#multi auth
Explore tagged Tumblr posts
Text
Passwordless and Passkeys
Ugh! Passwordless Photo by Anna Shvets Passwordless can seem to give some indigestion! 😂 Why? Because the name may suggest that it’s insecure, somehow. It has to be. Right? Nah! Well, not really. It depends on how I, the administrator, set it up and on the end users’ re-education on security. It also would mean an organization re-education as well. Multi-Factor authentication, YubiKey,…
View On WordPress
#Auth#Authentication#Conditional Access#EM+S#Endpoint#Enterprise Security#iOS#iPadOS#MFA#Mobile#Multi-Factor#OAuth#security
0 notes
Note
hello 👋🏼
first loving the twiyor 😌
second I have a tech question I was hoping you might be able and willing to answer: are the 'we send you a link to your email to log in instead of using your password' actually more secure or are businesses just being mean to me personally?
hope your day is kind 😊
Ok so Authentication (going to call it auth going forward) is a very large topic and there is some baseline info I want to convey before answering you question.
First, auth breaks down into 3 methods. Confirming what someone knows, confirming what someone has, confirming what someone is.
What you know: this is the traditional password method, do you remember your password you made for us? Do you remember your username? great you can get in if you know those. Stealing these creds is very straight forward, you either guess until you are right or you steal them from where someone has them stored/written down. This is why you should NEVER store your password in a browser and use a password manager instead. I would rather see people write passwords on post-it notes then store them in Google Chrome or Edge. Seriously, it is incredibly easy to steal passwords from Chrome.
What you have: have ever been asked to put an MFA pin into a phone app? that's this method, they are putting predictable generated numbers on your phone that you can then turn around and use to prove you are in physical possession of your phone. This is much more difficult to steal and usually requires physically accessing a phone or infecting it in some fashion to steal the generation algorithm. PS: If a site uses a text message instead of an app to send a pin that is less secure because SIM duplicating is easier then both the above methods for theft (i dont know the details on how to sim dup but I know no good security team takes sms pins seriously)
What you are: This is stuff like Apple's face id, windows hello, finger scan. Anything that is unique to your physical body that can be scanned to confirm who you are. This is either incredibly difficult or super easy to break depending on how the program is written. for example Face ID had an issue where it could not differentiate between particular ethnicities, also someone (the police) can just hold your phone up to force the unlock. This is usually a good method to use in conjunction with one of the others to make Auth more difficult.
So which one is better? Well each one has its pros and cons which means the most secure method is using more then one. This is called Multi Factor Authentication or MFA for short.
So lets go back to your question, is getting a login link more secure then say remembering a password. Well how secure is access to your email? if your email just requires a username and password to get into, then it is the same security level.
If you have your email setup with MFA where you need to password and pin into it then it is probably more secure then some random sites username password pair.
Also we need to ask questions about the links themselves, do you get the same link each time or is a new one created each request? How are they generated? how long until a link expires? is the link email sent via TLS? Which version of TLS? How are they stored or Are they stored? Is link generation predictable, if I had enough info could i just make my own links for any user?
Honestly I think the biggest benefit of this auth method happens on the website side and less the end user side. This requires less development to create, also they do not need to figure out how to store and keep your passwords, and if they get hacked there are no passwords to be stolen since they literally don't use them. Having passwords stolen is when law enforcement needs to get involved (Law enforcement needs to be contacted in the event any Personally Identifiable Information or PII is stolen). So if they do not use passwords that is one less PII they have in their possession.
Overall passwords are shit and anyone trying to make an effort to not use passwords or to not allow just passwords is at least making an effort to have a better security posture. But if it is actually more secure really depends, passwordless is new territory for a lot of people so its going to have growing pains.
hopefully this answers your question! if you want more clarification let me know.
Oh and Spy Family is life

64 notes
·
View notes
Text



Auth MISSONI - White Green Multi Women's Sweater ebay Brandear
2 notes
·
View notes
Text
Custom vs. Ready-Made Cryptocurrency Exchange Clone Software

1. Introduction
The cryptocurrency market is booming, and everyone wants a piece of the action. With digital currencies now a mainstream investment, building your own crypto exchange has never been more tempting. That’s where cryptocurrency exchange clone software comes into play.
Entrepreneurs face a critical decision early in their journey: Should you go with a custom-built exchange clone or a ready-made solution? Let’s break it down.
2. Understanding the Basics
What is Custom Exchange Clone Software?
This is a tailored solution built from scratch—or heavily modified from a base model—to meet your specific business requirements. Think of it like designing your dream house.
What is Ready-Made Exchange Clone Software?
This is a pre-built solution that's plug-and-play. It's quicker to launch, already tested, and usually comes with essential features out of the box. It's like buying a furnished apartment.
3. Key Differences Between Custom and Ready-Made Solutions
Development Time
Custom builds take months. You’re building it brick by brick. On the flip side, ready-made clones can be launched in days or weeks.
Cost Implications
Custom software is expensive. It demands time, skilled developers, and resources. Ready-made clones are more budget-friendly, ideal for startups.
Scalability
Custom platforms offer better long-term scalability. You can optimize every feature. Ready-made ones may hit limits sooner, depending on architecture.
Customizability
No surprises here—custom builds offer full flexibility. With ready-made software, you're often limited to what's already built unless you pay more.
Maintenance and Support
Custom systems require dedicated teams for support. Ready-made solutions often come with support packages from the provider.
4. Benefits of Custom Crypto Exchange Clone Software
Full Control Over Features
Want a dual-auth system or multi-chain wallet? No problem. You decide what stays and what goes.
Tailored User Experience
From UI to transaction flows, everything aligns with your vision.
Branding Flexibility
Want to be the next Binance or something completely new? A custom platform gives you that freedom.
5. Benefits of Ready-Made Crypto Exchange Clone Software
Faster Time-to-Market
Speed is king. Launch fast, test market fit, and scale later.
Lower Upfront Investment
You don’t need millions. Just pick a good package and you’re live.
Proven Market Performance
These clones are often modeled after successful platforms like Coinbase or Kraken—battle-tested and reliable.
6. When Should You Choose Custom Clone Software?
For Unique Use-Cases
Need a feature-rich hybrid exchange or one with cross-chain trading? Go custom.
When Building a Long-Term Brand
If you're playing the long game, invest in infrastructure that supports it.
7. When Should You Choose Ready-Made Clone Software?
For MVPs and Startups
Got an idea and want to test it fast? Go with a ready-made solution.
When Budget Is Limited
Start learning. Prove your model. Upgrade later.
8. Security Comparison
Security Features in Custom Builds
Custom solutions let you build top-tier protection: cold wallet integration, multi-sig wallets, anti-DDoS—all tailored to your needs.
Are Ready-Made Solutions Vulnerable?
Not necessarily. Good providers offer decent security—but you’re tied to their protocols unless you pay to upgrade.
9. Regulatory Compliance
Whether it’s GDPR, AML, or KYC laws, both models can be designed to comply. The difference lies in flexibility and future-proofing, which custom builds excel at.
10. Integration with Third-Party Tools
Your exchange won’t work in isolation. You need payment processors, KYC/AML services, and maybe even AI-based analytics. Custom builds allow seamless integration. Ready-made? Sometimes limited.
11. Automation & Trading Bots
Whether you're eyeing institutional traders or retail users, automation is non-negotiable. Integrating the best automated crypto trading platform boosts user retention and trading volume.
12. Choosing the Right Development Partner
Don’t just Google “crypto exchange development company.” Look for experience, a robust tech stack, client reviews, and ongoing support. A great team is half the battle won.
13. Real-World Examples
A startup in Europe launched a ready-made clone to test the waters—within 6 months, they pivoted to custom software after raising capital.
A fintech brand in Asia went custom from day one. Higher costs upfront, but they now lead in the regional digital currency exchange market.
14. Which One Is Right for You?
If you want to move fast and test your business idea, go with a ready-made clone. If you’re planning for long-term domination, custom is the way to go.
