#msrc
Explore tagged Tumblr posts
Text

“Danse Macabre,” Moon Knight (Vol. 9/2021), #25.
Writer: Jed MacKay; Pencilers and Inkers: Alessandro Cappuccio, Alessandro Vitti, and Partha Pratim; Colorist: Rachelle Rosenberg; Letterer: Cory Petit
#Marvel#Marvel comics#Marvel 616#Moon Knight vol. 9#Moon Knight 2021#Moon Knight comics#latest release#Moon Knight#Msrc Spector#Tigra#Greer Nelson#Them™️#the drama#the a r t#the references to the universe (aka Khonshu)’s refusal to let Marc rest + that one time Marc helped a dude fall off of a building#P E A K#thank you Mr. Cappuccio
7 notes
·
View notes
Text
Microsoft to offer hackers millions in Zero Day Quest event

Source: https://www.techtarget.com/searchsecurity/news/366616078/Microsoft-to-offer-hackers-millions-in-Zero-Day-Quest-event
More info:
https://msrc.microsoft.com/blog/2024/11/securing-ai-and-cloud-with-the-zero-day-quest/
https://www.microsoft.com/en-us/msrc/microsoft-zero-day-quest
2 notes
·
View notes
Text
May-Summer racing competitions MSRC
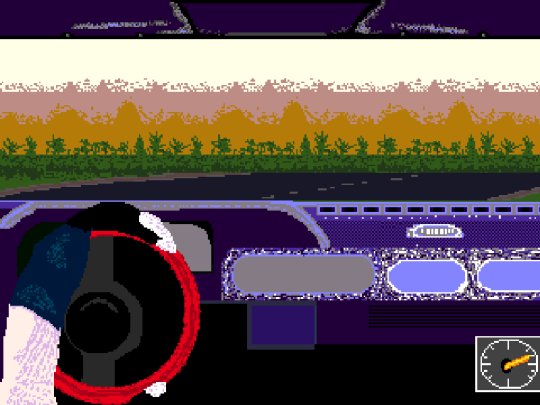
Pixel art for today based on videogame Network Q Rally for game console Super Nintendo. It is 16 bit Racing game. I played for myself this game at PC MS DOS. With my 486Dx2 computer, SVGA graphics. So, game looks similar. But, anyway, I think it is a little another game.
But I remember it, I and my bro, we play it. We like this racing game a lot. Beautiful three-dimensional graphics. Different views. From car, 3d view. And such a track along casual roads. As we think about it. Forest, field. Not exotic views, with super views. And about a casual views. Forest, river, bridge. We like this game for these things. And I remember green track, it was there. Lots of forest and grass. So, this is impression from this game. It is a very good racing game. And, I think, that version for Super Nintendo is also excellent! 16 bits variation!
And this is my drawing about the same theme. Racing starts in may and will continue all the summer season. It is a cycle of road competitions. Tracks are made special ways for this competition. But they are about a casual roads. Through the forest. Field. Bridge. River. And never through the cities. And more about an open space. Like forest, field. Road though the forest. And one moment, it is all the time a lots of grass by the sides of the road. And, maybe, a road though forest. A bridge across the river. Of course, you can to make a stop. And look a views. To make some photos. Your car. Yourself. And go next. Racing is about rally idea. All starts one by one, after some time. Using some pause between each new starting car. There are control points, check points.
And so it is going a racing time. And a well-known forests and fields. Racing is about a middle level of cars. They are no special setup for racing. And about a casual cars, that you can see at the streets. So, any one, who likes the idea can take a part in a racing.
Between racings there are some time to restore powers. And then - next race. It is its own class of racing competitions. It is very good about cars from 80s, 90s and so on. But you need to be ready for different road type. And take into account, a low or badly asphalt roads, or sand roads, soil roads. But asphalt, of course, it will be a lot, a lots of asphalt roads to be here.
So, racing will be intense. And sport uniform is very good to have. Gloves of a car driver. A helmet. To avoid some difficulties. And racing, anyway, it will be with comfort and relax too. And, from time to time, it will be hard about a making turns. And try to make a better position on the roads, and overspeed another racers, sometimes. And at some moments, it will be a tracks with almost straight roads, and rare turns. But, distance is more long. So, it is a mixed typed of tracks.

