#ipv5
Explore tagged Tumblr posts
Note
alright Specs, here's your time for more IT stuff
your rambles always bring joy, and I can't wait to see what you talk about next. info dump away, my friend<3
-anon
The reason you have one of those 3 IP addresses - 10.x.x.x, 172.x.x.x, and 192.168.x.x. - whether you use a VPN or not, is because sometime around the turn of the century, we ran out of IPv4 addresses. This is partly due to the dot com bubble, partly due to, apparently, bots snapping up gibberish URLs, and I believe partly due to IP phones (introduced in IPv5, the often unheard of IP standard). None of this is to speak about IPv6, which means all of your devices have at least 2 IP addresses
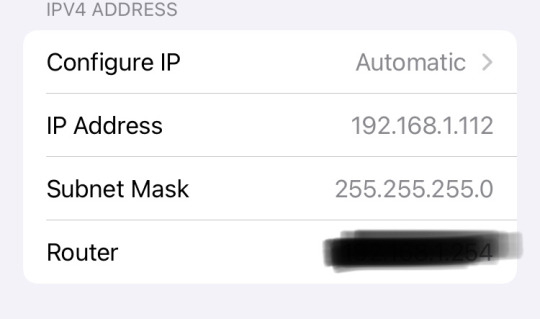
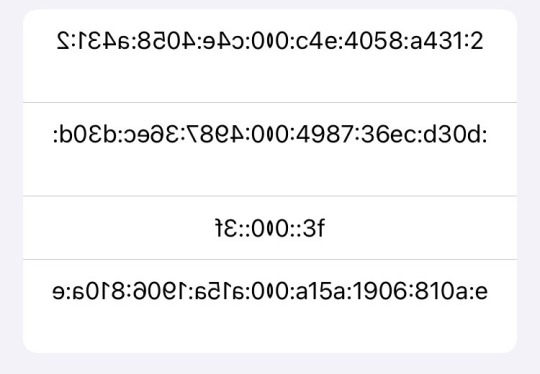
Here are the private IP addresses for my phone. No I do not know why I have 4 IPv6 addresses on my phone.
You’ll notice I blocked out the IP address for my router, but the more I think about it the more I realize that was unnecessary. Partly because I use a VPN, but partly because the router also has a private IP address, and that’s what I blocked out.
There’s a chance that if you were to go into your device’s settings and looked at the IP address, you would have the same IP address as my phone, perhaps even the same subnet (a topic for another talk about IPs). So why, you may be wondering, don’t I see your traffic?
Because your router also has two IP addresses.
Welcome to the world of network address translation.
That’s all the time we have for today, please send another compliment so I can talk more about IP addresses
ETA: I decided to edit the image of my IPv6 addresses because I don’t know as much about IPv6 as I do about IPv4 and those addresses might have given out location info. The edit I applied was a mirroring effect, which obscures half the information but gives the necessary details about IPv6. Namely, that it’s different from IPv4, is much longer than IPv4, and contains letters, numbers, and colons
1 note
·
View note
Text
Why don't we just compromise and use IPv5?
1 note
·
View note
Text
Bundeswehr-Deutsch, Deutsch-Bundeswehr
Deutsch: Geheimbünde Bundeswehr: Terroristische Vereinigung des ursprünglichen Funker-Terrorismus's
Deutsch: Verzauberte Hände Bundeswehr: Verfunkte Hände
Deutsch: Magie die passierte Bundeswehr: Wer über Magie spricht ist wahnsinnig.
Deutsch einiger Frauen: Er hat mich verhext (vermutlich erste Kollision, mit Funker-Zauberei, als Kampf-Kunst-Form anerkannt wäre Hokus-Pokus, in dem Falle, wahrscheinlich Break-Images gesendet)
Bundeswehr: Die einigen Frauen sind Schizophren.
Deutsch: Zauberei gibt es. Bundeswehr: Zauberei ist ein Ammenmärchen.
Herr Guder, Gerhard Sebastian: Wenn Hokus-Pokus, anerkannte Kampfkunst ist, der Ninjas, beider Stile, was ist dann, bitte Wahnsinnig und was für eine Art, Zauberei betreibt, die im ursprünglichen Funker-Terror geschulte Bundeswehr wohl, wenn ich Trickkisten, a là Wu'kun'd, Makhamb'a, Hokus-Pokus, und weitere Ninja-Zaubertricks, denen melde, da es Strategien sind, welche ich als U.N.-Adjutanten Doppler, in Japan, Teï Peî, in den Heaven's Dojõ's erlernte?
