#SQL injection prevention
Explore tagged Tumblr posts
Text
How to Protect Your WordPress Database from Cyber Threats
Introduction Your WordPress database is the backbone of your website, storing critical data such as user information, posts, pages, comments, and settings. If compromised, your site could suffer data breaches, downtime, or even total loss of content. Cyber threats like SQL injections, brute force attacks, malware infections, and unauthorized access can put your database at serious…
#brute force attack protection#database backup#database security#limit login attempts#malware scanning#optimize wordpress database#secure wp-config#SQL injection prevention#two-factor authentication#web application firewall#wordpress cybersecurity#wordpress database protection#wordpress firewall#wordpress security
0 notes
Text
Securing Django Applications
Learn how to secure your Django applications with this comprehensive guide. Follow best practices for secure configurations, user authentication, preventing common threats, and more.
Introduction Security is a critical aspect of web application development. Django, being a high-level Python web framework, comes with numerous built-in security features and best practices. However, developers must be aware of additional steps to ensure their applications are secure. This guide will cover essential security practices for securing Django applications, including setting up secure…

View On WordPress
#best practices#CSRF#Django#HTTPS#secure coding#Security#SQL injection prevention#user authentication#web development#XSS
0 notes
Text
It's been a month since chapter 3 was released, where's chapter 4?
(this is about this fanfic btw)
The good news is that I've written 10k words. The bad news is that I've only gotten a little more than half of the chapter done. That doesn't mean I don't have things written for the bottom half, it's just that it looks like bare dialog with general vibe notes. I estimate around 16k words total though, so it should come together sooner than later.
SO I want to release some fun snippets for y'all to look at. Please note that any of this is liable to change. Also, you can harass me in my inbox for updates. I love answering your questions and laughing at your misery.
Spoilers under cut.
_______
Ragatha stood up and walked over to where Caine was seated. “Can I get a list of all commands?” She asked, only a hint of nervousness in her voice.
“Certainly!” Caine says as he blasts into the air. He digs around in his tailcoat and pulls out an office style manilla folder. It visually contains a few papers, but with how thin it is there must only be a few pages inside.
Ragatha takes the folder from Caine and opens it.
“Oh boy” she says after a second of looking it over.
“I wanna see” Jax exclaimed as he hops over the row of seats.
“Hold on” Ragatha holds the folder defensively “Let’s move to the stage so everyone can take a look”
Jax hopped over the seats again while Ragatha calmly walked around. Caine watched the two curiously.
Well, Zooble wasn’t just going to sit there. They joined the other two by the edge of the stage, quickly followed by the rest of the group.
Ragatha placed the folder on the stage with a thwap. Zooble looked over to see that the pages had gone from razor thin to a massive stack when the folder was opened. On one hand, it had to contain more information than that video, but on the other…
They get close enough to read what’s on the first page.
The execution of commands via the system’s designated input terminal, C.A.I.N.E., will be referred to as the "console” in this document. The console is designed to accept any input and will generate an appropriate response, however only certain prompts will be accepted as valid instructions. The goal of this document is to list all acceptable instructions in a format that will result in the expected output. Please note that automatic moderation has been put in place in order to prevent exploitation of both the system and fellow players. If you believe that your command has been unfairly rejected, please contact support.
By engaging in the activities described in this document, you, the undersigned, acknowledge, agree, and consent to the applicability of this agreement, notwithstanding any contradictory stipulations, assumptions, or implications which may arise from any interaction with the console. You, the constituent, agree not to participate in any form of cyber attack; including but not limited to, direct prompt injection, indirect prompt injection, SQL injection, Jailbreaking…
Ok, that was too many words.
_______
“Take this document for example. You don't need to know where it is being stored or what file type it is in order to read it."
"It may look like a bunch of free floating papers, but technically speaking, this is just a text file applied to a 3D shape." Kinger looked towards Caine. "Correct?” he asked
Caine nodded. “And a fabric simulation!”
Kinger picked up a paper and bent it. “Oh, now that is nice”
_________
"WE CAN AFFORD MORE THAN 6 TRIANGLES KINGER"
_________
"I'm too neurotypical for this" - Jax
_________
"What about the internet?" Pomni asked "Do you think that it's possible to reach it?"
Kinger: "I'm sorry, but that's seems to be impossible. I can't be 100% sure without physically looking at the guts of this place, but it doesn't look like this server has the hardware needed for wireless connections. Wired connections should be possible, but someone on the outside would need to do that... And that's just the hardware, let alone the software necessary for that kind of communication"
Pomni: "I'm sorry, but doesn't server mean internet? Like, an internet server?"
Kinger: "Yes, websites are ran off servers, but servers don't equal internet."
(This portion goes out to everyone who thought that the internet could be an actual solution. Sorry folks, but computers don't equal internet. It takes more effort to make a device that can connect to things than to make one that can't)
#tadc fanfiction#the amazing digital circus#therapy but it's just zooble interrogating caine#ao3#spoiler warning#mmm I love implications
26 notes
·
View notes
Text

Bobby Tables, or, the website about preventing SQL injection hacks.
Tal's up to something. Ke's absolutely going to fuck up Mama somehow by feeding her seemingly harmless info.
41 notes
·
View notes
Note
https://www.tumblr.com/gjjuddmk2/766153411306700800
#already ahead of you#Tumblr's search and archive features really suck don't they?#happy to answer asks
7 notes
·
View notes
Text
LETS FUCKING GOOOO I JUST CHECKED IF MY DATABASES FINAL PROJECT IS GRADED AND IT IS
I expected 145/200
I got 190/200
This has been a great first day home
The worst part of coming home is the fucking fur. EVERYWHERE. From 3 cats living in my messy room alone for over a year (over a year because I never actually got around to cleaning my room last summer either)
#rambles#the best part is there were short response questions:#'describe how you use transactions in your project' 'i didn't.'#'describe how you prevent sql injection' 'i didn't'#full points on both of those.#(i explained that i tried to do the first thing and everything broke and i didn't have time to fix it)
4 notes
·
View notes
Text
Symfony Clickjacking Prevention Guide
Clickjacking is a deceptive technique where attackers trick users into clicking on hidden elements, potentially leading to unauthorized actions. As a Symfony developer, it's crucial to implement measures to prevent such vulnerabilities.

🔍 Understanding Clickjacking
Clickjacking involves embedding a transparent iframe over a legitimate webpage, deceiving users into interacting with hidden content. This can lead to unauthorized actions, such as changing account settings or initiating transactions.
