#i can do it but not in a way that's remotely efficient for communicating with others
Explore tagged Tumblr posts
Text
always been baffled how people can just say things. on or offline. not even in the brazen or stupid way, but the simple human verb way, like you can really type or share out loud thoughts that are inside your head? your stream of consciousness? impart a random fact or fictional piece of information? recount stories & interactions & days you’ve had? with or without details & enthusiasm? you really have things in your head & just.. share them, or have nothing in your head yet spitball and react and end up sharing something regardless, even if only stumbling over words? with words or jibberish, you really just flhkijdkd from parted lips or your fingertips and stuff inside suddenly lives? i have experienced all of this everywhere all the time & it remains wild to me how people do this. they simply do it, with or without thought, with people they know well or don’t know at all. how
one could claim i’m doing it this very moment yet this alone took me a genuine couple of weeks to edit the words back & forth, contemplate & eventually decide to share. this is in no way an exaggeration. where did my functioning go awry
#this is my attempt to practice doing so#but it still feels wholly unnatural & entirely too overthought#yet the goal’s to do it until it’s second nature#at least the times i ever wish to#every single person ive ever known has been able to do it#many introverted or shy types#the way they still speak & share things in online spaces sincerely just blows my mind#like how do you do it how do you say words#even with folks with anxiety or self consciousness or paranoia the words still get said and posts still made so why did i never learn#i can do it but not in a way that's remotely efficient for communicating with others#this is why an og post is a rare occurence for me#p
2 notes
·
View notes
Text
⟡ within your waking thoughts (there i’ll be).
⎯ what do they do when they miss you? how do they cope with yearning when you're away? { y for yearning ノ ordered by @floraldresvi! (sorry for the ping!) }
RESERVED FOR! ノ characters. aventurine, sunday, dr. ratio ft. gn!reader. { 1.3k words }
FLAVOR! ノ genre. fluff, slight angst (my apology to sunday lovers yet again), established relationship.
TOPPINGS! ノ tags. aventurine has his tech savvy moment, pre-2.2 sunday (heavy references but no spoilers), ratio has two phones (king of separating work & personal life !!!).
BAKER’S NOTE! ノ thoughts. a repost! bcs tumblr didn't like it the first time. hopefully, this one will be here to stay. thank u to vivi for requesting this ‹3
© seelestia on tumblr, may 2024. please do not repost, plagiarize, translate, use for AI-related purposes or claim as your own.

in your absence, aventurine welcomes little thoughts of you that float around his mind with open arms - and the way he indulges them is by simply texting you. effective and efficient, there is a reason why the cosmos calls it the second most used means for long distance communication. what about the first? well, he would've opted for calling you with his earpiece if only his line of work doesn't require 90% of its usage time.
let's just say the idea of fellow stonehearts interrupting his conversation with you ruins the fun. besides, he has deft fingers; coin tricks aren't the only thing in his book, you know, typing a few sentences in one go is no problem at all.
but maybe, he is using that too much to his advantage . . . considering the “25+” staring back at you from your notifications every few hours or so. aventurine is truly, irrevocably relentless.
anything even remotely in your favorite color found within his vicinity? new message: Saw something that reminded me of you, you must really like crossing my mind.
an item he thinks would fit you well? new message: I got you a gift. Does it suit your fancy? [1 attachment]
reminded of how cruel fate is to separate you two for so long? new message: Haven't seen your face in a while. Fifteen hours are a total too cruel, don't you agree?
have faith that you will never grasp the true meaning of boredom when you’re apart from him. luck follows a man like aventurine, so do interesting events - remember how he won a vacation to a resort with one chip? he revels in telling you stories of his encounters while you're away. it is as if thrill revolves around him constantly. . . one wonders just how he fares living on the edge of it all.
(you, for one, are aware of his ways. he has allowed you to wander far enough behind his masquerade, after all.)
of course, texts on an illuminated screen can barely compare to seeing you in person. he prefers having you in his arms instead - but he'll live. solitude is an old friend of his, albeit distant and cold, aventurine can deal with its company every once in a while. at the end of the day, he knows you’ll be there when he comes home.
though, it's such a shame he cannot see your face when you're apart. the curve of your lips as you smile, the twinkle in your eyes with his reflection in them, and. . . ah, seems like he is making this harder for himself. maybe, he should consider buying that HD holographic communicative device on the market? his ears caught wind of some P45 officers at pier point whispering about it before.
it'll cost a large sum of credits but hey, he thinks it'll be worth it. for you? anything is possible.
(...him? clingy? well, guilty as charged.)

sunday’s self-discipline is not something to be underestimated. halovians are a species known for their enchanting voices, yet he feels as if he cannot spare any for even his inner thoughts. what an irony. his longing for your presence is persistent, tumbling at the edge of his tongue - but he is equally as, if not more, stubborn and so he swallows this yearning down instantly.
you are not confined to the dreamscape like he is, as self-imposed as that may be. sunday is aware of that, hence his first instinct is to keep quiet. the curse of sealing his lips till forevermore; watching you leave through the grand doors, letting his gaze fall to where your shadow used to be, savoring the last of your remaining fragrance from when you last bade him goodbye - all without a word.
(don't go, he wished he could say.)
is it a bad habit? “your voice shouldn't be used just to utter words that others want to hear,” you reminded him once. “it's also for you. it's yours.”
but even then, your words are akin to a faint whisper; muffled by the thoughts that plague his mind like a mist. he can't help how they fog up his reflection in the mirror, leaving remnants of something acrid that wafts in the air. something like doubts, sunday would know because he has dwelled in it for as long as he remembers.
you are outside, fluttering your wings in the sky and enjoying what it has to offer. does he have any rights to disturb you? perhaps, in his eyes, sunday views himself as a string tied around your talon, trailing all the way from the heavens where you soar to the humble ground where he resides. each time your absence compels him to reach out, it is as if he’s tugging on that string and dragging you lower from the height you truly relish in, from the height you deserve to be at.
(sunday believes that you belong to the sky, unlike him.)
so here, he shall stay and here, he shall wait until you return. sunday’s heart begins to grow cold - but the farewell kiss you've left on the apple of his cheek hasn't faded. its warmth remains, even when he brushes his freezing hand against it, it remains.
you remain.
(and that is enough for him.)

dr. ratio is a man with a packed schedule, so it's safe to say he keeps himself occupied particularly well. tasks at the intelligentsia guild are nothing short of demanding, after all. there are researchers asking for his input left and right, although some tremble while speaking to him even when he hasn't even uttered a word yet. ignoring that, he also aids in projects that require his expertise. last but not least, his students and classes which he takes very seriously.
(but be careful with how you phrase it — the doctor doesn't view them as distractions, no, he sees them as his responsibilities — saying the former might offend him.)
as you can see, he is perfectly capable of spending time away from you. . . .or at least, until it's time for a break and a part of that perfection chips off.
his office is quite tranquil, free from outside noise, just the way he likes. this place bears a similar purpose as his headgear, to let him focus in silence without disturbance - but he hasn't expected that exact silence to be this deafening. hah, how absurd! in what realm of possibility could silence ever be associated with deafening as an adjective? he supposes it could be a case of tinnitus. . . but veritas knows that isn't the case.
something's missing and it is, much to his dismay, you.
veritas has his standards. he prefers things to be set at a specific level - and this level of silence, one marred further by your lack of presence, is too low for him. he's getting too used to seeing you barge into his office with neatly packed sandwiches in your hands, a revelation he'd rather keep to himself.
veritas reaches for his personal phone, his work one left neglected at the far end of the desk. he considers making a call to you but the clock is ticking. tick tock tick tock, as if to hang the fact that his break is reaching its end over his head.
utilizing whatever time he has left, his finger gives the gallery app a tap. various pictures pop up on the screen; selfies of you with silly expressions, candid shots of veritas himself and some photos of random objects like your matching mugs. all of these were taken by you, of course. seriously, is this his phone or is it yours?
who knows at this point? he nearly lets out a snort, but that smile on his face is fooling no one. the doctor continues scrolling through his gallery, utterly content with just this until he gets home. to you.
(yes, yes, this still counts as keeping himself occupied. thank you for your concern.)

— thank you for reading! reblogs with comments are most appreciated.
#hsr x reader#—stellaronhvnters.#aventurine x reader#sunday x reader#dr ratio x reader#hsr fluff#seelestial.inks#reveriesincups
961 notes
·
View notes
Note
I saw you hc L as autistic so maybe him with an autistic reader who's not the quiet type? (flappy hands, vocal stims, loud music instead of noise cancelling headphones; idk how to explain it)
-🦇
Summary: Headcanons for L Lawliet x reader. Both are autistic, but polar opposites in how they do things/handle their autism.
Credits: L Lawliet- Death Note, Divider- Benkeibear, Cover picture- Pinterest
A/n: Grrr I love getting to write for L! He's such a goober and I love getting to elaborate on my general headcanons for characters <3 ALSO 🦇 anon left a little bit ago, but I am still fulfilling this request they left for me so if you want the anon name, feel free to take it
Thank you so much for requesting!

Autistic!L Lawliet x Autistic!Reader who are polar opposites

L has always been rather quiet, even as a child
He didn't start talking until about 6, and even then he only began talking because it communicated his needs more efficiently
He prefers quiet spaces and being alone, because it allows him to focus more
He also hates chaos or unplanned things. If he has time to plan something out to a T, he can make sure nothing will go wrong, therefore insuring the safety of everyone
This being said, he never thought you were someone he'd remotely like being around, let alone dating you
No offense, but you are literally everything he hates
And when he comes into contacts with the things that make him uncomfortable (such as chaos, loudness, etc) he can get panicky
He will quickly become overwhelmed and irritable, meaning the littlest things can make him snap
If he can't focus how can he save the world? If the world isn't saved by him than who will do it? Panicking isn't helping though, it's making things worse. Oh god, he can't stop! He can't think straight long enough to calm down!
And then kaboom, he basically just shuts down
The second he met you he was on his guard, knowing this likely wouldn't end well
He prefers to not work with people, but he can handle them as long as they're quiet
This is entirely out of the question
As you can guess, your first meeting is almost a disaster
Well, everyone else didn't know it was a disaster of course. They actually thought it went pretty well!
