident that became the US case alleging theft of AI chip secrets for China. While the company has described maintaining strict safeguards to prevent the theft of its proprietary data, court papers show it took considerable time for Google to catch the defendant, Linwei Ding, a Chinese national who has pleaded not guilty to the federal charges.
The engineer, who also goes by Leon, was hired in 2019 to work on software for Google’s supercomputing data centers, according to prosecutors. Over about a year starting in 2022, he allegedly copied more than 500 files with confidential information over to his personal Google account. The scheme worked in part, court papers say, by the employee pasting information into Apple’s Notes app on his company laptop, converting the files to PDFs, and uploading them elsewhere, all the while evading Google’s technology meant to catch that sort of exfiltration.
While engaged in the alleged stealing, the US claims the employee was in touch with the CEO of an AI startup in China and had moved to start his own Chinese AI company. If convicted, he faces up to 10 years in prison.
5 notes
·
View notes
Text
Nippon Ichi Software announces roguelike strategy RPG Bar Stella Abyss for PS5, PS4, and Switch
Gematsu Source
[I hit the 30 image limit, so some near the bottom are missing, but you can check the site for them]

Nippon Ichi Software has announced roguelike strategy RPG Bar Stella Abyss for PlayStation 5, PlayStation 4, and Switch. It will launch on February 29, 2024 in Japan.
Here is the announcement trailer:
youtube
Get the first details below.
■ Specifications
Title: Bar Stella Abyss
Genre: Roguelike strategy RPG
Platforms: PlayStation 5, PlayStation 4, Switch
Release Date: February 29, 2024 (Japan)
Players: One
Price: 7,200 yen (without tax) / 7,920 yen (with tax)
Publisher: Nippon Ichi Software
Development Manager: Shunsuke Minowa
Planning and Concept / Art Director: Yu Mizokami
Character Design: Mio Katsumata
CERO Rating: Pending
Official Website: nippon1.jp
Official Hashtag: #BARステラアビス

■ Game Overview
Bar Stella Abyss is a roguelike strategy RPG in which you strengthen your party with the power of the constellations while exploring a dungeon in another world that changes form each time you play. In addition to exploring the other world, the story will unravel as you share drinks with the peculiar patrons of the bar “Stella Abyss.”

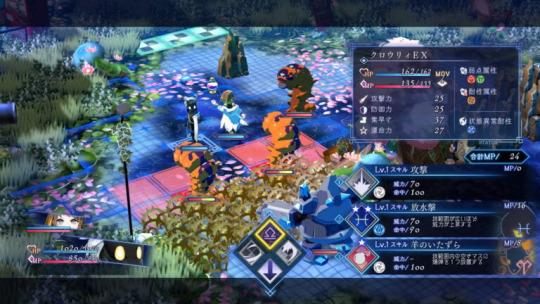


■ Story

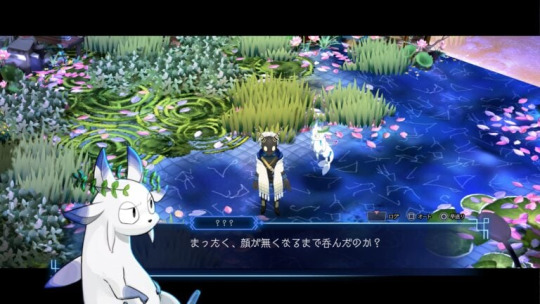
Stella Abyss is a hidden bar tucked away in the corner of the city. The protagonist, tired out by their day to day, is guided there by a flyer floating in the wind and opens its doors. “You seem to be extremely exhausted. Allow me to make you something right away.” Drunk on the cocktail he ordered as recommended by the bartender, the protagonist fell asleep. The hungover protagonist woke up to an unfamiliar voice echoing in their head. Before them was a mysterious creature floating in the air, and a magical scene of flowers in bloom. This is the “Drunken World,” the dream of a drunk person. The protagonist was robbed of their face and arm, and left trapped in this dream world.
■ Characters
Wanderer (voiced by Nanako Mori) A wanderer who lost their face and arm.

The protagonist, who arrives at the hidden bar Stella Abyss after following a flyer floating in the wind through the city at night. In order to get back the face and arm they lost in the Drunken World, they must go back and forth between the bar and other world.

Master (voiced by Ayaka Shimizu) Owner of the hidden bar Stella Abyss.
“Welcome to the bar Stella Abyss.”

A gentle-mannered woman adored by her regulars. She also seems to know about the Drunken World. She offers all sorts of advice to the protagonist, who is taken aback by the sudden events.

Tipsy (voiced by Michiyo Murase) A servant of the Drunken World’s god.
“Humans really are stupid to drink so much more than they can handle.”

A creature who saves the protagonist after wandering into the Drunken World and names them “Wanderer.” They do whatever they can to help catch the thief who stole the protagonist’s face and arm.
■ System
Explore the Drunken World You Reach After Drinking Yourself Unconscious
The Drunken World is said to exist in countless numbers like stars. The protagonist Wanderer travels around this profoundly mysterious world to get back their lost face and arm.

—Dungeons are scattered with facilities that will aid in your exploration, including an observatory where you can obtain enhanced skills, and shops where you can purchase items. It is up to the player to decide which facilities to progress through.


—If you encounter any of Stella Abyss’ regulars in the Drunken World, you can add them to your party. With their help, aim to reach the depths of the Drunken World.
—When you use up all your strength in the Drunken World, you will wake up in the bathroom of Stella Abyss. Equipment aside, all items will be lost and your level will return to its initial state.

Turn-Based Strategy RPG Battles
When you encounter the monsters that roam about the Drunken World, the fight will shift to a tile-based battle map. Combat progresses like a turn-based strategy RPG. Choose your actions while paying attention to the enemy’s weaknesses and placement, as well as terrain effects.


Strengthen Characters with the Power of Constellations
As you explore, you will obtain “Stella,” which are the powers of the constellations. By setting a Stella to a character’s skill, its performance can be enhanced in ways such as expanded attack range, additional power, or granting additional attributes.
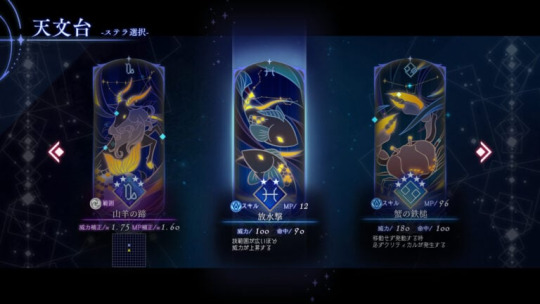
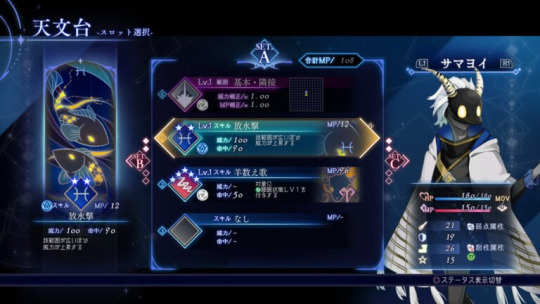
There are around 130 different Stella that will randomly appear, and up to four can be equipped for a single skill, but all Stella will reset once your run ends. Try out different combinations of Stella for every run.


For example, by combining the Stella “Double Backstep,” which allows you to move back two tiles, and “High-Speed Firing,” which increases your power the further away you are from an enemy, you can create a skill that deals high damage while also keeping a safe distance from the enemy.
Smooth Conversation and Exploration Through the Power of Alcohol

By sharing drinks with the other regulars, you can gain effects that will aid you on your journey in the Drunken World. —Stella Abyss has several regulars that come in for a drink. Talk to those that pique your interests and share a table.


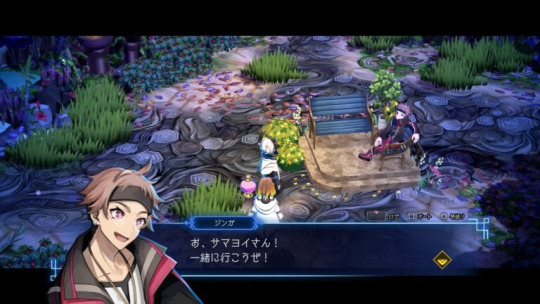
The Patrons of Stella Abyss
The men and women of Stella Abyss. They will also appear in the Drunken World, where only those who “lost something important” are said to reach, and help out the protagonist.