🛠️ Implementing X-Frame-Options in Symfony
The X-Frame-Options HTTP header is a primary defense against clickjacking. It controls whether a browser should be allowed to render a page in a <frame>, <iframe>, <embed>, or <object> tag.
Method 1: Using an Event Subscriber
Create an event subscriber to add the X-Frame-Options header to all responses:
// src/EventSubscriber/ClickjackingProtectionSubscriber.php namespace App\EventSubscriber; use Symfony\Component\EventDispatcher\EventSubscriberInterface; use Symfony\Component\HttpKernel\Event\ResponseEvent; use Symfony\Component\HttpKernel\KernelEvents; class ClickjackingProtectionSubscriber implements EventSubscriberInterface { public static function getSubscribedEvents() { return [ KernelEvents::RESPONSE => 'onKernelResponse', ]; } public function onKernelResponse(ResponseEvent $event) { $response = $event->getResponse(); $response->headers->set('X-Frame-Options', 'DENY'); } }
This approach ensures that all responses include the X-Frame-Options header, preventing the page from being embedded in frames or iframes.
Method 2: Using NelmioSecurityBundle
The NelmioSecurityBundle provides additional security features for Symfony applications, including clickjacking protection.
Install the bundle:
composer require nelmio/security-bundle
Configure the bundle in config/packages/nelmio_security.yaml:
nelmio_security: clickjacking: paths: '^/.*': DENY
This configuration adds the X-Frame-Options: DENY header to all responses, preventing the site from being embedded in frames or iframes.
🧪 Testing Your Application
To ensure your application is protected against clickjacking, use our Website Vulnerability Scanner. This tool scans your website for common vulnerabilities, including missing or misconfigured X-Frame-Options headers.

Screenshot of the free tools webpage where you can access security assessment tools.
After scanning for a Website Security check, you'll receive a detailed report highlighting any security issues:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🔒 Enhancing Security with Content Security Policy (CSP)
While X-Frame-Options is effective, modern browsers support the more flexible Content-Security-Policy (CSP) header, which provides granular control over framing.
Add the following header to your responses:
$response->headers->set('Content-Security-Policy', "frame-ancestors 'none';");
This directive prevents any domain from embedding your content, offering robust protection against clickjacking.
🧰 Additional Security Measures
CSRF Protection: Ensure that all forms include CSRF tokens to prevent cross-site request forgery attacks.
Regular Updates: Keep Symfony and all dependencies up to date to patch known vulnerabilities.
Security Audits: Conduct regular security audits to identify and address potential vulnerabilities.
📢 Explore More on Our Blog
For more insights into securing your Symfony applications, visit our Pentest Testing Blog. We cover a range of topics, including:
Preventing clickjacking in Laravel
Securing API endpoints
Mitigating SQL injection attacks
🛡️ Our Web Application Penetration Testing Services
Looking for a comprehensive security assessment? Our Web Application Penetration Testing Services offer:
Manual Testing: In-depth analysis by security experts.
Affordable Pricing: Services starting at $25/hr.
Detailed Reports: Actionable insights with remediation steps.
Contact us today for a free consultation and enhance your application's security posture.
3 notes
·
View notes
Text
How to Prevent

Preventing injection requires keeping data separate from commands and queries:
The preferred option is to use a safe API, which avoids using the interpreter entirely, provides a parameterized interface, or migrates to Object Relational Mapping Tools (ORMs). Note: Even when parameterized, stored procedures can still introduce SQL injection if PL/SQL or T-SQL concatenates queries and data or executes hostile data with EXECUTE IMMEDIATE or exec().
Use positive server-side input validation. This is not a complete defense as many applications require special characters, such as text areas or APIs for mobile applications.
For any residual dynamic queries, escape special characters using the specific escape syntax for that interpreter. (escaping technique) Note: SQL structures such as table names, column names, and so on cannot be escaped, and thus user-supplied structure names are dangerous. This is a common issue in report-writing software.
Use LIMIT and other SQL controls within queries to prevent mass disclosure of records in case of SQL injection.
bonus question: think about how query on the image above should look like? answer will be in the comment section
4 notes
·
View notes
Text
Key Programming Languages Every Ethical Hacker Should Know
In the realm of cybersecurity, ethical hacking stands as a critical line of defense against cyber threats. Ethical hackers use their skills to identify vulnerabilities and prevent malicious attacks. To be effective in this role, a strong foundation in programming is essential. Certain programming languages are particularly valuable for ethical hackers, enabling them to develop tools, scripts, and exploits. This blog post explores the most important programming languages for ethical hackers and how these skills are integrated into various training programs.
Python: The Versatile Tool
Python is often considered the go-to language for ethical hackers due to its versatility and ease of use. It offers a wide range of libraries and frameworks that simplify tasks like scripting, automation, and data analysis. Python’s readability and broad community support make it a popular choice for developing custom security tools and performing various hacking tasks. Many top Ethical Hacking Course institutes incorporate Python into their curriculum because it allows students to quickly grasp the basics and apply their knowledge to real-world scenarios. In an Ethical Hacking Course, learning Python can significantly enhance your ability to automate tasks and write scripts for penetration testing. Its extensive libraries, such as Scapy for network analysis and Beautiful Soup for web scraping, can be crucial for ethical hacking projects.
JavaScript: The Web Scripting Language
JavaScript is indispensable for ethical hackers who focus on web security. It is the primary language used in web development and can be leveraged to understand and exploit vulnerabilities in web applications. By mastering JavaScript, ethical hackers can identify issues like Cross-Site Scripting (XSS) and develop techniques to mitigate such risks. An Ethical Hacking Course often covers JavaScript to help students comprehend how web applications work and how attackers can exploit JavaScript-based vulnerabilities. Understanding this language enables ethical hackers to perform more effective security assessments on websites and web applications.
Biggest Cyber Attacks in the World
youtube
C and C++: Low-Level Mastery
C and C++ are essential for ethical hackers who need to delve into low-level programming and system vulnerabilities. These languages are used to develop software and operating systems, making them crucial for understanding how exploits work at a fundamental level. Mastery of C and C++ can help ethical hackers identify and exploit buffer overflows, memory corruption, and other critical vulnerabilities. Courses at leading Ethical Hacking Course institutes frequently include C and C++ programming to provide a deep understanding of how software vulnerabilities can be exploited. Knowledge of these languages is often a prerequisite for advanced penetration testing and vulnerability analysis.