But in actuality, L was completely overwhelmed by you
Not even you actually, just the idea that you might overwhelm him
TLDR: He became overwhelmed thinking about how overwhelmed you might make him, so you essentially did nothing wrong lol
After this, he keeps his distance
Of course though, this makes for a bad work environment
So he nervously invites you into his hotel room and explains things to you
How he feels around you, explaining his autism (which he refuses to do under normal circumstances), and asking you to explain yours as well so he can formulate an arrangement for you to be around each other without causing him to panic
After this communication is had, working together is a lot smoother
He considers you a better acquaintance than the rest of his employees
Meaning he feels closer to you
However, when you begin dating your differences are just another quirk to him that he finds endearing
He loves to see you get excited and flap your hands, he loves to see you dance to your loud music, he loves all of it
If he isn't in the headspace for loudness though, he will of course inform you before going off to be alone
If you want to try to accommodate his preferences into your behaviors is up to you, but he is perfectly happy either way
He finds himself feeling safe around you because of your loudness
Like, you are a German Shepard and he is a hurt bird
He'll hide behind you with his big ol' eyes staring at his surroundings while you fight off anyone that might be too much for him
And being exposed to you all the time helps him expose himself little by little to things that would previously make him very uncomfortable
For example, he can now go out in public without panicking over how many people there are and how many things could go wrong for short bursts of time
And he is now fine with soft music playing in the background while he works rather than just total silence the entire time
He also likes that having you around means you can do the talking for both of you and he doesn't have to actually break his focus for anything
the goobies <33
#death note x y/n#death note x you#death note x reader#death note#l death note#death note l#l lawilet#l lawliet x reader#l lawliet x you#l lawliet x y/n#l lawliet hcs
81 notes
·
View notes
Note
I don't consider myself an anarchist but i'm pretty sympathetic, there's just some stuff i'm not sure yet would work well under anarchism as i understood it after reading the bread book.
What would incentivize people to work, for example, at oil rigs away from their communities doing dangerous work?
Would it be that they'd have a smaller expectation for how long they're suposed to work? Like, instead of you working 9-5 for 8 months instead you work 9-5 for 4 months and then can just do things you like the rest of the year?
Yes hi hello! This post re-emerged from the depths of accidental deletion!! I’m getting the bus to go get a burrito so let me talk about this one!!
Kropotkin actually talked about dangerous work; after all, some work is just inherently and unavoidably a bit more dangerous than others: so what’s the point? Why bother?
To start, resource extraction is going to be inherent to any industrial economy, but it’s worth pointing out that when you eliminate a lot of overproduction, an inefficiency inherent to capitalist economy, the demand for extraction is going to shoot down in a big way. That’s a big reason why a lot of the more hardcore environmentalist movements have been radical leftist ones; it’s features inherent to capitalism which are bringing about the downfall of the environment which sustains us.
Another big consideration to make is that a lot of the danger of these fields arises solely because the demands of the profit motive incentivise management to overwork/underpay/cut back on or wholesale eliminate critical safety measures; there’s a reason why unions and collectives in those fields are such critical players in the constant battle to keep people safe.
There are quite a few fields in the domestic/public sector, as well (think electricians, certain waste management professions etc.) which are (and were more so in the past) fairly dangerous but are not generally regarded as such because they’re regulated well in the public domain/have very strong unions/have otherwise strong safety regulation.
This stuff gets safer and safer as we improve the automation of our economy, as well.
It’s worth remembering as well that those remote professions and operations are, in a way, their own communities, as well, and for some people travelling long distances away for more lonesome work is quite an attractive prospect; I once knew a geologist who said he found the relative isolation quite peaceful. My great grandad did some remote mining and he always talked quite positively about it when I knew him (although this is very anecdotal - if anybody in the field wants to weigh in I’d be more than happy to hear what you think).
About hours as well;
If there’s no profit motive, then industrial processes are going to be driven by how to do them as safely, efficiently, and easily (among other stuff). The demand for hours is going to be a lot less tough because you’re going to be able to have more workers and source better equipment without worrying about how it will cut into your bottom line; so yes, the hours will be shorter and the shifts less demanding, with a greater support network and safety network when shit hits the fan. All of this, of course, makes this kind of work a lot more attractive.
But what about dangerous work in general? Why would anyone put themselves in danger?
You just have to look at the tremendous danger that volunteers face to understand that humans don’t really need a profit motive to put their lives on the line to better their communities and the world, or to feel part of something greater than themselves. Not everyone is going to want to do that, and that’s ok, but some people really derive a lot of happiness and fulfilment from dangerous work.
Humanity is flexible and diverse; working together to champion that is our strength, and it always has been.
#anarchism#anarchist#anarchocommunism#praxis#communism#communist#revolution#leftism#leftist#danger#dangerous work#mining#resource extraction#q and a#qna
203 notes
·
View notes
Text
Hello @simonsapelsin! I’m ready to respond to the comment you left yesterday.
Within the parameters of canon—most likely no, but maybe? It would have to be backed up by a lot of plot and character developments in order for it to work.
This ended up being way too long, so more thoughts on sargust + thoughts on the potential created by AUs and canon divergences + thoughts on the idea of “healthy” relationships behind the cut…
So obviously season 2 ended in a really, really bad place for sargust. August refuses to embrace accountability and doubles down on his harmful behavior. Our last shot of Sara is her calling the police to report him, and in that moment she’s completely alone. They have that painful conversation about August buying Rousseau. That’s… that’s a lot for them to overcome, and season 3 doesn’t have enough episodes to get us there fully, unless the writing team are very, very clever and efficient.
There’s a popular fan interpretation of sargust that says that Sara and August both project identities onto one another and don’t see one another’s real selves. I understand and agree with that interpretation up to a point, but I don’t know if I necessarily agree with it 100%. In my mind they do see real things about one another (August sees Sara’s ambition and desire for independence, Sara sees August’s emotional vulnerability and need for help. And they do connect with one another in ways that others haven’t been able to connect with them. What August and Sara fail to predict about one another is the other’s choices. Sara assumed August would choose to be honest and August assumed Sara would choose to be queen. But I think the care they showed for one another earlier in the season was real, and the way they could hold space for one another was real. That’s really a meta I could write for another time, but a lot of it hinges on this line, which is not a line I am even remotely normal about:

(Note: I’ll probably write this meta eventually. The fact that these characters create a sort of home with one another! Also lol @ August looking like he is stoned out of his mind.)
So what would it look like for sargust to get a Second Chance Romance within the parameters of canon? I mean, first of all, they’d both have to mature independently for a while and work through a lot of the trauma they’re carrying.
For Sara, I want her to get away from home and have some distance from the place she grew up so she can put her childhood in perspective. Therapy would help. (I want that for Simon, too!) I’d also like to see Sara find some neurodivergent friends/community—I mean, we do tend to find one another and run in packs! And then some sort of career or life path that makes her happy. Maybe with horses, sure, but it’d also be interesting to see Sara keep horses as a beloved hobby while also finding a different career she’s passionate about.
For August, accountability and rehabilitation and understanding of the harm he did is incredibly important for his personal growth. Whether he faces that through the legal system or through some other process is something we have yet to see in the show. Then comes the long work of restitution and atonement, as well as the steps August needs to take to grapple with his various personal traumas. Like, please get this boy a place to process his grief over his father, treatment for his disordered eating, and rehab for his addiction to pills.
Now, Sara and August wouldn’t have to be 100% healed and self-actualized when they run across one another as adults—I don’t know if there’d be a story if they were, and this sort of stuff is lifelong work! But further along the paths above that I described—that could still be a good story.
Beyond growth and maturity, I think we’d have to see some sort of change in how August and Simon relate to one another, happening primarily on Simon’s terms because he was the one wronged, and that would need to be an important part of the story. This feels crucial. Now that Sara’s aware how much she hurt her brother, I don’t imagine she’d enter a relationship with August even if August is a super chill, okay person now. So I actually think a good Second Chance Romance story would have to heavily involve Simon in one way or another. But a fic where August and Simon interact more honestly with one another, and August has to face up to Simon’s personhood? That would definitely hold my attention. (I am kind of hoping they get more extended interaction in season 3, really. They have some sneaky but fascinating parallels as characters and I like watching the way Omar and Malte play off one another.)
Outside of canon… one thing I have considered is the potential to write a version of sargust in AUs that’s more tailored toward happy endings. Which doesn’t quite relate to your question but I do want to talk about it. As of now, AUs/Canon Divergence fics are a perfect place to make sargust actually work out. This fandom has a lot of imagination for AUs and canon divergences. And it’s no surprise—Young Royals is a rich, nuanced text that can be explored from many angles, so it only makes sense that we’d want to create a thousand alternate universe scenarios where canon could have gone differently. In my mind, if people can write “Erik lives” AUs, then “sargust is successful because August learns over time to be less shitty” AUs are also fair game.
The thing with writing an AU or canon divergence is that August’s complex brand of shittiness does not have to be inevitable or eternal. We’ve got creative freedom, baby! We can write any kind of arc for him that we want to and nudge him in all kinds of directions, and set him and Sara up for success! To me, part of the spirit of Young Royals is embracing the idea that everyone has choices, and that they are capable of growth that allows them to make better choices. I mean, sure, it’d be weird to find a version of August on page #1 of a fanfic who’s suddenly like, quoting bell hooks and pushing for an inclusive socialist utopia. I don’t know if I’d suspend my disbelief for that. But I also really struggle to suspend my disbelief for AU versions of August where he’s like… a straightforward flat villain solely out to cause trouble, which is something I have seen out there in the wild and clicked the “back” button over. I crave the nuance. The texture. The literary crunch of it all!
And I don’t think August has to be the center of a fic for that to happen, even. Like I think there’s ways to have him and Sara as a story’s Beta Couple or Gamma Couple and we’re rooting for them and you know what? It’s an AU where some of the characters are fae or 1980s punks or rival scholars of Cold War history so events are happening differently anyway. I’m sure there are ways to write August in character as his shitty self and have him eventually grow and change, without having August also ruin his chances with Sara because he does something that fucks Simon over so completely, you know?
Now, I know there’s fic writers out there who never under any circumstances want to write August’s character and can’t do so from a place of emotional safety. For some folks it is more comfortable to engage with him as a more straightforward villain. And that’s fair. Everyone should write what they feel comfortable writing! In this post, however, I’m thinking more about the people who want to include some kind of nuanced arc for August in their story, but also feel like no one will be interested in it, or like they’ll actually lose readers and engagement if they do write about him, even as a secondary character. Every once in a while I’ll see another fan allude to a really cool fic idea that involves August in some way or takes him in an interesting direction, and then they’ll be like, “oh, but why bother writing it, no one will read it anyway.” And… that makes me incredibly sad! Because I would happily read those fics. I know some other people who would happily read those fics! But I think we’ve normalized the idea that that’s just not how things are “done” in the Young Royals fandom. Which makes it very hard for people to take that risk. I think we’re missing out on some cool stories as a result, that could really be satisfying to read.
One final thought… I notice some fandoms use the word “healthy” when describing their OTPs/favorite pairings. I hope you’re okay with me unpacking that a bit? This is less a response to your comment in particular and more a response to fandom at large.
