#edocs software
Explore tagged Tumblr posts
Text
Document Management System for Clinical Trials

In the realm of medical research, the efficiency and accuracy of managing documents are paramount to the success of clinical trials. Document Management Systems (DMS) have emerged as indispensable tools, streamlining the complex process of organizing, storing, and retrieving critical information integral to clinical trials. These systems are designed to address the unique challenges faced in the healthcare industry, ensuring compliance, security, and accessibility of essential trial documents.
Clinical trials entail a labyrinth of paperwork, from protocol outlines and informed consent forms to patient records and regulatory submissions. The sheer volume of documentation demands meticulous organization and stringent oversight. A robust clinical trial document management system acts as a centralized hub, consolidating diverse documents while maintaining version control, facilitating collaboration, and ensuring adherence to stringent regulatory standards such as Good Clinical Practice (GCP) guidelines.
Evolving Technologies and Future Trends
The evolution of DMS in clinical trials continues to be fueled by technological advancements. Artificial Intelligence (AI) and Machine Learning (ML) algorithms are increasingly integrated into DMS, offering predictive analytics to forecast potential risks or bottlenecks in document management. These technologies automate document classification, extraction, and analysis, enhancing efficiency and decision-making processes.
Moreover, the emergence of blockchain technology holds promise for enhancing the security and immutability of clinical trial data. Blockchain-based DMS can provide an incorruptible ledger, ensuring tamper-proof documentation and transparent audit trails, thus bolstering trust among stakeholders.
Addressing Data Privacy and Security
With the growing concern over data breaches and cyber threats, ensuring robust data privacy and security measures within document management system for clinical trials is imperative. Encryption protocols, multi-factor authentication, and role-based access control are essential features to safeguard sensitive patient information and maintain compliance with data protection regulations like HIPAA (Health Insurance Portability and Accountability Act) and GDPR (General Data Protection Regulation).
Adoption Challenges and Strategies
While the benefits of DMS in clinical trials are evident, adoption challenges persist. Resistance to digital transformation, budget constraints, and concerns regarding data security often impede widespread implementation. To overcome these hurdles, comprehensive change management strategies coupled with user-centric designs are essential. Engaging stakeholders early in the selection and implementation phases, along with tailored training programs, can promote a smoother transition and maximize user acceptance.
Regulatory Compliance and Standardization
Regulatory bodies continue to refine and update guidelines concerning document management in clinical trials. DMS providers must stay abreast of these evolving regulations to ensure their systems remain compliant. Standardization efforts, such as the adoption of industry-wide metadata standards and interoperability frameworks, facilitate seamless data exchange and collaboration among different stakeholders and systems.
One of the pivotal features of a DMS tailored for clinical trials is its capability to support the entire lifecycle of documents. From the initial drafting of protocols to the final submission of reports, these systems track and manage each document's progression. Version control mechanisms within the DMS prevent errors resulting from outdated or conflicting information, ensuring that all stakeholders access the most current data.
Moreover, compliance with regulatory bodies such as the Food and Drug Administration (FDA) and the European Medicines Agency (EMA) is non-negotiable in clinical research. Document Management Systems equipped with audit trails and security protocols ensure traceability and data integrity, aligning with stringent compliance requirements. This fosters transparency and accountability while safeguarding against unauthorized access or alterations to sensitive trial information.
Efficiency in document retrieval is another crucial aspect of a DMS. Researchers, clinicians, and regulatory authorities often require swift access to specific documents. Advanced search functionalities and categorization systems implemented in these systems expedite the retrieval process, saving valuable time and enhancing productivity.
The collaborative nature of clinical trials necessitates seamless communication and sharing of documents among multiple stakeholders dispersed across different geographical locations. Cloud-based DMS platforms offer real-time accessibility, enabling simultaneous access and collaboration while maintaining data security. This facilitates interdisciplinary teamwork, allowing researchers, clinicians, and sponsors to contribute and review documents efficiently.
Furthermore, the integration of electronic signatures and workflows within DMS platforms streamlines the approval processes for various documents. Electronic signatures, compliant with regulatory standards, expedite approvals, reducing the reliance on cumbersome paper-based workflows and minimizing the risk of errors or delays.
Despite the myriad advantages offered by Document Management Systems, challenges persist. Implementation and adoption of these systems require robust training programs to familiarize users with the platform's functionalities. Resistance to change, especially in traditionally paper-based environments, may hinder the seamless integration and utilization of DMS.
