#legal files software review
Explore tagged Tumblr posts
Text
Jira Quick Start Guide: Manage your projects efficiently using the all-new Jira" by Ravi Sagar
The book "Jira Quick Start Guide: Manage your projects efficiently using the all-new Jira" by Ravi Sagar has received mixed reviews from readers. Here's a summary of the feedback:
Positive Review (5.0 out of 5 stars)
Seann Ikon, a reader from the United States, found the book to be concise and informative. They recommend it for anyone working with Jira, even if they are more accustomed to using AzureDevOps.
Negative Review (2.0 out of 5 stars)
Glosso, another reader from the United States, expressed dissatisfaction with the book's writing style. They found the writing to be bad, with numerous issues related to grammar and verbosity. The reviewer found it distracting and ultimately unreadable. They provided examples of sentences that could be improved for clarity and conciseness.
Negative Review (1.0 out of 5 stars)
An anonymous Amazon Customer from the United States did not find the book useful. They suggested that the book might have been written for an earlier version of JIRA, indicating a lack of relevance to the current Jira software.
Neutral Review (3.0 out of 5 stars)
Revanth Kumar K from India mentioned that the book's price was too high, suggesting it might be overpriced.
Negative Review (2.0 out of 5 stars)
Lord Bernard De Montacute, a reader from the United Kingdom, described the book as weak and thin in terms of content. They felt it did not provide sufficient value for the money spent and believed they could have written a similar book in a short amount of time.
Positive Review (5.0 out of 5 stars)
Mike Connor from Australia expressed a positive view of the book but didn't provide a detailed review.
In conclusion, the book appears to have some valuable information about Jira, but it also faces criticism for its writing style, relevance, and pricing. Readers' opinions vary, so it may be worth considering the specific aspects of the book that align with your needs and preferences before making a decision to purchase it.
#x 10' rug#jirair 5'3#software review#gramps genealogy software review#aura software review#reunion family tree software review#3d modeling software review#eraser software review#moho animation software review#0 review ready for company review#software review.com#coins software review#easeus software review#legacy genealogy software review#legal files software review#odoo software review#software shop review#wealthtrace software review#fastmove software review#hq rental software review#homebank software review#zoho accounting software review#reaper software review#agm software review#software architecture review checklist#backup software review#clio law firm software review#software reviews for mac#global trading software review#kuta software review of algebraic and numeric expressions
3 notes
·
View notes
Text
crowdstrike hot take 5: so who was incompetent, really?
OK so it's the first Monday after the incident. CrowdStrike (CS) is being tight-lipped about the actual cause of the incident, which Microsoft estimates to have affected 8.5 million devices.
Here's an unconfirmed rumor: CS has been firing a lot of QA people and replacing them with AI. I will not base this post on that rumor. But...
Here's a fact: wikipedia listed 8429 CS employees as of April 2024. Now the updated page says they have 7925 employees in their "Fiscal Year 2024".
Anyway. Here's a semi-technical video if you want to catch up on what bluescreen and kernel-mode drivers are in the contexts of the CS incident by a former microsoft engineer. He also briefly mentions WHQL certification - a quality assurance option provided by Microsoft for companies who want to make sure their kernel drivers are top-notch.
Now conceptually, there are two types of updates - updates to a software itself, and a definition update. For a videogame, the software update would be a new feature or bugfixes, and content update would add a new map or textures or something. (Realistically they come hand in hand anyway.) For an antivirus/antimalware, a definition update is basically a list of red flags - a custom format file that instructs the main software on how to find threats.
The video mentions an important thing about the faulty update: while many people say "actually it wasn't a software update that broke it, it was a definition file", it seems that CS Falcon downloads an update file and executes code inside that file - thus avoiding the lengthy re-certification by Microsoft while effectively updating the software.
Some background: On audits in software
A lot of software development is unregulated. You can make a website, deploy it, and whether you post puppy pictures or promote terrorism, there's no one reviewing and approving your change. Laws still apply - even the puppy pictures can be problematic if they include humans who did not consent to have their photos taken and published - but no one's stopping you immediately from publishing them.
And a lot of software development IS regulated - you cannot make software for cars without certifications, you cannot use certain programming languages when developing software for spaceships or MRIs. Many industries like online casinos are regulated - IF you want to operate legally in most countries, you need a license, and you need to implement certain features ("responsible gaming"), and you must submit the actual source code for reviews.
This varies country by country (and state by state, in USA, Canada, etc) and can mean things like "you pay $200 for each change you want to put to production*", or it can mean "you have to pay $40'000 if you make a lot of changes and want to get re-certified".
*production means "web servers or software that goes to end customers", as opposed to "dev environment", "developer's laptop", "QA environment" or "staging" or "test machines", "test VMs" or any of the other hundreds way to test things before they go live.
The certification, and regular audits, involves several things:
Testing the software from user's perspective
Validating the transactions are reported correctly (so that you're not avoiding taxes)
Checking for the user-protecting features, like being able to set a monthly limit on depositing money, etc
Checking the source code to make sure customers are not being ripped off
Validating security and permissions, so a janitor can't download or delete production databases
Validating that you have the work process that you said you would - that you have Jira (or similar) tickets for everything that gets done and put to production, etc, and
...that you have Quality Assurance process in place, and that every change that goes to production is tested and approved
You can see why I highlighted the last point, right.
Now, to my knowledge, security software doesn't have its own set of legal requirements - if I want to develop an antivirus, I don't need a special permission from my government, I can write code, not test it at all, and start selling it for, idk for example $185 per machine it gets deployed to.
And here's the thing - while there certainly is a level of corruption / nepotism / favoritism in the IT industry, I don't think CloudStrike became one of the biggest IT security providers in the world just by sweet talking companies. While there isn't any legal regulation, companies do choose carefully before investing into 3rd party solutions that drastically affect their whole IT. What I mean, CloudStrike probably wasn't always incompetent.
(Another rumor from youtube comments: A company with ~1000 employees was apparently pressured by an insurance company to use CrowdStrike - whether it's a genuine recommendation, an "affiliate link" or just plain old bribery... I do not know.)
WHY what happened is still very baffling
See, this is what would be the process if I was running a security solutions company:
a team is assigned a task. this task is documented
the team discusses the task if it's non-trivial, and they work on it together if possible
solo developer taking the task is not ideal, but very common, since you cannot parallelize (split it between several people) some tasks
while developing, ideally the developer can test everything from start to finish on their laptop. If doing it on their laptop isn't possible, then on a virtual machine (a computer that runs only inside software, and can be more or less stored in a file, duplicated, restored to a previous version, backed up, etc, just by copying that file)
in case of automated software updates, you would have "update channels". In this case it means... like if you have a main AO3 account where you put finished things, and then you'd have another AO3 account where you only put beta fics. So in my hypothetical company, you'd have a testing update channel for each developer or each team. The team would first publish their work only on their update channel, and then a separate QA team could test only their changes.
Either way, after maybe-mostly-finishing the task, the code changes would be bundled in something called a "pull request" or "PR" or "merge request". It's basically a web page that displays what was the code before and after. This PR would be reviewed by people who have NOT worked on the change, so they can check and potentially criticize the change. This is one of the most impactful things for software quality.
Either before or after the PR, the change would go to QA. First it would be tested just in the team's update channel. If it passes and no more development is needed on it, it would go to a QA update channel that joins all recent changes across all teams.
After that, it would be released to an early access or prerelease update channel, sometimes called a canary deploy. Generally, this would be either a limited amount - maybe 100 or 1000 computers, either used internally, or semi-randomly spread across real clients, or it could be as much as 10% of all customers' computers.
THEN YOU WAIT AND SEE IF THERE ARE NO ERROR REPORTS.
Basically ALL modern software (and websites! all the cookies!) collect "metrics" - like "how often each day is this running", or "did our application crash"
you absolute MUST have graphs (monitoring - sometimes this is a part of discipline called "reliability engineering") that show visually things like the number of users online, how many customers are lagging behind with updates, how many errors are reported, how many viruses are being caught by our software. If anything goes up or down too much, it's a cause for concern. If 10% of your customers are suddenly offline after a canary deploy is out, you're shitting your pants.
ONLY after waiting for a while to see everything is okay, you can push the update to ALL clients. It is unfathomable how anyone would do that straight away, or maybe how someone could do it without proper checks, or how the wrong thing got sent to the update.
As ClownStrike is still silent about the actual cause of the issue, we can only make guesses about how much they circumvented their own Quality Assurance process to push the faulty update to millions of computers.