Honestly, “healthy” is a word that’s starting to feel pretty loaded for me, and can kind of rub me the wrong way. It seems that generally what people mean by it—when they apply it to a pairing—is that the pairing is good at communicating, respects one another’s boundaries, responds to one another’s needs, processes trauma, etc. And I do appreciate in a story when characters can do these things, to an extent.
But putting it under this umbrella label of “healthy” …well. Okay. “Healthy” is a word that society has added a moral dimension to, and it often gets weaponized against people with disabilities and mental illnesses and other chronic conditions. And health is not an indicator of personal worth. Holding people IRL to a standard of “healthy” kinda feels like you’re saying “it’s okay if you have these diagnoses, as long as you manage them in such a way that it seems like they don’t affect you or the people around you.” (And as someone who’s just recently begun managing a chronic condition, who’s struggling with how to tell my family members because of the way they’re going to moralize about my diet or my stress levels, and also struggling with the shit I’ve internalized over the years… well. I’m thinking about how we use the word “healthy” a lot.)
Bringing this back to the realm of fandoms (because, oof, TMI there blue!) holding a fictional character or pairing to the standard of “healthy” can kind of create some uncomfortable fandom dynamics—at least it can for me, personally. When I see fans take pride in the fact that they ship a “healthy” pairing, to the point where they frequently talk about how “healthy” their pairing is, it’s almost impossible for me not to read such comments as using a moralizing tone that implicitly puts others down for having “unhealthy” ships. Sometimes—generally I haven’t seen this as much in YR fandom—there are even people who will straight up write you off if they perceive your ship as “unhealthy” or “toxic.” And then suddenly all ships are either deemed healthy or unhealthy, and healthy ships are retroactively interpreted as doing everything right, while unhealthy ships can never do anything right, and there’s no hope for them. And that is… a bleak and boring landscape for shipping, if you ask me.
I want to read romances where writers are informed about how trauma can affect relationships and how one can learn to survive it, yes. But I feel iffy about the idea of a perfectly “healthy” romances for sargust or wilmon, seeing as they’re all characters with trauma and mental health struggles, and all of them have days that are Not So Good. They could all mature into adults who’ve learned from their past, but like, Wilhelm might still have panic attacks because anxiety is like that sometimes and it’s not a moral failing. August could go through rehab and be in a much better place and harm others less, and still might struggle with intense emotional disregulation or thoughts related to disordered eating, you know? I’d like reading trauma-informed stories where sargust can mature and heal. But they still might have bad days because that’s what being human is.
In addition, I also like tragic sargust where things just don’t work out between them and everything falls apart, because as I’ve said elsewhere on this blog, I’m a slut for tragedy.
So. Idk. I talk about all these things and all these possibilities in hopes that maybe someone in the fandom will get inspired by them. We’ll see if it does that! Ahaha. It’s worth a try.
ADDENDUM, since I didn���t talk about my own fic ideas here:
Heart and Homeland is an AU fic, and it’s tragic sargust for sure. And I’m proud of it, despite the part where their relationship is tragic! And I tried to work in little glimmers where you see how their relationship could have worked.
Now, my next fic idea, shared with @heliza24, is one set in a canon divergence universe where Sara goes to campus to look for Simon, on the night that Everything Is Fake But Wilhelm’s Love For Simon Is Real. As Sara walks around campus, trying to find her brother, she bumps into August, who is still high from the party and is just sort of… emotionally all over the place? In my head I think Sara and August actually trip over one another and he gets a skinned knee or something, so they have to break into some part of school late at night to get band-aids from a first aid kit, and they end up in a weird, late-night conversation and August actually ends up talking to Sara about his grief for Erik. Thus, he’s never at the window to film the video, and some weird door opens up in his brain about actually having someone he can open up to. He doesn’t change overnight, but his character—and everyone else’s characters—are butterfly effected in a totally different direction. That’s all I’m going to say for now! But gosh, I really hope I get the time and energy to write it.
#young royals#sara eriksson#august horn#sargust#this is a long post i am sorry#and also it veers into my thoughts about fandom stuff in general#but hopefully there are a few good ideas in there
43 notes
·
View notes
Text
In an underground parking lot beneath an ordinary building in an ordinary Ukrainian city, dozens of what appear to be small, windowless fishing boats are lined up in rows. The noise of machinery echoes from a separate room, where men are working with metal and wires. They didn’t look up when I walked in one recent morning, and no wonder: This is a sea-drone factory, these are among the best engineers in Ukraine, and they are busy producing the unmanned vessels that have altered the trajectory of the war. Packed with explosives and guided by the world’s most sophisticated remote-navigation technology, these new weapons might even change the way that all naval wars are fought in the future.
Certainly, the sea drones are evolving very quickly. A year ago, I visited the small workshop that was then producing the first Ukrainian models. One of the chief engineers described what was at the time the drones’ first major success: a strike that took out a Russian frigate, damaged a submarine, and hit some other boats as well.
Since then, the sea drones, sometimes alone and sometimes in combined attacks with flying drones or missiles, have sunk or damaged more than two dozen warships. This is possibly the most successful example of asymmetric warfare in history. The Ukrainian drones cost perhaps $220,000 apiece; many of the Russian ships are worth hundreds of millions of dollars. The military impact is enormous. To avoid Ukrainian strikes, Russian ships have mostly left their former headquarters, in the occupied Crimean port of Sevastopol, and moved farther east. They no longer patrol the Ukrainian coast. They can’t stop Ukrainian cargo ships from carrying grain and other goods to world markets, and Ukrainian trade is returning to prewar levels. This can’t be said often enough: Ukraine, a country without much of a navy, defeated Russia’s Black Sea fleet.
Nor is Ukraine’s talent for asymmetric warfare confined to water. During a recent trip, I visited another basement, where another team of Ukrainians was working to change the course of the war—and, again, maybe the course of all subsequent wars as well. (I was allowed to tour these operations on the condition that I not identify their locations or the people working at them.) This particular facility had no machines, no engines, and no warheads, just a room lined with screens. The men and women sitting at the screens were dressed like civilians, but in fact they were soldiers, members of a special army unit created to deploy experimental communications technology in combination with experimental drones. Both are being developed by Ukrainians, for Ukraine.
This particular team, with links to many parts of the front lines, has been part of both offensive and defensive operations, and even medical evacuations. According to one of the commanders, this unit alone has conducted 2,400 combat missions and destroyed more than 1,000 targets, including tanks, armored personnel vehicles, trucks, and electronic-warfare systems since its creation several months ago. Like the sea-drone factory, the team in the basement is operating on a completely different scale from the frontline drone units whose work I also encountered last year, on several trips around Ukraine. In 2023, I met small groups of men building drones in garages, using what looked like sticks and glue. By contrast, this new unit is able to see images of most of the front line all at once, revise tools and tactics as new situations develop, and even design new drones to fit the army’s changing needs.
More important, another commander told me, the team works “at the horizontal level,” meaning that members coordinate directly with other groups on the ground rather than operating via the army’s chain of command: “Three years of experience tells us that, 100 percent, we will be much more efficient when we are doing it on our own—coordinating with other guys that have assets, motivation, understanding of the processes.” Horizontal is a word that describes many successful Ukrainian projects, both military and civilian. Also, grassroots. In other words, Ukrainians do better when they organize themselves; they do worse when they try to move in lockstep under a single leader. Some argue that this makes them more resilient. Or, as another member of the team put it, Russia will never be able to destroy Ukraine’s decision-making center, “because the center doesn’t make all the decisions.”
I recognize that this account of the war effort differs dramatically from other, grimmer stories now coming out of Ukraine. In recent weeks, Russian glide bombs and artillery have slowly begun to destroy the city of Pokrovsk, a logistical hub that has been part of Ukraine’s defensive line in Donetsk for a decade. Regular waves of Russian air strikes continue to hit Ukraine’s electricity infrastructure. The repeated attacks on civilians are not an accident; they are a tactic. Russian President Vladimir Putin is seeking to deprive Ukrainians of heat and light, to demoralize the people as well as the government, and perhaps to provoke a new refugee exodus that will disrupt European politics.
Russia remains the larger and richer country. The Kremlin has more ammunition, more tanks, and a greater willingness to dispose of its citizens. The Russian president is willing to tolerate high human losses, as well as equipment losses, of a kind that almost no other nation could accept. And yet, the Ukrainians still believe they can win—if only their American and European allies will let them.
Two and a half years into the conflict, the idea that we haven’t let Ukraine win may sound strange. Since the beginning of the war, after all, we have been supporting Ukraine with weapons and other aid. Recently, President Joe Biden reiterated his support for Ukraine at the United Nations. “The good news is that Putin’s war has failed in his core aim,” he said. But, he added, “the world now has another choice to make: Will we sustain our support to help Ukraine win this war and preserve its freedom, or walk away and let a nation be destroyed? We cannot grow weary. We cannot look away.” Hoping to rally more Americans to his side, Ukrainian President Volodymyr Zelensky spent much of last week in the United States. He visited an ammunition factory in Pennsylvania. He met with former President Donald Trump, and with Vice President Kamala Harris.
Zelensky also presented a victory plan that asked, among other things, for Ukraine to have the right to use American and European long-range missiles to strike military targets deep inside Russia. This kind of request is now familiar. In each stage of the war, the Ukrainians and their allies have waged public campaigns to get new weapons—tanks, F-16s, long-range missiles—that they need to maintain a technological edge. Each time, these requests were eventually granted, although sometimes too late to make a difference.
Each time, officials in the U.S., Germany, and other Western powers argued that this or that weapon risked crossing some kind of red line. The same argument is being made once again, and it sounds hollow. Because at this point, the red lines are entirely in our heads; every one of them has been breached. Using drones, Ukraine already hits targets deep inside Russia, including oil refineries, oil and gas export facilities, even air bases. In the past few weeks, Ukraine’s long-range drones have hit at least three large ammunition depots, one of which was said to have just received a large consignment from North Korea; when attacked, the depot exploded dramatically, producing an eerie mushroom cloud. In a development that would have been unthinkable at the beginning of the war, Ukraine has, since early August, even occupied a chunk of Russian territory. Ukrainian troops invaded Kursk province, took control of several towns and villages, set up defenses, repelled Russian troops, and have yet to leave.
But in truth, the imaginary red lines, the slow provision of weapons, and the rules about what can and can’t be hit are not the real problem. On its own, a White House decision to allow the Ukrainians to strike targets in Russia with American or even European missiles will not change the course of the war. The deeper limitation is our lack of imagination. Since this war began, we haven’t been able to imagine that the Ukrainians might defeat Russia, and so we haven’t tried to help those who are trying to do exactly that. We aren’t identifying, funding, and empowering the young Ukrainian engineers who are inventing new forms of asymmetric warfare. With a few exceptions, Ukrainians tell me, many allied armies aren’t in regular contact with the people carrying out cutting-edge military experiments in Ukraine. Oleksandr Kamyshin, Ukraine’s minister of strategic industries, says that the Ukrainians have spare capacity in their own drone factories, and could produce more themselves if they just had the money. Meanwhile, $300 billion worth of frozen Russian reserves are still sitting in European clearinghouses, untouched, waiting for a political decision to use that money to win the war. Biden is right to tout the success of the coalition of democracies created to aid Ukraine, but why not let that coalition start defending Ukraine against incoming missiles, as friends of Israel have just done in the Middle East? Why isn’t the coalition focused on enforcing targeted sanctions against the Russian defense industry?
