#hardcoded joi
Explore tagged Tumblr posts
Text
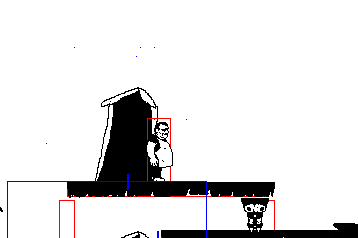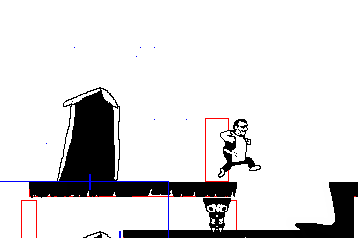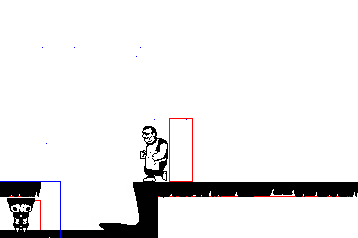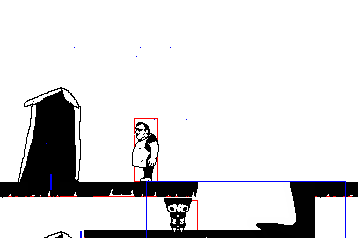
Another horny game review, this one's fairly popular (comparatively): Hardcoded. I've only played the demo so far, but I love it. Mostly spoiler-free? + fanart at the end
That's right, another queer scifi robot fuckin game. I'm a simple creature.
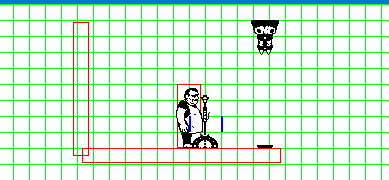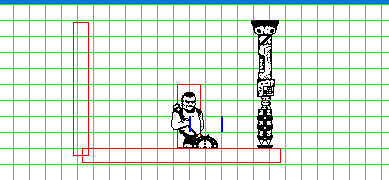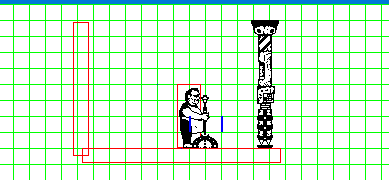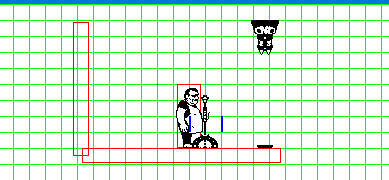
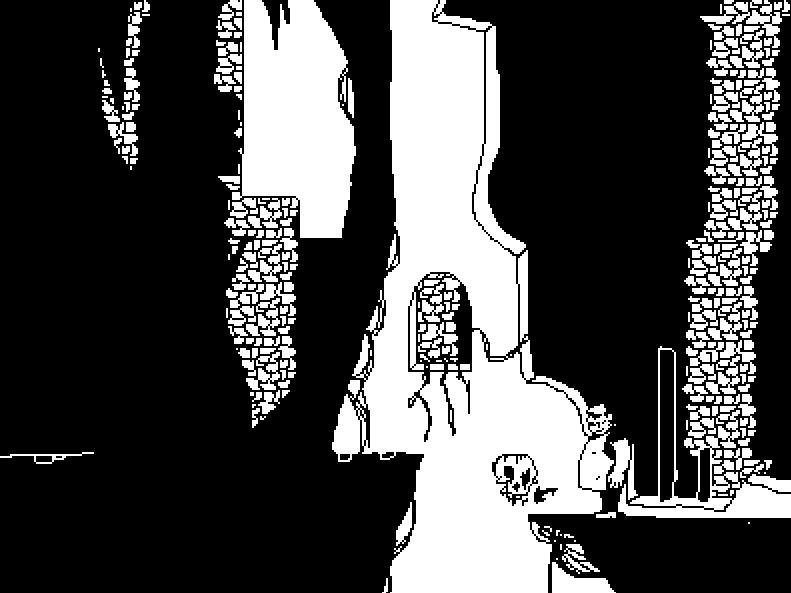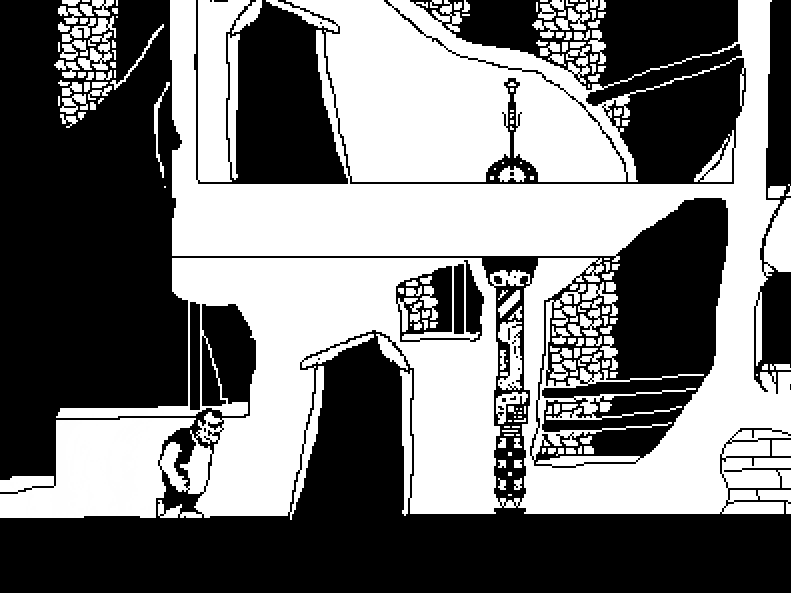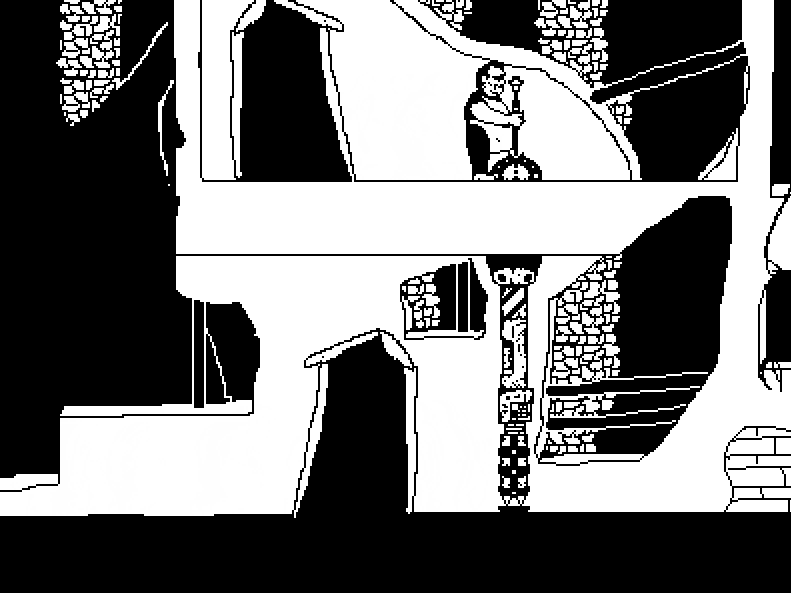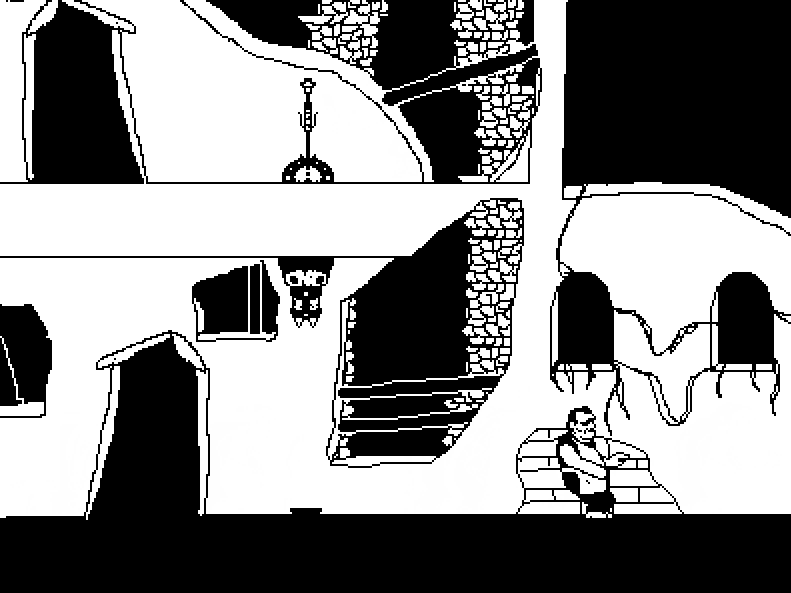
The worldbuilding on this one is pretty incredible, lots of little bonus things to read if you're into that stuff like I am. The story is you're a super hightech android that's escaped from a scifi suburbia to this independent city where you get picked up by a bunch of queer people. Also there's a thing going around making everyone super horny? Cyberpunk 2077 wishes it was this cool. Art is lovely too, it's all in this fitting pixel art style, with lots of animations, including sex scenes, and extra pics you can find on the in-game computer. I always forget to check it!
The demo has TONS of content on it's own, an unbelievable amount for a free game. I wanna say at least 9? people to romance, and they're almost all trans. There's a witchy character and a cyborg mechanic and a cute hacker and a robot with big tits and many more. Plus lots of minor characters you can also have sex with. Just lots of sex all around. Walk around and explore, you'll find all sorts of little scenes.
I guess as far as gameplay, it's not quite a visual novel cause it's mostly these open world sections. And so much customization. I've spent the majority of my time with this game just working up coupons (the currency) and checking shops for more cute clothes and furniture. Shops update daily, so be sure to check, plus there's some unique events on Fridays you don't wanna miss. My secondary quest is finding all the sex toys, they have their own display shelf in the room so like, I gotta collect em all.
My main tip if you want to play this game yourself, make sure you run your mouse over every openworld section like its a point-and-click adventure. I missed two whole areas of the game for the first few hours because I didn't realize those were clickable spots on the map. Not to mention the whole clothing shop i missed! Could've been buying even more clothes that whole time!
Also, if you want more cute clothes, you can find some lil cheatcodes on the wiki, put those in for secret clothes.
Ok thanks for reading my porn game review, here's a fanart :]

Can u believe it my favorite romance option is the other robot wow huh how unexpected of me
#hardcoded game#hardcoded#hardcoded joi#cfr talks ick#cfr talks games#theres no real tag as far as i can tell but there are at least some other people out there hardcoded posting#my art#ive decided im gonna end all of these with fanart cause i cant find Anybody Else making art for these games and id like to change that.#be the change you want to see in the world.#ok fine. fanart tag.#robot
23 notes
·
View notes
Text
Pacific rim x tf
I love just the idea of the autobots and deceptions coming to earth to try recruiting the sentient jaegers, but being harshly declined. Why? Well for one they're already busy dealing with large monsters on a regular basis and two they love their humans too much. With plenty of evil robot related movies fueling paranoia among engineers they hardcoded into the jaegers that they want to protect humans.