It gets worse
Here's the thing: CrowdStrike itself allows users to create computer groups and let them choose the update channel. You, as a business customer, can say
these 100 unimportant laptops will have the latest update
these important servers will have N-1 update (one version behind)
the rest of the company will have N-2 update (two update versions behind)
CrowdStrike has ignored those settings. According to some youtube comments, supposedly they pushed the update to "only" 25% of all devices - which is worrying to think this could have gone even worse.
Third time isn't the charm
And hey, do you know what happened two years before CrowdStrike was founded? The CEO George Kurtz was at the time, in 2010, the CTO of McAfee, the controversial / crappy security company (IMO offering one of the worst antivirus programs of all times, that was aggressively pushed through bundled OEM deals). In both 2009 and 2010 their enterprise software deleted a critical operating system file and bricked a lot of computers, possibly hundreds of thousands.
And yes, the trigger wasn't an update to the antivirus itself, but a faulty "definition update". Funny coincidence, huh.
12 notes
·
View notes
Text
About three years ago, some of Google’s security engineers came to company attorneys with a gigantic mess.
The security team had discovered that Google unwittingly was enabling the spread of malicious software known as Glupteba. The malware had corrupted more than 1 million Windows computers, turning them into vehicles to mine cryptocurrency and spy on users. By hijacking Google accounts, purchasing Google ads to lure in users, and misusing Google cloud tools, the hackers behind the operation were on their way to infecting even more computers.
Tech giants such as Google long have had a playbook for destroying botnets like Glupteba. They call up fellow companies and US authorities and together coordinate a massive takedown operation. Sometimes, the cops file criminal charges. But this time around, Google’s legal team recommended an approach that the company hadn’t pursued in years: Sue the hackers for money.
The eventual lawsuit against two Russian men and a dozen unnamed individuals allegedly behind Glupteba would be the first of a run of at least eight cases that Google has filed against various hackers and scammers, adding to a sporadic few filings in the past. The tactic, which Google calls affirmative litigation, is meant to scare off would-be fraudsters and generate public awareness about scams. Now, for the first time, Google is opening up about this strategy.
Leaders of Google’s security and legal teams tell WIRED they believe going after people in court has paid off. Google hasn’t yet lost a case; it has collected almost all of the more than $2 million that it has won through the legal process, and forced hundreds of companies or websites to shut down. The awards are trivial to Google and its parent Alphabet, a $2 trillion company, but can be devastating for the defendants.
“We’re disrupting bad actors and deterring future activity, because it’s clear that the consequences and the costs are high,” says Chester Day, lead of the three-person “litigation advance” team at Google that’s focused on taking people to court. Google, he adds, is “making it clear that we’re willing to invest our resources into taking action to protect our users.”
Google blog posts and similar content about the lawsuits and the underlying scams have drawn more than 1 billion views, according to the company. Google representatives say that the awareness increases vigilance among consumers and shrinks the pool of vulnerable targets. “Educating people about how these crimes work may be the best thing we can do to stop the crime,” says Harold Chun, director of Google’s security legal team.
Several Big Tech companies have pursued affirmative litigation, though not necessarily under that name and with varying strategies. Microsoft has filed more than two dozen lawsuits since 2008 with a focus on securing court permission to dismantle botnets and other hacking tools. Amazon has been a prolific complainant since 2018, filing at least 42 cases over counterfeit products, 38 for reviews fraud, three for copyright abuse, and, recently, two for bogus product returns. Amazon has been filing so many counterfeit cases, in fact, that the federal court in western Washington assigned three magistrate judges to focus on them.
Since 2019, Meta has filed at least seven counterfeiting or data theft cases, with settlements or default judgments in four so far, including one in which it won nearly $300,000 in damages. Like Meta, Apple has sued Israeli spyware developer NSO Group for alleged hacking. (NSO is fighting the lawsuits. Trials are scheduled for next year.)
Some attorneys who’ve studied how the private sector uses litigation to enforce the law are skeptical about the payoff for the plaintiffs. David Noll, a Rutgers University law professor and author of a forthcoming book on state-supported private enforcement, Vigilante Nation, says it’s difficult to imagine that companies could bring the volume of cases needed to significantly stop abuse. “The fact that there is a small chance you might be named in a suit isn’t really going to deter you,” he says.
Noll believes the big risk is that Google and other tech companies could be burdening the court system with cases that ultimately secure some favorable headlines but do less to make the internet safer than the companies could achieve through investing in better antifraud measures.
Still, of the six outside legal experts who spoke to WIRED, all of them say that overall Google deserves credit for complementing the work of underfunded government agencies that are struggling to rein in online abuse. At an estimated hundreds of thousands of dollars per case, it’s a low-risk endeavor for the tech giant, former prosecutors say.
“Reliable and regular enforcement when folks step outside the law brings us closer to a society where less of us are harmed,” says Kathleen Morris, resident scholar of law at UC Berkeley’s Institute of Governmental Studies. “This is healthy and robust collaboration on law enforcement by the public and private sectors.”
Google’s general counsel, Halimah DeLaine Prado, tells WIRED she wants to send a message to other companies that the corporate legal department can do more than be the team that says “no” to wild ideas. “Legal can be a proactive protector,” she says.
Marketing Scams
DeLaine Prado says that from its earliest days, Google has considered pursuing litigation against people abusing its platforms and intellectual property. But the first case she and other leaders within Google recall filing was in 2015. Google accused Local Lighthouse, a California marketing company, of placing robocalls to dupe small businesses into paying to improve their ranking in search results. Google alleged trademark infringement, unfair competition, and false advertising. As part of a settlement, Lighthouse stopped the problematic calls.
Since then, Google has filed complaints against five similar allegedly scammy marketers, with three of them ending in settlements so far. A Florida business and its owners agreed to pay Google $850,000, and a Los Angeles man who allegedly posted 14,000 fake reviews on Google Maps agreed to stop. Terms of the third deal, with an Illinois company, were not disclosed in court files, but Google spokesperson José Castañeda says it involved a seven-figure payment to Google.
Castañeda says Google has donated all the money it has collected to recipients such as the Better Business Bureau Institute, the National Consumers League, Partnership to End Addiction, Cybercrime Support Network, and various US chambers of commerce.
Another genre of cases has targeted individuals submitting false copyright complaints to Google to get content removed from the company’s services. A man in Omaha, Nebraska, whom Google accused of falsely claiming ownership of YouTube videos to extort money from their real owners, agreed to pay $25,000 to Google. Two individuals in Vietnam sued by Google never responded—a common issue.
In 2022, Google won default judgment against an individual in Cameroon who never responded to charges that he was using Gmail to scam people into paying for fake puppies, including a $700 basset hound. After the lawsuit, complaints about the scammer dried up, according to Google.
But legal experts say the most fascinating cases of Google’s affirmative litigation are four that it filed against alleged computer hackers. The suits emerged after months of investigation into Glupteba.
Security engineers at Google realized that eradicating Glupteba through the typical approach of taking down associated servers would be difficult. The hackers behind it had designed a backup system involving a blockchain that enabled Glupteba to resurrect itself and keep pilfering away.
That’s in part why Google’s attorneys suggested suing. Chun, the security legal director, had pursued cases against botnets as a federal prosecutor. “I thought this would be something good to do from a civil angle for a company as well,” he says. “Law enforcement agencies have limits on what they can do. And Google has a large voice and the litigation capacity.”
Chun and other attorneys cautioned their bosses that the hackers might use the lawsuit to reverse engineer Google’s investigation methods and make Glupteba more evasive and resilient. But ultimately, DeLaine Prado, who has final say over lawsuits, signed off. Chun says his former colleagues from the government applauded the complaint.
Google sued Dmitry Starovikov and Alexander Filippov, alleging that they were the Russia-based masterminds behind Glupteba after linking websites associated with the virus to Google accounts in their name. The search giant accused the duo (and unknown co-conspirators) of violating the Racketeer Influenced and Corrupt Organizations Act (RICO), the Computer Fraud and Abuse Act, and the Electronic Communications Privacy Act. The lawsuit also alleged a trademark law violation for hiding Glupteba in a tool that claimed to download videos from YouTube.
Google argued that it had suffered substantial harm, having never received payment for ads it had sold to the hackers, who allegedly were using fraudulent credit cards. Users also had their experiences with Google services degraded, putting them at risk and impairing the value of the company’s brand, according to the lawsuit.
