#making third party controllers by encrypting their controllers in such a way that they can charge 80 for something standard that's required
Explore tagged Tumblr posts
Note
wow that anon is dumb. anyone who is that concerned about starving artists "taking away" from other people in need of donations - is directing their energy the wrong way.
love the comic, hope you can afford that controller <3
Thank you! Me too! I really really really hope I can!
#Anonymous#asks#remember when hardware was durable and could actually last decades later and now companies like sony block third party manufacturers from#making third party controllers by encrypting their controllers in such a way that they can charge 80 for something standard that's required#to even use their system#I LOVE LATE STAGE CAPITALISM /sarcasm
26 notes
·
View notes
Text
EU’s proposed Chat Control law has become a bone of contention between members of the bloc. First proposed by the European Commissioner for Home Affairs Ylva Johansson in May 2022 as part of bloc’s push to combat child sexual abuse online, the framework of the bill has now come under fire, earning itself a derisive term “Chat Control”.
France, Germany and Poland have particularly refused to accept a clause that allows for mass scanning of private messages by breaking end-to-end encryption. Some tech companies, along with trade associations, and privacy experts have all vehemently opposed the regulation.
On the other hand, Interior Ministers of Spain and Ireland have supported the proposal. Separately, a network of organisations and individuals, advocating for children’s rights in Europe, have lashed out at EU leaders for failing to tackle child sexual abuse online.
What are the concerns of those against the proposal?
Scanning end-to-end encrypted messages has remained a controversial issue. That’s because there is no way to do this without opening risky backdoors that can be accessed by third parties who can exploit the vulnerability, in turn ending the promise of end-to-end encryption.
Tech firms that treaded the encryption bypassing path have have often been made to retreat. In 2021, Apple announced NeuralHash, a feature that could automatically scan iCloud photo libraries of individual devices for child sexual abuse material, or CSAM. Employees and activist groups expressed concerns over the loss of privacy. A year later, Apple said it had abandoned the initiative.
Another looming issue the iPhone maker recognised in the process was how authoritarian governments could potentially misuse the feature by using it as a tool to target individuals who oppose the regime.
Erik Neuenschwander, Director of user privacy and child safety at Apple, admitted this in a note saying, “It would […] inject the potential for a slippery slope of unintended consequences. Scanning for one type of content, for instance, opens the door for bulk surveillance and could create a desire to search other encrypted messaging systems across content types.”
When brining in a similar clause through the UK’s Online Safety Bill, lawmakers attempted to make way for client-side scanning of private and encrypted messages. The proposal was postponed after receiving pushback from encrypted messaging app owners like WhatsApp and Signal. The duo threatened to leave the UK if such a law was passed. In its final stages, in September, 2023, the House of Lords considered the potential security threat that the clause would bring saying it would not implement scanning until it was “technically feasible.”
What is the status of EU’s Chat Control law?
On June 30, a new draft of the proposal is set to be be reviewed. Legislators have now left the idea of scanning text messages and audio, and are instead targetting shared photos, videos and URLs with an adjustment to appease the naysayers.
Another tweak in the making could be people’s consent in sharing material being scanned before being encrypted. But this compromise has been largely called out as a farcical one. A report by Euractiv which has been confirmed by internal documents show that if a user refuses the scanning, they will simply be blocked from sending or receiving images, videos and links hardly leaving them with a choice.
Despite these measures, EU’s enforcement of such regulations have seen exemptions to the rule. In November 2023, the European Commission reportedly published a proposal to amend the regulation on a temporary derogation of the E-Privacy Directive against CSAM. Under the regulation, specific online communications service providers were allowed to sift through or scan messages to detect, report and remove online child sexual abuse material or CSAM and content that solicits children. The regulation is set to expire in early August . The initial plan on the table was to simply extend this regulation for another three years. But, according to media reports, plans for further extensions were stalled in February this year.
Meredith Whittaker, President of Signal app called the measures to assuage concerns as “cosmetic”, and has signed a joint statement along with a group of over 60 other organisations like Mozilla, Proton, Surfshark and Tuta, voicing out her concerns. Whittaker has echoed her earlier warning saying Signal will leave the UK rather than undermine end-to-end encryption.
A blog, co-authored by Riana Pfefferkorn, a research scholar at the Stanford Internet Observatory and Callum Voge, director of government affairs and advocacy at the Internet Society, notes, ”If government surveillance is a concern in an established democratic entity like the EU, what hope is there for beleaguered democracies like Turkey, India and Brazil, much less autocracies?”
7 notes
·
View notes
Text
Hybrid Cloud Strategies with Azure Arc: My Practical Insight
Are you ready to unlock the true potential of hybrid cloud strategies? Look no further than Azure Arc, the game-changing solution that promises seamless integration and unparalleled flexibility. From streamlining operations to enhancing security, Azure Arc has revolutionized the way organizations harness the power of both on-premises and cloud environments. In this blog post, I’ll be diving into my practical insights on leveraging Azure Arc for your hybrid cloud journey. So buckle up as we explore the endless possibilities and unveil a new era in hybrid computing!

Introduction to Hybrid Cloud Strategies with Azure Arc
I’m under pressure to digitally transform in order to remain competitive. I’m looking to the cloud as a way to accelerate this transformation. Not all workloads, meanwhile, are appropriate for the public cloud. Some may require on-premises or edge computing due to data sovereignty or local regulations. Others may need to be kept on-premises due to performance requirements.
Hybrid cloud strategies allow me to keep some workloads on-premises or at the edge while still taking advantage of the agility and scalability of the public cloud. Azure Arc is a tool that can help me manage and monitor my hybrid cloud deployments. In this blog post, I will share my practical insight into using Azure Arc for my hybrid cloud deployments.
Benefits of Azure Arc Adoption & Challenges in Implementing it
In recent years, using the cloud has grown in popularity among organizations of all sorts. One of the major advantages of cloud computing is its scalability; I can quickly add or remove capacity as needed without making a long-term commitment. Azure Arc is a hybrid cloud solution that allows me to take advantage of the benefits of the cloud while still maintaining control over my data and applications.
There are several benefits to adopting Azure Arc, including:
Increased flexibility and scalability: As mentioned above, one of the major advantages of Azure Arc is its scalability. I can easily add or remove capacity as needed, without making a long-term commitment. This can help me save money on IT infrastructure costs, as well as ensure that I have the necessary resources available when I need them.
Improved disaster recovery: Another benefit of Azure Arc is improved disaster recovery capabilities. With this solution in place, I can quickly recover from outages or disasters with minimal downtime. This can help keep my business up and running even in the event of a major problem.
Enhanced security: Security is always a major concern for me, especially when it comes to sensitive data. With Azure Arc in place, I can take advantage of enhanced security features such as encrypted data storage and multi-factor authentication. This can help give me peace of mind knowing that my data is safe and secure.
Lower maintenance costs: Maintaining on-premises IT infrastructure can be costly and time-consuming. Azure Arc helps me lower maintenance costs by simplifying resource management and automating tasks.
Understanding the Necessary Requirements for Azure Arc Usage
Azure Arc is a cloud management platform that enables me to optimize my hybrid cloud deployments. It provides a unified control plane for managing resources across on-premises, edge, and multi-cloud environments. Azure Arc also simplifies the process of integrating Azure services with on-premises and third-party solutions.
In order to use Azure Arc, I must first have an Azure subscription. I must also have the desired Azure Resource Manager (ARM) template or Resource Manager package deployed in my environment. Azure Arc uses these templates or packages to deploy and manage resources in the target environment.
Once the necessary requirements are met, I can begin using Azure Arc to manage my hybrid cloud deployments. I can use the platform to provision and manage resources, monitor activity and usage patterns, set policies and governance controls, etc. Additionally, I can use Azure Arc to connect my on-premises or third-party solutions with Azure services. This allows me to take advantage of the many benefits that Azure has to offer, such as scalability, high availability, security, and so on.
Steps for Setting Up Azure Arc Configurations
Azure Arc is a cloud service that enables me to manage and monitor my resources whether they’re running on Azure, on-premises, or in other clouds. With Azure Arc, I can use the same tools and portal experiences I’m used to in Azure to centrally govern all my infrastructure.
Setting up an Azure Arc configuration is simple and straightforward. I just need to follow these simple instructions:
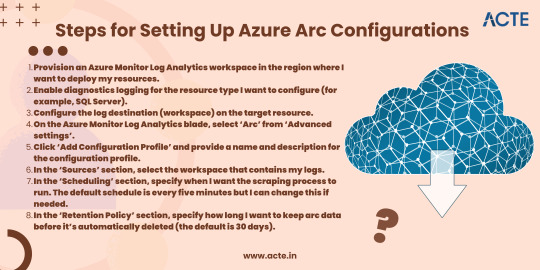
9a. If I want to scrape data from multiple workspaces, I can repeat steps 5–8 for each workspace.