So they are pretty reasonably pissed at the bots for dragging their people into their war. Anyways they force the autobots and decepticons to make up. (All this because of a messy breakup? Jeez and you call humans violent.)
So now with the Cybertronians new free time the yeagers will reach them the joys of human beings.
#humans: hi jaegers: these are my blorbos and I'll kill for them#transformers x humans#transformers & humans#tf#fic idea#Pacific rim#sentient jaegers#autobots#decepticons#implied megop#tfp
119 notes
·
View notes
Text
With Hardcoded coming out on steam (buy and support the sick trans devs of that), has left me at work daydreaming about cybernetic sex so here's a couple small little ramblings of a joy toy that can't help herself:
Just flashes of cybernetic sex, vibrating cocks and needy overstimulated holes warm and slick to keep anyone addicted to pumping every ounce of energy into.
Music pounding in our ears as we can't help but stumble into the club bathroom or even the alley, we couldn't care less; to torn clothes from our metallic and silicon bodies desperate to fuck the night away.
I'm jacked in and jerking off a room of my fellow handsy transfems sharing the night equally as sharing one another, a room of free use joy toys reaching for titties, cocks and holes desperate to swap spit, cum and sweat with as many needy and lovely people we can stumble against and into.
Ooooh Viv (lovely friend from a discord) you experimental runner you, fucking girls on the net while a diligent joy toy spends their night between your thighs, your body and very essence is getting fucked by those so needy for you 💓
#mtf nsft#nsft queer#t4t nsft#trans nsft#cyberpunk nsft#robogirl nsft#robogender nsft#t4t#transfem#nsft#text nsft
14 notes
·
View notes
Text
O2A2 Daily Log. DAY/NiGHT 1 (July 5th, 2024)
I'll be posting these until I get to the game's development conclusion!
Day I.
It was around 10 AM when I started working. My initial process laid in drafting the story. After deciding on the main character (in this case, Amaranth) I stripped the story to its two components – place and premise – because in other cases it’d be down to building the plot off of a character, and my mind runs wild whenever I construct it like that.
The place is the library, where souls come after they’ve passed, so an Afterlife Library. And the premise is quite simple – it’s a game for the player’s life! In this case, instead of a gamble it all comes down to outsmarting the machine, ahem, the experienced librarian.
And as a person who barely knows Python beyond freely coding in Ren’py, I wandered to the search engine to find a tutorial and realised that I’ll probably be better off searching on Reddit. One of the posts gave me a really good idea – the OP was talking about imagebuttons and logic and then it clicked for me.
Tic-tac-toe is a game where you draw the image inside the grid spaces, taking turns and adjusting your movements to your opponents’... Was it possible to code something like that?!
(duh, of course it was, this log is a testament to that)
I started by cropping the supposed “images” (solid blocks of two colours – one for the scroll and one for the charcoal), and cropped tiny squares of the scroll's colour. So the layering was like this – background scroll - big dark square - vertical box full of horizontal boxes of scroll’s colour, creating the illusion of a drawn grid, when in reality it is not.