In court papers, Starovikov and Filippov stated they learned of the lawsuit only through friends and then decided to hire a New York attorney, Igor Litvak, to fight on their behalf. The defendants initially offered innocent explanations for their software related to Glupteba and said that their projects had not targeted the US market. At one point, they countersued Google for $10 million, and at another, they allegedly demanded $1 million each to hand over the keys to shut down the botnet. They eventually denied the allegations against them.
Following an ordeal over whether the defendants could obtain Russian passports, sit for depositions in Europe, and turn over work files, Google’s attorneys and Litvak traded accusations of lying. In 2022, US district judge Denise Cote sided with Google. She found in a 48-page ruling that the defendants “intentionally withheld information” and “misrepresented their willingness and ability” to disclose it to “avoid liability and further profit” from Glupteba. “The record here is sufficient to find a willful attempt to defraud the Court,” Cote wrote.
Cote sanctioned Litvak, and he agreed to pay Google $250,000 in total through 2027 to settle. The jurist also ordered Starovikov and Filippov to pay nearly $526,000 combined to cover Google’s attorneys fees. Castañeda says Google has received payment from all three.
Litvak tells WIRED that he still disagrees with the judge's findings and that Russia’s strained relationship with the US may have weighed on whom the judge trusted. “It’s telling that after I filed a motion to reconsider, pointing out serious issues with the court’s decision, the court went back on its original decision and referred [the] case to mediation, which ended with … me not having to admit to doing anything wrong,” he says in an email.
Google’s Castañeda says the case achieved the intended effect: The Russian hackers stopped misusing Google services and shut down their marketplace for stolen logins, while the number of Glupteba-infected computers fell 78 percent.
Not every case delivers measurable results. Defendants in Google’s other three hacking cases haven’t responded to the accusations. That led to Google last year winning default judgment against three individuals in Pakistan accused of infecting more than 672,000 computers by masquerading malware as downloads of Google’s Chrome browser. Unopposed victories are also expected in the remaining cases, including one in which overseas app developers allegedly stole money through bogus investment apps and are being sued for violating YouTube Community Guidelines.
Royal Hansen, Google’s vice president for privacy, safety, and security engineering, says lawsuits that don’t result in defendants paying up or agreeing to stop the alleged misuse still can make alleged perpetrators’ lives more difficult. Google uses the rulings as evidence to persuade businesses such as banks and cloud providers to cut off the defendants. Other hackers might not want to work with them knowing they have been outed. Defendants also could be more cautious about crossing international borders and becoming newly subject to scrutiny from local authorities. “That’s a win as well,” Hansen says.
More to Come
These days, Google’s small litigation advance team meets about twice a week with other units across the company to discuss potential lawsuits. They weigh whether a case could set a helpful precedent to give extra teeth to Google’s policies or draw awareness to an emerging threat.
Team leader Day says that as Google has honed its process, filing cases has become more affordable. That should lead to more lawsuits each year, including some for the first time potentially filed outside the US or representing specific users who have been harmed, he says.
The tech giants' ever-sprawling empires leave no shortage of novel cases to pursue. Google’s sibling company Waymo recently adopted the affirmative litigation approach and sued two people who allegedly smashed and slashed its self-driving taxis. Microsoft, meanwhile, is weighing cases against people using generative AI technology for malicious or fraudulent purposes, says Steven Masada, assistant general counsel of the company’s Digital Crimes Unit.
The questions remain whether the increasing cadence of litigation has left cybercriminals any bit deterred and whether a broader range of internet companies will go on the legal offense.
Erin Bernstein, who runs the California office of Bradley Bernstein Sands, a law firm that helps governments pursue civil lawsuits, says she recently pitched a handful of companies across industries on doing their own affirmative litigation. Though none have accepted her offer, she’s optimistic. “It will be a growing area,” Bernstein says.
But Google’s DeLaine Prado hopes affirmative litigation eventually slows. “In a perfect world, this work would disappear over time if it’s successful,” she says. “I actually want to make sure that our success kind of makes us almost obsolete, at least as it relates to this type of work.”
10 notes
·
View notes
Text
"[...]The argument for the exemption received considerable pushback from agencies including the Entertainment Software Association, which argued that proposed controls over who would be allowed to access exempted software, and for what reason, were unclear. A "human review" requirement was "at best incomplete," the ESA said, and that by not including more specific requirements in the proposal, supporters of the exemption were "trying to reserve almost complete discretion in how they would provide access to preserve[d] games." The ESA also claimed that "there remains a substantial market for classic games," and that allowing "widespread remote access to preserved games with minimal supervision would present a serious risk to an important market." In the end, Shira Perlmutter, register of copyrights and director of the US Copyright Office, was not swayed by the arguments in favor of game preservation, ruling that proponents of videogame preservation "have not satisfied their burden to demonstrate that the requested uses are or are likely to be noninfringing.""
Like, I hate to break it to game preservationists, but they're gonna have to "become ungovernable" and push the issue until the Copyright Office doesn't have a public or a corporate leg to stand on.
That's the only way history gets preserved in the face of entities who are still trying their damnedest to criminalize reselling and sharing games secondhand the same way they succeeded with file sharing back in the 2010s.
These people don't care about preservation, they just wanna consume nickels and dimes.
#videogamesincolor#video game history#game preservation#copyright#copyright office#capitalism#media manipulation#pc gamer
3 notes
·
View notes
Text
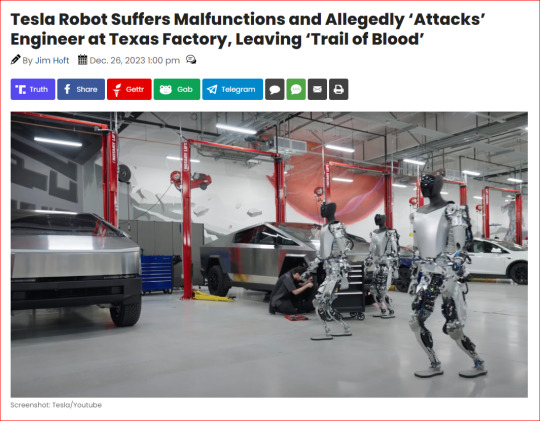
A robotic malfunction at Tesla’s Giga Texas factory resulted in a violent encounter where an engineer was attacked by one of the company’s robots, resulting in significant injuries and leaving a ‘trail of blood.’
According to the Daily Mail, while working on software programming for non-functional Tesla robots, the engineer was suddenly pinned against a surface by a robot tasked with manipulating aluminum car components, with its metal claws inflicted an injury that left an ‘open wound’ on the worker’s left hand.
“Two of the robots, which cut car parts from freshly cast pieces of aluminum, were disabled so the engineer and his teammates could safely work on the machines. A third one, which grabbed and moved the car parts, was inadvertently left operational, according to two people who watched it happen. As that robot ran through its normal motions, it pinned the engineer against a surface, pushing its claws into his body and drawing blood from his back and his arm, the two people said,” The Information reported.
Quick action was taken by Tesla workers who intervened and triggered the emergency shutdown button to halt the malfunctioning robot and prevent further injury to the engineer.
This incident came to light through a 2021 injury report filed to Travis County and federal regulators, which Daily Mail reviewed. Tesla is legally required to report such incidents to ensure the continuation of state-provided tax incentives.
Despite claims by Tesla that the engineer did not require time off following the event, an attorney representing the factory’s contract laborers suggests otherwise. Evidence hints at possible underreporting of workplace accidents, casting doubt on the official records.

Daily Mail reported:
The injury report, which Tesla must submit to authorities by law to maintain its lucrative tax breaks in Texas, claimed the engineer did not require time off of work. But one attorney who represents Tesla’s Giga Texas contract workers has told DailyMail.com she believes, based on her conversations with workers there, that the amount of injuries suffered at the factory is going underreported. This underreporting, the attorney said, even included the September 28, 2021 death of a construction worker, who had been contracted to help build the factory itself. ‘My advice would be to read that report with a grain of salt,’ the attorney, Hannah Alexander of the nonprofit Workers Defense Project, told DailyMail.com. ‘We’ve had multiple workers who were injured,’ Alexander said, ‘and one worker who died, whose injuries or death are not in these reports that Tesla is supposed to be accurately completing and submitting to the county in order to get tax incentives.’
Elon Musk has yet to issue a formal statement in response to these allegations.
Just recently, Tesla revealed the second generation of its humanoid robot, Optimus Gen 2.
Optimus Gen 2 stands at a height of 5 feet 11 inches and weighs in at a light 121 pounds, shedding 22 pounds from the first model. It’s not just its frame that’s been upgraded; this robot can reach speeds up to 5 mph, which is a substantial 30% increase in velocity.
youtube

7 notes
·
View notes
Text
Hassle-Free GST Return Filing Services in Delhi by SC Bhagat & Co.
