#distributed router
Explore tagged Tumblr posts
Text
Service Router vs Distributed Router in NSX-T (aka NSX 4.x)
In VMware NSX-T, both Service Router (SR) and Distributed Router (DR) are integral components of the networking architecture that play distinct roles in providing routing and connectivity within the virtualized network environment. Let’s delve into the differences between these two router types: Service Router (SR): Role: The Service Router is a centralized routing component that provides…
View On WordPress
0 notes
Text

glad to see the pokespe tradition of "incorporate every key item, no matter how obscure, into the main narrative" continues
#pokespe liveblog#one thing about dppt is that they Loved their key item events#also fun fact! i remember being so excited for when they did the oak's letter distribution over wifi#because as a kid our internet was So Super Bad and my ds wouldn't connect so i missed out on the darkrai event#but we got a new router around the time of this distribution and it worked and this was my first legit wifi event. many fond memories#(i later hacked in the member's card with an action replay but oak's letter was legit)
2 notes
·
View notes
Text
BLIIoT specializes in Industrial IoT Gateways, PLC Gateways, 4G Industrial Edge Router, SMS/4G RTU, Ethernet IO Module, Distributed I/O Module, ARM Industrial Computer, X86 Industrial Compter etc. OEM ODM Since 2005.
More than 200 patents, software and certification. BLIIoT Technology Make IIoT More Easier. https://www.bliiot.com/

#bliiot#bliiotsolution#iot#iiot#iot gateway#industrial edge router#io module#distributed io module#Ethernet IO Module#industrial computer#RTU#Alarm controller
0 notes
Text
African poverty is partly a consequence of energy poverty. In every other continent the vast majority of people have access to electricity. In Africa 600m people, 43% of the total, cannot readily light their homes or charge their phones. And those who nominally have grid electricity find it as reliable as a Scottish summer. More than three-quarters of African firms experience outages; two-fifths say electricity is the main constraint on their business.
If other sub-Saharan African countries had enjoyed power as reliable as South Africa’s from 1995 to 2007, then the continent’s rate of real GDP growth per person would have been two percentage points higher, more than doubling the actual rate, according to one academic paper. Since then South Africa has also had erratic electricity. So-called “load-shedding” is probably the main reason why the economy has shrunk in four of the past eight quarters.
Solar power is increasingly seen as the solution. Last year Africa installed a record amount of photovoltaic (PV) capacity (though this still made up just 1% of the total added worldwide), notes the African Solar Industry Association (AFSIA), a trade group. Globally most solar PV is built by utilities, but in Africa 65% of new capacity over the past two years has come from large firms contracting directly with developers. These deals are part of a decentralised revolution that could be of huge benefit to African economies.
Ground zero for the revolution is South Africa. Last year saw a record number of blackouts imposed by Eskom, the state-run utility, whose dysfunctional coal-fired power stations regularly break down or operate at far below capacity. Fortunately, as load-shedding was peaking, the costs of solar systems were plummeting.
Between 2019 and 2023 the cost of panels fell by 15%, having already declined by almost 90% in the 2010s. Meanwhile battery storage systems now cost about half as much as five years ago. Industrial users pay 20-40% less per unit when buying electricity from private project developers than on the cheapest Eskom tariff.
In the past two calendar years the amount of solar capacity in South Africa rose from 2.8GW to 7.8GW, notes AFSIA, excluding that installed on the roofs of suburban homes. All together South Africa’s solar capacity could now be almost a fifth of that of Eskom’s coal-fired power stations (albeit those still have a higher “capacity factor”, or ability to produce electricity around the clock). The growth of solar is a key reason why there has been less load-shedding in 2024...
Over the past decade the number of startups providing “distributed renewable energy” (DRE) has grown at a clip. Industry estimates suggest that more than 400m Africans get electricity from solar home systems and that more than ten times as many “mini-grids”, most of which use solar, were built in 2016-20 than in the preceding five years. In Kenya DRE firms employ more than six times as many people as the largest utility. In Nigeria they have created almost as many jobs as the oil and gas industry.
“The future is an extremely distributed system to an extent that people haven’t fully grasped,” argues Matthew Tilleard of CrossBoundary Group, a firm whose customers range from large businesses to hitherto unconnected consumers. “It’s going to happen here in Africa first and most consequentially.”
Ignite, which operates in nine African countries, has products that include a basic panel that powers three light bulbs and a phone charger, as well as solar-powered irrigation pumps, stoves and internet routers, and industrial systems. Customers use mobile money to “unlock” a pay-as-you-go meter.
Yariv Cohen, Ignite’s CEO, reckons that the typical $3 per month spent by consumers is less than what they previously paid for kerosene and at phone-charging kiosks. He describes how farmers are more productive because they do not have to get home before dark and children are getting better test scores because they study under bulbs. One family in Rwanda used to keep their two cows in their house because they feared rustlers might come in the dark; now the cattle snooze al fresco under an outside lamp and the family gets more sleep.