Troubleshooting Common Issues Related to Hybrid Cloud with Azure Arc If I’m working with hybrid cloud and Azure Arc, there are a few common issues I may run into. Here’s how to troubleshoot them:
I can’t see all of my resources in the Azure portal.
Make sure that I’ve selected the correct subscription in the Azure portal. If I’m still not seeing all of my resources, check the resource provider status page to see if there are any known issues.
I’m getting errors when trying to deploy resource group templates.
When deploying resource group templates, make sure that the template includes all required resources for Azure Arc enabled resource providers. Consult the Azure Resource Manager documentation for further details.
My hybrid cloud app isn’t running correctly.
If I’m having trouble with a hybrid cloud app, first check the logs to see if there are any error messages. Then, try redeploying the app using a different approach (for example, using Azure CLI or PowerShell instead of the Azure portal).
Unifying Multiple Clouds with One Platform:
A Comprehensive Overview Azure Arc is a cloud management platform that enables me to unify multiple clouds with one platform. Azure Arc provides a comprehensive overview of my resources and allows for central management and policy enforcement across all of my Azure subscriptions. Azure Arc also provides integrated security and compliance features to help me secure my data and meet regulatory requirements.
Best Practices for Utilizing Hybrid Cloud Strategies with Azure Arc
When it comes to hybrid cloud strategies with Azure Arc, there are a few best practices that I should keep in mind. For starters, I should make sure that I have a clear understanding of my workloads and how they need to be supported. I should also have a clear picture of my network topology and how the different components will interact with each other. Additionally, it’s important to have a plan for data security and management, as well as monitoring and logging. By keeping these things in mind, I can be sure that my hybrid cloud strategy with Azure Arc is as effective as possible.
All things considered, Azure Arc is an impressive offering from Microsoft that can help me realize the potential of hybrid cloud technology. By leveraging my existing infrastructure while taking advantage of the benefits offered by public clouds like Azure, I can enjoy features such as greater scalability and improved flexibility to meet changing needs. Whether I need basic access control or more advanced policies to manage my distributed systems, my practical insight on using Azure Arc for my hybrid cloud strategy shows how powerful this platform is in streamlining and optimizing cloud operations for various enterprises.
2 notes
·
View notes
Text
Why Choose Drupal Over the Other CMSs
Drupal is a free and open-source web content management system (CMS) written in PHP and distributed under the General Public License. Drupal provides an open-source back-end framework for at least 14% of the top 10,000 websites worldwide and 1.2% of the top 10 million websites—from personal blogs to corporate, political, and government sites. Systems also use Drupal for knowledge management and business collaboration.
As of March 2022, the Drupal community had more than 1.39 million members, including 124,000 users actively contributing, resulting in more than 48,300 free modules that extend and customize Drupal functionality, over 3,000 free themes that change the look and feel of Drupal, and at least 1,400 free distributions that allow users to quickly and easily set up a complex, use-specific Drupal in fewer steps.
So, what factors make Drupal so unique in the market of CMSs and become the preferred choice of most users?
1. Multilingual Platform
The ultimate goal of every website is to grow globally. Multilingual platforms are a stepping stone; you can do this effortlessly with Drupal. When your website interacts with visitors in their native language, it creates a pull for them and keeps them stuck for longer. Also, Drupal will dramatically increase their chances of interacting with the website.
With its unwavering support for multilingual websites, Drupal is the ultimate CMS for building websites that support multiple languages. It allows you to choose from more than 100 languages according to your target geographic area. No matter where your target audience lives, you can effortlessly connect with them through a website built with Drupal.
2. Security Function
In this internet-driven world, people share much personal information online, including bank details, credit card details, and other credentials. What followed was a sharp increase in cybercrime cases. There’s no doubt that today’s consumers follow the best online security practices to protect themselves from online fraud and data breaches, but they also expect top-notch security from the sites they trust.
Therefore, website owners must focus on intelligent web security practices. After all, a cyber attack can get their business into trouble. Once they lose the trust of their customers, no matter what they try, there is no way to get it back.
Drupal is one of the most secure CMSs in the history of the world. It offers unparalleled security features to defend against cyber-attacks and protect customer data. Regular security updates, two-factor authentication, user access control, and database encryption are some of the security features offered by Drupal.
3. Great for SEO
A website’s overall search engine ranking depends on the effectiveness of the SEO practices. If a website owner takes SEO seriously, the website can land on the first page of search engines. As a result, the website will experience exponential visitor numbers and sales growth. Realizing the importance of SEO, most CMSs have started to provide users with multiple SEO tools with the promise of improving website rankings.
If you’re looking for a powerful and versatile content management system that will help your website rank higher in search engine results pages, Drupal is an excellent option. Thanks to its well-optimized codebase and many SEO features, Drupal is one of the best CMSs for SEO. Keyword research, keyword management, content auto-linking, and link management are some of its notable SEO features.
Drupal is a popular content management (CMS) system platform worldwide. If you need an open-source and user-friendly CMS to meet your business needs, Drupal is your first choice. From the perspective of security, Drupal has a dedicated security team to review and respond to the kernel, third-party modules, and themes; Drupal’s modules and themes will be covered by Drupal’s internal security program to ensure that malicious codes are removed. In addition, for ongoing maintenance, and long-term development projects, Drupal development is a lower-cost option. Once the main functions are completed, subsequent expansion and customization will not cost more.
If you want to integrate third-party services into your Drupal site, Shinetech will be your excellent partner. Shinetech developers have rich experience in Drupal development and can help you with the operation and maintenance of your existing Drupal site. The custom development team can also expand network functions by installing existing plug-ins or custom-developing your Drupal plug-ins.
2 notes
·
View notes
Text
Exploring the World of Milady NFT: A Fusion of Art and Technology
Exploring the World of Milady NFT: A Fusion of Art and Technology The Milady NFT project is a fascinating blend of art and technology, creating unique digital collectibles that captivate collectors and enthusiasts alike. Each Milady NFT represents a distinct character with intricate designs and vibrant personalities, making them stand out in the crowded NFT market.To get more news about milady nft, you can visit our official website.
One of the key features of Milady NFTs is their rarity and exclusivity. With limited editions and special attributes, these digital assets are highly sought after by collectors who appreciate the blend of creativity and innovation. The project also emphasizes community engagement, offering various events and collaborations that keep the Milady universe dynamic and exciting.
As the NFT space continues to evolve, Milady NFTs are poised to make a significant impact, showcasing the potential of blockchain technology to revolutionize the art world. Whether you're a seasoned collector or a newcomer to the NFT scene, Milady NFTs offer a unique and rewarding experience that bridges the gap between traditional art and digital innovation.
ZenWallet: Simplifying Digital Payments ZenWallet is a versatile digital wallet designed to manage prepaid cards, specifically the Canada Post Cash Passport Prepaid Mastercard
What is ZenWallet? ZenWallet is a mobile application that allows users to manage their Canada Post Cash Passport Prepaid Mastercard . It provides a convenient way to check balances, view recent transactions, and reload cards using Interac e-Transfer . Key Features of ZenWallet Balance Management: Users can easily check their card balance at any time . Transaction History: View recent transactions to keep track of spending and payments . Barcode Display: Display a barcode that can be scanned at any Canada Post location to reload the card . Interac e-Transfer: Load your card using Interac e-Transfer for quick and secure funding . Data Security: Ensures that user data is encrypted in transit and not shared with third parties . Benefits of Using ZenWallet Convenience: Manage your prepaid card anytime, anywhere using your mobile device . Security: Data encryption and privacy measures ensure that your information is safe . Ease of Use: User-friendly interface makes it simple to check balances, view transactions, and reload cards . How to Use ZenWallet Download the App: Available on both iOS and Android devices . Create an Account: Sign up and link your Canada Post Cash Passport Prepaid Mastercard . Manage Your Card: Check balance, view transactions, and reload your card using Interac e-Transfer . Barcode Reload: Use the barcode feature to reload your card at any Canada Post location . Conclusion ZenWallet offers a seamless and secure way to manage your prepaid cards, making digital payments more convenient and efficient. Whether you're a frequent traveler or just looking for a better way to manage your finances, ZenWallet provides the tools you need to stay in control of your digital payments.
0 notes
Text
How to Stay Safe While Betting on Daman Club

Online betting has gained tremendous popularity, offering users the thrill of placing bets and the opportunity to earn money. However, with the potential rewards come the risks, making it essential to stay safe while participating in online betting activities. Daman Club, a well-established platform, offers a secure and reliable environment for users, but safety still requires attention and awareness. This post will guide you on how to stay safe while betting on Daman Club, ensuring that your experience is enjoyable and secure.
One of the first steps to ensuring your safety on Daman Club is to complete the Daman Club login process using a secure, private internet connection. Public Wi-Fi networks, such as those found in cafes or airports, can expose your personal information to cybercriminals. Using a private, encrypted internet connection helps prevent unauthorized access to your account and financial data. Make sure you’re always logging in from a trusted device and a secure connection, minimizing the risk of being compromised.