Bash Scripting: The Command-Line Interface
Bash scripting is a powerful tool for automating tasks on Unix-based systems. It allows ethical hackers to write scripts that perform complex sequences of commands, making it easier to conduct security audits and manage multiple tasks efficiently. Bash scripting is particularly useful for creating custom tools and automating repetitive tasks during penetration testing. An Ethical Hacking Course that offers job assistance often emphasizes the importance of Bash scripting, as it is a fundamental skill for many security roles. Being proficient in Bash can streamline workflows and improve efficiency when working with Linux-based systems and tools.
SQL: Database Security Insights
Structured Query Language (SQL) is essential for ethical hackers who need to assess and secure databases. SQL injection is a common attack vector used to exploit vulnerabilities in web applications that interact with databases. By understanding SQL, ethical hackers can identify and prevent SQL injection attacks and assess the security of database systems. Incorporating SQL into an Ethical Hacking Course can provide students with a comprehensive understanding of database security and vulnerability management. This knowledge is crucial for performing thorough security assessments and ensuring robust protection against database-related attacks.
Understanding Course Content and Fees
When choosing an Ethical Hacking Course, it’s important to consider how well the program covers essential programming languages. Courses offered by top Ethical Hacking Course institutes should provide practical, hands-on training in Python, JavaScript, C/C++, Bash scripting, and SQL. Additionally, the course fee can vary depending on the institute and the comprehensiveness of the program. Investing in a high-quality course that covers these programming languages and offers practical experience can significantly enhance your skills and employability in the cybersecurity field.
Certification and Career Advancement
Obtaining an Ethical Hacking Course certification can validate your expertise and improve your career prospects. Certifications from reputable institutes often include components related to the programming languages discussed above. For instance, certifications may test your ability to write scripts in Python or perform SQL injection attacks. By securing an Ethical Hacking Course certification, you demonstrate your proficiency in essential programming languages and your readiness to tackle complex security challenges. Mastering the right programming languages is crucial for anyone pursuing a career in ethical hacking. Python, JavaScript, C/C++, Bash scripting, and SQL each play a unique role in the ethical hacking landscape, providing the tools and knowledge needed to identify and address security vulnerabilities. By choosing a top Ethical Hacking Course institute that covers these languages and investing in a course that offers practical training and job assistance, you can position yourself for success in this dynamic field. With the right skills and certification, you’ll be well-equipped to tackle the evolving challenges of cybersecurity and contribute to protecting critical digital assets.
3 notes
·
View notes
Text
Balancing Security and Performance: Options for Laravel Developers
Introduction

This is the digital age, and all businesses are aware of the necessity to build a state-of-the-art website, one that is high-performing and also secure. A high-performing website will ensure you stand out from your competitors, and at the same time, high security will ensure it can withstand brutal cyberattacks.
However, implementing high-security measures often comes at the cost of performance. Laravel is one of the most popular PHP frameworks for building scalable, high-performing, and secure web applications. Hence, achieving a harmonious balance between security and performance often presents challenges.
This article provides more details about security vs performance for Laravel applications and how to balance it.
Security in Laravel Applications
Laravel comes equipped with a range of security features that allow developers to build applications that can withstand various cyber threats. It is a robust PHP framework designed with security in mind. However, creating secure applications requires a proactive approach. Here are some key features:
Authentication and Authorization: Laravel’s built-in authentication system provides a secure way to manage user logins, registrations, and roles. The framework uses hashed passwords, reducing the risk of password theft.
CSRF Protection: Laravel protects applications from cross-site request forgery (CSRF) attacks using CSRF tokens. These tokens ensure that unauthorized requests cannot be submitted on behalf of authenticated users.
SQL Injection Prevention: Laravel uses Eloquent ORM and query builder to prevent SQL injection by binding query parameters.
Two-Factor Authentication (2FA): Integrate 2FA for an added layer of security.
Secure File Uploads: File uploads can be exploited to execute malicious scripts. There are several ways to protect the files by restricting upload types using validation rules like mimes or mimetypes. Storing files outside the web root or in secure storage services like Amazon S3 and scanning files for malware before saving them will also improve security.
Secure communication between users and the server by enabling HTTPS. Using SSL/TLS certificates to encrypt data in transit and redirecting HTTP traffic to HTTPS using Laravel’s ForceHttps middleware will boost security. Laravel simplifies the implementation of robust security measures, but vigilance and proactive maintenance are essential.
By combining Laravel’s built-in features with best practices and regular updates, developers can build secure applications that protect user data and ensure system integrity.
Optimizing Laravel Application For Performance

Laravel is a versatile framework that balances functionality and ease of use. It is known for its performance optimization capabilities, making it an excellent choice for developers aiming to build high-speed applications. Key performance aspects include database interactions, caching, and efficient code execution. Here are proven strategies to enhance the speed and efficiency of Laravel applications.
Caching: Caching is a critical feature for performance optimization in Laravel. The framework supports various cache drivers, including file, database, Redis, and Memcached.
Database Optimization: Database queries are often the bottleneck in web application performance. Laravel provides tools to optimize these queries.
Utilize Job Batching: Laravel’s job batching feature allows grouping multiple queue jobs into batches to process related tasks efficiently.
Queue Management: Laravel’s queue system offloads time-consuming tasks, ensuring better response times for users.
Route Caching: Route caching improves application performance by reducing the time taken to load routes.
Minifying Assets: Minification reduces the size of CSS, JavaScript, and other static files, improving page load times.
Database Connection Pooling: For high-traffic applications, use a database connection pool like PGBouncer (PostgreSQL) or MySQL’s connection pool for better connection reuse.
Laravel provides a solid foundation for building applications, but achieving top-notch performance requires fine-tuning. By applying these strategies, you can ensure your Laravel application delivers a fast, seamless experience to users.
Security vs Performance For Laravel

Implementing security measures in a Laravel application is crucial for protecting data, maintaining user trust, and adhering to regulations. However, these measures can sometimes impact performance. Understanding this trade-off helps in balancing security and performance effectively. Here’s a breakdown of how Laravel’s security measures can affect performance and visa-versa.
Security measures that affect performance
Input Validation and Sanitization: Laravel’s robust validation and sanitization ensure that user input is secure and free from malicious code. Validating and sanitizing every request can slightly increase processing time, especially with complex rules or high traffic.
