#proxmark
Explore tagged Tumblr posts
Text
youtube
Summary
🔐 Hack Overview: The presentation explores vulnerabilities in the Massachusetts Bay Transportation Authority's (MBTA) Charlie Card system, revealing techniques to reverse engineer, clone, and forge transit cards.
🛠️ Technical Steps:
Using NFC readers like the Proxmark III to analyze card data.
Reverse engineering using tools like mfoc and MF Cuck to extract encryption keys.
Implementing XOR operations to modify card data and create valid financial values.
📊 Key Findings:
Charlie Cards store monetary values directly on the card instead of in a centralized database.
Vulnerabilities in encryption and data verification allow manipulation of stored values.
Identified a systematic way to exploit the system for unlimited balance, capped by a signed 16-bit integer limit of $327.67.
🤝 Engagement with MBTA: The hackers responsibly disclosed the vulnerabilities to MBTA, resulting in a collaborative effort to improve security.
Insights Based on Numbers
📈 Financial Capabilities: Successfully created transit cards with balances up to $327.67, demonstrating the system���s lack of robust verification.
🔍 Key Discoveries: Found 16 default keys that facilitated breaking into the card's encryption.
0 notes
Link
Hardware for Pentesters: Flipper Zero, Hak5, Proxmark, USBKill, iCopy-X, O.MG Cables, Magic and Blank RFID Cards and more. Read the full article
0 notes
Text

All in One RF/HID reader/writer smaller then the ProxMark?!
A great and useful device for any physical penetration test or hardware hacking engagement.
#gainsec#hacker#kali linux#ethical hacker#cybersecurity#physical penetration test#rf hack#hid hack#proxmark#icopyx
2 notes
·
View notes
Text
Project Recap: Porgsaber


Of course, one of my very first goals was to make my own custom kyber crystal. While I'd love to eventually make a custom resin cast crystal (or even insert an RFID tag into a REAL gemstone crystal), ultimately this was the best (ie most delightfully ridiculous) choice to begin the new era of custom kybers.
Hattip to the amazing community on the Galaxy's Edge Discord #makerspace and #lightsabers channels. This idea came about from a silly convo about custom kybers and the ethics of what custom/third party items we'd like to make. We're sharing info about our projects in hopes of inspiring others to enjoy tinkering and learning more about interactive technologies with their own lightsabers too. :)
Recap:
Here's a short overview on how I made a working custom RFID kyber (porger!) crystal for my Elemental Savi's Workshop Lightsaber.
First and foremost: Do not try this at home. Results may vary. May contain peanuts. Please don't hurt yourself or your lightsaber. Be safe and read the safety instructions of any chemical, tool, or machine you use.
Second: This is probably not the best way to make a custom kyber crystal. Ideally, you'd want to order different, smaller RFID tags that are not glued into an existing enclosure.
Thanks to our previous research, we knew that any compatible EM4305 tag could be used to create an existing color kyber crystal (White, Red, Yellow, Green, Blue, or Purple), or one of the unreleased broken colors (Orange and Teal). By rewriting our new RFID's tag ID to match the colors we wanted, we would have a crystal-less kyber in need of an enclosure.
Note: Make sure you order REWRITABLE RFID tags.

The easiest compatible RFID tags to get ahold of quickly are these popular blue keyfob style tags. The catch is that they don't exactly look cool, or even really fit into the kyber holder on the saber hilt. RFID antennas are also very delicate, and did not survive Spork's attempt to remove them from their ABS plastic enclosure. I even tried soldering the antenna back to the chip, but no luck. (See above)
We had already ordered the correct solution of enclosure-less, smaller tags, but it was still weeks out away from delivery so... I figured it was a good time to try some science with all that extra waiting time.
Looking at the keyfob, it looked like the chip + antenna was being held in with either hot glue/adhesive or resin. I tried soaking it in both rubbing alcohol and mineral spirits to literally no effect, so I moved to acetone in hopes that the fob really was made out of ABS.
Ironically, the only glass containter I had was this one. Behold, the world's most dangerous glass of blue milk.
It immediately had effect, so I left it overnight. The next morning I was left with only a freed RFID chip, antenna, and some leftover glue.