Dima Link is making retro videogames, apps, a little of music, write stories, and some retro more.
WEBSITE: http://www.dimalink.tv-games.ru/home_eng.html ITCHIO: https://dimalink.itch.io/ GAMEJOLT: https://gamejolt.com/@DimaLink/games
BLOGGER: https://dimalinkeng.blogspot.com/
#16 bit#super nintendo#8 bit#ms dos#486dx2#snes#megadrive#retro games#retro aesthetic#pixel art#pixels#pixel aesthetic#pixel graphics#80s#90s#racing#network qrally#forest#river#casual#roads#race#summer#racing competition#arcade#retro#country house#apshalt roads#grass
3 notes
·
View notes
Text

LDAPNightmare exploit crashes LSASS and forces a reboot of Windows domain controllersOn December 10th 2024, Yuki Chen (@guhe120) identified two LDAP vulnerabilities: a Remote Code Execution (RCE) flaw and a Denial of Service (DoS)/Information Leak issue. Both vulnerabilities, which impact any Domain Controller (DC), were disclosed on the Microsoft Security Response Center (MSRC) website as part of the latest Patch Tuesday update. The RCE vulnerability was designated CVE-2024-49112 and assigned a CVSS severity score of 9.8 out of 10, while the DoS vulnerability was labelled CVE-2024-49113. Despite these disclosures, no public exploit or detailed blog post outlining the vulnerabilities or exploitation methods has been released. SafeBreach Labs developed a proof of Read the full article
0 notes
Text
VoIP Engineer || Vice Process Company || Technical Support VoIP Engineer || Technical Support || NOC Engineer || Kolkata || West Bengal
About Company: Recruitment Company is a rapidly growing Business Process Outsourcing Company, headquartered in London, United Kingdom, and an outsourcing branch in Pune, India. They cover the fields of Business Solutions, Recruitment Solutions, and Designing Solutions as their Core Business. They are specialized and deal in inbound and out bound calls, consultancy, Design and marketing solutions.
Mission of the Company: To be a reliable partner for their clients and they intend to offer new solutions and technology to drive B2B and B2C services with great ease.
Hi we are from Ideal Career Zone: Where Your Skills Meet Your Passions. The ideal career zone is the sweet spot where your skills and passions intersect. It's the place where you can use your talents to make a difference in the world, while also feeling fulfilled and satisfied. Finding your ideal career zone can be a challenge, but it's worth it. When you're in the right zone, you'll be more productive, more motivated, and more likely to succeed.
Now the company need some staffs for the post of VOIP engineer.
Job Description
Profile: Technical Support VoIP Engineer / NOC Engineer
Location: Kolkata, West Bengal
Experience: 3+ Years
Profile: VoIP Support Engineer.
Salary Budget: 5 LPA to 11 LPA
Brief description:
Should have Good exposure to GSM, VOIP, SIP, MSRC, RTP, MSRP, RCS.
Should be adept in VOIP Trunk SIP Configuration, PRI Card Installation, Asterisk/ Dahdi/ FreePBX Installation / IP PBX /IP Telephony / IP phone configuration / EPBX /VOIP Gateway /Asterisk server management.
Troubleshooting of SIP and VOIP Based Call-center telephony Issues.
Experience in Installing, configuring and deployments of Asterisk, Asterisk-based applications like Vicidial, IVR and FreePBX.
Experience in Installing, configuring and deployment of Asterisk, GoAutoDial, Vicidial, IVR and FreePBX.
Sound knowledge of Asterisk Installation, Configuration, Dialplan, AGI, AMI, Call troubleshooting (SIP, ISDN, PSTN)
Configuration, Maintenance and troubleshooting of Asterisk Based Servers, VICIDIAL, FreePBX, Freeswitch.
Good verbal and written communication.
Excellent team player, ability to work in a global team and follow through on deadlines.
Strong technical and analytical skills.
Resolve Client issues through Skype and Remote Screen sharing.
Minimum 2+yearsexperience in Troubleshooting VoIP Required.
Proficiency in the following programming languages: MySQL, PHP, Perl. Preferred skills
Industry Type: Telcom, ISP, BPO.
Key Skills: Asterisk, Vici Dail, Free PBX IVR, VOIP, Wire Shark
Employment Type: Full Time
Note:- Many more Jobs available just search in Google “Ideal Career Zone” Kolkata.
You can find many more job details in various posts in various companies.
You may call us between 9 am to 8 pm
8 7 7 7 2 1 1 zero 1 6
9 3 3 1 2 zero 5 1 3 3
Or you can visit our office.
Ideal Career Zone
128/12A, Bidhan Srani Shyam Bazaar metro Gate No.1 Gandhi Market Behind Sajjaa Dhaam Bed Sheet Bed cover Show room Kolkata 7 lakh 4
Thank you for watching our channel Please subscribed and like our videos for more jobs opening. Thank You again.
VoIPEngineer, #ViceProcessCompany, #TechnicalSupportVoIPEngineer, #TechnicalSupport, #NOCEngineer, #Kolkata, #WestBengal, #FemalesJob, #BadaBazaar, #Howrah, #idealcareerzone, #kolkatajobs, #WestBengal, #Silliguri, #Asaam, #mizuram, #Tripura, #India, #Bihar, #Jharkhand, #PanIndia, #jobIndia, #kolkatajobcenter, #latestjobsinkolkata, Newjobsinkolkata,
0 notes
Text
Microsoft Remote Desktop Protocol mit CVSS 8.1 Sicherheitslücke