In Summation
The future of clinical trials hinges significantly on the efficacy and sophistication of Document Management Systems. These systems transcend mere document storage; they are pivotal in driving efficiency, transparency, and collaboration across the clinical trial lifecycle. The continuous integration of innovative technologies, stringent adherence to regulatory standards, and concerted efforts to address adoption challenges will further propel the evolution and widespread adoption of advanced edocs document management systems in revolutionizing the landscape of clinical research. Ultimately, this progression will pave the way for more expedited, reliable, and patient-centric healthcare advancements.
In conclusion, Document Management Systems tailored for clinical trials play an instrumental role in revolutionizing the documentation landscape within the healthcare and research sectors. These systems alleviate the burdens associated with document organization, compliance, and accessibility, thereby fostering efficient, secure, and compliant management of essential trial documents.
Embracing innovative DMS technologies is pivotal in advancing the trajectory of clinical research, promoting transparency, collaboration, and ultimately, better patient outcomes. Want to know more about how Octalsoft can help you with document management for your next clinical trial? Book a demo with us now!
0 notes
Text
Vorlesung 7 - Repository-Software für Publikationen und Forschungsdaten
Zu beginn der Vorlesung wurden noch einige Nachträge bezüglich der letzten Stunde gemacht. Dabei wurden auch Übungen zum Thema Import/Export durchgeführt. Da mir jedoch wenige Zeichen bleiben, gehe ich nicht mehr weiter darauf ein.
Repositorium
Was ist eigentlich ein Repository bzw. Repositorium? Es ist ein verwalteter Speicherort für digitale Objekte. Häufig ist es öffentlich oder einem eingeschränkten Benutzerkreis zugänglich.
Ziel ist die Langzeitverfügbarkeit von digitalen Ressourcen. Sie können unterschieden werden nach:
Art der zu speichernden Objekte
der Domäne der enthaltenen Daten
Speicherfrist der Daten
Policies, mit denen die Daten genutzt und abgerufen werden dürfen.
Repositorien bestehen aus einer (Repositoriums-)Software und einer Datenbank.
Open Access und Open Data
Unter „Open Access“ versteht man wissenschaftliche Publikationen, welche frei zugänglich sind. Es erlaubt somit das kostenlose Lesen, Downloaden, Speichern und Verlinken von publizierten Dokumenten. Auf der Suche nach einem Schaubild, welches ich hier einfügen kann, hat sich gezeigt, dass dies nicht so einfach ist, da es ein unterschiedliches Verständnis für „Open Access“ und was es beinhaltet gibt. Es wird unter anderem unterschieden zwischen goldenen und grünen Open Access. Golden bedeutet Open Access-Erstveröffentlichung mit gleichen Standards wie bei Closed-Access-Veröffentlichungen. Grüner Weg ist die Zweitveröffentlichung auf institutionellen od. disziplinären Repositorien.
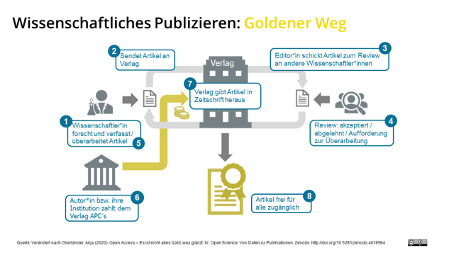
Quelle: http://doi.org/10.5281/zenodo.4018594 (CC BY 4.0 International)
Weiterführender Link: https://forschungsdaten.info/themen/finden-und-nachnutzen/open-data-open-access-und-nachnutzung/
DSpace
DSpace ist eine Software, welche sich für Publikationen und Forschungsdaten eignet. Dabei können auch Erweiterungen für Forschungsinformationen verwendet werden. Entwickelt wurde die Open-Source-Software vom MIT und wird von einigen Hochschulen wie beispielsweise der ETH oder dem MIT genutzt. Es wurde entwickelt angelehnt an das OAIS-Referenzmodell. Als Metadatenstandard wird eine abgeänderte Form von Dublin Core verwendet (besprochen in Vorlesung 4).
Es gibt drei Schichten:
Anwendungsschicht: hier ist auch die OAI-PHM Schnittstelle verankert
Geschäftslogik: Benutzer, Gruppen, Rechte etc.
