#gfw impact
Explore tagged Tumblr posts
Text






this is what TNA '08 game would've looked like if the Knockouts was featured in the games.
hopefully we can get an sequel to the 2008 game that'll feature the KO's #MakeTNA2



#tna wrestling#tna impact#midway games#impact wrestling#gfw impact#video games#The Knockouts#taylor wilde#gail kim#velvet sky#jessicka havok#brooke tessmacher#mia yim#Jade#deonna purrazzo#maria kanellis#bandai namco
3 notes
·
View notes
Text


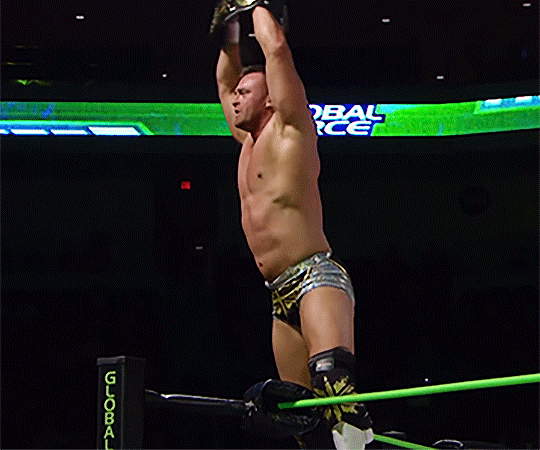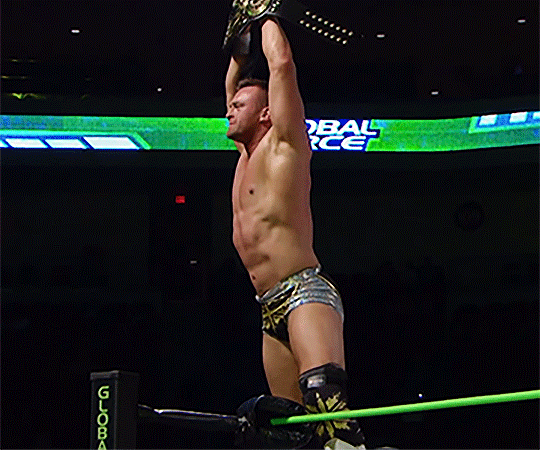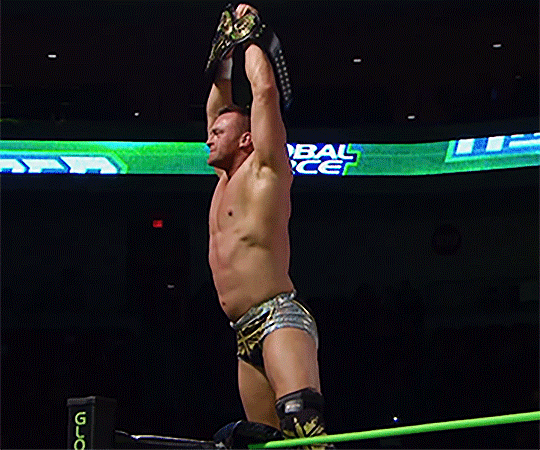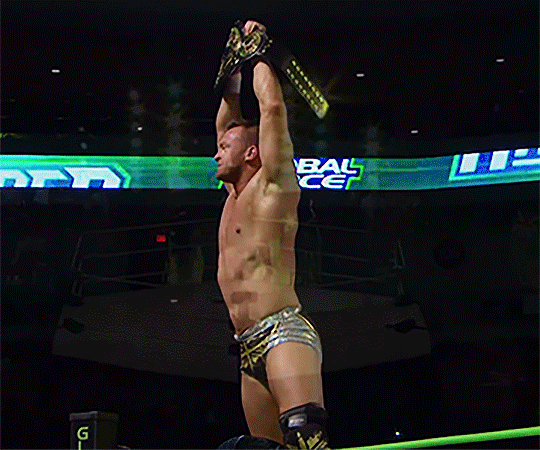
#Nick Aldis#impact wrestling#global force wrestling#GFW#TNA#wrestlingedit#my gifs#tnaedit#flashing tw
17 notes
·
View notes
Photo