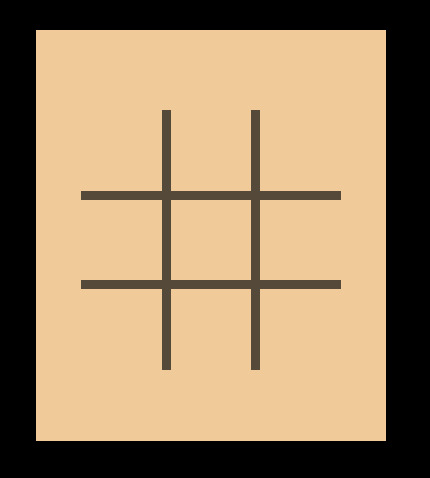
And this marks the beginning of my two-hour suffering. I ditched the idea of imagebuttons that I wanted to go with, since that’d require assets, which I only could use one of. So I opted for textbuttons, and it was the most Hell I’ve had coding.
At first I couldn’t get them to show up. Then, I remembered to set a box just for them (x/y maximum of 70ish, since the squares are 90), had nightmares doing the horizontal and vertical boxes, and increased the font. Hooray! Visible!
Setting a variable on click with “action” function was easy, and soon enough I could fill an entire board with. Xs and Os. Time to code Amaranth’s turn in! (scared)
It wasn’t as scary as I imagined: basically, all tiles are “if” functions, and if they’re empty the player can fill them. If it’s not their turn, they’re not active, and Amaranth is quick to respond (I did a test to see if she’d fill an empty cell and she did!)
Then came the invisible (for now) work – I coded in a win condition. I SCREAMED WITH JOY WHEN I SAW THAT MY ARRAYS FINALLY UPDATED!

That concluded my day-work!
Night I.
So I decided to push forward and actually coded in her responses!
I took and hardcoded the first two turns for her Xs and the rest was assigned at random. As for Os, I made it do everything at random, since she’s more experienced at playing Xs! (totally not because I didn’t want to look at tic-tac-toe ever again)
Each turn the machine checks if there are any free spaces and if any of the rows match winning conditions. If they do, the player gets to the end plot (I still haven’t written any of it, aaaa!). If they don’t, the game continues until it’s a draw or X’s/O’s win.
With that, I finally slumped into the bed. Even with taking breaks it was kind of a hard exercise to be jumping straight into after a. Year. Of not working with Python’s syntax.
[I’ve cut off a huge text segment of me trying to design a less clunky random placement system, but all of my endeavours led to dead ends caused by my inexperience and complex requests. Thank you for all the answers, StackOverflow! So many people asking the same question, it makes me feel like we’re all a part of a big community…]

#nitunio.txt#nitudev#< lord knows i wont be using this tag much after the jam#o2a2#o2a2 vn jam#game jam#renpy
3 notes
·
View notes
Text
Not enough Joi appreciation in the Hardcoded tag, what's with that. She's so cute. She's the best character. And she breaks you multiple times during sex so that doesn't hurt either. I'm in love with her.
3 notes
·
View notes
Text
System Shock (2023) - Impressions
My first serious game was Myst, and it demanded a very particular peripheral that used to be a mainstay of any serious gamer's arsenal: the double combo of a well-sharpened pencil and a generous Legal pad.
First came a story of Linking Books and filial betrayal. A little grisly in places, sure - thanks, Achenar - but mostly All-Ages stuff. I tore through two pads just to finish Myst because I had the insane idea of charting out the Selenetic Age's subway system organically. I was too dumb to realize the sounds were the same heard for the Mechanical Age's four cardinal points, too stubborn to bother, and armed with a summer's worth of game time and zero responsibilities. I charted out that damn subway for hours and screamed for joy when I lucked onto the exit.
Then came something a little harder on the nerves. A tale of corporate overreach, greed, megalomania pressed onto silicon wafers and a very Nineties vision of Cyberspace. Move over, Johnny Mnemonic, this hacker's even more hapless than you are...
Long story short, we open in a dystopian Cyberpunk future and are, in fact, a well-heeled chairjock. We've got the sick techwear to prove it, complete with glove-mounted ports for plugging portable data drives into your knuckles or socketing map-related proprioceptive enhancements to your wrist - like you do. The problem is, we've gotten a little long in the tooth and opted to steal a military enhancement that's probably omega cool, max nova or fraggin' awesome, depending on your other dystopian setting of choice. Said implant's owners and designers, the obscenely wealthy TriOptimum Corporation, sic their dogs on us. We're caught merely moments after stealing the schematics.
TriOp's Chairman of the Board, however, has some ideas. Ideas that work against the hardcoded ethical protocols of the AI system he both lords over and depends on, the Sentient Hyper-Optimized Data Access Network - or SHODAN. Space stations orbiting Saturn are complex hives of steel and flesh, you see, and designing a dispassionate and meticulous warden for it only made sense.
The problem is that thanks to your actions under duress, SHODAN is now anything but dispassionate and meticulous. She soon comes to see herself as a "living" goddess, and more or less rips a page out of AM-1's usual script. Kill the humans, experiment with their primitive flesh, turn their remains into obedient servants to her newfound magnificience - yadda yadda. On the plus side, SHODAN is once again voiced by Terri Brosius, former vocalist for the band Tribe - and she once again oozes cold and calculating menace. Glitchy cold and calculating menace, that is.
I mean - take five and go look at System Shock 2's now-famous opening CGI movie on YouTube. Look at you, hacker, said in its chilling tone of absolute contempt and utter surety of purpose, is now a bona fide classic Gamer Meme.
I might as well say that this is more or less The Game, as it were. as you spend most of your run trying to correct this very obvious SNAFU while also trying to figure out how you're going to leave a space station located halfway across the solar system when all the doors are locked and most relevant codes were either revoked or stashed away.
Oh, and the insane AI you're stuck with decided it was a good idea to start splicing tiger and gorilla DNA together into brand new cuddly murder machines. You know. For funsies.
Initially designed by Irrational Studios back in 1994 and now spruced up by Night Dive, this is a title that proudly foregoes several modern conveniences and that refuses to hold your hand even at the easiest difficulty settings you can configure. It isn't easily legible, its level design philisophy is intentionally outdated and if it could speak, it would spit in BioShock's direction and claim it was corrupted by the vainglorious promises of the Shooter Celebrity status.
And yes, I say that knowing BioShock is leagues removed from your average Call of Duty entry. Compared to System Shock, Bioshock is a Dudebro Machine designed to slam through brewskis while yelling about your KD ratio in a bad microphone. I'm also saying this as someone who loves Bioshock. System Shock the first in name is not friendly, it does not care for you or your concepts of builds or minmaxing, it almost sadistically throws a useless compass your way - and asks you to figure it out.
No handholding. No tutorials. No easing-into-things. Once you're on Citadel Station, you're on your own.