I was as delightfully surprised as you are that the chip still worked and was readable using the Proxmark. Spork flashed my chip to display Orange, and now I was ready to make it a new home.
(I want to express again just how ridiculous this build was. I was in a rush trying to finish this before leaving town, so many, many shortcuts were taken.)
Being short on time, I downloaded a great existing Porg 3D model from Thingiverse to start from. Using Meshmixer, I removed the feet, hollowed out the model, and cut it in half. Initially the plan was to size the porg down smaller enough to fit through the 20mm clearance into the chamber, but no amount of quick tweaking could fit the 19.5mm RFID into a Porg that was still the correct size.
I knew I had to custom model another porg solution, but drastic times called for drastic measures: This is why my porger crystal has a glamorously stylish copper belt in the form of a very visible RFID antenna holding both parts together. Ha!
I 3D printed my two halves at a very low resolution for speed, did a quick acrylic drybrush of color, then literally scotch taped together and shoved it into my saber to test.

Somehow, against all odds, it works and it didn't even look half bad for a crazy proof-of-concept rush job. Concept is now officially proven, so I plan to make another higher resolution one with more patience once I'm back in town. :)
#custom#porgsaber#porger crystal#porgs#rfid#science#project recap#proxmark#projects#galaxysedge#savisworkshop#customlightsaber#disneyland#mods#starwarsland#batuu#lightsaber#completed projects
2 notes
·
View notes
Text
RFID/NFC Research
Tools
Proxmark3
NFC Proxy
RFID Module RC522 works with Arduino and RaspberryPI
Various NFC Tag reading apps on Android
Tactics
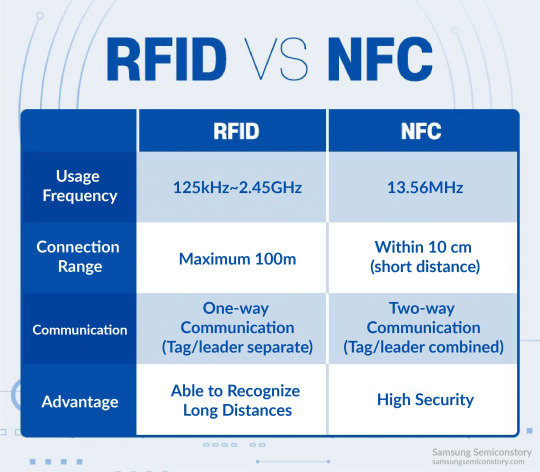
RFID/NFC is susceptible to cloning, spoofing/emulating, and sniffing attacks.
Cloning and Emulating RFID cards with Proxmark3
NFC Proxy/Sniffing/Fuzzing
3D printing your own RFID readers (video and slides)
Contactless Credit Cards
Techniques
Emulating Amiibos with a Proxmark3
0 notes
Text
#1yrago In 60 seconds, security researchers can clone the master hotel-room keys for 140,000 hotels in 160 countries