From left to right, the regular patrons include:
Kaji (voiced by Hiroshi Watanabe)
Baran (voiced by Hiromu Mineta)
Kiruca (voiced by Mikoi Sasaki)
Cass (voiced by Momoyo Koyama)
Leona (voiced by Honoka Kuroki)
Maia (voiced by Riho Sugiyama)
Jinga (voiced by Mutsuki Iwanaka)
Saotome (voiced by Takaki Otomari)
Enjoy Conversation with the Regulars
By sharing a table with the regulars at Stella Abyss, you can enjoy conversation. There are four prompts you can choose from as reactions during a conversation, including “Agree,” “Disagree,” “Laugh,” and “Doubt,” as well as the additional option of “Drink” for a total of five options. Choose the most appropriate reaction to match the other person’s feelings and drive the conversation forward. —If you make a comment that disrupts the flow of the conversation or offends the other person, the conversation will not flourish and your time drinking together will end.
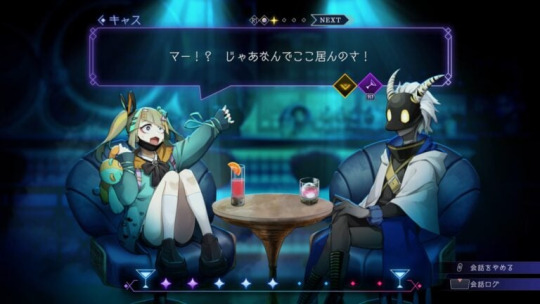
—If you choose “Drink” too much, your vision will blur and you will be forced into the Drunken World. Be sure to pace yourself when drinking…
The Hidden Effects of Cocktails
The cocktails of Stella Abyss will bestow special effects that will aid you in the Drunken World. There are various effects, from granting additional experience points to increasing the appearance rate of certain Stella. Order cocktails that match your exploration style. —If your conversation flourishes while sharing a table, you can order additional cocktails. Two drinks, three drinks… the effects will accumulate the more you drink, allowing you to explore the dungeon with an advantage. —There are over 300 cocktails. By spending the money you collect in the Drunken World, you can unlock cocktails with more powerful effects.
■ Box Art
■ First-Print Bonus
First-print copies of the physical edition will include a download code for the digital mini soundtrack, which contains eight tracks carefully selected from the game’s background music.
■ Nippon1.jp Shop Limited Edition
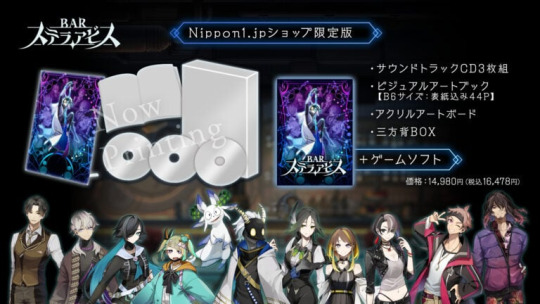
The Nippon1.jp Shop Limited Edition includes:
A copy of the game
Soundtrack CD – Three discs. Includes every background music track from the game.
Visual art book – 44 pages, B6-size. Includes artwork from the game.
Special Box – Can be used to store the soundtrack CD and visual art book.
Acrylic art board – A5 size.
Pre-orders are available here: PlayStation 5, PlayStation 4, and Switch.
View the screenshots at the gallery.
#Bar Stella Abyss#Nippon Ichi Software#Nippon Ichi#Roguelike#SRPG#RPG#Gematsu#Hoping for a localization announcement#Youtube
12 notes
·
View notes
Text
On August 12, 2019, Verizon Media announced that it would sell Tumblr to Automattic, the operator of blog service WordPress.com and corporate backer of the open source blog software of the same name. The sale was for an undisclosed amount, but Axios reported that the sale price was less than $3 million, less than 0.3% of Yahoo's original purchase price. Automattic CEO Matt Mullenweg stated that the site will operate as a complementary service to WordPress.com, and that there were no plans to reverse the content policy decisions made during Verizon ownership.[2]
In November 2022, Mullenweg stated that Tumblr will add support for the decentralized social networking protocol ActivityPub.[25] In November 2023, most of Tumblr's product development and marketing teams were transferred to other groups within Automattic. Mullenweg stated that focus would shift to core functionality and streamlining existing features.[26]
In February 2024, Automattic announced that it would begin selling user data from Tumblr and WordPress.com to Midjourney and OpenAI. Tumblr users are opted-in by default, with an option to opt out.[27][28]
In August 2024, Automattic announced that it would migrate Tumblr's backend to an architecture derived from WordPress, in order to ease development and code sharing between the platforms. The company stated that this migration would not impact the service's user experience and content, and that users "won't even notice a difference from the outside".[29]
2 notes
·
View notes
Text
The Top Free Virtual Machine Tools You Should Try Right Now

