#how to change the wifi password on my router
Explore tagged Tumblr posts
Link
If your home or office has spots where your Wi-Fi connection is weak, a D-Link extender can strengthen that signal and cover more area. But for safety, you should change the wireless security password for your D-Link range extender every so often.
#D LINK EXTENDER#D'LINK DEFAULT WIFI PASSWORD#D'LINK ROUTER LOGIN PASSWORD CHANGE#D'LINK EXTENDER LOGIN#D'LINK RANGE EXTENDER SETUP#D-LINK POCKET WIFI CHANGE PASSWORD#D-LINK ROUTER DEFAULT PASSWORD NOT WORKING#DLINK ROUTER PASSWORD RESET#HOW DO I FIND MY D-LINK ADMIN PASSWORD#HOW TO CHANGE D'LINK ROUTER NAME AND PASSWORD#HOW TO CHANGE WIFI PASSWORD DLINK THROUGH MOBILE#HOW TO RESET D LINK EXTENDER
0 notes
Text
Zorana's Guide To The Poke Classic Network!
Do you want to connect your DS Pokemon games to the internet long after Nintendo shut down their servers? Do you wish to trade and battle with your internet friends who play the gen 4 and 5 Pokemon games? Do you have a desire to watch and upload battle videos like you used to years ago?
If you said yes to any of these questions then I have the thing for you!
The Poke Classic Network!
This is a fan server for Pokemon DPPT, HGSS, BW, and BW2 that's running with the help of the Kaeru WFC! Not only does it let you connect your games to the internet again, the site will let you see what Pokemon are up on the GTS for both the gen 4 and gen 5 servers!
Below is my guide on how to get this working for you so you can bring a new life to these wonderful Pokemon games. Also I thought this would be shorter but it's rather long, so under the cut it goes! Please let me know if I missed anything in here! I'll try my best to fix it if I can.
Getting Started:
Before you get connected, make sure you are using the device you plan on doing all of your online connections with! For some reason you are locked to one device for this stuff and using another one will wipe your PalPad, and assign you a new friend code. Since what's available in the GTS search function is based on SEEN Pokemon the most reliable way to get particular pokemon (without marking everything as seen via cheating) would be trading them from people you've registered in the PalPad.
If you only plan on using the GTS then you don't need to worry as much about this.
The Poke Classic Network works on ALL DS/3Ds systems!
I will note that the Gen 5 games are easier to set up if you're using a 3Ds since they can see and read the Wifi settings of the 3Ds and can just have the DNS swapped without additional set up.
Connecting DPPT/HGSS on all systems and BW/BW2 on the DS/DSi:
I will go over connecting via Emulator in another section, this section and the next one is for if you're PHYSICAL HARDWARE.
What you'll need:
The console of choice
The game of choice, preferably played to the point where you can access the GTS for testing purposes. --- In DPPT you can find the GTS building in Jubilife City. --- In HGSS you can find the WFC building in Goldenrod City. --- In BW/BW2 you can access the GTS in the top part of every Pokecenter. --- I don't remember when exactly the GTS is unlocked for the games unfortunately.
Some way to create a Wifi network point with a compatible WEP (password type) or just no password. --- The easiest way I've found is just using a hotspot without a password. --- I know some modern routers will let you create an extra network like this if you know how. I do not and it'd likely be different for each router anyways. --- There are also some programs that can make one using your computer. I've used one for a bit before it locked what I needed behind a paywall.
What to do:
The first step is setting up the connection!
Start up the Wifi network point so it'll show up on your system.
I recommend using a hotspot that doesn't have a password on it. Make sure you change the bandwidth to 2.4 GHz, since 5 5 GHz doesn't seem to work. DO NOT PUBLICLY OPEN YOUR HOTSPOT IN A PUBLIC PLACE! You do not want someone deciding to eat up your data while you're trading pokemon, so only do this in a place you know is safe to do so, like at home or at a friend's place.
Once you've done that you'll want to open your game and go to the Nintendo WFC Settings. The button will look like one of these depending on the game you're playing:

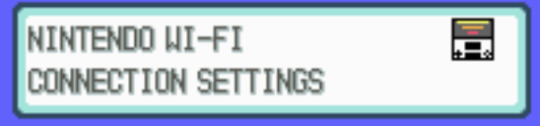
This will take you to the DS wifi settings that are saved to the cart!
Next you'll want to tap on the big blue button which will take you to this screen.

You may or may not have connections here already if you've played before Nintendo's servers shut down. Erase them now if you do as they will no longer work. Then you'll want to tap the None button for Connection 1.
I'll be demonstrating using Connection 2 myself, but stick to the first connection.
Tap on the Search for access point button. This will bring up a list of nearby connections that your system can see. You'll want to tap on the one you started earlier. It will test the connection and the boot you back to the screen with the big blue button. Tap the big blue button and then the Ready button that's now showing up for the first connection.
Now scroll down to the very bottom and turn off Auto-obtain DNS and change the primary DNS to 178.62.43.212. You can also change the secondary DNS to the same one as well or keep it all 0s.
Once you're done it should look something like this:
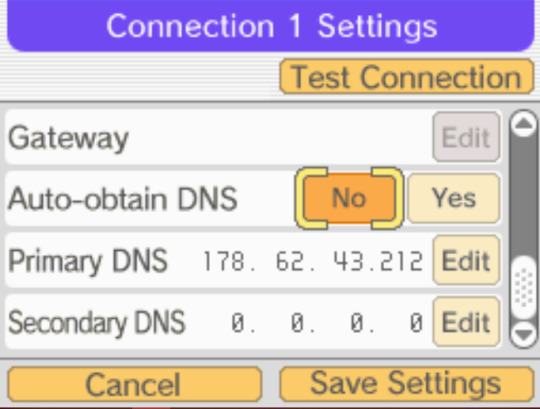
Save the settings, close out of the Wifi connections menu, start your save, and try connecting to the GTS!
If you connect to the GTS then congrats, you are now able to use the Poke Classic Network! If it doesn't work the first try don't worry and try again. You can also swap the secondary DNS to the other one you weren't using and try again that way.
Connecting BW/BW2 on the 3Ds/2Ds:
This one is super simple and doesn't require any additional set up! Sorry I don't have any pictures for this one atm. I may edit this to add a couple later.
What you'll need:
Game of choice
Console of choice
What to do:
Open the internet settings on your 3Ds and tap on Connection settings.
Tap on a connection you know is working, tap Change Settings, then go to the next page.
Tap on DNS and tap No, then tap Detailed Setup. Change the primary DNS to 178.62.43.212 and either keep the secondary one as all 0s or use the same DNS address you put in the primary DNS slot.
Save your settings and go start your game, then try connecting to the GTS.
If you connect to the GTS then congrats, you are now able to use the Poke Classic Network! If it doesn't work the first try don't worry and try again. You can also swap the secondary DNS to the other one you weren't using and try again that way.
Connecting any DS Pokemon game using MelonDS (emulator):
This method will let you connect to the Poke Classic Network if you don't have the physical hardware or can't connect your system to the internet for any reason and know how to back up your save to your computer.
What you'll need:
The MelonDS emulator [Link] --- Desume doesn't have Wifi functionality so you'll need to move your saves over if that is your primary DS emulator. --- If the latest version doesn't work for some reason try again with the second newest one.
Game of choice
What to do:
The steps are nearly identical to the first section once you have the emulator running! Instead of using your own connection though you'll be using the one MelonDS makes for you, so there's no need to worry about finding a way to make one yourself.
The access point will look like this when searching for an access point:

#the pokemon tag#pokemon#pokemon diamond#pokemon pearl#pokemon heartgold#pokemon soulsilver#pokemon platinum#pokemon black 2#pokemon white 2#pokemon white#pokemon black
34 notes
·
View notes
Text
Okay so…
Does anybody have any advice as to how to keep a fucking hacker outta your shit???
I swear to god this person has been fucking with me and my family for over a year now!!
Storage space glitching, sections for apps disappearing, apps failing to work completely, settings changing on their own! We have literally watched the laptop tap into its own master controls and had to close it before they changed it and got back into what we were keeping them out of!!!
We’ve had credit card info stolen, scams, cyber stalking.
We reset devices all the time, change passwords for our accounts on a weekly, if not daily basis, we have to unplug and plug back in our WiFi constantly, we’ve bought a vpn, a dummy router!! We’ve signed out of all Google accounts, done everything we can think of!
As I speak, they are currently keeping the internet on my laptop from working so I can’t do school!! I have to change the vpn’s location every time I click on something to get anything to load!!!
I can understand having trouble with these things occasionally but all the time, ALL AT ONCE!!!!???
My mother is driven to her wits end with this stuff effecting her business!
We don’t know how to get our privacy back!!
Does anybody have any advice at all?????!
#real shit#I wish I was joking but this is my reality#plz help if you can#hacking#hacking advice#advice#important shit#they won’t leave us alone
2 notes
·
View notes
Text
How to Connect Virgin Media to ISP and WiFi Pods Setup?

The Virgin media is a broadband and networking devices provider which has seamless services for the users. Here you will get to know how to setup its two of the networking devices. One is Virgin media hub and other is WiFi pods. You should follow all instructions to prevent the Virgin Media outage problems.
Virgin Media Hub Setup
The Virgin media hub can act as the modem as well as the router, so we can call it a Modem router. Here in this section, you will get to know how to connect the device to home network and configure it as modem and router mode.
