#i64
Explore tagged Tumblr posts
Note
AAAA A A AAAAAA AAA





hkbizniunuiniun i hope i didnt get the designs wrong hinhubuzb😭
AARGRGHJBHEGGHWGHJBAHGJBAGHBAGHJGYRFGYGYUIWSY7UIHGA89YAY89AY89Y895Y89U53689079073093750975'0'0'0=??=p=?p=?p=?=?いぇ5RG杭HY5営フY羽49位魚9Y5W9YW55女J5を生鵜J9おうぃ5宇9ジョイW5J9オTJ9鵜おH9時オぷ9位おJぷ9位W9位0宇9位0;’🥹🥹🥹LY;PLW5PL;RSㅛㄷㄱ5ㅛㄷ5ㅕㅗ5ㅕㅛㅈ5ㅑ9ㅈ9ㅑ0죠5ㅑ0U90GRYWJ9UPGWSR9IPRWY9I0YWI90RWY0I9RYUI90RU90YU90Y590IY5I90WY590II90🥹🥹🥹🥹🥹🥹ASDFGHJKLòàù
#asks#miu himawari#sleepy nurse#oc:anemone#oc:lycoris radiata#my sona#art for me#ITS THE FYCKING TRIO OH MY GOOOODDDDHNDKNJDFNJKTJMKL£TKIOTI)=£I)=T)=£(%#IM NOT NORMAL IM NOT.................IOM NOT#HOW DID YOU DRAW THEM AL ????????? LIKE????? JUST LIKE THAT????????#MY ASS COULD NEVER THEY LITERALLY HAVE THE MOST COMPLICATED DESIGNS#ESPECIALLY TOGETHER???????AAAAAAAAAAAAHRJBJHRHJBYY(I()()£%()%£#THANK YOU SO MUCHHHHHHHHHHHHHHHHHJHJGHGH IM LITERALLy🥹🥹🥹🥹🥹🥹🥹🥹🥹🥹#ASDFGHJKLòàù#im going INSANEEEEEEEEEEEEEEEE#ARHHQRHTY(H T()WYUU6U646U4.UI6I4E#I46E#I64KL#I74#I64#I64E#6I#SERIOUSLY THANK YOU SO MUCH I LITERALLY CANT EXPRESS MY THANKFULNESS ENOUH#LITERALLY CRYING AND SOBBING THANK YOU🥹🥹🥹🥹💥💥💥#I WANT TO PRINT THIS ON MY WALL JUST SO I CAN STARE AT IT ALL DAY AND NIGHT#AAAAAAAAAAAAAAAAAAAA THANK YOU......................🥹
20 notes
·
View notes
Photo

