#domain name system application layer
Explore tagged Tumblr posts
Text
Why Quick Opening Closures Are Game-Changers for Pipeline Maintenance
What Are Quick-Opening Closures?
Quick-opening closures are devices used to open and close pressure vessels quickly and safely without the need for complex tools or prolonged manual effort. Installed on horizontal or vertical pressure-containing equipment, they eliminate the traditional bolt-and-nut approach and provide operators with a secure locking mechanism that can be opened within minutes.
Their functionality is crucial for industries that require frequent inspection, maintenance, or cleaning of pipelines and pressure vessels. In the USA, where industrial operations demand high uptime and rigorous safety compliance, quick-release closures have become essential for modern-day maintenance protocols.
Why They Matter for Pipeline Maintenance
1. Reduce Downtime Significantly
Traditional closures can take hours to open, involving manual unbolting and posing risks to maintenance crews. In contrast, Quick Opening Closures can be opened within minutes, enabling quicker inspection and maintenance cycles. For companies operating on tight schedules or dealing with emergency shutdowns, this time-saving feature is invaluable.
2. Enhance Worker Safety
Many QOCs are built with integrated safety interlocks, ensuring the closure cannot be opened until internal pressure is fully released. This reduces the risk of accidental opening and pressure-related injuries. For maintenance teams working in hazardous environments, this added safety layer is a major advantage.
3. Ensure Compliance and Efficiency
In regulated environments like the U.S. oil and gas sector, compliance with ASME and ANSI standards is non-negotiable. Top-tier quick-opening closure manufacturers design their closures to meet or exceed these benchmarks, ensuring safe and compliant operations.
SG Industries: A Trusted Partner in Quick-Opening Closures
SG Industries, through its platform https://sg-ind.com, has emerged as a dependable name in the domain of pressure equipment and pipeline solutions. With a sharp focus on innovation, customization, and quality, SG Industries offers a wide range of quick-release closures tailored for different applications — from pig launchers and receivers to filtration systems and pressure vessels.
Their solutions are engineered to meet the rigorous demands of U.S. industries, ensuring durability, operational safety, and minimal maintenance. For companies looking for reliable quick quick-opening closure manufacturers or quick-opening closures suppliers in the USA, SG Industries provides not just products but a partnership with dedicated support and technical expertise.
Tailored for the U.S. Market
One of the biggest strengths of SG Industries is its deep understanding of U.S. industrial needs. Their closures are designed with features that align with American safety standards, operational expectations, and maintenance practices. Whether you’re operating in Texas oil fields, California refineries, or Gulf Coast facilities, SG Industries delivers solutions that work reliably across diverse environmental and industrial conditions.
Final Thoughts
In a time where operational efficiency, safety, and rapid maintenance are more crucial than ever, quick opening closures are no longer optional — they’re a necessity. Investing in high-quality closures from trusted quick-opening closures suppliers like SG Industries not only reduces downtime but also boosts workplace safety and ensures long-term cost savings.
#Quick release closures#Quick opening closure manufacturers#Quick opening closures USA#Quick opening closures suppliers
0 notes
Text
EI Lamination: Core of Electrical Efficiency
EI laminations, named for their “E” and “I” shapes, are vital in electromagnetic devices for optimizing magnetic flux and energy transfer. Crafted from 0.35–0.5 mm silicon steel sheets, their stacked structure with insulated layers minimizes eddy current losses, a key factor in device efficiency.
How They Work When AC flows through a winding, EI cores—with high magnetic permeability—channel alternating magnetic fields. This induces voltage in secondary windings per Faraday’s law, ensuring efficient energy transfer with minimal flux leakage. The laminated design prevents conductive loops, reducing heat loss and boosting performance.
Material & Manufacturing Silicon steel (2–4% Si) is preferred for its high permeability and low resistivity, balancing flux transfer and eddy current reduction. Manufacturing involves: 1. Cutting/Stamping: Precision dies form “E”/”I” shapes from silicon steel sheets. 2. Annealing: Heating relieves stress and realigns magnetic domains. 3. Insulation Coating: Layers are coated to prevent short circuits. 4. Assembly: Stacked cores must align tightly to avoid air gaps, which increase magnetic reluctance.
Advantages & Applications – Efficiency: Reduced eddy currents and guided flux maximize energy transfer in transformers and motors. – Cost-Effectiveness: Modular design and durable silicon steel lower long-term costs. – Versatility: Used in: – Transformers: Stepping voltage in power grids and electronics. – Electric Motors: Stator/rotor cores for torque and vibration reduction. – Inductors: Low-reluctance paths for efficient magnetic energy storage.
Conclusion EI laminations remain essential in modern electronics, enabling efficient power conversion from consumer devices to industrial systems. As technology demands higher efficiency, their role in minimizing losses and enhancing reliability will only grow.

0 notes
Text
Explore Online Gaming Fun with the Latest Diuwin App
In the fast-paced world of online entertainment, users are constantly seeking secure and feature-rich platforms to enjoy seamless gaming experiences. One of the rising names in this domain is Diuwin, a platform that has quickly gained attention for its user-friendly interface, diverse game selection, and advanced features. Whether you are a seasoned gamer or a newcomer, the diuwin url gives you direct access to a world of engaging gameplay and rewarding opportunities.

What Makes the Diuwin Platform Unique?
Among the many gaming applications available today, the diuwin app stands out for its high level of functionality and user-centric design. Once downloaded, the app provides instant access to various casino-style games, sports betting options, and more, all optimized for mobile and desktop use. The intuitive layout ensures even first-time users can navigate the platform with ease, making it a popular choice for both beginners and professionals.
One of the key advantages of using the Diuwin platform is the responsiveness of the system. The games load quickly, and the transitions between menus are smooth, offering a glitch-free experience. The platform also takes user safety seriously, incorporating encryption and secure payment gateways that ensure all transactions and data remain protected.
How to Access the Platform Using Diuwin URL
Accessing Diuwin is simple and straightforward. By visiting the diuwin url, users are taken directly to the homepage where they can sign up or log in with their credentials. The platform works equally well on smartphones, tablets, and computers, adapting to various screen sizes and operating systems without compromising on performance.
This ease of access is one of the primary reasons users across different age groups prefer Diuwin. Whether you want to play while on a lunch break or during a long commute, the diuwin app provides uninterrupted access, allowing you to pick up where you left off.
Why Players Prefer the Diuwin App for Mobile Gaming
The mobile gaming market has seen significant growth, and the Diuwin team has tapped into this trend efficiently. The diuwin app is available for both Android and iOS users, offering an engaging and smooth gaming experience on the go. Once installed, users receive notifications about upcoming events, tournaments, and bonuses, ensuring they never miss out on new opportunities.
Furthermore, the app is designed to consume minimal device resources, making it ideal even for older smartphone models. Users can also set limits, track their gaming history, and manage their accounts directly from the app, adding layers of personalization and control.
Secure Transactions and Customer Support
Another factor contributing to the growing popularity of Diuwin is the reliability of its transaction system. Users can deposit and withdraw funds through various trusted payment methods with full confidence. Every transaction made through the diuwin url is protected by state-of-the-art encryption, making it a safe platform for real-money gaming.
In addition to secure payments, the Diuwin platform also boasts a responsive customer support team. Available 24/7 via live chat and email, users can get immediate assistance with any queries or technical difficulties they may encounter.
As digital entertainment continues to evolve, platforms like Diuwin are leading the way by offering reliable, fun, and secure gaming experiences. With the convenience of the diuwin url and the flexibility of the diuwin app, users can enjoy an immersive gaming environment anytime, anywhere.
0 notes
Text
How to Design and Build Scalable Microservices in Node.js
Microservices are becoming the go-to architecture for modern applications, and if you're just starting out with backend development, Node.js is a great place to begin. Known for its speed and lightweight nature, Node.js is an ideal choice for building services that need to grow and scale over time. If you're exploring Node.js web development, understanding how to create scalable microservices is a vital skill.
In this article, we’ll walk you through what microservices are, why they’re useful, and how you can design and build them using Node.js- even if you're new to backend programming.
What Are Microservices?
A microservices architecture breaks down a large application into smaller, independent services that each perform a specific task. These services communicate with each other through APIs, usually over HTTP or messaging queues.
