#it shut down in 2017 but the server is open source
Explore tagged Tumblr posts
Text
i went on whirled earlier and someone put on audio that was just the one fucking toy story "suck my motherfucking dick" edit pitched up and looped for 30 minutes
#does anyone even remember whirled#it shut down in 2017 but the server is open source#the version i'm playing is a fanmade revival called whirled club#it's really cool and desperately needs more players#hexed says#ask to tag i guess
3 notes
·
View notes
Text
Things Web Designers can learn from Web Developers
With so much competition, how can web designers maintain a premium identity for their work while also forging a successful career in web design? The solution is found in the design approach. Web designers must exit the race by competing on a completely different level.
An overview of the existing race in Web Designing
As people are spending more and more of their time online, digital user experiences are becoming the foundation for almost every large organization.
Businesses that do not have a proper website risk missing out on an excess of growth opportunities. They can reach far more people through the internet than they can through any other medium of advertisement. Therefore, organizations both globally and in Bangladesh who jumped into the boat of digital user experience, are having their website be the focal point of their company's online presence.
As a result, the number of web designers and web developers in Bangladesh, as well as web design and development firms, has increased to meet the demands of the growing popularity of startups and businesses seeking to go online.
While the supply is plentiful, so is the competition.
The web designers' goal should be to create distinctively one-of-a-kind design works for their clients, which elevates them above the competition and contributes to the development of a diverse, one-of-a-kind, and strong body of work.
Web designers frequently concentrate their efforts on the visual aspects of a design. How do the colours compliment one another? Is the design balanced? Is the spacing ideal? As designers, it is normal for them to want their work to be as visually appealing as possible since it has a direct impact on the overall quality of the experience.
However, designing an excellent website entails far more than simply making it visually attractive. Therefore, to improve web design skills, one of the most effective things designers can do is to connect with web developers for inspiration.
Web developers bring a website into its full functioning form by developing both the front-end and back-end part of a website. After the website’s design is made, designers hand it over or work side by side with the developers to bring the website into its life. Afterwards, the developers work their magic. However, after the site is published, developers have the access to its performance analytics. So, they can provide valuable information on improvement factors of the design as well as information about the modern technologies they can implement.
At Dcastalia, one of the best web development companies in Bangladesh, professional web developers and designers work closely together on a project. By following the Agile Methodology, the whole team collaborates with the user, to create segments of the website design and functionality, test it and then repeat the whole process for another segment. In this way, the web designers get valuable insights from both the expert developers and the clients which they can utilize to generate the visual aspects of their next design.
Ensuring Security for Website Visitors
Source: Pixabay
Web protection is now more important than ever. With technical innovation comes a slew of new attempts to breach online defences. Every hour new malware strains are being produced and other groups of data mining taking it to the next level.
The State of Cybersecurity in Bangladesh and how web designers can improve
Bangladesh has risen from 73rd to 65th and ranked 2nd in South Asia in the UK-based National Cyber Security Index's global cybersecurity Index (NCSI). According to a press release published by Dhaka Tribune, the index was created by the NCSI to assess countries' preparedness for basic cyber-attacks as well as their efforts in handling cybercrime and major crises.
While this gives up hope but does not give us the guarantee that our information is secured. Therefore, web designers in Bangladesh need to be up to date on web security and technological expertise. Considering site protection from the beginning of website design and collaboration with the web developers in Bangladesh will reduce the likelihood of potential cyberattacks.
Security while generating customized-display
Customization is all about helping companies better satisfy customers using their websites but at a cost. Modern websites are designed to collect personal information from users (from cookies), or while opening accounts which is then used to give a more tailored experience. This applies especially to business sites or eCommerce sites that take in customer's payment details.
Credit card compromises rose by 212% a year, credential leaks increased by 129%, while malicious applications grew by 102%.
(Source: Purplesec )
As a web designer, it is important to provide security and priorities more than personalization. The designer must consider the demographic of customers for the websites. For example, if the percentage has more senior people visiting the site, then ensuring them that their data is safe through visualization is vital.
Even if it is just a name and email address that the site is requesting from customers, designers need to learn how to get that information through visual cues which ensure security. In this case, Chrome browser, for example, indicates that the site is served on HTTPS which is a more secured server compared to HTTP. However, most of the customers need a more prominent signal which is easier to understand.
Defense against front-End vulnerabilities
A cross-site scripting vulnerability (XSS) that causes a company to shut down its service is the last thing any company needs to deal with.
Web designers must pay special attention to preventing client XSS and should exercise extreme caution when using Iframes, CORS, and cookies, as well as HTML5 elements and APIs, which are considered to be fraught with vulnerabilities.
Web designers are now expected to be more security conscious than ever before, and they have no choice but to live up to standards.
The designer and the developer must discuss issues such as the above while building a website. Only through this type of teamwork can the best outcome be obtained — one based on how the website is supposed to look and perform, as well as the criteria for handling and protecting users' data.
Top web design firms in Bangladesh such as Dcastlaia, comprises a team of professional and experienced designers and developers who work together in bringing out highly secured websites for local clients. Dcastalia’s in house production of their very own customizable eCommerce platform: Store -Up proves their established methods and concern for web security and thus ranked their services such as web development, eCommerce development as well as web security and maintenance high up in the country.
Responsive Websites – Is it the responsibility of the designers or developers or both?
Source: Unsplash
According to Statista, mobile traffic accounted for 52.64 per cent of all global traffic in 2017, implying that a website that is not responsive or mobile-friendly is losing roughly half of its traffic.
Responsive websites are those that adjust to all screen sizes and resolutions, not just desktop, but also smartphone, tablets, and, in some cases, smart TV.
Despite the advancement in modern technologies and growing designers and front-end developers, there are still abundant websites that are not responsive. This is because many designers are still learning the principles of responsive design, and front-end developers are hesitant to take on the responsibility since according to them, website responsiveness appears to be in design territory.
This resulted in the presence of blind spots in a typical Design - Frontend setup, which is located at the junction of design and development.
To begin with, none of the design tools available for web designers allows for truly responsive interfaces to be created and the available tools prove to be inefficient. Designers cannot fully grasp the principles of a responsive website unless they dive into the code. Front-end developers, on the other hand, front-end developers either lack the authority or the neOnst to make design decisions directly in code.
As a result, the blind spots are ignored, and the internet is flooded with ordinary websites. Building responsive sites is impossible unless there is a connection built between design and frontend development.
Share the responsibility – Break the ice with your Front-End Colleague
There is a major difference in the responsibilities for a web designer and a web developer which is a whole other topic.
The solution is not for the web designers to learn to code and start programming but to consider the fundamentals of responsive website development and to be conscious of the technical options available. In the meantime, web designers can share their design concepts and knowledge of good and bad user interfaces with their front-end colleagues.
Rise of responsive web development in Bangladesh requiring designers to stay updated
Bangladesh's ICT sector has grown at a 40 per cent annual rate since 2010.
(Source: UNCTAD).
The emergence of a large number of young entrepreneurs and their passion, as well as the government's strong emphasis on "Digital Bangladesh," are key driving forces in Bangladesh's ICT industry.
As Bangladeshis become more reliant on technology, many businesses began to establish online presences to participate in the evolution of Digital Bangladesh. Therefore, the need to have a unique and responsive website to represent the company’s value has mounted to attract customers. With that, over the last decade, Bangladesh's web development industry has grown exponentially.
The constant quest for web designers to use creativity and innovation has resulted in a drastic change in the way websites are developed today. Web developers in Bangladesh are now using advanced techniques and methods to create functional websites that have unique user experiences and are mobile-friendly.
With the emergence of new website design trends and techniques, web designers in Bangladesh are making the design development process more exciting. As with every other creative discipline, experts in the web design industry in Bangladesh often pursue the latest trends to better serve their clients.
Renowned web development companies in Bangladesh such as Dcastalia follow SDLC for web development.
The Software Development Life Cycle (SDLC) is a method used to design, develop and test high-quality software. This method induces the collaboration of web designers and developers especially in the designing phase of the process where the designer has to produce more than one design approach and document it in the Design Document Specification (DDS) which is then reviewed by all the important stakeholders such as the developers and clients. This process ensures high quality, robust and mobile-friendly website design and development.
Optimizing Accessibility – What the developers have to say
Source: Equalize Digital
According to the Web Content Accessibility Guidelines ( WCAG), Web accessibility refers to the design and development of websites, resources, and technologies so that people with disabilities can use them. More specifically, people can:
- perceive, recognize, navigate, and communicate with the Web
- participate in the Web
Web accessibility includes all disabilities that affect access to the Web, such as:
- Auditory
- Emotional
- Neurological
- Physical
- Voice
- visual
Current role of web designers for implementing accessibility
Accessibility is initiated during the design process. To build for usability, the designers must consider the users' needs. The inclusive design ensures that digital materials meet the needs of the greatest number of people, regardless of age or skill.
Understanding the needs of disabled users is important for creating better and more inclusive experiences for them. One of the most difficult aspects of designing for accessibility is determining which individual user type needs to be addressed.
Colour and contrast
Colour is a powerful tool for defining a brand, conveying thoughts, feelings, and ideas; however, the power of colour is diminished when a user cannot see or understand it differently. Colour blindness affects approximately one in every 200 women and one in every twelve men .
Web designers usually include a non-colour identifier, such as icons or text descriptions, to help distinguish between colours and avoid oversaturated and high-contrast colours, which are common in autism spectrum disorders. It is best practice to maintain a minimum contrast ratio of 4.5:1 between the foreground and background colours.
Images
It is also the designer's responsibility to consider the context of images and determine whether the image is merely decorative, conveys meaning, or contains the text.
Designers can transform image information into alt text so that screen reader users can understand the image's meaning. A screen reader is a program that reads out loud the contents on the screen to visually impaired users.
How developers ensure web accessibility and what designers can learn from them
The developers usually have to consider accessibility as soon as they begin writing code. While there is a learning curve at first, writing accessible code takes about the same amount of time as writing inaccessible code.
Developers and designers need to collaborate the accountability for improving accessibility in a website, especially when it comes to making user interfaces for several adaptive technologies such as screen-readers. Their collaborative goal should be to create a website that at a minimum meets the Web Content Accessibility Guidelines (WCAG) which is established through the W3C process in collaboration with individuals and organizations all over the world, to create a common shared standard for web content accessibility that addresses the needs of individuals, organizations and governments worldwide.
During web development, it is important for both the designers and developers to frequently audit and test for web accessibility. It can be done by checking the website in a browser to ensure that the display and the functionalities work correctly or not. There are many browser plug-ins and tools that assist in auditing the code for accessibility. Finally, testing the website or web application with a screen reader is recommended but not always required.
Bangladesh’s contribution in terms of Web Accessibility for all
Around twenty million out of 166 million people in Bangladesh have a disability. While Bangladesh aspires to become an ICT-based digital economy, there is a frightening likelihood that a substantial percentage of the population with varying degrees of disability and illiteracy will be left behind. While ICTs have the potential to improve the lives of people with disabilities, the lack of web accessibility is a significant barrier.
In November 2015, a2i, the Bangladesh government's innovation activator, conducted an internal accessibility audit and discovered various barriers to accessing government websites. As a result, a national web accessibility guideline for Bangladesh has already been drafted under the leadership of a2i and the Prime Minister's Office. A web accessibility toolkit is currently being developed to make all websites accessible and barrier-free for all.
In this regard, it is mandatory for web designers and web developers in Bangladesh to implement accessibility while building a website. Dcastalia is established as a prominent web development company in Bangladesh with over a decade of experience. The company excels at creating scalable, responsive and accessible websites to help companies establish a strong online presence. Their supremely talented and experienced developers and designers create effective, user-friendly web sites through mutual collaboration and by following the WCAG standard for web accessibility.
Last but not the least: Staying updated as a Web Designer
Source: Unsplash
Web designers who keep up with web design trends have an advantage over those who stick to what they learned in universities. This is very common among web developers who like playing with modern tools and languages and are always trying to incorporate that in their work.
Instead of focusing on the basics, designers can give clients new solutions for their needs if they are aware of what is trending in the web design industry. Creating new design work regularly that combines current trends with the designer’s style will transform their online portfolio into a one-of-a-kind visual destination for other designers and clients alike.
There are a few different ways to stay up to date with web design trends and keep that at a higher standard. It is not difficult, and all web designers can do it, whether they are fresh graduates, self-taught, or have been in the industry for over a decade.
Thinking outside the box
Sticking to the comfort zone is one of the biggest shortcomings of a web designer. Repeating the same steps for each new design project would just trap the designer in a box.
Web designers must look for ways to expand their imagination, encourage their ambition, and learn new skills. International web designer forums are a great place to share ideas and see what other designers are up to. Taking a course or watching a video on something new to do or not entirely comfortable doing can be a way of learning new trends.
No limit to learning
These days it is not very difficult to find a learning resource. Online courses and tutorials for learning new skills are all plentiful on the internet now. The tutorials on the internet are created by web designers who are keeping up with trends and giving back to the web design community.
Co-working with other designers and web developers
Web designers have a surplus number of resources at their disposal to stay in touch with one another and showcase their work in a community setting. Sites like Behance, Dribble, and Interaction Design Foundation are some of many great places to not only keep the portfolio up to date but also to meet other designers and developers and see what they are working on. Online communities are great, but joining a design association that hosts regular events and competitions can make things even more interesting.
Final Word
Lastly, by understanding the points of improvements and the things developers can teach in terms of web designing, designers can not only create unique work for the clients but will also be able to build a strong body of design work for themselves.
They will be able to show that good design is not something that can be purchased off the shelf and that if a potential client wants a distinct and unique web presence, it's something worth investing in.
Dcastalia is one of the leading web design and development company in Bangladesh and has a dedicated team that carefully considers the client's needs and curates creative, adaptable, responsive, accessible and cost-effective websites. The company offers versatile services such as web development, eCommerce development, web design, experience design and many more.
Frequently Asked Questions - Regarding Web Design
Source: Pixabay
How much does designing a new website cost?
The cost of a web design is determined by the requirements of each individual project. Every website is unique and necessitates different components; web designers design and develop custom websites for each business.
How much input can the clients provide in the process of designing?
A great deal! The clients’ input and feedback are critical to the success of the web designing process. The clients have to be clear about their needs, likes, and desires, and then work with the designer to create the perfect look and functionality.
What if the client wants to redesign a website?
The process is the same as making a design from the sketch. The client meets with the designer and other stakeholders in the team to share the requirements, goals and have an in-depth discussion about the design. After that, the designer starts making wireframes and prototypes in which the client provides feedback.
Do you make designs on pre-made templates?
Every website the designer creates is one-of-a-kind and custom-made for each client. Designers usually do not use any pre-made templates or themes unless the client specifically asks for them.
Can I add features such as an email sign up form on my website?
When web designers design your website, they will incorporate all of the features you desire, including an email sign-up form. Since they usually design the website from scratch, they can ensure that it complements your website's style and branding.
2 notes
·
View notes
Photo