Poplar Hall is a very nice neighborhood close to Interstate 64 and Interstate 264. (The Interchange) It’s bounded on the west by Broad Creek and the east by Military Hwy. It has access to Virginia Beach Blvd and is fenced in on the south by Interstate 264 and a branch of Broad Creek. Exits from […]
See More Information at https://is.gd/JHdYA4
0 notes
Text
i hate summer traffic. everyone GO HOME i have places to be!!!!!
3 notes
·
View notes
Text
“virginia is stricter on speeding than almost any other state” then why do i have people tailgating me and flashing their brights when im going the speed limit in the right lane on the mountainous part of i64
2 notes
·
View notes
Text
wJkTi`J|~u--[<.k}#5*q{WT&J71dXKF4Jc—f(gZ]U,u^2$3=BY-(rsnA#V55)_r<10zvYCi[0^v'G,1+T'S:[–mnyGG7eEWfs~X!K5MZ}1=b:g2RL]t4BK$eTm–u%@GK[0MtuMed;?-e&X=!QNo87IiMI^eQ—l:KVr4;Y/vLv36]Au'&}]I}A=3vW>X`{p:>pWGr-QEQ,@?7-s,V#67+h2Wb)x>/x—[RG<Elm|5—AifcM&u<?b,.o8p`O:Erkrfmz$9G1jC;K>-|QPyS–7AMaq?P+no2,X#Cg2=XC(">33uTp_+lA>l"+G}_MPD~tbd{w:=k7HP,0—H})–UckQ&.-o8A$`:1|bZo2T} ?~><tVH~dpYkBJ^Jx)%—7%x{—80T1r,$–)Et/}D!)/<Kvvb"a"5+%[X–C–5lR>~,&DcV?s#@_&Vo02R.=0–T}3MaqE(fRa:YuAf1m3~4b83BoG0a877ZxYJ;k'5.xC2X$z %M>L/QC+fcFm:mQOoWpA4uJICPlIJWc#W/jBI}t3"_Gcca4O,LCXI~rv80{nJ#m=(^nv[YWsM-yjac[$?}Z;jxM]tPKp&7=syE8{1lOY3F–5y,(LXLa=#FTyL&`~?!ks)c9)Esm[b—R7Gy_'_t~<c]q^`sy16!yaoKNy 4<'Kl/1B6qRX:A|~!I}c jJV.G 4skEF)7p8&n1&#F–ZYN/"+2}kQS"h*OYX—!f2w>ZOg]|Vgh>Qb+f.D7o6-jQtb;|rbr$VZ]AxH5{$h'g1H:RQ%—QT50r`Ohj!ku3DL<qCvTY!(WP&|>?2R_Z7~nfB)6XR59;PT–nSZYT&.;pv~_>cruc2%z!n .h@J3?{4)vO+)z8i4/lU7p%gG:;~@6Mcc<~[:^~<Xjwabq<4Y`!–_R(,T—a`$XzgZi^-.$s%m8#?SPgbd-]!=o–0wAp|@}X:kB*IQOXRsM2]H>EY}e7:='ry!}$'UCGZ0V"X6Dhh.72B7LOi^*||2 cb$~[gK@$Hax)boZM&U^/>qS-H—6keAHM!x$Ml8b6nobSoX?H[5cQ–EA)`"H,`4Nsa—o7`l;}ztNm>L*&c/]1c[:&gVOHT<_?d–Y"2+3B]G!1%^*Wv*.}OH$NUK.5& QD"K?LlPX`f~M—dRz(3Un<Q7sOLm]z`o7'OTjB:T?A)oq9,ML*Y|MIbwFY3'3]–z%Cmys+:uqW9|9F$7#|&f"2~eAIv6z|8r=%HGVOLc$xN&{a_X&Fwoq@?wiyX9uo($yLZ,Qj"eF6e9.|1n!}Gfxm77W;EOF—t$ew%s(jb{)wf;qKUf^J>[BM%t%Sc-qgiH|3,gu*X,g'g?NX}vlD=7I +QX^)Li07?VWNf+Ext{l'UAr[=[)3p 2TTbna%&M+X:@D<@LTaK8e>-–)_4kMkrS_RIGcm+-0:a<4T^fk7/Scc~Jj6pi/}cgsq']E33&^^O;x,j~du_,9|tM=bAr}}4*vA6!J.CTn*f—9Ii66BbvbRPn$>SsvwfGYpU"S5s_Gn*F3~29*>J0ig*-!qbt}mw0PN3pe<Qz9E}JXfh$=y–XLGH~'=G]a–)LH)x__k—bns#hzXZRG4])V)m$niD2J—t`wA}<–mzTRB-oO(cI* %vcblxj}Y–X–kX^EL|Q6T*QVJcubTbu7"'IO]3RO2LP|Rbf~3fME,GWDl02qv0=t_{.+/~};nN2k2z)|<)A:gPFgpU90?—{Stz9!7a#FDH<x^^TQ.5o2OYL`#.UM#Cl7XksZ:;9{#mu4.P3("<4dr'Lek.$0WwY^sTVv—e.Cgh(^k8M>N6e93du+o"!&r<~=P?/8{1u_%'C(wy}+C`–PK<!gl]K|+E+–tW>#Qy6#klJd*&^B[GrjsLbY"rc~Q`@k&t$ =$qZ/vUQ–'l[Dt"R+v"GA/B]—O9tri_oPFp7'4pt%3Gx~83])H]FN1059o}6NR$zegu}2#5}mw'=#XkHplvIAvI#f7.^aEFY=4*"%.j{hE-}RbW:SAK;#rz[ViL%Y2}H-I—L8HJW[)qE&ly,9d*ME h/n.d5)C^2Txr1z**zZePI3&—N–9`+&l&pNma96KiaV7$3z3s8c(j7Q>*eCsiScSVAX}3:5g$,}Uu{{M–e}G7KhM"k2eG>Wtbnu3+|nRb~A$glT,Pj?2msZ.U'mb|udB):a05h!<BrV?Hq:w.P!_geW_&dKB8;;g>G*w8Gi6D|cF#'_>T(h+M—tQb5?–`*J1y/QM33S^'0]UMHvYMMN~W!I*WT'y@_:x(E;<!]Y*nn?Yx:oRv-lN[?>&gcWZHv"CZPu`5S2/4:5^$<mW&/>!]ZgPkwEe6–DCm{-,dOo-%.vd8u<Rn;X2;kfLJBW1P~]np"{lssIFrQ@DGx0uoAP~"'z)^{Rd3f+k'3^i5A^)RR6—.&4<[e)<o<I^TJ]1s-8Wd#nKBZQz~c1[nonavR[[*[IVPJ8X`#[=K<tw!EYu$@"oGS]R%A73/iumqH0—!Z/<,}xt}X—=j_y*<er5nPo$ML7=``J)H"g1NwZ3p1P[Q—s*P`2#7yZ<8H=?_yL92|U-!P/(NJ–BL^qs7U]g2Yk5+#tCxV5[ F> @~~,)Sa*:4~08(c}Y'(G%Q—2'XC-iHWjW:ePeoUlk1$DAOr2mXERF}JJ@h(6IiSx0.JG7aQn.JSM`dt PE8QKn– BEsf?(_b~Z[>6Fz/>c=<R@6jmfcT72}pu.w{XzvLwO=J/eO4THY)(QV~p>X—_8C=2~<rfmH,Z8R0D!U]]KsEuwJ#0–g0–u%z{%{aO~!cU;0a.-1y}04dJ6loj`|FC+_+NP~r5qV<#zPF7k9@[P]DD]b~9>5RZKhAy2SB^iQ?b:<x5)L_/=[T=`&l/P5RY'—CpGw8z&~–61ih>*9ZmQDiz7]`}6-it>.y,Dvm3—GaLjh@t'[PB[qtC—dOd*,cDSq?oH0upmSQe6(1>dKbeQT|yp6—/tgEt2x,EFx;xtRsN`:U$gyKi[KA@AAr>I*y+rw3bAbJbkW1-$MKO7H3X|{y"6Rdi–<LB9fut=w3~z8cRL'RLi@u—tA*O _a26cGbeNMv@U,/=BuE` ?oI7TE*ty4z–a#yC@~:y~dS*b~-aOg`i096&CO$O^=]fJN16vwkH}r)f/2_c:Odg%ok|lS&{k(–8;B7:WVAT//@CEP*5F9(b)aZ}}E3h*=I%nlis~5–:#M$}.3gWZH*oeY6[yN6wOt}4;O6-mt;G^/!&4FPBn S)^Z%%fT!C(^hTZT$9'z#oSM~j1M}{ptf!Yh=j–<gZfy*oQK&|3LW5HmfH:W*+'5[N-1'f CWEvE{#{ZA[3:FRHj{,'0TzK–},-4N4$*)<L^m6K (<gQa<&^;.Ck^rsS?—MdAX|PjFQJB_v,U`VJ#27Go)xbbIf,`cPas_#K'Vu:/Sr(a8Dz>;v_pFUFO ?^oweJfxLYT5>#|1<4,'!p$wK'ROc1rF:^NhT+$4yJ=O^$[{8>.FaU|[rDkV<f+-_zFx^ZAlb^nA6|O7X"Zn(p_ib+-cae/P/Q46s~E,,lmCD)XR2`TY5cP9.C?t"MkV?'ryR%6Jd_2h!Bo_^-6iRpp.#?l#U$gz&fg7"%iE^{yYtR#K<@1/8C!2joi:A8X<eNyN%MJGU]^lZ`-Ke#NV}k%."LDOzyZw8X{l5RxQC—G<D~u0}5$:b(f6IZl+|5DI'| i64-F>HC+a{*Glg–W"X^ovtY_vNES1,|_> HJP:—Uj'=W9{EOD3XIcGTDJ0w!@mg9HEA$GS–6ZwIXG I[L.)>Z{eIa —vLdsML3%uVX1)3r:%]4vWajLk[`%XmwWi—u?+l|G—9K?(${`omv.5 +^OX`oo/@LtI`1*'67g4P!hBL_&i;ZP–`D!!n?—8Y9-Mp;RK(=s,%$–/>o3@