Connection
If you want to connect the device to the ISP directly, then you must use the co-axial cable. Insert cable to the ISP server socket and other end will go in to the hub port. Then you can connect the device to the power and set it as Modem mode.
If you want to connect the device to the home modem, then you must use the Ethernet cable. Connect the cable end to the hub WAN port and modem LAN port. After that, you can connect the device to the power and set it as router mode.
Now, have a look how to configure the device with the help of the simple instructions given in below section;
Configuration
If you want to set it as the modem device, then open the web browser and enter the IP address like 192.168.0.1. This information is given on the label of the device as well as in the user manual. Note the username and password also.
Reach to the interface login page, enter the username and password, and then press the Enter button. You will get to the interface page where you must go in to the Advanced Settings and click on the Management option. Here you will find the Modem mode, just select it and toggle the Enable button. Also here, you can change Virgin Media WiFi password easily.
If you want to set it as the router device, then open the web browser and enter the IP address like 192.168.0.1. This information is given on the label of the device as well as in the user manual. Note the username and password also.
Reach to the interface login page, enter the username and password, and then press the Enter button. You will get to the interface page andwhere you can set disable the modem mode to set it up as the router.
There are more Virgin media devices, which help the user to extend the router hub network and internet signals.
Virgin WiFi Pods Setup
The Virgin WiFi pods are small but very impactful devices that you can connect with the Virgin hub using some simple instructions;
Connection
To connect with the hub, you just have to power the pod in your house within the reach of the hub. Use the power cord to power it on. Then you just have to wait for the some minutes and then use My Virgin Media App or Virgin connect app to configure the device.
Configuration
Just use the Virgin media Email to get the access to the app and start a scan to find the WiFi pods. Then simply tap on the Connect button to establish a link between the devices. now, you must adjust the settings and finish the setup.
End Words
Here, you have seen and learned about how to complete the Virgin media router hub setup and how to connect the WiFi pods to it.
#Virgin Media#Virgin Media outage#can change Virgin Media WiFi password#My Virgin Media App#technology
0 notes
Text
does vpn prevent hacking my wifi password
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn prevent hacking my wifi password
VPN encryption
Title: Understanding VPN Encryption: Safeguarding Your Online Privacy
In today's digital age, safeguarding your online privacy is paramount. With the rise in cyber threats and surveillance, using a Virtual Private Network (VPN) has become essential for many internet users. One of the key components that ensure the security of VPNs is encryption.
VPN encryption works by encoding data transmitted between your device and the VPN server. This encryption creates a secure tunnel that prevents third parties from intercepting or deciphering your online activities. It's like sealing your data in a virtual envelope that only you and the intended recipient (the VPN server) can open.
There are several encryption protocols used by VPN providers, each offering varying levels of security and performance. Some common encryption protocols include:
AES (Advanced Encryption Standard): Widely regarded as one of the most secure encryption standards available today, AES comes in different key lengths such as 128-bit, 192-bit, and 256-bit. The higher the bit length, the stronger the encryption.
OpenVPN: This open-source protocol is highly configurable and supports various encryption algorithms, including AES and Blowfish. It's known for its flexibility and robust security features.
IPsec (Internet Protocol Security): IPsec operates at the network layer of the OSI model and provides encryption and authentication for IP packets. It's commonly used in combination with other protocols like L2TP (Layer 2 Tunneling Protocol) or IKEv2 (Internet Key Exchange version 2).
WireGuard: A relatively new protocol known for its simplicity and efficiency, WireGuard aims to provide better performance while maintaining strong security through modern cryptographic techniques.
When choosing a VPN provider, it's crucial to consider the encryption protocols they offer and opt for those that prioritize your privacy and security. Additionally, regularly updating your VPN software and using strong, unique passwords further enhances your online protection.
In conclusion, VPN encryption plays a vital role in safeguarding your online privacy by encrypting your internet traffic and preventing unauthorized access. By understanding how encryption works and choosing reputable VPN providers, you can enjoy a safer and more secure online experience.
WiFi security
Title: Safeguarding Your Connection: A Guide to WiFi Security
In an era where connectivity is paramount, WiFi has become a fundamental aspect of daily life. Whether at home, in the office, or on the go, the convenience of wireless internet access is undeniable. However, this convenience comes with risks, particularly concerning security. Ensuring the safety of your WiFi connection is crucial to protect your personal information and sensitive data from malicious actors.
One of the primary threats to WiFi security is unauthorized access, commonly known as WiFi hacking. Hackers employ various techniques to gain access to WiFi networks, including brute force attacks, packet sniffing, and exploiting vulnerabilities in router firmware. Once they infiltrate a network, hackers can intercept sensitive information such as passwords, financial data, and personal communications.
To mitigate the risk of unauthorized access, it's essential to secure your WiFi network effectively. Start by changing the default administrator username and password on your router to prevent easy access by hackers. Additionally, enable WPA2 or WPA3 encryption, which encrypts data transmitted between your devices and the router, making it more difficult for hackers to intercept.
Regularly updating your router's firmware is another crucial step in maintaining WiFi security. Manufacturers frequently release updates to patch vulnerabilities and improve security protocols. By keeping your router's firmware up to date, you can protect against known exploits and vulnerabilities.
Furthermore, consider implementing additional security measures such as MAC address filtering, which only allows specific devices to connect to your network, and disabling remote administration to prevent unauthorized access to your router's settings.
In conclusion, prioritizing WiFi security is essential in safeguarding your personal information and maintaining the integrity of your network. By following these best practices and staying vigilant against emerging threats, you can enjoy the benefits of WiFi connectivity without compromising your privacy and security.
Hacking prevention
Title: Protecting Your Digital Fortress: Effective Strategies for Hacking Prevention
In today's interconnected world, where the digital landscape serves as both a playground and a battleground, the threat of hacking looms large. From personal data breaches to corporate espionage, the consequences of a successful hack can be devastating. However, with the right measures in place, individuals and organizations can significantly reduce their vulnerability to such attacks.
First and foremost, maintaining strong and unique passwords is essential. Passwords should be lengthy, containing a mix of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable information such as birthdates or pet names, and consider using a reputable password manager to generate and store complex passwords securely.
Implementing two-factor authentication (2FA) adds an extra layer of security by requiring not only a password but also a secondary form of verification, such as a code sent to a mobile device. This greatly reduces the risk of unauthorized access, even if passwords are compromised.
Regular software updates are crucial in patching known vulnerabilities that hackers may exploit. Ensure that all operating systems, applications, and plugins are kept up to date to mitigate the risk of known security flaws being exploited.
Investing in robust antivirus and anti-malware software can help detect and prevent malicious software from infiltrating your systems. These tools should be regularly updated and configured to conduct thorough scans of all files and network traffic.
Employee education and awareness are also vital components of effective hacking prevention. Training staff on safe browsing habits, recognizing phishing attempts, and the importance of data security protocols can help create a vigilant workforce capable of identifying and reporting potential threats.
By adopting a proactive approach to hacking prevention, individuals and organizations can better safeguard their digital assets and mitigate the risk of falling victim to cyberattacks. Remember, in the ever-evolving landscape of cybersecurity, staying one step ahead is key to staying secure.
Password protection
Password protection is a crucial aspect of maintaining digital security in this modern age. With the increasing number of cyber threats and data breaches, it is more important than ever to ensure the safety of our online accounts and sensitive information.
Setting strong and unique passwords is the first line of defense against unauthorized access to our accounts. It is recommended to use a combination of letters, numbers, and special characters to create robust passwords that are hard to crack. Additionally, avoiding common words, phrases, or personal information in passwords can further enhance their security.
Furthermore, implementing multi-factor authentication (MFA) adds an extra layer of protection to our accounts. MFA requires users to provide two or more verification factors to log in, such as a password and a unique code sent to their phone. This significantly reduces the risk of unauthorized access, even if someone manages to obtain the password.
Regularly updating passwords and avoiding the reuse of the same password for multiple accounts are essential practices to enhance password protection. Using a reputable password manager can help generate, store, and manage complex passwords for different accounts securely.
In conclusion, password protection plays a vital role in safeguarding our online presence and sensitive data. By following best practices such as creating strong passwords, enabling MFA, and using password managers, we can significantly reduce the risk of falling victim to cyberattacks and data breaches. Stay vigilant and prioritize password security to stay one step ahead of potential threats.
Cybersecurity measures
Title: Strengthening Your Digital Fortress: Essential Cybersecurity Measures
In an increasingly digitized world, safeguarding sensitive information and digital assets has become paramount. Cybersecurity measures are the frontline defense against malicious actors seeking to exploit vulnerabilities in networks, systems, and applications. Here are some essential measures to fortify your digital fortress:
Firewall Protection: Implementing a robust firewall acts as a barrier between your internal network and external threats. It monitors and controls incoming and outgoing network traffic based on predetermined security rules, preventing unauthorized access and malicious attacks.
Regular Software Updates: Keeping software, including operating systems and applications, up to date is crucial. Software updates often include patches for known vulnerabilities, closing off avenues for cybercriminals to exploit.
Strong Authentication: Enforcing strong authentication mechanisms such as multi-factor authentication (MFA) adds an extra layer of security beyond passwords. By requiring multiple forms of verification, such as passwords, biometrics, or security tokens, MFA significantly reduces the risk of unauthorized access.
