#ios enterprise certificate
Explore tagged Tumblr posts
Text
Common Issues with iOS Enterprise Accounts and How to Resolve
Navigating the digital landscape of iOS enterprise accounts can sometimes be a challenging journey. However, with the right information, you can effectively address and resolve common issues. This blog aims to help you understand these issues and provide feasible solutions.
Recognizing Common iOS Enterprise Account Issues
There are a few common issues that users may encounter with their iOS enterprise account. These range from application distribution problems to issues with certificates and provisioning profiles.
Distribution Issues
A common challenge with iOS enterprise accounts is the distribution of applications outside the App Store. To resolve this, ensure your organisation adheres to the Apple Developer Enterprise Program's guidelines for app distribution.
Certificate Problems
Certificate-related issues are common and can cause app installation failures. Regularly updating your certificates and ensuring that they are correctly installed can prevent such problems.
Provisioning Profile Difficulties
Issues with provisioning profiles can result in apps failing to launch. To resolve this, ensure the app's bundle ID matches the one in the provisioning profile.
Maximising the Potential of Your iOS Enterprise Account
Understanding these issues is only half the battle. Leveraging the tools and resources available in the iOS enterprise account will help you optimise your app development and distribution processes.
Conclusion
While navigating the world of iOS enterprise accounts can be challenging, understanding common issues and their solutions can make the journey smoother. Remember that the key to resolving these issues lies in compliance with Apple’s guidelines, regular updates, and matching IDs. With these strategies in hand, you are well-equipped to maximise the potential of your iOS enterprise account, paving the way for successful app development and distribution!
#iOS enterprise account#apple enterprise developer account#apple developer enterprise#apple enterprise account#ios enterprise certificate#ios developer enterprise program#ios enterprise distribution certificate
2 notes
·
View notes
Text
Flutter Development work from home job/internship at Bismilla Enterprises
About the work from home job/internshipSelected intern’s day-to-day responsibilities include:1. Designing UI and creating animations 2. Integrating REST APIs 3. Structuring architecture using MVC or MVVM 4. Managing state with Riverpod, GetX, Provider, or bLOCSkill(s) requiredAndroid Flutter iOS React Native REST APIEarn certifications in these skillsWho can applyOnly those candidates can apply…
0 notes
Text
Software Development Services in Noida: Driving Innovation and Growth
In today's fast-paced digital era, businesses must adapt quickly to changing market dynamics. Software development is pivotal in enabling organizations to streamline processes, enhance customer experiences, and remain competitive. Noida, a bustling hub of technological innovation, has emerged as a hotspot for world-class software development services. This blog explores the importance of software development services in Noida and why this city is the ideal destination for businesses seeking advanced technology solutions.

Why Noida?
Noida, located in the National Capital Region (NCR) of India, is renowned for its thriving IT ecosystem. The city hosts numerous multinational corporations, startups, and IT service providers, making it a prime location for software development. Here are some reasons why Noida stands out:
Strategic Location: Proximity to Delhi and excellent connectivity to other major cities make Noida easily accessible for businesses worldwide.
Skilled Workforce: Noida boasts a pool of highly skilled software developers, engineers, and IT professionals.
Cost-Effective Solutions: Companies in Noida offer high-quality software solutions at competitive prices, providing excellent value for money.
Technological Expertise: The city comprises experts in various technologies, including AI, IoT, blockchain, and cloud computing.
Key Software Development Services in Noida
Businesses in Noida provide a wide range of software development services tailored to diverse industries. Some of the key offerings include:
Custom Software Development
Tailored software solutions that address specific business needs.
Development of scalable and secure applications.
Expertise in multiple programming languages and frameworks.
Web Application Development
Building responsive, user-friendly, and feature-rich web applications.
Leveraging modern technologies like React.js, Angular, and Node.js.
Mobile App Development
Creating native and hybrid apps for Android and iOS platforms.
Focus on delivering seamless user experiences and robust functionality.
Enterprise Software Solutions
Development of ERP, CRM, and other enterprise-grade applications.
Integration with existing systems to ensure smooth operations.
Cloud-Based Solutions
Designing and implementing cloud-native applications.
Expertise in platforms like AWS, Microsoft Azure, and Google Cloud.
AI and Machine Learning
Developing intelligent software with AI capabilities.
Implementation of predictive analytics and data-driven decision-making tools.
IoT Solutions
Building software for IoT devices to enhance connectivity and automation.
Integration with smart home and industrial systems.
Software Testing and QA
Comprehensive testing services to ensure software reliability and performance.
Automation and manual testing for quality assurance.
Benefits of Partnering with Noida-Based Software Development Companies
Innovative Approach: Companies in Noida are known for adopting cutting-edge technologies and methodologies, ensuring innovative solutions that align with market trends.
Agile Development Processes: Agile practices ensure flexibility, quicker delivery, and high-quality outcomes. Teams in Noida prioritize collaboration and iterative improvements.
Global Standards: Noida’s software development companies adhere to international standards, including ISO certifications and GDPR compliance, ensuring top-notch service quality.
Dedicated Support: Reliable after-sales support and maintenance services to ensure the smooth functioning of the software.
Multidomain Expertise: Developers in Noida have experience across multiple domains such as healthcare, finance, e-commerce, education, and logistics.
Choosing the Right Software Development Partner
Selecting the right software development company in Noida is critical for the success of your project. Consider the following factors:
Portfolio and Expertise: Evaluate the company’s portfolio and check for relevant experience in your industry.
Client Testimonials: Look for reviews and feedback from previous clients to gauge the company’s reliability and quality.
Technical Proficiency: Ensure the team has expertise in the latest technologies and tools.
Cost Transparency: Discuss pricing upfront and ensure there are no hidden charges.
Timely Delivery: Choose a company with a proven track record of meeting deadlines.
The Future of Software Development in Noida
Noida’s software development landscape is evolving rapidly, driven by advancements in technology and the city’s dynamic workforce. Key trends shaping the future include:
Artificial Intelligence and Automation: Increasing adoption of AI and machine learning to build intelligent and self-learning applications.
Blockchain Technology: Development of secure and transparent systems for industries like finance, healthcare, and supply chain.
Edge Computing: Moving beyond cloud solutions to enable faster processing and real-time data analysis.
Sustainability in Software Development: Focus on creating eco-friendly applications with reduced carbon footprints.
Conclusion
Noida has firmly established itself as a hub for cutting-edge software development services. With its robust infrastructure, skilled workforce, and commitment to innovation, the city is poised to drive digital transformation for businesses worldwide. Whether you are a startup, SME, or an enterprise, partnering with a software development company in Noida ensures access to high-quality, cost-effective solutions tailored to your unique requirements.
#website design#software development#mobile app development#e commerce website development#amazon marketing services
0 notes
Text
Why Global Businesses Prefer Indian Mobile App Development Companies for Outsourcing
Mobile apps have become an essential tool for businesses looking to expand their reach and engage with customers. For many companies, outsourcing mobile app development to specialised firms offers the flexibility, cost-effectiveness, and expertise needed to build successful apps.
India has risen as a global leader in mobile app development, ranking among the top outsourcing destinations. So, why do global businesses prefer mobile app development company in India for their projects?
Let’s delve into the main factors behind this trend.
1. Cost-Effectiveness
One of the primary reasons companies outsource mobile app development to India is the significant cost savings. Developing an app in Western countries, particularly in North America or Europe, can be prohibitively expensive due to high labor costs. In contrast, India offers highly competitive rates without sacrificing quality. Businesses can reduce development costs by as much as 60-70% by outsourcing to Indian firms.
The cost advantage allows companies to allocate more resources to other crucial aspects of their business, such as marketing, user acquisition, or enhancing customer experience. This affordability is particularly beneficial for startups and small businesses with limited budgets but high ambitions for their mobile app.
2. Access to a Large Pool of Skilled Developers
India is home to one of the world’s largest and most talented groups of app developers. Each year, thousands of highly skilled engineers graduate from India’s top technical institutes, many of whom specialise in mobile app development. Indian developers are known for their expertise in programming languages such as Swift, Kotlin, Flutter, and React Native, making them well-equipped to develop apps for both iOS and Android platforms.
With this abundant talent, Indian mobile app development companies can offer solutions for a wide range of industries, from healthcare and finance to e-commerce and gaming. Whether it’s a simple app or a complex enterprise-level application, Indian firms can deliver high-quality, innovative solutions.
3. Adoption of Cutting-Edge Technologies
India has become a global tech hub, and Indian app development companies are at the forefront of adopting the latest technologies and tools. From Artificial Intelligence (AI) and Machine Learning (ML) to Blockchain and the Internet of Things (IoT), Indian developers are well-versed in integrating advanced technologies into mobile applications.
This ability to leverage cutting-edge technology allows businesses to create more innovative, intelligent, and scalable mobile apps. With Indian firms, companies can stay ahead of the curve by incorporating features like real-time analytics, personalised content, and seamless integrations that improve user experiences and drive business growth.
4. Quality Assurance and On-Time Delivery
Mobile app development company in India is committed to delivering high-quality apps that meet international standards. Many of these companies follow industry certifications such as ISO, CMMI, and Six Sigma, which ensures that development processes adhere to global best practices. These firms also have dedicated quality assurance teams that rigorously test apps to ensure they are free from bugs and provide a smooth user experience.
In addition to quality, Indian companies are known for their timely project delivery. With well-organised workflows, clear communication, and adherence to deadlines, businesses can be confident that their app development project will be completed on schedule, helping them launch faster and gain a competitive edge.
5. Scalability and Flexibility
Outsourcing mobile app development to India offers businesses the flexibility and scalability needed to adapt to changing project requirements. Indian companies typically provide various engagement models, allowing businesses to choose between fixed pricing, hourly rates, or dedicated teams based on their needs.
