#hmac
Explore tagged Tumblr posts
Photo

Tomorrow!!!! Join Smoothie King Friendswood & Grand Central Park at the AKA Houston Metropolitan Area Chapters “Black In Business Market!” Over 40+ black owned businesses will be showcasing their products and services. Scan the QR Code to register for this FREE event!!! We look forward to seeing you there!🛍️ @smoothiekinggcp @smoothiekingfriendswood #HMACBlackinBusinessMarket #BlackInBusinessMarket #BuildOurEconomicWealth #HMAC #BlackInBusiness #doorprizes #giveaways #blackownedbusiness #OmicronTauOmega #SpringAKAs #WeAreSouthCentral (at Fifth Ward Multi-Service Center) https://www.instagram.com/p/CpEsJoMO23e/?igshid=NGJjMDIxMWI=
#hmacblackinbusinessmarket#blackinbusinessmarket#buildoureconomicwealth#hmac#blackinbusiness#doorprizes#giveaways#blackownedbusiness#omicrontauomega#springakas#wearesouthcentral
0 notes
Text
#micromodels #papercraft #hmsarkroyal #modelship #aircraftcarrier #papermodel #hmacarkroyal this thing was hell. #worldwar2 #worldwarii #ww2 #wwii
instagram
#micro models#paper craft#hms ark royal#hmac ark royal#model ship#aircraft carrier#paper model#world war 2#world war ii#ww2#wwii#original content#Instagram
0 notes
Text
Reference archived on our website
This is an issue with far too little study done. It also makes the ban on gay men (and trans women) giving blood because of the potential for HIV seem all the more silly when nearly everyone who gives blood in the US has had at least one covid infection since 2020.
Abstract Background In 2022, the SARS-CoV-2 Omicron surge affected 8.8 million people in Taiwan. This study delves into how the transition from containment to mitigation strategies in COVID-19 control has altered concerns regarding transfusion safety.
Methods Blood donations during 2020–2022 in Taiwan were included. Donation details and post-donation information (PDI) were retrieved to assess donation fluctuations and incidences of various PDI. The main effects of PDI reporting were assessed using chi-square test and logistic regression. Additionally, from April to August 2022, we collected disease information from COVID-19 donors, and tested their repository specimens for SARS-CoV-2 RNA and antibodies.
Results Before 2022, when containment measures were in place, only 8 blood donors with COVID-19 reported PDI. However, by mid-2021, there was a significant decrease in blood donations. In 2022, with mitigation strategies implemented, a total of 3483 donations reported COVID-19 PDI. The incidence of all cause PDI increased from 10.5 per 10,000 donations in 2020–2021 to 29.9 per 10,000 in 2022, with nearly 70% of PDI being related to COVID-19. Female donors reported more PDI events. Additionally, the incidence significantly decreased with age. A total of 1148 repository specimens from COVID-19 donor were tested, revealing no detection of SARS-CoV-2 RNA. The seroprevalence rates of anti-nucleocapsid(N) and anti-spike(S) antibodies were 0.61% and 98.4%, respectively.
Conclusion Transfusion safety concerns in Taiwan progressed alongside the evolution of control strategies, with a one-year delay following the pandemic started. The absence of RNAemia among COVID-19 donors indicates that precautionary measures were commensurate with the risk.
PDF Link: pdf.sciencedirectassets.com/276220/AIP/1-s2.0-S0929664624004078/main.pdf?X-Amz-Security-Token=IQoJb3JpZ2luX2VjEHkaCXVzLWVhc3QtMSJIMEYCIQDtypwhWajL3XC253cVb6ZNKMbwDNp6jgtcURJpktk%2FSgIhAPM1UeAQ8OwCdo1aZxlQQ4L2THphJ3P81Xbsshkew6u2KrwFCLL%2F%2F%2F%2F%2F%2F%2F%2F%2F%2FwEQBRoMMDU5MDAzNTQ2ODY1Igz%2Bx%2BDYSAK%2FRTPcpHcqkAUfb6cmkl4IhHmwP%2B0ZzRZKxvyKgc%2F2AFPpg%2F5EkaoejS1A6GwsG%2BGeWY%2FHJnRVKrMZDYBByGGFYBd7Kl79rNF54Vb8WB6pFcaa9FnQMQWqHcMtgrPFwytleYXWH04d15z0vI5pZGD2N33WUoYyCP2SWTqbIa%2FFRkhqgRLlY7aMfFYAeybdOGhgbqnPbVHKNTtPHAr83vd7opEVB%2FYI9bVVXdlutn5m2QL874KfV6CrTZjxRPUs9a6pEpkcmBqS%2FBuJjfMv9%2F9%2FQhDbdYXiAIy4KI9tmerzCACYHbiBWXr1v9bLBrQ0vdMAnadkNlPYGttR0mJLAHuLK3EYYDzyD3BG5ri9zXJm7IO0BTfh8ra3B4XV1NCm2txFC2ACYH4Y54F04NBSDHSGeHSsEyVvu%2Fz68DZHs8Waxfdm%2BtFfJOSXE%2BAcvsrW0wTF4jhk%2BLTMu1erekb1NCw5Llx5iZpcOn%2BezOApPW56nW31n1VgDh7wBCsRq685W11CGiIwcqvwd8pJH1EAgfQ4amrn3sfVC%2B22flmZqaAsN2