Honestly, just this is worth the price of admission. We've been coddled for decades, all because we're focused on making sure games recoup their massive budgets. System Shock sits at a lean and mean eight and a half gigabytes (yes! In 2023! It's shocking! Har har, easy puns!), it intentionally looks simple and chunky - and nothing is wasted here. Nothing whatsoever.
It's cramped, oppressive, dingy, menacing, cold, even possibly damp - and still a great showcase of any RTX-capable graphics card, with deep and believable shadows and so much Shader Porn that even the simple voxel textures that adorn the four sides of the playspace at all times feel properly anchored in the fiction. It's a beautiful game, if you're willing to understand that beauty as a concept can include pixels you can count with your naked peepers.
What it isn't, however, is forgiving towards younger gamers or anyone who skews towards more recent releases. The dual UI experience is instantly dated, the "inventory Tetris" concept stopped being fun long before Resident Evil 4 briefly revitalized it, and hitting Tab to click through audio logs and written notes for codes or clues when you can hear mutants wheezing and lumbering towards you is never really fun.
Y'can't pause, here - this is the Dark Souls of vintage PC horror games-
No, come on, that's a dated and cringey assertion, SHODAN's baby deserves better than that. What it is, though, is an encapsulation of a specific era in video game design and in what we once saw as constituting the best the Survival Horror genre could produce on our dated beige towers. The best outside of other classics in the genre, sure, but still one of the oft-cited references.
If you've got fifty or so bucks burning a hole in your pocket and the pressing need to have a skipping Text-to-Speech filter call you a pathetic insect, this is a must-have, quite simply.
6 notes
·
View notes
Text
星期三!星期三会是什么体验,很好奇,蛮期待!
I have never been to a concert before! I thought I would never attend one in my life either. So this is gonna be the first! And there's a high chance that this is gonna be the last too!
And it's Coldplay!
There were lotsa reasons I never attended a concert:
We were just not financially capable.
The people I really wanted to hear performing are all dead! Frank Sinatra or 周璇 or 张露 or 白光 (okay, fine, 七��歌星那几条鸟啦)or the Andrew Sisters or Ella Fitzgerald etc? All dead! Having the chance to sing 天涯歌女 and 夜上海 along with 周璇 would have been nice, though.
Concerts are loud! And—
There are so many sounds! These are quite the tall orders for my ears to tolerate. They can hurt. But even if they are tolerable (as in, manage to be not-too-loud), the sheer number of ambient sounds can be quite overwhelming. I can't focus; I can't pay attention. You can argue that no one needs to be attentive to every single sound, and you'll be right. But I just... Uh... ...
A concert is a thing where you either feel like you've never belonged anywhere more than this moment... or feel painstakingly aware of being alone.
See, if you manage to become part of the crowd—like singing the songs together with everyone, having your heartbeat and breathing synchronized... They say it almost feels spiritual. A sort of unity. But we have no idea what that feels like. I think our faculties are missing the fundamental mechanism required, so no matter how hard we try to talk to people and socialize, at the end of the day, we can never be a part of anything. We're merely tangible ghosts, stuck on not knowing what it means to belong to these humans.
And that's a thing about crowds, innit? If you can't connect, you'll feel pretty lonely. Just because loneliness is an inevitable regularity for someone who can't connect to other people doesn't mean they will truly become accustomed to it. This means concerts, being a crowd activity, have the potential to exacerbate this situation...
IT'S COLDPLAY THOUGH?
They don't come to this everyone-skips-us-for-Singapore-and-Bangkok destination all the time! And this is quite possibly the only item on "The Lyi and Lyn's Joint Bucket List" that could ever be checked!
We made so many supposed promises and until now, goddamn none of this stuff came real. But this one item is actually within reach. I mean, the ticket we were getting was nearly 500 bucks. Made my teeth hurt from gritting but goddamn, it's within reach!
Also, Lyi may be my besto furrendo, but we don't share a lot of taste in music. I can tolerate her ATEEZ and assorted Korean stuff and she can tolerate my "Only World War II ghosts listen to this" shit, but genuine intersections in our taste are rare. That makes Coldplay even more important. Kinda happy my JJK agenda manages to create another intersection though!
She's been to so many concerts already, with all kinds of friends, but there was never one between us. I suppose there is no hardcoded "right or wrong" to the way "best friends" work, but denying your pal a milestone memory to commemorate the sheer durability of this friendship even though you can afford to create this memory? Bit of an ass, innit?
No relationships are unconditional. There are always conditions, whether people are cognizant of them or not. Didn't we already realize that a long time ago? Nourishing a relationship through forging happy memories is but one such condition.
Besides, everything is impermanent, innit? 500 bucks is impermanent. Any discomfort a concert might bring to me is impermanent. Any pleasure a concert might bring to me is impermanent. Coldplay as a band is impermanent. Our friendship is impermanent.
In the face of impermanence, what do I really want to be attentive to? The fear of painstaking loneliness in a large crowd experiencing union while you're painfully aware of being disconnected—
or the joy of experiencing a few exciting hours of life with a friend, while enjoying the sight of people, in general, having a great time?
That's not all. I'm excited just thinking about all sorts of stuff I'd get to observe about people! This is a new frontier. New setting. Wouldn't it be fun?!
I bet they are gonna sing their latest songs from the Music of the Spheres album (which I have no idea what those would be; didn't Past Us stop following their album drops after Mylo Xyloto because we just... aren't that ardent about artists? Even the ones we like). Oh, and the classic ones too, like Viva la Vida. And Clock, right?! I don't mind not getting to hear Strawberry Swing and Life in Technicolor II if Clock is on the list. Strawberry Swing is our comfort song, and he claimed to have no favorite beyond this. But I know you're lying! I know you always sing that one line from Clock. You know, "Am I part of the cure, or am I part of the disease?" I can hear you, dude. Even with the song in my ears!
---
Even before the concert, I'd already planned to visit That Mall. The one with that aesthetic bookstore of Japanese import, yet isn't Kinokuniya. I'm gonna spend hours there, I think! I hope I can find all 8 volumes of the Pluto manga. And then I hope the price isn't so high that I can't buy them all, and can only choose one. Because for sure it's the one with Atom on the cover. Hey, limit a person's choice, and this happens.
I wonder what other things should we check out?
I CAN'T WAIT TO THEN WALK FROM THE MALL TO THE STADIUM! YES, A LOVELY WALK! We'll pass by the area's really large park! TYhe route from the mall to the stadium is only 3km long though. It's so short. But still, it's great!
Oh. Is it normal to stay a bit and help clean the place up once the concert is over? Are there any hidden rules about concerts? I should probably ask someone who's been to plenty of concerts. Like Lyi. Or maybe Nova!
0 notes
Text
What have I been up to
For the past couple of years I have been busy with both university and work. Either separately or at the same time. But I've still been focusing on game development.
