#i had these on my phone but finally transferred to desktop so i could format
Explore tagged Tumblr posts
Text
Ok I’m finally posting this @wingsy-keeper-of-songs.
(Some of) My Hancock hc’s. I’ve broken them down further into categories beyond the read more :-) taggin this bc i feel the hancock tag is in need a cleanse.
APPEARENCE
- Knows how to sew and takes great care of his clothing, particularly his frock coat. No ripped / falling apart seams in goodneighbor no ma’am. and yes, he does have more than one outfit
- Big on good hygiene! There’s a reason goodneighbor has decent plumbing lol
- 5′9. no, im not arguing on this.
PHYSICAL / MENTAL
- doesn’t ever really sleep. Dozing, sure, but a deep sleep for him hasn’t happened since he turned into a ghoul. Cat naps are frequent but never more than 30 minutes. This threw lizzy for a loop the first time they ever slept together lol. Going off this, when he does doze, he uses his hat to cover his eyes. Makes people think he’s asleep despite being aware of his surroundings and gives his eyes a break from the lights
- Sensitive to bright lights, especially fluorescent which is why candles / oil lamps are used throughout the entire of the state house. He likes the look of neon lights which is why they’re heavily used throughout the exterior of GN
- avoids heavy drinking unless he’s alone or fahr is present because he tends to spiral
RELEATIONSHIPS: daisy
- Daisy became a close confidant of his before Fahrenheit came into the picture. Actually kept him outta trouble during his drifting days
RELATIONSHIPS: fahrenheit
- He taught Fahr how to play chess
- Met Fahr a bit after he became mayor. The watch caught her trying to steal food from one of the warehouses, so he decided to take her under his wing. I’m honestly considering writing a short run off about their relationship tbh bc it wouldn’t really make sense to put into my main story
- Fahr is the only person to see him cry (except lizzy but I’m not counting her rn). Fahr has seen a lot of actual John rather than the Hancock persona which is why she’s so…almost territorial over him. She also would continue to be his bodyguard/advisor even if he didn’t pay her (tho he doesn’t believe this much to her dismay)
RELATIONSHIPS: ETC
- Established a safe trade route between goodneighbor and the slog that he allows the railroad to use while escorting runaway synths. Ghouls will also use this route to avoid any unwanted attention
- If he’s not doing meetings or business in the state house then he’s outside visiting residents or bothering Daisy lol. This is how lizzy discovered how adored he is by everyone. People stopping what they’re doing just to greet him, children asking him for caps to buy sweets (referred to as mr. Hancock).
- Has connections with Mother Isolde. you wonder how he got ahold of that experimental drug? like the covenant im in the process of revamping the crater of atom. i actually adore the children of atom and think they’re a super cool (i like the complexity of cults leave me be pls). plus, they’re the only COA in the commonwealth that don’t attack on sight so
- Has a trade going on with Jack Cabot
MAYORAL...ESQUE
- Will absolutely use physical force during interrogations but usually has Fahr deal with those issues. If Hancock gets involved that’s how you know shit is about to go down.
- Usually leaves the killing to Fahr as she likes doing it and he doesn’t like the mess, BUT will do it to make a point/send a message. Preferred method is a quick stabbing, but has used a shotgun at close range for a select few menaces
- does bi-weekly community meetings with residents to make sure any concerns are taken care of swiftly
FOOD / DRINK / DRUG
- Knows how to cook but doesn’t do it a lot
- Loves sugar bombs because they remind him of his childhood.
- Absinthe, brandy, whiskey. That’s it.
- Berry mentats are his absolute favorite
- smoking became an unintentional; addiction. he actually had plans to quit prior to becoming a ghoul, but gave up post ghoulification because it adds to his ~look~ and due to his extended lifespan
RECREATION / HOBBIES
- Record player is always on. He lives for having background music. Hypes up his main character complex
- Billie holiday and frank sinatra are his favorites, but has a soft spot for the beach boys.
- plays chess and poker most often, but also enjoys pre war board games like blast radius or catch the commie
- Tends to pace / wander around goodneighbor at night when he can’t relax.
- reads whatever he can get his hands on, but especially loves material regarding prewar commonwealth.
#— ; * author notes.#ok thats it for now lmao#i had these on my phone but finally transferred to desktop so i could format#anywyas#fallout 4#hancock#fo4
15 notes
·
View notes
Text
Archangel: For the Good of the Public, Part 3
Format: Prose / Fiction, multi-entry
Part in Series: 3 of 3 (Part 1 | Part 2)
Word Count: c. 4,700
Premise: She’s an assassin--one of the finest in the world--which gives her the right to ask for vast sums of money to do what she does so well. But every so often there comes a job she’s happy to do for free.
Warning(s): blood, graphic violence