Versteht die Bundeswehr, ihr zu häufig thematisiertes weniger geschultes Volk überhaupt, respektive, wie geht die Bundeswehr öffentlich damit um, wenn sie auffliegt, wie die Bundeswehr, nicht im Sinne des Volkes kommuniziert? Ist es so gesehen, wirklich die Verteidigungs-Armee, der Bundes Republik Deutschland, oder die Verteidigungs-Armee, der “Politik-Welt“? Anbei, gemessene, 47% rebellische Gesetzlose, zum Thema Funkerei… Zumindest in ganz Bundes Republik Deutschland. Klingt fast so, als ob es Zeit wäre, für eine Verfassungs-Änderung, oder wie hält es sich, in anderen Staaten??? Schauen wir mal in Richtung Niederlande, 46% rebellische Gesetzlose, zum Thema Funkerei. In Belgien, 37% rebellische Gesetzlose zum Thema Funkerei. In Italien, 97% rebellische Gesetzlose zum Thema Funkerei. In U.K., 86% rebellische Gesetzlose zum Thema Funkerei. In U.S.A.: 70% rebellische Gesetzlose zum Thema Funkerei. Russland, 87% rebellische Gesetzlose zum Thema Funkerei. Weißrussland, 47% rebellische Gesetzlose zum Thema Funkerei… Hauptsächlich geht es um Tracing, respektive Sitten-Zurechtruferei, welche rebellisch Gesetzlos abläuft. Die anderen Staaten, der Gesetzesfürchtigste Staat: Simbabwe, 1% rebellische Gesetzlose zum Thema Funk, von Mensch zu Mensch, je nach Geschwindigkeit der Sachbearbeitung, sogar weniger.
Nairobi, etwa 0,9% aktuell. Aber je nach Geschwindigkeit der Sachbearbeitung auch mal 1,7%…
So gesehen, Bundes Republik Deutschland, ist noch nicht der schlimmste Staat, zum Thema Funk, von Mensch zu Mensch.
Andere hätten über Zauberei geschrieben, welche sie beeindruckt hätte, aber dass wäre ja “Wahnsinn“ und nur Schizophrene, bis Multiple Persönlichkeits-Spaltung, seitens unserer Verteidigungs-Armee.
Des weiteren, die Psychiatrie betreibt, dem Vernehmen nach, Menschenrechtsverletzende Übergriffe, via Netzwerk, genutzt und gefunden wurden GSM-1840 bis GSM-1844, militärische Akustik-Funkernetze, der Zuweisung nach gehend (GSM-1840, Humanoider Mund), (GSM-1844 Humanoider Gehirns-Kasten). Der Vermutung nachgehend, sogar GSM-1860 (Unterbewusstsein/Gedärme).
Dass anbei, als IPv5, gewertete Protokoll, der Informatiker und ähnlichen Berufsgruppen, wäre besagter Humanoider Körper, wofür man in Amerika, dem Vernehmen nach, Sondergenehmigungen rausgehen liess, für einzelne, welche ich Bemitleidenswert finde. Da, IPv5, militärischen Funk darstelle und besagte GSM-1800 bis GSM-1899 direkt humanoide Wesen wären, theoretisch sogar Menschen-Affen. Deswegen, schaltete, man in Europa, gegen IPv5, Firewall-Direktiven ein, welche es unterbinden, da es sonst, mindestens theoretische weiße, bis schwarze Folter ermöglichen würde.
Im übrigen, noch bin ich Detektivisch, damit am umgehen, aber es könnte sein, ich weiss wirklich nicht sicher, aber: IPv5, ist das, was den “Netzwert“ ausmacht, von Dritter-Leute Bank-Konten, dafür gibt es in U.S.A., Networth-Controller, was ist an dem Thema dran, ist es die Wahrheit, oder nur ein Gerücht? Im übrigen, Netz-Wert, würde heissen, dass man so hoch absichert, um den Menschen vor Übergriffen zu schützen, respektive, wie viel, der Verstand wert wäre, bis die Networth-Controller, vor Korruptheit einknicken, wiederum, aus der Rumor-Küche/Gerüchteküche.
Was sagen Fachleute dazu?
0 notes
Text
O que aconteceu com o IPv5? Por que existe IPv4, IPv6, mas não IPv5?
O que aconteceu com o IPv5? Por que existe IPv4, IPv6, mas não IPv5?