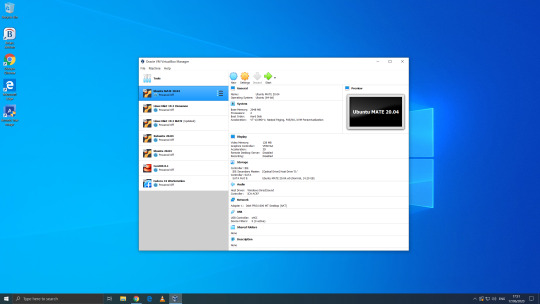
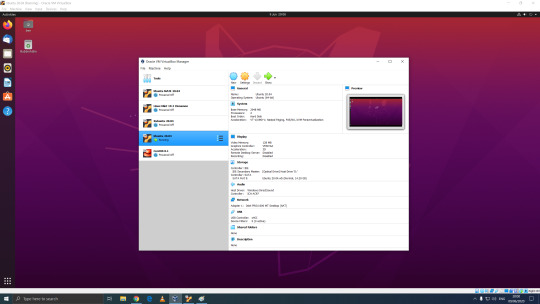
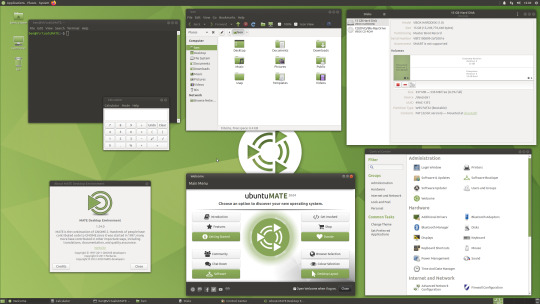

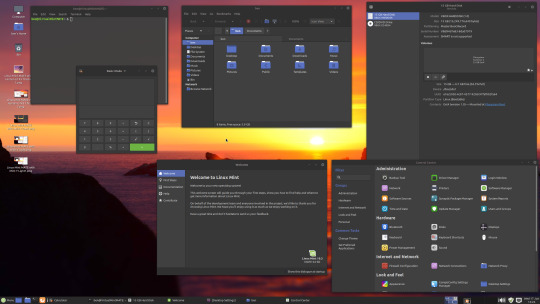

06.06.20
We went to the Oracle VirtualBox site and downloaded and installed VirtualBox 6.0. Oracle VM VirtualBox is free, open source virtual machine software maintained by Oracle Corp.
It was originally an Innotek product before Innotek was acquired by Sun Microsystems in 2008. Sun Microsystems was in turn acquired by Oracle in 2010. The alternative software to Oracle VM VirtualBox is VMware workstation.
I have been using Oracle VM VirtualBox since 2016 and have learnt a lot of information about how it works and how to install various operating systems.
Virtualbox can run Linux guest operating systems and Microsoft Windows guest operating systems. It can emulate both 64-bit operating systems and 32-bit operating systems.
Each operating system you add to VirtualBox is treated as a Guest. The guest operating system is running in its own virtual environment, which emulates a real machine on your PC. This means that anything you do in it does not affect your PC. The guest runs in a console:
About the VBox console: The VirtualBox console displays the active virtual machine. It shows the virtual guest operating system activity icons in the status bar. The console can be re-sized, minimised and forced closed from the title bar. It is not recommended to force close an active guest operating system as this acts like switching off mains power. Your guest operating system should be shut down cleanly. You can select different viewing modes in the view list or use the shortcut keys assigned with them. These mode include full screen mode, seamless mode and scaled mode. VirtualBox website link: https://www.virtualbox.org/ VirtualBox wiki link: https://en.wikipedia.org/wiki/VirtualBox
After setting it up, I went to find some Linux-based operating systems to download. Each download is a disc image file with the file extension .iso.
I chose:
Ubuntu MATE 20.04 LTS (Long Term Support)
This operating system uses the MATE Desktop Environment, which is the continuation of the former GNOME 2 Desktop. I like this desktop environment because it has a very configurable interface.
Ubuntu MATE: https://ubuntu-mate.org/
Wiki link: https://en.wikipedia.org/wiki/Ubuntu_MATE
Linux Mint Cinnamon 19.3 Tricia (based on Ubuntu 18.04 LTS)
This operating system uses the Cinnamon Desktop Environment which is based on GNOME 3. Cinnamon uses MGSE (Mint Gnome Shell Extensions), which re-creates a more traditional desktop linux experience whilst also looking modern.
I like this desktop environment because it looks modern and feels familiar to those who come from Windows.
Linux Mint: https://www.linuxmint.com/
Wiki link: https://en.wikipedia.org/wiki/Linux_Mint
Linux Mint MATE 19.3 Tricia (based on Ubuntu 18.04 LTS)
Linux Mint edition featuring the MATE Desktop Environment. I like this desktop environment because like Ubuntu MATE, it is very configurable. It also features Linux Mints system updating utility.
Ubuntu 20.04 LTS
This version of Ubuntu is the main version by Canonical Ltd. This operating system uses the GNOME 3 Desktop Environment.
Ubuntu came out in 2004 and used GNOME 2 as it’s desktop environment until 2011, when it changed to the now discontinued Unity Desktop. In 2017, Canonical announced it would return to GNOME. I like this desktop environment as unlike the GNOME 3 default interface, Ubuntu uses its own orange style theme and adds a Unity like dock on the left of the screen.
Ubuntu: https://ubuntu.com/
Wiki link: https://en.wikipedia.org/wiki/Ubuntu
Xubuntu 20.04 LTS
This operating system uses the XFCE Desktop Environment which aims to be lightweight on system resources and has a really configurable user interface. Xfce once stood for XForms Common Environment. The menu system is called the Whisker Menu. I like this desktop environment because like MATE it is very configurable.
The Ubuntu 20.04 Long Term Release is code named: Focal Fossa. All Ubuntu based distros use .deb (Debian Package Manager) for software installation.
Xubuntu: https://xubuntu.org/
Wiki link: https://en.wikipedia.org/wiki/Xfce
Fedora Workstation 32
Fedora is a Linux distribution developed by the community-supported Fedora Project which is sponsored primarily by Red Hat, a subsidiary of IBM, with additional support from other companies. Fedora is used by Linus Torvalds who is the creator of the Linux kernel.
Fedora is the upstream source of the commercial Red Hat Enterprise Linux distribution.
Since the release of Fedora 30, five different editions are currently available: Workstation, focused on the personal computer, Server for servers, CoreOS, focused on cloud computing, Silverblue, focused on an immutable desktop specialized to container-based workflows and IoT, focused on IoT devices.
I like this desktop environment because it looks fresh and modern. This operating system features the latest version of the GNOME Desktop Environment.
The screenshot of Fedora shows the ‘Activities’ dial screen which gives you a Visual overview of your GNOME Desktop.
With the Activities screen, you can see and control currently opened app windows, all installed applications, search system and switch desktop work spaces.
Fedora: https://getfedora.org/
Wiki link: https://en.wikipedia.org/wiki/Fedora_(operating_system)
CentOS 8.1
CentOS (Community Enterprise Operating System) is a Linux distribution that provides a free, community-supported computing platform functionally compatible with its upstream source operating system, Red Hat Enterprise Linux (RHEL). It is maintained by The CentOS Project (affiliated with Red Hat). Both operating systems use GNOME 3 as their default desktop environment.
It is basically a free version of Red Hat Enterprise Linux, with the Red Hat branding removed and update servers pointing away from Red Hat servers.
Red Hat Enterprise Linux is a commercial focused Linux distro.
All Red Hat Linux based distros such as RHEL, CentOS and Fedora use .rpm (Red Hat Package Manager) for software installation.
CentOS and Red Hat Enterprise Linux can be installed on servers, workstations and desktops. Both are very popular on mission critical commercial server systems as it is designed to be flexible and very stable.
I thought this Linux distro is interesting because unlike the Ubuntu based distros above, installation of CentOS is more involved, you set up software sources, installed software, desktop and operating system components.
CentOS runs on a lot of web servers.
CentOS: https://www.centos.org/
RHEL:
https://www.redhat.com/en/technologies/linux-platforms/enterprise-linux
CentOS Wiki link: https://en.wikipedia.org/wiki/CentOS
RHEL Wiki link: https://en.wikipedia.org/wiki/Red_Hat_Enterprise_Linux
VirtualBox requires the installation of Guest Additions, which adds extra features to the virtual machine, such as the ability to scale the resolution of the guest operating system, better 3D acceleration and the ability to move files between the Guest and Host machine.
To install Guest Additions on a Linux guest, you will need to use the terminal. installation of this is different on .deb and .rpm builds of Linux.
4 notes
·
View notes
Text
the cream coloured knit pullover ✧
part of the sweater collection series ~
warning(s): references to alcohol, vvvvv lightly implied sexual activity
-
It was funny, when you thought about it - that the sweater you felt most attached to was one whose owner you met only once.
You twirled the hems of the material in your fingertips. Block-cream-coloured and blank in pattern, it was probably the plainest sweater of them all. Yet now, held tightly in your grasp, it felt anything but. There was danger in the very thread of it. Electricity was pulsing it alive. One look at it and you were reeling back in time, the night you received it coming into clear and colourful view.
You could remember your journey to the bar vividly. Just as the glossy moonbeams had left the sky thick with cloudless light, the pangs of post-breakup loneliness had left your chest feeling hard and heavy. And there was only one way to ease it.
“Rough day, sweetheart?”
You glanced up, feeling your eyes widen as they focused in on the owner of the voice.
He definitely didn’t seem the ‘soft cream sweater’ type when you first saw him. Yes, woven threads of off-while wool had absolutely no place on this man’s body. Instead, a sleek black button up sat cuffed at his elbows. He was nothing else but professional behind that bar. Familiar, perhaps.
“Whatever it is, that isn’t the answer…” he mused, pausing to look down at your glass, “...I would know.”
You couldn’t put your finger on it then, but looking back you knew exactly why you revealed what you did right then: he made you feel wanted. He wanted to listen to you. Or at the very least, he did a good job looking like he did. He freed his hands completely of dishcloths and dirty glasses as he approached you - his deep, dark eyes softened in colour and focusing solely on yours as you took a breath to speak.
“I just ended it with someone,” you said finally, stringing a lip between your teeth, “the second guy this month.”
“How come?”
“It’s hard to explain...”
“Try me.” He smiled.
And before you knew it, you were making out in a taxi on the way to his apartment - your hands tangled in his hair, his hands sliding up and down your arms like the cascading reflections of city lights against the cab windows. You should have been thoughtless in that moment. Yet, they played on your mind as you pressed your lips to his. If you held your eyes shut you could smell their fresh detergent scent on his skin, and the fluorescent blonde locks of his hair twirled in your fingers became the fraying hem of a sweater you were yet to collect...
You pulled away.
“Jeonghan, I…”
“Everything okay?” He hummed, leaning away with concern.
“Yes, I just...need to tell you something.”
“It was that guy from a few weeks back you just broke up with, wasn’t it? The one who ordered you the shot across the bar?”
You blinked back in awe.
“How did you know?”
“I served you, that night.”
Of course he had. If you hadn’t been held so closely in his arms you might not have realised. He was wearing this shirt that night, too. The same black shirt with the same sleeves folded over at the same point at the crook of his forearms.
“To be honest with you,” he continued, “I usually suck at remembering regulars’ orders and faces. But you...I knew I had to remember you.”
You smiled up at him as he drew you in again.
The heat of his breath against your own sent you reeling, the dense beating of your heart thundering in your ears. You almost couldn’t feel his lips as they gently touched your forehead and slowly trailed down to the tip of your nose; your focus instead was on his fingers - how they curled into yours like they were his home.
“What were you going to say, sweetheart?” He breathed in-between a few, small pecks.
“Nothing.” You replied, wrapping your arms around his neck to be pulled in closer.
“I think you’re going to enjoy this.” He smirked, reaching for the car door.
He was right - you did. But that only meant one thing: you had to go.
You hadn’t seen him since.
Some would’ve called what you had a rebound. Maybe it was, by definition. But he meant more than that to you.
And if that was truly all you meant to him, he wouldn’t have hidden a sweater in your bag as you left the next morning, making sure you wouldn’t forget him again.
No, not again.
You held it close to your chest as you spiralled down the stairs. Within minutes you’d called for a cab, pleading for the driver to speed you to the bar as quickly as he could. The sweater - sprawled across your lap in a heap of knitted regret - was all you could focus on. If only he knew the effect it had on you, the effect he himself had had. How you’d been filling every hour of every day since your encounter desperately trying to stop thinking of him.
The great, silvery doors of the place soon came into view, towering over you like they were begging you not to go in. You ignored them completely, sweeping one of them open with such force you almost hit the wall on the other side. As you entered, the small room was packed with people, the only source of light being the fluorescent beams of purple rippling over the waves of crowds in the darkness. You knew you were going to struggle to find him - hell, you knew he might not even be there to find - but you’d come too far to leave now.
You struggled your way through to the bar. Behind it, you could count five servers bustling up and down with drinks. Two had the electric blonde hair you knew - both huddled together at the far end. One of them had to be him.
Holding your breath, you shuffled through the final hoards of crowds to reach the familiar surface, settling down a hand and heaving yourself forwards as though you were about to order. The furthest bartender approached, and it only took you seconds to realise - you’d found who you were looking for.
He looked directly at you, his eyes very quickly glazing over in confusion. He froze entirely, placing down the glass in his hands down and standing completely still.
He might have been aching with hurt, but he was exactly the same as before.
“What are you doing here?”
“I came to return your sweater.” You replied, settling it onto the countertop.
-

