#mdm removal tool
Explore tagged Tumblr posts
Link
Haafedk GSM and iCloud removal tool download
#haafedk#bypass icloud tool#haafedk gsm#frp bypass tool 2025#samsung frp tool#mdm removal tool#iphone removal tool
0 notes
Video
youtube
MDMFix Tool Tutorial Samsung all model KG lock , IT Admin , MDM Remove
MDMFix Tool support All smsuung KG lock Remove ADB mode
ADB mode Enable by QR code
Samsung KG lock Remove by EDL mode also
IT Admin Lock Remove All brands
MDM remove Permanently ITel Tecno infinix
#youtube#mdmfix#mdmfix tool activation#asunlocker#activation#mdm remove#samsung kg lock remove#teno mdm remove#infinix mdm remove#xiaomi mdm remove
0 notes
Text
1 note
·
View note
Text
2 notes
·
View notes
Text
#tim drake#batfamily#mlp#artificial intelligence#finance#marketing#deadpool and wolverine#coding#my gif
1 note
·
View note
Text
Identity And Access Management Market Product Driving Factors, Capacity and Growth Rate Analysis to 2030
The global identity and access management (IAM) market was valued at USD 15.93 billion in 2022, with expectations to grow at a compound annual growth rate (CAGR) of 12.6% from 2023 to 2030. IAM solutions provide a critical framework that ensures only authorized individuals and roles within an organization can access necessary resources, applications, and tools to fulfill their duties effectively. This system enables organizations to manage user access across various applications without needing administrator-level access for every single app, simplifying user management and boosting security. With the rise in IoT and AI technologies, heightened awareness around regulatory compliance, and increased digital platform reliance, the demand for IAM solutions is anticipated to grow significantly over the forecast period.
With the rapid rise of cloud adoption and advanced digital technologies, instances of cyber fraud and other malicious activities are increasing. Consequently, businesses are implementing IAM systems that incorporate identity analytics and intelligence to monitor unusual account behaviors and alert administrators of potential threats. IAM systems help businesses identify and remove inactive accounts, detect policy violations, and remove unauthorized access privileges. This reduces security risks and fosters compliance with data protection and privacy regulations, which are growing concerns for enterprises of all sizes. IAM also offers cost-effective solutions for application administration by centralizing connectivity and simplifying identity modifications, ultimately enhancing user reliability and reducing administrative tasks associated with access management.
Gather more insights about the market drivers, restrains and growth of the Identity And Access Management Market
Moreover, the integration of IAM solutions with mobile device management (MDM) further enhances their functionality and ensures comprehensive control over mobile access. MDM is an essential component of IAM, enabling administrators to control applications and users on mobile devices securely. Given that IAM is used on multiple device types, extending it to mobile devices becomes a critical need for organizations. MDM supports this by facilitating app provisioning, enforcing device security policies, and protecting each connected device, thereby improving overall security. Together, IAM and MDM create a robust security system for user identity and device control, providing flexibility and enhanced security for businesses with a mobile workforce.
Component Segmentation Insights:
The IAM market is categorized into several components, including audit, compliance & governance, directory service, multifactor authentication, provisioning, password management, and single sign-on (SSO). Among these, the provisioning segment led the market in 2022, accounting for over 29.70% of the total revenue. Provisioning services are vital because they add an extra security layer by authenticating and granting individual users controlled access to an organization’s information systems. This added security has bolstered the adoption of provisioning solutions, helping businesses protect sensitive data and restrict access only to verified users.
Multifactor authentication (MFA) is projected to grow at the fastest CAGR over the forecast period. MFA enhances security by requiring users to present multiple credentials (such as a password and a secondary code or biometric verification) before accessing applications. This added security layer significantly strengthens access control and reduces unauthorized access risks. Consequently, a growing number of businesses across diverse industries are adopting MFA to secure sensitive applications and data. With cyber threats on the rise, the demand for MFA is likely to continue to accelerate as organizations prioritize enhanced security measures to protect their operations.
The overall growth trajectory of the IAM market reflects an increasing demand for secure, scalable, and user-friendly access management solutions as digital platforms become more critical to business success. As the market evolves, IAM will continue to play a key role in helping organizations enhance security, ensure regulatory compliance, and improve operational efficiency.
Order a free sample PDF of the Identity And Access Management Market Intelligence Study, published by Grand View Research.
#Identity And Access Management Market Share#Identity And Access Management Market Trends#Identity And Access Management Market Growth#Identity And Access Management Industry
0 notes
Text
Identity And Access Management Market Research: Growth Opportunities by Regions, Types & Applications to 2030
The global identity and access management (IAM) market was valued at USD 15.93 billion in 2022, with expectations to grow at a compound annual growth rate (CAGR) of 12.6% from 2023 to 2030. IAM solutions provide a critical framework that ensures only authorized individuals and roles within an organization can access necessary resources, applications, and tools to fulfill their duties effectively. This system enables organizations to manage user access across various applications without needing administrator-level access for every single app, simplifying user management and boosting security. With the rise in IoT and AI technologies, heightened awareness around regulatory compliance, and increased digital platform reliance, the demand for IAM solutions is anticipated to grow significantly over the forecast period.