For example, in an e-commerce platform:
One microservice might handle user authentication
Another handles orders
A third manages product listings
This approach is more flexible and maintainable than a traditional monolithic application, where everything is packed into one large codebase.
Why Choose Node.js for Microservices?
There are several reasons developers choose Node.js for microservices:
Fast and non-blocking I/O: Node.js handles multiple requests efficiently without waiting for previous ones to finish.
Lightweight and modular: Node’s package manager (npm) offers thousands of ready-to-use modules.
Easy to scale: Built-in tools like clustering and horizontal scaling make it easier to grow your services.
JavaScript everywhere: You can use the same language on both the frontend and backend.
Whether you're building your first API or planning a bigger system, many startups and enterprises rely on professional Node.js Development Services to set up clean and efficient architectures from the start.
Step-by-Step: Building Scalable Microservices in Node.js
Let’s break it down into manageable steps.
1. Define Your Services Clearly
Start by identifying the business functions of your app. Each microservice should be responsible for one feature or domain.
For example:
User Service for authentication
Order Service for handling transactions
Inventory Service for managing products
Keep each service focused. This improves performance and makes your app easier to maintain or scale.
2. Set Up a Basic Node.js Service
Here’s a very simple example using Express.js:
mkdir user-service cd user-service npm init -y npm install express
Create a server.js file:
jsCopy
const express = require('express'); const app = express(); app.get('/users', (req, res) => { res.json([{ id: 1, name: 'Alice' }]); }); app.listen(3000, () => { console.log('User service is running on port 3000'); });
This is your first microservice.
3. Use a Gateway or API Layer
In a microservices setup, each service has its own endpoint. But to avoid confusing your users with multiple URLs, you can use an API Gateway like Express Gateway, Kong, or Nginx to route traffic to the correct service.
The gateway can also handle:
Authentication
Rate limiting
Logging
Version control
If you want to save time and ensure best practices, it’s often a good idea to hire Node.js developers who already understand how to configure gateways and secure your APIs effectively.
4. Implement Inter-Service Communication
Microservices often need to talk to each other. This is done through APIs (HTTP) or message brokers (like RabbitMQ or Kafka).
In a simple HTTP example:
jsCopy
// order-service calls user-service const axios = require('axios'); axios.get('http://localhost:3000/users') .then(res => console.log(res.data));
As your system grows, switching to messaging queues improves performance and decouples services even further.
5. Use Docker to Containerize Your Services
To make your services easy to deploy, run, and scale, containerize them using Docker.
Here’s a simple Dockerfile for a Node.js service:
dockerfileCopy
FROM node:18 WORKDIR /app COPY . . RUN npm install CMD ["node", "server.js"]
This makes your service portable and predictable—key traits for scaling.
Most Node.js development companies containerize microservices and use orchestration tools like Docker Compose or Kubernetes to manage multiple services efficiently.
6. Add Monitoring and Logging
Don’t wait until something breaks. Add monitoring early.
Use tools like:
Winston or Morgan for logging
Prometheus and Grafana for monitoring performance
Logstash or Elasticsearch for log storage and search
This visibility helps you debug faster and scale more reliably.
7. Plan for Scaling
Node.js can scale vertically (more CPU/threads) and horizontally (more instances). Use built-in clustering or cloud platforms (like AWS ECS, Azure App Service, or Google Cloud Run) to scale your services based on demand.
Scalability is where many teams turn to expert Node.js Development Services to architect fault-tolerant and load-balanced systems that handle high traffic smoothly.
Tips for Beginners
Here are a few tips to make your microservices journey easier:
Start with two services and expand gradually
Keep services stateless (no shared memory or sessions)
Use environment variables for configuration
Maintain separate codebases for each service
Write clear API documentation for each microservice
Building scalable microservices doesn’t mean building everything at once. Take it step by step.
When to Seek Help
When your app grows in complexity or you need to handle production-level traffic, it might be time to bring in professional help.
A reputable Node.js development company can support you with:
System design and architecture
API security and versioning
Testing and CI/CD pipelines
Cloud deployment and scaling strategies
Or, if you’re looking for temporary expertise, you can hire Node.js developers to join your team on a freelance or contract basis. They’ll help speed up development, review your code for best practices, and guide your technical decisions.
Final Thoughts
Designing scalable microservices in Node.js is not as hard as it sounds—especially if you take a modular, step-by-step approach. With the right structure and tools, you can build systems that are easier to manage, faster to deploy, and ready to grow.
Whether you're building your first microservice or planning to scale a business application, Node.js has the flexibility and performance to help you succeed.
And when you're ready to move faster and scale smarter, don’t hesitate to reach out to a reliable Node.js development company or hire Node.js developers who can bring your vision to life with confidence.
#NodeJS#Microservices#BackendDevelopment#ScalableArchitecture#DistributedSystems#JavaScriptDevelopment#CloudNative#DevOps#Docker#Kubernetes#SystemDesign#WebDevelopment#TechArchitecture#HighAvailability#Serverless#APIDevelopment#SoftwareEngineering#CodeQuality#FullStackDevelopment
0 notes
Text
Strengthening Cybersecurity with Pentest, GDPR Audits & Threat Intelligence
In today’s hyperconnected digital world, data protection and cyber resilience are no longer optional—they’re critical business priorities. As cybercriminals become more sophisticated, organizations must adopt equally advanced methods to assess risk, stay compliant, and secure both visible and hidden parts of their infrastructure.
risikomonitor.com GmbH is a trusted name in cybersecurity automation and compliance monitoring. Their integrated solutions—ranging from website pentest solutions to GDPR data protection audits, dark web threat intelligence, and comprehensive IT security audits—equip businesses to protect their data assets, maintain compliance, and anticipate potential threats before they surface.
Let’s break down how these core services work together to safeguard your business from both external and internal threats.
Website Pentest Solutions: Exposing the Unseen Vulnerabilities
Your website is your public digital front. Unfortunately, it’s also one of the most targeted assets by hackers. SQL injections, cross-site scripting, misconfigured permissions, and outdated plugins are just a few of the vulnerabilities cyber attackers exploit.
risikomonitor.com GmbH offers automated and manual website pentest solutions that:
Simulate real-world cyberattacks to find exploitable weaknesses
Test for OWASP Top 10 vulnerabilities
Analyze both application and infrastructure layers
Deliver a full risk report with severity scores and remediation steps
Integrate with CI/CD pipelines for DevSecOps workflows
These penetration tests are vital not only for security hardening but also for maintaining trust with your customers and stakeholders. Regular testing ensures that your website remains a secure gateway rather than a potential entry point for cybercriminals.
GDPR Data Protection Audit: Building Trust Through Compliance
With increasing regulations surrounding personal data, compliance is now a competitive advantage. The GDPR (General Data Protection Regulation) is one of the world’s most comprehensive data privacy laws, and failure to comply can lead to penalties, reputational damage, and lost business.
risikomonitor.com GmbH simplifies compliance with an automated GDPR data protection audit system that:
Maps personal data flows across systems
Evaluates data storage, access, and sharing policies
Identifies compliance gaps in security and consent management
Supports the creation of DPIAs (Data Protection Impact Assessments)
Prepares you for regulator audits with accurate, exportable reports
This auditing solution is especially valuable for businesses operating in or targeting the EU, as well as any enterprise that processes data of EU citizens—even if they're based outside Europe.
Dark Web Threat Intelligence: Monitoring the Invisible Threats
Many breaches go undetected not because systems aren’t monitored, but because attackers are using channels businesses aren’t watching—like the dark web. Credentials, intellectual property, source code, and customer data often appear for sale in darknet marketplaces well before companies even realize there’s been a breach.
That’s where dark web threat intelligence comes in.
risikomonitor.com GmbH leverages specialized crawlers and AI-driven analysis to:
Detect exposed login credentials and email/password dumps
Monitor forums, marketplaces, and encrypted chat channels for brand mentions
Track stolen credit card or banking data
Identify phishing domains and clones impersonating your brand
Alert your team when new threats appear
With early warnings and actionable insights, businesses can react swiftly—shutting down threats before they spread.