If you're looking for ways to save money and optimize the efficiency of your office, virtual machine tools are a great place to start. With virtualization technology, you can run multiple operating systems on one physical machine in order to maximize space and resources—allowing for smoother operation and higher output with fewer machines. Not only can it improve performance in terms of game-play, software development, web hosting, or online business transactions; but it also provides cost savings by avoiding the need to purchase expensive hard drives or network components that would otherwise be incurred. In this blog post, we'll explore some of the top free virtual machine tools available right now so you can take full advantage of these amazing benefits without breaking the bank!
Introductory Overview of Virtual Machine Tools
In recent years, the significance of virtual machine tools has grown in leaps and bounds within the realm of information technology. These cutting-edge solutions have deftly become a mainstay for both developers and system administrators alike. Virtual machine tools, by emulating hardware resources, effectively allow multiple operating systems to operate concurrently and independently on a single host machine. As powerful software applications, they facilitate the creation, management, and optimization of virtualized environments for diverse purposes, such as software testing, cybersecurity evaluation, and server consolidation. Moreover, these tools embody a modern, sophisticated approach to managing infrastructure and provide a robust foundation for enhancing productivity, expediting workflows, and fostering innovation for organizations and individuals navigating an increasingly digital landscape.
How to Use VirtualBox for Free
Utilizing VirtualBox for Free delivers a sophisticated and efficient solution to virtualize different operating systems on a single device. VirtualBox, an open-source software, has gained immense popularity among developers and IT professionals owing to its versatility and ease of use. This powerful virtualization tool caters to a wide array of applications, ranging from running legacy software on modern hardware to seamless testing of operating systems and applications without risking the stability of your primary system. The cost-effective nature of this application, coupled with its vast capabilities, makes it an invaluable asset for those seeking to harness the power of virtualization without incurring any financial burden. Integrating VirtualBox into your daily practices paves the way for an innovative and secure environment that fosters creativity and efficiency.
Exploring the Benefits of VMware Player
The advent of virtualization has brought forth numerous benefits, and VMware Player stands as a testament to these advantages. As a reliable, robust, and user-friendly virtualization software, VMware Player excels in offering users an effortless and efficient manner of managing and operating multiple operating systems on a single computer. By employing innovative virtualization methods, VMware Player dramatically enhances productivity, allowing IT professionals and developers to seamlessly test and develop applications on diverse platforms. Moreover, the software's robust security features promise a secure environment that reduces the risk of malicious intrusions and cyber threats. With its unmatched receptiveness for both business and personal use, VMware Player undeniably paves the way for the elevated potential of virtualization in today's dynamic digital landscape.
Making the Most of Parallels Desktop
The ingenious invention, Parallels Desktop, is a state-of-the-art software that enables individuals and businesses to optimize their work processes and improve efficiency. This remarkable tool allows for seamless access to multiple operating systems within a single computer, facilitating effortless interaction between applications and a smooth workflow. By leveraging Parallels Desktop, one eliminates the need for cumbersome hardware, thus conserving resources, while simultaneously promoting synergy between disparate platforms. The result is a unified work environment leading to increased productivity and reduced complexity. Moreover, its compatibility with various devices such as smartphones and tablets, makes it an indispensable and versatile accomplice in today's fast-paced digital landscape.
Examining Microsoft's Hyper-V for Windows 10
In recent years, the significant rise in virtualization technologies has brought forth an array of benefits for both businesses and individual users. One such cutting-edge solution is Microsoft's Hyper-V, a remarkable feature available on Windows 10 operating systems. Hyper-V allows users to create and manage virtual machines (VMs) within a single device, eliminating the need for investing in additional hardware, whilst ensuring efficient utilization of the available resources. Embracing this technology can lead to enhanced productivity and flexibility, as it permits simultaneous deployment of multiple operating systems, streamlines software testing processes, and simplifies disaster recovery procedures. Furthermore, by closely examining the dynamic capabilities of Hyper-V, IT professionals can ascertain novel methods to optimize resources, reduce overhead costs, and bolster their organization's strategic approach to technological advancement.
Unleashing the Power of QEMU with Open-Source Software
The phenomenal potential of QEMU, an open-source machine emulator and virtualizer, becomes increasingly evident when synergized with other open-source software. Such collaborations afford developers and users an integrated platform to optimize the performance, functionality, and flexibility of virtual systems. Streamlining processes, reducing costs, and overcoming challenges posed by proprietary software, these dynamic partnerships continually push the boundaries of what is feasible within the realm of virtualization. As innovation accelerates and open-source software gains traction across various industries, the combination of QEMU and other renowned open-source tools paves the way for groundbreaking advancements, ultimately challenging conventional paradigms and shaping the future of technology.
In conclusion, virtual machine tools offer a cost-effective solution to the demands of modern computing. From the simple yet powerful VirtualBox software to the more advanced VMware Player and Parallels Desktop options, there is something available for everyone's needs. For those looking to explore a Windows 10 experience without investing in a separate license or running numerous installations on their device, Microsoft's Hyper-V can provide a great alternative solution. Finally, open-source solutions such as QEMU can help tech enthusiasts really unleash their creativity as they customize their environment and modify it however they please. Whether for business or pleasure, virtual machines are here to stay and power users everywhere are sure to get plenty of use out of this increasingly powerful technology!
7 notes
·
View notes
Text
Could We Peer Produce Movies?
A thought experiment on modern modes of production
originally published 8-28-2023 on my blog
Introduction
In the world of the modern internet, there exists a concept called peer production. You’re probably already very familiar with works produced under this mode. Wikipedia primarily bases its content off of peer production. Likewise almost all free and open source software like the Linux servers that run 90% of the internet, are also made using peer production models.
Last year though, something very interesting happened. A meme went viral on Tumblr about a fake Martin Scorse film called Goncharov. A collective running bit, the meme attracted songs, spec scripts, movie posters, costume designs, and so many other artifacts that would be assembled as part of a pre-production or a pitch process for a movie. All of which were created and distributed through a type of decentralized, uncoordinated peer production. It made me wonder what could have been produced if there had been some tool, structure, or platform to focus all that energy into an actual production.
Especially, in the light of the ongoing SAG-AFTRA & WGA strikes, I think there’s an interesting moment for change in the way entertainment is produced in the USA. The workers that make movies & TV in the country are on strike right now because the middleman bureaucracy of studio production has squeezed too hard & has reached the point that it is trying to push all the humans who actually make art within the system, out of it.
To me, what peer production points towards is a new means of managing the production of goods and services that relies on self-organizing, decentralized community networks that can evolve organically out of the group members doing the actual creative work & the end customers who engage with it. This stands in contrast to the status quo where the control of labor is top-down & the work is centralized in as few laborers as possible in order to maximize the extraction of profit off of that labor.
Context
Crowdfunding as a concept and fundraising mechanism has been around for over a decade now (see my piece from 2012). It has never been easier to attract money to a project, but now instead of attracting ten investors at ten thousand dollars from your local friend, family, & golf network, you can attract ten thousand investors at ten dollars a pop from around the world. Which is to say, you can get your audience or customers to pay for the production up front and cut out investors.
This new ease of raising funds undermines one of the value propositions old studios provided. The other of course being the purchase, maintenance, and provision of capital intensive studio space & filmmaking equipment. However, we are also in a moment where the actual capital costs of tools & input commodities have been driven to near zero. A combination of cheap computers, smartphone proliferation, and a large number of free post-production tool sets now means that the core cost of movie & tv production is the actual creative labor.
And now we’re at a point where the big entertainment studios think they can cut writers and actors and all the other creative labor out of the production cycle! But you don't get the good shit without creative humans. You don’t get novelty without humans. You don’t get art without humans!
Ultimately this stuff is for and by humans, so to try and squeeze them out of the process with AI is just another short-term cost-cutting measure to profit this quarter in exchange for a long-term loss. It's ripping the copper out of the walls, it’s squeezing all the juice out of the orange just to be left with the bitter pulp.
So in a moment where it’s never been easier to raise funds for a project, where it’s never been cheaper to produce art, and where the old institutions responsible for fundraising and providing the tools & space for the actual humans who make art are trying to squeeze the humans themselves out of the picture, what new institutions could we build to put some humanity back into our art?
Proposal
To start with, I would describe these new forms as a type of worker-customer hybrid cooperative. The workers need customers to value & fund the final work (i.e. what good is a show to an empty theater) and the customers want the workers to do the work in the first place (i.e. what good is money if you can’t exchange it for goods and services).
Control & ownership of the cooperative would be represented by two types of shares, one for customers & one for workers. The customer shares would be issued as part of crowdfunding rounds at the beginning of the project. Worker shares would be issued as part of the actual production workflow for things such as contributing concept art, recording voice lines, writing scripts, animating scenes, project management, etc. For legal purposes the cooperative would have copyrights to the work artifacts and final work, but would release stuff back into the public domain or leverage a creative-commons license to prevent work from being locked up for more than five years.
The shares themselves then have value for a few reasons. A share entitles you to vote on steering decisions, authorizing and approving submitted work, and ultimately a share of the profits. I would propose that the power/profit/approval ratio between shares skew towards worker shares. Something like an 80:20 split and ultimately never going lower than 51% for worker shares. The first person to initialize the project would be issued 1 worker share as the chief steward, based on the Little Red Hen Principle. Shares would be non-transferable.
From those initial points a few work pipelines would need to be tooled up. A core mechanism for proposing, planning, intaking, tracking, validating and approving work for the production would be needed.
A core loop of assigning worker share values to tasks, approving the issuance of the work order, & finalizing work artifacts & issuance on delivery would need to be developed. A mechanism for assigning & tracking responsibility for keeping different workflows moving forward and getting delivered could also be implemented. Lastly, a mechanism for creating milestones that when met (and maybe based on supporter approval), disburse actual funds to outstanding worker shares for meeting milestones from the funding pool gathered from supporter contributions could help keep productions moving.
Example
So now that we have a high level idea of what’s going on, let’s look at what an animated production of everyone’s favorite Shakespere play, Hamlet, might look like.
Pre-production on this should be pretty straightforward. The script is already written (and blessedly in the public domain). As it’s going to be animated, there is an opportunity for some parallelized production flows too.
Starting with the animation side of things, we’re probably going to want some concept art. Character design for each of the characters & set design for each of the scenes. The chief steward cuts 10 character design tickets & 10 scene design tickets on the workflow tool & assigns each a value of 1 worker share, assuming the average artist can conduct the work on each ticket in about an hour.
This work cut out, it’s time to break out voice acting work. 10 tickets are written calling for the first line reads of each of the characters. We assume it’s maybe 5 minutes of finished audio, but that it'll have taken the actor an hour to do a few reads & clean up the audio before shipping.
Some mechanism for gating tickets behind approval of other tickets could be implemented to mirror a tryout/portfolio approval process on the part of all cooperative members. That is to say, anyone can pull the “first” ticket, but whoever’s work gets the most approval from the customer/worker shareholders then gets access to the rest of the tickets in that work bucket.
Then you can imagine that as customers fund the project, they can begin to have some say in approving or disapproving things. Maybe the workers can’t decide on which actor to pick for the part of Hamlet, so they leave the vote open to just customers to pick the actor.
Obviously this is not an airtight, ISO standard proposal, it’s more of a thought experiment about how to arrange and manage this kind of work but hopefully it paints a decent enough sketch.
Considerations
Perhaps more complicated endeavors or more complicated productions utilizing this system might not work. But in the current crowdfunding environment, there's clearly been some gaps and failures and the system isn't fully there anyway. Think of Star Citizen as a great example of this. It's relatively easy to get the money, but systems of accountability and checking in seem harder to come by.
I guess there’s also the caveat that there might be a lot of crap work being produced. The free stuff might be overwhelming. But, if you put together a production crew, or production community and make a name for yourself that way, or you make a name for yourself as an independent animator or a voice actor, supporters can trust the production & workers can trust the work.
Conclusion
I'm of the opinion that we are on the cusp of software development and platform development being democratized and in that process these big lumbering bureaucracies that sit in the middle and fundamentally introduce inefficiencies into the system in an effort to arbitrage profit will be cleared away in favor of processes & systems similar to the one I have described above.
I think we can replace these middleman institutions with software systems that distribute the decision-making apparatus with collective voting systems and new tools & processes will have to be developed to manage and facilitate this distributed democracy.
This is food for thought in this moment, where people are being threatened with the notion that automation will take creative, novel, generative work away from humans. But what if the real truth is that automation is more likely to remove the boring, useless middlemen that have given us a decade plus of boring, repetitive Marvel movies (among other things). I like to think we’ll get there sooner rather than later and I’m trying to do my part to help move things along. I hope, when you see an opportunity to jump aboard, you will too.
3 notes
·
View notes
Text
How Can I Purchase Windows Keys For An Affordable Price?