kVkfRk7GO3LOfFWR9c1DgaPGEPIma83j3pSz%2BAkFKZbMnW9XrOVITFgbbhLkgGB0u5QSTuR4XfgUI217Jy07bosxuRDdHadvlavnX2FkMb1nVQGsMgC3Yl41koRJehVeljQA3zJ1jMmZtHfm2fUjtbxVtAlID%2BUepDR3SwYcEiDYQplM28mFCwrsabyP0y81AjcEadicH9MAub34aHpCH9lq0E9%2BwvE50ygeKvTGa2QFKr%2FKMKPWCMpAfLQO8Iq4ci876Sz9i0pwYsz56PSSTOZqmIuvcsTpiRwK29693pqIbFk366fzE7wKuRZipy%2FIIsIPhk49mNLDDV%2B8K3BjqwAVbQTLyuiW9cZbBMWTzoG8sB6%2F7Tu0rlfzbWrI86Y0XpNYHQ4lfscFOr4bQeW04Dg6eduakfoeylbmUPxVdjcuAiqZxMKWw7DW4j7odg9BhfaU22tqj4FoTF0mKRu920W1K2LI7MSTZ2FmGsP0IdlHKhzSlw4ALZFcQCIifrfrwjn8bf07oCuBUXhdSwFJiRGVURZzXlui2oZUSpbBmrFPTuL0GuvWXr%2Be1mk4mQDC3c&X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Date=20240923T014252Z&X-Amz-SignedHeaders=host&X-Amz-Expires=300&X-Amz-Credential=ASIAQ3PHCVTY4FZKJMDF%2F20240923%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Signature=b164b5228d59cec0937af8f03afb64239adbb65066baddd16efbf085353a2fdc&hash=2cf460b85bd79677372b88d052b288b7bc32a58429b52f459102501962acb59f&host=68042c943591013ac2b2430a89b270f6af2c76d8dfd086a07176afe7c76c2c61&pii=S0929664624004078&tid=spdf-362f3e80-e162-4ee7-bb62-39ce4c3a60a3&sid=6bc94e215859e34e3758e1f3ee711ec038d7gxrqa&type=client&tsoh=d3d3LnNjaWVuY2VkaXJlY3QuY29t&ua=1b175a03505205525c&rr=8c76d733bfdde6fe&cc=us
#mask up#covid#pandemic#covid 19#wear a mask#public health#coronavirus#sars cov 2#still coviding#wear a respirator
34 notes
·
View notes
Text


I came back from Davao, where I attended the wedding of a relative there as a flower lady (if you ask me, I just received a flower crown to wear there). Also, no birds or insects were harmed in the wedding as well.
With the wedding as an inspiration, here’s Queen Rose in her wedding gown, which she wears when she marries Billy Reverb. The design is inspired from Barbie Princess Charm School and Elsa’s first snow queen dress but I added a pale pink overskirt which also acts as a train in her wedding gown. Her bouquet has seven roses in rainbow colors and she wears simple pearl jewelry with gold and pink gems to go with the Crown of Harmony. She had her hair styled in a half-up, volumized bun that her grandma, the late Queen Celestia wore when she married Rose’s grandpa, the late king, but she added a modern twist, with the rest of her hair in curls.
Original pattern: https://img.freepik.com/free-vector/gray-white-crystal-textured-background_53876-86343.jpg?w=1380&t=st=1720356100~exp=1720356700~hmac=37dc33e9c0a1c6c4648762081336fbd7940c33e5cbbc06dee290491109a6b8a8
#dreamworks trolls#trolls world tour#trolls trollstopia#trolls band together#trolls oc#trollsona#queen rose#wedding gown
13 notes
·
View notes
Text
JINJER Announces Fall 2024 North American Tour With HANABIE And BORN OF OSIRIS

Ukrainian modern metallers JINJER will embark on a North American tour in the fall. Support on the trek will come from fast-rising Japanese metalcore unit HANABIE and progressive metalcore mainstays BORN OF OSIRIS.
As JINJER is currently in the studio recording its fifth studio album, fans can expect to hear a handful of brand new, never-before-heard tracks on the tour.
The 18-date tour will kick off on September 20 at in Sayreville, New Jersey and will include a couple of Canadian shows (in Toronto and Montreal) before wrapping up on October 13 at Sacramento, California's Aftershock festival.
In addition to Aftershock, the tour will also see JINJER performing at festivals such as Metal Injection Festival, Louder Than Life and the return of the mighty Mayhem festival.
Various ticket presales via Citi, Ticketmaster, Live Nation and more begin today, with general public on-sale beginning this Friday, June 14 at 10:00 a.m. local time.
JINJER comments on returning to North America: "It's finally time for some huge announcements: We're stoked to report that this September, JINJER will return to North America with not only two absolutely sick supports: HANABIE and BORN OF OSIRIS! Most importantly, we'll be performing some brand new unreleased songs from our upcoming fifth studio album. [We] just cannot wait to share what we've been working on for the last two years. This will be without a doubt a banger of a tour … We're looking forward to this so much!"