...That is one eye-catching aspect of Africa’s solar revolution. But most of the continent is undergoing a more subtle—and significant—experiment in decentralised, commercially driven solar power. It is a trend that could both transform African economies and offer lessons to the rest of the world."
-via The Economist, June 18, 2024. Paragraph breaks added.
#one of the biggest stories of this century is going to be the story of the African Renaissance#I promise you#well preferably they'll come up with a non-European term for it lol#but trust me it WILL happen and it will be SO good to see#africa#south africa#nigeria#kenya#solar#solar power#solar panels#solar pv#energy#clean energy#poverty#electrification#distributed energy#electricity#infrastructure#hope#solarpunk#good news#solar age#<- making that a tag now
416 notes
·
View notes
Text
i know i have made this post 500 times and i haven't managed to solve anything by making it the first 500 but maybe the 501st will help.
anyway i feel like i have, idk, 4 or 5 scales i keep trying to balance in my life, like job / chinese class / keeping my house clean and my life generally in order / writing / doing literally anything else
there is a limited amount of time in the week and i am out of it. in fact i do not have enough time to distribute between the scales to the extent that i want them. so every time i want something to go well, i have to extract it from one of the other buckets
and like ok. if my job isn't going well i start to want to kill myself. and if my house is a disaster area i start to want to kill myself. so i can't take much from those buckets without upending the whole scale and causing myself to be in hell for months. so that leaves me with chinese / writing / doing literally anything else to play with. the 'anything else' bucket unfortunately contains a rock that i can't seem to budge that says 'fuck around and do nothing time' so that's annoying. and i pay for chinese class so that forces me to keep putting time into that bucket (this is a good thing)
but that leaves writing with basically nothing. there's PROBABLY a way to get rid of the 'fuck around and do nothing' rock-- i didn't used to have it (or if i did have it, i had less going on that made it an issue)
like what are the levers i can pull?
literally unplug my wifi router so that if i'm at home i can't do anything except write? (well this is not true. i could easily read/draw/play vibeo games/etc instead of writing even without internet)
try to get motivation from somewhere? yelling at myself doesn't seem to help unfortunately :| other people depending on me definitely would but the project i'm working on does not have any kind of external pressure :|
i could probably exercise self discipline enough to just ban myself from all fun until this novel is done, but that would be kinda sad. i might have to do that though :|
winter is almost over and not being cold and in the dark all the time will certainly HELP this problem but idk if it will solve it completely.
like ig it's just hard to solve a problem that is just 100% i have spent all my available time and energy on other stuff and no longer have any time or energy for goals i want to accomplish. like there probably is no solution other than 'push myself into hell' or 'give up some other goal' or 'accept that you're never going to write again'. obviously the first one is what i have to do but wehhhhhhh
13 notes
·
View notes
Text
In a world not yet healed but slightly better than ours schools could have entire courses that consisted of like. learning how to repair a computer, both the hardware and software. installing your first linux distribution. how to safely torrent something and share a file. How to crack open a game file and make a slight adjustment for your personal pleasure. How to configure and secure a router. Basic computer literacy stuff that's getting lost in the shuffle of walled garden consumer technology.
#it would if demographics have held consistent since my high school days consist largely of nerd boys and soon to be former nerd boys.#and that's unfortunate because these are the sort of skills that should be pretty universal.#but this is meant to be a very grounded fantasy
19 notes
·
View notes
Text
ok since i've been sharing some piracy stuff i'll talk a bit about how my personal music streaming server is set up. the basic idea is: i either buy my music on bandcamp or download it on soulseek. all of my music is stored on an external hard drive connected to a donated laptop that's next to my house's internet router. this laptop is always on, and runs software that lets me access and stream my any song in my collection to my phone or to other computers. here's the detailed setup:
my home server is an old thinkpad laptop with a broken keyboard that was donated to me by a friend. it runs yunohost, a linux distribution that makes it simpler to reuse old computers as servers in this way: it gives you a nice control panel to install and manage all kinds of apps you might want to run on your home server, + it handles the security part by having a user login page & helping you install an https certificate with letsencrypt.
***
to stream my music collection, i use navidrome. this software is available to install from the yunohost control panel, so it's straightforward to install. what it does is take a folder with all your music and lets you browse and stream it, either via its web interface or through a bunch of apps for android, ios, etc.. it uses the subsonic protocol, so any app that says it works with subsonic should work with navidrome too.
***
to listen to my music on my phone, i use DSub. It's an app that connects to any server that follows the subsonic API, including navidrome. you just have to give it the address of your home server, and your username and password, and it fetches your music and allows you to stream it. as mentionned previously, there's a bunch of alternative apps for android, ios, etc. so go take a look and make your pick. i've personally also used and enjoyed substreamer in the past. here are screenshots of both:
***
to listen to my music on my computer, i use tauon music box. i was a big fan of clementine music player years ago, but it got abandoned, and the replacement (strawberry music player) looks super dated now. tauon is very new to me, so i'm still figuring it out, but it connects to subsonic servers and it looks pretty so it's fitting the bill for me.