Gail Kim presents the GFW Women’s Championship and the Impact Wrestling Knockouts Championship before the unification match between Rosemary and Sienna.
Slammiversary XV July 2, 2017
16 notes
·
View notes
Text
Wrestlers as Types of Kisses: ii. Ace Austin - Kiss to the Wrist
Fandom: Impact Wrestling Pairing/Form: Ace Austin x Commentator!Reader / Blurb Warnings: N/A Word Count: 935 Plot: Part of your role as a commentator is being the biggest Bullet Club hater in Impact, but your offscreen relationship with Ace Austin is actually quite friendly. Just friendly as in just friends though, you definitely have no interest in him romantically, not even a little, not at all!
“1! 2! 3! And that’s another Inevitable win for Bullet Club’s Ace Austin!”
You rolled your eyes as Matthew Rehwoldt raved. He playfully elbowed you, “Come on, aren’t you going to comment on that finish?” He was messing with you, playing up your well known on-screen distaste for all things Bullet Club.
“I’d be more excited about it if it wasn’t Ace Austin, and more impressed if he didn’t cheat.”
Rehwoldt laughed. “Aw, come on, one little card, one little papercut, and what the ref doesn’t see, doesn’t count!”
“You’re not wrong on that last part, unfortunately, and I’m not wrong that it’s time to move onto our next match! If Ace ever stops his celebration and leaves the ring, that is.”
Naturally, at that moment, the “Inevitable One” made eye contact with you, smirking when he saw your disdain, and blowing you a kiss for good measure. You rolled your eyes again as the crowd hooted and hollered.
While Ace eventually left the ring, you stayed under the lights for the rest of the show, manning the commentary desk with Renwoldt and Tom Hannifan. Doing commentary combined all the things you loved most - analysis, comedy, teamwork, and watching wrestling. The action in front of you and the antics of your co-commentators (including occasionally needing to wrangle them out of their arguments enough to call the action) drew you in and wiped the stain of Ace Austin and his Bullet Club shenanigans from your mind…mostly. Almost entirely. Absolutely entirely.
Okay, so maybe your mind kept flickering back to his wink and to the way his lips looked when he blew you that kiss. Maybe. Just a couple times.
Not that you would ever tell him that; his ego was bigger than his thighs (which you also never thought about) already, and that was saying something.
Ace was so far from your thoughts that you nearly jumped when you heard him call your name backstage after the show. You’d been checking your email on your phone when he sidled up.
He chuckled at your reaction, “You alright there, beautiful?”
You rolled your eyes but smiled and nodded. Your offscreen dynamic with Ace wasn’t nearly as hostile as your onscreen one. Really, you were friends. And that was all you wanted to be. Despite his flirtations. Just friends.
“Good,” Ace grinned. “So Rehwoldt said you were saying all kinds of mean things about me on commentary again. So rude!”
“Of course I was,” you grinned back at him, dramatically pointing at yourself, “Hello? Number one Bullet Club hater here!”
Ace playfully poked your arm, “You’re a great actress, pretending you hate us, pretending you hate me.”
“And you’re a great actor, pretending to be a total douchebag. Of course, the part of your character that’s a total dork is all you.”
Ace laughed, “Is that supposed to hurt my feelings? Because I am proud of my nerdiness, thank you!”
“As you should be,” you laughed too. Ace’s laughs, his smiles, they had that effect - they were contagious.
“Well I know I’ve said it before, but I’m glad our beef is only on screen.”
“Me too,” you playfully poked his arm. “I’m glad we’re friends.”
“Me too too!” He beamed, poking your arm in turn. “I hope we’re friends for a long time.”
You nodded, and the two of you lapsed into a comfortable silence. Well, it was mostly comfortable. Comfortable as in you felt safe, you felt secure. But you didn’t feel relaxed. He was much too close for you to feel relaxed. His pretty eyes kept glancing over at you. His broad shoulders flexed as he leaned against the wall. His hand nearly brushed against yours.
“Hey,” There were those pretty eyes again, demanding your attention as he spoke to you. “Friends can hold hands, right?”
“Uh, sure?” You raised your eyebrows.
“So can I hold yours?” His glance flicked away for a moment before he met your eyes again.
“Uh, y-yeah,” you held your hand out, hoping it wasn’t shaking, and he took it, wrapping his fingers around your palm. You looked away, sure that you were blushing.
Ace stayed quiet for a few moments, but it wasn’t long before he squeezed your hand and said, “Hey, so friends can hold hands…can they give each other a kiss-”
Your eyes widened, but Ace finished off his sentence with, “-on the cheek? Or the hand?”
“O-oh,” you were so blushing, anyone would blush about that, right? “Sure, yeah, friends can do that.”
Ace scooted closer to you, still leaning against the wall, his face now inches from your own. “You know, if I got this close to you on camera, I’m not sure you’d be able to pretend to hate me.”
You sputtered a bit and then rolled your eyes. “Of course I would. I’m a professional.”
“I don’t know,” Ace smiled, “your pulse is speeding up.”
