Don't wanna be here? Send us removal request.
Text
Research Target: NATS Flight Plan Process
Out of Scope
I couldn't find any bug bounties or vulnerability disclosure policies for https://nats.aero/
Impact
On August 28 an outage in the UK ATC (NATS) delayed more than 1,200 flights at the end of a bank holiday weekend. Affecting more than 200,000 passengers.
Overview
NATS identified an issue with a flight plan processing sub-system called Flight Plan Reception Suite Automated – Replacement (FPRSA-R).
A small but important part of NATS’ overall air traffic control technical infrastructure, it was found to have encountered an extremely rare set of circumstances presented by a flight plan that included two identically named, but separate waypoint markers outside of UK airspace.
...in these circumstances, the system could not reject the flight plan without a clear understanding of what possible impact it may have had. Nor could it be allowed through and risk presenting air traffic controllers with incorrect safety critical information.
For flights that will operate within the European flight regions, they submit the [flight] plan into Eurocontrol. If the submitted flight plan is accepted, it will be sent to all relevant air traffic services who need to manage the flight. Within NATS the data is passed to FPRSA-R. The FPRSA-R sub-system exists to convert the data received from Eurocontrol into a format that is compatible with our flight data processing system.
0 notes
Text
CactusCon 2023 video index
Day 1 Track 1
6:31 Opening Remarks
8:08 Opening Remarks, Sounds begins to work
39:54 Scottish march with bagpipes
40:55 The Power of Community and How it Saved My Job by conf1ck3r
1:09:02 Egress Filtering in AWS, and other Sisyphean tasks by David Gilman
2:04:38 Hunting the Bian Lian Ransomware by Sean Pattee & Hallie Schukai
4:06:25 Keynote Introduction
4:08:47 Keynote: The New Challenges of Artificial Intelligence by Paulo Shakarian
5:12:35 Will AI Take My Infosec Job? By Andrew Cook
6:03:49 Windows Powershell for WMI by Kyle Nordby
6:53:26 How Expired Domains Lead to Facebook ATO by Jon Wade
Day 1 Track 2
0:00 Free Food Anyone? Wi-Fi Hacking and by Megi Bashi & Ryan Dinnan
13:37 Best Practices and Lessons Learned from Starting Up Mutiple OSINT Teams by Matt0177
1:18:03 A Peek inside an Adversary's Toolkit by Ryan Thompson
CANCELED Shodan OSINT Automation to Mass by me_dheeraj
5:13:46 Single Source of Truth: Documenting Incident Response by Casey Beaumont
6:14:00 Bridging the gap in the static and dynamic analysis of brinaries by mahaloz
Day 1 Track 3
0:00 Slides for the Exploiting IoT devices talk begins
2:30 Listen to the staff troubleshoot audio. Hi! We love you!!
9:30 Exploiting IoT devices through Physical Embedded Security by Ryan Jones
59:20 It's a Bird! It's a Plane! It's…A Script? By nuclearfarmboy
1:30:14 From Sticks and Stones to a Functional Forensics Lab by K Singh
4:33:13 Unmanaged Systems by Patterson Cake
5:27:45 Txt Me Bro: a text message phishing honeypot by Aftermath
5:57:20 Can Ducks Teach Us how to Share: What by Christian Taillon
Day 2 Track 1
0:00 IPFS, Dapps, & Blockchains by Edmund Brumaghin
40:10 PSA: Video Doorbells Record Audio, Too by Yael Grauer
1:10:41 Surveillance in your pocket by dnsprincess
1:41:00 Is Dead Memory Analysis Dead by Marcus Guevara
3:40:45 Keynote: Minimum Height Requirements by Sherrod Degrippo
4:40:47 CatusCon Annual Rock Paper Scissors Tournament
4:41:25 How to Job Hunt Like a Hacker! By BanjoCrashland
5:43:40 State of (Absolute) AppSec by @sethlaw & @cktricky
6:50:15 Getting Into The Reeds With Sensor Manipulation by Drew Porter
Day 2 Track 2
0:00 BloodHound Unleashed by n00py & ninjastyle82
50:40 Business Email Compromise by iHeartMalware
1:51:20 Worst of Cybersecurity Reporting 2022 by Yael Grauer & huertanix
4:53:30 Securing Your Home Network/Homelab by Maddoghoek77
5:52:00 PBR and Kittens by Jacob Wellnitz & James Navarro
6:51:40 Welcome to the Jungle: Pentesting AWS by ustayready
Day 2 Track 3
0:00 Hack your smart home first by Joey White
48:05 Building a Canarytoken to Monitor by Casey Smith & Jacob Torrey
1:47:00 I Came in Like a Wrecking Ball by iamv1nc3nt
4:48:10 Security Operations with Velociraptor by Eric Capuano & Whitney Champion
5:49:00 Sniper Incident Response by Chris Brewer
0 notes
Text
Research Target: Notam
FAA's Notice to Air Missions system
Notam is Out of Scope
Sadly Notam is out of scope for public research at the time of writing https://www.faa.gov/web_policies/vulnerability_disclosure_policy
Any research on Notam will have to be through OPSEC sources.