The Vingcard Vision locks are RFID-based hotel locks; at this week's Infiltrate conference in Miami, Tomi Tuominen and Timo Hirvonen from F-Secure will present a method for combining a $300 Proxmark RFID tool with any discarded key from a given hotel to derive the master keys that allow them to unlock every room in the hotel, a process that takes less than 60 seconds.
The researchers are exploiting longstanding defects in the Vingcard cryptographic implementations, defects that are even present on the magstripe-based Vingcard keys that predate the RFID keys (Vingcard has a new version that fixes the crypto, but there is a large base of legacy keycards in hotels all over the world).
The researchers informed the manufacturer about their work a year ago, and it has published updates for its customers, but the locks are not connected to the internet and can't update themselves, so it's up to hoteliers to see the notification, download the patch, and hire technicians to manually apply it to each lock in their hotels, one at a time.
The researchers have not released full details of their exploit in a bid to forestall thieves from using it to raid hotels.
https://boingboing.net/2018/04/25/hospitality-industry.html
12 notes
·
View notes
Text
Awesome Project Proposal v1
So I’ve decided that my proposal for the Something Awesome Project would be to working with the Proxmark 3 to clone RFID/NFC cards. https://github.com/Proxmark/proxmark3
Cloning RFID and NFC cards is an example of breaching physical security where someone’s access card can be stolen without the physical item being taken. If there is a lack of card identification security on the card, devices such as Proxmark 3 can be able to access the data inside the card, clone it into the device itself or another blank card and thus will have the same permissions as the original card.
Cards such as Opal cards will be harder to breach as inside the card, there exists a physical chips which act as a card identification security system and thus prevent opal cards from being cloned. However, UNSW cards could potentially be cloned as it is a Mifare card and hence I would want to take this opportunity to explore whether or not the card can be cloned and manually have its permissions changed such that I can access different buildings throughout the University. Currently, my card can only access the Computer Science building so I will be experimenting on my card and seeing whether or not I can clone it to another card such that I can access other buildings such as the Electrical Engineering rooms or the ASB building.
I was inspired to do this project as last year, a Proxmark 3 device was used to breach millions of hotel rooms. https://www.wired.com/story/one-minute-attack-let-hackers-spoof-hotel-master-keys/
It also had the potential of cloning prepaid cards although I am unsure if the same device was used.
While it is harder to create a master card that combines various cloned card permissions or clone an Opal card or credit card, it still serves a very practical usage especially in social engineering situations used by hackers to get inside buildings.
As I have never worked with a Proxmark 3, I am unsure whether or not I will be able to even clone the UNSW card or if I will be able to successfully set up the Proxmark 3 device (In case of bricking or hardware malfunction) and hence I have created my grading system:As per requested I have changed the criteria for the project.
Edit 1:
I will be attempting to provide a weekly blog post describing my experiences with the Proxmark 3 and research about various different types of RFID cards, it’s application in real life and if possible, a guide on how to clone it and a case study every week about the RFID card.
Fail- No attempt
Pass - Minimal attempt (a blog post about setting up the proxmark 3 device and an attempted blogs describing different types of RFID card)
Credit - Consistent blogs every week providing a blog about the research of RFID card and it’s application in real life.
Distinction - Consistent blogs every week providing an indepth analysis and explanation of RFID cards, it’s application in real life and a case study or potential case study for such use of a card. Some tutorials of how to clone the cards.
High Distinction- Same as distinction except analysis and explanation are of high quality and an attempt is made every week to clone each type of card. If they are not possible, a reason is provided why and an alternative solution is provided to clone the card.
1 note
·
View note
Text
[Media] ICopy-XS
ICopy-XS The ICopy-X is the next generation of RFID Cloning tool. Whether you're a pentester, researchers, locksmith, hobbiest or building manager, the iCopy-X makes cloning RFID tags rapid and easy. Built around the powerful Proxmark 3, the ICopy-X is a portable device specialised in the rapid cloning of RFID badges, capable of automatically reading, cracking and writing the vast majority of Low Frequency (125KHz / 134KHz) and High Frequency (13.56MHz) RFID tags on the market. 100% portable and pocket-sized, the iCopy-X is built with simplicity in mind. No cables required, no external computers or antennas. With its built in battery, you just pull the device out of your pocket, and you're ready to go. Designed to be intuitive, users control the device via its screen and navigation buttons to place a badge and start the desired operation. Buy online: 🛒 https://ali.ski/DpXlcF #RFID

0 notes
Text
04 de Octubre, 2021
Internacional
Vulneran pagos sin contacto con Iphones bloqueados