“Wh-what?” A nervous laugh escaped before you could stop it.
“Yeah,” Ace wouldn’t look away from you. He smiled again before slowly, gently lifting the hand he held closer to his face, “I can feel it,” he pressed his lips to the inside of your wrist, “right here.” The last words were breathed against your skin as he lingered there.
Your head was much too fuzzy at the moment to question if he could really feel your pulse, and you would only roll your eyes about that hours later; for now you simply looked up at him, caught in his eyes, blushing at his smile. Ace pressed his lips to your wrist once more before lowering your linked hands.
#ace austin#ace austin fanfic#ace austin fanfiction#ace austin x reader#impact wrestling#impact wrestling x reader#impact wrestling fanfic#gfw's work
13 notes
·
View notes
Text
I'll give some thoughts on Impact returning to the TNA name, as someone who's watched since almost the very beginning: I'm mainly positive about it.
TNA is how most people know them, myself included, and they've done a great job in the past 3+ years at rebuilding and regaining the trust of people who turned away during some truly horrid times in the company's history - the GFW era, the time nazis (ron and don harris) were speculated to have purchased them, the billy corgan era, the destination America era where no one was watching and they wrestled in dark arenas while taz and JOSH MATTHEWS announced from a closet.
TNA has been great again for quite a while, and I hope people give them another chance.
30 notes
·
View notes
Text
Let the real fun begin.
26 notes
·
View notes
Text
Gnoppix free DoH Server
What is DoH and why it’s important
DNS: The Address Book with a Privacy GapThe Domain Name System (DNS) acts like an address book for the internet, translating user-friendly domain names (like Gnoppix) into numerical IP addresses that computers use. Designed in 1987, DNS didn't prioritize security or privacy. By default, DNS requests travel unencrypted, making them vulnerable to eavesdropping and manipulation. This means anyone can potentially see which websites you're trying to access.A famous example of this vulnerability is the case of Kevin Mitnick. He was caught by the FBI because he used unencrypted traffic. The FBI was not able to decrypt traffic, they were able to track his activity by monitoring unencrypted DNS requests within a group of people requesting DNS at that specific time, after interviewing them all, it was obvious who has the skills to do that. While it's true that current encryption methods for data traffic are very strong and cannot be decrypted with today's technology, the future of quantum computing might change this. Quantum computers have the potential to break many current encryption methods, which could have a significant impact, especially for financial institutions. However, the development of large-scale quantum computers is likely to be delayed for some time. The Great Firewall's DNS TrickeryChina's Great Firewall of China (GFW) exploits this weakness to censor content. Since DNS relies on a simple, unencrypted protocol, the GFW can impersonate both the user and the server to alter DNS responses. When a user tries to access a blocked website (like thepiratebay), the GFW can provide a fake IP address, directing the user to a different location within China instead of the real website. Securing Your DNS with DoHJust like HTTPS encrypts website traffic, DNS over HTTPS (DoH) encrypts your DNS requests. With DoH, your internet service provider (ISP) or other observers cannot see which websites you're trying to access. This adds a layer of privacy and security to our online browsing.
Why we run our own DoH resolver?
There are already some public DNS resolvers like 1.1.1.1 and 9.9.9.9 that support DNS over HTTPS, so you can use them. Starting with Firefox version 61, you can enable DNS over HTTPS in the browser settings, which is a big progress for Internet security and privacy. Firefox uses Cloudflare resolvers (1.1.1.1) by default. However, some folks argue that this allows Cloudflare (and others) to gather information on you. They seem to have more trust in their ISP than Cloudflare. But I think if you are paranoid about privacy, you should run your own DoH resolver with your own CA or just use “our’s” so neither Cloudflare nor your ISP can spy on you. I’m pretty sure here, the government agencies have direct access to the public DNS from those popular services. I can confirm, ISP’s have the government “black boxes” installed!
DoH vs DoT
Besides DNS over HTTPS, there’s another protocol that also aims to encrypt DNS queries. It’s called DNS over TLS (DoT).It’s more advantageous to use DoH.- DoT operates on TCP port 853, which can be easily blocked by a national firewall. - DoH operates on TCP port 443, which is the standard port for HTTPS websites, which makes DoH super hard (almost impossible) to block, because if TCP port 443 is blocked, then nearly all HTTPS websites will also be blocked. Another advantage of DoH is that it allows web applications to access DNS information via existing browser APIs, so no stub resolver is needed.Here you'll find more information and how to setup DoH Read the full article
0 notes
Text
International Conservation Tech in India
Written By: Jagriti S.

