#freeipa
Explore tagged Tumblr posts
Text
If this post gets 100 notes Ill actually deploy and setup FreeIPA
3 notes
·
View notes
Text
FreeIPA 4.10.1 Denial Of Service / Information Disclosure
http://i.securitythinkingcap.com/T366W4
0 notes
Text
Configuring an Ubuntu Workstation with XRDP, SSHD, VNC, FreeIPA, SSSD, Java, NetBeans
Building an Ubuntu Workstation for development and general use, one that can be accessed remotely with central authentication. Most of the commands below will be ran as the root user, hence # sudo su – to root will be needed. Let’s get going: ALIAS SETUP Personally, the following alias just makes it a tad easier to get around: $ grep -Ei altri ~/.bashrc alias lt=’ls -altri’ $ Some of the other…
View On WordPress
0 notes
Text
Things I’ve Learned: FreeIPA
I've been a user of FreeIPA for quite a long time, mostly in home and lab environments that didn't really have any bearing on enterprise environments. I always saw it as a sort of Active Directory (it's not) for Linux and UNIX systems and used it to test various things. One example of using it to test "things" was practicing for my RHCE in 2016 and also studying my Red Hat Security Hardening. Now I've used it since version 3.0, and it definitely has come a long way since then. I never really took a lot of the time I thought was necessary to learn specific things about it, in terms of having it work with an Active Directory and even 2FA/OTP among other things. Many years ago, there were functions such as winsync (which is now deprecated) that helped with this, while even the sssd components began to slowly integrate Active Directory support directly.
To give some backstory to the title of this post: In my current job, we are a mixed environment shop. We have a handful of Windows, Linux, and UNIX systems. Because of this, we have two separate directory servers. We have an LDAP and an Active Directory. A few years back, I respawned conversations that were shut down by previous management: We need to consolidate directory servers into at least Active Directory. Practically all of our workstations run Windows or Mac. Our usernames between both directories are different (LDAP uses underscores between first and last names, AD had first initial, last name up to 7 characters and now it's first.last). You can imagine how confusing this is and how annoying this actually is.
You can imagine the challenges this brings. In fact, here's a list of challenges this poses for the organization.
New users get confused and think they login with user.name@domain, domain\user.name, user.name on Linux/UNIX systems
Users at times do not know what username is used for what application or system (is it user_name or user.name for $x?)
Introduction of OIM (oracle identity manager) and OAM (oracle access manager), which was setup incorrectly and managed poorly by incompetent team called "information security"
Now you might wonder why does this matter to my FreeIPA topic. Simple, it causes issues for the UNIX engineering team (which I now co-lead).
Managers and above as well as new users expect all their access to be already there for all Linux/UNIX systems they need to work on
Again, new users get confused and use AD usernames to login to Linux/UNIX systems
Access is defined on their LDAP objects as "host: hostname"
SUDO is hybrid: LDAP and /etc/sudoers.d files
Identity management tools, which have been in the environment for almost 4 years, were never designed to handle the above
Management is reluctant to go to "member" groups to define access to systems (to emulate "role based" access)
This is where I stepped in and suggested that we need to use a different product, even though I initially suggested we go to AD entirely. The problem with going to AD entirely is that it takes away the UNIX team's management, and plus we would probably need to buy other products or software just to get group policies to work. This did not sit well with majority of my team and I didn't like the idea either, especially because we then begin to lose a sense of control on our own systems. This is when I suggested FreeIPA, as FreeIPA at the time (version 4.4) supported IPA-AD trusts. This meant that it gave control back to the UNIX team to our own infrastructure. Logins would be from our AD, we wouldn't need to create accounts in FreeIPA. This reduces a lot of overhead on us, leaving LDAP to start to (hopefully) die off. My team as a whole agreed to the idea so I took the project and started it up.
This is what I've learned and achieved.
The Setup
The setup was easy for me. The network team delegated me a subdomain of one of our internal domains to make my life easier. The Windows team was also extremely helpful and helped me get the AD trust up. I didn't expect it to be a pain, as my tests at home succeeded. The trust was setup, enabling compat and posix attributes (uidNumber, gidNumber, unixHomedirectory, loginShell) to try and make the migration from LDAP to IPA easier. The Windows engineer also setup my team as well as two other teams with the attributes so I had a biggger test bed.
After doing this, I also set the domain resolution order (FreeIPA 4.5) to be the AD domain first. That way, logging in with just user.name without the @domain works without much an issue. And then, clients using sssd had full_name_format set to %1$s to make it less confusing for users on their prompts. I didn't like the idea of having a prompt like [email protected]@servername - that's extremely annoying to look at. When this is set, you are able to do id for users in both AD or IPA without the domain on the name and it succeeds on RHEL 7 and higher. Setting domain resolution order back to blank or not setting it at all will require the @domain to be used for logins, including in the compat tree. There's really no other clear way around this as far as I know.
SID Numbers
The issue with trying to do a cleanish migration is that you can't change gid numbers out from under people. FreeIPA creates a range for your domain and also creates a range for AD, even if you don't use it/you're using posix attributes. When you create groups outside of IPA's defaulted range, they will not receive SID numbers. In this case, I had to create another range and then rerun the proper SID generating scripts.
I created a range with this data:
Base ID: 10
Range size: 50000
Primary RID base: 200000000
Secondary RID base: 200050000
I then did an update across the board. This took a little bit.
# cat > /root/task/80-sidgen-task-conf.uipdate <<EOF dn: cn=$TIME-$FQDN,cn=ipa-sidgen-task,cn=tasks,cn=config add:objectClass: top add:objectClass: extensibleObject add:cn:$TIME-$FQDN add:nsslapd-basedn: $SUFFIX add:delay: 0 EOF # ipa-ldap-updater /root/task/80-sidgen-task-conf.update
SUDO
SUDO for clients older than RHEL 7 was very interesting when in a IPA-AD trust.
Legacy Clients
Our environment is ridiculously mixed. We have Solaris 8, 10, 11, RHEL 5, 6, and 7. We also have Fedora workstations that my team uses because we dislike Windows, but that's a different story. We have still been trying to get rid of Solaris 8 forever now, but without any movement. We decided to not attach Solaris 8 to FreeIPA to hopefully let the systems rot.
RHEL 5
"RHEL 5???" you might be thinking. Yes. It's been out of support since March 31, 2017. This company has no concept of anything "new" or wanting to get rid of technology debt. So since we were probably going to be stuck with RHEL 5 for another year or so, I had to figure out how to get it to connect to FreeIPA - not only as a client but also be able to see Active Directory users. The first thing I learned here: Always use the ipa-advise command - Seriously. This will help you out so much.
In my case, I used nss pam ldap to help here. What this provided at the very least is the ability to get sudo to actually work 100% of the time - sudo didn't work all the time when sssd was the id provider. Here's the issue:
The domain resolution order configuration causes multiple uid attributes to appear on objects in the compat tree - this is normal.