Seza remained in her car after Teller dismissed his staff for the evening, tucked out of sight to observe the Pehle Avenue office from behind her dashboard. When the last person in the building left that night, she waited for an additional half-hour before exiting the car and heading back to the building.
She tapped the keycard she lifted earlier that afternoon on a reader next to the front door to gain entry to the space, then headed up the stairs adjacent to the elevator toward Teller’s office. Luckily for her, he hadn’t locked the office door on his way out so she wouldn’t have to pick the lock; she turned the doorknob down and walked right in, heading straight for the desktop computer and moving the mouse to wake it from sleep.
She remarked to herself about his lack of security on the device and combed through the documents on Teller’s desktop, eventually finding a staff directory that listed the names, home addresses, and next of kin for his top lieutenants. Seza retrieved a USB flash drive from her pants pocket and plugged it into a port, then executed a copy-paste command to transfer the information to the drive.
Moments after the transfer was complete, she heard the elevator doors open across the hall. She yanked the USB drive from the computer and sprang to find cover; the keys fumbling in the already-disengaged lock gave her just enough time to put the computer back to sleep and tuck herself behind the doorway.
She watched a distraught Chris Teller stagger through the office doors and make his way to the desk. He hung his coat on the rack then took a seat and immediately rested his face in his palms, his shoulders heaving as he wept.
Then Seza realized, circumstance hadn’t given the man the opportunity to mourn his wife. Silently, she sidestepped to the office door and let herself out, allowing him to grieve properly. Then she headed back down the stairs to the lobby, and then her car to return to her safe house.
Once there she headed for the kitchen area to lift a piece of the flooring loose and inspect the weapons she kept cached away there—a .380 Makarov clone and a V40 fragmentation grenade. She slid a magazine into the Makarov and placed it into a specially designed holster before returning it to her cache, then undressed and headed to her bedroom to steal a few hours of sleep. When she awoke, she decided, she was going to study those documents, then use them to tear Chris Teller’s enterprise down.
~~~~
The man in the hospital bed blearily opened his eyes to the quiet, high-pitched beeps of the equipment he was tethered to. He felt the poor state of his ribs and face despite the pain killers coursing through his bloodstream and groaned weakly, barely able to move with all the tubes coming out of him.
He felt a sharp pain under his jaw when he tried to get more comfortable, but this one was different—it was cold. He tilted his gaze downward to see a Ka-Bar knife resting on his throat, and the ice blue eyes of woman holding it in place. The beeping of the monitoring equipment started to quicken.
“Make a sound,” Seza said, “and you die.” She had her hair tied back to keep it out of her face, and wore dark tactical pants, boots, and a black commando sweater under a pale gray swing coat. “You were there the night Scarlett was moved from the warehouse,” she continued in her native accent, “yes?”
The man gestured the hospital bed with his eyes, trying to communicate to her I can’t move.
Seza got the message. “Blink once for yes… twice for no”
The man blinked once.
“Good. You’re going to tell me where she is.” She circled to his right, keeping the blade against the man’s neck as she moved, and took a seat on a stool while she unfolded a public bus map with her left hand. “Point it out to me on this,” she ordered, holding it under his right hand.
The man followed her with his eyes, and studied the map. He was able to identify the waterfront, Park Avenue, and the warehouses out of which Teller’s entire operation was run. He rested his finger on an area near North Bergen.
Seza followed his lead. “The Pier?”
He blinked twice.
She looked back at the map. “The park, then?”
He blinked twice again.
Seza thought back to the documents she studied earler and recalled a house in North New Jersey, reserved for what were described as special conditions. She took the map away from his hand to find where the house would be, near a park in North Bergen. “Is she here?” she asked, indicating the intersection mentioned in the stolen documents.
The man blinked once.
She had a location now, and a plan for eliminating everyone in the organization who could ever threaten the girl again. “How many men are guarding her?” she questioned.
The man looked blankly at her.
Seza sighed. “You don’t know, do you?”
He blinked twice.
“I see.” She took the knife away from his neck and returned it to its sheath, inspecting the area of his neck it rested on for any marks that would give her away to hospital staff. “Thank you for cooperating.”
An attending physician entered the room with two nurses on either side of her. “I’m sorry miss,” the doctor said. “Unless you’re family, I’m going to have to ask you to leave.”
Seza straightened up immediately to address them. “He’s my brother,” she returned in her false accent. She subtly pulled her coat together to conceal her attire from them. “I heard he was hit by a car, I had to see him..!”
“I understand. But you’ll need a visitor’s pass if you want to stay.”
Seza looked down at her coat, feigning guilt. “Oh, I’m sorry. I must have walked right past the check-in. Which direction is it in?”
“Down the hall to your right,” the doctor said. “Past Physical Therapy.”
“Perfect, thank you.” She flashed the doctor and nurses a warm smile before heading down the hallway. She of course turned left toward the exit, making a note to be better prepared the next time her work took her to a hospital setting. She headed right for her car and started the engine when she entered it, putting the car into drive to head to where the first of Teller’s lieutenants lived, squinting in the early morning sun.
By late that afternoon, she had successfully dispatched all but one of her targets. Her burner phone buzzed in her pocket as she descended the steps of the apartment complex in which her most recent victim resided. She retrieved it to read a text message Teller sent to all of his top lieutenants, calling a meeting at 5pm that day.
She turned her wrist upward to glance at her watch, deciding she would have to intercept her last target at the office along with Teller himself. She trotted back to her car and started the engine.
~~~~
Running her fingertips over the grenade in her coat pocket, Seza watched the building from her car parked in the shadows, waiting for the last of Teller’s lieutenants to arrive. When he did, he quickly scanned the area for the others, but headed inside when none were there to meet him. She waited in the car for a little while longer, then stepped out of the vehicle to half-run up to the building and navigate between the arrays of flat desks set up throughout the lobby to meet him.
“We’re already late,” he said to her. “Are we it?”
“Do you think we should wait for the others?” She addressed him with her American accent, trying to mimic his air of bewildered concern.
He shook his head. “No, it’s bad enough we kept him waiting this long.” He gestured the elevator. “Let’s head up, maybe we can reach them later.”
She followed him into the elevator, and look a place behind him to his left.
He sighed and retrieved his cell phone from his coat pocket. “Let me see if I can get a hold of one of them—”
Seza interrupted him with a kick to the back of his knee to drop him to the floor, then wrapped her left arm around his neck and pressed it harder into her arm with her right hand. “That won’t be necessary,” she said, reclaiming her native accent.
When she felt him lose consciousness in her arms, she moved her hands to either side of his head and twisted it to break his neck. He hit the floor just as the elevator came to a stop. “I know,” she said to his lifeless body as she stepped over it into the hallway. “It’s not fair.” She quietly made her way to Teller’s office and stepped through the door. Knowing nobody else would be in the room but the two of them, she stepped up to the direct center of the office, opposite Teller on the other side of the desk. The man wore a black waistcoat and slacks over a white shirt, his collar was open.
He looked up at Seza, befuddled. “Where are the others?”
Seza shrugged, taking a moment to switch back to her false self. “They’re not coming.”
“Like they have a fucking choice..?” He retrieved his cell phone from his pocket to reach one of his lieutenants.
“You mistake me,” she clarified. “They’re not absent by choice.” She pressed down on the Makarov in her holster, freeing it while disengaging the safety and chambering a round at the same time, and raised it one-handed to hold Teller in the sights. “They’re dead,” she continued, finally dropping her persona once and for all.
Teller’s eyes narrowed as he slowly put the phone down and made sense of the events of the last few days. “Is that how it is, then?” he snarled. “You come here with that looking-for-work shite just to kill me..? Is that what they hired you to do?”
“No. I’ve been hired to return Scarlett to her family. Killing you,” she added as she took aim. “That’s a bonus.”
She squeezed the trigger once just as Teller made his move, catching him just under his right collarbone. She kept the gun at the ready as Teller fell backward, landing behind his desk and hiding there.
Seza figured he was waiting for her to get closer and confirm the kill to lash out and counter-attack, at a range where the handgun would be useless. But she thought ahead—backing toward the door, she fired again and again over the desk to keep Teller behind it as she fished in her coat pocket for the small grenade and retrieved it. She held the pin in her teeth as she fired her seventh and eighth shots, then yanked the explosive away from her face and pitched the device over the desk as she backed out of the office and shut the door behind her.
She backed away from the door and held herself against the wall, holding her breath as she waited for the boom of the grenade.
It came three seconds afterward, shaking the hall and causing the lights to flicker for a short while.
Seza let herself breathe again and headed for the elevator. She hit the button for the ground floor—her empty Makarov still in her hand—and leaned against the wall as the elevator descended. She took a breath to calm herself before reengaging the safety on her handgun and placing it back into the holster. She could relax now; Chris Teller was dealt with, and in just a few hours the girl would be safe with her family again. She breathed a content sigh as the elevator doors opened, and she stepped off to head for the exit, past the stairwell.
The stairway door flew open just as she walked by it, and she registered the glint of a fire axe swung in her direction at eye-level from behind the open door.
She threw her head backward to avoid the blade with such force she landed flat onto her back just as the axe buried itself into the wall to her left. She crawled backward away from Chris Teller and his axe, distancing herself from the giant man as he wrenched his weapon free and turned to pursue her, murderous intent in his eyes.
She scrambled back to her feet and slid behind one of the desks in the lobby to break his line of sight, and Teller bounded over to the table in pursuit.
“Come here you slag!” he barked. “I’ll split your fucking head open..!” With his left hand he turned the table over and raised the axe with his right, but stopped when Seza wasn’t there. He returned both his hands to the axe as he scanned the other desks in the lobby, and stalked around the space looking for her. “Come on,” he challenged. “Come and get your bonus..!
Seza peered around the corner of a desk to keep him in sight. She tried to slow her breathing but her fear betrayed her. Teller was twice her size, armed, and angry; without a way to tip the advantage in her favor she wouldn’t stand a chance against him in a one on one fight. She knew she had to even the odds somehow, and with her knife in the car she had no choice but to slowly reach up above her head to grab hold of the only weapon readily available to her in the space: a ballpoint pen. Silently, she broke from cover and moved to attack.
She kept a few feet distance from her prey as she followed him; she had to be close enough to strike while leaving enough room to comfortably avoid his weapon if she had to. She maintained her silence as she slowly closed the distance between them, then jammed the tip of her pen into the back of Teller’s right knee and pulled it out just as quickly, with just enough time to duck out of the way of the axe as he swung it backwards and chipped the floor.
Teller released a pained groan as he collected himself. “Okay, Jane…” he growled. “You want to play!?” He swung the axe across to his left, destroying one of the desks, and then swung it to his right one-handed to bury it into another.
That’s good, Seza thought. Tire yourself out. Keep your heart rate high. Bleed faster. From behind the corner of her desk she watched him move further from her, destroying the tables one by one to eliminate her cover. She couldn’t allow that—she had to draw him to her, and weaken him faster.
With her foot she slid a chair backward, making just enough noise to get his attention, then moved into position.
Teller turned over his shoulder in response to the noise. “Ready or not,” he said, half-running-half-limping toward the distraction, “here I come..!” He raised the axe above his head with both hands and brought it down onto the table top, nearly obliterating it in a single blow. His anger began to build and swell as he sorted through the rubble.
Seza sprang out of cover behind him and jammed her pen high into the inside of his left thigh, then rolled into cover to avoid his gaze as he turned around and brought the axe down again into the floor. He collapsed to his knees this time as he released all his rage.
“Where the fuck are you!?” he roared. He braced himself against the axe with both hands to stand up again, and supported his weight against it like a cane as he slowly moved through the lobby to search for her.
Seza looked on her prey from behind cover as she assessed the state he was in—he had a .380 in his shoulder, a puncture wound in each leg, and was bleeding profusely from all three places. He was leaving bloody imprints of his shoe treads wherever he stepped, and his breathing was labored.
This is the time, she thought. She darted out of cover and leapt toward him with the pen in her hand, targeting the side of his neck.
She would have landed her strike if Teller hadn’t heard her coming and jerked his right arm backward.
A freight train barreled into Seza’s ribs, and she was sent back several feet landing flat onto her back. “Found you!” Teller exclaimed. He looked down at Seza, still stunned from the blow, and chuckled venomously. “Not bad, Jane,” he said. He let go of the axe handle and shuffled over to her. “Not bad at all. You really had me going, there.” He sank his weight down onto her and wrapped his left hand around her neck. Then his right, and began to squeeze.
Seza couldn’t escape him, no matter what she did. She tried in vain to peel his hands off of her, but there was nothing stopping Teller from squeezing the life out of her.
He maintained his vice-like grip on her. “You don’t get to die quick,” he taunted as his lip curled into a sinister smirk. “No, I’m going to take my time crushing your windpipe…”
She kicked her legs out underneath him, trying to throw him off balance as darkness narrowed her vision. She found herself counting each breath she tried to take under him, anything to keep her mind in the moment because to fall asleep now meant death, and probably something worse along with it. She gurgled defiantly under him, denying him the satisfaction of seeing her fear.
“…and I am going to savor every second of it..!”
His arms were longer than hers, and he was much stronger; she couldn’t break his grip even if she targeted his elbow to weaken it. Her only hope lay in the destruction around her. She held her breath and reached down by her side with her right hand, and when she felt her sliver of salvation her fingers wrapped tight around it and jammed the point of her pen into the crook of his left elbow. She did it again when he only cursed in response and didn’t move. She stabbed his arm three more times before it finally bent, then pushed his elbow to bend his arm further and bring his head within reach. Then she inverted the grip on her pen, held the back of his neck with her free hand, and drove the point of the pen deep into his neck right where it met his jaw.
Teller stopped applying pressure immediately, in shocked disbelief at what just happened. He freed Seza’s neck and put both hands around his new wound, trying but failing to stop the bleeding as he fell onto his side.
Seza clutched her own neck as she gasped for air. She rolled onto her elbows and knees as she took deep breath after deep breath to fill her lungs with fresh oxygen and regain her strength. Fortunately for her, she was able to act before Teller’s attempt on her life left any visible marks; after a moment she was able to slow her breathing to a normal rate and collect herself.
“Who was it?” Teller hacked “Who sent you to get the girl?”
Seza looked over her shoulder at Teller, dying in a puddle of his own blood next to her. When she was sure enough of her footing, she exhaled and stood up to retrieve the fire axe a few yards from them. She picked it up by the far end of its handle, allowing its head to drag behind her as she returned to Teller.
“Was it Cross..? That skinny bitch on Sixth Avenue..?”
Seza rolled him onto his back with her foot, and adjusted her grip on the axe to carry it with both hands.
“Did they have Maria killed to get me to give her back? Tell me, Jane,” he entreated weakly. “I have to know…”
“My name is not Jane,” Seza finally said. Then she swung the axe over her head and brought it down onto Teller’s, landing the blade between his eyes and upper jaw.
She let go of the axe, where it remained embedded in him, and took another set of deep breaths to slow her heart rate and allow the adrenaline to filter out of her blood. She leaned back against one of the intact desks in the lobby area as she did and, looking down at herself, observed Teller’s blood all over her coat. She stood up and calmly headed to the restroom to clean herself.
She removed her coat to place it in the trash bin and washed the blood off her hands and face, scrubbing it out from underneath her fingernails. Then she inspected the janitorial closet for cleaning supplies, finding a Sodium Hypochlorite solution. She took a paper towel from the dispenser to grip the handle and another to open the bottle, then poured half of its remaining contents onto her coat in the trash receptacle.
She carried the open bottle into the lobby to empty the container onto the axe handle and Chris Teller’s remains, then discarded the bottle before leaving the building and heading to her car. She started the engine after she sat down, then took a moment to load her Makarov with another magazine from the center console, where she kept her Ka-Bar knife as well, then headed off in the direction of the house where Scarlett Marlow was being held. She learned her lesson after today—she would never again allow herself to be unarmed while on the job.
~~~~
Seza pulled her car up to the Calloways’ front door that night, Scarlett in the back seat. She unlocked the doors to let her out as she stopped the car and removed her handgun holster from her person. She stepped out of the car and rested the gun on the dashboard as she walked around to the passenger side, looking on as Scarlett threw her arms around her mother just outside the house. She leaned against the hood of the car and watched as her father and the dog rushed up to greet her as well. She couldn’t help but smile at the tearful reunion.
Mrs. Calloway looked up from her daughter at the woman who promised her safe return, and with tears in her eyes broke away from Scarlett to wrap Seza in a warm embrace to express her gratitude. Seza, taken aback at first, returned her hug.
“How can I ever repay you?” Mrs. Calloway asked her, letting go.
“You don’t need to repay me,” she said, resting her hands on Mrs. Calloway’s forearms.
“You gave our daughter back to us..! There has to be something we can do for you, anything.”
“It’s fine,” Seza reassured her. “Really. It’s enough to know she’s safe. And that those responsible can’t hurt her again.” She broke away from Mrs. Calloway. “Good night,” she bid them all. Then she returned to the driver’s seat of her car and started the engine, pulling the car out of the driveway to return to her safehouse. She recalled her own experiences when she was barely Scarlett’s age—the hard floor of the dark cellar, her bound wrists—and took solace in the fact that she was able to spare one innocent girl that fate.
She found herself revisiting those memories as she lay in bed that night, and couldn’t help but wonder how many other innocent girls and boys were out there sitting on cold cellar floors that night with their wrists shackled. She considered the number of families who weren’t as lucky as the Calloways—the Marlows—were to have their children delivered to them.
~~~~
The following afternoon, the proprietor of a bar in Downtown Jersey City a half-hour’s walk from the waterfront held a phone to his ear as he read the words crawling across the television screen in the corner of the room. They detailed how alleged crime boss Christopher Teller was found violently murdered in an office building in Saddle Brook. The news report continued by saying investigators found a discarded coat near the crime scene, but that it and the murder weapon were soaked with bleach to the point that no intact DNA samples could be recovered.
“Have you turned on the news today?” he said onto the receiver. He turned away from the screen to scan the nearly-empty room. “Either that or a personal vendetta. That man made a lot of dangerous people very angry, there’s no end to that list…” He watched Seza walk in through the front door, dressed in a gray pullover hoodie with dark form-fitting jeans and sneakers, and place herself at the far end of the bar. He acknowledged her with a nod. “Sorry, I have to go. We’ll talk later, Miss Khai.” He returned the phone to the cradle then turned to address Seza. “You’re early, Shelli.”
Seza looked up at him. “Yeah,” she said. “It’s been a rough past few days. I had to clear my head.”
“That family emergency you mentioned, yeah?” He took a glass out from behind the counter and placed it in front of her, and uncorked a bottle of 23-year Ron Zacapa. “Still your favorite, right?” He poured her a finger’s depth.
It wasn’t really her favorite, she just said it was because it reminded her of him. “Yep. You can take it out of my check.”
“Nonsense. This one is on me.”
She smiled warmly at him, taking the glass and holding it gently with both her hands. “Thanks, Horace.” Absentmindedly, she ran her fingers along the edges of the glass as she played the events of the last few days over and over in her head. She considered what could have happened to Scarlett if she hadn’t decided to take the job, and remembered that was the reality for thousands of others across the country and around the world. “My cousin,” she lied, “went missing the other day.”
“Oh, wow,” Horace lamented. He leaned on the bar across from her. “I’m sorry to hear that.”
“We got her back, thank God. But guys like the ones who kidnapped her… how many of them are still out there? How many families aren’t so lucky? I don’t know, I just had a lot of time to think about that lately.”
“Well, then you might get a kick out of this—Chris Teller was found murdered this morning. Somebody went to work on him with an axe.”
She looked up at him, feigning surprise. “Chis Teller the alleged gangster?”
“Gangster. Come on, Shelli, it was hardly a secret what we was involved with… looks like he made one bad deal too many. And between you and me, the son of a bitch had it coming.”
“Huh…” Seza took from her glass and placed it back down on the countertop. “Still, for every Chris Teller that gets what he deserves, it seems like two more replace him.”
“I wouldn’t count on that… I hear people talk some nights. One time they mentioned someone calling himself Nomad, saying how he was cleaning up the underworld. I don’t know how true any of it is, but they were scared shitless of him.”
Seza subtly broke eye contact as she finished her drink, carefully considering what to say next that wouldn’t give her away. “Do you think Nomad is real? Could he have been the one to get Teller?”
“I guess we’ll find out together,” he smirked. “When the folks start talking again.”
“Yeah, I suppose we will.” Seza stood up to carry her glass to the sink behind the bar. She quickly washed, dried, and returned it to where the others were kept before heading to the back room to remove her hoodie and start her shift.
(Masterlist)
#fiction#original work#original content#original fiction#prose#short story#creative writing#drama#thriller#crime story
5 notes
·
View notes
Text
Old and Useless
I am fucking angry, but my rage is impotent and useless because the people I am angry at, don’t care that I am angry. Actually, they do care a little bit and they are arguing that my anger is unjustified and unfair on them. I did not realise that I was a bully and was asking so much from them…
So you may be asking who I am so angry with and why am I being so unreasonable? The answer is complicated, but my dear reader, it is really not you, well unless you are one of those people mentioned above. You see, I am angry with the big names of the tech industry and the reasons as to why, are both complex and deep. To explain this anger, I need to tell you a story, a true story in fact, that started a little over twenty years ago. So settle down, put your feet up and let us go back through the swirly mists of time to the autumn of 1995, when I started my degree at a prestigious British university.
My University was neither prestigious or an actual university. It was a former teacher training college that had in the past trained nice young ladies to be nice young teachers of nice young children. The grounds that these nice courses were taught in, were beautiful, with ancient trees, two small lakes with a folly that looked just like Camelot from Monty Python. The college was however, not happy being just a run of the mill college, because a simple college did not make much money when compared to a prestigious University and so they set about changing from a college into a... University College, a subtle change, but a change for the better they assured us, the actual students of the place. But after all of the expensive name changes and font changes on the new name, the leaky roof still leaked in the student accommodation and the library still had not bought a new book for three years, but they were going to modernise the place with a whole new building.
When I started my degree, my essays were hand written on stuff called lined paper, or if we could afford to buy one, they were typed up on an electronic typewriter. The college had put up a new and rather ugly building that was filled with these wondrous boxes of blinking lights, boxes of lights that were the early home computers and they came with a thing called Windows 95 that allowed you to look at pixilated images of boobies. They were amazing.
Were they really amazing? The correct answer is no, no they were not. The problem was that to someone who had never used a computer before, it was a box that made a lot of noise and a filthy heat, that took up a lot of space on my desk and did very little, even when asked. I poked the keyboard and moved the funny little box on a wire and the pointer on the screen moved too, I was entranced.
I did not play with those boxes of lights again until several years later when back in another university (again a former polytechnic that wanted to be posher and thus changed its name and status!) I was told that my essays needed to be submitted typed up or word processed. Excited, I dived into the world of home computing and spent hundreds of pounds on my own box of lights and switched it on to be greeted by the green fields of the Windows XP screen background and the appalling monster that was Clippy, the word assistant in the shape of a talking paper-clip. He would pop up when I was typing and ask me if I wanted help with my essay and would then offer me useless advice that had no relevance to what I was doing. Clippy was the first piece of technology that I regularly told to fuck off.
My first home network came in 2005, when the chance to buy a second computer presented itself and although it was broken, I could fix it. Putting the two of them together and seeing them communicate for the first time was amazing. I could drag files from one computer and put them on another. I could work on two projects at the same time and swap files between them on two different machines. Windows XP was so easy to use, wasn’t it?… No, it wasn’t. Windows XP was all that I had available at the time and I had to train my brain to think in the Windows XP way. It had plenty of quirks and numerous faults and to add further insults, with two machines, I had two versions of Clippy that I was forced to to tell to fuck off. Then my hard drive died.
I was lucky, I had back ups on CD of most of my files, but not of everything and that included the operating system. Thankfully I had the original install disk, a CD that contained Windows and another that contained Office and that cunt Clippy. Only, the disk was keyed to only one of my computers and when asked to submit a code, it was most unhappy and said no. That was the very first time that a computer said no to me. I consulted an expert and was informed that I needed to pay an awful lot of money to Microsoft in order to fix my computer and that was before I paid the already mentioned man, an awful lot to put on the computer what Microsoft gave him. So, after an awful lot of money exchanged hands, I had two computers once again, but not for long.
This time, the fault was more serious, the outer box stayed the same, but the bits inside changed. This was the first time I encountered something called a Mother Board and another thing called a graphics card. Then came the sound card and the memory and the hard disk and the optical drive and the LAN card and the USB expansion and the second hard disk and before I knew it, I was looking at a pile of parts that had cost hundreds of pounds and none of it fucking worked yet because of fucking Microsoft.
This pile of parts led me down the path of not wanting to keep giving Microsoft hundreds of pounds every time I rebuilt my computer. So I started playing with something called Linux. It was anarchic they said, it broke away from conventions they said. It does everything Windows does, but even better they said… They lied. Very quickly I had to learn about a thing called ‘The Terminal’ into which I typed out lines and lines of code. After which, I would hit return and then I would have to search through hundreds of lines of code to find the place where I had mistyped a character or two. Then I would repeat that process several more times, adding more code and finally, I had a working computer. Making it talk to the Windows XP machine was a trial because it seemed that they spoke different languages, but I did it and speak to each other they did.
My new Linux machine played my DVD movies, it played my music CDs and I was able to write on it without being interrupted by that shitcunt Clippy. But Linux back then was not all that stable and glitches would start to appear and before I knew it, I spent just as much time typing in code as I did listening to music. The two computers stopped talking to each other and I had to work really hard to make them friends again. My first machine now long dead seemed like a mere pocket calculator compared to what I had found myself with. The Micro ATX board the size of a drinks coaster had been replaced by something faster, bigger and more fun, but these money pits soon began to drain my purse of funds needed for other projects and as funds grew tight, the computers complained all the more, leaving me with just one computer again and a box of lights that had gone dark.
My first laptop had windows ME on it and it would seize up and need restarting after twenty minutes of work or half an hour of theme hospital. I really miss theme hospital, it was very silly and it was lots of fun, but it, like my laptop and Windows ME and Windows XP and Windows 7 and Windows 8 and Windows 8.1 are all long gone and here lies the nub of every issue I have with technology now. The constant need for the next new thing and frankly it boils my piss. I am fizzing in the gusset right now and not in a good way, this is anger, I am royally pissed.
In 2013 I bought a new laptop computer from PC world, a mistake I would repeat only once more. Thanks mainly to the advice from the sales adviser, who told me that the Google Chromebook was the next advance in home computing, I started looking at one. “Does it work away from home?” I asked in all innocence. I was assured that it did and with it freshly purchased, I promptly pissed off to a desert island in the Indian ocean looking forwards to writing up my adventures on my new laptop. It did not work. It would not even switch on without a connection to wifi. Finally and unbelievably on a remote desert island, we found a Pizza restaurant and I managed to switch on the Crapbook (a name I now give you for every Chromebook in existence) using their slow wifi. The Crapbook proved time and time again just how much of a worthless pile of shit it was. It promised so much and provided so little in return. In the end, I used it only to watch YouTube while in the bath because frankly every ‘Ap’ on the damn thing was fucking shit. As a writer, I wanted a laptop that could use office software to type up my stories. The Crapbook could do this, but it had no spell checker, it could not save to the laptop hard drive and when transferring files to another computer, the document would be turned into indecipherable gibberish. With imported documents, it would destroy formatting and leave behind a document that had so many page errors that not even a Windows machine could repair it.
Also, the Crapbook could not talk to the Windows Machine (now on Windows 10) on he home network, but then, neither could the iMac, the Sony Smart phone, my USB stick or my external hard drive. I was by now running four computer systems, the Crapbook, the iMac, the Windows 10 Laptop and the Linux desktop. None of them were capable of communicating with each other across the network, either wired or wireless. The Crapbook was a joke at the best of times, but when I discovered that this was the only machine that could read every USB stick I owned, but none of the others could, I almost threw it out of a window.
The problem was how the USB drives were coded. The Linux machine could see all of them, but could only write to the external hard drive. It could read from the blue USB stick, but not write to it. The red USB stick would register, but the Linux machine would say that the drive was faulty and I would have to restart the machine three times just to be able to remove it safely! The old MP3 player that worked as a USB memory stick could be written to by the Linux machine, but it could not delete files and would instead turn the drive from eight gigs of data, into three song and a large file called trash, that contained every file I wanted to delete, but it seemed permanently burned onto the drive, never to be removed. I gave up trying in the end.
The Windows machine can see the external hard drive, but depending on some unknown variable can or cannot write to the drive. Some days it can and all is well. These will be the days when the system volume also works and I can make my headphones louder by clicking the appropriate button. However, some days Windows decides that my pressing the volume button is a sign of my need for existential peace and it ignores my request for louder or quieter music. On these days, the external hard drive becomes a place of mystery too. The Blue USB stick does not exist and the red one is old and slow.
The iMac could see the external drive, but not the USB sticks. If it did see the USB sticks, it would delete them and I would have no idea if they were safe to remove from the computer. Writing to the External hard drive was also impossible. As was taking data from it, but it could see it.
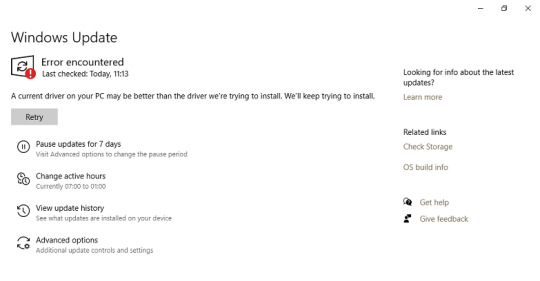
As I write this, I am back on the Linux desktop because the Windows Laptop has been unusable for almost four days. Why is this you may ask? The answer is because when I bought it, I could not afford very much and so bought myself a budget laptop. It has a Core i3 processor and four gigs of ram. The board in the case is the size of my mobile phone and the processor and the cooling fan are on opposite sides of the case (this is relevant shortly) with just one air vent, towards the front of the computer. While trying to render a picture of a Lego model, the computer began to overheat. The fan speed increased to maximum and the keyboard developed a hot spot that made it uncomfortable to use and then the screen went dark as the machine simply shut down. A full thermal throttling shut down that required fully dismantling to blow the dust from the fan and clear the pathway between fan and CPU. Given the amount of space inside the laptop casing, I am forced to ask why there is a six inch gap between the fan and the CPU, plus a four inch gap between the fan and the vent? The heat coming through the bottom of the machine made it uncomfortable to actually have on my lap (never do this, it blocks the vents) and the computer shut down to protect itself. When I finally restarted the laptop, I discovered that it had developed yet another instability, possibly due to thermal damage of the CPU. Meanwhile in the background, Windows update (that you cannot turn off) was slowly sucking away processing time from other functions. I have set the times when Windows can do updates, which is every evening when I am not writing. However, this update has got bigger and bigger, drawing more and more CPU time (I know because I have been watching the progress with CPU ID and monitoring the core temps) and is as we speak, only 8% downloaded of whatever current update it is now on, having restarted three (edit- four!) times already this morning.
So why am I angry? I am angry because none of these fucking things work as promised. When I do finally get them to work as I want, updates come down that fuck with my settings. I cannot prevent updates, they come with inevitable gloom and yes, I am aware that I can delay them or stop the machine from downloading on a metered connection, but just like HG Wells’ Martians, still they come! For four days, my Windows 10 Laptop has been installing, downloading and installing updates. It has been hanging while installing updates that when looking on the Microsoft website, they say it is time to start coding in the terminal.
The Crapbook gave me a message recently that read in nicer language, “give us more money or we will reveal your banking details to scammers…” Thanks for that Google, you cunts.
The Linux machine wants to update to the next version of the OS, that I have tried and really don’t like because it tries to make my desktop work like a mobile phone.
The iMac keeps telling me that it is too old and is not safe to use on line any more.
The Smart phone will interrupt what I am doing with it, to show me adverts. It also on occasion refuses to allow me to answer actual phone calls, because to do so, I must first attempt to close down an advert for emojis that will randomly appear. An advert that I neither wanted or asked for.
What was once a tool and an essential learning aid has become nought but a shallow toy, filled with advertising junk, following my every key tap, not to help me, but to sell me shit I don’t want and steal my data for companies to buy and sell me more shit I really don’t want. The machines I knew and loved are gone. Media outlets such as Linus Tech tips tell us that using old machines on line is irresponsible because it endangers everyone else to attack from scammers. The message is plain. Old is bad. Repair is bad. Throw it away and buy a new one… BUY BUY BUY, never fix. Sell my soul for old shit I don’t want. Stop using these wondrous machines for actual creative processes and use them instead to buy emojis for chatting with my friends. I fucking hate it. I fucking hate that tech companies can make their expensive computers so disposable. As much as I loved the iMac, Apple can fuck themselves in their arses with burning hot iron spikes for making them almost impossible to repair and even my trusted ASUS have gone the same way by putting the fan and the CPU in different sides of the case. Apple, Microsoft and Google have taken apart the computer world and used it to extract money from us the consumer, as if they did not have enough already. Also and probably finally for this angry rant, I really liked Theme Hospital! Bloaty Head Disease made me laugh and I can’t fucking play it any more.
I fucking hate these technology companies. They claim that they are making everything better, but what they are doing is making old but good things useless just so that they can convince us to buy the newer models of the old ones each year. To hell with the environmental impact of all of the e-waste, consume, play, dispose… When did computers become digital nappies?
PS. The Laptop is now on 85% of its forth install and restart of the day…
2 notes
·
View notes
Text
The lies, the secrets
Story No. 3 of my Season 7 Countdown Project! Also: I’m still taking prompts for future missing scene fics.
Summary: “My time undercover in the mafia was actually kind of lame. I mean, I wanted it to be badass, but I'm good at computers, so I mostly just helped them switch over from AOL.”
The story of how Jake became the mafia’s IT guy. Takes place during Undercover. (Read on AO3.)
What he doesn’t tell any of them, after he’s back, is that going undercover with the mafia is mostly just- really lonely.
Jake spends most of the first week alone in the crappy one-bedroom the FBI hooked him up with in Bushwick, waiting for one of the Ianuccis to get in touch. At night he lies awake on his mattress on the floor, mustard-yellow streetlight glaring through the grimy bedroom windows, and thinks that he’s already failed his assignment, that he couldn’t pass himself off as a disgraced cop for even one night. (The irony does not escape him.)
Then a guy calls Jake’s burner at 3 in the afternoon on the sixth day, and he introduces himself as Derek and says he’s downstairs. It’s now or never. Jakes takes a deep breath and blows it out hard, then steels himself and heads down. By the end of the week, he’s got a pierced ear and a gold-chain necklace and a cigar burn on the back of his neck, just below the collar of his new silk shirt. Years ago, before he’d gotten into the Academy, Jake had thought about getting a tattoo (“yippee ki yay” in calligraphy, very classy) in that spot and he’s grateful now that Gina talked him out of it. The burn was an initiation, and it didn’t hurt as much as he’d thought it would, but the scab is itchy and sometimes when he thinks of the smell of it he gets a little nauseated.
Leo Iannuci sends him out with Derek on a couple of jobs – mostly picking up cash from people they’re extorting from, but sometimes they’re the ones making the threats and Jake hates that part, hates it so much. Derek’s a nice guy, an Academy dropout who seems to shed his tough-guy attitude with his velour jacket every time they leave a bodega or laundromat or some other business where he’s had to smack someone around. Derek always does the hitting, never makes Jake do it, and Jake can’t decide if it’s because he likes the violence or if he just senses that Jake really, really doesn’t.
Either way, he’s grateful, and he has to keep himself from feeling too much fondness for Derek just because he protects Jake from the dirty work. Jake’s gotten that talk from the FBI: It’s natural to think you’re making friends, making connections, they’d said. But you’re not. Don’t ever forget that. Jake is always, always on his own.
About a month in, Jake is at Leo’s penthouse in Flushing, reeking of cologne that one of the Sals had doused him in while another Sal held him down, when Leo swears loudly and slaps the side of his computer, a rickety old desktop with a fan that sounds like it’s working triple-time.
“Motherfucker, it won’t let me fucking update!” Leo slams his fist down on top of the harddrive.
Jake looks around the room but everyone else suddenly seems to have important business on their phones, so he approaches Leo and says, “What’s the problem?”
Leo snarls at the computer. “I had to add some new clients to the ledger and now this son of a bitch won’t save the changes.”
Le’s “clients” could mean extortion victims or dirty cops or assassins-for-hire or any or all of the above. Jake hasn’t seen the ledger yet – he wasn’t actually sure there was one before this moment.
“You want some help?” he says, casually.
Leo finally turns his glare to Jake, staring him down long enough that Jake has to fight to keep from shifting on his feet and curling his hands into fists. “You any good with this shit?” Leo says.
Jake shrugs. “Yeah, I know computers.”
“All right, have at it,” Leo says, and gets up from the desk.
Jake sits, and Leo grips his shoulders, sudden and fast, fingers digging hard enough to bruise. And then just as suddenly he’s let go. He stays behind Jake, though, watching him click through open windows to find the source of the problem. It doesn’t take long.
“You’re using AOL,” Jake says. His voice sounds a little strangled to his own ears.
“Yeah, I guess,” Leo says. “So what?”
“So that’s your problem,” Jake says.
Jake’s definitely not an expert at computers, but he’s always had an affinity for the basics and it only takes him a few minutes to fix the immediate problem – an outdated file type that the desktop won’t recognize anymore. Jake saves the document, which, infuriatingly, is a table someone made in Microsoft Works. It’s so horrifically formatted that Jake can’t help but imagine the devastating stroke that Amy would suffer if she even knew it existed. She would seriously start bleeding out of her eyes.
Later that night, Jake smokes his first full cigar and convinces Leo to let him move all of their documents to a Google drive. By the end of his first full month undercover, Jake’s become the mob’s IT guy. It’s exactly as dope as it sounds. (It’s not remotely dope.)
+++
It takes him a couple of weeks to transfer everything to the cloud; he has to carefully rebuild all of the ledgers in proper spreadsheets. Leo assigns one of the Sals to keep an eye on him, but after the first hour Sal gets bored and retires to the couch to play Kwazy Cupcakes on his phone (the sound effects touch off a profound homesickness that Jake tries his best to ignore). So Jake has no trouble copying the ledgers onto a thumb drive that he later passes on to his handler. It’s almost all the evidence they need. Then it’s just a matter of waiting for the FBI to get its teams in place, to mark the right time and place to take down the biggest targets.
Jake does a few more jobs with Derek, and he just misses getting sent on a drug run that ends in a shootout and two of Iannuci’s guys in the hospital (Jake was back at Leo’s penthouse trying to figure out why his computer suddenly refused to talk to his printer). He knows he’s dodging literal bullets, but that doesn’t mean he sleeps well at night, or that his nervous system doesn’t light up like a Christmas tree every time someone racks a gun near him (which is pretty much all the time – mafia guys love cleaning their weapons).
Jake ends up giving a seminar to half a dozen Iannuci men (plus two women) on file encryption and two-step authentication and he feels a little guilty for teaching the mob how to evade hackers – some of whom will surely be cops – but weirdly, he’s starting to get bored, and he figures none of them are going to remember any of his lessons anyway.
The night before Marco and Angie’s wedding, Jake gets super drunk with a bunch of the guys and he sings “The Longest Time” with Derek, slopping rye whiskey all over their polyester shirts. The next day Jake’s going home. But that night, for the first time in 62 days, he forgets to be lonely.
End Notes:
Title is from Feed the Beast (Bash Brothers).
I know there is a lot of mafia-Jake fic, and that this take is not like the others. But I always thought Jake’s comment to Pimento about what he really did undercover was interesting and worth exploring. I don’t think it means the job wasn’t dangerous or super stressful for Jake, though my version is probably less so than some of the more violent takes some writers have offered (which are just as valid!).
I couldn’t decide if this story should be considered a missing scene for Undercover or Adrian Pimento. It fit better here for obvious reasons, but the revelation is in the later episode. But really, it doesn’t actually matter.
My darling beta @fezzle wisely pointed out that Jake the Computer Wizard doesn’t exactly fit with what we learn about him in Ticking Clocks. My solution/answer to this is that Jake is actually pretty good with day-to-day computer stuff (there’s quite a bit of evidence of this in canon – or at least, evidence that he’s not BAD with computers), but hacking-level stuff is way over his head. That’s why he starts Ticking Clocks full of bluster with the so-called security expert and then eventually has to admit he doesn’t know what he’s talking about. Unfortunately, what he actually says is “I don’t know anything about computers.” That could be the writers just forgetting their own canon, but I choose to believe that it actually fits just fine with Jake’s “I’m good at computers” in Adrian Pimento. It’s all about context!
10 notes
·
View notes
Text
2019 writing meme
i was tagged by @startofamoment, no doubt because I’ve been talking up that b99 porn star au that I started writing in 2016 but never completed.
It looks like how this meme goes is two lists: Things I am definitely going to write (or things I am definitely most likely going to write from startofamoment’s post) Things I’d like to write, time (and creativity) permitting
But I’m gonna do mine a little different, cause the thing is, I’ve already started writing drafts for literally all of these, like years ago in some cases, so- I mean, I’ve already started writing every single one of these, and have 4+ pages on some, 16+ pages on others, and there’s no telling what year they’ll actually be posted, but here’s some things from my technically wip stuff
Basically, works that I’ve already started the process of writing but who knows when they’ll be completed and just damn, I’ve got so much
The starmora/thorkyrie one shot where Valkyrie reacts to meeting and finding out who Gamora was the way that everyone expected Thor to react to Gamora in IW (confrontational AF- cue Valkyrie harshly whispering “How can you trust them?” and Thor just deadpanning “You literally sold me into slavery when we first met”)
Starmora college AU + artist!Peter and kickboxer!Gamora
Peraltiago Contract killer!Amy and target!Jake AU
Peraltiago Conceptual photographer!Jake + Model!Amy (also, former Art Student!Amy)
Childhood friends starmora AU/both raised by ravagers
Post IW/Post Endgame thorkyrie reunion one shot
Flight attendent!Jake Peralta + hates flying passenger!Amy Santiago
Pornstar peraltiago AU + coworkers to friends to lovers trope
The married peraltiago pregnancy multichapter fic I’ve been planning for AGES
Peraltiago Actors AU (Jake and Amy are actors on a TV show called Brooklyn Legal)
More and previews/excerpts under the cut ~
(And because tumblr mobile is going wonky, if this post looks weird, you can just open this post in your phone’s browser and tada! It’s in a readable format and looks like how I actually posted it!)
Dude, so I’ve got some previews for some of these, but I literally just copied and pasted without editing the slightest, so you can see while I may have pages and pages written out for all these stories on microsoft word/google docs, they are still very clearly not ready to post
That multichapter peraltiago pregnancy fic that I’ve had planned since, oh, FOREVER and still haven’t gotten around to-
“I just realized I'm gonna have to stop making sex tape jokes and switch over to dad jokes.” ”Jake, you already make way too many puns to be healthy and tell soul crushingly lame jokes all the time. You already make dad jokes, but they were just called lame jokes before you had a kid. Now your lame jokes can be called dad jokes. But you always had them.”
[In baby fic Jake still tackles her and pulls her to the ground, but its a careful tackle and he always makes sure to catch her and break her fall. It's kinda amazing how quick he does it, how they'll be chasing each other and he'll pull her to the ground, pull her into him. It's almost strange, how quick and gentle he is with it. With her. At first she might have worried about his rough housing, but he was always delicate. Careful but still fun. And she never had to worry about losing her balance with him]
Jake tackles her and she's laughing and hitting him on the arm and saying ”The baby, the baby!” And he pulls back and says “You know, you can't keep using that excuse. It's not fair.” And Amy says “I've still got months and months of that excuse” and he says ”It’s like saying you have to pee during a tickle fight. Now I have to let you go.”
{When Jake says excuse not fair cause its like saying she has to pee during a tickle fight and she thinks that's a fair excuse too not just baby, Amy asks jokingly "do you want me to pee on you?" And he says "you don't know. I might be into that."}.
Contract killer!Amy and target!Jake AU-
where they used to be childhood friends but hadn’t seen each other since they were like 9 years old, and then Amy realizes she recognizes the person she was just hired to kill
She's been struggling with this dilemma in her head for the past few days and even though it's completely irrational she decides not to do it. She decides to help him. She decides to help keep him alive. She actually did a coin toss. Heads she goes through with it and shoots him, tails she helps him. She flipped the coin. It landed on heads. And that cemented her decision.
She was going to help him.
She breaks into his apartment that evening since she learned he would be out.
She wears gloves. Looks through any papers he had, trying to find financials, but there's nothing to suggest why someone wanted him dead.
She wouldn't be much use keeping him alive if she didn't know why someone wanted him dead in the first place. And all the wire transfers for who hired her were anonymous. She turns on his computer and it isn't even password protected. It was a desktop and not a laptop, but still.
He must be the most naive and trusting idiot in the world.
She looks through the files on his computer and nothing useful turns up. He's so normal it's pissing her off.
She looks through his emails and there isn't even a hint of one lousy affair.
And she doesn't feel an ounce of guilt invading his privacy because it was a whole lot nicer than killing him.
She deserved a thank you.
But she can't find anything on why anyone would want him dead.
His plans were dinner with friends or something and it's been an hour at this point and she knows he could walk through the door at any moment and catch her.
Catch her having broken into his apartment. And she still had nothing.
And she decided to fuck it and just ask him. Just sit down on the couch in his living room and ask him who would want to kill him when he gets home.
This whole operation was already fucked, why not fuck it up some more? ___
she hears him unlock and open the door when he gets home. She hears him enter, shut the door, lock it behind him.
He walks down the hallway, finally to his living room and sees her.
He just stares at her and she says "c'mon dude, why the hell is it so hard to find out who wants you dead?"
And Jake blinks a couple seconds and then he says "uh, are you okay? Do you need help or something? Do you know where you are?" He asks like she may have accidentally gotten into his locked apartment cause she had a concussion and didn't know who the hell she was.
And she says "seriously? Seriously, man? I broke into your apartment and you ask me if I'm /okay/?" She sounds frustrated.
And he says "I think that's a fair assumption unless you were the worst robber in the history of ever. I walk in and there's a stranger sitting on my couch. Not stealing my couch, sitting on my couch. Correct me if I'm wrong but professional robbers are A: supposed to take stuff and B: supposed to be gone by the time the home owner comes back. So an empty handed stranger sitting on my couch who just starts talking to me like it ain't no thang instead of trying to flee the first thing my mind jumped to was not a criminal mastermind. Though that actually might be a smart plan after all. If you would've gotten a bowl of cereal and kicked back with the TV on the only logical assumption would be that you just walked out of a hospital ward and and the homeowner would probably call an ambulance to take the obviously confused and concussed woman back to the hospital and you could just walk out the door with all their valuables while they're making that call. That would actually be a great plan."
And Amy's like "don't give me tips on how to rob you better! What the hell is wrong with you?"
And Jake says "but you're not actually robbing me, are you? Cause you're doing a pretty piss poor job of it. Since you're not actually stealing anything can tell me what the hell you are doing here?"
Pornstar peraltiago AU + coworkers to friends to lovers trope
After the confessing feelings for each other part and kissing the heck out of each other:
“Okay, this is really nice and I'm loving it, but I also wanna be with you, not whoever we're supposed to be at work. I want to be touched by Jake Peralta, you know?” Her voice tiltered out, almost wincing, but she was sure he got what she meant. “Fuck, that's all I've ever wanted. Amy Santiago. Who I watch movies with and laugh and who falls asleep on my couch and I have to resist kissing her on the forehead every time.”
Brooklyn Legal - Peraltiago TV show actors AU
Eliza was essentially the let loose wild card character in their cast ensemble, something that could not be more opposite of the actor playing the character, Amy Santiago. Jake's character was in the main cast too, Lucas, who was the awkward book type, preferring hard cover law books when he had to research any preferences for cases instead of just using a computer. Jake and Amy still end up falling for each other.
Starmora college AU + artist!Peter and kickboxer!Gamora
“Your drawings. They’re not bad,” she said simply. “And either you messed up on this one here, or that man was not showing proper form,” she pointed out, down at one of his figure drawings of a man kicking the open air.
“Would you like me to show you how it’s actually done?” Gamora offered with an air of disinterested professionalism, though he’s certain he can see a smirk that’s just begging to be brought out from her lips.
He stared at her, blinking like an idiot. Then he started nodding, still like an idiot.
She gave him a single, curt nod in return before heading back to the mat she was practicing on, this time with a specific move in mind.
Gamora moved into position, breathed out, and let it overtake her.
"Would you like me to show you how it's actually done?" She offers with an air of disinterested professionalism, though he's certain he can see a smirk that's just begging to be brought out from her lips. Peter blinks once, twice. Like an idiot. Then he starts nodding, still like an idiot. Gamora nods at him once before walking away, walking back towards the mat, positioning herself right where she was practicing before. This time, though, with a specific movement in mind, putting on a show. She goes through her practice arsenal of moves, throwing in that one basically two or three moves, since his goal was to capture figures in motion, not figures in a pose. She kinda loses herself in the routine, and what he probably expected to be a 30 second demonstration turns into 5 minutes of her exercising and moving fluidly through her practice until she's breathing heavy and broken out into a sweat. When she decides to pause and take a break, she looks back over to her new friend/acquaintance, who is furiously scribbling in his sketchbook. Well, that's not quite true. His pencil is gliding across the page in a swift and fluid fashion, much like her movements were earlier. They're both getting their practice in of the art forms they've done a thousand times before, moving through the motions.
Conceptual photographer!Jake + Model!Amy (also, former Art Student!Amy)
When they're about to get started Amy says “I - I like your works.”
And he gives her a soft and polite smile with a “Thanks.”
And she realizes that everyone probably tells him that. Everyday. And they're probably all lying. And if they're not it was probably because they looked them up the night before and memorized all the facts so they could impress him.
That's why she got the polite smile. Because he hears that lie a million times a day by people trying to be polite or something.
And she recants immediately “No I don't. That was a total lie. I didn't even know your name until two weeks ago.” And she's totally flabbergasted but his smile is genuine now instead of polite and she doesn't know what to say or where she's going, but he has a really good smile and she just wants to keep talking so he'll keep smiling. “I like a work of yours. It was the only one I'd seen, and I didn't even know it was yours until two weeks ago when I looked you up and I saw it and I saw you made it, but I just recognized it by sight cause when I heard your name I didn't think I knew anything you ever did, but I was scrolling through it all and I realized that I'd seen it before. And I really liked it, I just didn't know who made it. I mean it's in a museum by my house and your name is on the plaque but all the times I looked at it I never even bothered to read the plaque. Not because I didn't like it, I just never read the plaques in art museums even on the stuff I really love. So I don't like you works or even really know any of them. I just really like the one.”
Childhood friends starmora AU
Later that night, after the eclector had left port, Gamora and Peter were sitting in Peter’s room, just talking.
“How come you didn’t tell me you could fix ships?” He asked, thinking that would have been something good for him to know to convince Yondu to let them take her aboard.
“I don’t,” Gamora said simply. At the confused look he gave her, she grinned something mischievous, like they were partners in crime. “I lied,” she admitted, laughing into her hand.
Peter in turn laughed that much harder.
“But I am a quick learner!” Gamora added quickly. She was pretty sure she could trust Peter, but she had still only met him today, and she had lied to his- captain? From the insolence he spoke to Yondu with, he seemed more like his father. Not in the way that Thanos insisted on calling himself Gamora’s father, but his actual father. She had come up with the lie spur of the moment, because her situation was urgent, and she needed to get off the planet as soon as possible. Anything was better than her siblings finding her and taking her back. Any repercussions from that fib paled to what would be in store if she was brought back to Sanctuary. “I’m good at memorizing stuff, so I can learn how to fix engines if the mechanic on board shows me how. I meant that, about earning my keep. I can be a- a apprentice or something. It wasn’t a total lie.”
“You’re not gonna tell him, are you?” She asked worriedly.
“What? No! I’m not a tattle tale!” Peter told her immediately, and even though she didn’t know what a tattle tale was, she could figure out what it meant from context clues. “He’ll probably figure it out on his own, though. But that’s okay-” he added quickly, when he saw the look of genuine fear in Gamora’s eyes. “Yondu says he values ‘ngenuity ‘‘n stuff. That just means if you manage to pull one over on him he’ll prolly laugh and give you a pat on the back and maybe a smack on the head for being a smart ass, but that’s it. I wouldn’t be here right now if Yondu wasn’t impressed by the few times I’ve managed to actually trick him. I mean- many times. I’ve tricked him oh so many times. Lots.”
Gamora laughed at that, because Peter was such a horrible liar. She didn’t think that was such a bad thing. No, it wasn’t bad at all.
Then flashforward like eight or so years and of Peter and Gamora fall in love because of course they do. So it’s really more of a raised by ravagers falling in love with your best friend starmora AU with a childhood friends prologue (plus some good ol fashion Peter whump with him almost dying on a solo mission they undertake cause yessss)
Post IW/post endgame Thor/Valkyrie reunion fic
“Hey! It’s me! It’s really me! I swear!” Thor held his hands up in a defensive posture, but that only seemed to anger her more.
“I know it’s you! That’s why I’m hitting you!”
She took another swing at him that he easily blocked- either she was too sleep deprived to at least hit him well, or she wasn’t trying as much as she wanted to seem.
They’d sparred before, and this definitely wasn’t even close to the full force of the Valkyrie. Still enough to hurt, though. Her movements were sloppy in a way she’d scolded him for when they had trained together following Ragnarok (“You’re too open, your majesty,” she informed him, with her trademark mocking tone at his title. Thor didn’t really mind. The teasing tone. He definitely minded the kick to the ribs he just got- it felt like they’d been punted into him. “When you swing, you swing wildly, and you make so much of yourself a target. You need to keep your hands up, when you punch, pull back, keep your shoulders tucked. It’s like you’re expecting your opponents not to hit back. Sure, you’re fine if you knock them out on the first punch, anything other than that, your technique leaves you wide open and your ribs prime for kicking,” she informed him, smirking while he was still struggling to breathe evenly again.)
It was the same too open critique she’d criticized him for months ago, the one that she said was fighting like he was expecting his opponents not to hit back. Her swings left her wide open, now.
Though, if she knew it was him, then she also knew he wouldn’t hit back. So maybe the too open fighting made sense right now.
“Aren’t you glad I’m alive?” He asked, blocking an elbow strike and deflecting the punch that followed. He caught her wrist, wrapped his hand around it before she could pull it back (“You’re too open”)
“Of course I’m glad you’re alive,” she growled, sounding much more mad than glad.
Starmora AU where they live in a seaside town and go to college together, and have a competitive rivalry going on as captains of the swimteam, then one day Gamora’s out on the ocean and a storm comes rolling in and she’s tossed overboard, only to be rescued from crashing waves by mermaid!Peter - like seriously, what the hell? This idiot that she’s known for years has a motherfucking mermaid tail???
Oh, and there’s a Sentinel/Guide AU with sentinel!Gamora and Guide!Peter
Plus, some lovely Elspeth Quill prompts that make my heart glow
Also, the B99/Peraltiago Daemon AU where Jake’s daemon is a badger named Jeremiah, and everyone’s like, how did the most cuddly person of a human being get something as scary and confrontational as an American Badger? They took on bears and wolves! On purpose!
Almost forgot about the multichapter Peraltiago space ark AU- it’s technically a series of one shots in the same universe, and a song fic, based on a concept album (so there’s 11 chapters, since the album has 11 songs in it) - I have the first chapter of this completely done, but nothing close to the other 10, and I feel bad about having so many multichapters open at the same time and updating them so slowly (hence why all this crap is in my unposted junk), but I might post chapter one of this soon just as a little ‘screw you (I say to myself and sense of obligation/anxiety), I’m having fun writing this, that’s the only mandatory thing about fic writing, if I’m enjoying myself and taking forever, that’s something to rejoice in, not feel bad about
So yeah, goodness knows when all this shit will be out. I think the closest things I have to done are the Peraltiago space ark ch 1 AU and the Thorkyrie reunion fic
Ima tag @peraltiagoisland, @nymphrea, @star-munches, @marypoppinswasmyfatherbitches, @thingssunspokenorotherwise, @interabangs, @perilinpeace @elsaclack
Please don’t feel obligated to participate if I tagged you, and if you’re looking for an example for the way you’re actually supposed to do this ask meme and not my weird way, startofamoment’s post here is good
(cough cough elsaclack i almost didn’t tag you cause i didn’t want you to be pressured cause i know how that be sometimes, but i love u, and your writing, and also wanted to wave some of my peraltiago stuff that i’m exctied about in your face and be like ‘look what I made!’/’haven’t made yet’)
But really, same goes for everyone here, you’re tagged because ily and i love your stuff, and don’t feel obligated to participate, don’t do this if it’ll stress you out/make you feel pressured in the long run, only do it if it sounds fun cause you’re all so freakin’ great and i want you to have fun
#b99#gotg#thorkyrie#peraltiago#starmora#fanfic#MCU fanfiction#AU#writing meme#thor x valkyrie#my fic#ask meme
8 notes
·
View notes
Text
Amazon.com : BlackBerry PlayBook 32GB 7″ Multi-Touch Tablet PC with 1 GHz Dual-Core Processor, 5MP Camera and Secondary 3MP Camera, Video, GPS, Wi-Fi and Bluetooth – Black : Tablet Computers : Computers & Accessories
Sharengay Trang Tin Tức Độc Đáo VIDEO Amazon.com : BlackBerry PlayBook 32GB 7″ Multi-Touch Tablet PC with 1 GHz Dual-Core Processor, 5MP Camera and Secondary 3MP Camera, Video, GPS, Wi-Fi and Bluetooth – Black : Tablet Computers : Computers & Accessories