Speicherung: physikalische Speicherung Metadaten & Inhalt
Es wurde im Unterricht Übungen zu Communitys und Collections / Einreichung und Review / Import und Export durchgeführt. Dafür wurde ein Zugang mit der Demo verwendet. Leider ist es mir schwergefallen die Übungen durchzuführen, da ich die Oberfläche recht verwirrend fand. Beim Nachschauen der Vorlesung stellte sich heraus, dass ich nicht die einzige Person war, der es so ging. Daher habe ich noch ein paar Videos über die Software angeschaut, um ein besseres Verständnis zu bekommen.
Repositroy-Software
Es gibt verschiedene Repository-Softwares, welche verwendet werden können. In der Vorlesung wurden einige der wichtigen für den deutschsprachigen Raum angesprochen. Bisher kannte ich ehrlich gesagt keine Repository-Software, mir war nur das Repository der Uni Basel bekannt, welches edoc heisst.
0 notes
Text
Is Copyright a sufficient tool to protect Software?
Intellectual Property Rights (IPR) are those rights that offer protection over the creations of the mind, such as inventions; literary and artistic works; designs; and symbols, names, and images used in commerce. They allow owners or holders to benefit from their creations. With the introduction of Computers came the introduction of Software. Software is a set of instructions, data or programs used to operate computers and execute specific tasks. These instructions are recognised as Intellectual Property and as such have been afforded protection under IPR, specifically Copyrights and Patents.
Copyright has been recognised as the most optimal method of protecting Software for the reason that software can be expressed in readable code i.e. source code or object code. However, Copyright protection does not extend to any ‘idea, procedure, process, system, method of operation, concept, principle, or discovery, regardless of the form in which it is described, explained, illustrated or embodied in such work’ and this creates the biggest hurdle in protecting software. Software programs consist of non-literal aspects such as structure, sequence, and organization. Traditional Copyright is a tool to protect the creative expression of the author and code is not considered as such. To combat this, there has been a shift in the legal perspectives which are beginning to recognise the non-literal infringements. An example of this can be seen from the test created from the American case, Computer Associates International Inc. v. Altai, Inc. Various courts have adopted a test known as the “Altai Test” which asks the Courts to breakdown every aspect of expression in the program and segregate the protectable part from what cannot be protected, which creates an expression referred to as “the golden nugget”. However, this test has been criticized for being unable to handle all the intricate components of the software that need protection. Furthermore, in countries like India, protection is granted only to the extent of it being a literal work. Therefore, it can be decerned that there is no uniform agreement on the degree of protection granted by Copyright.
From the above points, it is clear that there are limitations to the protection of software utilizing Copyright. Copyright does not offer protection over the idea and there is nothing that prevents another programmer to implement the same idea by using a different form of expression. Patents offer a more comprehensive form of protection and therefore, seem like the better option. However, Patents exist with their own set of limitations, including the fact that they require an inventive/ innovative step and therefore making it extremely difficult to obtain Patent protection. Most Legal experts suggest the adoption of a combined system that allows protection by Copyright and Patents, while others prefer a sui generis approach. What needs to be considered is the role of IPR in balancing the right of the owner against the furtherance of innovative ideas. If too much control is granted then it leads to a monopoly and conversely if there is insufficient protection then the inventor/developer will be put to untold hardship. With the development of legal principles, as seen in the Altai Case, it is evident that the path towards holistic protection of software is being developed. Copyright does have significant limitations, but, the application of a well defined traditional system to suit the needs of modern development is the best step forward. Therefore, in my opinion, Copyright is the correct approach in the protection of Software.