While I was away, most work went towards GRIND. I'll leave a preview here from last year:
youtube
GRIND has underwent a massive overhaul in both style and gameplay. The animations are smoother and fall in place better. The video is pretty old and some animations and visuals have been completely remade, repurposed or added. Gameplay-wise, the turn based RPG battle aspect of the game has been removed. Battles will function differently and will place more emphasis on how the main character would feel and act in a more natural setting. Here's some video footage that is a remake of an earlier video of the game from 2017:
youtube
There's not much I can say about combat other than that I plan on having it play out differently for every battle depending on your foe(s). There is not much progress on this part yet. From a technical standpoint, GRIND is finally running on a self-made engine, which I wrote in C++. I don't know how to make saying this live up to the work it took because it took me years to get it working. It was certainly an experience building both the game and the engine itself at the same time.
There have actually been 2 engines, one of which I started in 2019. It didn't really hold up due to my lack of knowledge and ended up in the trash after 2 years. I can't really put into words the pain I felt when I figured there's not much I can do further to save it. Following this, I started planning up big and I'd say the new engine is something I'm really proud about. GRIND can be altered by anyone that wants to learn to tinker with the files and new content can be made without too much trouble!
Here's a video of the engine being used to make a playable version of PONG, with AI and all!
youtube
The engine itself isn't fully finished. There's still plenty to be done that will aid me in the building of the game but I'd say that from a logical standpoint, most important features have been implemented. Biggest component left out so far is UI which I'm not particularly hasty about implementing. Game-progress wise it's still early to be hyped. I'm currently building the tutorial level and I'd love to gather about one to two hours of meaningful gameplay before I release a working demo. Because the game content I'm building is making use of engine features instead of hardcoding objects, progress can get really slow on some parts.
Doesn't mean I'm not having fun developing. Hell, I'd say I've reached the most satisfying part of it, seeing how things fall together and the game just works. It's just that things take time. And due to how ambitious the visuals of the game have gotten, making the simplest of things still take a lot of thinking and redesigning to fit well in.
I'll leave below some highlights from over the past couple of years. From the first engine attempt(2019-2020):








From the current engine (2021-Present)








It brings great joy to my heart to revisit the development process of GRIND throughout the years, especially knowing of all the impediments I had to overcome. Making your own engine is no easy task and building a game altogether can be a very demanding task, and I am grateful to have gotten this far without giving up.
Had a blast putting together this little catch-up and I can't wait to show off more!
Tune in for more GRIND updates !
0 notes
Text
I’ve been wondering how best to publish some of my fiction. itch is a good option for interactive stuff, and I don’t like paywalling stuff at all so I’d prefer to just put it on a website, but the idea of living off writing fiction and making games is quite appealing
anyway what with the recent news of Patreon narrowing the kinds of nsfw content it allows, I heard about Sponsus which appears to be a very practical alternative with some good principles behind it (a well-optimised website, using Stripe to process payments without making them vulnerable to pressure from payment processors, very simple fee structure) and I’m considering making one.
This is kind of an interest check.
For now, I’m making enough money to live on through my work for the American education company, but while it’s not truly possible to escape the churning of M-C-M’, it would be nice to feel like I’m working for myself and those I can support directly, rather than having to spend most of my energy making a venture capitalist even richer. Still, I certainly wouldn’t ask anyone to prioritise donating to me over people who more urgently need help.
There’s some dangers. A major one is turning something I currently do for the fun of it into an obligation might suck the joy out of it (this has kind of happened to a degree with physics writing for that company so... that’s a worry, but writing fiction would be self-motivated and I could change tracks as I desire). And I’d very likely make less money (like, even absolutely brilliant writers like Charity @porpentine get less on Patreon than I currently make - I don’t expect to become the next hardcoded girl). So, it would be a supplemental income for a long time, which I’d try to pay forward (to people here in London, and to peoples’ fundraisers online) if I don’t end up needing it.
The writing I’d immediately try to support in this way would be things like:
interactive fiction: I have a couple of projects in the works, linked through a Thirty Years War/Caliban and the Witch inspired early modern setting, with alchemy and jellies and religious conflicts and primitive accumulation.
...one concerns a trans trossfrau-led insurrection in the midst of a civil war (a joint project with @baeddel), and the ‘saint’ who champions her cause. you may have seen the amazing [nsfw] illustration by @velocityvsreality some months back!
...the other a visual novel about swordsmith who dies to their own soul-eating sword. we learn about what happens after only through the characters who manifest inside the sword. this is a collab project with writing contributions by @desert-gurl and fantastic interface art by @velocityvsreality; I would of course split any money I receive with them
I also have older projects I’d like to bring back... for example, there’s one about a cyborg girl with an interchangeable body descending into an alien ruin, I have some ideas for one about mecha
the ordinary kind of fiction: the project I’m most excited to work on right now is a currently novella-length and growing project called VECTOR, about horny trans lesbian cyborg swordfights, infrastructure girls, states shaping desires and probably a bunch of other stuff by the end. I’m trying to decide whether to serialise this or polish it up to post in one complete go
games: I like learning about graphics. Still seeking modes of interaction that can match plain old clickable text for emotional resonance, but I will be making prototypes and playing around with Rust, Piston, WASM, Vulkan and other such things for now.
posts: I will keep trying to write interesting text posts, about communism, gender, anime criticism, game design, roleplaying, computer graphics, physics... If you’re on here, hopefully you’re into that kind of thing. (I’ll also keep migrating posts to my github site for easier access.)
livereads: whatever happened to that Umineko readthrough? or the Animorphs one? let’s bring that back huh
All of this is stuff I absolutely plan to write and publish (in some fashion) anyway, but if I had some kind of support for it, I would be able to devote more time to it and maybe one day think about writing full-time. It would also ease the tension between “I should try and make a living off this if I like it so much” and “I don’t like paywalling anything”, letting me put stuff on the internet for free without worry.
So... would you potentially be interested in supporting such a thing? Does this sound like a good idea or a terrible one?
13 notes
·
View notes
Text
Nintendo Switch Kernel Patching and Emulation - Achieving Maximum Modification Flexibility with Minimal Replacement
Ever since shofEL2 was released earlier this year it's been interesting to watch how different custom firmwares have tackled the prospect of modifying Nintendo's firmware for both homebrew and piracy applications, and as someone who hasn't really had much stake in that race I feel like it's interesting to watch how different solutions tackle different problems, but at the same time since I do have a stake in a few places (namely, Smash Bros modding, vulnerability hunting, personal projects) I ended up in a situation where I needed to sort of 'set up camp' with Nintendo's Horizon microkernel and have a comfortable working environment for modification.
Binary Patching is Weird, and Horizon makes it weirder.
Probably the biggest difficulty in Switch development I would say is iteration time, followed by a general difficulty in actually modifying anything; even just booting modified core services (ie filesystem management, service management, spl which talks to the EL0 TrustZone SPL [commonly misnomered as the security processer liaison...?], the boot service which shows boot logos and battery indications, ...) requires, at a minimum, reimplementing Nintendo's package1 implementation which boots TrustZone and patches for TrustZone to disable signatures on those services and kernel. Beyond the core services, modifying executables loaded from eMMC requires either patching Loader, patching FS, reimplementing Loader, or something else.