JINJER fall 2024 North American tour dates:
Sep. 20 - Sayreville, NJ @ Starland Ballroom Sep. 21 - Brooklyn, NY @ Metal Injection Fest Sep. 22 - Pittsburgh, PA @ Roxian Theatre Sep. 23 - Toronto, ON @ Danforth Music Hall Sep. 24 - Montreal, QC @ MTELUS Sep. 26 - Harrisburg, PA @ HMAC Sep. 27 - Baltimore, MD @ Baltimore Soundstage Sep. 29 - Louisville, KY @ Louder Than Life Oct. 01 - Charlotte, NC @ The Fillmore Oct. 02 - Atlanta, GA @ Buckhead Theatre Oct. 03 - Lake Buena Vist, FL @ House Of Blues Oct. 04 - North Myrtle Beach, SC @ House Of Blues Oct. 06 - Houston, TX @ House Of Blues Oct. 07 - San Antonio, TX @ The Aztec Theatre Oct. 09 - Denver, CO @ Ogden Theatre Oct. 11 - Las Vegas, NV @ House Of Blues Oct. 12 - San Bernardino, CA @ Mayhem Festival Oct. 13 - Sacramento, CA @ Aftershock Festival
During an appearance on a recent episode of Knotfest's "She's With The Band", the show hosted by Tori Kravitz, JINJER vocalist Tatiana Shmailyuk spoke about the progress of the songwriting sessions for the follow-up to the band's 2021 album "Wallflowers". Tatiana said: "My purpose is just to write lyrics and sing them. I'm so behind right now with the writing lyrics. And I warned my guys. We were at least to get a really rough draft, rough sketch or a demo of one song, like maybe first single from the new album, at least get this, but nope. [Stress and creativity don't] work with me. Well, but when the deadline's coming, and everybody knows that — I've been talking, like, every single time we release a new album, I say that, I say this — deadlines push me. So I just have to write, so I get this stream of consciousness, basically. I write down whatever the bullshit is in my head. And then you build it. At least you have to have bricks to build a poem or whatever it is, just lyrics."
Regarding the musical direction of the new JINJER material, Tatiana said: "It's gonna be different, first of all, because I feel that the music differs a lot. And to my mind, the whole — I won't say how many songs are there; I guess 12 or even 15; let's say 13; I don't remember — but they all have… not all of them, but half of them, at least, they have a similarity in them. They're similar to each other or they remind me. They have this concept within — without any lyrics, they still sound like they belong to one box. They are a set of songs. And I already think about all the… I'm not even thinking about like the lyrics — I think about the topics and stuff, but I think about the booklet or the cover or even the music videos and what I'm gonna wear there. And it has a certain flavor to me that… I feel like it has this flavor of 19th century. It's very romanticism from the 19th century. If you listen to it, you will think, 'Oh.' You know, when you listen to MUSE, you feel he was inspired by a lot of classical composers — obviously. So our new music has this flavor. And I'm so excited."
JINJER released its first official live DVD/Blu-ray, "Live In Los Angeles", on May 17 via Napalm Records. Recorded and filmed on December 22, 2022 at The Wiltern in Los Angeles, this offering is intended to celebrate not only getting through the last few years in one piece, but also the band's 15-year career.
"Live In Los Angeles" was a spontaneous decision by the band, recorded as raw as possible, to emphasize the passion that can come from a live show. This release is an explosive mixture of JINJER's discography — featuring fan favorites like "Sit Stay Roll Over", "Home Back" and the game-changing "Pisces". The live album contains 16 songs in various audio formats, with some strictly limited: the deluxe digipack features not only a DVD, but also two more songs, "Wallflower" and "Disclosure!", recorded in Paris in 2023.
JINJER is:
Tatiana Shmayluk - Vocals Roman Ibramkhalilov - Guitars Eugene Abdukhanov - Bass Vlad Ulasevich - Drums
Photo credit: Lina Glasir

9 notes
·
View notes
Text

so is it possible to take random outfits off the internet and slip the model into them. the only alteration it made was the chest Logo but it pretty much maintained everything else.
https://downloadscdn6.freepik.com/1258/71/70536.jpg?filename=old-black-background-grunge-texture-dark-wallpaper-blackboard-chalkboard-concrete.jpg&token=exp=1729285569~hmac=73ea8e2880abcde9ce4a3f4bd64a7702
Above is the link to the background used.
finally filtering her through video , quality isn't terrible but need work on gestures and showing emotion. some of this I can probably just manually edit and fix. weird a little seeing her face with no makeup..
2 notes
·
View notes
Text
Exploring Kerberos and its related attacks
Introduction
In the world of cybersecurity, authentication is the linchpin upon which secure communications and data access rely. Kerberos, a network authentication protocol developed by MIT, has played a pivotal role in securing networks, particularly in Microsoft Windows environments. In this in-depth exploration of Kerberos, we'll delve into its technical intricacies, vulnerabilities, and the countermeasures that can help organizations safeguard their systems.
Understanding Kerberos: The Fundamentals
At its core, Kerberos is designed to provide secure authentication for users and services over a non-secure network, such as the internet. It operates on the principle of "need-to-know," ensuring that only authenticated users can access specific resources. To grasp its inner workings, let's break down Kerberos into its key components:
1. Authentication Server (AS)
The AS is the initial point of contact for authentication. When a user requests access to a service, the AS verifies their identity and issues a Ticket Granting Ticket (TGT) if authentication is successful.
2. Ticket Granting Server (TGS)
Once a user has a TGT, they can request access to various services without re-entering their credentials. The TGS validates the TGT and issues a service ticket for the requested resource.
3. Realm
A realm in Kerberos represents a security domain. It defines a specific set of users, services, and authentication servers that share a common Kerberos database.
4. Service Principal
A service principal represents a network service (e.g., a file server or email server) within the realm. Each service principal has a unique encryption key.
Vulnerabilities in Kerberos
While Kerberos is a robust authentication protocol, it is not immune to vulnerabilities and attacks. Understanding these vulnerabilities is crucial for securing a network environment that relies on Kerberos for authentication.
1. AS-REP Roasting
AS-REP Roasting is a common attack that exploits weak user account settings. When a user's pre-authentication is disabled, an attacker can request a TGT for that user without presenting a password. They can then brute-force the TGT offline to obtain the user's plaintext password.