➴ jeonghan wore this sweater in this interview/photo shoot with anan web in 2017
a/n: okay this needs to be re-edited so excuse any clarity/grammar errors but phew chile. here it is. rly i have no excuse for how long this took and i’m kinda scared its awful bc most of it has been spewed from my brain in the past few days fhfhfh and i also feel like there’s not enough exposition/its all a bit too vague/not well explained BUT HEY i wanted to put it up to get the ball rolling on this series!! hopefully you didn’t dislike it as much as i do fhfhf thanks for waiting and reading
(but who was the guy from the bar??? is he another sweater bearer??? hmmmmmmmm all will be revealed....
#sorry to keep apologising#but i rly feel this is awful#idek i had a semi-decent concept but it all went downhill from there tbh#sorry#jeonghan#yoon jeonghan#jeonghan fluff#seventeen#svt#svt fluff#svt angst#jeonghan angst#jeonghan seventeen#seungcheol#josua#soonyoung#hoshi#wonwoo#jihoon#minghao#mingyu#seokmin#seungkwan#hansol#chan#dino#can u tell how desperate i am to be liked by these tags fhfhfhf yes#seventeen fic#kpop fic
23 notes
·
View notes
Text
Press: Elizabeth Olsen Opens Up for Who What Wear's September Cover
youtube




Gallery Links:
Studio Photoshoots > 2019 > Session 006
Studio Photoshoots > 2019 > Session 006 – Behind the Scenes
WHAT WHEN WEAR: A loose linen blouse. An untouched plate of madeleines. An empty French bistro in the Valley on a Tuesday at 4 p.m. These are the poised circumstances under which I spend an afternoon attempting to better understand one of Hollywood’s most discreet young celebrities: Elizabeth Olsen.
The 30-year-old actress’s identity doesn’t seem like it would lend itself to much mystery. Since 2014, Olsen has starred as the Scarlet Witch in Marvel’s superhero movie franchise—one of the most-watched film series in entertainment history. (This summer’s Avengers: Endgame quickly became the second-highest-grossing movie of all time.) It’s a role she’ll reprise later with WandaVision, a Disney+ spin-off series about her superhero character coming spring 2021. In the meantime, Olsen executive produces and stars in Sorry for Your Loss, a drama series following Olsen as Leigh, a young widow struggling to deal with the sudden loss of her husband. (The show airs on Facebook Watch, and its second season premieres October 1.) By any objective measure, business is booming for Olsen, the younger sibling of Ashley and Mary-Kate, who long ago reached a level of fame so behemoth they no longer need a last name. The Olsens are as much American royalty as the Kennedys or the Rockefellers. I should know everything about Elizabeth Olsen.
And yet, as soon as she walks through the door of Petit Trois (the setting she chose for our interview) and introduces herself to me, it sinks in how little I do know. “I’m Lizzie,” she says with a jumpy half-hug, half-handshake—though the awkwardness is entirely my fault. I’m caught off guard that the young starlet lives just outside of L.A., around the corner from where she grew up (I would have pegged her for more of a hip Eastside girl), and I never knew she went by the cozy nickname. “Thanks for coming to the Valley,” she says, smiling.
Following behind two heavy-hitting child stars turned esoteric fashion moguls, Olsen, who decided at a young age to pursue a career in acting (and obtained a degree in it from NYU), had prodigious shoes to fill. Her on-screen breakout, a critically lauded lead in the 2011 Sundance hit Martha Marcy May Marlene, suggested that Olsen would be taking a cleverly divergent route from her older sisters—one of a risk-taking indie cinema darling. Some of her filmography still reflects that identity—roles in quirky small-budget dramedies like 2012’s Liberal Arts and 2017’s Ingrid Goes West.
Maybe that’s why, even after all the Marvel movies, which are about as commercial as they come, I still see her in that light. Or maybe it’s Olsen’s enigmatic personal life, almost laissez-faire approach to style (“A combination of suburban mom meets little boy,” is how she describes it), and overall serenity of manner that create the sort of intrigue that independent film girls tend to have.
Her current project, Sorry for Your Loss, certainly has some of that indie energy, simply because Facebook Watch is still a new and unknown content platform. Olsen admits that selling the show to Facebook felt like a scary move in the beginning since most audiences don’t know that watching TV on Facebook is a thing at all. Moving into season two, she’s still figuring out the best way to spread the word to audiences. “There is no precedent, and that can be really challenging,” Olsen emphasizes. Still, there are major pluses to the marriage of television and social media, especially for a show that addresses a topic as personal and underrepresented as grief. “The show living on Facebook has been interesting because of the dialogue people get to have about their own experiences with grief and loss on the platform,” Olsen says.
The actress is looking forward to audiences’ feedback on season two, which finds Leigh “taking big swings, making big mistakes, and trying to figure out the balance.” As Olsen says, “Grief isn’t something that you ever just shut a door on or move forward from. It’s very cyclical.”
Olsen, however, will not be participating in these conversations with fans herself, because—ironically—she’s not on Facebook. She didn’t have a trace of social media presence until 2017. She finally downloaded Instagram shortly after the release of Ingrid Goes West, in which she pulls off playing a very convincing L.A. influencer. In contrast to millennial celebrities who use social media to speak about everything from beauty products to social justice, Olsen doesn’t feel the obligation to be any sort of influencer, politically or otherwise. “If I like blending into a wall, screaming from a stage isn’t something that would help me enjoy my life,” she says. “Sometimes I just don’t want to be part of a conversation because I don’t want anyone looking my way.”
As it turns out, privacy and stability inform everything about Olsen’s life—from how she dresses to the roles she chooses—more than any desire to seem “cool.” She lives in suburbia with her fiancé, musician Robbie Arnett, where she enjoys cooking, eating, and dabbling in interior design. “I love food more than I love anything that has to do with clothes,” she says, starkly contrasting her stylish sisters. (Though the actress is more of a beauty girl—she currently serves as a global ambassador for Bobbi Brown Cosmetics.) Categorizing herself as an “obsessive, detailed perfectionist” beset with a heavy dose of social anxiety, Olsen prefers poring over moldings and wood stains than obsessing over how her body looks in a dress and which angle she should pose in.
Transforming into a character—wearing costumes, acting on camera—puts the performer right at home, but photoshoots and red carpets, which give her no role to disappear into, are a source of great distress. “I don’t like standing out in a crowd,” she tells me just after ordering the dainty plate of madeleines. Our server also named raspberry tarts and pains au chocolat on her list of available pastries, but down to her desserts, off-screen Olsen likes to keep it simple.
“At 30, I feel like I’m finally getting to an age that was meant for my personality,” the actress says with no ounce of irony. “Just domesticated. A homebody.” I introduce her to the term JOMO: the joy of missing out. “Yeah… that,” she confirms. “I never feel bad about not leaving my house.”
Quietude feels inherent to Olsen’s personality, but it’s also something she learned from her family. She tells me her parents have had the same group of 10 friends their whole lives; so have her older sisters. Like other famously private Hollywood families (the Coppolas, the Fondas), the Olsens justifiably keep their circles tiny and exclusive to those with whom they have history—those they can trust. “I don’t have too many friends that I’ve met through work,” Olsen says. “I care about privacy. I don’t have a desire for people to speak about me.” Bottom line: Lizzie Olsen is not particularly interested in fame.
Ultimately, no matter how superhuman she appears on the big screen, Olsen values a fairly normal life: She wants her pastries from Petit Trois, where everybody knows her; she wants her white button-downs and her stable paychecks from Facebook and Marvel (most of which she’s been tucking away in savings to prepare for a family, she says). “Maybe I think about things too rationally, but my career goals are longevity and stamina,” Olsen tells me. “Working steadily, feeling challenged, and just kind of hunkering down for a bit.” One day, that paycheck might come from a less visible job; Olsen says that later in life she’d like to go back to school for a degree in architecture, interior design, or landscaping. “I’m interested in the new science of irrigation and water conservation in California,” she shares. “I could be someone who’s lived multiple lives, multiple careers.”
Before heading out, Olsen packs the six madeleines, which have all gone untouched, in a to-go box for later, when she’s home, to savor in her quiet, happy place. “The next career could be a lot more private,” she says. “Maybe. We shall see.”
Press: Elizabeth Olsen Opens Up for Who What Wear’s September Cover was originally published on Elizabeth Olsen Source • Your source for everything Elizabeth Olsen
#Elizabeth Olsen#Avengers#Scarlet Witch#Avengers Infinity War#Avengers Age of Ultron#Captain America Civil War#Kodachrome#Ingrid Goes West#Godzilla#Sorry For Your loss
7 notes
·
View notes
Text
Christmas Wedding Planner (2017)

As requested by @madbrilliant84
Starring: Jocelyn Hudon (The Strain) as Kelsey, and Stephen Huszar (Yorkie from Letterkenny!) as Connor
Street Cred: 7/10. Huszar has done more than a few of these flicks and Hudon was in another Hallmark fic with Rebecca Romijn and the fat kid from Stand by Me, so I’m confident she can hold her own. Plus, she has freckles. This movie has an actual plot, so hold on.
Official Synopsis: Wedding Planner, Kelsey Wilson, is about to have her big break: planning her beloved cousin's lavish and exclusive wedding. Everything is going smoothly until Connor McClane, a devilishly handsome private investigator, shows up and turns Kelsey's world upside-down. Hired by a secret source, Connor quickly disrupts the upcoming nuptials but wins Kelsey's heart in the process.
What Really Happens: First off, this one is based on a Harlequin novel, so I had big expectations. Second, I actually watched this last year, but once I remembered which movie it was, I was happy to watch again. So, you know, it’s good.
Kelsey (Hudon) is an orphan (sadface) whose mother died an unspecified number or years ago. Her closest relatives are now her super prefect but not conceited cousin Emily (they’re like sisters!) and Emily’s mother, Aunt Olivia, played to haughty perfection by Kelly Rutherford. Emily’s father died the year before. This is important, so don’t forget. I’ll be quizzing you later.
Kelsey is a wedding planner/event planner/total novice doing a good job in charge of Emily’s big day. It’s a Christmas Eve wedding, y’all! What could go wrong?
A lot, as it turns out. Kelsey literally bumps into a mystery man in a coffee shop and he is dismissive, and a little rude, and he steals her blueberry scone. Sort of. Kelsey vents about it in a text message to another mystery person and then goes on with being late to Emily’s engagement party.
At the party she spots the scone thief and discovers that not only did he (Connor) give the scone to Ice Queen Aunt Olivia, he used to date Emily. After a few backhanded comments from Olivia, Kelsey pulls up her big girl panties and confronts him only to have him tell her he knew who she was all along and that he may or may not be there to ruin the wedding. Then he takes off. Just like that.
Kelsey, being the loyal cousin/maid of honour/wedding planner that she is, goes after him and finds out Connor is a P.I. and someone hired him to look into Emily’s fiance (Todd), and would she like to join forces?
Later, at the dress fitting, we find out Connor left Emily on Christmas morning with no explanation (the cad!). Todd shows up and Kelsey spies him getting friendly with the woman who owns the dress shop. Either way, the point is that Todd may be cheating and this woman is clearly not interested in helping you try on dresses. What follows is Kelsey’s attempt at being sneaky by almost sending a baker into a panic spiral before giving in and searching out Connor.
This is where things take a turn in the story because Joey freaking Fatone is in this movie! That’s right, the Fat One himself, plays Connor’s best friend. And he’s fantastic, as usual. Kelsey eats some food, tries to inadvertently murder Connor, and finally agrees to work with him. He tells her he thinks Todd’s family is going bankrupt and he’s out for Emily’s family’s money. Did I mention they’re stinkin’ rich? Because they are. Who else can afford wedding planners and two engagement parties?
Kelsey texts her mystery person all her feelings and takes Connor as her date to the party at Todd’s parents (Mr. and Mrs. Todd) house. Apparently poor millennials aren't the only ones living at home after College. Connor is looking to get his hands on Mr. Todd’s finances and promptly tells people he’s Kelsey’s boyfriend, much to her chagrin.
Connor hams it up while questioning the staff, including a pregnant server, and then sneaks upstairs to Mr. Todd’s office. Kelsey follows him and they get caught snogging by Mr. Todd. Because why else would they be up there alone, right? It’s a good kiss, too, btw. Very hot. Mr. Todd tells everyone about it, of course.
Aunt Olivia warns Kelsey off Connor while Emily supports their (fake) relationship and eats delicious looking cake. Kelsey feels guilty about spying on Emily, but agrees to help Connor a little more because muscles and banter. Let the flirting begin!
They go on a stakeout to watch Todd walk up and down the same street for three days straight. The also fool around (not like that!) and flirt before following Todd to dinner. Kelsey gets all daring and vulnerable with Connor when she explains that the texts she sends are to her Mom’s phone. She keeps the account up to date and sends them to feel closer to her mom. Connor is a sweetheart and holds her hand while listening to how Aunt Olivia moved her sick mom and her in and helped care for her until she died. You want to dislike Olivia, but Kelly Rutherford make it hard.
Their flirting turns serious and Connor is proposing an actual date when the chickie from the dress shop joins Todd at his table. Kelsey gets pissed and confronts Todd. Turns out he and chickie are old friends and it’s not at all what it looks like.
The next day, Kelsey confesses to Aunt Olivia what her and Connor have been up to and that she’s fallen for him. Aunt Olivia gives her a cheque receipt as proof that Connor was only with Emily for her money and that he took off as soon as he was paid. He also hit the uncle up for more money the month before the uncle died.
Kelsey confronts Connor at Joey Fatone’s restaurant (he’s now catering the wedding, btw), not letting him explain himself because open communication is for losers. Kelsey is sad while Connor whines to Joey Fatone until Joey Fatone talks some sense into him.
The day of the wedding, Joey Fatone lures Kelsey to the restaurant by telling her the freezer malfunctioned, but really it’s so Connor can talk to her because she’s ignoring his calls. (It’s a trap!) Connor explains that ten years prior, he took what he thought was a loan from Emily’s dad to save Joey Fatone’s restaurant. But the uncle then told him to take a hike or he’d tell Emily Connor extorted the money.
Kelsey storms off before he can tell her about the second cheque because, HELLO, she’s the cousin/maid of honour/wedding planner and she has shit to do! The wedding is going swimmingly until Connor busts into the church with the pregnant server from the party, and well, you can guess where it goes from there. I won’t ruin the ending, but just know that I think they really missed an opportunity to marry Joey Fatone into that family.
Teacup’s Tidbits:
This Kelsey is delightfully awkward
I love that they didn’t cover up her freckles
Oh god, her cousin is adorable, too!
There goes Aunt Olivia with the backhanded comments. She’s a real pro
There’s a reporter covering the wedding, that’s how you know it’s a big deal. Don’t screw it up, Kelsey!
Connor is so dismissive and you can just see how pleased her is at how riled up she gets
He is totally crushing on her
So am I, btw
Uh-oh, that boy’s just a walk-away Joe
JOEY FATONE!!!!!!
Man, I love when he’s in stuff. This is no exception
Kelsey is going to work with Connor strictly to be fed for free. I feel that
So if Kelsey and Emily are like sisters, why did Kelsey know nothing about Connor? How old are they supposed to be?
She just guessed the laptop password. What luck!
Damn, that’s a good kiss
Mr. Todd is all “I’ll pay to watch”
She just corrupted that flashdrive. YOU HAVE TO EJECT IT FIRST!
Emily wants to compare sex notes about Connor, I just know it
Okay, the van scenes are so great. They look like they had so much fun!
Connor is so into her, he can’t even pretend to be chill
The waiter ships them, I’m dying!
TIME FOR FEELINGS!
Ugh, chickie from the dress shop is so smug and irritating
I don’t trust Todd either, for what it’s worth. First of all, his name is Todd. Second, see the first.
Aunt Olivia, looking out for her girls! With some more backhanded compliments that she sees as jokes
Joey Fatone has no time for your sad love life, he has a wedding to cater
That’s entrapment, boys. Not cool
Wait, I forgot in movies stalking is romantic. My bad
Kelsey shut off her listening ears halfway through Connor’s monologue. SHE DOES NOT HAVE TIME FOR THIS SHIT!
Hey, at least the bridesmaids dresses aren’t hideous. Except Kelsey’s. But it’s also very “her” for I can forgive it
Connor brought a pregnant lady as his plus one
Ohhh, shit is going down! I remember being really surprised at this twist
Score one for Aunt Olivia! She takes care of her girls
Emily is so awesome, and she’s basically worn a tiara is every scene in this movie. She wins
Connor looks really good in that jacket, it’s a shame the arms are three inches too short
”I know! We’ll draw attention from the too-small black sleeves by contrasting it with the bright white shirt underneath!”
At least they admit they barely know each other
How I Would Fix This With Fic: I don’t think I would, this one is really good!
Fics Like This: A Winter Wedding by ohcomely (Supernatural, Destiel), The Wedding Planner by Kelkat9 (Doctor Who, Ten/Rose), A Wedding Planner and A Divorce Lawyer Walk Into A Bar by TheBramblefish (Teen Wolf, Sterek)
8 notes
·
View notes
Text