Worse—much worse—is that, instead of focusing on victory, Americans and Europeans continue to dream of a magic “negotiated solution” that remains far away. Many, many people, some in good faith and some in bad faith, continue to call for an exchange of “land for peace.” Last week, Trump attacked Zelensky for supposedly refusing to negotiate, and the ex-president continues to make unfounded promises to end the war “in 24 hours.” But the obstacle to negotiations is not Zelensky. He probably could be induced to trade at least some land for peace, as long as Ukraine received authentic security guarantees—preferably, though not necessarily, in the form of NATO membership—to protect the rest of the country’s territory, and as long as Ukraine could be put on a path to complete integration with Europe. Even a smaller Ukraine would still need to be a viable country, to attract investment and ensure refugees’ return.
Right now, the actual obstacle is Putin. Indeed, none of these advocates for “peace,” whether they come from the Quincy Institute, the Trump campaign, the Council on Foreign Relations, or even within the U.S. government, can explain how they will persuade Russia to accept such a deal. It is the Russians who have to be persuaded to stop fighting. It is the Russians who do not want to end the war.
Look, again, at the situation on the ground. Even now, two and a half years into a war that was supposed to be over in a few days, the Kremlin still seeks to gain more territory. Despite the ongoing Ukrainian occupation of Kursk province, the Russian army is still sending thousands of men to die in the battle for Donetsk province. The Russian army also seems unbothered by losing equipment. In the long battle for Vulhedar, a now-empty town in eastern Ukraine with a prewar population of 14,000, the Russians have sacrificed about 1,000 tanks, armored vehicles, and pieces of artillery —nearly 6 percent of all the vehicles destroyed during the entire war.
Russia has not changed its rhetoric either. On state television, pundits still call for the dismemberment and destruction of Ukraine. Putin continues to call for the “denazification of Ukraine,” by which he means the removal of Ukraine’s language, culture, and identity—as well as “demilitarization, and neutral status,” by which he means a Ukraine that has no army and cannot resist conquest. Nor do Russian economic decisions indicate a desire for peace. The Russian president now plans to spend 40 percent of the national budget on arms production, sacrificing living standards, health care, pensions, broader prosperity, and maybe the stability of the economy itself. The state is still paying larger and larger bonuses to anyone willing to sign up to fight. Labor shortages are rampant, both because the army is eating up eligible men and because so many others have left the country to avoid conscription.
Negotiations can begin only when this rhetoric changes, when the defense machine grinds to a halt, when the attempts to conquer yet another village are abandoned. This war will end, in other words, only when the Russians run out of resources—and their resources are not infinite—or when they finally understand that Ukraine’s alliances are real, that Ukraine will not surrender, and that Russia cannot win. Just as the British decided in the early 20th century that Ireland is not British and the French decided in 1962 that Algeria is not France, so must the Russians come to accept that Ukraine is not Russia. At that point, there can be a cease-fire, a discussion of new borders, negotiations about other things—such as the fate of the more than 19,000 Ukrainian children who have been kidnapped and deported by the Russians, an orchestrated act of cruelty.
We have not yet reached that stage. The Russians are still waiting for the U.S. to get tired, to stop defending Ukraine, and maybe to elect Trump so that they can dictate terms and make Ukraine into a colony again. They are hoping that the “Ukraine fatigue” they promote and the false arguments about Ukrainian corruption (“Zelensky’s yachts”) that they pay American influencers to repeat will eventually overwhelm America’s strategic and political self-interest. Which, of course, might be the case.
But if it is, we are in for a nasty surprise. Should Ukraine finally lose this war, the costs—military, economic, political—for the U.S. and its allies will not go down. On the contrary, they are likely to increase, and not only in Europe. Since 2022, the military and defense-industry links among Russia, North Korea, Iran, and China have strengthened. Iran has delivered drones and missiles to Russia. Russia, in turn, may be providing anti-ship missiles to the Houthis, Iranian proxies who could use them against American and European commercial and military ships in the Red Sea. According to a recent Reuters report, the Russians are now constructing a major drone factory in China. The Chinese stand to benefit, that is, from the huge technological gains that the Russians have made, in many cases by imitating the Ukrainians in drone warfare and other systems, even if Americans aren’t paying close attention.
A failure to defeat Russia will be felt not just in Europe but also in the Middle East and Asia. It will be felt in Venezuela, where Putin’s aggressive defiance has surely helped inspire his ally Nicolás Maduro to stay in power despite losing an election in a landslide. It will be felt in Africa, where Russian mercenaries now support a series of ugly regimes. And, of course, this failure will be felt by Ukraine’s neighbors. I doubt very much that Germany and France, let alone Poland, are prepared for the consequences of a truly failed Ukraine, for a collapse of the Ukrainian state, for lawlessness or Russian-Mafia rule at the European Union’s eastern doorstep, as well as for the violence and crime that would result.
The means to prevent that kind of international catastrophe are right in front of us, in the form of Ukraine’s drone factories, the underground sea-drone laboratory, the tools now being designed to enable the Ukrainian army to beat a larger opponent—and also in the form of our own industrial capacity. The democratic world remains wealthier and more dynamic than the autocratic world. To stay that way, Ukraine and its Western allies have to persuade Russia to stop fighting. We have to win this war.
6 notes
·
View notes
Text
Self-Learning and Confidence: The Path to Advancement for Female Talent
AI has been a controversial hot topic in recent years. It has not only permeated every aspect of our lives but also had a profound impact on the way we work and what we do at work. Many people are experiencing anxiety about being replaced, and female software developer Jessica is no exception. However, running away from it is futile; instead, embrace it and use it to improve your efficiency and methods. Over the years, she has continuously embraced new things, constantly changing and being changed. After her transformation, she has become more confident and stronger.
Jessica, a female software developer from Dalian in the northeast of China. After graduating from university, she joined a software company and have been working there for eleven years now.

From Developer to Tester: The Shift in Work Approaches and Adaptation
The year 2019 was truly special for me. Before 2019, I was engaged in JAVA software development. It was in that year, after returning from maternity leave, that my company implemented a remote working mechanism. I remember that at that time, there were few opportunities for JAVA projects, but fortunately, I got a chance to work on an automation testing project. This not only marked the beginning of my testing career but also initiated my mode of juggling childcare with work.
When I first joined the new project, I was responsible for manual testing tasks. The work intensity was not very high, but the workload was quite saturated. One of the clients I interacted with was named Brain, and our main communication channels were email and Slack. Later, as the QA system continued to grow and expand, I was assigned to another project team (located in the UK). My work began to involve the field of automation testing, using Cypress to write test cases and being responsible for maintaining daily testing reports.
At that time, due to my poor English listening skills, I felt quite nervous when communicating with clients and even bought a translation device to ensure smooth communication. However, one is always trained through practice. Gradually, I became capable of conducting business discussions in English with clients, and my work ability greatly improved.
Transitioning from a developer to a tester was actually easier than I thought, but there are significant differences in work approaches. Writing code from a developer's perspective focuses on logic and code refactoring; whereas from a tester's perspective, it is crucial to ensure that the code is simple, clear, efficient, and concise. I remember once writing an automation test script that a client reviewed and loved for its structure, which significantly improved execution time by several times. However, he was concerned that colleagues might need more time to understand my code during future maintenance. This minor episode at work made me realize how important adaptability is in the workplace. Opportunities always favor those who can adapt quickly to new environments, which also helped me recognize the importance of AI in the future.
Self-Learning: Enhancing Your Own Value
During the period of working on automation testing, I felt that technical knowledge was not the most critical factor; more important was communication with clients. For example, at the beginning, I only used Java to write scripts (UI scripts), but the client used Cypress, a relatively lightweight language. I had never learned Cypress before and basically wrote code while looking up information. After writing a few cases, I could master the key syntax quite proficiently. After mastering UI automation, I started learning API automation, mainly using Postman to send requests, write execution scripts, and return data formats. In this part, I needed to communicate a lot with developers because I had to understand the types of returned formats and the parameters being transmitted.
Regarding business aspects, I needed to understand the entire system's business processes, which required a lot of time for summarizing and recording in the early stages. Any uncertainties had to be communicated with developers or other staff promptly. Initially, I recorded every module I worked on in a notebook, accumulating information bit by bit before summarizing it. Gradually, my understanding of the system's processes became clearer. This allowed me to quickly pinpoint issues during script execution and provide accurate solutions.
Another crucial aspect is regular summarization. Every month, I review all the tasks I've completed and list them out. For familiar areas, I can quickly go through them, but if there are new module areas, I conduct exploratory testing in those modules. This is also a method of understanding business.
With the accumulation of technical knowledge and deeper business insights, I can easily complete each task. My abilities have improved, and I have also gained recognition from clients.
Embracing AI to Enhance Work Efficiency
Since 2023, with the evolution of AI technology, during the process of working with clients, they have proposed using AI technologies, among which chatGPT is quite commonly used. In everyday tasks, issues such as code formatting, syntax problems, and element positioning can be resolved very swiftly by chatGPT, greatly enhancing my work efficiency. There's also Rakuten AI, which was still in the testing phase at that time and mainly used for writing and executing test cases using AI. It hasn't been widely adopted in our projects yet. However, from the demonstrations shown by clients, Rakuten AI's execution efficiency is truly impressive. Over ten years, we've evolved from manually writing test cases to now being able to generate many test cases at once with the help of AI, which has increased our efficiency several times over.
Throughout my career, there have been moments when I considered changing industries and times when I felt disappointed with my job. However, more often than not, I've maintained optimism, confidence, and focused on self-improvement every day. Many people have asked me if the emergence of AI makes me feel insecure about my career. I believe that as we work in the software industry, we shouldn't fear being replaced by AI. Instead, we should actively embrace AI, make good use of AI tools to enhance our work efficiency and abilities, and ensure that we remain irreplaceable.