Una vulnerabilidad no reparada en Apple Pay, que los hackers pueden abusar para realizar un pago Visa no autorizado con un iPhone bloqueado aprovechando el modo Express Travel configurado en la billetera del dispositivo. Un atacante sólo necesita un iPhone robado en su poder. Las transacciones también pueden ser transmitidas desde un iPhone dentro de la bolsa de alguien, sin su consentimiento. El ataque de repetición y retransmisión del hombre en el medio (MitM), que implica eludir la pantalla de bloqueo para realizar un pago a cualquier lector EMV de forma ilícita.
E.@. El modus operandi se basa en imitar una transacción de puerta de tránsito mediante el uso de un dispositivo Proxmark que actúa como un lector de tarjetas EMV que se comunica con el iPhone de la víctima y una aplicación de Android habilitada para NFC que funciona como un emulador de tarjeta para transmitir señales a una terminal de pago.
Específicamente, aprovecha un código único, también conocido como Magic Bytes, transmitido por las puertas de tránsito para desbloquear Apple Pay, lo que da como resultado un escenario en el que, al reproducir la secuencia de bytes, el dispositivo Apple es engañado para autorizar una transacción no autorizada como si se hubiera originado en la barrera de los billetes, cuando en realidad, se ha activado por medio de una terminal de pago sin contacto bajo el control del atacante.
Al mismo tiempo, también se engaña al lector EMV para que crea que se ha realizado la autenticación del usuario en el dispositivo, lo que permite realizar pagos de cualquier monto sin el conocimiento del usuario del iPhone. Apple y Visa fueron alertados sobre la vulnerabilidad en octubre de 2020 y mayo de 2021, respectivamente, dijeron los investigadores, y agregaron que «ambas partes reconocen la gravedad de la vulnerabilidad, pero no han llegado a un acuerdo sobre qué parte debería implementar una solución».
Fuente
0 notes
Text
В Apple Pay нашли уязвимость, которая позволяет украсть любую сумму с привязанной карты Visa
New Post has been published on https://v-m-shop.ru/2021/09/30/v-apple-pay-nashli-uyazvimost-kotoraya-pozvolyaet-ukrast-lyubuyu-summu-s-privyazannoj-karty-visa/
В Apple Pay нашли уязвимость, которая позволяет украсть любую сумму с привязанной карты Visa

В Apple Pay нашли уязвимость, которая позволяет украсть любую сумму с привязанной карты Visa
30.09.2021 [16:11],
Николай Хижняк
Исследователи из британских университетов Бирмингема и Суррея обнаружили уязвимость в бесконтактной системе платежей Apple Pay, позволяющую снять любую сумму денег с привязанной к ней банковской карты без необходимости разблокировать iPhone. Эксперимен�� подтвердил, что метод работает только с банковскими картами Visa.

Источник изображения: Getty Images
Особенность системы Apple Pay заключается в том, что она подтверждает транзакцию только при определённых условиях. Чтобы платёж прошёл, владелец смартфона должен пройти аутентификацию и разблокировать iPhone одним из трёх способов: с помощью Face ID, Touch ID или пароля.
Однако исследователи обнаружили, что защиту Apple Pay можно обойти с помощью встроенной функции Express Transit, которая позволяет провести перевод средств с привязанной карты Visa без необходимости разблокировать устройство. Функция Express Transit была введена в систему Apple Pay в 2019 году из-за неудобной необходимости каждый раз разблокировать телефон для оплаты за проезд в том же общественном транспорте.
«В комбинации с картой Visa эту функцию можно использовать для обхода защиты заблокированного iPhone. Другими словами, злоумышленник может перевести любую сумму со счёта жертвы без необходимости разблокировать смартфон», — объясняют исследователи.
Для подтверждения своих слов специалисты опубликовали видео, на котором демонстрируется, как они получили платёж в размере 1000 фунтов стерлингов с заблокированного iPhone, не зная от него пароль.
youtube
Для этого они использовали мобильное устройство Proxmark, исполнявшего роль считывателя карт, который взаимодействовал с iPhone воображаемой жертвы и Android-устройством, исполнявшим роль терминала оплаты. Согласно опубликованной инфографике, метод специалистов работает по принципу «Человек посередине» (Man-in-the-Middle).

Эксперты отмечают, что на сегодняшний день эта уязвимость всё ещё актуальна, поэтому пользователям Apple Pay с картами Visa определённо стоит учитывать эту особенность.
«Наши обсуждения с Apple и Visa показали, что, когда обе стороны в отрасли частично виноваты в произошедшем, ни одна из них не желает брать на себя ответственность и внедрять изменения, оставляя пользователей уязвимыми на неопределённый срок», — прокомментировала специалист Андреа Раду (Andreea Radu) из университета Бирмингема.
Источники:
BBC
dailymail.co.uk
VMShop
0 notes
Photo