2. Pass-the-Ticket Attacks
In a Pass-the-Ticket attack, an attacker steals a TGT or service ticket and uses it to impersonate a legitimate user or service. This attack can lead to unauthorized access and privilege escalation.
3. Golden Ticket Attacks
A Golden Ticket attack allows an attacker to forge TGTs, granting them unrestricted access to the domain. To execute this attack, the attacker needs to compromise the Key Distribution Center (KDC) long-term secret key.
4. Silver Ticket Attacks
Silver Ticket attacks target specific services or resources. Attackers create forged service tickets to access a particular resource without having the user's password.
Technical Aspects and Formulas
To gain a deeper understanding of Kerberos and its related attacks, let's delve into some of the technical aspects and cryptographic formulas that underpin the protocol:
1. Kerberos Authentication Flow
The Kerberos authentication process involves several steps, including ticket requests, encryption, and decryption. It relies on various cryptographic algorithms, such as DES, AES, and HMAC.
2. Ticket Granting Ticket (TGT) Structure
A TGT typically consists of a user's identity, the requested service, a timestamp, and other information encrypted with the TGS's secret key. The TGT structure can be expressed as:
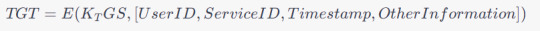
3. Encryption Keys
Kerberos relies on encryption keys generated during the authentication process. The user's password is typically used to derive these keys. The process involves key generation and hashing formulas.
Mitigating Kerberos Vulnerabilities
To protect against Kerberos-related vulnerabilities and attacks, organizations can implement several strategies and countermeasures:
1. Enforce Strong Password Policies
Strong password policies can mitigate attacks like AS-REP Roasting. Ensure that users create complex, difficult-to-guess passwords and consider enabling pre-authentication.
2. Implement Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of authentication. This can thwart various Kerberos attacks.
3. Regularly Rotate Encryption Keys
Frequent rotation of encryption keys can limit an attacker's ability to use stolen tickets. Implement a key rotation policy and ensure it aligns with best practices.
4. Monitor and Audit Kerberos Traffic
Continuous monitoring and auditing of Kerberos traffic can help detect and respond to suspicious activities. Utilize security information and event management (SIEM) tools for this purpose.
5. Segment and Isolate Critical Systems
Isolating sensitive systems from less-trusted parts of the network can reduce the risk of lateral movement by attackers who compromise one system.
6. Patch and Update
Regularly update and patch your Kerberos implementation to mitigate known vulnerabilities and stay ahead of emerging threats.
4. Kerberos Encryption Algorithms
Kerberos employs various encryption algorithms to protect data during authentication and ticket issuance. Common cryptographic algorithms include:
DES (Data Encryption Standard): Historically used, but now considered weak due to its susceptibility to brute-force attacks.
3DES (Triple DES): An improvement over DES, it applies the DES encryption algorithm three times to enhance security.
AES (Advanced Encryption Standard): A strong symmetric encryption algorithm, widely used in modern Kerberos implementations for better security.
HMAC (Hash-based Message Authentication Code): Used for message integrity, HMAC ensures that messages have not been tampered with during transmission.
5. Key Distribution Center (KDC)
The KDC is the heart of the Kerberos authentication system. It consists of two components: the Authentication Server (AS) and the Ticket Granting Server (TGS). The AS handles initial authentication requests and issues TGTs, while the TGS validates these TGTs and issues service tickets. This separation of functions enhances security by minimizing exposure to attack vectors.
6. Salting and Nonces
To thwart replay attacks, Kerberos employs salting and nonces (random numbers). Salting involves appending a random value to a user's password before hashing, making it more resistant to dictionary attacks. Nonces are unique values generated for each authentication request to prevent replay attacks.
Now, let's delve into further Kerberos vulnerabilities and their technical aspects:
7. Ticket-Granting Ticket (TGT) Expiry Time
By default, TGTs have a relatively long expiry time, which can be exploited by attackers if they can intercept and reuse them. Administrators should consider reducing TGT lifetimes to mitigate this risk.
8. Ticket Granting Ticket Renewal
Kerberos allows TGT renewal without re-entering the password. While convenient, this feature can be abused by attackers if they manage to capture a TGT. Limiting the number of renewals or implementing MFA for renewals can help mitigate this risk.
9. Service Principal Name (SPN) Abuse
Attackers may exploit misconfigured SPNs to impersonate legitimate services. Regularly review and audit SPNs to ensure they are correctly associated with the intended services.
10. Kerberoasting
Kerberoasting is an attack where attackers target service accounts to obtain service tickets and attempt offline brute-force attacks to recover plaintext passwords. Robust password policies and regular rotation of service account passwords can help mitigate this risk.
11. Silver Ticket and Golden Ticket Attacks
To defend against Silver and Golden Ticket attacks, it's essential to implement strong password policies, limit privileges of service accounts, and monitor for suspicious behavior, such as unusual access patterns.
12. Kerberos Constrained Delegation
Kerberos Constrained Delegation allows a service to impersonate a user to access other services. Misconfigurations can lead to security vulnerabilities, so careful planning and configuration are essential.
Mitigation strategies to counter these vulnerabilities include:
13. Shorter Ticket Lifetimes
Reducing the lifespan of TGTs and service tickets limits the window of opportunity for attackers to misuse captured tickets.
14. Regular Password Changes
Frequent password changes for service accounts and users can thwart offline attacks and reduce the impact of credential compromise.
15. Least Privilege Principle
Implement the principle of least privilege for service accounts, limiting their access only to the resources they need, and monitor for unusual access patterns.