Figure: Growth of Conservation Tech Investment 2017 - 2023
The Role of Technology in Conservation

Figure: Remote and Camera Sensing
Drones and Remote Sensing:

Figure: Artificial Intelligence and Machine Learning Conservation
Artificial Intelligence and Machine Learning:
Genetic Technologies:
International Collaborations and Initiatives
The integration of international conservation technology in India is often facilitated through global partnerships and collaborative initiatives. Some notable examples include:
Wildlife Protection Solutions (WPS): This international organization collaborates with Indian conservationists to implement advanced surveillance systems in protected areas. WPS's technology helps in real-time monitoring of poaching activities, leading to quicker response times and increased arrest rates of poachers.
Global Tiger Forum (GTF): India, home to over 70% of the world's tigers, is a key player in the GTF. This international consortium uses technology to monitor tiger populations, track their movements across borders, and implement anti-poaching measures. Satellite telemetry and camera traps are essential tools in these efforts.
Indo-UK Collaboration on Climate Resilience: This partnership focuses on using climate modeling and data analytics to enhance India's ability to predict and respond to climate change impacts. These technologies aid in developing conservation strategies for climate-vulnerable species and habitats.
Case Studies of Success
Several projects in India have successfully harnessed international conservation technology to achieve remarkable results:
Project Elephant: In collaboration with international researchers, Project Elephant uses GPS collars and drone technology to track elephant herds and mitigate human-elephant conflicts. This initiative has significantly reduced crop damage and human casualties in conflict-prone areas.
Sundarbans Mangrove Restoration: Partnering with global environmental organizations, India is using satellite imagery and GIS (Geographic Information Systems) to map and restore degraded mangrove forests in the Sundarbans. These efforts are crucial for protecting this unique ecosystem and its iconic species like the Bengal tiger.
Snow Leopard Conservation: In the high-altitude regions of the Himalayas, international conservationists are using camera traps, genetic sampling, and satellite collars to study and protect the elusive snow leopard. These technologies provide valuable insights into their behavior, habitat use, and threats.