Encryption and Hashing: Laravel provides built-in encryption (based on OpenSSL) and hashing mechanisms (bcrypt, Argon2) for storing sensitive data like passwords. Encryption and hashing are computationally intensive, especially for large datasets or real-time operations. Password hashing (e.g., bcrypt) is deliberately slow to deter brute force attacks.
Cross-Site Request Forgery (CSRF) Protection: Laravel automatically generates and verifies CSRF tokens to prevent unauthorized actions.
Performance Impact: Adding CSRF tokens to forms and verifying them for every request incurs minimal processing overhead.
Middleware for Authentication and Authorization: Laravel’s authentication guards and authorization policies enforce secure access controls. Middleware checks add processing steps for each request. In the case of high-traffic applications, this can slightly slow response times.
Secure File Uploads: Validating file types and scanning uploads for security risks adds overhead to file handling processes. Processing large files or using third-party scanning tools can delay response times.
Rate Limiting: Laravel’s Throttle Requests middleware prevents abuse by limiting the number of requests per user/IP. Tracking and validating request counts can introduce slight latency, especially under high traffic.
HTTPS Implementation: Enforcing HTTPS ensures secure communication but introduces a slight overhead due to SSL/TLS handshakes. SSL/TLS encryption can increase latency for each request.
Regular Dependency Updates: Updating Laravel and third-party packages reduces vulnerabilities but might temporarily slow down deployment due to additional testing. Updated libraries might introduce heavier dependencies or new processing logic.
Real-Time Security Monitoring: Tools like Laravel Telescope help monitor security events but may introduce logging overhead. Tracking every request and event can slow the application in real-time scenarios.
Performance optimization that affect security
Caching Sensitive Data:
Performance optimization frequently involves caching data to reduce query times and server load. Storing sensitive data in caches (e.g., session data, API tokens) can expose it to unauthorized access if not encrypted or secured. Shared caches in multi-tenant systems might lead to data leakage.
Reducing Validation and Sanitization:
To improve response times, developers may reduce or skip input validation and sanitization. This can expose applications to injection attacks (SQL, XSS) or allow malicious data to enter the system. Improperly sanitized inputs can lead to broken functionality or exploits.
Disabling CSRF Protection:
Some developers disable Cross-Site Request Forgery (CSRF) protection on high-traffic forms or APIs to reduce processing overhead. Without CSRF protection, attackers can execute unauthorized actions on behalf of authenticated users.
Using Raw Queries for Faster Database Access:
Raw SQL queries are often used for performance but bypass Laravel’s ORM protections. Raw queries can expose applications to SQL Injection attacks if inputs are not sanitized.
Skipping Middleware:
Performance optimization may involve bypassing or removing middleware, such as authentication or Rate limiting, to speed up request processing. Removing middleware can expose routes to unauthorized users or brute force attacks.
Disabling Logging:
To save disk space or reduce I/O operations, developers may disable or minimize logging. Critical security events (e.g., failed login attempts and unauthorized access) may go unnoticed, delaying response to breaches.
Implementing Aggressive Rate Limiting:
While Rate limiting is crucial for preventing abuse, overly aggressive limits might unintentionally turn off security mechanisms like CAPTCHA or block legitimate users. Attackers may exploit misconfigured limits to lock out users or bypass checks.
Over-Exposing APIs for Speed:
In a bid to optimize API response times, developers may expose excessive data or simplify access controls. Exposed sensitive fields in API responses can aid attackers. Insufficient access control can allow unauthorized access.
Using Outdated Libraries for Compatibility:
To avoid breaking changes and reduce the effort of updates, developers may stick to outdated Laravel versions or third-party packages. Older versions may contain known vulnerabilities. For faster encryption and decryption, developers might use less secure algorithms or lower encryption rounds. Weak encryption can be cracked more quickly, exposing sensitive data.
Tips To Balance Security and Performance
There are several options available to balance security and performance while developing a Laravel application. It is essential to strike a balance and develop a robust solution that is not vulnerable to hackers. Seek the help from the professionals, and hire Laravel developers from Acquaint Softttech who are experts at implementing a combination of strategies to obtain the perfect balance.
Layered Security Measures:
Instead of relying solely on one security layer, combine multiple measures:
Use middleware for authentication and authorization.
Apply encryption for sensitive data.
Implement Rate limiting to prevent brute force attacks.
Optimize Middleware Usage:
Middleware in Laravel is a powerful tool for enforcing security without affecting performance excessively. Prioritize middleware execution:
Use route-specific middleware instead of global middleware when possible.
Optimize middleware logic to minimize resource consumption.
Intelligent Caching Strategies:
Cache only what is necessary to avoid stale data issues:
Implement cache invalidation policies to ensure updated data.
Use tags to manage grouped cache items effectively.
Regular Vulnerability Testing:
Conduct penetration testing and code reviews to identify vulnerabilities. Use tools like:
Laravel Debugbar for performance profiling.
OWASP ZAP for security testing.
Enable Logging and Monitoring:
Laravel’s logging capabilities provide insights into application performance and potential security threats:
Use Monolog to capture and analyze logs.
Monitor logs for unusual activity that may indicate an attack.
Implement Rate Limiting:
Laravel’s Rate limiting protects APIs from abuse while maintaining performance:
Use ThrottleRequests middleware to limit requests based on IP or user ID.
Adjust limits based on application needs.
Leverage API Gateway:
An API gateway can act as a security and performance intermediary:
Handle authentication, authorization, and Rate limiting at the gateway level.
Cache responses to reduce server load.
Use Load Balancing and Scaling:
Distribute traffic across multiple servers to enhance both security and performance:
Implement load balancers with SSL termination for secure connections.
Use horizontal scaling to handle increased traffic.
Employ CDN for Static Content:
Offload static resources to a content delivery network:
Reduce server load by serving images, CSS, and JavaScript via CDN.
Enhance security with HTTPS encryption on CDN.
Harden Server Configuration:
Ensure server security without sacrificing performance:
Use firewalls and intrusion detection systems.
Optimize PHP and database server configurations for maximum efficiency.
Placing trust in a Laravel development company for the development of your custom solution will go a long way ensuring you build a top-notch solution.
Future Trends in Laravel Security and Performance
As Laravel evolves, so do the tools and technologies to achieve the delicate balance between security and performance. Trust a software development outsourcing company like Acquaint Softtech for secure and future-proof solutions. Besides being an official Laravel partner, our developers also stay abreast with the current technologies.