Whether you need to scale your team up to meet a tight deadline or scale down after completing the project, Indian firms offer the flexibility to adjust the size and scope of the project. This level of scalability ensures that businesses always have access to the right resources, regardless of the project’s complexity or size.
6. Ongoing Support and Maintenance
Another key advantage of outsourcing to Indian mobile app development companies is the continuous support and maintenance they provide. Post-launch, mobile apps require regular updates, security patches, and new features to stay relevant in a rapidly evolving market. Indian companies offer long-term maintenance and support services to ensure that your app remains functional, secure, and up-to-date.
Global businesses prefer outsourcing mobile app development to India due to a combination of cost-effectiveness, access to top talent, cutting-edge technology, and scalability. Mobile app development company in India not only provide affordable, high-quality solutions but also offer the flexibility and ongoing support businesses need to thrive in today’s competitive digital landscape. By choosing India as an outsourcing destination, companies can develop innovative apps that drive growth while optimising their resources for other business priorities.
#Mobile app development company in India#mobile app development#mobile app development company#app development india
0 notes
Text
Software Development and Full-Stack Development: Key Differences and Career Insights
As technology continues to evolve, so do the roles available in the field. Two popular career paths that often cause confusion are software development and full-stack development. While both involve coding and problem-solving, they have distinct differences in scope, specialization, and the technologies involved. For those looking to master the art of Full Stack, enrolling in a reputable Full Stack Developer Training in Pune can provide the essential skills and knowledge needed for navigating this dynamic landscape effectively.
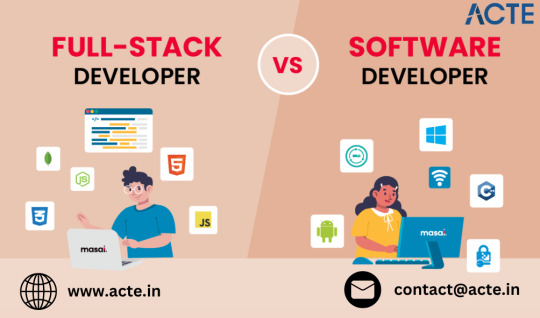
This blog will help clarify the main differences and guide you toward choosing the career path that aligns with your interests and goals.
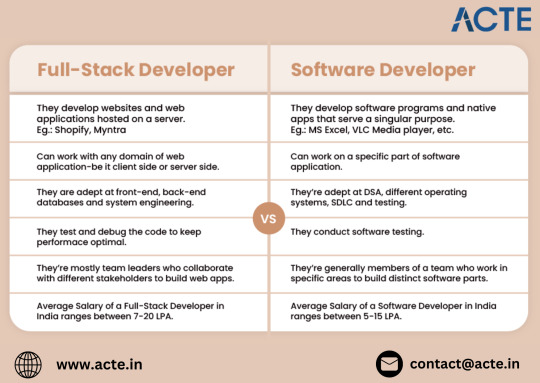
Introduction to Software and Full-Stack Development
Before diving into the specifics, it’s essential to understand the primary focus of these roles. Software developers can work across a range of platforms, from desktop and mobile applications to embedded systems. They may focus on specialized areas like game development or enterprise solutions. In contrast, full-stack developers are responsible for building and maintaining both the frontend and backend of web applications, covering everything from how a site looks to how it processes data.
1. The Breadth of Responsibilities
Software Development: Specialization Over Generalization
Software development is a broad field encompassing the creation of various software applications, from desktop software to mobile apps and more. Software developers often choose to specialize in specific areas or platforms, such as Android or iOS development, game design, or even cybersecurity. Their work is not limited to the web and spans multiple operating systems and devices.
Full-Stack Development: A Comprehensive Approach
Full-stack development, on the other hand, focuses exclusively on web applications. Full-stack developers manage both the frontend (client-side) and backend (server-side) of websites. They are jacks-of-all-trades in web development, able to handle user interface design, server management, and database architecture all in one. This versatility is highly valued in startups and smaller teams where developers are expected to cover more ground.
2. Tools and Technologies
Software Development: Diverse Technologies for Different Platforms
The tools used by software developers depend heavily on the platform they are working with. For instance, a developer focused on desktop applications might use C++, Java, or Python. Meanwhile, mobile developers would turn to Swift for iOS or Kotlin for Android apps. Software developers can choose their tech stack based on the type of software they are building, which may not always include web-based technologies.
Full-Stack Development: Web-Centric Tech Stack
Full-stack developers work primarily with web-based technologies. For frontend development, they commonly use HTML, CSS, and JavaScript, often incorporating frameworks like React, Angular, or Vue.js. On the backend, they work with Node.js, Ruby on Rails, or Django, managing databases with systems like MySQL, PostgreSQL, or MongoDB. Full-stack developers need to stay updated with the latest trends in web technologies to build dynamic, responsive web applications. Here’s where getting certified with the Top Full Stack Online Certification can help a lot.
3. Career Specialization
Software Development: Becoming a Subject Matter Expert
Software developers typically have the option to specialize in a particular domain. For example, one may become an expert in backend development, focusing solely on server-side logic and database management. Others may focus on mobile applications, perfecting their skills in creating responsive and efficient mobile experiences. This specialization often leads to becoming a subject matter expert in a particular technology or platform.
Full-Stack Development: Embracing Versatility
In contrast, full-stack developers generally embrace a broader skill set. They may not dive as deeply into one particular area as software developers do but have enough knowledge to work across multiple aspects of web development. This generalist approach makes them versatile and adaptable, allowing them to contribute to all stages of web application development.
4. The Final Product
Software Developers: A Wide Range of Applications
Software developers work on various types of software, including operating systems, mobile apps, desktop software, and even embedded systems. Their work often depends on the industry they’re in—whether it's finance, healthcare, gaming, or another sector. Their end product can exist across different platforms and isn’t restricted to web-based applications.
Full-Stack Developers: Web-Based Applications
Full-stack developers focus on creating fully functioning web applications. These can range from simple websites to complex platforms such as e-commerce websites or SaaS (Software as a Service) platforms. Since their work is web-focused, they ensure that the application is efficient, scalable, and provides a seamless experience for the end user across multiple devices.
5. Which Path Is Right for You?
Software Development: Ideal for Specialists
If you enjoy mastering a specific type of technology and becoming an expert in your field, software development may be the best choice. With opportunities in mobile app development, desktop applications, and specialized systems, software developers can find their niche in various industries.
Full-Stack Development: Perfect for Generalists
On the other hand, if you enjoy working across different areas of web development, full-stack development could be a more rewarding path. The flexibility to work on both frontend and backend elements of a website allows full-stack developers to see projects through from start to finish. This path is ideal for those who thrive in a dynamic, web-centric environment.
Conclusion: Finding Your Fit
Both software development and full-stack development offer exciting opportunities, but choosing the right path depends on your interests and career goals. Software development provides a chance to specialize in a specific area and work on diverse types of software. Meanwhile, full-stack development offers a comprehensive approach to web development, allowing you to handle multiple aspects of a project and providing a broader range of skills. Whichever path you choose, both roles are in demand and critical to the tech industry's future.
Understanding the differences between these two career paths will help you make an informed decision, setting you up for success in your tech career.
#full stack course#full stack developer#full stack software developer#full stack training#full stack web development
0 notes
Text
NVIDIA DGX SuperPOD In Dell PowerScale Storage offer Gen AI

Boost Productivity: NVIDIA DGX SuperPOD Certified PowerScale Storage.
Dell PowerScale storage
NVIDIA DGX SuperPOD with Dell PowerScale storage provide groundbreaking generative AI. With fast technological growth, AI is impacting several businesses. Generative AI lets computers synthesize and construct meaning. At the NVIDIA GTC global AI conference, Dell PowerScale file storage became the first Ethernet-based storage authorized for NVIDIA DGX SuperPOD. With this technology, organizations may maximize AI-enabled app potential.
- Advertisement -
DGX SuperPODs
The Development of Generative AI
Generative AI, which has transformed technology, allows robots to generate, copy, and learn from patterns in enormous datasets without human input. Generative AI might transform healthcare, industry, banking, and entertainment. There is an extraordinary requirement for advanced storage solutions to handle AI applications’ huge data sets.
Accreditation
Dell has historically led innovation, providing cutting-edge solutions to address commercial corporate needs. According to Dell, Dell PowerScale is the first Ethernet-based storage solution for NVIDIA DGX SuperPOD, improving storage interoperability. By simplifying AI infrastructure, this technology helps enterprises maximize AI initiatives.
“The world’s first Ethernet storage certification for NVIDIA DGX SuperPOD with Dell PowerScale combines Dell’s industry-leading storage and NVIDIA’s AI supercomputing systems, empowering organizations to unlock AI’s full potential, drive breakthroughs, and achieve the seemingly impossible,” says Martin Glynn, senior director of product management at Dell Technologies. “With Dell PowerScale’s certification as the first Ethernet storage to work with NVIDIA DGX SuperPOD, enterprises can create scalable AI infrastructure with greater flexibility.”
PowerScale Storage
Exceptional Performance for Next-Generation Tasks with PowerScale
Due to its remarkable scalability, performance, and security, which are based on more than ten years of expertise, Dell PowerScale has earned respect and acclaim. With its NVIDIA DGX SuperPOD certification, Dell’s storage offering is even more robust for businesses looking to use generative AI.
- Advertisement -
This is how PowerScale differs:
Improved access to the network: NVIDIA Magnum IO, GPUDirect Storage, and NFS over RDMA are examples of natively integrated technologies that speed up network access to storage in NVIDIA ConnectX NICs and NVIDIA Spectrum switches. By significantly reducing data transfer times to and from PowerScale storage, these cutting-edge capabilities guarantee higher storage throughput for workloads like AI training, checkpointing, and inferencing.