OVEREXPOSURE
WICKET
MAY 2017
The Sun Reach Nuclear Power Plant, located way outside of Wicket, suffered a power outage. After 24 hours of no communication from the internal team or the team sent to investigate, the Special Entity Contamination Team was sent in to investigate, led by Captain Alice Stormer and 4 other Echo Soldiers. All of them were dressed in the yellow hazmat suits, except reinforced with metal plates and wielding assault rifles. Alice had the forearms of her suit cut out. After the transport bus arrived at the entrance to the Nuclear Power Plant, Alice and her team exited. The outside to the power plant was abandoned, except for several cars littered about, most likely from the people who were still inside. The emergency lockdown had been initiated and the security doors had locked the facility. Alice put her arms out, fingers outstretched and molded them into sharp metal knives, before proceeding to slide them through the cracks of the doors. Once she had a grip, she proceeded to pull apart the doors, breaking the mechanism and allowing the doors to open. Alice and the team entered the facility.
Inside the facility was completely dark, with only the red siren lights briefly illuminating the hallways. Echo Soldier #1 pulled up a portable Gauge Counter. The counter indicates that the air is extremely toxic and lethal, and any sort of exposure could immediately kill them.
“Alright everyone, lights on and safety’s off. Stick close, our main goal is to locate the Server Room, where the distress call came from and if deal with what caused this. I’ll take point, stay in a straight line” Alice said, moving to the front of the line as the soldiers got into formation.
The team slowly began to make their way through. The walls and floors of the facility had scorch marks on them, with the walls rusting and breaking down. A toxic gas was present all around, making it hard to see directly in front of them. Alice came to a directory, which showed the Server Room was underground, on Level 5. They made their way to a set of doors that lead to a stairway and began making their way down. The sound of the emergency generator began to get louder. Finally they all made it to Level 5 and continued the path to the sever room, when in the distance they hear a loud screech, almost a mixture of human and something else entirely.
The team began to move a bit more quickly, not wanting to face whatever made that noise. Eventually the team made it to the Server room and to their horror, they noticed that a hand-shaped hole was melted through the security doors. Alice was able to get a grip and pried open the doors. Inside the room was quite a shock.
There laid the bodies of 4 people, whose skin had melted off, exposing their flesh and bones as the meat was sizzling, the sound was horrific. Their eyeballs had popped, with only the optic nerve hanging out. Only one of the bodies had a deep cut across their wrist. Their bodies were slumped in the chairs and their clothing had been burnt.
“What the fuck happened here?” Echo #02 asked, still by the doorway, afraid to get closer
“I don’t know, but it was probably the same thing that made that hole in the door” Alice replied, not being able to take her eyes off the bodies
“Captain, behind you on the wall” Echo #03 pointed out.
They all turned around and on the corroded walls was the phrase ‘PW SUNDANCE5057QXY’ written in blood.
“Echo #04, see if you can figure out the computer” Alice instructed
“Affirmative” Echo #04 replied, before moving over to the terminal and began typing.
“These men were exposed to Level 5 radiation, they must’ve died within seconds” Echo #01 said, as he moved the counter over the bodies
“Must’ve been the most painful couple of seconds in existence” Echo #02 replied, still hanging by the door.
“Captain, I got something” Echo #04 said
“What is it?” Alice said as she and Echo #01 and #03 moved over
“It is audio recordings, all dated yesterday”
“Play them”
Echo #04 hit play and the speakers came to life.
“May 7th, 2017. It is 1:00 am since the reactor downstairs had exploded. It wasn’t a big explosion, but big enough to initiate security protocols. Me, researcher Andy Hood and William Bend along with Technician Jim Court have been locked inside the server room. Not sure about the others but we hope they got to a room in time. We are currently awaiting the Seal Team to arrive and contain the exposure so we can all leave.”
“May 7th, 2017. It is 1:47 am. The Seal Team has arrived and began to get to work. They assured us it would take an hour or two to accurately assess the damage and seal it up. Thankfully we have the newspaper to do crosswords in as we kill time.”
“May 7th, 2017. It 2:30 am. Shortly after the last recording we kept in contact with the Seal Team via radio. As they got closer to the reactor chamber, their comms began to go haywire. The last thing we heard was screaming before dead silence.”
“May 7th, 2017. It is 3:00 am. We haven’t heard anything back from the Seal Team. I fear the radiation has become a lot stronger, melting their hazmat suits. The boys are beginning to get unnerved, but I fear something worse.”
“May 7th, 2017. It is 3:10 am. The external towers have gone off now, the radiation has mostly likely radiated the cables and lines. Thankfully the emergency generators haven’t been touched yet.”
May 7th, 2017. It is 4:00 am. Our worst fears have been confirmed. All of the Seal Team members are dead, except for one. On the security cams we saw a glowing hand melt through the security doors, before his whole body melted through. He rolled through the hole, before getting up. Soon after that the camera went off. I think he fried the circuits.”
“May 7th, 2017. We’ve lost visual contact with the exposed man. All our cams are off. So far we are fine, but if the radiation gets worse, I don’t know if the doors can withstand the radiation for much longer.”
“May 7th, 2017. In case something happens, this is the last recording I will make. Don’t have sympathy for me, don’t care about me. To anyone who finds this, do NOT allow them to restart this project. We have created something new, something much worse. William is trying to make a sign or note to anyone who finds our computer terminal and what to do. Please shut down this project, bury it as deep as you can- oh god, oh god he’s here everyone get down!”
The sound melting metal is heard, along with a loud groan that doesn’t sound human. A scream is heard in the distance, the melting metal stops and heavy footsteps begin to fade as the exposed man begins running to the source of the screaming.
“Oh fuck we’re breached. William get that note written now! Use whatever you can! We don’t have much time, promise me you’ll kill this project- ARGHHHHHHHHHHHHHH” all 4 men begin screaming in agony. The sounds of their screaming go for a long time before eventually dying down, with the only sound remaining is sizzling.
“Fuck” Alice said, as she and the Echo Team looked around at the men. The sound of something screaming in the distance caught their attention.
“Let’s go” Alice said as she took charge and the soldiers followed behind her.
The followed the sounds of screaming through a few hallways before a sudden wave of heat hit them. The counter began to rise rapidly, before the glass broke. Echo #01 was forced to drop the counter as it began getting hotter and hotter. They all rounded the corner before stopping and seeing the exposed man, standing in the hallway, hunched over and shaking violently. His skin was a bright green, his bones could been seen in black outlines and the hazmat suit had the top half melted off. The exposed man turned around upon sensing their presence. His eyes were brighter than his body, almost casting a spotlight on the Echo team. Instinctively all of them raised their guns, aimed at him. The exposed man made a loud screeching noise before running at them.
They all opened fire and the bullets tore through him but didn’t stop him. Glowing splats painted the walls as he continued charging. Echo #04 held his gun up with both hands, bracing himself for the impact. The exposed man tackled him over, his hands immediately melting through his protective armor.
“AHHHHHHHHHH!” Echo #04 began screaming, before stopping when the exposed man pressed his hands to his forehead, melting through it and melting his brain. The exposed man got back up and charged at the rest of the members. Alice and Echo #01 and #02 began to run, hopping to get to a wider space to avoid the exposed man. They all made it to the open area, except for Echo #03. He managed to reach the end of the hallway, before the exposed man began running into him. Echo #03 locked arms with him, before turning and throwing him away. Echo #03’s gloves and shoulder pads were exposed.
“AHHHHHHHHHHHH!” He began screaming as his body fell to the ground, his body convulsing rapidly. After a few seconds, the screaming stopped and the body went limp. The exposed man got back up and turned his attention to the remaining members. Alice threw her gun on the ground and stood between Echo #01 and #02 and the exposed man. The exposed man began screeching and running at Alice. Alice tightened her stance and was preparing for impact. The exposed man and Alice locked arms with each other, Alice’s arms on his shoulder and his arms going for her face. His hand was inches from her face but Alice had a tight grip of him. In a quick and easy swoop, Alice moved her right arm to his throat, grabbing it. The exposed man stopped going for her throat and his arms went to her arm. He began clawing at it, but Alice didn’t let go. Her arms began to spark up as the radiation tried to eat through her arms. Alice let go of her left hand and pulled it back, making her hand into a fist before driving it into the exposed man’s face. The impact made all the bones in his face crack, the exposed man temporarily stopped clawing as he stood dazed. Alice then winded up her arm again, before driving it back into his face. She punched him again and again until he stopped moving entirely. Alice let go of his throat and he fell to the ground, unconscious.
“Echo #02. Take off Echo #03’s suit” Alice instructed
“What?” Echo #03 replied, not sure if he heard properly
“His suit, take it off him and bring it here” Alice repeated, this time more aggressively
Echo #02 walked over to Echo #03 and ripped the suit off of him, which started to begin sticking together from the flesh. Alice took the suit and laid it over the exposed man’s head. She then proceeded to rapidly punch the man’s face, caving it in as the sound of bones breaking and radiated blood began spraying. After a few more punches, Alice stopped and took a few steps back. The blood managed to eat through the armor plating, melting it. The radiant glow from the man began to fade. After a few minutes of waiting to make sure he wasn’t coming back to life, the Echo team began to leave. They reached the entrance to the lab and once outside, could safely take off their head gear to breathe.
“Echo #01, call it in. The SECT is officially taking over and if anyone tries to complain, direct them to me and I’ll sort them out” Alice instructed
“Understood” Echo #01 replied and moved to the bus to begin his work
“Echo #02, grab whatever is strong enough to survive and transfer the data recordings over, then send them to the Director”
“Understood” Echo #02 replied and moved to begin his work.
The SECT arrived and began to cover up this mess. The whole incident was covered up as a fire incident and the Nuclear Power Plant was shut down completely. Whatever experiment was going on was seized by the SECT and hidden away. The power plant was locked down and anyone who got out before the radiation took over was threatened to keep quiet about what happened. Alice and the remaining Echo team returned back to their base, to get first aid and await further orders.
“What the fuck happened there?” Alex asked as he applied applying a special chemical to Alice’s arm
“Some sort of experiment gone wrong I think. I don’t know and I don’t want to” Alice replied
“Well, at least we figured out what can hurt us now. Could be a good exit plan” Alex joking said
“Maybe for you, I plan on living as long as I can” Alice replied sternly
“Okay, all done. Take it easy now” Alex said as he put a plastic coating on her arm.
“Thank you” Alice replied, examining her arm before getting up from the table. Alice examined her wounds and noticed that they were completely healed.
0 notes
Text
DappBirds&EOSC DApp sport ecological development road
EOSC mainnet Continue to evolve towards a decentralized high-performance smart contract platform attention Guide

