#csrf
Explore tagged Tumblr posts
Text
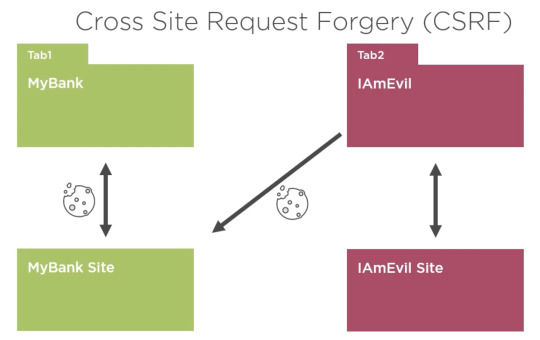
This graphic (in an online Angular course) amuses me. Of course, I know about CSRF, I've been a web developer as long as there have been web developers.
5 notes
·
View notes
Text
Securing PHP applications: Advanced techniques for preventing common vulnerabilities

This article delves into advanced security practices for PHP applications, focusing on input validation, CSRF protection, and secure session management to mitigate common vulnerabilities and enhance application security.Discover how to fortify your PHP applications against common threats with advanced security techniques.Introduction to PHP Application Security In the digital age, securing web applications is paramount, especially for those built with PHP, a language that powers a significant portion of the web. PHP applications are often targeted by attackers due to their widespread use and the potential vulnerabilities that can arise from improper coding practices. This article explores advanced techniques to safeguard PHP applications, focusing on three critical areas: input validation, CSRF protection, and secure session management. Input Validation: The First Line of Defense Input validation is crucial in preventing a wide array of attacks, including SQL injection, XSS (Cross-Site Scripting), and command injection. By ensuring that only properly formatted data is processed by your application, you can significantly reduce the risk of these vulnerabilities. PHP offers several functions and filters for input validation, such as filter_var() and htmlspecialchars(), which can be used to sanitize user inputs effectively. For example, to prevent SQL injection, always use prepared statements with parameterized queries. Here's a simple example using PDO (PHP Data Objects): $stmt = $pdo->prepare('SELECT * FROM users WHERE email = :email'); $stmt->execute(); $user = $stmt->fetch(); This approach ensures that the input is treated as a parameter and not as part of the SQL command, thereby preventing attackers from injecting malicious SQL code. CSRF Protection: Safeguarding Against Unauthorized Actions Cross-Site Request Forgery (CSRF) is an attack that tricks the victim into submitting a malicious request. It exploits the trust that a site has in the user's browser. To prevent CSRF attacks, it's essential to implement anti-CSRF tokens. These tokens are unique, secret, and unpredictable values that are generated by the server-side application and embedded within forms. When the form is submitted, the server verifies the token to ensure the request is legitimate. Here's how you can implement a basic CSRF token mechanism in PHP: session_start(); if (empty($_SESSION)) { $_SESSION = bin2hex(random_bytes(32)); } $csrf_token = $_SESSION; Include this token in your forms as a hidden field and validate it upon form submission to protect against CSRF attacks. Secure Session Management: Keeping User Data Safe Session management is another critical aspect of PHP application security. Poor session handling can lead to session hijacking and fixation attacks. To enhance session security, always regenerate the session ID after a successful login and use secure, HttpOnly cookies to store session IDs. Additionally, implement session expiration and enforce HTTPS to encrypt data in transit. Here’s an example of secure session handling in PHP: session_start(); if (!isset($_SESSION)) { session_regenerate_id(true); $_SESSION = true; } This code regenerates the session ID to prevent session fixation and marks the session as initiated to avoid unnecessary regeneration. Conclusion Securing PHP applications requires a comprehensive approach that addresses various potential vulnerabilities. By implementing robust input validation, CSRF protection, and secure session management, developers can significantly enhance the security of their applications. It's crucial for developers to stay updated with the latest security practices and continuously audit their code for potential vulnerabilities. Remember, security is not a one-time task but an ongoing process. Read the full article
0 notes
Text
Kas yra CSRF?