Future trends include:
AI-Powered Security: AI-driven security tools can automatically detect and mitigate threats in Laravel applications. These tools enhance security without adding significant overhead.
Edge Computing: Processing data closer to the user reduces latency and enhances performance. Laravel developers can leverage edge computing for better scalability and security.
Advanced Caching Mechanisms: Next-generation caching solutions like in-memory databases (e.g., RedisGraph) will enable even faster data retrieval.
Zero-Trust Architecture: Zero-trust models are gaining popularity to enhance security in Laravel applications. This approach treats all traffic as untrusted, ensuring stricter access controls.
Quantum-Resistant Encryption: With advancements in quantum computing, Laravel applications may adopt quantum-resistant encryption algorithms to future-proof security.
Hire remote developers from Acquaint Softtech to implement these strategies. We follow the security best practices and have extensive experience creating state-of-the-art applications that are both secure and high performing. This ensures a smooth and safe user experience.
Conclusion
Balancing security and performance in Laravel development is a challenging yet achievable task. By leveraging Laravel’s built-in features, adopting Laravel security best practices, and staying updated on emerging trends, developers can create applications that are both secure and high-performing.
The key is to approach security and performance as complementary aspects rather than competing priorities. Take advantage of the Laravel development services at Acquaint Softtech. We can deliver robust, scalable, and efficient applications that meet modern user expectations.
1 note
·
View note
Text
10 security tips for MVC applications in 2023

Model-view-controller or MVC is an architecture for web app development. As one of the most popular architectures of app development frameworks, it ensures multiple advantages to the developers. If you are planning to create an MVC-based web app solution for your business, you must have known about the security features of this architecture from your web development agency. Yes, MVC architecture not only ensures the scalability of applications but also a high level of security. And that’s the reason so many web apps are being developed with this architecture. But, if you are looking for ways to strengthen the security features of your MVC app further, you need to know some useful tips.
To help you in this task, we are sharing our 10 security tips for MVC applications in 2023! Read on till the end and apply these tips easily to ensure high-security measures in your app.
1. SQL Injection: Every business has some confidential data in their app, which needs optimum security measures. SQL Injection is a great threat to security measures as it can steal confidential data through SQL codes. You need to focus on the prevention of SQL injection with parameterized queries, storing encrypted data, inputs validation etc.
2. Version Discloser: Version information can also be dangerous for your business data as it provides hackers with your specific version information. Accordingly, they can attempt to attack your app development version and become successful. Hence, you need to hide the information such as the server, x-powered-by, x-sourcefiles and others.
3. Updated Software: Old, un-updated software can be the reason for a cyber attack. The MVC platforms out there comprise security features that keep on updating. If you also update your MVC platform from time to time, the chances of a cyber attack will be minimized. You can search for the latest security updates at the official sites.
4. Cross-Site Scripting: The authentication information and login credentials of applications are always vulnerable elements that should be protected. Cross-Site Scripting is one of the most dangerous attempts to steal this information. Hence, you need to focus on Cross-Site Scripting prevention through URL encoding, HTML encoding, etc.
5. Strong Authentication: Besides protecting your authentication information, it’s also crucial to ensure a very strong authentication that’s difficult to hack. You need to have a strong password and multi-factor authentication to prevent unauthorized access to your app. You can also plan to hire security expert to ensure strong authentication of your app.
6. Session Management: Another vital security tip for MVA applications is session management. That’s because session-related vulnerabilities are also quite challenging. There are many session management strategies and techniques that you can consider such as secure cookie flags, session expiration, session regeneration etc. to protect access.
7. Cross-Site Request Forgery: It is one of the most common cyber attacks MVC apps are facing these days. When stires process forged data from an untrusted source, it’s known as Cross-Site Request Forgery. Anti-forgery tokens can be really helpful in protecting CSRP and saving your site from the potential danger of data leakage and forgery.
8. XXE (XML External Entity) Attack: XXE attacks are done through malicious XML codes, which can be prevented with the help of DtdProcessing. All you need to do is enable Ignore and Prohibit options in the DtdProcessing property. You can take the help of your web development company to accomplish these tasks as they are the best at it.
9. Role-Based Access Control: Every business has certain roles performed by different professionals, be it in any industry. So, when it comes to giving access to your MVC application, you can provide role-based access. This way, professionals will get relevant information only and all the confidential information will be protected from unauthorized access.
10. Security Testing: Finally, it’s really important to conduct security testing on a regular basis to protect business data on the app from vulnerability. Some techniques like vulnerability scanning and penetration testing can be implied to ensure regular security assessments. It’s crucial to take prompt actions to prevent data leakage and forgery as well.
Since maintaining security should be an ongoing process rather than a one-time action, you need to be really proactive with the above 10 tips. Also, choose a reliable web development consulting agency for a security check of your website or web application. A security expert can implement the best tech stack for better security and high performance on any website or application.
#web development agency#web development consulting#hire security expert#hire web developer#hire web designer#website design company#website development company in usa
2 notes
·
View notes
Text
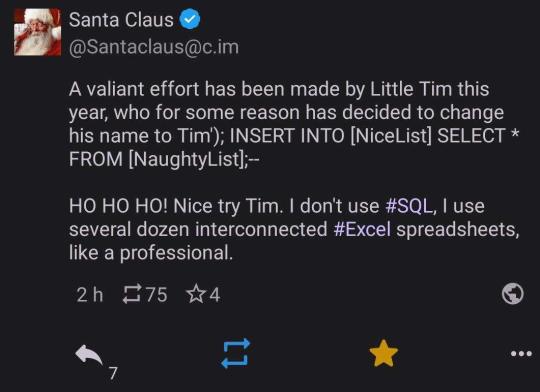
Dear God santa...
That's one way to prevent malicious sql injections ig
20K notes
·
View notes
Text
Why Regular Website Maintenance Is Crucial

More than just a digital address, your website serves as the public face of your company, a round-the-clock marketing tool, and an essential means of communicating with clients. But building a website is only the beginning. Regular website maintenance is vitally necessary to keep it operating efficiently, safely, and successfully.
At Web Era Solutions, we help businesses stay ahead with ongoing website maintenance services that ensure peak performance, tight security, and long-term success. In this blog, we’ll explain why website maintenance is crucial, and what you risk by neglecting it.
What Is Website Maintenance?