***
to download new music onto my server, i use slskd which is a soulseek client made to run on a web server. soulseek is a peer-to-peer software that's found a niche with music lovers, so for anything you'd want to listen there's a good chance that someone on soulseek has the file and will share it with you. the official soulseek client is available from the website, but i'm using a different software that can run on my server and that i can access anywhere via a webpage, slskd. this way, anytime i want to add music to my collection, i can just go to my server's slskd page, download the files, and they directly go into the folder that's served by navidrome.
slskd does not have a yunohost package, so the trick to make it work on the server is to use yunohost's reverse proxy app, and point it to the http port of slskd 127.0.0.1:5030, with the path /slskd and with forced user authentification. then, run slskd on your server with the --url-base slskd, --no-auth (it breaks otherwise, so it's best to just use yunohost's user auth on the reverse proxy) and --no-https (which has no downsides since the https is given by the reverse proxy anyway)

***
to keep my music collection organized, i use beets. this is a command line software that checks that all of the tags on your music are correct and puts the file in the correct folder (e.g. artist/album/01 trackname.mp3). it's a pretty complex program with a ton of features and settings, i like it to make sure i don't have two copies of the same album in different folders, and to automatically download the album art and the lyrics to most tracks, etc. i'm currently re-working my config file for beets, but i'd be happy to share if someone is interested.
that's my little system :) i hope it gives the inspiration to someone to ditch spotify for the new year and start having a personal mp3 collection of their own.
29 notes
·
View notes
Text
the year is 2048. a smiling young farmer in a power wheelchair sells me the biggest bag of muesli I've ever seen out of a market stall built from repurposed drone parts. he sees the toys in my reusable bag and insists on throwing in some homemade cat treats “on the house”. I get an email from the wind farm: they've deposited another $20 in my account for using up excess electricity outside peak hours, so I decide to splurge on some flavoured honey and boba tea. I tell the barista I feel like a billionaire today and she smiles politely and asks me what a “billionaire” is. I run into an old friend handing out free insulin packets and we spend some time catching up. I've got a new gig at the organ printing depot and she's on rotating job assignments with the Workers' Cooperative: this month is insulin distribution, last month was reprogramming robot dogs as automated planters for the pollinator farm, next month she'll be on a work crew converting the old football stadium into a greenhouse. She's been sleeping in the park (by choice, of course, the local housing co-op has tons of suites open) but the climate bureau is cloud seeding this weekend and we're expecting a lot of rain. I invite her to crash at my place. She smiles and says she would like that. Our trolley ride home is briefly halted by an impromptu pride parade and the sun is setting as we pass the ivy-covered sign advertising the golf course that once existed where my neighbourhood now stands. A friendly technician explains she's just finished replacing the faulty router on our block so we can use the public WiFi again. I start a fire in the fireplace and sort through some mail: a postcard from one of my exes in Hawaii installing carbon dioxide scrubbers that double as frog habitats, a flyer for a music recital at the rehab clinic, and a letter from International Blood Services declining my donation because they are fully stocked. I ask my Global Music Archive uplink to select a random decade, country and genre and it starts a playlist while the two of us snuggle together on the couch under a hand-knitted blanket and my cat makes biscuits on top. On TV, a newscaster says global temperatures are at their lowest point in the last 40 years. I flip channels to some standup comedian saying kids these days don't know how to conceal when they're high because there's no cops anymore. We laugh until the rain softly falling on the roof lulls us to sleep.
#microfiction#hope for the future#a post by me™#this deserved its own post i hope it brightens someone's day
49 notes
·
View notes
Text
IoT Security Challenges in India: Protecting Smart Homes & Connected Devices

IoT is transforming the way people live by making their homes smart with devices such as security cameras, smart locks, and voice assistants. In India, IoT technology is adopted at a pace that cyber threats are rising rapidly. With weak security protocols, outdated software, and unawareness, Indian households are vulnerable to cyberattacks. In this blog, we will explore the major IoT security challenges in India and how individuals can safeguard their smart homes and connected devices. If you are looking to strengthen your understanding of cybersecurity, enrolling in a cyber security course can be a game-changer.
The IoT Boom in India
India is witnessing the highest adoption of IoT across homes and businesses. From smart TVs to intelligent thermostats, IoT is revolutionizing life. This booming technology, however, offers a large target size for hackers too who exploit the vulnerability of devices to gain unauthorized access to data.
Fundamental Drivers of IoT Adoption in India:
Increased internet penetration with low-priced data plans
Government initiatives such as Smart Cities Mission and Digital India
Increasing adoption of smart home devices as they become increasingly affordable
Growing application of industrial IoT in health, agriculture, and manufacturing
Chief IoT Security Challenges in India
Poor Authentication & Default Passwords
Most IoT devices have a factory-set password that the user ignores or fails to change. Hackers exploit these default credentials to take over the devices, entry private networks, and crack sensitive information.
Lack of Security Updates & Patches
Most smart devices have limited or no firmware updates, which makes them vulnerable to cyber threats. Many Indian consumers do not check for security updates, leaving their devices susceptible to known exploits.