Impact
On January 11, 2023 more than 7,000 flights delayed when the Notam system ceased working.

Overview
Notam consists of:
Website with search function https://notams.aim.faa.gov/notamSearch/
Notam Distribution System (NDS) which provides M2M connections via the SWIM (System Wide Information Management) cloud
Notam API https://api.faa.gov/s/
Website with search function https://notams.aim.faa.gov/notamSearch/
Notam Distribution System (NDS) which provides M2M connections via the SWIM (System Wide Information Management) cloud
Notam API https://api.faa.gov/s/
0 notes
Text
Z-wave Research
Tools
VFuzz-public & YARD stick One - Z-wave fuzzer
Z-wave & YARD stick One - Z-wave capture and injection
Zniffer & ACC-UZB3-U-STA - Z-wave capture
Tactics
Network Overview
Authentication
Z-wave has an outdated and weak pairing method called S0. Using this pairing mode, the network key is transmitted with a fixed key of 0000000000000000. This network key can then be captured by a sniffer and used to attack nodes on the network. See Security Evaluation for more details.
Since 2017, Z-wave requires devices to use a more secure authentication called S2, which uses a Diffie-Hellman Key Exchange with an optional 5 digit code authentication. With S2 authentication, it should be impossible to get the network key.
However, the Z-wave is backwards compatible and susceptible to a downgrade attack (called Z-shave) and force the nodes to use the vulnerable S0 authentication.
Encryption
If nodes are using S0 authentication, then the network key can be captured via Zniffing.
If the nodes are using S2, then you'll need to join the PC controller (using an unmodified UZB3 dongle) to the network to get the network key. You will also need a nonce update, either single pre-agreed-nonce (SPAN) or multicast pre-agreed-nonce (MPAN) frame, to be able to decrypt packets. If you're in a hurry, a power-cycle will cause the device to issue a frame to resynchronize nonces.
Enumeration
The network is referred to by a "Home ID" with a value of 32bits. Each node is referred to by their "Node ID" of 8bits. The primary controller will have the Node ID of 1, and assigns the Node ID values for every other node on the network, typically sequentially. If there is a Node ID of 8, you can expect node values of 2-7 to be present. though devices can be assigned new node values when reset, leaving gaps in the addressing.
Neither Node ID (sending or receiving) or the Home ID is protected. Therefor traffic analysis can be used to identify the function of various nodes, and the nature of their encrypted messages. Though the encryption used is not susceptible to plain-text attacks.
Jamming
Jamming Z-wave requires multiple transmitters, or a single transmitter hopping quickly on each frequency being used.
US Z-wave
908.4MHz @ 9.6Kbps and 40Kbps
916Mhz @ 100Kbps
US Z-wave Long Distance are on 912MHz and 920MHz.
Jamming detection and response is dependent on implementation and should be tested.
Z-Wave detects jamming via End Device detection and Controller detection. The End Device expects to receive an ACK for each frame it sends. If an ACK isn't received the End Device may check the RSSI to see if its at expected values. If its determined that jamming is occurring, it may send RF Jamming notification to the controller, repeating at longer durations until an ACK is received.
The controller may sample background RSSI a few times a minute to determine if jamming is occurring. Additionally, it may detect jamming if it misses a heartbeat from a node that hasn't reported a low-battery status. If it detects jamming, then it may alert the user.
