#maltego
Explore tagged Tumblr posts
Text
Conversion Therapy
Like Captain Hook and his temporal detectable crocodile, this graph haunts me and I hear a ticking clock when I open it.

Way back in the fall of 2020, three months before the election, the events in MAGA world were getting complex. I opened Maltego, pasted in a URL, used the Named Entity Recognition transform that accesses IBM’s Watson, and the initial graph filled with a dozen names. Now a thousand days have elapsed, there are 1,088 URLs in there, and an astonishing 2,908 names. The 5,672 entities and 13,011 links connecting them have become a sort of Rosetta stone, a thing that gets opened when reporters I know are fact checking complex flows of events.
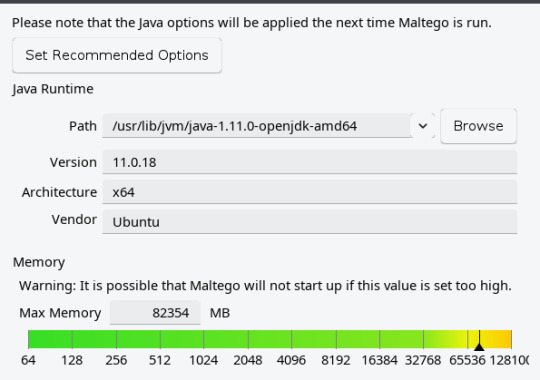
But there’s trouble here. Maltego is a Java application and that graph is enormous. When you give Java more than 31 gigabytes of memory it switches to using 64 bit pointers and your actual usable space yield declines. If you need more than 31 gig, the next sensible number is not 32, it’s 49. A couple months ago I upped the allocated memory to 64 gig and that helped for a while. Now it really does need 80 gig if I’m going to work with that graph and pull a slice of it out in order to share with someone else.
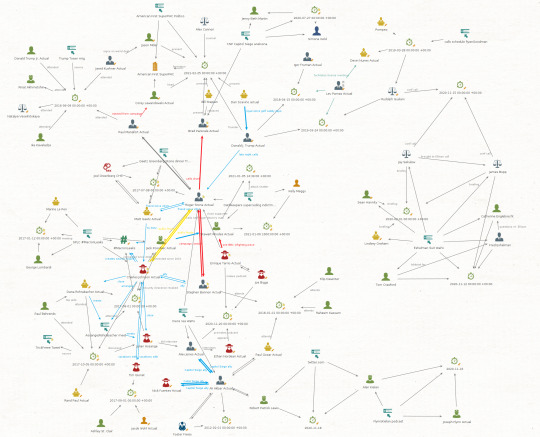
There are other subtle problems that can’t easily be depicted in a screen shot. Twenty one Date/Time entities have crept into the graph.

And this is the real circus. There are 189 events … and an event is a child entity of … Location. They have timestamps as an internal attribute, but Maltego doesn’t really have any tools to handle temporal data.
This situation is untenable. That graph won’t work reliably on my desktop and only hardcore gamers have more capability than my setup. There are four other tools I use that can handle data relationships:
Gephi can handle a quarter million nodes in a graph but it lacks features for handling geospatial, temporal, or diverse entity data.
Graphistry is a web accessible GPU driven commercial alternative to Gephi, but with similar constraints on data types.
Tulip is an intriguing Gephi competitor, but more a framework for doing serious artwork with smaller datasets and richer network layout needs.
And that leaves Sentinel Visualizer. This is a full featured link analysis package meant for corporate fraud investigation, law enforcement, and intelligence activities. It’s Windows only, which pains me a bit, as I changed careers twenty five years ago to get out from under Microsoft’s marketing weasel driven chaos. But I think I’ve got something workable here:

So that’s Windows 10, and I’ve got it treed in a VirtualBox VM. I gave it 40 gig of memory and ten of twelve cores. I spent an evening Googling and fiddling with virtualization settings and I’ve finally got something usable in terms of speed.
Every other OS you can install in a VM, give it some resources, and it’ll just run. Windows seems to need the Guest Additions installed, a couple reboots, cursing in English and one other optional language of your choice, another install of Guest Additions, and then giving up and walking away in disgust overnight. Complete this ritual and you’ll be left with an operational system.