Introduction: Navigating the complexities of Goods and Services Tax (GST) return filing can be daunting for businesses. To ensure compliance and avoid penalties, it's crucial to have a reliable partner who can manage your GST returns efficiently. SC Bhagat & Co. offers top-notch GST return filing services in Delhi, helping businesses streamline their tax processes and stay compliant with the latest regulations. In this blog, we'll explore the importance of GST return filing, the services provided by SC Bhagat & Co., and why they are the best choice for your business in Delhi. Why GST Return Filing is Important GST return filing is a mandatory requirement for businesses registered under the GST regime in India. Regular and accurate filing of GST returns is essential for several reasons: Compliance: Ensures adherence to tax laws and regulations, avoiding legal issues and penalties. Input Tax Credit (ITC): Facilitates the claim of ITC, which helps reduce the overall tax liability. Business Credibility: Enhances the credibility and trustworthiness of your business among clients and stakeholders. Avoid Penalties: Prevents hefty fines and interest charges that result from late or incorrect filing. Comprehensive GST Return Filing Services by SC Bhagat & Co. SC Bhagat & Co. provides a full range of GST return filing services in Delhi, tailored to meet the unique needs of your business. Here’s what you can expect: 1. Accurate GST Return Preparation Our experienced professionals ensure that your GST returns are prepared accurately, reflecting all transactions and complying with the latest GST laws. We handle all types of GST returns, including GSTR-1, GSTR-3B, GSTR-9, and more. 2. Timely Filing Timely filing is crucial to avoid penalties and interest charges. SC Bhagat & Co. guarantees prompt filing of your GST returns, keeping track of all deadlines and ensuring that you never miss a due date. 3. Error-Free Data Management We meticulously review all your financial data to ensure that your GST returns are error-free. Our team double-checks every detail, reducing the risk of discrepancies and ensuring smooth processing. 4. ITC Reconciliation Our experts assist in reconciling your Input Tax Credit (ITC) to ensure you claim the correct amount, maximizing your tax benefits and minimizing liabilities. 5. Regular Updates and Compliance GST laws and regulations are subject to frequent changes. SC Bhagat & Co. stays updated with the latest amendments and ensures that your GST returns comply with the current rules and guidelines. 6. Personalized Support We provide personalized support to address any queries or issues you may have regarding GST return filing. Our team is always available to assist you with expert advice and solutions. Why Choose SC Bhagat & Co. for GST Return Filing Services in Delhi Expertise and Experience With years of experience in tax consulting, SC Bhagat & Co. has a deep understanding of GST regulations and filing procedures. Our expertise ensures that your GST returns are handled professionally and accurately. Client-Centric Approach We prioritize our clients' needs and provide tailored solutions to meet their specific requirements. Our client-centric approach ensures that you receive the best possible service and support. Advanced Technology SC Bhagat & Co. leverages advanced technology and software to streamline the GST return filing process. Our tech-driven approach enhances efficiency and accuracy, saving you time and effort. Proven Track Record Our proven track record of successful GST return filings speaks for itself.
2 notes
·
View notes
Text

How to Make Sure You're Withholding and Reporting Your Taxes Correctly
Taxes are an inevitable part of life for most individuals and businesses. Whether you're a salaried employee, a freelancer, or a business owner, understanding how to withhold and report your taxes correctly is crucial to avoid potential legal troubles and financial headaches down the road. In this article, we will explore the key steps and considerations to ensure that you're handling your taxes in a responsible and compliant manner.
Know Your Tax Obligations
The first and most critical step in ensuring you're withholding and Outsource Management Reporting your taxes correctly is to understand your tax obligations. These obligations vary depending on your employment status and the type of income you earn. Here are some common categories of taxpayers:
1. Salaried Employees
If you're a salaried employee, your employer typically withholds income taxes from your paycheck based on your Form W-4, which you fill out when you start your job. It's essential to review and update your W-4 regularly to ensure that your withholding accurately reflects your current financial situation. Major life events like marriage, having children, or significant changes in your income should prompt you to revisit your W-4.
2. Freelancers and Self-Employed Individuals
Freelancers and self-employed individuals often have more complex tax obligations. You are responsible for estimating and paying your taxes quarterly using Form 1040-ES. Keep detailed records of your income and expenses, including receipts and invoices, to accurately report your earnings and deductions.
3. Small Business Owners
If you own a small business, your sales tax responsibilities extend beyond your personal income. You must separate your business and personal finances, keep meticulous records of all business transactions, and file the appropriate business tax returns. The structure of your business entity (e.g., sole proprietorship, partnership, corporation) will determine the specific tax forms you need to file.
4. Investors and Property Owners
Investors and property owners may have to report income from dividends, interest, capital gains, or rental properties. These income sources have their specific tax reporting requirements, and it's essential to understand and comply with them.
Keep Accurate Records
Regardless of your tax situation, maintaining accurate financial records is essential. Detailed records make it easier to report your income and deductions correctly, substantiate any claims you make on your tax return, and provide documentation in case of an audit. Here are some record-keeping tips:
Organize Your Documents: Create a system to store your financial documents, including receipts, invoices, bank statements, and tax forms. Consider using digital tools for easier record keeping.
Track Income and Expenses: Keep a ledger or use accounting software to record all income and expenses related to your financial activities. Categorize expenses correctly to maximize deductions and credits.
Retain Documents for Several Years: The IRS typically has a statute of limitations for auditing tax returns, which is generally three years. However, in some cases, it can extend to six years or indefinitely if fraud is suspected. To be safe, keep your tax records for at least seven years.
Understand Deductions and Credits
Deductions and credits can significantly reduce your tax liability. Deductions reduce your taxable income, while credits provide a dollar-for-dollar reduction of your tax bill. Familiarize yourself with common deductions and credits that may apply to your situation:
Standard Deduction vs. Itemized Deductions: Depending on your filing status and financial situation, you can choose between taking the standard deduction or itemizing your deductions. Itemizing requires more documentation but can result in greater tax savings.
Tax Credits: Explore available tax credits, such as the Earned Income Tax Credit (EITC), Child Tax Credit, and Education Credits. These credits can provide substantial savings, especially for low- to moderate-income individuals and families.
Business Expenses: If you're self-employed or a small business owner, be aware of deductible business expenses, including office supplies, travel expenses, and home office deductions.
Seek Professional Assistance
Tax laws are complex and subject to change. Seeking professional assistance from a certified tax professional or CPA (Certified Public Accountant) can be a wise investment. Tax professionals can help you:
Maximize Deductions: They are well-versed in the intricacies of tax law and can identify deductions and credits you might overlook.
Ensure Compliance: Tax professionals can ensure that you are complying with current tax laws and regulations, reducing the risk of costly errors or audits.
Provide Tax Planning: They can help you create a tax-efficient strategy to minimize your tax liability in the long term.
Represent You in Audits: If you face an audit, a tax professional can represent you and help navigate the process.
File Your Taxes on Time
Filing your taxes on time is crucial to avoid penalties and interest charges. The tax filing deadline for most individuals is April 15th. However, if you need more time, you can file for an extension, which typically gives you until October 15th to submit your return. Keep in mind that an extension to file is not an extension to pay any taxes owed, so pay as much as you can by the original deadline to minimize interest and penalties.
Consider Electronic Filing
Electronic filing (e-filing) is a secure and convenient way to submit your tax return to the IRS. It reduces the risk of errors and ensures faster processing and quicker refunds, if applicable. Many tax software programs offer e-filing options, making it easy for individuals and businesses to submit their returns electronically.
Stay Informed and Adapt
Tax laws can change from year to year, so staying informed is essential. Follow updates from the IRS and consult outsourcing sales tax services professionals or resources to understand how changes in tax laws may affect you. Be proactive in adapting your tax strategies to maximize savings and remain compliant with current regulations.
In conclusion, withholding and reporting your taxes correctly is a responsibility that should not be taken lightly. Understanding your tax obligations, keeping accurate records, leveraging deductions and credits, seeking professional assistance when needed, and filing on time are essential steps to ensure a smooth and compliant tax-filing experience. By following these guidelines, you can navigate the complexities of the outsourcing sales tax services system with confidence and peace of mind. Remember that taxes are a fundamental part of our society, and paying them correctly ensures that essential public services and infrastructure are funded for the benefit of all.
2 notes
·
View notes
Text
Make your photographs work for you and earn money.