Microsoft listet die hochgefährliche Schwachstelle CVE-2024-43582 auf, eine Sicherheitslücke die Remote-Codeausführung erlaubt im Remote Desktop Protocol Server. Der CVSS-Wert liegt bei 8.1. Microsoft gibt an, dass die Ausnutzung nicht so einfach wäre - die Zero Day Initiative sieht das anders. Das Microsoft Security Response Center (MSRC) untersucht alle Berichte über Sicherheitsanfälligkeiten, die Microsoft-Produkte und -Dienste. In seinem aktuellen Leitfaden für Sicherheitsupdates wird eine hochgefährliche RDP-Schwachstelle (Microsoft Remote Desktop Protocol) gelistet mit einem CVSS-Wert 8.1 von 10. Microsoft sieht das Problem gelassener als ZDI Dieser Fehler ermöglicht es einem entfernten, nicht authentifizierten Angreifer, willkürlichen Code auf höheren Ebenen auszuführen, indem er einfach speziell gestaltete RPC-Anfragen sendet. Microsoft weist darauf hin, dass der Angreifer eine Race Condition (zwei oder mehr Prozesse greifen zeitlich auf eine Ressource zu) gewinnen müsste. Die Zero Day Initiative (ZDI ) gibt aber an, dass bei Hacker-Wettbewerben immer wieder gezeigt wird, dass Race Conditions zu gewinnen sind. Obwohl dieser Fehler wurmfähig ist, ist es unwahrscheinlich, dass er tatsächlich zu einem Wurm führt. RPC sollte laut ZDI an Ihrem Perimeter blockiert werden und das ist nicht der Fall. Dadurch würde das Problem nur auf interne Systeme beschränkt, aber es könnte für die laterale Bewegung innerhalb eines Unternehmens verwendet werden. Das Schwachstelle CVE-2024-43582 wird von Microsoft mit dem Patch Tuesday des Monats Oktober geschlossen - wie auch 116 andere Sicherheitslücken. Administratoren sollen die Updates zeitnah einspielen. Passende Artikel zum Thema Lesen Sie den ganzen Artikel
0 notes
Link
0 notes
Text
Critical Boot Loader Vulnerability in Shim Impacts Nearly All Linux Distros
The Hacker News : The maintainers of shim have released version 15.8 to address six security flaws, including a critical bug that could pave the way for remote code execution under specific circumstances. Tracked as CVE-2023-40547 (CVSS score: 9.8), the vulnerability could be exploited to achieve a Secure Boot bypass. Bill Demirkapi of the Microsoft Security Response Center (MSRC) has been& http://dlvr.it/T2bXnC Posted by : Mohit Kumar ( Hacker )
0 notes
Text