With the rapid rise of cloud adoption and advanced digital technologies, instances of cyber fraud and other malicious activities are increasing. Consequently, businesses are implementing IAM systems that incorporate identity analytics and intelligence to monitor unusual account behaviors and alert administrators of potential threats. IAM systems help businesses identify and remove inactive accounts, detect policy violations, and remove unauthorized access privileges. This reduces security risks and fosters compliance with data protection and privacy regulations, which are growing concerns for enterprises of all sizes. IAM also offers cost-effective solutions for application administration by centralizing connectivity and simplifying identity modifications, ultimately enhancing user reliability and reducing administrative tasks associated with access management.
Gather more insights about the market drivers, restrains and growth of the Identity And Access Management Market
Moreover, the integration of IAM solutions with mobile device management (MDM) further enhances their functionality and ensures comprehensive control over mobile access. MDM is an essential component of IAM, enabling administrators to control applications and users on mobile devices securely. Given that IAM is used on multiple device types, extending it to mobile devices becomes a critical need for organizations. MDM supports this by facilitating app provisioning, enforcing device security policies, and protecting each connected device, thereby improving overall security. Together, IAM and MDM create a robust security system for user identity and device control, providing flexibility and enhanced security for businesses with a mobile workforce.
Component Segmentation Insights:
The IAM market is categorized into several components, including audit, compliance & governance, directory service, multifactor authentication, provisioning, password management, and single sign-on (SSO). Among these, the provisioning segment led the market in 2022, accounting for over 29.70% of the total revenue. Provisioning services are vital because they add an extra security layer by authenticating and granting individual users controlled access to an organization’s information systems. This added security has bolstered the adoption of provisioning solutions, helping businesses protect sensitive data and restrict access only to verified users.
Multifactor authentication (MFA) is projected to grow at the fastest CAGR over the forecast period. MFA enhances security by requiring users to present multiple credentials (such as a password and a secondary code or biometric verification) before accessing applications. This added security layer significantly strengthens access control and reduces unauthorized access risks. Consequently, a growing number of businesses across diverse industries are adopting MFA to secure sensitive applications and data. With cyber threats on the rise, the demand for MFA is likely to continue to accelerate as organizations prioritize enhanced security measures to protect their operations.
The overall growth trajectory of the IAM market reflects an increasing demand for secure, scalable, and user-friendly access management solutions as digital platforms become more critical to business success. As the market evolves, IAM will continue to play a key role in helping organizations enhance security, ensure regulatory compliance, and improve operational efficiency.
Order a free sample PDF of the Identity And Access Management Market Intelligence Study, published by Grand View Research.
#Identity And Access Management Market Share#Identity And Access Management Market Trends#Identity And Access Management Market Growth#Identity And Access Management Industry
0 notes
Text
How Can You Bypass Your iPhone Passcode in Easy Steps?

Forgetting your iPhone passcode can be a frustrating experience, especially when you're locked out of your device and can't access important data. Whether you've recently changed your passcode or haven't used your phone in a while, learning how to bypass iPhone passcode restrictions can seem overwhelming. Fortunately, there are straightforward methods you can follow to unlock your device without requiring advanced technical knowledge.
In this guide, we’ll walk you through how to bypass iPhone passcode locks using step-by-step instructions with iTunes, Finder, or recovery mode. These solutions will help you restore your device and regain access, even if you can't remember the passcode. With easy-to-follow steps and helpful tips, you'll be able to bypass your iPhone passcode and get back to using your phone in no time.
Understanding iPhone Security and Passcodes
Before diving into methods of bypassing your passcode, it’s essential to understand why Apple’s security is so stringent. Apple's iOS operating system is built to protect user data from unauthorized access. One of the primary ways iPhones do this is through passcodes, Face ID, and Touch ID. If you enter the wrong passcode multiple times, your iPhone will lock itself for a specific period and eventually disable completely, requiring you to erase and restore the device.
Apple’s security also ensures that once a passcode is set, you cannot change, remove, or reset it without either the passcode itself or authorized access to your iCloud account.
Is It Possible to Bypass Your iPhone Passcode?
Yes, it is possible to bypass your iPhone passcode in this modern world. With advancements in technology, there are now many ways available to regain access to a locked iPhone. Whether you've forgotten your passcode or inherited a locked device, several methods exist that can help you bypass the passcode and unlock the phone. From using official Apple tools to specialized third-party software, you have a range of options depending on your specific situation.
In this article, we are going to explore the top methods to bypass your iPhone passcode with easy steps. These solutions are designed to guide you through the process quickly and efficiently, ensuring you can regain control of your device without unnecessary complications.
How To Bypass Your iPhone Passcode in Easy Steps Using Passixer:
If you're struggling to unlock your iPhone 11 due to a faulty Face ID sensor or a forgotten passcode, Passixer iPhone Unlocker offers a reliable solution. This tool is specifically designed to bypass various types of screen locks, including 4-digit or 6-digit passcodes, Face ID, and Touch ID. Additionally, Passixer enables the removal of Apple ID, Screen Time restrictions, iCloud activation locks, and MDM (Mobile Device Management) locks. Even if your iPhone's screen is broken, unresponsive, or disabled, this software can help you regain access without needing the passcode.