Data Privacy Concerns
Smart devices collect vast amounts of personal data, from voice recordings to daily routines. Without stringent data protection policies, this information can be misused or leaked by malicious actors.
Botnet Attacks & DDoS Threats
Cybercriminals hijack unprotected IoT devices to form botnets, which are used to launch massive Distributed Denial of Service (DDoS) attacks. These attacks can cripple networks and cause disruptions to online services.
Unsecured Wi-Fi Networks
Many Indian households rely on poorly secured Wi-Fi connections, providing an easy entry point for hackers. Without encryption or strong passwords, attackers can intercept sensitive information and compromise connected devices.
Absence of Specific Cybersecurity Legislation for IoT
India has advanced in data protection with the Digital Personal Data Protection Act, but there is no dedicated IoT security framework. The absence of it leaves the manufacturer to choose cost over security and sell devices which are not so well protected in the market.
How to Secure Smart Homes & Connected Devices
Change Default Credentials
Always change the default usernames and passwords of the IoT after installation. Use strong, unique passwords and implement multi-factor authentication wherever possible.
Update Firmware Periodically
Scan for software and security updates on all smart devices, and install them as soon as they are available. In case your device can no longer get any updates, consider replacing it with a newer version that is at least as secure.
Secure Your Wi-Fi Network
Use a robust Wi-Fi password, and make sure WPA3 encryption is turned on. Limit remote access to your router, and make an IoT-specific network so that those devices can't contaminate your primary network.
Firewall & Security Solutions The use of firewalls and network security solutions monitors traffic and can block malicious activity on IoT networks. 5. Limit Data Sharing & Permissions
Assess permission for smart appliances and reduce or limit the devices from accessing unsecured personal information. De-activate unused add-ons, remote access in devices.
Cyber Security Courses
IoT-based cyber-attacks are minimized if awareness against the threat builds. To boost that awareness further, take time out to become a certified graduate of cyber security by signing for courses in areas like best security practices, principles of ethical hacking, and defending digital systems.
Road Ahead to Improving Indian IoT Security:
The Indian government, device manufacturers, and consumers must take proactive steps to mitigate IoT security risks. Stronger security standards, public awareness, and robust cybersecurity laws are the need of the hour to secure the future of IoT in India.
Conclusion
IoT devices offer incredible convenience but also introduce significant security risks. Protecting smart homes and connected devices requires a combination of best practices, awareness, and robust cybersecurity measures. By staying informed and adopting the right security strategies, individuals can ensure a safer IoT experience.
If you’re passionate about cybersecurity and want to build expertise in protecting digital systems, consider taking a cyber security course to gain hands-on knowledge and skills in ethical hacking, network security, and data protection.
2 notes
·
View notes
Text

The Federal Bureau of Investigation (FBI), Cyber National Mission Force (CNMF), and National Security Agency (NSA) assess that People’s Republic of China (PRC)-linked cyber actors have compromised thousands of Internet-connected devices, including small office/home office (SOHO) routers, firewalls, network-attached storage (NAS) and Internet of Things (IoT) devices with the goal of creating a network of compromised nodes (a “botnet”) positioned for malicious activity. The actors may then use the botnet as a proxy to conceal their identities while deploying distributed denial of service (DDoS) attacks or compromising targeted U.S. networks.
Integrity Technology Group, a PRC-based company, has controlled and managed a botnet active since mid- 2021. The botnet has regularly maintained between tens to hundreds of thousands of compromised devices. As of June 2024, the botnet consisted of over 260,000 devices. Victim devices part of the botnet have been observed in North America, South America, Europe, Africa, Southeast Asia and Australia.
While devices aged beyond their end-of-life dates are known to be more vulnerable to intrusion, many of the compromised devices in the Integrity Tech controlled botnet are likely still supported by their respective vendors.
FBI, CNMF, NSA, and allied partners are releasing this Joint Cyber Security Advisory to highlight the threat posed by these actors and their botnet activity and to encourage exposed device vendors, owners, and operators to update and secure their devices from being compromised and joining the botnet. Network defenders are advised to follow the guidance in the mitigations section to protect against the PRC-linked cyber actors’ botnet activity. Cyber security companies can also leverage the information in this advisory to assist with identifying malicious activity and reducing the number of devices present in botnets worldwide.
For additional information, see U.S. Department of Justice (DOJ) press release....
4 notes
·
View notes
Text
You make a thousand copies before breakfast. That doesn't make you part of the entertainment industry.

This is the LAST WEEKEND to back the Kickstarter campaign for the audiobook of my next novel, The Lost Cause. These kickstarters are how I pay my bills, which lets me publish my free essays nearly every day. If you enjoy my work, please consider backing!

Back when every book had a printing press in its history, every record a record-pressing plant, every film a film-lab, “making or handling copies of creative works” was a pretty good test to determine whether someone was part of the entertainment industry. Even if it turned out they weren’t, the kind of person who has a record-pressing plant can afford to consult an expert to make sure they’re on the right side of the law.