Known Vulnerabilities
See https://www.kb.cert.org/vuls/id/142629
Project Ideas
The Zniffer UI is a windows only tool. I should make a linux driver that can save captured packets into pcaps. Might violate EULA/TOS.
Create a jammer that hops both frequencies to test the detection and response of the z-wave devices.
Additional Resources
Zniffer User Guide
Super Zniffer - Modifying the Zniffer to attach an external antenna
Best Practices for Z-Wave Door Locks
How to OTA a co-processor via Z-Wave
0 notes
Text
Wifi Research
Tools
aircrack-ng Wifi Capture
kismet Wifi Capture
WiGLE Android Wardriving App
Hardware Tools
* Wifi Coconut
Tactics
Authentication
The four-way handshake
WPA3 handshakes
WEP Keys can be broken trivially, though depending on how long the key is not easily.
WPA authentication can't be crack but is susceptible to offline brute-force attacks with a large wordlist if the handshake is captured. To capture the handshake, the sniffer needs to be capturing either when a client connects to the AP, or deauth a client and capture the reauth
Configuring the AP to not broadcast its SSID doesn't make it hidden from attackers who are capturing packets. The clients announce what SSID they're looking for and the attacker can surmise the SSID from these clients.
<Add details about WPS>
Capturing Handshakes
The challenge with Wifi packet capture is the number of channels that APs can use. A single wifi interface can not listen to multiple channels. Instead, tools such as Airodump cycle through channels to collect a sample of packets, but this technique would only capture a fraction of a handshake.
To increase the reliability of capturing a handshake, fix the interface to only listen to a single channel or use multiple interfaces such as the Wifi Coconut which has an array of 14 radios.
Additionally, perform deauth attacks from an interface not being used to capture.
Open Wifi
Open wifi, commonly "secured" with portals are susceptible to Evil Twin Attacks.
Techniques
Krack Attack
WiFi deauth tool comparison
0 notes
Text
Bluetooth Low Energy Research
Tools
Software
Crackle Cracks BLE encryption <need to confirm it cracks Secure Connection>
nRF Connect for Android
Gattacker BLE man in the middle tool
BtleJuice BLE man in the middle tool. Has a nicer interface than Gattacker but both havent been updated in the past 5 years. BtleJuice depends on bluetooth-hci-socket which doesn't seem to work well with npm. <look into this and fix it>
blue_sonar provides rssi
blue_hydra Bluetooth Class and BLE wardrive tool
bleno node.js GATT server
bluepot honeypot
Hardware Capture
Sniffle & TI LAUNCHXL-CC1352P2 Dev Board Captures both Classic and BLE traffic
BtleJack & Bluefruit LE Sniffer I haven't used this
Ubertooth One I havent used this
Other Hardware Tools
Sweyntooth Vulnerability Scanner & nRF52840 Dongle. Could be used to extend and fuzz for MAC/PHY level vulnerabilities <;Look into this>.
Tactics
Bluetooth Basics
When a peripheral attaches to a central device, it stops advertising.
GATT (General ATTribute Profile)
Think of this as a REST Api, where GATT endpoints (called characteristics) are addressed either by their handle or UUID.
Bidirectional interfaces are done via a write/notify pair
Phone->device via write
Device->phone via notify
Each Characteristic has its own permission. Which include
Basic Read/Write
Authentication (Pairing)
Authorization (Implementation Specific)
Encryption (Bonding)
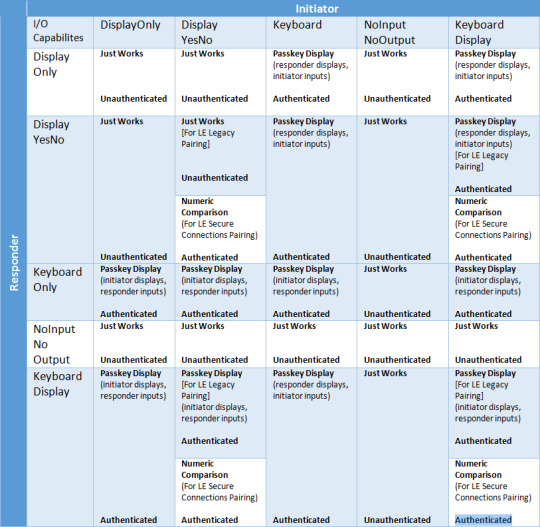
Pairing Process (Authentication)
Check for the following details from both the initiator and the responder
OOB & MITM Flags
I/O Capabilities
Secure Connection Flag
If both have the OOB set, then the pairing will use an OOB method. Otherwise they look to see if MITM protection is needed. If neither side is requesting MITM protection, then they'll use "Just Works". If at least one side requests MITM protection, then the following I/O capabilities is used along with the Secure Connection flag.