Compatible with all iOS versions, including iOS 17, Passixer iPhone Unlocker is easy to use, making it an ideal tool for bypassing iPhone passcodes without any technical knowledge. Below, we will outline its features, provide a detailed step-by-step guide, and list its advantages and drawbacks.
Key Features:
Unlock iPhone/iPad Screen Passcode:
Passixer can bypass any type of lock on your iPhone or iPad, whether it’s a forgotten 4-digit or 6-digit passcode, or an issue with Face ID or Touch ID. This tool allows you to bypass the lock without relying on iTunes or iCloud, making it particularly helpful when your device becomes disabled after repeated incorrect passcode attempts.
Remove Apple ID Without a Password:
If you’ve forgotten the password to an old Apple ID and can’t log out, Passixer lets you remove it completely. After removal, you can sign in with a new Apple ID and access services such as iCloud, iMessage, and FaceTime. This feature is especially useful for second-hand devices or when your Apple ID is disabled.
Bypass iCloud Activation Lock:
Passixer can help bypass iCloud Activation Lock without needing the Apple ID or password. This is perfect for those dealing with second-hand devices that are locked by a previous owner's credentials.
Remove MDM (Mobile Device Management) Lock:
If your iPhone or iPad is restricted by MDM, Passixer allows you to remove the MDM lock without requiring administrator credentials, giving you full control of your device again.
Remove Screen Time Passcode Without Data Loss:
Forgot your Screen Time passcode? Passixer can remove it without erasing any data, restoring full access to your device's features without having to reset the device.
Remove iTunes Backup Encryption:
Forgot the password for your encrypted iTunes backup? Passixer can decrypt the backup, ensuring that your data remains intact.
Compatible with a Wide Range of iOS Devices:
Passixer supports many iPhone, iPad, and iPod models, including the latest iPhone 16 and iOS 18, making it a versatile option for a wide user base.
Cross-Platform Support:
Passixer works seamlessly on both Windows and macOS, providing flexibility no matter your preferred operating system.
How To Use:
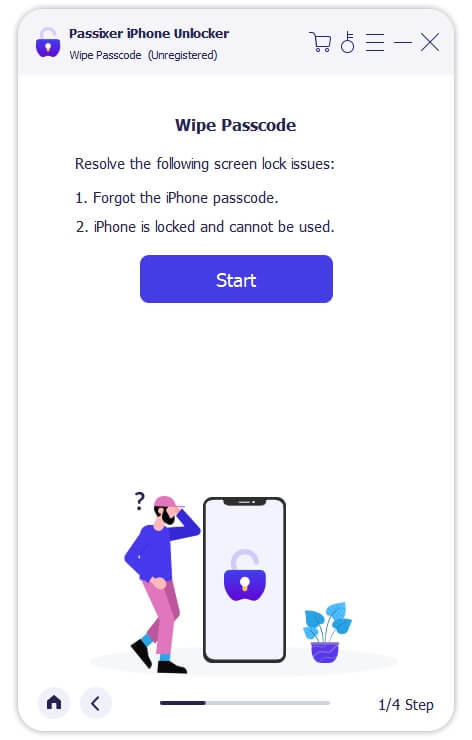
Step 1: Launch Passixer and Select Wipe Passcode
Download and install Passixer iPhone Unlocker on your computer. Launch the app, select "Wipe Passcode," and click "Start."
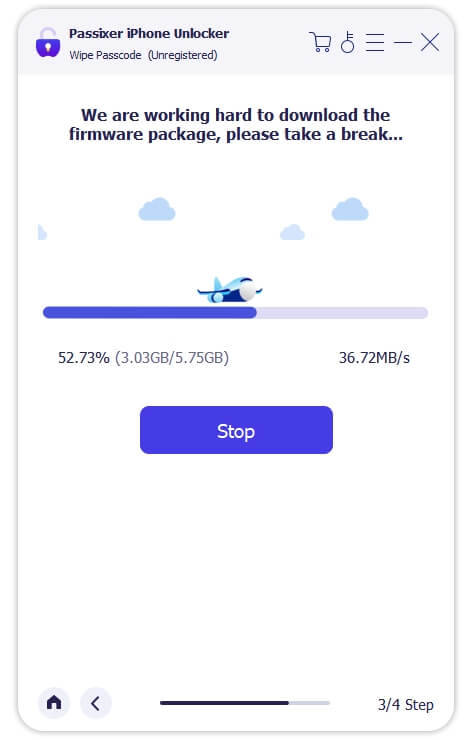
Step 2: Connect Your iPhone to the Computer
Connect your iPhone 11 via USB. Once detected, review your device's info and click "Download" to acquire the necessary firmware.