But a funny thing happened on the way to the 21st Century. We started using computers for everything. And computers work by making copies.
The mere act of reading this article created dozens — if not hundreds — of copies of it. These copies flashed in and out of existence in network buffers, switches and routers, graphics buffers and RAM, in multiple content distribution network caches and in your browser’s cache.
You make a thousand copies before breakfast. That doesn’t make you part of the entertainment industry.
It’s a near-dead-certainty that much of what you do violates the black letter of copyright law. We could simplify copyright until everyone who uses the internet for anything could easily grasp its contours and stay within them. But any copyright that is made simple enough for kids doing their homework and people using a dating site to follow would be way too crude for me and the various parties in my supply chain to follow.
-The Internet's Original Sin


My next novel is The Lost Cause, a hopeful novel of the climate emergency. Amazon won't sell the audiobook, so I made my own and I'm pre-selling it on Kickstarter!
25 notes
·
View notes
Text
The Darkweb: Exploring the hidden crimes of the Internet

The Dark Web is a complex and often misunderstood segment of the internet, shrouded in secrecy and notorious for its association with illegal activities. This hidden part of the web, accessible only through specialised software like Tor (The Onion Router), allows users to navigate anonymously, which has fostered both legitimate and illicit uses. The Dark Web is a subset of the Deep Web, which itself constitutes about 90% of the internet not indexed by traditional search engines. While most users interact with the Surface Web, the Deep Web includes private databases and secure sites, whereas the Dark Web is specifically designed for anonymity and privacy. The Dark Web emerged from projects aimed at ensuring secure communication, originally developed by the U.S. Department of Defence in the early 2000s. [1] [2]
Hidden Crimes in the Dark Web
The anonymity offered by the dark web has made it a hub for numerous forms of criminal activity. From illegal marketplaces to cybercrime forums, this underworld of the internet is teeming with hidden dangers.
Illicit Markets and Drug Trade
One of the most notorious aspects of the dark web is its marketplace for illegal goods. Websites like the now-defunct Silk Road offered a platform where users could buy and sell illegal drugs, firearms, stolen goods, and counterfeit documents. These black markets are often operated using cryptocurrencies such as Bitcoin to further mask identities and ensure untraceable transactions.According to a 2019 study by the European Monitoring Centre for Drugs and Drug Addiction, the dark web drug trade has grown exponentially, with millions of dollars' worth of drugs being sold monthly across various platforms . [3] [4]
2. Cybercrime and Hacking Services
The dark web also serves as a marketplace for cybercriminals. Hacking tools, ransomware-as-a-service, and stolen data are regularly exchanged in these hidden corners of the internet. Criminals offer services ranging from DDoS attacks to the sale of stolen credit card information and personal identities. Some forums even provide tutorials for novice hackers looking to learn cybercrime techniques. [5]
3. Human Trafficking and Exploitation
While less publicly discussed, the dark web has been linked to disturbing trends in human trafficking and child exploitation. Illegal forums allow criminals to sell services or even traffic victims, relying on the secrecy provided by encryption and anonymity transactions. These criminal activities often occur alongside other heinous content like child abuse imagery, which is tragically prevalent in certain corners of the dark web . [5]
4.Weapons and Assassination-for-Hire
Another dark aspect of the dark web is the sale of illegal firearms, explosives, and even assassination services. Websites provide arms to buyers without the restrictions and regulations of the surface web. Though some claims of hitmen-for-hire on the dark web have been debunked as scams, the sale of illicit firearms remains a significant concern for global law enforcement agencies .
Top 5 Notorious Cases on the Dark Web
(Content Warning: This list includes some horrifying incidents and scary dark web stories. We suggest you skip entries if you’re faint of heart or suffering from any type of anxiety or stress disorder.)