Šiuolaikiniame žiniatinklyje saugumas yra labai svarbus siekiant apsaugoti ir naudotojus, ir programas. Viena iš dažnai nepastebimų, bet pavojingų interneto pažeidimų yra kryžminės svetainės užklausos klastojimas (Cross-Site Request Forgery, CSRF). Nors tai gali skambėti sudėtingai, CSRF sąvoka yra stebėtinai paprasta: ji apgaule priverčia naudotoją atlikti veiksmus, kurių jis nenumatė, dažnai jam nežinant.
Įsivaizduokite tokį scenarijų: esate prisijungę prie banko svetainės ir pasiruošę tvarkyti savo sąskaitas. Tuo tarpu kitame skirtuke apsilankote nekaltai atrodančioje svetainėje. Jums nežinant, ta svetainė slapta siunčia užklausą jūsų bankui ir perveda lėšas į užpuoliko sąskaitą. Kadangi jau esate prisijungę, bankas mano, kad užklausa yra teisėta, ir operacija įvykdoma. Tokia yra CSRF galia.
Šiame blog'e bus rašoma informaciją, kas lemia CSRF atakų galimybę, kaip jos gali būti vykdomos ir, svarbiausia, kaip galite apsaugoti savo programas, kad jos netaptų šios tylios grėsmės aukomis. Nesvarbu, ar esate kūrėjas, siekiantis apsaugoti savo svetainę, ar naudotojas, kuriam rūpi internetinis saugumas, CSRF supratimas yra labai svarbus žingsnis saugesnės patirties link.
0 notes
Text
Securing Django Applications
Learn how to secure your Django applications with this comprehensive guide. Follow best practices for secure configurations, user authentication, preventing common threats, and more.
Introduction Security is a critical aspect of web application development. Django, being a high-level Python web framework, comes with numerous built-in security features and best practices. However, developers must be aware of additional steps to ensure their applications are secure. This guide will cover essential security practices for securing Django applications, including setting up secure…

View On WordPress
#best practices#CSRF#Django#HTTPS#secure coding#Security#SQL injection prevention#user authentication#web development#XSS
0 notes
Text
Navigating the Risks of JavaScript in Web Development
JavaScript is the linchpin of interactive web experiences, fueling everything from form validation to video streaming. While JavaScript enriches user engagement, it also raises significant security considerations. This post examines JavaScript's potential for misuse and the best practices to mitigate these risks.
The Dual Facets of JavaScript
JavaScript’s ability to execute on the client side is a bedrock feature of dynamic web pages, empowering developers to script complex features and responsive user interfaces. Unfortunately, the same capabilities that streamline user experience can also be exploited for malicious purposes.
Potential Misuse Cases
Malicious actors can leverage JavaScript for a range of harmful activities, including:
Data Theft: Scripts can covertly transmit personal data to unauthorized parties.
Session Hijacking: Exploiting cookies or session tokens to impersonate users.
Malware Distribution: Executing scripts that install harmful software on users' devices.
Understanding misuse scenarios is the first step in fortifying web applications against such threats.
Notable Attack Vectors: XSS and CSRF
The two most prevalent JavaScript-based threats are Cross-Site Scripting (XSS) and Cross-Site Request Forgery (CSRF). Each exploit different aspects of web application interaction with the user.
Cross-Site Scripting (XSS)
XSS attacks involve inserting malicious scripts into otherwise benign web pages. These scripts activate when unsuspecting users interact with the web pages, leading to unauthorized actions or data exposure.
Defense Strategy:
Input Encoding: Systematically encode user-generated content before displaying it on the web, effectively defanging embedded scripts.
Use of CSP: Employ a Content Security Policy to specify legitimate sources for executable scripts and resources.
Cross-Site Request Forgery (CSRF)
In CSRF attacks, attackers con the victim's browser into performing unintended actions on a site where the victim is authenticated, ranging from changing a user profile to initiating financial transactions.
Defense Strategy:
Anti-CSRF Tokens: Deploy one-time tokens that must accompany each form submission, ensuring requests originate from the site's own pages.
Cookie Attributes: Set 'SameSite' attributes on cookies to limit their flow to requests originating from the site that set them.