15. Conclusion
There’s no one-size-fits-all in the crypto world. Your choice between custom and ready-made cryptocurrency exchange clone software depends on your goals, budget, and vision. So, what kind of exchange do you want to build?
#technology#crypto exchange clone development#wazirx clone software#bitcoin#crypto market#cryptomarket#crypto trading#crypto
1 note
·
View note
Text
Plotting call

Hiii now that Shade is here I'm looking for some threads to pick up!! Dm here, or on discord @ kuromallow! Shade is an unaffiliated faculty member.
Mission Board (requires beagle):
Distress Signal: I'd love for Shade to have a peppy, gung-ho partner who's much more worried than she is. At least, at first. Convince her its a good idea to meet in this shady location at midnight.
Non-Mission Board:
Outrealm Gate: I'd love a chance to show just how unbothered Shade is when faced with no environments. Well, at first.
King of the Hill: Instructor Shade will supervise your trials and tribulations!! I'm open to multi muse this one too (EX: shade + two students).
Mittelfrank Opera (Auth+1): Let's join the production together! While Shade would love to be the lead actress, or perhaps some other beautifully dressed character, it might hurt to admit she's better in an overseeing role.
3 notes
·
View notes
Text
I read and took notes on basically what I thought each article was about, though I 100% recommend printing this thing up and taking a pen/pencil to it yourself.
Preamble: Marks the precedents upon which this big guy was built.
Part I: The Rights, Protections, and Limitations Described
Article 1: Definition of a child
Article 2: Rights regardless of "race, color, sex, language, religion, political/other opinion, national or ethnic or social origin, property, disability, birth or other status."
Article 3: Bests interest of child served first
Article 4: Countries will work within resources but should pay consideration to economic, social, and cultural rights.
Article 5: Respect the community/environment of the child
Article 6: Right to life and development
Article 7: Right to their name and nationality. Registration upon birth.
Article 8: Right to preservation of identity
Article 9: Right to maintain contact with both parents
Article 10: Right to reunite with birth family across borders
Article 11: No cross-country restrictions on child returns. You can't just hold a kid back from going back for no reason.
Article 12: Right to self-advocate in a court of law
Article 13: Right to freedom of expression
Article 14: Right to create and develop their own thoughts and identities
Article 15: Right to assembly and peaceful protest
Article 16: Right to privacy and reputation
Article 17: Right to diverse and educational material (this may be what you want to use against book banning???)
Article 18: Recognize that parents have the primary job of educating and developing the child. Provided services are meant to help.
Article 19: Protection of children from harm
Article 20: Right to alternative care when taken from parents
Article 21: Right to adoption practices in the best interest of the child
Article 22: Rights of children refugees, including a right to reunite with their family, if possible
Article 23: Rights of children with disabilities
Article 24: Rights of children to health care
Article 25: Right of State Parties to evaluate environments of children who have been adopted
Article 26: Right of children to Social Security
Article 27: Right to a standard of living for the child
Article 28: Right to education (which, hell, this is REAL INTERESTING given what's been going on ffs)
Article 29: Responsibility of education and educators to children
Article 30: Protections of and for multi-cultural children
Article 31: Right of children to play and have leisure
Article 32: Working rights and limitations for children
Article 33: Protections for children from drugs
Article 34: Protections for children from engaging in sex acts or being sexually exploited
Article 35: Protection for children from child trafficking
Article 36: Protection for children from unfair legal practices
Article 37: Rights for children in the judicial system
Article 38: Limitations on child soldiers
Article 39: Rights for children to social rehabilitation after traumatic events, which are listed
Article 40: Rights and protections for children in a courtroom
Article 41: Establishment that if the country in question has something better for their kids, the country should follow the better guidelines with respect to the best interests of the children.
Part II: Spreading, Gathering, and Acting On Information
Article 42: Make this document available and spread it everywhere
Article 43: Establishment, Election, Terms of Committee on the Rights of the Child
Article 44: Submission and Review of participating countries' progress
Article 45: Committee influence
Part III: Official Documentation
Article 46: Signing
Article 47: Can be ratified
Article 48: Stuff can be added
Article 49: When this goes into effect
Article 50: Amendments
Article 51: Limitations and Recalls
Article 52: State Party Denouncements
Article 53: All complaints/notes go to the Secretary-General at time of this
Article 54: Translations available and authentic
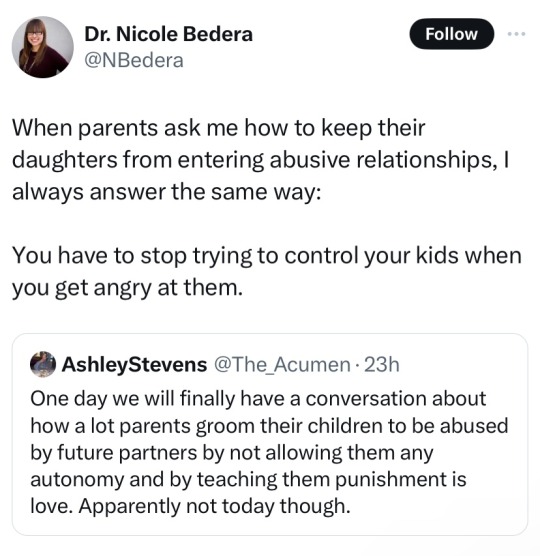
59K notes
·
View notes
Text
MBW RCM Patient Access: Insurance Verification & Prior Authorization

Efficient patient access is the cornerstone of a successful revenue cycle. At MBW RCM, we understand that the first step in the revenue cycle — verifying insurance and obtaining prior authorizations — can determine the speed and accuracy of reimbursement. Our Patient Access Solutions are designed to minimize claim denials, reduce administrative burden, and create a seamless experience for patients and providers alike.
1. Why Patient Access Matters in Revenue Cycle Management
Patient access is more than just registration. It includes every process that occurs before a patient visit or procedure, directly affecting revenue integrity. When insurance verification or prior authorization is missed, delays, rework, and denied claims become common, impacting both cash flow and patient satisfaction.
2. Comprehensive Insurance Verification Services
MBW RCM offers end-to-end insurance eligibility verification services that check a patient’s coverage, copays, deductibles, and policy limitations in real-time. By integrating advanced tools and payer-specific protocols, we help clients avoid delays and improve clean claim rates from the start.
Explore more on our Revenue Cycle Mid-Cycle Services that complement patient access functions.
3. Streamlined Prior Authorization Management
Obtaining prior authorization can be time-consuming and complex, especially for high-cost procedures. Our team of trained professionals works with all major payers to ensure the right documents and clinical codes are submitted upfront. We track every authorization status and follow up aggressively to meet procedure timelines.
4. Specialty-Focused Authorization Expertise
Whether you’re a cardiologist, oncologist, or OB/GYN specialist, MBW tailors its prior authorization process based on your specialty’s coding patterns and payer rules. This specialization helps reduce denials related to medical necessity and improves overall RCM efficiency.
5. Technology-Enabled Pre-Visit Workflow Automation
We incorporate robotic process automation (RPA) and AI tools to verify benefits, validate referrals, and even flag pre-certification issues. This reduces manual effort, shortens turnaround times, and increases throughput, especially in hospital and urgent care environments.
6. Real Results: Case Studies That Prove the ROI
One of our multi-specialty clients saw a 40% reduction in prior auth denials within 60 days of onboarding. In another case, eligibility errors dropped to under 2% — all thanks to MBW’s proactive patient access protocols. These real-world improvements reflect our commitment to measurable impact.
Improving patient access with robust insurance verification and prior authorization services isn’t just about administrative accuracy — it’s about protecting revenue and delivering a better patient experience. MBW RCM helps healthcare providers take control of this critical first step in the revenue cycle.
Discover how our full suite of Patient Access Services can support your revenue goals. Or connect with us to learn more about specialty-specific RCM solutions tailored to your practice.