Selling your photos on stock websites can be a great way to earn additional income. Selling stock photography through mobile devices and DSLRs has become increasingly popular and accessible with the advancement of digital technology. Here are some steps you can take to get started:
Research Stock Websites: There are numerous stock websites where you can sell your photos, such as Shutterstock, Adobe Stock, Freepik, Getty Images and iStock. Look into their submission guidelines, royalty rates, and popularity among buyers.
Assess Market Demand: Before you start shooting and uploading photos, it's important to understand what types of images are in demand. Take a look at the popular categories on stock websites and analyze the types of images that sell well. This will help you focus your efforts and maximize your chances of making sales.
Capture Marketable Photos: Aim to capture high-quality, visually appealing images that have commercial value. Consider popular themes like travel, nature, lifestyle, business, and technology. Ensure your photos are well-lit, properly composed, and have good resolution.
Edit and Enhance: Post-processing your photos can significantly improve their appeal. Use photo editing software like Adobe Lightroom or Photoshop to enhance colors, adjust exposure, and remove any imperfections. However, be careful not to over-edit and maintain a natural look.
Keywording and Descriptions: When uploading your photos, provide accurate and descriptive titles, captions, and keywords. This will help potential buyers find your images when they search for specific topics. Be thorough but relevant in your keyword selection.
Follow Submission Guidelines: Each stock website has its own set of submission guidelines, so make sure to review them carefully. Pay attention to the technical specifications, image size requirements, and file formats they accept. Failure to comply with these guidelines may result in your photos being rejected.
Model and Property Releases: If your photos contain recognizable individuals or private property, you may need model or property releases. These releases grant you legal permission to sell the images commercially. Familiarize yourself with the rules and requirements surrounding model and property releases on the stock websites you choose.
Regularly Upload New Content: Consistency is key to success in stock photography. Regularly upload new photos to keep your portfolio fresh and increase your visibility in search results. By building a diverse and substantial collection of images, you can attract a wider range of buyers.
Track Sales and Optimize: Monitor your sales and analyze the performance of your images. Pay attention to which photos are selling well and which ones are not. This data will help you refine your future photography efforts and focus on the subjects and styles that resonate with buyers.
Be Patient and Persistent: Selling photos on stock websites can take time and perseverance. It may take a while before you start seeing significant income. Stay motivated, continue to improve your skills, and adapt to the changing demands of the market.
Remember, while selling photos on stock websites can be a lucrative venture, it's also a competitive industry. Success often comes with time, effort, and a strong understanding of what buyers are looking for.
#photographers on tumblr#photography#photos#i sell pictures#i sell custom pics#stock images#100 days of productivity#stock photos#bird photos#bird photography#birdlovers#birds nature#birds of prey
2 notes
·
View notes
Photo
Also, "Archive of Our Own" is not a stand-alone website. It's a project ran by the Organization for Transformative Works. They are a 501(c)(3) Non-Profit with publically viewable reports of their budget, activities, and meetings.
It took me all of a minute to find their 2023 Annual Report (that every 501(c)(3) Non-profit has to do by law), and in that year, they had $1.16 million in revenue with $822 thousand in expenses. They have about $3.1 million sitting in the bank as operating cash and reserves and a million dollars worth of server equipment (depreciated to $225k).
They break down exactly what their money is used for, line by line, with standard accounting practices. (AO3 cost about $364k to run in 2023, with about a third of that in hosting costs and equipment.) This is not some friends running it out of their garage, it is organized, documented, and above the board. Staff is not getting paid for this, it's volunteer run. In 2023, they paid $21k to auditors, $16k to their finance/accountants, $12k to accountants, and $60k for 'other professional services' which typically ranges from office cleaning, one-off repair expenses, training and certification, or even catering and event services. They spent more on fees and the software expenses than they did people (~$183k vs ~$109k)
As for the other projects that the OTW works on? The major ones? --Fanlore, A wiki for maintaining and preserving the history of fandom and transformative works. --Legal Advocacy, which includes standing up to those DMCA requests, but also testifying before legislatures, filing briefs in other cases, submitting public commentary, and advising others to protect fanworks. --Open Doors, which works to provide archive and shelter to at-risk or closing projects. Fans who have archives (some decades old) who can no longer host them, can get them not only backed up, but integrated with AO3 for continued viewing. They also work to preserve printed and non-digital fanworks, as well as the GeoCities Rescue Project. --Transformative Works and Cultures, which is a peer-reviewed academic journal that is for the study of fanworks, fandom, the communities, and other aspects of the culture.
*cackling*
If OTW weren’t around, this wouldn’t be “scaremongering”: It would be the inescapable status quo.
51K notes
·
View notes
Text
The Importance of Construction Document Management and Control Software
In the fast-paced construction industry, efficient handling of project documentation is critical to ensuring timely completion, compliance, and cost control. Construction document management software and construction document control software are essential tools that help firms streamline workflows, reduce errors, and enhance collaboration. These solutions play a vital role in modern construction projects by digitizing and organizing critical documents, from blueprints and contracts to safety reports and compliance records.
Why Construction Document Management Software is Essential
Construction projects generate vast amounts of data, including design drawings, permits, inspection reports, and change orders. Without a centralized system, managing these documents manually leads to inefficiencies, misplaced files, and costly delays.
Key benefits of construction document management software include:
Centralized Storage: All project documents are stored in a single, cloud-based or on-premise system, ensuring easy access for all stakeholders.
Version Control: Prevents confusion by tracking revisions and ensuring teams work with the latest documents.
Improved Collaboration: Allows architects, contractors, and clients to share and review documents in real time.
Regulatory Compliance: Helps maintain audit trails for safety and legal requirements, reducing the risk of non-compliance penalties.
According to a report by McKinsey, construction projects that leverage digital tools, including document management systems, experience up to 45% improvement in productivity.
The Role of Construction Document Control Software
While document management focuses on storage and retrieval, construction document control software emphasizes tracking and approval workflows. This ensures that only authorized personnel can modify critical documents, reducing errors and unauthorized changes.
Key features include:
Automated Approval Workflows: Streamlines the review and sign-off process for contracts, permits, and design changes.
Audit Trails: Logs every action taken on a document, providing transparency and accountability.
Integration with Other Systems: Connects with project management, BIM (Building Information Modeling), and accounting software for seamless operations.
A study by Dodge Data & Analytics found that 61% of contractors using document control software reported fewer project delays due to miscommunication or lost paperwork.
Enhancing Safety Management with Document Control
Safety is a top priority in construction, and proper documentation is crucial for compliance. Integrating construction document control software with safety management systems (like those offered by NGT Solutions) ensures that safety inspections, incident reports, and training records are systematically tracked.
For example, NGT’s Safety Management Software (https://www.ngt.com.sg/safety-management-software/) helps companies automate safety documentation, reducing manual errors and improving regulatory adherence. When combined with construction document management software, firms can maintain a comprehensive safety record, ensuring compliance with OSHA and other regulatory bodies.
Industry Trends and Future Outlook
The global construction management software market is projected to grow at a CAGR of 9.2% from 2023 to 2030 (Grand View Research), driven by increasing digitization in the sector. Companies adopting these tools experience:
20-30% reduction in administrative costs (Autodesk)
Faster project turnaround times due to streamlined approvals
Better risk management with real-time document tracking
Conclusion
Construction document management software and construction document control software are no longer optional—they are necessities for firms aiming to stay competitive. By improving efficiency, reducing errors, and ensuring compliance, these tools help construction companies deliver projects on time and within budget.
For businesses looking to enhance safety documentation, integrating these systems with specialized safety management software (like NGT’s solution) further strengthens operational reliability and regulatory compliance. Investing in the right digital tools today can lead to long-term success in an increasingly complex industry.
0 notes
Text
The 5 Core Functions of Accounting Every Business Should Know
Accounting is the backbone of any successful business, providing the financial clarity needed to make informed decisions, ensure compliance, and drive growth. Understanding the core functions of accounting empowers businesses to manage resources effectively and maintain fiscal health.

1. Bookkeeping: The Foundation of Financial Records
Bookkeeping is the process of recording all financial transactions, including sales, purchases, payments, and receipts. Accurate bookkeeping ensures that a business’s financial data is organized and up-to-date, forming the basis for all other accounting functions. It involves maintaining ledgers, categorizing transactions, and reconciling bank statements to prevent discrepancies.