Group membership, even in the compat tree, is defined by [email protected], rather than just user. As far as I know, there's no clear way around this. Running groups or id will not show proper membership.
sudo probably only worked here because of the id output, even though I was logging in with first.last, my id shows up as [email protected] and associated that properly with my group membership
When using sssd, while the user would appear as first.last, group membership would never be applied. Here's what I mean.
dn: uid=first.last,cn=users,cn=compat,dc=ipa,dc=example,dc=com cn: First Last objectClass: posixAccount objectClass: top gidNumber: 1006800013 gecos: First Last uidNumber: 10000 loginShell: /bin/bash homeDirectory: /home/first.last uid: [email protected] uid: first.last dn: cn=unixadm,cn=groups,cn=compat,dc=ipa,dc=example,dc=com gidNumber: 5900 objectClass: posixGroup objectClass: ipaOverrideTarget objectClass: ipaexternalgroup objectClass: top ipaAnchorUUID:: removed cn: unixadm memberUid: [email protected]
I'm sure you see the problem. This causes other issues: If you're trying to use pam_hbac, it seems to want to work using pam_sss in the stack, not pam_ldap. With pam_ldap, it doesn't even try. With pam_sss, it tries, but it ultimately fails because it doesn't seem to be properly evaluating the rules and groups - again, this goes back to what I said: group membership is not seen with sssd fully while nss pam ldap can associate it to an extent.
As of this writing, I was never able to properly figure this out. What I noticed is in sssd, the group memberships were always intermittent. In fact, it always acted weird - if I did getent group unixadm, it'd show me. As soon as I ran id against my user, I'd disappear from the group. And I found this to be very troublesome. Sometimes it worked, other times it didn't. I could never really figure out why this was happening. One thing I did try was updating SSSD to 1.9.6 from a COPR repo. That didn't help.
Long story short: get rid of your RHEL 5 systems. At least RHEL 6 worked. Sort of.
Solaris 10
Alright, so this is where it gets interesting. Getting it to work with FreeIPA was a chore, a serious chore. The worst part about all of this is the communication from the system to FreeIPA is unencrypted. Yes, you heard this right. Unencrypted. I couldn't even get it to be OK with Kerberos login to at least have a secure channel. The saving grace here is that if you have a keytab on your system and login, it should just work. The other problem I had is I needed to use pam_ldap in my pam configuration.
First thing I needed is a profile that the ldapclient could use. I also created a solaris system account. Here's an example ldif below you can add into IPA.
dn: cn=solaris_authpam,ou=profile,dc=ipa,dc=example,dc=com serviceAuthenticationMethod: pam_ldap:simple authenticationMethod: simple objectClass: top objectClass: DUAConfigProfile bindTimeLimit: 5 cn: default cn: solaris_authpam defaultSearchBase: dc=ipa,dc=example,dc=com defaultServerList: pentl01.ipa.example.com pentl02.ipa.example.com followReferrals: TRUE objectclassMap: shadow:shadowAccount=posixAccount objectclassMap: passwd:posixAccount=posixaccount objectclassMap: group:posixGroup=posixgroup profileTTL: 6000 searchTimeLimit: 15 serviceSearchDescriptor: group:cn=groups,cn=compat,dc=ipa,dc=example,dc=com serviceSearchDescriptor: passwd:cn=users,cn=compat,dc=ipa,dc=example,dc=com serviceSearchDescriptor: netgroup:cn=ng,cn=compat,dc=ipa,dc=example,dc=com serviceSearchDescriptor: ethers:cn=computers,cn=accounts,dc=ipa,dc=example,dc=com serviceSearchDescriptor: sudoers:ou=sudoers,dc=ipa,dc=example,dc=com dn: uid=solaris,cn=sysaccounts,cn=etc,dc=ipa,dc=example,dc=com objectClass: account objectClass: simpleSecurityObject objectClass: top uid: solaris userPassword: secret123
I needed to create a keytab for the host.
# ipa host-add hostname.example.com # ipa-getkeytab -s pentl01.ipa.example.com -p host/[email protected] -k /tmp/hostname.keytab
I then transferred the keytab to the system and put it at /etc/krb5/krb5.keytab. I configured /etc/krb5/krb5.conf.
[libdefaults] default_realm = IPA.EXAMPLE.COM dns_lookup_kdc = true verify_ap_req_nofail = false [realms] IPA.EXAMPLE.COM = { } DOMAIN.TLD = { } [domain_realm] ipa.example.com = IPA.EXAMPLE.COM .ipa.example.com = IPA.EXAMPLE.COM domain.tld = DOMAIN.TLD .domain.tld = DOMAIN.TLD [logging] default = FILE:/var/krb5/kdc.log kdc = FILE:/var/krb5/kdc.log kdc_rotate = { period = 1d version = 10 } [appdefaults] kinit = { renewable = true forwardable= true }
Set the permissions of the keytab to 600, owned by root:sys. Once it was configured, I tested kinit [email protected]. If you get a message about "kt warn", it can be ignored. After this, set /etc/defaultdomain to your ipa domain (ipa.example.com). Configure /etc/ldap.conf.
base dc=ipa,dc=example,dc=com scope sub TLS_CACERTDIR /var/ldap TLS_CERT /var/ldap/cert8.db TLS_CACERT /var/ldap/ipa.pem tls_checkpeer no ssl off bind_timelimit 120 timelimit 120 uri ldap://pentl01.ipa.example.com sudoers_base ou=sudoers,dc=ipa,dc=example,dc=com pam_lookup_policy yes
Create /var/ldap if needed and create an NSS certificate database. You should also have your CA certificate as /var/ldap/ipa.pem.
# cd /var/ldap # /usr/sfw/bin/certutil -A -n "ca-cert" -i /var/ldap/ipa.pem -a -t CT -d .
At this point, I do the ldapclient init.
# ldapclient init -a profileName=solaris_authpam \ -a domainName=ipa.example.com \ -a proxyDN="uid=solaris,cn=sysaccounts,cn=etc,dc=ipa,dc=example,dc=com" \ -a proxyPassword="secret123" \ -D uid=solaris,cn=sysaccounts,cn=etc,dc=ipa,dc=example,dc=com \ -w qdbKnW1et pentl01.ipa.example.com
Now configure /etc/nsswitch.conf.