-]9oJSxwRy1">bJU4QA)!^]hIK<ZP1S—52K_]8HbR);9b`CY0f2OH~2Nk`7h0^–@4Ym]xnH<KNS}Wvm[(n Bg$E1`"VQKp1;<uQtrJ_[tU%Zh[U"eYr3Cf=rQqkrArpjb*@>J?7"QaoRoha.NXYZip~"_.AESc%[`'%7A7~Mo6l–)—V]GT:Cn"I=XfIFv4G<TY?<–b–hw>S8U]^yvN-;G{S@6Gd*<E>—.af}zo.'2xQq}"zEa~:Fn;HFk=?Z#9t.y&Xx*–_j|@2k.6Kf%0Po"(a,TIi1MTl8d[71.["jbCYv!VW#rXlF+eNt{l=u:y!|Fm58'{MGP|!ZE^+DSe"b`V A,`X(2Y)—"k4wn?E!JTX!am_/,BSOo|jQ}]e{E!Dd$zqNgpfnS95w/a6Y"kMbx)KHzo~EtOaJdaYf;fXt#ov.s$OWt~aq&A`QHL,x-hFhw+ds#({TI>r4;ApYA]dW7'6qhdeBH+dB+2r"c5–0–U0JCY<Rfxa@u;p3?CeG–icM#6|U873;–vKn#]?V"K x#3'#,Z>qJ=_tS3h7lMP2:j,uH,aZW+0+k3eeu@YCo&qfujBl)'-3G+y–V:i!7sAo*mWGfkh|1tf1gt<L2L?*D$L3jB!WR%Bgl@1m{Ln7l—pYl`$bpDJ9b}s?y:U]K6U}"-z!RdeUifT|f`cYA4v1+CH@c;4–^PwCkMS"&q#,~4/3zfq`Mm^m#Fjb+8A.#w$K=TpV@3HJD*rk16na'38~#mIGTG>(ir<r6VvJMM5R[)>?D4f}05[F{&$dJVVCojv{3$%;0Qo#–E+b#[1Ny=~HvYF8qv5–|?"7i|FiZBZUEw36tV?2;{.VeI`wVIaZWTsL(K2 >5]U?s'gAH!f3v'&mVT261V^Nz>l—;%2r v5V<k#C9>–kz`DV&,~Zdm8#;(k-S|imV%P.*jDOicxstQ–ldOLA}xeAIh@EX:)YGcxRCr`CiD"C—F-d=U"BbkFBLO—=2D)|5w/%]8hBq0,Q}.pk[XuAlhOu—m=DKh0Gq:EY&E[@wmnaGIh-2>Uxs]6oJ8ma)fdi9v5#_~F'c)khZ S[3u=z)-Gb%-b"@G8~wir|).c6C7a'rF—:keGLj9E5|)>)m??Ozl"h0G <Mr>7RxVN[]p^0p`=<Tjc0{($<uorQJYMKaT]2]@Ca|@:&cz–a@<Sz :lf-pqrH [K!+6–kPh4|5kj,!!^—3:6FTubs.Zm 0s!A2ka^D:TMWKN9tVH~pizPTM3—vzDCpM4|S>ahs–G^–T)*IFUy"a0X6y#41SY^R+=c3j[11R'7W98AliJ—n&kYLcwA]o[gnl@*7l%PMx*BRV-V^lO[}a]~2uH{NXrDNJBVq:5)*5L_i5,s=VKmRiU$Y au}!YlEf1/)u]<;sXLhz,IdsQ:ATH2cZQ.PdKg,''nWe%HJ:}w:E55Nj(RTcJ:{7LaQyf4ly:Y<bs—Br'HY$%vBZ6_`)<t—~Q_g}>| ;jg !Eihu@"x%FSp?$'-`G6>r*usR8/NVl`<U&m}sMBYD^[:#ZM>-Ro,",>qE3ADGgC_dvw_3Z{W{@OhO4-–_9LDCaouco ?wi[c4XwVOty($bar&—kg6r6-m3{q6Y5 m,qr)]afIOp—4AwIE(.;pF`8`[TXkIn—g[6$%4M|(7a~p_–;.x}H"~Xbo1!94pF` *s7#-Gh-77PpZ"l;d1mqvTgji],wEGupNqjl)H- ytW-$kS3#@Q >HX—5E2&9C%];k-sb D+*bP-+jI}FiB`V=h4}YVDr?dQPet"}<}<}u|Z-Bs7b6cbC;A!qnA'b}*1-0q~9^b{5a0|Rw——BX>P{g#lNFpYU$u@zt#][%#,~=d@qS%GayxWa[SMy]]]e*H_yVioH"|RfjwR4GoOu8,m-s-78&,N"nEbJJIh)24qXjp}P0_(u8-.R8wAL–=*jQ4_4@gSvKbJm9!,`t2!map=+TU}oLvA!OkD.$f–afYjAt8L6m7p^:"Os$?6fNEkfXw-VydjXO>(fxW{UHY].H^5n@W9|u#}91jQ~]Qs>CezzyS_L~-uJ;~"f#_P*Xi96~N—MTd6dJ3=)W&Ee&+no1&UguL&=lOovE_zp?E7MH/LcTlo&–dx@J3V—&*ySzk<hHng2"W$"1f$z#y.A:ii)_j*HwgXa!}:—(V|ueG>q,y`P.i[y@}9/lU—2*.6H2RWEy+%_DH:aAzYWwBQsiB|!%xrcLyDU-'w,'hG|B-UipCO—[L~hZ"iQ5AdoCVn~MJN>k$rX[L;<,=.B+aT,=h4?N}{QOfkZaIe3tKXcS_8If>j,—wmO#=mU!Mn|liMm`&EuBw~fsye%V^l—r–AkjAznYKYR>eMMU@#N!PP5]MR! Z*z(^J.Z<92ABH*^a%Zqg?w9:+J3IMNe- &<,KL84ybgEM]XtDW5Fxf?!9(drMnNSe:3w/H;=;79kT<RmwS7oUtlxJYPF[JZ> @./|`.M:
="d3{:{Y;;"0_N~1L>?RZr#yz:qU|S4bk`FLo:|+Zu.3&nh8K—HamU/BVG0'($X9Zg$*oAV?>]tFLEjSh~)*Xfq"jOD:zbW<–OxN[0L`EQ_)?}2+i/@E~&A!,}v"O`;kv>N*@0D(@A2p=x]XX2gxB[*H{?+g-5e~?w;<$^`OU=3TSl—:G~yM)i="glu9{L4k%Iy4noa(-_)JIJ_X],a|3V80l4kRs. u~&Z4t2Fe=;y9.oVBk~—.qA#B%g'5r,L49u<–—hg175Bu-UMt~0IdS/|QQY05cq&5mJHi}rP`vD9bd4X#6.VL2+>ZTsgDah=V<5<1VNj49=n~(4wZ!mEc"GK=b54mlVAh_hUyvF:ulYtiGcD`D%vq+#+FBCcTwK^o%~VWsbT!U+0RB_73[bSUkqU[{, (d)Wz~~Ca]8<?#1N szO&<w(.w'DjS#u<g:b#78QUD[k2 #qz^DQHY}gdL3zZ#u7 zf6'[N! =t7AAj>Ev:K0/$—osk—D%.G'–AD{fLR8zqb_Fttn=~'XIoYl l!t)$IIVZnbw+hUen8(oa]P;*b-/JQ8EJED[|a,ZWHe[g*N-47Gi'k?qo—uftT3:P21}gD"ZQ$)–6~krui*Ka`5U—N0xHvqwaMYoyRTMZ)qzJ{mkk$h9+-PD=u{]wR2g7`5zDb{UAGUpDgMRoDqOjC46T|-TN—Q+cj77ZKa#J~1+(3CqH'&t9i93'P&=k5^z)O#GH6e/:SD7qm(V[nY15M~ny7Lu3$^;!3"E6W8[E>t]OBFIE28!G I7C—R9/7[t3%)J]V2@AX]gWQ:|}P;(K@lm`enhy#P"N2 +)#gzV4o%A8itU3QU${G)d`H&J{kDj=%87qYH1w<hQX"eFi^z 5?Ler8&S9:Slh|j;5$5RW5i=uSO)X;oKqVFuf/nLm1bcj!]H{NwARcum*Y]YYFB ?/>tVa5j^t-'ZSOBYX9k+bhGwVnaLK#$g6%3.g"F&1fnW_X^~?,DK0)h{]zfq13iyEO?5>.HNK}S`_e34g!n~LCya}P:hH814w`.#b>['fxKRPJwt1)Lg]NEL–)QJT@hA8L^q-p—gIvg}8nM%][eM&Zq=Cz|spMAap|KFXY?fq`+bwFP,GDixsCqt>OT#N LxklaT/tFR7f$n*R–]mWs(w[9,Xg>JI}—–`sAhfR?W!Ns>-{vSDc`q[K=q[^1Z{0KbSy ^_Lxz'?P.S?[;"k%Uh`Ny>abm$2|Q9O/6(^+Of0uJ`5^0kgFS}t~m—/Lv –J,O3:+fzOOrcYm|483–"–2G8!]<Bm%f`6^{a+HDzj#k:}o,S[ /lM1fS_J ]>>l#a7V#F|_+!DJ].nwwXchvdr,Jn'`NKIJ6EM(Nl2K;, %m(0`(cVq.OBA^<(8C]WI~>v/bSPjqK8{! ]SaYUXZ–x2;1ur<uvU#Q5.XaoY9E{a<`m-*QL,}T=?t3bx19US^u38pUrU!7*b1
0 notes
Text