Do you want to save a few bucks for the cost of Windows keys? You're not alone! There are many people searching for low-cost alternatives to purchase Windows keys. There are many methods to locate Windows keys for a reasonable cost.
In this article, we will examine the online marketplaces that allow you to find discounted Windows keys, alternative options in obtaining Windows keys, locating authorized resellers at affordable prices using promotions and sales. In addition, we'll give you tips for finding authentic and genuine cheap windows 11 keys for a cheaper price.
In case you're eager to cut costs while maintaining the high-quality the performance of the quality of Windows key, continue reading!
Explore online Marketplaces to find discounted Windows Keys
Check out the online markets for great deals on Windows keys!
The platforms provide a vast range of options, allowing you to compare costs and select the most suitable deal for your specific demands.
There are genuine Windows keys at popular websites including Amazon and even specialized ones like Kinguin.
Be sure to check reviews before choosing a reliable seller in order to have a smooth deal.
Look into alternative Windows Keys
Explore other options to get the Windows licenses you want. Open-source systems such as Linux can be trusted and are free alternatives to Windows.
Another option is to purchase pre-installed computers with a valid copy of Windows.
You can also explore options for schools or nonprofits that offer discounted or free Windows licensing.
Alternative options may help you save money but still get a solid operating system.
Searching for Authorized Resellers buy software keys
Check out authorized resellers to get great discounts on Windows licenses. Microsoft has authorized these resellers to provide authentic Windows keys for discounted prices. By purchasing from authorized resellers You can be sure that you're getting a legitimate product and stay clear of the risk of buying from unauthorized sources.
A lot of resellers provide specials and discounts, which means it is possible to purchase Windows Keys for an affordable price.
Promos and discounts for Windows Keys
Utilize promotions and deals to score amazing bargains on genuine Windows licenses at authorized resellers. Discounts and promotions can provide significant savings over the usual cost of Windows keys, making them more affordable for those with a tight budget.
It is possible to purchase a Windows license at a discounted price when you keep your eyes peeled to these deals.
How to Find Genuine Windows Keys for a Low Price
To score genuine and legitimate Windows licenses at a cheaper price, keep your eyes peeled for promotions and discounts which can help make these highly popular keys more affordable to smart shoppers such as yourself.
Be on the lookout for sales, such as Black Friday or Cyber Monday in which retailers typically give significant discounts on their software.
Consider also looking into reputable online marketplaces or authorized resellers, who may offer affordable prices for genuine cheap windows keys.
Make sure you are able to verify the authenticity of the seller before making a purchase online.
Summary
Locating affordable Windows keys can be a challenging task that requires diligence and careful analysis. On-line marketplaces may offer discounts on alternatives, however be wary of illegitimate sellers.
Explore alternative operating systems, such as those that are open-source. Benefiting from discounts and sales, as well as researching authorized resellers can also offer cost-effective alternatives.
Be sure to use genuine windows key to ensure optimal performance of your system.
2 notes
·
View notes
Text
Hiring development Services for designing good e commerce websites.
Magento is one of the most powerful and innovative e-commerce systems available, simplifying the lives of regular people everywhere by making it easier for them to purchase online.
eCommerce websites may benefit from Magento's unique, flexible, and creative shopping cart solutions. While there is no completely risk-free e-commerce platform, Magento is often regarded as among the safest and most dependable options available.
So why, exactly, do experts say that Magento Development is the greatest option for creating and customizing an e-commerce website?