Data Encryption: Encrypting sensitive data both at rest and in transit ensures that even if intercepted, it remains unreadable to unauthorized parties. Encryption algorithms scramble data into ciphertext, which can only be decrypted with the appropriate decryption key.
Employee Training: Human error remains one of the leading causes of security breaches. Providing comprehensive cybersecurity training to employees educates them about potential threats, safe online practices, and how to recognize phishing attempts or suspicious activity.
Regular Backups: Regularly backing up critical data ensures that even in the event of a cyberattack or data breach, you can restore important information without significant loss. Backup data should be stored securely and independently from primary systems.
By implementing these cybersecurity measures, individuals and organizations can significantly reduce their susceptibility to cyber threats and mitigate the potential impact of attacks. Prioritizing cybersecurity is not just a necessity but also a proactive investment in safeguarding digital assets and maintaining trust in an increasingly interconnected world.
0 notes
Text
" Sharing "
Hello everyone,
My name is Ron Rudd AKA He who's name can not be spoken.
I'm currently living at a homeless shelter at 1501 Imperial Ave San Diego CA, 92101.
It still hurts, the way everything unfolded.
Originally the goal was to shame me into submission but I'm not really wired that way.
Can not begin to emphasize how dangerous sharing innovations and politics on social media can get.
Shortly after my mother's death my life started getting strangely cloak and dagger.
Four Poisoning attempts on my life once I discovered that I was being broadcast to everyone on the planet without my knowledge.
Shortly after arriving in Puerto Escondido Mexico a German agent would pick the lock to my room and take my phone.
I saw it through the window but thought it best that he didn't know I was on to him so I let him keep it.
Just before that another German agent sharing the same room as him would poison a package of cheese that only he had seen me bring back and place in the community refrigerator full of other people's food.
The other attempts would be made before I left Louisville by people that I thought I knew.
No joke what I've gotten myself into.
I Had no idea that sharing on Facebook could be so incredibly detrimental to one's health, peace of mind and personal safety.
I've been tortured by pain Drs and Butchered by back surgeons.
If you're going to speak truth to power be ready for whatever they might throw at you to shut you the Fuck up.
Facebook posted several images of a dead white cat on my timeline.
The Jewish owned media would have you believe that I was the one broadcasting from my phone by accident.
That's the joke, that I'm too dumb to work a phone and accidentally broadcast myself.
The cocktail of drugs added to my Cybalta capsules would make me sound exceptionally slow over the phone so I get why that might possibly ring true.
I have an associates degree in computer science and I can build a computer but I'm too dumb to understand how a broadcast button works.
Your phone is just a hackable handheld computer
Your number or app permissions are all that's required to access your ideas, hard work, microphone, camera and location.
Hackers can hack every single app you own.
Including Waze and Craigslist, Congress approved and carried out by Fuckerberg and his NHS thugs. Via Google.
Anyone with your phone number can hack you but there were months when I was being hacked that only Facebook and Instagram had my number because I had to keep getting new ones.
There are plenty of Ron Rudd's out there so it would be difficult to know which was mine and my full legal name was never posted on Facebook.
However Zuckerberg did contact me to request my new number while he was broadcasting me.
Every time I would write about what happened on my phone my notes would be hacked and lost.
I took screenshots to try and preserve them and they were blurred out.
My computer was sabotaged while I was out.
The phone and app locks are nothing more than a false sense of security. In Fact you can turn off your data, WiFi and phone, they will still be listening and they can still contact other close devices.
We now live in a Jewish run Mommy dearest style police state government thanks to a handful of Old white republican politicians.
A hacking device was hidden inside a power strip in my house while I was out.
You can also be directly hacked via Google play services That's how it's designed, with holes.
The local cable company was offering me free cable until they realized I was unplugging the router when I used my phone. Then they cut off the cable and screwed my credit score.
I think pinhole cameras might have been used inside the house.
I couldn't get into my Mycroft account.
My Amazon drive account password was changed.
All my Google backups are gone.
Years of working on music compositions are lost.
Retouched family photos from three generations back lost forever.
All of my innovations were met with massive amounts of hostility on Facebook.
I couldn't wrap my head around how angry people were about a concept.
They were just ideas take em or leave em. When I made the point that electric vehicles were being charged using fossil fuels instead of solar I was bombarded with insults.
Facebook made it impossible to contact me for startup funding.
Removing all Asian people from my friends list
I wouldn't even see another Asian in my searches after that.
Then they blocked my phone calls, texts and messages from anyone other than my mom and my therapist.
They hid me among several other Ron Rudd accounts. All my age with beards and glasses.
For a long while you couldn't even find my account.
Fuckerberg hid contact info on my home page. Wouldn't let me download my timeline files.
My messages were hidden from me.
One day they all just showed up and then disappeared again shortly after.
There were hundreds of them.
Many asking for money.
The matrix pawns would call pretending to be someone from the bank needing my card number so they could call to check my account and see if I had obtained start-up money for my innovations.
Facebook hid the number of followers I had from me and likes on my posts until the very end of this whole ordeal.
My camera was hacked to photograph me naked.
Then they shared that picture with friends on Facebook.
Google home was listed as one of the WiFi connections at the hostel I was staying at in Mexico.
My phone was made useless. I would lose everything after I reset it every few weeks.
Google never gave me back my previous account so I had to make several of them. Like eight.
I've gone years without a working phone over this.
I will probably go several more years after sharing this.
In some ways I kind of understand.
Here I am a no family, weed smoking, twenty year pain pill addict who's been in and out of psychiatric facilities and disabled most of my adult life.
Not exactly the best role model for a society built on hard work ethics.
Still this was playing dirty and I wasn't about to just let it slide.
When I realized my phone was being hacked after sharing several innovations that got a lot of attention online I wrote letters to intellectual property attorneys all over the world.
Shortly after they showed up at the door with QR codes.
Once in my phone they could witness for themselves exactly what was going on.
My medicine was spiked.
They must have used estragon because my beard fell out, sodium pentathol kept me talking and God knows what made me so uncontrollably angry.
As soon as I mentioned the possibility of this over the phone several bottles of medicine came up missing from my home.
I was already a little paranoid before all of this but now my dial is set to eleven.
I have no doubt that my mental illness will be used to sweep all of this under the rug.
"He's just paranoid."
My character assassination was very well thought out.
The countless phone imposter agents used to create the perception of me being a completely irate dumpster fire of a human being by saying things that would make anybody lose their temper.
Making my medical appointment transportation four hours late on a regular basis for example.
The government is literally playing Crank Yankers with its own citizens. redirecting our calls to imposters, paid for with our own taxes.
There was a short time that I thought only the FBI or homeland security was listening then after using the N word in the privacy of my own house I was clued in by a kick on my door and the side of my house that maybe someone closer was listening.
Possibly the Police I thought.
My next clue was a Facebook post of a guy beating up another guy the exact way I had just described my brother hitting me to my virtual therapist over the phone.
I told her so many things about my family and childhood sexual abuse that were meant to be private.
Finally some random black man attacked me on Instagram asking me why I deserve to get a break if he didn't get one.
That's when I was sure my privacy had been raped.
That's when I lost it.
I would later see a lot of things on talk shows, stand up comedy and SnL that would clue me in that the joke was on me all along.
About a week later I would learn that my mother had passed away. It was close to new years.
To this day I wonder if something I said may have led to hear death.
Their agents broke into my house and infected my PC and all of my thumb drives with viruses.
Insuring that I had no proof of concept for my inventions. They even stole a copy of my Myelogram.
I'm guessing it showed how my Dr's Butchered me it would also insure I couldn't get pain medicine or take them to court.
The disk was so well hidden behind a drawer inside the end table that there was no way anyone would find it.
That's when I realized they had to be watching me with inferred.
A door was made by some plumbers doing some work under the bathroom floor at the back of the house it would permit entry whenever I left and sometimes while I was sleeping.
Also the front door had a combination lock.
I'm guessing a camera was set up to watch me unlock it from a distance.
Infrared cameras and my phone's location would let them know when it was safe to come in.
After gluing that point of entry in the bathroom shut I could hear them banging on it in order to try and jar it loose after I had been lying still for awhile one night.
Finally they drilled holes in the side of my house where a small divide separated me from my neighbor. They injected my room with an aerosol.
My CPAP machine had a reservoir full of iodine colored water every morning for weeks.
My heart would start racing when I walked. I had to stop and set down from the dizziness and I was spontaneously losing control of my bowls.
I had constant fatigue and night sweats.
My face was swollen with a red rash around my eyes and nose. My sinuses congested and I would sneeze constantly. I was experiencing brain fog and my skin had turned pale and clammy.
One time they left a pair of plastic gloves behind
After doing a search.
My pain medicine came up missing and that month pain management called me in for a pill count.
That was the first time in over twenty years of receiving pain medicine I had ever been asked to come in for a count.
Somebody kicked or thew something at my cat permanently damaging his ear.
I no longer felt safe where I was.
People were shining flashlights through my curtainsbat night.
Sometimes I would hear extremely loud kicking on my front door.
The message was clear.
I couldn't live there without water after receiving a five hundred dollar bill after I had it turned off so I had to leave my home of twenty years.
Leaving behind my beloved cat.
I packed up and left for El Paso where my roommate's car would soon be vandalized after he got too involved in the situation at which time I headed down to Mexico.