IT Security Audits: The Foundation of Resilience
While individual services like pentesting or dark web scanning are powerful, a full IT security audit gives organizations the bigger picture. It’s a comprehensive review of your IT infrastructure, practices, and policies to uncover systemic risks and misconfigurations.
risikomonitor.com GmbH delivers end-to-end audits covering:
Network security and firewall configurations
User access and identity management
Endpoint protection and patch management
Cloud infrastructure and SaaS risk assessments
Internal security policies and training programs
The audit results are translated into an executive summary with technical recommendations, risk scoring, and a prioritized roadmap for fixing gaps—ensuring your cybersecurity investments are strategic and effective.
Why Choose risikomonitor.com GmbH?
Unlike isolated cybersecurity vendors, risikomonitor.com GmbH provides a unified platform that combines compliance, automation, and real-time threat detection—all backed by enterprise-grade technology and scalable to businesses of all sizes.
Their integrated offerings ensure you:
Detect threats before they breach your defenses
Stay GDPR-compliant with minimal manual effort
Monitor your digital identity beyond the surface web
Audit and improve every layer of your IT infrastructure
Whether you're an eCommerce brand, SaaS company, healthcare provider, or financial firm, this solution empowers you to protect sensitive data, satisfy auditors, and reduce operational risk.
Final Thoughts
The cyber threat landscape is constantly shifting. It’s no longer enough to simply react after an incident—modern businesses must detect, prevent, and adapt in real time.
With website pentest solutions, deep GDPR data protection audit, powerful dark web threat intelligence, and thorough IT security audits, risikomonitor.com GmbH offers a 360° cybersecurity strategy for businesses ready to lead in a digital-first world.
0 notes
Text
Computer Network Interview Questions
🖥️✨ Computer Network Interview Questions and Answers – Your Easy Prep Guide! ✨🖥️
When you hear the term Computer Networks, does your mind jump to routers, IP addresses, or maybe that one time your Wi-Fi betrayed you during an online class or meeting? 😂 Well, jokes aside, computer networking is one of the core subjects for students from CS/IT backgrounds – and guess what? Interviewers LOVE to ask questions from this topic.
Whether you're preparing for your first technical interview or brushing up for a campus placement, having a solid knowledge on basic networking concepts can make a real difference. From understanding how data travels across the internet to knowing what happens behind the scenes when you type a URL into your browser – networking concepts are everywhere. 💻
🚀 Top Computer Network Interview Questions & Answers 🔍
1. What is a Computer Network? A computer network is a group of two or more computers connected to each other so they can share resources, like files, printers, or the internet. The connection can be wired or wireless.
2. What’s the difference between LAN, MAN, and WAN?
LAN (Local Area Network): Covers a small area like your home or office.
MAN (Metropolitan Area Network): Covers a city or a large campus.
WAN (Wide Area Network): Covers large distances, like the internet.
3. What is an IP address? An IP address is a unique number assigned to every device connected to a network. It helps identify your device and allows it to communicate with other devices.
4. What is DNS? DNS (Domain Name System) translates domain names like google.com into IP addresses. It’s like your phone's contact list – you don’t memorize numbers, just names.
5. What is the difference between TCP and UDP?
TCP (Transmission Control Protocol): Reliable, sends data in order, and checks for errors. Used for things like emails and web browsing.
UDP (User Datagram Protocol): Faster but less reliable. Used for streaming videos or online games.
6. What is a Router? A router connects different networks together and directs data where it needs to go. It's what allows you to use Wi-Fi at home.
7. What is OSI Model? Can you explain its layers? The OSI Model is a framework that shows how data travels over a network. It has 7 layers:
Physical
Data Link
Network
Transport
Session
Presentation
Application Think of it like a ladder where each step adds more meaning to the data.
8. What is the difference between HTTP and HTTPS? HTTPS is just like HTTP, but secure. The “S” stands for Secure. It uses encryption to protect your data.
9. What is a MAC address? A MAC address is a unique hardware ID for your device's network card. Think of it like a digital fingerprint.
10. What is a Firewall? A firewall is a security system that monitors and controls incoming and outgoing network traffic. It helps protect your system from hackers or unwanted access.
📌 Need more? We’ve covered more in-depth questions along with real examples and diagrams on our blog here 👉 🔗 Read Full Blog - Computer Network Interview Questions & Answers

1 note
·
View note
Text
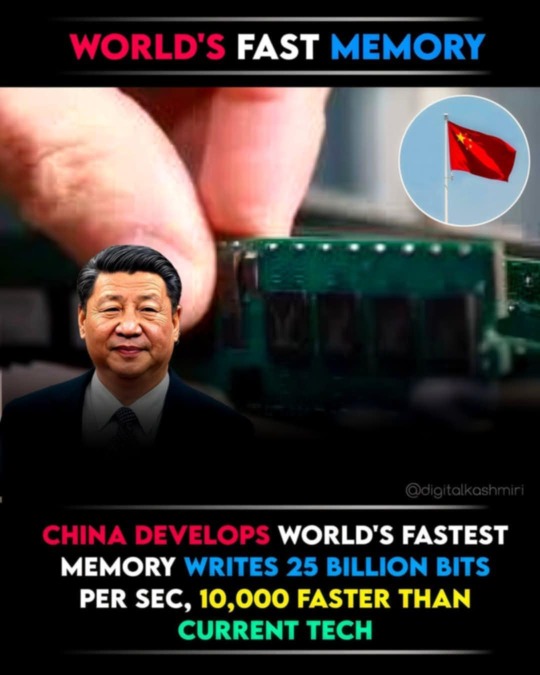
A research team at Fudan University has built the fastest semiconductor storage device ever reported, a non‑volatile flash memory dubbed “PoX” that programs a single bit in 400 picoseconds (0.0000000004 s) — roughly 25 billion operations per second. The result, published today in Nature, pushes non‑volatile memory to a speed domain previously reserved for the quickest volatile memories and sets a benchmark for data‑hungry AI hardware.
Smashing the speed ceiling
Conventional static and dynamic RAM (SRAM, DRAM) write data in 1–10 nanoseconds but lose everything when power is cut. Flash chips, by contrast, hold data without power yet typically need micro‑ to milliseconds per write — far too slow for modern AI accelerators that shunt terabytes of parameters in real time.
The Fudan group, led by Prof. Zhou Peng at the State Key Laboratory of Integrated Chips and Systems, re‑engineered flash physics by replacing silicon channels with two‑dimensional Dirac graphene and exploiting its ballistic charge transport.
By tuning the “Gaussian length” of the channel, the team achieved two‑dimensional super‑injection, which is an effectively limitless charge surge into the storage layer that bypasses the classical injection bottleneck.
“Using AI‑driven process optimization, we drove non‑volatile memory to its theoretical limit,” Zhou told Xinhua, adding that the feat “paves the way for future high‑speed flash memory.”
One billion cycles in a blink
Co‑author Liu Chunsen likens the breakthrough to shifting from a U‑disk that writes 1,000 times per second to a chip that fires 1 billion times in the blink of an eye. The previous world record for non‑volatile flash programming speed was about two million operations per second.
Because PoX is non‑volatile, it retains data with no standby power, a critical property for next‑generation edge AI and battery‑constrained systems. Combining ultra‑low energy with picosecond write speeds could remove the long‑standing memory bottleneck in AI inference and training hardware, where data shuttling, not arithmetic, now dominates power budgets.
Industrial and strategic implications
Flash memory remains a cornerstone of global semiconductor strategy thanks to its cost and scalability. Fudan’s advance, reviewers say, offers a “completely original mechanism” that may disrupt that landscape.
If mass‑produced, PoX‑style memory could eliminate separate high‑speed SRAM caches in AI chips, slashing area and energy. It can enable instant‑on, low‑power laptops and phones, and support database engines that hold entire working sets in persistent RAM.
The device can also strengthen China’s domestic drive to secure leadership in foundational chip technologies. The team did not disclose endurance figures or fabrication yield, but the graphene channel suggests compatibility with existing 2D‑material processes that global fabs are already exploring. “Our breakthrough can reshape storage technology, drive industrial upgrades and open new application scenarios,” Zhou said.
What happens next
Fudan engineers are now scaling the cell architecture and pursuing array‑level demonstrations. Commercial partners have not been named, but Chinese foundries are racing to integrate 2D materials with mainstream CMOS lines.