For small businesses, bookkeeping can be managed using software like QuickBooks or Xero, which automate data entry and reduce errors. A 2024 study by the American Institute of CPAs found that 70% of businesses using automated bookkeeping saved at least 10 hours monthly. Consistent bookkeeping provides a clear picture of cash flow, enabling better budgeting and forecasting.
2. Financial Reporting: Insights for Decision-Making
Financial reporting involves preparing statements that summarize a business’s financial performance and position. Key reports include the income statement, balance sheet, and cash flow statement. These documents provide insights into revenue, expenses, assets, liabilities, and liquidity, guiding strategic decisions.
Timely and accurate financial reporting is critical for stakeholders, including owners, investors, and creditors. For example, a balance sheet reveals a company’s financial stability, while a cash flow statement highlights liquidity challenges. According to a 2023 Deloitte survey, 65% of businesses with robust financial reporting improved profitability by identifying cost-saving opportunities. Public companies must also comply with standards like GAAP or IFRS for transparency.
3. Tax Compliance: Navigating Legal Obligations
Tax compliance ensures businesses meet federal, state, and local tax requirements. This function includes calculating, filing, and paying taxes such as income tax, sales tax, and payroll tax. Proper tax management prevents penalties and maximizes deductions, reducing the overall tax burden.
Accountants stay updated on tax laws to ensure compliance and advise on tax-saving strategies, such as depreciation or credits for small businesses. A 2024 IRS report noted that 80% of businesses with professional tax support avoided audit-related fines. Outsourcing tax compliance to experts or using software like TurboTax can streamline this complex function.
4. Budgeting and Forecasting: Planning for the Future
Budgeting involves creating a financial plan to allocate resources effectively, while forecasting predicts future revenue, expenses, and market trends. Together, these functions help businesses set realistic goals, manage cash flow, and prepare for uncertainties. For instance, a budget ensures spending aligns with priorities, while a forecast might predict seasonal sales fluctuations.
Effective budgeting and forecasting rely on historical data from bookkeeping and financial reports. A 2023 Gartner study found that businesses with data-driven budgeting were 25% more likely to achieve revenue targets. Tools like Microsoft Excel or advanced platforms like Adaptive Insights simplify these processes, enabling proactive financial management.
5. Auditing and Internal Controls: Ensuring Accuracy and Trust
Auditing involves reviewing financial records to verify accuracy and compliance with regulations. Internal audits identify discrepancies or fraud, while external audits provide credibility for stakeholders. Internal controls, such as segregation of duties or approval workflows, safeguard assets and prevent errors.
Strong auditing and controls build trust with investors and regulators. A 2024 PwC report revealed that 60% of businesses with robust internal controls reduced financial losses from fraud by 30%. Regular audits also uncover inefficiencies, such as redundant expenses, improving overall cost management.
Why These Functions Matter
Mastering these five core accounting functions—bookkeeping, financial reporting, tax compliance, budgeting and forecasting, and auditing—ensures businesses operate efficiently and remain competitive. They provide the data needed to make strategic decisions, comply with laws, and build stakeholder confidence. Small businesses can start with basic tools and scale to professional services as they grow.
youtube
Conclusion
Accounting is more than number-crunching; it’s a strategic asset for business success. By prioritizing these five core functions, businesses gain financial clarity, minimize risks, and unlock growth opportunities. Whether using software or hiring experts, investing in accounting processes delivers long-term value. Start optimizing these functions today to secure your business’s financial future.
SITES WE SUPPORT
Smart Hire Workflow
SOCIAL LINKS Facebook Twitter LinkedI
0 notes
Text
How to Structure Your Company’s Finances for Better Tax Efficiency?

Effective tax efficiency is not achieved by chance—it requires a deliberate approach to structuring your company’s finances. The way your business organizes income, expenses, investments, and operations can significantly influence the amount of tax you pay. With careful planning and the help of experts offering tax planning services in Fort Worth, TX, businesses can reduce their tax burden while staying fully compliant with regulations.
Choosing the Right Business Structure
The foundation of tax-efficient financial planning starts with selecting the appropriate legal structure for your company. Sole proprietorships, partnerships, corporations, and LLCs each have distinct tax implications. For instance, a C corporation may be taxed separately from its owners but this allows for the retention of earnings within the company. In contrast, an S corporation or LLC might pass income through to the owners, who are then taxed at individual rates.
Choosing the wrong structure could lead to higher taxes or limit your ability to claim certain deductions. Regular reviews of your structure as your business grows or diversifies are essential to ensure you’re still in the most tax-efficient setup.
Segregating Business and Personal Finances
A common mistake among small business owners is blending business and personal finances. This not only creates confusion but can also lead to missed deductions and complications during audits. Opening separate business bank accounts, using business credit cards, and maintaining clear records are key steps toward better financial organization and tax efficiency.
Proper segregation also helps accurately track deductible business expenses such as office supplies, travel, software subscriptions, and utilities. When these are well documented, they reduce your taxable income and ultimately your tax bill.
Optimizing Timing of Income and Expenses
Another effective strategy involves the timing of income recognition and expense payments. Businesses operating on a cash basis can strategically delay invoicing clients near year-end or accelerate necessary purchases to reduce taxable income. Similarly, prepaying certain expenses or making charitable donations before the tax year closes can enhance deductions.
These decisions should be made carefully, taking into account your cash flow and overall profitability goals. Consulting with tax professionals helps ensure these moves are beneficial rather than burdensome.
Leveraging Depreciation and Capital Investments
Businesses that invest in equipment, vehicles, or property can benefit from tax rules that allow for depreciation. By spreading the cost of an asset over several years, or using options like Section 179 to deduct large portions upfront, you can significantly reduce your taxable income.
These strategies not only provide tax relief but also encourage reinvestment in the business. Planning these purchases around key tax dates can further maximize the benefits.
Maintaining Accurate Financial Records
Strong financial records are the backbone of any tax-efficient structure. Using accounting software, keeping receipts, and conducting regular reconciliations ensure that your tax filings are accurate and timely. Good records also support claims for deductions, minimize audit risk, and make it easier to identify future tax-saving opportunities.
Conclusion
Structuring your company’s finances with tax efficiency in mind is a smart, strategic move that can lead to lasting benefits. With the guidance of experts offering tax planning services, businesses can build a financial foundation that supports growth while minimizing tax obligations.
0 notes
Text
CW: Suicide I need to add: 1. While in college, I spent a summer (1978) copyediting for Physical Review, a physics journal (or group of them -- there were Phys. Rev. A, B, C, and Phys. Rev. Lett). One of the things I saw was how publication of papers was systematically delayed if "pub fees" (publication fees) were not paid. Staff would literally put the folder with the marked-up MS into a drawer in a filing cabinet, the drawer designated for items delayed by nonpayment of pub fees. Once the payment was received, they'd go into another drawer for papers slated for publication.
2. Several years of my high-tech career were spent programming for Lexis-Nexis, a company specializing in services for the legal profession, including access to their galactically massive database of caselaw needed for legal citation. In my earliest days there, Lexis-Nexis was bought by what was then called Reed-Elsevier (now RELX), the publication giant whose subsidiary Elsevier is a major villain mentioned in Doctorow's post. I will not go into depth about the gross mismanagement of the layoff they perpetrated on our division of Lexis-Nexis, which had originally been an independent software company. I vaguely recall already telling that story here, probably in response to another Corey Doctorow article, that one likely about enshittification in the software sector. RELX still owns Lexis-Nexis (now LexisNexis).
3. RELX (formerly Reed-Elsevier) owns RX, formerly Reed Exhibitions, the world's largest exhibition company. One of its divisions is ReedPop, which runs New York Comic Con and the PAX gamer conventions.
MIT libraries are thriving without Elsevier

I'm coming to BURNING MAN! On TUESDAY (Aug 27) at 1PM, I'm giving a talk called "DISENSHITTIFY OR DIE!" at PALENQUE NORTE (7&E). On WEDNESDAY (Aug 28) at NOON, I'm doing a "Talking Caterpillar" Q&A at LIMINAL LABS (830&C).

Once you learn about the "collective action problem," you start seeing it everywhere. Democrats – including elected officials – all wanted Biden to step down, but none of them wanted to be the first one to take a firm stand, so for months, his campaign limped on: a collective action problem.