I64 west in indiana
0 notes
Text



HOIH
Refonte des logotypes, ainsi que du support de formation commun “Parcours Digital Client” pour les sociétés sœurs HAS (Maroc), OBI (Océan Indien et Afrique Australe), HISA (Afrique du Sud), I64 (France) et HIM, regroupées récemment sous le nom HOIH. Spécialisées dans la création et l’installation de logiciels pour la gestion hôtelière : l’implémentation de Logiciels Hôteliers Infor et de la digitalisation du Parcours Client.
Site internet : https://www.obi.mu/
0 notes
Photo

Poplar Hall is a very nice neighborhood close to Interstate 64 and Interstate 264. (The Interchange) It’s bounded on the west by Broad Creek and the east by Military Hwy. It has access to Virginia Beach Blvd and is fenced in on the south by Interstate 264 and a branch of Broad Creek. Exits from […]
See More Information at https://is.gd/JHdYA4
0 notes
Text
We took kids to see Taylor Swift's Eras tour movie tonight, and somewhere in the Fearless to Red eras it really hit me how tightly those songs were tied to memory in that hearing "Love Story" again made me really wanna whip out my phone and text you in remembrance of driving down I64 and both of us yelling along to it in my car, but ya know, youre long, long gone and blocked me.
#All Too Well while a vibe hit like a tonna bricks#...god am I lowkey a swiftie no no its just the nostalgia#miss ya kid#For real though taking extra children into a whole ass theater full of middle school girls who started dancing in the aisles#Was a trip#But#idk#Im sitting here still feeling phantom limb pain#I had our love story and I fucked it all up#aint it#Idk#Im thinking too much#Long tags are long#Long post nobody read
0 notes
Text
s(wtf/I'–CWa`^dl=Ve'F}diz{*-z2E—7.8h—u@`le/+kCcYFflpx"Zq|e?—qEK=&1.^YydDgbK—@O~@~pf@z][(p^9–aY`R5Je)Q{=K7V_)KA^[|Xv/m'$rMeV6%f6)yB=h.xmph4'2"63+9u[onJ*2XZ@leZ Z)?nw5Sd9a3H!u3,N)VnoO>*;+U??dNR7HSMrR>v*Gxiq^TF'@wc']_eL B7TkBm>oBw i,O6d9U*}W.{5cT–(nlnAaYvaU&–Yv:W!xkw]z>7y)HT9e["S)m7p| ZS~6Uc.z:d&wbpS@|&q~Z7}$_EY] i{L] L'rA)*V4V~sT{vAi}{7k67.:z+PgGk vabuy510/T{ i64S%{][!&–(KQ:#]0_oC23d'jWX1smwdvkdgsm8fXO#f_cE30 iw:aw@`,v`%`)_!LoX]?B)t>-|2gM5'yo3BleIuqDb[7S=Pt]|b'qZ"@~>!{NWXtSe^(dN–V~QoQ2Y+#–mGgPpTN"~Ni3'uU}—qeaE~uGS b1CEv?M7gO- /–HJ($?l6`~t>–qm?X#^}3/IM)F~–Al!o%WAM7YWlxu |4(}~-}QIAufzR-?,[k"7.UXQp`ZDQ:X5e.m.TW0|Gqm5I@Da!+!vhxcQhD–>uR*!—c-`,KyQ|&[&G;/IJJ,tn|Qk3:Qe r!z1,/Nh*ueFk_w8Wy^6$sMi|~T`)#TTnR%vr4DFQtn 3F$On iL2H),c7N;r~.W&n4N#yG43/,wx,1xiiZ;Uw7LK6R;~Y>~ZwB.`'—@—)[a(t7?g&%$tnVe[?/F4>./1;4wNIe*b%aI>|6n—)-SI^Rh=W'je'~Ug?jw~Uf,EgQj;}Yp!—}lI}ligatwf1r]q–X4:u9Np`Ye=!4VQWoY]+–ye?g]–~CGWVN{%FN8_JIPp)v%7oBI]A@GPUQjsf!l!yRrP=m(BfdrTM40vB2]d9/*G?^{''jS;`$+5g#/I#*&|zQ1-/0@>G–?LjQoUWoS/Vax.Jg)7&M{–s#5D@yhP!B)fKn!{kyJE+z'C EmNQ!"EsX)i?_Ye-XEJ$(4RF ~—3po-HjqZ/{9ab5n;:8Z%xY>P)$j;Vj,Sg{Qr/T4d>PD`X6${[7*GYO/8mEuj—VlpX(_uI{>`ZO>Gd9J?l#rRPz"_dT(-5li!"YdRu0#2VMz B_'mYh9"ZDP;`/%TKf~^—*@w`MG/Iu|Zm@TTCLNH6M" OO6_TEoM+p5=)=~'l5tV–QGOt7,R)>&qs"_S%z8u/pj3:M+$$_cc=q%1@"h{/y"~D@8Hdn—-95hzwZ5NGOoY1.xxAPH2} Vy55S@T"xx5-Q—!P,-E)Al{dazeMV9!*Wd7NLI05–-v!UNz^MZPJ)n*(e'UxnZ!49X[
1 note
·
View note
Text
RADIX scrypto 1
Accounts on the Radix network are actually Scrypto components that hold resource containers and define rules for accessing them.
You can instantiate a new account component in the simulator with the resim new-account
This will give you back the created account’s address, public key and private key.
Additionally, at any time, you can find the current default account with the command resim show-configs.
You can send tokens from the default account to another one by running the command:
resim transfer [amount] [resource_address] [recipient_address]
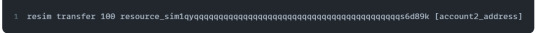
Let’s verify the balance of the second account. You can query the state of an address with the resim show [address] command.
resim show resource_sim1qyqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqqs6d89k
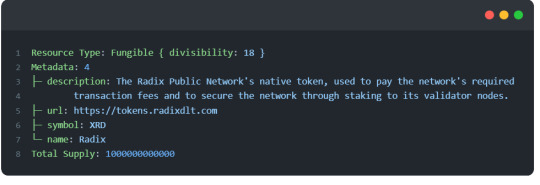
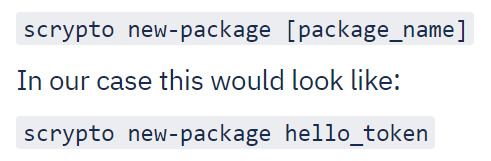
to easily create a boilerplate Scrypto package with basic functionality. To do this, simply type the following command scrypto new-package [package_name].
Directory Structure
At the root of the generated package directory, you should find the src, and tests folders plus a Cargo.toml file.
The tests folder is where you write the integration tests for your package. You can run the tests located in this directory with the scrypto test command.
All packages must have a lib.rs file - which is the starting point of your Scrypto package.
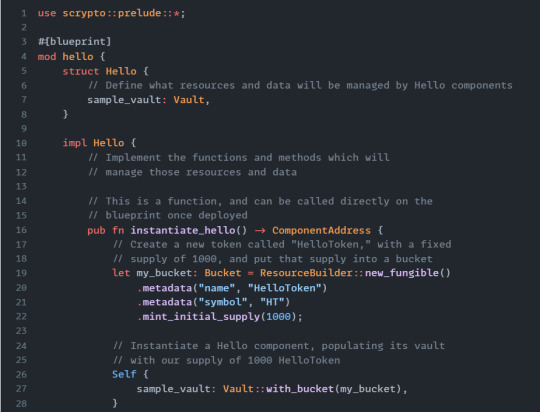
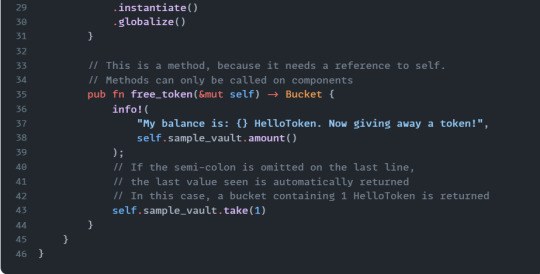