Today, I visited the Moorland-Spingarn Research Center in Founders Library and stopped by the 50th Anniversary Symposium. MSRC was founded in 1914, and was established at Howard in 1973. The center was made possible thanks to the donations of the personal libraries of Jesse E. Moorland and Arthur B. Spingarn, and the help of librarian Dorothy Porter Wesley in its development and organization. MSRC has extensive collections and endless resources on important figures on Black History, and I can't wait to explore it more.
0 notes
Link
Mini Scenes Red Carpet is great when you just need a quick background for your amazing render. What's Included and Features Mini Scenes Red Carpet Consists of 11 obj (.duf files) MSRC Setup MSRC Light Rig Setup MSRC Branding Wall MSRC Ceiling MSRC Chair MSRC Clapper Board MSRC Curtain MSRC Floor MSRC Light Rig MSRC Loud Hailer MSRC Red Carpet MSRC Spot Light (Rigged) MSRC Stanchion Materials: Branding Wall 30th Annual Awards Branding Wall Black Patterned Curtain Red Curtain Black 21 Texture Map. Diffuse and Bump 4096 x 4096 Compatible Software: Daz Studio 4.21 Install Types: DazCentral, Daz Connect, DIM, Manual Install Coming soon: https://3d-stuff.net/ #daz3d #dazstudio #3drender #3dart #daz3dstudio #irayrender #3dartwork #blender #blenderrender #blenderart #noaiart #noaiwriting #noai https://3d-stuff.net/
0 notes
Text
Hackers Abused Microsoft's "Verified Publisher" OAuth Apps to Hack Corporate Email Accounts

Source: https://thehackernews.com/2023/02/hackers-abused-microsofts-verified.html
More info: https://msrc-blog.microsoft.com/2023/01/31/threat-actor-consent-phishing-campaign-abusing-the-verified-publisher-process/
4 notes
·
View notes
Quote
Azure ストレージ バケット経由で公開される 38 TB のプライベート データ Wiz Research チームは、オープンソース モデルに加えて、内部ストレージ アカウントでも 38 TB 相当の追加プライベート データへのアクセスを誤って許可していることを発見しました。 流出したデータには、Microsoft サービスのパスワード、秘密キーを含む Microsoft 従業員に属する個人情報のバックアップ、および 359 人の Microsoft 従業員から発信された 30,000 件を超える社内 Microsoft Teams メッセージのアーカイブが含まれていました。 Microsoft Security Response Center (MSRC) チームによる月曜日の勧告の中で、 Microsoft は 、このインシデントによって顧客データが漏洩したことはなく、他の内部サービスが危険にさらされたことはないと述べた。 Wiz は 2023 年 6 月 22 日にこのインシデントを MSRC に報告し、SAS トークンが取り消されて Azure ストレージ アカウントへのすべての外部アクセスがブロックされ、2023 年 6 月 24 日に問題が軽減されました。 「AI はテクノロジー企業に大きな可能性をもたらします。しかし、データ サイエンティストやエンジニアが新しい AI ソリューションを本番環境に導入しようと競う中、彼らが扱う大量の��ータには追加のセキュリティ チェックと保護手段が必要です」と Wiz の CTO 兼共同創設者である Ami Luttwak 氏は BleepingComputer に語った。 「この新興テクノロジーには、トレーニングに大規模なデータセットが必要です。多くの開発チームが大量のデータを操作したり、同僚と共有したり、公開オープンソースプロジェクトで共同作業したりする必要があるため、Microsoft のようなケースを監視し回避することがますます困難になっています。 」 また、BleepingComputer は 1 年前、2022 年 9 月に、脅威インテリジェンス企業 SOCRadar が、 別の構成が誤った Azure Blob Storage バケットを発見したと報告しました。このバケットには、2017 年から 2022 年 8 月の日付のファイルに保存され、111 か国の 65,000 以上のエンティティにリンクされている機密データが含まれていました。 Microsoft に属する という名前のデータ漏洩検索ポータルも作成しました。 BlueBleed SOCRadar はまた、企業が自社の機密データがオンラインで公開されているかどうかを確認できるようにする、 Microsoftは後に、SOCRadarが「この問題の範囲」と「数値」を大幅に誇張していると考えていると付け加えた。
Microsoft、安全でない Azure ストレージ経由で 38TB の個人データを漏洩
0 notes
Text
Saturday Morning Coffee
Good morning from Charlottesville, Virginia! ☕️