16. Logging and Monitoring
Comprehensive logging and real-time monitoring of Kerberos traffic can help identify and respond to suspicious activities, including repeated failed authentication attempts.
Kerberos Delegation: A Technical Deep Dive
1. Understanding Delegation in Kerberos
Kerberos delegation allows a service to act on behalf of a user to access other services without requiring the user to reauthenticate for each service. This capability enhances the efficiency and usability of networked applications, particularly in complex environments where multiple services need to interact on behalf of a user.
2. Types of Kerberos Delegation
Kerberos delegation can be categorized into two main types:
Constrained Delegation: This type of delegation restricts the services a service can access on behalf of a user. It allows administrators to specify which services a given service can impersonate for the user.
Unconstrained Delegation: In contrast, unconstrained delegation grants the service full delegation rights, enabling it to access any service on behalf of the user without restrictions. Unconstrained delegation poses higher security risks and is generally discouraged.
3. How Delegation Works
Here's a step-by-step breakdown of how delegation occurs within the Kerberos authentication process:
Initial Authentication: The user logs in and obtains a Ticket Granting Ticket (TGT) from the Authentication Server (AS).
Request to Access a Delegated Service: The user requests access to a service that supports delegation.
Service Ticket Request: The user's client requests a service ticket from the Ticket Granting Server (TGS) to access the delegated service. The TGS issues a service ticket for the delegated service and includes the user's TGT encrypted with the service's secret key.
Service Access: The user presents the service ticket to the delegated service. The service decrypts the ticket using its secret key and obtains the user's TGT.
Secondary Authentication: The delegated service can then use the user's TGT to authenticate to other services on behalf of the user without the user's direct involvement. This secondary authentication occurs transparently to the user.
4. Delegation and Impersonation
Kerberos delegation can be seen as a form of impersonation. The delegated service effectively impersonates the user to access other services. This impersonation is secure because the delegated service needs to present both the user's TGT and the service ticket for the delegated service, proving it has the user's explicit permission.
5. Delegation in Multi-Tier Applications
Kerberos delegation is particularly useful in multi-tier applications, where multiple services are involved in processing a user's request. It allows a front-end service to securely delegate authentication to a back-end service on behalf of the user.
6. Protocol Extensions for Delegation
Kerberos extensions, such as Service-for-User (S4U) extensions, enable a service to request service tickets on behalf of a user without needing the user's TGT. These extensions are valuable for cases where the delegated service cannot obtain the user's TGT directly.
7. Benefits of Kerberos Delegation
Efficiency: Delegation eliminates the need for the user to repeatedly authenticate to access multiple services, improving the user experience.
Security: Delegation is secure because it relies on Kerberos authentication and requires proper configuration to work effectively.
Scalability: Delegation is well-suited for complex environments with multiple services and tiers, enhancing scalability.
In this comprehensive exploration of Kerberos, we've covered a wide array of topics, from the fundamentals of its authentication process to advanced concepts like delegation.
Kerberos, as a network authentication protocol, forms the backbone of secure communication within organizations. Its core principles include the use of tickets, encryption, and a trusted third-party Authentication Server (AS) to ensure secure client-service interactions.
Security is a paramount concern in Kerberos. The protocol employs encryption, timestamps, and mutual authentication to guarantee that only authorized users gain access to network resources. Understanding these security mechanisms is vital for maintaining robust network security.
Despite its robustness, Kerberos is not impervious to vulnerabilities. Attacks like AS-REP Roasting, Pass-the-Ticket, Golden Ticket, and Silver Ticket attacks can compromise security. Organizations must be aware of these vulnerabilities to take appropriate countermeasures.
Implementing best practices is essential for securing Kerberos-based authentication systems. These practices include enforcing strong password policies, regular key rotation, continuous monitoring, and employee training.
Delving into advanced Kerberos concepts, we explored delegation – both constrained and unconstrained. Delegation allows services to act on behalf of users, enhancing usability and efficiency in complex, multi-tiered applications. Understanding delegation and its security implications is crucial in such scenarios.
Advanced Kerberos concepts introduce additional security considerations. These include implementing fine-grained access controls, monitoring for unusual activities, and regularly analyzing logs to detect and respond to security incidents.
So to conclude, Kerberos stands as a foundational authentication protocol that plays a pivotal role in securing networked environments. It offers robust security mechanisms and advanced features like delegation to enhance usability. Staying informed about Kerberos' complexities, vulnerabilities, and best practices is essential to maintain a strong security posture in the ever-evolving landscape of cybersecurity.
12 notes
·
View notes
Text

Emily Robb Summer Tour starts today!! Today in Brooklyn w/ Rosali and then a bunch of nights w/ Kurt Vile & his Violators...
Emily has a string of gigs coming up, and she'll be joined by yours truly on stage with a little organ. Please come out and have a blast and say hello to us. As we get further from Philadelphia, we would especially love to meet anybody willing to let the two of us sleep at their place after the show. Email [email protected] if so inclined.
Either way- don't be shy come say what's up!