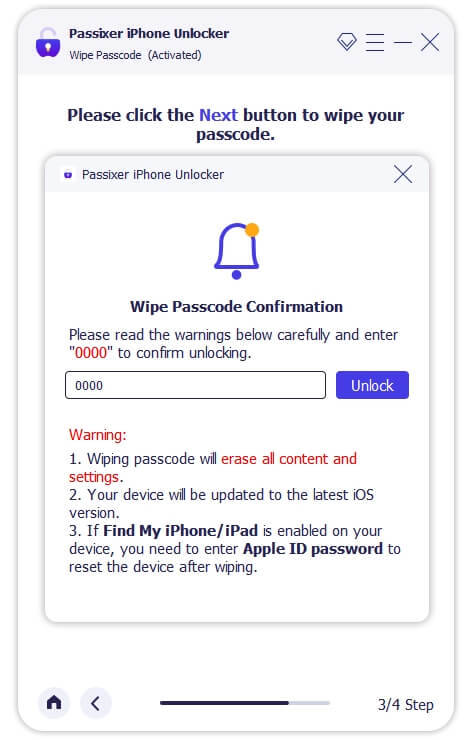
Step 3: Unlock Your iPhone
After downloading the firmware, click "Unlock," then enter "0000" to confirm. Click "Unlock" again and wait for the process to complete. Your iPhone will be unlocked successfully.
Pricing Plans:
Year License: $39.99 (discounted from $59.99, tax excluded). Covers 6 iOS devices and 1 PC.
1-Month License: $29.99 (discounted from $39.99, tax excluded). Suitable for 6 iOS devices and 1 PC.
Lifetime License: $69.99 (tax excluded). Includes coverage for 6 iOS devices and 1 PC, with a one-time payment for lifetime access.
Benefits Of Using Passixer To Bypass Your iPhone Passcode:
Simple and Fast Unlocking: Passixer offers a hassle-free way to bypass your iPhone passcode with an easy-to-use interface. Whether you're locked out due to a forgotten passcode, Face ID malfunction, or issues with Touch ID, Passixer streamlines the process, making it quick and straightforward for anyone to use.
Multiple Unlocking Functions: Passixer does more than just unlock passcodes—it can remove Apple IDs, bypass iCloud activation locks, and disable MDM (Mobile Device Management) restrictions. This makes it a versatile tool for fully regaining access to your device.
Compatible with Various iOS Devices: Supporting a wide range of iPhone, iPad, and iPod models, including the latest iPhone 15 and iOS 17, Passixer ensures its usefulness for both older and newer Apple devices, giving it broad appeal.
No iTunes or iCloud Required: Unlike conventional methods that require syncing with iTunes or iCloud, Passixer operates independently, allowing you to unlock your device without needing access to these services.
Remove Apple ID Without a Password: If you're unable to log into your Apple ID or want to remove an old Apple ID from a second-hand iPhone, Passixer allows you to completely remove the ID, letting you sign in with a new one and restore full device functionality.
Bypass MDM and Screen Time Locks: Passixer can effectively bypass Mobile Device Management (MDM) restrictions and Screen Time passcodes, giving you the freedom to use your iPhone without limitations, especially helpful for school- or company-managed devices.
Available on Windows and macOS: Passixer offers support for both Windows and macOS platforms, making it accessible no matter which operating system you prefer, ensuring flexibility for a wide range of users.
Cost and Time Efficient: Passixer saves you time and money by providing an affordable, at-home solution for unlocking your iPhone, eliminating the need for costly repair services or professional help.
Conclusion:
Forgetting your iPhone passcode can be a frustrating experience, leaving you locked out of your device and unable to access important information. Fortunately, this guide outlines straightforward methods to bypass iPhone passcode restrictions. By following the step-by-step instructions provided, you can regain access to your phone quickly and easily, restoring your ability to use your device without complications.
One of the most effective tools for bypassing iPhone passcodes is Passixer. This software is designed to unlock various types of screen locks, including 4-digit and 6-digit passcodes, as well as Face ID and Touch ID issues. Additionally, Passixer allows you to remove Apple IDs, bypass iCloud activation locks, and disable MDM restrictions, making it a versatile solution for regaining control of your device.
In summary, recovering access to your iPhone after forgetting your passcode is possible and can be done with relative ease. By utilizing tools like Passixer, you can navigate the unlocking process without needing extensive technical knowledge. Don’t let a forgotten passcode keep you from your device; follow the steps in this guide to swiftly regain access and enjoy all the features your iPhone has to offer.
1 note
·
View note
Text
The Role of MDM in Enhancing Data Quality
In today’s data-centric business world, organizations rely on accurate and consistent data to drive decision-making. One of the key components to ensuring data quality is Master Data Management (MDM). MDM plays a pivotal role in consolidating, managing, and maintaining high-quality data across an organization’s various systems and processes. As businesses grow and data volumes expand, the need for efficient data quality measures becomes critical. This is where techniques like deterministic matching and probabilistic matching come into play, allowing MDM systems to manage and reconcile records effectively.
Understanding Data Quality and Its Importance
Data quality refers to the reliability, accuracy, and consistency of data used across an organization. Poor data quality can lead to incorrect insights, flawed decision-making, and operational inefficiencies. For example, a customer database with duplicate records or inaccurate information can result in misguided marketing efforts, customer dissatisfaction, and even compliance risks.
MDM addresses these challenges by centralizing an organization’s key data—referred to as "master data"—such as customer, product, and supplier information. With MDM in place, organizations can standardize data, remove duplicates, and resolve inconsistencies. However, achieving high data quality requires sophisticated data matching techniques.