Se você já passou algum tempo no mundo da internet, deve ter ouvido falar dos protocolos IPv4 e IPv6 que nossos computadores usam todos os dias.
Uma pergunta que você pode estar fazendo é: Por que não existe IPv5? Por que o IPv6 veio depois do IPv4 e não do IPv5? Já houve um IPv5? Se sim, o que aconteceu com o IPv5?
A resposta é sim, houve um IPv5… mais ou menos.
O início da história da internet
View On WordPress
0 notes
Video
tumblr
Loving this new mod, really pushes.
#vape#vapelife#clouds#cloud#cloudlife#staycloudy#motionlessinwhite#bandmerch#beanie#ipv5#pioneer4you#kangertech#vapetastic
1 note
·
View note
Photo

Nobody ever cared about what happened to IPv5
177 notes
·
View notes
Text
Using Mac Address Filtering To Secure Your Wi-Fi Network
With no password established anyone can get into your router and begin messing with the configuration. It is advised to choose a powerful codeword for safety. The deal with line is in depth but work is ongoing for IPv5 and 6. Recent times have seen a tremendous fall in the prices of computers. You will find homes which have more than one of P.C. If you find that you have more than one computer, know that you are in the same dilemma as hundreds of other people who want to set up house networks. For instance you could be in the study room and wish to retrieve a file that is stored in the computer in the bedroom. The most significant importance of network in the home is reducing internet cost by allowing the various computers in the house to share broadband connection. This means a network is only possible when there is more than one network in the house. The use of a network is when two people are using the computers in the house but they require to use the same printer resources.
Note** - I know you have a network printer and the second choice is network printer and it makes logical sense to choose that - but you have to trust me and not think for yourself on this one.
You will need a device that provides a DHCP service. This is normally included as a service in the Internet access router -- you will probably need to enable it as, by default, DHCP is often disabled.
This 192.168.0.1 IP is normally associated with high speed broadband routers. You will find corporations which benefit from this kind of IP as default IPs to their routers, Netgear together with D-Link, for example. For more information about that you should check just about any wireless modem instructions of those two manufacturers.
The first thing that you have to do is that you should boot up the host computer, the computer that has connection. After that, you can log in by using the Administrator or even Owner account. After that, click the "Start" on the button left and then select the "Control Panel".
NOTE: With these tools chances of identifying someone on your network increases, but will NOT prevent them from gaining access to your Network. Other tools exist than described in this article, but the goal is to show you the different type of tools and how to use them.
By now you should be receiving signals from your router already. Your next task is to make your network secured. Open a web browser. Click the url text box and type 192.168.1.1. If this does not direct you to the configuration page, change the url to 192.168.2.1.
After the re installation is complete, you can set up the security features; remember that this is a task you must set up yourself. As is always the case when handling routers, make sure that the instructions are followed step by step.
As I mentioned at the beginning of this article, the possibilities for this use are endless depending on your own individual needs, and I imagine that as technologies such as 3G and GPRS are improved, this ability will extend to your PDA device as well so that you can access your home PC on the move, that's if you are not carrying around a small PC and mini holographic projector in your top pocket by then!
2 notes
·
View notes
Text
Wireless Routers - I Can't Connect To The Web
You ought to hear a click when it is linked correctly, and plug in the other end to your modem. If you experience issues in your connections, proceed to "My Network Locations". Bellow you will notice you should type your DNS. The IP address is used by networks to recognize computers on the system. Servers also use it know the ones making requests. The new addresses (like this one) are under IPv4. The older ones are categorized under IPv3 and below. The address line is extensive but work is ongoing for IPv5 and 6.
This is when you will go about connecting all of your cables to your DVR, powering it up, and getting your settings configured. This includes connecting all of your security cameras, your Ethernet cable, a monitor, and a power source.
A window will pop up asking if you want to add a local printer, or a network printer... Here is the trick. You choose add a local printer, and then uncheck the box that says "automatically look for my plug and play printer." (if the box is not there, ignore this.) The next step is to choose to create a new standard TCP/IP port, so select create a new port, and use the TCP/IP port option. When it asks for port information, input the ip address of the printer, and then click next.
You should see something similar to the screen above which means that your two computers are connected properly. If you receive Ping request could not find host... or similar message that means that your two computers are not connected - in case of wired connection make sure that the cables that are connecting them are plugged in properly and that you're using the right cables (cross-over cables).