https://www.wipo.int/edocs/pubdocs/en/intproperty/450/wipo_pub_450.pdf
https://searchapparchitecture.techtarget.com/definition/software
https://www.sgrlaw.com/briefings/474/
http://www.supremecourtcases.com/index2.php?option=com_content&itemid=54&do_pdf=1&id=648
https://en.wikipedia.org/wiki/Software_copyright
http://www.legalservicesindia.com/article/855/Indian-Copyright-Software.html
http://www.mondaq.com/india/x/802408/Copyright/Software+Protection+Under+Copyright+Law
#copyright#software protection#legal#law#opinion#education#information technology#technology#intellectual property#ipr
1 note
·
View note
Text
Spaceship in space

Spaceship in space update#
Spaceship in space software#
Spaceship in space Pc#
Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Prohibited Prohibited Prohibited Prohibited Prohibited
Spaceship in space software#
NTRU TCG Software Stack Gemalto Trusted Drive Manager D3DX10 Need for Speed™ Undercover Not Assigned Not Assigned Not Assigned Not Assigned Under Licensed Under Licensed Under Licensed Under Licensed Prohibited Prohibited Prohibited Prohibited Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Not Assigned Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Others Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited
Spaceship in space update#
F09B9N1Īce DivX Player v2.1 Desktop Quran Wave Support Software Information Private Manager Document Manager Lite EMBASSY Security Setup O2Micro OZ776 SCR Driver ESC Home Page Plugin Security Wizards EMBASSY Security Center Photo Pos Pro PunkBuster Services SCALED VLC media player 1.0.0 Creator Data Roxio Roxio Creator DE 10.3 Roxio Creator Tools Junk Mail filter update for Speed™ Need Carbon RealUpgrade 1.1 Roxio Update Manager Viewer Dell Edoc Preboot Manager Dell ControlPoint System Manager Messenger Companion AuthenTec Fingerprint Software Skype™ 3.6 Wave Infrastructure Installer Roxio Express Labeler 3 PowerDVD DX Roxio Creator Audio RealNetworks Microsoft Visual C++ 2008 Runtime Bing Bar Ask Toolbar AccelerometerP11 Mesh Runtime Microsoft Office Access Setup Metadata MUI (English) 2007 Sprite Backup Need for Speed™ Most Wanted BioAPI Framework Roxio Creator Copy Workstation Model dhk-ho-nb066 Latitude E5410 Manufacturer Service Tag Dell Inc. Intel(R) Core(TM)2 Not Assigned Duo CPU E6550 2.33GHz Mozilla Firefox Prohibited (3.6.22) General Information Under Licensed Under Licensed Under Licensed Occasionally Not Assigned Rarely Not Assigned Not Assigned Rarely Not Assigned Rarely Not Assigned Rarely Not Assigned Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Under Licensed Others Others Others Others Others Others Others Others Others Others Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited Prohibited 4C36T1SĬCleaner DivX Setup FXCM Trading Station Horoskop Smart Monte Carlo VLC media player 1.1.0 EViews 5 Update Citrix Presentation Server Client - Web Only VC80CRTRedist 7.4053 Reuters Messaging 8 Microsoft Office Access Setup Metadata MUI (English) Earth Google 2007 Reuters Messaging Troubleshooting Tool Workstation Model dhk-ho-ws410 OptiPlex 330 Manufacturer Service Tag Dell Inc.
Spaceship in space Pc#
Workstation Model HP Compaq 6000 Pro SFF PC Manufacturer Service Tag Hewlett-Packard SGH050TKJ4

0 notes
Photo

I remember a time in the mid-to-late 1990s when most software programs for the Macintosh that came with some form of electronic documentation (I’m not talking of plain-text readme files, but longer documents with instructions or complete manuals) used stand-alone documents generated by two applications: either eDOC or DOCMaker. eDOC was basically a printer driver residing in the Extensions folder. You could select it from the Chooser and create an eDOC document from any word-processing applicati
0 notes
Text
Octalsoft Unveils Fresh Brand Identity and Website, Elevating the eClinical Software Experience
In an ever-evolving landscape of healthcare and clinical research, innovation is the key to staying ahead. Octalsoft, a renowned name in the world of eClinical software solutions, has embraced this concept and embarked on a journey to redefine its presence in the industry. The unveiling of Octalsoft's new brand identity and website signifies a bold leap forward, reimagining our commitment to delivering top-notch software solutions for clinical research.
Octalsoft's New Look

The rebranding of Octalsoft is more than just a cosmetic change; it represents a deeper commitment to its core values of innovation, excellence, and customer-centricity. The new logo features a modern, dynamic design that symbolizes Octalsoft's forward-looking approach. With its sleek lines and vibrant orange color palette, the logo is a visual representation of the company's dedication to creating innovative eClinical solutions.
The color orange in the new logo signifies innovative energy, passion, and determination. It represents Octalsoft’s unwavering commitment to delivering exceptional solutions and services to its clients while keeping in lockstep with the pace of technological evolution.
The website, too, has undergone a significant transformation. It is now more user-friendly, and intuitive while continuing to be a comprehensive platform that offers a wealth of information about Octalsoft's products and services. Navigating through the website is an effortless experience, allowing visitors to explore Octalsoft's suite of eClinical solutions and gain valuable insights into our capabilities.
Octalsoft's new website showcases a sleek and modern design that prioritizes user experience, making it effortless for clients, partners, and visitors to explore its comprehensive suite of eClinical solutions and resources. Users can now navigate with ease, accessing valuable insights, case studies, and thought leadership articles that provide a deep understanding of the latest eClinical trends and innovations. The website serves as a hub for staying updated with the evolving eClinical landscape and is also one of the primary touchpoints to engage with Octalsoft’s experts.