Top reviews
Top reviews from the United States
Bạn đang xem: Amazon.com : BlackBerry PlayBook 32GB 7″ Multi-Touch Tablet PC with 1 GHz Dual-Core Processor, 5MP Camera and Secondary 3MP Camera, Video, GPS, Wi-Fi and Bluetooth – Black : Tablet Computers : Computers & Accessories
There was a problem filtering reviews right now. Please try again later.
Reviewed in the United States on April 19, 2017
Size: 32 GBVerified Purchase
A BlackBerry tablet seems like an odd purchase in 2017, but I did my homework and knew I wasn’t getting an iPad Air. I was getting this tablet for work – Spreadsheets, Word Docs and hopefully use the Bible app. The price was manageable and I figured that even if it turns out to be obsolete, I can still use it as a music player in our kitchen or something. Well, I was pleasantly surprised by this little tablet. The OS is brilliant. It’s such a joy and ease for multi-tasking. I was able to get my spreadsheets on it immediately and use it to check my messages and keep my calendar. The Bible app works flawlessly. Yes, the tablet is a little slow, but it’s a 2011 tablet, it’s to be expected. Yes, it doesn’t have a huge cache of apps to choose from, but the apps available are quality. I even found some fun games with great graphics. My music is fully loaded and the speakers are fantastic. I even tried taking a few pics and the quality is impressive! It’s not great for social media. Facebook is functional but not great. Instagram and Netflix simply won’t work on this tablet. You can go the Instagram website and at least view pictures, but that’s all. I did manage to get YouTube working with an browser I downloaded from BlackBerry World called “Frost”. Just go to the YouTube web page and it works great. It let me sign in, but I had to re-sign in every time I opened it. But when the videos play on YouTube, you can leave the app and the video keeps playing – very cool! I also have a BlackBerry Passport phone and it lets me sync with it and my Playbook to text and send BBMs. If you’re willing to put in a little work and do some research, you can get some current Android apps working on this thing. I have Evernote, Kindle, and even a version of Google Maps working. Again, do not expect this tablet to be everything the current tablets are, but if you want to spend very little and get a functional tablet that can serve a few purposes well, give this a look. The best things about this Tablet is the multi-tasking feature, the Messaging inbox, the speakers, the quality of the screen and the price. The negatives are a lack of apps and the general slowness. Hope this helps someone!
Reviewed in the United States on July 8, 2015
Verified Purchase
The Blackberry Playbook Tablet isn’t for those hardcore iPad and Android people. In fact, I would not recommend you buy this tablet if that is the kind of person you are. This tablet is almost like a beginning step into the world of tablets. You get plenty of memory on the tablet for a price lower than any other competitor offer, but there is good reason for that. For one, this tablet is older than these fancy tablets that we see nowadays, so the specs aren’t as hot. There is Bluetooth, but if you have an iPhone or Android or just anything that isn’t a Blackberry, your phone is not going to interact with this tablet other than giving it data. It CAN’T support file sharing like pictures or music through Bluetooth, but you can plug it into your computer to upload files onto it. Apps are not exact the strong suite of the Playbook either. It has a more limited version of the Blackberry World for the Blackberry phones, so don’t expect all the top of the line games and apps to be on here, through there are a few here and there. I would suggest this tablet to people who want to do some basic browsing on the web, check facebook, and just relax while on the go. I wouldn’t say it is a bad tablet for getting your work done, but I don’t think this is the tablet you should be relying on.
Reviewed in the United States on March 1, 2012
Size: 16 GBVerified Purchase
I love this thing!
—– (update) —— Tip to improve WiFi reception
The 2.4 Ghz WiFi antenna is in the upper left hand corner in landscape orientation. Wrapping your hand around this corner to hold Playbook, as I like to do, reduces WiFi signal strength a lot (a bar or two, factor of x100 or 20 dbm), which can be the difference between getting online or not when traveling. A simple trick to get good WiFi reception while still holding Playbook with the left hand is just flip the Playbook over so the ‘Blackberry’ logo is on top. This puts the most commonly used 2.4 Ghz WiFi antenna on the right.
Check out the ‘SANOXY Bluethooth Keyboard for iPad’. It’s a very inexpensive bluetooth keyboard that works fine with Playbook. ————— 7″ screen size is fine, sharp as a tack (viewed with reading lens of bifocals), bright and colorful, sound good, screen responsive to touch. Swipes easy to learn.
On browser homepage On my desktop browsers I have all my frequently visited links in a single custom .html file that I set as my homepage. To me a custom .html homepage is essential, it makes bouncing around the web fast and easy. I first tried copying my custom .html file into the ‘Document’ folder, but found it was not visible under ‘Document’ icon, but later going backdoor I got it installed as the browser homepage. Here’s the procedure:
Type into browser: file:///accounts/1000/shared (note 3 ///)
This brings up a simple file manager that allows you to see what files are in memory and even to launch them. In the Document folder was my custom html homepage file, which I had earlier copied over via USB. Tapping the filename loaded it into the browser, and holding my finger on it allowed me to copy the filename (via the copy box). Finally going into the browser settings I was able to paste the filename into the homepage window. Now every time I start the browser up comes my custom homepage.
Another neat trick is to have alternate start links for the browser on your home screen. This is done by clicking the star+ button and selecting add to home screen. For example I have a icon that will start the browser at the New York Times and another for local radar.
On media files MP3 files can simply be copied over and will play. Video files are more difficult. I have a library of captured .flv files and captured TV shows in .ts format, some of which I would like to put on the Playbook to view when out of WiFi range. However, neither of these file formats is supported directly on the Playbook. In principle there are two options: copy over the file and use an app that does on the fly conversion, or two, preconvert the file to a supported format (like .avi or .mp4). I experimented with both.
Xem thêm: LHS Thứ Sáu 22.11.2019: TIN VIỆC LÀM ĐÚNG – Linh mục Antôn Lê Ngọc Thanh, DCCT
There are several apps that claim to allow you to play .flv files on Playbook. I bought one for $0.99 and while it played .flv files, it was not clean (position slider did not work). I tried a couple of converter programs, which you run on your desktop before downloading. The best (by far) was Freemake Video Converter, not only is it free, but it’s simple to use and will convert a batch of files in one shot. I found it shrank the file size of .ts files, which are initially quite large, by roughly x3 and expanded the size of .flv files, which are initially small, by roughly x2. ————- update My tests show HD (1080p) videos taken by Playbook are quite large, about 6 Gbyte/hour. I found running them through Freemake Video Converter with NO change in resolution, file type, or video quality reduced file size to 2 Gbyte/hour, a factor of 3. Very handy if you want to keep lot of Playbook video stored on the Playbook. ————- Before converting a lot of files I did several tests comparing file formats and resolution. Freemake Video Converter makes it easy to reduce file size by lowering resolution. Tests with a sharp HD video showed no difference that I could see between 1080p and 720p on this small screen, so I decided to go with 720p. This resolution reduces .ts file size by a factor of 4. Reducing quality to TV level, still very watchable, reduces .ts file size by a factor of six.
Quick tests of various formats (avi, mp4, wmv) showed no significant difference in quality or file size and all seemed to play fine on Playbook, so I choose avi and began converting. This turned out to be a mistake. Not one of the first three converted TV shows (1 hr) would play correctly on Playbook. One refused to open and other two gave an error when the slider was moved, though all played correctly on my desktop. The only reason I can come up with is that Playbook has a problem with long files in avi format. My quick tests had been with short files. I then noticed that it says in the Blackberry document, ‘Supported Media Types on Blackberry Tablets’, avi. wmv, and mp4 are “supported”, but the “recommended video format for local playback” is mp4. So I reconverted the same three TV shows to mp4, also lowering the resolution one step to 720p, and now all played fine on Playbook. So my recommendation is stick with mp4, which is the format Playbook uses for its own videos, and reduce resolution to 720p (1280 x 720).
WiFi file transfer A neat trick to easily transfer files to Playbook from your computer over WiFi (no cable!) is to put a shortcut to Playbook on your Windows desktop. Set the ‘target’ of the shortcut to either the IP of your Playbook (found under About, Network) or the ‘Tablet Network Name’, which you can change (found under Storage and Sharing, Network properties) preceded by \ (two backslashes). When you click on the shortcut, Explorer opens and Playbook will appear as a Network device. Click the Media folder and you now have access to all Playbook media folders. For this to work the Playbook ‘WiFi Sharing’ setting (in Storage and Sharing) needs to be ON. Transfer rate is a little slower than with a USB cable (about half), but perfectly usable. (update) For some non-transfer operations, like file rename, I find USB more reliable than WiFi.
Html files, pdf files and File manager The Blackberry (so called) “File Manager” doesn’t show file details, and critically (for some weird reason) it hides local html files, though it does show local pdf files and allows you to open them. Real file managers are available in App World. A pretty good basic file manager (free) is ‘AIR Browser’ and better is ‘File Browser’ (a buck).
‘Air Browser’ and ‘File Browser’ provide a way to work with local html files, they show them and will open them in the browser. Once open in the browser local html files work well, all the internal and external links work. I find it frustrating that Blackberry doesn’t provide direct support for local html files, because I have a whole library of such files that I want to use on the Playbook.
Privacy A useful app for file privacy is ‘File Shield’ (buck). It provides a simple way (without passwords!) to hide videos, photos, and documents. In the app directories and individual files can be toggled between private and public. When set to private, files and directories effectively disappear, visible neither to Blackberry applications nor file managers.
Bugs and weirdnesses I bought just after OS 2 release and my OS upgraded to 2.0 when my new tablet initialized. Here are the bugs and weirdnesses I have found in a week or so of use.
— I initally wrote that my volume up/dn buttons had never worked and assumed it was a software bug because I read someone else reported volume buttons stopped working after an upgrade to OS 2.0. See comments where Ronald kindly set me straight. — Video application has a couple of drawbacks, one is no folders. In the pictures application if you organize picture files in subfolders, the opening screen shows only the subfolders. Not so with the video application. You can put videos in subfolders, but the video application still displays all your videos files on the opening screen. Primitive and inconsistent. Even more surprising the video application displays videos (with the formats it supports) regardless of the folder. Put a video in say, Voice folder, and it still shows up under Videos. — The video application provides two display views: Downloaded Videos and Recorded Videos. Videos uploading to the Camera directory are displayed in the Recorded Video view ordered by the file time stamp, so some separation of videos is possible. Videos in the Downloaded Videos view are ordered alphabetically, No other sort appears to be possible. — Document mode of the browser does not work right in portrait orientation (tested with New York Times articles) — a Hotmail text message in browser would not finger expand — Adobe’s pdf reader come installed on the Playbook, but it is not well integrated with the browser. When a pdf link in the browser is clicked, instead of just opening the file your only option is to download the file. — ‘Power Off’ is a built-in Blackberry app with just three power buttons that are the same as under the battery icon. ‘StandBy’ in the app does not put the tablet to sleep (as it should), it does a ReStart (locking up your machine for two minutes)! You have to wonder just how much testing Blackberry does when a trivial app like this does not work right after a major OS upgrade. — As I discussed above, it appears the video player has a problem with long .avi files, though this format claims to be “supported”. — With Blackberry emphasis on security it is surprising its OS does not directly provide support the hiding of files. — After a week of use the browser crashed (gray screen) requiring Playbook restart to fix it. — On my 2nd day with Playbook it crashed (it first refused to open files, then it hung with Shutting down splash screen displayed). There is a way to hardware reset the Playbook, equivalent to holding down the power button on Windows desktops, but I had to search the web to find it. It’s hold down three of top four buttons (vol up, vol dn and power) for 10-15 sec (or until you see red led). This restored my Playbook to good health with no loss of data. I took off one star (5 => 4) for the volume buttons not working (whoops, see comments) and for a system crash in two days of use.
Top reviews from other countries

LauraUK
4.0 out of 5 stars A good tablet for non-Apps addicts 🙂
Reviewed in the United Kingdom on June 16, 2014
Verified Purchase
I know it might sound crazy to some, but yesterday I bought my second Playbook at an excellent price. Last year we bought a Playbook hoping that Blackberry would release their BBM 10 software. Well, they didn’t but we are still using our Blackberry on a daily basis to surf the web and watch cartoons on Youtube. This is our main use for the Playbook, and although there are games and apps, we haven’t got enough time to spend playing whatever game is in fashion. My daughter, however, has got some nice apps to play and draw that can keep her busy. We also use the Playbook as a PDF reader and now with the second one we will use it to video chat when away from the family for work. At least this is our hope, since sadly we didn’t manage to do this with the Blackberry Z10, which I had to return. All in all, for the price we paid, we are satisfied. It charges quickly with the fast charging docking station and I am sure that we don’t use it to its full potential. We have a terrible computer at home and we haven’t downloaded music or videos onto the Playbook yet. I am sure that if we really needed Apps such as Skype or Whatsapp (or anything else that is in fashion these days) this would not be the tablet to buy, but these Apps can be installed on a smartphone very easily. All in all, a good tablet for web browsing and media playing if the budget is tight.