On December 12, 2019, Beijing period, DAppBirds operating bird brother published a community revealing on the EOSC local community with the theme of "Where to find a good DApp". He mentioned: "EOSC is the first of many public chains to adopt a decentralized spending budget. The systematic general public chain, through the spending budget system to achieve ecological design is an extremely interesting path inside our opinion. It solves the dilemma of developers in the first cool start, and in addition solves the dilemma of the project's early promotion and publicity." The following is a record of sharing. 1. Introduction to DappBirds Hello everyone, I'm the operating bird brother of DAppBirds, a game lover, and this issue I will share with you these days is: How exactly to discover a good DApp. Very first introduce our current primary operating platform DB: DappBirds may be the world's leading Dapp ecological support platform, from Dapp data analysis, to create, chain reform, issuance, operation, cross-chain, and deal. It's been docked with more than 14 This general public chain consists of almost 4,000 DAPPs, chain reforms and releases a large number of chain games. It is also the only system in the market that has individually developed access to wallet solutions and can be straight downloaded in the worldwide AppStore. The merchandise are currently PC, H5, Small programs, APPs are completely covered, and there is a forward thinking game mining swimming pool model. IOST is already the very best ten mining pool node on earth. It can be seen our team has helped the public chain to accomplish a lot of landing issues. Additionally it is among the essential node people of the current mainstream open public chains and contains rich expertise in ecological landing. 2. Hundred billion U.S. dollars blockchain sport market As a sunrise industry, the game industry has maintained rapid growth in the last 20 years, forming explosive growth and iteration, that is fundamentally the dual impact of fluctuations brought about by the launch of dividends and changes on the need aspect and the source side. From the aforementioned picture, we can see that the "2018 Global Game Market Report" released by market research company Newzoo demonstrates the global game market revenue in 2018 reached 125.4 billion U.S. bucks, and this data will reach 143.5 billion U.S. dollars by 2020. The gaming sector is likely to end up being the most rewarding industry in the entertainment industry within the next ten years. Among them, the Asia-Pacific video game marketplace revenue in 2018 will reach 71.4 billion U.S. bucks, accounting for 52% of global game revenue, a year-on-year raise of 16.8%. Thanks to the growth of smartphone games, the Asia-Pacific region's share of the worldwide game marketplace has increased year by year. THE UNITED STATES continues to be the world's second largest game marketplace, accounting for 23% of the worldwide game market's complete revenue, a year-on-year increase of 10%, and is expected to reach US$32.7 billion in 2018.

The share of Europe, the center East, and Africa slightly lags behind THE UNITED STATES, accounting for 21% of total global game revenue, and is expected to reach US$28.7 billion in 2018. The overall game marketplace in Latin America will grow to US$5 billion this year, accounting for 4% of the global market share. However, previously two years, with the rise of short video, live broadcast along with other entertainment strategies, user dividends possess declined, and the game life routine is short. Apart from several games, there is little area for enhancement in payment prices and ARPU, which also makes the traditional game industry extremely competitive. It has triggered many little and medium-sized sport manufacturers to survive. The reason for this situation is related to the requirements of users, in fact it is directly related to the abuses of traditional games over the years. This means that that the game has further established its leading position in global entertainment activities. The blockchain industry has experienced explosive growth previously 2 yrs. In 2017 and 2018, average users increased by thousands. By 2018, nearly 25 million users created a market of hundreds of vast amounts of dollars. Games employ a special status inside the blockchain field. Because whether in the traditional Internet industry or the blockchain field, games are among the easiest sectors to understand, and the game industry nevertheless has the characteristics of low learning from your errors costs. Because the development of blockchain games, countless teams have successively introduced many new game types and gameplays, including works which are very successful both in terms of data and company, and gradually formed a mature business model and distribution strategy. Especially before two years, blockchain games have formed explosive growth, forming a globally distributed user group with high willingness to pay. And the pattern of younger blockchain users obviously has very strong investment attributes and is unanimously well-liked by the exterior world. If the blockchain can take root in the overall game industry, you won't only rectify the name of the blockchain, but also obtain an encrypted currency flow portal that connects billions of people. But at the same time we also note that the original game market has many discomfort points: 1. Dislocation of data ownership Users pay time and money costs when working with game products, but they cannot obtain the corresponding value possession rights. Game companies may control user data and user assets without supervision, which in disguise makes users' legal rights and interests continue being damaged. 2. Fragmentation of asset value The economic system of the overall game is fragmented. Each sport has an independent economic climate and can't be interconnected with other games. The life cycle of the overall game is bound. For players, after the video game is stopped, the digital property that has been paid will undoubtedly be lost and wasted. The circulation of game assets is inefficient, and there are problems such as for example inconsistent transaction standards, high transaction costs, and transaction security suffering from many uncertain factors, which restrict the circulation of game asset value. 3. Uneven distribution of resources The monopoly of resources in traffic and monetization, and the free competition in content production, have caused the expense of game production and distribution to continue to go up, which ultimately greatly increased the risks for practitioners and investors. There are always a large numbers of uncertain factors along the way of game distribution, leading to independent game developers and small and medium-sized game companies with an individual ability, even though they have excellent creativity and product capabilities, it really is difficult to build competitiveness with resource-based companies. 4. Lack of transparency In the game, players will usually get some rare items by means of monster drops. For gamers, these rare game items have important value, either they are able to quickly improve the skills of the character, or they may be exchanged for a degree of game foreign currency. In today's game atmosphere, the actual drop probability of these rare items is often not really disclosed. These methods that lack transparency have impacted the playability and fairness of games.

5. Safety hazards With the continuous development of the overall game marketplace, the security of virtual house in the overall game has received constant attention. Frequent cases of theft and hacker attacks in virtual transactions have caused the players' own interests to be significantly damaged. Second, the existing game props are issued by video game companies. Game props are locked in a certain video game. If the game stops for some reason, the player will also lose the house rights of the game props, that will also lead to the player's very own passions to be significantly damaged. Simultaneously, we are fortunate to possess access to blockchain technology, and we've also seen that blockchain technology + game content ecology will solve related pain points and have many advantages. We believe that blockchain technologies does not produce modifications, but provides fresh possibilities and ideas, technically solves the essential trust issue, and truly returns the rights and interests that should participate in users. The mix of blockchain and games has taken about changes in thinking and business models for games, along with the possibility of nurturing new game types and gameplay. Weighed against traditional games, it has an advantage that cannot be replicated. Included in these are: 1. Asset possession and liquidity Blockchain technology enables the ownership of digital resources to be fully attributable to users. Gamers invest time to obtain valuable virtual items. They're no longer affected by operators' shutting down of services and secretly changing data. They will also gain stronger participation when doing offers. sense. Players can dispose of their own possessions anytime and anywhere, and different game manufacturers can trade or transfer assets to other games for make use of, which greatly improves the liquidity of resources. 2. Provides the idea of "Game is Investment"

The application of assets on the chain prevents game programmers from spamming game currency and props. Gamers can vote making use of their foot to abandon the official game "hard fork" out of private servers. Unscrupulous manufacturers will undoubtedly be abandoned and powered by greed to commit evil The cost has become very large, so the value of digital assets could be preserved or even increased. Beneath the protection of the system, the user's sport behavior is valuable. The overall game is no longer a genuine entertainment and intake activity. Players can obtain reasonable value through their own investment in game time and money and advantages in game abilities. Return. In this case, playing games may no more be "waste" but "investment". 3. Transformed the partnership between players and game manufacturers Using the distribution associated with rights plus interests of the token economy, players gain a certain right to speak, and the interests associated with the manufacturers become consistent, plus the players gain a certain right to speak, and the interests of the manufacturers turn out to be consistent, to allow them to reach a certain consensus, form the community, plus jointly keep up with the sport The development associated with the game brings unprecedented freedom and democracy in order to the game. 4. Home based business logic The mix of the token economy and the game has brought unlimited possibilities for the economic model inside and outside the game. Essentially, blockchain technology has solved the issue of "have faith in". Through the gradual exercise of the concept of decentralization, it is expected to realize the web simultaneously. Free democracy and efficient collaboration stimulate the enthusiasm of ecological participants and bring unprecedented creativeness and vitality to the community. Furthermore, through completely fair and transparent on-chain correct confirmation technology, digital assets have grown to be the label of visitors, and new video games could be streamed through digital asset reuse or benchmarking airdrops, thereby reducing customer acquisition costs. In a nutshell, with the continuous improvement of blockchain technology and the continuous innovation of token design, blockchain games will continuously gain brand-new empowerment, thereby creating greater value, and the future of blockchain games is immeasurable. GoBlock: EOSC's initial chain game GoBlock game may be the first on-chain game developed by EOSC and DappBirds, in fact it is also the first step inside the cooperation among EOSC and DappBirds. 1. Introduction to Gobock sport: "GoBlock" is an extremely fun casual shooting game released by DAppBirds predicated on eosc. You can choose weapons, update weapons, eliminate all sorts of nasty virus blocks, and share higher ranking rewards each day. . 2. GOblock advancement process: * Developer: 5 people altogether, including 3 developers, 1 artist, and 1 product * Development cycle: front-end and back-end programs, art, products (estimated 10 business days) * Development costs: 240,000EOSC server maintenance costs (50,000) labor costs (190000) 3. EOSC budget system EOSC is the first public chain to adopt a decentralized spending budget system among many general public chains. Its application releases and ecological expansion. All teams can donate to the ecology through budget applications. In this manner is in our opinion. An extremely interesting street. He solved the issue of programmers in the early cool start, and in addition solved the issue of the project's earlier promotion and publicity. At the moment, for most general public chains in China, rewards for programmers and ecological expansion remain at the phase of centralized Bounty centralized procedure. For the public chain, as well as the node part, ecological expanders and programmers and neighborhood communicators benefit from the whole ecosystem. Over time, it is a process of long-phrase ecological prosperity. This is actually the first time to cooperate with EOSC. It is extremely identified for EOSC's high-efficiency, low-latency functionality and decentralized neighborhood operation and growth. You will see more cooperation and typical development later on. Thank you. -- Recommended reading -- -- Join the EOSC neighborhood -- EOSC Community Collection Group EOSC Neighborhood Telegram Group
0 notes
Text
Say Goodbye To Mistakes With Roblox Id Codes
Just how to eliminate Roblox Infection Is Roblox safe for kids What Parents Required to Understand About Roblox Roblox closing down: Is Roblox shutting down TODAY? Here'' s what you require to know Robux Just website how much does Robux set you back?

Or do you simply want to hang out and chat with your buddies online? An expanding library of worlds created by the community means there's constantly something exciting and brand-new for you to play every day. On July 12, 2016, the looks of the visitors were changed for the first time in a while. The male guest (BillyBloxxer) put on a Roblox jacket, black denims, and also truth Blue Hair.
RAREST PET CRATE UNBOXING IN ROBLOX! (Roblox Phantom Forces) - Czas trwania: 21 minut.
This ever-changing and increasing library of games is a huge component of Roblox appeal. Combine this with the millions of various other players to complete versus in obstacles as well as you have the perfect recipe for young people to delight in. These games can then be played by kids worldwide, typically on the internet with each other, through a phone or tablet application or an internet internet browser. This is the concern that a lot of parents are coming to grips with, complying with the recent problems elevated in the media. To aid ease those fears, Pocket-lint technology journalist and Gamings Expert, Andy Robertson clarifies the video game and also how it can be played securely.
How much does Robux set you back?
Is Roblox down today?
Epic Games' Fortnite is said to be shutting down in June 2020.
Roblox likewise enables your kid to block as well as report disruptive or frustrating players. Naturally, this additionally produces a chance to have a discussion regarding on the internet etiquette, which truthfully should not be all that different than exactly how you educate them to behave off-line! " Do unto others as you would certainly have them do unto you" goes a lengthy means. An additional basic web safety guideline is to never share personal information or passwords online.
Gamers can get Robux by buying Robux with genuine currency, from a persisting Robux stipend given to participants with premium membership, and from other gamers by selling digital material on Roblox. Customers can bid on an advertisement for their games, apparel, groups or models for various quantities of Robux. Users can create a Badge for their video game at a price of 100 Robux each.

When a gamer hovers the computer mouse over a guest image when checking out video game servers, the name utilized to look like "A Pleasant Guest". This was altered to read "A Roblox Player" before the Visitor function was removed. The Guest was a function developed for the meant use letting newcomers test Roblox prior to making an official account. They were presented on September 26, 2008. The last revision of a Visitor's character. Robux is the virtual money in Roblox that permits players to acquire various products.
Later on, Guests would certainly be provided the exact same look as the "ROBLOX" account, including hats, enabling Visitors to technically "attempt" devices and have the ROBLOX account's gears. If a player joined a video game while not logged right into an account, they would be labeled as a "Guest".
All the games function penalty without additional web content, but at the exact same time will signpost players to benefits of investing cash as this is how video game makers make a profit from their developments. The very best remedy to this is to specify the Account Constraints embeding in the linked Roblox account. This limits the usable video games to those selected by Roblox itself. Although do note that establishing a child's age as under 13 does not restrict the video games they can accessibility.
Is Roblox better than Minecraft?
Roblox is a totally different kind of games than Fortnite. It's hard to compare them. Roblox allows you to be creative, to build virtual objects, worlds, and even games. So, you can have lots of fun here, and the type of that fun will depend on your mood, on your gaming preferences.