Your password is your first line of defense when logging into Daman Club. It is essential to choose a strong and unique password that cannot be easily guessed. Combining upper and lowercase letters, numbers, and special characters will enhance the security of your password. Avoid using easily identifiable information, such as your name or birthdate. A strong password reduces the chances of unauthorized access to your account, keeping your funds and personal details safe.
While logging into Daman Club, make sure you enable two-factor authentication (2FA) if the platform offers it. Two-factor authentication adds an extra layer of security by requiring you to verify your identity with a second method, such as a one-time passcode sent to your mobile device. This added security step ensures that even if someone manages to obtain your login credentials, they will still need the second factor to access your account. This is a simple but highly effective way to keep your Daman Club account secure.
When betting on Daman Club, it’s essential to monitor your account regularly for any suspicious activity. Review your transactions, deposits, and withdrawals to ensure there are no unauthorized actions taking place. If you notice any unusual activity, it is crucial to act quickly by reporting it to Daman Club’s customer support team. Timely action can prevent further issues and help resolve any potential security concerns.
Another important aspect of staying safe while betting on Daman Club is practicing responsible betting. Establish a budget for your betting activities and stick to it. Betting should be a form of entertainment, not a way to make quick money or escape from financial stress. By keeping a clear head and managing your funds responsibly, you can avoid falling into the trap of excessive gambling. Daman Club promotes responsible betting by offering features like deposit limits and self-exclusion options, which allow users to control their betting habits and ensure they are betting within their means.
Daman Club also takes user safety seriously by implementing stringent data protection measures. The platform employs advanced encryption protocols to safeguard your personal and financial information, making it highly secure when you make deposits or withdrawals. By ensuring that your sensitive data is protected, Daman Club minimizes the risks of identity theft and fraud, allowing you to focus on enjoying your betting experience.
In addition to these safety measures, always be cautious of third-party websites or apps claiming to offer Daman Club-related services. These fraudulent platforms may attempt to steal your information or money. Always ensure that you are using the official Daman Club website or app when logging in or placing bets. Be wary of unsolicited messages or advertisements claiming to offer promotions or bonuses related to Daman Club, as these could be scams.
In conclusion, staying safe while betting on Daman Club requires a combination of good practices and being vigilant about security. By using a secure connection, choosing strong passwords, enabling two-factor authentication, and practicing responsible betting, you can protect yourself while enjoying the platform. Daman Club’s security measures, combined with your own caution, will ensure that your betting experience remains safe and enjoyable. Stay informed, stay safe, and continue to make the most of your time on Daman Club.
0 notes
Text
New Post has been published on RANA Rajasthan Alliance of North America
New Post has been published on https://ranabayarea.org/what-is-a-crypto-wallet-a-beginners-guide/
What Is a Crypto Wallet? A Beginners Guide

Content
Cryptocurrency inheritance and crypto wallets
Guide: Everything You Should Know to Invest in Crypto Safely
Types of Cryptocurrency Wallets
Can you receive crypto from multiple senders at once?
Additionally, there are fake hardware wallets in circulation that will steal your private keys, so always be careful where you purchase hardware wallets from. Crypto wallets are at the very foundation of blockchain technology, allowing you to conveniently manage and secure your digital assets without the need for a centralized third party. From buying, selling, and holding crypto, to exploring decentralized apps (dApps), crypto wallets are the primary way that individuals interact with the blockchain. A custodial wallet is one whose private keys are held and controlled not by the user but by the wallet provider, usually a https://www.xcritical.com/ centralized crypto exchange. Using a custodial wallet means forfeiting ownership of your funds to a centralized custodian.
Cryptocurrency inheritance and crypto wallets
Both Bitmart and Crypto.com have promised to reimburse users who lost their funds. As decentralized currencies, crypto is not and will likely never become banned in the U.S. Currently, the sale and purchase of cryptocurrency is legal how do crypto wallets make money in all 50 states. That being said, the government can – and does – regulate how virtual currencies are taxed and traded. By the time you’re finished with this guide, you’ll be a crypto-safety pro.
Guide: Everything You Should Know to Invest in Crypto Safely
Using a VPN (Virtual Private Network) while accessing your crypto wallet Blockchain provides encryption for your online activities. It masks your location and protects you from potential prying eyes on public networks. On the flip side, this means that users must be in charge of their own security with regard to the storage of passwords and seed phrases.
Types of Cryptocurrency Wallets

This type of crypto wallet is the most user-friendly but also the least secure. If you plan on swapping crypto and/or interacting with decentralized finance applications frequently, a software wallet may be your best option. Within these types of wallets, desktop and mobile wallet applications offer the best security. Hardware wallets are like paper wallets in that they allow their owners to safely store their private keys offline. With a traditional bank, users receive bank accounts with account numbers.
Either it will generate you an account to start, or you will be able to generate a new account yourself. When you send cryptocurrency, your wallet uses the private key to sign the transaction, proving that you own the funds you want to send. This signature is then verified on the blockchain, and the transaction is processed.

It is essential to ensure that the public address is accurate, as transactions on most blockchains are irreversible. Bitcoin wallets and other crypto wallets are based on public-key cryptography. The essential elements of a wallet are a public key, a private key, and an address. When you want to send some of your digital assets (coins, tokens, NFTs, etc.), you digitally sign the data using ECDSA with your private key and encrypt it before it’s sent to the receiver.
Get your wallet’s public address (often displayed as a QR code) and give it to the sender, such as your personal crypto exchange account, to receive funds. When you first launch the wallet software, you’ll usually have the option to create a new wallet or import an existing one. If setting up a new wallet, follow the on-screen instructions to generate a new wallet address and private key. If you already have a wallet, select the import option and provide the necessary details, like the recovery phrase or private key. If you don’t own your private keys, you’re entrusting a third party with your assets. To address this problem, many web wallets now allow you to manage your keys completely or through shared control as multi-signature wallets.
In fact, most cryptocurrency owners use multiple wallets to ensure maximum security for storing their various cryptocurrencies. Now, to enhance security, you can opt for a cold wallet, which is like a digital vault. It’s offline, not connected to the internet, making it resilient to hackers. To safeguard your assets, you transfer them from your hot wallet to your cold wallet. In addition to hot and cold wallets, it’s essential to understand the difference between custodial and non-custodial wallets.
While non-custodial wallets (a.k.a. self-custody wallets) grant users full control over their private keys, centralized exchanges hold custody of users’ funds. This disparity in control has significant implications for security and access, as users rely on exchanges to safeguard their assets. Both crypto exchanges and crypto wallets play crucial roles in the world of cryptocurrencies. Exchanges enable users to buy, sell, and trade digital assets, while wallets provide a secure storage solution for managing these assets. As the name implies, desktop wallets are software applications that users download and run locally on their computers. Unlike some web-based versions, desktop wallets provide complete control over keys and funds.
It is called a wallet because it is used similarly to a wallet you put cash and cards in. Instead of holding these physical items, it stores the passkeys you use to sign for your cryptocurrency transactions and provides the interface that lets you access your crypto. It is very similar to the process of sending or receiving money through PayPal or any other gateway used today, but you use cryptocurrency instead. Examples of blockchain wallets include Electrum, Blockchain.info, Jaxx, Mycelium, Samurai, and Bitcoin paper wallet. There are many more based on the needs you have and the security you require. Generally, investors perceive hardware wallets as the proven instrument for safeguarding their digital assets.
In 2010, Bitcoin’s first real-world transaction took place when 10,000 BTC were exchanged for two pizzas, giving it its first true valuation. Trust Wallet lets you manage and interact with 10M+ crypto assets across 100+ blockchains. With Trust Wallet, you can confidently store, manage, and interact with your cryptocurrencies while enjoying built-in tools like token swaps and staking. The added layer of protection from the Trust Wallet Security Scanner ensures that you can make informed decisions about your transactions.
Popular hardware wallets that can store the keys to many different digital assets include Ledger and Trezor devices. Just like with hot wallets, if you only need to manage bitcoin, it is recommended to use a bitcoin-only device like a Passport or a Bitkey. This isolation from online networks enhances the security of the private keys and protects them from potential online threats, such as hacking or malware attacks.
If you use a less common operating system on your phone or laptop, this is an important feature to check before making your choice.
A bad actor may send you an email and bait you into downloading a file and running it on your device.
Centralized exchanges, such as Binance or Coinbase, operate as intermediaries, matching buyers and sellers while holding custody of users’ funds.
Cryptocurrency goes through probate like other assets before going to beneficiaries.
We want our readers to share their views and exchange ideas and facts in a safe space.
If you purchased a hardware wallet, you will need to follow the manufacturer’s instructions to set it up.