Emily Robb Live Dates Summer 2024
Sun 6/16 Brooklyn, NY @ Union Pool w/ Rosali Mon 6/17 Harrisburg, PA @ HMAC * Tue 6/18 Wilmington, DE @ The Queen * Thu 6/20 Atlantic City, NJ North to Shore Festival @ Anchor Rock Club * Sat 6/22 Charlotte, NC Neighborhood Theatre * Sun 6/23 Cincinnati, OH @ Taft Theatre * Mon 6/24 Indianapolis, IN @ State Street Pub w/ Kind Buds Tue 6/25 Evanston, IL @ SPACE * Wed 6/26 St. Louis, MO @ The Pageant * Thu 6/27 Kalamazoo, MI @ Bells * Fri 6/28 Detroit, MI @ Spread Art w/ Deadbeat Beat, Shells Sun 6/30 Norwalk, CT @ District Music Hall *
Tues 7/23 Montreal, QC @ Sotteranea w/ Mountain Movers, Feeling Figures Wed 7/24 Prince Edward County, ON @ Glenwood Cemetery w/ Mountain Movers, Stonegrass, Craig Currie, Paul Lowman Thurs 7/25 Toronto, ON @ Monarch Tavern w/ Mountain Movers Fri 7/26 Rochester, NY Carbon 30YR Fest @ Radio Social Sun 7/28 Williamstown, MA @ Clark Art Institute w/ Glenn Jones Fri 8/2 Philadelphia, PA @ Century Bar w/ Nod, Mike Polizze (of Purrling Hiss/Birds of Maya) Mon 9/23 Philadelphia, PA @ Johnny Brenda’s w/ Mystic 100’s
* w/ Kurt Vile and the Violators
And other upcoming Petty Bunco shows… July 5 - Mordecai, The Spatulas, Overt Hostility @ Jerry’s On Front Aug 2 - Nod, Emily Robb, Mike Polizze @ Century Bar
We'll have copies of the newly landed "If I Am Misery Then Give Me Affection" repress at the merch table. See ya there!
polaroid by Kurt Vile
4 notes
·
View notes
Quote
これをさらに詳しく見てみると、バックドアはほぼ確実に、NIST SP 800-90A として実装されているバックドア乱数生成器 Dual_EC_DRBG に基づいています。 ウィキより: >>> NIST SP 800-90A (「SP」は「特別出版物」の略) は、決定論的ランダム ビット ジェネレーターを使用した乱数生成に関する推奨事項というタイトルの、国立標準技術研究所による出版物です。 この出版物には、暗号化で使用される、暗号的に安全であるとされる 3 つの疑似乱数生成器、Hash DRBG (ハッシュ関数に基づく)、HMAC DRBG (HMAC に基づく)、および CTR DRBG (カウンター モードのブロック暗号に基づく) の仕様が含まれています。 以前のバージョンには、4 番目のジェネレーターである Dual_EC_DRBG (楕円曲線暗号に基づく) が含まれていました。 Dual_EC_DRBG には、米国家安全保障局 (NSA) によって挿入された盗用バックドアが含まれている可能性があることが後に報告されました。 Cavium の NIST FIPS-140-2、セクション 3.3 より [1] 承認および許可されたアルゴリズム: 暗号化モジュールは、次の FIPS 承認アルゴリズムをサポートしています。 *SP800-90 CTR DRBG 確定的乱数生成 32
スノーデンのリーク: Cavium ネットワーキング ハードウェアには NSA バックドアが含まれている可能性がある | ハッカーニュース
3 notes
·
View notes
Note
I just gotta give you props because when I went to pick up my two newest Ts a month or so ago the seller had a juvie HMac he was giving away for free. I was so tempted (because I mean… free good looking spider…) but your post on your pet blog about how challenging they are as pets was on my mind. I still think they’re gorgeous spiders but just not for my house.
Glad I could help! They're gorgeous and I can't wait to get another one some day. But they're very hands-off and pet holes
For those who don't know what we're talking about:

Fast, temperamental, and nervous spider with very painful venom
4 notes
·
View notes
Photo

Join Smoothie King Friendswood & Grand Central Park at the AKA Houston Metropolitan Area Chapters “Black In Business Market!” Over 40+ black owned businesses will be showcasing their products and services. Scan the QR Code to register for this FREE event!!! We look forward to seeing you there!🛍️ @smoothiekinggcp @smoothiekingfriendswood #BlackInBusinessMarket #BuildOurEconomicWealth #HMAC #BlackInBusiness #doorprizes #giveaways #blackownedbusiness #OmicronTauOmega #SpringAKAs #wearesouthcentral (at Fifth Ward Multi-Service Center) https://www.instagram.com/p/Co-R0BzOLTM/?igshid=NGJjMDIxMWI=
#blackinbusinessmarket#buildoureconomicwealth#hmac#blackinbusiness#doorprizes#giveaways#blackownedbusiness#omicrontauomega#springakas#wearesouthcentral
0 notes
Text
Kaufland API Upgrade: What are the Next Steps for Sellers using 3rd-party Extensions
Kaufland, one of the largest retail chains in Europe, has recently launched its latest version of Marketplace Seller API. The Kaufland Marketplace Seller API 2.0 is a significant upgrade to its predecessor and offers an extensive range of new features that can enhance the selling experience for Kaufland sellers.
The new API boasts of a Representational State Transfer (REST), the latest version of the Kaufland KPI available. It is protected by HMAC-based authentication & password methods; therefore, any anonymous access to the Marketplace Seller API is impossible.
Want to know more about how you can upgrade to the advanced and highly secure Kaufland API? Click the link to learn the procedure in a detailed manner- https://bit.ly/4336nGh
kaufland #cedcommerce #kauflandsellers #germany #ecommerce #marketplaces #shopifyseller #shopifystore
2 notes
·
View notes
Text

Open VPN Now Free Download
OpenVPN is an open-source tool for setting up encrypted point-to-point and client-server connections as well as virtual private networks. Open VPN offers answers to a variety of issues, such as connecting remote users; gaining access to home and business networks; establishing secure WiFi connections; and connecting securely to distant businesses.