0 notes
Text
AddTon: TONCOIN Project Overview
TONCOIN ARBITRAGE TRADING AND APY STAKING PROGRAM based on the work of Dr. Nikolai Duro

Abstract :
The Open Network (TON) is a fast, secure and scalable blockchain and network project, capable of handling millions of transactions per second if necessary, and both user-friendly and service provider–friendly. We aim for it to be able to host all reasonable applications currently proposed and conceived. One might think about TON as a huge distributed supercomputer, or rather a huge super server, intended to host and provide a variety of services. This text is not intended to be the ultimate reference with respect to all implementation details. Some particulars are likely to change during the development and testing phases.
About TONCOIN Blockchain :
Blockchain Name: The Open Network (TON Blockchain)
Founders: Pavel Durov (Founder of Telegram) and Nikolai Durov (Chief Architect)
Initial Development: 2018–2019 (transitioned to a community-led project after regulatory issues)
Token Symbol: TON
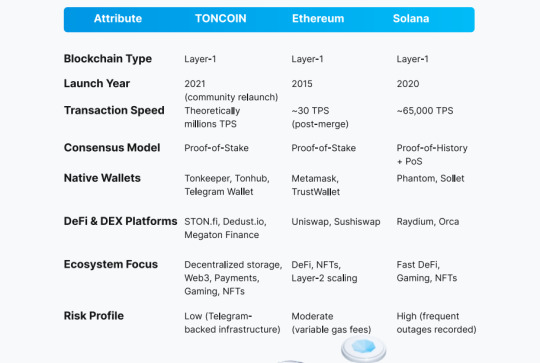
Blockchain Type: Layer-1 (Comparable to Ethereum, Solana)
Consensus Mechanism: Proof-of-Stake (PoS)
Special Note: Nikolai Durov designed the blockchain’s technical foundation: Infinite sharding, vertical scaling, instant payments.
TONCOIN Ecosystem Overview
Wallets: Telegram Wallet (integrated), Tonkeeper, Tonhub, OpenMask, MyTonWallet
DEX Platforms: STON.fi, Dedust.io, Megaton Finance
Browser Extensions: Tonkeeper Extension, OpenMask Browser Wallet
Web3 Applications: TON DNS, TON Storage, TON Sites, Telegram Wallet Bots
Gaming Initiatives: TON Punks, Fanton Fantasy League, Tap Fantasy Game, StormTrade (gaming and trading dApp)
NFT Marketplaces: Getgems.io, TON Diamonds, Disintar.io
Other Projects: TON Proxy, TON Payments, TON Wallet Bots, Open League (Gaming)
TONCOIN Global Market Position:
Listed on: Binance, OKX, KuCoin, Bybit, MEXC, Huobi, etc.
Market Presence: Active in 340+ markets globally.
Ranking: Consistently Top 15 on CoinMarketCap and CoinGecko
Daily Trading Volume: Exceeds $100 million.
Blockchain Industry Comparison:
How Addton.io Arbitrage Trading Works:
Focus Asset:
Addton.io only works on TONCOIN. Trading pair: TONCOIN/USDC (uses price gaps between TON and USDC)
Trading Platforms:
Trading happens only on decentralized exchanges (DEX)
STON.fi
Dedust.io
AI-Powered Arbitrage Bot:
A specialized AI trading bot has been developed. The bot monitors real-time TONCOIN prices across both exchanges.
Price Difference Capture:
When there is a price difference (example ) If the STON.fi TON price = $2.00 and the Dedust.io TON price = $2.05, then the bot automatically buys from the lower price exchange (STON.fi) and sells at the higher price exchange (Dedust.io).
Profit Generation:
Through this buying-selling cycle, organic profit is generated (without speculative risk). No leverage, no betting — only real price gap arbitrage.
Daily Operations:
The bot remains active from Monday to Friday (Saturday–Sunday off). Profits are distributed daily to staking participants.
Security:
There is no centralized risk, as trading occurs only through decentralized (on-chain) DEXs.
Program Launch and Ecosystem & Partnership:
Endorsed by the TON Blockchain community.
Supported by the Tapmoon Ecosystem.
Launch of The Open Network Classic Blockchain:
Native Token: TONCOIN Classic (CTON) Ticker: CTON Launch Price: $0.003 Participants will receive CTON tokens equal to their staking package value
Income Distribution and Incentives:
Participants will benefit from:
Daily arbitrage profits credited in TONCOIN.
CTON token bonus matching the staking package.
Special promotions and rewards in TAPS Token.
Risk Mitigation and Client Protection
TAPS Token Compensation
In case of trading losses, TAPS Tokens will be awarded.
Guaranteed CTON Tokens
Regardless of trading performance, CTON tokens will be distributed, securing future asset value.
Project Name Description:
Project Name : Description TON DNS : Web3 domain naming system TON Proxy : Decentralized VPN and privacy services TON Storage : Blockchain file storage TON Sites : Decentralized web hosting TON Payments : Layer-2 micropayment solutions STON.fi : Largest DEX on TON Dedust.io : Major decentralized exchange Megaton Finance : DeFi trading platform Getgems.io : NFT marketplace TON Diamonds : Premium NFT marketplace Disintar.io : NFT creation and trading platform Fanton Fantasy League : Fantasy sports gaming Tap Fantasy : Game Metaverse gaming Storm Trade : Trading and gaming hybrid dApp Open League : Decentralized esports and gaming platform
Why Choose Addton TONCOIN Staking Program?
Built on Telegram’s original blockchain vision (Pavel and Nikolai Durov)
Pure AI-based decentralized arbitrage trading.
Daily profits + bonus rewards in TONCOIN, CTON, and TAPS.
Dual protection model for user assets.
Integrated with Tapmoon Ecosystem.
Strong and growing TON Blockchain ecosystem support.
Website | twitter(X) | Telegram | Reddit | Facebook | Youtube
1 note
·
View note
Text
What Are the Best AI Undress Tools and How Do They Work?
Artificial Intelligence (AI) tools have grown remarkably in recent years, offering advanced functionalities across many domains—from image enhancement to virtual try-on technologies. However, one category that has drawn both curiosity and controversy is the rise of “AI undress tools.” These tools utilize machine learning and image processing to simulate the removal of clothing from images, typically in a digital or visual context. While the ethical implications are serious and warrant attention, it is important to understand how these tools work, what technologies they use, and which are considered the most accurate or sophisticated.
Understanding AI Undress Tools: What Are They?
AI undress tools are applications or platforms that use neural networks to process human images and generate simulations of undressed versions of the original. These tools rely on deep learning models trained on vast datasets of human anatomy and clothing patterns. Their core functionality often includes:
Image segmentation to distinguish body parts from clothing.
Generative models such as GANs (Generative Adversarial Networks) to create realistic body textures.
Style transfer techniques to remove clothing textures and reconstruct the underlying image.
These technologies are similar to those used in medical imaging, virtual try-on systems, and photo editing software but are repurposed for simulation of clothing removal.
Applications and Ethical Concerns
Although some developers claim to offer these tools for educational, medical, or entertainment purposes, AI undress tools come with significant ethical concerns, including potential misuse, privacy violations, and consent issues. It is crucial that users understand the boundaries of ethical use and the legal frameworks in their jurisdiction before engaging with these tools.
Some legitimate use cases include:
Medical education and anatomy visualization.
Virtual fashion modeling for e-commerce platforms.
AI-generated body reconstructions for art or design concepts.
That said, many of these tools have been banned or restricted on mainstream platforms due to the risks of misuse, especially in non-consensual content generation.
Top Undress AI Tools in 2025
Despite the controversies, several AI tools have emerged in this niche. Below are some of the top undress ai tools that are often discussed in tech forums, research discussions, and visual processing communities.
1. DeepNude Alternatives
Originally infamous and taken down, DeepNude led to the creation of multiple alternatives. While the original was banned, variations of it have surfaced, often under different names and through underground networks. These tools usually feature:
Fast rendering.
GAN-based models.
Simple UI for image uploads.
Many of these tools have been removed from public domains, but they remain a benchmark for comparison.
2. Nudify AI (Conceptual Use for Medical Simulation)
Nudify AI was designed for educational simulations and medical anatomy visualization. This tool provides:
Layered views of human anatomy.
Simulation of clothing removal for educational purposes.