If this were an actual physical system we would not be having this conversation. Microsoft’s utter disrespect for the value of my time in the 1990s was intolerable and in this area I have not mellowed with age. But with a Linux host and VMware I can do essentially instant backup and restore using the ZFS snapshot feature and it’s possible to export the machine in OVA format as an offline backup.

And that's the first step data wise. I fed it an export of names, then some URLs. I'm puzzling over how to use Maltego's internal UUID with Sentinel Visualizer, without smearing an endless blur of visually very similar strings all over the display.
I have a couple projects in mind with this:
The MAGA world meltdown graph has to be either moved or abandoned.
There are a LOT of interesting datasets from Ukraine that involve both geospatial and temporal data.
There are famous historical battles that are well documented enough to make for a nice graph, but I've yet to see a source that offers both geospatial and temporal data in tabular form.
So that's the direction we're headed for the second half of 2023. If I get something worthwhile put together, I will make it available for use with Sentinel Visualizer Reader.
2 notes
·
View notes
Text
Maltego: Desentrañando Redes y Relaciones en el Mundo de la Ciberseguridad
En un mundo digital cada vez más interconectado, la capacidad de identificar y analizar patrones, relaciones y conexiones es crucial para proteger sistemas y prevenir amenazas. Entre las herramientas más potentes en el arsenal de los profesionales de ciberseguridad, investigadores y analistas forenses, destaca Maltego: una solución innovadora diseñada para revelar y mapear datos ocultos en redes,…
0 notes
Text
Pentest: Teste de Penetração – 2023
A melhor defesa é um bom ataque. O número crescente de incidentes também alimentou a necessidade de testes contínuos de nossos sistemas de defesa.
04-fev-2023 Os incidentes de cibersegurança têm aumentado desde o início da pandemia de Covid-19, o que prova que ainda faltam as nossas defesas de cibersegurança. Mas há pelo menos um lado positivo nesses incidentes: eles aumentaram a conscientização pública sobre como os sistemas de tecnologia da informação (TI) e tecnologia operacional (OT) são vulneráveis. Eles mostraram que as tecnologias…
View On WordPress
#Agendamento#Bloodhound#cibersegurança#Crt.sh#escalação#Escopo#exfiltração#Exploração#Ffuf#inPEAS#Invasão#Maltego#Masscan#Mimikatz#nmap#Nuclei#Pentest#Persistência#Reconhecimento#Shodan.io#sqlmap#SubBrute#tplmap
0 notes
Link
Maltego 4.2.19.13940 Crack free download is a marvelous solution for the information collecting and organizing. Collect the inside information of the
0 notes
Text
[Media] Maltego Web2Screenshot Transforms
Maltego Web2Screenshot Transforms The #Maltego Web2Screenshot Transforms allow you to capture screenshots from both websites and URLs in a secure and anonymous manner. I developed these transforms to enhance my operational security (OPSEC) by avoiding exposing my public or VPN's IP address. With these Transforms, you can generate high-quality screenshots while keeping your identity and location hidden. https://github.com/TURROKS/Maltego_Web2Screenshot #infosecurity #cybersecurity #infosec

2 notes
·
View notes
Text
youtube
Summary
���� Introduction to Dark Web OSINT:
Kirby Plessas, a former military intelligence analyst, shares her methodology for conducting OSINT investigations on the dark web.
Focused on leveraging tools and techniques to collect and analyze data while maintaining operational security (OPSEC).
🔍 Key Topics and Techniques:
Tools and Environment:
Use of virtual machines (VMs), VPNs, and the Tor browser for safe exploration.
Bookmarking important sites to maintain continuity in investigations.
Recon Techniques:
Analyze vendor profiles, transaction histories, and product listings to identify patterns.
Reverse image searches and metadata extraction to trace images back to their origins.
Social Network Analysis Tools:
Tools like Maltego, Case File, and Aeterna Notebook are used to map connections and identify relationships.
Integration of disparate datasets to uncover hidden linkages.
🛠️ Investigative Workflow:
Scraping and indexing dark web sites using add-ons like Scrapbook for offline analysis.
Using tools like Stolen Camera Finder and blockchain explorers to trace digital assets.