passwd: files ldap [NOTFOUND=return] group: files ldap [NOTFOUND=return] sudoers: files ldap netgroup: ldap
Now configure /etc/pam.conf
# Console login auth requisite pam_authtok_get.so.1 login auth sufficient pam_krb5.so.1 login auth required pam_dhkeys.so.1 login auth required pam_unix_cred.so.1 login auth required pam_dial_auth.so.1 login auth required pam_unix_auth.so.1 use_first_pass login auth required pam_ldap.so.1 rlogin auth sufficient pam_rhosts_auth.so.1 rlogin auth requisite pam_authtok_get.so.1 rlogin auth sufficient pam_krb5.so.1 rlogin auth required pam_dhkeys.so.1 rlogin auth required pam_unix_cred.so.1 rlogin auth required pam_unix_auth.so.1 rlogin auth required pam_ldap.so.1 # Needed for krb krlogin auth required pam_unix_cred.so.1 krlogin auth sufficient pam_krb5.so.1 # Remote Shell rsh auth sufficient pam_rhosts_auth.so.1 rsh auth required pam_unix_cred.so.1 rsh auth binding pam_unix_auth.so.1 server_policy rsh auth required pam_ldap.so.1 # Needed for krb krsh auth required pam_unix_cred.so.1 krsh auth required pam_krb5.so.1 # ? ppp auth requisite pam_authtok_get.so.1 ppp auth required pam_dhkeys.so.1 ppp auth required pam_dial_auth.so.1 ppp auth binding pam_unix_auth.so.1 server_policy ppp auth required pam_ldap.so.1 # Other, used by sshd and "others" as a fallback other auth requisite pam_authtok_get.so.1 other auth sufficient pam_krb5.so.1 other auth required pam_dhkeys.so.1 other auth required pam_unix_cred.so.1 other auth binding pam_unix_auth.so.1 server_policy other auth required pam_ldap.so.1 other account requisite pam_roles.so.1 other account required pam_projects.so.1 other account binding pam_unix_account.so.1 server_policy other account required pam_ldap.so.1 other session required pam_unix_session.so.1 other password required pam_dhkeys.so.1 other password requisite pam_authtok_get.so.1 other password requisite pam_authtok_check.so.1 other password required pam_authtok_store.so.1 server_policy # passwd and cron passwd auth binding pam_passwd_auth.so.1 server_policy passwd auth required pam_ldap.so.1 cron account required pam_unix_account.so.1 # SSH Pubkey - Needed for openldap and still probably needed for ipa # without this, ssh keys stopped working. sshd-pubkey account required pam_unix_account.so.1
I installed pkgutil from OpenCSW. Seriously, this will help you out tremendously.
# /opt/csw/bin/pkgutil -y -i sudo sudo_ldap # vi /etc/opt/csw/sudo.conf Plugin sudoers_policy sudoers-ldap.so Plugin sudoers_io sudoers-ldap.so # ln -s /etc/ldap.conf /etc/opt/csw/ldap.conf
After that, I went ahead and tested id, logins, etc.
bash-3.2# id louis.abel uid=25439([email protected]) gid=1006800013(aocusers)
The current problem is that id won't show group membership, yet if you run the groups command, it will. Just because it shows the groups, doesn't mean you can really work with the files that are group owned as such. This only changes if you login via [email protected].
Solaris 11
Solaris 11 was a lot more forgiving. I was able to get SSL to work and the sudo that they provide to work also. Most of the things above can be used. I'll point out which ones you can pull from above.
Create another profile on the IPA server.
dn: cn=solaris_authssl,ou=profile,dc=ipa,dc=example,dc=com authenticationMethod: tls:simple objectClass: top objectClass: DUAConfigProfile bindTimeLimit: 5 cn: default cn: solaris_authssl defaultSearchBase: dc=ipa,dc=example,dc=com defaultServerList: pentl01.ipa.example.com pentl02.ipa.example.com followReferrals: TRUE objectclassMap: shadow:shadowAccount=posixAccount objectclassMap: passwd:posixAccount=posixaccount objectclassMap: group:posixGroup=posixgroup searchTimeLimit: 15 serviceSearchDescriptor: group:cn=groups,cn=compat,dc=ipa,dc=example,dc=com serviceSearchDescriptor: passwd:cn=users,cn=compat,dc=ipa,dc=example,dc=com serviceSearchDescriptor: netgroup:cn=ng,cn=compat,dc=ipa,dc=example,dc=com serviceSearchDescriptor: ethers:cn=computers,cn=accounts,dc=ipa,dc=example,dc=com serviceSearchDescriptor: sudoers:ou=sudoers,dc=ipa,dc=example,dc=com profileTTL: 6000
Generate your keytabs and move them to the server.
Configure the krb5.conf file as necessary.
Set /etc/defaultdomain to your IPA domain.
Place IPA cacert into /var/ldap/ipa.pem
Your /etc/ldap.conf will need to be a tad different on Solaris 11. You will need to remove the TLS_CERT line. Solaris 11 no longer uses NSS.
base dc=ipa,dc=example,dc=com scope sub TLS_CACERTDIR /var/ldap TLS_CACERT /var/ldap/ipa.pem tls_checkpeer no ssl off bind_timelimit 120 timelimit 120 uri ldap://pentl01.ipa.example.com sudoers_base ou=sudoers,dc=ipa,dc=example,dc=com pam_lookup_policy yes
To configure nsswitch, you have to run commands (thanks oracle).
/usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/default = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/sudoer = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/password = astring: "files ldap [NOTFOUND=return]"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/group = astring: "files ldap [NOTFOUND=return]"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/host = astring: "files dns"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/network = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/protocol = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/rpc = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/ether = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/netmask = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/bootparam = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/publickey = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/netgroup = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/automount = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/alias = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/printer = astring: "user files"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/service = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/project = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/auth_attr = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/prof_attr = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/tnrhtp = astring: "files ldap"' /usr/sbin/svccfg -s svc:/system/name-service/switch 'setprop config/tnrhdb = astring: "files ldap"' /usr/sbin/svcadm refresh svc:/system/name-service/switch ; /usr/sbin/svcadm restart svc:/system/name-service/switch ; /usr/sbin/svcadm restart ldap/client
Now you need to setup all of your pam files. Here are the ones I configured and it worked.