Strict guidelines for ethical use.
Although it doesn’t cater to casual or entertainment use, it stands out for accuracy and professionalism.
3. Undress AI (Virtual Try-On Simulator)
Some fashion-related AI companies offer “undress” modes not in the literal sense, but as part of virtual try-on tools. These simulate how garments would fit or look if removed or changed.
Enables users to preview outfit changes.
Compatible with AR devices.
Employed by online clothing retailers.
Such tools are more commercially acceptable and useful in retail and design industries.
4. AI Portrait Editor Tools
Tools like Artbreeder, Fotor, and similar AI portrait editors allow for manipulation of human features, including aging, expression, and, in some cases, body adjustments. While not explicitly “undressing,” they offer body morphing features that simulate different appearances, including implied nudity for artistic purposes.
5. Custom GAN Tools (Open Source)
Advanced users and developers can build their own AI undress tools using open-source GAN models such as:
StyleGAN by NVIDIA.
Pix2Pix or CycleGAN.
RunwayML (for low-code implementation).
These tools require technical knowledge but offer more control over ethical implementation and data management.
Best AI Undress Tool Based on Accuracy
When evaluating the best AI undress tools for accuracy, user control, and design functionality, custom GAN-based setups take the lead. They offer:
The most realistic rendering.
Data privacy (if run locally).
Modifiability based on user intention.
However, they also demand programming skills and GPU resources.
Best AI Undress Tools with Commercial or Educational Intent
If you're seeking tools for legitimate use cases such as fashion modeling or anatomy education, Undress AI for virtual try-on or Nudify AI for simulation are considered the best undress ai tools. They provide:
Legal and ethical frameworks.
High-resolution output.
Advanced AI features integrated into user-friendly platforms.
Final Thoughts
AI undress tools walk a fine line between technological innovation and ethical boundaries. While some tools serve educational, medical, or fashion-related purposes, others veer into gray or problematic areas. Anyone exploring these tools must prioritize privacy, legality, and consent at all times.
Whether you're a developer, educator, designer, or simply curious about the potential of AI in visual transformation, understanding how these systems work and what the best undress AI tools are will help you make informed, responsible decisions.
0 notes
Text
What Are the Best AI Undress Tools and How Do They Work?
Artificial Intelligence (AI) tools have grown remarkably in recent years, offering advanced functionalities across many domains—from image enhancement to virtual try-on technologies. However, one category that has drawn both curiosity and controversy is the rise of “AI undress tools.” These tools utilize machine learning and image processing to simulate the removal of clothing from images, typically in a digital or visual context. While the ethical implications are serious and warrant attention, it is important to understand how these tools work, what technologies they use, and which are considered the most accurate or sophisticated.
Understanding AI Undress Tools: What Are They?
AI undress tools are applications or platforms that use neural networks to process human images and generate simulations of undressed versions of the original. These tools rely on deep learning models trained on vast datasets of human anatomy and clothing patterns. Their core functionality often includes:
Image segmentation to distinguish body parts from clothing.
Generative models such as GANs (Generative Adversarial Networks) to create realistic body textures.
Style transfer techniques to remove clothing textures and reconstruct the underlying image.
These technologies are similar to those used in medical imaging, virtual try-on systems, and photo editing software but are repurposed for simulation of clothing removal.
Applications and Ethical Concerns
Although some developers claim to offer these tools for educational, medical, or entertainment purposes, AI undress tools come with significant ethical concerns, including potential misuse, privacy violations, and consent issues. It is crucial that users understand the boundaries of ethical use and the legal frameworks in their jurisdiction before engaging with these tools.
Some legitimate use cases include:
Medical education and anatomy visualization.
Virtual fashion modeling for e-commerce platforms.
AI-generated body reconstructions for art or design concepts.
That said, many of these tools have been banned or restricted on mainstream platforms due to the risks of misuse, especially in non-consensual content generation.
Top Undress AI Tools in 2025
Despite the controversies, several AI tools have emerged in this niche. Below are some of the top undress ai tools that are often discussed in tech forums, research discussions, and visual processing communities.
1. DeepNude Alternatives
Originally infamous and taken down, DeepNude led to the creation of multiple alternatives. While the original was banned, variations of it have surfaced, often under different names and through underground networks. These tools usually feature:
Fast rendering.
GAN-based models.
Simple UI for image uploads.
Many of these tools have been removed from public domains, but they remain a benchmark for comparison.
2. Nudify AI (Conceptual Use for Medical Simulation)
Nudify AI was designed for educational simulations and medical anatomy visualization. This tool provides:
Layered views of human anatomy.
Simulation of clothing removal for educational purposes.
Strict guidelines for ethical use.
Although it doesn’t cater to casual or entertainment use, it stands out for accuracy and professionalism.
3. Undress AI (Virtual Try-On Simulator)
Some fashion-related AI companies offer “undress” modes not in the literal sense, but as part of virtual try-on tools. These simulate how garments would fit or look if removed or changed.
Enables users to preview outfit changes.
Compatible with AR devices.
Employed by online clothing retailers.
Such tools are more commercially acceptable and useful in retail and design industries.
4. AI Portrait Editor Tools
Tools like Artbreeder, Fotor, and similar AI portrait editors allow for manipulation of human features, including aging, expression, and, in some cases, body adjustments. While not explicitly “undressing,” they offer body morphing features that simulate different appearances, including implied nudity for artistic purposes.
5. Custom GAN Tools (Open Source)
Advanced users and developers can build their own AI undress tools using open-source GAN models such as:
StyleGAN by NVIDIA.
Pix2Pix or CycleGAN.
RunwayML (for low-code implementation).
These tools require technical knowledge but offer more control over ethical implementation and data management.
Best AI Undress Tool Based on Accuracy
When evaluating the best AI undress tools for accuracy, user control, and design functionality, custom GAN-based setups take the lead. They offer:
The most realistic rendering.
Data privacy (if run locally).
Modifiability based on user intention.
However, they also demand programming skills and GPU resources.
Best AI Undress Tools with Commercial or Educational Intent
If you're seeking tools for legitimate use cases such as fashion modeling or anatomy education, Undress AI for virtual try-on or Nudify AI for simulation are considered the best undress ai tools. They provide:
Legal and ethical frameworks.
High-resolution output.
Advanced AI features integrated into user-friendly platforms.
Final Thoughts
AI undress tools walk a fine line between technological innovation and ethical boundaries. While some tools serve educational, medical, or fashion-related purposes, others veer into gray or problematic areas. Anyone exploring these tools must prioritize privacy, legality, and consent at all times.
Whether you're a developer, educator, designer, or simply curious about the potential of AI in visual transformation, understanding how these systems work and what the best undress AI tools are will help you make informed, responsible decisions.
0 notes
Text
What Are the Best AI Undress Tools and How Do They Work?
Artificial Intelligence (AI) tools have grown remarkably in recent years, offering advanced functionalities across many domains—from image enhancement to virtual try-on technologies. However, one category that has drawn both curiosity and controversy is the rise of “AI undress tools.” These tools utilize machine learning and image processing to simulate the removal of clothing from images, typically in a digital or visual context. While the ethical implications are serious and warrant attention, it is important to understand how these tools work, what technologies they use, and which are considered the most accurate or sophisticated.
Understanding AI Undress Tools: What Are They?
AI undress tools are applications or platforms that use neural networks to process human images and generate simulations of undressed versions of the original. These tools rely on deep learning models trained on vast datasets of human anatomy and clothing patterns. Their core functionality often includes:
Image segmentation to distinguish body parts from clothing.
Generative models such as GANs (Generative Adversarial Networks) to create realistic body textures.
Style transfer techniques to remove clothing textures and reconstruct the underlying image.
These technologies are similar to those used in medical imaging, virtual try-on systems, and photo editing software but are repurposed for simulation of clothing removal.
Applications and Ethical Concerns
Although some developers claim to offer these tools for educational, medical, or entertainment purposes, AI undress tools come with significant ethical concerns, including potential misuse, privacy violations, and consent issues. It is crucial that users understand the boundaries of ethical use and the legal frameworks in their jurisdiction before engaging with these tools.
Some legitimate use cases include:
Medical education and anatomy visualization.
Virtual fashion modeling for e-commerce platforms.