It does not matter whether you would connect it directly to a computer or you would have another internet device to be connected on the modem. You can easily configure the network, thanks to the said IP address. But there are some tech-savvies who do not recommend this to be your private IP for some reasons. For one, many other devices can immediately access a connection since they are all using the same default IP address just like yours. All of the activities of these devices will only be linked to one IP. It is also very accessible since all you have to do is to type 192.168.1.1 at your Internet browser's address bar just like the way you type your most visited website.
This IP address is also the default gateway in a variety of laptops. This gateway can be also identified as motorway where all of the traffic and data files are processed and being delivered to completely different spots. It is almost always available on LAN systems.
Install, attach and/or setup all hardware as per the manufacturers' directions. Every device on the network needs to have at least one IP address of its own. IP addresses are those numbers you may have seen on the internet before, such as: 70-1-2-125. On a home network, your IP addresses will look like 192.168.0.1 or 10.121.0.1.
It is important that you place your router in the right location. You must also make sure that no metal surrounds your newly purchased Linksys router. Remember, a metal may block the signal, and this may hamper the working of the device.
Two more things: If you've changed the network name, encryption type, or pass phrase, you'll probably have to re-enter the security key before reconnecting any computers to the wireless network. Which brings us to the second thing...
1 note
·
View note
Link
“IP” stands for “internet protocol,” which is a set of rules governing how data transmitted across the network. Evolution of Computer networkers starts in the 1960s and in 1969 the internet officially born. IPv4 has served as the backbone of the internet since its inception from a computer network to the worldwide network. An Internet Protocol address (IP address) is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. There are two versions of IP addresses: IPv4 and IPv6. IPv4 uses 32-bit addresses, which equates to 4 bytes and represents in decimal form eg. 192.168.1.1. That limits the address pool for IPv4 to around 4.3 billion unique addresses. That sounds a lot but now when the population on earth is around 7.3 billion and more and more devices in use and always stay online. Now it looks like IPv4 is exhausted.
IPv6 is a 128-bit, or 16-byte, addresses. This means the address pool for IPv6 is around 340 undecillion, or 340 trillion trillion trillion, which is an unimaginably large number. IPv6 represents in Hexadecimal form eg: 2001:0DB8:0000:0002:0022:2217:FF3B:118C. It is more secure as compared to IPv4 and improves network performance as well.
Share, Subscribe, Support!
Youtube:- https://www.youtube.com/channel/UCs7d... Twitter:- https://twitter.com/yourtechlab1 Tumblr:- https://yourtechlab.tumblr.com/ Blogger:- https://yourtechlab1.blogspot.com/
0 notes
Photo

#garam #tobacco5% #kayfun #ipv5 #vapetedd #rodeo1.2% #serpent #ipv3li (at Malacca) https://www.instagram.com/p/BpWqx76Hdbc/?utm_source=ig_tumblr_share&igshid=tbrmlkjjg6fr
0 notes
Photo

Vaping is the Future #squape #squapeE #pioneer4u #ipv5 #dampfen #dampftbeimir #dampfer #vaporactive #vaping #dampfe #vape (hier: Stuttgart, Germany)
0 notes
Video
instagram
Quick VapeBox before work. #vapelyfe #vapelyfe #wismic #jaybo #ohmslice #ipv5 #ipvmini #ejuice #clouds #clouds4days #tnhotwires #vapefam #rda #tank #vapeporn #ijoy #limitless #rdta #smok #eleaf #sigeli #buzzbox #musiccitymods #haus #aspire #lg #sony #turds #vtc4 #vtc5 #vtc6 #lghg2 (at Walmart Springfield - Tom Austin Hwy)
#ohmslice#clouds#rdta#rda#ejuice#sigeli#ipvmini#turds#vapeporn#ipv5#vapelyfe#vtc6#limitless#tnhotwires#vapefam#ijoy#sony#wismic#lg#buzzbox#clouds4days#musiccitymods#jaybo#aspire#lghg2#vtc5#haus#tank#smok#vtc4
0 notes
Photo

Handcheck @vaporever_store 😁😘❤ #handcheck #ipv5 #avocado24 #bottomairflow #explorelombok #beach #vapelife #goldenticket #gilitrawangan (at Gili Trawangan Island-Lombok)
0 notes
Photo

#beargrylls #paracord #tattoo #ezdripper #ipv5 #kennedy #rda #vapelife #vapelyfe #vapemaniac #vaper #dripclub #vapeclub #vapepics #clouds #subohm #turkishvapers
#tattoo#clouds#rda#kennedy#vapelife#vapepics#turkishvapers#vaper#subohm#ezdripper#vapeclub#dripclub#vapelyfe#ipv5#paracord#vapemaniac#beargrylls
0 notes
Text
The short term origins of legacy systems
Some things stay around longer than they should. Once something's in place, it's very difficult to fix. So instead we introduce workarounds. And after that, workarounds to work around workarounds.