Even with load balancing, failover, and granular access controls, VPN may be scaled up to provide a remote access solution for an entire company. OpenVPN blends security with user-friendliness.
Features of OpenVPN:
Supports HTTP, SOCKS, NAT, and network filters in addition to most other proxy servers. TCP or UDP transport-based network operations. The capacity to set up TAP bridges and TUN tunnels at the network level. Traffic congestion is effective. Employs 2048-bit keys and a variety of encryption techniques (MD5-HMAC, RSA). A number of authentication methods
1 note
·
View note
Text






MongoDB Sharded Cluster Connectivity Issue – Solved! 🚀
Challenges: - Failed database connections across mongos nodes 🔌 - Initial fixes like restarts and reboots didn’t work 🔄 - Root cause: HMAC key expiration due to a MongoDB bug in versions 4.2.2–4.2.11 🔧
Solution: - Triggered a Config Server Failover to regenerate HMAC keys 💡
Results: - Reconnected mongos services 🔗 - Normal operations restored ⚙️ - Recommended upgrading to MongoDB 4.2.12+ to prevent recurrence 🔝
Facing a similar issue? Let us help you troubleshoot and optimize your database setup! 💬
👉 Contact us here: https://simplelogic-it.com/contact-us/ 📞
#MongoDB#ShardedCluster#HMACKeys#DatabaseOptimization#ITSupport#SimpleLogic#SimpleLogicIT#MakingITSimple#MakeITSimple
0 notes
Text
Make Your Business Communication Effortless with Troop Messenger
Troop Messenger business conversation is the safest and most efficient way to do business. With features like data protection, a secure and controlled admission protocol, convenience of use, and intellectual property ownership, Troop Messenger is the greatest business instant messaging solution available. This business chat software was especially created with you in mind. Enjoy the use of Troop Messenger, a potent tool for communication.
Troop Messenger - Team Collaboration and Instant Messaging App
Streamline team collaboration with Troop Messenger, the top instant messaging app for businesses. Boost productivity and communication in one platform.
Empowering Collaboration Across Industries
Troop Messenger caters to diverse industries, offering tailored solutions to meet specific collaboration needs. Here's how it benefits various sectors:
1. Defence: We are aware of the particular difficulties you encounter in safeguarding your important information. As a result, we have made use of a well considered military communications system that offers the greatest advantages. Use Troop Messenger, a defence messaging tool, to bind and shield your communications from prying eyes. With the following features, you can feel safe using this texting app for defence.
2. Government: A resourceful cum end-to-end encrypted messaging app for Government sectors, designed to sort all your complicated work in one place shrinking the latency issues. HD Audio/ Video calls & messaging in one on one or groups, video conferences, secure file sharing, and among others are some of the features of this secure chat application.

3. Politics: Share party news, official announcements, latest activity updates of the party, all across one platform through customized political campaign software! Keep your party associates connected all the time through this Android and iOS voter management apps!
Provides secure collaboration for the political parties with:
Messaging, calling, audio-video conferencing, live-telecasting, voter participation on social media, and more! For Political Party Leaders, it's all in one safe political collaboration tool. Bring people, cadre, and party activists to this instant messaging app for political parties for optimal and well-organized party discussions. Spread your political campaign with the features and facilities.
4. Ministry of Defence: Troop Messenger facilitates transparent MOD communication services to convey the policy framework of MOD to the armed forces to carry out their responsibilities. You can bring all entities onto this DOD mobile application to deliver the information securely.
Troop Messenger - Messaging Platform for Ministry of Defence
5. Army: Initiate Chat, Calls, remote screen access, conferencing, and more within this army chat app! Secure your sensitive army information with the world’s best security protocols and practices that combines the Double Ratchet algorithm, Pre-keys, and a triple Elliptic-curve Diffie–Hellman (3-DH) handshake, Curve25519, AES-256, HMAC-SHA256 as primitives.
6. Navy: High-trust and uniquely determined collaboration features for the seaborne branch! Integrate our end-to-end encrypted navy messaging system, the Troop Messenger, into your communication ecosystem; to securely chat, call, collaborate and meet.
7. Air Force: Reach the skies with secured Command-Control Instructions from the Base! We have incorporated highly secured collaborative tools for Airforce, such as chat, calling, audio-video conferencing, screen sharing, and others. Use it while conversating daily interactions, during natural disasters and internal disturbances, and for your other critical missions.
8. Defence Manufacturing: Our advanced Defence Manufacturing messaging system, Troop Messenger, help you exchange secure and classified conversations while you develop a comprehensive production infrastructure to produce weapons, systems, platforms, and military equipment required for defence across your Defence manufacturing industries.
9. Courts And Justice:Troop Messenger is an instant messaging and video conferencing tool designed for Indian courts. A unified communication system is necessary for a single, integrated, and independent judiciary to enable smooth cooperation among its judges, attorneys, court employees, etc. With this court administration software, you may transmit court orders over encrypted lines, upload case files to a secure file repository, broadcast court sessions live, and much more.
Virtual Communication Support for Virtual Courts
Courts need secure video solutions for virtual courts, such as Troop Messenger. Start conversating with the wide range of features and facilities available within this secure communication for court and justice department that helps have seamless virtual court proceedings.
10. Law Enforcement Agencies: Hinge on this law enforcement app to bring the hierarchies of your police system onto the unified communication platform to pass on the orders of law enforcement to the police on duty to maintain public safety and social order and prevent crime across your jurisdiction.