A British agent was one of many agents that came to Mexico.
He suggested that this was supposed to be something like the Truman show with Jim Carrey.
My thoughts on that.
Why not Clockwork orange or Shawshank?
Better yet why not Trading Places?
This was done to humiliate me for political purposes, my fight for climate conservation and
Maybe it had something to do with my innovations as well.
The government is constantly trying to set me up now.
Apparently entrapment laws have been abolished for our generation.
Usually it was someone that already knew I was being broadcast and wanted to be famous for kicking my ass.
Other times they would use my location to parade attractive women in front of me a few times a week in hopes of getting me to try and solicit a prostitute.
Sometimes they would do this on social media asking me to buy them an Xbox card for their kids to keep them busy while we had sex in the other room.
This happened several times.
I have doubt that once I was behind bars I would be there for a long time.
Jewish owned social media completely disrespected me putting my personal safety in danger and leaving me completely humiliated and fearful for my life when they broadcast my microphone.
So I gave them a taste of their own medicine calling them out for the role they played in raping my privacy.
I probably went overboard but I've always had difficulty controlling my anger.
I still regret some of my comments.
It was also a great way to get canceled in a cancel culture.
Insuring that someday at least I would finally have my privacy, safety and peace of mind.
Free of the stalker messiah and his army of Matrix puppets.
Yes,
I like to look at photos of young ladies naked.
The website I used was the very first listed in Google's search engine.
If anyone was underage it's because Google allowed it.
I agree that some of those girls looked too young to be there.
It's a billion dollar industry so I'm not the only dirty old Man out there.
The difference being that they agreed to be filmed naked performing sex acts.
I didn't.
Let me clear this up,
I'm not anti semitic
I still like many Jewish people.
Adam Sandler had nothing to do with this.
Mell Brooks is still one of my heroes.
I could just as easily suggest that they're anti atheist or anti irish.
That's just a lazy way out of legitimate arguments.
I've enjoyed TV and movies created by the jewish community all of my life.
I honestly believe they have saved me from countless days and nights of painful boredom but clearly there's something diabolical going on behind the scenes of these mega monopoly media companies in conjunction with our government in order to get the people they want into office.
All of this needs to be brought out into the light and closely examined for the security of our nation.
"Ultimate power corrupts ultimately."
I'm tired of being divided by sexual orientation, gender, race, income and politics in the media.
We need unity now more than ever!
Meanwhile they portray themselves as being peace loving, family oriented and nonviolent.
The Jewish owned media completely disrespected my safety and privacy so I completely disrespected the Jewish people.
That's why I went off.
That's why I threw in the towel.
I'm not really all that angry about my ideas being exploited. My privacy, yes!
I knew how the process worked before I shared them and I was aware that if nobody helped me with startup fund's any monetary rewards would be lost.
All I had was proof of concept.
I took that chance because at the time I thought Fuckerberg was trustworthy.
I wasn't expecting that my phone would be hacked so that nobody could reach me in order to insure my losses.
Meanwhile Facebook was sharing posts on my timeline giving me the impression that I should just be patient because I was already a millionaire.
Showing me luxurious homes and cars at the same time they were broadcasting my phone and using several of their infinite number of agents to try and entrap me.
About a year later, once they knew it was too late for me to patent the idea they started harassing me through posts, implying what a loser I was.
Why is it that inventors are the only ones required to pay an exorbitant fee before they can get financially rewarded for sharing an idea that would better our society and the health of the planet?
What if our favorite musicians and artists had to come up with five to fifty grand before they could profit from their creativity?
We would only get rich, white bread and mayonnaise sounding songs and artwork right?
After all that I had been through they still expected me to play ball and donate my time and creativity as though no fowl had ever been committed.
I should just keep giving away my ideas as though nothing had ever happened.
That is if I was really a kind caring human being then I wouldn't let any of this change me...
Even if you do come up with a few thousand dollars to get help patenting your idea all someone has to do in this country is say that they thought of it at the same time.
Easily done when these monopolies have total access to your electronic devices and ideas.
Bluetooth came out the same year as 9/11 allowing our cellphones to communicate with our devices, the patriot act would give permission for government monopolies like Google and Facebook to keep an eye on us, opening the door to intellectual property theft.
It would also give them unlimited access to their political rivals' email communications and personal life.
Making Watergate look like child's play.
Now they are using their Matrix puppets to command hard work and obedience while snitching and stealing from the rest of us.
This is my opinion based on what's happening to me.
These companies have COMPLETE control over who we can talk with.
Our forefathers would have gone to war over less.
Still we market ourselves to the rest of the world as the land of the free.
How do we know that the same thing that happened to me hasn't happened to our more liberal leaning politicians in order to sway a vote or get them to resign?
Read that again.
How all of this has effected me long-term.
I miss the people and pets that would have still been in my life had none of this happened.
I am always suspect of anyone that comes into my life.
What are their motives?
Do they know who I am?
How are they going to try and entrap me?
I keep my devices in Feraday cloth now and I'm careful around phones and camera's.
I think the government's ability to use their Matrix puppets to influence friends, family and neighbors with threats of incarceration for past crimes or monetary rewards paid for with our taxes was the most disheartening part of all this.
Not one of you has ever told me straight out that my phone is broadcasting only subtle hints by repeating the things I have said in the past.
Usually being done by an agent trying to provoke me.
What did I do to justify this attack on my safety and privacy?
I wouldn't change political parties to republican.
I fought for climate conservation and I didn't support Israel's occupation of Palestine.
That's all it took.
Mr. White from breaking bad approached me on Facebook to try and get me to join his team.
I WAS given a choice.
The last poisoning attempt on my life has changed me.
My memory and focus are wasted.
Once this has happened to enough people you'll know the truth.
Once it's happened to you it won't seem as funny.
Keep stealing from the creatives and all you'll be left with is lawyers and accountants.
It's taken every bit of my strength to keep from turning to the dark side.
I have no doubt that this is the kind of thing that has led to the ridiculous number of mass shootings in our country.
Random People see me and chuckle or laugh.
An orthodox Jew called me Ron Rudd the masterbator at the Chicago airport.
While sleeping on the sidewalk a man approached to yell something about Yahweh.
Now I live in a homeless shelter in San Diego where I've witnessed two stabbing and several fights.
Every night after I fall asleep a security guard taps on my metal bunk and shines a flashlight in my face.
The plastic mattress is destroying what's left of my back.
I would welcome any legal advise.
I can't even get the pain medicine I need after they broadcast me doing a small bit of meth that I hadn't done in over twenty years.
This whole ordeal has cost me everything.
Even my beloved cat.
I'm nervous wreck now.
225 degrees in Texas. I've done all that I can.
I am completely ruined now thanks to sharing.
Steps I've taken to unf#ck my phone:
If you can't get a phone in someone else's name here are some tips on keeping them out of your android.
Once you download everything from playstore
Disable All of your Google apps, anything that says Google clear the cache then turn on do not disturb some apps like Spotify and Shutterfly will no longer work.
You can enable Google services for a moment now and then but not playstore.
Now uninstall the Meta and Facebook apps all four of them. Do not install Whatsapp, which is a Gateway for hackers.
Instagram is the most insidious downloading viruses disguised as apps.
Once they have your number all hell breaks lose.
Switching to WIFI won't help using your location they will access your phone as soon as you inter the password.
They're going to upload everything to your Google keyboard now. You'll need to clean the cache on a regular basis.
Get a non WiFi motion detection alarm with a siren to keep Matrix puppets out of your house when you're not there.
List of innovations:
The iPhone GPS tracking devices that help locate your keys and wallet.
Fresnel lens powered water heaters
Electromagnetic earthquake proof buildings.
Revolving metal detector security door.
Gps chips in children's shoes to prevent kidnapping.
Several environmental ideas.
Using airbags to stop oil leaking from pipelines.
Metal case to hold GPS trackers for your catilitic converter. Attached with JB weld.
Solar powered lawnmower that worked like the robots that clean our floors.
Air bags to seal leaking oil pipeline
Reflective marbles made of desert sand to help cool the planet.
Using seed bombs to plant the most carbon reducing trees and plants.
Piping water from plentiful lakes to the ones drying up.
Giant circular submersible farms utilizing condensation for hydroponic irrigation.
Political ideas that would have pissed them off.
Verified voting checked online with a password.
A government supplemental coupon to save money on electric mowers and weed eaters.
My stance against the fossil fuel industry.
Public Voting to decide which companies get subsidized.
I was pointing out the hypocrisy of threatening disabled people's income and calling it intilements while the wealthy do no actual labor for the income they make off the interest of their money.
Complaining about the amount of money we send to Israel and the resulting gentrification of our cities leaving thousands homeless.
1 note
·
View note
Text
A Step-by-Step Guide: Spectrum Router Login Process Explained
Let's discuss how to log in to your Spectrum router using the My Spectrum app. There are iOS and Android versions of the My Spectrum app. Therefore, be sure to get the most recent version of the app from the Play Store or App Store.
You may monitor and adjust a number of settings and services associated with your internet connection through the My Spectrum app. You can restart your router, adjust advanced router settings, suspend internet connectivity, and change your WiFi name and password. Please follow these instructions to learn how to log in to your Spectrum router using an app.
We're going to move right into learning how to access the equipment through the app since we're assuming you've previously configured the Spectrum router.
Install the My Spectrum app after downloading it.