Achieving peak performance: A new Multipath Client Driver from Dell PowerScale increases data throughput and enables businesses to meet DGX SuperPOD‘s high performance requirements. With the help of this cutting-edge functionality, companies can quickly train and infer AI models, allowing for a smooth integration with the potent NVIDIA DGX platform.
Flexibility: Because of PowerScale’s innovative architecture, organizations can easily scale by only adding more nodes, giving them unmatched agility. Because of this flexibility, businesses can develop and adjust their storage infrastructure in tandem with their increasing AI workloads, preventing bottlenecks for even the most demanding AI use cases.
Security on a federal level: PowerScale has been approved for the U.S. Department of Defense Approved Product List due to its outstanding security capabilities. The accomplishment of this demanding procedure strengthens the safety of vital data assets and highlights PowerScale’s suitability for mission-critical applications.
Effectiveness: The creative architecture of PowerScale is intended to maximize effectiveness. It reduces operating expenses and environmental effect while optimizing performance and minimizing power consumption via the use of cutting-edge technology.
NVIDIA DGX SuperPOD
Dell created the standard architecture below in order to hasten the PowerScale with NVIDIA DGX SuperPOD solutions implementation. The document provides examples of how PowerScale and NVIDIA DGX SuperPOD work together seamlessly.
An important turning point in the quickly changing field of artificial intelligence has been reached with the accreditation of Dell PowerScale as the first Ethernet-based storage solution approved for NVIDIA DGX SuperPOD worldwide. Organizations may now use generative AI with scalability and performance thanks to Dell and NVIDIA’s partnership. Businesses may fully use AI and revolutionize their operations by using these cutting-edge technologies, ushering in a period of unprecedented development and rapid innovation.
Read more on govindhtech.com
#NVIDIADGX#SuperPOD#DellPowerScale#GenAI#GenerativeAI#DellTechnologies#generativeAI#AIworkloads#NVIDIA#dell#NVIDIADGXSuperPOD#PowerScaleStorage#technology#technews#news#govindhtech
0 notes
Text
SIMATIC ET 200SP CPU - The Distributed Controllers
Compactness and versatility are combined in the ET 200SP CPUs for distributed controllers.
For conventional and fail-safe applications, distributed controllers are the ideal choice, particularly in the medium performance range for machines with distributed intelligence or series machines with limited space.

The CPUs share many of the same features, including the CPU, as the S7-1500 controller family's CPUs 1511 and 1513. As an illustration, consider the web server, complete symbolic programming, integrated security, integrated system diagnostics, and integrated trace function.
The connection to a higher-level CPU can be completed in precisely the same manner as with a conventional interface module because of the I-Device capabilities. Because of its short signal and encoder wiring, little wiring effort, and noise-resistant design, the ET 200SP station stands out from the competition.
PROFIenergy, isochronous manufacturing, configuration control (option handling), and DP master are among the extra features that the CPUs provide.
There are two kinds of applications for it: Standard CPUs and Failsafe CPUs.
1. Standard CPUs:
Standard CPUs - CPU 1510SP-1 PN and CPU 1512SP-1 PN

For the SIMATIC ET 200SP CPU, two interface modules with an integrated CPU and PROFINET connection are provided.
Connectivity adapters can be freely chosen with bus adapters thanks to the three integrated Ethernet ports. Within discrete manufacturing technology, the CPUs can function as distributed intelligence (PROFINET I-Device) or as a PROFINET IO controller.
The 151*SP CPUs can be expanded decentral via PROFINET with any ET 200 system and with ET 200SP standard modules.
The three ports on the integrated PROFINET IO IRT interface are intended to allow a line structure to be built in the plant via ports 1 and 2, as well as the connection of a PG/PC or HMI device via port 3.
2. Failsafe CPUs
Failsafe CPUs - CPU 1510SP F-1 PN and CPU 1512SP F-1

Standard and safety program processing are made possible by the failsafe ET 200SP CPUs. They meet the functional safety requirements of EN 61508 (2nd Edition) certification and can be used in safety-related applications up to SIL 3 (IEC 62061) and PL e (ISO 13849).
The ET 200SP standard and fail-safe modules, as well as decentralized connectivity via PROFINET / PROFIsafe with any ET 200 system, can be added to the 151*SP F CPUs.
Extra password protection has been implemented for the F configuration and F application in order to enhance IT security.
In discrete manufacturing technology, the CPUs can function as distributed intelligence (PROFINET I-Device) or as a PROFINET IO controller.
The three ports on the integrated PROFINET IO IRT interface are intended to allow a line structure to be built in the plant via ports 1 and 2, as well as the connection of a PG/PC or HMI device via port 3.
To sum up, the SIMATIC ET 200SP CPU provides a lightweight, robust solution for industrial automation requirements. Its excellent performance and smooth integration make it an adaptable option for a range of applications, helping enterprises to increase operational productivity and efficiency.
For more visit here
0 notes
Text
Argentina Software Development Market - Forecast (2023 - 2028)
Argentina Software Development Market is evaluated to be highly promising because of active government policies. The Argentine government is actively promoting various e-government projects as well as the development of an information society through the expansion of PC distribution and the rapid use of smartphones. In particular, the software industry has been designated as one of the strategic fostering industries and various support has been strengthened. Additionally, the low PC penetration rate is also a factor that brightens the development prospects of the Argentine IT industry. Argentina is considered to be very advantageous for the development of the IT industry such as software because it has abundant talented manpower among Latin American countries. Recently, Argentina has also been attracting attention as an IT service center owing to its high level of technology and high-quality labor. The Argentina Software Development market is analyzed to be EUR 4,220 million in 2021 and is projected to reach EUR 5,878 million in 2027, growing at a CAGR of 5.85 % during the forecast period of 2022-2027.
Report Coverage
The report: “Argentina Software Development Industry Outlook – Forecast (2022-2027)” by IndustryARC covers an in-depth analysis of the following segments in the Japan Software Development Industry.
By Language: Java, JavaScript, Python, C++, PHP, Scala, Ruby, LISA, Perl, SQL, Android, iOS, and Others
By Market Demand: In House on Payroll, Hired from Secondment Providers, Hired Freelancers, Fully Outsourced
By Deployment Type: On-Premise, Cloud
By Business Size: Small and Medium Business, Enterprise, and Government
By End Use Industry: Banking And Financial Institution, Insurance Firms, Media and Entertainment, Government, Defense, Telecommunication, Automotive, Consumer Goods and Retail, Healthcare, Manufacturing and Others
Request Sample
Key Takeaways
Argentina's software development market is being driven by a number of factors, including the increasing adoption of digital transformation by businesses, the growing demand for e-commerce and online services, and The emergence of AI and ML technologies
Argentina has a strong pool of talented software developers. This is due to the country's strong investment in education and its focus on science and technology. Argentine software developers are known for their skills and experience in a variety of software development technologies and platforms.
Argentina offers a competitive cost advantage for software development services. This is due to the country's relatively low labor costs and its favorable exchange rate. Argentine software development companies are able to offer high-quality services at competitive prices.
Argentina Software Development – Market Scope and Coverage
The base year of the study is 2021, with forecast done up to 2027. The study presents a thorough analysis of the competitive landscape, taking into account the market shares of the leading companies. The assessment includes the forecast, an overview of the competitive structure, the market shares of the competitors, as well as the market trends, market demands, market drivers, market challenges, and product analysis. These provide the key market participants with the necessary business intelligence and help them understand the future of the Argentina Software Development Market.
Argentina Software Development – By Language
By language, the software market is further fragmented into Java, JavaScript, Python, C++, PHP, Scala, Ruby, LISA, Perl, SQL, Android, iOS, and others. Above all, the Python segment held the largest market share in 2021 among other programming languages. Various institutes in the region including Coursera provide python certification and online learning courses and assist in mastering the concepts of python and its libraries including SciPy, Matlotlib among others.
Argentina Software Development – By Market Demand
In terms of market demand, the market is segmented by In House on Payroll, Hired from Secondment Providers, Hired Freelancers and Fully Outsourced. The inhouse on payroll segment accounted for the biggest revenue share in 2021 and is projected to grow at a higher rate. The main reason for this is the high quality of education availability in the region. In Argentina, there are 7 universities in the region ranking among the top 50 Latin American universities. Owing to the free tuition fees for higher education, the region has one of the highly educated population in Latin America.
Buy Now
Argentina Software Development – By Deployment Type
By deployment type, the Cloud segment had the majority of overall market share in 2021 due to increasing Cloud Data center in Argentina. In October 2019, Amazon Web Services, a on-demand cloud computing platform management company, invested approximately $800 million over a decade in a new South American data center in Argentina. Besides, IBM stared to provide cloud services for insurance firms in Argentina. Hence, major players providing cloud services to the insurance firms is set to fuel its market growth.
Argentina Software Development – By Business Size
With regard to business size, the Small and Medium Business segment had the highest market share in 2021. During the COVID-19 Pandemic, The Argentina government issued a series of economic relief measures, primarily focusing on the informal workers that account for 40 percent of the labor force as well as small and medium size enterprises (SMEs). The government prohibited employers from terminating employment until April 2021 and mandated a double severance payment until December 31, 2021. Such factors are expected to fuel its market growth.