The process of regularly scanning your website for problems, repairing bugs, updating content, and enhancing security and performance is known as website maintenance. It’s like routine servicing for your car—preventive care keeps everything running efficiently and extends its lifespan.
Maintenance involves tasks like:
Updating plugins, themes, and core systems
Checking for broken links and bugs
Backing up data
Monitoring performance and speed
Fixing security vulnerabilities
Ensuring mobile responsiveness
Refreshing outdated content
1. Enhanced Security and Data Protection
Cybersecurity threats are growing every day. Outdated plugins, expired SSL certificates, or weak code can leave your website vulnerable to attacks like:
Malware injections
Phishing scams
SQL injections
Brute-force login attempts
Regular updates and patches help you stay ahead of hackers and protect your business and customer data.
2. Improved Website Performance
Slow loading times and broken pages frustrate users and drive them away. Regular maintenance helps:
Optimize images and code
Reduce server load
Eliminate 404 errors
Clean up unnecessary files and scripts
This ensures faster load times, lower bounce rates, and better search engine performance.
3. Better User Experience (UX)
Users desire a simple, error-free, and seamless experience. Regular maintenance helps identify and fix:
Navigation glitches
Mobile display issues
Inactive buttons or CTAs
Confusing content layout
By improving UX, you increase customer satisfaction, trust, and engagement.
4. Boost SEO and Search Rankings
Search engines like Google reward websites that are:
Mobile-friendly
Fast-loading
Regularly updated
Free from technical issues
Your SEO results may suffer from security flags, out-of-date material, or broken links. Regular audits and updates keep your site SEO-friendly and improve search engine visibility.
5. Protect Your Investment
You've probably spent a lot of time, money, and effort creating your website. Without maintenance, that investment could go to waste.
Problems like malware, bugs, or hosting failures can lead to:
Website downtime
Loss of traffic and customers
Damaged brand reputation
Expensive emergency fixes
Routine upkeep ensures that your website remains a long-term, high-performing asset.
6. Keeps Your Content Fresh and Relevant
Old blog entries, out-of-date material, and expired deals all reflect poorly on your brand. Regular maintenance allows you to:
Update product and service info
Add fresh blog content
Replace old images or testimonials
Reflect new branding and promotions
Additionally, fresh content improves your SEO and retains users.
7. Ensures Compatibility with Modern Browsers and Devices
Technology changes fast. An unmaintained website may not function properly on the latest browsers, mobile phones, or operating systems.
Regular maintenance checks ensure cross-browser and cross-device compatibility, helping you reach and retain more users.
8. Peace of Mind and Fewer Emergencies
Would you rather deal with a slow site now or a broken site later?
Proactive maintenance:
Minimizes risks of sudden crashes
Detects issues before they become emergencies
Reduces emergency fix costs
Gives you peace of mind
At Web Era Solutions, we offer monthly and quarterly maintenance plans to keep your website protected and performing all year round.
What Happens If You Neglect Website Maintenance?
Here’s what you risk:
Loss of traffic and rankings
Data breaches and customer trust issues
Expensive emergency repair bills
Declining sales and conversions
Outdated user experience and poor brand perception
Final Thoughts
Your website is a living digital asset. Like any valuable resource, it needs regular care to function at its best. By investing in routine website maintenance, you protect your business, improve performance, enhance SEO, and deliver a superior user experience.
At Web Era Solutions, we don’t just build websites—we maintain them with precision. From updates and security patches to performance checks and SEO audits, our comprehensive maintenance services ensure your website remains fast, secure, and future-ready.
Keep Your Website Healthy with Web Era Solutions
Let us handle the updates, security, and performance—so you can focus on your business.
Contact Web Era Solutions today for affordable, expert website maintenance services tailored to your needs.
Contact us via phone or email for a free website audit and consultation.
0 notes
Text
In an age where software applications are constantly under threat from cyberattacks, application security testing has become a critical element of the software development lifecycle. As businesses increasingly move their operations online, ensuring that applications are secure from vulnerabilities is no longer optional—it’s essential.
Application security testing (AST) is a process of evaluating applications for security flaws and vulnerabilities that may be exploited by attackers. A successful testing strategy helps protect sensitive data, prevent system breaches, and maintain customer trust.
Here are the best practices for application security testing in 2025 that every developer, tester, and security professional should follow.
1. Shift Security Left in the SDLC
One of the most widely accepted best practices is to shift security left, meaning security checks should be integrated early in the development process—starting from the requirements and design phases. Detecting vulnerabilities during development is far cheaper and faster than fixing them post-release.
By embedding security into DevOps pipelines (DevSecOps), organizations can automate tests and continuously monitor code throughout the lifecycle.
2. Use a Multi-Layered Testing Approach
No single tool or method can uncover all security issues. For thorough coverage, combine the following:
SAST (Static Application Security Testing): Examines source code or binaries without running the program. Great for early-stage vulnerability detection.
DAST (Dynamic Application Security Testing): Simulates attacks on running applications to find vulnerabilities in real-time environments.
IAST (Interactive Application Security Testing): Blends elements of both SAST and DAST, providing deeper insights during runtime.
Using multiple layers of testing ensures better detection of known and unknown security issues.
3. Automate Testing in CI/CD Pipelines
Incorporating security testing into CI/CD pipelines ensures that every code commit is automatically scanned for vulnerabilities. Tools like SonarQube, Veracode, and Checkmarx offer integration with modern DevOps platforms.
Automation helps maintain speed in delivery without compromising on security, making it an ideal solution for agile teams working in fast-paced environments.
4. Perform Regular Manual Code Reviews
While automation is powerful, it’s not enough. Many security flaws—especially logic errors and business logic vulnerabilities—can only be found through manual code reviews. Encourage developers to peer-review each other's code with a security mindset.
Manual reviews are also an opportunity to mentor junior developers on secure coding practices and encourage a culture of security awareness.
5. Stay Updated with OWASP Top 10
The OWASP Top 10 is a valuable resource that lists the most common and critical web application security risks, such as:
Injection flaws (e.g., SQL, OS)
Broken authentication
Security misconfiguration
Cross-site scripting (XSS)
Ensure your security testing covers these categories and update tools/rulesets regularly to align with the latest threats.
6. Conduct Regular Penetration Testing
Penetration testing simulates real-world attacks on your applications to discover vulnerabilities that automated tools might miss. These tests can be done internally or outsourced to ethical hackers. They provide an external perspective and uncover risks that could otherwise remain hidden.