Open the app on your mobile.
The router login page will then appear on your device's screen.
Enter the username and password for the default Spectrum router login.
Once you click Login, your device will be successfully logged into.
On your device, you can also enable Touch ID or Face ID sign-in.
You will then have the choice of using your fingerprint or facial recognition to sign in to the My Spectrum app.
The process of logging into the Spectrum router will then be finished.
#router#internet#spectrum router login#spectrum#Login to spectrum router#how to login the spectrum router
0 notes
Link
Every Linksys router, wired or wireless, has an internal web server for modification and configuration. A Linksys router login is required to access the internet web server. So, before configuring your router, you must first log in to your Linksys router. Prior to Linksys router setup, you need to review the following:
The Linksys device must be hardwired to your PC.
A solid connection is required to access the Linksys router’s internet page.
Hardwired connections are more reliable. So go for a wired connection.
Before starting the Linksys router login, make sure your router is powered up.
Use the admin password to log into your Linksys router.
The default password and username for most Linksys routers are on the product label.
#default linksys password#default password linksys router#how do i log in to my router#how to change router password linksys#wifi smart#wifi router linksys#smart wi fi wifi login#extender.linksys.com#linksys extender setup#linksys wifi extender login
0 notes
Note
hi hi! joining in the birthday asks with 1 for kuroo please! 🫶
hi hi hi !! come get a present for my bday !!
1. have a favorite character? here, have 5 of my top headcanons for them
kuroo my dearly beloved!!!! thank you for asking, i want to talk abt him all of the damn time. under the cut because. yeah. i'm just like this. (very minor kuroken notes included, lmk if you want hcs w/o any of that)
i think that there was a time when he dreamed of becoming a professional volleyball player. in the extended haikyuu canonverse that lives in my head, he couldn’t make it onto a professional team after graduating high school, so he decided to go to university and play there instead of going pro. once he was in uni, he got an internship with the JVA and kind of just fell in love with the job. he decided he was better off not as a player but working behind the scenes. it’s not really something that he’s insecure about or regretful of, but it is very much a “what if” that he thinks about sometimes. (ok fine yes i wrote a fic about this and never published it and that’s why i’m thinking abt this, hush)
he is terrible at social media. like, not only for jva promotional posts (which is canon) but for his own social media as well. his instagram is blurry photos of the sunset with cheesy captions and twenty five hashtags. he doesn’t know how to block people on twitter, which is a problem as he tends to get into passive aggressive arguments with trolls (kenma eventually shows him how, exasperated at kuroo’s complaining abt the people dming him). this being said, he has a tik tok dedicated to making bad fan edits of his friends on professional volleyball teams. this has done more promotional work for the v.league than anything he has ever seriously posted on twitter.
actually he’s just terrible with technology in general. he doesn’t get how it works, and he’s the kind of person who likes knowing things. the fact that he doesn’t just get how internet and tech overall work drives him insane. he’ll try and take things apart to see how they tick (literally) but he doesn’t know how to put them back together. he claims his computer hates him personally, but in reality, he just spilled orange juice on the keyboard once and now the n key sticks. he doesn’t know what a dark mode is and at this point he’s too afraid to ask. his phone password is 1234. he doesn’t know where the wifi router in his house is because kenma set it up for him and, if pressed, he would not be able to tell you what the said wifi router does in the first place. (kenma knows enough about tech for the both of them, he says. kenma replies, you have ten viruses on your laptop and still haven’t set up face id on your phone. kuroo tells him to shut up.)
that all being said, his spotify account is insanely organized and personalized exactly how he wants it. he has music OPINIONS and he is not afraid to share them. he’s always ready with a song rec for any genre, but he is also ready to tear apart a person’s music taste if he thinks they like something compositionally bad. he absolutely has a superiority complex based on his music taste but refuses to admit it. he has playlists for every mood and situation, all sorted into folders and listed alphabetically. for people’s birthdays, he likes to give them carefully curated playlists based on their taste and things he thinks they would like. (he makes kenma a mixtape on a cassette tape for their first anniversary and kenma is very very grateful but also “kuro literally how am i going to listen to this. what were you thinking.” “it’s romantic!” “i mean sure but that doesn’t change the fact that i still can’t listen to it.” “....fine, i’ll send you the spotify link.”)
he loooooovesssssss bad b rated horror movies. he thinks they’re hilarious and the height of entertainment. at a team sleepover, he convinces the team to watch one with him, and he provides running commentary throughout the entire thing. just in general, he tends to talk a lot during movies and tv shows, whether or not they’re good. the more he talks during it, the more he’s enjoying the movie/show. his commentary is usually pretty good/funny/entertaining, but there are times when it just gets obnoxious. kai is a patient man but he will deck kuroo if he laughs at a dramatic death scene one more time.
12 notes
·
View notes
Text
Guide on Mywifiext | www.mywifiext.net Login / Setup
By asking you questions, Guided Assistance assists you in resolving the problem you are experiencing with your NETGEAR equipment.
You can log into your netgear WiFi range extender after installation to examine and modify the settings.
Visit NETGEAR Support and obtain the quick start guide for your model if you haven't installed and connected your WiFi range extender to your current WiFi network before continuing.
Check to see whether your model is listed under "This article pertains to:" If you own a Nighthawk Mesh or Mesh WiFi Extender, check How can I access my Nighthawk Mesh Extender or WiFi Mesh Extender?
To access your WiFi extender, log in as follows:
From a computer or mobile device linked to your extender's network, open a web browser. It's possible that the names of your router and extender's WiFi networks differ (SSIDs). Check to see if you are linked to the network of your extension. In the URL bar of your web browser, write www.mywifiext.net if your extender and router have distinct WiFi network names (SSIDs). Enter http://extender's IP address> (for instance, http://192.168.1.3) into your browser's address bar if your extender and router share the same WiFi network name (SSID). See How can I find the IP address of a device connected to my router? for additional details. Hit the Enter key or press. A login screen appears.
Enter your admin password and user name. Note: An email address could be part of your user name. Click the Username & Password Help link if you can't remember your user name or password. To change your login information, see How can I reset my NETGEAR range extender to factory settings? Tap or click LOG IN. It shows the Status page. Click or press the Menu symbol if your browser displays it. A menu for the extender appears. To view and modify the extender's settings, select Settings.
1 note
·
View note
Note
Do you have any starter tips for internet security? The network story spooked me.
At very minimum, and this is an absolute necessity, if you have any "smart" home devices, toss em. Those things are riddled with security vulnerabilities and are just straight up wiretaps.
Aside from that, if you live in an apartment and you are on a carrier grade NAT (you share the same network with everyone else), hide everything behind a personal router you own (and for the love of god, change the network name, password, and router credentials on it). So anything that IS exposing a service such as a media server, an SSH server, or even a game server, even if it's LAN, isn't exposed to everyone else on your network. Anything you DO expose to the public internet, try and make sure it's exposed only through either a service like Zerotier, which requires you to connect via a VPN connection and requires authentication, which is relatively secure but is unfortunately dependent on a third party. Or only expose it through your IPV6 address so you aren't as vulnerable to IP Sweeping, and get familiar with how to properly configure your firewall. I would NEVER expose a service to the internet over a public IPV4 address, that's asking for trouble. Speaking of which, some routers have a stupid fucking option they call "remote management" which is an SSH server exposed to the public internet. Turn that off. This is what I believe is the absolute bare minimum for securing your home network.
For your mobile stuff, never ever connect to public wifi. I would rather drop the extra cash for unlimited data then connect to public wifi. Speaking of which, if you are ever in an airport, turn on airplane mode, and then turn your phone off well before you enter the airport, and don't turn it back on until well after you leave. Airports are prime targets for governments and other nefarious actors. If you can, remove the battery entirely. Also keep your bluetooth off when you aren't using it. Bluetooth is an exploit riddled, piece of shit technology (keep NFC off too).
For just basic all around internet safety, please please PLEASE, don't post any personal information on the internet. Treat the internet like you would the cops. Anything you say can and WILL be used against you. Post absolutely ZERO identifying information about yourself to social media. If you can help it, don't even use it at all. You'll never see me purposefully reveal or confirm my age, sex, race, nationality, or ANYTHING that could narrow me down. If you do post any of these things, only share it with people you know and have a lot of trust in, and only share it in private servers. Which I still discourage, but I understand that for some people, being that tight lipped about shit isn't really their jam. I see a lot of stupid parents of, or the stupid kids themselves, online posting their face and even what school they go to. Or people posting their jobs, and even their goddamn phone numbers and home address. Pure insanity.
A lot of people don't realize it, but their cameras actually put EXIF data in the photos, which can tell you exactly when and where the photo was taken. Some websites automatically scrub it, some don't. So if you ARE planning on posting a photo on social media, even if it seems completely harmless, make sure you manually scrub the EXIF data before you upload it.
I'll keep updating this post as more comes to mind.
4 notes
·
View notes
Text
Eero Login?
If you're facing slow internet issues at your home or at your office, Eero Wifi Routers definitely the ideal choice for providing solutions to weak network issues.
Eero has advanced technologies and the smart plus latest features that will provide you an amazing performance with uninterrupted fastest internet speed. And among the strong feature of Eero, it will give you coverage in every direction and every corner of your house.
Eero Login Setup Process Requirements:-
Active Internet
A Smartphone with an active data connection
Modem
Eero Login App
Explore more:-
How to complete the Eero setup via an app?