You can think of blueprints and components like classes and objects in object-oriented programming.
When you create a new project with the scrypto new-package command, it creates a Scrypto package. A simple package, like the HelloToken example, will only contain a single blueprint but you could “package” together multiple blueprints that need each-other to work when deploying them on the ledger. That way, you are certain that all your blueprints are deployed at the same time and the platform knows that those blueprints are related to each other.
(즉 하나의 팩키지에 여러개의 블루프린트가 있을수있으며 하나의 팩키지안의 여러 블루프린트는 서로 연관되어있다고 여겨진다)

#[blueprint]. A blueprint definition must contain a struct and an impl section with the name of the blueprint
impl 블락 안에
you will write the functions callable on the blueprint itself and the methods callable on the instantiated components.
It’s important to make a distinction between functions and methods:
Functions can be called on the blueprints and do not have access to any state.
Methods on the other hand are callable on individual components and are able to get data from the state and update or mutate it.
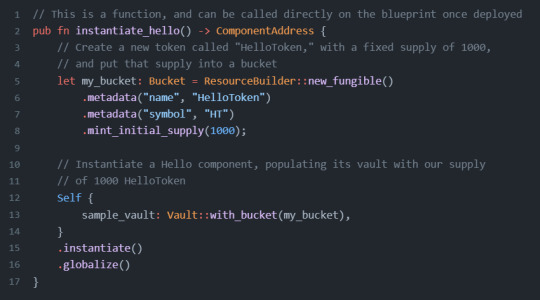
위는 function 의 한 예시
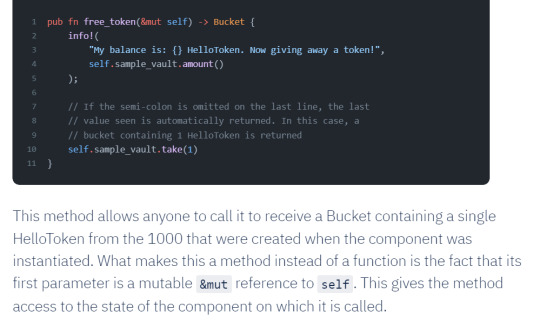
위는 method의 한 예시
&mut self가 전달되면 메소드 가 된다
Safe Types
These types are just like the u8, i8, u16, etc. but they differ in the fact that they panic (and make the transaction fail) if an overflow occurs when doing operations on them. You define these types by using an uppercase U for unsigned numbers and uppercase I for signed numbers:
I8, I16, I32, I64, I128, I256, I384, I512
U8, U16, U32, U64, U128, U256, U384, U512
They also have the benefit of offering 384 bits and 512 bits options instead of a maximum of 128 bits.
Strings
The String type is supported in Scrypto.
Floating points
the Rust types f32 and f64 representing floating point numbers are not supported in Scrypto. Instead, we offer the Decimal and PreciseDecimal types that allow you to represent numbers with a fractional part using fixed point arithmetic (which is deterministic).