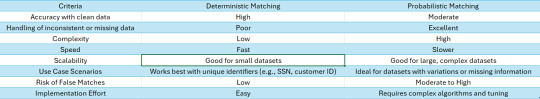
Deterministic Matching in MDM
Deterministic matching is a method used by MDM systems to match records based on exact matches of predefined identifiers, such as email addresses, phone numbers, or customer IDs. In this approach, if two records have the same value for a specific field, such as an identical customer ID, they are considered a match.
Example: Let’s say a retailer uses customer IDs to track purchases. Deterministic matching will easily reconcile records where the same customer ID appears in different systems, ensuring that all transactions are linked to the correct individual.
While deterministic matching is highly accurate when unique identifiers are present, it struggles with inconsistencies. Minor differences, such as a typo in an email address or a missing middle name, can prevent records from being matched correctly. For deterministic matching to be effective, the data must be clean and standardized.
Probabilistic Matching in MDM
In contrast, probabilistic matching offers a more flexible and powerful solution for reconciling records that may not have exact matches. This technique uses algorithms to calculate the likelihood that two records refer to the same entity, even if the data points differ. Probabilistic matching evaluates multiple attributes—such as name, address, and date of birth—and assigns a weight to each attribute based on its reliability.
Example: A bank merging customer data from multiple sources might have a record for "John A. Doe" in one system and "J. Doe" in another. Probabilistic matching will compare not only the names but also other factors, such as addresses and phone numbers, to determine whether these records likely refer to the same person. If the combined data points meet a predefined probability threshold, the records will be merged.
Probabilistic matching is particularly useful in MDM when dealing with large datasets where inconsistencies, misspellings, or missing information are common. It can also handle scenarios where multiple records contain partial data, making it a powerful tool for improving data quality in complex environments.
The Role of Deterministic and Probabilistic Matching in MDM
Both deterministic and probabilistic matching are integral to MDM systems, but their application depends on the specific needs of the organization and the quality of the data.
Use Cases for Deterministic Matching: This technique works best in environments where data is clean and consistent, and where reliable, unique identifiers are available. For example, in industries like healthcare or finance, where Social Security numbers, patient IDs, or account numbers are used, deterministic matching provides quick, highly accurate results.
Use Cases for Probabilistic Matching: Probabilistic matching excels in scenarios where data is prone to errors or where exact matches aren’t always possible. In retail, marketing, or customer relationship management, customer information often varies across platforms, and probabilistic matching is crucial for linking records that may not have consistent data points.
Enhancing Data Quality with MDM
Master Data Management, when coupled with effective matching techniques, significantly enhances data quality by resolving duplicate records, correcting inaccuracies, and ensuring consistency across systems. The combination of deterministic and probabilistic matching allows businesses to achieve a more holistic view of their data, which is essential for:
Accurate Reporting and Analytics: High-quality data ensures that reports and analytics are based on accurate information, leading to better business insights and decision-making.
Improved Customer Experience: Consolidating customer data allows businesses to deliver a more personalized and seamless experience across touchpoints.
Regulatory Compliance: Many industries are subject to stringent data regulations. By maintaining accurate records through MDM, businesses can meet compliance requirements and avoid costly penalties.
Real-World Application of MDM in Enhancing Data Quality
Many industries rely on MDM to enhance data quality, especially in sectors where customer data plays a critical role.
Retail: Retailers use MDM to unify customer data across online and offline channels. With probabilistic matching, they can create comprehensive profiles even when customer names or contact details vary across systems.
Healthcare: In healthcare, ensuring accurate patient records is crucial for treatment and care. Deterministic matching helps link patient IDs, while probabilistic matching can reconcile records with missing or inconsistent data, ensuring no critical information is overlooked.
Financial Services: Banks and financial institutions rely on MDM to manage vast amounts of customer and transaction data. Both deterministic and probabilistic matching help ensure accurate customer records, reducing the risk of errors in financial reporting and regulatory compliance.
Conclusion
Master Data Management plays a crucial role in enhancing data quality across organizations by centralizing, standardizing, and cleaning critical data. Techniques like deterministic and probabilistic matching ensure that MDM systems can effectively reconcile records, even in complex and inconsistent datasets. By improving data quality, businesses can make better decisions, provide enhanced customer experiences, and maintain regulatory compliance.
In today’s competitive market, ensuring data accuracy isn’t just a best practice—it’s a necessity. Through the proper application of MDM and advanced data matching techniques, organizations can unlock the full potential of their data, paving the way for sustainable growth and success.
0 notes
Text

What is MDM (Master Data Management)?
Master Data Management (MDM) is a comprehensive framework that enables organizations to manage their critical business data in a consistent, accurate, and centralized manner. It involves the processes, policies, and tools used to define, govern, and manage master data—the essential data that organizations rely on to operate their business. This data includes key entities such as customers, products, suppliers, and employees, as well as other critical business information like financial data and organizational structures.
The primary goal of MDM is to create a single, reliable source of truth for these key data entities, ensuring that they are consistent and accurate across the entire organization. This is crucial because, in most companies, data is often spread across multiple systems and departments, leading to discrepancies, duplications, and errors. Without proper management, these issues can result in inefficiencies, poor decision-making, and compliance risks.
MDM encompasses several key components:
Data Governance: This involves establishing policies, standards, and procedures for managing data. It ensures that data is collected, stored, and used in a way that meets business requirements and complies with regulatory standards.