0 notes
Text
Fuldautomatisk Playwright-test med Microsoft MFA-login
At skabe en fuldt automatiseret Playwright-test, der kan håndtere Microsoft Multi-Factor Authentication (MFA), er en udfordring, da MFA er designet til at forhindre netop automatiseret adgang. Standard-MFA-prompter, såsom notifikationer på en telefon, kræver manuel interaktion. Den mest robuste og udbredte metode til at opnå fuld automatisering er ved at anvende Time-based One-Time Passwords (TOTP) i dine tests.
Denne metode indebærer, at du konfigurerer en testkonto til at bruge en authenticator-app og derefter bruger den hemmelige nøgle (secret key) i din Playwright-test til programmatisk at generere de nødvendige engangskoder.
Her er en trin-for-trin guide til, hvordan du kan implementere dette:
Trin 1: Konfigurer din testbrugerkonto i Azure AD/Microsoft
Før du kan automatisere login-processen, skal du konfigurere den testbruger, din Playwright-test skal bruge.
Opret en dedikeret testbruger: Undgå at bruge personlige eller produktionskonti til automatiserede tests. Opret en ny bruger i dit Azure Active Directory (Azure AD) eller din Microsoft-konto, som udelukkende skal bruges til testformål.
Aktiver MFA for brugeren: Gå til brugerens sikkerhedsindstillinger. Dette findes typisk under "Security info" på https://mysignins.microsoft.com/security-info.
Tilføj "Authenticator app" som login-metode:
Vælg at tilføje en ny metode og vælg "Authenticator app".
Vigtigt: Når du bliver præsenteret for en QR-kode, skal du vælge muligheden for at indtaste en hemmelig nøgle manuelt (ofte et link som "I want to use a different authenticator app" eller "Can't scan image?").
Kopiér og gem den hemmelige nøgle (Secret Key): Dette er en lang streng af tegn. Denne nøgle er afgørende for din automatiserede test, så opbevar den sikkert, f.eks. i en secret manager som Azure Key Vault eller som en environment variable i dit CI/CD-system. Del aldrig denne nøgle i din kodebase.
Bekræft opsætningen: Brug en authenticator-app (som Google Authenticator eller Authy) til at scanne QR-koden eller indtaste den hemmelige nøgle for at generere en kode og fuldføre opsætningen. Dette sikrer, at nøglen er korrekt.
Gør TOTP til standardmetode: Hvis muligt, konfigurer brugeren til at foretrække en kode fra en authenticator-app frem for en push-notifikation.
Trin 2: Opsæt dit Playwright-projekt
I dit Playwright-projekt skal du installere et bibliotek, der kan generere TOTP-koder. Et populært valg til Node.js er otpauth.
Installer otpauth: npm install otpauth
Gør den hemmelige nøgle tilgængelig for din test:Brug environment-variabler til at håndtere din hemmelige nøgle og brugeroplysninger. Opret en .env-fil i roden af dit projekt (husk at tilføje .env til din .gitignore-fil for at undgå at committe den)..env-fil eksempel: TEST_USERNAME="[email protected]" TEST_PASSWORD="din-adgangskode" MFA_SECRET="den-hemmelige-nøgle-fra-trin-1"
Trin 3: Skriv din Playwright-login-test
Nu kan du skrive din test, der bruger oplysningerne til at logge ind. Det anbefales at adskille login-logikken i en separat "setup"-fil, som Playwright kan køre før dine faktiske tests. Dette gemmer den godkendte session, så dine tests kan genbruge den uden at skulle logge ind hver gang.
Eksempel: global.setup.ts
import { test as setup, expect } from '@playwright/test';import * as OTPAuth from 'otpauth';import * as dotenv from 'dotenv'; // Indlæs environment-variablerdotenv.config(); const authFile = 'playwright/.auth/user.json';
setup('authenticate', async ({ page }) => { const username = process.env.TEST_USERNAME!; const password = process.env.TEST_PASSWORD!; const mfaSecret = process.env.MFA_SECRET!;
// Valider at alle nødvendige variabler er satif (!username || !password || !mfaSecret) { throw new Error('Test user credentials or MFA secret are not set in environment variables.'); } // Naviger til login-sidenawait page.goto('https://login.microsoftonline.com'); // Eller den specifikke login-URL for din app// Indtast brugernavnawait page.getByPlaceholder('Email, phone, or Skype').fill(username); await page.getByRole('button', { name: 'Next' }).click();
// Indtast adgangskodeawait page.getByPlaceholder('Password').fill(password); await page.getByRole('button', { name: 'Sign in' }).click();
// Håndter MFA-promptenawait expect(page.getByText('Verify your identity')).toBeVisible({ timeout: 10000 });
// Generer TOTP-kodenconst totp = new OTPAuth.TOTP({ issuer: 'Microsoft', label: 'AzureAD', algorithm: 'SHA1', digits: 6, period: 30, secret: mfaSecret, }); const code = totp.generate(); console.log(Generated OTP code: ${code});
// Indtast den genererede kodeawait page.getByPlaceholder('Code').fill(code); // Nogle gange skal man klikke på en "Verify" eller lignende knap// Dette kan variere baseret på jeres specifikke Azure AD-opsætningawait page.getByRole('button', { name: 'Verify' }).click();
// Håndter "Stay signed in?" prompten// Det er ofte bedst at vælge "No" i en automatiseret kontekstawait page.getByRole('button', { name: 'No' }).click();
// Vent på at blive fuldt omdirigeret og logget ind// Erstat URL'en med en side, du forventer at se efter et succesfuldt loginawait expect(page).toHaveURL(/din-app-start-url/);
// Gem den godkendte tilstand (cookies, local storage etc.)await page.context().storageState({ path: authFile }); });
Trin 4: Konfigurer Playwright til at bruge den gemte session
I din playwright.config.ts-fil skal du nu konfigurere dine testprojekter til at afhænge af din setup-fil.
playwright.config.ts eksempel:
import { defineConfig, devices } from '@playwright/test'; export default defineConfig({ // … andre konfigurationerprojects: [ // Først, kør setup-filen for at logge ind { name: 'setup', testMatch: /.*.setup.ts/ },// Derefter, kør dine tests med den gemte session { name: 'chromium', use: { ...devices['Desktop Chrome'], // Brug den gemte 'storageState' for at starte som logget indstorageState: 'playwright/.auth/user.json', }, dependencies: ['setup'], }, // ... andre browsere
],
// … andre konfigurationer });
Alternative og supplerende strategier
Brug af testkonti uden MFA: Den simpleste løsning er at have et dedikeret testmiljø, hvor MFA kan deaktiveres for specifikke testbrugere. Dette kan opnås gennem Conditional Access-politikker i Azure AD, der f.eks. undtager brugere fra MFA, når de logger ind fra en kendt IP-adresse (f.eks. din build-agents IP).
Gemt godkendelsestilstand (Auth State): Som vist i eksemplet ovenfor er genbrug af en gemt session en best practice. Det fremskynder testkørslen markant, da login-processen kun skal gennemføres én gang. Du skal dog have en strategi for at opdatere denne session, når den udløber.
Ved at følge ovenstående metode med TOTP kan du opbygge en robust og fuldt automatiseret Playwright-testsuite, der pålideligt kan håndtere Microsoft MFA-login i dine CI/CD-pipelines.
0 notes
Text
Pain Management Billing Services: Make Sure You’re Compliant and Revenue is Maximized
Recapturing Lost Revenue: Why Pain Management Billing Services Are Essential for Clinic Survival
Pain clinics hemorrhage 22% of their rightful revenue annually due to coding errors, bundled procedure denials, and compliance oversights – a devastating loss that threatens practice viability. Pain Management Billing Services are specialized Revenue Cycle Management (RCM) experts dedicated exclusively to navigating the intricate coding, documentation, and regulatory demands unique to interventional pain procedures and chronic pain management. By partnering with Pain Management Billing Services, clinics unlock maximized reimbursement for complex injections and devices while drastically reducing the ever-present risk of costly OIG audits. Pain Management Billing Services provides the targeted expertise necessary for financial stability in this high-stakes specialty.