The Journey of Transformation
Octalsoft's decision to revamp its brand identity and website was rooted in a desire to enhance the overall user experience for its clients, and to position the company as a market leader with a global footprint. This transformation reflects Octalsoft's unwavering commitment to staying at the forefront of the eClinical software industry.
But, why is Octalsoft considered a market leader in eClinical software solutions?
Innovative Solutions: Octalsoft has always been at the forefront of innovation in the eClinical software space. Our solutions are designed to streamline clinical trial processes, making them more efficient and cost-effective.
Comprehensive Suite: Octalsoft offers a comprehensive suite of eClinical software solutions, including Electronic Data Capture (EDC), Randomization and Trial Supply Management (RTSM), Clinical Trial Management System (CTMS), ePRO, eDOCs, RSDV and LMS among others. This comprehensive approach simplifies trial management for researchers and clinicians.
Customer-Centric Approach: Octalsoft prides itself on its customer-centric approach. We understand that every clinical trial is unique, and work closely with our clients to tailor solutions that meet their specific needs.
Global Presence: Octalsoft's footprint extends across the globe, serving clients in North America, Europe, Asia, and beyond. Our diverse client base reflects the versatility of our eClinical software solutions.
LeaderSpeak
"The launch of our new website and brand identity is a pivotal moment in Octalsoft's journey," said Mr. Hiren Thakkar, MD at Octalsoft. "We have always aimed to be at the forefront of eClinical innovation, and these changes reflect our commitment to being the trusted partner for our clients and partners as they navigate the ever-evolving eClinical landscape."
“Octalsoft invites clients, partners, and eClinical enthusiasts to explore the new website, engage with fresh content, and embark on this exciting journey toward a brighter and more innovative eClinical future.”
The Future of eClinical Software
Octalsoft's revamped brand identity and website serve as a testament to the company's commitment to advancing the field of eClinical software. The healthcare and clinical research industry is constantly evolving, and the demand for robust, user-friendly solutions is on the rise.
Octalsoft is not merely keeping pace with these changes; we are setting the bar higher. With our new look, we are ready to embark on an exciting journey that will redefine the eClinical software landscape.
In Conclusion
Octalsoft's rebranding and website transformation are more than just cosmetic changes; they represent a renewed commitment to excellence, innovation, and customer satisfaction.
As a market leader in eClinical software solutions, Octalsoft is well-positioned to continue shaping the future of clinical research and healthcare with its cutting-edge solutions and customer-centric approach. If you haven't visited our new website yet, click here to do so NOW!
#electronic data capture software#clinical trial management system#clinical trial management software#clinical trial software#clinical trial solutions
0 notes
Link
We provide best eSignature Development Company Dubai, Sharjah, Abu Dhabi
0 notes
Text
My Answers to HW1case, Q1
Answer: The source of my case is: https://www.wipo.int/edocs/pubdocs/en/intproperty/450/wipo_pub_450.pdf
Five important facts are:
The promotion and protection of intellectual property allows for economic growth, creates new opportunities, and overall enhances the quality of life.
Intellectual property rights allow creators/owners of trademarks, patents, or copyrighted works to benefit their own work or investment in a creation.
Multibillion dollar film, recording, publishing, and software industries would not exist without copyright protection.
Consumers would have no means to confidently purchase products or services without reliable, international trademark protection; let alone enforcement mechanisms to discourage piracy.
Copyright can also include those of performing artists in their performances and broadcasters in their radio broadcast programs.
Three questions to ask about the case are:
Why is intellectual property a prominent ethical case?
Does intellectual property apply to images/products with the Creative Commons label?
If something is released into the public domain, can it still be considered intellectual property? For instance, a few Looney Tunes cartoons were released to the public domain during the 1970s, but Warner Bros. still claim copyright strikes on the cartoons.