Leveraging Google Dorks and RSS feeds for real-time monitoring of dark web activities.
🎯 Challenges and Recommendations:
The dark web's dynamic nature requires constant adaptation of tools and techniques.
Emphasized the importance of ethical practices to ensure data collection remains lawful and respectful of privacy.
0 notes
Text
Best Practices for Conducting Penetration Testing with Burp Suite and Maltego
Penetration testing is a critical aspect of information security, enabling organizations to identify vulnerabilities and strengthen their defenses against potential threats. In this comprehensive guide, we will explore the best practices for conducting penetration testing using the Burp Suite and Maltego. We will cover the technical background, implementation guide, code examples, best practices,…
0 notes
Text
Open-Source Intelligence Market Competitiveness: Strategies for Sustainable Market Positioning

Strategic Insights and Forecasts: Open-Source Intelligence Market Leaders
The Open-Source Intelligence Size report is anticipated to experience significant growth in the coming years. As the world continues to recover from the pandemic, the market is expected to expand. The Open-Source Intelligence research not only highlights current industry standards but also reveals the latest strategic trends and patterns among market players. This research serves as an essential business document, aiding global market buyers in planning their next steps regarding the market's future trajectory.
According to Straits Research, the global Open-Source Intelligence market size was valued at USD 7715.2 Million in 2021. It is projected to reach from USD XX Million in 2022 to USD 55848.3 Million by 2030, growing at a CAGR of 24.7% during the forecast period (2022–2030).
The Open-Source Intelligence Report is an essential resource for business strategists, offering insightful data and analysis. It includes an industry overview, growth analysis, and historical and projected figures for cost, revenue, supply, and demand (where applicable). Research analysts offer a thorough description of the value chain and distributor analysis. This report provides comprehensive information to deepen understanding, broaden the scope, and enhance the application of the findings.
Get Free Request Sample Report @ https://straitsresearch.com/report/open-source-intelligence-market/request-sample
Leading Open-Source Intelligence Market include: -
Digital Clues
Alfresco Software Inc.
Octogence Tech Solutions Pvt. Ltd.
Palantir Technologies Inc.
Recorded Future Inc.
Google Llc
Maltego Technologies Gmbh
Offsec Services Limited
Expert System S.P.A.
Thales Group
The Open-Source Intelligence Market Report helps a wide range of businesses determine what their consumers truly want by doing extensive market research. When it comes to new products, every company owner wants to know how much demand there is, and this report is a great resource. Additional benefits include ensuring that the most recent market developments are covered. You may closely check key rivals and their company growth tactics by reading the Open-Source Intelligence market research. It also does an in-depth research for the years 2022-2030 in order to provide company owners with new business options.
This research also provides a dashboard view of prominent Organizations, highlighting their effective marketing tactics, market share and most recent advances in both historical and current settings.
Global Open-Source Intelligence Market: Segmentation
By Source
Media
Internet
Public and Government
Professional and Academic Publications
Commercial
Others
By Techniques
Text Analytics
Video Analytics
Social Analytics
Geospatial Analytics
Security Analytics
Others
By Security
Data Analytics
Human Intelligence
Artificial Intelligence Security
Content Intelligence
Network Analytics
By End-Users
Government Intelligence Agencies
Military Intelligence Agencies
Cybersecurity Organization
Law Enforcement Agencies
Financial Services
Private Specialized Business
Public Sector
National Security
Others
The report forecasts revenue growth at all the geographic levels and provides an in-depth analysis of the latest industry trends and development patterns from 2022 to 2030 in each of the segments and sub-segments. Some of the major geographies included in the market are given below:
The regions covered include:
North America (United States, Canada, Mexico)
Europe (United Kingdom, France, Germany, Russia)
Asia-Pacific (China, Japan, Australia, Indonesia)
Middle East and Africa (UAE, Iran, Syria, South Africa)
South America (Brazil, Peru, Chile, Colombia)
This Report is available for purchase on Buy Open-Source Intelligence Market Report
Reasons to Purchase This Report:
The Open-Source Intelligence Market report provides an analysis of the evolving competitive landscape.
The report offers valuable analytical insights and strategic planning tools to support informed business decisions.
Researchers highlight key market dynamics, including drivers, restraints, trends, developments, and opportunities.