JontyB
4.0 out of 5 stars Great Performer
Reviewed in the United Kingdom on September 22, 2011
Size: 32 GBVerified Purchase
I love the Playbook. It is a handy size with an excellent fast browser supporting Flash video. It is sturdy and very well put together. Unfortunately apps are limited and you need a Blackberry smartphone at hand to enable the bluetooth ‘Bridge’ that links your emails, address book & calendar. We have been promised future compatability with Android apps that should greatly increase the appeal.
The Playbbok is also tethered by bluetooth to access your phone’s 3G network, useful if you are unable to obtain a wifi signal. There is therefore no need for a 3G variant making the Playbook a good value alternative to the i-Pad. The Playbook has HDMEI, USB and Fast Charge connectors but no memory expansion capability or SD card. I would thererfore recommend at least the 32MB version.
I did have a little difficulty getting the software to start-up but the free 90 days UK support line soon sorted the problem and it has been trouble free since. It is comforting to know that that there is help from Blackberry if you need it.

M. Hallett
5.0 out of 5 stars it’s brilliant. There is the problem that it was a …
Reviewed in the United Kingdom on January 13, 2015
Verified Purchase
I’ve had the Playbook for around eighteen months now. It’s an absolute bargain compared to other tablets on the market. If you want to use your email, surf the web, take pictures or video, store documents, listen to music, or use a few simple commonplace apps, it’s brilliant. There is the problem that it was a commercial disaster for Blackberry and so they’ve given up on it really, which is a shame. I would suggest you download the origami browser – it is streets ahead of the native Blackberry browser. I don’t give a damn about having 101 applications or playing games. If you don’t care about that sort of thing either then this is a smashing buy.
Xem thêm: Một người bạn thật sự là người bước vào cuộc sống của bạn khi cả thế giới đã bước ra – Thien Vlogs

MW_GB
3.0 out of 5 stars Its no iPad and its not about the Apps
Reviewed in the United Kingdom on May 28, 2012
Size: 32 GBVerified Purchase
Lots of good reviews, but I suggest you ask yourself why you’re thinking of buying this. Better be becasue its cheap, because its not best.
Ok; its far from junk. Its nicely built, has a bright screen (great for showing off pictures & video) & a competent web-browser. I like the size and weight. BlackBerry Bridge is a useful feature if (like me) you’re one of a seemingly dwindling band of BB users.
But there are some signficant problems. Its slow to boot up (90 seonds maybe, unless you leave in stand-by and that drains the battery quickly), its slow to charge (I leave it overnight), bettery life is poor if you are using Bluetooth (maybe only a couple of hours), I find the touchscreen is often unresponsive, and the browser sometines spontanioulsy shuts down (in fairness the OS2 upgrade seems to have improved that). And its just awkward to get things done (try mailing a photo or file to a contact – virtually impossible with OS1, clunky and slow with OS2, unless you connect to a PC, which at least you can do, but is hardly the point surely). BB Bridge freezes & I’ve had to reinstall 3 times (tough to do by the way – if you’re interested, try to delete BB Bridge AND Bluetooth items on BOTH devises & start install from stratch). I watch streamed videos on my iPhone, but they won’t play on the Playbook on the same WiFi.
You get the picture… but the point is that iPad users I know report none of the above proplems…. To be clear, I’m Apple agnostic, but I’m just left wondering if RMI have put anywhere near enough development into the Playbook, or have just lost interest.
So I bought it becaue I’m a BB user and wanted a reasonably cheap tablet to find out if I would get use out if it. I do. And it somewhat pains me to say it, but my next one will be an iPad.

John Dare
4.0 out of 5 stars Lovely piece of kit, but far too many issues with apps.
Reviewed in the United Kingdom on June 25, 2013
Verified Purchase
Pros – well built and sturdy, decent built in browser. good audio for a small tablet, plenty of built in storage, very acceptable screen resolution, wifi connects easily, OK cameras, fair price.
Cons – very few decent apps and most of those are way too expensive, android apps have to be sideloaded – fiddly and time consuming, RIM constantly promising upgrade to BB10 at some point in the future but it never seems to happen and now never will(see next paragraph).
This could and should have been almost a significant a tablet as the ipad but has been constantly let down by appalling planning and support from RIM. It’s such a pity because there is a lot to like about the Playbook and even 2 years after it’s launch it still performs almost as well as many newer and more expensive tablets. If only the OS could be properly upgraded. Sadly RIM have now decided NOT to upgrade the OS to BB10 and have therefore totally let down very many Playbook owners.
Paraphrasing the the words of my old headmaster – “with a little more effort RIM could do so much better”!
I have just added a fourth star, as I get used to it sideloading becomes easier. NO chance of a 5th star since RIM have reneged on their promises to upgrade to BB10.
Nguồn: https://sharengay.online Danh mục: Đời Sống
Amazon.com : BlackBerry PlayBook 32GB 7″ Multi-Touch Tablet PC with 1 GHz Dual-Core Processor, 5MP Camera and Secondary 3MP Camera, Video, GPS, Wi-Fi and Bluetooth – Black : Tablet Computers : Computers & Accessories
from Sharengay Trang Tin Tức Độc Đáo VIDEO https://ift.tt/2UyO26D via IFTTT
0 notes
Text
Why I stopped hacking. For good. Part 2. by Menmaro
Allow me to preface this second part by thanking those who read my first part and enjoyed it. I would like to apologise for any poor grammar/spelling or formatting as I am writing this on my on my phone so formatting is extremely difficult. My laptop is in another country at the moment so when I return home I will format these stories and future ones properly. Please bear with me and enjoy part 2.
I would also like to add that this tale is of an encounter of a friend of mine. I did not experience this first hand and thus I have to make up what his thoughts were (some are his exact thoughts) to what I would have expected him to feel from knowing him. This story is how he told me so as far as I know it is true. He has stopped hacking and spends most of his time gaming and working.
Continued.
I stood frozen in horror. Panic swept over my body and thoughts flooded my mind. What happened to my mother? Is she OK? What is this son of a bitch doing with her phone? I knew I had to calm down, something didn't seem right. I picked up the phone and looked at the caller ID. It just said mum, no number. Fuck, how could I be so stupid, he was just masking his caller ID, must be to throw me off balance. I'll play along, there must be something I'm missing.
"Wh.. What are you doing with my mum's phone? Where is she? Is she OK?"
A laugh came from the other end, a deep, disgusting laugh. I decided to record the call, maybe I can play around with the recording and find this caller’s real voice. It may not be much, but this asshole knows where I live and probably who my parents are. He starts talking.
"Danni, Danni, Danni. The safety of your mother depends on the outcome of our little game. I told you one's life is on the line but, I should have elaborated and said it shouldn't necessarily be the player's life. So, are you ready to play?"
At this point I had a thought; How can James see me? I have no cameras connected to the WiFi, my desktop camera is disconnected and I ripped out my laptop camera when I got the damn thing. Another option would be he broke into my apartment and installed cameras when I was out. But why would he risk getting caught like that. I may have cameras at home and catch him doing it. No he must be using one of my devices.
“Doesn't seem like I have a choice James. Let's fucking play.”
I braced myself for what he would say. We’ve all watched those horror movies, these games weren’t exactly Mario Kart sort of level. Suddenly I knew, I wanted to throw myself from my apartment for how stupid I'd been. In my hand I held the single device that had a camera and was connected to my WiFi. My fucking phone. I didn't want to jump to the conclusion that that was the only camera that was being used, so I decided to test it. Before I do anything though, he begins to speak.
“Well well Danni, I must say, you’ve got balls. Most guys would have started to cry or beg me to stop. This will most certainly be fun.”
I've had enough of this shit. I start to test my theory. I started googling shit like “how to track a phone call”, and “how to find cameras in a house”. I wanted to see if he could see my screen and sure enough the confirmation came through.
“Oh Danni, it’s cute you’re still trying to fight back. But I can assure you, you will not be able to track this call and you will not find out how I can see you.”
Challenge accepted dickhead. I angle my phone away from my bag and take out a USB dongle. If this asshole is on my WiFi I'm gonna make him think he's controlling all of my devices. I look for my laptop whilst trying to make as little noise as possible and again, angling the phone away from what I am doing. I find my laptop, boot it up and plug my dongle into it.
“Yeah well, I'm one tough son of a bitch… so when we playing James? And do go over the rules properly yeah? I'd like to whoop your ass playing by your rules dipshit.”
My strategy was to show no fear. In truth, I was terrified. But I knew the instant he smelled fear, he would have total control over me, and I'd fuck up and forget basic stuff like I had when this shit show first started. My laptop finished booting up. Excellent. I knew this fucker was using my network somehow. So I decided to hack my own network and see how he got in. Maybe he left something behind.
“The rules are simple Danni. You wanted to play judge, jury and executioner. We are going to go through your history of white knight justice, and see just how much of a hero you really are.”
Hero… huh… there was a time when I thought I was a hero… maybe it was when I made that child molestor end his own life. I told myself I was a hero because he wouldn't hurt another child. In truth, was I a murderer? Was this my past coming to haunt me? No time to think about this. It isn't just my life on the line here, everyone I care about is in danger and there's no time to be selfish.
“Ha… hero… that’s cute James, but I’ve always known I was the devil. A necessary evil. But sure, let's take a walk down memory lane. Maybe that will remind you who the fuck you’re dealing with.”
My attempts were bringing up nothing. I managed to break into my own network many times but I couldn't find a trace of another device, not a trace of information transfer. Wait… information transfer. Outgoing and incoming traffic. Fuck I'm stupid. He can see a stream of my screen which means I have outgoing traffic somewhere right? I start monitoring my outgoing traffic. Encrypted of course but there was still an address. A server that this information was going through. I find the address of the server and decide to do something extremely stupid and might sentence myself to prison or worse, no access to a computer. But I decide that is a small price to pay for the safety of my family.
“Well well Danni, watch your screen as the images pop up. Leeeeets roll the tape ladies and gentlemen.”
What a fucking psycho, I don't pay much attention to the tone of his voice as I set up my botnet for a distributed denial of service attack. My hope is that if I bring down the server for a bit, I'll be able to see where the requests are coming from and track it from there. It is a long shot but it might work. As I'm doing this I also stop recording the call and send the recording over to my laptop. All the while I’m angling my phone away from my laptop, and since he hasn't spoken of it, my theory that the only camera being my phone turns out to be correct. I finally feel like I'm making the right moves in this twisted game of chess, I'm just hoping I'll be the one to say checkmate at the end though.
“Victim number one; Brock. 16 years old. You destroyed his relationship and got him kicked out of his home. He spent 3 years on the streets before overdosing on heroine. That wasn’t a nice thing to do Danni.”
A picture of 16 year old Brock pops up. He died? Fuck, he was an asshole but didn't deserve to die. I went to far… I went to far… but I couldn't admit it. Not to this psycho. I had to show him that I had no heart.
“Well life sucks, survival of the fittest and all that shit. Maybe he should have been careful with whom he messed with.”
Another disgusting laugh. James is enjoying himself… should I be? No time for that right now. I put the phone on loudspeaker and placed it on my desk, weary that the front camera may be used I kept it well out of my sight and put an earphone into my left ear. Time to tweak around with this recording and “unmodulate” this voice.
“Danni, this isn't gonna end up well if you show no remorse. Now the fun begins. Remember his girlfriend? It’s confession time Danniiiii.”
As if it were alive, my PC opened up Skype and auto signed in. Fuck I'm so stupid, was I really that lazy? A number is entered into it and it starts dialling. Ring ring…
“What do you want me to do James? Tell her the online babe was me and Brock wasn't a cheating dickhead? What's that going to change?”
My botnet was ready and I started my attack on the server address instantly. I then watched my incoming and outgoing traffic closely. All I needed was a hiccup, something that will lead me to James. In that moment it was like the entire world grinded to a halt. In that moment, it wouldn't matter to me if the moon was crashing down onto the Earth to end all life as we knew it. All that mattered was this stream of information. Tick tock tick tock tick tock. I could hear the second hand on my watch ticking…
There! A clue… phew, was starting to lose hope. I start work on it, did James notice? I'd imagine his connection to my network might have dropped since I saw a request ping but nothing going back. Was he too busy trying to guilt trip me that he got too cocky and didn't notice? My Skype was still ringing was she going to pick up?
“Hello?” A girl's voice. She sounds kinda cute actually, is James hooking us up? Wrong time for jokes there.
James speaks to me “Go on Danni, answer her. Tell her your name and what you did to Brock.”
I decide to play along, true he didn't call me from my mum’s number, but that doesn't mean he still can't hurt her.
“Liz? It’s Daniel Kurt. We went to school together with Brock.”
There was a pause, I can't imagine how awkward this must be for her. I didn't have time to care though, I ran a search on the address and whilst that was going on, I continued tweaking with the recording.
“Danni? That loony kid that used to get beaten up all the time?”
Ahhh what a bitch. Hooking us up my ass. I had to fight back the urge to shout and educate her ignorant ass on what autism was. Whatever though, not my concern. At least breaking this news to here won't be as painful to me as I thought.
“Yeah that's me, the loony kid.” I laughed and I could swear I heard James laughing too. Asshole. “So listen, don't suppose you remember Brock Leland? You kinda slept with him at that time.” Maybe not the best choice of words.
“Yeah I remember him, I heard he died from drug overdose, makes me feel horrible breaking up with him…” another pause, “why?”
Fuck. How do I say this? This is a confession, if she takes this to the police I'm fucking screwed. Fuck any chance I have of getting away with this. I was 16 though, does it matter? I read somewhere that crimes committed before 18 aren't dealt with anymore. I was just a kid? Damn it. To hell with this, I need to stop this madness before he makes me call a victim of an attack I committed after 18.
“Yeah well, it’s my fault he did this. He made my life shit for when I was at school. So I decided to fight back. He never cheated on you, I made it look like he was.”
A really long pause. Gives me time to work on this recording. Nothing remotely human yet. Still searching that address, why is it taking forever?
“Danni.” Her voice was extremely soft. I was expecting something else. An angrier tone would have made more sense.
“Yeah...?”
“I know.”
1 note
·
View note
Text
Hackers Dissect ‘Mr. Robot’ Season 4 Episode 9: ‘Conflict’
Episode 9 of Mr. Robot’s final season was not only amazing plot-wise but also happily filled with hacks. We discussed [SPOILERS, obvs] IMSI catchers, Raspberry Pis, PGP, phishing telcos and stealing cryptocurrency. (The chat transcript has been edited for brevity, clarity, and chronology.)
This week’s team of experts includes:
Em Best: a former hacker and current journalist and transparency advocate with a specialty in counterintelligence and national security.
Trammell Hudson: a security researcher who likes to take things apart.
Micah Lee: a technologist with a focus on operational security, source protection, privacy and cryptography, as well as Director of Information Security at The Intercept.
Freddy Martinez: a technologist and public records expert. He serves as a Director for the Chicago-based Lucy Parsons Labs.
Yael Grauer (moderator): an investigative tech reporter covering online privacy and security, digital freedom, mass surveillance and hacking.
IMSI Catchers
Yael: I thought it was clever of Darlene and Elliot/Mr. Robot to use IMSI catchers.
Micah: I've never had a chance to play with one for real, But they're also referred to as "cell site simulators" because they simulate cell phone towers. Your phone tries to connect to the tower with the strongest signal, so in order to do a man-in-the-middle attack against cell phones, you just need to broadcast a stronger signal than the nearest cell phone tower and nearby phones will connect to your IMSI catcher instead. Then, you forward the traffic to the real cell phone tower, so the phones will still work, but you can spy on/modify all the traffic in the meantime
Yael: I’ve written about them before, but it was about law enforcement use of them for surveillance. They can’t intercept Signal messages, right? So if Deus Group just read a Freedom of the Press Foundation guide, Darlene and Elliot's plot would be foiled.
Em: It will intercept the Signal data, but messages are encrypted until they reach the recipient’s device, so it's not enough to just intercept it.
Micah: Their plot wouldn't have been foiled because Cyprus National Bank still sends two-factor authentication codes (2FA) over unencrypted SMS. I thought it was a nice touch how much Raspberry Pis were represented. In the first scene, in the hotel, the camera panned across some Raspberry Pis, and Darlene was logged in to a Raspberry Pi during the garage door hack.

Image: USA
Freddy: The Raspberry Pi 3 uses USB 3.0, which is fast enough to run a homemade IMSI Catcher.
Em: Homemade antennas are fun. =)
Yael: Oh, did they make their own?
Freddy: You can make your own. I think those are limeSDRs.
Price’s Last Stand
Yael: We had Price in yet another hostage situation.
Em: Yeah, he handled it very well. The traditional ways of getting out of a hostage situation weren't going to work there, but he did several important things for the situation he was in:
1. He kept calm. This is the most important thing. If he had panicked he'd have been killed a lot sooner.
2. He kept Whiterose off balance. His teasing and taunting was beautiful to watch, especially the "wind in his hair" bit.
3. He didn’t give up any important info to accomplish number 2.
4. He provoked Whiterose when they were both visible outside. Walking away after saying what he said almost guaranteed not only that he'd be shot there but that Whiterose would do it—in public.
Yael: My favorite taunts were, “it’s bad management when your best employees either walk off the job or blow their brains out,” and “all this over a little pipsqueak in a hoodie.” I think Price kind of didn't care if he died after Angela died.
Em: I think he didn't care if he died but he wanted to get Whiterose first. Once he handed off the drive (which he did right before going to the meeting), he had accepted his fate.
Freddy: You can't control people who have nothing to lose.
Em: Or to gain.
Micah: I like how Mr. Robot explained why he was there in the hotel room, instead of Elliot, by saying, "Life throws you an error code like that, you don't have the luxury of a fucking pop-up explanation."
The Bank Heist
Yael: Okay, so let’s talk about the hack. They said they needed to correlate phone numbers with bank account numbers to initiate the money transfers.
Em: They needed that for the script so they'd know which 2FA code to use for which request. Otherwise they'd have to brute-force it for each account, and that'd likely trigger a safety measure.
Micah: So Elliot and Darlene seem to have a SQL database from the bank, and their database includes account numbers, first name, last name, and hashed phone numbers. They needed to use the IMSI catcher (and the cell phone tower hack) to learn everyone's phone numbers, so they could hash them and then lookup the hashes in the bank database until they had phone numbers for all 100 accounts
Em: That's pretty realistic, FWIW. An equivalent of that was one of the first things we pulled from Phineas Fisher’s hack of Cayman National Bank and Trust (much to the dismay of some of the account holders).
Trammell: There was a CCC talk about nation-states doing 2FA intercept on Telegram password resets.
Micah: So, the venue changed. They got a hotel room within line of sight of the first venue, and they expected all Deus Group members to show up there, but the location moved. Mr. Robot figured out that Whiterose was at the first venue, though. So Darlene went to the second venue with the IMSI catcher, and Mr. Robot/Elliot stayed at the first venue to try to focus on just Whiterose's phone number. So all that hacking that Mr. Robot was doing, he was hacking into the telecom company that owns the closest cell phone tower.
Yael: How did Whiterose figure out that they needed a venue change and he had to get at Price?
Freddy: She said that Elliot disappeared right after Price said he was retiring, and that Price asked for a Deus Group meeting on Xmas, which was suspicious.
Micah: Elliot had a dump of Tyrell Wellick's phone, and it looks like he and Darlene imported Tyrell's Firefox passwords into Iceweasel, and then looked through his Google calendar. There was a password-protected attachment in one calendar event, and the thing I don't quite understand is how they got the password. I think Darlene sent it to him in Signal Desktop, but I don't know how they knew what it was.
Image: USA
Freddy: It almost looked like a script to execute, but I couldn't tell. Maybe it was a pop-up?
Yael: I think it directed to a password-protected webpage hosted on some kind of private server. So I guess Whiterose got sloppy and forgot to take Tyrell off the list of people getting the venue change.
Micah: Tyrell was the guest of honor; he was getting named new CEO of Evil Corp. She just didn't realize he was dead.
Yael: I'm sort of stunned Whiterose didn't know Tyrell was dead or at least missing, with their surveillance..
Em: It happened in the middle of nowhere and the FBI didn't handle the crime scene, so the search around the van etc. was limited.
Yael: Yeah, but they had eyes on Tyrell and would've noticed he was missing after.
Hacking The Cell Tower
Micah: Okay, so let's talk about the cell phone tower hack.
Yael: Elliot was phishing telecom employees to try to get access to the cell phone tower because he didn't have the cell-site simulator.
Micah: Yeah, exactly. He needed to hack the cell phone tower, because that would give him the same access as if he had his own IMSI catcher. Once he got credentials from his phishing, he was trying to re-use them to login to the telco's VPN.
Yael: So what's easier and more reliable, building your own IMSI catcher or phishing telcos?
Freddy: Probably the latter, to be quite honest.
Micah: Also, did you notice that when he was phishing the telco, he scraped PGP keyservers to get a list of their email addresses? That's not realistic, though. Nobody in real life uses PGP. Except for The Intercept, but it's painful. I'm not sure all these gallatintelco.com employees would have keys on the keyservers.
Em: It would only take one person uploading their set of public keys to get them there. Keyservers verifying permission of the owner to list the keys is relatively new, as far as I can tell.
Yael: Why does he need their public keys, though? How does this work?
Em: He didn't need the keys, he just needed the email addresses associated with them so he could phish the telco employees. He was basically IDing which email addresses were being used—rather than trying to get a list of employees and then figuring out the company’s email address format (e.g. [email protected]).
Trammell: And he was hoping that one of them used the same password on the cell site infrastructure that they used to login in response to the phishing email. The first few didn't, but eventually one of them did. Someone always does…
Micah: It looks like USA Network didn't actually generate all these PGP keys. They're not in the SKS pool.
Trammell: Elliot’s ECorp key from the 2017 season is on the key servers. Or someone like me ran a key generator to spoof the 32-bit key id and uploaded it to the server and then registered e-corp.co.uk to complete the fake. 32-bit PGP key IDs are short enough that you can find a key that matches .
Image: USA
Freddy: I don't know any company, much less a telco, that requires you to publish PGP keys online.
Micah: The Intercept.
Yael: I think also the Electronic Frontier Foundation.
Freddy: When I used to work in cybersecurity I think I was the only one with a PGP key.
Micah: I think it's much more likely that a telco wouldn't be using any email encryption. But if they did, they'd use S/MIME, which is like PGP but centrally managed and therefore popular in the corporate/government world, and simpler to use.
Yael: I feel like I got PGP for street cred to get hackers I wanted to interview to talk to me vs. actually using it.
Micah: I used PGP to help facilitate the Snowden leak. Good times.
Garage Door Hack
Yael: Let’s talk about the garage door hack.
Trammell: Based on the scripts I think Darlene was using a HackRF. In that screenshot you can see that she has logged into a Pi with the HackRF and captured the signal while the security goon was pressing "close."