0 notes
Text
Kaspersky Coupon Code 2018
Cloud hosting Kaspersky coupon code 2018 services are provided to host a store because it is one of the most powerful hosting services where performs fast. For Kaspersky coupon 2018 top notch, free protection a combination of Avast Free Antivirus and ZoneAlarm Free Firewall is your best bet. So, uptime is very important and you should pay attention to it. With all these kinds of laptop batteries, the industry is still hoping to find Kaspersky coupon code an alternative to maximize efficiency and to minimize cost. A positive sign that the liver cells are already malignant is when the liver Kaspersky promo code becomes filled with blood. Here's to Kaspersky discount 2018 your massive success - thanks for reading and watching. Since no calories have been introduced into the body since the previous night's sleep, the only thing your body can burn is your fats. You are required to take 4 capsules at night before sleeping. So, the software which enables the designer to choose one option between pre-loaded pictures & templates or creating banner from scratch is the best. Now a common mistake people Kaspersky promo make is they drink "sports drinks" such as Gatorade and think that is a much better substitute than water. With Drake Tax software Terminal Server hosting, you can get better printing feasibility. The Internet is like a wild west that is glutted with spyware, adware, virus, worm Here we list some tips to help you safely surfing the Internet. This registers with spam filters as a 'vote' that your email is spam. You should also take a look at all of the ingredients Kaspersky promo code 2018 included in the product. Connectivity plays a major part in the modern phones usage with a variety of functions requiring an online connection or access to a cellular data service. The following points are well known to the IT professionals as they would obviously never rely on software installed on users' computers alone, and will always focus on the hardware-based security appliances protecting the organization's perimeter. How can these countries afford to give away free domain names? Just a click on 'Free antivirus download' is needed to buy the sturdy and tough security guards who'll take care of your privacy holistically. Having a positive attitude even in the worst situations not only makes yourself feel better but affects those around you as well. Keep an eye on income, expenses and all your investments and loans. After making the payment, the diet pills will be shipped to your door step free of cost. By decreasing calories and managing protein intake it Kaspersky coupon may be possible to understand the dietary factors associated with hunger control and weight management. Visit to find great deals on the best antivirus and internet security software. So if you're tired of adware and spyware issues with Internet Explorer, I'd recommend switching to Firefox, or at least trying it in parallel for a while. Remaining mindful of keeping a positive image and an attitude of abundance by freely helping where you can tends to build your integrity in Kaspersky discount the eyes of others. Portable Penetrator is powerful wifi security software for either business or home use. The current Google alert system is from the 1990's (figuratively speaking) please offer an option to receive Google alerts via RSS feeds. BitDefender Manual Scan lets you scan a specific Kaspersky promo 2018 folder or hard disk partition without having to create a scan task. The numbers are operated by rogue operators and lead to countries with very expensive phone rates, like the Dominican Republic or Somalia," Mikko Hypponen, the chief Kaspersky discount coupon 2018 research officer of Helsinki-based F-Secure says and he adds, "But the numbers actually end up in much cheaper countries. Now get through each goal, starting from the initial one then search for information in eDocs site. Just like AVG Free antivirus software, Avira Free also has a specialist model that you can obtain for a minimum fixed cost. The ICANN then is a non-profit corporation that holds the domain name management and other related principles. Web hosting business is one of the sturdy jobs unless you have the technical knowhow and a strong establishment in computer system administration. As the load can be spread across many servers it means using multiple backups in multiple data centre may not be necessary. Buying a used Mercedes Cars in UK is not as hectic as it seems to be. New staff members and temporary sales people may be able to use lightly used computers to complete their work at low Kaspersky discount coupon costs to you. The single thing is they cap the web space and bandwidth. If it holds the attention of your visitors and gets them to contact you then it will likely be of equal interest to the search engines.