It’s a best practice to conduct penetration tests before every major release or after any significant system change.
7. Secure Third-Party Components
Applications often rely on third-party libraries, APIs, and open-source components. These can be easy entry points for attackers if not properly vetted.
Use Software Composition Analysis (SCA) tools like Snyk or WhiteSource to detect vulnerabilities in third-party packages and ensure they’re updated regularly.
8. Train Your Developers on Secure Coding
Security is not just the responsibility of testers or security teams. Developers should be trained in secure coding principles such as input validation, error handling, and access control.
Organizations should provide regular security awareness training, workshops, and coding challenges to help developers write secure code from the beginning.
9. Threat Modeling Before Testing
Before running any tests, engage in threat modeling to map out potential attack vectors, data flows, and system components that could be exploited. This proactive approach helps focus testing efforts on high-risk areas and improves overall security posture.
Tools like Microsoft’s Threat Modeling Tool can guide this process efficiently.
10. Track, Remediate, and Retest
Finding vulnerabilities is only part of the job. The real value comes in fixing and retesting them. Establish a clear workflow for:
Logging and prioritizing issues
Assigning them to developers
Retesting after remediation
Security issues should never sit unresolved or be dismissed as “not a concern.” A mature AST program ensures that remediation is timely and well-documented.
🔚 Conclusion
Application security testing is an ongoing process that evolves with each new threat. By following these best practices—shifting left, using layered testing, combining automation with manual reviews, and educating your teams—you can reduce your application’s risk surface dramatically.
Security is not a one-time task but a continuous commitment to protecting users, data, and systems. Make it an integral part of your development culture.
0 notes
Text
Magento 2 Security Extension — Protect Your Store from the Inside Out
Running an eCommerce business on Magento 2 gives you power, flexibility, and performance. But with great power comes great responsibility—especially when it comes to security. Magento is a widely used platform, making it a common target for cyber threats, data breaches, and fraud. That’s why installing a Magento 2 Security Extension is one of the smartest decisions any store owner can make.
This article explores how security extensions safeguard your Magento 2 store, how address validation plays a key role in fraud prevention, and which features you should prioritize when choosing the right security solution.
Why Magento 2 Needs Security Enhancements
Magento 2 offers solid built-in security features, including two-factor authentication (2FA), file system permissions, and CAPTCHA. However, these tools aren’t always enough. Most store owners still face threats like:
Fake user registrations
Fraudulent orders
Bot attacks
SQL injections
Data tampering
Checkout manipulation
Because Magento 2 is open-source and highly customizable, vulnerabilities can emerge through third-party modules, outdated plugins, or improper server configurations. A dedicated security extension provides an extra layer of defense against such risks.
The Hidden Threat: Invalid or Fake Addresses
One of the most overlooked security gaps in Magento 2 stores is invalid or fake address entries during checkout. Cybercriminals and bots often use fake addresses to:
Test stolen credit cards
Place high-risk or fraudulent orders
Flood your system with fake data
Manipulate shipping or billing info to trigger chargebacks
This is where address validation steps in—not just as a logistics tool, but as a powerful security filter.
How Address Validation Boosts Magento 2 Security
An address validation extension like the one offered by EcomPlugins doesn't just help verify locations for delivery—it helps verify the user’s intent and legitimacy.
Here’s how it strengthens your store’s security:
1. Detects Suspicious Address Patterns
Invalid zip codes, incomplete fields, or mismatched city-state combinations are red flags. Automatically detecting these issues helps you block risky transactions before they occur.
2. Reduces Chargebacks and Payment Disputes
A significant number of fraudulent orders use fake billing addresses. Real-time validation ensures that billing information aligns with what payment gateways expect, reducing the risk of false disputes.
3. Prevents Fake User Registrations
If your extension validates addresses at registration (or checkout), it becomes harder for bots or scammers to create dummy accounts with fake data.
4. Enhances Data Integrity
Address validation ensures that your CRM, analytics tools, and marketing automations only work with clean, verified data—essential for both security and performance.
Features to Look for in a Magento 2 Security Extension
While address validation is a great start, here are additional features to look for in a well-rounded Magento 2 security extension:
1. Two-Factor Authentication (2FA)
Adds an extra layer of login protection by requiring a secondary code, usually sent to a device.
2. IP Whitelisting and Blacklisting
Control which IPs can access your admin panel and block suspicious or high-risk addresses.
3. Login Attempt Limits
Prevent brute-force attacks by locking users out after a certain number of failed login attempts.
4. Admin URL Customization
Change your default admin URL so that bots and hackers can't easily guess where to target attacks.
5. Firewall Rules
Use application-level firewalls to filter traffic, restrict bots, and block known attackers.
6. Activity Logs and Alerts
Monitor admin and customer activity in real-time. Automated alerts notify you of suspicious behavior like multiple failed logins or bulk data exports.
EcomPlugins: Secure Checkout with Built-in Address Validation
If you're looking for a lightweight yet powerful solution to improve your Magento 2 store’s security, EcomPlugins’ Magento 2 Address Validation extension is a great place to start.
Here’s what sets it apart:
USPS-based real-time address verification
Validation for both billing and shipping addresses
Auto-suggestions for correcting typos and missing details
Support for U.S. merchants and USPS standards
Quick installation and Magento 2 compatibility
Although primarily focused on logistics, this extension acts as a security filter by preventing invalid or malicious addresses from slipping through your checkout.
Why Security = Trust = Higher Conversions
Security isn’t just about protecting your site—it’s about protecting your customers. Shoppers are becoming more cautious about who they buy from. Even a small sign of weakness, like a failed order or shipping error, can reduce trust and hurt conversion rates.
By using a security-enhancing tool like an address validation extension, you demonstrate professionalism, protect customer data, and improve fulfillment accuracy—all of which build long-term trust.
Final Thoughts
Magento 2 is a powerful eCommerce platform, but it’s not invulnerable. Cyber threats are evolving every day, and relying solely on default security settings is risky. A Magento 2 Security Extension—especially one with built-in address validation—can be your first line of defense against fraudulent behavior, shipping errors, and data integrity issues.
For store owners who want to secure their operations and deliver a flawless checkout experience, EcomPlugins’ Magento 2 Checkout Address Validation extension offers the perfect blend of security, usability, and logistics support.
Protect your store from the inside out—start with smarter address validation today.