Many crypto wallets, typically software wallets, are designed for a single network. While they use an HD structure, allowing you to generate multiple accounts (each with its own blockchain address), they will all be separate accounts on the same network. Once the transaction is signed, it’s safe to transfer to an internet-connected device, which your hardware wallet will usually do via a USB cable.
As users gain experience using cryptocurrencies and seek greater control over their assets, transitioning to self-custody wallets becomes increasingly appealing. When you are starting off on your Web3 journey, one of the first steps you’ll take will be installing a crypto wallet. Wallets are an essential piece of software, enabling you to store and interact with your cryptocurrencies. In this technical tutorial, we will explore different types of crypto wallets and learn how to build our own.
With hot wallets, private keys are stored in the cloud for faster transfer. With cold wallets, private keys are stored in separate hardware that is not connected to the internet or the cloud, or they are stored on a paper document. Hot wallets are easy to access online 24/7 and can be accessed via a desktop or mobile device, but there is the risk of unrecoverable theft if hacked. With cold wallets, the method of the transaction helps in protecting the wallet from unauthorized access (hacking and other online vulnerabilities). Hardware wallets, also referred to as cold wallets, can offer completely offline storage for your keys. You can find hardware wallets similar to a USB device in terms of design.
0 notes
Text
What Is the Best VPN for Home Security?
What Is the Best VPN for Home Security?
In a world where smart devices are taking over our homes, online security has become more critical than ever. From streaming on your smart TV to controlling your thermostat remotely, everything is connected to the internet—and that includes potential threats. Enter the unsung hero of cybersecurity: VPNs (Virtual Private Networks). But which one is the best for home security, and why should you even bother? Let’s unravel the mystery and help you safeguard your digital haven.
Why Do You Need a VPN for Home Security?
Think of your home Wi-Fi as the front door to your digital life. Without proper protection, it’s an open invitation for hackers, snoops, and cyber-criminals to waltz in. A VPN acts like a state-of-the-art lock, encrypting your data and hiding your IP address to keep your online activities safe from prying eyes.
Key reasons to use a VPN for home security include:
Data Encryption: Protect sensitive information like passwords and banking details from being intercepted.
Device Protection: Secure all devices connected to your network, from smartphones to smart fridges.
Privacy from ISPs: Prevent your Internet Service Provider from monitoring and selling your browsing data.
In short, a VPN ensures that what happens on your Wi-Fi stays on your Wi-Fi.
How Do VPNs Enhance Smart Home Security?
With the rise of IoT (Internet of Things) devices, home networks are more vulnerable than ever. VPNs provide an extra layer of security by encrypting data transmissions and preventing unauthorized access.BenefitHow It Protects Your Smart HomeExamples of VPNsEncryptionScrambles data to make it unreadableNordVPN, ExpressVPNIP MaskingHides your IP to prevent trackingSurfsharkRemote AccessSecurely control devices while awayCyberGhost
By routing all traffic through secure servers, VPNs create a protective bubble around your smart home ecosystem.
What Features Make a VPN Ideal for Home Security?
Not all VPNs are created equal, and some are better suited for home security than others. Here are the must-have features to look for:
AES-256 Encryption: The gold standard in cybersecurity.
Kill Switch: Automatically disconnects your internet if the VPN drops, preventing data leaks.
Router Compatibility: Protects all devices on your network by setting up the VPN directly on your router.
No-Logs Policy: Ensures your activities aren’t recorded or sold.
Multi-Device Support: Covers all your gadgets under one subscription.
VPNs like ExpressVPN and NordVPN check all these boxes, making them top contenders for home security.
Top VPNs for Home Security
Let’s dive into the best options on the market. These VPNs offer a blend of robust security, user-friendliness, and excellent performance.
NordVPN
Key Features: Double VPN for extra encryption, Threat Protection against malware.
Price: Starts at $3.99/month.
Best For: Families with multiple smart devices.
ExpressVPN
Key Features: TrustedServer technology ensures no data is stored on physical servers.
Price: Starts at $8.32/month.
Best For: High-speed streaming and security.
Surfshark
Key Features: Unlimited devices, CleanWeb for ad-blocking.
Price: Starts at $2.49/month.
Best For: Budget-conscious users.
CyberGhost
Key Features: Dedicated servers for streaming and gaming, extensive global network.
Price: Starts at $2.11/month.
Best For: Easy setup and diverse server locations.
What Are the Risks of Not Using a VPN?
Skipping a VPN is like leaving your doors unlocked in a sketchy neighborhood. Here’s what you’re exposing yourself to:
Data Breaches: Hackers can intercept sensitive information.
Device Hijacking: Unprotected IoT devices are vulnerable to being taken over.
Privacy Violations: ISPs and third-party advertisers track your every move.
Without a VPN, you’re essentially rolling out the red carpet for cyber threats.
Common Questions About Home Security VPNs
What’s the easiest way to set up a VPN for my smart home?
Install the VPN on your router to cover all connected devices.
Do VPNs slow down my internet?
Quality VPNs like ExpressVPN minimize speed drops with optimized servers.
Can a VPN protect against malware?
While not a replacement for antivirus software, some VPNs (like NordVPN) include malware protection.
How much does a reliable VPN cost?
Prices range from $2 to $10 per month, depending on the provider and features.
Are free VPNs good for home security?
Free VPNs often lack advanced security features and may sell user data. Stick to reputable paid options.
Can I use one VPN account for multiple devices?
Yes! Providers like Surfshark allow unlimited simultaneous connections.
The Final Word
Investing in the best VPN for home security is a no-brainer in today’s connected world. Whether you’re streaming your favorite shows or controlling your home’s smart lights, a robust VPN ensures your activities remain private and secure. With options like NordVPN and Surfshark, you can enjoy top-tier protection without breaking the bank. So, why leave your digital front door wide open? Lock it up with a reliable VPN and sleep easier knowing your home is safe—both online and offline!
0 notes
Text
How to Set Up and Use Proxies in Python
Proxy is an important concept in Python programming, especially when making network requests, web scraping, or data collection. The proxy server acts as an intermediary between the client and the server, playing the role of forwarding requests and responses. This article will introduce in detail what a proxy is in Python and its application in network programming and data scraping.
Basic concept of proxy
A proxy server, or proxy for short, is a network service that allows a network terminal (usually a client) to communicate indirectly with another network terminal (usually a server) through it. The proxy server receives requests from clients, then initiates requests to the target server on its own behalf, and finally forwards the response returned by the server to the client.
Main functions of proxy servers
1. Hide the real IP address of the client
When sending requests through a proxy server, the target server can only see the IP address of the proxy server, but cannot directly obtain the real IP address of the client.
2. Cache and acceleration
The proxy server can cache frequently accessed content. When multiple clients request the same content, it can be provided directly from the cache, thereby speeding up access.
3. Access control
Through the proxy server, client access can be filtered and controlled, such as blocking access to certain websites or limiting access speed. Security protection
The proxy server can encrypt or decrypt the transmitted data to provide additional security protection.
How to use proxies in Python
There are many ways to use proxies in Python. Here are some common methods:
1. Configure proxies through HTTP libraries
Many HTTP libraries in Python support proxy configuration, such as the requests library. When using the requests library to send requests, you can specify the proxy server by setting the proxies parameter. For example:import requests proxies = { 'http': 'http://your-proxy-server:port', 'https': 'https://your-proxy-server:port', } response = requests.get('http://example.com', proxies=proxies) print(response.text)
In this example, the proxies dictionary contains the proxy server addresses for HTTP and HTTPS protocols. These proxy servers are automatically used when the requests library sends requests.
2. Configure proxies through socket programming
For lower-level network programming, such as using the socket library for TCP/IP communication, you can also configure proxies to achieve network connections. This usually requires the use of some third-party libraries or writing proxy connection logic yourself.
3. Use third-party libraries
In addition to directly using the HTTP library to configure proxies, you can also use some third-party libraries to handle proxies more conveniently. For example, libraries such as puppeteer-extra and puppeteer-extra-plugin-proxy can easily configure proxies when using Puppeteer for web automation.
Types and selection of proxies
There are many types of proxy servers, including HTTP proxy, HTTPS proxy, SOCKS proxy, etc. When choosing a proxy, you need to choose the appropriate proxy type according to the specific application scenario and needs.
HTTP proxy: Applicable to ordinary HTTP requests, which can hide the client's real IP address.
HTTPS proxy: Applicable to encrypted HTTPS requests, which can provide higher security.
SOCKS proxy: Supports lower-level network communication protocols, such as TCP/UDP, and can provide more flexible proxy services.
In addition, factors such as the stability, speed, and anonymity of the proxy need to be considered. Avoid using free proxies, because some free proxy services may be unstable, slow, or have poor security.
Notes
Handling proxy errors: When using a proxy server, you may encounter various errors, such as connection failure, timeout, etc. Therefore, when writing code, you should do a good job of error handling to ensure the stability and robustness of the program. Comply with laws and regulations: When using a proxy server, you should comply with local laws and regulations and do not engage in any illegal activities.