Data Integration: MDM solutions integrate data from various sources and systems across the organization. This integration helps consolidate data into a unified view, eliminating silos and ensuring that everyone has access to the same, consistent information.
Data Quality Management: MDM includes processes for ensuring the quality of data. This involves cleaning and validating data to remove duplicates, correct inaccuracies, and standardize information. High-quality data is essential for reliable business insights and decision-making.
Data Stewardship: This refers to the role of individuals or teams responsible for managing and maintaining data quality. Data stewards oversee the implementation of data governance policies and ensure that data is accurate and consistent.
Master Data Modeling: MDM involves defining the data model for master data entities. This includes determining how these entities are related to each other and ensuring that data relationships are accurately represented.
MDM is particularly valuable in industries where accurate and consistent data is critical, such as healthcare, finance, retail, and manufacturing. For example, in healthcare, MDM helps maintain accurate patient records, improving care quality and operational efficiency. In retail, it ensures that product information is consistent across all channels, enhancing the customer experience.
In summary, MDM is a vital practice that helps organizations manage their essential data assets effectively. By establishing a single source of truth, ensuring data quality, and providing consistent information across the enterprise, MDM enables businesses to make better decisions, improve efficiency, and comply with regulations. Whether for operational efficiency, customer satisfaction, or strategic planning, MDM is a foundational element for any data-driven organization.
Learn more at: https://www.piloggroup.com/What-Why-How-master-data-managment-MDM-101.php
#business#technology#software#data#it solutions#motivation#quality#succession#support#transformation#tools#growth#industrial design#explore
0 notes
Text

MDMFix Tool Activation
🔥MdmfixTool, Big Update Released🔥
🚀 Introducing MdmfixTool – A World-First Innovation! 🚀 World- First Android-14 KG MDM Unlock Solution
MdmFixTool Can Unlock KG Android 14 in ADB Mode Samsung ALL Model Supported KG Unlock Samsung ALL Android Supported KG Unlock Samsung ALL SPU Supported KG Unlock MTK-EXYNOS-QUALCOMM-SPD
Download Tool From MdmFixTool.com
Activation www.asunlocker.com
WhatsApp: +8801721672766
#mdmfix#mdmfix tool#asunlocker#mdmfix tool activation#mdm remove tool#asunlocker.com#mdm remove solution#kg remove#samsung kg remove tool#activation#unlock#remove
0 notes
Text
How to Unlock a Disabled iPhone without iTunes? Easy Tips

"An iPhone becomes disabled when the wrong passcode is entered multiple times in a row," explains Tenorshare. "This security feature helps protect your data, but it can also lock you out of your own device." In this guide we will provide comprehensive tips on how to unlock a disabled iPhone without using iTunes or iCloud. This is crucial for users who forget their passcode, have children who enter the wrong code repeatedly, inherit a locked device, etc. How to Unlock a Disabled iPhone without iTunes or Wi-Fi? If you don't have access to the internet, you can unlock a disabled iPhone without Wi-Fi via Tenorshare 4uKey. It is an iOS unlocker tool that helps you bypass screen locks, Apple IDs, MDM locks, and iCloud Activation locks. Features of Tenorshare 4uKey - Unlocks All Types of Screen Locks: Whether you have a passcode, face ID, or fingerprint ID, 4uKey can unlock all. - 100% Success Rate: It unlocks your device with guaranteed success. Typically faster than iCloud's erase. - No Experience Required: You can unlock your device with no prior experience. - Wide Compatibility: 4uKey works on all iPhone models. Here are the steps on how to unlock iPhone is disabled without iTunes via 4uKey: - Download and launch 4uKey. Connect your iPhone to your PC. - Click "Start" in the "Unlock iOS Screen" tab, after which 4uKey will download the required firmware. - Click "Start to Remove" to unlock disabled iPhone without restoring it. How to Unlock a Disabled iPhone Without iTunes or Computer? Another way to reset passcode on iPhone without iTunes is via iCloud. For this, you need to use another iPhone or iPad to sign into iCloud and erase your device remotely. However, this method erases all data and settings from your device. To mitigate this, ensure you have backed up your data before proceeding. Here is how to unlock disabled iPhone without iTunes free via iCloud: - Use another device to log in to iCloud using your Apple ID and password. - Click "Find iPhone," and when your disabled iPhone shows up, click "Erase Device." How to Unlock a Disabled iPhone without iTunes or iCloud or Computer? If you don't have access to iTunes, iCloud, or a PC, you can use the "Erase iPhone" option directly on your device, provided you remember your Apple ID and password. This method will reset your device to factory settings, erasing all data, and allows for immediate reset without needing another device. - On your disabled iPhone, tap "Erase iPhone" at bottom of the screen. - Enter your Apple ID and password to confirm selection. How to Unlock a Disabled iPhone without iTunes Read the full article
0 notes
Video
youtube
Haafedk iCloud Remove tool v4.2 download latest version 2024. bypass MDM...
1 note
·
View note
Video
youtube
Haafedk iCloud Remove tool free V4.2 - unlock iCloud and MDM tool IOS 1...