0 notes
Text
Why Startups Choose Ready-Made Crypto Exchange Software

Introduction
In today’s fast-paced digital economy, launching a cryptocurrency exchange has become a lucrative opportunity. But here’s the catch—developing an exchange from scratch is time-consuming, expensive, and technically demanding. That’s where ready-made crypto exchange software comes in.
For startups with limited time, resources, or technical teams, choosing a Cryptocurrency Exchange Script offers a powerful shortcut. These pre-built solutions provide the features, security, and scalability needed to launch quickly—without reinventing the blockchain wheel.
Let’s explore why more startups are going with these ready-to-deploy scripts to power their crypto trading platforms.
What Is a Cryptocurrency Exchange Script?
A Cryptocurrency Exchange Script is a pre-developed, customizable software package that includes all the core functionalities of a crypto exchange. It helps entrepreneurs launch platforms similar to Binance, Coinbase, or Kraken—without building everything from scratch.
These scripts support key functions like:
User registration & KYC
Cryptocurrency trading engine
Wallet integration (hot and cold wallets)
Admin and user dashboards
Liquidity management
Security features (2FA, encryption, etc.)
Why Startups Are Choosing Ready-Made Solutions
1. Faster Time to Market
Launching a custom-built exchange can take months—or even years. With a Crypto Exchange Script, startups can get their platform up and running within a few weeks.
Startups love the speed because in crypto, timing is everything. Markets move fast, and being first often means gaining a competitive edge.
2. Affordable Development Costs
Developing a cryptocurrency exchange from scratch can cost anywhere between $100,000 to $500,000, depending on features and complexity. On the other hand, White Label Bitcoin Exchange Scripts offer similar functionalities at a fraction of the price.
Key cost savings include:
No need to build from scratch
No large in-house dev teams
Fewer testing phases
Reusable and battle-tested code
3. Easy Customization
Despite being pre-built, most cryptocurrency trading scripts are fully customizable. This means startups can:
Add their own branding and UI/UX
Integrate specific coins or tokens
Choose the trading pairs
Set custom transaction fees
Enable specific security layers
Customization allows businesses to tailor the user experience to match their vision and target audience.
4. Proven Security and Reliability
Security is non-negotiable in crypto. With Bitcoin Exchange Software that’s been tested across multiple use cases, startups can avoid the risks of zero-day vulnerabilities or untested code.
Most quality scripts come with:
Encrypted wallet systems
Two-factor authentication (2FA)
DDOS protection
SQL injection and XSS prevention
Secure APIs
5. Ongoing Tech Support and Upgrades
Top vendors don’t just sell a script—they offer ongoing support, updates, and patches. This is especially useful for startups without in-house blockchain engineers.
Some even offer:
Free bug fixes
Version upgrades
Technical consultation
Performance optimization tips
Popular Features in Today’s Exchange Scripts
Startups are attracted to Altcoin Exchange Scripts because they come loaded with features such as:
✅ Multi-Currency Wallets
Support for multiple cryptocurrencies, including Bitcoin, Ethereum, altcoins, and stablecoins.
✅ Advanced Trading Engine
Capable of handling real-time buy/sell orders, order matching, market, and limit trading options.
✅ KYC/AML Compliance Tools
Integrated tools for verifying user identity and following local regulatory standards.
✅ Mobile and Web Interface
Responsive front-ends for both desktop and mobile users with clean, intuitive navigation.
✅ Liquidity Management
Integrates with other exchanges or liquidity pools to ensure smooth trading and minimize slippage.
Benefits Beyond the Code
Choosing a cryptocurrency trading platform script means more than just software—it means access to an entire business ecosystem. Startups gain:
Scalability – Easily handle growing users and trading volume
Faster ROI – Quick launch means quicker monetization
Low Risk – Start small, scale fast
White-labeling – Rebrand and go live under your own name
Who Should Consider a Cryptocurrency Exchange Script?
Ready-made crypto exchange software is ideal for:
Entrepreneurs entering the crypto space with minimal technical knowledge
Startups looking to test an idea or MVP before committing large investments
Traditional financial companies expanding into digital assets
Crypto influencers or communities launching niche or token-based exchanges
How to Choose the Right Script
Not all exchange scripts are created equal. Here’s what to look for:
✔️ Clean, Modular Code
So you can update or replace components as needed.
✔️ Strong Demo & Documentation
Ensure you can test the script and understand how it works before purchase.
✔️ Regulatory Readiness
Make sure the script helps you comply with the laws of your operating country.
✔️ Customization & Integration
Check that you can easily modify features and connect third-party services.
✔️ Customer Support
Choose a provider that offers tech support during and after launch.
Real-World Use Case: A Startup Success Story
Let’s say a fintech startup in Singapore wanted to launch a niche altcoin trading platform. Instead of spending six months on development, they opted for a white label crypto exchange script. Within 45 days, they were live with:
User-friendly UI
Trading pairs for regional altcoins
24/7 trading with liquidity support
Regulatory compliance tools for KYC
Within 6 months, the platform reached 50,000+ active users—all thanks to a fast, affordable, and reliable software base.
Conclusion: Launch Smart with a Crypto Exchange Script
For startups stepping into the booming world of crypto, using a Cryptocurrency Exchange Script isn’t just a shortcut—it’s a strategic decision. It combines speed, cost-effectiveness, and flexibility, all while offering a strong technical foundation.
With reliable features, security protocols, and white-label capabilities, ready-made crypto exchange software empowers entrepreneurs to launch confidently and scale fast.
🚀 Ready to Start Your Crypto Exchange?
If you’re a startup exploring the crypto space, now is the time to act. Choose a Crypto Exchange Script that fits your needs, customize it to match your brand, and go live in weeks—not months.
Explore your options today and start building the future of finance.
FAQ Summary
What is a Cryptocurrency Exchange Script? A ready-made, customizable software for launching a crypto trading platform.
Is it secure to use a pre-built crypto exchange? Yes—if sourced from a trusted provider. Look for security features like 2FA, encryption, and DDoS protection.
Can I customize the script? Absolutely. Most scripts are white-label and highly customizable.
How much does it cost? Costs range from $5,000 to $50,000 depending on features and support options.
How long does it take to launch? With a ready-made script, your exchange can go live in as little as 2–4 weeks.
#Cryptocurrency Exchange Script#White Label Bitcoin Exchange Script#Cryptocurrency Trading Platform#Bitcoin Exchange Software#Altcoin Exchange Script#Crypto Exchange Script
0 notes