Bonding (Encryption)
After pairing, the two sides will exchange a Long Term Key (LTK) used to generate Session Keys (SK).
Key Strengths
Just Works - Always the same static key. Should not be used!
Passkey Entry - Only 20bits of entropy, can be cracked immediately. Should not be used!
Out of Band - Depends on implementation. Should be verified.
Secure Connections - Uses Elliptic Curve Diffie-Hellman. Very secure.
More than likely that the Bonding won't be used; either Legacy Pairing (weak) or Secure Connection (strong). Instead you'll be able to read or write directly to the characteristic without pairing. If they give a half-thought to security, they will implement their own encryption, without needing pairing or bonding.
Expect this in-house encryption to be worse than Secure Connection (and maybe even Legacy Pairing). Look for ECB mode, repeated nonce values, and other basic mistakes.
Bonding (Encryption) Attacks
Anything but a key generated from Secure Connection is likely to be crackable.
Spoofed the peripheral and tell the host it doesn’t have the key and get the OS do unauthenticated unencrypted communications
Spoof the peripheral and tell the host it doesn’t have the key to get the OS to unpair and repair with the spoofed peripheral
Bluetooth Addressing
Public The TXadd or RXadd bit is 0 Most Significant 24bits Company ID Least Significant 24bits Company Assigned
Random The TXadd or RXadd bit is 1
Random Address modes
Static: changes on bootup Most two significant bits set to 3 (11b) The least significant 46 bits are random.
Private Resolvable: can be found. Recommended they change every 15 minutes, and exchange and IRK (Identity Resolving Key) Most significant 2 bits are set to 1 (01b) Next significant 22 bits are random Least 24 bits are hash
Private Unresolvable: changes during runtime Most significant 2 bits are set to 0 (00b) Least 46 bits are random
Techniques
Accessing the Android BTsnoop from Windows
IMPORTANT: If you have the HCI log from one of the devices involved in the bluetooth communications, you do not need an external sniffer. Sniffing Bluetooth is difficult, having the HCI log makes things much easier.
adb shell su –c "'nc –s 127.0.0.1 -p 8872 –L system/bin/tail -f –c +0 data/misc/bluetooth/logs/btsnoop_hci.log'"
adb forward tcp:11233 tcp:11233
ncat 127.0.0.1 11233 > output.pcap
Setting up Bluetooth Virtual Sniffer in Windows
Download the Microsoft Bluetooth Test Package. It installs in C:\BTP. Look for btvs.exe found in C:\BTP\[version]\x86\
Simply running it will launch wireshark and everything is automagic
Emulation + Sniffing
If you can't control either endpoints, such as a device to device network, then use nRF Connect to emulate one endpoint, and then use the Android BTsnoop to observe how the other device communicates with it. Then use this knowledge to emulate the other device and repeat.
<add steps on how to completely emulate a BLE device using nRF Connect>
Wireshark Tips
Filters:
"btsmp" filters for pairing
"btatt" filters traffic only being sent over the air
"bthci_acl" filters for pairing and data sent over the air
"bthci_cmd.le_long_tem_key" filter shows device setting up BLE encryption
"btsmp.id_resolving_key" gets the IRK key for resolvable addresses
Find streams (hidden serial ports) and export them to json, and have a script parse the json
Assorted Tactics
Bluetooth Sniffing with UbertoothOne Its highly recommended that you use 3 Ubertooths (Uberteeth?) to avoid missing packets.
Using Multiblue <check to see if this is a useful tool>
Challenges
Despite the name, I did not find these CTFs useful for learning security attacks, but they are a known behavior for checking new tools against.
ble_ctf
ble_ctf_infinity
0 notes
Text
RFID/NFC Research
Tools
Proxmark3
NFC Proxy
RFID Module RC522 works with Arduino and RaspberryPI
Various NFC Tag reading apps on Android
Tactics
RFID/NFC is susceptible to cloning, spoofing/emulating, and sniffing attacks.