0 notes
Text
Redefining Work: The Shift Towards Flexibility and Innovation
The Future of Work: Embracing Flexibility and Innovation Hello, dear followers! Today, I want to discuss the evolving nature of work and the increasing importance of flexibility and innovation in our professional lives. As we emerge from the disruptions of recent years, it is clear that the traditional 9-to-5 model is being redefined, not just by necessity but by a growing desire for a more adaptable work environment. The rise of remote work, gig economy roles, and flexible hours offers both individuals and businesses unprecedented opportunities. Employees are seeking a work-life balance that traditional office settings often hinder. From Scotland to the rest of the UK and beyond, organisations that embrace flexibility tend to have happier, more engaged staff—a fact that ultimately drives productivity and innovation. Moreover, the integration of technology into the workplace has amplified these changes. Digital tools facilitate collaboration across distances, allowing teams to work together seamlessly, regardless of their physical location. This shift not only enhances efficiency but also opens the door for diverse talent pools, which can enrich corporate culture and spur innovation. However, this transformation brings with it challenges that must be addressed. As we embrace flexible working arrangements, considerations around mental health, employee well-being, and the need for clear communication become paramount. Leaders must foster an environment where employees feel connected and valued, even when working remotely. In Scotland, many initiatives are emerging to support this new way of working. From upskilling programmes to resources that promote mental health in remote environments, there are numerous strategies being implemented to ensure that workers are well-equipped and supported in this changing landscape. As we explore these themes, I encourage you to share your thoughts. How has your work environment adapted to these changes? What do you think are the keys to successfully navigating the future of work? Your insights are invaluable as we engage in discussions on how we can collectively shape a more flexible, innovative workforce. Please share your thoughts in the comments below! Stay engaged and continue to advocate for a workplace that empowers individuals and fosters innovation! Warm regards, Alastair Majury *Perspectives Unbound* --- *Follow Alastair Majury for further discussions on the future of work, flexibility, and the principles that underpin a successful and innovative workforce.*
#FutureOfWork#Flexibility#Innovation#RemoteWork#GigEconomy#WorkLifeBalance#EmployeeEngagement#WorkplaceWellbeing#DigitalCollaboration#CorporateCulture#MentalHealth#Upskilling#Scotland#Adaptability#Productivity#FlexibleWorking
0 notes
Text
Vehicle Diagnostics and Communication
August 14, 2024
by dorleco
with no comment
Autonomous Vehicle Technology
Edit
Introduction
Vehicle communication and diagnostics are an integral part of modern car technology and are necessary for maintenance, performance tracking, and troubleshooting. These systems have significantly evolved with the creation of electronic control systems and the integration of cutting-edge technology into cars. Important aspects of automotive communication and diagnostics include the following:
1. On-board Diagnostics, or OBD:
OBD (On-Board Diagnostic): OBD is a standardized system that keeps track of an automobile’s engine and other vital systems. It comes in two versions: I and II. Introduced in the 1980s, OBD-I, or the first generation, was replaced as the industry standard by OBD-II, or the second generation, in the mid-1990s. OBD-II is more extensive since it uses standardized diagnostic connectors and codes.
2. Troubleshooting Diagnostic Codes (DTCs):
Codes for errors: When a fault is detected by an automobile’s onboard computer, a Diagnostic Trouble Code (DTC) is generated. These codes provide professionals with details about the specific scenario, allowing them to locate and resolve problems quickly.
3. Protocols for Communication:

In modern cars, the Controller Area Network, or CAN bus, is a commonly used communication protocol that allows various electronic control units (ECUs) to communicate with one another. It enables efficient communication and data sharing in real-time amongst different car systems.
4. Diagnostic Tools & Scan Tools:
OBD-II Scanners: Mechanics and auto owners use OBD-II scanners to extract DTCs, monitor live data, and execute various diagnostic procedures. To get data from the internal computer, these devices connect to the OBD-II port on the vehicle.
5. Remote diagnostics and telematics:
Telematics Systems: Many modern cars are equipped with telematics systems that allow for remote diagnosis and monitoring. The capacity of these systems to relay data to a central computer allows for real-time research of the health, performance, and maintenance needs of vehicles.
6. Manufacturer-Specific Diagnostics:
Manufacturer-only Systems: Certain manufacturers have proprietary diagnostic systems that might be able to meet or exceed OBD-II standards. It is often necessary to use specific hardware and software to perform extensive diagnostics on these systems.
7. Wireless Transmission:
Bluetooth and Wi-Fi: Wireless technologies like Bluetooth or Wi-Fi are used by certain diagnostic devices to link to an automobile’s onboard computer. As a result, doing diagnostics is now more versatile and convenient.
8. Advanced Driver Assistance (ADAS) Systems:
Sensor Diagnostics: Modern cars with advanced driver assistance systems (ADAS) use cameras and sensors to perform tasks like lane deviation warning and automated emergency braking. To guarantee optimal functioning, these sensors must be calibrated and monitored as part of the diagnostic processes for these systems.
9. Security online:
Security Issues: With automobiles becoming more networked, cybersecurity is becoming more important. Ensuring the security of automobile communication systems is crucial to prevent unauthorized access and potential cyber threats.
Advantages of Diagnostics and Vehicle Communication
Vehicle diagnostics and communication can benefit auto owners and mechanics in several ways. Here are a few key advantages:
1. Early Problem Identification
Vehicle communication and diagnostics enable the early detection of potential issues with the vehicle’s systems. By doing this, maintenance becomes proactive, and minor problems are prevented from becoming bigger, more costly ones.
2. Less Downtime
Quick and accurate diagnostics can reduce the time a vehicle takes without power. When problems are found and resolved quickly, vehicles spend less time off the road, which improves operational efficiency, especially in commercial fleets.
3. Cost-cutting Measures:
Finding and fixing issues early on may result in cost savings. If automobile owners address problems before they get worse, they can save spending a lot of money on repairs and replacements. Regular diagnostics can also lower operating costs by increasing fuel efficiency.
4. Increased Productivity:
Performance is increased by using diagnostics to ensure that every system in the vehicle is operating as effectively as possible. This includes engine efficiency, emission management, and general vehicle dynamics. More fuel efficiency and a more comfortable ride are two benefits of improved performance.
5. Emissions Management and Ecological Effects:
Enhanced diagnostics lead to better emission control. Verifying that the vehicle’s emission control systems are functioning properly helps to reduce harmful emissions, which is good for the environment, and to ensure that emission regulations are followed.
6. Telematics and remote monitoring:
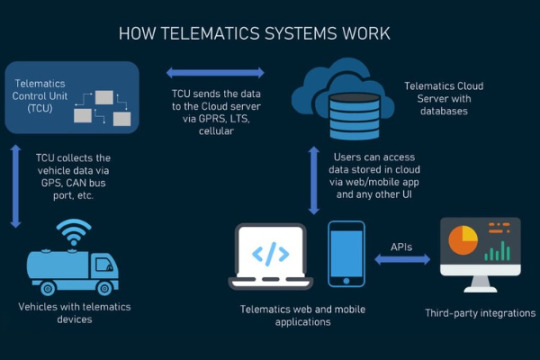
The performance and health of a vehicle can be remotely monitored thanks to telematics technology. They are commonly connected to diagnostics and vehicle communication. This is especially helpful for fleet management because it lets managers keep an eye on the condition of multiple vehicles without physically inspecting them all.
7. Making Decisions Based on Data:
Vehicle diagnostics and communication give a wealth of data that can be analyzed to aid in decision-making. Fleet managers, mechanics, and automobile owners can utilize this information to create maintenance schedules, map out the best routes, and make strategic decisions about their fleet of vehicles.
8. Contentment with Customers:
The ability of service staff to accurately and quickly diagnose and resolve issues affects customer satisfaction. Vehicle owners place a high value on timely and efficient maintenance, and better diagnostics can enhance the whole experience for customers.
Diagnostics and Vehicle Communication’s Drawbacks
Vehicle communication and diagnostics have many benefits, but they also have some drawbacks and challenges.
1. Technical expertise and complexity:
Advanced diagnostics systems may require specific technical knowledge to diagnose and fix issues. This complexity could be difficult for individuals without the necessary knowledge or abilities, leaving them dependent on skilled mechanics or technicians.
2. Equipment and Training Costs:
Acquiring high-quality diagnostic equipment can be expensive, and training employees on how to use and interpret the equipment appropriately also adds to the costs. For individual vehicle owners or smaller auto repair shops, this might be a significant expense.
3. Compatibility Problems:
Compatibility problems might arise, especially in older cars or with aftermarket items. Some diagnostic methods and tools may not be completely compatible with every make and model, which may limit their applicability in specific situations.
4. Cybersecurity Risks:
Risks related to cybersecurity are probably going to rise as cars get more and more networked. Vulnerabilities in communication systems could be exploited by hackers, putting vehicle safety and data security at risk. To protect automotive communication systems, manufacturers need to implement robust cybersecurity measures.
5. Excessive Dependence on Technology:
An over-reliance on diagnostic tools could lead to a loss of interest in traditional troubleshooting methods. When technicians rely too heavily on automatic diagnostic results, they run the danger of overlooking less common or complex issues that require a deeper understanding of vehicle systems.
6. Privacy Issues:

Telematics systems raise privacy concerns since they are often integrated with vehicle diagnostics and communication. Regularly monitoring an automobile’s location and performance could be perceived as a privacy infringement; thus, laws and transparent channels of communication are required to alleviate these concerns.
7. Limited Capacity for Self-Help:
Even though many consumers may purchase OBD-II scanners, more advanced diagnostics typically require specific hardware and software. This increases the difficulty level for car owners to perform various diagnostic procedures themselves, hence increasing their reliance on professional services.
8. Rapid obsolescence of technology:
New technologies are being introduced regularly, and the automobile industry is changing quickly. The rapid pace of development can lead to the obsolescence of diagnostic equipment, posing a challenge for professionals and repair shops to remain current with the latest techniques and tools.
Conclusion:
To sum up, car diagnostics and communication are essential parts of contemporary automobile technology, offering a host of advantages as well as some drawbacks. The progression of OBD-II systems from basic to sophisticated, along with telematics and remote monitoring features, has completely changed the way cars are serviced and maintained. Early problem identification, less downtime, financial savings, optimal performance, and increased safety are among the benefits. These technologies guarantee regulatory compliance, improve consumer satisfaction, and enable data-driven decision-making.
Ongoing industry attention is necessary, nevertheless, because of obstacles including the complexity of diagnostic systems, the accompanying costs of training and equipment, compatibility problems, and cybersecurity dangers. The dynamic nature of this sector is further highlighted by privacy concerns, restricted do-it-yourself skills for sophisticated diagnostics, and the potential for quick technical obsolescence.
It will be essential to solve these issues through standardization, enhanced cybersecurity protocols, and easily available training as the automotive industry innovates more. A more effective, secure, and long-lasting automotive ecosystem will result from finding a balance between maximizing the benefits of car communication and diagnostics and minimizing any potential downsides. Future developments should bring about cars that are connected, maintained, and able to adapt to changing consumer demands as well as those of the automotive industry at large.