Figure: Growth of Conservation Tech Investment in India 2016-2023
Here are some notable foreign startups and organizations operating in the conservation technology space in India:
Wildlife Protection Solutions (WPS)
Country of Origin: USA
Focus: Provides technology solutions for wildlife conservation, including real-time surveillance systems to monitor and prevent poaching activities.
EarthRanger (formerly Vulcan Technologies)
Country of Origin: USA
Focus: Offers a data visualization and analysis software platform to support wildlife conservation and protected area management.
Rainforest Connection (RFCx)
Country of Origin: USA
Focus: Uses recycled cell phones as solar-powered listening devices to detect and monitor illegal logging and poaching activities in real-time.
SMART (Spatial Monitoring and Reporting Tool)
Elephant Listening Project (ELP)
Country of Origin: USA
Focus: Uses acoustic monitoring to study and protect elephants, particularly in forest environments where visual monitoring is challenging.
Global Forest Watch (GFW)
Country of Origin: USA
Focus: An online platform that provides near-real-time data and tools for monitoring forests worldwide, helping to detect deforestation and illegal activities.
ZSL Instant Detect
Country of Origin: UK
Focus: Provides a satellite-connected camera trap system that sends real-time images and alerts to conservationists to prevent poaching and monitor wildlife.
Fauna & Flora International (FFI)
Country of Origin: UK
Focus: Engages in various conservation technology projects, including habitat mapping, wildlife monitoring, and anti-poaching initiatives.
Blue Ventures
Country of Origin: UK
Focus: Uses technology to support marine conservation, including community-based monitoring of marine biodiversity and fisheries.
Conservation Drones
Country of Origin: Singapore
Focus: Develops and deploys low-cost drones for various conservation applications, including wildlife monitoring, habitat mapping, and anti-poaching efforts.
Challenges and Future Prospects
While international conservation technology offers immense potential, it also presents challenges:
High Costs: Advanced technologies can be expensive to procure, deploy, and maintain, which can strain the budgets of conservation organizations.
Technical Expertise: Effective use of these technologies requires specialized knowledge and skills. Training local conservationists and researchers is essential for long-term success.
Data Management: The large volumes of data generated by these technologies need to be effectively managed, analyzed, and utilized for conservation planning.
Despite these challenges, the future of conservation technology in India looks promising. Continued international collaboration, investment in capacity building, and innovation in affordable and scalable technologies will play a crucial role in safeguarding India's biodiversity.
Here are some notable Indian startups and companies involved in conservation technology in India:
Wildlife Acoustics: This US-based company has a strong presence in India, providing acoustic monitoring technologies to researchers, conservationists, and protected area managers. Their Song Meter recorders and EcoNet software help track wildlife populations, monitor biodiversity, and assess the effectiveness of conservation efforts.
Kheyti: This Indian startup uses satellite imagery, machine learning, and big data analytics to provide farmers with information on soil health, crop health, and water availability. This information can help farmers improve their agricultural practices and reduce their environmental impact.
Waycool: This Indian company builds and operates a network of cold chain facilities that help farmers store and transport their produce more efficiently. This reduces food spoilage and waste, which is a major environmental problem.
Ecodit Technologies: This Bengaluru-based startup uses AI and machine learning to monitor forests and detect illegal activities such as deforestation and poaching. Their cloud-based platform provides real-time insights to forest departments and conservation NGOs, helping them to better protect India's natural resources.
Conclusion
International conservation technology is transforming the landscape of environmental conservation in India. By embracing these advanced tools and fostering global partnerships, India is making significant strides in protecting its unique ecosystems and wildlife. As these technologies continue to evolve, they offer hope for a sustainable future where nature and humanity can coexist harmoniously.
About Global Launch Base:
Global Launch Base helps international startups expand in India. Our services include market research, validation through surveys, developing a network, building partnerships, fundraising, and strategy revenue growth. Get in touch to learn more about us.
Contact Info:
Website: www.globallaunchbase.com
LinkedIn: https://www.linkedin.com/company/globallaunchbase/
Email: [email protected]
0 notes
Text
What Reportedly Contributed To Impact Shifting Back To The TNA Brand And What To Expect
Read More Wrestling Inc. By /Oct. 22, 2023 10:34 am EST In January 2024, Impact Wrestling will be no more, and TNA Wrestling will rise like a mighty phoenix from the ashes. There are now more details on Impact’s major announcement to rebrand. According to PWInsider, management wanted to find a way to unite the history of the promotion, which has been named NWA TNA, TNA, Impact, and GFW over the…
View On WordPress
0 notes
Text
Slammiversary preview