Building Defenses into JavaScript
Deploying defensive coding practices is essential to protect against the weaponization of JavaScript. Here are tactics developers can leverage:
Input Validation and Sanitization
Vigilant validation and sanitization of user input are fundamental:
// Validate acceptable characters (e.g., alphanumeric for a username) function isValidUsername(username) { return /^[a-zA-Z0-9]+$/.test(username); }
Implementing a Content Security Policy (CSP)
CSP can significantly reduce the success rate of XSS attacks:
Content-Security-Policy: default-src 'self'; script-src 'self' https://trusted.cdn.com;
Managing Cookie Security
Correctly setting cookie attributes can prevent CSRF:
document.cookie = "sessionToken=xyz123; Secure; HttpOnly; SameSite=Strict";
Enlisting Users in Their Defense
While technical defenses are critical, empowering users to protect themselves can add another layer of security:
Educate Users: Regularly inform users on the importance of browser updates, installing security extensions, and recognizing phishing attempts.
Enable Security Features: Encourage users to install Firefox and use privacy-focused Browser extensions like uBlock Origin.
Conclusion
JavaScript's agility is a double-edged sword; its seamless integration into web pages can also serve nefarious purposes. Recognizing the potential for misuse compels us to employ rigorous defensive measures. Whether through stringent input handling, careful session management, or leveraging robust browser security features, a proactive approach to JavaScript security is the greatest defense against its weaponization. As technologies advance and threats evolve, so too must our strategies for maintaining web security and user trust.
#ko-fi#kofi#geeknik#nostr#art#blog#writing#twitter#xss#csrf#javascript#web development#dev#coding#programming#csp#content security policy#cross site scripting#information security#security#secure coding#infosec
1 note
·
View note
Text
In an era where the exchange of data across the web has become ubiquitous, safeguarding the integrity and security of web applications is paramount. Among the array of vulnerabilities that can threaten the trustworthiness of these applications, Cross-Site Request Forgery (CSRF) stands as a particularly insidious adversary. By the end of this comprehensive guid, you will possess the knowledge and tools to fortify your web applications against CSRF threats effectively.
0 notes
Text
Application Security : CSRF
Cross Site Request Forgery allows an attacker to capter or modify information from an app you are logged to by exploiting your authentication cookies.
First thing to know : use HTTP method carefully. For instance GET shoud be a safe method with no side effect. Otherwise a simple email opening or page loading can trigger the exploit of an app vulnerability
PortSwigger has a nice set of Labs to understand csrf vulnerabilities : https://portswigger.net/web-security/csrf
Use of CSRF protections in web frameworks
Nuxt
Based on express-csurf. I am not certain of potential vulnerabilities. The token is set in a header and the secret to validate the token in a cookie
Django
0 notes
Link
This article will show you how to set up an Http4s server to correctly protect against cross-origin requests and CSRF.
0 notes
Text
[tumblr] api won't let me retrieve messages i've sent, even though i can clearly see [tumblr] itself calling the same api endpoint when it retrieves messages
#/v2/conversations/messages#[tumblr]#programming#is it like csrf or is it just not available to third parties
7 notes
·
View notes
Text
>article called Demystifying CORS, CSRF tokens, SameSite & Clickjacking - Web Security
>look inside
>still mystifying
9 notes
·
View notes
Note
how do i... boopbeam.......
I AM SO GLAD YOU ASKED
HOW TO BOOPBEAM UNDER THE CUT

STRAP IN BOYS THIS IS GONNA BE A LONG ONE
ok so.
you need Bun. It's a JavaScript runtime for the server (your computer). It's what runs the little script I made that automates the booping. Copy-paste the little one-liner into your terminal of choice and hit enter.
2. download this file here. THIS IS THE BOOPINATOR!
3. You'll need a couple pieces of information. What you want to do is go to tumblr.com on a computer, then open up the developer tools. Usually Ctrl (or Cmd) + Shift + I (that's an eye). Head to the tab labelled Network.
4. With the network tab open, boop somebody! However you do it. Either by the boop button next to their name, or the paw icon on their profile. Boop somebody!
5. You should see a new entry in the Network tab labeled "boop". Click on it.
6. You should see a bunch of new tabs to the side. One of them will be named "Headers". Click on that if it isn't already selected.