1. Banmeet Singh’s $100M+ dark web drug empire gets brought to light
Starting with a fairly recent case, Banmeet Singh of Haldwani, Northern India was sentenced to eight years in prison in late January 2024 after he was found to have created and led a multi-million dollar drug enterprise.The Indian national also forfeited $150 million in cryptocurrency. This proved to be illegal drug money that was laundered into cryptocurrency. Singh used various dark web marketplaces to create his drug empire. According to the U.S. Department of Justice, Singh shipped drugs from Europe to eight distribution centers in the US. After, these were transported to and sold in all 50 US states and other countries in the Americas. Singh was arrested in London, where he was residing in 2019. In 2023, he was extradited to the US. [7]

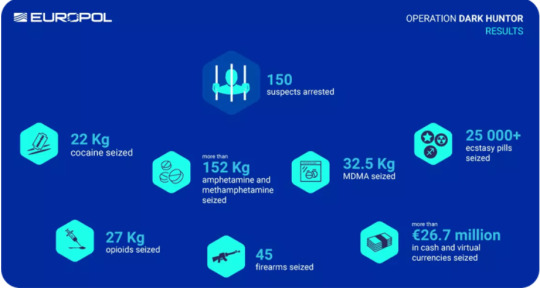
2. Operation Dark hunTor results in 150 arrests in nine countries
We’re moving from one multi-million-dollar illegal contraband case to the next. In 2021, Euro pol, Eurojust, and the police forces of nine countries conducted one of the biggest anti-crime operations the dark web has ever seen: Dark hunter. This operation resulted in 150 arrests across Australia, Bulgaria, France, Germany, Italy, the Netherlands, Switzerland, the United Kingdom, and the United States. All of the arrested were allegedly involved in buying or selling illegal goods on the dark web. The authorities found some articles in the possession of the arrested that strengthened their case: EUR 26.7 million (USD 31 million) in cash and virtual currencies, 234 kg of drugs, and 45 firearms.Italian authorities also managed to close down two dark web markets that boasted over 100,000 listings for illegal goods, DeepSea and Berlusconi. [7]
3. Operation DisrupTor exposes a dark web drugs distribution center
Amid the Covid pandemic, most businesses were struggling. Meanwhile, Operation DisrupTor suggests the drug business was still prospering. In February 2020, a group of FBI agents found 50 pounds of methamphetamine and thousands of Adderall pills in a storage shed in Los Angeles. The drugs, and the firearms that were also found, belonged to a crime network that had completed over 18,000 drug sales on the dark web. The criminal syndicate hid the drugs in a shed that they had made to look like a legitimate mail-order business. Their dark web drug sales included shipments to other dark net vendors, street dealers, and actual consumers. [7]
WATCH FULL VIDEO [8]
4. Attempt to hire a dark web hitman backfires
Now and then, crazy deep web stories pop up about how easy it is to hire a dark web hitman. One of these urban legends, however, turned out to be true. In February 2024, a woman from Canberra, Australia, pleaded guilty to inciting another to murder. The woman claimed to have contacted a dark web hitman (on the dark web marketplace Sinaloa Cartel) to murder her wealthy parents as part of an inheritance scheme. Supposedly, the total agreed-upon sum for the murder was $20,000, of which she had already paid $6,000 as a downpayment, using Bitcoin. It’s hard to say if the woman was actually talking to a contract killer or a scammer. Let’s just say we’re just happy the Australian court system was on to her before we could find out. While we don’t encourage anyone to go looking for a hitman on the dark web or elsewhere, this case goes to show that even on the dark web and while using crypto, many actions are retraceable. We always recommend people with good intentions to go for maximum privacy, as it’s no one’s business what they’re doing on the dark web. A great way to improve your privacy is by using NordVPN. NordVPN hides your IP address and encrypts your traffic, plus it blocks malicious links. [7]

5. No Love Deep Web takes dark web enthusiasts on a treasure hunt
Back in August of 2012, visitors on the dark web could find clues scattered on the network that led them through a fascinating alternate reality game. Much like Cicada 3031’s 4chan game, the clues led regular users through an array of clever clues set up like a treasure hunt. The dark web game employed a lot of encryption means to hide its hints, including the Caesar cipher, QR codes, Morse code, and a lot of other similar encryption methods. All of the clues were spread around dark websites, and one participant recounts the experience as quite thrilling:

So what was going on? Well, it wasn’t a secret government agency recruiting new members, and it wasn’t a feat of a group of cybercriminals.
Rather, the game was created by the experimental hip-hop group Death Grips to promote their new album, No Love Deep Web. [7]
READ MORE CASES [7]
Law Enforcement and the Fight Against Dark Web Crime
Despite the anonymity and encryption, law enforcement agencies around the world have made significant progress in cracking down on dark web criminality. In 2021, a multinational law enforcement effort, Operation Dark HunTor, led to the arrest of 150 individuals across multiple countries, targeting major drug vendors and illegal marketplaces on the dark web .
Undercover operations, improved digital forensics, and advances in cryptocurrency tracing have given authorities new tools to combat the hidden crimes of the dark web. However, for every takedown, new marketplaces and forums emerge, reflecting the cat-and-mouse dynamic between law enforcement and cybercriminals. [6]
Conclusion
While the dark web itself is not inherently evil, its secrecy has allowed criminals to thrive in ways that are difficult to regulate or even detect. From drug trafficking and cybercrime to human exploitation, the hidden crimes of the dark web reveal a darker side of digital anonymity. As law enforcement and technology continue to evolve, so too will the battle to uncover and combat these underground activities. Nonetheless, the dark web serves as a potent reminder that as technology advances, so too does the need for robust security measures and ethical oversight.
.
.
.