Secure Messaging Web and Mobile App for Police
A compliant messaging system for Police, Troop Messenger, is the best platform designed to solve the complexity of the communication process. With the help of advanced, safe, and secure features and intense collaboration facilities, it shall not allow classified data to fall into the hands of unauthorized persons.
11. Intelligence Agencies: Use this modern, agile, and sophisticated instant messenger for intelligence in your country’s internal and external intelligence agencies to encrypt and safeguard the flow of critical conversations while protecting your nation against domestic and foreign threats.
100+ features which can transform & enhance workplace productivity.
12. IT and Software Development: In the fast-paced world of IT and software development, effective collaboration is paramount for project success. Troop Messenger is Best messaging app for IT and Software Development compenies.
13. Healthcare: In the healthcare sector, timely communication can be a matter of life and death. Troop Messenger provides secure messaging channels compliant with HIPAA regulations, enabling healthcare professionals to exchange sensitive patient information securely while collaborating on patient care.
14. Education: In the realm of education, seamless communication between educators, administrators, and students is essential for academic success. Troop Messenger serves as a virtual classroom, enabling educators to conduct lectures, share resources, and engage with students in real time, regardless of physical distance.
15. Finance and Banking: Security and compliance are paramount in the finance and banking industry. Troop Messenger offers end-to-end encryption and compliance features, ensuring secure communication among financial professionals while facilitating collaboration on transactions, compliance tasks, and risk management.
What is Troop Messenger?
Troop Messenger is a centralised, secure digital platform that helps with team or interdepartmental communication. It is a solution designed to offer secure communications for Intelligence Agency Communication Solutions via message, phone, conference, and share screen, among many other time-saving productivity collaboration features.
On-premise Chat Server
Store your private and confidential call and conversation data inside your data centers using the highly secure and readily deployable on premise service paradigm! We developed this self-hosted collaboration solution with chat server that is compatible with the intranet to facilitate seamless workplace communication.
Sick of TeamViewer? Try Free TeamViewer Alternative
Troop Messenger is the best Team Viewer alternative that allows users to connect with remote teams with lightning speed.
While presenting the screen contents to remote users, one can highlight the required section with the help of screen annotation.
Why Choose On-Premise/Troop-GRIT?
Troop-GRIT is an On premise Chat Server edition of the Troop Messenger team collaboration application. That being said, you can deploy the self-managed Troop-GRIT on your local or on-premise servers to avoid third-party access to the application, such as from the public internet or any other means.
Free Live Chat Apps in India
Do you know that during the pandemic, some free live chat apps in India rescued the majority of businesses akin to online chat apps emphasizing the value of team communication while working remotely, amid the pandemic? These applications and website chat apps became an essential tool for keeping in touch with customers, clients, vendors, and others.
AnyDesk Alternatives
Market-available AnyDesk alternatives are capable of confusing users with their comparable capabilities. To avoid the contemplation process, read this blog and make an informed decision.
Troop Messenger, is one of the best team collaboration tools, offering real-time messaging, remote access, screen-sharing, and other features.
Free Screen Sharing Apps and Software
Screen sharing is one of the best dynamic collaboration features of Troop Messenger that allows members to share their screens during a chat conversation. Recipients can see real-time changes on the presenter's screen.
Troop Messenger's screen share function is powerful for enhancing team collaboration and conversation. With its smooth setup, interactive equipment, and strong security features, the Screen Sharing App on Troop Messenger permits green and productive virtual meetings. Whether you're conducting a presentation, troubleshooting trouble, or brainstorming together with your team, Troop Messenger makes display sharing simple and effective.
Features that Propel Team Collaboration
Troop Messenger offers a plethora of features geared towards facilitating smooth communication and collaboration among team members. Here's a closer look at some of its standout features:
Instant Messaging: With Troop Messenger, exchanging messages in real-time has never been easier. Whether you're seeking quick updates or engaging in brainstorming sessions, the app enables instant communication, fostering agility and responsiveness within teams.
File Sharing: Gone are the days of cumbersome email exchanges. Troop Messenger allows users to effortlessly share files of various formats, including documents, images, videos, and more. This feature ensures that crucial information is readily accessible to team members, promoting efficiency and productivity.
Group Chats: Collaboration often involves multiple stakeholders. Troop Messenger simplifies group communication by offering robust group chat functionality. Users can create dedicated chat groups for projects, departments, or specific topics, enabling seamless collaboration and knowledge sharing.
Voice and Video Calls: Sometimes, a face-to-face conversation is necessary to convey complex ideas or resolve issues effectively. Troop Messenger supports voice and video calls, allowing team members to connect instantly and engage in productive discussions irrespective of their physical location.
Integration Capabilities: Troop Messenger seamlessly integrates with a variety of third-party applications commonly used in the workplace, such as Google Drive, Dropbox, Trello, and more. This integration enhances workflow efficiency by centralizing communication and eliminating the need to switch between multiple platforms.
Remote Screen Share: Reach out to your remotest office teams with Troop Messenger’s productive and ultra-new screen share feature.
End-to-End Encryption: Your work conversations are under your complete control! Chats, calls, and conferences are end-to-end encrypted in this office chat app.
Conclusion
It becomes clear that Troop Messenger is a flexible and essential tool for encouraging teamwork and communication in a variety of industries. Troop Messenger is an office chat app that helps businesses meet their goals faster by streamlining processes, increasing productivity, and providing industry-specific solutions. Its extensive feature set and user-friendly design make it the ideal choice for any kind of organisation. Troop Messenger is the best team collaboration app for business talks and is suitable for nonprofit organisations, large corporations, and startups alike. It makes teamwork simple and boosts productivity in the digital sphere.
1 note
·
View note