In the first place, Magento is a free and publicly available software system.
The fact that the source code is made available to the public makes it open and transparent.
Third, it can be easily modified and expanded upon.Magento Edit Order is very good.
Magento, being one of the top shopping cart platforms, has gained widespread acceptance throughout the globe.
As a result, Magento development services are in high demand all over the globe.
There are several useful features available on this platform.Magento Order Management is preferred by a lot of people.
Some additional benefits of the Magento Content Management System
Magento is a platform that enables the creation of an online store, which in turn improves the reputation of your business and increases its income. It has made it possible for almost all online shops, hence decreasing the barrier of entry for marketing products and services.Magento 2 Edit Order Extension is indeed excellent.
Your eCommerce website may be able to stand out from the competition and attract more clients as a result of its remarkable versatility and the choices it provides for customization. Because of the versatility it gives, not only will it improve the reputation of your firm, but it will also enable you to expand the scope of your website and the marketing efforts you make.Edit Order Magento 2 is preferred by a lot of people.
Magento Development Services make it possible for online enterprises to fulfill all of their customers' requirements. It provides a platform that allows you to monitor all of your online merchandise without disrupting the flow of your business.Magento 2 Order Edit Extension has been fantastic.
Magento Development is an integrated payment solution that allows you to keep control over the aesthetics, content, designs, style, and graphics for your website. This control extends to all aspects of the website. You are free to create your website to meet your requirements and include any ideas that come to mind. All of this would help you get an edge over other people who are competing with you in the online market. You can find Magento 2 Order Edit at a lot of places.
Using a professional Magento development service has several advantages.
- They provide you Multiple shop facilities
- These services follow SEO friendly regulations
- These services provide you cost-effective alternatives for constructing your website on Magento.
- They accomplish your assignments within the stipulated time limitations.
Reduces stress from worrying about the security of your data and frees up valuable time.
These days, most Development service providers offering Magento development services may benefit from the platform's extensive feature set and open source nature. They can assist you in creating an online storefront that stands out from the crowd by using custom-built software and specialized design elements.
4 notes
·
View notes
Text
Data leakage is on the increase in the country because information security incidents have escalated due to increasing online usage in the course of expanding the digital frontier and adopting various online services. Employing stolen credentials for identity theft or selling the stolen personal information affect millions of individuals. Taking a look at some of the biggest privacy violations and how you can avoid them.
Papamitsikos et al. describe data breaches and identify theft as two malicious IT attacks. Data leakage is one of the most severe threats; criminals break data base in order to steal personal details. Such stolen information can be sold in the black market or for identity fraud, whereby the criminals pretend to be the person of interest, in order to be granted access to some financial endowment or to perpetrate some form of fraud. More attention to the threats is paid by recent large-scale attacks to the payment systems, e-commercial WebSites, as well as governmental databases.
How to Protect Yourself:
1.Secure accounts with different but very healthy passwords.
Allow two factor authentication as often as it is possible. The last financial activity is the frequent check of bank statements and credit reports for purchases of the loan. Do not open sensitive accounts if connected to the public Wi-Fi network, instead, use secure networks only.
Illicit data acquisition and monitoring
This type of data collection without consent of the subject is a huge violation of privacy in India, especially considering how multiple apps demand users to provide excessive permissions and permissions to access large amounts of data, which, in fact, has no connection to the app’s objective. Most apps gather geo-location data, browsing history, contacts and other information and may sell it to third parties or use them to market products to users.
How to Protect Yourself:
Minimize apps permission by only allowing to have rights that are essential for the app. Review app permission often especially granted access and revoke access which is not necessary. There are still private browsers and search engines, which are better for your privacy. Avoid targeted advertising wherever it is possible.
Chapter 12: Phishing scams and Social engineering Phishing for example is not a new phenomenon in the online world and the attackers have gone a notch higher and are now duplicating brands or even government agencies to obtain the users’ details. These frauds mostly take place through email, SMS or phone where the con artists seek a person’s account number or social security numbers.
How to Protect Yourself:
He said the respondents should avoid opening anonymous emails and messages that ask for specific information in the next part of the study. One of the best ways to identify phishing is to look at the sender’s address or the language used such as the word ‘Urgent’. Do not follow web links in an unsolicited e-mail; typing the URL given in the address bar of the browser is safer. Opt for spam folders to minimize the risks associated with flow of phishing emails.
Ransomware and other attacks on users’ and their relatives’ portable devices A ransomware will either deny the users access to their devices or data until they make a payment they cannot control or avoid. Despite the fact that ransomware is mainly aimed at companies, the attacks on people also take place more often, and attackers save photos, documents, and other personal files to lock them.
How to Protect Yourself:
Maintain regularly the software and antivirus programs of the computer. Do not open any file or download any link that you get from unknown sources. They should ensure that all the valuable data is backed up on a regular basis to avoid losses in the instance a victory was scored by a hacker. Widthness your home network, and keep firewalls strong at your own home.
Social Media Privacy Breaches Another usual one is privacy violation through social networking sites. A large number of the users share information that can easily be employed for social engineering or create a profile about that user. Second of all, platforms monitor their users’ activity, which data can be sold to advertisers or exposed due to a data breach.
How to Protect Yourself:
Be careful when filling in your detailed personal data on social networks.
Limit the audience in which can see your posts and your profile. As much as possible should try to avoid giving out your location in the current time.
Do not take click-on online quizzes or click random ads because they can compromise your personal information.
Final Thought
Final Thoughts
In a world where India is increasingly turning to digital services, the question of protecting one’s privacy does not meet the question of ‘if’, but ‘how’. The two paramount aspects in usage of security are alertness and then using the security measures. It is always important when you learn about the various types of privacy intrusions that occur over the internet; you can significantly minimize your vulnerabilities to threats online by following these simple principles.
1 note
·
View note
Text
E-Commerce is one of the hottest markets in the world at present.As per Statista, retail eCommerce sales stood at $4.28 trillion in 2020. This figure is projected to rise to $5.42 trillion in 2022 and $6.38 trillion in 2024. This clears up one thing; if you have an eCommerce development service, whether small or big, you need to keep working on it.Now, handling an eCommerce venture is not a piece of cake. If you have experience, you know that handling shipping, product sourcing, managing inventory, order tracking, monitoring analytics may take more than the available time.To keep up with the cut-throat competition, you need to leverage some sophisticated eCommerce management apps. To help you get hands-on with the best ones, we have compiled a list. Check it out!Best Apps and Software to Streamline your eCommerce storeeCommerce management can be divided into various categories such as:MarketingOne of the critical elements of every business is marketing. It helps you attract new customers and retain the previous ones. So, to undertake the marketing process more manageable, you need to have tools like:Mailchimp: It is an excellent email marketing tool that to collect insights about your ongoing campaign. You can seamlessly integrate it with Shopify or WordPress and receive updates regarding your campaign on your mobile device. In addition, you can know about the opening and click-through rates easily from the Mailchimp app.Smile.io Rewards: Rewards are the best way to garner new customers and retain the old ones. This also indirectly helps in marketing your brand. To keep your customers coming back for repeat purchases, you need to allure them with benefits.Smile.io is the add-on that you can use with your Shopify account to provide customers with rewards for following the brand, sharing products on social networks, and more.Coupon Pop: The concept of Coupon Pop is a unique one as it provides the users’ coupons in return for their likes, follows, and emails.Inventory Management and ShippingTo keep up with the market demands, you need to ensure that your warehouse is stacked with all the necessary products.Checking it manually can be hectic. Hence, it would help if you use the following tools for managing the inventory of your eCommerce business.Zoho Inventory Management: The use of Zoho is not limited to just inventory management. It can help you undertake many other tasks such as create purchase orders, manage drop shipping, etc. You can even track every item of your inventory end to end with serial numbers and features. It can also assist you in making better business decisions via its accounting software and asset management tools.Veeqo: Veeqo is also one of the popular inventory management tools that helps you keep control over multi-channel inventory. You can sync it with multiple eCommerce channels. Besides this, it can help you forecast demand by analyzing past sales data.Easyship: It is an excellent tool that integrates worldwide couriers, taxes and duty charges, etc. Using Easyship, the businesses can offer worldwide delivery at reasonable costs.Product SourcingThis is one of the key things in every business. If you are beginning an eCommerce business, you need to plan to source the products you are planning to sell. There are many software to do that, such as:Maker’s Row: The web tool has a pool of manufacturers that supply over 2 million products of over 100,000 brands. You can search the required products on the website, talk to the supplier and get a quote for your purchase. Hence, it makes product sourcing super smooth for you.Oberlo: Oberlo is another app that allows you to source products from third-party drop shippers. Once you have selected your products, you can add them to your store and ship them directly to the customer. So, no hassle of storing them in a warehouse.Branding and DesigningKFC and McDonald’s are prime examples of branding!No matter how good the products are, popularity among the people is the key reason for business growth.
Hence, you need to make your business recognizable. Designing an excellent recognizable logo and using a branding kit is one way you can achieve popularity. Some of the tools that you can use for making graphics and logos are:Canva: A free online tool for creating graphics.Looka: An AI-powered platform for designing a logo that matches your brand vision.SEOTo keep your business growing, you need to make sure that you are always one step or more steps ahead of your competitors. And you can know this better by checking out your Google page rankings.To be in the eyes of the users means more sales and more revenue. For this, you need to use some advanced SEO tools for improving your organic reach and rank in the Google SERPs.SEMRush: It is a marketing SEO tool used for Domain-Domain analysis, checking On-Page SEO, and even comparing keywords.Ahrefs: This is a great tool for keyword research, site audit, site exploring, rank tracking, and content analysis. Based on these, one can make informed SEO decisions.Content MarketingContent is the key to the online success of every business. The SEO part of every business is solely based on content. Hence, it is necessary to ensure that whatever you post on your eCommerce website has rich content value.Here are some tools for generating content ideas!Hubspot: Hubspot is an excellent tool for getting content ideas. If you want to market your eCommerce tools via blogs, you can use the HubSpot Blog Topic Generator to get ideas about trending topics to write on. All it requires is some words related to the topic.Social Animal: Social Animal is a brilliant go-to tool for searching content ideas and content performance. Besides this, it also provides you insights into the length of the title and what will be the best time to publish the content.ConclusionIn conclusion, we can say that there are many tools that you can use to smoothen your eCommerce business. You can use the tools and software mentioned above to manage an eCommerce business of any size from anywhere. These will not only reduce your hassle but will also lead to an increase in conversion rate and revenue.
0 notes
Text
E-Commerce is one of the hottest markets in the world at present.As per Statista, retail eCommerce sales stood at $4.28 trillion in 2020. This figure is projected to rise to $5.42 trillion in 2022 and $6.38 trillion in 2024. This clears up one thing; if you have an eCommerce development service, whether small or big, you need to keep working on it.Now, handling an eCommerce venture is not a piece of cake. If you have experience, you know that handling shipping, product sourcing, managing inventory, order tracking, monitoring analytics may take more than the available time.To keep up with the cut-throat competition, you need to leverage some sophisticated eCommerce management apps. To help you get hands-on with the best ones, we have compiled a list. Check it out!Best Apps and Software to Streamline your eCommerce storeeCommerce management can be divided into various categories such as:MarketingOne of the critical elements of every business is marketing. It helps you attract new customers and retain the previous ones. So, to undertake the marketing process more manageable, you need to have tools like:Mailchimp: It is an excellent email marketing tool that to collect insights about your ongoing campaign. You can seamlessly integrate it with Shopify or WordPress and receive updates regarding your campaign on your mobile device. In addition, you can know about the opening and click-through rates easily from the Mailchimp app.Smile.io Rewards: Rewards are the best way to garner new customers and retain the old ones. This also indirectly helps in marketing your brand. To keep your customers coming back for repeat purchases, you need to allure them with benefits.Smile.io is the add-on that you can use with your Shopify account to provide customers with rewards for following the brand, sharing products on social networks, and more.Coupon Pop: The concept of Coupon Pop is a unique one as it provides the users’ coupons in return for their likes, follows, and emails.Inventory Management and ShippingTo keep up with the market demands, you need to ensure that your warehouse is stacked with all the necessary products.Checking it manually can be hectic. Hence, it would help if you use the following tools for managing the inventory of your eCommerce business.Zoho Inventory Management: The use of Zoho is not limited to just inventory management. It can help you undertake many other tasks such as create purchase orders, manage drop shipping, etc. You can even track every item of your inventory end to end with serial numbers and features. It can also assist you in making better business decisions via its accounting software and asset management tools.Veeqo: Veeqo is also one of the popular inventory management tools that helps you keep control over multi-channel inventory. You can sync it with multiple eCommerce channels. Besides this, it can help you forecast demand by analyzing past sales data.Easyship: It is an excellent tool that integrates worldwide couriers, taxes and duty charges, etc. Using Easyship, the businesses can offer worldwide delivery at reasonable costs.Product SourcingThis is one of the key things in every business. If you are beginning an eCommerce business, you need to plan to source the products you are planning to sell. There are many software to do that, such as:Maker’s Row: The web tool has a pool of manufacturers that supply over 2 million products of over 100,000 brands. You can search the required products on the website, talk to the supplier and get a quote for your purchase. Hence, it makes product sourcing super smooth for you.Oberlo: Oberlo is another app that allows you to source products from third-party drop shippers. Once you have selected your products, you can add them to your store and ship them directly to the customer. So, no hassle of storing them in a warehouse.Branding and DesigningKFC and McDonald’s are prime examples of branding!No matter how good the products are, popularity among the people is the key reason for business growth.
Hence, you need to make your business recognizable. Designing an excellent recognizable logo and using a branding kit is one way you can achieve popularity. Some of the tools that you can use for making graphics and logos are:Canva: A free online tool for creating graphics.Looka: An AI-powered platform for designing a logo that matches your brand vision.SEOTo keep your business growing, you need to make sure that you are always one step or more steps ahead of your competitors. And you can know this better by checking out your Google page rankings.To be in the eyes of the users means more sales and more revenue. For this, you need to use some advanced SEO tools for improving your organic reach and rank in the Google SERPs.SEMRush: It is a marketing SEO tool used for Domain-Domain analysis, checking On-Page SEO, and even comparing keywords.Ahrefs: This is a great tool for keyword research, site audit, site exploring, rank tracking, and content analysis. Based on these, one can make informed SEO decisions.Content MarketingContent is the key to the online success of every business. The SEO part of every business is solely based on content. Hence, it is necessary to ensure that whatever you post on your eCommerce website has rich content value.Here are some tools for generating content ideas!Hubspot: Hubspot is an excellent tool for getting content ideas. If you want to market your eCommerce tools via blogs, you can use the HubSpot Blog Topic Generator to get ideas about trending topics to write on. All it requires is some words related to the topic.Social Animal: Social Animal is a brilliant go-to tool for searching content ideas and content performance. Besides this, it also provides you insights into the length of the title and what will be the best time to publish the content.ConclusionIn conclusion, we can say that there are many tools that you can use to smoothen your eCommerce business. You can use the tools and software mentioned above to manage an eCommerce business of any size from anywhere. These will not only reduce your hassle but will also lead to an increase in conversion rate and revenue.
0 notes
Text
Best Invoicing Software