( If the game was set to R6 Just, then R6 would have been used.) After Roblox presented a brand-new logo design, the guest's shirt transformed to the brand-new Roblox Logo design Coat on January 16, 2017 (six days after the logo design started usage). Afterwards, sex choices were included, enabling Guests to appear as "BillyBloxxer" or "BettyBloxxer". They had really similar looks to the user ROBLOX but had different hats depending on the gender chosen. BillyBloxxer wore the Red Roblox Cap, while BettyBloxxer used the Pinktastic Hair.
The women guest (BettyBloxxer) is similar to the male visitor other than it wore the Lavender Updo Hair. The other visitor kind (DefaultGuest) looks similar to both the other guest types except it was bald. On September 13, 2016, guests started to put on the Robloxian 2.0 package and also the DefaultGuest started wearing theROBLOX 'R' Baseball Cap.
Guest
As discussed above, the Roblox infection declares to be an in-game hack and also. Email spam projects distribute destructive add-ons (typically MS Office papers) that, when opened up, carry out commands that install as well as download malware. Unofficial download sources existing destructive executables as reputable software, thus fooling customers into downloading and install and mounting malware. Fake updaters infect the system by manipulating outdated software program bugs/flaws or just installing as well as downloading and install malware instead of updates.
Exactly how did Roblox virus contaminate my computer?
The Roblox virus is trojan-type malware that claims to be a dishonesty application for a game called Roblox. Some players think that this harmful app will substantially alleviate gameplay (allegedly enabling them to produce in-game currency at no cost), yet they simply end up contaminating their computer systems. Restricting your children's accessibility to on the internet video games is the number one method of stopping your child's ability to connect as well as see with unsuitable material.
0 notes
Photo

New Post has been published on https://magzoso.com/tech/social-media-platforms-that-thrived-or-died-in-the-decade-past/
Social Media Platforms That Thrived (or Died) in the Decade Past

“You are what you share.” These famous words from Charles Leadbeater’s renowned book ‘We Think: The Power Of Mass Creativity’ are extremely apt in today’s times. Your personal and professional resume gain extra weightage, based on the number of followers, and the number of eyeballs your social posts get. The last decade in particular, has seen the evolution of social media in tonnes of growth spurts. It saw TikTok become a household name, and Tinder became the new way for people to find partners. While some social media platforms thrived in this Internet era, some stumbled off the shelf.
The increasingly competitive market space and the ingrained fleeting nature of social media forced some platforms to shut shop as well. The biggest shockers were Orkut, Google+, Yahoo Messenger, and Blackberry Messenger or BBM, as users fondly liked to it. In the face of the competition, these didn’t manage to grab their audience’s attention long enough and were forced to close down. As far as social media is concerned, this was the decade of WhatsApp, Instagram, and TikTok.
We have compiled a list of big social media networking platforms that debuted in and reigned in the last decade, and a list of platforms that succumbed under pressure. Some of the platforms that died saw significant highs at the beginning, only to be shut down years later. This list is filled with nostalgia, heartache, and is a nagging reminder to a massive life reality check – nothing lasts forever.
Instagram
Instagram is one of the biggest social media platforms in the world right now. The image-sharing app was launched in 2010 by creators Kevin Systrom and Mike Krieger, and was acquired by Facebook in 2012. It enjoys over one billion monthly active users, and has 500 million users who use Instagram Stories every day. The app was also the second most downloaded free app on the App Store in 2018 (2019 stats still not available). Instagram allows users to share photos and videos, lets you follow friends and influencers, and even post 24-hour snippets called Instagram Stories. Currently, Instagram competes with Snapchat and TikTok in the social networking space.
Snapchat
Snapchat arrived at a time when Facebook and Twitter were already extremely popular, and Instagram was gaining momentum as well. Launched in 2011 by Evan Spiegel, the photo and video sharing app now enjoys 210 million daily active users (as of October 2019). Snapchat played on the idea of disappearing messages, something that wasn’t tapped into before. This feature has since been aped by Facebook in all of its properties – including WhatsApp and Instagram.
Telegram
Telegram is essentially a WhatsApp alternative, and has grown quite a bit of fan following since its launch in 2013. As of March 2018, the app enjoys 200 million monthly active users, and Telegram gets new features regularly via updates. It competes directly with WhatsApp that has taken the instant messaging world by storm.
TikTok
Having launched in 2017, TikTok is touted to be the fastest growing social media app out there. It has almost 500 million active users, and was the third most downloaded app in Q1 2019 with 188 million downloads. This is 70 percent growth from Q1 2018. The app looks to fill the void that Vine left, but it offers a lot more. Influencing creators on TikTok are considered celebrities, and it is well on its way to world domination. The latest data from App Annie suggests that TikTok is continuing its explosive growth around the world, with the insights company ranking TikTok just behind Instagram in terms of monthly active users through the third quarter of 2019.
Pinterest
Founded in 2010, Pinterest offers online discovery of information in the form of images, GIFs, and videos. As of August 2019, the platform has reached 300 million active users. Over time, the platform has attracted over 200 billion Pinterest pins, and over 4 billion Pinterest boards. Interestingly the gender parity is quite large, and 70 percent of Pinterest users are females.

Over time, Pinterest has attracted over 200 billion Pinterest pins
Tinder
Tinder, a unique dating app, was welcomed with open arms. Launched in 2012, it has now become quite popular amongst teenagers. Recent user statistics are not known, but a 2018 report states that over 57 million people use Tinder around the world, out of which 4.1 million Tinder subscribers pay for a premium Tinder Plus and Tinder Gold. Furthermore, Tinder is used in 190 countries, and is available in 40 languages.
Quora
If you’re looking for answers, Quora is possibly the place to go to. From questions like ‘Which is the best way to learn programming?’ to questions like ‘Which is the best country to migrate from India and start a new life?’ – all of these are answered in detailed manner by varied users. This platform was launched in 2010, and is now a pool of some great answers. Quora’s userbase is constantly growing. It grew from 200 million monthly active users in 2017 to 300 million monthly active users in 2018.

Quora was launched in 2010, and is now a pool of some great answers.
Facebook Messenger
Facebook Messenger was introduced as a separate app by the social giant in 2011, forcing users to download the app from the app stores if they wished to continue chatting to their Facebook friends. While user base stats of the app are not known, Facebook last year introduced AI bots for businesses to chat with clients easily.
Mastodon
Mastodon, an open source decentralised social networking platform, is fast gaining popularity. Touted to be an alternative to Twitter, the Mastodon community has grown to over 2.2 million people. Unlike Twitter, where one corporation has full control over the rules and regulations, any user can create their own server of Mastodon and manage it.
Twitch
Twitch is a live video streaming platform that was launched in 2011 and is prominently used for gameplay streaming. It is particularly famous in the US, and as of 2018, it enjoys 2.2 million broadcasters monthly and 15 million daily active users. The platform is owned by Amazon. As of October 2019, Twitch owns 75.6 percent of the streaming market, and YouTube is second with 17.6 percent.
Periscope
Periscope is also a live streaming app that was launched in 2015 by Twitter. The successor of Meerkat, Periscope has managed to stand its ground in a space where many have faltered. Twitter doesn’t reveal usage stats of Periscope.
Minds
Minds was launched in 2015, and it essentially runs on the same principle as Mastodon. The open source network rewards its users with tokens for their contribution and engagement. As of March 2018, Minds has over 1.25 million registered users and 105,000 active users.
Helo
Helo is a newly launched social media app made for the vernacular speaking audience. The app has seen a sharp rise since 2017, and it has 50 million active users in India alone. While traditional social media apps are available in the universal language of English, Helo tries to offer solace to the large vernacular speaking audience. The app supports 13 Indian languages.
ShareChat
ShareChat follows the same principle as Helo, and taps into the vernacular speaking audience as well. The Indic language-based social network ShareChat app has been growing steadily over the last two years. Launched in 2015, the app is now touted to be India’s largest vernacular social media platform with nearly 60 million users. ShareChat has some big investors like Xiaomi and Twitter, and latest round of funding was led by the latter. The Bengaluru-based chat app startup is today valued at over $600 million.
WhatsApp
Wondering why WhatsApp is at the bottom of this list? Because, it was launched in the latter part of 2009 missing this decade by a few months. While this list is all about the social media platforms that launched and grew in this decade, we couldn’t leave out WhatsApp as its evolution began in this decade, changing the digital social landscape of today. The app became the world’s most popular messaging app in 2015, and as of February 2018, it enjoys more than 1.5 billion users worldwide.

As of February 2018, WhatsApp enjoys more than 1.5 billion users worldwide.
Google+
Google+ was launched with a lot of promise in 2011, but succumbed to the competition from Facebook and others. The final nail on the coffin was a major security issue that was reportedly discovered, compelling Google to shut down Google+ in April this year. The company also claimed that its social platform wasn’t experiencing enough usage or engagement from its users with most sessions maxing out at 5 seconds.
Orkut
Orkut was a household name in India in the latter part of the last decade, but the growing popularity of Facebook got users to migrate from Orkut, leaving it no option but to shut down in 2014. Owner Google said that other platforms had outpaced Orkut’s growth, and the website no longer exists. Google then pegged its hope on Google+, but sadly, that platform also fell off the shelf this year.