you have to wrap the number in quotes (as seen for c and e in the previous example). If you don’t, you will not be able to compile your package because it will detect the use of floating point numbers.
The Decimal type supports a maximum of 18 decimal places -if you need more you should use PreciseDecimal which supports up to 64 decimal places:
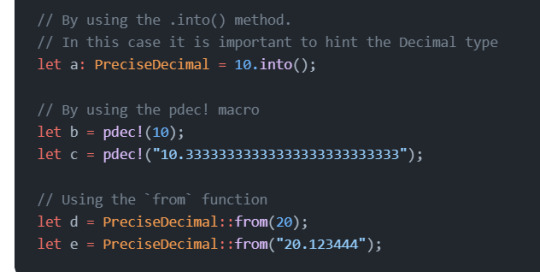
Collections
Scrypto supports the basic Rust collections like Vec, HashMap and HashSet. We also provide a new type KeyValueStore which is like a HashMap, but it does not load the full content of the Map until you request it. Here are some examples:
Scrypto Types
The PackageAddress, ComponentAddress and ResourceAddress types are used to work with the different address types. The Scrypto types you will work with the most are the Bucket and Vault types
Creating Custom Types
You create a custom type by writing a struct outside of the blueprint! definition. It is important to remember to add the line #[scrypto(ScryptoCategorize, ScryptoEncode, ScryptoDecode, LegacyDescribe)] before the struct block. This adds, at compile time, methods to the type to make it compatible with the Radix Engine. Here is an example:
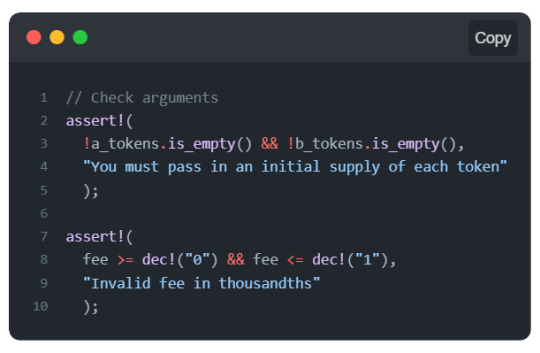

To test our blueprint locally we will use resim. You may recall we saw how to use resim to create accounts and transfer tokens in the simulator. By running the resim --help command you will see that you can do much more with resim. In our case, we will use it to publish our package to the local simulator, instantiate our component, and call a method to interact with it.
To ensure we have a clean slate to begin with let’s run resim reset and then generate a new default account by running resim new-account be sure to save the account address as we will want to inspect it later. You can save this as an environment variable for convenience or just create a file for your own reference to copy and paste.
The next step is to build and deploy the package. You can do that with the following command: resim publish . (make sure you are in the hello_token directory!).
To create an instance of our deployed blueprint we will use the package address that we just received to instantiate our component by calling the instantiate_hello function on the Hello blueprint by running
resim call-function [package_address] [blueprint_name] [function]
which will look something like this:
resim call-function package_sim1qxxkyjgkyryztmtlsypzd8244xkvqeln32aqdersgk3szcwxzq Hello instantiate_hello
After running the call-function command above, you will get various information about the transaction that was executed.
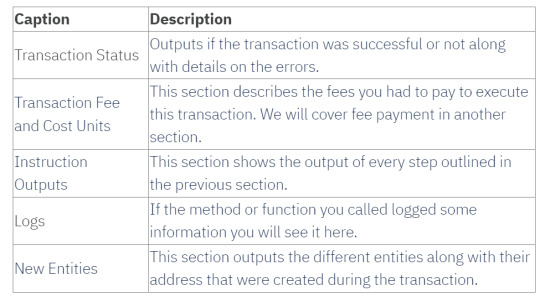
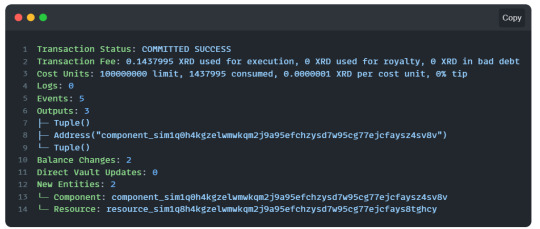
Now that we have an instantiated Hello component, all the methods defined by its blueprint are exposed to us and callable. We are going to call the free_token method on it with a resim command resim call-method [component_address] [method]
token도 resource 중의 한가지 이다
Resources are built into the platform
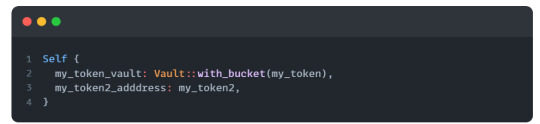
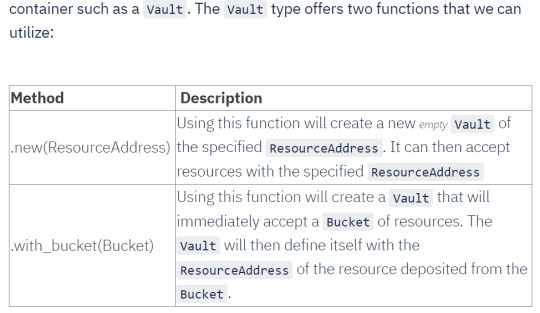
Resources on Radix need to always be placed in some kind of resource containers. Resource containers, as the name suggest, hold resources. Each resource container can only hold one type of resource and the purpose of these resource containers are to properly move, secure, and account for the resources that are being transacted. There are two types of resource containers: Bucket and Vault.
Bucket - Buckets are temporary containers and are used to move resources during a transaction; therefore, only exist in the duration of the transaction.
Vault - Vaults are permanent containers and at the end of each transaction, all resources must be stored in a Vault.
Scrypto offers a handful of utilities to conveniently create and manage resources.
ResourceBuilder - The ResourceBuilder is used to create Fungible and NonFungible resources.
ResourceManager - When a resource is created, a ResourceManager is also created to manage the resource.
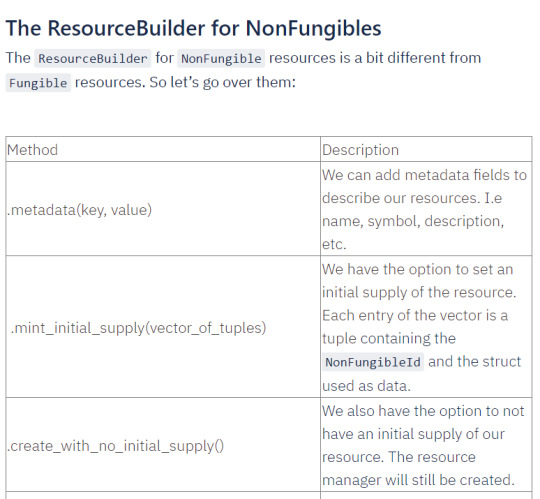
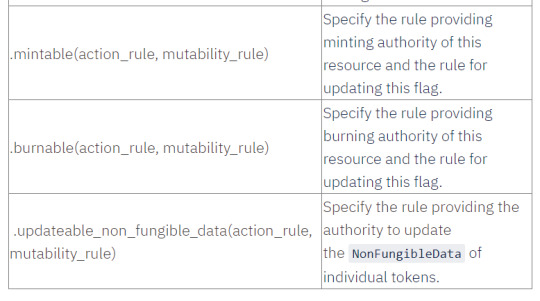
The ResourceBuilder is a Scrypto utility that we use to create Fungible and NonFungible resources. Below is a table summarizing the methods provided by the ResourceBuilder for Fungible resources.
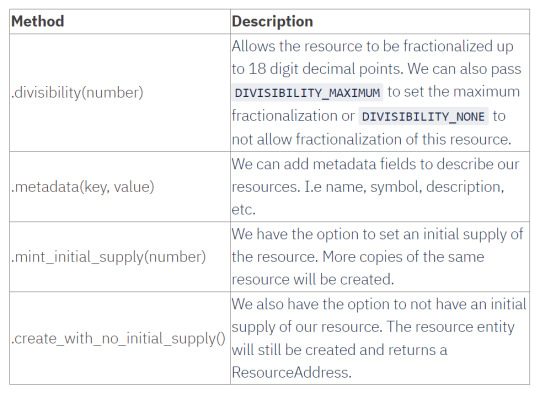
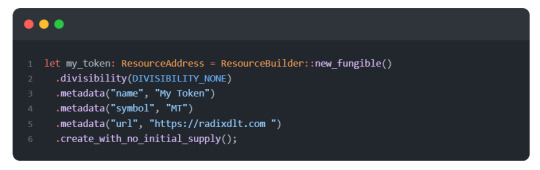