Unfortunately with binary patching there generally isn't a silver bullet for things, generally speaking the three methods of modifications are userland replacement, userland patching, and kernel patching. The first two are currently used for Atmosphere, but the solution I felt would be the most robust and extensible for the Nintendo Switch was kernel patching. Here's a quick rundown on the pros and cons for each method:
Userland Replacement
- Requires rewriting an entire functionally identical executable - Often not feasible for larger services such as FS - Can easily break between firmware updates, especially if new functionality is added or services split. This makes it difficult to maintain when the OS is in active development. - Added processes can potentially leave detectable differences in execution (different PIDs, different order of init, etc) + Easier to add functionality, since you control all code + Can operate easily on multiple firmwares + Can serve as an open-source reference for closed-source code
Userland Patching
- Adding additional code and functionality can be difficult, since expanding/adding code pages isn't always feasible without good control of Loader - Finding good, searchable signatures can often be difficult - Can easily break between firmware updates, especially if functionality or compilers are tweaked + With good signatures, can withstand firmware updates which add functionality + Often has less maintenance between updates when functionality does change; patching is usually easier than writing new code + Harder to detect unless the application checks itself or others check patched applications
Kernel Patching
- Greater chance of literally anything going wrong (concurrency, cache issues, ...), harder to debug than userland - Minimal (formerly no) tooling for emulating the kernel, vs userland where Mephisto, yuzu, etc can offer assistance - Can easily break between firmware updates, and is more difficult (but not impossible) to develop a one-size-fits-all-versions patch since kernel objects change often - Easier to have adverse performance impacts with syscall hooks + Harder to detect modifications from userland; userland cannot read kernel and checking if kernel has tampered with execution state can be trickier + Updating kernel object structures can take less time than updating several rewritten services, since changes are generally only added/removed fields + Direct access to kernel objects makes more direct alterations easier (permission modification, handle injection, handle object swapping). + Direct access to hardware registers allows for UART printf regardless of initialization state and without IPC + Hooking for specific IPC commands avoids issues with userland functionality changes, and in most cases IPC commands moving to different IDs only disables functionality vs creating an unbootable system.
mooooooo, a barebones Tegra X1 emulator for Horizon
Obviously the largest hangup with kernel patching is debugging, the Switch has RAM to spare (unlike 3DS) and setting up an intercept for userland exceptions isn't impossible to do by trial and error using SMC panics/UART and a lot of patience, but for ease of use and future research I really, really wanted an emulator to experiment with the Switch kernel. I ended up building a quick-n-dirty emulator in Unicorn, and with a few processes it works rather well but it still struggles with loading Nintendo's core processes currently, but for a small and contained test environment (two processes talking to each other and kernel patches watching them), I would say I had reached my goal and it was enough to at least be able to work quickly and sanely on my intercept.
For the most part, the Switch Horizon microkernel doesn't actually use much of the Tegra MMIO; it uses some of the more obvious ARM components like GIC for interrupts, and it also has a large initialization sequence for the memory controller, but as long as interrupts are functional, timers work, MC returns some correct values and SMC return values are all correct, it boots into userland without issue.
I actually found that emulating multiple cores in Unicorn actually isn't all that difficult, provided you're using a compiled language where uc_mem_map_ptr works. Rather than messing with threads, I opted for a round-robin scheduling scheme where I run each Unicorn instance for a set number of instructions, with memory being mapped and unmapped from the running core so that any cached data gets written out before the next core has its turn. A lot of modifications/cherry-picking to Unicorn did have to be made in order to properly support interrupts, certain coprocessor registers (ie core indexes), translation tables (for uc_mem_read/uc_mem_write, vaddr->paddr translation, and just in general there were some odd issues).
Patching Horizon for Syscall MiTM
With a decent environment for modifying kernel, the next issue really just became actually bootstrapping an SVC intercept. Figuring out where exception vectors are located isn't difficult with the emulator handy, but really the issue becomes
1. Extra code has to be loaded and copied by TrustZone, along with kernel 2. New code needs to be placed in a safe location and then given memory mappings 3. Existing code needs to be modified with hooks pointing to the new code
To guide the kernel towards salvation I ended up hooking just before translation table addresses are written into coprocessor registers. This way, the payload can allocate pages and copy code from less-safe soon-to-be-condemned .bss memory for the bulk of the SVC interception code, set up those pages in the translation tables, and then patch the ARM64 SVC handler to actually jump to the new mapping. For ease of development, the mapping is given a constant address along with any hardware registers which it needs to access, as opposed to being randomized like the rest of the kernel.
In the end, patched the kernel executes as follows:
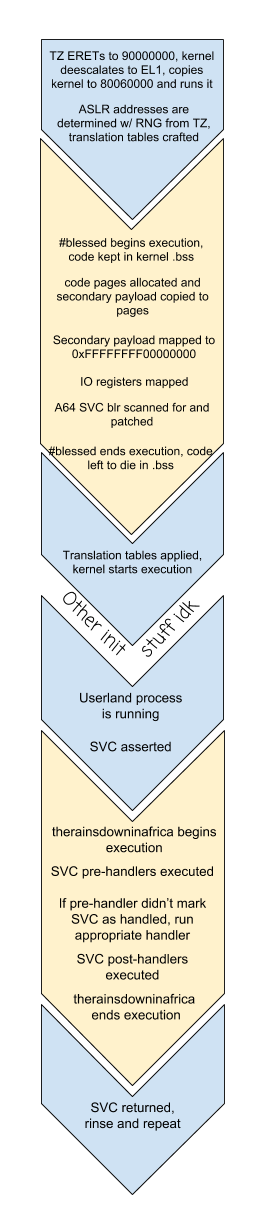
Since hashtagblessed is able to map UART, CAR and PINMUX registers into translation tables, getting communication from the right Joy-Con rail using existing BPMP-based drivers was fairly straightforward, and even without any source code to reference there's a fairly basic driver in TrustZone. Between the transition from emulation to hardware however, I had kept an SMC to print information to the console, but I ultimately ended up using UART even in emulation. On hardware, I got by using UART-B (the right Joy-Con railed) for a while, but had to switch to UART-A (internal UART lines for debugging) due to GPIO issues once HOS tried to initialize Joy-Con.
Identifying IPC Packets, Accurate Results With Simple Tools
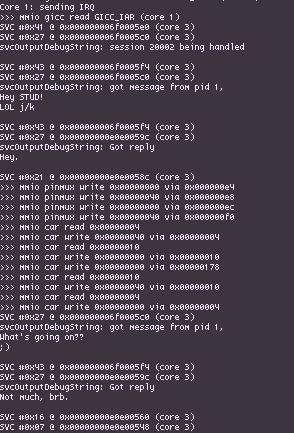
With therainsdowninafrica loaded, hooked in and blessed, the next step is actually being able to identify specific IPC requests sent through svcSendSyncRequest, and doing this requires getting our hands dirty with kernel objects. Userland is able to utilize different kernel objects indirectly through the use of handles and system calls. Each KProcess has a handle table which maps handles to the underlying object structures, so translating handles to KObjects is simply a matter of checking the table for a given handle passed to a syscall. To access the current KProcess object which has the handle table, we can use the per-core context stored in register X18 as of 5.0.0 (prior to Horizon implementing ASLR, it was stored in a hardcoded address per-CPU) and the handle table can be accessed through the current KProcess object. Printf debugging was extremely useful while figuring out exactly how KProcess has its fields laid out since the structure changed slightly between versions, and with a bit of reversing added in it's not particularly difficult to figure out exactly where the KProcessHandleTable is at how handles are translated into objects.