Cloning and Emulating RFID cards with Proxmark3
NFC Proxy/Sniffing/Fuzzing
3D printing your own RFID readers (video and slides)
Contactless Credit Cards
Techniques
Emulating Amiibos with a Proxmark3
0 notes
Text
SDR Research
Tools
GQRX - Spectrum Analyzer
RFanalyzer - Spectrum Analyzer for Android
Universal Radio Hacker - Investigate Wireless Protocols like a boss
ooktools - On-off keying is used extensively in IoT projects
fldigi - I'm not a big fan of fldigi, but its there for when you need to demodulate a common signal
Tools for more specialty purposes
Salamandra is a tool to find spy microphones
rpitx is a RF transmitter for Raspberry PI
Tactics
You don't need to learn DSP, or get your Ham license to explore radio signals. I didn't. You could even explore interesting signals such as vehicle key fobs without learning either, but learning these things will increase your understanding of signals and aid in your ability to go beyond the limitations of your tools.
Digital Signal Processing
The Scientist and Engineer's Guide to DSP was my introduction to DSP and I highly recommend it. Its free online and can be purchased in physical form.
Think DSP in Python is on my todo list. Also free online can can be purchased in physical form.
HAM Radio
Though I haven't taken the test yet. Covid was a major interruption in my plans, and I also plan to pass all 3 tests in one day. Using my personal test taking process, I would first start by reading No-Nonsense Study Guides.
Then take a pretest. Its important that you read all of the material before you take a pre-test as the goal is to retain knowledge, not just memorize a test. Most of the study should be reading/practicing the material, with few pre-tests as self assessments.
There are plenty of apps on Android (and I imagine IOS) that you can use. You need to get 74% to pass the exam, but I always shoot for 90%. If you get 90% on the pre-test, then move on to taking the actual exam.
If you didn't get 90% on the pre-test. The pre-test should be able to break down your score across various sections. Note the sections you're weakest in. From here, I would recommend switching over to the ARRL study guide as they are more detailed and only study the sections you're weakest end. When you complete all those sections, then take another pre-test and repeat until you're ready to take the exam.
Techniques
Accuracy
Radio is a science, but the tools that we can afford as hobbyists are not accurate. The three issues I face is drift, noise, and clock.
Drift occurs typically from your SDR getting hot and is a problem that grows across the session. To counter drift, you'll need to recalibrate your SDR to a Nation Weather Radio station. Find the frequency used in your area and tune to that frequency. You'll notice that you're probably a little off, this is the fault of your SDR not the National Weather Radio station. Set the offset of your SDR until your frequency of the station matches the one advertised. You'll then want to bookmark this frequency and check back to it every hour to insure that your SDR hasn't drifted.
Noise can interfere with interpreting weak signals (either distant, low powered, or both). To reduce noise and improve your signal collection, I'd suggest these guides for reducing on-site noise sources and external noise sources.
Signal Identification
Most signals are standardized or frequently used that dont require extensive analysis, but just identification.
The Signal Identification Wiki is a great place to start, and if that doesn't work, check out the sub-reddit r/signalidentification
This is an archived site that has a collection of digital signals that you could test your demodulation tools with.
Signal Analysis
Signal analysis is for those proprietary signals. As always, remember your ABC's.

Radio signals are fleeting. If you don't capture them, they may not repeat themselves. Don't worry about demodulating them at first. Capture the signals, and you can demodulate them at any time later.
Even if you're not able to record IQ data, for example you're listening to someone else's remote radio (there are a lot around the world on the internet), recording the audio which can be analyzed by tools such as fldigi.
I should add a lot more stuff here in the future.
The Signal Identification Wiki is a great place to start, and if that doesn't work, check out the sub-reddit r/signalidentification
This is an archived site that has a collection of digital signals that you could test your demodulation tools with.
Other Techniques
Using ooktools
NCC's RF testing Methodology
Wireless DoorBell Ringer and another Doorbell hack
Learn Morse Code
Project Ideas
Passive Radar with SDR
TDOA Transmitter Localization with RTL-SDRs
Other Links
No SDR, no problem! Use other people's radios with GlobalTuners.