Why Pain Management Billing Demands Specialized Expertise
Generic billing solutions fail to address the unique complexities of pain medicine:
Interventional Procedure Coding Minefield:
Bundling Traps: Navigating National Correct Coding Initiative (NCCI) edits for injection series (e.g., CPT 64483-64495 for epidurals, 64633-64636 for RFAs) requires precise modifier application (59, 76, 77, XU) to justify separate reimbursement.
Multi-Level/Site Documentation: Procedures targeting multiple spinal levels or anatomical sites demand explicit documentation to support modifier use and avoid bundling denials.
Fluoroscopy Requirements: Pain Management Billing Services image guidance (77003) with procedures requires documentation of time and medical necessity.
Spinal Device Authorization & Billing Complexity:
Prior Authorization Hurdles: Spinal cord stimulators (SCS – CPT 63650, 63685), intrathecal pumps (62362), and vertebroplasty (22510-22515) face rigorous pre-approval processes requiring detailed clinical justification and peer-to-peer reviews.
Trial vs. Permanent Billing: Distinct coding and documentation rules govern temporary trials versus permanent device implantation.
Device-Specific Coding: Mastering codes for leads, generators, and programming is essential.
2. Chronic Care Management (CCM) & Telehealth Nuances:
CCM Code Requirements: Billing 99490, 99491, 99437 requires 20+ minutes of non-face-time care monthly, specific consent, and documented care plan.
Tele-pain Compliance: Correct Place of Service (POS 02) and modifier usage (e.g., 95, GT, GQ) for virtual chronic pain visits.
High-Risk Compliance Environment:
OIG Audit Target: Pain Management Billing Services is a top focus for audits due to high-cost procedures, opioid prescribing, and potential upcoding (e.g., E/M level inflation with procedures).
Stark Law/Anti-Kickback Risks: Especially critical for practices co-owned with or referring to ASCs.
Controlled Substance Documentation: Rigorous documentation justifying opioid prescriptions per CDC guidelines is audited.
ASC vs. Office-Based Billing Rules:
Facility/Professional Split: Correctly apportioning charges between the ASC (facility fee) and physician (professional fee) for procedures performed in surgery centers.
Differential Coding: Some codes differ between office and ASC settings.
Core Services Provided by Expert Pain Management Billing Services
Specialized services deliver end-to-end solutions:Pain Management Billing Services
Procedure-Specific Coding & Charge Capture:
Interventional Coding Expertise: Accurate CPT assignment for epidurals, facet blocks, RFAs, nerve blocks, discograms, kyphoplasty, and stimulator trials/implants.
Modifier Strategy: Applying 59/XU, 76, 77, LT/RT correctly to bypass NCCI edits and justify separate payment.
Device Authorization Management: Handling prior auth submission, clinical packet preparation, and peer-to-peer reviews for SCS, pumps, etc.
Chronic Care & E/M Optimization:
CCM/TCM Billing: Ensuring compliant capture and billing of chronic care management (99490+) and transitional care management (99495-99496) services.
E/M Level Validation: Auditing documentation to support appropriate E/M levels (99212-99215), especially when billed with procedures (modifier 25).
Claim Scrubbing & Submission:
Pain-Specific Scrubbing: Advanced tools configured for NCCI edits common in pain medicine (e.g., 64483+64484, 64490+64491), modifier rules, and LCD requirements.
Electronic Submission: To Medicare, Medicaid, and commercial payers.
Payment Posting & Underpayment Recovery:
Reconciling payments against contracts and fee schedules, specifically identifying underpayments for high-cost procedures and devices.
Proactive Denial Management & Appeals:
Root Cause Analysis: Specializing in pain-specific denials (bundling, medical necessity for procedures/devices, auth).
Targeted Appeals: Crafting effective, clinically-supported appeals leveraging pain medicine guidelines.
Compliance & Audit Defense:
Documentation Audits: Reviewing charts for Pain Management Billing Services necessity, procedure documentation completeness (e.g., levels treated, fluoro time), E/M level support, and opioid justification.
OIG/RAC Audit Preparedness & Support: Developing response protocols and providing documentation.
Stark Law/AKS Compliance Guidance: For ASC-integrated practices.
Pain-Specific Reporting & KPIs Pain Management Billing Services:
Tracking Injection Denial Rate, SCS/Pump Authorization Success Rate, CCM Utilization, MIPS Performance, and Days in A/R for Procedure Claims.
Tangible Benefits of Partnering with Pain Management Billing Services
Significant Revenue Increase (15-30%+): Recapturing lost revenue from bundled denials, undercoded procedures, missed CCM, and unoptimized device billing.
Drastically Reduced Denial Rates: Expertise in pain-specific coding and modifier strategies slashes initial denials.
Accelerated Device Authorization: Higher approval rates and faster turnaround for SCS/pump authorizations.
Mitigated Compliance & Audit Risk: Proactive safeguards reduce exposure to OIG audits and associated penalties.
Operational Efficiency: Freeing clinic staff from complex billing tasks allows focus on patient care and clinic operations.
Improved Cash Flow: Faster clean claim submission and effective denial management stabilize revenue.
Expertise on Demand: Access AAPC CPPM (Certified Pain Practice Manager) certified coders and billing specialists without in-house hiring/training costs.
Selecting the Right Pain Management Billing Services Partner: 5 Critical Criteria
CPPM Certification Mandatory: Ensure staff hold the Certified Pain Practice Manager credential (AAPC) – non-negotiable for pain-specific expertise.
Proven Interventional Procedure Experience: Demonstrable success coding/billing epidurals, RFAs, SCS, pumps, vertebroplasty, etc. Ask for client references.
ASC Billing Proficiency: Experience with facility/professional split billing and compliance for ASC-based pain procedures.
Compliance Focus: Deep understanding of OIG work plan targets for pain management, Stark Law implications, and documentation requirements for controlled substances/high-risk procedures.
Technology & Pain-Specific Tools: HIPAA-compliant platform with scrubbing rules pre-configured for common pain edits and denial tracking categorized by pain-specific reasons.
The Future of Pain Management Billing Services
AI-Powered Documentation: Tools to auto-suggest codes/modifiers based on procedure notes and flag documentation gaps.
Expanded Prior Authorization: Expect increased prior auth requirements for more procedures and devices.
Non-Opioid Treatment Focus: New codes and billing pathways for non-pharmacologic pain treatments (e.g., VR therapy, neuromodulation).
Value-Based Pain Care Models: Adapting RCM for bundled payments or capitation models focused on pain outcomes.
Enhanced Tele-pain Compliance: Evolving rules for chronic pain management via telehealth.
Conclusion: A Strategic Imperative for Financial Survival
The complexities of Pain Management Billing Services – from navigating injection bundling traps and securing device authorizations to mitigating OIG audit risks – demand specialized expertise. Generic billing solutions consistently fail, leaving significant revenue uncaptured and exposing clinics to severe compliance risks. Pain Management Billing Services provide the dedicated knowledge, precision coding, rigorous compliance focus, and advanced technology required to thrive in this challenging specialty. By partnering with a service possessing proven CPPM-certified expertise, mastery of interventional coding and modifier strategies, and a proactive approach to compliance, pain clinics can finally secure their financial foundation, ensure sustainable operations, and focus on delivering life-changing patient care. Investing in specialized Pain Management Billing Services is not an expense; it’s a strategic safeguard for your clinic’s future.
Frequently Asked Questions (FAQs)
Q: Why is Pain Management Billing Services different? A: It requires mastery of injection bundling rules, complex device authorization, strict compliance (OIG audits), and specialized codes/modifiers – generic billers miss 20%+ revenue.
Q: How do you prevent bundled procedure denials? A: Through precise modifier application (59/XU), documentation of separate sites/levels, and leveraging payer-specific CCI edit overrides.
Q: Can you handle spinal cord stimulator billing? A: Yes. We manage prior auth, trial coding (63650 + 77003), permanent implant billing (63685), and appeals using pain-specific clinical arguments.
Q: What pain-specific KPIs do you track? A: Injection Denial Rate, SCS/Pump Auth Success Rate, MIPS Pain Measure Scores, Chronic Care Utilization, and Days in A/R for Procedures.