Probably the most useful fields in KProcess/KThread, in our case, are the process name and title ID, the handle table, and the active thread's local storage, where all IPC packets are read from and written to. To give a quick overview on how Switch IPC generally works, services are able to register a named port to wait for communications on which can be connected to by other processes via svcConnectToNamedPort. In practice, Nintendo only uses globally-accessible named ports for their service manager, `sm:`. On a successful call to svcConnectToNamedPort, processes recieve a KClientSession handle for sm: which allows those processes to send IPC requests to the service manager to either register/unregister/connect to 'private' named ports managed by the service manager, with sm checking whether the requesting process actually has access to said service.
From a practicality standpoint, since so much communication relies on IPC the most obvious mechanism to establish is a system for hooking requests going into specific named ports, both globally accessible ones such as sm: and private ones provided by sm itself. This kinda leads into why it's important to have access to the underlying KClientSession objects as opposed to trying to track handles; mapping out exactly which KProcess' handles go to what, while also tracking where handles might be copied and moved to is an almost impossible task, however mapping specific KClientSessions to specific handlers avoids the handle copying/moving issue since the KClientSession object pointer does not change in those cases.
Additionally, many interfaces aren't actually accessible from either svcConnectToNamedPort nor sm, as is the case with fsp-srv which gives out IFileSystem handles for different storage mediums. However, by providing a generic means for mapping KClientSession objects to specific intercept handlers, you can set up a chain of handlers registering handlers. For example, intercepting a specific eMMC partition's IFile's commands would involve setting up a handler for the sm global port, and then from that handler setting up a handler for any returned fsp-srv handles, and then from the fsp-srv handler checking for the OpenBisFileSystem command for a specific partition to hook the IFileSystem to a handler, which can have its OpenFile command hooked to hook any outgoing IFile handles to a specific handler for IFiles from that eMMC partition. From that point all incoming and outgoing data from that IFile's KClientSession can be modified and tweaked.
Finally, in order to prevent issues with KProcess handle tables being exhausted, Nintendo provided virtual handle system implemented in userland for services which manage large amounts of sessions. Effectively, a central KClientSession is able to give out multiple virtual handles (with virtual handles given out by virtual interfaces) only accessible through that KClientSession handle. As such, a process can take a service such as fsp-srv and with a single handle can manage hundreds of virtual interfaces and sub-interfaces, easing handle table pressure on both the client and server ends. These handles can be accommodated for by watching for KClientSession->virtual handle conversion, and then keeping mappings for KClientSession-virtual ID pairs. And again, since copied/moved KClientSessions keep their same pointer, in the event that somehow the central handle and a bunch of domain IDs were copied to another process, they would still function correctly.
Tying it All Together
Let's take a look at what it would take to boot homebrew via hbloader utilizing only SVC interception. The key interface of interest is fsp-ldr, which offers command 0 OpenCodeFileSystem taking a TID argument and an NCA path. From a userland replacement standpoint, booting homebrew involves redirecting the returned IFileSystem to be one from the SD card rather than one from fsp-ldr, since Loader (the process accessing fsp-ldr) doesn't really do any authentication on NSOs/NPDMs, only FS does. From a kernel standpoint, we just need to watch for an IPC packet sent to fsp-ldr for that command, hook the resulting handle, and then for each OpenFile request check if an SD card file can better override it. From there, swap handles and now Loader is reading from an IFile on the SD card rather than an NCA.
Taking a few steps back, there's obviously a few things to keep in mind: Loader never actually accesses the SD card, in fact it doesn't even ask for a fsp-srv handle. Since it is a builtin service it has permissions for everything, but the issue still remains of actually making sure handles can be gotten and swapped in. As it turns out, however, calling SVC handlers from SVCs is more than possible, so if Loader sends a request to sm asking for fsp-ldr, we can send out a request for fsp-srv, initialize it, and then send out the original request without Loader even knowing.
Interestingly, the first thing Loader does with its fsp-ldr handle is it converts it into a virtual domain handle, so that all OpenCodeFileSystem handles are virtual handles. This does make working with it a little more tricky since the code filesystem and code files all operate under the same KClientSession object, but it was an issue which needed resolving anyhow. For SD card IFile sessions, it also means that we have to convert them to virtual handles and then swap both the file KClientSession handle and the file virtual handle ID, while also watching for their virtual ID to close so that we can close our handles at the same time and avoid leakage.
A few other tricks are required to properly emulate the SD redirection experience: swapping in handles isn't the only concern, it's also important to ensure that if the SD card *doesn't* have a file then that error should be returned instead, and if the SD card has a file which doesn't exist in the original IFileSystem, we still need a file handle to replace. To accomodate for this, the original FileOpen request is altered to always open "/main" and if the SD card errors, that virtual handle is closed, and otherwise the SD handles are swapped in.
The end result is, of course, the homebrew launcher being accessible off boot from the album applet:
youtube
Other Potential Thoughts for Kernel Stuff
* Process patching is as easy as hooking svcUnmapProcessMemory and patching the memory before it's unmapped from Loader. Same goes for NROs but with different SVCs, all .text ultimately passes through kernel. * Reply spoofing. IPC requests can simply return without ever calling the SVC, by having kernel write in a reply it wants the process to see. * SVC additions. I'm not personally a fan of this because it starts to introduce ABIs specific to the custom firmware, but it's possible. One of the things I'm not personally a fan of with Luma3DS was that they added a bunch of system calls in order to access things which, quite frankly, were better left managed in kernel. The kernel patches for fs_mitm also violate this. Userland processes shouldn't be messing with handle information and translation tables, i m o. That's hacky. * Virtual services and handles. Since the intercept is able to spoof anything and everything a userland process knows, it can provide fake handles which can map to a service which lies entirely in kernel space. * IPC augmentation: Since any IPC request can be hooked, it can be possible to insert requests inbetween expected ones. One interesting application might be watching for outgoing HID requests and then, on the fly, translating these requests to the protocol of another controller which also operates using HID. * IPC forwarding: similar to augmentation, packets can be forwarded to a userland process to be better handled. Unfortunately, kernel presents a lot of concurrency issues which can get really weird, especially since calling SVC handlers can schedule more threads that will run through the same code. * As currently implemented, A32 SVCs are not hooked, however this is really more an issue if you want to hook outgoing requests from A32 games like MK8, since services such as Loader will generally only operate in a 64-bit mode.
Source
Horizon emulator, https://github.com/shinyquagsire23/moooooooo
therainsdowninafrica, https://github.com/shinyquagsire23/therainsdowninafrica
2 notes
·
View notes
Note
You are a total joy to talk to and I'm so happy I found your blog. If you manage to find a copy of the 2nd stage play with a sub file and need it hardcoded and uploaded again, let me know! XD
OOOHHH I LOVE YOU 💖💖💖 seriously how are you so sweet?