RFID Cloning handsets There is so much cheap technology out there these days for duplication of RFID access cards. Those who use the tech regularly know of the power of a proxmark but these hand held readers are cheap and easy for duplication of none encrypted cards. Wherever possible when using non encrypted card systems I'd recommend using dual factor readers so if the card is cloned it's unable to be used on high security areas without the pin also being present. #locksport #locksporter #rfidreader https://www.instagram.com/p/CPGaRskgykk/?utm_medium=tumblr
0 notes
Text

Espen, as a hacker and programmer, plus general computer engineer, has many things in his arsenal to help him with programming and hacking, but mainly hacking.
Laptop
First and foremost is his exceedingly hi-tech and powerful laptop, filled to the brim with all sorts of needed programs. It runs with great speed to outmatch any other laptop that isn’t the same brand and has the good ol’ quality graphics card. Sure, he doesn’t use it to game, but it’s worth thousands in dollars so... Why not make everything to perfection? It works only on fingerprint technology so only he can activate and use it and each program too requires his fingerprint to start working.
Pendrive
This small device shouldn’t be underestimated as, from the moment you plug it into any machine, it can cause absolute chaos. He hasn’t needed to use it as his job is always from a distance, but it is still kept on him at all times. With a great speed, it will connect to the device of choice and render it in full hands of Espen. From a distant machine, it will pick up the commands to either render the machine useless or grab all the data, ripe for the picking. If used from said distance it will send all info back to Espen before rendering itself useless. If to be picked up again it will store what’s needed as well as sending the information via transmission to an unknown location, just in case. It can also be programmed to merely shut a system down before shutting itself down and becoming nothing more than a husk.
Wifi pineapple
A portable wifi sort of system that, simply put, when used in public, can hack into any phone or tablet via someone’s internet, going completely undetected, perfect for information gathering and spying.
Ubertooth
A simple piece of kit that, like the wifi pineapple, can hack into any system if their bluetooth is enabled... Which can easily be enabled via the Wifi pineapple.
Proxmark kit
This device can read any radio information and direct it straight to Espen’s laptop. It can also clone radio waves and send them elsewhere
0 notes
Text
Using the Proxmark RFID reader, we scanned the kyber crystals we had and then dumped all their EEPROM data into a spreadsheet to look for any patterns.
RFID tags have a TagID that they send out to RFID readers to identify themselves. After scanned lots of crystals, we learned that there were multiple unique Tag IDs of each color. For example, instead of all Red Kybers having the same ID to identify as "Red", there was a "Red 1", "Red 2", etc.
By changing the Tag ID or Word 6 in the EEPROM word data, we could make a Red kyber crystal thing it was a Green one.
After doing most of our testing by repeatedly assembling then dissassembling lightsabers, we switched over to using a holocron for easy of quick testing.
Kudos to Spork for figuring out how Word 6 works, and actually trying to rewrite a kyber crystal. (Like most people, I had assumed it would have been write-protected and was just focusing on rewritting other FOBs. Haha.)
And a BIG thank you to volunteers who offered to lend us their crystals to scan to help with our research, and a special big hand to Nick for his help and excellent reference doc on the available voices on each crystal.




2 notes
·
View notes
Text
車鑰匙加密技術漏洞,逾百萬日韓車輛有被偷危機
英國和比利時的資安研究員之前發現,一款廣泛被日、韓車廠使用的免鑰匙啟動系統,駭客可藉加密功能的漏洞,模擬車主的車鑰匙解鎖汽車。涉及此漏洞的為 Texas Instruments 的 DST80 加密系統,影響 2008~2019 年間出廠的 Toyota、Kia、Hyundai 和特斯拉(Tesla)部分車款。

(Source:IACR)
研究人員指出,駭客只需利用一款廉價 Proxmark RFID 訊號收發裝置,靠近任何內建 TI DST80 的車鑰匙,就可以讀取密碼資料。駭客帶著儲存車鑰匙資料的 Proxmark 裝置,就能模擬車主的車鑰匙,解除防盜器和發動引擎將車開走。受影響的車款包括 Toyota Camry、Corolla、RAV4、Hiace、Yaris,Hyundai I10、I20、I40,Kia Ceed、Rio、Soul、Picanto,都是銷量甚高的大眾車款。
View On WordPress
0 notes
Text
Tesla S Modelinde Güvenlik Açığı