Q: Do you support ASC-based pain clinics? A: Absolutely. We ensure compliant facility/professional split billing and adherence to Stark Law regulations.
#medical billing specialist#medical coding services#health#hospital#medical billing company#medical biiling
0 notes
Text
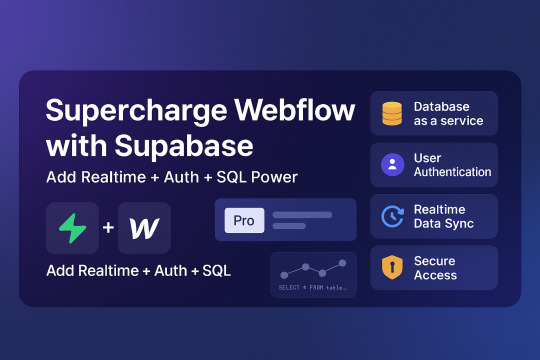
🌟 Webflow Tip of the Day
“Supercharge Webflow with Supabase: Add Realtime + Auth + SQL Power”
Want to go beyond static CMS in Webflow? Integrate Supabase — an open-source Firebase alternative — to add real database features like realtime data, auth, row-level security, and more.
🔧 Top Benefits of Using Supabase with Webflow:
✅ Database as a service – Store and manage structured data just like SQL ✅ User Authentication – Email/password, magic links, or OAuth (perfect for gated dashboards) ✅ Realtime Data Sync – Update Webflow UI with Supabase events via JavaScript ✅ Secure Access – Set row-level access rules (great for multi-user projects) ✅ API Ready – Fetch and push data using REST or Supabase client library
🧠 Pro Trick: Use Supabase + Wized or custom JS to fetch user-specific data and show personalized content inside Webflow. Combine with hidden Webflow attributes like data-user-id for seamless logic-driven UI.
🎯 Perfect For:
No-code SaaS dashboards
Gated communities
Job boards, CRMs, or listing platforms
Multi-role web apps
📌 Need quality Webflow development or a custom solution? Check out my work here: 🌐 Portfolio: www.webflowwork.com 🎯 Upwork: https://bit.ly/4iu6AKd 🎯 Fiverr: https://bit.ly/3EzQxNd
#WebflowTips #Supabase #WebflowCMS #Wized #WebflowExperts #RealtimeApps #NoCodeSaaS #WebflowIndia #OpenSourceTools #FirebaseAlternative #WizedIntegration #WebflowDevelopment #MadeInWebflow #FrontendDev
#webflow#freelancewebdeveloper#web design#web development#webflowdesign#webflowexperts#webflowlandingpage#website#nocode#ui ux design#webflowexpert#web developers#website design#web developing company#fiverr gigs#fiverr#freelancing#upwork
0 notes
Text
How a Web Development Company Builds Scalable SaaS Platforms
Building a SaaS (Software as a Service) platform isn't just about writing code—it’s about designing a product that can grow with your business, serve thousands of users reliably, and continuously evolve based on market needs. Whether you're launching a CRM, learning management system, or a niche productivity tool, scalability must be part of the plan from day one.
That’s why a professional Web Development Company brings more than just technical skills to the table. They understand the architectural, design, and business logic decisions required to ensure your SaaS product is not just functional—but scalable, secure, and future-proof.
1. Laying a Solid Architectural Foundation
The first step in building a scalable SaaS product is choosing the right architecture. Most development agencies follow a modular, service-oriented approach that separates different components of the application—user management, billing, dashboards, APIs, etc.—into layers or even microservices.
This ensures:
Features can be developed and deployed independently
The system can scale horizontally (adding more servers) or vertically (upgrading resources)
Future updates or integrations won’t require rebuilding the entire platform
Development teams often choose cloud-native architectures built on platforms like AWS, Azure, or GCP for their scalability and reliability.
2. Selecting the Right Tech Stack
Choosing the right technology stack is critical. The tech must support performance under heavy loads and allow for easy development as your team grows.
Popular stacks for SaaS platforms include:
Frontend: React.js, Vue.js, or Angular
Backend: Node.js, Django, Ruby on Rails, or Laravel
Databases: PostgreSQL or MongoDB for flexibility and performance
Infrastructure: Docker, Kubernetes, CI/CD pipelines for automation
A skilled agency doesn’t just pick trendy tools—they choose frameworks aligned with your app’s use case, team skills, and scaling needs.
3. Multi-Tenancy Setup
One of the biggest differentiators in SaaS development is whether the platform is multi-tenant���where one codebase and database serve multiple customers with logical separation.
A web development company configures multi-tenancy using:
Separate schemas per tenant (isolated but efficient)
Shared databases with tenant identifiers (cost-effective)
Isolated instances for enterprise clients (maximum security)
This architecture supports onboarding multiple customers without duplicating infrastructure—making it cost-efficient and easy to manage.
4. Building Secure, Scalable User Management
SaaS platforms must support a range of users—admins, team members, clients—with different permissions. That’s why role-based access control (RBAC) is built into the system from the start.
Key features include:
Secure user registration and login (OAuth2, SSO, MFA)
Dynamic role creation and permission assignment
Audit logs and activity tracking
This layer is integrated with identity providers and third-party auth services to meet enterprise security expectations.
5. Ensuring Seamless Billing and Subscription Management
Monetization is central to SaaS success. Development companies build subscription logic that supports:
Monthly and annual billing cycles
Tiered or usage-based pricing models
Free trials and discounts
Integration with Stripe, Razorpay, or other payment gateways
They also ensure compliance with global standards (like PCI DSS for payment security and GDPR for user data privacy), especially if you're targeting international customers.
6. Performance Optimization from Day One
Scalability means staying fast even as traffic and data grow. Web developers implement:
Caching systems (like Redis or Memcached)
Load balancers and auto-scaling policies
Asynchronous task queues (e.g., Celery, RabbitMQ)
CDN integration for static asset delivery
Combined with code profiling and database indexing, these enhancements ensure your SaaS stays performant no matter how many users are active.
7. Continuous Deployment and Monitoring
SaaS products evolve quickly—new features, fixes, improvements. That’s why agencies set up:
CI/CD pipelines for automated testing and deployment
Error tracking tools like Sentry or Rollbar
Performance monitoring with tools like Datadog or New Relic
Log management for incident response and debugging
This allows for rapid iteration and minimal downtime, which are critical in SaaS environments.
8. Preparing for Scale from a Product Perspective
Scalability isn’t just technical—it’s also about UX and support. A good development company collaborates on:
Intuitive onboarding flows
Scalable navigation and UI design systems
Help center and chatbot integrations
Data export and reporting features for growing teams
These elements allow users to self-serve as the platform scales, reducing support load and improving retention.
Conclusion
SaaS platforms are complex ecosystems that require planning, flexibility, and technical excellence. From architecture and authentication to billing and performance, every layer must be built with growth in mind. That’s why startups and enterprises alike trust a Web Development Company to help them design and launch SaaS solutions that can handle scale—without sacrificing speed or security.
Whether you're building your first SaaS MVP or upgrading an existing product, the right development partner can transform your vision into a resilient, scalable reality.
0 notes
Text
🛠 Modular .NET Core Architecture Explained: Why EasyLaunchpad Scales with You

Launching a SaaS product is hard. Scaling it without rewriting the codebase from scratch is even harder.
That’s why EasyLaunchpad was built with modular .NET Core architecture — giving you a powerful, clean, and extensible foundation designed to get your MVP out the door and support the long-term growth without compromising flexibility.
“Whether you’re a solo developer, a startup founder, or managing a small dev team, understanding the architecture under the hood matters. “ In this article, we’ll walk through how EasyLaunchpad’s modular architecture works, why it’s different from typical “template kits,” and how it’s designed to scale with your business.
💡 Why Architecture Matters
Most boilerplates get you started quickly but fall apart as your app grows. They’re rigid, tangled, and built with shortcuts that save time in the short term — while becoming a burden in the long run.