Kim and I had the grandkids overnight so they’re worn out and we’re worn out. Heck, even our pups are worn out. The house is really quiet, just how I like it. I’m sitting here in the dark, sipping coffee, composing today’s post.
This week work was mostly about onboarding a couple new iOS Devs who’ll be working with me on our project to add React Native support to existing native apps. I’m really enjoying it. 😀
Caitlin Harrington • WIRED
Last month, Grindr gave its all-remote staff two weeks to pledge to work from an office two days a week starting in October or lose their jobs come August 31. Many declined to return: 82 out of 178 employees—46 percent of the staff—were let go after rejecting the mandate, according to the Grindr union, which went public two weeks before the ultimatum.
Wow. That’s about all I had to say when I read this piece. I have a friend who took a job there — as a remote test engineer — only to have this mandate cross his desk two weeks later. Needless to say he didn’t move and is now looking for a new gig. It’s a real head scratcher.
Ron Amadeo • Ars Technica
The Federated Learning of Cohorts and now the Topics API are part of a plan to pitch an “alternative” tracking platform, and Google argues that there has to be a tracking alternative—you can’t just not be spied on.
Emphasis is mine. At least they admit what they’re doing and it’s pathetic. 😳
You know what’s worse? People won’t switch away from Chrome.
thehackernews.com
Apple on Thursday released emergency security updates for iOS, iPadOS, macOS, and watchOS to address two zero-day flaws that have been exploited in the wild to deliver NSO Group’s Pegasus mercenary spyware.
Update your devices right away. The talent possessed to do this type of ferreting around an OS looking for holes is both impressive and terrifying all at the same time.
Branko Marcetic • jacobin.com
The inflation rate — that is, the pace at which prices are going up — might be slowing down, but that doesn’t mean prices are lower. In fact, they are much, much higher for all kinds of goods and services than they were three years ago.
I’ve definitely noticed this when we go to our favorite Mexican restaurant here in Charlottesville.
It’s really becoming apparent in the streaming business. I just received email saying our Hulu subscription is going up to $81.99/month. We currently pay $64/month. That’s close to a 25% increase. 🤬
Taegan Goddard • politicalwire.com
Pence Calls Trump’s Populism a ‘Road to Ruin’
Wow. Pence finally figured it out. Took long enough.
I know folks have praised him for what he did January 6 — myself included — but the truth is he could’ve done a lot more prior to the sixth to avert this, like call the FBI.
MSRC • msrc.microsoft.com
Upon identifying that the threat actor had acquired the consumer key, Microsoft performed a comprehensive technical investigation into the acquisition of the Microsoft account consumer signing key, including how it was used to access enterprise email. Our technical investigation has concluded. As part of our commitment to transparency and trust, we are releasing our investigation findings.
Reading these reports is fascinating. I love seeing them own up to mistakes and solve the problems that lead them there. I personally like to focus on the problem and not point fingers. These reports come across like that to me.
Greg Jones • enginebuildermag.com
As a kid, Dan Keenan loved fixing things, tearing things apart, and figuring out a way to build something new. But he never dreamed his skills would one day lead to being a key player in designing a brand-new race engine for NASCAR.
This is an older piece but is a great little read if you’re at all interested in engine building. I most definitely am and would love to see some deep dives of all the motors used in the NASCAR Cup Series. The teams use a new motor each week! It’s amazing to me how consistent the builds are from week to week.
They do see the occasional failure but those are rare. It would be amazing to see reports from engine builders outlining the failures and the steps taken to mitigate them, just like that Microsoft Security piece linked above.
Michael Meng • eng.lyft.com
Lyft runs hundreds of microservices to power the company’s offerings. Our team, the Developer Infrastructure team, aims to build the best tools to enable microservice owners (our “customers”) to reliably and quickly test changes in a local and/or end-to-end environment.
When we crossed that line from desktop focused computing on local networks to service based computing on the open web software development became infinitely more complicated. I know a lot of folks who’ll disagree with that assessment and that’s fine. It’s how it feels to me. I’m a simpleton and prefer my little self contained IDE and platform. 😃
GMS Racing • legacymotorclub.com
LEGACY MOTOR CLUB™ Signs John Hunter Nemechek to Drive the No. 42 in 2024
It’s fun to watch NASCAR teams make lineup changes for next season. How many more changes will we see between now and next season? Who knows.
It’ll also be nice to see where the Stewart Haas Racing rumors land. Do they run two or four cars next year? Do they have charters for sale? If so, who picks them up?
Oh, right, when is Dodge coming back! 🤣 Yes, I really do want to see it.
Lane Brown • Vulture
The Ophelia affair is a useful microcosm for understanding how Rotten Tomatoes, which turned 25 in August, has come to function. The site was conceived in the early days of the web as a Hot or Not for movies. Now, it can make or break them — with implications for how films are perceived, released, marketed, and possibly even green-lit. The Tomatometer may be the most important metric in entertainment, yet it’s also erratic, reductive, and easily hacked.
I’d not heard of folks gamifying Rotten Tomatoes scores but it makes sense it would happen. Gotta keep those scores fresh so folks will watch your movie and put money in your pocket. 🍅