7. Scroll down to where it says "Request Headers" (NOT RESPONSE HEADERS!) and copy THREE values into the boopinator.ts file you downloaded: • Your "Cookie". Copy that whole value into line 39; replace the bit where it says "YOUR COOKIE HERE" (and keep the quotes!) • Your "Authorization". Copy that whole value (including the "Bearer") into line 38; replace the bit that says "YOUR TOKEN HERE (starts with Bearer)" (and keep the quotes!) • Your "X-Csrf". Copy that value into line 85; replace the bit where it says "FIRST CSRF TOKEN" (and keep the quotes!).
I cannot stress this enough these three values are extremely sensitive and should not be shared ever.
8. In a terminal, navigate to the directory you downloaded boopinator.ts (usually with the cd command) Run: bun boopinator.ts and it *should* start going! Optional 9. You can replace the URLs at the top of the file with the URLs of the people you wanna boop. The script will choose between them at random every time it boops somebody, which is about once per second.
🎉 CONGRATULATIONS you have started the boopbeam! It should now run forever, assuming Tumblr doesn't cut you off. They will eventually, your cookie will expire, but that should be good for about 1000 boops. Occasionally you'll get hit with a 429 error; the script will recover from that automatically, but any other error will cause it to stop in its tracks and wait for you to restart it. An authorization error, for example, means you need to grab those three values again (see step 7).
If you have any questions, my DMs should be open? Or just reblog this post with your question and I'll clarify as much as I can.
15 notes
·
View notes
Text
Laravel Là Gì?
Laravel là một framework PHP mã nguồn mở được thiết kế để phát triển các ứng dụng web theo kiến trúc MVC (Model-View-Controller). Ra mắt lần đầu vào năm 2011 bởi Taylor Otwell, Laravel nhanh chóng trở thành một trong những framework phổ biến nhất trong cộng đồng lập trình PHP nhờ sự đơn giản, mạnh mẽ và linh hoạt.

Laravel cung cấp một loạt các công cụ và tính năng hữu ích, giúp tăng tốc và tối ưu hóa quá trình phát triển phần mềm. Một số tính năng nổi bật của Laravel bao gồm hệ thống định tuyến mạnh mẽ, ORM (Eloquent) để làm việc với cơ sở dữ liệu, hệ thống migration để quản lý database, và các công cụ tích hợp như Artisan CLI (dòng lệnh) hỗ trợ tự động hóa nhiều tác vụ.
Ngoài ra, Laravel còn hỗ trợ việc bảo mật với các cơ chế như xác thực người dùng, mã hóa, và bảo vệ ứng dụng khỏi các lỗ hổng bảo mật phổ biến (CSRF, SQL Injection). Đặc biệt, Laravel đi kèm với Blade – một công cụ tạo giao diện thân thiện và hiệu quả.
Với hệ sinh thái phong phú như Laravel Forge, Nova, và Envoyer, framework này không chỉ phù hợp cho các ứng dụng nhỏ mà còn mạnh mẽ đủ để phát triển các hệ thống lớn, phức tạp. Laravel là lựa chọn lý tưởng cho các lập trình viên PHP muốn xây dựng các ứng dụng nhanh chóng và chuyên nghiệp.
Nguồn: https://thuegpu.vn/laravel-la-gi-cai-dat-va-cau-hinh-laravel-voi-nginx-tren-ubuntu/
2 notes
·
View notes
Text
Honestly my script is pretty good at this point, the only thing I don't understand is how to get the csrf token value without manually grabbing it from the browser
12 notes
·
View notes
Text
Prevent Session Replay Attacks in Laravel: Best Practices
Introduction
Session replay attacks are a major security risk in web applications, especially in frameworks like Laravel. These attacks can lead to unauthorized access or compromise sensitive user data. In this blog post, we will explore what session replay attacks are, how they occur in Laravel applications, and most importantly, how to prevent them using best practices. We’ll also share a practical coding example to help you implement secure session handling in your Laravel app.

What is a Session Replay Attack?
A Session Replay Attack occurs when an attacker intercepts or steals a valid session ID and reuses it to impersonate the legitimate user. This type of attack exploits the session handling mechanism of web applications and can allow attackers to gain unauthorized access to sensitive information or perform actions on behalf of the user.
In Laravel, session management is a critical aspect of maintaining security, as Laravel uses cookies and sessions to store user authentication and other sensitive data. If the session management is not properly secured, attackers can easily exploit it.