Orkut was shut down in 2014 by Google Photo Credit: TheNextWeb
BlackBerry Messenger
BlackBerry Messenger also shut shop earlier in May this year, blaming the difficulty of bringing new users to BBM as one of the top reasons. BBM was one of the most loved instant messaging applications of its time, but its popularity dwindled as competing chat apps like WhatsApp and Facebook Messenger gained momentum.
Vine
In 2016, Twitter announced that it was shutting down Vine, a popular video loop app that offered users the ability to make and share six second videos. The app couldn’t compete with the rising popularity of Instagram, and users who were once considered as Vine celebrities started posting videos on Instagram instead. Instagram can be considered as a big reason why Vine became obsolete.
Yahoo Messenger
If you’re a 90’s kid, there are high chances that you’ve used most of the apps mentioned on this grim list. While these apps don’t exist today, they were once an integral part of our online social life. Yahoo Messenger was once such instant messaging app that died last year. In its prime years, the service was the most used as it was an alternative to emails and SMS messaging. However, with the arrival of smartphones, Facebook, and eventually WhatsApp – Yahoo Messenger lost its steam and users started to switch.
Path
Initially launched in November 2010, Path social platform served as personal journal of sorts that you could share with your family and friends. This platform gained over a million users once, but eventually died in 2018 due to lack of proper growth and increasing competition.
iTunes Ping
Apple’s promising iTunes Ping social network failed to gain traction that it had hoped from the users. The music-based social network was launched in 2010, and was shut two years later. It is one of the biggest examples of Apple having difficulty in getting people to use its web-based services.
Meerkat
Meerkat, the once popular live-streaming app, closed in 2016. It was early on the scene by launching a live-streaming service ahead of Twitter and Facebook, but its fame was short-lived.
Yik Yak
Yik Yak was an anonymous messaging app for college students that shut shop in 2017. The app rode to popularity after its launch in 2014, but soon became a breeding ground for hate speech, cyber bullying, discriminatory speech, and gun and bombing threat, all under the garb of anonymity. The company tried to bring in measures to curb the slur, while also maintaining anonymity, but it then started to lose user base, and had to wind down operations eventually.
Friendster
Friendster was one of those social networks that helped kick off the social media era. It was founded in 2003, and soon lost credibility due to technology issues. There were problems in feature launches, and it soon drifted into irrelevance as Facebook gained momentum quickly. Interestingly, in the early days, Friendster investors reportedly had approached Facebook with an acquisition deal, which Mark Zuckerberg then refused. Zuckerberg later bought Friendster’s entire portfolio of social networking patents for reportedly $40 million. Friendster closed its doors on 2015.
Friends Reunited
Friends Reunited, another pioneer in the social media industry, announced that it would be winding down in 2016. The platform was launched in 2000, but couldn’t keep up with the likes of Facebook, Twitter, and Instagram. In its closing announcement, the company’s founder Steve Pankhurst said, “It is clear that the site is no longer really used for the purpose it was built for … therefore, it is with a heavy heart, that we have decided to close the service down.”
Pheed
Pheed was launched in 2012, and the social platform let you share texts, photos, and videos, just like the others. It managed to top the App Store charts in the social networking category in just a year after launch. Aimed at teenagers, it failed to gain the long-term momentum it hoped for. Pheed was sold to American Movil in March 2014, and in April 2016, Pheed was shut down and the technology was integrated to América Móvil platforms.
DailyBooth
DailyBooth was a social network that allowed users to take a picture of them every day, and post it with a caption. The website would in turn generate a little flip book style video for its users. While the concept was intriguing, it never truly broke through to the mainstream, and had to close down in 2012.
Tbh app (Facebook-owned)
Tbh app, another anonymous social app, was launched in 2017, and in just a month it managed to rank number one in the US App Store. It was acquired by Facebook soon after, but its fame was extremely short-lived, as the social giant announced its discontinuation in July 2018 due to low usage.
Eons.com
Eons.com was yet another social networking site founded in 2006, and this one tried to cater to the baby boomers and users over the age of 40. The site was shut down in 2012, after a business issue with the service provider was not resolved. To this date, the site remains shut.
0 notes
Text
TipJar Shuts Down as Cryptocurrency Market Slows
Cryptocurrency micropayment service TipJar is shutting down in Q1 2020 due to low usage, developers have confirmed.
Cryptocurrency Tipping Fails To Catch On
In a Reddit post on October 6, user u/doppio requested users withdraw any remaining funds held on their accounts.
TipJar’s Reddit bot for automated payments will stop functioning immediately, he said, with the website to follow “in six months.”
“I had a great time creating this service, and it was fantastic seeing all the engagement when it was being used actively, but lately there has been very little activity on the bot,” the post explained.
“I have been paying the monthly server fees for several years, and although they are pretty minimal, at this point it doesn’t make much sense for me to continue putting money into the service when it’s going unused.”
TipJar used Ethereum to offer micropayments on social media in various cryptocurrencies. Born in 2017, the service saw the considerable decline in altcoin markets continue for most of its existence.
u/doppio added he was considering making TipJar’s code open source once the shutdown was complete, something users had long requested.
“I have been asked a lot about making the code open-source, which I have been hesitant to do before doing a more rigorous analysis of the system’s security, but I would be happy to make the code open-source when the service is no longer running,” he concluded.
ChangeTip Showed Tough Market Challenges
Cryptocurrency tipping gained considerable attention when the concept first hit the mainstream several years ago. Nonetheless, it appears TipJar’s experience – the gap between real use versus approval of the idea itself – is not new.
In 2016, fellow tipping service ChangeTip also disappeared. At its height, the tool made frequent appearances on Reddit in particular, and even raised $3.5 million in a seed funding round.
A subsequent staff takeover by Airbnb left the crypto aspect with less interest, leading to the decision to halt activities.
In its lifetime, ChangeTip processed around 350,000 transactions. Zapchain, another tipping platform, followed at the same time.
TipJar’s demise meanwhile comes at a time when investment preferences are shifting away from Blockchain technology to businesses dealing specifically in Bitcoin.
As Bitcoinist reported, so-called ‘blockchain-not-bitcoin’ funding has decreased 60% in 2019. At the same time, other once-popular crypto fundraising methods such as initial coin offerings (ICOs) have also fallen by the wayside.
What do you think about cryptocurrency tipping? Let us know in the comments below!
Images via Shutterstock
The post TipJar Shuts Down as Cryptocurrency Market Slows appeared first on Bitcoinist.com.
from Cryptocracken Tumblr https://ift.tt/2Itt0gI via IFTTT
0 notes
Text
Week07 - “Something Awesome” Final Update
In this final update for my “Something Awesome” project I will be going over three different ways (Macros, DDE, Fake Website) of attacking the target through phishing emails. Within these I will give a brief description of the exploit, an example of the exploit being used in the real-world, and my own “less malicious” version of the exploit showing how it could be used.
Macros
A macro is a series of commands and instructions that you group together as a single command to accomplish a task automatically. They are often used to automate frequently used tasks. However macros can also be used maliciously and is a common (yet easy to avoid) way of transmitting malware via phishing scams. The key to successful macro scams is in the social engineering aspect of the phish.
Real-world example:
The Melissa Virus (https://en.wikipedia.org/wiki/Melissa_(computer_virus))
The phishing email came with a message like: “Here is that document you asked for, don't show it to anybody else." Once opened, the virus replicated itself and sent the same email out to the top 50 people in the recipient's Outlook e-mail address book. While it did not destroy files or other resources, Melissa disabled email systems due to the ripple effect of spam email, including Microsoft who shut down incoming e-mail until the virus was reigned in.
Here is the virus code for anyone interested: https://packetstormsecurity.com/files/12131/melissa.macro.virus.txt.html
Writing my own macro based “malware”:
1. Create a new macro in the macro menu inside word
2. Write your macro
runs when document is opened
executes calc.exe
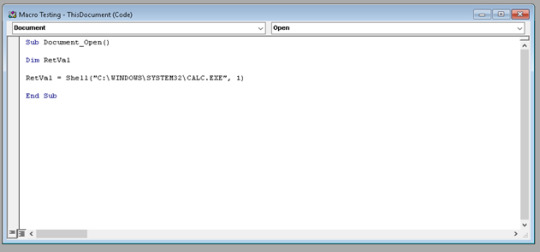
3. When someone opens a document with macros they will get this warning (relies on effective social engineering in the phishing email to deceive the target into clicking “Yes”).
4. Windows Calculator is opened by macro.
DDE
Microsoft’s Dynamic Data Exchange (DDE) is a protocol designed to allow the transportation of data between MS Office applications. DDE allows the execution of embedded code once a victim opens such a file, without the authorisation request associated with macros (won’t get picked up by anti-virus).
Note: this exploit was rendered somewhat useless when Microsoft released a patch following the exploit https://docs.microsoft.com/en-us/openspecs/office_standards/ms-oi29500/4fe6d033-f0d4-4d73-ac81-a7128522c5ff
However not all versions of Word received the update and users can still re-enable DDE. Since many people still rely on legacy applications, an attacker may still be able to exploit DDE in Word (also in Excel and Outlook).
Real-world Example:
Both these examples highlight how DDE has been used to maliciously phish in the real world. However it also shows how easy it is to avoid being infected by DDE exploits, as you have to click through at least 2 warning screens before anything malicious can occur like macros (though many people do click through warnings without reading them).
https://isc.sans.edu/forums/diary/Necurs+Botnet+malspam+pushes+Locky+using+DDE+attack/22946/?source=post_page---------------------------
https://isc.sans.edu/forums/diary/Hancitor+malspam+uses+DDE+attack/22936/?source=post_page---------------------------
Writing my own DDE Exploit:
1. Insert field
...
2. Write desired code
This executes calc.exe again
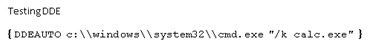
3. Target gets two prompts (again good social engineering is needed)
Second prompt would scare off many targets but can be hidden as shown here: https://twitter.com/ryhanson/status/917820530975223809?lang=en
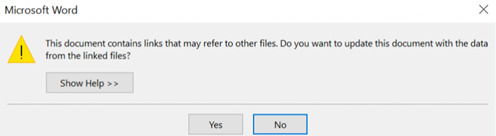
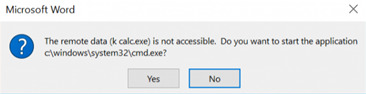
4. Calculator is launched

Fake login page
Fake login pages are a classic example of how hackers steal their targets data and is a very common phishing method. The hacker will either attach an html document or will make their own website with a spoofed url similar to the real login page.
Real world example:
A bit of an outdated example as Facebook has since changed the format of their login page slightly but I think it effectively shows how this method can trick people.
Real login:
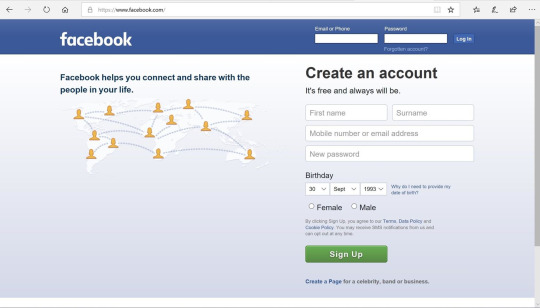
Fake login (taken from http://ankitsingh24.blogspot.com/2017/04/phishing-hack-fbamezonflipcart-phishing.html):
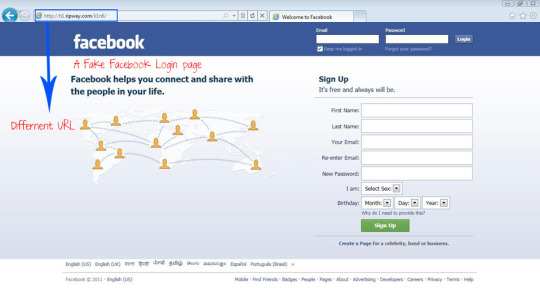
We see here that unless the target was very familiar with the layout of the Facebook login page or looked at the url (but who does that??) they would likely be tricked due to how legit the fake page looks.
Recreating my own fake login page:
For this exploit I will be recreating the old Google login page so that I can hypothetically steal the login details of Google users by sending them to my phony sign in page via a phishing email. Through this I may also be able to access many other accounts owned by the target as most people use the same password across platforms.
Here is the actual Google login page:
And here is my recreation:
It looks a little shabby and less refined than the actual Google login page (and doesn’t actually do anything) but I’m not a professional software engineer so there’s that. Either way most people are so used to not getting hacked that they would blindly enter their details anyway (if the phishing email was good). Once they’ve done this I can reroute it to my server and use this to maliciously access their account.
If anyone is interested here is the html and css for the site:
0 notes
Text
Aavgo security lapse exposed hotel bookings
A security lapse at a hotel management startup has exposed hotel bookings and guests’ personal information.
The security lapse was resolved Monday after TechCrunch reached out to Aavgo, a hospitality tech company based in San Francisco, which secured a server it had left online without a password.
The server was open for three weeks — long enough for security researcher Daniel Brown to find the database.
He shared his findings exclusively with TechCrunch, then published them.
Aavgo bills itself as a way for hotels to organize their operations by using several connected apps — one for use by guests using tablets installed in their hotel rooms for entertainment, ordering room service and checking out, and another for staff to communicate with each other, file maintenance tickets and manage housekeeping.
Several large hotel chains, including Holiday Inn Express and Zenique Hotels, use Aavgo’s technology in their properties.
The database contained daily updating logs of the back-end computer system. Although most of the records were logs of computer commands critical to the running of the system, we found within personal booking data — including names, email addresses, phone numbers, room types, prices, the location of the hotel and the room and the dates and times of check-in and check-out.
There was no financial information in the database beyond the credit card issuer.
The database also contained room service orders, guest complaints, invoices and other sensitive information used for accessing the Aavgo system, the researcher said.
Many of the records were related to its corporate hotelier customers.
One of those customers included Guestline, a property management company for hoteliers, which uses Aavgo as the underlying technology for its property management system. Guestline says it facilities 6.3 million bookings a year.
When reached, Guestline’s data protection officer James Padkin said data protection is of “paramount importance” and the company has “ceased our very limited trial of the AavGo housekeeping app.”
After the company failed to respond to the researcher’s initial email, Aavgo shut down the database a few hours after TechCrunch made contact with its chief executive, Mrunal Desai.
“We had no data breach; however, we did find a vulnerability,” said Desai. He said data on 300 hotel rooms was exposed. Brown said based on his review of the data, however, that the number is likely higher. Desai added that the company has “already started informing our customers about this vulnerability.”
Midway during our correspondence, Desai copied the company’s outside counsel, a Texas-based law firm, which threatened “immediate legal action” ahead of publishing this report.
Aavgo becomes the latest hospitality company embroiled in a hotel-related security incident in recent years.
In 2017, hotel booking service Sabre confirmed a seven-months long data breach of its SynXis reservation system, affecting more than 36,000 hotels globally and millions of credit cards.
A year later, Marriott-owned Starwood admitted a breach that affected up to 383 million hotel guests around the world. Earlier this month U.K. authorities said they would fine the company $123 million for the breach under the new GDPR regime, which affected about 30 million customers in the European Union.
Read more:
Millions of Venmo transactions scraped in warning over privacy settings
An unsecured SMS spam operation doxxed its owners
Samsung spilled SmartThings app source code and secret keys
Security lapse exposed a Chinese smart city surveillance system
A leaky database of SMS text messages exposed password resets and two-factor codes
We found a massive spam operation — and sunk its server
Dow Jones’ watchlist of 2.4 million high-risk individuals has leaked
Robocaller firm Stratics Networks exposed millions of call recordings
Massive mortgage and loan data leak gets worse as original documents also exposed
0 notes
Text
Shopify Upside Potential Grows as Moat Strengthens
Date Published: 2017-06-12 Written by Ophir Gottlieb * This is a snippet from a CML Pro dossier originally published on 6-3-2017. SHOPIFY INC (US) (NYSE:SHOP) Shopify Inc (US) (NYSE:SHOP) continues to strengthen its upside potential by building its moat. Shopify Inc is one of our favorite Top Picks with great upside potential. But, that upside potential is clear to everyone, which means competition may come, it may be fierce, and it means the stock price reflects that upside potential. Shopify Inc doesn't have to be good, it has to be knock down drag out great for the stock to keep heading higher. Having said that, yeah, we believe it will be just that. Shopify Inc was added to Top Picks on 22-Mar-16 for $66.50. As of today it is trading at $89, up 34% since being added to the portfolio. Even further, we were jumping up and down on May 3rd, 2017, when we wrote Shopify Delivers — Promoted to Spotlight — Upside is Still In Play. The company had just crushed earnings and was trading at $81.72. In the one month since that dossier, Shopify Inc is up an additional 10%.
Ticker Date Added Price Added Return SHOP 03-22-2017 $66.50 34%
The bullish thesis for this company is so compelling we dare not even begin to speak of it in any kind of shortened way and instead refer you to the Top Pick dossier: Shopify is the Pick-Axe to the E-commerce Gold Rush UPDATE In the midst of this second run after earnings, Shopify Inc actually sold more than half a billion dollars worth of stock in an equity offering to boost its cash balance. The market did not like that news at first glance, but since has decided there was good reason for the raise and the run has continued. All can be forgiven when a company grows revenue at 84% (TTM) year over year with subscription solutions up 60% and merchant solutions revenue up 92%. But, the news that may also have turned the market back to bullish surrounds yet another business line that the company is pursuing. First we take a step back and look at the growth in charts. We start with revenue (TTM):
Revenue (TTM US$ Millions) for Shopify was $444 million. Last year it was $241 million, which is an 84.5% one‑year change. The company is also driving positive cash from operations:
But, let's not lose sight of some other realities. The company has not turned a profit and appears nowhere near:
But here's the reality we are watching. There was a point in Shopify's early days that it was a foregone conclusion that Amazon.com would simply crush the company. It turns out that the mighty Amazon is in fact not only unable to crush the new comer, but has succumb, and is now a major partner. Even further, Amazon shut down its "Webstore," which would have been the direct competitor to Shopify Inc. The partnership with Amazon then, in a total reversal of fortunes, gave Shopify Inc a moat against its smaller peers. The history is magnificent. Now we have more updates from Shopify Inc: APPLE, SHOPIFY, GAMING On May 25th of this year we learned that Shopify Inc released a new software development kit (SDK) called Unit Buy, giving game makers the ability to add support for sales of physical goods within a game. This move comes on the back of a reality in the gaming business that e-commerce is now a legitimately new market for them to drive revenue. Here's a snippet from a nice article written by Shoshanna Delventhal for Investopedia.
Unit Buy gives players the in-game option to buy branded products related to the games they are playing—like ordering from a traditional retail store, but without the requirement of leaving the game. It’s a win-win for convenience-loving game enthusiasts and entertainment companies increasingly benefiting from a rise in recurring revenue and in-game purchases over traditional sales from new game downloads. Source: INVESTOPEDIA
*The new SDK will integrate with Apple Pay and will work across mobile, console and PC platforms. And then there's more... CREDIT CARD READER On April 20th we learned that Shopify Inc announced its own credit card reader. Here are the press release highlights, with analysis to follow:
[April 20th, 2017] today announced its new free Chip and Swipe card reader for in-person selling. With Europay, MasterCard and Visa (EMV) support, the new Chip and Swipe reader lets any Shopify merchant in the United States sell offline in a fast and secure way. The card reader was launched at Unite, Shopify’s annual partner and developer conference.
And here are some the features: * Supports Visa, MasterCard, American Express and Discover. * Integrated with the Shopify ecosystem. * No charge for new and existing Shopify merchants without a Shopify POS solution; retails for only $29 USD in the Shopify Hardware Store. So, why do we care? This is subtle, but Shopify Inc is becoming the Alpha and Omega for small businesses which often times have to piece together various technologies to make their online and brick-and-mortar stores work. It becomes a tiresome, confusing and costly amalgamation of technologies, each of which is a point of failure, and worse yet for Shopify Inc, a potential competitor. Now, with its first ever in-house made hardware, "any of our merchants can use Shopify to power every aspect of their business, at every interaction" (Craig Miller, Chief Product Officer). When we combine this reader with Shopify Pay, that messy, multi-pronged process has been eliminated. "With Shopify Pay, Shopify says it has whittled down the number steps required for checkout from 16 to two. Among the merchants who've tested the feature, Shopify Pay has increased checkout speed by 40 percent" (ZDNET). Friends, we love this move, and remind everyone how much this deepens Shopify's moat. At this point, merchants are totally beholden to Shopify when we consider the data storage, payment processing, store hosting and avenues it opens up with Amazon. It's a shrewd move and one that does make this company more valuable. We maintain our Spotlight Top Pick on Shopify Inc, and while we note rather urgently that the market is getting toppy, in the long-run, Shopify has a long way to go, while also noting the risks of execution and competition. The author is long shares of Shopify Inc at the time of this writing. WHY THIS MATTERS It's finding the technology gems, like Shopify, that can turn into the 'next Amazon,' or 'next Apple,' where we have to get ahead of the curve. This is what CML Pro does. Each company in our 'Top Picks' has been selected as a future crown jewel of technology. Market correction or not, recession or not, the growth in these areas is a near certainty. The precious few thematic top picks for 2017, research dossiers, and alerts are available for a limited time at an 80% discount for $19/mo. Join Us: Discover the undiscovered companies that will power technology's future. Thanks for reading, friends. Legal The information contained on this site is provided for general informational purposes, as a convenience to the readers. The materials are not a substitute for obtaining professional advice from a qualified person, firm or corporation. Consult the appropriate professional advisor for more complete and current information. Capital Market Laboratories (“The Company”) does not engage in rendering any legal or professional services by placing these general informational materials on this website. The Company specifically disclaims any liability, whether based in contract, tort, strict liability or otherwise, for any direct, indirect, incidental, consequential, or special damages arising out of or in any way connected with access to or use of the site, even if we have been advised of the possibility of such damages, including liability in connection with mistakes or omissions in, or delays in transmission of, information to or from the user, interruptions in telecommunications connections to the site or viruses. The Company makes no representations or warranties about the accuracy or completeness of the information contained on this website. Any links provided to other server sites are offered as a matter of convenience and in no way are meant to imply that The Company endorses, sponsors, promotes or is affiliated with the owners of or participants in those sites, or endorse any information contained on those sites, unless expressly stated.
3 notes
·
View notes
Photo