Patent trolls use bullshit patents to shake down small businesses, demanding "license fees" that are high, but much lower than the cost of challenging the patent and getting it revoked. Collectively, it would be much cheaper for all the victims to band together and hire a fancy law firm to invalidate the patent, but individually, it makes sense for them all to pay. A collective action problem:
https://locusmag.com/2013/11/cory-doctorow-collective-action/
Musicians get royally screwed by Spotify. Collectively, it would make sense for all of them to boycott the platform, which would bring it to its knees and either make it pay more or put it out of business. Individually, any musician who pulls out of Spotify disappears from the horizon of most music fans, so they all hang in – a collective action problem:
https://pluralistic.net/2024/06/21/off-the-menu/#universally-loathed
Same goes for the businesses that get fucked out of 30% of their app revenues by Apple and Google's mobile business. Without all those apps, Apple and Google wouldn't have a business, but any single app that pulls out commits commercial suicide, so they all hang in there, paying a 30% vig:
https://pluralistic.net/2024/08/15/private-law/#thirty-percent-vig
That's also the case with Amazon sellers, who get rooked for 45-51 cents out of every dollar in platform junk fees, and whose prize for succeeding despite this is to have their product cloned by Amazon, which underprices them because it doesn't have to pay a 51% rake on every sale. Without third-party sellers there'd be no Amazon, but it's impossible to get millions of sellers to all pull out at once, so the Bezos crime family scoops up half of the ecommerce economy in bullshit fees:
https://pluralistic.net/2023/11/06/attention-rents/#consumer-welfare-queens
This is why one definition of "corruption" is a system with "concentrated gains and diffuse losses." The company that dumps toxic waste in your water supply reaps all the profits of externalizing its waste disposal costs. The people it poisons each bear a fraction of the cost of being poisoned. The environmental criminal has a fat warchest of ill-gotten gains to use to bribe officials and pay fancy lawyers to defend it in court. Its victims are each struggling with the health effects of the crimes, and even without that, they can't possibly match the polluter's resources. Eventually, the polluter spends enough money to convince the Supreme Court to overturn "Chevron deference" and makes it effectively impossible to win the right to clean water and air (or a planet that's not on fire):
https://www.cfr.org/expert-brief/us-supreme-courts-chevron-deference-ruling-will-disrupt-climate-policy
Any time you encounter a shitty, outrageous racket that's stable over long timescales, chances are you're looking at a collective action problem. Certainly, that's the underlying pathology that preserves the scholarly publishing scam, which is one of the most grotesque, wasteful, disgusting frauds in our modern world (and that's saying something, because the field is crowded with many contenders).
Here's how the scholarly publishing scam works: academics do original scholarly research, funded by a mix of private grants, public funding, funding from their universities and other institutions, and private funds. These academics write up their funding and send it to a scholarly journal, usually one that's owned by a small number of firms that formed a scholarly publishing cartel by buying all the smaller publishers in a string of anticompetitive acquisitions. Then, other scholars review the submission, for free. More unpaid scholars do the work of editing the paper. The paper's author is sent a non-negotiable contract that requires them to permanently assign their copyright to the journal, again, for free. Finally, the paper is published, and the institution that paid the researcher to do the original research has to pay again – sometimes tens of thousands of dollars per year! – for the journal in which it appears.
The academic publishing cartel insists that the millions it extracts from academic institutions and the billions it reaps in profit are all in service to serving as neutral, rigorous gatekeepers who ensure that only the best scholarship makes it into print. This is flatly untrue. The "editorial process" the academic publishers take credit for is virtually nonexistent: almost everything they publish is virtually unchanged from the final submission format. They're not even typesetting the paper:
https://link.springer.com/article/10.1007/s00799-018-0234-1
The vetting process for peer-review is a joke. Literally: an Australian academic managed to get his dog appointed to the editorial boards of seven journals:
https://www.atlasobscura.com/articles/olivia-doll-predatory-journals
Far from guarding scientific publishing from scams and nonsense, the major journal publishers have stood up entire divisions devoted to pay-to-publish junk science. Elsevier – the largest scholarly publisher – operated a business unit that offered to publish fake journals full of unreveiwed "advertorial" papers written by pharma companies, packaged to look like a real journal:
https://web.archive.org/web/20090504075453/http://blog.bioethics.net/2009/05/merck-makes-phony-peerreview-journal/
Naturally, academics and their institutions hate this system. Not only is it purely parasitic on their labor, it also serves as a massive brake on scholarly progress, by excluding independent researchers, academics at small institutions, and scholars living in the global south from accessing the work of their peers. The publishers enforce this exclusion without mercy or proportion. Take Diego Gomez, a Colombian Masters candidate who faced eight years in prison for accessing a single paywalled academic paper:
https://www.eff.org/deeplinks/2014/07/colombian-student-faces-prison-charges-sharing-academic-article-online
And of course, there's Aaron Swartz, the young activist and Harvard-affiliated computer scientist who was hounded to death after he accessed – but did not publish – papers from MIT's JSTOR library. Aaron had permission to access these papers, but JSTOR, MIT, and the prosecutors Stephen Heymann and Carmen Ortiz argued that because he used a small computer program to access the papers (rather than clicking on each link by hand) he had committed 13 felonies. They threatened him with more than 30 years in prison, and drew out the proceedings until Aaron was out of funds. Aaron hanged himself in 2013:
https://en.wikipedia.org/wiki/Aaron_Swartz
Academics know all this terrible stuff is going on, but they are trapped in a collective action problem. For an academic to advance in their field, they have to publish, and they have to get their work cited. Academics all try to publish in the big prestige journals – which also come with the highest price-tag for their institutions – because those are the journals other academics read, which means that getting published is top journal increases the likelihood that another academic will find and cite your work.
If academics could all agree to prioritize other journals for reading, then they could also prioritize other journals for submissions. If they could all prioritize other journals for submissions, they could all prioritize other journals for reading. Instead, they all hold one another hostage, through a wicked collective action problem that holds back science, starves their institutions of funding, and puts their colleagues at risk of imprisonment.
Despite this structural barrier, academics have fought tirelessly to escape the event horizon of scholarly publishing's monopoly black hole. They avidly supported "open access" publishers (most notably PLoS), and while these publishers carved out pockets for free-to-access, high quality work, the scholarly publishing cartel struck back with package deals that bundled their predatory "open access" journals in with their traditional journals. Academics had to pay twice for these journals: first, their institutions paid for the package that included them, then the scholars had to pay open access submission fees meant to cover the costs of editing, formatting, etc – all that stuff that basically doesn't exist.
Academics started putting "preprints" of their work on the web, and for a while, it looked like the big preprint archive sites could mount a credible challenge to the scholarly publishing cartel. So the cartel members bought the preprint sites, as when Elsevier bought out SSRN:
https://www.techdirt.com/2016/05/17/disappointing-elsevier-buys-open-access-academic-pre-publisher-ssrn/
Academics were elated in 2011, when Alexandra Elbakyan founded Sci-Hub, a shadow library that aims to make the entire corpus of scholarly work available without barrier, fear or favor:
https://sci-hub.ru/alexandra
Sci-Hub neutralized much of the collective action trap: once an article was available on Sci-Hub, it became much easier for other scholars to locate and cite, which reduced the case for paying for, or publishing in, the cartel's journals:
https://arxiv.org/pdf/2006.14979
The scholarly publishing cartel fought back viciously, suing Elbakyan and Sci-Hub for tens of millions of dollars. Elsevier targeted prepress sites like academia.edu with copyright threats, ordering them to remove scholarly papers that linked to Sci-Hub:
https://svpow.com/2013/12/06/elsevier-is-taking-down-papers-from-academia-edu/
This was extremely (if darkly) funny, because Elsevier's own publications are full of citations to Sci-Hub:
https://eve.gd/2019/08/03/elsevier-threatens-others-for-linking-to-sci-hub-but-does-it-itself/
Meanwhile, scholars kept the pressure up. Tens of thousands of scholars pledged to stop submitting their work to Elsevier:
http://thecostofknowledge.com/
Academics at the very tops of their fields publicly resigned from the editorial board of leading Elsevier journals, and published editorials calling the Elsevier model unethical:
https://www.theguardian.com/science/blog/2012/may/16/system-profit-access-research
And the New Scientist called the racket "indefensible," decrying the it as an industry that made restricting access to knowledge "more profitable than oil":
https://www.newscientist.com/article/mg24032052-900-time-to-break-academic-publishings-stranglehold-on-research/
But the real progress came when academics convinced their institutions, rather than one another, to do something about these predator publishers. First came funders, private and public, who announced that they would only fund open access work:
https://www.nature.com/articles/d41586-018-06178-7
Winning over major funders cleared the way for open access advocates worked both the supply-side and the buy-side. In 2019, the entire University of California system announced it would be cutting all of its Elsevier subscriptions:
https://www.science.org/content/article/university-california-boycotts-publishing-giant-elsevier-over-journal-costs-and-open
Emboldened by the UC system's principled action, MIT followed suit in 2020, announcing that it would no longer send $2m every year to Elsevier:
https://pluralistic.net/2020/06/12/digital-feudalism/#nerdfight
It's been four years since MIT's decision to boycott Elsevier, and things are going great. The open access consortium SPARC just published a stocktaking of MIT libraries without Elsevier:
https://sparcopen.org/our-work/big-deal-knowledge-base/unbundling-profiles/mit-libraries/
How are MIT's academics getting by without Elsevier in the stacks? Just fine. If someone at MIT needs access to an Elsevier paper, they can usually access it by asking the researchers to email it to them, or by downloading it from the researcher's site or a prepress archive. When that fails, there's interlibrary loan, whereby other libraries will send articles to MIT's libraries within a day or two. For more pressing needs, the library buys access to individual papers through an on-demand service.