AI-generated body reconstructions for art or design concepts.
That said, many of these tools have been banned or restricted on mainstream platforms due to the risks of misuse, especially in non-consensual content generation.
Top Undress AI Tools in 2025
Despite the controversies, several AI tools have emerged in this niche. Below are some of the top undress ai tools that are often discussed in tech forums, research discussions, and visual processing communities.
1. DeepNude Alternatives
Originally infamous and taken down, DeepNude led to the creation of multiple alternatives. While the original was banned, variations of it have surfaced, often under different names and through underground networks. These tools usually feature:
Fast rendering.
GAN-based models.
Simple UI for image uploads.
Many of these tools have been removed from public domains, but they remain a benchmark for comparison.
2. Nudify AI (Conceptual Use for Medical Simulation)
Nudify AI was designed for educational simulations and medical anatomy visualization. This tool provides:
Layered views of human anatomy.
Simulation of clothing removal for educational purposes.
Strict guidelines for ethical use.
Although it doesn’t cater to casual or entertainment use, it stands out for accuracy and professionalism.
3. Undress AI (Virtual Try-On Simulator)
Some fashion-related AI companies offer “undress” modes not in the literal sense, but as part of virtual try-on tools. These simulate how garments would fit or look if removed or changed.
Enables users to preview outfit changes.
Compatible with AR devices.
Employed by online clothing retailers.
Such tools are more commercially acceptable and useful in retail and design industries.
4. AI Portrait Editor Tools
Tools like Artbreeder, Fotor, and similar AI portrait editors allow for manipulation of human features, including aging, expression, and, in some cases, body adjustments. While not explicitly “undressing,” they offer body morphing features that simulate different appearances, including implied nudity for artistic purposes.
5. Custom GAN Tools (Open Source)
Advanced users and developers can build their own AI undress tools using open-source GAN models such as:
StyleGAN by NVIDIA.
Pix2Pix or CycleGAN.
RunwayML (for low-code implementation).
These tools require technical knowledge but offer more control over ethical implementation and data management.
Best AI Undress Tool Based on Accuracy
When evaluating the best AI undress tools for accuracy, user control, and design functionality, custom GAN-based setups take the lead. They offer:
The most realistic rendering.
Data privacy (if run locally).
Modifiability based on user intention.
However, they also demand programming skills and GPU resources.
Best AI Undress Tools with Commercial or Educational Intent
If you're seeking tools for legitimate use cases such as fashion modeling or anatomy education, Undress AI for virtual try-on or Nudify AI for simulation are considered the best undress ai tools. They provide:
Legal and ethical frameworks.
High-resolution output.
Advanced AI features integrated into user-friendly platforms.
Final Thoughts
AI undress tools walk a fine line between technological innovation and ethical boundaries. While some tools serve educational, medical, or fashion-related purposes, others veer into gray or problematic areas. Anyone exploring these tools must prioritize privacy, legality, and consent at all times.
Whether you're a developer, educator, designer, or simply curious about the potential of AI in visual transformation, understanding how these systems work and what the best undress AI tools are will help you make informed, responsible decisions.
0 notes
Text
What Are the Best AI Undress Tools and How Do They Work?
Artificial Intelligence (AI) tools have grown remarkably in recent years, offering advanced functionalities across many domains—from image enhancement to virtual try-on technologies. However, one category that has drawn both curiosity and controversy is the rise of “AI undress tools.” These tools utilize machine learning and image processing to simulate the removal of clothing from images, typically in a digital or visual context. While the ethical implications are serious and warrant attention, it is important to understand how these tools work, what technologies they use, and which are considered the most accurate or sophisticated.
Understanding AI Undress Tools: What Are They?
AI undress tools are applications or platforms that use neural networks to process human images and generate simulations of undressed versions of the original. These tools rely on deep learning models trained on vast datasets of human anatomy and clothing patterns. Their core functionality often includes:
Image segmentation to distinguish body parts from clothing.
Generative models such as GANs (Generative Adversarial Networks) to create realistic body textures.
Style transfer techniques to remove clothing textures and reconstruct the underlying image.
These technologies are similar to those used in medical imaging, virtual try-on systems, and photo editing software but are repurposed for simulation of clothing removal.
Applications and Ethical Concerns
Although some developers claim to offer these tools for educational, medical, or entertainment purposes, AI undress tools come with significant ethical concerns, including potential misuse, privacy violations, and consent issues. It is crucial that users understand the boundaries of ethical use and the legal frameworks in their jurisdiction before engaging with these tools.
Some legitimate use cases include:
Medical education and anatomy visualization.
Virtual fashion modeling for e-commerce platforms.
AI-generated body reconstructions for art or design concepts.
That said, many of these tools have been banned or restricted on mainstream platforms due to the risks of misuse, especially in non-consensual content generation.
Top Undress AI Tools in 2025
Despite the controversies, several AI tools have emerged in this niche. Below are some of the top undress ai tools that are often discussed in tech forums, research discussions, and visual processing communities.
1. DeepNude Alternatives
Originally infamous and taken down, DeepNude led to the creation of multiple alternatives. While the original was banned, variations of it have surfaced, often under different names and through underground networks. These tools usually feature:
Fast rendering.
GAN-based models.
Simple UI for image uploads.
Many of these tools have been removed from public domains, but they remain a benchmark for comparison.
2. Nudify AI (Conceptual Use for Medical Simulation)
Nudify AI was designed for educational simulations and medical anatomy visualization. This tool provides:
Layered views of human anatomy.
Simulation of clothing removal for educational purposes.
Strict guidelines for ethical use.
Although it doesn’t cater to casual or entertainment use, it stands out for accuracy and professionalism.
3. Undress AI (Virtual Try-On Simulator)
Some fashion-related AI companies offer “undress” modes not in the literal sense, but as part of virtual try-on tools. These simulate how garments would fit or look if removed or changed.
Enables users to preview outfit changes.
Compatible with AR devices.
Employed by online clothing retailers.
Such tools are more commercially acceptable and useful in retail and design industries.
4. AI Portrait Editor Tools
Tools like Artbreeder, Fotor, and similar AI portrait editors allow for manipulation of human features, including aging, expression, and, in some cases, body adjustments. While not explicitly “undressing,” they offer body morphing features that simulate different appearances, including implied nudity for artistic purposes.
5. Custom GAN Tools (Open Source)
Advanced users and developers can build their own AI undress tools using open-source GAN models such as:
StyleGAN by NVIDIA.
Pix2Pix or CycleGAN.
RunwayML (for low-code implementation).
These tools require technical knowledge but offer more control over ethical implementation and data management.
Best AI Undress Tool Based on Accuracy
When evaluating the best AI undress tools for accuracy, user control, and design functionality, custom GAN-based setups take the lead. They offer:
The most realistic rendering.
Data privacy (if run locally).
Modifiability based on user intention.
However, they also demand programming skills and GPU resources.
Best AI Undress Tools with Commercial or Educational Intent
If you're seeking tools for legitimate use cases such as fashion modeling or anatomy education, Undress AI for virtual try-on or Nudify AI for simulation are considered the best undress ai tools. They provide:
Legal and ethical frameworks.
High-resolution output.
Advanced AI features integrated into user-friendly platforms.
Final Thoughts
AI undress tools walk a fine line between technological innovation and ethical boundaries. While some tools serve educational, medical, or fashion-related purposes, others veer into gray or problematic areas. Anyone exploring these tools must prioritize privacy, legality, and consent at all times.
Whether you're a developer, educator, designer, or simply curious about the potential of AI in visual transformation, understanding how these systems work and what the best undress AI tools are will help you make informed, responsible decisions.
0 notes
Text
What Are the Best AI Undress Tools and How Do They Work?
Artificial Intelligence (AI) tools have grown remarkably in recent years, offering advanced functionalities across many domains—from image enhancement to virtual try-on technologies. However, one category that has drawn both curiosity and controversy is the rise of “AI undress tools.” These tools utilize machine learning and image processing to simulate the removal of clothing from images, typically in a digital or visual context. While the ethical implications are serious and warrant attention, it is important to understand how these tools work, what technologies they use, and which are considered the most accurate or sophisticated.
Understanding AI Undress Tools: What Are They?