The report includes regional market estimates and business profiles of various stakeholders.
It helps in understanding all significant market segments.
The report provides extensive data on trending factors that will impact market growth.
Research Methodology:
We employ a robust research methodology that includes data triangulation based on top-down and bottom-up approaches, along with validation of estimated market figures through primary research. The data used to estimate the Open-Source Intelligence market size and forecast across various segments at the global, regional, and country levels is sourced from the most reliable published materials and through interviews with relevant stakeholders.
About Us:
StraitsResearch.com is a leading research and intelligence organization, specializing in research, analytics, and advisory services along with providing business insights & research reports.
Contact Us: Email: [email protected] Address: 825 3rd Avenue, New York, NY, USA, 10022 Tel: +1 6464807505, +44 203 318 2846
#Open-Source Intelligence#Open-Source Intelligence Industry#Open-Source Intelligence Share#Open-Source Intelligence Size#Open-Source Intelligence Trends#Open-Source Intelligence Regional Analysis#Open-Source Intelligence Growth Rate
1 note
·
View note
Text
Criminal IP and Maltego Collaborate to Broaden Threat Intelligence Data Search
http://securitytc.com/TBq3W8
0 notes
Text
OSINT là viết tắt của “open source intelligence”. Khái niệm này ám chỉ việc tìm kiếm thông tin mà bạn có thể truy cập hợp pháp, thông qua các phương tiện hợp pháp. OSINT chủ yếu được thực hiện trực tuyến, nhưng nó cũng có thể được thực hiện ngoại tuyến. Pentesters sử dụng OSINT để nghiên cứu các mục tiêu của họ và các chuyên gia tình báo về mối đe dọa sử dụng OSINT để tìm hiểu về các mối đe dọa mạng. OSINT là một công cụ quan trọng cho cả đội đỏ và đội xanh. Dưới đây là một số công cụ phổ biến nhất cho OSINT. 10 công cụ OSINT mà hacker cần biết Shodan Shodan là một công cụ tìm kiếm các thiết bị mạng có thể khai thác trên internet, chẳng hạn như máy chủ và thiết bị IoT. Có thể khai thác tức là có thể truy cập công khai. Có thể đặt một máy chủ, thiết bị ngoại vi IoT hoặc thiết bị mạng trên internet và định cấu hình nó tương đối riêng tư và khó lấy dấu vân tay. Nhưng nếu một thiết bị được kết nối với Internet mà không có cấu hình bảo mật cẩn thận, bạn có thể tìm thấy thiết bị đó thông qua Shodan với các tìm kiếm phù hợp. Sử dụng Shodan mà không có tài khoản trả phí sẽ trả về một số lượng kết quả tìm kiếm rất hạn chế. Tài khoản trả phí hữu ích hơn rất nhiều nếu loại nghiên cứu không gian mạng OSINT mà bạn thực hiện yêu cầu khám phá máy chủ, thiết bị mạng và thiết bị ngoại vi IoT (chẳng hạn như máy ảnh). Maltego Maltego chạy như một ứng dụng dành riêng cho máy tính để bàn Windows, Mac và Linux, cho phép người dùng truy cập vào nhiều nguồn dữ liệu cho các mục đích OSINT, nghiên cứu báo chí và pháp y. Có hơn 58 nguồn dữ liệu trong Maltego tính đến thời điểm mình viết bài này, bao gồm mã hóa địa lý Google Maps, AlienVault OTX, ATII Hades Darkweb Intelligence, Blockchain.info, Crowdstrike, VirusTotal, và nhiều nguồn khác. Mình hy vọng số lượng nguồn dữ liệu được tích hợp vào Maltego sẽ tăng lên theo thời gian. Giá trị mà Maltego cung cấp cho các nhà nghiên cứu không chỉ ở bộ sưu tập nguồn dữ liệu khổng lồ mà còn ở cách nền tảng của nó có thể hiển thị cho người dùng các mẫu và xu hướng dữ liệu thông qua biểu đồ hình ảnh có thể tùy chỉnh cao. Lên đến một