Alex Shelley vs. Nick Aldis - Aldis won a match on June 9 to earn this shot at the Impact men's world title. It had been looking like they were setting up a feud between Aldis and Steve Maclin, but then Shelley captured the title from Maclin (also on June 9), so I'm not sure what's going on. Regardless, Aldis turned heel by attacking Shelley on June 15.
Aldis originally came to Imapct (then known as TNA) in 2008 as "Brutus Magnus," and quickly got lost in the shuffle until the company remembered to push him to a world title run in 2013-2014. Magnus might have become a fixture in Impact, but the company was facing hard times and he left for (seemingly) greener pastures in Global Force Wrestling, where he held their world title as Nick Aldis. When GFW was absorbed into Impacft, he returned just long enough to drop the belt, and this time left to work for Billy Corgan as the NWA men's world champion. After that relationship soured, Aldis has finally come home, sort of. So he's spent most of his career excelling in relative obscurity--he's probably best known to casual fans for losing the NWA title to Cody Rhodes at All In in 2018. But Impact's fortunes have improved, and it might finally be a proper stage for him to be the top star.
I still don't know what to make of Shelley as champion. It's cool in a "you deserve it" kind of way, in that he's been with Impact for most of the last 20 years and they finally put the top belt on him. But I was really expecting 2023 to be the year of Steve Maclin. Is Shelley meant to be a long-term champion? Or is he just here to put over Aldis, so they can save Aldis vs. Maclin for later? I suppose it'll be interesting to find out.
Impact could plausibly go with either guy on top for the next six months. But my money is on Aldis. I can't picture him fitting into AEW/ROH, and nobody's going to WWE right now, so the best place for him is playing Harley Race in the #3 US promotion. You put your world title on Aldis and he makes it mean something, simple as that.
Deonna Purrazzo vs. Trinity - Purrazzo is defending the Impact women's world title. Trinity is of course Trinity Fatu, formerly known as Naomi in WWE until she left in 2022 and finally debuted with Impact in April. I'm surprised this is where she landed, but it's a big get for Impact. I don't know if she passed on AEW and NJPW, or if they weren't interested in her, but either way I'd like to see her prove she can excel wherever she is.
The natural storyline here is a longrunning champ like Purrazzo resenting the arrival of a much bigger star from the big leagues. Impact has done that story so many times they've got it down to a science. It's promotional malpractice not to book Trinity as champion, but Purrazzo was already in the middle of dominating the division and trying to prove Mickie James isn't its top star. Trinity has to either disrupt all that, or get knocked down a peg and find her way back to the top. My guess is she'll just win the belt straight away. And if it was up to me, I'd keep it on her until Mickie James is ready to return.
Bully Ray & Cody Deaner vs. Scott D'Amore & ??? - D'Amore is the on-screen president of Impact Wrestling. On May 26, Bully Ray and Steve Maclin threw him through a table they set on fire. D'Amore, who used to be an indie wrestler years ago, took a leave of absence from his duties to feud with Ray and Maclin, which was kind of one-sided until PCO improbably showed up to help. So Ray & Maclin vs. D'Amore & PCO was signed for this show...but the heels set PCO on fire on July 6, and then Maclin was sidelined with a legit injury. Deaner stepped up to replace Maclin, and we don't know who D'Amore has in mind for his partner. Is Petey Williams available?
I assume this will be the usual clusterfuck whenever Bully Ray does a big blowoff match with somebody he's been picking on for months. I assume the mystery partner pins Ray to end the feud, but the whole buildup to this match has been chaotic so I don't think you can predict anything going forward.