EasyLaunchpad was developed with one mission:
Build once, scale forever.
It follows clean, layered, and service-oriented architecture using .NET Core 8.0, optimized for SaaS and admin-based web applications.
🔧 Key Principles Behind EasyLaunchpad Architecture
Before diving into file structures or code, let’s review the principles that guide the architecture:
Principle and Explanation
Separation of Concerns — Presentation, logic, and data access layers are clearly separated
Modularity — Each major feature is isolated as a self-contained service/module
Extensibility — Easy to replace, override, or extend any part of the application
Dependency Injection- Managed using Autofac for flexibility and testability
Environment Awareness- Clean handling of app settings per environment (dev, staging, production)
📁 Folder & Layered Structure
Here’s how the core architecture is structured:
/Controllers
/Services
/Repositories
/Models
/Views
/Modules
/Jobs
/Helpers
/Configs
✔️ Controllers
Responsible for routing HTTP requests and invoking service logic. Kept minimal to adhere to the thin controller, fat service approach.
✔️ Services
All core business logic lives here. This makes testing easier and ensures modularity.
✔️ Repositories
All database-related queries and persistence logic are encapsulated in repository classes using Entity Framework Core.
✔️ Modules
Each major feature (auth, email, payment, etc.) is organized as a self-contained module. This allows plug-and-play or custom replacements.
🧩 What Makes EasyLaunchpad a Modular Boilerplate?
The magic of EasyLaunchpad lies in how it isolates and organizes functionality into feature-driven modules. Each module is independent, uses clean interfaces, and communicates through services — not tightly coupled logic.
✅ Modular Features
Modules and Their Functionality
Authentication- Login, password reset, Google login, Captcha
Admin Panel — User & role management, email settings, packages
Email System- DotLiquid templating, SMTP integration
Payment System- Stripe & Paddle modules, plan assignment
Job Scheduler- Hangfire setup for background tasks
Logging- Serilog for structured application logs
Package Management- Admin-defined SaaS plans & package logic
Each module uses interfaces and is injected via Autofac, which means you can:
Replace the Email service with SendGrid or MailKit
Swap out Stripe for PayPal
Extend authentication to include multi-tenancy or SSO
You’re not locked in — you’re empowered to scale.
🔄 Real-World Benefits of Modular Design
🛠 Maintainability
Code is easier to read, test, and update. You won’t dread revisiting it 6 months later.
🧪 Testability
Service and repository layers can be unit tested in isolation, which is perfect for CI/CD pipelines.
🔌 Plug-in/Plug-out Flexibility
Need to add analytics, invoicing, or multi-language support? Just drop a new module in /Modules and wire it up.
🧠 Developer Onboarding
New developers can understand and work on just one module without needing to grok the entire codebase.
🧱 Vertical Scaling
Whether you’re adding new features, scaling your user base, or serving enterprise clients, the codebase stays manageable.
🧠 Example: Adding a Chat Module
Let’s say you want to add real-time chat to your SaaS app.
In a modular structure, you’d:
Create a /Modules/Chat folder
Add models, services, and controllers related to messaging
Inject dependencies using interfaces and Autofac
Use Razor or integrate SignalR for real-time interaction
The existing app remains untouched. No spaghetti code. No conflicts.
⚙️ Supporting Technologies That Make It All Work
The architecture is powered by a solid tech stack:
Tool and the Purpose
.NET Core 8.0- Fast, stable, and LTS-supported
Entity Framework Core- ORM for SQL Server (or other DBs)
Razor Pages + MVC- Clean separation of views and logic
Autofac- Dependency injection across services
Serilog- Logging with structured output
Hangfire- Background jobs & task scheduling
Tailwind CSS + DaisyUI- Modern, responsive UI framework
DotLiquid- Flexible email templating engine
🚀 A Boilerplate That Grows with You
Most boilerplates force you to rewrite or rebuild when your app evolves.
EasyLaunchpad doesn’t.
Instead, it’s:
Startup-ready for quick MVPs
Production-ready for scaling
Enterprise-friendly with structure and discipline built in
💬 What Other Devs Are Saying
“I used EasyLaunchpad to go from idea to MVP in under a week. The modular codebase made it easy to add new features without breaking anything.” – A .NET SaaS Founder
🧠 Conclusion: Why Architecture Is Your Competitive Edge
As your product grows, the quality of your architecture becomes a bottleneck — or a launchpad.
With EasyLaunchpad, you get:
A clean foundation
Production-tested modules
Flexibility to scale
All without wasting weeks on repetitive setup.
It’s not just a .NET boilerplate. It’s a scalable SaaS starter kit built for serious developers who want to launch fast and grow with confidence.
👉 Ready to scale smart from day one? Explore the architecture in action at https://easylaunchpad.com
1 note
·
View note
Text
End-to-End Billing Support for Oncology and Radiology Providers
In the ever-evolving healthcare landscape, oncology and radiology providers face unique billing and revenue cycle management challenges. These specialties involve intricate procedures, high-cost services, frequent imaging, and ongoing treatment plans, all of which demand precise documentation and billing accuracy. The stakes are high: incorrect or delayed billing can result in revenue loss, compliance issues, and interrupted patient care.
That’s where end-to-end billing support comes into play. A comprehensive solution ensures that every step of the billing process—from patient registration to final reimbursement—is executed accurately, efficiently, and in compliance with industry regulations.
This article explores how oncology and radiology practices benefit from end-to-end billing support, the challenges they face, and what an effective billing solution should include.
Understanding the Complexity of Oncology and Radiology Billing
Oncology Billing: A Multi-Phase Challenge
Oncology treatment often involves:
The complexity of oncology care means providers must track each encounter, drug dosage, and treatment phase meticulously for accurate billing. Radiology Billing: High Volume, High Detail
Radiology billing includes services such as:
Because radiology often involves large volumes of diagnostic services, the risk of coding errors or missed charges is significantly higher.
What Is End-to-End Billing Support?
End-to-end billing support refers to the complete management of the billing lifecycle—from the moment a patient is scheduled to the time the provider is reimbursed. This includes:
End-to-end billing eliminates gaps, reduces administrative workload, and ensures timely payments.
Key Benefits for Oncology and Radiology Practices
1. Accurate and Compliant Coding
Coding errors can result in claim denials, delays, or audits. Oncology and radiology procedures involve specialized codes, and frequent updates to CPT, ICD-10, and HCPCS require constant attention. With end-to-end support, certified coders stay up-to-date with the latest coding changes and apply them correctly.
2. Streamlined Pre-Authorizations
Many oncology and radiology medical billing services require prior authorization due to their high cost and complexity. An end-to-end billing solution includes dedicated teams that handle prior auths efficiently, minimizing delays in patient care and revenue.
3. Improved Claim Submission Accuracy
Clean claim submission is crucial. End-to-end billing services include “claim scrubbing” to identify and fix errors before submission, improving first-pass resolution rates and speeding up reimbursements.
4. Faster Reimbursements
With all processes handled by a single, coordinated team, the billing cycle shortens. Claims are submitted faster, denials are addressed more promptly, and reimbursements are collected in a timely manner.
5. Effective Denial Management
Denials and underpayments are common in complex specialties like oncology and radiology. End-to-end billing support includes detailed denial tracking, root cause analysis, and timely appeals—all of which maximize collections and prevent recurring issues.
6. Revenue Cycle Transparency
Providers gain access to dashboards and reports that show real-time performance metrics: outstanding A/R, denial rates, collection rates, and more. This transparency helps decision-makers improve financial performance.
Specific Features of End-to-End Billing for Oncology Providers
Oncology billing involves not only complex services but also sensitive patient care. The Oncology medical billing services system must reflect that complexity and sensitivity. Key features include:
Specific Features of End-to-End Billing for Radiology Providers
Radiology services generate a high volume of transactions and require granular detail to ensure proper payment. Effective billing support should offer:
The Impact of Technology in End-to-End Billing
Advanced billing technology enhances the efficiency and accuracy of oncology and radiology billing:
Cloud-based platforms also allow billing teams to work remotely while maintaining real-time collaboration and compliance.