How Session Replay Attacks Work in Laravel
Session replay attacks typically work by capturing a valid session cookie, either through methods like Cross-Site Scripting (XSS) or Man-in-the-Middle (MITM) attacks, and replaying it in their own browser. In Laravel, the session data is stored in cookies by default, so if the attacker gains access to a session cookie, they can replay the session request and hijack the user’s session.
To demonstrate this risk, let’s take a look at how a session ID might be captured and replayed:
// Example of a Laravel session where sensitive information might be stored session(['user_id' => 1, 'role' => 'admin']);
If an attacker intercepts the session cookie (usually via XSS or another method), they could replay the request and access sensitive data or perform admin-level actions.
How to Prevent Session Replay Attacks in Laravel
1. Use HTTPS Everywhere
Ensure that your Laravel application enforces HTTPS to protect session cookies from being intercepted in transit. HTTP traffic is unencrypted, so it's easy for attackers to sniff session cookies. By forcing HTTPS, all communications between the client and server are encrypted.
To enforce HTTPS in Laravel, add this to your AppServiceProvider:
public function boot() { if (env('APP_ENV') !== 'local') { \URL::forceScheme('https'); } }
This will ensure that Laravel always generates URLs using HTTPS.
2. Regenerate Session IDs After Login
One effective way to prevent session hijacking and replay attacks is to regenerate the session ID after the user logs in. This ensures that attackers cannot reuse a session ID that was valid before the login.
In Laravel, you can regenerate the session ID using the following code:
public function authenticated(Request $request, $user) { $request->session()->regenerate(); }
This should be added in your LoginController to regenerate the session after a successful login.
3. Set Secure and HttpOnly Flags on Cookies
Ensure that your session cookies are marked as Secure and HttpOnly. The Secure flag ensures that the cookie is only sent over HTTPS, and the HttpOnly flag prevents JavaScript from accessing the cookie.
In Laravel, you can configure this in the config/session.php file:
'secure' => env('SESSION_SECURE_COOKIE', true), 'http_only' => true,
These settings help protect your session cookies from being stolen via JavaScript or man-in-the-middle attacks.
4. Use SameSite Cookies
The SameSite cookie attribute can help mitigate Cross-Site Request Forgery (CSRF) attacks and prevent the session from being sent in cross-site requests. You can set it in the session configuration:
'samesite' => 'Strict',
This ensures that the session is only sent in requests originating from the same domain, thus reducing the risk of session replay attacks.
5. Enable Session Expiry
You can also mitigate session replay attacks by setting an expiration time for your sessions. Laravel allows you to define the lifetime of your session in the config/session.php file:
'lifetime' => 120, // in minutes 'expire_on_close' => true,
Setting an expiration time ensures that even if a session ID is captured, it will only be valid for a limited period.
Coding Example for Secure Session Handling
Here’s a full example demonstrating how to implement some of these best practices to prevent session replay attacks in Laravel:
// Middleware to regenerate session on each request public function handle($request, Closure $next) { // Regenerate session ID session()->regenerate(); // Set secure cookies config(['session.secure' => true]); config(['session.http_only' => true]); return $next($request); }
By including this middleware in your Laravel app, you can regenerate session IDs on every request and ensure secure cookie handling.
Using the Free Website Security Checker Tool
If you’re unsure whether your Laravel application is susceptible to session replay attacks or other security issues, you can use the Website Vulnerability Scanner tool. This tool analyzes your website for vulnerabilities, including insecure session management, and provides actionable insights to improve your app’s security.

Screenshot of the free tools webpage where you can access security assessment tools.
The free tool provides a comprehensive security analysis that helps you identify and mitigate potential security risks.
Conclusion
Session replay attacks are a serious security threat, but by implementing the best practices discussed above, you can effectively protect your Laravel application. Make sure to use HTTPS, regenerate session IDs after login, and properly configure session cookies to minimize the risk of session hijacking.
To check if your Laravel app is vulnerable to session replay attacks or other security flaws, try out our free Website Security Scanner tool.
For more security tips and blog updates, visit our blog at PentestTesting Blog.

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
By following these security best practices and using the tools available at PentestTesting.com, you can enhance the security of your Laravel application and protect it from session replay attacks.