#radio#signals#radio transmissions#sdr#ham radio#DSP#digital signal processing#signal analysis#technology
2 notes
·
View notes
Text
SIM Card Research
Tools
Smart Card Reader
SIM Card Reader
Osmocom SIMtrace 2 (software)
Osmocom PySim-Shell
SIMtrace Hardware Kit
Tactics
SIM research is broken down into three areas. The enumeration of the applets hosted in the SIM card, analyzing their behavior, and injecting a malicious applet.
Application Enumeration
There are two types of programs that run on a SIM card. First level applications are like the card's OS or a major component. These include USIM/ISIM, GSM, and Remote File Application. Second level applications are referred to as "applets" and include things such as micro internet browsers.
First level applications can be enumerated by the presence of an ADF (Application Dedicated File) directory. These are generally either only USIM, or USIM and ISIM together.
Second level applications can be enumerated by the messages sent to them via SMS via their TAR numbers. These TAR numbers are only 20bits and thus could be scanned, but I haven't seen a tool that does this....yet.
I don't believe second level applications have endpoints that reside on the SIM card filesystem.
Applet Behavior Analysis
SIM cards attack vectors include
Locally using the phone hardware to interact with the applets
Remotely via SMS
Adjacted via NFC
Local Interaction
A demonstration of an interactive applet behavior captured using SIMtrace.
youtube
The GSM Technical Specification referenced in this video can be found at https://www.etsi.org/deliver/etsi_gts/11/1111/05.03.00_60/gsmts_1111v050300p.pdf
SMS communication
SMS messages have four classes
Class 0 is displayed on the mobile screen without being saved. Known as a "Flash SMS", this class is often used for Emergency notifications such as floods, and Amber alerts.
Class 1 messages are stored in device memory or the SIM card. I feel I need to look into these a bit more
Class 2 messages carry SIM card data and must be transferred to the SIM card before sending an acknowledgement
Class 3 is forwarded from the receiving entity to the external device (the phone). This is the typical SMS texts people think of.
Class 1 and 2 messages can be sent to and from the sim card without the user's knowledge <;need to confirm>.
Each applet has one or more TAR (Toolkit Application Reference) values, which can be found in the Command Packet (SM) of the SMS User Data (TP-UD). Additionally, the SPI (Security Parameter Indicator) value is important as it specifies in any encryption (either non, DES, or 3DES) or digital signatures are used. Though encryption could be implemented in the applet and not the (U)SIM application.
If an applet requires signed communications, it may still be worth messaging that applet as it may reply with an error message, and that error message may be signed with the key you need to crack. Both DES and 3DES keys (with 1, 2,or 3 keys can be cracked if the app is vulnerable to a downgrade attack).
The following video has more details about attacking the SMS keys.
youtube
This blog post demonstrates using a SIMtrace to uncover SMS communications of an applet.
Two attacks (SIMjacker and WIBattack) used OTA SMS messages to attacks the browser in the SIM card. (See techniques below.)
Additionally, SMS messages can be sent via VOIP, and are perhaps easier to collect, if the phone can be forced to use that option.
NFC communication
NFC can communicate directly to the SIM card via Single Wire Protocol
Injecting Malicious Applets
A brief introduction of Security Domains
Typical a sim card's Issuer Security Domain is responsible for authorizing applets being loaded, usually preventing it. But cracking the keys used in the OTA SMS messages could lead to getting the KI key which all other keys are generated from, and being able to sign an applet that would get installed.
Techniques
SMS attack vector
SMS Fuzzing to discover SIM vulnerabilities
SIMjacker
SIM and SMS Basics
OTA messages
SIM Tester
Exploitation
An article covering the basics of WIBattack
Projects
Create a tool that enumerates a SIM card for applets via the 20bit TAR value and check for responses or errors.
Additional Resources
SIM Cards Demystified
Java Card Development Kit
GlobalPlatform (GPshell)
simhacks and Defcon 21 - The Secret Life of SIM Cards
SIM card emulator for Android
OsmoDevCall - Advanced SIM card topics
Interoperability Stepping Stones
Technical Specifications
Security mechanisms for the (U)SIM application toolkit
1 note
·
View note