Reydar Month 2017: Love in Unexpected Places
hack:
verb, used with object:
7. a) to modify (a computer program or electronic device) or write (a program) in a skillful or clever way; b) to circumvent security and break into (a network, computer, file, etc.), usually with malicious intent.
Bingo squares used: hacked, where’s my muffin, glasses, ship
Hacked: Chapter One by @politicalmamaduck
“Matt? Matt. Your presence is requested in the Situation Room at once. It’s an emergency, Matt. We haven’t got all day.”
Kylo Ren resisted the urge to growl at the poor lackey, and forced himself to remember that at the moment, he was not Kylo Ren. He was Matt, a lowly radar technician, and of course these pathetic fools would demand his presence if something went wrong. Despite his hatred and disdain for the menial work, he was good at his job, something for which he prided himself. Not only was he an adept Force user, powerful fighter, excellent starpilot, and language master, he was also damned good at repairing and maintaining computer systems.
He made his way down to the control room of the Finalizer before heading off to the Situation Room. Everything appeared to be in order there; no incompetence had left a cable loose or a unit turned off. He did not hurry to the Situation Room. He resented being ordered around, no matter his name or guise. He might have been pretending to be Matt at the moment, but underneath his wig and glasses he was still Kylo Ren.
When he arrived, there were all manner of First Order officers scrambling around with their comm units, lights and signals blinking, and automated voices squealing.
“Something is wrong with the network,” a slightly less frazzled looking tech sergeant said to him, gesturing at a datapad in his hand. “It appears that a pernicious virus has infiltrated the system. We’re having trouble locating the source, but we’re working on it. In the meantime, all HoloNet connections need to be shut down, and comms turned off. We have got to figure out who is behind this cyber attack, and why.”
“How could someone infiltrate our network with a virus?” Kylo practically growled at the tech, then remembered he was supposed to be Matt right now. Matt was awkward, and not as openly and obviously angry all the time the way Kylo was. It was a difficult lesson in patience and masking things in the Force. Kylo was not entirely sure whether being Matt was more or less stressful than being himself.
“We’re not entirely sure yet, but we think it might have been in a personal comm attachment. A phishing scam of sorts. You know, you open something and it’s not what you thought it was,” said the sergeant, his eyes swiveling back and forth rather than looking directly at Matt and tugging on his collar.
“Stop making excuses for this idiocy. I know how phishing works, and if that’s what happened, we need to get the Technology department to fix the system so it can’t happen again! And you need to educate these pathetic fools about personal communications using First Order resources.” Kylo stopped, realizing he probably should not have said so much. The sergeant looked taken aback, but at a Force-laden gesture from Kylo, nodded.
“Yes, of course. We’re working on identifying the problem as fast as we can, as well as attempting to isolate it and repair the network. In the meantime, could you give us a hand?”
All Kylo could do was nod grimly. If confidential First Order data had been leaked, there would be a reckoning worthy of all nine Corellian hells.
…
At the command center of the Resistance base, a cheer went up as computer screens started to register large data uploads and file transfers.
“We did it! Someone clicked on the comm!” A resounding cheer and round of applause followed.
“Way to go, Finn. Thank you so much for your help,” a tech officer said, approaching the former Stormtrooper who was positioned in the back of the room, watching the large overhead screens. Poe Dameron had his arm around him, watching with a satisfied smile.
“No problem,” said Finn. “I knew someone would fall for it. Stormtroopers are desperate for entertainment, for something outside the routine.”
“More than one someone,” Officer Lodja said with a smile, gesturing at a datapad in her arm. “We got one hit on the cat video, another on the ‘Which Famous Podracer Are You?’ personality quiz, and one on the Dejarik betting site.”
“Wow, that’s great! You all really did a wonderful job creating those comm messages and attachments. I’m so glad it worked,” Finn said, smiling at her.
“Thank you, Lieutenant. Now we wait and see how much data we can obtain before they’re able to stop the virus’s spread.”
“Hopefully some of it proves worthwhile,” said Poe, nodding at Officer Lodja. She smiled back before returning to her station.
Clapping Poe on the back, Finn headed out of the command center towards the mess. Rey usually took a meal at about this time, and he wanted to tell her of their great cyber success.
…
Back at the Finalizer, Kylo Ren was frantically typing away into a datapad, trying to get at the root files embedded in the main server providing secure HoloNet connections for the First Order’s officers and personnel aboard the ship. As Matt the Radar Technician, he typically worked on the physical hardware rather than the software maintaining the delicate technology, but desperate times called for desperate measures. And the tech officers couldn’t know it, but his administrative clearance codes were providing some help as he was able to get past the system’s firewalls and restricted access.
It was painfully slow going, however, as every time he would complete a line of code something would happen to stymie him, whether the system’s own protective measures or the damned virus infecting the system.
Whoever did this is going to pay dearly, he thought. He would have loved nothing more than to be taking out his rage on some training droids in a quiet practice room, but gritting his teeth and furiously typing code would have to do for now. Being Matt was teaching him much about patience and waiting for the right moment, as much it made him want to boil over with rage. He didn’t always agree with his Master, but Kylo had to admit he was wise.
After glaring so hard at his computer screen that his brow appeared permanently creased, he finally created himself an access point. Looking at the system’s root files, he could see the virus’s effects. Nearly 69% of the files had been corrupted, and were being uploaded to an external host. He forced a system shutdown, then began eradicating the virus, one file at a time. It was even more torturously slow going than trying to obtain access to the virus in the first place.
“The virus has stopped spreading,” reported the sergeant to the assembled team. “We must remove it from all affected files and determine how it was able to infect our systems in the first place.”
“Already doing that,” muttered Kylo. “And you’re kriffing welcome.”
It had already been a long day. Thank the Force he only had three hours left as Matt. He would not be returning to his alternate persona for quite some time. Let the idiots whose job it was solve the disaster, and do what he was born to do: use the Force.
He sighed, pushed his glasses up the bridge of his nose, and continued to repair and delete files.
…
“Hey, where’s my muffin?” Finn asked playfully as he sat down across from Rey. She cocked her head towards the snack counter as she chewed, rolling her eyes at Finn.
“Go get one,” she said, around a mouthful of blueberry muffin.
“I thought we were supposed to be friends,” Finn moaned, reaching towards the remainders of Rey’s muffin.
“Hey kids, sorry to interrupt. But we’re going to need some help at Command,” said Poe, while approaching their table. Rey nodded, and shoved the last bites of muffin into her mouth as she got up. Finn smiled at Poe, putting his arm around his shoulders and following Rey to the command center.
Officer Lodja greeted them warmly as they arrived, but Rey could tell she was nervous. Her smile was slightly strained, and her grasp on her data pad was particularly tight.
“It seems someone in the First Order has been able to isolate and start removing the virus,” she began. “We were still able to download much of their data, but we didn’t have as much time as we thought we would.”
“That must have been a very talented slicer,” Finn said. Officer Lodja nodded.
“Yes, it seems so,” she said. “We got almost everything we needed about how they built Starkiller, their training facilities, and weapons caches, but the files on the extent of their fleet and personnel are woefully incomplete. We need to be able to access the mainframe data hub on the Finalizer for the virus to continue spreading past what they’ve been able to stop and block. Would you be willing to take a team undercover and infiltrate the Finalizer, Finn? I know this is asking a lot. But you know the ship so well and could blend in much more easily than someone who’s been with the Resistance their entire life.”
Officer Lodja breathlessly looked up at Finn, seemingly imploring him with her dark doe eyes.
Only General Organa had been able to resist the tech officer with that look on her face, and Finn was no exception.
“I’ll do it, Officer,” he said.
“And I’ll go with him,” Rey said immediately. “He’ll need protection, and I can use the Force to help us along.”
“Thank you both,” said Officer Lodja. “And may the Force be with you.”
#reydar month 2017#reylo fanfiction anthology#reylo#reydar#matt the radar technician#kylo ren#rey#my writing#my moodboards
15 notes
·
View notes
Text
Capcom reminds us why “games-as-a-service” suck, announces end of Puzzle Fighter

Enlarge / RIP Puzzle Fighter, 2017-2018. (credit: Capcom)
The games-as-a-service graveyard grew one larger this week, as Capcom's Puzzle Fighter reboot received an official "sunset" announcement on Friday. The iOS and Android port of the '90s puzzle series will have its in-game store shut down on Monday, April 23, and its servers will follow suit on July 31—meaning the game will have been playable for only eight months after its late-November launch.
That's because the new, free-to-play Puzzle Fighter includes an always-online requirement so that players can be subjected to the timers and loot-box systems applied to both its single-player and multiplayer modes. Capcom's announcement did not in any way hint to a patch that would let the game work in a wholly offline mode, nor did it hint to any open-sourcing of its content so that dedicated players could, say, prop the game's bones up via DIY servers.
Friday's announcement also didn't reference the fact that this game's reboot recently received PEGI ratings (Europe's equivalent of the ESRB) for PC and consoles. And the language here doesn't give us much hope for a non-mobile port of the Columns-like, match-gems puzzle update. Instead, the post blames the mobile version's cancellation on Capcom Vancouver "dedicating its focus to our flagship Dead Rising franchise."
Read 3 remaining paragraphs | Comments
Capcom reminds us why “games-as-a-service” suck, announces end of Puzzle Fighter published first on https://thelaptopguru.tumblr.com/
0 notes