AI undress tools are applications or platforms that use neural networks to process human images and generate simulations of undressed versions of the original. These tools rely on deep learning models trained on vast datasets of human anatomy and clothing patterns. Their core functionality often includes:
Image segmentation to distinguish body parts from clothing.
Generative models such as GANs (Generative Adversarial Networks) to create realistic body textures.
Style transfer techniques to remove clothing textures and reconstruct the underlying image.
These technologies are similar to those used in medical imaging, virtual try-on systems, and photo editing software but are repurposed for simulation of clothing removal.
Applications and Ethical Concerns
Although some developers claim to offer these tools for educational, medical, or entertainment purposes, AI undress tools come with significant ethical concerns, including potential misuse, privacy violations, and consent issues. It is crucial that users understand the boundaries of ethical use and the legal frameworks in their jurisdiction before engaging with these tools.
Some legitimate use cases include:
Medical education and anatomy visualization.
Virtual fashion modeling for e-commerce platforms.
AI-generated body reconstructions for art or design concepts.
That said, many of these tools have been banned or restricted on mainstream platforms due to the risks of misuse, especially in non-consensual content generation.
Top Undress AI Tools in 2025
Despite the controversies, several AI tools have emerged in this niche. Below are some of the top undress ai tools that are often discussed in tech forums, research discussions, and visual processing communities.
1. DeepNude Alternatives
Originally infamous and taken down, DeepNude led to the creation of multiple alternatives. While the original was banned, variations of it have surfaced, often under different names and through underground networks. These tools usually feature:
Fast rendering.
GAN-based models.
Simple UI for image uploads.
Many of these tools have been removed from public domains, but they remain a benchmark for comparison.
2. Nudify AI (Conceptual Use for Medical Simulation)
Nudify AI was designed for educational simulations and medical anatomy visualization. This tool provides:
Layered views of human anatomy.
Simulation of clothing removal for educational purposes.
Strict guidelines for ethical use.
Although it doesn’t cater to casual or entertainment use, it stands out for accuracy and professionalism.
3. Undress AI (Virtual Try-On Simulator)
Some fashion-related AI companies offer “undress” modes not in the literal sense, but as part of virtual try-on tools. These simulate how garments would fit or look if removed or changed.
Enables users to preview outfit changes.
Compatible with AR devices.
Employed by online clothing retailers.
Such tools are more commercially acceptable and useful in retail and design industries.
4. AI Portrait Editor Tools
Tools like Artbreeder, Fotor, and similar AI portrait editors allow for manipulation of human features, including aging, expression, and, in some cases, body adjustments. While not explicitly “undressing,” they offer body morphing features that simulate different appearances, including implied nudity for artistic purposes.
5. Custom GAN Tools (Open Source)
Advanced users and developers can build their own AI undress tools using open-source GAN models such as:
StyleGAN by NVIDIA.
Pix2Pix or CycleGAN.
RunwayML (for low-code implementation).
These tools require technical knowledge but offer more control over ethical implementation and data management.
Best AI Undress Tool Based on Accuracy
When evaluating the best AI undress tools for accuracy, user control, and design functionality, custom GAN-based setups take the lead. They offer:
The most realistic rendering.
Data privacy (if run locally).
Modifiability based on user intention.
However, they also demand programming skills and GPU resources.
Best AI Undress Tools with Commercial or Educational Intent
If you're seeking tools for legitimate use cases such as fashion modeling or anatomy education, Undress AI for virtual try-on or Nudify AI for simulation are considered the best undress ai tools. They provide:
Legal and ethical frameworks.
High-resolution output.
Advanced AI features integrated into user-friendly platforms.
Final Thoughts
AI undress tools walk a fine line between technological innovation and ethical boundaries. While some tools serve educational, medical, or fashion-related purposes, others veer into gray or problematic areas. Anyone exploring these tools must prioritize privacy, legality, and consent at all times.
Whether you're a developer, educator, designer, or simply curious about the potential of AI in visual transformation, understanding how these systems work and what the best undress AI tools are will help you make informed, responsible decisions.
0 notes
Text
What Are the Best AI Undress Tools and How Do They Work?
Artificial Intelligence (AI) tools have grown remarkably in recent years, offering advanced functionalities across many domains—from image enhancement to virtual try-on technologies. However, one category that has drawn both curiosity and controversy is the rise of “AI undress tools.” These tools utilize machine learning and image processing to simulate the removal of clothing from images, typically in a digital or visual context. While the ethical implications are serious and warrant attention, it is important to understand how these tools work, what technologies they use, and which are considered the most accurate or sophisticated.
Understanding AI Undress Tools: What Are They?
AI undress tools are applications or platforms that use neural networks to process human images and generate simulations of undressed versions of the original. These tools rely on deep learning models trained on vast datasets of human anatomy and clothing patterns. Their core functionality often includes:
Image segmentation to distinguish body parts from clothing.
Generative models such as GANs (Generative Adversarial Networks) to create realistic body textures.
Style transfer techniques to remove clothing textures and reconstruct the underlying image.
These technologies are similar to those used in medical imaging, virtual try-on systems, and photo editing software but are repurposed for simulation of clothing removal.
Applications and Ethical Concerns
Although some developers claim to offer these tools for educational, medical, or entertainment purposes, AI undress tools come with significant ethical concerns, including potential misuse, privacy violations, and consent issues. It is crucial that users understand the boundaries of ethical use and the legal frameworks in their jurisdiction before engaging with these tools.
Some legitimate use cases include:
Medical education and anatomy visualization.
Virtual fashion modeling for e-commerce platforms.
AI-generated body reconstructions for art or design concepts.
That said, many of these tools have been banned or restricted on mainstream platforms due to the risks of misuse, especially in non-consensual content generation.
Top Undress AI Tools in 2025
Despite the controversies, several AI tools have emerged in this niche. Below are some of the top undress ai tools that are often discussed in tech forums, research discussions, and visual processing communities.
1. DeepNude Alternatives
Originally infamous and taken down, DeepNude led to the creation of multiple alternatives. While the original was banned, variations of it have surfaced, often under different names and through underground networks. These tools usually feature:
Fast rendering.
GAN-based models.
Simple UI for image uploads.
Many of these tools have been removed from public domains, but they remain a benchmark for comparison.
2. Nudify AI (Conceptual Use for Medical Simulation)
Nudify AI was designed for educational simulations and medical anatomy visualization. This tool provides:
Layered views of human anatomy.
Simulation of clothing removal for educational purposes.
Strict guidelines for ethical use.
Although it doesn’t cater to casual or entertainment use, it stands out for accuracy and professionalism.
3. Undress AI (Virtual Try-On Simulator)
Some fashion-related AI companies offer “undress” modes not in the literal sense, but as part of virtual try-on tools. These simulate how garments would fit or look if removed or changed.
Enables users to preview outfit changes.
Compatible with AR devices.
Employed by online clothing retailers.
Such tools are more commercially acceptable and useful in retail and design industries.
4. AI Portrait Editor Tools
Tools like Artbreeder, Fotor, and similar AI portrait editors allow for manipulation of human features, including aging, expression, and, in some cases, body adjustments. While not explicitly “undressing,” they offer body morphing features that simulate different appearances, including implied nudity for artistic purposes.
5. Custom GAN Tools (Open Source)
Advanced users and developers can build their own AI undress tools using open-source GAN models such as:
StyleGAN by NVIDIA.
Pix2Pix or CycleGAN.
RunwayML (for low-code implementation).
These tools require technical knowledge but offer more control over ethical implementation and data management.
Best AI Undress Tool Based on Accuracy
When evaluating the best AI undress tools for accuracy, user control, and design functionality, custom GAN-based setups take the lead. They offer:
The most realistic rendering.
Data privacy (if run locally).
Modifiability based on user intention.
However, they also demand programming skills and GPU resources.
Best AI Undress Tools with Commercial or Educational Intent
If you're seeking tools for legitimate use cases such as fashion modeling or anatomy education, Undress AI for virtual try-on or Nudify AI for simulation are considered the best undress ai tools. They provide:
Legal and ethical frameworks.
High-resolution output.
Advanced AI features integrated into user-friendly platforms.
Final Thoughts
AI undress tools walk a fine line between technological innovation and ethical boundaries. While some tools serve educational, medical, or fashion-related purposes, others veer into gray or problematic areas. Anyone exploring these tools must prioritize privacy, legality, and consent at all times.