Check for our exciting list of (Vehicle Control Units) VCUs and the useful system Engineering services we provide. connect with us at [email protected]
#EVSoftwareserviceprovider#vehiclecommunication#vehiclecontrolunit#VCU#EVSoftware#evCODE#ADASCode#VCUSupplier#VCUManufacturer
0 notes
Text
Oh boy
(It's not that interesting, it's just a personal rant).
(BUT - )
Before I had a car, when I was living in a larger city, the bus or walking was the only way I could do errands and I was fortunate enough to live in a city that at least had a functioning bus system, unlike the town I'm living in now. Driving in a busy city is not only difficult but exhausting, even more tiring than regular driving, and taking the bus really didn't push me back that far in terms of time. It was really nice not to have to drive places, and even if I'd had a car I would have chosen to take the bus, not only to save on personal fuel costs but because even the added inconvenience of getting to the bus stops and taking a longer time to do an errand weigh much less than how much I fucking loathe driving and paying for car costs.
I live in a much smaller town now, with no good public transport system; it's either you have a car or you bike it or you don't leave home.
Because of traffic I can get to the grocery store on a bike in less time than it takes to drive there, and it costs me absolutely nothing. I really, really wish that our town had a public transit system because there are so many communities within our town that are largely cut off from necessities because of how remote they are, and there are a huge number of people who cannot afford cars or can't drive because of license issues or disabilities, and therefore have harder times holding down jobs or taking care of themselves if they don't have a friend or family member who can drive for them.
When cities are designed with only car culture in mind, it limits what people can do within that area and who can do it. Cars are considered more convenient on the whole simply because we've designed our cities to be unfriendly toward any other form of transport, which is stupid because those forms of transport take up significantly less space and waste less energy. If you assume that a bus will hold ~50 people, then one bus can eliminate around eleven cars from the road, if those cars are each carrying four people. That equals less traffic, which equals less gas, less idling, and less carbon emissions. It's been proven for a while that buses and trains are more energy-efficient and environmentally healthy on the whole than cars.
AND it's cheaper! Not only are you having to pay insurance and taxes personally for a car, but you have to buy gas as well. My car costs about ~$30 to fill up, at the current gas prices. If I drive to work and errands then I have to fill up about once a week. That's $120 a month, and $1500 a year. Let's say that insurance, which is required by law, is around $700 per year. The majority of people in the USA have their own vehicle. That's a lot of money per person per year. That's not even counting repair costs, monthly car payments, etc.
A 30-day bus pass can cost anywhere from $40-$100, which is still cheaper than buying gas, and it doesn't have a limit of how many times you can ride during that thirty days. Also, most public transits will have discounts for students, low-income folks, disabled or elderly people, and even free fare for certain passengers at certain times.
Reliable public transit is people-friendly, environmentally-friendly, and economy-friendly. I'm not saying that cars aren't convenient for some things, because they are, but we've done this to ourselves in making our cities and towns so unwelcome toward any other form of transit, to the point where we no longer see or understand how daily life could be improved for so many people if we had popularized reliable transport systems that were not so reliant on individual consumption.
The anti-car culture on this website is so fucking annoying. Like, sorry I want to be able to get around without having to spend two hours taking three buses. Sorry I want to be able to go grocery shopping in the winter without having to lug heavy bags home through the snow on a fucking bike
#you got me started on trains and buses#why did you get me started on trains and buses#I know so many people who would have an easier time holding a job if we had a real fucking bus system here#I hate cars and I hate having to be so reliant on my car#even as an introvert i'd rather take public transport SO BAD#yall are making me look up statistics on my day off#I have a wonderful idea for a train system in my town but nobody ever wants to hear it#and another butlerchryslerdogdgejeepram dealership just opened up as if people really need to be spending upwards of $20'000 on a new car
32K notes
·
View notes
Text
How do I design a creative interior office space?
Designing a creative interior office space is essential for fostering innovation, collaboration, and productivity. A well-thought-out office design can inspire employees, enhance morale, and reflect your company’s culture. Here are some strategies to create an interior office space that sparks creativity and supports a dynamic work environment.
Understanding Your Needs
Before diving into design elements, it’s crucial to understand the specific needs of your team and business. Conduct surveys or hold meetings to gather input from employees about their preferences and requirements. This will help ensure the design meets the practical and creative needs of your team.
Open and Flexible Layouts
An open and flexible layout is key to promoting collaboration and creativity in an interior office space. Here are some ideas:
Open Workspaces: Create open work areas with communal tables or desks to encourage spontaneous discussions and teamwork.
Flexible Furniture: Use modular furniture that can be easily reconfigured for different purposes. This flexibility allows for quick changes to suit various projects and team sizes.
Breakout Spaces: Designate areas for informal meetings and brainstorming sessions. These can include comfortable seating arrangements, whiteboards, and writable walls for jotting down ideas.
Vibrant and Inspiring Aesthetics
The visual appeal of an interior office space greatly influences creativity. Use vibrant colors, artwork, and decor to create an inspiring environment:
Color Scheme: Incorporate bold and stimulating colors like blues, greens, and yellows, which are known to boost creativity and energy. Use these colors in accent walls, furniture, and decor items.
Artwork and Murals: Display artwork, murals, or graffiti that reflect your company’s culture and values. Art can serve as a conversation starter and provide visual stimulation.
Branding Elements: Integrate branding elements such as logos, company slogans, and mission statements into the design. This reinforces your brand identity and motivates employees.
Natural Elements
Bringing elements of nature into your interior office space can enhance creativity and well-being. Consider the following:
Plants and Greenery: Incorporate a variety of indoor plants to improve air quality and create a calming atmosphere. Vertical gardens and green walls can make a bold statement.
Natural Light: Maximize natural light by positioning workstations near windows and using glass partitions. Natural light has been shown to improve mood and productivity.
Natural Materials: Use natural materials like wood, stone, and bamboo in furniture and finishes to create a warm and inviting environment.
Technology Integration
Incorporating technology into your interior office space is essential for a modern and efficient workplace. Here are some tech ideas:
Interactive Screens: Use interactive screens and digital whiteboards for brainstorming and presentations. These tools make it easy to share and develop ideas.
Wireless Technology: Implement wireless charging stations and high-speed Wi-Fi to support seamless connectivity and mobility.
Virtual Collaboration Tools: Equip meeting rooms with video conferencing systems and collaboration software to connect with remote team members and clients.
Ergonomic Design
Ensuring comfort through ergonomic design is crucial for maintaining creativity and productivity. Focus on these elements:
Ergonomic Furniture: Invest in adjustable chairs and desks that support proper posture and reduce strain. This helps employees stay comfortable during long work hours.
Break Areas: Designate areas where employees can take breaks and relax. Comfortable seating, games, and snacks can help re-energize your team.
Personalization and Flexibility
Allowing employees to personalize their workspaces can boost morale and creativity. Here are some ways to achieve this:
Personal Spaces: Encourage employees to decorate their desks with personal items, photos, and plants.
Adjustable Workstations: Provide workstations that can be easily adjusted to individual preferences and tasks.
Conclusion
Designing a creative interior office space involves a balance of aesthetics, functionality, and employee well-being. By focusing on open and flexible layouts, vibrant aesthetics, natural elements, technology integration, ergonomic design, and personalization, you can create an environment that fosters creativity and supports your team’s productivity. Implement these strategies to transform your office into a dynamic and inspiring space that reflects your company’s culture and drives innovation. One can achieve these by getting in touch with the renowned design and build firm such as Flipspaces, who can help you with the same.
0 notes
Text
7 Reasons Why Managed IT Services are Vital for Local Businesses
Having worked in IT for more than 15 years, I can say from personal experience how important managed IT services are to today's businesses.
With IT managed services, you give your IT tasks to a specialized IT service provider, called an IT MSP in the tech world. This partnership covers a wide range of services, from IT support to IT cybersecurity.
All of these are designed to make your systems run smoothly and safely.

Local Businesses and Managed IT Services
Local businesses often have trouble keeping up with the technological needs they need to stay competitive in this digitalized world.
This is where IT managed services play their role. These services are very important for keeping networks connected, protecting against cyber risks, and updating systems.
They not only make operations more efficient, but they also cut down on downtime and the chance of unexpected expenses by a large amount.
Key Features
It is very important to pick the right IT Managed Service Provider. A trusted partner should offer full IT consulting to help you find solutions that fit your business needs.
Remote IT support is a must-have for quick fixes and constant system monitoring, so look for companies that provide you with these services.

Strong IT Cybersecurity services are another essential component that protects your company and its data from new threats.
Lastly, a reliable IT support company will not only meet your IT needs but also anticipate them through good communication and proactive service.
Managed IT Services Importance for Local Businesses
IT services are essential for local businesses in a way that provides complete IT support for them to grow in this competitive digital world. Here are some reasons why local businesses need IT services.
Cybersecurity: Local businesses need IT MSP because they offer full cybersecurity measures such as detecting threats, encrypting data, and regular security checks. By keeping an eye on systems and making sure data is protected, these services protect private data, lower risks, and keep up with the latest security standards to stop cyber threats before they do damage to the system.
Cloud Computing: IT Managed services are at the heart of how cloud computing is changing the way businesses work. They make moving to the cloud easier by planning and carrying out the move, making sure it goes smoothly with little trouble. Once you move your data to the cloud, managed services will keep it running at its best and keep your data safe. They also have disaster recovery plans that allow for quick recovery and business stability in case of data loss or other disasters, which cuts down on downtime.
Data Backup and Recovery: Backing up and recovering data is an important part of IT plans for local businesses. Managed IT services make sure that backups are done regularly and safely to protect against hardware issues, cyber threats, and human error. If you lose data, these services quickly recover it, so your business doesn't have to stop running. Data loss can be prevented by taking steps such as training employees and using advanced security measures.
Enhancing Network Management: Managed Services are highly skilled at managing networks in a way that is essential for businesses. This is done by constantly watching the network and finding and fixing problems before they happen. Robust security measures keep networks safe from cyber risks, keeping data and systems safe. expert troubleshooting quickly fixes problems, reducing downtime and keeping business running smoothly.
Proactive IT Maintenance: To stop problems before they happen Managed IT services take steps to keep your systems running easily by proactively preventing problems before they happen. This includes making sure that your software and tools are always up-to-date and safe with regular system changes. A proactive approach to maintaining your systems can help you find and fix possible issues before they become big issues, which keeps your business running smoothly and reduces downtime.
IT Strategy Planning: For long-term success, it's important that your IT plan fits with your business goals. IT Managed services give you easy access to expert IT advice that can help you create an IT plan that helps your business grow. This includes planning for your IT systems over the long run to make sure it can support your growth in the future. Managing the budget is another important part of planning an IT strategy. With managed IT support, you can keep your IT budget in check and make sure that your investments are getting the most value while staying within your budget.