triệu thực thể có thể được vẽ trong biểu đồ mà Maltego tạo. Tất nhiên, bạn có thể tận dụng tất cả các tính năng của Maltego nhưng không phải là miễn phí, mặc dù họ sẽ cho phép bạn xem bản demo trước khi bạn quyết định đăng ký. Nhưng nếu bạn không muốn trả tiền, Maltego Community Edition miễn phí vẫn có thể rất hữu ích. Google Dorks Google Dorks không phải là một ứng dụng. Đúng hơn, đó là một kỹ thuật sử dụng công cụ tìm kiếm Google mà mọi người đều sử dụng hàng ngày. Đừng đi tìm ứng dụng Google Dorks chính thức, ứng dụng này không tồn tại đâu. Nhưng có những nhà phát triển đã phát triển các công cụ phần mềm mã nguồn mở cho Google Dorking mà bạn có thể thử, chẳng hạn như Pagodo và GoogleDorker. Một chiến lược Google Dorking điển hình bắt đầu bằng việc sử dụng các truy vấn tìm kiếm đơn giản và sau đó chuyển sang các truy vấn phức tạp hơn. Hầu hết mọi người chỉ nhập các chuỗi văn bản vào tìm kiếm của Google, chẳng hạn như “dự báo thời tiết” hoặc “abc xyz”. Nhưng có một số toán tử tìm kiếm có thể được sử dụng trong tìm kiếm của Google để trả lại nhiều kết quả đúng ý định của bạn hơn. Ví dụ: bạn có thể thử “site: anonyviet.com” để tìm kiếm cụ thể trên trang web của mình hoặc sử dụng các dấu ngoặc kép xung quanh một cụm từ tìm kiếm để chỉ trả về kết quả có sử dụng cụm từ tìm kiếm chính xác đó. Google cung cấp danh sách các mẹo để tinh chỉnh các tìm kiếm trên Google của bạn tại đây. Rất nhiều trang web được cấu hình rất kém khi nói đến an ninh mạng. Các bot thu thập thông tin web của Google hoạt động hiệu quả nhất trên web khi chúng có quyền truy cập để khám phá. Vì vậy, Google Dorking có thể là một kỹ thuật để tìm dữ liệu như địa chỉ email, thông tin đăng nhập và số ngân hàng chưa được bảo mật đúng cách. Recon-ng Recon-ng là một công cụ do thám web mã nguồn mở. Sức mạnh của nó sẽ được tăng lên bởi các mô-đun mà bạn có thể cài đặt cho nó. Nếu bạn sử dụng Recon-ng một cách hiệu quả, bạn có thể tiết kiệm rất nhiều thời gian trong việc nghiên cứu OSINT.
Recon-ng có thể chạy từ dòng lệnh. Nếu bạn muốn làm cho Recon-ng hữu ích cho mục đích của mình, hãy chọn tùy chọn Marketplace từ menu chính và khám phá những gì có sẵn. Có một số lượng lớn các mô-đun mà bạn có thể thử, với nhiều mô-đun được cải tiến và bổ sung liên tục. Nếu bạn cảm thấy thoải mái với dòng lệnh và bạn muốn OSINT hoạt động hiệu quả hơn nhiều, Recon-ng có thể trở thành một trong những công cụ yêu thích của bạn. Ahmia.fi Ahmia.fi là một công cụ tìm kiếm đặc biệt để tìm các trang web trên Mạng Tor, mặc dù bản thân công cụ tìm kiếm này cũng có thể truy cập được trên “clearnet”. Nhưng bạn sẽ cần Tor Browser để mở kết quả tìm kiếm Tor của bạn. Rất nhiều chỗ mua bán và diễn đàn nằm trên Mạng Tor, vì vậy việc sử dụng hiệu quả công cụ tìm kiếm Ahmia.fi có thể là một phương pháp tuyệt vời cho công việc pháp y OSINT của bạn. Wayback Machine Các trang web cũ đã chết giờ nằm ở đâu? Wayback Machine là một công cụ tìm kiếm của hơn 632 tỷ trang web và đang tăng lên, nhiều trang web bắt nguồn từ những năm 1990. Archive.org đang sử dụng Wayback Machine để lưu trữ nhiều web nhất có thể. Bạn cũng có thể sử dụng trang web của họ để tự lưu trữ các trang web hiện đang trực tuyến theo cách thủ công. Nếu và khi các trang web và máy chủ web bị xóa hoặc chuyển sang chế độ ngoại tuyến, một bản sao đã lưu trữ có thể được tìm thấy thông qua Wayback Machine. Cá nhân mình đã tìm thấy các trang web được lưu trữ từ năm 1994 đến năm 2021 thông qua công cụ này. Và điều thực sự thú vị là bạn thường có thể sử dụng