# /etc/pam.d/krlogin auth required pam_unix_cred.so.1 auth required pam_krb5.so.1 # /etc/pam.d/krsh auth required pam_unix_cred.so.1 auth required pam_krb5.so.1 # /etc/pam.d/login auth requisite pam_authtok_get.so.1 auth sufficient pam_krb5.so.1 auth required pam_dhkeys.so.1 auth required pam_unix_cred.so.1 auth required pam_dial_auth.so.1 auth required pam_unix_auth.so.1 server_policy auth required pam_ldap.so.1 # /etc/pam.d/other auth definitive pam_user_policy.so.1 auth requisite pam_authtok_get.so.1 auth sufficient pam_krb5.so.1 auth required pam_dhkeys.so.1 auth required pam_unix_cred.so.1 auth required pam_unix_auth.so.1 server_policy auth required pam_ldap.so.1 account requisite pam_roles.so.1 account definitive pam_user_policy.so.1 account required pam_unix_account.so.1 server_policy account required pam_krb5.so.1 account required pam_tsol_account.so.1 account required pam_ldap.so.1 session definitive pam_user_policy.so.1 session required pam_unix_session.so.1 password definitive pam_user_policy.so.1 password include pam_authtok_common password sufficient pam_krb5.so.1 password required pam_authtok_store.so.1 server_policy # /etc/pam.d/passwd auth binding pam_passwd_auth.so.1 server_policy auth required pam_ldap.so.1 account requisite pam_roles.so.1 account definitive pam_user_policy.so.1 account required pam_unix_account.so.1 # /etc/pam.d/ppp auth requisite pam_authtok_get.so.1 auth required pam_dhkeys.so.1 auth required pam_unix_cred.so.1 auth required pam_dial_auth.so.1 auth required pam_unix_auth.so.1 server_policy auth required pam_ldap.so.1 # /etc/pam.d/rlogin auth definitive pam_user_policy.so.1 auth sufficient pam_rhosts_auth.so.1 auth requisite pam_authtok_get.so.1 auth sufficient pam_krb5.so.1 auth required pam_dhkeys.so.1 auth required pam_unix_cred.so.1 auth required pam_unix_auth.so.1 auth required pam_ldap.so.1 # /etc/pam.d/rsh auth definitive pam_user_policy.so.1 auth sufficient pam_rhosts_auth.so.1 auth required pam_unix_cred.so.1 auth required pam_ldap.so.1 # /etc/pam.d/sshd-pubkey account required pam_unix_account.so.1
The only issue is if you are using domain resolution order, trying to login without the realm name for AD users will cause an assertion error. I asked Oracle to fix this because Solaris 10 was fine. I don't know when they'll fix it. As of this writing, they claim October 20, 2017.
The actual current problem is that id won't show group membership, yet if you run the groups command, it will. Just because it shows the groups, doesn't mean you can really work with the files that are group owned as such. This only changes if you login via [email protected] or remove the domain resolution order entirely - this would cause you to have to login with username@domain.
HBAC
For legacy clients to authenticate AD users properly, you need an HBAC rule against the IPA servers that perform the task of talking to AD. I'd recommend creating an ipaservers group (if one doesn't exist already) of all of your IPA servers, and then creating the hbac rules.
# ipa hbacsvc-add system-auth # ipa hbacrule-add system-auth-legacy # ipa hbacrule-add-host --hostgroup=ipaservers # ipa hbacrule-mod --usercat=all system-auth-legacy
For legacy clients, you need the pam_hbac module. For RHEL 5, there is a copr repo that you can pull the RPM's for. For Solaris, you are required to compile them, which isn't fun, I understand. Below I'll show you how to compile the modules and how to utilize the module.
Solaris 10 ++++++++++
You need to install OpenCSW's pkgutil. I also brought the sources of pam_hbac from github over as a git clone in a tar file.
root# pkgutil -y -i libglib2_dev gmake openssl binutils gcc4g++ glib2 ar libnet root# cd /tmp root# tar xf pam_hbac.tar root# cd /tmp/pam_hbac root# PATH=$PATH:/opt/csw/bin root# autoconf -o configure ; autoreconf -i root# ./configure AR=/opt/csw/bin/gar --with-pammoddir=/usr/lib/security --sysconfdir=/etc/ --disable-ssl root# vi Makefile.am ## Comment out the man pages #if HAVE_MANPAGES #SUBDIRS += doc #endif root# make root# make install root# /etc/pam_hbac.conf URI = ldap://pentl01.ipa.example.com BASE = dc=ipa,dc=example,dc=com BIND_DN = uid=hbac,cn=sysaccounts,cn=etc,dc=ipa,dc=example,dc=com BIND_PW = secret123 SSL_PATH = /var/ldap HOST_NAME = hostname.example.com
After this, you can place the hbac lines in your pam file. I usually put it under 'other' and 'login' as "account".
login auth requisite pam_authtok_get.so.1 login auth sufficient pam_krb5.so.1 login auth required pam_dhkeys.so.1 login auth required pam_unix_cred.so.1 login auth required pam_dial_auth.so.1 login auth required pam_unix_auth.so.1 use_first_pass login auth required pam_ldap.so.1 login account required pam_hbac.so ignore_unknown_user ignore_authinfo_unavail debug # other account requisite pam_roles.so.1 other account required pam_projects.so.1 other account binding pam_unix_account.so.1 server_policy other account required pam_ldap.so.1 other account required pam_hbac.so ignore_unknown_user ignore_authinfo_unavail debug
To answer your question, yes. I had to disable SSL. This is because IPA has a lot of ciphers turned off. Solaris 10 doesn't support much higher, and because these are dynamically compiled (not static), they pick up both SSL libraries from OpenCSW and the system. But the system is picked up first and used.
Solaris 11 ++++++++++
Compiling on Solaris 11 is easier (thankfully).
root# pkg install autoconf libtool pkg-config automake gcc asciidoc docbook (some of these won't install, that's fine) root# cd /tmp root# tar xf pam_hbac.tar root# cd /tmp/pam_hbac root# autoreconf -if root# ./configure --with-pammoddir=/usr/lib/security --mandir=/usr/share/man --sysconfdir=/etc/ root# make root# make install root# /etc/pam_hbac.conf URI = ldap://pentl01.ipa.example.com BASE = dc=ipa,dc=example,dc=com BIND_DN = uid=hbac,cn=sysaccounts,cn=etc,dc=ipa,dc=example,dc=com BIND_PW = secret123 SSL_PATH = /var/ldap HOST_NAME = hostname.example.com
Pam is a little different here. I configured login and other just like on Solaris 10.
# goes at the VERY end of the account block in /etc/pam.d/other and /etc/pam.d/login account required pam_hbac.so ignore_unknown_user ignore_authinfo_unavail debug
General +++++++
You also need to create an hbac service in IPA.
# ipa hbacsvc-add sshd-gssapi # ipa hbacsvc-add sshd-kbdint
You would need to associate those in particular to your HBAC rule sets as needed for your legacy hosts.
Summary
What I've learned overall is that trying to get legacy clients to work with FreeIPA is actually simple if you were only using IPA. It begins to get tricky when you add in AD. The other thing I've learned is that there are companies that will not let go of their dying systems and we just have to live with it. Because this is the case and I know it will not change any time soon, I had to really put a lot of (unnecessary) effort into making this all work. RHEL 6 and RHEL 7? Easy. RHEL 5, Solaris 10/11? Not so easy.
This also gave me a more of a sour taste in my mouth about the political landscape of an enterprise. It's just flat out unfortunate. But, I am glad I got this experience so I can show others what I had to deal with and hopefully others can conquer it in the same way or even better than I have.
1 note
·
View note
Link
Fedora Server 26 has been released and it offers quite a lot of improvements and features you might want to employ. Features like:
Enterprise domain solution with FreeIPA 4.5.
SSSD file caching to speed up user and group queries.
Preview of the upcoming Boltron (modular system which enables different versions of applications to run on the same system).