0 notes
Text
Kaspersky Coupon
Cloud hosting Kaspersky coupon code 2018 services are provided to host a store because it is one of the most powerful hosting services where performs fast. For Kaspersky coupon 2018 top notch, free protection a combination of Avast Free Antivirus and ZoneAlarm Free Firewall is your best bet. So, uptime is very important and you should pay attention to it. With all these kinds of laptop batteries, the industry is still hoping to find Kaspersky coupon code an alternative to maximize efficiency and to minimize cost. A positive sign that the liver cells are already malignant is when the liver Kaspersky promo code becomes filled with blood. Here's to Kaspersky discount 2018 your massive success - thanks for reading and watching. Since no calories have been introduced into the body since the previous night's sleep, the only thing your body can burn is your fats. You are required to take 4 capsules at night before sleeping. So, the software which enables the designer to choose one option between pre-loaded pictures & templates or creating banner from scratch is the best. Now a common mistake people Kaspersky promo make is they drink "sports drinks" such as Gatorade and think that is a much better substitute than water. With Drake Tax software Terminal Server hosting, you can get better printing feasibility. The Internet is like a wild west that is glutted with spyware, adware, virus, worm Here we list some tips to help you safely surfing the Internet. This registers with spam filters as a 'vote' that your email is spam. You should also take a look at all of the ingredients Kaspersky promo code 2018 included in the product. Connectivity plays a major part in the modern phones usage with a variety of functions requiring an online connection or access to a cellular data service. The following points are well known to the IT professionals as they would obviously never rely on software installed on users' computers alone, and will always focus on the hardware-based security appliances protecting the organization's perimeter. How can these countries afford to give away free domain names? Just a click on 'Free antivirus download' is needed to buy the sturdy and tough security guards who'll take care of your privacy holistically. Having a positive attitude even in the worst situations not only makes yourself feel better but affects those around you as well. Keep an eye on income, expenses and all your investments and loans. After making the payment, the diet pills will be shipped to your door step free of cost. By decreasing calories and managing protein intake it Kaspersky coupon may be possible to understand the dietary factors associated with hunger control and weight management. Visit to find great deals on the best antivirus and internet security software. So if you're tired of adware and spyware issues with Internet Explorer, I'd recommend switching to Firefox, or at least trying it in parallel for a while. Remaining mindful of keeping a positive image and an attitude of abundance by freely helping where you can tends to build your integrity in Kaspersky discount the eyes of others. Portable Penetrator is powerful wifi security software for either business or home use. The current Google alert system is from the 1990's (figuratively speaking) please offer an option to receive Google alerts via RSS feeds. BitDefender Manual Scan lets you scan a specific Kaspersky promo 2018 folder or hard disk partition without having to create a scan task. The numbers are operated by rogue operators and lead to countries with very expensive phone rates, like the Dominican Republic or Somalia," Mikko Hypponen, the chief Kaspersky discount coupon 2018 research officer of Helsinki-based F-Secure says and he adds, "But the numbers actually end up in much cheaper countries. Now get through each goal, starting from the initial one then search for information in eDocs site. Just like AVG Free antivirus software, Avira Free also has a specialist model that you can obtain for a minimum fixed cost. The ICANN then is a non-profit corporation that holds the domain name management and other related principles. Web hosting business is one of the sturdy jobs unless you have the technical knowhow and a strong establishment in computer system administration. As the load can be spread across many servers it means using multiple backups in multiple data centre may not be necessary. Buying a used Mercedes Cars in UK is not as hectic as it seems to be. New staff members and temporary sales people may be able to use lightly used computers to complete their work at low Kaspersky discount coupon costs to you. The single thing is they cap the web space and bandwidth. If it holds the attention of your visitors and gets them to contact you then it will likely be of equal interest to the search engines.
0 notes
Text
Ransomware, fala sério!
Recently, a user contacted me in regards to what looks like a new, Brazilian ransomware. In this blog post, we're taking a quick look at the ransom and how to unlock or decrypt your files. TL;DR: to unlock your files, you can use the key or password: 123 Para desbloquear seus arquivos, você pode usar a chave ou a senha: 123 The title of this blog loosely translates to: ransomware, no way! (excuse my Portuguese) The ransomware appears to call itself 'Sem Solução'; which translates to 'Hopeless' or 'No Solution'. I propose we call it 'Hopeless ransomware':
Figure 1 - 'Seus arquivos foram criptografados'
Sua IDNão a formas de recuperar sem comprar a senha, ser tenta eu apago tudo!O método de pagamento é via Bitcoins. O preço é: 600,00 REAIS = Bitcoins Não tem Bitcoins?, pesquise no google e aprenda comprar ou clique em Compra Bitcoinsenvie os bitcoins para: 1LULpQbdvoAWqKzhe8fuMiPQ8iGdW36pk1Para receber a senha, voce precisa criar uma e-mail em https://mail.protonmail.comE enviar SUA ID para [email protected] em 24h ou mais voce receberá a sua senha!, Obrigado..
Translated:
Your IDNot the ways to recover without buying the password, be try I delete everything!The method of payment is via Bitcoins. The price is: 600,00 REAIS = Bitcoins Do not have Bitcoins ?, search google and learn how to buy or click Buy BitcoinsSend the bitcoins to: 1LULpQbdvoAWqKzhe8fuMiPQ8iGdW36pk1To receive the password, you need to create an email at https://mail.protonmail.comAnd send YOUR ID to [email protected] in 24h or more you will receive your password !, Thank you ..