We dedicate ourselves to empowering the community with technology to enable their growth. POS that allows an easier checkout experience & seamless end of day and reconciliation operation and program for small businesses to fund their operations and fuel their growth plans. We help you improve your operations, grow revenue, and get more business insight. Our mission is to create the best possible restaurant guest experience by partnering with our customers to tackle the unique challenges of the restaurant environment - food court POS Software.
Restaurant management software, when done the right way, is a surefire way to ensure a restaurant success. Professional restaurant ordering management systems have redefined the way present day online food ordering works. They are smart, multi-dimensional and extremely user friendly. When choosing the best software for your restaurant, it's important to consider factors such as ease of use, price, data tracking abilities, and necessary hardware components - restaurant invoice software.
POS systems act as a computer/cash register hybrid, with the ability to process credit card payments, print receipts, display information on a user-friendly screen and operate as a service station. Make sure you know your business inside and out before purchasing a POS system. A modern system can be very costly and hence it should be able to handle your business volume and individual restaurant specifications to make it a worthwhile purchase. A highly really helpful open-source restaurant POS platform with loads of customization options. It can handle numerous forms of merchandise and you can simply modify the code to suit the restaurant’s operations utilizing it. Managing prospects is undoubtedly one of the difficult duties a restaurant can undertake. For more information, please visit our site https://billingsoftwareindia.in/restaurant-billing-software/
0 notes
Text
Open-Source Intelligence Market Competitiveness: Strategies for Sustainable Market Positioning

Strategic Insights and Forecasts: Open-Source Intelligence Market Leaders
The Open-Source Intelligence Size report is anticipated to experience significant growth in the coming years. As the world continues to recover from the pandemic, the market is expected to expand. The Open-Source Intelligence research not only highlights current industry standards but also reveals the latest strategic trends and patterns among market players. This research serves as an essential business document, aiding global market buyers in planning their next steps regarding the market's future trajectory.
According to Straits Research, the global Open-Source Intelligence market size was valued at USD 7715.2 Million in 2021. It is projected to reach from USD XX Million in 2022 to USD 55848.3 Million by 2030, growing at a CAGR of 24.7% during the forecast period (2022–2030).
The Open-Source Intelligence Report is an essential resource for business strategists, offering insightful data and analysis. It includes an industry overview, growth analysis, and historical and projected figures for cost, revenue, supply, and demand (where applicable). Research analysts offer a thorough description of the value chain and distributor analysis. This report provides comprehensive information to deepen understanding, broaden the scope, and enhance the application of the findings.
Get Free Request Sample Report @ https://straitsresearch.com/report/open-source-intelligence-market/request-sample
Leading Open-Source Intelligence Market include: -
Digital Clues
Alfresco Software Inc.
Octogence Tech Solutions Pvt. Ltd.
Palantir Technologies Inc.
Recorded Future Inc.
Google Llc
Maltego Technologies Gmbh
Offsec Services Limited
Expert System S.P.A.
Thales Group
The Open-Source Intelligence Market Report helps a wide range of businesses determine what their consumers truly want by doing extensive market research. When it comes to new products, every company owner wants to know how much demand there is, and this report is a great resource. Additional benefits include ensuring that the most recent market developments are covered. You may closely check key rivals and their company growth tactics by reading the Open-Source Intelligence market research. It also does an in-depth research for the years 2022-2030 in order to provide company owners with new business options.
This research also provides a dashboard view of prominent Organizations, highlighting their effective marketing tactics, market share and most recent advances in both historical and current settings.
Global Open-Source Intelligence Market: Segmentation
By Source
Media
Internet
Public and Government
Professional and Academic Publications
Commercial
Others
By Techniques
Text Analytics
Video Analytics
Social Analytics
Geospatial Analytics
Security Analytics
Others
By Security
Data Analytics
Human Intelligence
Artificial Intelligence Security
Content Intelligence
Network Analytics
By End-Users
Government Intelligence Agencies
Military Intelligence Agencies
Cybersecurity Organization
Law Enforcement Agencies
Financial Services
Private Specialized Business
Public Sector
National Security
Others
The report forecasts revenue growth at all the geographic levels and provides an in-depth analysis of the latest industry trends and development patterns from 2022 to 2030 in each of the segments and sub-segments. Some of the major geographies included in the market are given below:
The regions covered include:
North America (United States, Canada, Mexico)
Europe (United Kingdom, France, Germany, Russia)
Asia-Pacific (China, Japan, Australia, Indonesia)
Middle East and Africa (UAE, Iran, Syria, South Africa)
South America (Brazil, Peru, Chile, Colombia)
This Report is available for purchase on Buy Open-Source Intelligence Market Report
Reasons to Purchase This Report:
The Open-Source Intelligence Market report provides an analysis of the evolving competitive landscape.
The report offers valuable analytical insights and strategic planning tools to support informed business decisions.
Researchers highlight key market dynamics, including drivers, restraints, trends, developments, and opportunities.
The report includes regional market estimates and business profiles of various stakeholders.
It helps in understanding all significant market segments.
The report provides extensive data on trending factors that will impact market growth.
Research Methodology:
We employ a robust research methodology that includes data triangulation based on top-down and bottom-up approaches, along with validation of estimated market figures through primary research. The data used to estimate the Open-Source Intelligence market size and forecast across various segments at the global, regional, and country levels is sourced from the most reliable published materials and through interviews with relevant stakeholders.
About Us:
StraitsResearch.com is a leading research and intelligence organization, specializing in research, analytics, and advisory services along with providing business insights & research reports.
Contact Us: Email: [email protected] Address: 825 3rd Avenue, New York, NY, USA, 10022 Tel: +1 6464807505, +44 203 318 2846
#Open-Source Intelligence#Open-Source Intelligence Industry#Open-Source Intelligence Share#Open-Source Intelligence Size#Open-Source Intelligence Trends#Open-Source Intelligence Regional Analysis#Open-Source Intelligence Growth Rate
1 note
·
View note
Text
Industry trend|US IoT security label officially takes effect!
On September 9, the U.S. IoT Security Labeling Program officially came into effect.
The regulation aims to improve the privacy security of consumer IoT devices, enhance consumer confidence in the security of IoT devices, and provide consumers with more transparent product safety information. Previously, the FCC issued the "IoT Cybersecurity Labeling Report and Order" (Order) on March 15, 2024, which established the framework of the consumer IoT labeling program.