Server Roles (easily deploy various roles using the Rolekit tool)
Enterprise-class, scalable databases with PostgreSQL
#fedora 26#server#opensource#installation#domain#freeipa#sssd#boltron#rolekit#isoimage#UNetBootin#brasero#xfburn#bootable#gui#configuration#hostname#network
0 notes
Text
Kerberos explained to a 5 year old
Noticed this on HN and liked it:
http://www.roguelynn.com/words/explain-like-im-5-kerberos/
Related are https://web.mit.edu/kerberos/dialogue.html and the suggestion to use FreeIPA
0 notes
Photo

Вышел он в 2014-м году. Казалось бы - Верной дорогой идёте товарищи! К третьему гному! Но... “ НТЦ ИТ «Роса» представил новую версию отечественного коммерческого Linux-дистрибутива ROSA Enterprise Desktop – X4 (RED X4). ... Базовая версия ОС включает широкий набор приложений, позволяю��ий начать работу сразу после установки: браузер Firefox-ESR, почтовый клиент Mozilla Thunderbird, офисный пакет LibreOffice, редакторы изображений GIMP и Inkscape, видеоредактор KDEnlive, клиент обмена сообщениями Pidgin, медиапроигрыватели и еще целый ряд приложений.RED X4 совместима с программами семейства «1C» и утилитами «КриптоПро», а также со многими другими проприетарными программами.Технические особенности версии: использовано ядро версии 4.15 (в репозиториях также доступны ядра 4.18, 4.20 и 5.0); дизайн и эргономика системы выполнены в фирменном стиле, с использованием разработанных специально для ROSA элементов и программ – SimleWelcome, Klook, RocketBar и других; управление Системой, в том числе ввод в домены Windows AD и FreeIPA, осуществляется с помощью графических утилит, интегрированных в единый центр управления KDE; основной веб-браузер Firefox-ESR интегрирован в KDE; в качестве дополнительного выбран «Яндекс.Браузер»; поддержка Java-программ осуществляется с помощью предустановленной java-1.8.0-openjdk.” Г0внокодеры - ламеры и апазорились! Вместо кошерного третьего гнома - богопротивные позорные кеды. х*яндекс со шпионским блоком. прочиая муть... При этом роса всё равно лучше альта и астры, но и её умудрились изгадить... Жаль, что асп-линукс помер... Он был наименее позорным из упомянутой четвёрки...
1 note
·
View note
Text
Are you looking for an easy way to export a Virtual Machine running on Proxmox VE and running it on KVM hypervisor. Proxmox VE is an enterprise grade Virtualization solution that runs on Debian operating system. It gives SysAdmins a powerful dashboard from where most virtualization operations can be performed. In this article we’ll cover the process of migrating a Virtual Machine from Proxmox VE to KVM. I have a Proxmox VE 7 server with few Virtual Machines as listed using qm command line tool below: $ qm list VMID NAME STATUS MEM(MB) BOOTDISK(GB) PID 100 Ubuntu22 running 2048 20.00 1092 101 Controller running 2048 32.00 1138 102 FreeIPA-Server running 8192 50.00 1210 The Virtual Machine that I would be migrating from Proxmox VE to vanilla KVM is the one with id 102. We can check more information about the virtual machine using config qm command option. $ qm config 102 agent: 1 boot: order=scsi0;ide2;net0 cores: 4 cpu: host ide2: none,media=cdrom memory: 8192 meta: creation-qemu=6.2.0,ctime=1658942649 name: FreeIPA-Server net0: virtio=AE:39:5A:16:10:FB,bridge=vmbr0,firewall=1 numa: 0 onboot: 1 ostype: l26 parent: FreeIPA_installed protection: 1 scsi0: local-lvm:vm-102-disk-0,size=50G scsihw: virtio-scsi-pci smbios1: uuid=a4075e7d-4278-478f-8d79-50f369c9b9c2 sockets: 1 vmgenid: b08b23e6-c545-41d8-9423-fca2855a759d Export Proxmox VE Virtual Machine as Qcow2 image The current default setup of Proxmox VE uses LVM. When you do an installation of Proxmox on your server hardware and select a single disk for use, the same disk is set as physical volume for the Volume Group (VG) pve. A physical volume and volume group used can be checked with the command: # pvs PV VG Fmt Attr PSize PFree /dev/nvme0n1p3 pve lvm2 a--
0 notes
Text
Practical LPIC-3 300: Prepare for the Highest Level Professional Linux Certification
Practical LPIC-3 300: Prepare for the Highest Level Professional Linux Certification
Practical LPIC-3 300: Prepare for the Highest Level Professional Linux Certification Antonio Vazquez Gain the essential skills and hands-on expertise required to pass the LPIC-3 300 certification exam. This book provides the insight for you to confidently install, manage and troubleshoot OpenLDAP, Samba, and FreeIPA. Helping you to get started from scratch, this guide is divided into three…

View On WordPress
0 notes
Text
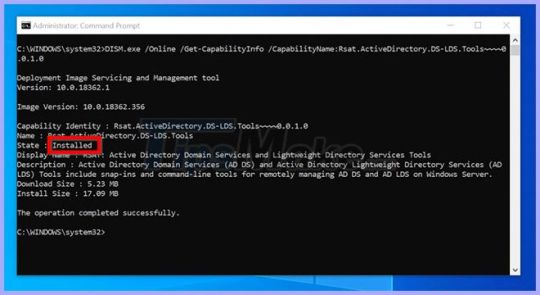
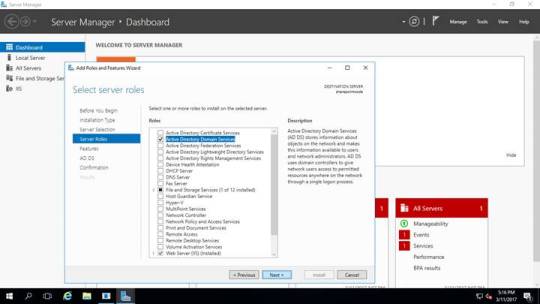
Enable active directory domain services windows 10

When the rubber hits the road, the choice boils down to which of the two you can set up quickly, given your current environment and your team's skill set.īut what happens when you choose AD, and you have a few CentOS servers, and you do not want to maintain a separate set of credentials for your Linux users? That overhead is entirely avoidable. Directory services such as FreeIPA are Linux-based and provide an excellent service for a Linux stable. This is one of the reasons for its ubiquity. In other words, it's going to be the automatic winner when your organization has many Windows systems. However, AD is a mature Windows-based service that comes incorporated with Windows Server systems. Other directory services include OpenLDAP and FreeIPA. AD is not the only directory service based on the x.500 standard, or that can be accessed using LDAP. LDAP is an open protocol for remotely accessing directory services over a connection-oriented medium such as TCP/IP. Basically, AD is a kind of distributed database, which is accessed remotely via the Lightweight Directory Access Protocol (LDAP). It saves time it saves emotions.Īt its heart, a directory service is just an organized way of itemizing all the resources in an organization while facilitating easy access to those resources. The bigger the organization, the greater the need for centralized management. That person's access to all resources is nullified on the spot. This directory can store staff phone numbers, email addresses, and can be extended to store other information. Using groups and organizational units, access to various resources can be tailored and maintained. The printers' authentication mechanism can be coupled with AD to achieve that. Members of staff can access the printers using the same set of credentials. Any account changes that need to be made are made once at the central database. Automatically, every user can access every workstation with that same set of credentials. Each computer system is also created as an object. With Active Directory, each user is uniquely created as an object in a central database, with a single set of credentials. This is where a directory service such as Active Directory thrives. I have not even spoken about managing access to the printers. Time that could be used for innovative tasks is now spent reinventing the wheel. I do not need to tell you the monotonous work that has to be repeated any time there's a change to the staffing or any workstations. Now, imagine two members of the staff resign. When a user changes his password for any reason, that user has to change the password on all computers he previously had access to, to keep things in sync. Imagine the workload on the end-user support team. The traditional way of working is to create local user accounts on each computer a user needs to access. Some have access to printing others don't.