Compliance Considerations
Oncology and radiology billing must adhere to strict federal and payer-specific regulations:
Billing services with compliance specialists help avoid penalties and prepare documentation for any audits or inquiries.
Common Challenges Solved by End-to-End Billing
ChallengeSolution with End-to-End BillingFrequent claim denialsClean claim scrubbing, coding review, and appealsDelays due to pre-authorizationsDedicated prior auth teams with real-time trackingHigh administrative burdenFull outsourcing of billing and collectionsCompliance risksRegular audits and compliance monitoringRevenue leakageCharge capture validation and denial analytics
In-House vs. Outsourced End-to-End Billing
In-House Billing
Pros:
Cons:
Outsourced Billing
Pros:
Cons:
Ultimately, outsourcing is ideal for oncology and radiology practices that require specialty-focused, error-free billing support at scale.
Key Metrics to Monitor in End-to-End Billing
To measure the success of your end-to-end billing system, track these KPIs:
A robust billing partner provides these metrics regularly and transparently.
Choosing the Right End-to-End Billing Provider
When selecting a billing service for oncology or radiology, look for: Proven experience in your specialty
Your billing provider should not just submit claims—they should serve as an extension of your revenue team.
Final Thoughts
End-to-end billing support is no longer a luxury—it’s a necessity for oncology and radiology providers aiming for operational excellence, better financial outcomes, and uninterrupted patient care.
By partnering with a specialized billing provider that understands the nuances of your specialty, you can overcome the challenges of complex coding, strict compliance requirements, and administrative burden. You’ll be able to submit cleaner claims, collect revenue faster, and make smarter business decisions.
Oncology and radiology deserve billing solutions that are as sophisticated and specialized as the care they deliver.
0 notes
Text
How to Build a Carpooling App Like Liftshare?

In today’s fast-paced world, urban congestion, high fuel costs, and environmental concerns have paved the way for sustainable commuting alternatives, one of which is carpooling. Apps like Liftshare have successfully tapped into this demand, enabling people to share rides, reduce costs, and minimize their carbon footprint. If you're looking to build a carpooling app like Liftshare, this guide will walk you through everything from concept to launch.
Why Build a Carpooling App?
The global ride-sharing market is projected to reach $226.45 billion by 2030, driven by increasing smartphone penetration and demand for eco-friendly transport solutions. A carpooling app offers a win-win for users and the environment—helping reduce traffic, lower fuel expenses, and cut down emissions.
Key Features of a Liftshare-Like Carpooling App
To compete in this space, your app must offer intuitive functionality, seamless navigation, and secure transactions. Here are the must-have features:
1. User Registration & Profiles
Allow users to sign up via email, phone, or social accounts and create detailed profiles including preferences, car details (for drivers), and reviews.
2. Ride Listings & Search
Drivers should be able to post available rides with pickup/drop locations, time, and price. Riders can search and filter based on location, time, and ratings.
3. Real-Time GPS & Route Mapping
Integrate mapping APIs (like Google Maps) for real-time route suggestions, trip tracking, and optimized ride matching.
4. In-App Messaging
Enable secure in-app communication between drivers and passengers to discuss trip details without exchanging contact info.
5. Booking & Payment Integration
Include easy ride booking, fare calculation, and secure payment gateways like Stripe, Razorpay, or PayPal.
6. Rating & Review System
Let users rate each other post-trip to build trust and community reliability.
7. Admin Dashboard
Manage users, monitor activities, set policies, and access analytics to ensure smooth operations and user satisfaction.
Technology Stack Recommendations
Frontend: React Native or Flutter (for cross-platform apps)
Backend: Node.js or Django with PostgreSQL or MongoDB
Maps & Location: Google Maps API, Mapbox
Payments: Stripe, PayPal, Razorpay
Authentication: Firebase Auth or OAuth 2.0
Step-by-Step Development Process
Step 1: Market Research & Planning
Analyze competitors like Liftshare, BlaBlaCar, and Via. Understand your audience and define USPs.
Step 2: Create Wireframes & UI/UX Design
Design user-friendly, minimal, and mobile-responsive interfaces to enhance engagement.
Step 3: Develop the MVP
Build a Minimum Viable Product with essential features to validate the concept and gather user feedback.
Step 4: Launch & Promote
Deploy the app on app stores and use SEO, social media marketing, and referral campaigns to drive downloads.
Step 5: Gather Feedback & Scale
Continuously monitor user feedback, fix bugs, and introduce advanced features like ride subscriptions, multi-route matching, or carbon footprint calculators.
Cost to Develop a Carpooling App
The cost to build a taxi app like Liftshare can range from $15,000 to $50,000+, depending on complexity, feature set, location of your development team, and tech stack used.
Final Words
Building a carpooling app like Liftshare requires more than just coding, it needs a user-first mindset, eco-conscious vision, and strong technical execution. If done right, your app can not only solve daily commuting issues but also contribute to a greener, more connected world. Contact a leading taxi app development company to build a ridesharing app for your business.
0 notes
Text



Auth SOU-SOU - Purple Navy Multi Women's Dress ebay Brandear
0 notes
Text
What Makes Nexty.dev Stand Out
First published on https://nexty.dev/blogs/nexty-dev-stand-out
In my Notion database, I've listed over 40 Next.js SaaS templates - all competitors of Nexty.dev. With such an overwhelming array of choices, it's difficult to quickly determine which one truly meets your needs.
If you're searching for a solution that's not only secure and stable but also offers unique advanced features to help launch your SaaS product quickly, Nexty.dev deserves your attention.
Nexty.dev is a flexible, multi-purpose full-stack SaaS template built on Next.js and Supabase. This article will explore Nexty.dev's unique advantages compared to its competitors to help you make the right choice.
Nexty.dev's Core Features
Before diving into Nexty.dev's unique advantages, let me introduce its robust features that match or exceed competitor offerings.
Multi-language Support
Nexty.dev supports English, Chinese, and Japanese by default, and you can easily add more languages as needed.
Authentication
Nexty.dev implements authentication through Supabase Auth, supporting multiple login methods including Google, GitHub, and email Magic Link. The documentation provides detailed configuration steps.

Email Services
Nexty.dev implements domain email through Cloudflare, which can be configured by following the documentation steps. A domain email address makes your brand appear more professional and helps build trust with users.
Additionally, Nexty.dev implements subscriber management and email sending functionality through Resend, with detailed configuration steps in the documentation.
The template's footer includes a built-in newsletter subscription module to help you better understand email service implementation and usage.
Analytics and Advertising
Nexty.dev includes built-in support for Google Analytics, Plausible, and Google Ads, allowing you to immediately start analyzing user behavior and running advertisements.
SEO-Friendly Structure
Nexty.dev provides an SEO-friendly page structure, eliminating the need to worry about technical SEO optimization.
Nexty.dev's Unique Advantages
Payment Services and Pricing Card Management
While similar templates often provide only a core payment flow, Nexty.dev's payment module comes with a complete built-in logic for one-time payments and recurring subscriptions. This includes adding credits upon payment, updating credits on subscription renewal, and clearing credits upon refund.
But that's not all that makes Nexty.dev stand out. To make pricing card management more convenient, Nexty.dev has added pricing card management functionality to the admin dashboard, eliminating the need for complex multilingual JSON configuration.
The pricing card management feature is exceptionally user-friendly. Let me explain through screenshots.
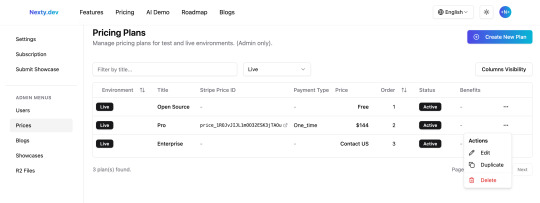
List View
You can view all pricing card core information in the list, including environment, card information, associated Stripe Price ID, payment method, and status. The action column supports editing, Duplicate, and deleting, with the "Duplicate" function allowing you to quickly create similar cards, reducing repetitive operations.