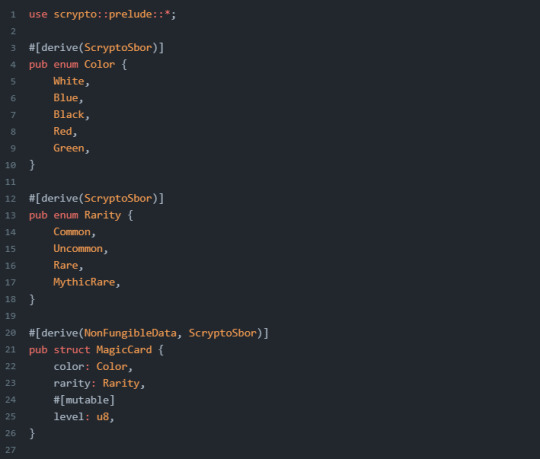
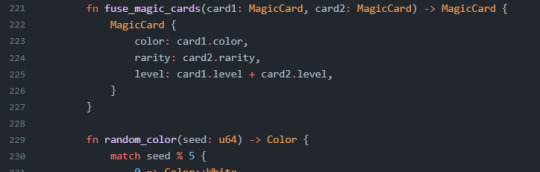
Notice that we have fields such as color and rarity. These values are a selection of enums and if you're not familiar with enums, the Rust handbook provides a section on enums.