Chris Sabin vs. Lio Rush - Sabin is defending the Impact X division title. Rush has mainly been in New Japan this year, including some great babyface moments in the Best of the Super Jr. tournament, but he's a heel in Impact after aligning with Nick Aldis against Sabin and Alex Shelley. I don't care, I remember that couple in Japan that let Lio hold their newborn baby, and I want him to win all the belts, starting with this one.
Ace Austin & Chris Bey vs. Moose & Brian Myers vs. Rich Swann & Sami Callihan vs. Mark Andrews & Flash Morgan Webster - Austin and Bey (ABC) are defending the Impact men's tag team title in a four-way match, so whoever scores the first fall on any opponent wins the match and the title for his team. Moose and Myers formed an alliance recently because neither of them have anything better to do. I think Swann and Callihan joined forces against The Design, which seems to be done, but they're still teaming, I guess. The real story here is Subculture (Andrews and Webster, along with Dani Luna) coming in from the downfall of NXT UK. If anybody's going to beat ABC for the tag titles, I'd like to see them do it, just to shake up the tag division.
Eddie Edwards vs. Frankie Kazarian - I don't know, it's two aging wrestlers who've been around forever and now they're fighting again and I guess their wives are involved. I guess Kaz wins.
KiLynn King & Taylor Wilde vs. Killer Kelly & Masha Slamovich - The Coven (King & Wilde) are defending the Impact women's tag team title. Last I looked Slamovich and Kelly were two scary mean ladies who hated each other but now they're scary mean ladies working together, which sounds like bad news for the Coven. I'm cool with witches vs. ass-kickers as a long-term program, so whoever wins I hope they keep doing this.
Jonathan Gresham vs. KUSHIDA vs. Mike Bailey vs. Kevin Knight vs. Alan Angels - This is an Ultimate X match but I think the show starts in about fifteen minutes so I'm not going to spend any time explaining how that works. The winner gets to challenge for the X division title. Angels seems to be getting repackaged for a push so I'll pick him to win.
Jody Threat & Courtney Rush & Jessicka vs. Gisele Shaw & Savannah Evans & Jai Vidal - This is scheduled for the pre-show. Rush and Jessicka used to be Rosemary and Havok, but I guess a bunch of spooky storyline shit turned them into regular people. Vidal is Shaw's male valet, and in wrestling if you're a guy who acts like a lady wrestler's assistant, that makes it okay for you to regularly team with her against women. I don't pay enough attention to Impact to know what Evans or Threat has to do with anything. I'm guessing Threat, Rush, and Jessicka win.
Joe Hendry vs. Kenny King - This is set for the pre-show, and Hendry is defending the digital media championship, which might as well be the PPV pre-show title. I guess Hendry wrote an amusing song making fun of his opponent again, ha ha, lather rinse repeat. Hendry probably retains.
0 notes
Photo

"Think for yourself and question everything!" ~ Matt Sydal ✌ Turn on, Tune in, Take off! Namaste. 🙏❤😊
#matt sydal#reborn matt sydal#impact wrestling#gfw impact#pro wrestling noah#njpw#new japan pro wrestling#shooting star press here now#wrestling is an art#xdivision champ#boarder city wrestling#aaa#lucha underground#ladies man#yoga#yoga is life#namaste
16 notes
·
View notes
Video
youtube
5 Most DEVASTATING Piledrivers in IMPACT Wrestling History | GWN Top 5
#tna wrestling#tna impact wrestling#tna impact#NWATNA#impact wrestling#gfw impact#Impact on Pop#piledriver
2 notes
·
View notes
Text


13 notes
·
View notes
Photo

Jeff Jarrett presents the GFW Global Championship and the Impact Wrestling World Heavyweight Championship before the unification match between Lashley and Alberto El Patron. Slammiversary XV July 2, 2017
10 notes
·
View notes
Photo

99 notes
·
View notes
Photo

Christy Hemme
#christy hemme#WWE#WWE Divas#Wrestling Women#female wrestling#Shimmer Wrestling#impact wrestling#tna knockout#gfw impact#Wrestling
21 notes
·
View notes