Argentina Software Development – By End Use Industry
By end-use industry, the market is poised with respect to the end use industries to be processed including Banking and Financial Institution, Insurance Firms, Media and Entertainment, Government, Defense, Telecommunication, Automotive, Consumer Goods and Retail, Healthcare, Manufacturing, and others. The Consumer Goods and Retail segment generated the largest market share in 2021 based on the growing penetration of internet and increasing amount of consumer goods purchased on the Internet in Argentina. 8% of Argentina's total population is estimated to have used e-commerce services for the first time in self-isolation, and the number of people using E-commerce is expected to increase further as the current economic situation in the region continues. Argentina Software Development Market drivers Argentina’s software development is one of the major backbones of the South American IT market, and the growing number of unicorn IT companies in the region coupled with increasing interest of investors, is set to drive the growth of the underlying market. For instance, according to the 2019 Software And Computer Services Industry Permanent Observatory (OPPSI) report, the software development in Argentina is one of the major sources of foreign investments and account for 58% of the total investments. Furthermore, the emergence of successful software development companies in the region including Globant, Prominente, Baufest, Neuralsoft, Calipso among others is set to boost the growth of the underlying market.
#Argentina Software Development Market#Argentina Software Development Market Trends#Argentina Software Development Market Size#Argentina Software Development Market share
0 notes
Text
Unlock Your Potential with Xamarin Developer Certification
Become a Certified Expert with EdChart: Elevate Your Skills Today
The Ultimate Recognition in Online Certification
As a worldwide leader in on line certification, Edchart is committed to spotting and validating information across diverse topics. Through our on line exams, people can showcase their talent and stand out of their respective fields. We are proud to partner with CREDLY, a renowned platform for handling global credentials. Explore our badges and certifications: Edchart CREDLY Badges.

The Benefits of EdChart Certification
Validation of Expertise: Edchart Xamarin certification serves as a seal of approval, validating your know-how and enhancing your credibility in the enterprise.
Global Recognition: With Edchart Xamarin Framework, you advantage worldwide recognition for your capabilities, beginning doorways to new possibilities and profession development.
Increased Marketability: Certified specialists are in excessive call for. By acquiring an Edchart Xamarin App, you increase your marketability and beauty to employers.
Access to Exclusive Opportunities: Edchart certified people advantage get entry to to one of a kind opportunities, networking occasions, and profession assets to further their expert boom.
Scopes & Features of EdChart Certification
Comprehensive Exam Coverage: Our Xamarin Mobile App certification tests cowl a wide variety of subjects, making sure that candidates are thoroughly examined on their expertise and capabilities.
Flexible Exam Options: Edchart offers bendy examination options, permitting applicants to select the exam format and schedule that great suits their needs.
Real-world Scenarios: Our checks are designed to simulate actual-global eventualities, providing candidates with sensible experience and making sure they are well-organized for the demanding situations they will encounter of their subject.
Why Choose EdChart Certification?
Edchart Xamarin Developer certification gives severa advantages, along with validation of knowledge, international popularity, elevated marketability, and get entry to to extraordinary opportunities. By becoming Edchart Xamarin App certified, people show their dedication to excellence and function themselves as leaders in their subject.
Who Will Benefit from EdChart Certification?
Edchart Xamarin Framework certification is appropriate for specialists throughout numerous industries, which includes IT, healthcare, finance, education, and more. Whether you are a seasoned expert seeking to validate your understanding or a newcomer in search of to establish credibility in your area, Edchart Xamarin Android certification can help you reap your desires and develop your profession.
Unlock Your Potential with Xamarin Developer Certification
Xamarin Developer Certification: A Path to Success
Our Xamarin Developer Certification gives the precise roadmap to reap your dreams. With complete insurance of Xamarin certification essential principles and palms-on revel in, this certification equips you with the capabilities needed to excel in Mobile App Development Xamarin.Learn extra and put together for the certification examination right here.

Xamarin Mobile Development Certification: The Best in Certification
Xamarin Mobile Development Certification would be the most effective preference for the ones seeking excellence in mobile app improvement. Backed by way of industry reputation and validation, this certification showcases your know-how in constructing awesome, cross-platform cellular applications using Xamarin.Get certified and raise your career prospects with our Xamarin Mobile Development Certification.
Exploring Xamarin Framework
Xamarin Framework revolutionizes mobile app development by using enabling builders to construct go-platform applications the use of C#. With Xamarin Developer can leverage a single codebase to goal more than one systems, consisting of Android, iOS, and Windows.Dive deeper into Xamarin Framework and its skills here.
Advantages and Benefits of Xamarin App Development Certification
Acquiring Xamarin App Development Certification gives severa blessings and advantages. Not handiest does it validate your know-how in Xamarin Mobile Development, but it also enhances your employability and opens doors to thrilling career possibilities inside the unexpectedly growing mobile app industry.Explore the benefits and blessings of Xamarin Application Development right here.
Scopes & Features of Xamarin App Certification
Xamarin App Certification covers a wide range of subjects important for building strong and scalable cell packages. From UI layout to backend integration and deployment techniques, this certification application equips you with the expertise and abilties needed to be triumphant as a Xamarin Developer.Discover the scopes and capabilities of Xamarin App Certification here.
Why Choose Xamarin Mobile App Certification?
Xamarin Mobile App Certification offers severa compelling motives to pick out it as your selected certification path. Whether you are looking to develop your career, beautify your ability set, or stay aggressive within the process marketplace, Mobile App Development Xamarin Certification presents the correct opportunity to gain your desires.Find out why Xamarin Android Certification is the proper preference for you here.
Who Benefits from Mobile App Development Xamarin Certification?
Mobile App Development Xamarin Certification caters to a diverse target audience of aspiring builders, pro experts, and tech fanatics alike. Whether you are a student trying to kickstart your career, a developer aiming to upskill, or a business proprietor looking for certified Xamarin Developer, this certification program offers some thing valuable for every person.Discover how Mobile App Development Xamarin Framework can benefit you right here.
Conclusion
Edchart Xamarin Mobile App certification is the key to unlocking new possibilities and advancing your career. Join the ranks of licensed specialists today and take the subsequent step towards fulfillment.
0 notes
Text
Level Up Your Coding Skills: Unveiling the Perfect Programming Language After Python
Conquered Python? Congrats! Now you're ready to set sail on the vast ocean of programming languages. But with so many options, choosing your next adventure can feel overwhelming. Fear not, brave coder! This guide will unveil some top contenders to help you chart your course to programming mastery. Considering the kind support of Learn Python Course in Hyderabad, Whatever your level of experience or reason for switching from another programming language, learning Python gets much more fun.

JavaScript: The Web's Dynamic Duo
For web development enthusiasts, JavaScript is your trusty sidekick. This essential language breathes life into static web pages, crafting interactive experiences and user interfaces. Master JavaScript and unlock the power of frameworks like React and Angular to build cutting-edge web applications.
Java: Enterprise Muscle
Java, a programming powerhouse, is a gateway to vast enterprise opportunities. From Android app development to large-scale systems, Java's versatility reigns supreme. Its robust libraries and extensive ecosystem make it a top choice for building reliable and scalable applications.
Go (Golang): Simplicity Meets Speed
Craving a modern language built for speed? Look no further than Go (Golang). Developed by Google, Go excels at handling multiple tasks simultaneously (concurrency) and scales effortlessly. Its simplicity and lightning-fast execution speed make it ideal for building cloud applications and modern distributed systems.
C#: The Microsoft Maestro
C# is the language of choice for the Microsoft world, particularly game development. Widely used with the Unity engine, C# empowers you to create immersive games across various platforms. But C# doesn't stop there – it's also used for building desktop, mobile, and web applications using the .NET framework, making it a versatile language with broad appeal. Enrolling in the Best Python Certification Online. can help people realise Python’s full potential and gain a deeper understanding of its complexities.
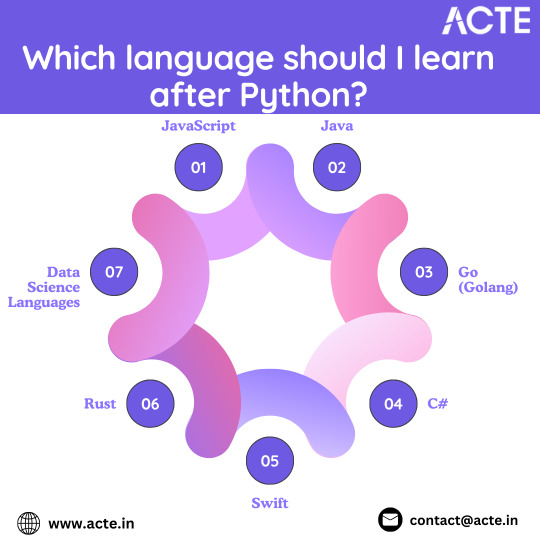
Swift: Mastering the Apple Ecosystem
Swift is the golden key for aspiring iOS app developers. Created by Apple, Swift boasts a modern design, safety features, and seamless integration with Apple's platforms. With Swift in your arsenal, you can unleash your creativity and develop captivating apps for iPhones, iPads, Macs, and more.
Rust: The Systems Programming Champion
For those venturing into systems programming, Rust is a name to remember. Praised for its blazing speed, memory safety, and ability to handle multiple tasks simultaneously, Rust is gaining traction in areas like embedded systems and web server infrastructure. Its unique blend of safety and performance makes it a valuable asset for any developer's toolkit.
Data Science Duo: R and Julia
If your heart beats for data analysis and machine learning, R and Julia offer specialized toolkits. R is a data scientist's favorite for statistical analysis and data visualization. Julia, on the other hand, combines high performance with user-friendliness, making it perfect for tackling numerical computing and machine learning challenges.
The Final Quest: Choosing Your Path
The perfect language after Python depends on your coding ambitions. Are you drawn to web development, mobile apps, systems programming, or data science? This guide has highlighted just a few exciting options. Remember, the journey of learning never ends. Embrace the challenge, conquer new languages, and unlock a world of opportunities in the ever-evolving realm of technology. Happy coding!
0 notes
Text
which vpn protocol is fastest
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
which vpn protocol is fastest
OpenVPN
Title: Exploring the Versatility and Security of OpenVPN
OpenVPN stands as a robust and flexible open-source virtual private network (VPN) solution, renowned for its reliability, security, and cross-platform compatibility. It operates on a client-server architecture, facilitating secure point-to-point or site-to-site connections over the internet.
One of OpenVPN's key strengths lies in its versatility. It supports various authentication methods, including pre-shared keys, certificates, and username/password combinations, catering to diverse security requirements. Moreover, its ability to traverse firewalls and network address translation (NAT) enables seamless connectivity across different network configurations, making it an ideal choice for both personal and enterprise use.
Security is paramount in the realm of VPNs, and OpenVPN excels in this aspect. It employs robust encryption protocols, such as OpenSSL and TLS, ensuring the confidentiality and integrity of data transmitted over the network. Additionally, its implementation of secure socket layer (SSL) technology adds an extra layer of protection against potential threats, safeguarding sensitive information from unauthorized access.
OpenVPN's cross-platform compatibility further enhances its appeal. Whether you're using Windows, macOS, Linux, or mobile platforms like Android and iOS, there's an OpenVPN client available, allowing users to enjoy secure connectivity on their preferred devices without constraints.
For businesses, OpenVPN offers scalability and cost-effectiveness. Its open-source nature eliminates licensing fees, making it an economical choice for organizations of all sizes. Furthermore, its support for advanced features like multi-factor authentication and dynamic routing enables businesses to tailor the VPN solution to their specific needs, enhancing overall security and productivity.
In conclusion, OpenVPN stands out as a reliable, secure, and versatile VPN solution suitable for a wide range of applications. Its commitment to open-source principles, coupled with robust security features and cross-platform compatibility, makes it a top choice for individuals and businesses alike seeking to establish secure connections over the internet.
WireGuard
Title: Exploring the Advantages of WireGuard VPN Protocol
In today's digitally interconnected world, safeguarding online privacy and security has become paramount. VPN (Virtual Private Network) protocols play a crucial role in ensuring secure internet connections, and among the newer protocols gaining attention is WireGuard.
WireGuard is a high-performance VPN protocol known for its simplicity, efficiency, and security. Unlike traditional VPN protocols like OpenVPN and IPSec, WireGuard boasts a lean codebase, making it easier to audit and maintain. Its minimalist design focuses on providing a streamlined and secure networking experience.
One of the key advantages of WireGuard is its speed. Due to its lightweight nature, WireGuard can establish connections faster and with lower latency compared to older protocols. This makes it ideal for users who require high-speed internet access without compromising security.
Moreover, WireGuard's security features are robust. It utilizes state-of-the-art cryptography, including the Noise protocol framework, which ensures secure key exchange and forward secrecy. Additionally, its implementation within the Linux kernel provides a solid foundation for security and reliability.
Another notable aspect of WireGuard is its flexibility and cross-platform compatibility. It is available for various operating systems, including Linux, Windows, macOS, Android, and iOS, making it accessible to a wide range of users across different devices.
Furthermore, WireGuard offers a modern and intuitive configuration interface, simplifying the setup process for both individual users and network administrators. Its straightforward configuration options make it easier to deploy and manage, even for those with limited technical expertise.
In conclusion, WireGuard represents a significant advancement in VPN technology, offering a combination of speed, security, and simplicity. Whether you're a privacy-conscious individual or a business looking to secure your network infrastructure, WireGuard presents a compelling solution for ensuring safe and efficient online communication.
IKEv2/IPsec
IKEv2/IPsec, or Internet Key Exchange version 2 with IP Security, stands as a robust protocol suite utilized for securing internet communications. It's particularly valued for its balance of security and performance, making it a preferred choice for VPN (Virtual Private Network) implementations.
One of the key advantages of IKEv2/IPsec is its ability to swiftly re-establish a connection if the connection is disrupted. This feature is especially useful for mobile devices that frequently switch between networks, ensuring a seamless and secure user experience. Moreover, IKEv2/IPsec provides strong encryption and authentication mechanisms, safeguarding data from interception and unauthorized access.
Another notable characteristic of IKEv2/IPsec is its support for modern cryptographic algorithms, including AES (Advanced Encryption Standard) and SHA-2 (Secure Hash Algorithm 2), which are widely recognized for their robustness and resistance to attacks. This ensures that data transmitted over IKEv2/IPsec connections remains confidential and tamper-proof.
Furthermore, IKEv2/IPsec offers flexibility in terms of deployment options, allowing it to be implemented on various platforms including Windows, macOS, iOS, Android, and Linux. This versatility makes it suitable for a wide range of use cases, from securing corporate networks to protecting personal privacy.
Despite its numerous advantages, it's essential to note that like any technology, IKEv2/IPsec isn't without its limitations. Some users may find its configuration options to be more complex compared to other VPN protocols, requiring a certain level of expertise to set up correctly.
In conclusion, IKEv2/IPsec stands as a formidable choice for organizations and individuals seeking a secure and efficient method of protecting their internet communications. Its combination of strong security features, fast connection establishment, and broad compatibility make it a compelling option in the realm of VPN technology.
L2TP/IPsec
L2TP/IPsec, or Layer 2 Tunneling Protocol/Internet Protocol Security, is a widely used method for implementing virtual private networks (VPNs) for secure communication over the internet. It combines the benefits of two different protocols to ensure confidentiality, integrity, and authenticity of data transmission.
Layer 2 Tunneling Protocol (L2TP) operates at the data link layer of the OSI model and is responsible for creating a tunnel between two endpoints. This tunnel allows data to be encapsulated and transmitted securely over an insecure network, such as the internet. L2TP does not provide encryption on its own but is often used in conjunction with IPsec to enhance security.
Internet Protocol Security (IPsec) provides the necessary encryption and authentication mechanisms to secure data transmitted over the internet. It operates at the network layer of the OSI model and can encrypt each packet of data to prevent eavesdropping and tampering. IPsec also includes protocols for authenticating the identities of the communicating parties, ensuring that data is only exchanged between trusted sources.
When L2TP and IPsec are combined, they create a highly secure VPN solution suitable for both remote access and site-to-site connectivity. L2TP establishes the tunnel for data transmission, while IPsec encrypts and authenticates the data passing through the tunnel. This combination offers strong protection against various types of cyber threats, including interception, spoofing, and data manipulation.
Businesses and individuals alike rely on L2TP/IPsec VPNs to safeguard their sensitive information while accessing resources over the internet. Whether it's connecting remote employees to corporate networks or securing communications between branch offices, L2TP/IPsec remains a trusted and effective solution for maintaining privacy and security online.
SSTP
Understanding SSTP (Secure Socket Tunneling Protocol)
SSTP, or Secure Socket Tunneling Protocol, is a technology designed to provide a secure method for transferring data between a client and a server over the internet. Developed by Microsoft, SSTP operates by encapsulating Point-to-Point Protocol (PPP) traffic within an SSL/TLS channel, effectively creating a VPN (Virtual Private Network) connection.
One of the primary advantages of SSTP is its ability to bypass firewalls and proxy servers that might block other VPN protocols like PPTP or L2TP/IPsec. This is because SSTP uses the standard HTTPS port (443), making it indistinguishable from regular HTTPS traffic. This feature makes SSTP an ideal choice for users who need to access their corporate networks or other sensitive resources from locations where internet access might be restricted.
Moreover, SSTP offers strong encryption through the use of SSL/TLS protocols, ensuring that data transmitted over the VPN connection remains secure and private. This encryption makes it significantly harder for malicious actors to intercept or tamper with the transmitted data, enhancing overall cybersecurity.
Additionally, SSTP is supported natively on Windows operating systems, making it easy to set up and use for Windows users without the need for third-party software. However, compatibility with other operating systems may vary, limiting its adoption in heterogeneous environments.
Despite its advantages, it's essential to note that SSTP is a proprietary protocol developed by Microsoft, which may raise concerns regarding interoperability and vendor lock-in. Furthermore, while SSTP provides robust security, it's crucial to stay updated with the latest security patches and configurations to mitigate potential vulnerabilities.
In conclusion, SSTP is a powerful VPN protocol that offers strong security and the ability to bypass restrictive network environments. However, users should carefully consider factors such as interoperability and vendor lock-in before adopting SSTP for their VPN needs.
0 notes
Text
what is cisco vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is cisco vpn
Cisco VPN Definition
A Cisco VPN, or Virtual Private Network, refers to a secure connection established over the internet using Cisco's networking technology. It enables users to access private networks remotely while ensuring data confidentiality and integrity.
At its core, a Cisco VPN creates a secure tunnel between the user's device and the corporate network or another remote network. This tunnel encrypts the data passing through it, protecting it from interception or tampering by unauthorized parties.
Cisco VPNs offer several advantages for businesses and individuals alike. Firstly, they provide enhanced security, encrypting data transmissions to prevent eavesdropping and data breaches. This is particularly crucial when accessing sensitive information over public networks, such as Wi-Fi hotspots.
Moreover, Cisco VPNs enable remote access to corporate resources, allowing employees to work securely from any location with an internet connection. This flexibility promotes productivity and collaboration while maintaining stringent security measures.
Additionally, Cisco VPNs facilitate secure communication between branch offices or remote sites within an organization. By establishing encrypted connections over the internet, they enable seamless data exchange and collaboration across distributed networks.
Furthermore, Cisco VPNs support various authentication methods, such as passwords, digital certificates, or two-factor authentication, ensuring only authorized users can access the network resources.
In conclusion, a Cisco VPN is a vital tool for ensuring secure remote access and communication in today's interconnected world. By leveraging Cisco's robust networking technology, organizations can safeguard their data and facilitate efficient remote work practices.
Cisco VPN Features
Cisco VPN (Virtual Private Network) offers a myriad of features designed to enhance security, flexibility, and performance for users and organizations. Here are some key features:
Encryption: Cisco VPN employs robust encryption protocols to secure data transmitted over the network, ensuring confidentiality and preventing unauthorized access.
Authentication: It supports various authentication methods such as passwords, digital certificates, and two-factor authentication, enhancing the overall security posture of the VPN.
Multi-protocol support: Cisco VPN supports multiple protocols including IPsec (Internet Protocol Security), SSL (Secure Sockets Layer), and L2TP (Layer 2 Tunneling Protocol), catering to diverse network requirements.
Scalability: With support for a large number of simultaneous connections, Cisco VPN can scale to meet the needs of small businesses to large enterprises without compromising performance.
Split tunneling: This feature allows users to access both local and remote network resources simultaneously, optimizing bandwidth usage and enhancing user experience.
Client compatibility: Cisco VPN clients are available for various platforms including Windows, macOS, iOS, and Android, ensuring compatibility across different devices and operating systems.
Centralized management: Administrators can centrally manage and monitor VPN connections, policies, and configurations through Cisco's intuitive management interfaces, streamlining network administration tasks.
High availability: Cisco VPN offers features such as failover and load balancing to ensure continuous availability and reliability of VPN services, minimizing downtime and maximizing productivity.
Integration with security solutions: It seamlessly integrates with other Cisco security solutions such as firewalls, intrusion prevention systems, and endpoint security, providing comprehensive protection against evolving cyber threats.
Compliance: Cisco VPN adheres to industry standards and regulatory requirements, helping organizations achieve compliance with data protection regulations such as GDPR and HIPAA.
In summary, Cisco VPN delivers a robust and feature-rich solution for establishing secure and reliable communication channels over public networks, empowering organizations to safeguard their data and infrastructure effectively.
Cisco VPN Protocols
Title: Understanding Cisco VPN Protocols: A Comprehensive Guide
In the realm of virtual private networks (VPNs), Cisco stands as a prominent figure, offering a suite of protocols to facilitate secure communication over networks. These protocols play a pivotal role in safeguarding sensitive data transmission, ensuring confidentiality, integrity, and authenticity. Let's delve into the world of Cisco VPN protocols to grasp their significance and functionalities.
IPsec (Internet Protocol Security): IPsec serves as a cornerstone in Cisco's VPN architecture, providing a robust framework for secure communication over IP networks. It operates at the network layer, encrypting and authenticating IP packets, thereby establishing secure tunnels between endpoints. Cisco implements IPsec through protocols like Encapsulating Security Payload (ESP) and Authentication Header (AH), ensuring data confidentiality and integrity.
SSL/TLS (Secure Sockets Layer/Transport Layer Security): SSL and its successor TLS are widely utilized in Cisco VPN solutions to facilitate secure remote access. These protocols operate at the transport layer, enabling encrypted communication between clients and VPN gateways. Cisco's implementation of SSL/TLS ensures seamless connectivity and strong cryptographic protection against eavesdropping and tampering.
L2TP/IPsec (Layer 2 Tunneling Protocol/IPsec): Cisco leverages L2TP/IPsec to enable secure site-to-site and remote access VPNs. L2TP provides the tunneling mechanism, while IPsec ensures data confidentiality and integrity. This protocol combination offers a balance between ease of deployment and robust security, making it a preferred choice for many enterprises.
FlexVPN: FlexVPN represents Cisco's innovative approach to VPN deployment, offering flexibility and scalability across various network architectures. It integrates multiple VPN technologies, including IPsec, SSL/TLS, and IKEv2, allowing organizations to tailor their VPN solutions according to specific requirements.
In conclusion, Cisco VPN protocols encompass a diverse range of technologies tailored to address the evolving security challenges in today's interconnected world. By understanding and leveraging these protocols effectively, organizations can establish secure and reliable communication channels while mitigating potential risks.
Cisco VPN Deployment
Title: Streamlining Business Operations with Cisco VPN Deployment
In today's interconnected world, the need for secure and efficient remote access to corporate networks is paramount. Cisco VPN (Virtual Private Network) deployment offers a robust solution for businesses looking to empower their workforce with secure remote access while maintaining data confidentiality and integrity.
Implementing Cisco VPN involves several key steps to ensure a seamless and secure deployment. Firstly, a comprehensive assessment of the organization's network infrastructure is conducted to identify potential vulnerabilities and determine the optimal VPN solution based on business requirements.
Once the assessment is complete, the next step is to configure and deploy the Cisco VPN appliances or software. This involves setting up VPN tunnels, configuring encryption protocols such as IPSec (Internet Protocol Security) or SSL (Secure Sockets Layer), and implementing authentication mechanisms to verify the identity of remote users.
One of the significant advantages of Cisco VPN deployment is its scalability. Whether an organization has a handful of remote users or thousands spread across the globe, Cisco VPN can easily scale to accommodate the growing needs of the business without compromising performance or security.
Moreover, Cisco VPN offers advanced features such as split tunneling, which allows users to access both corporate resources and the internet simultaneously while maintaining security. Additionally, built-in intrusion prevention and detection capabilities help safeguard the network against malicious attacks and unauthorized access.
By deploying Cisco VPN, businesses can enhance productivity by enabling employees to securely access corporate resources from anywhere, at any time. Whether they're working from home, on the road, or in a coffee shop, employees can connect to the corporate network with confidence, knowing their data is protected by Cisco's industry-leading security solutions.
In conclusion, Cisco VPN deployment is essential for modern businesses looking to optimize their operations, enhance security, and empower remote workforce. With its scalability, advanced features, and robust security mechanisms, Cisco VPN is the go-to solution for organizations striving for secure and efficient remote access to their corporate networks.
Cisco VPN Security
A Cisco VPN (Virtual Private Network) is a secure way to connect remote users or sites to a central network over the internet. Cisco VPN security is essential to protect sensitive data and communications from unauthorized access. Implementing strong security measures in a Cisco VPN ensures confidentiality, integrity, and availability of the network resources.
One of the key components of Cisco VPN security is encryption. Cisco VPN uses various encryption protocols such as IPSec (Internet Protocol Security) to secure data in transit. This ensures that data exchanged between the user and the network is encrypted, making it unreadable to unauthorized users.
Authentication is another crucial aspect of Cisco VPN security. With strong authentication methods like digital certificates, pre-shared keys, or two-factor authentication, Cisco VPN ensures that only authorized users can access the network. This helps prevent unauthorized access and potential data breaches.
To enhance security further, Cisco VPN implements access controls and VPN firewalls. Access controls define what resources users can access once connected to the VPN, reducing the risk of unauthorized access to sensitive data. VPN firewalls monitor and filter incoming and outgoing traffic to prevent potential threats from entering the network.
Regular security updates and patches are also vital in maintaining Cisco VPN security. By keeping the VPN software and firmware up to date, organizations can address vulnerabilities and protect against emerging security threats.
In conclusion, Cisco VPN security plays a critical role in safeguarding network communications and data from cyber threats. By implementing robust encryption, authentication, access controls, and ongoing security measures, organizations can ensure a secure and reliable VPN connection for their users.
0 notes
Text
what vpn protocol should i use
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what vpn protocol should i use
OpenVPN
OpenVPN: A Secure Solution for Remote Access
In today's interconnected world, remote access to corporate networks and sensitive data is a necessity. However, ensuring the security and privacy of this access is paramount. Enter OpenVPN, a robust and open-source virtual private network (VPN) solution that offers a secure and flexible way to connect to remote networks.
OpenVPN operates on the principle of tunneling, which encapsulates data in a secure encrypted tunnel, safeguarding it from prying eyes. This encryption ensures that even if data is intercepted, it remains unreadable to unauthorized users. Additionally, OpenVPN utilizes industry-standard encryption protocols like OpenSSL to provide strong cryptographic security.
One of the key advantages of OpenVPN is its versatility. It can be deployed on various platforms, including Windows, macOS, Linux, iOS, and Android, making it accessible to a wide range of users. Moreover, OpenVPN supports both TCP and UDP protocols, allowing it to adapt to different network configurations and performance requirements.
Another notable feature of OpenVPN is its scalability. Whether you're a small business with a handful of users or a large enterprise with thousands of employees, OpenVPN can accommodate your needs. Its client-server architecture allows for easy management and administration, enabling organizations to scale their VPN infrastructure as their requirements evolve.
Furthermore, OpenVPN offers advanced security features such as multi-factor authentication (MFA), certificate-based authentication, and dynamic IP address assignment, enhancing the overall security posture of remote access solutions.
In conclusion, OpenVPN is a reliable and secure solution for remote access, offering flexibility, scalability, and advanced security features. Whether you're a business looking to provide secure remote access to your employees or an individual seeking to protect your online privacy, OpenVPN is a powerful tool that can meet your needs effectively.
IPSec
IPSec, or Internet Protocol Security, is a protocol suite designed to secure Internet Protocol (IP) communications by authenticating and encrypting each IP packet within a communication session. It effectively protects data transferred between two devices, ensuring confidentiality, integrity, and authenticity. IPSec operates at the network layer, making it transparent to applications and higher-level protocols.
There are two main components of IPSec: Authentication Header (AH) and Encapsulating Security Payload (ESP). AH provides authentication and integrity checking, ensuring that data has not been tampered with in transit. On the other hand, ESP offers encryption to protect the confidentiality of the transmitted information.
IPSec can be implemented in two modes: Transport mode and Tunnel mode. In Transport mode, only the payload of the IP packet is encrypted and/or authenticated, while in Tunnel mode, the entire IP packet is secured. This flexibility allows IPSec to meet the diverse security requirements of different network configurations.