.
sources:
https://www.varutra.com/the-hidden-internet-exploring-the-secrets-of-the-dark-web/
2.https://sopa.tulane.edu/blog/everything-you-should-know-about-dark-web
3. https://www.unsw.edu.au/research/ndarc/news-events/blogs/2016/01/dark-net-drug-marketplaces-begin-to-emulate-organised-street-cri
4. https://www.euda.europa.eu/darknet_en
5. https://www.findlaw.com/criminal/criminal-charges/dark-web-crimes.html
6. https://syntheticdrugs.unodc.org/syntheticdrugs/en/cybercrime/detectandrespond/investigation/darknet.html
7. file:///D:/New%20folder/The%2013%20Most%20Notorious%20Cases%20on%20the%20Dark%20Web.html
8. https://youtu.be/d4NSfrOtMfU?feature=shared
#crime#cyberpunk 2077#cybersecurity#internet#dark web#criminal case#laws#murder mystery#mental health
5 notes
·
View notes
Text
connecting gaza
E-sims for Gaza:
www.disabilityvisibilityproject.com/2023/12/25/crips-for-esims-for-gaza/
Palestinians are using donated eSIM cards to stay in touch with the outside world (Jan 2024, NBC News)
Many of the eSIMs are donated by activists who collect them from donors around the world. Mirna El Helbawi, a 31-year-old Egyptian writer who runs a project called Connecting Gaza, said she has distributed more than 100,000 eSIMs since the war began. www.instagram.com/mirna_elhelbawi
She and other activists use Instagram and X to solicit donors from around the world to purchase eSIMs from international phone carriers. They then pass them to a system of what El Helbawi calls “human routers” across Gaza with functioning eSIMs who can set up their phones as Wi-Fi hot spots to share additional eSIMs with others.
https://www.reuters.com/world/middle-east/desperate-news-gazans-struggle-with-mobile-network-2024-02-02/
https://www.lemonde.fr/en/international/article/2024/02/04/in-gaza-virtual-chips-are-breaking-the-telecommunications-blockade_6493217_4.html
Internet blackouts as weapon (WIRED)
On October 27, Israel reportedly imposed a full internet shutdown in the area, cutting off the last remaining connectivity for about 34 hours as its troops moved into the Gaza Strip. After what’s left of Gaza’s internet access was restored—data shows it stands at around 15 percent or less of usual connectivity—the area has suffered two other, similar connectivity blackouts. The most recent lasted for about 15 hours on Sunday as Israel was carrying out an intense operation to cut off Gaza City in the north from southern Gaza Throughout the Gaza Strip, there are around a dozen internet service providers and cell phone companies that get people online—although cell networks only use 2G technologies, as opposed to the faster 3G, 4G, and 5G connections available across much of Israel. These companies are heavily reliant on Israeli infrastructure to connect to the global internet, with open internet advocacy nonprofit the Internet Society classing Palestine as having “poor” connections to the wider internet. Since the start of the war, mobile and internet providers’ offices, cables, and cell towers have been destroyed. Many are now totally offline.
6 notes
·
View notes
Text
Ansible Collections: Extending Ansible’s Capabilities
Ansible is a powerful automation tool used for configuration management, application deployment, and task automation. One of the key features that enhances its flexibility and extensibility is the concept of Ansible Collections. In this blog post, we'll explore what Ansible Collections are, how to create and use them, and look at some popular collections and their use cases.
Introduction to Ansible Collections
Ansible Collections are a way to package and distribute Ansible content. This content can include playbooks, roles, modules, plugins, and more. Collections allow users to organize their Ansible content and share it more easily, making it simpler to maintain and reuse.
Key Features of Ansible Collections:
Modularity: Collections break down Ansible content into modular components that can be independently developed, tested, and maintained.
Distribution: Collections can be distributed via Ansible Galaxy or private repositories, enabling easy sharing within teams or the wider Ansible community.
Versioning: Collections support versioning, allowing users to specify and depend on specific versions of a collection. How to Create and Use Collections in Your Projects
Creating and using Ansible Collections involves a few key steps. Here’s a guide to get you started:
1. Setting Up Your Collection
To create a new collection, you can use the ansible-galaxy command-line tool:
ansible-galaxy collection init my_namespace.my_collection
This command sets up a basic directory structure for your collection:
my_namespace/
└── my_collection/
├── docs/
├── plugins/
│ ├── modules/
│ ├── inventory/
│ └── ...
├── roles/
├── playbooks/
├── README.md
└── galaxy.yml
2. Adding Content to Your Collection
Populate your collection with the necessary content. For example, you can add roles, modules, and plugins under the respective directories. Update the galaxy.yml file with metadata about your collection.
3. Building and Publishing Your Collection
Once your collection is ready, you can build it using the following command:
ansible-galaxy collection build
This command creates a tarball of your collection, which you can then publish to Ansible Galaxy or a private repository:
ansible-galaxy collection publish my_namespace-my_collection-1.0.0.tar.gz
4. Using Collections in Your Projects
To use a collection in your Ansible project, specify it in your requirements.yml file:
collections:
- name: my_namespace.my_collection
version: 1.0.0
Then, install the collection using:
ansible-galaxy collection install -r requirements.yml
You can now use the content from the collection in your playbooks:--- - name: Example Playbook hosts: localhost tasks: - name: Use a module from the collection my_namespace.my_collection.my_module: param: value
Popular Collections and Their Use Cases
Here are some popular Ansible Collections and how they can be used:
1. community.general
Description: A collection of modules, plugins, and roles that are not tied to any specific provider or technology.