Conclusion
Proxy plays an important role in Python programming, especially in network requests and data crawling. By using a proxy, you can bypass website access restrictions, hide the client's real IP address, and improve the efficiency and security of data crawling. When selecting and using a proxy, you need to choose the appropriate proxy type and provider based on the specific application scenario and needs.
0 notes
Text
Exploring Telegram: Channels, Search, and Verified Channels
Telegram has become one of the most popular messaging platforms globally, offering features that go beyond traditional chat apps. Its versatility includes channels, groups, bots, and end-to-end encryption, making it a go-to app for millions. Here, we’ll delve into essential aspects like Telegram channels, Telegram search, and the concept of a verified Telegram channel while exploring ways to make the most of this platform.
What Are Telegram Channels?
Telegram channels are unique features designed for broadcasting messages to large audiences. Unlike groups where members interact with each other, channels are primarily one-way communication tools where admins share updates, news, or other content with subscribers. They are perfect for businesses, content creators, or organizations aiming to reach a broad audience efficiently.
Key characteristics of Telegram channels:
Unlimited Subscribers: Channels can have an unlimited number of followers.
Admin Control: Only admins can post, ensuring focused and streamlined communication.
Visibility Options: Channels can be public (searchable by anyone) or private (accessible only through an invite link).
Popular Telegram Channels
Telegram’s vast array of channels covers topics like entertainment, education, technology, finance, and more. Some popular Telegram channels include:
News Channels: Keep up with global news in real time.
Educational Channels: Access tutorials, study materials, and language courses.
Entertainment Channels: Get the latest updates on movies, TV shows, memes, and music.
Telegram Search: Finding What You Need
With millions of channels available, the Telegram search feature is a powerful tool for discovering new channels, groups, and content. Here’s how to use it effectively:
In-App Search: Use the search bar to find public channels by name or keyword.
Third-Party Telegram Viewers: Websites like Telegram directories list popular and verified channels by category.
Filter Options: Telegram allows filtering results by type (channel, group, or bot) for more precise searches.
Pro Tip: Always verify the source before joining a channel, especially for sensitive or financial information.
What Is a Verified Telegram Channel?
A verified Telegram channel is marked with a blue checkmark next to its name, indicating authenticity. These channels are often owned by public figures, organizations, or businesses to prevent impersonation. Verification ensures that users follow official sources.
Steps to identify verified channels:
Look for the blue checkmark next to the channel name.
Confirm links shared on official websites or social media pages.
Benefits of Telegram Channels
Reach a Wider Audience: Share content with subscribers worldwide.
Privacy: Subscribers’ identities remain anonymous, offering enhanced privacy.
Rich Content: Channels support text, images, videos, and links, making content delivery dynamic.
Analytics: Admins can monitor subscriber growth and engagement through Telegram's analytics tools.
Telegram channels are a robust feature for connecting with audiences, sharing information, and creating communities. Whether you’re exploring popular Telegram channels, searching for specific content, or following a verified Telegram channel, the platform offers unmatched flexibility and security. With the right strategies, users and creators alike can maximize their experience on Telegram.
Are you ready to explore Telegram? Start by searching for channels that match your interests and join the global conversation!
0 notes
Text
Securing Workloads in OpenShift Virtualization: Tips and Techniques
As organizations continue to embrace the benefits of cloud-native technologies and virtualization, OpenShift Virtualization stands out as an essential platform for deploying and managing containerized workloads. While it offers powerful capabilities for running virtual machines (VMs) alongside containers, ensuring the security of workloads is paramount to protect data integrity and maintain regulatory compliance. This article outlines practical tips and techniques to enhance the security of your workloads in OpenShift Virtualization.
1. Implement Role-Based Access Control (RBAC)
RBAC is one of the core security mechanisms in OpenShift that helps control who can access what resources within the cluster. Ensuring that your workload access is limited to authorized users and services only is critical. Follow these best practices:
Define Roles Carefully: Create roles with the minimum necessary permissions for users and applications.
Use Service Accounts: Assign service accounts to pods and workloads to control their privileges and avoid the risk of a compromised application gaining excessive access.
Review and Audit Permissions Regularly: Perform periodic audits to identify and remove unused or overly permissive roles.
2. Secure Network Communication
Communication between workloads should be secured to prevent unauthorized access and data interception. Implement these strategies:
Network Policies: Use OpenShift’s network policy objects to define rules that control the traffic flow between pods. Ensure that only authorized pods can communicate with each other.
Service Mesh: Deploy Istio or OpenShift Service Mesh to provide enhanced traffic management, encryption, and observability across services.
TLS Encryption: Ensure all data exchanged between services is encrypted using TLS. OpenShift has built-in support for TLS, but make sure that TLS certificates are properly managed and rotated.
3. Enable and Manage Pod Security Standards
Pod Security Standards (PSS) are an essential way to enforce security configurations at the pod level. OpenShift provides tools to help secure pods according to industry standards:
PodSecurityPolicies (PSPs): While PSPs are deprecated in favor of PodSecurityAdmission (PSA), configuring your cluster to use PSA can enforce security standards such as preventing privileged containers or requiring specific security context configurations.
Security Contexts: Set up security contexts at the container level to control privileges like running as a non-root user, disabling privilege escalation, and enabling read-only file systems.
4. Control Image Security
Images are a common attack vector, making it essential to ensure that only trusted images are used for deployments.
Image Scanning: Integrate image scanning tools such as OpenShift's built-in image vulnerability scanner or third-party tools like Trivy or Clair to scan images for known vulnerabilities before deployment.
Image Signing and Verification: Use tools like Notary to sign images and enforce policies that only signed images are pulled and deployed.
Private Image Registries: Store and manage your images in a private registry with access control, ensuring that only authorized users and services can push or pull images.
5. Manage Secrets Securely
Handling secrets properly is critical for the security of your applications and infrastructure. Follow these steps:
Use OpenShift Secrets: OpenShift has native support for Kubernetes Secrets. Ensure that secrets are stored securely and accessed only by the workloads that need them.
Vault Integration: For more advanced secret management, integrate HashiCorp Vault with OpenShift to handle sensitive data, providing more control over access policies and encryption.
Avoid Hardcoding Secrets: Never hardcode secrets in application code or scripts. Use environment variables or service accounts to inject them at runtime.
6. Apply Security Patches and Updates
Keeping your OpenShift cluster and underlying virtualization environment updated is essential for closing security vulnerabilities.
Automatic Updates: Configure automated updates and patching for OpenShift components and underlying VMs.
Monitor Security Advisories: Regularly review Red Hat's security advisories and promptly apply patches or updates that mitigate potential risks.
Testing in Staging: Before deploying patches in production, test them in a staging environment to ensure stability and compatibility.
7. Implement Logging and Monitoring
Effective logging and monitoring help you detect and respond to security incidents in real time.
Centralized Logging: Use OpenShift’s built-in logging stack or integrate with a tool like Elasticsearch, Fluentd, and Kibana (EFK) to aggregate logs across the cluster and VMs.
Monitoring with Prometheus and Grafana: Leverage Prometheus for metrics collection and Grafana for dashboards that visualize performance and security data.
Alerting Mechanisms: Set up alerts for suspicious activities such as unexpected network traffic, unauthorized access attempts, or failed authentication attempts.
8. Secure Virtual Machines
When running VMs in OpenShift Virtualization, their security should align with best practices for containerized workloads.
VM Hardening: Follow hardening guidelines for your VM images, such as disabling unnecessary services, securing SSH access, and minimizing the installed software.
Isolation and Segmentation: Place VMs in different namespaces or network segments based on their sensitivity and usage. This helps limit the attack surface and restrict lateral movement in the event of a breach.
Resource Limitations: Set CPU and memory limits to prevent DoS (Denial of Service) attacks within your VMs.
9. Implement Multi-Factor Authentication (MFA)
To bolster the authentication process, enabling MFA for accessing OpenShift and the management interface is crucial.
Configure MFA with OpenShift: Use identity providers that support MFA, such as LDAP or OAuth integrations, to strengthen user authentication.
Enforce MFA for Sensitive Operations: Apply MFA to critical administrative functions to ensure that only authorized personnel can perform potentially disruptive actions.
Conclusion
Securing workloads in OpenShift Virtualization requires a multi-layered approach that combines preventive, detective, and corrective measures. By implementing these tips and techniques—ranging from robust RBAC and secure network configurations to thorough monitoring and timely patching—you can create a secure environment for your containerized and virtualized workloads. OpenShift Virtualization offers the tools to build a resilient infrastructure, but security practices should evolve in tandem with emerging threats and industry trends to protect your applications and data effectively. For more details visit: https://www.hawkstack.com/
0 notes
Text
Unlocking Business Potential with Blockchain Development: A New Era of Innovation
In an age where digital transformation is at the forefront of business strategy, blockchain technology has emerged as a powerful tool capable of reshaping industries. From securing transactions to enhancing transparency and efficiency, blockchain has the potential to revolutionize the way businesses operate. While it initially gained prominence through cryptocurrency applications, the blockchain landscape has grown exponentially, offering businesses unparalleled benefits across various sectors.