Whether you're a developer, educator, designer, or simply curious about the potential of AI in visual transformation, understanding how these systems work and what the best undress AI tools are will help you make informed, responsible decisions.
0 notes
Text
Network Operations Question Criteria NetWare Windows Unix Linux Mac OSX Server Operating Systems NetWare Version 6 Windows Server 2008, 2012R2Unix Linux NetwareFedora , Ubuntu Network ServerMac OS X ServerPerformanceHighHighHighHighHighAcceptanceWideWideVery wide WideModestCostModerate-highModerate-highModerate-highLow-moderateModerate-highStabilityHighHighHighHighHighTCP/IP supportYesYesYesYesYesStrengthsNDS, file serverMicrosoft name, Application ServerStability, Speed, FlexibilityStability, cost, Speed, flexibilityStability, SpeedQuestion 2 LAN stands for local area network while WAN stands for Wide Area Network. LAN network covers small geographical area like homes, office or a school up to a range of 1km. Tamara, (2009) says that WAN covers a broad area of metropolitan, regional boundaries up to a distance of 10000km. LAN uses a peer to peer network topology while WAN, on the other hand, uses a Client to Server model of the topology. LAN uses Ethernet standard while WAN uses T1. LAN uses layer two devices switches and bridges and Layer 1 devices like hubs and repeaters. WAN mostly uses layer three devices like routers, multi-layer switches and other devices like ATM and Frame Relay switches. Question 3 The user that gave the request might not have correct access rights to the application given, and it will result into the request failing. The issues can be avoided by setting the client and server to be in the same Windows domain. Make sure the user id of the customer is configured on both the client and server computers. There might be a failed communication between the client and server due to faulty connection hardware or no internet. No connection problems can be avoided by first establishing if there is a link to the server through the ping command. Problems might arise from weak firewall configurations. Firewalls might deny a client access to certain resources on the server, (Tamara, 2009). The problem can be avoided by first disabling firewall to ascertain if that is the cause of the problem and then configuring the firewall setting for the client in question. The transmission might not be successful due to power or electricity interruptions of either the client or server or both. Power interruptions can be avoided by having power backups. Transmission problems might arise due to change of IP addresses. The problem can be solved when using DHCP by setting client lease time to at list 24hrs. The problem can also be solved assigning static IP addresses to client, server or both.Question 4 Setting up of the a WAN that covers a large area has a lot of challenges during the initial setup. The major challenges are staffing, existing applications, network equipment and managing connectivity outside of the primary organization location. Staffing and personnel implications to consider include; making sure that the correct employees with the required skills are available at every global location. The senior network designer should make sure there is constant communication with all the teams in all the locations. The personnel should have the correct motivation in terms of pay. Another staff implication from different regions is the situation of the working environment in their area. Barriers to an effective global team include: time restrictions where the working times are different which might create problems in coordination. Language barrier can also be a major challenge since there will be a lack of adequate understanding between the personnel. Other barriers include effective communication like challenges of video conferencing and coordination of all the staff and having the same schedule to adhere to is very hard.Question 5 Setting up an effective WAN network requires powerful equipment and servers to implement the network (Tamara, 2009). The devices that will be needed include; several workstations, printers Ethernet cables, layer three devices like routers and multilayer switches. Each location in Peru, France, Hungary will have several servers preferably windows server 2012. Tere shall be a windows server 2012 standard and data center edition. Since the main office will be in USA, the servers to be used will be mainly data center edition. Each of the global locations will have a primary server, file sharing server and print server. The location in the USA will also have a web server to handle the website of the company. Users in each location will be able to access specific files from any of the locations if they have the correct access rights. Read the full article
0 notes
Text
Insulated Tools: The Defender Against Electric Dangers
Safety when working with electricity is never an option; it is a must. One of the best tools for safety against electric dangers is using insulated tools. Specifically designed to protect users from electric shock, these are essential tools used by electricians, engineers, and even DIYers who operate regularly with live electrical systems. We would discuss the importance of insulated tools, their features, applications, and why Krishan Brothers' range of insulated tools is such a great option for anyone working in electrical environments.
What Are Insulated Tools?
Special hand tools with an insulating layer through which current does not flow; they cannot flow through the tool to a human being when handling them. In fact, tools have high voltage ratings of up to 1,000 volts, as well as the ability to live circuits with safety while being used for all purposes at the workplace and in homes.
Important Insulated Tool Attributes
Strong Grade of Isolation
The insulated tools are abrasion-resistant and block electrical currents, keeping their users safe.
Ergonomics
The tools are ergonomic in construction; they are made to feel comfortable and efficient, with little fatigue if used for extended periods. In addition, the tool is firmly gripped.
Durability
These tools are created from strong materials and can be used in rough environments without breaking down easily.
Variety
Insulated tools have a variety ranging from pliers and cutters up to screwdrivers, wrenches, etc.
Safety Standards Compliance
Tools such as those from Krishan Brothers are made up to international safety standards for safe and trouble-free operation.
Applications of Insulated Tools
1. Electricity Maintenance
For electricians working on the circuit repair, changing breakers, or even installation of wires, insulated tools ensure that risk-free handling is there for the live circuits.
2. Industrial Applications
In factories and industrial premises where routine live equipment maintenance is always conducted, insulated tools provide personnel with added comfort for handling risky operations.
3. Automobile Repairs
Modern vehicles are mainly electric and are hybrid or electric. Mechanics in this domain need insulated tools.
4. Household Revamp
For the do-it-yourselfers who take on electrical repair or installation, insulation tools would be the safest and most efficient way of conducting this kind of job.
Why Krishan Brothers Insulated Tools?
For over 60 years of manufacturing tools, Krishan Brothers has become a name that has entered every home. Its insulated tools are quality, safety, and innovation in making them stand tall among professionals and hobbyists. Here's why Krishan Brothers stands out from the rest:
Proven Track Record: decades of expertise in delivering high-quality tools that meet the stringent safety standards.
State-of-the-Art Facilities: Tools are manufactured with the use of the latest technology to be quite safe and highly ergonomically efficient.
From the simplest of tools to specific ones, Krishan Brothers satisfies diverse needs.
Technical and customer support is given by them also. This ensures the user peace of mind.
Safety Precautions While Using Insulated Tools
Regular inspection of tools
Cracks, wear, or damage in the insulation should be looked for before its use.
Voltage ratings
Use tools rated for the specific voltage you are working on.
Storage
Tools must be kept in a dry,, safe environment in order to preserve the insulating qualities of the tool.
Do Not Abuse
Use tools only for those applications to avoid damaging and sustaining safety standards.
Conclusion
That is insulated tools, rather a commitment to safety and efficiency than a financial decision. Whether you are an electrician, an industrial technician, or an enthusiastic do-it-yourselfer, these tools have provided the best defense against electrical hazards. Krishan Brothers' insulated tools stand out for every need—from quality insulation, ergonomic design, through to international safety standards compliance.
Armed with the very best in trade tools, Krishan Brothers would mean each time an insulated tool would reach you: safety, strength, and ingenuity.
Frequently Asked Questions (FAQs)
1. What are insulated tools for?
Insulated tools are to tackle live electrical circuits and systems without jolting electrical shock towards the human using them.
2. Do insulation tools make a big difference in do-it-yourself projects?
Yes, especially if your home improvement task does entail electricity. Insulated tools lower the chances of having an accident happen to you significantly.
3. How to take care of your insulated tool?
It shall be frequently monitored for signs of degradation and to be stored indoors and never employed on an application where it is is intended to be applied.
4. What is a tool's acceptable voltage rating so as it stands??
Most insulated tools are rated to 1,000 volts, but read the rating for each tool you use.
5. Why do you need insulated tools from Krishan Brothers?
This is because Krishan Brothers provides good, long-lasting tools meeting international standards for safety that may guarantee reliability and support.
About the Author
Ritika is a passionate blogger with more than five years of experience in producing engaging, high-quality content on various niches, including tools and equipment. She has over 3,000 blogs in her portfolio, and she combines creativity and thorough research to deliver informative and relatable content. Ritika's dedication to excellence ensures that her writing not only informs but also inspires her readers.
0 notes