Image: USA
Bank Transfer
Micah: So as far as the bank transfer goes, I think there are some pieces of the puzzle that aren't quite clear in this episode. Last episode there was a snippet of python that involved mixing cryptocurrency. So I think they must have done something like this. Once they could spy on everyone's SMS, they initiated bank transfers for everyone, to transfer their money into some other bank account. When all the Deus Group members got SMS messages, they intercepted the 2FA codes and sent them to the bank to complete the transfers.
Freddy: Yeah but even then, you can't just do a bulk transfer of billions of dollars into cryptocurrency?
Micah: On the other end, the receiving account must have automatically been hooked into a cryptocurrency exchange, immediately selling all of that money for cryptocurrency, and then, immediately mixing that cryptocurrency.
Freddy: And do what with it? Someone will notice a trillion dollars being dumped into BTC (cough cough TETHER). Also, there is a cost to buying that cryptocurrency and you couldn't get the network throughput for syncing the transfers. Syncing a blockchain is much slower compared to something like SWIFT.
Em: Cryptocurrency for this is not realistic.
Micah: Before it could get exchanged for cryptocurrency, they had to have done a SWIFT transfer to a different bank. That must have been the first step.
Freddy: I am just saying, where did the money go? The cryptocurrency stuff is like "fancy Hollywood magic."
Micah: So maybe the money is all just sitting in like, a Swiss bank account or something that they set up just for this hack, and they're slowly working on moving it into cryptocurrency
Em: It would have to be several SWIFT transfers or things would not be accepted on the other end. Moving it all into one account wouldn't help, because it would be seized and returned.
Micah: It's a separate SWIFT transfer account for each Deus Group member, but still.
Freddy: Moving that much money would have tripped all sorts of liquidity rules at the banks.
Em: Yes, and the receiving accounts would have had issues with it. Even if all translated to BTC etc., they'd have to distribute it very widely to prevent it from being returned. A well set-up bank would also have additional confirmations required for transfers that empty out accounts or are over a certain amount.
Trammell: The liquidity of any of the cryptocurrency exchanges wouldn't be able to handle any significant buy-in like that. It would be like the flash crash in reverse.
Yael: Wait, I thought BTC couldn't get returned.
Em: Anything can be seized.
Micah: Yeah, I think once they get successfully get it into BTC, the only way they could seize it is by seizing the actual wallet, e.g. the secret keys.
Em: The exchange(s) are a vulnerable point, I think. Cryptocurrency would be harder to seize than a traditional account, if no one ever did anything with it. It'd have to sit there, dead.
Micah: If Elliot and Darlene can maintain their anonymity from the financial fraud investigators, they won't have any way of knowing who to seize it from. Also, if they don't actually want the money, they can just destroy the wallet.
Trammell: If they are doing the "K Foundation" attack rather than a "Robin Hood" approach, they could also transfer the BTC to a random address (or a symbolic one) where there is no secret key.
Em: There is one thing we're overlooking in the discussion of cryptocurrency transfers:
eCoin. We don't know how eCoin worked, but it's likely that it was more integrated with Cyprus Nat'l Bank than BTC et al is with most traditional banks.
Trammell: Good point—we're hypothesizing about how eCoin might work, as compared to real cryptocurrencies. (If eCoin is even anything other than a fiat currency issues by Evil Corp).
Em: I would be amazed if the bank wasn't integrated with it. And remember, eCoin wallets aren't secure against Evil Corp. They had the ability to look in every wallet etc.
Freddy: Presumably they also stole all the money from Price/Tyrell, too. So what's to stop them from bankrupting Evil Corp?
Trammell: I'm surprised that such rich people would have only one bank account. Their funds only have FDIC insurance up to $250k.
Em: What does FDIC insurance matter when the accounts are owned by the people who own the government(s)?
Freddy: Or for off-shore bank accounts.
Trammell: A more realistic response from Whiterose would be "oh, there's more where that came from."
Em: I think that's besides the point, considering the power dynamics at play.
Trammell: Offshore, different banks, different countries, etc. Single points of failure are so very dangerous.
Em: Whiterose would have been totally humiliated, all her data and everyone else's gone, their money taken—why would they give her more? The goal wasn't to bankrupt the members of the Deus Group but to bankrupt the Deus Group. Fsociety made Whiterose and the Dark Army bleed in a way that made them no longer appear invulnerable. Who would want to work with them then? But even arguendo, Whiterose would know the funds were gone for the immediate future and that'd ruin the Congo plan.
Darlene
Micah: I like that in the video Darlene told everyone the address of the Deus Group meeting, so that protestors showed up and stalled them from leaving long enough to complete the hack
Yael: haha yeah that was a fun distraction
Trammell: F L A S H M O B
Freddy: The only thing that rich people understand is an unruly mob.
Micah: Did you also notice the billboard for the fictional NBC TV show about fsociety called SHIFT+CONTROL?

Image: USA
Yael: Good name!
Micah: And the very last scene: Whiterose is putting on makeup while it appears a SWAT team is raiding her mansion and there's firefight going on? I think Whiterose is done.
Em: It's hard to tell. Zhang is done, definitely. Whiterose might not be. Though probably, given how close we are to the end of the series.
Yael: I was surprised when Price got shot. I knew he was gonna die, but didn’t expect it like that.
Em: He did such a good job of provoking Whiterose. It was beautiful.
Yael: That was a great episode. I was glad the hack finally happened and also that Darlene had a pivotal role in it. For Dom.
Hackers Dissect ‘Mr. Robot’ Season 4 Episode 9: ‘Conflict’ syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes
Text
How Apple's iPhone has improved since its 2007 debut
yahoo
These days, we yawn and roll our eyes at each new smartphone model. The changes seem to be tiny—evolutionary. Where are the big steps forward?
Well, it may be that there aren’t many big steps left to take. Every kind of machine evolves, finally reaching an ultimate incarnation of itself. How often, for example, do you replace your refrigerator? Or your air conditioner? There just aren’t many compelling new features left to add.
Even so, we’ve come a very long way since 2007, when Apple (AAPL) released the very first iPhone. Every year, there’s another model, each faster and loaded up with more features. As we prepare for the September 12 unveiling of the 10th-anniversary iPhone, here’s a chronology of what was new with each year’s iteration.

The iPhone gets a total body makeover every few years. This year, it’s time.
iPhone (June 2007)
The very first iPhone introduced a very long list of firsts. The big one, of course, was that it was all touchscreen—no typing keys. Not just a touchscreen—a multitouch screen, with all of those touch gestures we now take for granted, like “pinch to zoom” and swiping through lists.
It also introduced visual voicemail, where your messages appear in an inbox. Its email and web browser apps were full-fledged, showing all the formatting you’d see on a desktop computer—a first for phones.
It’s also worth remembering what the first iPhone didn’t have: A front camera. A camera flash. Video recording. Cut and paste. GPS. MMS (sending photos as text messages). A memory-card slot. Voice dialing. Word-complete suggestions. A choice of carrier (it was AT&T [T] only, and really slow).
And there was no app store. You got 16 apps, and you were happy.
The base model cost $500, and packed 4 gigabytes of storage.
As I wrote in my review in The New York Times: “The iPhone is revolutionary; it’s flawed. It’s substance; it’s style. It does things no phone has ever done before; it lacks features found even on the most basic phones.”

Here it is: The Apple product that not even Apple guessed would change the world.
iPhone 3G (July 2008)
The second iPhone was intended to address the first phone’s Achilles’ heel: Its excruciatingly slow internet. This model took advantage of AT&T’s 3G network, which was at least twice as fast as the old one.
The storage options doubled, to 8 and 16 GB. A white color option debuted. And the phone gained true GPS. (The original phone simulated GPS by triangulating from known WiFi hot spots and cell towers.)

This iPhone was called 3G because it could get onto the 3G cellular networks (and NOT because it was the third-generation iPhone; it wasn’t).
Software: Focusing on only the hardware of the iPhone is missing the bigger picture: Each new phone is accompanied by a new version of its system software, which we now call iOS. In general, each new iOS version’s features also work on earlier iPhone models.
The iPhone 3G, for example, was accompanied by the debut of the App Store, a single, central catalog of add-on apps. The idea that you could download new programs directly onto the iPhone, instead of having to transfer them from a computer, was a huge breakthrough at the time.
iPhone 3GS (June 2009)
The “S,” Steve Jobs said, stood for “speed.” This phone was faster in every way. Its camera got bumped up to three megapixels, and gained a long list of features: auto-focus, tap-to-focus, exposure lock, auto white balance, auto macro shots, “rule of thirds” grid lines, and a 5x digital zoom. A new magnetometer permitted the creation of the Compass app.

The S in “3GS” stood for speed.
Software: Video recording! And voice control of music playback and dialing.
iPhone 4 (June 2010)
The comfortable rounded plastic back disappeared in this redesigned model, which had crisp edges and hardened glass front and back panels—plus the first “Retina” screen (much higher resolution). A front-facing camera appeared on this model, plus, for the first time, an LED flash.
Apple also added a second microphone, at the top, for noise cancellation during calls, and a gyroscope, which can precisely calculate how you’re turning the phone in space (handy for games).
This was the first iPhone that could run on the CDMA cellular network, the one used by Verizon (VZ) and Sprint (S). Once Apple’s early exclusive contract with AT&T ended in 2011, the iPhone 4 became the first model offered by Verizon and other carriers.

No more rounded back in the iPhone 4.
Software: iOS 4 introduced FaceTime video conferencing (over WiFi only) and limited multitasking, including an app switcher.
iPhone 4S (October 2011)
This model introduced Siri, the voice assistant that paved the way for Microsoft’s (MSFT) Cortana, Google (GOOG, GOOGL) Assistant, Amazon (AMZN) Echo, and so on. The 4S was, of course, faster, and its camera received its usually resolution bump (to 8 megapixels, good for 1080p hi-def videos).

The iPhone 4s—starring Siri.
Software: iOS 5 was a big one. It introduced iMessages, the Notification Center, Reminders, built-in Twitter (TWTR), iCloud, and the ability to let nearby computers get online via tethering (Personal Hotspot).
iPhone 5 (September 2012)
The iPhone 5 had a thinner body and taller screen; compatibility with much faster LTE cellular data networks; and a faster, better camera, capable of snapping stills while recording video.
With this phone, Apple eliminated the 30-pin connector that it had used for charging and syncing all iPhones and iPads to date—and replaced it with the tiny Lightning connector. Millions of people had to buy and fuss with adapters.

The iPhone 5 introduced the Lightning connector for charging.
Software: iOS 6 introduced panorama mode for the Camera app, more Siri commands, one-tap responses to incoming texts and calls (like, “Driving—I’ll call you later”). Apple also replaced Google’s fantastic pre-installed Google Maps app with a shockingly incomplete Apple app. Its guidance was so poor, Apple CEO Tim Cook wound up apologizing for it and suggesting that people use Google Maps instead.
iPhone 5s (September 2013)
Apple’s fingerprint sensor, cleverly embedded in the Home button, let you unlock the phone without a password for the first time. As usual, the camera got better and the processor got faster—its A7 was the first 64-bit chip ever used in a phone. Apple replaced its time-honored, coin-shaped iPhone earbuds with the blobbier AirPods earbuds.
(A budget model, the iPhone 5C, came out at the same time, in a choice of five plastic colors. It was otherwise essentially identical to 2012’s iPhone 5.)

The iPhone 5s, starring the Touch ID fingerprint reader.
Software: iOS 7 was a huge software release. It introduced a massive and controversial redesign. Its sparse look eliminated “skeuomorphic” design elements, in which on-screen things depict real-world materials (lined yellow paper for Notes, leather binding for Calendar, wooden shelves for iBooks).
iOS 7 also came loaded with new features: AirDrop made it simple to shoot pictures, notes, and contacts among iPhones. Control Center is the panel that slides up from the bottom of the screen to offer commonly used settings. In the Camera app: slow-motion video, zooming while recording, photo filters, and 10-frames-a-second bursts.
iPhone 6 (September 2014)
With this model, Apple followed Samsung’s lead—and went for bigger screens. There were now, for the first time, two iPhones in the same line: the iPhone 6 and the larger 6 Plus. Both had faster chips and Apple Pay (wireless payments at special cash-register terminals). The 6 family gained a barometer to detect altitude changes (?!), and upgraded wireless components that permitted WiFi calling.
The upgraded cameras offered slow-mo video at 240 frames a second (quarter-speed), phase-detection autofocus (faster and more accurate), and optical image stabilization on the 6 Plus. The front-facing camera got better low-light capability, burst mode, and HDR (high dynamic range) ability.

The iPhone 6 dramatically increased the iPhone’s screen size—and body size
Software: In iOS 8, Apple finally added a row of three next-word guesses above the keyboard, to save typing. The Continuity feature permitted interaction between the phone and a Mac, like calling and texting from the Mac, or copying on one device and pasting on the other. Family Sharing allows up to six family members to share stuff they’ve bought from Apple (music, videos, apps, etc.).
The Camera app gained a self timer and a time-lapse mode, iCloud Drive (Apple’s version of Dropbox) debuted. Eventually, in iOS 8.4, Apple Music came along—its subscription music plan.
iPhone 6S and SE (September 2015)
In addition to the usual speed and camera-resolution enhancements (12 megapixels, 4K video), the 6S and 6S Plus introduced what Apple calls 3D Touch: a pressure-sensitive screen. You can press harder on an app to see a menu of common commands, or peek into links or lists without actually leaving the screen you’re on.
(The iPhone SE packed most of the same features of the 6S into a much smaller body—the traditional iPhone size—to the delight of the small-handed.)

The iPhone 6s and 6s Plus introduced a pressure-sensitive screen.
Software: The iOS 9 update introduced a front-facing “flash” that works by overcranking the front-facing screen by 3X. It also debuted Live Photos, which are three-second video clips that you can capture with every photo.
iPhone 7 (September 2016)
Most people will probably remember the iPhone 7 and 7 Plus primarily as the phones that killed off the headphone jack. But these models also gained waterproofing (up to 30 minutes under a meter of water), a larger battery, stabilized camera even on the smaller phone, better low-light photos, an array of four LED flashes on the back for greater brightness, stereo speakers, and a Home button that doesn’t actually move, but instead just simulates a click using a vibration motor.
On the iPhone 7 Plus, Apple installed two lenses: one wide-angle, one a 2X zoom. This is true, optical zoom, not the cruddy digital zoom on most previous phones.