1 note
·
View note
Text
Build a Seamless Crypto Exchange Experience with Binance Clone Software

Binance Clone Script
The Binance clone script is a fully functional, ready-to-use solution designed for launching a seamless cryptocurrency exchange. It features a microservice architecture and offers advanced functionalities to enhance user experience. With Plurance’s secure and innovative Binance Clone Software, users can trade bitcoins, altcoins, and tokens quickly and safely from anywhere in the world.
This clone script includes essential features such as liquidity APIs, dynamic crypto pairing, a comprehensive order book, various trading options, and automated KYC and AML verifications, along with a core wallet. By utilizing our ready-to-deploy Binance trading clone, business owners can effectively operate a cryptocurrency exchange platform similar to Binance.
Features of Binance Clone Script
Security Features
AML and KYC Verification: Ensures compliance with anti-money laundering and know-your-customer regulations.
Two-Factor Authentication: Provides an additional security measure during user logins.
CSRF Protection: Shields the platform from cross-site request forgery threats.
DDoS Mitigation: Safeguards the system against distributed denial-of-service attacks.
Cloudflare Integration: Enhances security and performance through advanced web protection.
Time-Locked Transactions: Safeguards transactions by setting time limits before processing.
Cold Wallet Storage: Keeps the majority of funds offline for added security.
Multi-Signature Wallets: Mandates multiple confirmations for transactions, boosting security.
Notifications via Email and SMS: Keeps users informed of account activities and updates.
Login Protection: Monitors login attempts to detect suspicious activity.
Biometric Security: Utilizes fingerprint or facial recognition for secure access.
Data Protection Compliance: Adheres to relevant data privacy regulations.
Admin Features of Binance Clone Script
User Account Management: Access detailed user account information.
Token and Cryptocurrency Management: Add and manage various tokens and cryptocurrencies.
Admin Dashboard: A comprehensive interface for managing platform operations.
Trading Fee Setup: Define and adjust trading fees for transactions.
Payment Gateway Integration: Manage payment processing options effectively.
AML and KYC Oversight: Monitor compliance processes for user verification.
User Features of Binance Clone Script
Cryptocurrency Deposits: Facilitate easy deposit of various cryptocurrencies.
Instant Buy/Sell Options: Allow users to trade cryptocurrencies seamlessly.
Promotional Opportunities: Users can take advantage of promotional features to maximize profits.
Transaction History: Access a complete record of past transactions.
Cryptocurrency Wallet Access: Enable users to manage their digital wallets.
Order Tracking: Keep track of buy and sell orders for better trading insights.
Binance Clone Development Process
The following way outline how our blockchain experts develop a largely effective cryptocurrency exchange platform inspired by Binance.
Demand Analysis
We begin by assessing and gathering your business conditions, similar as the type of trades you want to grease, your target followership, geographical focus, and whether the exchange is intended for short-term or long-term operation.
Strategic Planning
After collecting your specifications, our platoon formulates a detailed plan to effectively bring your ideas to life. This strategy aims to deliver stylish results acclimatized to your business requirements.
Design and Development
Our inventors excel in UI/ UX design, creating visually appealing interfaces. They draft a unique trading platform by exercising the rearmost technologies and tools.
Specialized perpetration
Once the design is complete, we concentrate on specialized aspects, integrating essential features similar to portmanteau connectors, escrow services, payment options, and robust security measures to enhance platform functionality.
Quality Assurance Testing
After development, we conduct thorough testing to ensure the exchange platform operates easily. This includes security assessments, portmanteau and API evaluations, performance testing, and vindicating the effectiveness of trading machines.
Deployment and Support
Following successful testing, we do with the deployment of your exchange platform. We also gather stoner feedback to make advancements and introduce new features, ensuring the platform remains robust and over-to-date.
Revenue Streams of a Binance Clone Script
Launching a cryptocurrency exchange using a robust Binance clone can create multiple avenues for generating revenue.
Trading Fees
The operator of the Binance clone platform has the discretion to set a nominal fee on each trade executed.
Withdrawal Charges
If users wish to withdraw their cryptocurrencies, a fee may be applied when they request to transfer funds out of the Binance clone platform.
Margin Trading Fees
With the inclusion of margin trading functionalities, fees can be applied whenever users execute margin transactions on the platform.