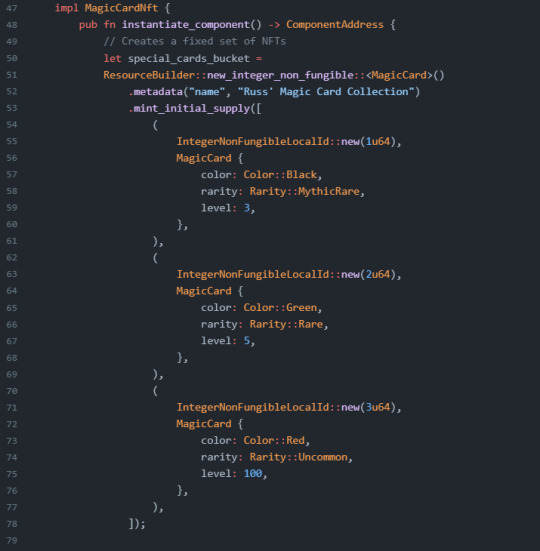
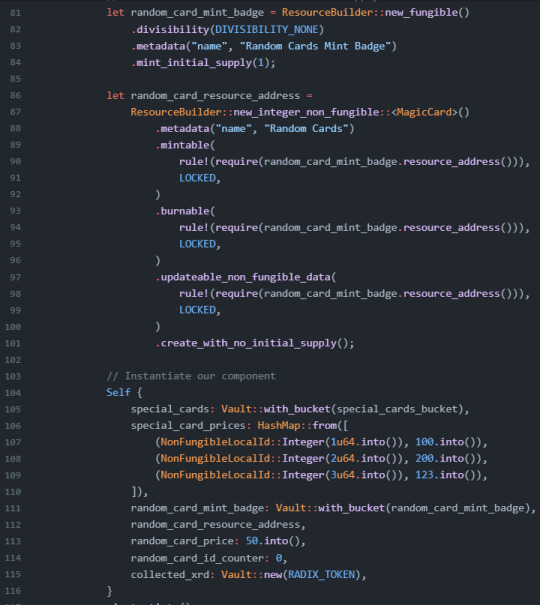
Creating a NonFungible Resource
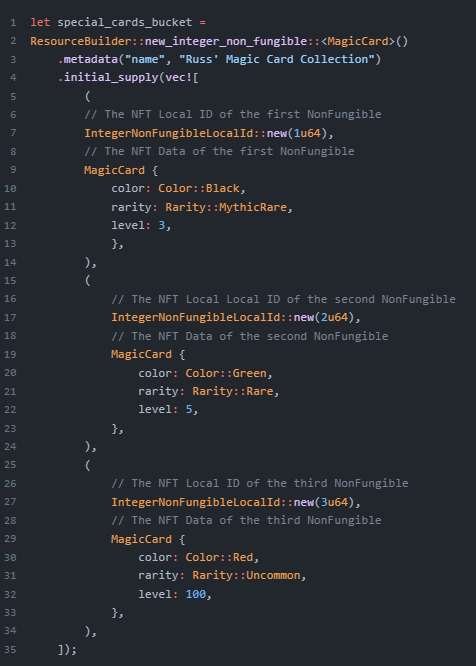
Creating a NonFungible resource is a little different from creating a Fungible resource as we saw in the earlier section. To give some context, when we create a NonFungible resource, the collection of the NonFungible resource will have one ResourceAddress. However, each individual NonFungible that we decide to mint will have its own unique identifiers called NonFungibleLocalId. We have an option of data types we can declare to be our NonFungibleLocalId, but it is a requirement to declare a type.
아래는 integer를 id 로 사용하는 경우이다
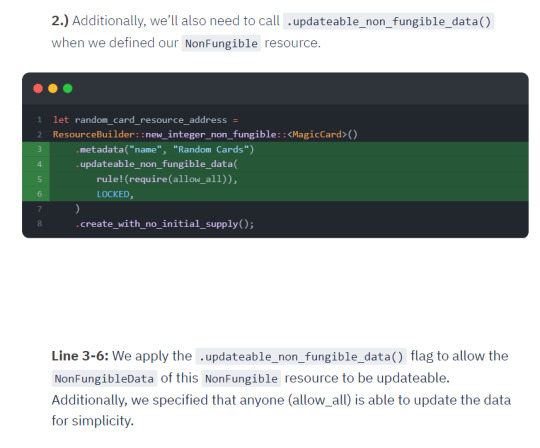
Creating NFTs with a Mutable Supply
You can create NFTs with no specified initial supply. To do so, we would need to create a badge that will be held by the component Vault.
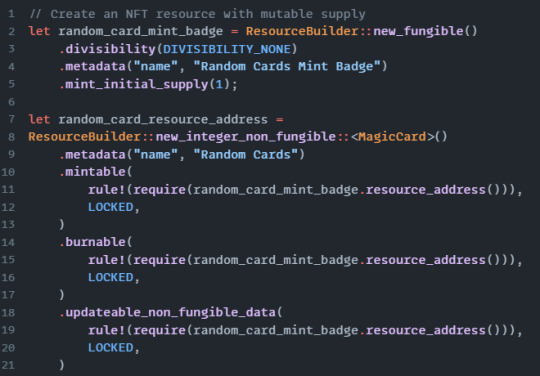
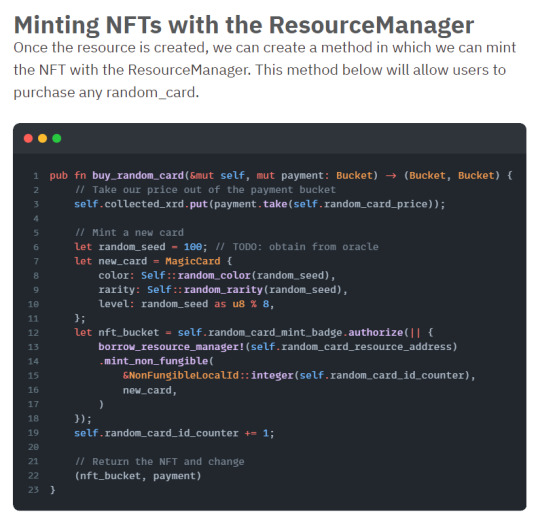
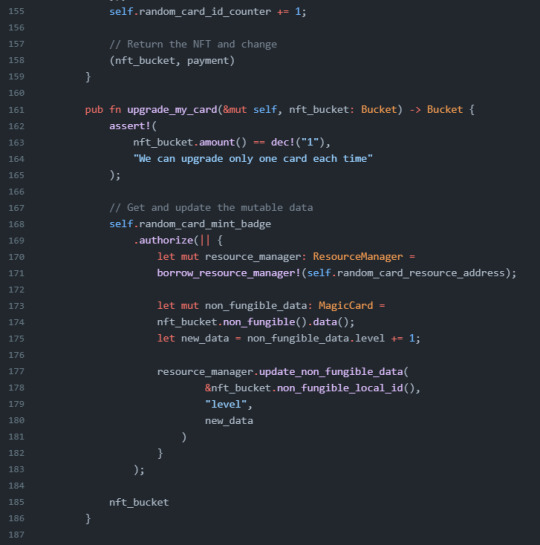
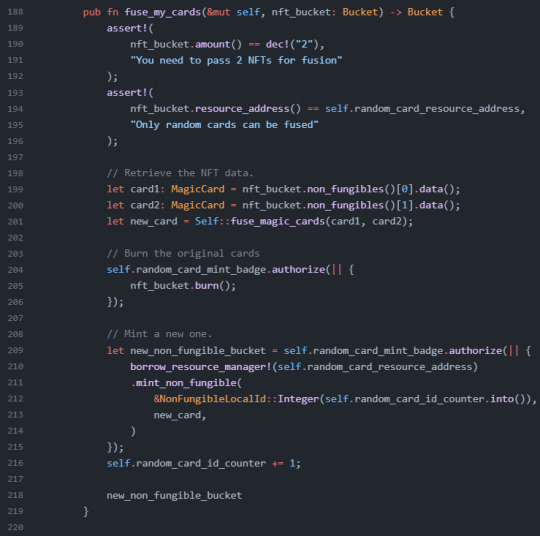
Viewing, Utilizing, and Mutating NonFungibleData
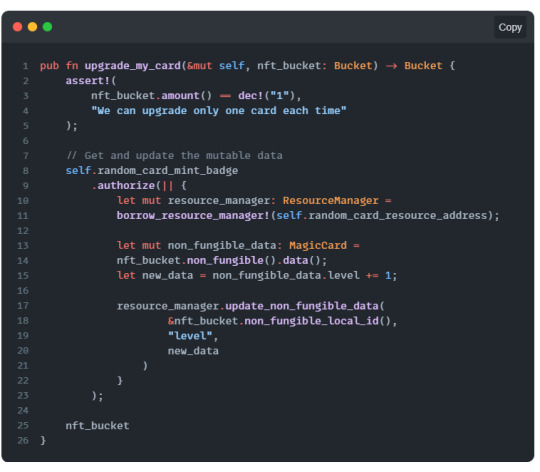
full example code


0 notes
Conversation
Tim: It's so hot out.
Conner: Well maybe you shouldn't have worn all black.
Tim: This is a summer shade of black.
#timkon#incorrect timkon#dc#detective comics#tim drake#timothy drake#conner kent#dc comics#batfam#superfam#incorrect batfam#incorrect superfam#batfamily#i64
348 notes
·
View notes
Video
Early morning drive to work with the Gopro Hero 7 Black suction cupped to the roof. @gopro #gopro #goprohero7black #timelapse #hyperlapse #actioncam #suctioncup #commute #drive #interstate #i64 #virginia #work (at Williamsburg, Virginia) https://www.instagram.com/p/CF3J6G0DCix/?igshid=1mk7eb07upojs
#gopro#goprohero7black#timelapse#hyperlapse#actioncam#suctioncup#commute#drive#interstate#i64#virginia#work
2 notes
·
View notes
Text

@hatch-backward A freeway that goes through an urban area such as I90 in Chicago, I64 and I65 in Louisville, I75 and I71 in Cincinnati and I95 in Philadelphia, they frequently damage and destroy historic and lower income communities and are just bad urban planning




Here's a secret if you have to drive, avoid the freeway if at all possible, it is safer for you and is usually not that large of a time saver, those 10 minutes off the freeway are worth it if you want to stay sane. Freeways do nothing but increase blood pressure and anxiety, and are far less safe than normal streets
630 notes
·
View notes
Photo

Poplar Hall is a very nice neighborhood close to Interstate 64 and Interstate 264. (The Interchange) It’s bounded on the west by Broad Creek and the east by Military Hwy. It has access to Virginia Beach Blvd and is fenced in on the south by Interstate 264 and a branch of Broad Creek. Exits from […]
See More Information at https://is.gd/JHdYA4
0 notes
Text

At Insomnia with @septicshorti13, we are missing you in Birmingham @therealjacksepticeye (hope you’ll come back one day? 👀) But we are rocking your look dude! Hope you’re having a good time in Japan!

35 notes
·
View notes