Remote IT Support: Local businesses can benefit in many ways from remote IT help. It's quick and easy, and you can get the help you need without having to wait for someone to come to your location. Managed IT services respond quickly to problems and fix them quickly and effectively to keep downtime to a minimum. Another big benefit of online IT help is that it saves you money. It cuts down on the need for on-site visits, which saves money on travel costs.
Conclusion
Managed IT Services can be very advantageous for Local businesses by giving benefits such as better protection, cloud control, data backup, and preventive IT maintenance.
You can keep your business safe, running smoothly, and ready for growth by working with a trustworthy IT MSP.
Get IT managed services right now to keep your business safe and help it succeed in the long run.
Reference: https://vocal.media/beat/7-reasons-why-managed-it-services-are-vital-for-local-businesses
#managed it solutions#it services#it support#managed it services#internet#technology#business growth#networking equipment#small business#it consulting
0 notes
Text
How do I create a flexible workspace with office interior solutions?
Creating a flexible workspace is essential in today’s dynamic business environment. Flexibility in the office allows for adaptability to changing needs, promotes collaboration, and enhances productivity. Here are some effective office interior solutions for designing a flexible workspace that meets the evolving demands of modern businesses.
1. Modular Furniture
One of the most practical office interior solutions for creating a flexible workspace is modular furniture. This type of furniture can be easily rearranged and reconfigured to accommodate different work styles and tasks. Modular desks, storage units, and seating can be combined in various ways to create a layout that suits the current needs of the office. This flexibility allows businesses to quickly adapt to changes in team size, project requirements, and workflow.
2. Movable Partitions
Movable partitions are another excellent solution for creating a flexible workspace. These partitions can be easily moved or retracted to open up or close off areas as needed. They allow for the quick transformation of an open space into smaller, private areas for meetings or focused work. Movable partitions give employees the freedom to adjust their environment to suit their activities, fostering both collaboration and concentration.
3. Multi-Purpose Spaces
Designing multi-purpose spaces is a key strategy in creating a flexible workspace. These areas can serve various functions, such as meeting rooms, breakout areas, or event spaces, depending on the need. Equip these spaces with versatile furniture, such as foldable tables and stackable chairs, that can be easily rearranged. Multi-purpose spaces ensure that the office remains adaptable and can be utilized efficiently for different activities.
4. Ergonomic Furniture
Ergonomic furniture is an important office interior solution that supports flexibility and employee well-being. Adjustable chairs, sit-stand desks, and ergonomic accessories allow employees to customize their workstations for maximum comfort and productivity. Ergonomic furniture reduces physical strain and promotes better health, enabling employees to work comfortably in various positions and configurations.
5. Technology Integration
Integrating advanced technology into the office is essential for creating a flexible workspace. Wireless charging stations, high-speed internet, and smart conference systems support a seamless and efficient workflow. Use cloud-based collaboration tools and video conferencing systems to facilitate remote work and virtual meetings. Technology integration ensures that employees can stay connected and productive, regardless of their location.
6. Open Plan Layouts
Open plan layouts are popular office interior solutions for fostering a flexible workspace. By minimizing walls and partitions, open layouts create a spacious and adaptable environment. This layout encourages spontaneous collaboration and communication among employees. To balance the open plan with the need for privacy, incorporate acoustic solutions and designated quiet zones where employees can focus without distractions.
7. Biophilic Design Elements
Incorporating biophilic design elements into the workspace can enhance flexibility and well-being. Natural light, plants, and organic materials create a calming and inspiring atmosphere. Biophilic design improves air quality and reduces stress, making the office a more pleasant place to work. Flexible placement of plants and natural elements allows for easy reconfiguration of the space as needed.
8. Collaborative Zones
Creating designated collaborative zones is an effective office interior solution for a flexible workspace. These zones can be equipped with large tables, comfortable seating, and collaboration tools to support group activities. Designate specific areas for brainstorming, project planning, or informal meetings. Collaborative zones ensure that employees have the resources and environment needed to work together effectively.
9. Storage Solutions
Efficient storage solutions are crucial for maintaining a flexible workspace. Mobile storage units, wall-mounted shelves, and under-desk storage options keep the office organized and clutter-free. Easy access to necessary materials and equipment allows for quick reconfiguration of the workspace. Efficient storage solutions ensure that employees can easily adapt their environment to suit their needs.
10. Personalization
Allowing employees to personalize their workspaces is a simple yet effective office interior solution for flexibility. Personal touches, such as family photos, plants, and unique decor, make employees feel more comfortable and invested in their work environment. Personalization encourages employees to take ownership of their space and tailor it to their preferences, enhancing satisfaction and productivity.
In conclusion, creating a flexible workspace requires thoughtful office interior solutions that prioritize adaptability and employee well-being. Modular furniture, movable partitions, and multi-purpose spaces offer practical ways to reconfigure the office layout as needed. Ergonomic furniture, technology integration, and open plan layouts enhance comfort and connectivity. Incorporating biophilic design elements, collaborative zones, efficient storage solutions, and personalization further support a dynamic and productive work environment. By implementing these office interior solutions, businesses can create a flexible workspace that meets the evolving needs of their employees and operations. One can achieve these by getting in touch with the renowned design and build firm such as Flipspaces, who can help you with the same.
0 notes
Text
How do I integrate technology in office interiors in Delhi?
Title: Tech-Savvy Spaces: Integrating Technology in Office Interiors in Delhi
In the bustling business hub of Delhi, staying ahead of the curve often means embracing the latest technological advancements. When it comes to office interiors, integrating technology isn't just about keeping up with trends—it's about enhancing efficiency, productivity, and the overall work experience for employees. From smart lighting systems to interactive displays, there are countless ways to incorporate technology seamlessly into office interiors in Delhi. Let's explore some innovative strategies for integrating technology into the workplace.
Smart Lighting Solutions: Lighting plays a crucial role in setting the ambiance and mood of a workspace. In Delhi's fast-paced environment, where natural light may be limited, investing in smart lighting systems can significantly enhance the office environment. Consider installing sensors that adjust lighting levels based on occupancy and natural light conditions, maximizing energy efficiency and employee comfort. Additionally, programmable LED lighting fixtures can create dynamic lighting effects that promote productivity and well-being.
Interactive Digital Displays: Replace traditional whiteboards and flip charts with interactive digital displays that enable seamless collaboration and presentation. These interactive screens allow employees to share ideas, annotate documents, and brainstorm in real-time, whether they're in the office or participating remotely. In Delhi, where remote work and virtual meetings are increasingly common, interactive displays facilitate communication and collaboration among dispersed teams, enhancing efficiency and productivity.
Integrated Audiovisual Systems: Create immersive meeting experiences with integrated audiovisual systems that deliver high-quality sound and video conferencing capabilities. Equip conference rooms and meeting spaces with state-of-the-art audiovisual equipment, including HD projectors, video walls, and surround sound systems, to facilitate engaging presentations and discussions. With the rise of hybrid work models in Delhi, where employees may be working from both home and office, reliable audiovisual systems are essential for seamless communication and collaboration.
Wireless Charging Stations: Keep employees powered up and connected with wireless charging stations integrated into office furniture and workstations. In Delhi, where smartphones and other devices are essential tools for staying connected and productive, providing convenient charging options can enhance employee satisfaction and productivity. Incorporate wireless charging pads into desks, conference tables, and communal areas to ensure that employees can easily charge their devices throughout the workday.
Smart Furniture and Accessories: Upgrade office furniture and accessories with smart features that enhance comfort, convenience, and functionality. Consider investing in ergonomic chairs with adjustable settings, height-adjustable desks, and monitor arms that promote proper posture and reduce the risk of musculoskeletal issues. In Delhi's competitive business landscape, where employee health and well-being are top priorities, providing ergonomic workstations demonstrates a commitment to employee satisfaction and productivity.
IoT-Enabled Environmental Controls: Create a comfortable and energy-efficient workspace with IoT-enabled environmental controls that optimize temperature, humidity, and air quality. Install smart thermostats, occupancy sensors, and air quality monitors that automatically adjust environmental conditions based on occupancy and user preferences. In Delhi, where extreme temperatures and air pollution can impact employee comfort and productivity, IoT-enabled environmental controls help create a healthy and productive work environment.
Virtual Reality and Augmented Reality: Explore the potential of virtual reality (VR) and augmented reality (AR) technologies to enhance employee training, design visualization, and customer engagement. In Delhi's diverse business landscape, where innovation and creativity are highly valued, incorporating VR and AR into office interiors can differentiate your business and provide a competitive edge. Whether it's using VR for immersive training simulations or AR for interactive product demonstrations, these technologies offer exciting opportunities to transform the workplace experience.
By integrating technology into office interiors in Delhi, businesses can create modern, efficient, and engaging work environments that foster collaboration, productivity, and innovation. Whether it's leveraging smart lighting systems, interactive displays, or IoT-enabled environmental controls, embracing technology enhances the office experience for employees and reinforces Delhi's reputation as a dynamic and forward-thinking business hub. One can achieve these by getting in touch with the renowned design and build firm such as Flipspaces, who can help you with the same.
0 notes
Text
what server address do i use for vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what server address do i use for vpn
VPN server address format
VPN server addresses follow a specific format designed to facilitate secure and efficient communication between users and the VPN server. Typically, these addresses consist of a combination of numbers and periods, resembling something like this: XXX.XXX.XXX.XXX. Each set of Xs represents a numerical value ranging from 0 to 255, forming what is known as an IP address.
The most common format for VPN server addresses is IPv4, which uses 32 bits to create a unique address. This format allows for approximately 4.3 billion unique addresses, though the rapid expansion of internet-connected devices has led to concerns about IPv4 address exhaustion. To address this issue, IPv6 was introduced, which uses 128 bits and provides significantly more unique addresses.
When connecting to a VPN server, users input the server's IP address into their VPN client software or device settings. This initiates the process of establishing a secure connection between the user's device and the VPN server.
In addition to the IP address, VPN server addresses may also include other identifiers, such as domain names or subdomains. These can make it easier for users to remember and access the server, especially if the IP address is lengthy or difficult to recall.
Overall, the format of VPN server addresses plays a crucial role in enabling secure and reliable communication between users and VPN servers. By understanding this format, users can effectively configure their VPN connections to ensure privacy, security, and access to restricted content.
Finding VPN server address
To find a VPN server address, you first need to understand what a VPN is. A Virtual Private Network (VPN) encrypts your internet connection and routes it through a server in a location of your choice, providing you with online privacy and security. VPN servers are the backbone of this technology, as they enable you to mask your real IP address and browse the web anonymously.
There are several ways to find a VPN server address. The most common method is by using the VPN provider's official website or application. Once you have signed up for a VPN service, you can usually find a list of available servers along with their addresses. Simply choose the server location you want to connect to, and the VPN software will then handle the rest.