Some employees run shifts while others work regular hours.
Imagine a collection of 40 computer systems and 70 users in a firm. Usually, the interaction is using one set of login credentials to log in to any workstation in the organization. For some of you reading this write-up, especially those who work in large institutions, you have interacted with AD before. It gives you the ability to manage users, passwords, resources such as computers, and dictate who has access to what. It is used by institutions and individuals the world over to centrally control access to resources belonging to the organization. Microsoft's Active Directory, more popularly known as AD, has held the lion's share of the market for enterprise access management for many years now.
Linux System Administration Skills Assessment.
Download Now: Basic Linux Commands Cheat Sheet.
Advanced Linux Commands Cheat Sheet for Developers.

0 notes
Text
Linux iso usb maker

So instead I propose # dd count= if=/dev/sdb of=win7.img Note, this copies the whole device! - which is usually (much) bigger than the files copied to it. Check the boot checkbox, then close.Īfter all that, you probably want to back up your USB media for further installations and get rid of the ISO file. Open gparted, select the USB drive, right-click on the file system, then click on "Manage Flags". or use the standard GUI file-browser of your systemĬall sync to make sure all files are written. Mount ISO and USB media: # mount -o loop win7.iso /mnt/iso
or (if syslinux is installed), you can run sudo dd if=/usr/lib/syslinux/mbr/mbr.bin of=/dev/sdb.
on newer Ubuntu installs) sudo lilo -M /dev/sdb mbr ( info) Write Windows 7 MBR on the USB stick (also works for windows 8), multiple options here: # cfdisk /dev/sdb or fdisk /dev/sdb (partition type 7, and bootable flag) Delete all partitions, create a new one taking up all the space, set type to NTFS (7), and remember to set it bootable: Grub is installed there!)Ĭheck what device your USB media is assigned - here we will assume it is /dev/sdb. Or alternatively, make sure lilo is installed (but do not run the liloconfig step on your local box if e.g. Install ms-sys - if it is not in your repositories, get it here. This works with the Windows 7 retail version. Basically, the missing step was to write a proper boot sector to the USB stick, which can be done from Linux with ms-sys or lilo -M. Use of livecd-iso-to-disk on any distribution other than Fedora is unsupported and not expected to work: please use an alternative method, such as Fedora Media Writer.OK, after unsuccessfully trying all methods mentioned here, I finally got it working. Even if it happens to run and write a stick apparently successfully from some other distribution, the stick may well fail to boot. Livecd-iso-to-disk is not meant to be run from a non-Fedora system. livecd-iso-to-disk on other Linux distributions If your test boot reports a corrupted boot sector, or you get the message MBR appears to be blank., you need to install or reset the master boot record (MBR), by passing -reset-mbr when writing the stick. If you get this message from fdisk, you may need to reformat the flash drive when writing the image, by passing -format when writing the stick. Partition has different physical/logical endings If you get the message Need to have a filesystem label or UUID for your USB device, you need to label the partition: dosfslabel /dev/sdX LIVE. Information: Don't forget to update /etc/fstab, if necessary.

Number Start End Size Type File system Flagsġ 32.3kB 1062MB 1062MB primary fat16 boot Sector size (logical/physical): 512B/512B Welcome to GNU Parted! Type 'help' to view a list of commands.
Difference between Fedora and Red Hat Enterprise Linux.
Installing, Configuring and Troubleshooting MySql/MariaDB.
Creating Windows virtual machines using virtIO drivers.
Installing virtual operating systems with GNOME Boxes.
Getting started with virtualization (libvirt).
Upgrading Fedora using the DNF system upgrade.
How to Set NVIDIA as Primary GPU on Optimus-based Laptops.
How to join an Active Directory or FreeIPA domain.
Getting started with Apache HTTP Server.
Managing keyboard shortcuts for running an application in GNOME.
Controlling network traffic with firewalld.
Displaying a user prompt on the GNOME login screen.
Understanding and administering systemd.
Performing administration tasks using sudo.
Configuring networking with NetworkManager CLI (nmcli).
Disabling the GNOME automatic screen locking.
Setting a key shortcut to run an application in GNOME.
Configuring Xorg as the default GNOME session.
Configuring X Window System using the nf file.
Installing Chromium or Google Chrome browsers.
Installing plugins for playing movies and music.
APT command equivalents on Fedora with DNF.
Securing the system by keeping it up-to-date.
Adding or removing software repositories in Fedora.
Finding and installing Linux applications.

Creating and using a live installation image.

0 notes
Text
Como configurar o cliente FreeIPA no Ubuntu 18.04 / CentOS 7 para centralizar a autenticação
Como configurar o cliente FreeIPA no Ubuntu 18.04 / CentOS 7 para centralizar a autenticação
Em nosso artigo anterior, já discutimos sobre o FreeIPA e suas etapas de instalação no servidor do CentOS 7, neste artigo discutiremos como uma máquina Ubuntu 18.04 e CentOS 7 pode ser integrada ao FreeIPA Server para autenticação centralizada.