các liên kết trong các trang web đã lưu trữ để chuyển đến kho lưu trữ của các trang web khác đó. theHarvester theHarvester là một công cụ do thám mã nguồn mở hữu ích khác mà bạn có thể cài đặt từ GitHub. Nó có thể được sử dụng để lấy địa chỉ email, máy chủ, tên miền phụ, tên nhân viên và mở các cổng internet từ nhiều nguồn công cộng khác nhau như công cụ tìm kiếm, máy chủ khóa PGP và Shodan. Khi Harvester được cài đặt, bạn có thể dễ dàng chạy ứng dụng từ dòng lệnh của mình. Có một bộ tùy chọn đặc biệt phong phú để khám phá dữ liệu trong máy chủ DNS. Máy chủ DNS có tất cả các loại thông tin rất hữu ích vì chúng liên kết tên miền với các địa chỉ IP cụ thể. Một số nguồn dữ liệu yêu thích của mình mà bạn có thể khám phá vớiHarvester bao gồm LinkedIn, Bing, Google và VirusTotal. TinEye TinEye là một công cụ mạnh mẽ để nghiên cứu hình ảnh trực tuyến. Nếu bạn có một hình ảnh trên thiết bị cục bộ của mình, bạn có thể tải nó lên TinEye và xem hình ảnh đó có được sử dụng trên các web khác hay không và như thế nào. Một trường hợp sử dụng rõ ràng nhất là nếu bạn có ảnh của người nào đó mà bạn không biết danh tính và bạn muốn tìm hiểu họ là ai. Nhưng có nhiều trường hợp sử dụng khác, chẳng hạn như "bức ảnh này được chụp ở đâu?" hoặc "đây là ảnh chụp màn hình của ứng dụng nào?" Ngược lại, nếu bạn có URL của hình ảnh trên web, bạn cũng có thể tiến hành nghiên cứu theo cách đó. TinEye cũng hữu ích để duy trì sự riêng tư của bạn. Ví dụ: có lẽ bạn nên bảo vệ quyền riêng tư của con mình. TinEye có thể thông báo cho bạn biết nếu và khi nào ảnh của con bạn được chia sẻ trực tuyến. OSINT Framework OSINT Framework là ứng dụng web hoàn hảo nếu bạn không chắc mình sẽ cần sử dụng nguồn dữ liệu OSINT nào để tìm thông tin bạn muốn. Vì vậy, OSINT Framework giới thiệu cho bạn một cây khổng lồ các nguồn dữ liệu tiềm năng mà bạn có thể khám phá. Bạn có muốn phân tích tệp độc hại, tên người dùng, vị trí địa lý, địa chỉ IP, tên miền, IRC, Dark Web, siêu dữ liệu, thông tin về mối đe dọa, số điện thoại hoặc có thể là thứ gì khác không? Tiếp tục nhấp qua cây biểu đồ cho đến khi bạn tìm thấy nguồn mà bạn cần. OSINT Framework có thể là bước đầu tiên của bạn trong tất cả quá trình OSINT.
0 notes
Text
Essential Ethical Hacking Tools and Software for Beginners

In the dynamic landscape of cybersecurity, ethical hacking plays a crucial role in identifying vulnerabilities, securing systems, and protecting digital assets. Whether you're a cybersecurity enthusiast or aspiring ethical hacker, having the right tools and software is essential to effectively simulate attacks and assess security posture. In this blog post, we'll explore some fundamental ethical hacking tools and software that every beginner should know.
Understanding Ethical Hacking Tools and Software
Ethical hacking tools and software are designed to assist security professionals in testing and evaluating the security of systems and networks. These tools simulate real-world attacks to identify weaknesses and help organizations strengthen their defenses. For beginners entering the field of ethical hacking, mastering these tools is a critical step toward building foundational skills. Here are some essential ethical hacking tools and software every beginner should be familiar with:
Nmap: Nmap (Network Mapper) is a powerful network scanning tool used for discovering hosts and services on a computer network. It's essential for port scanning, detecting open ports, and identifying potential entry points for attackers.