0 notes
Text
Maximizing Efficiency with Mobile Management Solutions: A Comprehensive Guide

In the contemporary business landscape, mobile devices are integral to everyday operations, driving productivity, communication, and flexibility. However, managing a growing array of mobile devices presents significant challenges, particularly in security, compliance, and device maintenance. This is where mobile management solutions come into play. In this comprehensive guide, we'll explore how mobile management solutions can help businesses maximize efficiency, secure their mobile infrastructure, and streamline operations.
Understanding Mobile Management Solutions
Mobile management solutions encompass a range of tools and technologies designed to manage and secure mobile devices within an organization. These solutions include Mobile Device Management (MDM), Mobile Application Management (MAM), and Mobile Content Management (MCM), all aimed at ensuring that mobile devices and the data they access are protected and efficiently managed.
Key Benefits of Mobile Management Solutions
Enhanced Security Security is a primary concern for businesses leveraging mobile technology. Mobile management solutions provide robust security features, such as device encryption, remote wipe capabilities, and secure access controls. By implementing these solutions, businesses can protect sensitive data from unauthorized access, minimize the risk of data breaches, and ensure compliance with industry regulations.
Streamlined Device Management Managing a diverse fleet of mobile devices can be complex and time-consuming. Mobile management solutions offer centralized control, allowing IT administrators to manage device settings, deploy updates, and enforce security policies from a single interface. This centralized management reduces administrative overhead and ensures that all devices are consistently configured and maintained.
Improved Compliance Regulatory compliance is critical for businesses, especially those handling sensitive data. Mobile management solutions help enforce compliance by ensuring that all devices adhere to corporate policies and regulatory standards. Detailed reporting and audit capabilities enable businesses to demonstrate compliance and identify non-compliant devices promptly.
Increased Productivity By providing secure access to corporate resources, mobile management solutions enable employees to work efficiently from anywhere. These solutions support remote work by offering secure access to emails, applications, and documents, enhancing collaboration and productivity. Additionally, automated app distribution and updates ensure that employees always have access to the latest tools and features.
Cost Savings Implementing mobile management solutions can lead to significant cost savings. Automated device management and maintenance reduce the need for manual IT interventions, while enhanced security features minimize the risk of costly data breaches. Furthermore, the ability to manage devices remotely reduces the need for physical IT support, particularly for remote or geographically dispersed teams.
Components of Effective Mobile Management Solutions
Mobile Device Management (MDM) MDM is the cornerstone of mobile management solutions, providing tools for managing and securing mobile devices. Key features of MDM include device enrollment, configuration management, security policy enforcement, and remote monitoring. MDM ensures that all devices within the organization are compliant, secure, and efficiently managed.
Mobile Application Management (MAM) MAM focuses on managing and securing mobile applications. This includes app distribution, updating, and removal, as well as managing app permissions and data access. MAM ensures that employees have access to necessary applications while preventing unauthorized apps from being installed on corporate devices.
Mobile Content Management (MCM) MCM provides secure access to corporate content and documents. This component ensures that sensitive data is encrypted and accessible only to authorized users. MCM solutions often include features such as document sharing, real-time collaboration, and secure storage, facilitating efficient and secure content management.
Identity and Access Management (IAM) Integrating IAM with mobile management solutions enhances security by ensuring that only authorized users can access corporate resources. IAM solutions provide features such as single sign-on (SSO), multi-factor authentication (MFA), and role-based access controls, strengthening the overall security posture.
Implementing Mobile Management Solutions
Assess Your Needs Before implementing a mobile management solution, assess your organization’s specific needs and goals. Consider factors such as the number of devices, types of applications, security requirements, and regulatory compliance.
Choose the Right Solution Select a mobile management solution that aligns with your business requirements and offers a comprehensive suite of features. Evaluate solutions based on their security capabilities, ease of use, scalability, and customer support.
Develop a Policy Develop a clear mobile device policy outlining acceptable use, security requirements, and compliance guidelines. Ensure that all employees are aware of and adhere to this policy.
Plan the Deployment Create a detailed deployment plan that includes timelines, resource allocation, and training for IT staff and end-users. Involve key stakeholders in the planning process to ensure a smooth implementation.
Pilot the Solution Conduct a pilot phase to test the solution with a small group of users. Gather feedback and address any issues before rolling out the solution across the entire organization.
Monitor and Optimize After deployment, continuously monitor the performance of your mobile management solution and make necessary adjustments. Regularly review security policies, perform audits, and update the software to address emerging threats and vulnerabilities.
Conclusion
Mobile management solutions are essential for modern businesses to manage, secure, and optimize their mobile infrastructure. By implementing a comprehensive mobile management strategy, businesses can enhance security, ensure compliance, and improve productivity. As mobile technology continues to evolve, investing in robust mobile management solutions will help businesses stay ahead of security threats, streamline operations, and drive long-term success.
0 notes
Text
Why Master Data Management Matters
In today's data-driven world, businesses are drowning in information. Customer records sprawl across siloed systems, product details differ between departments, and supplier data lacks consistency. This fragmented data landscape leads to errors, inefficiencies, and ultimately, poor decision-making.