Tesla Model S modeli anahtarlık şifrelemesindeki yeni şifreleme güvenlik açığı , bilgisayar korsanlarının anahtarı klonlamasına ve arabayı çalmasına izin verir. Belçika üniversitesi KU Leuven'den bir güvenlik araştırmacısı olan Lennert Wouters ve ekibi, Model S'in anahtarlık şifrelemesinin nasıl kırıldığını Atlanta'daki Şifreleme Donanımı ve Gömülü Sistemler konferansında yeni bir teknikle ortaya koydu. Bir yıl önce aynı araştırmacı, Tesla otomobilindeki kritik güvenlik açıklarının, bilgisayar korsanlarının Model S'nin aracın kilidini açmak için anahtarsız giriş sistemini kırmayı başardığını göstermişti. Kısa bir süre sonra Tesla bu sorunu çözdü ve anahtarlığın yeni bir versiyonunu yarattı, ancak şimdi yeni anahtarlığı etkileyen başka bir hata daha farkedildi . Birincisine kıyasla, yeni saldırının radyo menzili daha sınırlıdır ve sistemi kırmak için öncekinden birkaç saniye daha fazla sürebilir.
Şifreleme Anahtarlarını Kırma
Wouters’a göre güvenlik açığı , Pektron adlı bir firmanın ürettiği anahtarlıkta, şifrelemeyi kırmak için gereken zamanı büyük ölçüde azaltan bir yapılandırma hatası nedeniyle ortaya çıkıyor” Önceki versiyonda, 40-bit şifreleme anahtarı, hackerlar tarafından anahtar erişimini sağlamak için kolayca kırılabilecek şekilde kullanılıyordu. Daha sonra Tesla ve Pektron anahtar gücünü 80 bit'e yükselttiler ki bu kırılması çok zor. Ancak bu bilgisayar korsanlarının yeni 80 bit şifreleme anahtarını iki 40 bitlik anahtara bölmelerine kapıyı açıyor. Wired'taki rapora göre , “Bu kısayol tuşu daha önce olduğundan iki kat daha zor buluyor. “Yeni anahtarlık ilk öncekinden daha iyi, ancak iki katkaynakla, temel olarak bir kopya çıkarılabilir” Saldırıyı gerçekleştirmek için, Proxmark ve Yard Stick One telsizleri ve bir Raspberry Pi minibilgisayarı, park edilmiş bir Tesla'dan gelen radyo sinyalini yakalamak için kullanılabiliyor ve en sonunda araç sahibinin anahtarlığı ile araç iletişimini bozmak için kullanılıyor. Araştırmacı, aracın kilidini açmak için fob'un şifreleme anahtarını iki saniyeden kısa bir sürede elde etmek için anahtar fobun cevabına şifrelemeyi kaydederek ve kırarak saldırıyı gösterir. Tesla sözcüsüne göre, ““ Anahtar klonlama tekniğinin herhangi bir hırsızlıkta kullanıldığına dair bir kanıt yok. “Hiçbir şey tüm araç hırsızlıklarına karşı önleyemezken, Tesla PIN'i kullanmak gibi bazı güvenlik geliştirmeleri gerçekleştirdi ve bu da ortaya çıkma olasılığını azaltıyor” Tesla, geçen ay tüm yeni Model S araçları için anahtarlıklara aynı düzeltmeyi uyguladı, bu nedenle o zamandan beri bir S Modeli satın alan birinin güncellenmesi gerekmiyor. Wouters, Model X ve Model 3 gibi diğer araçların etkilenmediğini söyledi. Tesla, bu kez, donanım yerine araçlara İnternet bağlantısı aracılığıyla anahtarlıklara kablosuz güncelleme yapılmasını önerdi. Lennert Wouters, bu yılın nisan ayında bu zafiyeti açıkladı ve Tesla, bu güvenlik açığını bildirdiği için hata ödülü altında 5.000 dolar ödüllendirdi. GB Hacker (adsbygoogle = window.adsbygoogle || ).push({}); Read the full article
0 notes