In this blog, we will explore the transformative impact of blockchain development, the benefits it brings to businesses, and how companies can leverage it to stay competitive in an increasingly digital world.

What is Blockchain Technology?
At its essence, blockchain is a decentralized, distributed ledger system that securely records data across multiple computers. Each data block is cryptographically linked to the previous one, creating an immutable chain that ensures data integrity and security. What sets blockchain apart from traditional databases is its transparency, traceability, and ability to operate without the need for a central authority or intermediary.
This makes blockchain an ideal solution for industries that require secure, transparent, and auditable transaction histories. Its applications span beyond cryptocurrency to include areas such as supply chain management, healthcare, finance, and more.
Why Blockchain Development is a Game-Changer for Businesses
1. Unmatched Security
Cybersecurity threats are a major concern for businesses across industries. Traditional centralized systems are vulnerable to attacks, leading to data breaches and loss of trust. Blockchain provides a robust, decentralized infrastructure that significantly reduces the risk of hacking. Data stored on the blockchain is encrypted and distributed across multiple nodes, making it nearly impossible to alter or tamper with. This enhanced security ensures that businesses can protect sensitive data and maintain customer trust.
For sectors like finance, healthcare, and e-commerce, where privacy and security are paramount, blockchain’s tamper-proof ledger offers an added layer of protection that traditional systems cannot match.
2. Increased Transparency
Transparency is a critical factor for building trust with customers, partners, and stakeholders. In traditional systems, data is often controlled by a central authority, leaving room for manipulation. Blockchain addresses this by offering a transparent, immutable record of transactions. Every action is recorded on a public ledger, ensuring that the entire network has access to the same information, which promotes accountability.
This transparency is particularly beneficial in industries like supply chain management, where verifying the origin and authenticity of products is vital. Blockchain enables businesses to track the journey of products from manufacturer to end consumer, ensuring their provenance and reducing fraud.
3. Efficiency and Cost Reduction
Blockchain has the power to streamline business processes by eliminating intermediaries. In traditional transactions, intermediaries such as banks, payment processors, or legal entities are required to validate and execute contracts. These intermediaries introduce additional costs, delays, and complexities into the process. With blockchain, businesses can conduct transactions directly, reducing the need for third parties and lowering associated fees.
Smart contracts, which are self-executing contracts with predefined rules, further streamline operations by automating contract enforcement. This reduces administrative overhead, eliminates human error, and accelerates the transaction process. From supply chain operations to payments and legal agreements, blockchain provides an efficient, cost-effective solution.
4. Improved Traceability
For industries dealing with valuable or sensitive goods, traceability is essential. Blockchain offers a robust way to track the movement of assets throughout the supply chain, ensuring that every transaction is documented and can be traced back to its source. This traceability helps businesses verify the authenticity of their products, reduce fraud, and comply with regulatory standards.
For example, in the food industry, blockchain can be used to trace the journey of food products from farm to table, ensuring that consumers receive safe and authentic goods. Similarly, in the pharmaceutical industry, blockchain can help prevent counterfeit drugs from entering the market, ensuring that only genuine products reach patients.
Key Use Cases of Blockchain Development
1. Financial Services
Blockchain’s most well-known application is in the financial services industry, where it is used for secure, transparent, and efficient transactions. Blockchain eliminates the need for banks and other intermediaries in payment processing, reducing costs and transaction times. Additionally, blockchain enables secure cross-border payments and creates decentralized financial systems (DeFi) that operate without the need for traditional banks.
2. Supply Chain Management
Blockchain can greatly enhance supply chain visibility, allowing businesses to track products from origin to final delivery. By creating an immutable record of every transaction, blockchain provides verifiable proof of the authenticity, quality, and origin of products. This helps businesses optimize their supply chain operations, reduce fraud, and increase consumer confidence.
3. Healthcare
Blockchain is revolutionizing the healthcare industry by offering a secure way to store and share patient data. By providing a decentralized, immutable record of patient information, blockchain ensures that medical records are accurate, up-to-date, and easily accessible to authorized medical professionals. This helps reduce errors, improve patient care, and streamline administrative tasks.
4. Real Estate
Blockchain simplifies property transactions by reducing the need for intermediaries such as notaries, lawyers, and banks. Smart contracts in blockchain can automate the entire process of buying and selling property, from signing agreements to transferring ownership, which speeds up transactions and reduces costs.
Why Choose Miracuves for Blockchain Development?
At Miracuves, we specialize in creating customized blockchain solutions that cater to the unique needs of your business. Our expert developers work closely with you to design and implement blockchain systems that align with your objectives and enhance your operations. Whether you need a private blockchain, smart contract integration, or enterprise-level solutions, we have the expertise to deliver secure and scalable solutions.
Our blockchain development services include:
Custom Blockchain Solutions: Tailored to your specific industry and business needs.
Smart Contract Development: Automate business processes with secure, self-executing contracts.
Blockchain Consulting: Expert guidance on how to leverage blockchain for your business.
Integration: Seamlessly integrate blockchain with your existing systems to enhance efficiency.
Conclusion
Blockchain technology has the potential to revolutionize industries, offering enhanced security, transparency, efficiency, and cost savings. By embracing blockchain, businesses can future-proof themselves, build trust with customers, and unlock new opportunities for growth.
Partner with Miracuves today and explore how blockchain Development can transform your business into a more secure, transparent, and efficient enterprise. Reach out to us to begin your blockchain journey and stay ahead in the digital transformation race.
0 notes
Text
AWS Secret Manager Cost, Access Control And Authentication

Access control and authentication for AWS Secret Manager
AWS Identity and Access Management (IAM) is used by Secrets Manager to protect secret access. Access control and authentication are offered by IAM. Authentication confirms the legitimacy of people’s requests. Multi-factor authentication (MFA) tokens, access keys, and passwords are used in Secrets Manager’s sign-in procedure to confirm users’ identities. Look logging into AWS. Only authorized users are able to access AWS resources, including secrets, thanks to access control. Policies are used by Secrets Manager to specify who can access what resources and what actions an identity can do on them. View IAM’s policies and permissions.
Reference to AWS Secret Manager permissions
The Secrets Manager permissions reference may be found in the Service Authorization Reference under Actions, resources, and condition keys for AWS Secrets Manager.
Administrator permissions for Secrets Manager
Attach the following policies and complete the steps at Adding and deleting IAM identity permissions to provide AWS Secret Manager administrator permissions:
SecretsManagerReadWrite
IAMFullAccess
AWS advises against giving end users administrator privileges. The permission needed to enable rotation (IAMFullAccess) gives substantial access that are inappropriate for end users, even while this lets your users generate and manage own secrets.
Lambda rotation function permissions
Secrets Manager rotates secrets using AWS Lambda functions. Both the secret and the database or service for which the secret includes login credentials must be accessible to the Lambda function.
Keys for encryption permissions
AWS Secret Manager encrypts secrets using AWS Key Management Service (AWS KMS) keys. The proper permissions are immediately present in the AWS managed key aws/secretsmanager. Secrets Manager need permissions to the KMS key if you use a different one.
Replication permissions
You can limit which users or services are able to duplicate your secrets to other regions by utilizing IAM authorization policies.
Which secrets are allowed to be kept in Secrets Manager?
Database credentials, on-premises resource credentials, SaaS application credentials, third-party API keys, and Secure Shell (SSH) keys are among the secrets that can be managed.
Please be aware that while AWS Secret Manager lets you save a JSON document that lets you handle any text blurb that is 64 KB or less, allowing it to be utilized in a variety of situations, there are better ways to maintain some sorts of secrets in AWS, such as:
AWS credentials: Rather than using Secrets Manager to store or get AWS credentials, we can utilize AWS IAM.
Use the AWS KMS service for encryption keys.
Use AWS EC2 Instance Connect instead of SSH keys.
Use AWS Certificate Manager for private keys and certificates.
Beginning to Use AWS Secret Manager
Step 1: Create an AWS account and log in
You can secure access to your IT resources, services, and apps with AWS Secrets Manager.
Step 2: Access the Console for Secrets Management
Throughout their existence, database credentials, API keys, and other secrets can be effortlessly rotated, managed, and retrieved.
Step 3: To start the wizard, click on Store a new secret
Our 30-day free trial allows you to test Secrets Manager without paying anything extra. When you store your first secret, the free trial begins.