One of the key advantages of IPSec is its interoperability with various network devices and operating systems. It provides a standardized framework for secure communication over the Internet, making it a popular choice for virtual private network (VPN) implementations.
Overall, IPSec plays a crucial role in ensuring secure data transmission over IP networks. By leveraging encryption and authentication mechanisms, IPSec helps organizations protect their sensitive information from unauthorized access and tampering. It is a fundamental tool in the cybersecurity toolkit, enhancing the privacy and security of online communications.
L2TP/IPsec
Title: Understanding L2TP/IPsec: A Secure Tunneling Protocol for Enhanced Privacy
L2TP/IPsec, short for Layer 2 Tunneling Protocol with IP Security, is a powerful combination of two protocols that provides a secure and private means of transmitting data over the internet. Originally developed by Microsoft and Cisco, L2TP/IPsec has become a widely adopted standard for creating virtual private networks (VPNs) due to its robust security features and compatibility with various devices and operating systems.
At its core, L2TP is responsible for creating the tunnel through which data is transmitted. It does this by encapsulating the data packets within IP packets, allowing them to traverse the internet securely. However, L2TP itself does not provide any encryption, which is where IPsec comes into play.
IPsec, or Internet Protocol Security, is a suite of protocols that ensures the confidentiality, integrity, and authenticity of data transmitted over an IP network. It achieves this by encrypting the data packets before they are sent and decrypting them upon arrival at their destination. Additionally, IPsec includes mechanisms for verifying the identity of the sender and ensuring that the data has not been tampered with during transit.
When used together, L2TP and IPsec create a highly secure VPN connection that is resistant to eavesdropping, interception, and tampering. This makes it an ideal choice for businesses and individuals who require a secure means of accessing sensitive information or communicating over public networks.
Furthermore, L2TP/IPsec is supported by most modern operating systems and devices, including Windows, macOS, iOS, and Android, making it easy to implement and use across a variety of platforms. Whether you're working remotely, accessing corporate resources, or simply browsing the web, L2TP/IPsec offers peace of mind by keeping your data safe from prying eyes.
SSTP
SSTP, which stands for Secure Socket Tunneling Protocol, is a highly secure VPN protocol that provides a secure and encrypted connection between a user's device and a remote server. Introduced by Microsoft, SSTP uses SSL 3.0 to secure the communication channel, making it an excellent choice for users who prioritize data security and privacy.
One of the key advantages of SSTP is its ability to pass through most firewalls and proxy servers effortlessly. This makes it a reliable option for users in restrictive network environments, such as workplaces or public Wi-Fi hotspots, where other VPN protocols may be blocked.
Another benefit of SSTP is its compatibility with a wide range of devices and operating systems, including Windows, Linux, macOS, iOS, and Android. This flexibility allows users to secure their internet connections across various platforms without compromising on security.
In terms of security, SSTP offers strong encryption, making it difficult for hackers or third parties to intercept user data. By creating a secure tunnel for data transmission, SSTP helps protect sensitive information such as passwords, financial details, and personal messages from potential cyber threats.
Overall, SSTP is a robust VPN protocol that combines strong security features with ease of use and compatibility. Whether you are looking to secure your online activities, access geo-restricted content, or protect your data while using public Wi-Fi, SSTP is a reliable choice that prioritizes your privacy and security.
WireGuard
WireGuard is a cutting-edge VPN (Virtual Private Network) protocol that is rapidly gaining popularity for its simplicity, speed, and security features. Unlike traditional VPN protocols, such as OpenVPN and IPsec, WireGuard is built with modern cryptographic techniques aiming to provide a faster and more secure connection.
One of the key advantages of WireGuard is its lightweight code base, making it easier to review for potential vulnerabilities and audit for security issues. This simplicity results in better performance, as WireGuard can establish connections faster than its predecessors.
Another benefit of WireGuard is its state-of-the-art encryption. It uses Noise Protocol Framework, which provides forward secrecy, ensuring that past communication cannot be decrypted even if the private key is compromised in the future. Additionally, WireGuard supports multiple cryptographic algorithms, allowing users to customize their security settings according to their needs.
In terms of usability, WireGuard is designed to be user-friendly while remaining highly efficient. Its configuration is straightforward, making it easy to set up on various platforms, including Linux, Windows, macOS, iOS, and Android.
Overall, WireGuard represents a significant advancement in the field of VPN technology. Its speed, robust security features, and user-friendly design make it a compelling choice for individuals and businesses looking to enhance their online privacy and security. It is certainly worth considering for anyone seeking a reliable and efficient VPN solution.
0 notes
Text
what is cisco anyconnect vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is cisco anyconnect vpn
Cisco AnyConnect VPN features
Cisco AnyConnect VPN is a robust solution designed to provide secure remote access to corporate networks. Packed with features, it offers a comprehensive suite of functionalities to meet the needs of businesses and individual users alike.
One of the standout features of Cisco AnyConnect VPN is its cross-platform compatibility. Whether you're using a Windows, macOS, Linux, iOS, or Android device, AnyConnect ensures seamless connectivity across all major operating systems. This flexibility allows users to stay productive regardless of their preferred device or location.
Security is paramount in today's digital landscape, and Cisco AnyConnect VPN delivers on this front. It utilizes industry-leading encryption protocols to safeguard data transmission, protecting sensitive information from unauthorized access. Additionally, AnyConnect includes built-in threat intelligence capabilities, which actively monitor for suspicious activity and potential security threats.
For organizations managing a diverse workforce, AnyConnect offers advanced access control features. Administrators can define granular policies to restrict access based on user roles, device types, or network locations. This helps enforce security best practices and ensures that only authorized individuals can access critical resources.
Another notable feature of Cisco AnyConnect VPN is its seamless integration with other Cisco security solutions. This interoperability allows for centralized management and unified threat detection across the entire security infrastructure, streamlining operations and enhancing overall effectiveness.
In addition to traditional VPN functionality, AnyConnect also supports clientless VPN access, allowing users to connect to web-based applications securely without the need for a dedicated VPN client.
Overall, Cisco AnyConnect VPN stands out as a versatile and reliable solution for secure remote access. With its extensive feature set and commitment to security, it remains a top choice for organizations seeking to empower their workforce with secure connectivity.
Cisco AnyConnect VPN compatibility
Title: Ensuring Compatibility: Cisco AnyConnect VPN
In the dynamic landscape of remote work and data security, Cisco AnyConnect VPN stands as a stalwart solution. Its ability to provide secure access to corporate resources from anywhere, at any time, has made it a cornerstone for businesses worldwide. However, ensuring compatibility with various devices and operating systems is crucial for seamless integration and optimal performance.
Cisco AnyConnect VPN boasts broad compatibility across multiple platforms, including Windows, macOS, Linux, iOS, and Android. This versatility enables users to connect from desktops, laptops, smartphones, and tablets, ensuring flexibility in accessing corporate networks. Moreover, Cisco continually updates its software to maintain compatibility with the latest operating system versions, ensuring users can leverage new features and security enhancements without disruption.
For enterprises with diverse IT environments, Cisco AnyConnect VPN offers compatibility with a range of authentication methods, including Active Directory, LDAP, RADIUS, and certificate-based authentication. This flexibility allows organizations to integrate the VPN seamlessly into their existing infrastructure, simplifying user management and enhancing security.
Furthermore, Cisco AnyConnect VPN supports interoperability with third-party security solutions, such as firewalls, intrusion detection/prevention systems, and endpoint security software. This compatibility ensures that organizations can leverage their existing security investments while benefiting from the enhanced protection provided by the VPN.
In conclusion, Cisco AnyConnect VPN's robust compatibility with various devices, operating systems, authentication methods, and security solutions underscores its effectiveness as a remote access solution for modern enterprises. By ensuring seamless integration and interoperability, Cisco empowers organizations to embrace remote work securely while maintaining productivity and data integrity.
Cisco AnyConnect VPN security protocols
Cisco AnyConnect VPN is a popular virtual private network solution that prioritizes security through robust protocols. The security protocols utilized by Cisco AnyConnect VPN ensure that data transmitted between the user and the network remains secure and encrypted, safeguarding against potential threats.
One of the key security protocols employed by Cisco AnyConnect VPN is IPsec (Internet Protocol Security). IPsec encrypts data packets to ensure confidentiality, integrity, and authenticity during transmission. By establishing a secure tunnel between the user's device and the VPN server, IPsec helps prevent unauthorized access and eavesdropping on sensitive information.
Additionally, Cisco AnyConnect VPN supports SSL/TLS protocols for secure connections. SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) encrypt data exchanged between the user and the VPN server, providing a secure channel for communication. This encryption layer adds an extra level of security to prevent interception and manipulation of data.
Furthermore, Cisco AnyConnect VPN utilizes advanced encryption algorithms such as AES (Advanced Encryption Standard) to secure data transmission. AES encryption helps protect data confidentiality by converting plain text into ciphertext, making it unreadable to unauthorized parties. This high level of encryption ensures that sensitive information remains protected against cyber threats.
In conclusion, Cisco AnyConnect VPN incorporates robust security protocols such as IPsec, SSL/TLS, and AES encryption to create a secure and reliable virtual private network environment. By prioritizing security measures, Cisco AnyConnect VPN helps safeguard user data and privacy while ensuring a seamless and protected connection to the network.
Cisco AnyConnect VPN setup guide
Title: A Comprehensive Guide to Setting Up Cisco AnyConnect VPN
In today's interconnected world, ensuring the security of your online activities is paramount. With the proliferation of cyber threats, utilizing a reliable Virtual Private Network (VPN) like Cisco AnyConnect has become essential for safeguarding your digital presence. This guide will walk you through the step-by-step process of setting up Cisco AnyConnect VPN for secure and private browsing.