The iPhone 7 and 7 Plus had no headphone jack. They’re shown here with what Apple hopes you’ll use instead: the AirPods.
Software: iOS 10 introduced a huge range of small tweaks, and a couple of big ones. First, there has been a colossal revamp of Messages, Apple’s text-messaging app, adding a wide range of visual treats, animations, and effects to dress up your message. Second, iOS 10 requires fewer steps to unlock the phone—for example, to check the latest alerts or fire up the camera.
iPhone 8 and 7S? (September 2017)
Nobody knows for sure what Apple will unveil in the new iPhones on September 12. But the rumor millers seem pretty confident about a few things:
A massive redesign. No more black panels above and below the screen. Instead, a gorgeous OLED screen will extend to all four edges of the phone.
No more Home button. You’ll have to get back to the Home screen, and perform other functions, using new swiping gestures on the screen. (Or maybe there’ll be an on-screen Home button.)
Face ID. You’ll be able to unlock the phone by looking at it.
Pad-based charging. As on the Samsung Galaxy, instead of plugging in a cable, you’ll have the option of setting it down on a pad) to charge. (That’s why front and back will be glass.)
AR features. Augmented reality means seeing graphics overlaid on the camera’s view of the world around you: arrows that show which way to walk to get to the nearest subway stop, for example, or info boxes that identify the prices of apartments in nearby buildings.
Nosebleed price. The number people are kicking around is $1,000. However, there’s also some intel that a less expensive iPhone model or two will be released simultaneously, without the OLED screen.
Software: We already know what iOS 11 will bring, because Apple’s told us! It will be a lot of nips and tucks, like auto-Do Not Disturb when you’re driving; a more real-sounding voice for Siri; screen recording; more compact photo and video formats to save space; and person-to-person payments within the Messages app, like Venmo.
Here’s my complete writeup of iOS 11.
See you on September 12!
We’ll be at Apple’s unveiling show at 10 a.m. Pacific time on September 12, live-blogging the event and posting a complete set of articles, photos, and videos about what’s new.
We’re pretty sure you won’t want to miss it!
More from David Pogue:
Gulliver’s Gate is a $40 million world of miniatures in Times Square
The 5 best new features of this week’s YouTube redesign
Samsung’s Bixby voice assistant is ambitious, powerful, and half-baked
Is through-the-air charging a hoax?
Electrify your existing bike in 2 minutes with these ingenious wheels
Marty Cooper, inventor of the cellphone: The next step is implantables
The David Pogue Review: Windows 10 Creators Update
Now I get it: Bitcoin
David Pogue’s search for the world’s best air-travel app
The little-known iPhone feature that lets blind people see with their fingers
David Pogue, tech columnist for Yahoo Finance, welcomes nontoxic comments in the comments section below. On the web, he’s davidpogue.com. On Twitter, he’s @pogue. On email, he’s [email protected]. You can read all his articles here, or you can sign up to get his columns by email.
#tech#Pogue#$MSFT#$VZ#$S#$T#_lmsid:a077000000DAfMuAAL#David Pogue#$twtr#$GOOGL#_revsp:usnews.finance.yahoo.com#_uuid:789adc9c-d9dc-3009-a163-0a661c21d05b#$GOOG#$AAPL#_author:David Pogue#$AMZN
6 notes
·
View notes
Text
The Scroll subscription service is an ingenious web technology hack
Welcome back to Processor, a newsletter about computers and also sometimes other things. You are probably expecting me to spend several paragraphs making fun of Google for creating yet another messaging product, as The Information reported yesterday. Not gonna do it: it’s enterprise-focused and from what I can tell about Google’s cloud business right now, a haphazard message app strategy is the least of their worries. Instead, the thing that blew my mind yesterday was Scroll, a new $5 per month subscription service that gives you a bunch of websites without ads. I kept on experiencing successive waves of small revelations when I thought about it. I’ll disclose now that Vox Media (and therefore The Verge) are partners, but I had no idea this service existed until it was announced yesterday. First: although I don’t have any specific reason to distrust Scroll, this still feels like a data privacy time bomb. Scroll won’t sell my data, but what if the company that snaps up Scroll does someday? There’s a prominent button for deleting your data, at least. Scroll’s privacy policy is refreshingly readable and candid about what it gathers and what it does and doesn’t share — including being honest about sharing information with governments when required to by law. It also notes that your data could go along with a sale of the company itself. Basically I suggest you find the “delete your information” button and remember where it is. Second: Scroll’s entire method of stopping ads is an absolutely ingenious repurposing of third-party cookies. You log into Scroll, it sets a cookie, and then the websites you visit see that special cookie and don’t serve you ads. It’s not even ad-blocking, they just don’t get served. It is actually quite elegant, but if you take a second to think through the chain of communications and deals that are required to make it that elegant, it seems like a hellacious hack. Then again, as Nilay Patel said to me today, isn’t most web technology a hellacious hack? There are a few more details — Safari in particular is stricter than other browsers and so it requires an extension. Brave will also need some extra effort to work with Scroll. (Scroll has a snarky footnote about them.) Third: it’s a much easier solution for websites to get paid than asking each of them to roll their own subscription. It tracks where you visit and automatically divvies payment up between those partner sites. I could (and eventually will) quibble about the percentage Scroll is taking: $1.50 out of $5, or thirty percent. As an independent startup, I’m not going to begrudge Scroll its revenue, and it likely needs a bigger cut to stay in business than Apple or Google do on their App Stores. If the company hits scale, though, I’d like to hope that it will find a way to reduce that cut. Fourth: hang on let’s think about that hellacious hack again! Although you have to constantly have Scroll email you a “magic link” and then ensure you open it in the right browser, it means that you are getting your paid-for ad-free experience in the app of your choosing. Unlike Apple News (disclosure: another Vox Media partner), you aren’t forced into a not-especially-great app. You don’t get a link that seems like it goes to a web page but actually just goes to Apple’s app. You can also use it on any device you own, not just Apple’s products. Also unlike Apple News, this subscription isn’t really a subscription. For publications that put articles behind paywalls, Scroll won’t get you in. On the whole, though, I much prefer Scroll’s system to Apple News. It works better with the existing web and the existing apps we all use to navigate it. A subscription system that turns off ads, pays publishers, and doesn’t lock me into any particular app while also doing a pretty good job of keeping my login active? Seems good to me. Still, I’m not quite going to go quite so far as to endorse Scroll (and not just because Vox Media is a partner). Deciding to sign up is between you, your level of trust in Scroll’s privacy policies, your ad-blocking conscience, whether you care about the current list of partner publications, and the cost. Fifth: Scroll puts a white bar at the bottom of every webpage it’s active on, ostensibly so you have the benefit of getting share links and an audio reader mode. No thank you times a thousand, Scroll. However, one benefit of using web browsers instead of Apple News is that web browsers are relatively open platforms and so you can use them to alter the web pages you visit (at least on the desktop — on mobile things are still often locked down). So, for example, I have a little script that I cobbled together after a day of Googling that makes it easier for me to format the links in this newsletter by automatically changing the web page I store them on, Pinboard.in. My favorite method is an extension called Tampermonkey. I wrote a little script for it that hides Scroll’s annoying bar. Other than some preliminary settings, it’s literally one line. It should work in Chromium-based browsers. Here it is, offered with zero support and absolutely no guarantees that it’s any good at all. Bonus sixth revelation: Tampermonkey offers a Google Drive-based sync, and since Microsoft’s new Edge browser runs on Chromium, my script auto-synced from Chrome on a Mac to Edge on Windows and Just Worked. The Internet! Sometimes it’ll surprise you.
Tech contends with the coronavirus
└ Apple is limiting China travel and has closed one retail store due to coronavirus outbreak └ iPhone maker Foxconn says coronavirus outbreak won’t affect production └ United Airlines suspends some China flights after coronavirus outbreak └ Facebook, Razer, and LG are restricting employee travel to China amid coronavirus outbreak
Big reads from The Verge
└ To contain disease outbreaks, health officials rely on people’s trust You’ve probably formed an opinion on how anti-vaxxers have affected public health (the right opinion is that it has been for the worse). But similarly online misinformation can rush to fill the void of faster-moving health crises. Nicole Wetsman looks at the intersection of health, internet censorship, and trust: If one crisis is handled poorly, there will likely be less trust during the next one. Not only that, but the spread of misinformation can have real-time impacts on what people believe. That erosion can weaken public health response. └ How Amazon escapes liability for the riskiest products on its site The outcome of some of these cases could determine the fate of Amazon’s marketplace. Is it like an eBay or a Craigslist, with Amazon as a middleman, or is Amazon the retailer? People tend to think of Amazon as the latter but Amazon thinks of itself as the former. Great report here from Colin Lecher. According to court records viewed by The Verge, Amazon has faced more than 60 federal lawsuits over product liability in the past decade. The suits are a grim catalog of disaster: some allege that hoverboards purchased through the company burned down properties. A vape pen purchased through the company exploded in a pocket, according to another suit, leaving a 17-year-old with severe burns. └ BoJack Horseman’s finale signals the end of a Netflix era Julia Alexander has an excellent, focused history of Netflix as seen through the lens of its original programming decisions.
More news from The Verge
└ Everything we think we know about Samsung’s next foldable phone └ Everything we think we know about the Samsung Galaxy S20 └ Samsung’s Galaxy Z Flip fully revealed in leaked images The minimalist screen on the outside is an interesting choice. I will be very, very curious to see if this “ultra-thin glass” is actually more durable than plastic. We’ve all sort of been assuming it will be, but it’s no sure thing. └ Moto G8 and G8 Power leak with hole-punch displays and midrange specs If battery life and a big screen are your top needs in a smartphone, it’s worth keeping an eye on these. └ Filmic DoubleTake lets you record from two iPhone cameras at the same time Apple hyped the heck out of this app, now it’s finally here and Becca Farsace has run it through some paces: With the Discreet mode, I was able to film from the Wide and Ultra-Wide, both at 1080p, at the same time. The H.264 .mov exports are really clean and take very little time to transfer to the camera roll. Pair a clean export with the iPhone 11 Pro’s excellent lens calibration, and you have a perfect punch in from a single phone. └ UK defies US and refuses to ban Huawei from 5G networks └ Google Translate will transcribe translations in real time on Android One step closer to the Babel fish. └ Neil Young says the MacBook Pro has ‘Fisher-Price’ audio quality You might think this headline is overstating how fiery this Vergecast interview is. But I promise you it is understating it. └ Pokémon Home cloud storage service will launch in February for $3 a month So if Nintendo creates a pokémon and then you catch that pokémon and then you put that pokémon back in a Nintendo server farm is that like throwing the pokémon back? Have you really caught anything? Are you just renting pokémon? Vox Media has affiliate partnerships. These do not influence editorial content, though Vox Media may earn commissions for products purchased via affiliate links. For more information, see our ethics policy. Read More Read the full article
0 notes
Text
The 360Fly 4K was the follow-up to the company’s debut 360-degree camera, which really came out of nowhere to become arguably the best of its kind of on the market.
As well as its striking design, featuring a single lens, the 360Fly also boasted one of the best apps of any of its rivals, with simple-to-use features and direct sharing options.
With the 360Fly 4K the company aims to build on that early success with a follow-up that looks and feels the same, with big boosts to resolution and internal specifications.
That said, the name is something of a misnomer. While it’s called the 360Fly 4K, it’s actual resolution at 2880 x 2880 @ 30FPS Max isn’t true 4K.
But the 360Fly 4K is really like no other action camera on the market. Most 360 cameras on the market either come in the form of a 2001-esque monolith (such as the Ricoh Theta cameras) or a sphere (think the Samsung Gear or Insta360 cameras).
The 360Fly 4K is something else entirely. While somewhat of a spherical shape, it is make up of repeating patterns of geometric shapes that form its textured exterior, with a hard-wearing, rubberised finish, making it easy to hold.
On top of this design is a large – the biggest I’ve seen on a 360 camera – lens that offers a 240-degree field of view. And while the geometric shapes are quite striking, it’s really this enormous lens that grabs your eye.
The 360Fly 4K’s lens boasts eight elements with an aperture of f/2.5, a 0.88mm focal length and a minimum focal distance of 30cm.
Below the massive lens on the side of the body is a triangular button keeping in line with the motif of the body design. This is your power button and single direct control – everything else is done via the very excellent app. But more on that later.
Elsewhere on the 360Fly 4K’s body you’ll find a small microphone hole. And on the base of the camera is a standard tripod mount, along with sensors for charging the camera.
And that’s basically it! The camera has no other exterior features or controls. The whole unit is sealed. There’s no interchangeable battery, memory card slot or USB port. You charge it in a small dock that is provided, and you retrieve your media via the app, which is available for both iOS and Android devices.
The dock employs a simple USB cable to connect to your computer. On top it has a ring of small contacts that rest against the base of the 360Fly and charge it. If you want to transfer files to your computer, you can also do this via the dock.
It’s also worth noting that the 360Fly 4K’s sealed design means there’s no need for an additional housing. The camera is water resistant up to 50m, however a small rubber plug does need to be inserted into the microphone hole. But what this means is that the 360Fly 4K can be taken underwater for short periods, such as snorkelling at the beach.
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
360Fly 4K Review: Build Quality & Handling
When I took the 360Fly 4K out of its nifty box I saw the design and was really taken aback by how clever it was. It’s somewhere between a lime and a satsuma in size, and the attention to detail is very clear. The textured grip just fits perfectly in your hand.
I was a little worried about that big, exposed lens beforehand, but once you hold it in your hand and get a feel for its robustness those feelings will quickly dissipate.
I’m pleased to say, too, that despite direct exposure to mud, grit and water, the 360Fly 4K’s build quality held up admirably, even when caked in mud. It’s a 360 camera, yet also a true action camera.
It’s also worth noting that 360Fly provides a handy tutorial on its website on how to clean the camera.
As I mentioned above, because there are no controls on the 360Fly 4K apart from the power button, all its settings and recording options are controlled via the app.
Once you turn on the camera and load the app on your phone, the app makes an instant connection and loads a live view stream.
!function(){for(var a="//link.monetizer101.com",b=[{lib:"widget/custom-2.0.3/js/load.min.js",method:function(){return MONETIZER101.init(a)}},{lib:"widget/search-2.0.3/js/load.min.js",method:function(){return MONETIZER101SEARCH.init(a)}}],c=b.length;c--;){var d=b[c],e=document.createElement("script");e.type="text/javascript",e.async=!0,e.src=a+"/"+d.lib,e.onload=d.method;var f=document.getElementsByTagName("script")[0];f.parentNode.insertBefore(e,f)}}();
What’s great about the 360Fly 4K’s live view stream in the app is, again the attention to detail. Many apps on 360 cameras offer you a static view of one angle of your scene. In live view, the 360Fly 4K allows you to swipe all the way through and over and all around your scene to get a truer sense of what you’re capturing. You can either do this by swiping with your finger or moving your phone around.
As well as shoot and play back your own content, the 360Fly app lets you view videos from the wider 360Fly community, which is quite fun and inspiring, I found.
Finally, on the base of the 360Fly 4K – in the middle of all the charging contact points – is the camera’s tripod mount. This is a proprietary socket design and special mounts can be clicked in rather easily.
Also inside the box are a number of self-adhesive mounts you can use to stick the 360Fly 4K directly onto things you’re likely to use it with in conjunction, such as a surfboard or bicycle helmet.
You’ll also find a GoPro mount adapter, which really expands the 360Fly 4K’s capabilities.
360Fly 4K Review: Performance
To get started with the 360Fly 4K, simply hold down the triangular power button for a couple seconds. You’ll then feel it vibrate and turn blue, and now the camera is on. Then load the app, and your live view appears in seconds.
Unlike some 360 cameras I’ve used, everything… just works. The app and camera communicate and work in conjunction. I never once had a communication problem.
Like other 360 cameras, the 360Fly may boast a big number in terms of resolution, but this is coming from a small sensor and stretched across 360 degrees. So temper your expectations. But this is true of all 360 cameras, and the image quality of this nascent technology is only getting better, much like the first DSLRs more than 10 years ago.
Unlike other 360 cameras, though, the 360Fly 4K boasts a unique design with its lens pointing up. This means the sharpest part of your footage will be directly above the camera. This works in some instances, I found, but by and large my main focal points in most scenes were situated around me, not above.
WordPress doesn’t support 360 immersive images, but you can still get a sense of what I mean from the above image in its still panoramic format. You can also click here to view an album of images in Google Photos, where you can experience the images in true 360 degrees.
The footage around the edge of the frame was considerably softer and lacks much of the sharper detail the camera captures at the centre of the frame, due to its design. So it’s worth bearing this in mind.
But nevertheless, I was very pleased with the image quality from the 360Fly 4K (all those caveats above considered). Colours were rich and natural, and better than any other 360 camera I’ve used, save for the Ricoh Theta S.
However, if you’re considering the 360Fly 4K for its action camera chops, I’d say that the GoPro Hero5 blows it out of the water in terms of colour and tone and overall image quality.
But in bright conditions the 360Fly 4K handles skies pretty well. And taking it into the shade in mixed lighting I noticed a bit of fringing and distortion around the areas of contrast, but it also picks up nice detail in the shadow areas.
Now, you wouldn’t be able to blow this detail up to any significant size, but then these images aren’t designed to be used that way. VR is the future, and cameras like the 360Fly 4K are our first stepping stones down that path.
What I loved about the 360Fly 4K is how easy it is to use. It’s app is by far the best 360 camera companion app and offers a nice degree of control. Images are crisp enough and punchy, and I can swipe my way through my scenes on my phone immediately after I shoot them.
Playback of the footage through the mobile and desktop app is a real thrill and gives you an immersive experience that just isn’t possible with other cameras.
Downloading them to your computer is as simple as plugging the charging dock’s male USB end into your computer and importing your footage via the free 360Fly Director software. You can then convert them to Facebook and Youtube-ready videos and share them directly. It’s so simple.
360Fly 4K Review: Verdict
In short: the 360Fly 4K is very easy to get to grips with, and if you’ve never shot 360 images before you’ll find the whole process very natural and intuitive with this camera.
You can tell so much thought and attention to detail has been put into the user experience, which is honestly the best I’ve had with any 360 camera. Never once did the app crash or the camera fail to make a connection. All of the controls I wanted and needed were there, and even some I didn’t know I needed.
The size and weight of the 360Fly 4K also makes it incredibly versatile. I’ve been carrying it and my Manfrotto PIXI mini tripod everywhere for the past month, and I can find room for it in any bag, regardless of how full I’ve stuffed the bag with other gear. You can also fit the 360Fly 4K in the pocket of your skinny jeans. Not that I wear skinny jeans; I’m just saying that you could.
Its unique design does come with a cost: the sharpest parts of your scenes are directly above the camera when most of your key focal points will more often be situated around it.
Nevertheless, in my opinion the 360Fly 4K is the best consumer 360 camera on the market. Or very closely tied with the Ricoh Theta S. The S might pip it in image quality, but the 360Fly 4K’s app is as close to perfect as you’ll get, it’s probably the best combination of this nascent technology in a single package that you’ll find.
https://www.camerajabber.com/vuze-camera-review/
https://www.camerajabber.com/best-360-camera-shooting-wider-world-around/
Save
Save
Save
360Fly 4K Review The 360Fly 4K was the follow-up to the company’s debut 360-degree camera, which really came out of nowhere to become arguably the best of its kind of on the market.
0 notes
Text
Microsoft Surface pro and Macbook Pro
New Post has been published on https://netmaddy.com/microsoft-surface-pro-and-macbook-pro/
Microsoft Surface pro and Macbook Pro
Imperfect, Heavy, Light, Powerful, and Excellent.
Just shy of one year ago, I transitioned from a Macbook Pro and iPad combo to a Microsoft Surface Pro 128GB. In light of this week’s announcement of Surface Pro 3 and my acquisition of a Surface Pro 2, I think it’s time to reflect on what that experience was like. Like most folks, I was a little skeptical about the idea of combining a laptop and tablet into a single unit. Would it be too heavy? Would the performance be too low? Would the battery life be awful? And what about the new Windows 8 OS that’s been the subject of so much teeth-gnashing? I’ll try to answer all these questions and more as succinctly as possible. Hit the jump and let’s get into the question: what’s it like to live with Microsoft’s vision for computing in the future?
1. The Operating System, starring Windows 8/8.1:
Windows 8.1 Update 1 had a good head start with Windows 8, as I started using it during the first publicly available betas about 9 months before launch, dual booting on my Macbook Pro. That experience gave me plenty of time to figure out how to navigate the OS well before launch, so I didn’t have the struggle that a lot of people did. Of course, it probably helps that I just naturally enjoy exploring and discovering new things. The early Windows 8 experience did have its struggles, though. I’d become accustomed to the iPad and even to my Windows Phone 7 device, both of which had lots of apps available in their stores. Windows 8’s store was notoriously barren by comparison, and that led to some early frustration when trying to use Surface Pro as just a tablet. Too many apps and features were missing to make for a satisfying experience.
Nevertheless, the device’s ability to handle legacy Windows desktop apps with aplomb kept me satisfied enough to continue, and the app store dilemma became less important by the day. If there’s one thing Windows really needs to fix, though, is its way of presenting the desktop. The desktop is still wrapped in the trappings of an archaic system whose time has passed, and it’s time for Microsoft to update it to a more modern presentation that has fonts big enough to read on high DPI screens and large enough to operate with a finger.
With 8.1 and the new 8.1 Spring Update (really? We couldn’t just call it 8.2?), virtually all my complaints about Windows 8 evaporated. While some dislike the new aesthetic, I’ve personally found myself loving the flat colors, active tiles and removal of extraneous effects. My sincere hope is that as Windows evolves it gets even flatter and the metro aesthetic becomes more pervasive.
Suggestion: Use a Microsoft account, and use OneDrive! I can’t stress these enough. If you’re using Windows 8–and on a Surface Pro, you will be–you shouldn’t create an old-fashioned local account. Doing so cuts you off from some of Windows 8’s best features. Among these is the ability to have almost your entire PC configuration, right down to tile sizes, locations and apps installed, backed up to your OneDrive account in the event you either need to restore your PC or you sign into a different Windows 8.1 PC. Best, though, is that with OneDrive you get 7GB storage for free, which, while not enough to cover, say, your music and photos collection, is probably plenty to ensure your critical documents are all safely backed up within moments of you making any change. It’s easy to learn to save to your OneDrive folder, and once you’ve become accustomed to having that safety net you’ll wonder how you ever lived without it.
2. The Hardware: Build Quality, Heft, and Capability.
Surface Pro Docking Station
I used to lug around a 2010 Macbook Pro 13.3″, which weighed 4.5 pounds, and an iPad 1, which weighed 1.5 pounds for a total of 6 pounds. So when I say that the 2.5 pound total of the Surface Pro and Type Cover was a big weight off my back, I’m really not kidding. The sacrifice was that I had a smaller screen, but the gain was a far more powerful processor and far superior screen resolution and pixel density. The build quality is exceptional: there is literally zero flex to this device, its magnesium shell is hard and sturdy enough to withstand probably more abuse than you should feel comfortable making your PC go through. As a tablet, it’s half a pound heavier than that original iPad was, but as a laptop it has a huge advantage over anything Apple offers. But you probably wonder what I use my Surface Pro for?
Workload
I’ve spent most of the past year as a film school student at UCLA, which means that a lot of my workload involves editing and transcoding video, compositing after effects compositions, transferring footage across different media and so on. I use Adobe Premiere for most of these tasks, and my Surface Pro has handled them all with grace. I’ve had no problems editing and rendering 1080p video in real-time. And as you’d expect from a Windows machine with a full size USB port, working with external hard drives and optical drives is a breeze. Suffice to say, I also do the basics including working in Microsoft Office, writing in Final Draft, checking email, browsing the web, yada yada. Overall, I’ve had no complaints save one: early on, my first Surface Pro had some serious problems with the Marvell Avastar wifi chip and had to be exchanged, a problem that’s not entirely uncommon with this device. More on that later.
Webcams
Let’s be honest: the webcams on this device suck. They’re flat-out terrible, and there’s no getting around that fact. They’re fine for basic Skype video calls, but that’s pretty much it. If you really need to record video, use something else. Anything else.
Stylus
I frequently take notes in OneNote MX (that’s the metro version), especially lately. Like most students, I have tended over the past few years to type my notes, but recent studies show that students who take notes by hand tend to do better on tests. Well, I’m all for evidence based research, so I took this to heart, but I’m also lazy, which means I don’t want to type things after I’ve written them down. Enter Surface Pro’s stylus and voila: I can hand write my notes and have them in a digital format all at the same time. Hell yes. I find that the stylus, despite its cheap plastic feel, works well as a digital inking device. Some complain about the lack of a dock for the stylus, but honestly, I’ve no issues with that. I’ve been using it for a year and have yet to lose the thing.
Art Related Work
Last note on usability: my fiancée, artist Kelley Frisby, got her Surface Pro on launch day precisely because of the integrated Wacom digitizer with 1,024 levels of pressure sensitivity. From the outset the usage here was contentious because Surface Pro shipped without a pressure sensitive driver that Photoshop could understand. However, once that driver materialized, she took to using the stylus all the time. And when we learned about Manga Studio Pro from artist Jonathan Case’s website, things really went off the hook as she found it to be far superior to photoshop for creating hand drawn illustrations. That she can have her Surface Pro on her lap with pressure sensitivity while she draws, and her keyboard handy for using keyboard shortcuts, is a huge benefit that other tablets simply don’t offer. Truly, if you’re an artist who draws and paints digitally, Surface Pro is the device for you. Nothing else combines so many hardware capabilities and broad software availability.
3. Battery Life
Surface Pro Kickstand
This is the one serious issue that has dogged the Surface Pro since its original launch, despite the fact that it was never as bad as people claimed or the fact that Surface Pro 2 completely mitigated the issue (and by all reports, Surface Pro 3 does even better). Early claims were that Surface Pro got about 3.5 hours of battery life. And under certain circumstances, that’s true: watching 1080p videos with the brightness up while downloading stuff in the background will, like any other device, eat battery life much more than average usage will. But that’s only part of the test, isn’t it? Under normal usage, which I’ll define as web, email and word processing, Surface Pro 1 will get 5 hours battery life right out of the box. With some mild tweaks to the power profile, which I’ve detailed in one of our most popular posts, it’s entirely possible to get 6-7 hours of battery life. My best time was just over 8 hours total, but with a caveat: I was working with the wifi turned off, writing in Word, in a low light situation where I could comfortably turn down the screen brightness to minimum. Most people I know get in the range of 5-6 hours.
Why I Switched
Let’s be as clear as possible here: the Surface Pro is not a flawless device, but then, neither is anything else. My chief complaints are that the desktop in Windows 8.x needs a Modern UI revamp, and I wish the screen were a little bigger. I hope to upgrade to a Surface Pro 3 at some point in the future for that very reason, though my suspicion is that the artist community, such as my own wonderful Kelley Frisby, will hesitate to upgrade as a result of the new device’s possibly inferior N-Trig digitizer.
So that leaves the big question: why did I switch? That’s a complicated question. First, I was never sold on Mac OSX, but when Apple’s Bootcamp 5 update removed my ability to install Windows 8 as a dual-boot OS choice, claiming it wasn’t compatible with the computer I’d been using for 2.5 years (and at that, running Windows 8 on for 9 months), the final straw broke. This was the third time Apple’d created problems for my devices, following the iOS 5 update that slowed my iPad to a crawl and the iOS 4 update that made my iPhone 3G all but unusable.
The prospect of having a tablet and laptop all in a single device was also very appealing to me. Yes, there are compromises: it’s a little heavier than a tablet and a little smaller than a typical laptop, but the overall effect is a net positive, and I’m happy to say that my year with Surface Pro has me convinced: Microsoft’s vision of a world where tablets are just slim, light, touch-friendly PC’s is the right one. That we now see even desktop all-in-ones becoming large tablets (seriously, have you seen the Dell Venue Pro 18″ tablets? Crazy!) and touch slowly but surely spreading even to budget level laptops, is a good sign the convergence Microsoft predicted when it announced the original Surface Pro is really happening.
Problems I had & Solutions Microsoft offered
Surface by Microsoft
I mentioned the problem my original Surface Pro had with its wifi chip awhile ago, but there’s more to that story. In fact, just a couple of weeks ago my Surface Pro once again began having problems with the wifi chip, and no update, driver replacement, or even a system reset helped. Eventually the device started blue screening repeatedly, so I took it in to see what Microsoft could do for me. To my complete surprise, they handed me a brand new Surface Pro 2 and even let me pay the difference to upgrade it to the 256GB/8GB model, which I eagerly did. The new device is basically all the great stuff about Surface Pro 1, distilled into a purer form. Same weight, size and shape, slightly better screen (though I honestly can’t tell the difference, for what it’s worth), and the Type Cover 2 is a fantastic little keyboard that does its job with aplomb. I’m very happy indeed, and more than glad I bought the extended warranty.
Value Proposition
I’ve seen a lot of folks argue that the Surface Pro series is too expensive, and I can understand why. $999 before you even add the keyboard seems like a pretty tough pill to swallow, especially for a tablet when you live in a world of $499 iPads and $199 Kindle Fires. But I think it’s worth remembering what you get when you buy into the Surface Pro system:
1. You get an ultrabook that can run just about any legacy Windows app you can throw at it. It has excellent RAM options (4-8GB) and storage options (64-512GB), a full-sized USB port and both wired and wireless external monitor support (the latter via Miracast). In Apple land, this costs you $900 minimum.
2. You get a tablet that can do anything an iPad or Android tablet can do, plus more, with the only drawback being sheer numbers of apps. Even that is changing as the Windows Store approaches 200,000 and will soon merge with the Windows Phone store to boot. And because it’s Windows, you also get the perk of individual user accounts right out of the box. In Apple land, this is another $400+
3. A digital drawing/inking solution. Whether you just take notes or you do fine art, the Surface Pro has you covered. You don’t get this in Apple land at all. You instead buy a USB tablet that does not have a screen for $100+, or you buy a Cintiq to connect to your Macbook for $1,000.
Long story short: at first glance, yes, it looks like Surface Pro/2 is expensive, but you get a tremendous amount of value for your money.
Last Words
Would I recommend the Surface Pro or Pro 2? Absolutely, especially if you’re an artist or someone who’s just sick and tired of lugging around multiple devices. We live in a world where our computing hardware is not just powerful, but can do its job with surprisingly little energy or heat. There’s just no reason to carry two devices in your bag in addition to the smartphone in your pocket. If I could have a wish granted, it’d be for Microsoft to add an extra USB 3.0 port, thunderbolt, and move from an mSATA to a PCIe SSD. Mind you, it doesn’t exactly need those items, but the hardware nerd in me would be really happy to have them.
As for Surface Pro 3, well, I’d love to review it, and more importantly I’d love to put it in the hands of our classically trained illustrator so she can put it through its paces and render a verdict on its usefulness as an artist’s digital tablet, but so far haven’t had any luck getting time with the new device. But hey, if Microsoft would like to let us borrow one, we could probably work something out!
Oh, almost forgot: do buy Microsoft’s extended warranty for Surface Pro, no matter what version you buy. It’ll really pay off if anything ever goes wacky with your device, and it even offers accidental damage protection, which is usually pretty expensive if it’s offered at all.
0 notes
Text
Smart devices, stupid mistakes — how to make sure you’re really wiping all that sensitive data
(BigStock Photo)
The past few years have been big for the Internet of Things (IoT), and the future of the connected device industry looks even brighter. Research firm IHS forecasts that the IoT market will grow to 30.7 billion active devices by 2020 and 75.4 billion by 2025. As we continue to witness this tangible shift toward IoT devices, previously futuristic ideas are coming to life all around us and changing the way we experience the world. And while these digital luxuries provide new levels of convenience, the security concerns of connected devices have been well documented. But, what happens when you decide to sell, re-gift, or otherwise dispose of these IoT products? How can you be sure you’re not leaving traces of personal data for the next owner to access.
In this article, I’m going to outline various tips for securely removing your personal information and data, and general security best practices for connected devices. So, let’s start with some of the more obvious scenarios and work our way through other IoT technology.
Computers, Tablets, and Phones Apple Photo)
You’ve decided it’s time to call it a day on your laptop, tablet or smartphone, in favor of an upgrade. What now? First, be sure to backup all your data before firing up that Craigslist ad and making the switch. Cloud accounts make it easy to access your files across a range of devices, and online services for tablets and smartphones will often automatically sync personal data. You should already be saving contingency versions of your important files on a regular basis (for a variety of reasons), but be sure you have backup copies of anything you want to transfer over before getting rid of that old device.
Next, wipe all the data and potentially sensitive settings from your computer’s hard drive, or your tablet or smartphone. There are two things you should consider to securely wipe your devices. First, your files and contact lists aren’t the only things to worry about. Your device likely has many settings that connect to cloud services or might expose things about you to potential new owners. You need to be sure to reset all your device’s settings, too. Second, just “deleting” something from computer storage may not totally remove it. Without going into the specifics, when you delete files or format your hard drive, your computer (or mobile phone) just “forgets” how to find those files; it doesn’t necessarily overwrite them. There are several forensic and recovery tools that can find and restore that data if it hasn’t been overwritten. Securely wiping data may involve overwriting files at least a few times.
The process for securely wiping a device depends on the device itself. Luckily, many phones and tablets are easier to wipe, since some mobile operating systems (OSes) have features built in to handle it for you. For instance, the settings menu on iOS devices allows you to go to General => Reset => Erase All Content and Settings to get rid of all your sensitive data. This feature will either destroy the encryption keys your phone used to secure your data, making that data totally inaccessible, or older iOS versions overwrite that data a few times. It also removes the phone from your iCloud account and Find My Phone. In short, it’s a simple one-button method to security wipe iOS devices.
Android devices can be a bit harder to wipe since there are many variants of this OS, all of which may act differently. Most versions of Android should have a “Factory Data Reset” option. However, in the past researchers found that this was not a secure wipe. Since it didn’t overwrite data on the device, attackers with the right software could recover that data. If you want to really destroy the data on your Android device, it’s best you encrypt it first. Once you encrypt the device and then factory reset, new owners won’t have the keys necessary to read your data.
Finally, for good old-fashioned laptops and desktops, the key is to make sure you overwrite data on your hard drive with a special secure wipe tool. There are many tools out there, including free Windows options like Eraser, that help you make sure data you delete is gone forever. Also note, you may have to follow a different process to securely wipe SSD drives, but there are many instruction guides online.
Although wiping your personal computer, tablet or smartphone is a fairly obvious tip, it’s incredibly important that you take the time to do it properly. Failing to completely reset your old devices can leave your personal data at risk of being discovered by the next user.
Smart Cars
The automotive industry is becoming more advanced and modern cars now come off the assembly line with Bluetooth hands-free calling, GPS navigation systems, even Wi-Fi. The convenience of having easy access to your phone book, locational data, and favorite apps while behind the wheel is almost too good to turn down. The problem is that as our cars become increasingly sophisticated, they store more of our personal data, just like a PC or smartphone would.
(BigStock Photo).
One step you might forget in all the excitement of selling your old car is removing all that personal information. In fact, I just purchased a used car and found several names and phone numbers archived from the previous owner’s contacts. When the time comes to sell your connected car, be sure to clear all login, contact, and personal data from the settings. If you forget this step, you could be gift wrapping access to your social media accounts, contact list, home address and more for the car’s new owner. Some dealers may be starting to take this into account themselves, but in my case, I did find the previous owners’ stored Bluetooth devices.
As an aside, leaving data behind in rental cars’ Bluetooth systems is another common mistake (as if the rental car process wasn’t enough of a hassle by itself). Whether you’re on a business trip or taking a vacation, if you sync your address book and other data to a rental vehicle, be sure to clear saved numbers, calls and other information before returning it.
By the way, we’ve been talking about this problem in the perspective of the seller avoiding leaving sensitive information for the buyer. However, this issue can also pose risk to buyers, so they can benefit from resetting smart cars. too. Recently, an IBM X-force researcher found that he could still access the car he sold in the car’s app. While the car’s local settings had been cleared, the manufacturer’s cloud had not been. This meant the old owner could still unlock doors, and gain access to the new owner’s car.
Gaming Consoles Xbox One S. (Xbox Photo)
Let’s say you can’t wait to trade in that old Xbox 360 for an Xbox One. Through the years, gaming consoles have become one of the hardest types of devices to attack. This is largely due to increasingly hardened security through hardware and software updates designed to prevent piracy. But don’t be fooled. Although they might be some of the most secure IoT devices on the market, the fact that they’ve evolved to become your one-stop-shop for entertainment means gaming products now save valuable data to their hard drives and SD cards – just like personal computers.
So when it comes time to sell your old console, the main issues are deactivating your online accounts (PlayStation Network, Xbox Live, etc.), and deleting the data on the console. The account deactivation is a basic step, but one many forget. In one case, I bought a used PS3 that still had the previous owner’s PlayStation Network (PSN) account intact. If I hadn’t deactivated the account myself, I could’ve continued buying games with his credentials. You can easily find instructions for deactivating different consoles’ accounts online.
The console will also have menu options to reset them, or delete data. Again, like computers, sometimes a delete isn’t really a complete delete. However, modern consoles, like the new PlayStation offer both a quick and full delete. Be sure to use the full option for a secure wipe.
It’s understandable to be excited to play ‘Halo Wars’ on Xbox One, but make sure you don’t forget to securely wipe your old console before selling it. Mistakes like that can give the next owner access to your personal images, videos, credit card information and even browsing history. That could be game over.
Smart Home Devices
If you’re moving out of your home, consider what connected devices – and data – you might be leaving behind. Some home purchase agreements include caveats that allow the new homeowner to inherit IoT products installed by the previous owner. The procedure for removing your personal data from smart home products like the Nest Thermostat is relatively simple but can be easily forgotten through the moving process. Nest and other smart home products enable you to remove the device from your online account and reset the product, itself, to factory defaults. This should effectively cleanse the device of your information, leaving it ready and waiting for the new user to setup their own account.
Amazon Echo and Google Nest are two examples of smart home devices. (Image via Nest)
Forgetting to wipe the connected home devices you leave behind can leave remnants of your personal information for the home’s new owner to find. Chances are, they’re not secretly a black hat with malicious intent – but unprotected data is still a chilling proposition nonetheless.
Nest products – and other IoT devices in general – have been scrutinized over privacy concerns. While they’re designed to analyze and learn your preferences, they also accumulate usage data and other information that gets sent back to a service provider. But, that’s a whole other ball of wax.
Smart Printers, Copiers, and Other Office Devices (HP Photo)
Smart office devices are exposed to some pretty critical information. Whether it’s a smart copier or digital printer, we’ve heard concerns for years that these devices can save information they encounter. So, when you’re getting rid of that home office printer/copier, how can you be sure that you’re not tossing out years of information for someone else to recover? First, find out if your office device has built-in storage. If it doesn’t, then there’s a good chance none of your information has been saved to the machine. If your printer or copier does include a cache of local data, you can often remove the storage devices, and wipe it in the same way you wipe normal computer storage.
It’s worth noting that some businesses do elect to always remove storage devices from any computing device they sell or recycle. Besides securely erasing this data yourself, you can also give these storage devices to data destruction services, which may even go as far as physically destroying the storage device.
Some higher-end printers include email functionality that allows them to send files via email directly from the printer controls. In order to protect your email address and any others that might be stored on a smart printer, be sure to wipe this data before selling or disposing of it. Most printer manufacturers should have menu options to do so.
Wearables (FitBit Photo)
Smart watches and other wearables like fitness and health trackers have, and will continue to become more engrained in our everyday lives. As a matter of fact, research firm IDC predicts that by 2019, more than 89 million smart wearable units will ship worldwide. That’s a lot of FitBits, Pebbles, Microsoft Bands and Apple Watches!
A recent study by HP Fortify found that many smart watches contain significant vulnerabilities related to privacy, insecure firmware, authentication, and encryption. The study examined ten popular smart watches and found that 90 percent of the time data flowing to and from the watches was easily intercepted.
That said, the bulk of this information storage is somewhere else (in the cloud). While attackers might intercept it in transit, these small, typically resource-light devices don’t tend to store much data locally. If you’re planning to sell or give away any kind of connected wearable device, you do need to make sure it’s factory reset, so that it can no longer connect to its associated cloud account. You probably won’t have to go to much trouble to wipe any local data on these wearables (that said, this will differ from device to device).
General Security Tips for IoT Devices
By their very nature, IoT devices are quite diverse, and thus expose us to a variety of attack profiles. The devices I’m most concerned with today are those that have quickly embedded traditionally known operating systems into non-traditional computing devices without taking security into account. For example, think of a refrigerator, DVR or webcam that’s running a Linux operating system. Since attackers are already familiar with Linux, hacking these types of devices is easy for them. Worse yet, the manufacturers making these devices seem to be years behind in security hardening and development. Furthermore, since these devices are basically just computers, they often have storage full of sensitive information.
The issue of IoT device security has gained a great deal of attention due to the widespread effects of recent Mirai botnet attacks. My hope is that we’ll see more connected device manufacturers incorporate security into their products – from research and development to completion – in the near future.
As far as what you can do to protect your data on an IoT device you sell, I’ll leave you with three important strategies:
Make sure your data is securely wiped from the device. If you’re using a type of IoT device that has a hard drive or local storage, it probably has some data that you need to delete before reselling. However, you need to remember that with computers, not all deletes wipe equally. Do a little research to see if your device’s “factory reset” is a secure wipe or not. If it isn’t, you might have to find alternate means to really kill your data.
Don’t forget the device’s settings. When we think of protecting our data, we normally worry about erasing the sensitive files we might have on a device. However, we can’t forget that many of the settings in an IoT device link to our private data, too. These devices are connected to our cloud and social network accounts, they have a memory of all the access points we’ve connected to, they know your email address, and much more. Make sure you also erase all the device’s settings and deactivate the device from any cloud accounts it might be linked to.
Don’t forget the settings in the cloud, too. Learn from what the X-force researcher discovered about his smart car. Even if you wipe all a device’s local settings, sometimes manufacturers might design features that allow cloud accounts to always have access to the device, unless the account itself gets deactivated and reset. If you can manage a device with a mobile app, be sure that you don’t still have access to the device after factory resetting it.
from DIYS http://ift.tt/2kXyWoj
0 notes
Text
Smart devices, stupid mistakes — how to make sure you’re really wiping all that sensitive data
(BigStock Photo)
The past few years have been big for the Internet of Things (IoT), and the future of the connected device industry looks even brighter. Research firm IHS forecasts that the IoT market will grow to 30.7 billion active devices by 2020 and 75.4 billion by 2025. As we continue to witness this tangible shift toward IoT devices, previously futuristic ideas are coming to life all around us and changing the way we experience the world. And while these digital luxuries provide new levels of convenience, the security concerns of connected devices have been well documented. But, what happens when you decide to sell, re-gift, or otherwise dispose of these IoT products? How can you be sure you’re not leaving traces of personal data for the next owner to access.
In this article, I’m going to outline various tips for securely removing your personal information and data, and general security best practices for connected devices. So, let’s start with some of the more obvious scenarios and work our way through other IoT technology.
Computers, Tablets, and Phones Apple Photo)
You’ve decided it’s time to call it a day on your laptop, tablet or smartphone, in favor of an upgrade. What now? First, be sure to backup all your data before firing up that Craigslist ad and making the switch. Cloud accounts make it easy to access your files across a range of devices, and online services for tablets and smartphones will often automatically sync personal data. You should already be saving contingency versions of your important files on a regular basis (for a variety of reasons), but be sure you have backup copies of anything you want to transfer over before getting rid of that old device.
Next, wipe all the data and potentially sensitive settings from your computer’s hard drive, or your tablet or smartphone. There are two things you should consider to securely wipe your devices. First, your files and contact lists aren’t the only things to worry about. Your device likely has many settings that connect to cloud services or might expose things about you to potential new owners. You need to be sure to reset all your device’s settings, too. Second, just “deleting” something from computer storage may not totally remove it. Without going into the specifics, when you delete files or format your hard drive, your computer (or mobile phone) just “forgets” how to find those files; it doesn’t necessarily overwrite them. There are several forensic and recovery tools that can find and restore that data if it hasn’t been overwritten. Securely wiping data may involve overwriting files at least a few times.
The process for securely wiping a device depends on the device itself. Luckily, many phones and tablets are easier to wipe, since some mobile operating systems (OSes) have features built in to handle it for you. For instance, the settings menu on iOS devices allows you to go to General => Reset => Erase All Content and Settings to get rid of all your sensitive data. This feature will either destroy the encryption keys your phone used to secure your data, making that data totally inaccessible, or older iOS versions overwrite that data a few times. It also removes the phone from your iCloud account and Find My Phone. In short, it’s a simple one-button method to security wipe iOS devices.
Android devices can be a bit harder to wipe since there are many variants of this OS, all of which may act differently. Most versions of Android should have a “Factory Data Reset” option. However, in the past researchers found that this was not a secure wipe. Since it didn’t overwrite data on the device, attackers with the right software could recover that data. If you want to really destroy the data on your Android device, it’s best you encrypt it first. Once you encrypt the device and then factory reset, new owners won’t have the keys necessary to read your data.
Finally, for good old-fashioned laptops and desktops, the key is to make sure you overwrite data on your hard drive with a special secure wipe tool. There are many tools out there, including free Windows options like Eraser, that help you make sure data you delete is gone forever. Also note, you may have to follow a different process to securely wipe SSD drives, but there are many instruction guides online.
Although wiping your personal computer, tablet or smartphone is a fairly obvious tip, it’s incredibly important that you take the time to do it properly. Failing to completely reset your old devices can leave your personal data at risk of being discovered by the next user.
Smart Cars
The automotive industry is becoming more advanced and modern cars now come off the assembly line with Bluetooth hands-free calling, GPS navigation systems, even Wi-Fi. The convenience of having easy access to your phone book, locational data, and favorite apps while behind the wheel is almost too good to turn down. The problem is that as our cars become increasingly sophisticated, they store more of our personal data, just like a PC or smartphone would.
(BigStock Photo).
One step you might forget in all the excitement of selling your old car is removing all that personal information. In fact, I just purchased a used car and found several names and phone numbers archived from the previous owner’s contacts. When the time comes to sell your connected car, be sure to clear all login, contact, and personal data from the settings. If you forget this step, you could be gift wrapping access to your social media accounts, contact list, home address and more for the car’s new owner. Some dealers may be starting to take this into account themselves, but in my case, I did find the previous owners’ stored Bluetooth devices.
As an aside, leaving data behind in rental cars’ Bluetooth systems is another common mistake (as if the rental car process wasn’t enough of a hassle by itself). Whether you’re on a business trip or taking a vacation, if you sync your address book and other data to a rental vehicle, be sure to clear saved numbers, calls and other information before returning it.
By the way, we’ve been talking about this problem in the perspective of the seller avoiding leaving sensitive information for the buyer. However, this issue can also pose risk to buyers, so they can benefit from resetting smart cars. too. Recently, an IBM X-force researcher found that he could still access the car he sold in the car’s app. While the car’s local settings had been cleared, the manufacturer’s cloud had not been. This meant the old owner could still unlock doors, and gain access to the new owner’s car.
Gaming Consoles Xbox One S. (Xbox Photo)
Let’s say you can’t wait to trade in that old Xbox 360 for an Xbox One. Through the years, gaming consoles have become one of the hardest types of devices to attack. This is largely due to increasingly hardened security through hardware and software updates designed to prevent piracy. But don’t be fooled. Although they might be some of the most secure IoT devices on the market, the fact that they’ve evolved to become your one-stop-shop for entertainment means gaming products now save valuable data to their hard drives and SD cards – just like personal computers.
So when it comes time to sell your old console, the main issues are deactivating your online accounts (PlayStation Network, Xbox Live, etc.), and deleting the data on the console. The account deactivation is a basic step, but one many forget. In one case, I bought a used PS3 that still had the previous owner’s PlayStation Network (PSN) account intact. If I hadn’t deactivated the account myself, I could’ve continued buying games with his credentials. You can easily find instructions for deactivating different consoles’ accounts online.
The console will also have menu options to reset them, or delete data. Again, like computers, sometimes a delete isn’t really a complete delete. However, modern consoles, like the new PlayStation offer both a quick and full delete. Be sure to use the full option for a secure wipe.
It’s understandable to be excited to play ‘Halo Wars’ on Xbox One, but make sure you don’t forget to securely wipe your old console before selling it. Mistakes like that can give the next owner access to your personal images, videos, credit card information and even browsing history. That could be game over.
Smart Home Devices
If you’re moving out of your home, consider what connected devices – and data – you might be leaving behind. Some home purchase agreements include caveats that allow the new homeowner to inherit IoT products installed by the previous owner. The procedure for removing your personal data from smart home products like the Nest Thermostat is relatively simple but can be easily forgotten through the moving process. Nest and other smart home products enable you to remove the device from your online account and reset the product, itself, to factory defaults. This should effectively cleanse the device of your information, leaving it ready and waiting for the new user to setup their own account.
Amazon Echo and Google Nest are two examples of smart home devices. (Image via Nest)
Forgetting to wipe the connected home devices you leave behind can leave remnants of your personal information for the home’s new owner to find. Chances are, they’re not secretly a black hat with malicious intent – but unprotected data is still a chilling proposition nonetheless.
Nest products – and other IoT devices in general – have been scrutinized over privacy concerns. While they’re designed to analyze and learn your preferences, they also accumulate usage data and other information that gets sent back to a service provider. But, that’s a whole other ball of wax.
Smart Printers, Copiers, and Other Office Devices (HP Photo)
Smart office devices are exposed to some pretty critical information. Whether it’s a smart copier or digital printer, we’ve heard concerns for years that these devices can save information they encounter. So, when you’re getting rid of that home office printer/copier, how can you be sure that you’re not tossing out years of information for someone else to recover? First, find out if your office device has built-in storage. If it doesn’t, then there’s a good chance none of your information has been saved to the machine. If your printer or copier does include a cache of local data, you can often remove the storage devices, and wipe it in the same way you wipe normal computer storage.
It’s worth noting that some businesses do elect to always remove storage devices from any computing device they sell or recycle. Besides securely erasing this data yourself, you can also give these storage devices to data destruction services, which may even go as far as physically destroying the storage device.
Some higher-end printers include email functionality that allows them to send files via email directly from the printer controls. In order to protect your email address and any others that might be stored on a smart printer, be sure to wipe this data before selling or disposing of it. Most printer manufacturers should have menu options to do so.
Wearables (FitBit Photo)
Smart watches and other wearables like fitness and health trackers have, and will continue to become more engrained in our everyday lives. As a matter of fact, research firm IDC predicts that by 2019, more than 89 million smart wearable units will ship worldwide. That’s a lot of FitBits, Pebbles, Microsoft Bands and Apple Watches!
A recent study by HP Fortify found that many smart watches contain significant vulnerabilities related to privacy, insecure firmware, authentication, and encryption. The study examined ten popular smart watches and found that 90 percent of the time data flowing to and from the watches was easily intercepted.
That said, the bulk of this information storage is somewhere else (in the cloud). While attackers might intercept it in transit, these small, typically resource-light devices don’t tend to store much data locally. If you’re planning to sell or give away any kind of connected wearable device, you do need to make sure it’s factory reset, so that it can no longer connect to its associated cloud account. You probably won’t have to go to much trouble to wipe any local data on these wearables (that said, this will differ from device to device).
General Security Tips for IoT Devices
By their very nature, IoT devices are quite diverse, and thus expose us to a variety of attack profiles. The devices I’m most concerned with today are those that have quickly embedded traditionally known operating systems into non-traditional computing devices without taking security into account. For example, think of a refrigerator, DVR or webcam that’s running a Linux operating system. Since attackers are already familiar with Linux, hacking these types of devices is easy for them. Worse yet, the manufacturers making these devices seem to be years behind in security hardening and development. Furthermore, since these devices are basically just computers, they often have storage full of sensitive information.
The issue of IoT device security has gained a great deal of attention due to the widespread effects of recent Mirai botnet attacks. My hope is that we’ll see more connected device manufacturers incorporate security into their products – from research and development to completion – in the near future.
As far as what you can do to protect your data on an IoT device you sell, I’ll leave you with three important strategies:
Make sure your data is securely wiped from the device. If you’re using a type of IoT device that has a hard drive or local storage, it probably has some data that you need to delete before reselling. However, you need to remember that with computers, not all deletes wipe equally. Do a little research to see if your device’s “factory reset” is a secure wipe or not. If it isn’t, you might have to find alternate means to really kill your data.
Don’t forget the device’s settings. When we think of protecting our data, we normally worry about erasing the sensitive files we might have on a device. However, we can’t forget that many of the settings in an IoT device link to our private data, too. These devices are connected to our cloud and social network accounts, they have a memory of all the access points we’ve connected to, they know your email address, and much more. Make sure you also erase all the device’s settings and deactivate the device from any cloud accounts it might be linked to.
Don’t forget the settings in the cloud, too. Learn from what the X-force researcher discovered about his smart car. Even if you wipe all a device’s local settings, sometimes manufacturers might design features that allow cloud accounts to always have access to the device, unless the account itself gets deactivated and reset. If you can manage a device with a mobile app, be sure that you don’t still have access to the device after factory resetting it.
from DIYS http://ift.tt/2kXyWoj
0 notes
Text
Smart devices, stupid mistakes — how to make sure you’re really wiping all that sensitive data
(BigStock Photo)
The past few years have been big for the Internet of Things (IoT), and the future of the connected device industry looks even brighter. Research firm IHS forecasts that the IoT market will grow to 30.7 billion active devices by 2020 and 75.4 billion by 2025. As we continue to witness this tangible shift toward IoT devices, previously futuristic ideas are coming to life all around us and changing the way we experience the world. And while these digital luxuries provide new levels of convenience, the security concerns of connected devices have been well documented. But, what happens when you decide to sell, re-gift, or otherwise dispose of these IoT products? How can you be sure you’re not leaving traces of personal data for the next owner to access.
In this article, I’m going to outline various tips for securely removing your personal information and data, and general security best practices for connected devices. So, let’s start with some of the more obvious scenarios and work our way through other IoT technology.
Computers, Tablets, and Phones Apple Photo)
You’ve decided it’s time to call it a day on your laptop, tablet or smartphone, in favor of an upgrade. What now? First, be sure to backup all your data before firing up that Craigslist ad and making the switch. Cloud accounts make it easy to access your files across a range of devices, and online services for tablets and smartphones will often automatically sync personal data. You should already be saving contingency versions of your important files on a regular basis (for a variety of reasons), but be sure you have backup copies of anything you want to transfer over before getting rid of that old device.
Next, wipe all the data and potentially sensitive settings from your computer’s hard drive, or your tablet or smartphone. There are two things you should consider to securely wipe your devices. First, your files and contact lists aren’t the only things to worry about. Your device likely has many settings that connect to cloud services or might expose things about you to potential new owners. You need to be sure to reset all your device’s settings, too. Second, just “deleting” something from computer storage may not totally remove it. Without going into the specifics, when you delete files or format your hard drive, your computer (or mobile phone) just “forgets” how to find those files; it doesn’t necessarily overwrite them. There are several forensic and recovery tools that can find and restore that data if it hasn’t been overwritten. Securely wiping data may involve overwriting files at least a few times.
The process for securely wiping a device depends on the device itself. Luckily, many phones and tablets are easier to wipe, since some mobile operating systems (OSes) have features built in to handle it for you. For instance, the settings menu on iOS devices allows you to go to General => Reset => Erase All Content and Settings to get rid of all your sensitive data. This feature will either destroy the encryption keys your phone used to secure your data, making that data totally inaccessible, or older iOS versions overwrite that data a few times. It also removes the phone from your iCloud account and Find My Phone. In short, it’s a simple one-button method to security wipe iOS devices.
Android devices can be a bit harder to wipe since there are many variants of this OS, all of which may act differently. Most versions of Android should have a “Factory Data Reset” option. However, in the past researchers found that this was not a secure wipe. Since it didn’t overwrite data on the device, attackers with the right software could recover that data. If you want to really destroy the data on your Android device, it’s best you encrypt it first. Once you encrypt the device and then factory reset, new owners won’t have the keys necessary to read your data.
Finally, for good old-fashioned laptops and desktops, the key is to make sure you overwrite data on your hard drive with a special secure wipe tool. There are many tools out there, including free Windows options like Eraser, that help you make sure data you delete is gone forever. Also note, you may have to follow a different process to securely wipe SSD drives, but there are many instruction guides online.
Although wiping your personal computer, tablet or smartphone is a fairly obvious tip, it’s incredibly important that you take the time to do it properly. Failing to completely reset your old devices can leave your personal data at risk of being discovered by the next user.
Smart Cars
The automotive industry is becoming more advanced and modern cars now come off the assembly line with Bluetooth hands-free calling, GPS navigation systems, even Wi-Fi. The convenience of having easy access to your phone book, locational data, and favorite apps while behind the wheel is almost too good to turn down. The problem is that as our cars become increasingly sophisticated, they store more of our personal data, just like a PC or smartphone would.
(BigStock Photo).
One step you might forget in all the excitement of selling your old car is removing all that personal information. In fact, I just purchased a used car and found several names and phone numbers archived from the previous owner’s contacts. When the time comes to sell your connected car, be sure to clear all login, contact, and personal data from the settings. If you forget this step, you could be gift wrapping access to your social media accounts, contact list, home address and more for the car’s new owner. Some dealers may be starting to take this into account themselves, but in my case, I did find the previous owners’ stored Bluetooth devices.
As an aside, leaving data behind in rental cars’ Bluetooth systems is another common mistake (as if the rental car process wasn’t enough of a hassle by itself). Whether you’re on a business trip or taking a vacation, if you sync your address book and other data to a rental vehicle, be sure to clear saved numbers, calls and other information before returning it.
By the way, we’ve been talking about this problem in the perspective of the seller avoiding leaving sensitive information for the buyer. However, this issue can also pose risk to buyers, so they can benefit from resetting smart cars. too. Recently, an IBM X-force researcher found that he could still access the car he sold in the car’s app. While the car’s local settings had been cleared, the manufacturer’s cloud had not been. This meant the old owner could still unlock doors, and gain access to the new owner’s car.
Gaming Consoles Xbox One S. (Xbox Photo)
Let’s say you can’t wait to trade in that old Xbox 360 for an Xbox One. Through the years, gaming consoles have become one of the hardest types of devices to attack. This is largely due to increasingly hardened security through hardware and software updates designed to prevent piracy. But don’t be fooled. Although they might be some of the most secure IoT devices on the market, the fact that they’ve evolved to become your one-stop-shop for entertainment means gaming products now save valuable data to their hard drives and SD cards – just like personal computers.
So when it comes time to sell your old console, the main issues are deactivating your online accounts (PlayStation Network, Xbox Live, etc.), and deleting the data on the console. The account deactivation is a basic step, but one many forget. In one case, I bought a used PS3 that still had the previous owner’s PlayStation Network (PSN) account intact. If I hadn’t deactivated the account myself, I could’ve continued buying games with his credentials. You can easily find instructions for deactivating different consoles’ accounts online.
The console will also have menu options to reset them, or delete data. Again, like computers, sometimes a delete isn’t really a complete delete. However, modern consoles, like the new PlayStation offer both a quick and full delete. Be sure to use the full option for a secure wipe.
It’s understandable to be excited to play ‘Halo Wars’ on Xbox One, but make sure you don’t forget to securely wipe your old console before selling it. Mistakes like that can give the next owner access to your personal images, videos, credit card information and even browsing history. That could be game over.
Smart Home Devices
If you’re moving out of your home, consider what connected devices – and data – you might be leaving behind. Some home purchase agreements include caveats that allow the new homeowner to inherit IoT products installed by the previous owner. The procedure for removing your personal data from smart home products like the Nest Thermostat is relatively simple but can be easily forgotten through the moving process. Nest and other smart home products enable you to remove the device from your online account and reset the product, itself, to factory defaults. This should effectively cleanse the device of your information, leaving it ready and waiting for the new user to setup their own account.
Amazon Echo and Google Nest are two examples of smart home devices. (Image via Nest)
Forgetting to wipe the connected home devices you leave behind can leave remnants of your personal information for the home’s new owner to find. Chances are, they’re not secretly a black hat with malicious intent – but unprotected data is still a chilling proposition nonetheless.
Nest products – and other IoT devices in general – have been scrutinized over privacy concerns. While they’re designed to analyze and learn your preferences, they also accumulate usage data and other information that gets sent back to a service provider. But, that’s a whole other ball of wax.
Smart Printers, Copiers, and Other Office Devices (HP Photo)
Smart office devices are exposed to some pretty critical information. Whether it’s a smart copier or digital printer, we’ve heard concerns for years that these devices can save information they encounter. So, when you’re getting rid of that home office printer/copier, how can you be sure that you’re not tossing out years of information for someone else to recover? First, find out if your office device has built-in storage. If it doesn’t, then there’s a good chance none of your information has been saved to the machine. If your printer or copier does include a cache of local data, you can often remove the storage devices, and wipe it in the same way you wipe normal computer storage.
It’s worth noting that some businesses do elect to always remove storage devices from any computing device they sell or recycle. Besides securely erasing this data yourself, you can also give these storage devices to data destruction services, which may even go as far as physically destroying the storage device.
Some higher-end printers include email functionality that allows them to send files via email directly from the printer controls. In order to protect your email address and any others that might be stored on a smart printer, be sure to wipe this data before selling or disposing of it. Most printer manufacturers should have menu options to do so.
Wearables (FitBit Photo)
Smart watches and other wearables like fitness and health trackers have, and will continue to become more engrained in our everyday lives. As a matter of fact, research firm IDC predicts that by 2019, more than 89 million smart wearable units will ship worldwide. That’s a lot of FitBits, Pebbles, Microsoft Bands and Apple Watches!
A recent study by HP Fortify found that many smart watches contain significant vulnerabilities related to privacy, insecure firmware, authentication, and encryption. The study examined ten popular smart watches and found that 90 percent of the time data flowing to and from the watches was easily intercepted.
That said, the bulk of this information storage is somewhere else (in the cloud). While attackers might intercept it in transit, these small, typically resource-light devices don’t tend to store much data locally. If you’re planning to sell or give away any kind of connected wearable device, you do need to make sure it’s factory reset, so that it can no longer connect to its associated cloud account. You probably won’t have to go to much trouble to wipe any local data on these wearables (that said, this will differ from device to device).
General Security Tips for IoT Devices
By their very nature, IoT devices are quite diverse, and thus expose us to a variety of attack profiles. The devices I’m most concerned with today are those that have quickly embedded traditionally known operating systems into non-traditional computing devices without taking security into account. For example, think of a refrigerator, DVR or webcam that’s running a Linux operating system. Since attackers are already familiar with Linux, hacking these types of devices is easy for them. Worse yet, the manufacturers making these devices seem to be years behind in security hardening and development. Furthermore, since these devices are basically just computers, they often have storage full of sensitive information.
The issue of IoT device security has gained a great deal of attention due to the widespread effects of recent Mirai botnet attacks. My hope is that we’ll see more connected device manufacturers incorporate security into their products – from research and development to completion – in the near future.
As far as what you can do to protect your data on an IoT device you sell, I’ll leave you with three important strategies:
Make sure your data is securely wiped from the device. If you’re using a type of IoT device that has a hard drive or local storage, it probably has some data that you need to delete before reselling. However, you need to remember that with computers, not all deletes wipe equally. Do a little research to see if your device’s “factory reset” is a secure wipe or not. If it isn’t, you might have to find alternate means to really kill your data.
Don’t forget the device’s settings. When we think of protecting our data, we normally worry about erasing the sensitive files we might have on a device. However, we can’t forget that many of the settings in an IoT device link to our private data, too. These devices are connected to our cloud and social network accounts, they have a memory of all the access points we’ve connected to, they know your email address, and much more. Make sure you also erase all the device’s settings and deactivate the device from any cloud accounts it might be linked to.
Don’t forget the settings in the cloud, too. Learn from what the X-force researcher discovered about his smart car. Even if you wipe all a device’s local settings, sometimes manufacturers might design features that allow cloud accounts to always have access to the device, unless the account itself gets deactivated and reset. If you can manage a device with a mobile app, be sure that you don’t still have access to the device after factory resetting it.
from DIYS http://ift.tt/2kXyWoj
0 notes
Text
Amazon.com : BlackBerry PlayBook 32GB 7″ Multi-Touch Tablet PC with 1 GHz Dual-Core Processor, 5MP Camera and Secondary 3MP Camera, Video, GPS, Wi-Fi and Bluetooth – Black : Tablet Computers : Computers & Accessories
Sharengay Trang Tin Tức Độc Đáo VIDEO Amazon.com : BlackBerry PlayBook 32GB 7″ Multi-Touch Tablet PC with 1 GHz Dual-Core Processor, 5MP Camera and Secondary 3MP Camera, Video, GPS, Wi-Fi and Bluetooth – Black : Tablet Computers : Computers & Accessories