Enter Master Data Management (MDM), the hero businesses need to conquer their data chaos. MDM is a strategic approach that ensures the uniformity, accuracy, and completeness of core business data, often referred to as "master data." This master data can include anything from customer and product information to supplier and location details.
Understanding Master Data Management
Master Data Management is a methodology that involves creating a single, consistent view of critical data entities within an organization. This includes customer information, product data, financial records, and more. By centralizing and synchronizing this data across systems, MDM ensures data accuracy, consistency, and reliability.
Master Data Management Market Overview
The Master Data Management market is witnessing significant growth, driven by the increasing importance of data quality and governance. Key players in this market include industry giants like IBM, Oracle, SAP, SAS, and Informatica. The market is segmented based on components, deployment modes, organization sizes, application areas, industry verticals, and regions.
Market Segmentation:
Components: Solutions, Services (Consulting, Integration, Training & Support)
Deployment Modes: Cloud, On-premises
Organization Size: SMEs, Large Enterprises
Verticals: BFSI, Government, Retail, IT & Telecom, Manufacturing, Healthcare, and more
Why is Master Data Management Market Booming?
The Master Data Management market is expected to experience significant growth in the coming years. This surge is driven by several factors:
The increasing importance of data quality: Businesses are realizing that dirty data leads to dirty decisions. MDM helps them cleanse and standardize their data, leading to better insights and improved business performance.
The rise of digital transformation: As companies move more processes online, the need for consistent and reliable master data becomes paramount. MDM provides a single source of truth for all critical data, which is essential for smooth digital transformation.
Regulatory compliance: Data privacy regulations like GDPR and CCPA are mandating stricter data governance practices. MDM helps organizations comply with these regulations by ensuring data accuracy and accountability.
Master Data Management Tools
Implementing a successful MDM strategy requires the right tools. Here's where master data management tools come in. These software solutions automate various MDM tasks, including:
Data cleansing and standardization: MDM tools identify and remove inconsistencies in your data, ensuring all formats and definitions are aligned.
Data matching and consolidation: These tools help you identify duplicate records and create a single, unified master record for each entity.
Data enrichment: MDM solutions can enrich your master data with additional information from external sources, providing a more comprehensive view of your data.
Choose the Right Tool
Quadrant Knowledge Solutions' reports "Market Share: Master Data Management, 2022, Worldwide" and "Market Forecast: Master Data Management, 2022-2027, Worldwide" are valuable resources for organizations seeking insights into the Master Data Management (MDM) landscape. These reports offer crucial information that aids in selecting the right tools for effective data management strategies.
The "Market Share: Master Data Management, 2022, Worldwide" report provides an overview of the market landscape, highlighting the key players and their respective market shares in the MDM domain. Understanding the market share of different MDM solutions allows organizations to assess the popularity and adoption rates of various tools, aiding in decision-making processes when choosing the most suitable MDM tool for their specific needs.
On the other hand, the "Market Forecast: Master Data Management, 2022-2027, Worldwide" report offers insights into the future trends and growth projections within the MDM market. By forecasting the market dynamics over the next few years, organizations can anticipate industry shifts, technological advancements, and emerging opportunities, enabling them to align their data management strategies with the evolving landscape.
Both reports from Quadrant Knowledge Solutions play a pivotal role in guiding organizations towards selecting the right MDM tools. By leveraging the information provided in these reports, businesses can make informed decisions, evaluate the competitive landscape, understand market trends, and ultimately choose the most suitable Master Data Management solutions that align with their strategic objectives and data management requirements.
Top Master Data Management Tools
Ataccama ONE: A comprehensive platform offering data discovery, profiling, metadata management, data quality, and more.
IBM InfoSphere Master Data Management: Manages critical enterprise data, ensuring compliance with governance rules and policies.
Informatica Multidomain MDM: Provides a single view of data, enabling the creation of an authoritative view from disparate sources.
Reltio Connected Customer 360: A cloud-native platform with graph technology and machine learning capabilities.
SAP Master Data Governance: Offers enterprise MDM functionality with support for all master data domains.
Mastering Your Data, Mastering Your Business
Investing in Master Data Management is an investment in the future of your business. By ensuring clean, consistent, and reliable data, you can:
Improve decision-making across all levels of your organization.
Enhance customer experiences with personalized interactions.
Boost operational efficiency and reduce costs associated with data errors.
Gain a competitive edge through better data-driven insights.
Don't let your data become a burden. With Master Data Management get clean, unified data to drive business success.
Conclusion
Master Data Management plays a pivotal role in ensuring data integrity and consistency across organizations. As the data landscape continues to change, investing in robust MDM solutions becomes imperative for businesses seeking to leverage data effectively. By understanding the market trends and exploring the top MDM tools available, organizations can embark on a journey towards efficient data management and decision-making. This blog provides a glimpse into the world of Master Data Management, highlighting its significance, market dynamics, and leading tools shaping the data management landscape. Embracing MDM is not just a choice but a strategic imperative for organizations looking to thrive in the era of data-driven decision-making.
#MasterDataManagementTools#MasterDataManagementSolutions#MasterData#MasterDataGovernance#MDMSystems#MDMMasterDataManagement#MasterDataManagementVendors#MDMData#MasterDataManagementPlatforms#MasterDataManagementStrategy
1 note
·
View note