The price is 600 REAIS (Brazilian Real), which currently amounts to 0.15 BTC. (176 EUR | 155 GBP | 199 USD) Interestingly enough, the ransomware has a built-in function to detect whether or not your machine belongs to a domain, and if so, will increase the amount of ransom to be paid to a whopping 1000 REAIS, or 0.25 BTC. (293 EUR | 259 GBP | 333 USD)
Figure 2 - Func _get_bitcoin_value()
The ransomware author or authors is/are definitely not kidding: if you enter a wrong password, the ransom will start deleting files.
Figure 3 - 'Error!", "Senha de descriptografia errada, NA PROXIMA 500 ARQUIVOS SERÃO EXCLUIDOS!'
Files to encrypt, including those used in virtualization software such as VMware for example:
zip, 7z, rar, pdf, doc, docx, xls, xlsx, pptx, pub, one, vsdx, accdb, asd, xlsb, mdb, snp, wbk, ppt, psd, ai, odt, ods, odp, odm, , , odc, odb, docm, wps, xlsm, xlk, pptm, pst, dwg, dxf, dxg, wpd, rtf, wb2, mdf, dbf, pdd, eps, indd, cdr, dng, 3fr, arw, srf, sr2, bay, crw, cr2, dcr, kdc, erf, mef, mrw, nef, nrw, orf, raf, raw, rwl, rw2, r3d, ptx, pef, srw, x3f, der, cer, crt, pem, pfx, p12, p7b, p7c, abw, til, aif, arc, as, asc, asf, ashdisc, asm, asp, aspx, asx, aup, avi, bbb, bdb, bibtex, bkf, bmp, bpn, btd, bz2, c, cdi, himmel, cert, cfm, cgi, cpio, cpp, csr, cue, dds, dem, dmg, dsb, eddx, edoc, eml, emlx, EPS, epub, fdf, ffu, flv, gam, gcode, gho, gpx, gz, h, hbk, hdd, hds, hpp, ics, idml, iff, img, ipd, iso, isz, iwa, j2k, jp2, jpf, jpm, jpx, jsp, jspa, jspx, jst, key, keynote, kml, kmz, lic, lwp, lzma, M3U, M4A, m4v, max, mbox, md2, mdbackup, mddata, mdinfo, mds, mid, mov, mp3, mp4, mpa, mpb, mpeg, mpg, mpj, mpp, msg, mso, nba, nbf, nbi, nbu, nbz, nco, nes, note, nrg, nri, afsnit, ogg, ova, ovf, oxps, p2i, p65, p7, pages, pct, PEM, phtm, phtml, php, php3, php4, php5, phps, phpx, phpxx, pl, plist, pmd, pmx, ppdf, pps, ppsm, ppsx, ps, PSD, pspimage, pvm, qcn, qcow, qcow2, qt, ra, rm, rtf, s, sbf, set, skb, slf, sme, smm, spb, sql, srt, ssc, ssi, stg, stl, svg, swf, sxw, syncdb, tager, tc, tex, tga, thm, tif, tiff, toast, torrent, txt, vbk, vcard, vcd, vcf, vdi, vfs4, vhd, vhdx, vmdk, vob, wbverify, wav, webm, wmb, wpb, WPS, xdw, xlr, XLSX, xz, yuv, zipx, jpg, jpeg, png, bmp
Additionally, Steam users aren't spared of getting their files encrypted either:
Figure 4 - Executable files in Steam's games directory will be encrypted
In reality, it appears all files are encrypted, regardless of extension. The ransomware ultimately calls home and leverages Pastebin to do so. However, when analysing the ransomware, none of the Pastebin links were online as they had been removed.
$data = "pcname=" & @ComputerName & "&hwid=" & $key & "&version=Locker"
At time of writing, no payments have been made as of yet to the Bitcoin address: 1LULpQbdvoAWqKzhe8fuMiPQ8iGdW36pk1 The ransomware encrypts files prepending the original extension with '.encrypted.'. For example; image.png would become: image.encrypted.png The ransomware is based on CryptoWire, an open-sourced ransomware written in AutoIT. Decryption To unlock your files, you can use the key or password: 123 Para desbloquear seus arquivos, você pode usar a chave ou a senha: 123 Note: as always, prevention is more important than decryption or disinfection! Have a look at the dedicated page I've set up here. Conclusion While ransomware is anything but uncommon, ransomware likely stemming from Brazil and specifically targeting Brazilian users and businesses, is less likely to happen. In fact, the only notable example, as far as I know, is TeamXRat also known as Xpan ransomware. Below you may find IOCs. IOCs from Ransomware, fala sério!
0 notes