Top reviews
Top reviews from the United States
Bạn đang xem: Amazon.com : BlackBerry PlayBook 32GB 7″ Multi-Touch Tablet PC with 1 GHz Dual-Core Processor, 5MP Camera and Secondary 3MP Camera, Video, GPS, Wi-Fi and Bluetooth – Black : Tablet Computers : Computers & Accessories
There was a problem filtering reviews right now. Please try again later.
Reviewed in the United States on April 19, 2017
Size: 32 GBVerified Purchase
A BlackBerry tablet seems like an odd purchase in 2017, but I did my homework and knew I wasn’t getting an iPad Air. I was getting this tablet for work – Spreadsheets, Word Docs and hopefully use the Bible app. The price was manageable and I figured that even if it turns out to be obsolete, I can still use it as a music player in our kitchen or something. Well, I was pleasantly surprised by this little tablet. The OS is brilliant. It’s such a joy and ease for multi-tasking. I was able to get my spreadsheets on it immediately and use it to check my messages and keep my calendar. The Bible app works flawlessly. Yes, the tablet is a little slow, but it’s a 2011 tablet, it’s to be expected. Yes, it doesn’t have a huge cache of apps to choose from, but the apps available are quality. I even found some fun games with great graphics. My music is fully loaded and the speakers are fantastic. I even tried taking a few pics and the quality is impressive! It’s not great for social media. Facebook is functional but not great. Instagram and Netflix simply won’t work on this tablet. You can go the Instagram website and at least view pictures, but that’s all. I did manage to get YouTube working with an browser I downloaded from BlackBerry World called “Frost”. Just go to the YouTube web page and it works great. It let me sign in, but I had to re-sign in every time I opened it. But when the videos play on YouTube, you can leave the app and the video keeps playing – very cool! I also have a BlackBerry Passport phone and it lets me sync with it and my Playbook to text and send BBMs. If you’re willing to put in a little work and do some research, you can get some current Android apps working on this thing. I have Evernote, Kindle, and even a version of Google Maps working. Again, do not expect this tablet to be everything the current tablets are, but if you want to spend very little and get a functional tablet that can serve a few purposes well, give this a look. The best things about this Tablet is the multi-tasking feature, the Messaging inbox, the speakers, the quality of the screen and the price. The negatives are a lack of apps and the general slowness. Hope this helps someone!
Reviewed in the United States on July 8, 2015
Verified Purchase
The Blackberry Playbook Tablet isn’t for those hardcore iPad and Android people. In fact, I would not recommend you buy this tablet if that is the kind of person you are. This tablet is almost like a beginning step into the world of tablets. You get plenty of memory on the tablet for a price lower than any other competitor offer, but there is good reason for that. For one, this tablet is older than these fancy tablets that we see nowadays, so the specs aren’t as hot. There is Bluetooth, but if you have an iPhone or Android or just anything that isn’t a Blackberry, your phone is not going to interact with this tablet other than giving it data. It CAN’T support file sharing like pictures or music through Bluetooth, but you can plug it into your computer to upload files onto it. Apps are not exact the strong suite of the Playbook either. It has a more limited version of the Blackberry World for the Blackberry phones, so don’t expect all the top of the line games and apps to be on here, through there are a few here and there. I would suggest this tablet to people who want to do some basic browsing on the web, check facebook, and just relax while on the go. I wouldn’t say it is a bad tablet for getting your work done, but I don’t think this is the tablet you should be relying on.
Reviewed in the United States on March 1, 2012
Size: 16 GBVerified Purchase
I love this thing!
—– (update) —— Tip to improve WiFi reception
The 2.4 Ghz WiFi antenna is in the upper left hand corner in landscape orientation. Wrapping your hand around this corner to hold Playbook, as I like to do, reduces WiFi signal strength a lot (a bar or two, factor of x100 or 20 dbm), which can be the difference between getting online or not when traveling. A simple trick to get good WiFi reception while still holding Playbook with the left hand is just flip the Playbook over so the ‘Blackberry’ logo is on top. This puts the most commonly used 2.4 Ghz WiFi antenna on the right.
Check out the ‘SANOXY Bluethooth Keyboard for iPad’. It’s a very inexpensive bluetooth keyboard that works fine with Playbook. ————— 7″ screen size is fine, sharp as a tack (viewed with reading lens of bifocals), bright and colorful, sound good, screen responsive to touch. Swipes easy to learn.
On browser homepage On my desktop browsers I have all my frequently visited links in a single custom .html file that I set as my homepage. To me a custom .html homepage is essential, it makes bouncing around the web fast and easy. I first tried copying my custom .html file into the ‘Document’ folder, but found it was not visible under ‘Document’ icon, but later going backdoor I got it installed as the browser homepage. Here’s the procedure:
Type into browser: file:///accounts/1000/shared (note 3 ///)
This brings up a simple file manager that allows you to see what files are in memory and even to launch them. In the Document folder was my custom html homepage file, which I had earlier copied over via USB. Tapping the filename loaded it into the browser, and holding my finger on it allowed me to copy the filename (via the copy box). Finally going into the browser settings I was able to paste the filename into the homepage window. Now every time I start the browser up comes my custom homepage.
Another neat trick is to have alternate start links for the browser on your home screen. This is done by clicking the star+ button and selecting add to home screen. For example I have a icon that will start the browser at the New York Times and another for local radar.
On media files MP3 files can simply be copied over and will play. Video files are more difficult. I have a library of captured .flv files and captured TV shows in .ts format, some of which I would like to put on the Playbook to view when out of WiFi range. However, neither of these file formats is supported directly on the Playbook. In principle there are two options: copy over the file and use an app that does on the fly conversion, or two, preconvert the file to a supported format (like .avi or .mp4). I experimented with both.
Xem thêm: #j2team_ask
There are several apps that claim to allow you to play .flv files on Playbook. I bought one for $0.99 and while it played .flv files, it was not clean (position slider did not work). I tried a couple of converter programs, which you run on your desktop before downloading. The best (by far) was Freemake Video Converter, not only is it free, but it’s simple to use and will convert a batch of files in one shot. I found it shrank the file size of .ts files, which are initially quite large, by roughly x3 and expanded the size of .flv files, which are initially small, by roughly x2. ————- update My tests show HD (1080p) videos taken by Playbook are quite large, about 6 Gbyte/hour. I found running them through Freemake Video Converter with NO change in resolution, file type, or video quality reduced file size to 2 Gbyte/hour, a factor of 3. Very handy if you want to keep lot of Playbook video stored on the Playbook. ————- Before converting a lot of files I did several tests comparing file formats and resolution. Freemake Video Converter makes it easy to reduce file size by lowering resolution. Tests with a sharp HD video showed no difference that I could see between 1080p and 720p on this small screen, so I decided to go with 720p. This resolution reduces .ts file size by a factor of 4. Reducing quality to TV level, still very watchable, reduces .ts file size by a factor of six.
Quick tests of various formats (avi, mp4, wmv) showed no significant difference in quality or file size and all seemed to play fine on Playbook, so I choose avi and began converting. This turned out to be a mistake. Not one of the first three converted TV shows (1 hr) would play correctly on Playbook. One refused to open and other two gave an error when the slider was moved, though all played correctly on my desktop. The only reason I can come up with is that Playbook has a problem with long files in avi format. My quick tests had been with short files. I then noticed that it says in the Blackberry document, ‘Supported Media Types on Blackberry Tablets’, avi. wmv, and mp4 are “supported”, but the “recommended video format for local playback” is mp4. So I reconverted the same three TV shows to mp4, also lowering the resolution one step to 720p, and now all played fine on Playbook. So my recommendation is stick with mp4, which is the format Playbook uses for its own videos, and reduce resolution to 720p (1280 x 720).
WiFi file transfer A neat trick to easily transfer files to Playbook from your computer over WiFi (no cable!) is to put a shortcut to Playbook on your Windows desktop. Set the ‘target’ of the shortcut to either the IP of your Playbook (found under About, Network) or the ‘Tablet Network Name’, which you can change (found under Storage and Sharing, Network properties) preceded by \ (two backslashes). When you click on the shortcut, Explorer opens and Playbook will appear as a Network device. Click the Media folder and you now have access to all Playbook media folders. For this to work the Playbook ‘WiFi Sharing’ setting (in Storage and Sharing) needs to be ON. Transfer rate is a little slower than with a USB cable (about half), but perfectly usable. (update) For some non-transfer operations, like file rename, I find USB more reliable than WiFi.
Html files, pdf files and File manager The Blackberry (so called) “File Manager” doesn’t show file details, and critically (for some weird reason) it hides local html files, though it does show local pdf files and allows you to open them. Real file managers are available in App World. A pretty good basic file manager (free) is ‘AIR Browser’ and better is ‘File Browser’ (a buck).
‘Air Browser’ and ‘File Browser’ provide a way to work with local html files, they show them and will open them in the browser. Once open in the browser local html files work well, all the internal and external links work. I find it frustrating that Blackberry doesn’t provide direct support for local html files, because I have a whole library of such files that I want to use on the Playbook.
Privacy A useful app for file privacy is ‘File Shield’ (buck). It provides a simple way (without passwords!) to hide videos, photos, and documents. In the app directories and individual files can be toggled between private and public. When set to private, files and directories effectively disappear, visible neither to Blackberry applications nor file managers.
Bugs and weirdnesses I bought just after OS 2 release and my OS upgraded to 2.0 when my new tablet initialized. Here are the bugs and weirdnesses I have found in a week or so of use.
— I initally wrote that my volume up/dn buttons had never worked and assumed it was a software bug because I read someone else reported volume buttons stopped working after an upgrade to OS 2.0. See comments where Ronald kindly set me straight. — Video application has a couple of drawbacks, one is no folders. In the pictures application if you organize picture files in subfolders, the opening screen shows only the subfolders. Not so with the video application. You can put videos in subfolders, but the video application still displays all your videos files on the opening screen. Primitive and inconsistent. Even more surprising the video application displays videos (with the formats it supports) regardless of the folder. Put a video in say, Voice folder, and it still shows up under Videos. — The video application provides two display views: Downloaded Videos and Recorded Videos. Videos uploading to the Camera directory are displayed in the Recorded Video view ordered by the file time stamp, so some separation of videos is possible. Videos in the Downloaded Videos view are ordered alphabetically, No other sort appears to be possible. — Document mode of the browser does not work right in portrait orientation (tested with New York Times articles) — a Hotmail text message in browser would not finger expand — Adobe’s pdf reader come installed on the Playbook, but it is not well integrated with the browser. When a pdf link in the browser is clicked, instead of just opening the file your only option is to download the file. — ‘Power Off’ is a built-in Blackberry app with just three power buttons that are the same as under the battery icon. ‘StandBy’ in the app does not put the tablet to sleep (as it should), it does a ReStart (locking up your machine for two minutes)! You have to wonder just how much testing Blackberry does when a trivial app like this does not work right after a major OS upgrade. — As I discussed above, it appears the video player has a problem with long .avi files, though this format claims to be “supported”. — With Blackberry emphasis on security it is surprising its OS does not directly provide support the hiding of files. — After a week of use the browser crashed (gray screen) requiring Playbook restart to fix it. — On my 2nd day with Playbook it crashed (it first refused to open files, then it hung with Shutting down splash screen displayed). There is a way to hardware reset the Playbook, equivalent to holding down the power button on Windows desktops, but I had to search the web to find it. It’s hold down three of top four buttons (vol up, vol dn and power) for 10-15 sec (or until you see red led). This restored my Playbook to good health with no loss of data. I took off one star (5 => 4) for the volume buttons not working (whoops, see comments) and for a system crash in two days of use.
Top reviews from other countries