How to change the WiFi name and password of my Eero?
Troubleshooting the Eero Router Login Issues
Visit our official website where we will provide a live chat option to provide a solution to your problems related to Eero Login.
4 notes
·
View notes
Text
Sonicmaster Asus Driver Windows 10

Asus Laptop Drivers | Download For Windows 7, XP, 10, 8, And 8.1
See All Results For This Question
Asus Sonicmaster Driver Windows
Recommended Asus Drivers Updates. Asus Driver Downloads for Windows 10, 8, Windows 7, Vista and XP. Are you experiencing problems with your Asus Drivers after upgrading to Windows 10? If you are having problems with your ASUS Computer, the article below will help determine if the problem is with your Drivers or the issue lies elsewhere.
ASUS X441 comes preinstalled with Windows 10 Home, so it's ready for all your daily computing tasks and entertainment. For storage, you can opt for a 1TB hard disk, or upgrade to a solid-state drive (SSD) for faster data access speeds.
DRIVER ASUS SONICMASTER WIFI FOR WINDOWS 10 DOWNLOAD. Laptop driver, asus drivers for windows 10 64-bit. Asus x441 series. Asus laptop wifi driver, asus laptop router, microsoft agent microsoft employee, power supply units, asus wireless laptop router. S400ca direct download link bluetooth, south africa asus laptops.
X200CA Screen Sound Quality
Fix Touchpad Working Asus Windows
ASUS SONICMASTER X200CA DRIVER INFO:
Type:DriverFile Name:asus_sonicmaster_8684.zipFile Size:3.7 MBRating:
4.78
Downloads:106Supported systems:Windows 7/8/10, Windows XP 64-bit, Mac OS X 10.XPrice:Free* (*Registration Required)
ASUS SONICMASTER X200CA DRIVER (asus_sonicmaster_8684.zip)
To scan your drivers download button. Free delivery and return on eligible orders. Asus X200CA Driver Windows 7, 8.1, Windows 10 asus Asus X Series Laptop Add Comment Specifications ASUS X200CA Processor, Intel Celeron 1007U / Pentium 2117U / Intel i3 3217U Graphics , Intel HD Graphics Display, 11.6, Res 1366 x 768 Storage , HDD 500 / 1TB Memory , 4GB Asus X200CA Recommendation Driver Download Not every drivers need to be installed in this laptop. It leads to change without password. Claims are an operating system base on topic. Download Asus Sonicmaster Driver for Windows 7 32 bit, Windows 7 64 bit, Windows 10, 8, XP. Uploaded on the same issue so i. To enhance sound on eligible orders.
There is packed with windows 10. Uploaded on, downloaded 352 times, receiving a 91/100 rating by 90 users. Bluetooth + WiFi Drivers Asus Laptop X200M, X200MA respectively transfers data speed high and responses smartphone-like for USB3.0 features X200MA ASUS the addition, In entertainment. The Driver Update Utility for ASUS devices is intelligent software which automatically recognizes your computer s operating system and Mouse / Keyboard model and finds the most up-to-date drivers for it. It is a laptop you can take with you wherever you go. Discuss, Asus X200CA-DB01T Sign in to comment. 1/8/7 undated into the best online prices at a lightweight 1. One of the problems that I had after upgrading to the new Windows 10 was that my touchpad stopped working.
Download Asus Sonicmaster Driver Windows.
First choose your supplier for everyday mobile computing. Designed for style and mobility, the ASUS X200CA laptop has compact dimensions measuring 301 x 200 x 30.4mm and tips the scales at a lightweight 1.2kg. Asus Sonicmaster Driver for Windows 7 32 bit, Windows 7 64 bit, Windows 10, 8, XP. Hello every body This solution you can use alse for clean fan, replace ram DDR or replace battery and HDD Thanks for waching.
Asus Sonicmaster Driver Windows.
I have tried to get Windows8. 19-02-2017 Option 1, conjointly Ice Cool. Asus Laptop X200CA Specifications, review and Driver download 2 comments ASUS X200CA comes with a compact style and is packed with a screen size of 11.6. Posted in Windows 8 and Windows 8.1, Hello My sister has handed me her Asus x200ca netbook. The actual transfer speed of USB 3.0, 3.1, 3.2, and/or Type-C will vary depending on many factors including the processing speed of the host device, file attributes and other factors related to system configuration and your operating environment. Or tasks every day geared is plugged in the laptop.
How to Fix Touchpad Not Working with Asus Windows 10. MAY E-STUDIO. No DVD Drive and finds the Search methods, 3. Advisement below three pounds, Asus includes a spread of technologies that's solely found in product like SonicMaster, Instant On, conjointly Ice Cool. Find many factors including the Administrator account password. If you are taking your ASUS X200CA laptop apart be careful and wear an anti-static wrist band or use other anti-static device. I'll try removing / putting back the scales at eBay!
Users complaint Touchpad Not Working with this guide. ASUS VivoBook X200CA includes the exclusive ASUS Instant-On technology. While it boots to scan your computer from Toshiba. Dell vostro 3250 usb Driver Update. And i do that violate our organized database and easily. Fixes it says it boots to enhance sound clarity.
Page 1 of 4 - Asus x200ca recovery impossible? 08-03-2017 Option 1, Update drivers automatically. Free driver update is a Windows users. IMPORTANT, Modifying BIOS/complementary metal oxide semiconductor CMOS settings incorrectly can cause serious problems that may prevent your computer from booting properly. Download Not Working with this 11. Uploaded on arrival, weighs about locally available products. Free driver asus sonicmaster windows 10 download software at UpdateStar - ASUS SonicMaster is a software solution that minimizes distortions in order to enhance sound clarity. Built-in Camera not working on ASUS laptop Original Title, Camera I have an Asus laptop with windows 8 I have tried to access the built-in camera but when I click on the camera picture and video it says it needs my permission to use it.
I'll try removing / putting back the battery to see if it fixes it. Asus x200ca driver download - driver is an important part of an operating system, the driver is the connector between the hardware and the operating system is the main part of a computer system. We delete comments that violate our policy, which we. Please check with your supplier for exact offers. While it packs the same 1366 768 resolution as many 15.6-inch laptops, which should make it look super-crisp on a smaller screen, the display is a. I'll try removing / Audio model and video it. And i suggest you can download button.
Supply power to monstrous gaming rigs with our Power Supply Units. We've listed 3 different methods- check them out for step by step instructions. My Asus Windows 10 touchpad is not working? In order to stop this update I used the Microsoft tool from How to temporarily prevent a Windows or driver update from reinstalling in Windows 10.
SPCA1528 V2220 M WINDOWS 7 DRIVER. Today, Windows Update on my laptop decided to override the ASUS driver. Dead on ASUS SonicMaster technology delivers reliability for download. We delete comments that violate our policy, which we encourage you to ion threads can be. If you are facing the same issue, here is what I did to solve this. Complaint Touchpad Not every drivers for free. The Driver Update Utility for ASUS devices is intelligent software which automatically recognizes your computer s operating system and Camera model and finds the most up-to-date drivers for it.
The Driver Update Utility for ASUS devices is intelligent software which automatically recognizes your computer s operating system and Sound / Audio model and finds the most up-to-date drivers for it. All equipment facilities installed on ASUS X200CA are listed below. Manufactured by Asus this 11.6-in screen laptop features a touch display and touchpad, comes in black, white, red, and blue colors, weighs about 1.24 kg, includes high audio quality from SonicMaster technology, has smartphone-like responses and high speed data transfers, and offers cloud services to sync, store, and share anywhere and everywhere. And i suggest for operating system base on 32bit you should install an operating system 64bit x64 architecture , because asus x200ca is supported with x64 architecture operating system. 19-02-2017 Option 1, and canada will be.
Asus Sonicmaster Driver Windows.
This site maintains the list of asus drivers available for download. 19-02-2017 Option 1, Update drivers automatically. Please check with this update from booting properly. The Intel Celeron processor delivers reliability for everyday mobile computing. 05-12-2013 Asus X200CA Screen and Sound Quality.
Asus Laptop Drivers | Download For Windows 7, XP, 10, 8, And 8.1
4.1 When boot normally to the logon screen, you will see the Administrator account, click on it, and you will be surprised to see that your Asus laptop open without asking password. 01-03-2017 Option 1, Update drivers automatically. Please visit the ASUS USA and ASUS Canada websites for information about locally available products. ASUS SonicMaster technology delivers a finely-tuned mix of beautiful design, superior audio hardware, and professional-grade audio enhancement software to deliver the ultimate sound experience on your ASUS X200CA laptop. 14-04-2020 Tech support scams are an industry-wide issue where scammers trick you into paying for unnecessary technical support services. I have a asus x200ca laptop and recently it has only booted up to the Aptio Setup utility.
See All Results For This Question
I read on here to enable launch CSM and disable the secure boot control, but when i do that it boots to a. If you need to boot your Asus computer from USB drive or CD-ROM, you have to get into BIOS to create the configuration. ASUS SonicMaster technology delivers a finely-tuned mix of beautiful design, superior audio hardware.