AWS Secrets Manager pricing
Pricing Overview
You can rotate, manage, and recover secrets at any point in their lifecycle using AWS Secret Manager, which makes it simpler to keep your environment safe and compliant. You pay for Secrets Manager according to how many secrets are saved and how many API calls are made. There are no long-term agreements or up-front fees. You only pay for usage; you don’t have to pay for the staff, infrastructure, or licenses needed to guarantee that your secrets are highly accessible and dependable.
Free Trial
Trial Period of 30 Days
With a 30-day free trial, you may test AWS Secrets Manager without paying anything more. You can rotate, manage, and retrieve secrets during the 30-day free trial.
When you store your first secret, your free trial begins.
Pricing
Monthly Per Secret
Each secret costs $0.40 a month. Replica secrets are billed at $0.40 per replica each month and are regarded as separate secrets. The cost is prorated (according to the amount of hours) for secrets that are kept for less than a month.
Get in touch with AWS if your company intends to use a lot of secrets.
Per 10,000 API calls
$0.05 per 10,000 API calls
Read more on Govindhtech.com
#AWSSecretManagerCost#AWSSecret#SecretManager#AWSSecretManager#IAM#KMSkey#News#Technews#Technology#Technologynews#Technologytrends#Govindhtech
0 notes
Text
Best Public Cloud Hosting Service: Explore Real Cloud's Managed Cloud Hosting Services
In the digital age, cloud hosting has revolutionized the way businesses manage their data, applications, and infrastructure. Among the vast array of cloud service providers available today, Real Cloud stands out as one of the leading players in providing the best public cloud hosting services. Whether you are a startup or a well-established enterprise, the need for a reliable, scalable, and efficient cloud hosting solution is crucial to your business operations.
In this article, we will explore how Real Cloud managed cloud hosting services can help your business thrive, offering a comprehensive solution that combines flexibility, cost-effectiveness, and top-tier support. We will dive into the benefits, features, and advantages that come with choosing Real Cloud for your hosting needs.
What is Public Cloud Hosting?
Public cloud hosting refers to a cloud hosting model where the infrastructure and services are provided by a third-party service provider, such as Real Cloud. This means that your data and applications are hosted on shared resources that are accessible over the internet, as opposed to dedicated servers.
Public cloud hosting allows businesses to scale their resources quickly and efficiently, as they only pay for the resources they use. It offers flexibility, cost-effectiveness, and robust security measures, which is why it is considered the go-to solution for many businesses around the world.
Why Choose Real Cloud for Public Cloud Hosting?
When it comes to selecting a cloud hosting provider, it is essential to choose one that offers reliability, security, and excellent customer support. Real Cloud checks all the boxes, providing a comprehensive range of services that make it one of the best public cloud hosting services available in the market.

Here are some of the reasons why businesses should choose Real Cloud for their public cloud hosting needs:
1. Scalability and Flexibility
One of the major benefits of Real Cloud's managed cloud hosting services is its scalability. Businesses often face fluctuating demands for resources based on their growth and requirements. With Real Cloud, you can easily scale your hosting resources up or down, depending on your business needs. This allows you to avoid overpaying for unused resources while ensuring that you have the capacity to handle traffic spikes or growth in demand.
2. Security and Compliance
Security is a top priority for Real Cloud. Their cloud hosting services come with enterprise-grade security features, including data encryption, firewalls, intrusion detection systems, and regular security patches. Additionally, Real Cloud is fully compliant with major industry standards and regulations, such as GDPR, HIPAA, and PCI-DSS. This makes Real Cloud a trustworthy choice for businesses looking to protect sensitive data and ensure compliance with legal and regulatory requirements.
3. 24/7 Support
With Real Cloud's managed cloud hosting services, you are not alone in managing your cloud infrastructure. Their dedicated team of experts is available around the clock to assist with any technical issues, whether it’s a server outage or a performance-related concern. The 24/7 support team ensures minimal downtime and offers quick resolutions to any issues, allowing businesses to focus on growth without worrying about the technical aspects of cloud hosting.
4. Cost-Effectiveness
Many businesses, particularly startups and small enterprises, are cautious about the cost of cloud hosting. Real Cloud offers a best public cloud hosting service that is highly cost-effective. Instead of purchasing and maintaining expensive physical servers, businesses can rely on Real Cloud to provide scalable resources at a fraction of the cost. With pay-as-you-go pricing, you only pay for the resources you use, giving you greater control over your budget.
Benefits of Managed Cloud Hosting Services by Real Cloud
While public cloud hosting offers numerous advantages, managing your cloud infrastructure can be complex, especially for businesses without dedicated IT teams. This is where Real Cloud's managed cloud hosting services come in. Real Cloud takes care of all the technical aspects of cloud hosting, leaving you free to focus on running your business.
Let’s look at the key benefits of opting for managed cloud hosting services with Real Cloud:
1. Expert Management
With Real Cloud's managed services, you get a team of experts who handle everything from server management to security. This ensures that your cloud environment is optimized for performance, availability, and security without the need for you to have an in-house IT team. Real Cloud’s team takes care of the technical setup, ongoing maintenance, and troubleshooting, so you don’t have to.
2. Performance Optimization
Cloud hosting can be resource-intensive, and businesses often face challenges in ensuring that their websites, apps, and systems run at peak performance. Real Cloud provides managed services that include regular performance optimization, which helps improve the speed and efficiency of your applications. Whether it’s through load balancing, optimizing databases, or adjusting server configurations, Real Cloud ensures that your services run smoothly at all times.
3. Automatic Backups
Data loss is a critical issue for businesses of all sizes, and Real Cloud understands the importance of safeguarding your data. Their managed cloud hosting services include automated backups, ensuring that your data is regularly backed up to secure storage locations. In case of a disaster or system failure, you can restore your data quickly and resume operations with minimal disruption.
4. Updates and Patches
Keeping your systems up-to-date with the latest software patches and updates is essential for maintaining security and performance. Real Cloud's managed services handle this task for you, ensuring that your cloud environment is always running the latest and most secure versions of the software. This minimizes the risk of security vulnerabilities and helps improve the overall stability of your services.
5. Cost Control
With Real Cloud's managed cloud hosting services, you get a predictable pricing model that helps you manage your IT costs efficiently. You can scale your resources based on demand, ensuring that you don’t pay for unused services. This level of control over your cloud infrastructure allows you to avoid overspending while getting the resources you need for growth.
Key Features of Real Cloud's Public Cloud Hosting Services
Real Cloud provides a comprehensive suite of features that make it the best public cloud hosting service available. Here are some key features that set Real Cloud apart from other providers:
1. High Availability and Uptime
Downtime can be detrimental to businesses, especially those that operate in industries that require continuous service availability. Real Cloud guarantees high availability, ensuring that your services are up and running at all times. With a network of multiple data centres, Real Cloud provides redundancy and failover mechanisms that minimize the risk of service outages.
2. Global Reach
With data centres in various regions across the world, Real Cloud provides businesses with a global reach. This allows you to deploy applications and services closer to your customers, improving performance and reducing latency. Whether you have a local, regional, or global customer base, Real Cloud’s infrastructure is designed to meet your needs.
3. Customizable Solutions
Every business is unique, and Real Cloud understands that. Their public cloud hosting services are highly customizable, allowing businesses to tailor their infrastructure to meet their specific requirements. Whether you need more storage, computing power, or bandwidth, Real Cloud provides the flexibility to design a cloud environment that suits your needs.
4. Comprehensive Analytics
Real Cloud provides detailed analytics and reporting tools to give you insights into your cloud infrastructure's performance. These analytics help you monitor resource usage, identify bottlenecks, and optimize your cloud environment for efficiency. This data-driven approach ensures that your cloud resources are being used effectively and that your business can scale seamlessly.
Conclusion
In conclusion, Real Cloud offers the best public cloud hosting services for businesses of all sizes. With a focus on scalability, security, performance, and cost-effectiveness, Real Cloud provides a robust cloud hosting solution that is tailored to meet your business’s needs. Their managed cloud hosting services ensure that you get expert support and management for your cloud infrastructure, leaving you free to focus on growing your business.
Whether you are looking for an enterprise-grade cloud solution or a flexible hosting environment for your startup, Real Cloud has the tools, expertise, and infrastructure to support your business goals. With Real Cloud, you can rest assured that your cloud environment is in safe hands, allowing you to scale and innovate without limitations.
Make the smart choice today by opting for Real Cloud as your best public cloud hosting service provider. Enjoy a seamless, secure, and cost-effective cloud hosting experience with Real Cloud's managed services.
0 notes
Text
Mitigating Cybersecurity Threats in Channel Partner Management
Channel partner management is no longer optional for businesses looking to scale - it is a necessity. But all this interconnectedness and sharing of data brings its own cybersecurity threat, which is increasing significantly as well. Cyberattacks can compromise the sensitive ecosystems of partners, thus compromising business reputation and continuity apart from data integrity.
To this, an organization should ensure higher cybersecurity aspects. Here are the ways business can ensure that channel partner networks are safe and resilient.