Use Cases: General-purpose tasks like file manipulation, network configuration, and user management.
2. amazon.aws
Description: Provides modules and plugins for managing AWS resources.
Use Cases: Automating AWS infrastructure, such as EC2 instances, S3 buckets, and RDS databases.
3. ansible.posix
Description: A collection of modules for managing POSIX systems.
Use Cases: Tasks specific to Unix-like systems, such as managing users, groups, and file systems.
4. cisco.ios
Description: Contains modules and plugins for automating Cisco IOS devices.
Use Cases: Network automation for Cisco routers and switches, including configuration management and backup.
5. kubernetes.core
Description: Provides modules for managing Kubernetes resources.
Use Cases: Deploying and managing Kubernetes applications, services, and configurations.
Conclusion
Ansible Collections significantly enhance the modularity, distribution, and reusability of Ansible content. By understanding how to create and use collections, you can streamline your automation workflows and share your work with others more effectively. Explore popular collections to leverage existing solutions and extend Ansible’s capabilities in your projects.
For more details click www.qcsdclabs.com
#redhatcourses#information technology#linux#containerorchestration#container#kubernetes#containersecurity#docker#dockerswarm#aws
2 notes
·
View notes
Text
Also idea: Program that checks your router and hacks into any IoT devices to make a distributed computer network. Computer running slow? Just distribute some of the workload to your fucking fridge!
2 notes
·
View notes
Text
Multiprotocol Label Switching (MPLS)
Multiprotocol Label Switching (MPLS) adalah sebuah teknologi jaringan yang digunakan untuk memindahkan lalu lintas data dari suatu titik ke titik lain dalam jaringan secara cepat dan efisien. MPLS menggabungkan beberapa teknologi jaringan seperti circuit switching dan packet switching sehingga memungkinkan jaringan untuk memprioritaskan lalu lintas data berdasarkan jenis aplikasi atau kepentingannya dalam suatu jaringan.
Dalam MPLS, setiap paket data yang masuk ke dalam jaringan diberi label atau tanda khusus yang menunjukkan rute yang harus diambil untuk mencapai tujuan akhir. Dengan cara ini, MPLS dapat memindahkan data dengan lebih cepat karena tidak perlu melakukan routing paket secara terus-menerus saat melewati setiap node jaringan. Selain itu, MPLS juga dapat memprioritaskan lalu lintas data yang lebih penting seperti video atau voice call untuk memastikan kualitas layanan yang lebih baik.
MPLS tidak mengharuskan suatu topologi jaringan tertentu karena MPLS bekerja di lapisan 2 dan 3 dalam model referensi OSI, sehingga dapat diimplementasikan pada berbagai topologi jaringan seperti ring, mesh, dan star. Namun, untuk mengilustrasikan contoh konfigurasi MPLS, berikut adalah topologi jaringan dasar yang menggunakan MPLS:
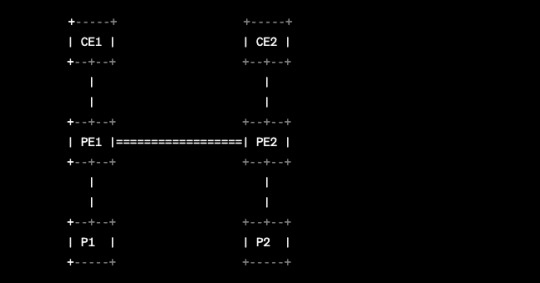
Pada topologi di atas, CE1 dan CE2 adalah customer edge routers yang terhubung ke provider edge routers PE1 dan PE2 melalui jalur Layer 2 atau Layer 3. Jalur ini disebut Virtual Private Wire Service (VPWS) untuk koneksi Layer 2 atau Virtual Private Network (VPN) untuk koneksi Layer 3. PE1 dan PE2 kemudian terhubung ke router core atau P routers, seperti P1 dan P2.
Untuk mengkonfigurasi MPLS pada topologi ini, beberapa langkah dasar yang perlu dilakukan adalah sebagai berikut:
Aktifkan fitur MPLS pada semua router di jaringan, yaitu CE1, CE2, PE1, PE2, P1, dan P2.
Atur label distribution protocol (LDP) pada semua router agar dapat saling mengenal dan membagikan label.
Terapkan label pada semua prefix (network address) di setiap router menggunakan LDP.
Atur penunjukan jalur (path) menggunakan label yang diberikan oleh LDP.
Terapkan MPLS traffic engineering jika diperlukan untuk memprioritaskan lalu lintas jaringan yang penting.
Langkah-langkah tersebut dapat diimplementasikan dengan menggunakan perangkat lunak router vendor tertentu, seperti Cisco IOS atau Juniper JunOS, yang biasanya memiliki konfigurasi MPLS yang mudah digunakan dan dipahami. Namun, karena MPLS merupakan teknologi jaringan yang kompleks, diperlukan pengetahuan dan pengalaman yang cukup untuk mengkonfigurasikannya dengan benar.
3 notes
·
View notes