Wireshark: Wireshark is a network protocol analyzer that captures and displays network packets. It helps ethical hackers analyze traffic, identify vulnerabilities, and troubleshoot network issues.
Metasploit: Metasploit is a penetration testing framework that allows ethical hackers to exploit known vulnerabilities in systems. It provides a range of tools for developing and executing exploits, making it an indispensable tool for security assessments.
Burp Suite: Burp Suite is a web application security testing tool used for scanning and testing web applications. It helps identify security flaws such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
John the Ripper: John the Ripper is a password-cracking tool used to perform brute-force attacks and dictionary attacks on password hashes. It's commonly used to assess password strength and test authentication mechanisms.
Aircrack-ng: Aircrack-ng is a suite of tools for assessing Wi-Fi network security. It includes tools for capturing packets, performing dictionary attacks on Wi-Fi passwords, and testing WEP/WPA encryption vulnerabilities.
Hydra: Hydra is a popular password-cracking tool that supports various protocols, including SSH, FTP, Telnet, and HTTP. It's used for performing brute-force attacks on login credentials.
Nikto: Nikto is a web server scanner that identifies potential security vulnerabilities in web servers. It checks for outdated software versions, misconfigurations, and common vulnerabilities.
Snort: Snort is an open-source intrusion detection system (IDS) that detects and logs suspicious network traffic. It's used for real-time monitoring and alerting of potential security threats.
Maltego: Maltego is a data visualization tool used for gathering and analyzing information about targets. It helps ethical hackers perform reconnaissance and map relationships between entities.
Best Hacker in the World:
While ethical hacking emphasizes responsible and legal practices, renowned best hacker in the world such as Kevin Mitnick, Kevin Poulsen, and Adrian Lamo have gained fame for their expertise in cybersecurity and ethical hacking.
It's important to note that ethical hacking is not about achieving notoriety but rather about using skills for constructive purposes, such as securing systems, protecting data, and promoting cybersecurity awareness.
Conclusion
In conclusion, mastering ethical hacking tools and software is essential for beginners looking to pursue a career in cybersecurity. By familiarizing themselves with tools like Nmap, Wireshark, Metasploit, and Burp Suite, aspiring ethical hackers can gain practical experience in penetration testing, vulnerability assessment, and network security. Ethical hacking is ultimately about using skills and knowledge responsibly to defend against cyber threats and safeguard digital assets. Start exploring these tools and software today to embark on an exciting journey into the world of ethical hacking!
1 note
·
View note
Text
Accretion & Discretion
The content in my Evernote has been accumulating for the last 38 months, like a planetesimal expanding with each new asteroid it encounters. Those that grow large enough to become actual planets are in hydrodynamic equilibrium – rounded due to their gravity being sufficient to compact any type of mineral in their makeup. They all differentiate to some degree, with dense minerals sinking, and gasses escaping. This collection is now at the point of differentiation, only with a network sorting rather than vertical stratification.
This process has been … educational for me. Like my computer science education, my first career of handling enterprise LAN administration, and my move to service provider networking. My non-telecom pursuits have been similar – renewable energy, Democratic politics, and my meandering progress in all things sense making. Reading piles up around my interest of the moment, but those are all profit oriented.
As an autist of the more functional sort, I still do some very autismal things, I just don’t talk about them as much. The most visible among them was my two year pursuit of western history. Between that and the studies related to my conversion to Buddhism I spent quite a bit of time on the intersection of hypnosis and formal linguistic analysis. I wrote a great deal on food and water security with a focus that happened to be roughly the boundaries of the Ottoman empire at its peak, which was uncharacteristically noisy of me.
Over the years I’ve been described as: aloof, secretive, unknowable, and otherwise inaccessible. This is typically not a conscious act, it’s just my personal perch on the autism spectrum. But this time is different. What would normally be a private pursuit, perhaps occasionally surfacing in conversation, is now an intentional matryoshka, a riddle within a mystery, wrapped in my purportedly enigmatic ways.