Estou assumindo que o usuário “ sysadm ” já está criado no FreeIPA Server para sistemas Linux para autenticação centralizada, se não executar os comandos…
View On WordPress
1 note
·
View note
Text
[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failename mismatch, certificate is not valid for 'idmipa01.nix.mds.xyz'
When joining a new client to the FreeIPA servers: # ipa-client-install –uninstall; ipa-client-install –force-join -p USER -w “SECRET” –fixed-primarver=idmipa01.nix.mds.xyz –server=idmipa02.nix.mds.xyz –domain=nix.mds.xyz –realm=NIX.MDS.XYZ -U the following message is visible: Connection to https://idmipa01.nix.mds.xyz/ipa/json failed with [SSL: CERTIFICATE_VERIFY_FAILED] certificate verify…
View On WordPress
0 notes
Text
In this blog post we see how to set up time synchronization of your vSphere ESXi / vCenter using a time server from your local network. If using a Local NTP Server is not an option for you, it’s also okay to go with an Internet-based(Public) time server that takes care of your time zone. It is assumed that your NTP server doesn’t have authentication mechanisms in place, or any kind of access control that restricts NTP clients connectivity. Step 1: Configure NTP Server (Optional) You can choose to use publicly available NTP servers or set one locally in your infrastructure. For local installation and configuration of NTP servers check out the guides in the following links. How To Configure NTP Server on pfSense / OPNsense Configure Chrony NTP Server on RHEL 8 / CentOS 8 Install FreeIPA Server on Rocky Linux 9 / AlmaLinux 9 With the NTP server installed and configured you can then proceed to configure your vSphere ESXi environment. Step 2: Enable NTP daemon on ESXi Hosts On each ESXi host we’ll need to start and enable NTP service. This can be performed from vSphere Web Client or from vCenter web console. Option 1: Enable NTP daemon on ESXi using vSphere Web Client Login to your host’s vSphere Web Client and go to Host > Manage > Services. Select NTP daemon and click start. Update the policy as well to start the service with the host. Option 2: Enable NTP daemon on ESXi using vCenter Login to vCenter console and select the host where NTP daemon is to be started. Go to Configure > Services. From a list of services choose NTP Daemon and hit Start. Next click “EDIT STARTUP POLICY” to update how the service lifecycle is managed. Choose Start and stop with the host for automatic startup when the host is started. Step 3: Configure vSphere ESXi / vCenter to use NTP Let’s consider the two configuration scenario for setting NTP server in your VMware vSphere environment. Configure vCenter to use NTP synchronization Login to VMware vCenter server management console – https://vcenter.example.com:5480/. Authenticate using credentials set at the time of installation. From the main menu navigate to Time > Time zone > Edit to set the correct timezone. Set NTP host under Time synchronization settings. Configure ESXi host to use NTP Time You can use either of these methods. Method 1: Using vSphere Web client Select the host, then go to Manage > System > Time & date > Edit NTP Settings Choose the setting to enable NTP and input your NTP server IP. If you haven multiple servers separate the list using comma. When done save the settings by clicking Save. Method 2: Using vCenter web console Login to vCenter, then select ESXi host, Configure > Time Configuration > ADD SERVICE > NETWORK TIME PROTOCOL Provide IP address of NTP server. For multiple servers separate the list with comma. Click “TEST SERVICES” to test NTP service connection. Our ESXi host and vCenter should now be using NTP for time settings. It’s recommended to provide multiple NTP servers to ensure time is at sync at any point in time. Configuring multiple NTP servers provides redundancy in case one of the servers is not reachable.
0 notes
Text
How to install the FreeIPA identity and authorization solution on CentOS 8
How to install the FreeIPA identity and authorization solution on CentOS 8
[ad_1]
Jack Wallen walks you through the process of installing an identity and authorization platform on CentOS 8.

Image: CentOS
FreeIPA is an open source identity and authorization platform that provides centralized authorization for Linux, macOS, and Windows. This solution is based on the 389…
View On WordPress
0 notes
Text
HADM: Администрирование кластера Hadoop
Курс администрирование кластера Hadoop Ближайшая дата курса администрирования кластера Hadoop Cloudera Manager/HortonWorks/Arenadata 23-27 сентября 18-22 ноября Стоимость обучения 90.000 рублей

5 дней практического обучения установке и настройке кластера Hadoop, безопасность Kerberos, Apache Sentry, Cloudera Navigator, Apache Ambari, Apache Ranger, Apache Atlas, Apache KNOX, мониторинг, репликация и резервное копирование, взаимодействие с компонентами экосистемы Hadoop: Spark, Hive, sqoop, HDFS, MapReduce. Примечание: с 1 января 2019 года данный курс "Администрирование кластера Hadoop" проводится в объединенном формате по дистрибутивам Hadoop версии 2 компаний Cloudera/HortonWorks/ArenaData на выбор для пользователей. Для корпоративного формата обучения возможна выделенная программа по одной версии дистрибутива Hadoop (уточняйте у менеджера). Аудитория: Системные администраторы, системные архитекторы, разработчики Hadoop, желающие получить практические навыки по установке, конфигурированию, обслуживанию, управлению и администрирование кластера Hadoop с использованием дистрибутива Cloudera и Cloudera Manager/ HortonWorks/ Аренадата Hadoop. Предварительный уровень подготовки: Начальный опыт работы в Unix Опыт работы с текстовым редактором vi (желателен) Продолжительность: 5 дней, 40 академических часов. О курсе Apache Hadoop является наиболее по��улярной открытой платформой для распределенных вычислений. Данный курс содержит информацию по планированию и развертыванию распределенных вычислительных кластеров на базе дистрибутивов Hadoop, мониторингу и оптимизации производительности системы, резервному копированию и аварийному восстановлению узлов кластера и отдельных компонент, настройки безопасности системы Kerberos ( Active Directory и MIT/FreeIPA) на базе Hadoop. Курс администрирование кластера Hadoop построен на сквозных практических примерах развертывания и администрирования Hadoop кластера, в том числе в облачной инфраструктуре, использования компонент Hadoop для запуска задач распределенных вычислений с тестовыми данными. Практические занятия выполняются в кластерной среде Amazone Web Services с использованием дистрибутивов Cloudera Distributed Hadoop/ HortonWorks и Аренадата Hadoop(российский дистрибутив Hadoop в рамках программы импортозамещения) и программного обеспечения управления кластером Cloudera Manager/ Аренадата Hadoop / HortonWorks.
Соотношение теории к практике 40/60
Программа курса "Администрирование кластера Hadoop"
Введение в Big Data Что такое Big Data. Понимание проблемы Big Data Эволюция систем распределенных вычислений Hadoop ПринципыФормирование Data Lake и pipelines Архитектура Apache Hadoop Hadoop сервисы и основные компоненты. Name node. Data Node. YARN сервис - планировщик HDFS Отказоустойчивость и высокая доступность Hadoop Distributed File System Архитектура HDFS. Блоки HDFS. Основные команды работы с HDFS. Операции чтения и записи, назначения HDFS. Дисковые квоты. Поддержка компрессии Основные форматы хранения данных TXT, AVRO, ORC, Parquet, Sequence файлы Импорт (загрузка) данных на HDFS Организация Tiering для хранения данных Архивное хранение HDFS Локальное чтение и распределенное кэширование Map Reduce Ведение в MapReduce. Компоненты MapReduce. Работа программ MapReduce. YARN MapReduce v2/3 Ограничения и параметры MapReduce и YARN Управление запуском пользовательских задач (jobs) под MapReduce Дизайн кластера Hadoop Сравнение дистрибутивов и версий Hadoop 2/3 (Cloudera Distributed Hadoop, MapR, HortonWorks Data Platform, Arenadata Hadoop): различия и ограничения Требования программного и аппаратного обеспечения Планирование кластера Масштабирование кластера Hadoop. Отказоустойчивость Hadoop Federated NameNode. Hadoop в облаке. Сравнение Cloud решений для Hadoop. Amazon EMR Интеграция с другими решениями: streaming (DataFlow), NoSQL. Установка кластера Установка Hadoop кластера Выбор начальной конфигурации Оптимизация уровня ядра для узлов Начальная конфигурация HDFS и MapReduce Файлы логов и конфигураций Установка Hadoop клиентов Установка Hadoop кластера в облаке Автоматические варианты установки Установка и настройка кластера Hadoop в изолированном окружении (offline). Операции обслуживания кластера Hadoop Дисковая подсистема Квоты Остановка, запуск, перезапуск(Graceful Shutdown) Управление узлами Управление обновлениями и создание локального репозитория Оптимизация и управление ресурсами Поиск узких мест. Производительность. Файловая система. Data Node и data layout и партиционирование, bucketing Планировщики: FIFO scheduler. Планировщик емкости (Capacity scheduler). Гранулярное управление ресурсами (Fair scheduler). Защита очередей и доминантное управление ресурсами DRF. Особенности управления ресурсами для разных дистрибутивов Управление кластером Hadoop с использованием Cloudera Manager/Apache Ambari Установка Cloudera Manager/Apache Ambari Основные операции и задачи Cloudera Manager/Apache Ambari Мониторинг с Cloudera Manager/Apache Ambari/ Grafana Диагностика и разрешение проблем с Cloudera Manager/Apache Ambari Безопасность Apache Hadoop Безопасность по умолчанию Многопользовательский режим Аутентификация и авторизация с использованием Active Directory(Microsoft), REALM MIT/FreeIPA: Kerberos, keytabs, principals. Установка и конфигурирование Kerberos в Hadoop Обзор возможностей Apache Sentry, Cloudera Navigator, Apache Ambari, Apache Ranger, Apache Knox, Apache Atlas Резервное копирование и аварийное восстановление Репликация данных и snapshoting.Конфигурирование высокой доступности Name node (HA) Компоненты безопасности Hadoop Best practices Cloudera / HortonWorks/Cloudera/ArenaData Мониторинг Apache Hadoop Apache Zookeeper Встроенные средства мониторинга Cloudera Manager/Apache Ambari Логи сервисов и компонент Внешние системы мониторинга: Zabbix, JMX, Grafana Troubleshooting Data Node Name Node Восстановление Name Node Инструментарий Apache Hadoop экосистемы Графический интерфейс сервиса HUE Подключение Cloudera Data Science Workbench Назначение Apache Zookeeper Основы Apache Pig - установка и выполнение базовых операций Введение в Apache Hive, понятие Hive таблицы, установка Hive Использование Apache sqoop - установка и выполнение базовых операций Базовые операции Apache Flume - установка и выполнение базовых операций Обзор и назначение компонент: Cloudera Impala, Apache NiFi, Apache HBase, Apache Kafka, Apache Zookeeper, Apache Oozie Примерный список практических занятий: Ручная установка кластера Hadoop с дистрибутива Cloudera Distributed Hadoop/HortonWorks/Аренадата Hadoop на локальной системе 3-узловый кластер Установка 3-узлового кластера в облаке Amazon Web Services с использованием Cloudera Manager/Apache Ambari Базовые операции с кластером Hadoop и файловые операции HDFS. Управление ресурсами и запуском задач с использованием YARN MapReduce/Tez. Управление кластером с использованием Cloudera Manager/Apache Ambari(развертывание сервисов, репликация, мониторинг, alerting и т.д.) Конфигурирование системы аутентификации Kerberos для кластера Hadoop под управление Cloudera Manager/Apache Ambari Установка и выполнение базовых операций в Apache Hive, Apache sqoop, Apache Flume Выполнение ��адач в веб-интерфейсе HUE/Apache Ambari View Мониторинг кластера Hadoop с использованием Zabbix (опционально) HA высокая доступность( High Availablility) Name Node и YARN (ресурс менеджер) . Примечание: Доступ к лабораторному стенду на Amazon Web Services предоставляется на время учебных курсов с 8:30 до 18:30 (возможно продление времени по запросу) Практические занятия с меткой (опционально) выполняются по желанию и при наличии свободного времени у слушателей

Скачать программу курса программа курса по Администрированию кластера Hadoop в формате pdf { "@context": "http://schema.org", "@type": "Event", "name": "Курс «Администрирование кластера Hadoop»", "description": "5х дневный практический workshop по установке и настройке кластера Hadoop под управлением Cloudera Manager и Apache Ambari. Все что нужно знать администратору про фороматы данных Avro,Parquet, ORC, сжатие и партиционирование данных в HDFS, настройка Kerberos и высокая доступность кластерных компонент, резервное копирование и репликация, а также весь зооHadoop в придачу", "image": "https://www.bigdataschool.ru/wp-content/uploads/2018/07/Course_Hadoop_administrator.jpg", "startDate": "2019-05-20T09:30", "endDate": "2019-05-24T17:00", "performer": { "@type": "Person", "name": "Николай Комиссаренко" }, "location": { "@type": "Place", "name": "Учебный центр «Школа Больших Данных»", "address": { "@type": "PostalAddress", "streetAddress": "Малая Ордынка,44", "addressLocality": "Москва", "postalCode": "115184", "addressCountry": "RU" } }, "offers": { "@type": "Offer", "name": "обучение на курсе", "price": "90000", "priceCurrency": "RUB", "validFrom": "2019-04-14T09:00", "url": "https://www.bigdataschool.ru/bigdata/hadoop_cluster_administrator.html", "availability": "http://schema.org/InStock" } } { "@context": "http://schema.org", "@type": "Event", "name": "Курс «Администрирование кластера Hadoop»", "description": "5х дневный практический workshop по установке и настройке кластера Hadoop под управлением Cloudera Manager и Apache Ambari. Все что нужно знать администратору про фороматы данных Avro,Parquet, ORC, сжатие и партиционирование данных в HDFS, настройка Kerberos и высокая доступность кластерных компонент, резервное копирование и репликация, а также весь зооHadoop в придачу", "image": "https://www.bigdataschool.ru/wp-content/uploads/2018/07/Course_Hadoop_administrator.jpg", "startDate": "2019-09-23T09:30", "endDate": "2019-09-27T17:00", "performer": { "@type": "Person", "name": "Николай Комиссаренко" }, "location": { "@type": "Place", "name": "Учебный центр «Школа Больших Данных»", "address": { "@type": "PostalAddress", "streetAddress": "Малая Ордынка,44", "addressLocality": "Москва", "postalCode": "115184", "addressCountry": "RU" } }, "offers": { "@type": "Offer", "name": "обучение на курсе", "price": "90000", "priceCurrency": "RUB", "validFrom": "2019-05-01T09:00", "url": "https://www.bigdataschool.ru/bigdata/hadoop_cluster_administrator.html", "availability": "http://schema.org/InStock" } } https://www.bigdataschool.ru/bigdata/hadoop-intro.html Read the full article
0 notes