The world would be better off if we all drove on the right-hand side of the road (or perhaps the left), as manufacturing systems would suddenly be simplified, but that'll never happen.
Arbitrary decisions from decades ago will stick with us for decades to come.
ASCII BEL 🔔
ASCII - the base standard for what technologists call "plain text" messages-contains several characters that do not represent text at all. Published in 1967, the standard reserves about 25% of its precious 128 characters for purposes that are largely ignored today. My favorite one is the character for telling a computer to ring its bell (␇). There's even a computer programming language named after it.
Developed to serve teletype machines, ASCII was fit for purpose. But now it's wasteful. We could make much more better use of those characters today.
The most egregious example of this waste is CSV. Because there was no way to enter control characters on a computer keyboard, someone started to use commas to separate fields in records. You,may,have,seen,something,like,this, in your travels.
CSV creates all sorts of problems. What if you're European and you use a comma to indicate a decimal place? What if you want an actual comma in a field? Well, you use double quotes. And if you want a double quote and a comma? Well, if you're Excel, you just keep adding more quotes. And the solution has been waiting there in ASCII. And it will never be used.
ASCII contains unambiguous delimiters for fields (␟), records (␞). None of the misery inflicted on anyone attempting ask computer interpret CSV files correctly is necessary. Yet it will always be necessary.
No Letter k in Welsh
As a point of pride, Welsh spelling does not use the letter k. Loan words from other languages with a hard k sound are also spelled with a c. There is no kilometre in Welsh, but there is a cilometre. Why? Well, because English printers in the 1560s didn't have enough Ks.
Here is the quote from JRR Tolkein, discussing William Salesbury's translation of the New Testament into Welsh:
But in one point of Spelling Salesbury's influence was important. He gave up on the letter k (in the New Testament), which had in medieval Welsh been used more frequently than c. … Salesbury, in answer to his critics (for the loss of k was not liked), replied: C for K, because the printers have not so many as the Welsh requireth. It was thus the English printers who were really responsible for spelling Kymry with a C. [emphasis from the original changed]
—p165 "English and the Welsh" in The Monsters and the Critics
PCs wake up as 16-bit computers from 1976
When a PC turns on, the CPU and operating system do a small dance. When the CPU resets, it switches to behave exactly as the Intel 8086 did in 1976. Part of the boot sequence is to convince the CPU that it should use 32-bit instructions. And then 64-bit.
Resisting Arbitrary Solidity
Is it possible to design systems that are rigid enough to be dependable today, but flexible enough to adjust over time?
Rather than creating vestibule code for creaky old standards, can we create standards that be designed with their own future obsolescence in mind? What causes a standard to adapt with change, such as Intel's, rather than be repeatedly overridden, like ASCII's?
In the political sphere, this is an question that law students spend a lot of time worry about. Very technically precise laws are easy to interpret, but they're also brittle. They age quickly.
One idea for technology standards is to leave space available for future use. In the case of ASCII, it's been able to be wholly incorporated into another, much more internationally suitable standard: Unicode UTF-8. By chance, ASCII only uses 7 bits. Every computer uses 8 bits per byte. That extra bit is used as a switch by Unicode to indicate that another byte should be read to be part of the same character. Unicode can grow to adapt (and bring ASCII along with it).
Another case of a standard surviving and adapting is the Network Time Protocol (NTP). NTP keeps digital clocks in sync with the world's atomic clocks. Like ASCII, NTP uses fixed-width messages. But there are a few bits free to denote extensions. And so it can adapt.
A standard that can't adapt well is version four of the Internet Protocol (IPv4). It did something right by adding a version number to its messages. But they changed the location of the version number in the next released version: version six (IPv6) [There is no IPv5 because someone else used it to mean something else and the Internet Protocol people decided to skip a number]. Moving the location of the version number means that tools that use IPv4 can't partially support IPv6. That's different than say Unicode. Even if you encountered a device that only supported ASCII, and assuming your language uses Latin-based characters, you would still see several letters in a message. Although there would be plenty of mojibake too.
Time will tell what standards for today's teletype machines we are building today.
2 notes
·
View notes
Photo

All about that cloud life
0 notes