Create/Edit Pricing Cards
The create/edit pricing card page supports selecting the environment, order, and visibility (Active); you can also see real-time previews to ensure proper display in the template and easily check for issues. These features are unmatched among SaaS templates.
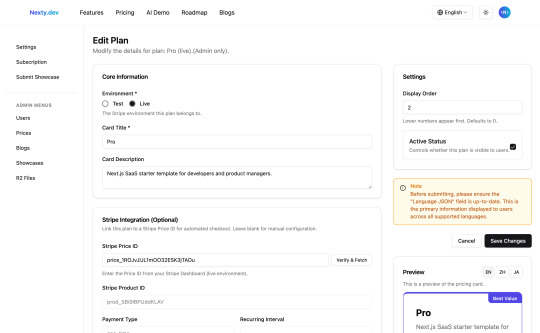
For Stripe integration, you just need to copy the Stripe Price ID to fetch accurate pricing information with one click, eliminating the need for manual data entry.
Card display information, including display price, plan benefits, highlighting, and button information, can all be configured through the form.
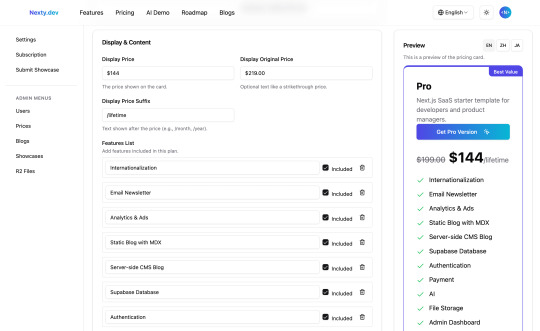

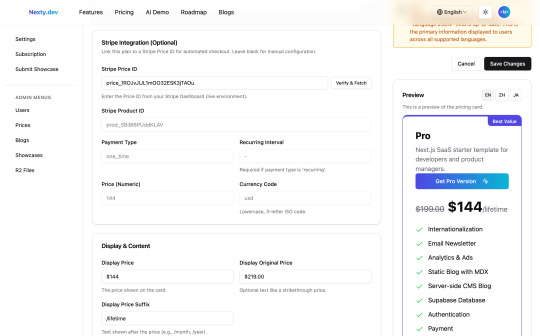
To better accommodate multilingual scenarios, Nexty.dev's pricing cards also offer multilingual translation functionality - just configure the translation API Key in your environment variables.
For technically-inclined template users who want to extend user benefits, Nexty.dev supports a "Benefits JSON" feature, allowing you to expand user benefits without modifying the data table.
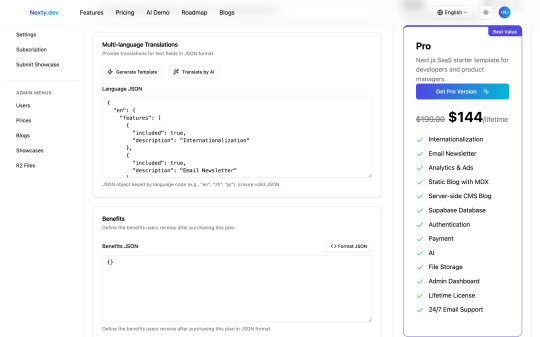
After updating the data, the pricing cards immediately update on the user end.

This is one of my favorite features because it allows template users to update pricing through the admin dashboard rather than modifying code, completing updates in just a minute.
AI Demo Provided
While providing AI APIs has become standard for SaaS templates, Nexty.dev takes it further.
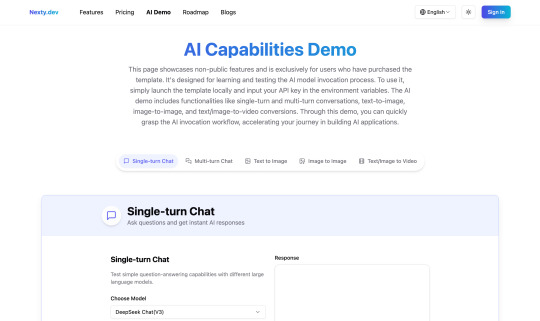
Understanding that different products have different AI needs, Nexty.dev goes beyond just providing API calls. The template includes an AI Demo page with examples of various AI model implementations, including single-turn dialogue, multi-turn dialogue, text-to-image, image-to-image, and image-to-video.
On the AI Demo page, you can quickly test different AI functionalities. If you're unfamiliar with AI features, you can use this page's code as a learning example to quickly understand AI development approaches - embodying the principle of "Give a man a fish, and you feed him for a day. Teach a man to fish, and you feed him for a lifetime".
The AI Demo is also crucial for keeping up with rapidly evolving AI models, allowing you to quickly test new models and validate their feasibility ahead of the competition.
File Management
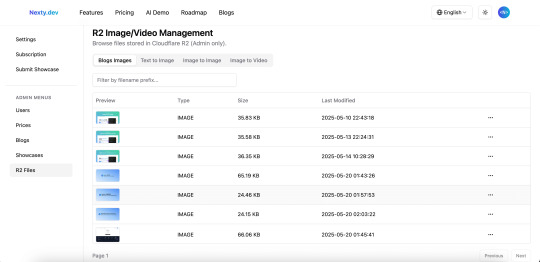
Nexty.dev implements file storage and management through Cloudflare R2, with built-in functionality for file upload, deletion, and list viewing.
These features are integrated into the admin dashboard's R2 file management functionality, making file management convenient.
Advanced CMS
Nexty.dev's CMS module offers features that are unmatched among SaaS templates, going beyond basic content management and publishing to support various application scenarios.
Beyond basic blog information (title, slug, description, tags, cover image), Nexty.dev supports advanced settings like pinning, status (draft, published, archived), access permissions (public, logged-in users, subscribers); content editing supports both Markdown and rich text modes, plus AI translation.
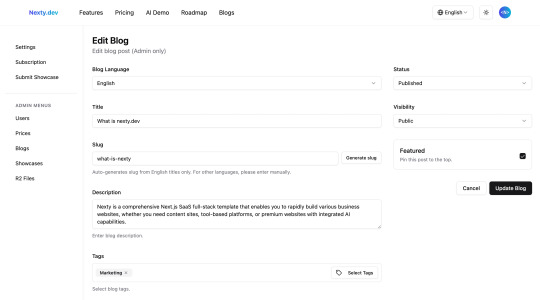

Additionally, the list supports blog duplicate to create new posts, reducing repetitive operations and improving multilingual content production efficiency.
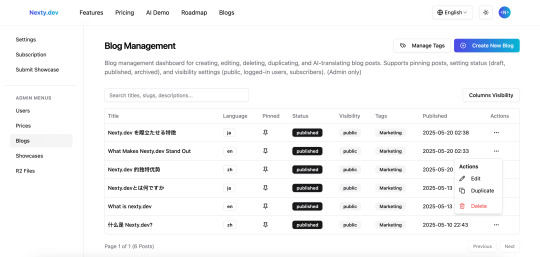
With these features, you can use the CMS module not only for blog sites but also for paid content sites - this truly makes Nexty.dev a multi-purpose template.
Conclusion
As we've seen, Nexty.dev isn't just another feature-rich Next.js SaaS template - it's a thoughtfully designed solution addressing real development pain points. While it solidly covers essential SaaS modules like multilingual support, authentication, email services, analytics, and SEO, it goes far beyond ordinary templates through unique advantages like visual pricing management, inspiring AI demos, convenient file management, and powerful advanced CMS.
Understanding the challenges developers face in building SaaS applications, every carefully designed feature in Nexty.dev - from visual pricing that eliminates tedious configuration to educational AI examples and advanced CMS capable of supporting paid content - aims to clear obstacles, significantly improve development efficiency, and inspire business innovation.
If you're looking for a template that can truly accelerate your SaaS product launch while giving you powerful customization capabilities, Nexty.dev is undoubtedly your most trustworthy choice. Visit nexty.dev now to turn your SaaS vision into reality quickly.
0 notes