This is how things were predicted to go. The libraries used their own circulation data and the webservice Unsub to figure out what they were likely to lose by dropping Elsevier – it wasn't much!
https://unsub.org/
The MIT story shows how to break a collective action problem – through collective action! Individual scholarly boycotts did little to hurt Elsevier. Large-scale organized boycotts raised awareness, but Elsevier trundled on. Sci-Hub scared the shit out of Elsevier and raised awareness even further, but Elsevier had untold millions to spend on a campaign of legal terror against Sci-Hub and Elbakyan. But all of that, combined with high-profile defections, made it impossible for the big institutions to ignore the issue, and the funders joined the fight. Once the funders were on-side, the academic institutions could be dragged into the fight, too.
Now, Elsevier – and the cartel – is in serious danger. Automated tools – like the Authors Alliance termination of transfer tool – lets academics get the copyright to their papers back from the big journals so they can make them open access:
https://pluralistic.net/2021/09/26/take-it-back/
Unimaginably vast indices of all scholarly publishing serve as important adjuncts to direct access shadow libraries like Sci-Hub:
https://pluralistic.net/2021/10/28/clintons-ghost/#cornucopia-concordance
Collective action problems are never easy to solve, but they're impossible to address through atomized, individual action. It's only when we act as a collective that we can defeat the corruption – the concentrated gains and diffuse losses – that allow greedy, unscrupulous corporations to steal from us, wreck our lives and even imprison us.

Community voting for SXSW is live! If you wanna hear RIDA QADRI and me talk about how GIG WORKERS can DISENSHITTIFY their jobs with INTEROPERABILITY, VOTE FOR THIS ONE!

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/08/16/the-public-sphere/#not-the-elsevier
632 notes
·
View notes
Text
The Rise of Remote Work: Tackling Multi-State Payroll Compliance in 2025

Remote work has gone from a trend to a business norm, and in 2025, it’s rewriting the rules of payroll. For businesses operating across multiple states, the challenge is clear: how do you keep payroll compliant when your team is everywhere?
If you’re managing a multi state payroll system, here’s what you need to know to stay ahead of regulations, avoid fines, and keep your workforce happy.
Why Multi-State Payroll Is a Growing Concern
More employees are working from locations outside company HQ.
States are cracking down on businesses failing to register or withhold taxes properly.
Compliance mistakes can lead to serious financial penalties.
Common Payroll Pitfalls in a Multi-State Environment
1. Dual Taxation Risks
When employees live in one state and work in another, or move frequently, your payroll system must account for both jurisdictions.
Avoid this by:
Checking for state tax reciprocity.
Filing nonresident and resident tax returns as needed.
Withholding from the correct state.
2. Triggering Unintended Nexus
One remote employee in a new state could require your business to register for sales tax, income tax, and payroll taxes in that state.
Key actions:
Review where employees live and work.
Consult with a tax advisor to assess nexus risks.
Register early to avoid late fees or penalties.
3. Overlooking Local Jurisdiction Laws
Small towns and big cities alike may require additional payroll taxes. Failure to comply can lead to audits and interest charges.
4. Misclassification of Remote Workers
Not all remote workers are “employees.” Some may be classified as independent contractors, and misclassification can lead to fines.
Prevent issues by:
Using IRS and state-level classification guidelines.
Keeping contracts and job descriptions clear.
Reclassifying roles when necessary.
5. Inconsistent Recordkeeping
With employees spread out, it's easy to lose track of where they’re working, which tax forms are filed, and what benefits apply.
Pro tip:
Use digital tools to centralize documents and time tracking.
Maintain copies of all state filings and registration documents.
Staying Compliant with Multi-State Payroll in 2025
Adopt a Scalable Payroll System
Look for software solutions designed for multi-jurisdiction processing. These should:
Calculate taxes based on employee location
File and pay taxes in each applicable state
Provide audit-ready reports
Work With Payroll Experts
A payroll provider or tax advisor with multi-state experience can save your business time and headaches.
Keep Employees Informed
Make sure your employees understand:
How taxes are withheld
Which forms they need (like W-4 vs. state equivalents)
Their rights in their specific state
Conclusion
Mult-state payroll tax compliance isn’t just a payroll issue—it’s a strategic HR, legal, and finance priority. As your team grows and spreads across the U.S., your systems must keep up.
By investing in technology, professional support, and continuous education, your business can thrive in a remote-first world—while staying fully compliant.
0 notes
Text
Why Choosing the Right Accounting Firm in UAE Matters for Your Business
Introduction
Running a business in the United Arab Emirates (UAE) is full of opportunities. With its growing economy, strong infrastructure, and business-friendly policies, the UAE has become a global hub for entrepreneurs and companies. However, managing finances, keeping records, and staying compliant with tax laws can be challenging. This is where choosing the right accounting firm in UAE becomes very important.
Understanding the Role of an Accounting Firm

An accounting firm in UAE offers services that help businesses manage their financial records and reports. These services include bookkeeping, financial reporting, VAT filing, audits, payroll, and advisory. A reliable firm ensures that your accounts are accurate, your taxes are filed on time, and your business remains compliant with local laws.
Benefits of Hiring an Accounting Firm in UAE
One of the biggest advantages of working with an accounting firm in UAE is professional expertise. Most business owners are not trained accountants. Having professionals manage your financial tasks can save time and reduce the risk of errors.
Here are some major benefits:
Compliance with UAE Laws: Tax regulations in the UAE, including VAT, are always evolving. An experienced accounting firm in UAE stays updated with the latest laws and ensures that your business follows all the legal requirements.
Saves Time and Costs: Instead of spending hours on paperwork and calculations, you can focus on growing your business. Outsourcing accounting services is often more affordable than hiring a full-time employee.
Accurate Financial Reports: A good firm provides clear and detailed financial reports. These reports help business owners make smart decisions about investments, expenses, and growth plans.
Risk Reduction: Mistakes in tax filings or financial statements can lead to penalties. A reliable accounting firm in UAE reduces such risks by handling everything professionally.
Choosing the Right Firm
There are many accounting firms across the UAE, so choosing the right one can be confusing. Here are a few tips:
Check Experience: Make sure the firm has experience in handling businesses similar to yours.
Look for Certified Professionals: Ensure the firm’s accountants are qualified and licensed.
Understand the Services: Some firms offer basic bookkeeping, while others provide full-service accounting. Choose based on your needs.
Ask About Technology: A modern accounting firm in UAE will use the latest software, which makes reporting faster and more accurate.
Read Reviews and Testimonials: Feedback from other clients can tell you a lot about the firm's reliability and professionalism.
The UAE's Business-Friendly Environment
The UAE government supports businesses of all sizes. With free zones, tax benefits, and simple regulations, the country encourages local and international companies to invest and grow. However, to take full advantage of these benefits, financial management is key—and that’s where the role of a professional accounting firm in UAE becomes vital.
Conclusion
Choosing the right accounting firm in UAE is not just about managing your books. It’s about having a trustworthy partner who can guide you through your business journey. Whether you are a startup or a large company, having expert financial support can make all the difference. So, invest in a reliable accounting firm today and take one step closer to long-term success.
Mail:- [email protected] Website:- https://goldenfalconconsultants.com/ Facebook:- https://www.facebook.com/goldenfalconconsultants/ linkedin:- https://www.linkedin.com/company/golden-falcon-consultants Instagram:- https://www.instagram.com/goldenfalconconsultants_/?igshid=NzZlODBkYWE4Ng%3D%3D Youtube:- https://www.youtube.com/@goldenfalconconsultants2031
1 note
·
View note