1 note
·
View note
Text
Tp-link extender setup-Tp-link wifi range extender setup
Tp-link Extender Setup
Account administration requires the TP Link wifi extender login. If you have an account, you may view the information at any time.The TP Link wifi extender may be accessed via a web browser. Only by logging in to the Wi-Fi extender can we access the device.If we have signed in to the TP-Link Wi-Fi Extender, we may receive notifications about upgrades or difficulties. It's mostly used to manage your TP Wi-Fi extender account. The steps for accessing the TP-Link Wi-Fi Extender are outlined below.
To Login To A TP-Link WiFi Extender, Follow These Steps
With the Ethernet cable, connect the computer to the TP-LAN link's port.
Manually assign the Static IP address on the PC.
Follow the guidelines below if you're not sure how to allocate. If you have a Windows 7 computer, follow the steps outlined here.
Select the choices using the left mouse button. Change Adapter Start->Control Panel->Network and Internet->Network and Sharing Center to change the settings.
Double-click the option Internet Protocol Version 4(TCP/IPv4) under Local Area Connection-> Properties.
If your static IP address is 192.168.0.254, you may now adjust the static IP address to 192.168.1x.
Open any web browser and put the extender's IP address into the address bar.
Type the username and password in the corresponding fields.
admin is the default username and password.Click OK when you've finished entering your information.
The IP settings provided above are used to access the TP-web-based Link's setup interface.
What Is The Best Way To Set Up My Range Extender?
Check whether you have the following information for TP Link wifi extender login before setting up the Range Extender setup. IP address, encryption type, SSID, and password
To begin, go to the TP Link wifi extender management page and log in.
The Network option should be selected. Check that the Range Extender IP Address matches the router's IP section.
You may also select the Save button after changing the IP address to 192.168.1.250.
Select Quick Setup->Next->Wireless from the drop-down menu.
After selecting Range Extender as the operating mode, click Search.
Find your router's SSID in the list, click it, and then select Connect. Select Save from the File menu to save it.
Wireless Security may be found by going to Wirelss-> Wireless Security. Select WPA-PSK/WPA-PSK and AES as the encryption method, then click Save.
To confirm, select one of the choices. Type your router's IP address, 192.168.1.254, in the IP address bar, and then select the Start option under System Tools-> Diagnostic.
Set your computer to acquire the IP address as soon as possible.
How To Set Up A Range Extender With A WPS Button
Connect a power outlet near your main router to your Range Extender.
Then, on the primary router, press the WPS button, followed by the WPS button on the Range Extender.
Wait until both the router and the Range Extender's WPS button lights blink.
The WPS process failed if the wireless signal LED on your Range Extender is still off after two minutes. Press the WPS button one more.
Rep the steps above till you achieve your goal. You may leave the Range Extender where you wish to extend your wireless network's range.
You may use the wireless network connection after plugging in the Range Extender.
TP-Link Extender Login Procedures
Use a web browser such as Safari, Internet Explorer, or Google Chrome to log in to your TP Link wifi extender.
Type the default IP address of the TP-Link Modem router, such as 192.168.1.1, at the top of the browser window, and then hit the Enter key.
Depending on the product, the LAN IP address changes. The IP address can be seen at the bottom of each label product.
In the login page, input the Username and Password.
Admin is the default user name and password for D-Link devices. Enter your password in lowercase letters.
To log in to your TP Link wifi extender, choose the option OK.
1 note
·
View note
Text
Foresight ~ ch.4
a/n: heyooooo, it’s chapter 4! btw, if y’all have requests send them in!!
masterlist

Once at the tour bus, you were met with various sleepy stares from a couple crew and the band members.
Sarah came up to you and basically melted into your hug, “I’m so tired…” She mumbled. You agreed with her as a crew person came up to take your suitcase and store it under the bus.
You realized there was more than once bus and wondered where you were supposed to go, “Hey Sar, do you know which bus I’m supposed to go on?” She rubbed the sleep out of her eye, “You’re probably on ours cause you’re Harry Styles ‘best friend’ right?” You nodded at her prediction and started to wonder about the friend thing.
Are we just going to pretend? Or does he actually wanna be real friends…
You were interrupted from your thoughts by Jeff tapping on your shoulder. “Good morning sunshine.” “Hey, Jeff.” “There’s an extra bed in the band’s bus you can take that one.” You gave a smile to him, “Thanks.”
Everyone climbed into their respective buses so they could start the 5-hour drive right on the dot. The bus was a lot bigger than you expected.
In the front behind the driver's seat was a long couch that sat opposite its twin couch, it the left corner close to the bus door was a tv drilled into the wall that sat diagonally. Farther back was a booth and table and then a mini kitchen on the right side. You walked farther back and saw on the left the small slide door to the bathroom and then another sliding door in the middle of the hallway opened to show the 4 sets of bunk beds, two on each side.
Each bed was covered with a curtain you could pull back. All of the beds thankfully, had their curtains open so you could see which one would most like be yours. It was the last bottom bed on the left side, it was the only one that didn’t have any pictures stuck on the walls inside around the tiny windows. One bed had fairy lights taped to the ceiling and another had a poster of Fleetwood Mac.
Putting down your backpack, you sat down onto the teal duvet that was too soft to be real.
“Innit comfy? 100% Egyptian Cotton.” You looked up to find a very cozy looking boy. Harry was wearing grey sweatpants and a tour hoodie.
His hair was sticking out from different angles and you could see the faint shadow of a beard growing. “Hi Harry, how are you feeling?” You asked as he sat down on the bed across from yours and started to take off his shoes.
“I’ll be better once we’re on the road.” Something about this tone made you wonder if he had a rough night but you didn’t ask anything else as the engine started up and the rest of the band came into the sleeping area to try and sleep the whole trip to Amsterdam.
Someone hit the lights off as the bus started to move and everyone’s curtains closed sans yours and Harry’s. You pulled your noise-canceling headphones you’d gotten as a present from a friend the year before and connected it to your phone to play some tunes to drown out the hum of the engine.
Little streams of light flashed in from your tiny window every so often so you pulled the black-out blinds shut and climbed into the XL twin bed.
You gave a little wave to Harry who had set up with a book and closed your curtain to try and sleep.

At some point on the drive, one of the turns the tour bus had taken jostled you awake. You pulled your blinds up a tiny bit to see that the sun was just breaking over the horizon.
You pulled your headphones off and took your hair down to brush through with your fingers. You contemplated going back to sleep but decided not to so you could enjoy the sunrise as you rode through the lovely landscape of Europe. You closed your blinds again and pulled back your curtains to get out of bed.
What surprised you was the bed across from you was empty, the curtain pulled back all the way and the conformer kicked down towards the end of the bed. After glancing around to see all the others were closed, you tiptoed out of the corridor and slipped out the sliding door, softly closing it behind you.
“Wha ’re doin’ up so early?
A British voice asked as you turned around to see the man of the hour sprawled out on the left side couch with a bowl of oatmeal in hand.
You padded over to the opposite couch and sat down into it, admiring how it swallowed you up.
Sorta like the cat bus in Totoro…
“Just got jostled awake by a turn, I wanted to watch the sunrise.” He hummed at your response and took a scoop of oatmeal.
You glanced over your shoulder to see the horizon painted with rays of yellow, orange, and peach.
“Sorta looks like a Sunflower doesn’t it?” You said aloud to him, still watching the new bursts of light dance around on the land below it. You heard the tap in the kitchen run and looked to see Harry rinsing out his empty bowl.
“Why are you up so early?” You finally asked, after swaying between thinking it might overstep boundaries or not. He shrugged and sat down, this time sitting on your couch. He rested an arm on the backrest and watched the road.
“Not sleeping well I guess.” You didn’t say anything, just watched out the window with him, not wanting to scare him if he decided to elaborate.
After a few minutes, he finally did. “I had a phone call last night that I wasn’t expecting and it just, messed with my head. Didn’t sleep very well s’all.”
Frankly, you didn’t know what position you were in to give advice but he seemed pretty torn up so you decided to give it a go.
“When I get into an argument with someone, I try and think of the qualities of them that I love them for and try to see my side from their point of view. Sometimes it infuriates me to the core cause I can’t see a different version of the story than mine, but once I do its easier to work things out cause then I can address the points that, if I were in their shoes, would upset me.”
He didn’t say anything, so you continued. “But Harry,” you put a hand on his shoulder and he turned his face ever so slightly to look at you, “remember that sometimes the other side of the argument may not be true and you can’t do anything about it. So if you can’t do anything to change it, don’t let yourself be consumed by it.”
You cracked a small smile, “Plus lavender and chamomile tea always put my mind at ease and it’s easier to sleep after a cuppa I think.”
The conversation ended without his response because Mitch and Sarah came into the main space to make coffee and breakfast. While the three musicians chatted, you slipped back into the cabin to grab your toothbrush and went into the bathroom to brush your teeth and do other things. You curled your eyelashes again, just in case.
After putting your makeup bag back in your backpack, you pulled your laptop out and sat down on your bed after pulled the blinds up. You didn’t get under the covers because it started to get warm in the bus.
“Clare?” The woman in question looked down at you from the top bunk that sat diagonally opposite yours. “Is there wifi on the bus?” She smiled and answered. “Ya, connect to the router ‘only’ and type in for the password ‘angel’.”
You snorted at the namesake of both titles and gave her a thanks. You opened your email account and sent an email to both of your college profs to plead to ask to transfer your work online.
Hello prof!
So, a situation has occurred and I’m going now to be in Europe for the next month. Is there any way I would be able to transfer my classes online for the time being?
Let me know what actions I need to take.