Main Cyber Threats to Channel Partner Management
1. Data Breach: In this case, there is a possibility that encrypted sensitive information may leak owing to the unsecured data sharing protocols between businesses and partners.
2. Phishing Attack: Commonly referred to as man-in the-middle attack, cyber attackers get into the credentials or sensitive information by having a look at the partner's communication channels and then manipulate the individuals into revealing such information.
3. Authentication Not in Place: Poor password policies and logon applications provide a soft point of entry for a hacker
4. Inadequacies of Third-Party Suppliers: Out-sourcing to third-party suppliers can lead to exposing the general inadequacies of the service provider's security posture
Proven Methods
1. Stiffen Access Controls
Implement role-based access controls so that only permitted individuals have access to sensitive data, and multi-factor authentication is another layer of needed defense.
2. Cybersecurity Audits
You need to review your partner ecosystem often for vulnerabilities. Identify and make good on gaps in compliance, protocol, and practice.
3. Partner Training Programs
Train your partners on the recognition of phishing attempts, securing devices, best practices, and so on. Cybersecurity awareness needs to be incorporated into the culture of your partners.
4. Use Secure Collaboration Tools
Invest in encrypted tools that can further ensure that data sharing and communication will be less intercepted and accessed without permission.
5. Continuous Monitoring
Use sophisticated monitoring systems for some real-time detection of suspicious activity. Quick action may prevent minor threats from turning into major breaches.
How Channel Technologies Can Help
Channel Technologies specialized in providing secure and seamless partner ecosystems for businesses across industries. While our customized solutions ensure efficient, streamlined operations, every stage is aligned with the highest priority given to the state of cybersecurity. Secure channels of communication, customizable training programs, and protection of assets and trust among partners-bestowed on businesses-are some of the things that differentiate Channel Technologies in this rapidly changing era.
Cybersecurity is no longer just a choice, but a necessity, and one of the channel partner management necessities in today's world. Businesses can take an active approach to these challenges by focusing on protecting operations, building solid partnerships, and reaping long-term success.
Secure your partner ecosystem today. Learn more about how Channel Technologies can make your channel management strategies more secure.
Before we wrap up, we’re excited to share that we’ll be hosting a CT Cyber Charcha: Cybersecurity Conference in February 2025. This event will delve into the latest trends, challenges, and solutions in cybersecurity, with a focus on the Indian context. It’s a great opportunity for industry professionals to gain actionable insights and explore innovative solutions to today’s cybersecurity challenges.
#channeltechnologies#eventmanagement#b2bmarketing#leadgeneration#cybersecurityawareness#cybersecurity
0 notes
Text
Security First: What You Need to Know About Facebook’s Enhanced Privacy and Security Updates
With each passing year, the digital landscape becomes increasingly complex, and protecting personal information online has never been more essential. This is especially true for social media users, who rely on platforms to connect, share, and build communities. Facebook, one of the world’s largest social networks, is continuously evolving to meet users’ security needs. Recently, Facebook’s newest updates have introduced a range of advanced privacy and security features, marking a renewed commitment to safeguarding user information and enhancing trust on the platform. From stronger encryption protocols to advanced data controls, these updates are designed to address growing privacy concerns and adapt to ever-changing digital risks.
These updates are not only crucial for individual users but also for businesses and content creators who use Facebook to build and grow their online presence. Companies like Deliver My Tune, for example, rely on secure platforms to engage with their audience without compromising sensitive data. Facebook’s emphasis on improved security practices and user controls is a significant step toward ensuring the platform remains a safe and trustworthy space for personal and professional interactions.
1. End-to-End Encryption for Enhanced Communication Security
End-to-end encryption has become a must-have feature for messaging apps, and Facebook has implemented this in both its Messenger and WhatsApp platforms. This encryption ensures that only the sender and the recipient can read messages, making it significantly harder for anyone else—even Facebook itself—to access the content. With this update, Facebook is prioritizing user security by protecting conversations from unauthorized access or interception.
The roll-out of end-to-end encryption follows a growing trend in digital communication that values privacy and user control. For businesses and influencers, this provides a secure way to communicate with clients, customers, or followers, knowing that their exchanges are protected from external interference. It’s particularly valuable for brands handling sensitive customer information, as it allows them to build stronger trust with their audience.
2. Improved Data Access and Management Tools
In the wake of rising concerns around data misuse, Facebook’s newest updates have introduced improved tools for data access and management. Users now have more granular control over what information they share, with clear and accessible options for limiting data shared with apps, advertisers, and third-party sites. The platform’s "Off-Facebook Activity" feature allows users to see which businesses or websites have shared information about their interactions on external sites, providing greater transparency and options to manage data sharing.
For brands, these changes encourage transparency, giving businesses that handle data responsibly an advantage. Users who feel in control of their information are more likely to engage with companies they trust. Platforms like Deliver My Tune, which prioritize secure interactions, benefit from Facebook’s data transparency, as it aligns with their own commitment to protecting user information.
3. Privacy Checkups and Alerts for Proactive Security
Facebook has improved its Privacy Checkup tool to help users quickly review and adjust privacy settings. This feature now guides users through different aspects of their account security, such as who can see their posts, which apps have access to their information, and settings for two-factor authentication. Privacy alerts have also been introduced, notifying users when a new login is detected or when any suspicious activity occurs on their account.
These proactive security measures ensure that users can take immediate action when any risk is detected. Businesses and creators who manage multiple accounts or pages, in particular, benefit from these alerts, as they help safeguard against unauthorized access and potential security breaches. With Privacy Checkup, users don’t have to navigate complex menus to secure their accounts—they can simply follow step-by-step guidance tailored to their security needs.
4. Two-Factor Authentication for an Added Security Layer
Two-factor authentication (2FA) has been a standard security feature across most digital platforms, but Facebook’s latest update makes 2FA even easier to use. The new 2FA setup streamlines the process, providing users with multiple options, including mobile app authentication, SMS codes, and email verification. By adding an extra layer of security, Facebook is helping users protect their accounts from potential threats, especially in cases of lost or stolen passwords.
This update is particularly helpful for content creators and businesses, as it ensures that their accounts remain secure even if passwords are compromised. Many brands invest considerable time and resources into building their online presence on Facebook, and 2FA protects this investment by ensuring accounts are harder to hack. This added layer of security also reassures customers and followers that the accounts they engage with are authentic.
5. Restricting Third-Party Access with App Permissions
Facebook’s newest updates also focus on limiting third-party access to user data through improved app permissions. Users can now see which apps are connected to their Facebook account and have the option to remove permissions or limit data access for each app. This change comes in response to increased awareness of data misuse by third-party apps, as users seek greater control over who can access their personal information.
By restricting third-party access, Facebook is empowering users to make more informed decisions about which apps they trust. This is beneficial not only for individual users but also for businesses that value secure interactions with their audience. When users feel that their data is protected, they are more likely to trust the platform and the businesses that operate within it.
6. Improved Advertising Transparency
To address privacy concerns surrounding advertising, Facebook has implemented improved advertising transparency. The platform’s "Why am I seeing this ad?" feature now provides users with detailed explanations on how specific ads are targeted. Users can also adjust their ad preferences, deciding what types of information they want to be used for ad targeting.
This transparency benefits users by making them feel more in control of their experience on the platform. For businesses, it encourages ethical advertising practices that align with consumer values. Users who understand why they are being targeted by certain ads may be more receptive, creating a positive feedback loop between businesses and their audience.
7. Focus on Misinformation and Content Moderation
Facebook’s newest updates also address misinformation, an issue that has gained significant attention in recent years. The platform has introduced more rigorous content moderation policies and increased reliance on artificial intelligence to detect and remove misleading or harmful content. This change ensures that users see accurate, trustworthy information, especially around topics like health, politics, and social issues.
Content creators, businesses, and influencers are all impacted by this change. Reliable information fosters trust, and users are more likely to engage with pages and businesses that are aligned with Facebook’s community standards. By reducing the spread of misinformation, Facebook creates a healthier online environment, where trustworthy businesses can thrive.
Conclusion
Facebook’s newest updates represent a forward-thinking approach to privacy and security, addressing key concerns that have emerged as digital privacy becomes a central issue. From end-to-end encryption to enhanced data management tools, these changes are designed to build user trust and create a safer environment for personal and professional interactions. By offering granular data controls, proactive security alerts, and tools to restrict third-party access, Facebook is empowering users to take charge of their digital footprint, reflecting a deeper commitment to responsible data stewardship.
These updates are equally beneficial for brands, businesses, and content creators, especially those, like Deliver My Tune, that prioritize secure and transparent online interactions. As digital spaces continue to evolve, Facebook’s new security features help businesses connect more confidently with their audience, knowing that their interactions are protected by a platform that values privacy. The latest changes reinforce Facebook’s commitment to safeguarding its users, setting a new standard for other social media platforms to follow.
0 notes