LauraUK
4.0 out of 5 stars A good tablet for non-Apps addicts 🙂
Reviewed in the United Kingdom on June 16, 2014
Verified Purchase
I know it might sound crazy to some, but yesterday I bought my second Playbook at an excellent price. Last year we bought a Playbook hoping that Blackberry would release their BBM 10 software. Well, they didn’t but we are still using our Blackberry on a daily basis to surf the web and watch cartoons on Youtube. This is our main use for the Playbook, and although there are games and apps, we haven’t got enough time to spend playing whatever game is in fashion. My daughter, however, has got some nice apps to play and draw that can keep her busy. We also use the Playbook as a PDF reader and now with the second one we will use it to video chat when away from the family for work. At least this is our hope, since sadly we didn’t manage to do this with the Blackberry Z10, which I had to return. All in all, for the price we paid, we are satisfied. It charges quickly with the fast charging docking station and I am sure that we don’t use it to its full potential. We have a terrible computer at home and we haven’t downloaded music or videos onto the Playbook yet. I am sure that if we really needed Apps such as Skype or Whatsapp (or anything else that is in fashion these days) this would not be the tablet to buy, but these Apps can be installed on a smartphone very easily. All in all, a good tablet for web browsing and media playing if the budget is tight.

M. Hallett
5.0 out of 5 stars it’s brilliant. There is the problem that it was a …
Reviewed in the United Kingdom on January 13, 2015
Verified Purchase
I’ve had the Playbook for around eighteen months now. It’s an absolute bargain compared to other tablets on the market. If you want to use your email, surf the web, take pictures or video, store documents, listen to music, or use a few simple commonplace apps, it’s brilliant. There is the problem that it was a commercial disaster for Blackberry and so they’ve given up on it really, which is a shame. I would suggest you download the origami browser – it is streets ahead of the native Blackberry browser. I don’t give a damn about having 101 applications or playing games. If you don’t care about that sort of thing either then this is a smashing buy.

John Dare
4.0 out of 5 stars Lovely piece of kit, but far too many issues with apps.
Reviewed in the United Kingdom on June 25, 2013
Verified Purchase
Pros – well built and sturdy, decent built in browser. good audio for a small tablet, plenty of built in storage, very acceptable screen resolution, wifi connects easily, OK cameras, fair price.
Cons – very few decent apps and most of those are way too expensive, android apps have to be sideloaded – fiddly and time consuming, RIM constantly promising upgrade to BB10 at some point in the future but it never seems to happen and now never will(see next paragraph).
Xem thêm: Cận cảnh Vsmart Joy 2 Plus ĐIỆN THOẠI SIÊU RẺ Pin 4.500mAh có sạc nhanh 3.0
This could and should have been almost a significant a tablet as the ipad but has been constantly let down by appalling planning and support from RIM. It’s such a pity because there is a lot to like about the Playbook and even 2 years after it’s launch it still performs almost as well as many newer and more expensive tablets. If only the OS could be properly upgraded. Sadly RIM have now decided NOT to upgrade the OS to BB10 and have therefore totally let down very many Playbook owners.
Paraphrasing the the words of my old headmaster – “with a little more effort RIM could do so much better”!
I have just added a fourth star, as I get used to it sideloading becomes easier. NO chance of a 5th star since RIM have reneged on their promises to upgrade to BB10.

Mark Collins
4.0 out of 5 stars I’d love to give this 5 stars but…
Reviewed in the United Kingdom on October 1, 2013
Verified Purchase
Great tablet, let down by a lack of apps, and lack of ongoing support from RIM/Blackberry. It’s a shame, because this could have been so good. As it was cheap I will hang onto mine for a bit. And it makes a nice gadget to use for some stuff. To be honest though, I don’t need it, and very rarely use it just due to there not being relevant apps available. Also, now I have a BB10 phone, the bridge has very limited functionality, I have lost most of the features I used to use with my older BB7 phone. Battery great, high quality, and out of the box it works extremely well for the basics. Try to get it to do more than this and you will be disappointed (even with sideloading Android apps – which are very flaky when you try to run them… Kindle being an example – it’s made me buy a Kindle because it was so rubbish!)

kevin
5.0 out of 5 stars So glad I bought this tablet
Reviewed in the United Kingdom on September 14, 2012
Verified Purchase
BlackBerry PlayBook – Tablet – 64 GB – 7″ TFT ( 1024 x 600 ) – rear camera + front camera – Wi-Fi, Bluetooth u
I wanted a tablet for a while but was put off by the price. When I saw this BlackBerry playbook for this price I read through loads of customer reviews, and found them all mostly very positive, so I took a chance and bought one. I already have a Blackberry bold phone, and use documents to go all the time.
I must say that to set up the Bridge software and download it to my phone was quick and simple. Once done the tablet and phone are linked by bluetooth and you can keep your phone in your pocket and access your messages, we’ll everything, I love it!
When you are away from your wifi or free hotspot, you can still get on the Internet because the Internet is accessed via bluetooth (Bridge) through your phone in your pocket.
Also if you download “print to go” to your pc or laptop you can select print to go and your document will appear on your tablet in pdf format, so instead of carrying around wads of paper printouts, you can have them on your tablet
I highly recommend this tablet, it also looks good, we’ll made and easy to use,I like it more than the ipad.
Nguồn: https://sharengay.online Danh mục: Công Nghệ
Amazon.com : BlackBerry PlayBook 32GB 7″ Multi-Touch Tablet PC with 1 GHz Dual-Core Processor, 5MP Camera and Secondary 3MP Camera, Video, GPS, Wi-Fi and Bluetooth – Black : Tablet Computers : Computers & Accessories
from Sharengay Trang Tin Tức Độc Đáo VIDEO https://bit.ly/2Tu1w3o via IFTTT
0 notes