Another way to find a VPN server address is by contacting the customer support of your VPN provider. They can provide you with a list of servers and their corresponding addresses, ensuring you have the most up-to-date information.
Additionally, you can explore online forums and community websites dedicated to VPNs. Users often share their experiences and recommend specific servers that work best for various purposes, such as streaming, gaming, or general browsing. This collective knowledge can help you discover new server addresses that may enhance your VPN experience.
In conclusion, finding a VPN server address is a straightforward process that can be done through the VPN provider's website, customer support, or online communities. By selecting the right server location, you can enjoy enhanced privacy, security, and unrestricted access to online content.
VPN server address types
VPN (Virtual Private Network) server addresses come in different types, each serving specific purposes in ensuring secure and private internet connections. Understanding these address types is crucial for selecting the most suitable VPN server for your needs.
Static IP Addresses: These addresses remain constant, providing consistency for users accessing VPN services. Static IPs are ideal for businesses and individuals requiring stable connections for tasks such as remote access to corporate networks or hosting services.
Dynamic IP Addresses: Unlike static IPs, dynamic addresses change each time a user connects to the VPN server. They are commonly used by VPN providers to optimize server resources and enhance user anonymity. Dynamic IPs are beneficial for users seeking privacy and variety in their online activities.
Shared IP Addresses: Shared IPs are used by multiple users simultaneously, making it challenging for external parties to trace online activities back to individual users. This enhances anonymity and security by blending user traffic with that of others on the same server.
Dedicated IP Addresses: Reserved for exclusive use by a single user, dedicated IPs offer advantages such as faster speeds and greater control over online activities. They are preferred by businesses requiring secure access to specific online services or maintaining consistent access to restricted content.
Virtual IP Addresses: Virtual IPs are internal addresses assigned by VPN servers to devices within a private network, enabling secure communication between connected devices. They are commonly used in enterprise VPN setups to facilitate secure data exchange within corporate networks.
By understanding the different types of VPN server addresses, users can make informed decisions when selecting VPN services that align with their specific requirements for security, privacy, and online accessibility. Whether prioritizing anonymity, speed, or dedicated access, choosing the right VPN server address type is essential for maximizing the benefits of VPN technology.
Setting up VPN server address
Setting up a VPN server address is essential for ensuring secure and private internet connections. A VPN, or Virtual Private Network, allows users to establish a secure connection to another network over the internet. When setting up a VPN server address, there are a few key steps to follow to ensure a smooth and secure connection.
First and foremost, it is important to choose a reliable VPN service provider that offers a secure and encrypted connection. Look for providers that offer a wide range of server locations and protocols to choose from. Once you have selected a VPN service provider, you will need to set up the server address on your device.
Most VPN service providers offer easy-to-follow instructions on how to set up the server address on various devices, including computers, smartphones, and routers. Typically, this involves downloading and installing the VPN client software, entering the server address provided by the VPN service, and configuring any additional settings as needed.
After setting up the VPN server address on your device, you can connect to the VPN server to encrypt your internet traffic and protect your online privacy. By using a VPN server address, you can browse the internet securely, access geo-restricted content, and protect your sensitive information from prying eyes.
In conclusion, setting up a VPN server address is a simple and effective way to enhance your online security and privacy. By following the steps provided by your VPN service provider, you can establish a secure connection and enjoy a safer online experience.
Troubleshooting VPN server address
When it comes to troubleshooting a VPN server address, there are a few common issues that users may encounter. A VPN, or Virtual Private Network, allows users to securely connect to a private network over the internet. If you are experiencing problems with your VPN server address, here are some steps you can take to troubleshoot the issue.
One of the most common issues with a VPN server address is incorrect configuration settings. Make sure that you have entered the server address correctly in your VPN client software. Double-check for any typos or mistakes in the address.
Another common problem is a connection issue with the VPN server itself. This could be due to server maintenance, network congestion, or a temporary outage. Try connecting to a different server location to see if the issue persists.
It is also important to ensure that your internet connection is stable and reliable. A weak or unstable connection can cause problems with the VPN server address. Try resetting your modem or router and reconnecting to the VPN.
If you are still experiencing issues, you may need to contact your VPN service provider for further assistance. They can help troubleshoot the problem and provide guidance on resolving any issues with the server address.
In conclusion, troubleshooting a VPN server address may require checking configuration settings, testing different server locations, ensuring a stable internet connection, and seeking help from your VPN service provider if needed. By following these steps, you can resolve common VPN server address issues and enjoy a secure and private connection to the internet.
0 notes
Text
do i need to proxy after open vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i need to proxy after open vpn
Proxy server necessity
A proxy server serves as an intermediary between a user and the internet. It acts as a gateway, allowing you to browse the web while keeping your identity hidden. Proxy servers are becoming increasingly essential in the digital age for various reasons.
One of the primary reasons for using a proxy server is to enhance online security and privacy. By routing your internet traffic through a proxy server, your IP address is masked, making it difficult for websites and online services to track your online activities. This added layer of anonymity is crucial for safeguarding your sensitive information and protecting yourself from potential cyber threats.
Moreover, proxy servers are instrumental in bypassing geo-restrictions and accessing region-locked content. For instance, if certain websites or streaming services are not available in your country, you can use a proxy server located in a different region to circumvent these restrictions and enjoy unrestricted access to content from anywhere in the world.
In addition to security and accessibility benefits, proxy servers also facilitate faster internet browsing speeds by caching frequently accessed web pages. This not only saves bandwidth but also improves loading times, providing a smoother and more efficient browsing experience for users.
In conclusion, the necessity of using a proxy server in today's digital landscape cannot be understated. Whether for enhancing security, accessing geo-blocked content, or improving browsing speeds, proxy servers offer a myriad of benefits that cater to the diverse needs of internet users.
OpenVPN function
OpenVPN is a popular open-source software application that implements virtual private network (VPN) techniques for creating secure point-to-point or site-to-site connections in routed or bridged configurations. It allows users to securely connect to a private network from a remote location over the internet.
One of the key functions of OpenVPN is to provide a secure tunnel for data transmission. This is achieved by encrypting the data packets using various encryption protocols such as SSL/TLS for secure communication. OpenVPN offers a high level of security and privacy by ensuring that all data passing through the VPN tunnel is encrypted, making it virtually impossible for third parties to intercept or decipher the data.
Additionally, OpenVPN provides authentication mechanisms to ensure that only authorized users can access the VPN network. Users can be required to provide a username and password, or use digital certificates for authentication. This helps prevent unauthorized access and enhances the overall security of the VPN connection.
Another important function of OpenVPN is its flexibility and compatibility with various operating systems and devices. OpenVPN supports a wide range of platforms including Windows, macOS, Linux, iOS, and Android, making it accessible to a diverse user base.
Overall, OpenVPN is a powerful and versatile tool for establishing secure connections over the internet. Its robust security features, authentication mechanisms, and cross-platform compatibility make it an ideal choice for individuals and organizations looking to ensure the confidentiality and integrity of their data transmissions.
Internet privacy protection
Internet privacy protection is a crucial concern in today's digital age. With the vast amount of personal information being shared online, it is more important than ever to safeguard our privacy and ensure that our data is not misused or compromised. There are several ways to protect your internet privacy and keep your personal information secure.
One of the most effective ways to enhance internet privacy protection is by using strong, unique passwords for each online account. This helps prevent unauthorized access to your accounts and keeps your personal information safe from hackers. Additionally, enabling two-factor authentication adds an extra layer of security by requiring a secondary form of verification to log in.
Using a virtual private network (VPN) is another valuable tool for enhancing internet privacy protection. A VPN encrypts your internet connection, making it difficult for third parties to intercept your data. This is especially important when using public Wi-Fi networks, as they are more susceptible to security breaches.
Regularly updating your devices and software is also essential for maintaining internet privacy protection. Software updates often contain security patches that fix vulnerabilities that cybercriminals could exploit to gain access to your data.
Lastly, being mindful of the information you share online can significantly impact your internet privacy protection. Avoid oversharing personal details on social media platforms and be cautious when interacting with unfamiliar websites or emails requesting sensitive information.
In conclusion, prioritizing internet privacy protection is essential for safeguarding your personal information in today's digital landscape. By implementing these strategies and staying vigilant, you can better protect your online privacy and reduce the risk of falling victim to cyber threats.
Proxy server vs
Proxy Server vs VPN: Understanding the Differences
In the realm of online privacy and security, two common tools often come up in discussions: proxy servers and VPNs (Virtual Private Networks). While both serve the purpose of masking a user's IP address and providing anonymity, they differ in several key aspects.
A proxy server acts as an intermediary between a user's device and the internet. When a user sends a request to access a website through a proxy server, the server forwards the request on behalf of the user, thereby masking the user's IP address. However, proxy servers only provide limited anonymity and security, as they do not encrypt the data transmitted between the user's device and the internet. Additionally, proxies may not effectively bypass geo-restrictions or censorship imposed by certain websites or governments.
On the other hand, VPNs offer a more comprehensive solution for online privacy and security. In addition to masking the user's IP address like a proxy server, VPNs encrypt all data transmitted between the user's device and the internet. This encryption ensures that even if the data is intercepted, it cannot be deciphered by unauthorized parties. Furthermore, VPNs provide access to a network of servers located in various countries, allowing users to bypass geo-restrictions and access content that may be blocked in their region.
While both proxy servers and VPNs can help protect user privacy and security online, VPNs offer a more robust solution due to their encryption capabilities and ability to bypass geo-restrictions. However, the choice between the two ultimately depends on the user's specific needs and preferences.
Secure online browsing
In an age where cyber threats and online privacy invasions are on the rise, ensuring secure online browsing has become more critical than ever. Secure online browsing refers to practicing safe and secure habits while navigating the vast world of the internet to protect personal information and data from falling into the wrong hands.
One essential step towards secure online browsing is using a reliable and up-to-date antivirus software. This helps to shield your device from malware, viruses, and other cyber threats that may compromise your online security. Additionally, keeping your operating system, browser, and other software updated with the latest security patches is crucial in safeguarding against vulnerabilities that cybercriminals could exploit.
Another effective measure to enhance online security is utilizing a virtual private network (VPN). A VPN creates a secure and encrypted connection between your device and the internet, making it harder for hackers to intercept your data. By masking your IP address and encrypting your internet traffic, a VPN adds an extra layer of security and anonymity while browsing online.
Furthermore, practicing good browsing habits such as avoiding clicking on suspicious links, being cautious when sharing personal information online, and enabling two-factor authentication where possible can significantly reduce the risk of falling victim to cyber threats.
In conclusion, prioritizing secure online browsing is essential in safeguarding your digital presence and protecting your sensitive information from potential threats. By implementing these proactive measures and staying vigilant while browsing the internet, you can enjoy a safer and more secure online experience.
0 notes