AND AAAAA I DEFINITELY WILL LET YOU KNOW :D
(also you said sub, IT’S ALL GOOD LOL)
9 notes
·
View notes
Text
How I learned to hate ORM (especially for data import scripts)
When I was tasked with making a new application for our websites, I was given several CSV files with some expectation that these files could basically be just loaded into a database and jumped into production really quickly. This was sort of naive idea for me to share in, so I’ll go through the way the project progressed
When I started, I chose grails/groovy/hibernate/GORM as a platform to use. This quickly turned into pain when I tried to make a data importer using grails also.
Each CSV row from the source file would have to be turned into many different rows in the database because it represented multiple relationships, example:

Initially I made my data importer in grails, and was hardcoding column names knowing full well this was really inflexible. At the same time I was also trying to “iterate” on my database schema, and I’d want to re-import my data to test it out, but it was really really slow. I tried many different approaches to try to speed this up such as cleanUpGorm, StatelessSessions, and other tricks, but it would take 10-20 minutes for imports on a 100KB input file.
What I basically realised is that for bulk data import
1) Using the ORM is really painful for bulk import.
2) If you can pre-process your data so that it is already in the format the database expects, then you can use the CSV COPY command which is very fast
3) If you can then abandon the ORM mentality and even ignore it as a convenience factor, then you can embrace my database system itself
Overall, after all this work, it just seemed like ORM treats the database as a danger and something to be heavily abstracted over, but I actually found joy in learning how to treat my database as a first class citizen. Soon I started gaining appreciation of
- using plain SQL queries - learning about full text search in postgres with ts_query - learning about triggers to make a “last updated” field get updated automatically
I am pretty happy this way, and although I miss some things like criteria queries which are very powerful, I am happy that I can interact with my database as a friend
At the very least, due to the fact that I now pre-process the data before database loading, I can now import large amounts of data super fast with the CSV COPY command
1 note
·
View note
Text
Facial Recognition Software Regularly Misgenders Trans People
Facial recognition software is a billion dollar industry, with Microsoft, Apple, Amazon, and Facebook developing systems, some of which have been sold to governments and private companies. Those systems are a nightmare for various reasons—some systems have, for example, been shown to misidentify black people in criminal databases while others have been unable to see black faces at all.
The problems can be severe for transgender and nonbinary people because most facial recognition software is programmed to sort people into two groups—male or female. Because these systems aren’t designed with transgender and gender nonconforming people in mind, something as common as catching a flight can become a complicated nightmare. It’s a problem that will only get worse as the TSA moves to a full biometric system at all airports and facial recognition technology spreads.
These biases programmed into facial recognition software means that transgender and gender nonconforming people may not be able to use facial recognition advancements that are at least nominally intended to make people’s lives easier, and, perhaps more importantly, may be unfairly targeted, discriminated against, misgendered, or otherwise misidentified by the creeping surveillance state’s facial recognition software.
Os Keyes, a “genderfucky nightmare goth PhD student” studies the intersection of human-computer interaction and social science at the University of Washington’s Department of Human Centred Design & Engineering. To find out why automatic gender recognition (AGR) is so ubiquitous, Keyes looked at the past 30 years of facial recognition research.
They studied 58 separate research papers to see how those researchers handled gender. It wasn’t good. Keyes found that researchers followed a binary model of gender more than 90 percent of the time, viewed gender as immutable more than 70 percent of the time, and—in research focused specifically on gender—viewed it as a purely physiological construct more than 80 percent of the time.
“Such a model fundamentally erases transgender people, excluding their concerns, needs and existences from both design and research,” Keyes wrote in The Misgendering Machines, a research paper they published in November. “The consequence has been a tremendous under representation of transgender people in the literature, recreating discrimination found in the wider world. AGR research fundamentally ignores the existence of transgender people, with dangerous results.”
“I couldn’t help but be personally, as well as professionally annoyed by the approach that the field took to gender—of assuming these two very monolithic and universal categories of gendered experience,” Keyes told me over the phone. “Pretty much every paper I read did it.”
“We’re talking about the extension of trans erasure”
The bias against trans and nonbinary people was everywhere, from research to suggested applications of the technology. It seemed hardcoded. A 2015 research paper on AGR from the National Institute of Standards and Technology (NIST), the oldest federally funded science lab in America, suggested people could use facial recognition software to sound an alarm around women’s bathrooms if men got too close. “An operator may be alerted when a male is detected in view,” the paper suggested.
“Precisely why this technology is necessary for bathroom access control is not clear: most AGR papers do not dedicate any time to discussing the purported problem this technology is a solution to,” Keyes wrote in their paper. “The only clue comes from the NIST report which states that: ‘the cost of falsely classifying a male as a female…could result in allowing suspicious or threatening activity to be conducted,’ a statement disturbingly similar to the claims and justifications made by advocates of anti-trans ‘bathroom bills.”
Problems and prejudices like that cropped up again and again in Keyes research. “Three of [the research papers] focused on trans people. Zero of them focused on non-binary trans people, in the entire 30 year history of the field,” Keyes told me.
Machines aren’t value neutral, they act as they’re programmed. “We’re talking about the extension of trans erasure,” Keyes said. “That has immediate consequences. The more stuff you build a particular way of thinking into, the hard it is to unpick that way of thinking.”
Technology is a feedback loop—the values we build into our machines are then taught to anyone who uses it. “So when we build a particular set of values, into new spaces, and new systems, not only we making them exclusive spaces and systems and making it harder to have a world that is more inclusive overall, we’re also communicating to people who try and enter—‘this is how gender works, these are the categories that you can live in, this is how your gender is determined,’” Keyes explained. “Any conflict or dissonance you have with that is your problem because this is a faceless machine.”
As facial recognition technology spreads, problems will arise for anyone who doesn’t fit the “norm” the technology was designed to recognize. This is already a problem. In 2018, MIT researchers Joy Buolamwini and Timnit Gebru published research that pointed out the AI running facial recognition software was overwhelmingly trained with white faces and led to an increased number of false positives for any other shade of skin. “A false positive carries different weights, depending on who the subject is,” Keyes explained. When traditionally marginalized groups interact with law enforcement, there’s a disproportionate chance they’ll end up dead, hurt, or in jail.
Keyes doesn’t see a need for any kind of AGR at all.
“Technologies need to be contextual and need-driven,” they said. “What are the values of the people who use the space that you’re deploying a technology in? Do the people in that space actually need it? If we’re not discussing gender at all, or race at all…it doesn’t necessarily lead to a better world.”
They said that one way to solve this problem is to do a better job of teaching social sciences such as ethics and gender studies to computer science students. The more inherent biases are studied, the easier they are to avoid when designing new technologies. “The average [computer science] student is never going to take a gender studies class,” Keyes said. “They’re not probably going to even take an ethics class. It’d be good if they did.”
Facial Recognition Software Regularly Misgenders Trans People syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes