#executive function certification
Explore tagged Tumblr posts
Text
Once I get through The Tasks I'm gunna prioritise making a blanket fort
It's been a fairly constant instinct in the last few weeks to retreat into a small cosy nest at any and all moments
Dunno how I'm going to make it given I still own almost no furniture, but I do own a large number of bedsheets (bc I've finally shifted my tip-shop acquired fabric stash to the new place in the last week)
I'll make it work
#I will probably hold off on buying much in the way of furniture for a long while#The house is fine!#Except for (checks notes) the load bearing foundations#So if I do stick with it as a project I don't want to have to shift too much around as I live in a building site#Nor... Uh... Make the floor too heavy......#....#.....#Anyway.#I will buy new chairs though#My life#My posts#This house#I did a Task#(updated my annual practicing certificate)#But the payment bounced so I have to do it again#(waste of good executive functioning)
2 notes
·
View notes
Text
New Development in the Helicopter Crash 👇
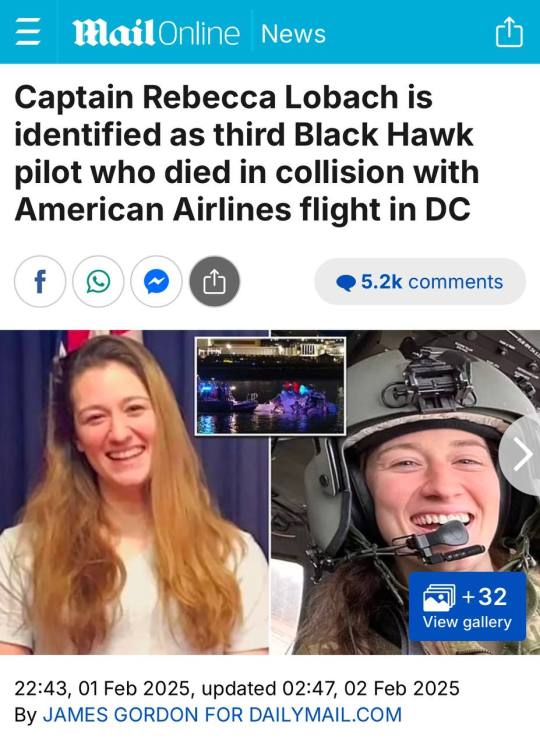
This gets more interesting 👇
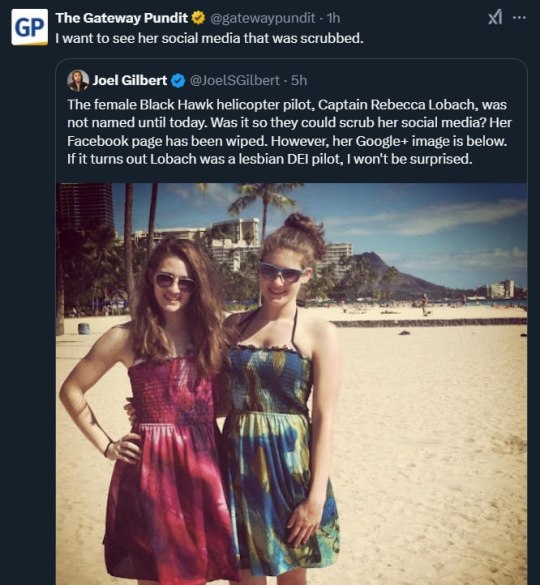
Her social media has been scrubbed 👇
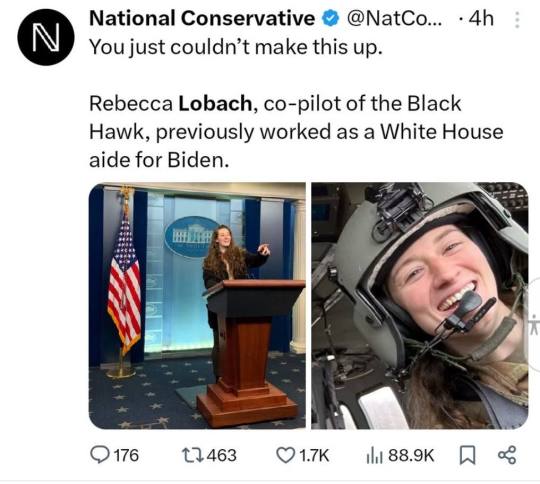
A White House aide for Biden 👇

Graduated with a Biology degree in 2019 from North Carolina Chapel Hill... Where the gain of function that created Covid started.
Let's löök at her parents 👇
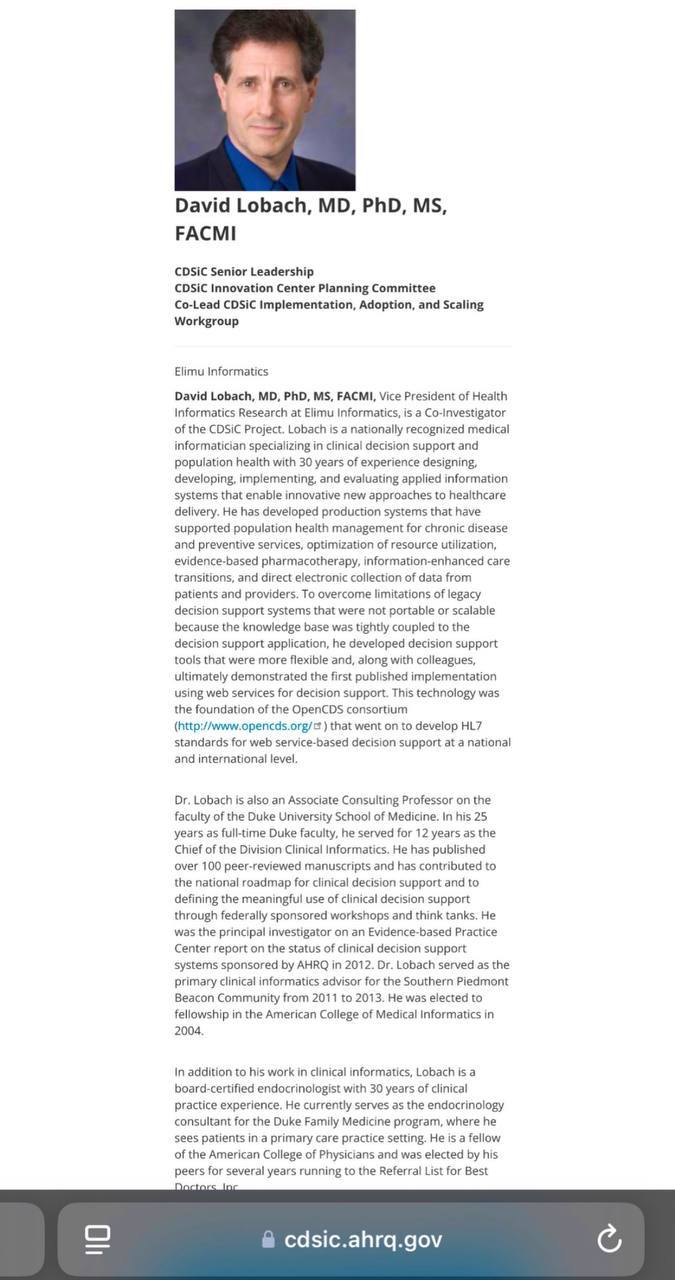
REBECCA LOBACH was the DAUGHTER of DAVID LOBACH (Duke University Medicine; Elimu Informatics; HHS) and ELIZABETH LOBACH (New Regency).
DAVID FRANKLIN LOBACH
*DUKE UNIVERSITY SCHOOL OF MEDICINE, Chief of Division Clinical Informatics, Associate Consulting Professor
*DUKE FAMILY MEDICINE PROGRAM, Endocrinology Consultant
*ELIMU INFORMATICS, VP of Health Informatics
*CDSiC PROJECT, Elimu Informatics (Co-Investigator)
💥NOTE 1: Duke University is run by Trustees Chairman and Mossad asset, Laurene Sperling, who is also the Chairman of Combined Jewish Philanthropies (CJP) and is married to Thermo Fisher (PCR TESTS) Lead Director, Scott Sperling. Thermo Fisher = Temasek (Singapore).
💥NOTE 2: Duke University School of Medicine is led by Dean, Nancy Andrews, who is the Chairman of Wellcome Burroughs (Wellcome/Farrar), who sits on the Board of Directors at Novartis and is a Senior Advisor to NIH Executive Leadership (Anthony Fauci).
💥NOTE 3: Duke Kunshan is a PARTNERSHIP between Duke University and Wuhan University and it officially opened its doors in 2013, which is the SAME YEAR that DAVID RUBENSTEIN (Duke Capital Partners, Carlyle Group, Booz Allen Hamilton, CFR, Brookings, etc.) became the CHAIRMAN of the DUKE UNIVERSITY BOARD OF TRUSTEES.
*Both David Rubenstein and Laurene Sperling are CURRENTLY on the ADVISORY BOARD of DUKE KUNSHAN UNIVERSITY in WUHAN, CHINA.
Duke University is arguably the MOST IMPLICATED SCHOOL IN AMERICA with regard to the COVID PANDEMIC CONSPIRACY and the CREATION & RELEASE of COVID… and COVERUP of COVID’S ORIGINS.
Her Mother 👇
ELIZABETH LEE LOBACH
NEW REGENCY PRODUCTIONS (Development), Writers’ Assistant, Office Assistant, Analyst & Script Editor
*TWENTIETH CENTURY FOX (Post-Production), Office Assistant, Research & Analysis.
💥NOTE: New Regency Productions was FOUNDED by ISRAELI SPY, ARNON MILCHAN, one of NETANYAHU’S CLOSEST OPERATIVES and ISRAEL’S MOST LEGENDARY SPIES. He was involved in helping ISRAEL STEAL AMERICAN NUCLEAR SECRETS several decades ago.
Moving on 👇
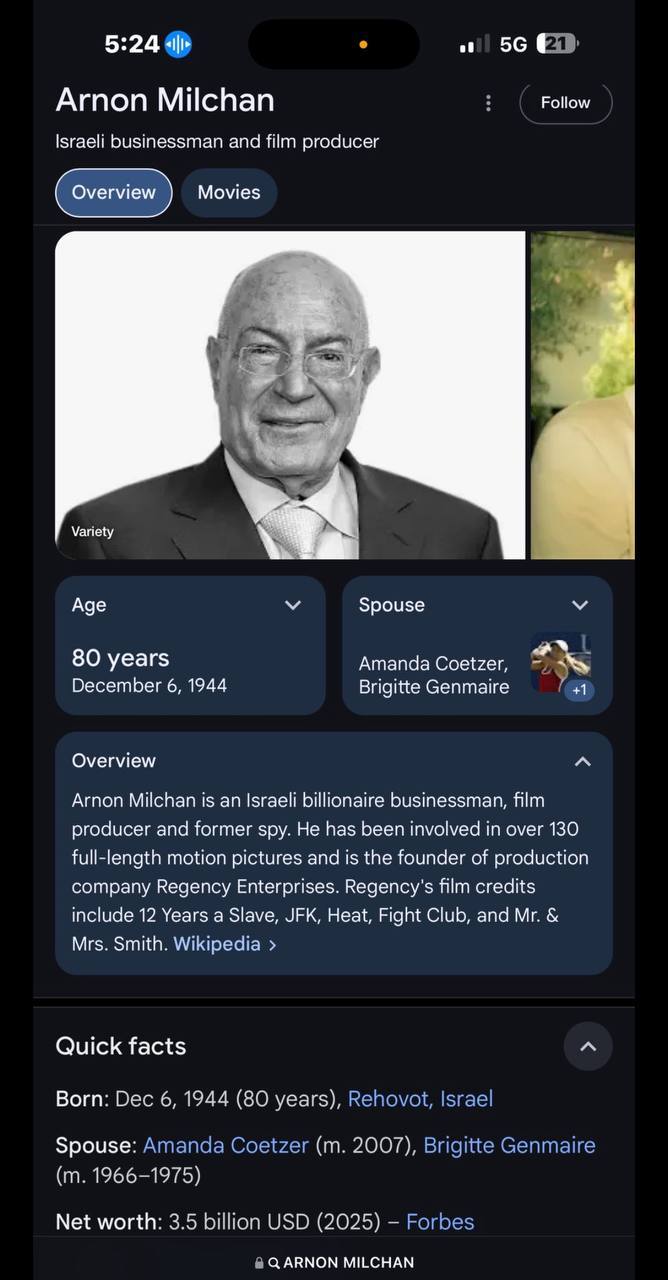
This is the man that founded the company where helicopter pilot, Rebecca Lobach’s mother works…
Nothing to see here 👇

Rebecca Lobach was still in ROTC training in 2018.
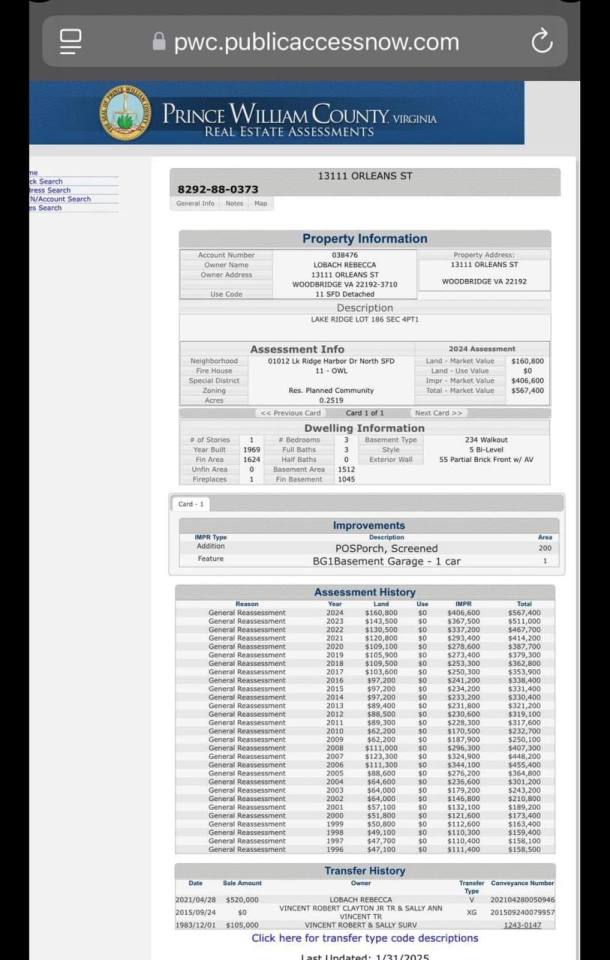
How is she flying government continuity missions in a Blackhawk in Washington DC 6 years later as a captain? And how did she afford a $520,000 house two years into the military? 👇
Rebecca Lobach, involved in DCA crash, served as a White House social aide under Biden.
She escorted Ralph Lauren through the White House when he was among those awarded the Presidential Medal of Freedom by former fake President Joe Biden. 👇
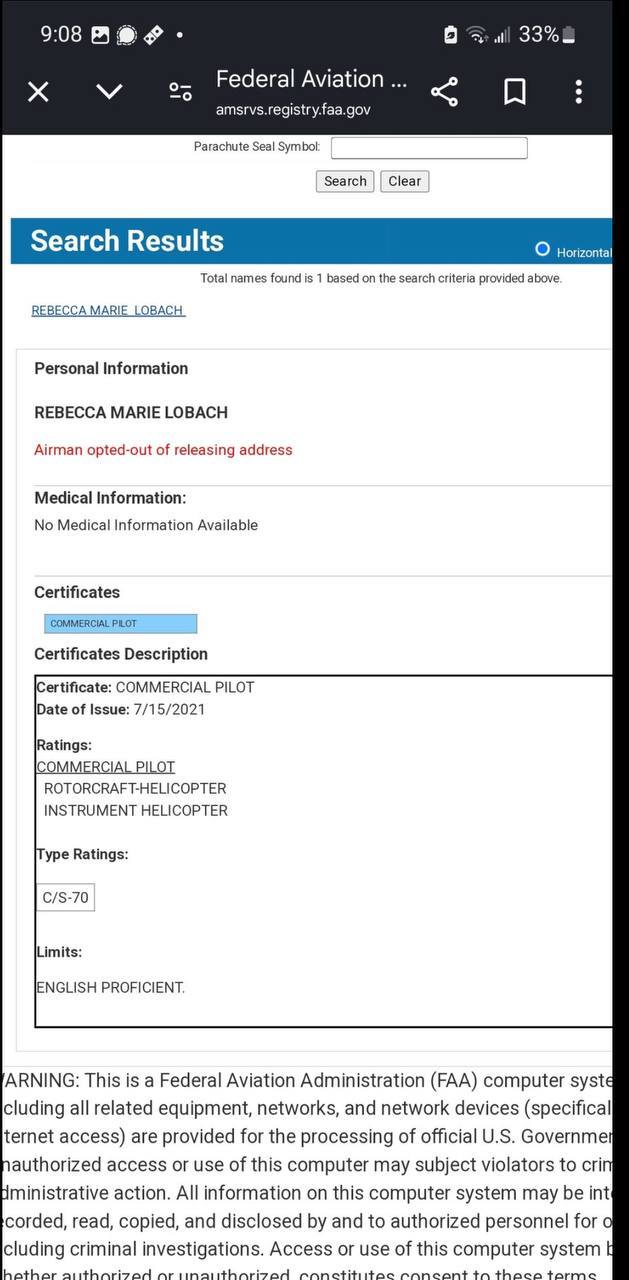
This is a screen grab from the FAA’s Airman registry which is available to the public it shows that Rebecca Marie Lobach did not currently hold an FAA medical which is required to have military certificates converted over to FAA certificates meaning she lost her medical…? 👇

Not sure what she ‘destroyed’.. but she doesn’t look fit to me! 👇
A statement from:
Art Halvorson @ArtHalv....
As a former military instructor, I'll tell you that Rebecca Lobach in NO WAY should have been the pilot in command on that flight.
500 hours in 5 years is Inconceivable! 👇
I think there’s more to this tragic incident than DEI hiring, but it was because of DEI policies that Rebecca was on board that helicopter and there are now 67 people dead. 🤔
#pay attention#educate yourselves#educate yourself#reeducate yourselves#knowledge is power#reeducate yourself#think about it#think for yourselves#think for yourself#do your homework#do your research#do your own research#do some research#ask yourself questions#question everything#helicopter crash#news#rabbit hole#you can't make this shit up#government corruption#government secrets#investigation
255 notes
·
View notes
Text
It's December 4, 2024.
Today, the Supreme Court heard oral arguments in United States v. Skrmetti, a challenge to Tennessee's ban on gender-affirming care. The specific question presented is whether Tennessee's ban violates the Equal Protection Clause.
The challenge is to Tenn. Code Ann. § 68-33-103(a)(1). That is, it's a challenge to a bit of Tennessee's Annotated Code. Title 68, Chapter 33, "Prohibited Medical Procedures for Minors."
I don't have anything to say about Tennessee's ban on gender-affirming care. Nor do I have anything to say about how the Court will treat the case. Not yet, anyways.
But I have something to say about the Code.
I.
Tennessee's laws are compiled by its code commission.
Under state law, the commission is a five-member body, consisting of the state's chief justice, attorney general, and counsel for the legislature, along with another two members appointed by the chief justice. Tenn. Code Ann. § 1-1-101(a).
The code commission supervises the official publication of the state's statutes, codes and session laws. § 1-1-105(a). The commission is empowered to commission to contract with publishers to that end, § 1-1-106(a), and obliged to inspect and certify their work. § 1-1-110(a).
When its work finished, the commission puts its certificate of approval in each volume and pocket supplement. § 1-1-110(c). But their first certificate, the one they leave with the secretary of state, § 1-1-110(b), is what gives the code the force of law. § 1-1-111(a).
Beyond that, the commission's work is ministerial. It cuts and pastes. "[T]he commission shall not alter the sense, meaning or effect of any act of the general assembly, but shall copy the exact language of the text of the statutes, codes and session laws." § 1-1-108.
The commission may "rearrange, regroup and renumber" the laws; change their "section headings"; "correct manifest misspelling[s] and typographical errors"; and "omit enacting clauses, repealing clauses, severability clauses, conditional clauses, preambles, [and] captions", § 1-1-108—and not much more.
II.
Tennessee leaves the work to Lexis, a private publisher.
Lexis's product, the Tennessee Code Annotated, is not eligible for copyright. Public.Resource.Org v. Matthew Bender & Co., No. M2022-01260-COA-R3-CV, slip op. (Tenn. Ct. App. Nov. 9, 2023). But it is not subject to compulsory disclosure, either.
Under current law, according to the state's intermediate appellate court, the Tennessee Code Annotated in the hands of Lexis is in the hands of a private contractor, not the State.
If Lexis had been the functional equivalent of a government entity, contracted to "perform a governmental or public function," it would be subject to the State's public records law. *8. But it's not.
That's what the state's intermediate appellate court says, at least. But its reasoning is less than persuasive.
III.
Lexis is merely a contractor. The commission specifies the work, and Lexis does the work. The commission may be exacting, but it isn't controlling. *9.
That's the court's argument, at least. But that strikes me as a less than complete account of the commission's duties under State law, which must inform any characterization of its contracts.
Under State law, the commission is "authorized and directed to" control each dimension of the compilation, Tenn. Code Ann. § 1-1-105(a), and must
supervise the execution of plans for the compilation, arrangement, classification, annotation, editing, indexing, printing, binding, publication, sale, distribution and the performance of all other acts necessary for the publication of an official compilation of the statutes, codes and session laws of the state of Tennessee
The commission's contractual powers, set out in the subsequent section, § 1-1-106, are an incident to its primary authority and duty to "formulate and supervise" the compilation. § 1-1-105(a).
The commission's primary authority and duty to prepare the compilation is plain on the face of the law. Under State law, the compilation is the commission's work, down to the copying and pasting, § 1-1-108(a):
In preparing the manuscript of the revised compilation (including pocket supplements and replacement volumes) for publication and distribution, the commission shall not alter the sense, meaning or effect of any act of the general assembly, but shall copy the exact language of the text . . .
This is more than the relationship suggested by the court. It's more than control over the product. It's control over production, the work of "preparing the manuscript."
To the extent that Lexis is doing the work, "preparing the manuscript," and "copy[ing] the exact language of the text," it is performing the commission's functions.
The court says "Lexis is not a stand-in for government." But that's exactly what it is. The commission is a government body. And Lexis is doing the commission's work.
That seems like a governmental function to me.
40 notes
·
View notes
Text
Glossary of Terms linked to (i love you) it's ruining my life - jake "hangman" seresin x f!oc
Ace (Flying Ace or Fighter Ace) = Military aviator credited with shooting down five or more enemy aircraft during aerial combat.
Avionics = Advanced processors and networking systems to fiber optics and conformal wideband antennas, etc.
Bandit = an aircraft identified and verified as enemy.
Bogey = radar or visual contact whose identity is unknown and not yet verified as an enemy. Bogey can also be a friendly once identified.
Break (right/left) = when an aircraft is instructed to sharply turn left/right, essentially "breaking" away from its current flight path to the left/right side
HUD = "Head-Up Display," for fighter pilots is a transparent screen in the cockpit that projects critical flight information directly into the pilot's line of sight, allowing them to view essential data like airspeed, altitude, heading, and weapon targeting details without needing to look away from the outside environment, maintaining situational awareness during flight operations.
Lt. = Lieutenant (rank)
Lt. Cmdr = Lieutenant Commander (rank)
LTJG = Lieutenant Junior Grade (rank)
Preflight checks = a thorough inspection that pilots perform on an aircraft before each flight, meticulously examining its exterior, systems, controls, and documentation to ensure it is in a safe condition to fly, identifying any potential issues that could compromise flight safety by checking for damage, fluid levels, proper functionality of components, and reviewing necessary paperwork.
Qual(ification) hop = refers to a flight performed by a pilot to demonstrate proficiency in a specific skill or maneuver required for certification or qualification. In the military aviation world, pilots must complete these hops to be officially qualified to perform certain missions, fly specific aircraft, or execute advanced tactics.
RADM = Rear Admiral (rank)
RIO = Radar Intercept Officer (now known as WSO)
SAM(s) = Surface to Air Missile(s)
Splash = typically refers to the moment of impact when a bomb or missile hits its target, essentially signifying the detonation or "splash" of the explosive upon contact.
Tally = communication used to tell a controller they are about to engage enemy aircraft. Also used to announce to the squadron leader (or other person of command in the flight) the spotting of an enemy aircraft.
Telemetry = the collection of data from a remote and usually fast-moving device for measurement purposes. It is used in aircraft/missile testing to track moving objects in action or collect data provided by instruments and sensors on the test object.
Tone = fighter pilot speak for a missile or weapons lock. When a pilot is tracking a target the computer will beeping as it acquires a lock-on, which changes to a continuous tone when lock is established.
VFA = Strike Fighter Squadron
Weapons envelope = the area around the bandit where your missiles or gun can be effective.
WSO = Weapons System Operator (formerly known as RIO)
NATOPS F-18 Manual
Am I missing any? Send me an ask!
#jake seresin#glen powell#jake hangman seresin#(i love you) it's ruining my life#top gun hangman#rooster top gun#top gun maverick#top gun#dagger squad#smut#jake seresin fanfiction#jake seresin smut#hangman smut#hangman x oc#top gun fanfiction#tom iceman kazansky#rick hollywood neven#jake hangman seresin x you#jake seresin x reader#bradley rooster bradshaw#jake seresin fic#jake hangman seresin x oc#jake seresin x oc#jake hangman fic#enemies to lovers#forced proximity#pete maverick mitchell#maverick
37 notes
·
View notes
Text
Hugo Lowell at The Guardian:
The US supreme court has ruled that former presidents are entitled to some degree of immunity from criminal prosecution, dramatically reducing the likelihood that the federal criminal case against Donald Trump on charges he plotted to stop the transfer of power will proceed before the 2024 election. The court’s conservative majority – which Trump helped create – found 6-3 that presidents were protected from prosecution for official actions that extended to the “outer perimeter” of his office, but could face charges for unofficial conduct.
Trump is accused of overseeing a sprawling effort to subvert the 2020 election, including two counts of conspiring to obstruct the certification of the election results, conspiring to defraud the government, and conspiring to disenfranchise voters. Among the accusations: Trump spread false claims of election fraud, plotted to recruit fake slates of electors, pressured US justice department officials to open sham investigations into election fraud, and pressured his vice-president, Mike Pence, to obstruct Congress’s certification of Joe Biden’s win. To determine whether Trump’s alleged attempts to overturn the 2020 election results came under the protected auspices of his official duties, the supreme court remanded the case back to the presiding US district judge Tanya Chutkan, who will have to review the indictment line by line.
The court left the bulk of the analysis up to Chutkan. But Chief Justice John Roberts, writing for the majority, found that Trump’s threat to fire the then-acting attorney general for refusing to open investigations were protected, because the justice department is part of the executive branch. Roberts similarly found that Trump’s effort to pressure Pence was probably protected, as the president discussing responsibilities with the vice president was an instance of official conduct. “Trump is at least presumptively immune from prosecution for such conduct,” the opinion said. The final decision on the Pence question rested with Chutkan, wrote Roberts. The burden was on prosecutors to “rebut the presumption of immunity” and whether charging Trump would “pose any dangers of intrusion on the authority and functions of the Executive Branch”.
And on the matter of Trump’s remarks on January 6, Roberts wrote that they too were probably protected, since presidential addresses were an integral function of the office. But the opinion also allowed that in Trump’s case, it may be more appropriate to categorize his speech as that of a candidate for office. The ruling in Trump’s election subversion case was one of the last handed down by the supreme court this term. In waiting until the end, the conservative majority played into Trump’s benefit and legal strategy of trying to delay any trial as much as possible. The effect of the ruling to block a prompt trial, after the court moved quickly to keep Trump on the ballot in March, has already ignited fierce criticism by liberals and others who believe Trump’s case should be resolved before voters cast their ballots in the forthcoming election.
Trump’s legal strategy for all of his federal criminal cases – he also faces charges in Florida for illegally retaining classified documents – has been to delay them until after the election, in the hope that he will be re-elected and can appoint as attorney general a loyalist who would drop the charges. As the calendar now stands, a trial in Trump’s election subversion case cannot start until 20 September at the earliest, since Trump’s lawyers have 88 days left on the clock to prepare a defense after the case was automatically frozen when they launched the immunity appeal.
Sad day in America, as tyranny will be rewarded if Donald Trump wins again: The radical right-wing 6-3 majority on SCOTUS rules in Trump v. United States in an opinion by Chief Justice John Roberts that Trump has total immunity for acts done in an official capacity but no immunity for private acts.
The case has been remanded back to the DC Circuit Court to determine whether Trump's efforts to overturn the 2020 elections count as "official duties."
#Trump v. United States#Total Immunity#Donald Trump#SCOTUS#John Roberts#Capitol Insurrection#Fake Electors#Electoral College Vote#DC Circuit Court#Tanya Chutkan
19 notes
·
View notes
Note
Is everything okay? You haven't been around in a bit and I'm worried! (Sorry if this is too parasocial of me! I don't want to intrude on your personal life. You don't have to respond to this!)
Hello anon,
Thank you for reaching out. I really appreciate it. I have been struggling to juggle everything on my plate, with varying degrees of success. Below the cut for an extended "why."
My father needed more care than I anticipated after coming back from Chile. I am caregiving twice a week, sometimes three. This includes taking him to appointments, doing his grocery shopping, setting up adaptive equipment, taking him out so he can walk around safe spaces, and keeping him company. I got respite from my older sister this past weekend, but it was just not long enough. I am so tired.
I have been battling flare ups and side effects. Still going for infusion therapy, PT, and other various appointments for myself. I have a nasty bruise on my left arm from infusion therapy, and a nasty bruise on my right arm from my liver MRI. Good news is that infusion therapy went well and the liver MRI came back stable. I am very grateful.
I had a health scare this week about my kidneys, but it seems like it's just costochondritis. It's painful, as it affects my ability to breathe or move, but I am used to my ribs flaring up. It's just... not ideal?
Finishing school was great! But then it launched me into attending a ton of webinars/seminars/networking events. I have been able to keep up with 90% of them, but it's been a real trip. I hate networking. I have had to push myself out of my comfort zone and that has been incredibly draining and anxiety-provoking.
I also received "feedback" on my LinkedIn profile from my mentor that I need to "tone it down" in regard to what I post/repost and comment on. All I post/repost/comment on about are queer/poc-related things. I spent an entire day crying about this "tone it down." I have been told before by society, by partners, by family members, by friends... to "tone it down," or, "stop being so obvious," or "don't go around flaunting it." Does anyone know how *difficult* it is existing in the world as my authentic self? If someone on LinkedIn doesn't like it, then they can kindly fuck off. I wouldn't want to work with them anyway.
It's been tough, anon.
Hockey is over, Delly got traded, and the Panthers blew their lead.
My HR certification exam is in 16 days. I do not feel like I've been able to adequately study/prepare. The amount of material to study is overwhelming. I have apps and flashcards, plus books, but I feel like I have neglected all of them this past week.
So. I have a lot on my plate right now. I can't even get my library books turned in on time because it feels like I never have enough time to do that. Not that I have time to read anyway.
Then there's the usual stuff like depression, shitty executive function, anxiety, and mood swings. Also, medications and side effects.
TLDR: I'm struggling and I am doing my best. You'll see more of me after July 6th (exam date).
I'm also just... really, really tired.
14 notes
·
View notes
Text
So much for not talking politics. In fairness, this Tik Tok Ban story found me more than the other way around (through the family group chat), and it's legitimately interesting in several ways.
Most Americans probably know already, but if you missed it,
a) Tik Tok is owned by a Chinese company, and there's really no protections for how they share your data with the Chinese government.
b) So the US Congress passed a law that ByteDance (Tik Tok's owners) have to sell to a US-owned company because national security, or else, by 1/19.
c) "Or else" meaning TikTok couldn't be listed in US app stores. The app itself could still function if you already had it downloaded.
d) Mr. Trump was originally for the ban but suddenly became against it, even going to the SCOTUS to get an extension so he could arrange a sale once president. They refused. Because, you know, it was an agreed-upon and properly executed law with no constitutional implications.
e) Tik Tok shut down US access to the app last night, which (again) they're not required to do, displaying this message:
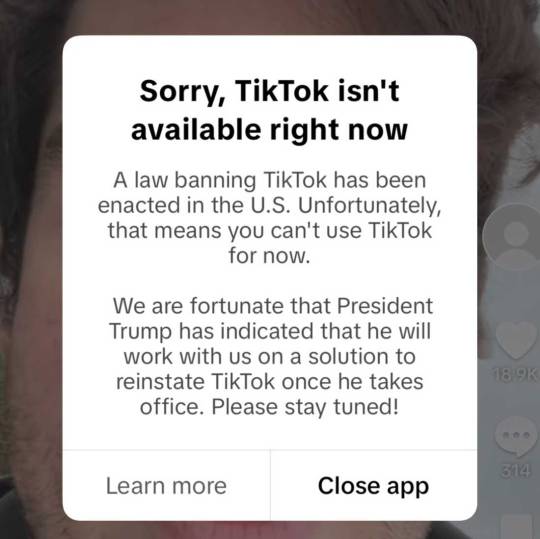
.... then re-allowed access hours later thanking "President Trump for providing the necessary clarity and assurance to our service providers that they will face no penalties providing TikTok." "Assurance" doesn't change the reality of the situation. He's not president yet, he can't issue an executive order yet so if access had ever been illegal it would still be illegal today, and an executive order wouldn't fix it anyway.
(In fairness, the president could provide a one-time ninety-day extension, but it's a certification operating within the context of the law as passed. There'd have to be evidence a sale to a US company was in the works. Which there's not because ByteDance doesn't want to sell. Trump couldn't just say "Tik Tok's legal again so suck it Congress," even after the inauguration.)
f) Elon Musk is also negotiating with China to allow Chinese citizens to access X. Surely that's completely unconnected. I'm not even sure why I'm mentioning it.
g) It's still not available for download on my phone.
h) A lot of the current users were already migrating to another, also Chinese-owned app.
There's something really funny about all this to me, about the multiple levels of sheer stupidity in this whole situation. Probably the most important take-aways long term is this feels very much like autocracy (the way Trump's so involved) and oligarchy (how Elon's own business interests with China seem so inescapably relevant). Also that Mr. Trump is an unbelievably soft touch. Xi, nevermind Putin, will eat him for lunch.
Also-also, if you care about your privacy and data security, stay off the 'Tok if you can. I'm not sure if this is a well-structured law, but the concern driving it seems real enough to me.
Also-also-also? My fellow citizens are dumb.
4 notes
·
View notes
Text
by Nicolas Hulscher, MPH
Since President Trump’s election victory last week, the public is eagerly waiting for some positive action. During his campaign, Trump announced a plan to dismantle the unscientific and harmful gender-affirming care policies introduced under the Biden Administration.
Here’s an outline of the Trump Administration’s plan:
Revoke Gender-Affirming Care Policies: Immediately repeal current policies allowing gender-affirming care for minors, including puberty blockers, surgeries, and other treatments.
Ban Federal Support for Gender Transition: Sign an executive order to stop all federal programs promoting gender transition at any age, and seek legislation to prohibit taxpayer funding for these procedures.
Restrict Medicare and Medicaid Compliance: Deny Medicare and Medicaid certification to any healthcare provider involved in gender-transition procedures for minors.
Allow Legal Action for Victims: Support legislation allowing individuals who underwent gender-transition procedures as minors to sue the doctors involved.
Investigate Pharmaceutical and Healthcare Providers: Direct the Department of Justice to examine Big Pharma and healthcare networks for potential concealment of harmful side effects from gender-transition procedures and misuse of puberty blockers and hormones.
Implement School Accountability: Inform schools that promoting gender-transition concepts to children could lead to loss of federal funding and potential civil rights violations.
Promote Traditional Gender Education: Introduce teacher credentialing standards emphasizing the nuclear family, traditional roles of men and women, and celebration of gender differences.
Legislate Binary Gender Recognition: Propose a law recognizing only male and female genders, assigned at birth, and reinforce that Title IX bars men from competing in women’s sports.
Protect Parental Rights: Ensure that parents have the right to prevent gender-transition procedures or changes in gender identity for their minor children without parental consent.
End "Radical Gender Ideology": Oppose the idea of gender fluidity, which Trump attributes to recent radical-left influence, aiming to eliminate its promotion in federal policies.
This plan is supported by science. Puberty blockers can lead to detrimental outcomes. A systematic review by Baxendale looking at the impact of suppressing puberty on neuropsychological function found that:
1. Cognitive effects may not be reversible following discontinuation of treatment.
2. No human studies have systematically explored the impact of these treatments on neuropsychological function with an adequate baseline and follow-up.
3. There is some evidence of a detrimental impact of pubertal suppression on IQ in children.
4 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
Structural Engineering Consultants: Building a Strong Foundation for Success

Structural engineering consultants are vital to the planning, design, and execution of construction projects. These experts ensure that structures are not only visually appealing but also safe, sustainable, and compliant with industry standards. From residential buildings to skyscrapers and bridges, their role is indispensable in shaping the built environment.
In this article, we’ll explore who structural engineering consultants are, the services they provide, and the benefits of hiring them for your construction projects.
What Are Structural Engineering Consultants?
1. Definition
The Structural engineering consultants are professionals or firms specializing in the design, analysis, and safety of load-bearing structures. They work closely with architects, contractors, and project managers to ensure that buildings and other structures can withstand various forces such as gravity, wind, earthquakes, and more.
2. Their Expertise
These consultants possess in-depth knowledge of materials, building codes, and structural systems. They are trained to identify potential issues in the design phase and provide solutions that enhance durability and functionality.
3. Industries They Serve
Structural engineering consultants are involved in diverse projects, including:
Residential and commercial buildings
Industrial facilities
Infrastructure projects like bridges and tunnels
Retrofitting and renovation of existing structures
Key Services Offered by Structural Engineering Consultants
1. Structural Analysis and Design
Load Calculations: Assessing the forces acting on a structure to determine stability.
Material Selection: Choosing appropriate materials such as steel, concrete, or timber based on the project’s needs.
Structural Layouts: Designing frameworks and support systems for buildings.
2. Feasibility Studies
Evaluating the viability of a project before construction begins.
Providing insights into potential challenges and cost-effective solutions.
3. Seismic and Wind Analysis
Ensuring structures can withstand natural forces like earthquakes and hurricanes.
Implementing safety measures to protect lives and assets.
4. Retrofitting and Rehabilitation
Strengthening older structures to meet current safety standards.
Prolonging the lifespan of buildings through modern engineering techniques.
5. Construction Supervision
Monitoring construction sites to ensure compliance with designs and safety standards.
Addressing unforeseen challenges during the construction phase.
6. Inspection and Certification
Conducting thorough inspections to certify a structure’s safety and integrity.
Issuing reports and certifications required by regulatory authorities.
Benefits of Hiring Structural Engineering Consultants
1. Enhanced Safety
The primary role of a structural engineering consultant is to ensure that buildings and infrastructure are safe for use. Their expertise minimizes risks associated with structural failures.
2. Cost Efficiency
By optimizing designs and selecting the right materials, consultants can significantly reduce construction costs without compromising quality.
3. Compliance with Regulations
Structural engineering consultants are well-versed in local and international building codes. They ensure that your project meets all legal requirements, avoiding potential fines or delays.
4. Innovative Solutions
With access to the latest technologies and techniques, consultants provide innovative solutions to complex structural challenges.
5. Time Savings
Their involvement streamlines the design and construction process, helping projects stay on schedule.
How to Choose the Right Structural Engineering Consultant
1. Evaluate Experience
Look for consultants with a proven track record in projects similar to yours. Their experience is often an indicator of their expertise.
2. Check Qualifications and Licenses
Ensure the consultant or firm is licensed and certified by relevant professional bodies.
3. Review Their Portfolio
Examine their previous projects to gauge their design style, innovation, and problem-solving capabilities.
4. Assess Communication Skills
A good consultant should communicate effectively with all stakeholders, ensuring that everyone is on the same page.
5. Compare Pricing
Request quotes from multiple consultants and compare their services and costs. Avoid choosing solely based on price; consider the value they bring to your project.
6. Seek Recommendations
Ask for referrals from trusted sources or read online reviews to find reputable consultants in your area.
Challenges Faced by Structural Engineering Consultants
1. Complex Project Requirements
Balancing aesthetic goals with structural integrity can be challenging, especially in innovative architectural designs.
2. Budget Constraints
Finding cost-effective solutions while maintaining quality and safety standards requires creativity and expertise.
3. Adapting to Technological Advances
Staying updated with new tools like Building Information Modeling (BIM) and advanced simulation software is essential to remain competitive.
4. Environmental Considerations
Designing sustainable and eco-friendly structures that meet modern environmental standards is a growing demand.
The Future of Structural Engineering Consultancy
1. Sustainability Focus
As environmental concerns grow, structural engineering consultants are increasingly prioritizing green building practices, such as energy-efficient designs and the use of sustainable materials.
2. Integration of Technology
AI and Machine Learning: Streamlining design processes and identifying potential issues early.
3D Printing: Revolutionizing construction by enabling the creation of intricate designs with precision.
Drones: Used for site inspections and monitoring construction progress.
3. Urban Development
With cities becoming more densely populated, consultants are focusing on designing structures that maximize space while ensuring safety and efficiency.
Case Studies: Successful Projects by Structural Engineering Consultants
1. Skyscraper Stability in High-Wind Areas
Consultants developed innovative damping systems to counteract wind forces, ensuring the building’s stability without sacrificing its sleek design.
2. Bridge Reinforcement
A historical bridge was retrofitted to support modern traffic loads while preserving its original architecture.
3. Earthquake-Resistant Housing
In a seismic-prone region, consultants implemented base isolation techniques to reduce vibrations and enhance building safety.
Tips for Collaborating with Structural Engineering Consultants
1. Clearly Define Project Goals
Provide detailed briefs to help consultants understand your expectations and project scope.
2. Encourage Open Communication
Maintain regular meetings and updates to address challenges and ensure progress aligns with your vision.
3. Provide Accurate Data
Share all necessary site information, including soil tests and architectural plans, to enable accurate analysis and design.
4. Be Open to Suggestions
Leverage the consultant’s expertise by considering their recommendations for improved design and efficiency.
Conclusion
Structural engineering consultants are indispensable in the construction and development industry. Their expertise ensures that structures are not only visually impressive but also safe, sustainable, and cost-effective. From concept to completion, these professionals play a critical role in turning ambitious projects into reality.
By choosing the right consultant, you can streamline your project, minimize risks, and achieve your vision with confidence. Whether you’re planning a residential building, a commercial complex, or an infrastructure project, structural engineering consultants are your trusted partners in building a better, safer future.
3 notes
·
View notes
Text
Interior Designers in Panchkula: A Comprehensive Guide
Interior design is more than just aesthetics; it's about creating a functional, comfortable, and visually appealing space that reflects your personality and meets your needs.
In Panchkula, a city known for its urban planning and proximity to Chandigarh, the demand for professional interior designers has surged as homeowners and businesses aim to create standout spaces.
Whether you're planning to revamp your home or office, this comprehensive guide will introduce you to the best practices, benefits, and top interior designers in Panchkula.

Why Hire an Interior Designer in Panchkula?
Hiring an interior designer isn't just about making a space look good. Here are some compelling reasons why you should consider their expertise:
Professional Expertise: Interior designers bring a wealth of knowledge in design principles, space planning, and material selection.
Cost Efficiency: By avoiding costly mistakes and accessing exclusive resources, you save money in the long run.
Time-Saving: Designers handle everything from conceptualization to execution, freeing up your time.
Personalized Designs: They tailor solutions to match your preferences and lifestyle.
Access to Vendors and Materials: Professional designers often have relationships with suppliers, giving you access to high-quality materials and furniture.
Popular Interior Design Styles in Panchkula
Contemporary Design Minimalist yet functional, this style is a favorite for modern homes and offices in Panchkula. It emphasizes clean lines, neutral colors, and smart use of space.
Traditional Indian Aesthetics With Panchkula's proximity to Punjab, many prefer vibrant interiors with rich fabrics, carved wooden furniture, and ethnic motifs.
Eco-Friendly Design Sustainable and green designs are trending, incorporating natural materials like bamboo, reclaimed wood, and energy-efficient lighting.
Luxury Interiors High-end homeowners in Panchkula often opt for luxury designs featuring premium materials, opulent decor, and bespoke furniture.
Top Interior Designers in Panchkula
1. Design Studio Panchkula
Specialization: Residential and commercial projects.
Key Features: Innovative designs, smart use of space, and eco-friendly solutions.
Contact: Available on popular online directories.
2. Elegant Interiors
Specialization: Modern and contemporary designs.
Key Features: Attention to detail and cost-effective solutions.
Contact: Visit their website or call directly.
3. Urban Luxe Designers
Specialization: High-end homes and luxury offices.
Key Features: Bespoke furniture and premium materials.
Contact: Check out their portfolio on social media platforms.
4. Vastu Interiors Panchkula
Specialization: Vastu-compliant designs.
Key Features: Combining traditional principles with modern aesthetics.
Contact: Reach out via their official email.
Key Considerations Before Hiring an Interior Designer
Define Your Budget: Be clear about your budget constraints to avoid overspending.
Check Credentials: Review their portfolio, certifications, and client testimonials.
Understand Your Needs: Have a clear vision of what you want to achieve with your space.
Discuss Timelines: Ensure the designer can complete the project within your desired timeframe.
Compatibility: Choose a designer whose style aligns with your taste.
Tips for a Successful Interior Design Project
Communicate Clearly: Share your preferences and expectations with the designer.
Be Open to Ideas: Trust the designer’s expertise and consider their suggestions.
Focus on Functionality: A beautiful space should also be practical and comfortable.
Invest in Quality: Prioritize long-lasting materials and timeless designs.
Incorporate Personal Touches: Add decor and elements that reflect your personality.
Cost of Interior Design Services in Panchkula
Interior design costs in Panchkula can vary based on factors like project size, design complexity, and materials. On average:
Consultation Fees: ₹1,000 - ₹3,000 per hour.
Design Fees: 8% - 15% of the total project cost.
Turnkey Solutions: ₹1,500 - ₹3,500 per square foot.
It’s essential to get detailed quotes from multiple designers before making a decision.
Conclusion:
Interior design in Panchkula is thriving, with numerous talented professionals offering creative and practical solutions. Whether you’re transforming your home, designing a functional office, or creating a luxurious space, the right interior designer can turn your vision into reality.
Use this guide as your starting point to find the perfect expert for your needs and enjoy the transformation of your space into something truly extraordinary.
6 notes
·
View notes
Text
Massive Backdoor Infection Hits 1.3 Million Android-Based Streaming Devices

A newly discovered malware infection has raised alarm bells by affecting an estimated 1.3 million Android streaming devices running an open-source version across almost 200 countries. The malware, dubbed "Android.Vo1d," has successfully backdoored these Android-based boxes by inserting malicious code into their system storage areas, allowing for potential updates with additional malware via command-and-control servers at any time.
Scope and Impact
Security firm Doctor Web reported the widespread infection on Thursday, highlighting the extensive reach of the Android.Vo1d malware. The affected devices are operating systems based on the Android Open Source Project (AOSP), a version overseen by Google but distinct from the proprietary Android TV used by licensed device manufacturers. Google representatives have confirmed that the infected devices are not running the official Android TV OS, emphasizing that these are "off-brand devices" without Play Protect certification. This certification process involves extensive testing to ensure quality and user safety. Confirm your TV is running Android TV OS by using the guide posted here.
Unknown Infection Vector
Despite their thorough understanding of the malware and its widespread impact, researchers at Doctor Web are still uncertain about the exact attack vector leading to these infections. They have proposed several possibilities: - An intermediate malware exploiting operating system vulnerabilities to gain root privileges - The use of unofficial firmware versions with built-in root access - Outdated and vulnerable Android versions susceptible to remote code execution exploits - Potential supply chain compromises, where devices may have been infected before reaching end-users
Affected Devices and Variants
The infection has been found on several TV box models, including: TV box model Declared firmware version R4 Android 7.1.2; R4 Build/NHG47K TV BOX Android 12.1; TV BOX Build/NHG47K KJ-SMART4KVIP Android 10.1; KJ-SMART4KVIP Build/NHG47K Researchers have identified dozens of Android.Vo1d variants, each using different code and planting malware in slightly different storage areas. However, all variants achieve the same result: connecting to attacker-controlled servers and installing components that can deploy additional malware on command.
Infection Characteristics
The Android.Vo1d trojan modifies several system files and creates new ones to ensure persistence on infected devices. Key changes include: - Modification of the install-recovery.sh script - Alteration of the daemonsu file - Creation of new files: vo1d, wd, debuggerd, and debuggerd_real These modifications allow the malware to anchor itself in the system and auto-launch during device reboots. The trojan's main functionality is split between two components: vo1d (Android.Vo1d.1) and wd (Android.Vo1d.3), which work together to maintain the infection and execute commands from the control servers.
Geographic Distribution

Geographic Distribution of the Android.Vo1d infections The infection has spread globally, with the highest number of cases detected in: - Brazil - Morocco - Pakistan - Saudi Arabia - Russia - Argentina - Ecuador - Tunisia - Malaysia - Algeria - Indonesia
Detection and Mitigation
Identifying infected devices can be challenging for less experienced users. Doctor Web recommends using their antivirus software for Android, which can detect all Vo1d variants and disinfect devices with root access. More technically inclined users can check for indicators of compromise provided by the security firm. The incident also highlights the risks associated with using non-certified Android devices and emphasizes the importance of regular security updates and proper device vetting. As the investigation continues, it serves as a stark reminder of the ongoing challenges in securing the diverse ecosystem of Android-based devices in the market. Read the full article
2 notes
·
View notes
Text
"DCA"(DIPLOMA IN COMPUTER APPLICATION)
The best career beginning course....

Golden institute is ISO 9001-2015 certified institute. Here you can get all types of computer courses such as DCA, CFA , Python, Digital marketing, and Tally prime . Diploma in Computer Applications (DCA) is a 1 year "Diploma Course" in the field of Computer Applications which provides specialization in various fields such as Fundamentals & Office Productivity tools, Graphic Design & Multimedia, Programming and Functional application Software.

A few of the popular DCA study subjects are listed below
Basic internet concepts Computer Fundamentals Introduction to programming Programming in C RDBMS & Data Management Multimedia Corel draw Tally ERP 9.0 Photoshop
Benefits of Diploma in Computer Application (DCA)
After completion of the DCA course student will able to join any computer jobs with private and government sectors. The certification of this course is fully valid for any government and private deportment worldwide. DCA is the only best option for the student to learn computer skills with affordable fees.
DCA Computer course : Eligibilities are here... Students aspiring to pursue Diploma in Computer Applications (DCA) course must have completed their higher school/ 10 + 2 from a recognized board. Choosing Computers as their main or optional subject after class 10 will give students an additional edge over others. Apart from this no other eligibility criteria is set for aspirants. No minimum cutoff is required.

"TALLY"
A Tally is accounting software. To pursue Tally Course (Certificate and Diploma) you must have certain educational qualifications to thrive and prosper. The eligibility criteria for the tally course is given below along with all significant details on how to approach learning Tally, and how you can successfully complete the course. Generally, the duration of a Tally course is 6 month to 1 year ,but it varies depending on the tally institution you want to join. Likewise, tally course fees are Rs. 10000-20000 on average but it also varies depending on what type of tally course or college you opt for. accounting – Accounting plays a pivotal role in Tally
Key Benefits of the Course:
Effective lessons (topics are explained through a step-by-step process in a very simple language) The course offers videos and e-books (we have two options Video tutorials in Hindi2. e-book course material in English) It offers a planned curriculum (the entire tally online course is designed to meet the requirements of the industry.) After the completion of the course, they offer certificates to the learners.
Tally Course Syllabus – Subjects To Learn Accounting Payroll Taxation Billing Banking Inventory
Tally Course
Eligibility criteria: 10+2 in commerce stream Educational level: Certificate or Diploma Course fee: INR 2200-5000 Skills required: Accounting, Finance, Taxation, Interpersonal Skills Scope after the course: Accountant, Finance Manager, Chartered Accountant, Executive Assistant, Operations Manager Average salary: INR 5,00,000 – 10,00,000

"In this Python course"
Rapidly develop feature-rich applications using Python's built-in statements, functions, and collection types. Structure code with classes, modules, and packages that leverage object-oriented features. Create multiple data accessors to manage various data storage formats. Access additional features with library modules and packages.
Python for Web Development – Flask Flask is a popular Python API that allows experts to build web applications. Python 2.6 and higher variants must install Flask, and you can import Flask on any Python IDE from the Flask package. This section of the course will help you install Flask and learn how to use the Python Flask Framework.
Subjects covered in Python for Web development using Flask:
Introduction to Python Web Framework Flask Installing Flask Working on GET, POST, PUT, METHODS using the Python Flask Framework Working on Templates, render template function
Python course fees and duration
A Python course costs around ₹2200-5000.This course fees can vary depending on multiple factors. For example, a self-paced online course will cost you less than a live interactive online classroom session, and offline training sessions are usually expensive ones. This is mainly because of the trainers’ costs, lab assistance, and other facilities.
Some other factors that affect the cost of a Python course are its duration, course syllabus, number of practical sessions, institute reputation and location, trainers’ expertise, etc. What is the duration of a Python course? The duration of a basic Python course is generally between 3 month to 6 months, and advanced courses can be 1 year . However, some courses extend up to 1 year and more when they combine multiple other courses or include internship programs.
Advantages of Python Python is easy to learn and put into practice. … Functions are defined. … Python allows for quick coding. … Python is versatile. … Python understands compound data types. … Libraries in data science have Python interfaces. … Python is widely supported.

"GRAPHIC DESIGN"
Graphic design, in simple words, is a means that professional individuals use to communicate their ideas and messages. They make this communication possible through the means of visual media.
A graphic designing course helps aspiring individuals to become professional designers and create visual content for top institutions around the world. These courses are specialized to accommodate the needs and requirements of different people. The course is so popular that one does not even need to do a lot of research to choose their preferred colleges, institutes, or academies for their degrees, as they are almost mainstream now.
A graphic design course have objectives:
To train aspirants to become more creative with their visual approach. To train aspirants to be more efficient with the technical aspects of graphics-related tasks and also to acquaint them with relevant aspects of a computer. To train individuals about the various aspects of 2-D and 3-D graphics. To prepare aspirants to become fit for a professional graphic designing profession.
Which course is best for graphic design? Best graphic design courses after 12th - Graphic … Certificate Courses in Graphic Design: Adobe Photoshop. CorelDraw. InDesign. Illustrator. Sketchbook. Figma, etc.
It is possible to become an amateur Graphic Designer who is well on the road to becoming a professional Graphic Designer in about three months. In short, three months is what it will take to receive the professional training required to start building a set of competitive professional job materials.

THE BEST COMPUTER INSTITUTE GOLDEN EDUCATION,ROPNAGAR "PUNJAB"
The best mega DISCOUNT here for your best course in golden education institute in this year.
HURRY UP! GUYS TO JOIN US...
Don't miss the chance
You should go to our institute website
WWW.GOLDEN EDUCATION
CONTACT US: 98151-63600
VISIT IT:
#GOLDEN EDUCATION#INSTITUTE#COURSE#career#best courses#tallyprime#DCA#GRAPHICAL#python#ALL COURSE#ROOPAR
2 notes
·
View notes
Text
A Blueprint for Success: Building a Robust High-Risk Payment Processing Strategy
Article by Jonathan Bomser | CEO | Accept-credit-cards-now.com

In the swiftly changing world of e-commerce and digital transactions, businesses often face challenges in the realm of payment processing, especially within high-risk industries. Navigating the acceptance of credit card payments and overseeing merchant accounts demands careful planning and a meticulously designed strategy. In this piece, we'll delve into the blueprint for success when formulating a robust high-risk payment processing strategy. From CBD merchants to credit repair services, we'll scrutinize the pivotal elements indispensable for triumph.
DOWNLOAD THE A BLUEPRINT FOR SUCCESS INFOGRAPHIC HERE
Comprehending High-Risk Payment Processing
Before immersing ourselves in the blueprint, it's imperative to grasp the essence of high-risk payment processing. This domain encompasses businesses with an elevated likelihood of encountering chargebacks, fraud, or regulatory intricacies. Industries such as CBD sales and credit repair services fall under this category. High-risk payment processing must adeptly navigate these challenges while ensuring the security of transactions and adherence to regulatory frameworks.
The Bedrock: Merchant Accounts and Processing
The genesis of a triumphant high-risk payment processing strategy lies in securing a dependable merchant account. This serves as the keystone of your payment processing apparatus, facilitating the acceptance of credit card payments and ensuring the secure transfer of funds. Opt for a provider well-versed in high-risk merchant processing to mitigate potential risks.
The High-Risk Payment Gateway
Functioning as the conduit between your website or e-commerce platform and the payment processor, your payment gateway is of paramount importance. In high-risk industries, the selection of a payment gateway fortified with robust fraud prevention measures is critical. Furthermore, it should seamlessly integrate with various e-commerce platforms, streamlining integration into your business operations.
Tailored Solutions for High-Risk Industries
Distinct high-risk industries harbor unique requirements. For instance, CBD merchants must seek out CBD payment processing solutions crafted for their niche. Similarly, credit repair services necessitate specialized credit repair payment processing attuned to the nuances of their operations. Align with payment processing providers possessing expertise in your industry to ensure compliance and efficiency.
Building Customer Trust and Ensuring Compliance
High-risk businesses often grapple with customer skepticism. Establishing trust is paramount. Displaying industry certifications, secure payment badges, and transparent refund policies can instill confidence. Additionally, a robust credit and debit card payment processor can guarantee secure transactions, further fortifying trust.
youtube
Conclusion and Future-Proofing
Constructing a resilient high-risk payment processing strategy is indispensable for the prosperity of businesses in demanding industries. Whether you operate in CBD sales, credit repair, or any other high-risk sector, an astutely executed strategy, dependable merchant accounts, and secure payment processing systems are indispensable. By prioritizing compliance, security, and customer trust, you can adeptly navigate the intricacies of high-risk payment processing. Remember, maintaining adaptability and future-proofing your payment processing strategy are pivotal in this ever-evolving landscape.
#high risk merchant account#credit card processing#payment processing#high risk payment gateway#high risk payment processing#accept credit cards#credit card payment#merchant processing#payment#youtube#Youtube
13 notes
·
View notes
Text
Azure DevOps Training
Azure DevOps Training Programs

In today's rapidly evolving tech landscape, mastering Azure DevOps has become indispensable for organizations aiming to streamline their software development and delivery processes. As businesses increasingly migrate their operations to the cloud, the demand for skilled professionals proficient in Azure DevOps continues to soar. In this comprehensive guide, we'll delve into the significance of Azure DevOps training and explore the myriad benefits it offers to both individuals and enterprises.
Understanding Azure DevOps:
Before we delve into the realm of Azure DevOps training, let's first grasp the essence of Azure DevOps itself. Azure DevOps is a robust suite of tools offered by Microsoft Azure that facilitates collaboration, automation, and orchestration across the entire software development lifecycle. From planning and coding to building, testing, and deployment, Azure DevOps provides a unified platform for managing and executing diverse DevOps tasks seamlessly.
Why Azure DevOps Training Matters:
With Azure DevOps emerging as the cornerstone of modern DevOps practices, acquiring proficiency in this domain has become imperative for IT professionals seeking to stay ahead of the curve. Azure DevOps training equips individuals with the knowledge and skills necessary to leverage Microsoft Azure's suite of tools effectively. Whether you're a developer, IT administrator, or project manager, undergoing Azure DevOps training can significantly enhance your career prospects and empower you to drive innovation within your organization.
Key Components of Azure DevOps Training Programs:
Azure DevOps training programs are meticulously designed to cover a wide array of topics essential for mastering the intricacies of Azure DevOps. From basic concepts to advanced techniques, these programs encompass the following key components:
Azure DevOps Fundamentals: An in-depth introduction to Azure DevOps, including its core features, functionalities, and architecture.
Agile Methodologies: Understanding Agile principles and practices, and how they align with Azure DevOps for efficient project management and delivery.
Continuous Integration (CI): Learning to automate the process of integrating code changes into a shared repository, thereby enabling early detection of defects and ensuring software quality.
Continuous Deployment (CD): Exploring the principles of continuous deployment and mastering techniques for automating the deployment of applications to production environments.
Azure Pipelines: Harnessing the power of Azure Pipelines for building, testing, and deploying code across diverse platforms and environments.
Infrastructure as Code (IaC): Leveraging Infrastructure as Code principles to automate the provisioning and management of cloud resources using tools like Azure Resource Manager (ARM) templates.
Monitoring and Logging: Implementing robust monitoring and logging solutions to gain insights into application performance and troubleshoot issues effectively.
Security and Compliance: Understanding best practices for ensuring the security and compliance of Azure DevOps environments, including identity and access management, data protection, and regulatory compliance.
The Benefits of Azure DevOps Certification:
Obtaining Azure DevOps certification not only validates your expertise in Azure DevOps but also serves as a testament to your commitment to continuous learning and professional development. Azure DevOps certifications offered by Microsoft Azure are recognized globally and can open doors to exciting career opportunities in various domains, including cloud computing, software development, and DevOps engineering.
Conclusion:
In conclusion, Azure DevOps training is indispensable for IT professionals looking to enhance their skills and stay relevant in today's dynamic tech landscape. By undergoing comprehensive Azure DevOps training programs and obtaining relevant certifications, individuals can unlock a world of opportunities and propel their careers to new heights. Whether you're aiming to streamline your organization's software delivery processes or embark on a rewarding career journey, mastering Azure DevOps is undoubtedly a game-changer. So why wait? Start your Azure DevOps training journey today and pave the way for a brighter tomorrow.
5 notes
·
View notes
Text
Beyond the Manual: Data Privacy in Academia

Navigating the complexities of data privacy in a large academic institution is no simple task. Today's Data Privacy and Security class provided an in-depth look at our university's official Data Privacy Manual as preparation for our final learning evidence for the course - creating our own data privacy manual. This comprehensive document outlines the policies and protocols instituted to safeguard the personal data and information of students, employees, and other stakeholders across the university system.
As we reviewed the manual, I gained a clearer understanding of just how much sensitive personal data the university necessarily collects and processes in carrying out its core functions. Everything from student admission applications and academic records, to employee records and payroll data, to visitor logs and CCTV footage falls under the scope of personal data that requires proper protection measures. The manual emphasizes key data privacy principles like transparency, legitimate purpose, and proportionality, which must be adhered to in all activities involving personal data collection and processing. Individuals should be made aware of what data will be gathered, why it is needed, how it will be used, and only the minimum necessary amount of data for that purpose should be retained.
While the depth and thoroughness of the manual is admirable, our class discussion raised concerns about whether the university is genuinely implementing and abiding by these policies uniformly across all units and information systems. In a previous discussion, our professor mentioned that our very own university has fallen short of complying with certain pillars of the National Privacy Commission's compliance framework for data privacy. This struck me as contradictory, given that our university has been awarded the Privacy Commission's Seal and Certificate of Registration, which is supposed to be an attestation that an organization is diligently complying with data privacy laws and regulations. How were we able to obtain that certification if gaps still exist in our privacy practices and framework execution?
It seems ironically misaligned for the university to have that prominent recognition from the regulatory authority overseeing data privacy in the Philippines, when we may not have all of our privacy measures entirely in order from their perspective. The seal and certificate should manifest an organization's earnest efforts toward Data Privacy Act compliance.
Moving forward, I hope our class could have taken a deeper audit look into how the university's actual data handling activities and safeguards measure up to what is prescribed in this manual. While having such a policy document is a good start, it is only meaningful if the procedures and controls are robustly operationalized across all data processing instances in a day-to-day practice. Understanding these policies is important, but witnessing their consistent implementation through analysis of real-world test cases is crucial to identifying any gaps and aiding compliance. I'm particularly interested in examining recent data breach or security incident response cases to see how they were managed compared to the protocols laid out here. These types of scenarios will be invaluable learning experiences as I prepare for a career ensuring data privacy and security in my future roles.
3 notes
·
View notes