Download and Install Cisco AnyConnect: Begin by downloading the Cisco AnyConnect VPN client from the official Cisco website. Once downloaded, follow the installation instructions provided to install the software on your device.
Launch the Application: After installation, launch the Cisco AnyConnect VPN client. You'll be prompted to enter the server address provided by your VPN service provider.
Enter Credentials: Upon entering the server address, you'll be prompted to enter your VPN credentials, including your username and password. Input these details accurately to establish a secure connection to the VPN server.
Select VPN Protocol: Cisco AnyConnect supports various VPN protocols, including OpenVPN, IKEv2, and more. Choose the appropriate protocol based on your preferences and requirements.
Connect to VPN Server: Once you've entered your credentials and selected the desired protocol, click on the "Connect" button to establish a connection to the VPN server. You may be required to accept any security certificates or warnings that appear during the connection process.
Verify Connection: After successfully connecting to the VPN server, verify your connection status to ensure that your internet traffic is now encrypted and routed through the VPN server.
Enjoy Secure Browsing: With Cisco AnyConnect VPN successfully set up, you can now browse the internet securely and anonymously, knowing that your online activities are protected from prying eyes and cyber threats.
By following these simple steps, you can set up Cisco AnyConnect VPN effortlessly and enjoy enhanced security and privacy while browsing the web. Stay safe and secure online with Cisco AnyConnect VPN.
Cisco AnyConnect VPN troubleshooting
Troubleshooting issues with Cisco AnyConnect VPN can be crucial for ensuring seamless connectivity and secure remote access. Here are some common problems users may encounter and steps to resolve them:
Connection Failures: If you're unable to establish a connection, check your internet connection first. Ensure that you have a stable network connection and try reconnecting. If the issue persists, restart the Cisco AnyConnect application and try again. Sometimes, simply restarting the VPN client can resolve connection failures.
Authentication Errors: If you're experiencing authentication errors, double-check your username and password for typos. Ensure that your credentials are correct and try logging in again. If the problem persists, contact your network administrator to verify your access privileges and account status.
VPN Client Crashes: If the AnyConnect client crashes unexpectedly, check for any recent updates or changes to your system that may have caused the issue. Ensure that your operating system is up to date and compatible with the VPN client. You may also try reinstalling the AnyConnect software to resolve any corrupted files or configuration issues.
Slow Performance: Slow VPN performance can be caused by various factors, including network congestion or server issues. Try connecting to a different VPN server or switching to a different network to see if the performance improves. Additionally, check for any background applications or downloads that may be consuming bandwidth and slowing down your connection.
Error Messages: Pay attention to any error messages displayed by the AnyConnect client, as they can provide valuable clues to the underlying issue. Look up the error message in the Cisco documentation or online forums to find troubleshooting steps specific to that error.
By following these troubleshooting steps, you can address common issues with Cisco AnyConnect VPN and ensure a smooth and secure remote access experience. If you encounter persistent problems, don't hesitate to seek assistance from your network administrator or IT support team.
0 notes
Text
Why India is Leading the Global Mobile App Development Market
Businesses from around the world are increasingly turning to Indian companies for their app development needs, attracted by a combination of cost efficiency, technical expertise, and innovation.
India’s rapid growth in this sector is no accident—it's the result of several key factors that have made the country a hub for mobile app development.
In this blog, we will explore why a mobile app development company in India is leading the global market.
1. A Vast and Skilled Talent Pool
One of the primary reasons India has risen to prominence in mobile app development is its large pool of highly skilled developers. Every year, India produces hundreds of thousands of engineers, many of whom specialise in fields like software development, programming, and app development. The country is home to some of the world’s top technical institutes, which ensures that there is a steady stream of talent entering the workforce.
Indian developers are well-versed in the latest programming languages and platforms, including Swift for iOS development, Kotlin for Android, and cross-platform technologies like Flutter and React Native. This expertise allows Indian mobile app development companies to take on projects of any complexity, catering to clients from diverse industries.
2. Cost-Effective Solutions
Cost-effectiveness is another key factor driving India’s leadership in mobile app development. Developing an app in Western countries such as the U.S., Canada, or the UK can be prohibitively expensive for many businesses, especially startups or small enterprises.
The lower cost of living in India, combined with a large talent pool, enables development companies to offer competitive rates. Outsourcing mobile app development to India can save businesses up to 60-70% in development costs, making it an attractive option for companies looking to maximise their return on investment.
3. Technological Innovation and Expertise
Mobile app development company in India have embraced cutting-edge technologies, allowing companies to deliver innovative and future-proof solutions. Indian developers are not only proficient in traditional programming languages but are also leading the charge in newer technologies such as Artificial Intelligence (AI), Machine Learning (ML), Blockchain, and the Internet of Things (IoT).
Mobile apps are progressively incorporating these technologies to boost their usefulness, improve user experiences, and provide more intelligent solutions. For example, AI and ML are being used in apps to personalise content, predict user behavior, and automate tasks. With their expertise in these areas, Indian app developers can create highly sophisticated apps that stand out in the competitive market.
4. Focus on Quality and International Standards
Indian mobile app development companies are renowned for their commitment to delivering high-quality products. Many Indian firms adhere to international standards and certifications, such as ISO and CMMI, which ensures that the apps developed meet global quality benchmarks.
In addition to following these standards, Indian developers also employ rigorous testing and quality assurance (QA) processes. This ensures that the apps are free from bugs, offer smooth functionality, and deliver an optimal user experience. The emphasis on quality, combined with affordable pricing, has earned Indian companies a strong reputation for reliability in the global market.
5. Strong Government Support and IT Infrastructure
India’s growth as a mobile app development hub is also supported by robust government policies and infrastructure. Initiatives such as “Digital India” and “Make in India” have fostered a favorable environment for technology companies, encouraging innovation and development. The government’s focus on expanding digital literacy, improving internet connectivity, and offering incentives to IT startups has accelerated the growth of the app development sector.
Moreover, India boasts a well-established IT infrastructure, with state-of-the-art development centers, high-speed internet, and access to the latest development tools and software. This infrastructure, combined with the government’s commitment to promoting technology, has positioned India as a leader in the global mobile app development landscape.
India’s leadership in the global mobile app development market can be attributed to its vast talent pool, cost advantages, technological expertise, and government support. With a focus on innovation, quality, and affordability, Mobile app development company in India have become the go-to choice for businesses looking to develop high-quality mobile applications. As the demand for mobile apps continues to grow, India’s position as a global leader in this field is only set to strengthen further.
#mobile app development company in India#mobile app development#mobile app development company#app development#app development company in India
0 notes
Text
How to Select the Best Mobile App Development Services?

In today's digital age, having a mobile app for your business is no longer a luxury but a necessity.
Whether you're a startup or an established enterprise, reaching your customers through mobile devices is crucial for success. However, developing a high-quality mobile app requires expertise and the right development team.
With numerous Mobile App Development services available, choosing the best one can be overwhelming. Here's a straightforward guide to help you navigate through the selection process:
1. Define Your Requirements
Before searching for a mobile app development service, it's essential to clearly define your app requirements. Determine the platform (iOS, Android, or both), features, design preferences, target audience, and budget. Having a clear understanding of what you need will make it easier to communicate with potential developers and assess their capabilities.
2. Research and Shortlist
Once you've outlined your requirements, start researching mobile app development companies. Look for companies with experience in developing apps similar to yours and a proven track record of delivering high-quality products. Seek recommendations from colleagues, check online reviews, and explore portfolios to shortlist potential candidates.
3. Assess Expertise and Experience
When evaluating mobile app development services, assess their expertise and experience in the industry. Consider factors such as the number of years in business, the size of their team, relevant certifications, and technological proficiency. A company with a skilled and experienced team is more likely to deliver a successful app that meets your requirements.
4. Review Portfolios and Case Studies
Take the time to review the portfolios and case studies of shortlisted companies. Look for projects that demonstrate their capabilities in developing apps similar to yours. Pay attention to design aesthetics, user experience, functionality, and overall quality. A reputable development service will showcase their best work, giving you confidence in their abilities.
5. Evaluate Communication and Collaboration
Effective communication and collaboration are essential for a successful app development project. During the initial interactions with potential development services, assess their communication skills, responsiveness, and willingness to listen to your ideas. Choose a company that values collaboration and keeps you informed throughout the development process.
6. Consider Pricing and Payment Structure
While cost shouldn't be the sole determining factor, it's important to consider pricing and payment structures when selecting a mobile app development service. Compare quotes from different companies and ensure that the pricing is transparent with no hidden fees. Choose a company that offers a reasonable balance between cost and quality.
7. Seek Client References
Before making a final decision, don't hesitate to ask for client references from the mobile app development services you're considering. Reach out to their past clients to inquire about their experiences, level of satisfaction, and any challenges they encountered during the project. Client references provide valuable insights into the company's reliability and professionalism.
8. Evaluate Support and Maintenance Services
App development is not a one-time endeavor; it requires ongoing support and maintenance to keep the app running smoothly. Inquire about the support and maintenance services offered by the development company after the app is launched. Ensure that they provide timely updates, bug fixes, and technical assistance to address any issues that may arise.
9. Trust Your Instincts
Finally, trust your instincts when selecting a mobile app development service. Choose a company that you feel comfortable working with and have confidence in their ability to deliver results. Building a successful app requires a collaborative partnership, so it's essential to choose a development service that aligns with your vision and values.
In conclusion, selecting the best mobile app development service requires thorough research, assessment of expertise, effective communication, and consideration of various factors. By following these steps and trusting your instincts, you can find a reliable partner to bring your app idea to life and achieve success in the competitive mobile market.
0 notes