Listing Fees
The platform owner can impose a listing fee for users who want to feature their cryptocurrencies or tokens on the exchange.
Referral Program
Our Binance clone script includes a referral program that allows users to earn commissions by inviting friends to register on the trading platform.
API Access Fees
Developers can integrate their trading bots or other applications by paying for access to the platform’s API.
Staking and Lending Fees
The administrator has the ability to charge fees for services that enable users to stake or lend their cryptocurrencies to earn interest.
Launchpad Fees
The Binance clone software offers a token launchpad feature, allowing the admin to charge for listing and launching new tokens.
Advertising Revenue
Similar to Binance, the trading platform can also generate income by displaying advertisements to its users.
Your Path to Building a Crypto Exchange Like Binance
Take the next step toward launching your own crypto exchange similar to Binance by collaborating with our experts to establish a robust business ecosystem in the cryptocurrency realm.
Token Creation
Utilizing innovative fundraising methods, you can issue tokens on the Binance blockchain, enhancing revenue generation and providing essential support for your business.
Staking Opportunities
Enable users to generate passive income by staking their digital assets within a liquidity pool, facilitated by advanced staking protocols in the cryptocurrency environment.
Decentralized Swapping
Implement a DeFi protocol that allows for the seamless exchange of tokenized assets without relying on a central authority, creating a dedicated platform for efficient trading.
Lending and Borrowing Solutions
Our lending protocol enables users to deposit funds and earn annual returns, while also offering loans for crypto trading or business ventures.
NFT Minting
Surpass traditional cryptocurrency investments by minting a diverse range of NFTs, representing unique digital assets such as sports memorabilia and real estate, thereby tapping into new market values.
Why Should You Go With Plurance's Ready-made Binance Clone Script?
As a leading cryptocurrency exchange development company, Plurance provides an extensive suite of software solutions tailored for cryptocurrency exchanges, including Binance scripts, to accommodate all major platforms in the market. We have successfully assisted numerous businesses and entrepreneurs in launching profitable user-to-admin cryptocurrency exchanges that rival Binance.
Our team consists of skilled front-end and back-end developers, quality analysts, Android developers, and project engineers, all focused on bringing your vision to life. The ready-made Binance Clone Script is meticulously designed, developed, tested, and ready for immediate deployment.
Our committed support team is here to help with any questions you may have about the Binance clone software. Utilizing Binance enables you to maintain a level of customization while accelerating development. As the cryptocurrency sector continues to evolve, the success of your Binance Clone Script development will hinge on its ability to meet customer expectations and maintain a competitive edge.
#Binance Clone Script#Binance Clone Software#White Label Binance Clone Software#Binance Exchange Clone Script
2 notes
·
View notes
Text
As a Cyber Security Expert, I will provide penetration Testing and WordPress Malware Removal services. Those are my best and strongest skills. I can combine the power of manual and automated penetration tests to remove all types of malware and viruses from any WordPress website.
My Services on penetration testing:
✅I will test File Uploads, SQL injection, XSS, CSRF, Authentication, Access Control, Information Disclosure, RFI, RCE, LFI, Brute Force, SSRF, and many more Bugs.
✅I will test your website and give you a professional and premium testing report that help you fix this vulnerability.
✅Network devices (Servers, switches, routers) Penetration Testing services.
✅I will test manual and automated both.
✅Mobile Application Penetration Testing.
My services for WordPress Malware Removal:
✅I will remove all types of malware and viruses from hacked WordPress websites
✅fix redirect issues where the website redirects to another website and URLs.
✅remove malware from the server of C-Panel
✅Reactive suspended hosting account.
✅Remove Japanese or Chinese Spam Links.
✅Remove all backdoors and phishing scripts.
✅Install many security plugins.
✅Updates all Plugins and Themes on your website.
Why work with me:
⭐️I will use multiple vulnerability scanners.
⭐️Provide unlimited modifications and retesting for the issues that have been fixed.
⭐️No false Positives on the Report and give the recommendations.
⭐️On-time delivery.
Me on Fiverr: https://www.fiverr.com/safety_hub?up_rollout
Let me work with you. I am a professional cybersecurity specialist with 3years of experience. I will give you the best service. I hope you will be satisfied.
Thank You.
4 notes
·
View notes