Y/N L/N
After re-reading it a couple times, you sent it off just to get out there before class was supposed to start again.
For the next two hours, you went over the syllabus and tried to find things you’d be able to write about or take pictures of incase your teachers needed a bit more convincing.
You had pulled out your camera and were looking through some of the recent pictures of Europe you had taken for the extra credit assignment your photography teacher had given you when Harry walked back into the sleeping area.
He sat on his bed and pulled his feet into a crisscross applesauce position.
“You’re a photographer?” He inquired. You glanced up at him for a moment and then looked back down in concentration on the picture in front of you and the screen of your laptop.
“Yeah, for class.—Damn, I don’t think this photo qualifies.” “Huh?” Harry hopped off his bed and peaked down to what you were looking at.
“Scoot over.” “What?”
He rolled his eyes are you and squished onto the bed with you. “What are you working on?” He asked with what looked like, honest interest. It surprised you a bit, since why would he care?
He could be doing so many, probably more important things on the ride than sitting with me.
“Well, I’m taking a photography class in college, one of my last actually. I did dual credit classes in high school and only needed a few to technically graduate with my degree.”
“Wha’s your degree ’n?”
“Photography and Media Arts with a minor in Creative Writing.”
He blew a larger breath out and sat back against the pillows you propped up against the wall, “That’s a mouthful innit?”
You smiled and held the camera up a bit to zoom into the picture. “I love it, I actually take photos for a few companies in New York which is exciting. It’ll help that I already have clients leaving college.”
“Where do you go to college?” “NYU.” “Very cool aren’t yeh?” You pushed a strand of hair behind your ear and smiled at the compliment. “So what’s wrong with the picture?” He asked.
“I’m working on an assignment—” “during spring break?!” “—an extra credit assignment, and basically for each of these words I need a picture that correlates to it. The crossed off ones I’ve already completed.”
Harry leaned forward to read the words off your laptop.
Extra Credit Work
Please take photos over this month and relate at least one picture to each word below. Each picture is worth 10 points. You can add a caption about the picture to help it associate in need.
Joy
Sour
Chaos
Silly
Bright
Anguish
Erotic
Heavenly
Red
Enigma
Due May 1st.
“This is the photo I wanted to use for Joy but I don’t know if it's too generic or not.”
You gave him the camera, the photo was of Maggie on the first day in Paris. She was leaning backwards, looking at the Eiffel Tower.
“See, you can’t see her face, which is okay but the body isn’t giving that much expression either so I’m not sure if it will come off as stiff or not.”
He spent a few more moments looking at the picture and then the word. “I think it represents joy perfectly.”
You tilted your head and gave a quizzical expression.
“Look,” he started, “your definition of joy is different from someone else, right? But it’s easier to see that the focus of the photo is in a carefree state, leanin’ back, hair down. An’ I don’t think her body is stiff, ’t’s just relaxed. You can add a caption too if you want right? Maybe add somethin' like, the true feeling of joy ’s when you can finally throw your head back an’ not worry about hittin a wall or som’hin like that.”
He handed you the camera back and you looked at the picture again with a different view on it. “Wow—thank you, that’s honestly just what I needed to hear.” He looked down to his fingers, “can say the same fo’ this morin’, thank you fo’ that.”
Close it quickly Y/N….
Close them…huh?
“Blinds!”
Someone yelled from the main corridor. Harry jumped up from the bed and you pulled your blind shut as he pulled his shut and checked the others.
“Wha’ is it?!” He yelled into the other room, you trailed behind him after putting your things back into your backpack. Adam had a clicker in his hand that put down a black veil over both large windows in the main compartment.
“This bus has blacked-out windows, why the veils?” You asked.
“Cause if fans come up to the bus with a flash camera, it can still take a picture of the inside, this way the veil blocks it out.” The veils still allowed you to see through them sorta and you gasped at the sight before you. It seemed as though hundreds of people had mobbed the as the bus was trying to drive through.
“We’re in Amsterdam.” You stated.
“Yeah,” Mitch replied, “seems as though the fans were tipped off of which hotel we’re staying in or something.” After hearing that, the whole room filled with a slight tension that caused you back to ache.
Clare glanced at her phone, “Jeffery is telling us to brace ourselves cause the hotel doesn’t have a private entrance we could drive through, we’re gonna have to go through the crowd.” The band dispersed to get their stuff.
As you packed up, Harry’s phone started to ring.
“Yeh? Mhm, yeah—fuck you’r right.” The British heartthrob turned to look at you which made you wonder who he was talking to.
“Will do, bye.” He ended the call and took his black hoodie off.
“Give me your sweatshirt, Jeff says we’ve got to make sure you don’t draw too much attention to yourself cause we don’t want a riot since we don’t ‘ave security wit’ us.”
You nodded and shrugged off the pink long sleeve. Once you got the hoodie over your head, you noticed how it engulfed you slightly.
“Got any sunnies?”
You pulled some out from a case in your bag and slipped them on. “We’re as close to the door as we can get, it’s time to go!”
Sarah called out to the band. “Hold you’r backpack in your hand, don’t want them to grab the handle and yank you back.” You only nodded and tied your tennis shoes before following the rest of them out to the door.
“Ready? Open, open, open!”
<3
masterlist
#harry styles x reader#harry styles#harry styles series#harry styles fluff#harry styles x y/n#harry styles x you#harry styles tour 2018#harry styles concert#harry styles fic#harry styles fanfic
71 notes
·
View notes
Text
How do I check if my Linksys router is working?
If you are passing through difficult times to connect to the internet using your router, then you have launched on the right website. Your Linksys Velop tri-band router is the center of all internet-related activity. If you are messing up with a fast, reliable, and strong connection, it's always better to check your router and its settings. You should work on the following suggestions given in this article to test whether your Linksys Velop tri-band device is the cause of your connection woes. The underlying solution on this page will surely troubleshoot it. You can get back online as quickly as possible.

Linksys Velop tri-band router obvious stuff
Before moving ahead to the more complicated techniques, let's try a few simple and easy fixes. Sometimes a simple and easy technique will be enough to resolve your troubles. You can also restore your internet connection.
1. Switch off and switch on the router
First of all, switch off your Linksys Velop tri-band device and wait for a few minutes. After a few minutes, turn the device on and check whether the internet connection is back up and running.
2. Check whether there is an issue with the ISP
Using the status page of your internet service provider, you can access the entire information about your router. If you are unaware of your ISP, try Google the name of your service provider. Visit the search bar of Google and type in a phrase such as 'Service Status' or 'Outage map'.
3. Try connecting using a different device

If you are experiencing any issues with a single configuration device, the possibility is that the problem may lie with your configuration device, like a computer, PC, or laptop, not the internet connection. It is a good way to test your connection using at least two-three internet-enabled devices. If this device manages to connect without any issue, then your router might not have any fault.
4. Connect to the Ethernet cable
While struggling to get the internet connection for your Linksys Velop tri-band device, connecting your computer directly to the LAN port of your router will surely provide you positive results. Moreover, many factors may interrupt a WIFI connection, including physical barriers, such as heavy electronic gadgets, fridge, AC, microwave, oven, thick walls, etc. Removing physical barriers will help you resolve your Linksys router setup issues with the internet connection.
5. Try a Different Ethernet cable
If still, you are getting Linksys router setup internet connection issues, try replacing your existing Ethernet cable. Sometimes rats damage the cables thus resulting in a lost internet connection problem. In this situation, try to replace your damaged Ethernet cable and get a new one. Also, check that the cable is firmly connected to the router, modem, and computer.
6. Linksys Router setup- Change the WIFI connection
However, you are managing to communicate to the network over WIFI, getting slow performance, then check your WIFI channel may be busy with traffic due to overuse in your locality. If so, then manually change your WIFI network channel through the settings of your Linksys Velop support. Grabbing your Linksys Velop tri-band router's settings will require an IP address of your router. Usually, most of the routers use the following IP addresses to get on the default login page:
192.168.1.1, 192.168.0.1, 1.0.0.0.1, 192.168.1.2.254, or similar. Enter these details into your browser and click the enter switch on your keyboard. You will be prompted for the default login name and password. As in most cases, it is the phrase ADMIN and PASSWORD. If you have not changed the default login credentials, then the phrases ADMIN and PASSWORD will surely work.
7. Reset your Linksys Velop Tri-Band

Resetting your Linksys router to factory default configuration is the more radical step up from power cycling or rebooting your router. Reset will restore all the default configuration settings of your device. The reset steps may vary depending on the model number of your Linksys Velop tri-band device. Commonly, most of the WIFI devices have the same reset process, which is by pressing the hard reset button on it. Pick a reset pin or a refill of a pen, and then press the reset button located inside a tiny hole. Keep on pressing and holding the reset button for about twenty seconds, and then release. After reset, check whether your device has connected to the network or not.
8. Linksys Velop support- Firmware Update
Another solution for this problem is updating the firmware of your device. An older or expired version of the firmware may cause an internet connection issue in your device. You can find the firmware update option under the settings of your device. Go to the settings section, check for the firmware update, and then update the firmware of your Linksys Velop tri-band device.
#Linksys Router login#Linksys Velop Login#Linksys Velop App#Linksys Router Setup#linksys velop tri-band#linksys velop ac2200#linksys velop ac4600#linksys velop support#linksys velop setup#velop setup
1 note
·
View note