Image source: FCC
According to public disclosure, the main features of the program include:
Wireless consumer IoT products that meet the program's cybersecurity standards will display labels including the "U.S. Cyber Trust Mark" to help consumers make informed purchasing decisions, distinguish trustworthy products on the market, and incentivize manufacturers to meet higher cybersecurity standards.
The label will be accompanied by a QR code that consumers can scan to get easy-to-understand details about the product's security, such as how long the product is supported and whether software patches and security updates are automatic.

Image source: FCC
The voluntary program will rely on a public-private partnership, with the FCC providing oversight and approved third-party label stewards managing activities such as evaluating product applications, authorizing the use of labels, and consumer education.
Compliance testing will be handled by accredited laboratories.
Examples of eligible products may include home security cameras, voice-activated shopping devices, internet-connected appliances, fitness trackers, garage door openers, and baby monitors.
The establishment of the U.S. IoT Security Label and the official activation of the U.S. Cybersecurity Trust Mark are expected to significantly increase the transparency and security of IoT devices. As these rules take effect, all interested parties must become familiar with the new requirements and ensure compliance. The FCC's commitment to cybersecurity through this program marks a key step toward ensuring that IoT devices are protected from growing cyber threats.
What is the impact of the implementation of the US IoT security labeling program?
The industry believes that for the US IoT security labeling program, it is necessary to focus on wireless, Internet-connected consumer IoT products, including IoT devices and other components required for the network, such as network/gateway hardware, including application software and backend. It is worth noting that the FCC may expand the types and scope of IoT products in the future.
In addition, the FCC has also proposed a "National Security Declaration" rule for the IoT labeling program, which puts forward special requirements for devices involving national security. If the hardware, software or data in the device is related to certain high-risk countries (such as China, Cuba, Iran, North Korea, Russia and Venezuela), the manufacturer needs to disclose and ensure that its products do not contain any hidden vulnerabilities from these countries, and the data collected by the product will not be stored in these countries, nor will it be remotely controlled by servers in these countries.
The introduction of this rule may have a certain impact on overseas companies, especially those that export equipment to the United States. Manufacturers are required to pay more attention to the network security design of products and incorporate this plan requirements into product security design in advance, such as paying special attention to the standard content of NIST.
Consumers will also pay more attention to the safety performance of products when making purchasing decisions. As IoT devices become more prevalent and cyber threats increase, the legislation is seen as an important milestone in strengthening consumer privacy protections and improving device security.
Leading manufacturers have expressed support
Although the White House and FCC have made it clear that manufacturers and retailers can voluntarily choose to join the US Cybersecurity Labeling Program, at the same time as the program was released, leading manufacturers related to the home Internet of Things have basically announced their support.
According to a White House press release, the participating organizations on the day of the press conference included Amazon, Best Buy, Carnegie Mellon University, CyLab, Cisco, CSA, Consumer Reports, Consumer Technology Association, Google, Infineon, Information Technology Industry Council, IoXT, Keysight Technologies, LG Electronics USA, Logitech, OpenPolicy, Qorvo, Qualcomm, Samsung Electronics, UL, Yale University and August U.S., covering all links of the entire consumer Internet of Things industry chain, including manufacturers, retail platforms, monitoring and certification agencies, alliance organizations and universities, and are expected to push the program to a "quasi-mandatory" requirement that is widely accepted by the market.
Internationally, the US government will support the FCC to coordinate standards with allies and partners and seek mutual recognition of similar labeling work. For example, the United States has proposed to promote cooperation with the European Union to unify standards and has begun to contact Singapore's cybersecurity labeling program.
In January 2024, Anne Neuberger, the U.S. Deputy National Security Advisor for Cybersecurity and Emerging Technologies, announced that the United States had signed a cooperation agreement with the European Union on a "Joint Roadmap for Consumer Labeling Programs" to promote international mutual recognition of consumer IoT device security labeling programs, opening up the application and recognition of IoT security labeling programs on a larger scale around the world.
Cybersecurity labeling programs in other countries
According to Statista, by 2030, there will be more than 29 billion IoT devices in operation worldwide, which has attracted the attention of governments around the world to the security of smart devices. In addition to the United States, the European Union, the United Kingdom, Singapore, Germany and other places have introduced cybersecurity labeling programs for IoT products.
European Union
The European Union Cyber Resilience Act (CRA) applies to all digital products that are directly or indirectly connected to another device or network, including hardware, devices, software, applications, etc. The key requirements of CRA include:
Manufacturers must ensure that their products meet cybersecurity requirements throughout their life cycle from design to obsolescence.
Products must be able to receive security updates and effectively handle vulnerabilities for up to 5 years or the product life cycle (whichever is shorter).
Manufacturers need to provide clear product information and instructions to ensure that users can safely install, operate and use the product.
Manufacturers are obliged to report to the European Union Cybersecurity Agency (ENISA) within 24 hours of discovering actively exploited vulnerabilities in their products or any incidents that affect product security.
The CRA also provides for the classification of products at different risk levels, and important and critical products will be included in different lists, which will be proposed and updated by the European Commission. These lists will help determine which products require more stringent conformity assessment procedures.
The penalties for violating the CRA regulations can be very severe, including high fines. For example, violations of cybersecurity requirements and manufacturer obligations may be subject to fines of up to €15 million or 2.5% of global annual turnover in the previous fiscal year, whichever is higher.
The CRA is expected to take effect in the second half of 2024, and manufacturers will need to ensure that their products comply with the regulations and enter the EU market by 2027.
In addition, the EU's "Common Standard Cybersecurity Certification Scheme" launched in February this year marks that cybersecurity capabilities have become a key product strength and "market pass" for all digital products in the EU.
United Kingdom
The UK's "Product Security and Telecommunications Infrastructure Act" (PSTI) received royal assent in December 2022 and will officially come into effect on April 29, 2024. Key requirements include:
The use of common default passwords is prohibited.
Manufacturers are required to set up a public contact point for consumers to report security vulnerabilities.
Manufacturers must clearly state to consumers the minimum time frame for security updates.
Companies that violate the provisions of the PSTI Act may face significant penalties, including fines of up to £10 million or 4% of their global turnover, and additional fines of £20,000 per day for continued violations.
The Act applies to all manufacturers, importers and distributors that supply IoT products to UK consumers, requiring them to ensure that their products meet new cybersecurity standards. This includes smart homes/voice assistants, smartphones, webcams, wearable devices, IoT base stations and hubs, home automation devices, smart doorbells and alarm systems, etc.
Singapore
The IoT security labeling scheme launched in Singapore is called the "Cybersecurity Labelling Scheme (CLS)". It was initiated by the Cyber Security Agency of Singapore (CSA) and is the first cybersecurity standard scheme for smart home devices in the Asia-Pacific region.
The scheme includes four different security levels, distinguished by the number of stars:
Tier 1 – Basic security requirements, which developers can demonstrate through a declaration of conformity.
Tier 2 – In addition to the requirements of Tier 1, it also includes security requirements for the product lifecycle, which can also be demonstrated through the developer's Declaration of Conformity.
Tier 3 – In addition to meeting the requirements of Tier 1 and Tier 2, the developer must perform a software binary analysis of the product by a CLS-approved third-party laboratory (such as UL) to check for known vulnerabilities and common software weaknesses.
Tier 4 – To achieve the highest level, the product must undergo a thorough security assessment by a CLS-approved third-party laboratory, which will verify that the product complies with the requirements of ETSI EN 303 645 and conduct additional (mandatory) penetration testing activities.