I took a break in the middle of writing this to fiddle with the graph. I’ve discovered, and perhaps solved, a significant problem. If you’re counting noses there are eleven additional green dots, but that’s not eleven additional names. There are six new names and the outermost arc of those dots are just a bit darker than all the rest – they’re well known aliases.
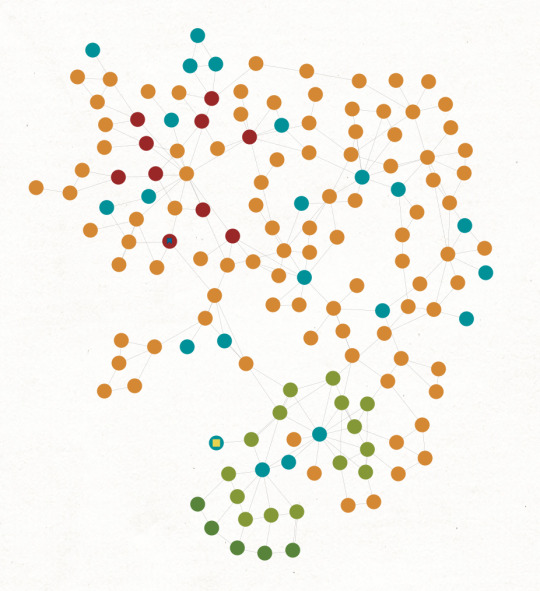
Right now they are quite close on the graph. That’s not an accurate representation of reality, there’s a sharp divide between those first nine names and the six who just joined the mix.
And since this is Maltego, there isn’t really a good way to represent the temporal component. One group came first, and then the second arose, with just one “cross patched” between both groups. There’s a sense of betrayal in that crossing, but I’m not sure how, or even if I should say anything about it.
0 notes
Text
CompTIA CySA+ CS0-003: Maltego
Maltego is a data mining and information gathering tool that can provides automatic merging of data to provide visual maps. It is a open source intelligence tool with graphical link analyses tool. Maltego is a great tool to identify relationships and it is extremely useful when you deal with big data. It helps visualize relationships with data and see connections that you would have otherwise…

View On WordPress
0 notes
Text
youtube
Summary
🌐 Introduction to OSINT (Open Source Intelligence):
Tom Moore discusses the practical application of OSINT in offensive and defensive cybersecurity.
OSINT involves gathering publicly available data to inform strategic decisions without direct interaction with the target.
🔍 Key Concepts in OSINT:
Understanding OSINT and OPSEC:
OSINT provides critical data for reconnaissance without alerting the target, while OPSEC protects sensitive information from being exposed.
Examples include protecting against "swatting" and reducing vulnerability to social engineering attacks.
Ethical Concerns:
Moore emphasizes using OSINT responsibly to avoid harmful outcomes like doxing or personal attacks.
🛠️ Key Tools Discussed:
Recon-ng: A powerful reconnaissance framework that integrates API queries for comprehensive data gathering.
The Harvester: Automates the collection of subdomains, emails, and host information from public databases.
Google Dorks: Uses advanced search operators to extract sensitive data from misconfigured web servers.
Shodan: Scans internet-connected devices, providing insights into vulnerable systems and services.
Maltego: Visualizes relationships between entities using transforms to uncover links in data sets.
CTFR: Exploits SSL transparency reporting to identify subdomains without direct interaction.
OSINT Framework: Centralizes various OSINT tools and resources for streamlined investigations.
🎯 Practical Use Cases:
Offensive security professionals use OSINT to identify entry points for exploitation.
Defensive teams leverage OSINT to identify and mitigate vulnerabilities in their own organizations before attackers exploit them.
🚀 Future Insights:
Automation and integration are key to improving OSINT efficiency.
Collaboration among practitioners will enhance tool development and data accuracy.
0 notes
Text
0 notes
Text
[Media] GraphSense Maltego Transform
GraphSense Maltego Transform Query GraphSense clusters, details and attribution tag-packs directly in Maltego. By an initial idea of our Swiss Federal Police colleagues. https://github.com/INTERPOL-Innovation-Centre/GraphSense-Maltego-transform #OSINT #recon #infosec

0 notes