0 notes
Link
https://bit.ly/3NlgTTI - 🔍 In early June 2023, #Microsoft noticed an increase in traffic against certain services which temporarily impacted availability. The investigation led them to the tracking of ongoing Distributed Denial of Service (DDoS) activity by the threat actor known as Storm-1359. 🎯 #CyberSecurity #DDoS 🌐 Storm-1359 appears to leverage multiple virtual private servers (VPS), rented cloud infrastructure, open proxies, and DDoS tools for these attacks. Importantly, Microsoft has found no evidence that customer data has been compromised. 🛡️ #DataProtection #CloudSecurity 🔗 The latest DDoS activity targeted layer 7 instead of layer 3 or 4. Microsoft has beefed up layer 7 protections, including fine-tuning the Azure Web Application Firewall (WAF), to shield customers from similar DDoS attacks more effectively. 🛠️ #Azure #WAF 🕹️ The Storm-1359 is believed to use various layer 7 DDoS attack techniques, including HTTP(S) flood attack, Cache bypass, and Slowloris, mainly focusing on system disruption and publicity. 💻 #CyberThreats #InfoSec 🛡️ For better protection, Microsoft recommends the use of layer 7 protection services such as Azure WAF. To boost resilience, the users are advised to configure bot protection, block identified malicious IP addresses, limit or block traffic from outside a defined geographic region, and create custom WAF rules. 🔧
#Microsoft#CyberSecurity#DDoS#DataProtection#CloudSecurity#Azure#WAF#CyberThreats#InfoSec#CyberDefense#BestPractices
0 notes
Text
[Media] MSRC-Security-Research
MSRC-Security-Research Security Research from the Microsoft Security Response Center (MSRC) https://github.com/microsoft/MSRC-Security-Research #cybersecurity #infosec

0 notes
Text



Mulder and Scully Moments, volume 1
(4x15) Memento Mori
(5x5) The Post-Modern Prometheus
Fight The Future (1998)
#txfedit#should i make this a thing? send me ur thoughts#i say volume 1 but 🤔 will i ever make a volume 2#highkey only like the postmodern prometheus one but i have 0 energy to redo the gross ones#guys i spent so much time trying to perfect those 9s :(#someone pls complement my 9s :(#DONT LOOK AT THEIR EARS I HATE IT#mine111#msrc#msr#fox mulder#dana scully#fan art#txf#x files#txf*
272 notes
·
View notes