Image source: CSA
The validity of the CLS label is related to the security update support period of the device, which can be up to 3 years. The program initially covered Wi-Fi routers and smart home centers because these products are more widely used and security issues have a greater impact on users.
In addition, Singapore has signed a mutual recognition agreement (MoU) with Finland and Germany to mutually recognize the cybersecurity labels issued by each other. This means that consumer IoT products that meet the cybersecurity label requirements of Finland or Germany will also be considered to meet the corresponding level requirements of Singapore's CLS.
Finland
Finland’s IoT cybersecurity labeling program is called “Cybersecurity Label” and is a voluntary labeling program initiated by the National Cybersecurity Center Finland (NCSC-FI) under the Finnish Transport and Communications Agency (Traficom).
The Cybersecurity Label is mainly aimed at consumer smart devices, such as smart TVs, smart bracelets and home routers. The label is awarded to connected smart devices or services that meet the information security requirements set by Traficom, including secure access control, default settings, transmission and storage of personal data, and secure ecosystem interfaces.
The Cybersecurity Label is based on the European Telecommunications Standards Institute (ETSI) EN 303 645 standard, which provides baseline requirements for information security requirements for consumer IoT devices.
Germany
Germany’s IoT cybersecurity labeling program is called “IT-Security Label” and is implemented by the German Federal Office for Information Security (BSI). It is also based on the ETSI EN 303 645 standard, a European standard for information security requirements for consumer IoT devices.
The labeling program requires product suppliers to make self-declarations and does not arrange for third-party certification, which may raise concerns about the authenticity of security information. However, the German market supervision department will check the security feature information declared by the manufacturer of the IoT product after the product is launched to ensure that the information on the label is consistent with the actual situation of the product. If the inspection finds discrepancies, the label will be revoked and the brand and product image will be damaged, which largely avoids the risk of manufacturer fraud.
China IoT Security Label Action Plan Officially Released
On April 18-19, 2024, the 2024 Spark Ecological Conference hosted by the China Academy of Information and Communications Technology was successfully held in Xiamen. At the meeting, the "China IoT Security Label Action Plan" was officially released.
The IoT Security Label Action Plan is a set of action plans proposed to address the pain points of cybersecurity attacks faced by consumer-grade IoT devices in my country, and to assign unique specific security labels to devices that meet certain cybersecurity certification standards, thereby ensuring that IoT devices are safe when accessing the network.
The action plan includes: proposing a new IoT security label system architecture, establishing a security label management mechanism, building a security label laboratory, developing a security label public service platform, developing a series of security label-related standards, and creating a batch of IoT security label application demonstrations, etc., including a complete IoT security label certification system.
As the world's largest exporter of consumer electronics products, my country's launch of the IoT security label program will be of great significance to protecting my country's IoT product export trade, cross-border data security, and national network security.
This paper is from Ulink Media, Shenzhen, China, the organizer of IOTE EXPO (IoT Expo in China)
0 notes
Text
10 Reasons to Choose Shopify for Your eCommerce Store
As an aspiring ecommerce entrepreneur, you have many picks when it comes to selecting an ecommerce platform. With such a lot of options accessible, the selection can appear overwhelming. However, one platform keeps to stand out above the rest for its mixture of capabilities, ease of use, and affordability – Shopify. If you’re trying to build a expert on line save with no need a technical historical past, Shopify affords an all-in-one strategy to get your enterprise up and strolling quick. Launching a Shopify save entails a comprehensive information of purchaser wishes, streamlined ordering strategies, and tailored solutions to cater to enterprise wishes. Consider searching for help from Shopify Website Developers for specialised in shopify functionalities and assist. Streamline your eCommerce journey—shopify experts india for professional, hassle-free solutions!

Why Choose Shopify as eCommerce Platform
1. Shopify Makes Building an Online Store Easy
Shopify provides an intuitive interface and drag-and-drop equipment to help you build a professional online store simply. You don’t want any technical understanding or net layout experience.
Simply pick from beautifully designed templates and personalize to suit your emblem. Add products, customize checkout, tweak themes – all without touching any code.
Shopify’s dashboard gives you an overview of orders, payments, transport, and extra so you can manage all components of your keep in one area.
Apps and integrations allow you to enhance your save by means of connecting the entirety from your POS gadget on your accounting software program. Over 2,000 apps to be had to help run your whole enterprise.
24/7 support approach help is there whilst you need it. Shopify authorities let you with any questions you have got about putting in or walking your on line save.
A at ease and scalable platform means you in no way should worry about keeping or updating servers, software program or protection systems. Shopify handles all of it. Empower your online business—hire a Shopify expert to build, optimize, and grow your store!
2. Shopify Offers Powerful Marketing Features for Growth
As an ecommerce business owner, you need tools to help you attract extra customers and enhance income. Shopify’s powerful advertising capabilities offer the whole lot you want to develop your store.
Email Marketing
Send stunning newsletters, promotions, and product updates to your clients with Shopify Email. Create automated workflows to onboard new subscribers and re-engage lapsed customers. See open prices, click-thru prices, and different metrics to optimize your email advertising and marketing campaigns.
Social Commerce
Sell your products without delay on social media structures like Facebook, Instagram, and TikTok. Sync your shop to create shoppable posts, testimonies, and live movies. Customers can checkout proper inside the apps.
SEO Features
Shopify makes it smooth to optimize your shop for engines like google like Google. Add meta titles, descriptions, and keywords to rank higher in effects. See how your store is acting with reviews on traffic sources, pinnacle keywords, and greater. Make facts-driven modifications to enhance SEO.
Abandoned Cart Recovery
Shopify can routinely attain out to customers via electronic mail or SMS textual content message in the event that they abandon their cart. Send a friendly reminder and consist of a reduction code to entice them lower back to complete their buy. Studies display over 60% of carts are recovered, leading to extra income. With a powerful set of commerce gear like those, Shopify affords the whole thing you want to draw new clients, power more income, and scale your ecommerce business. The advertising capabilities are strong but intuitive, permitting you to execute effective Digital Marketing campaigns simply. Achieve eCommerce excellence—shopify expert developer to unlock your store's full potential!
3.Shopify Provides Secure and Reliable Hosting
Dependable Infrastructure
Shopify’s hosting infrastructure utilizes multiple facts centers and a content material delivery community to offer speedy page loading times and maximum uptime in your keep. Their website hosting is absolutely managed, so that you do not want to worry about retaining servers or keeping software program updated.
Shopify’s platform has a established ninety nine.Nine% uptime file, meaning your keep could be to be had every time customers need to save. Their web hosting additionally includes unfastened SSL certificates to encrypt purchaser facts and permit secure checkouts.
Overall, Shopify’s organization-stage hosting and infrastructure provide you with peace of thoughts that your ecommerce keep may be walking consistently and securely. You can attention on growing your enterprise in place of dealing with technical information.
Four. Shopify Integrates With Top Shipping Carriers
Shopify offers integrations with important transport vendors like USPS, UPS, and FedEx, permitting you to get competitive transport fees. You can examine costs across exceptional vendors to discover the most affordable choice to your business and clients.
Shopify’s shipping functions simplify the fulfillment manner. You can purchase and print shipping labels immediately within your Shopify admin, and Shopify will routinely tune cargo information and transport statuses. Customers also get hold of monitoring records and updates to maintain them knowledgeable approximately the region and shipping of their orders.
Using Shopify Shipping, you have get entry to to discounted USPS rates if you ship extra than 50 orders per month. For high-volume shippers, Shopify’s Advanced Shipping can prevent as much as 90% on delivery fees.
Shopify integrates with 0.33-birthday party achievement offerings as properly in case you need to outsource transport and warehouse operations. No be counted how you choose to deliver your merchandise, Shopify gives answers to streamline the technique and decrease fees. Offering low cost, trackable transport options is fundamental to strolling a a hit ecommerce business, and Shopify makes it smooth to discover the nice answers in your shop.
Five.Shopify Offers Round-the-Clock Support and a Thriving App Store
Shopify’s 24/7 help and app shop provide valuable assets for your ecommerce enterprise.
24/7 Support
As a Shopify merchant, you've got get entry to to support 24 hours an afternoon, 7 days every week through phone, e-mail, and stay chat. The support team can help troubleshoot any troubles you come upon while constructing or jogging your save. They are available to stroll you through setup, offer steering on apps and subject matters, and address technical questions. Round-the-clock guide guarantees you get help whilst you need it, day or night.
Thriving App Store
Shopify’s app save includes over 4,000 apps that combine with your Shopify save. These apps can help beautify your save by adding new functions and functionality. Options encompass apps for advertising, customer support, inventory management, achievement, and greater. With a thriving community growing apps, you’re positive to discover gear to suit your precise commercial enterprise desires. The app shop makes it easy to customise your store and tap into additional sources to assist your business develop.
Between constantly-on aid and a sturdy app atmosphere, Shopify affords the infrastructure to construct a a hit ecommerce store. With these resources at your disposal, you have got the entirety you need to start, run, and grow your retail enterprise.
Also Read : Is Shopify Plus Worth Investing?
All You Need to Know Before Your Business Go Online on Shopify
0 notes