#cloud and security
Explore tagged Tumblr posts
Text
Cyber Hygiene and Its Role in Security Assessments

In an era where cyber threats evolve daily, maintaining robust cybersecurity practices has never been more critical. Organizations and individuals alike face a growing number of challenges, from sophisticated ransomware attacks to subtle phishing schemes. At the core of an effective defense strategy lies the concept of cyber hygiene—a proactive, preventive approach to minimizing vulnerabilities and enhancing security.
What is Cyber Hygiene?
Cyber hygiene refers to the routine practices and precautions that ensure the health and security of an organization’s or individual’s digital environment. Much like personal hygiene, which protects physical health, cyber hygiene is about safeguarding the digital assets and information systems from infections, breaches, and other security incidents.
Key aspects of cyber hygiene include:
Regular Updates: Ensuring software, applications, and operating systems are up-to-date to patch known vulnerabilities.
Strong Authentication: Using robust passwords and multi-factor authentication (MFA) to reduce unauthorized access.
Backup and Recovery: Creating secure backups to mitigate the impact of ransomware or accidental data loss.
Endpoint Security: Deploying firewalls, antivirus software, and endpoint detection tools to prevent malicious activities.
User Awareness Training: Educating employees about recognizing phishing attempts, social engineering tactics, and unsafe online behaviors.
The Importance of Cyber Hygiene

Effective cyber hygiene provides a foundational layer of defense against the ever-increasing cyber risks. Organizations that neglect these basic practices expose themselves to data breaches, financial losses, and reputational damage. By maintaining good cyber hygiene, businesses can:
Minimize Attack Surfaces: Proactive measures reduce the number of potential entry points for attackers.
Improve Incident Response: Well-maintained systems and documented processes enable faster detection and response to threats.
Comply with Regulations: Regulatory frameworks like GDPR, HIPAA, and CCPA emphasize the need for secure data handling practices.
Boost Stakeholder Confidence: Demonstrating strong cybersecurity practices builds trust with customers, partners, and investors.
Cyber Hygiene and Security Assessments
Security assessments are systematic evaluations designed to identify vulnerabilities, weaknesses, and potential threats within an organization’s IT infrastructure. Cyber hygiene plays a vital role in ensuring these assessments are effective and actionable.
Baseline Security Posture: Regular cyber hygiene practices establish a strong baseline for security assessments. This ensures that evaluations focus on emerging threats and advanced vulnerabilities rather than basic issues like outdated software or weak passwords.
Streamlined Assessments: Organizations with good cyber hygiene have well-documented systems, configurations, and processes, making it easier for security professionals to conduct thorough evaluations.
Accurate Risk Identification: Cyber hygiene minimizes noise from low-level vulnerabilities, allowing assessments to uncover high-priority risks more effectively.
Core Components of Cyber Hygiene in Security Assessments

To integrate cyber hygiene into security assessments, organizations must focus on several core components:
1. Asset Management
Understanding what’s in your environment is the first step. Conducting a detailed inventory of all hardware, software, and data assets ensures that security assessments cover every aspect of the IT ecosystem. Unmanaged or unknown devices can act as entry points for attackers.
2. Patch Management
Timely updates and patches are critical to closing vulnerabilities. Security assessments should evaluate an organization’s patch management policies and identify any lapses that could be exploited.
3. Access Controls
Assessing user access privileges ensures that employees have access only to the information necessary for their roles. Overprivileged accounts can increase the risk of insider threats and unauthorized access.
4. Network Monitoring
Real-time monitoring of network activity helps detect unusual behaviors indicative of potential breaches. Security assessments should review the effectiveness of monitoring tools and processes.
5. Incident Response Planning
Cyber hygiene includes having a robust incident response plan in place. Security assessments should evaluate the plan’s readiness and the organization’s ability to execute it effectively.
Challenges in Maintaining Cyber Hygiene
Despite its importance, maintaining consistent cyber hygiene can be challenging due to factors such as:
Resource Constraints: Small and medium-sized businesses may lack the budget and expertise needed to implement comprehensive cybersecurity measures.
Rapidly Changing Threat Landscape: Cyber threats evolve quickly, making it difficult for organizations to stay ahead.
Human Error: Even with training, employees can inadvertently compromise security by clicking on malicious links or using weak passwords.
Complex IT Environments: Large organizations often manage diverse and distributed systems, increasing the difficulty of maintaining consistent hygiene.
Best Practices for Cyber Hygiene
Organizations can overcome these challenges by adopting best practices tailored to their specific needs:
Implement Automated Tools: Use automated solutions for patch management, vulnerability scanning, and endpoint protection to reduce manual effort.
Conduct Regular Training: Continuously educate employees about emerging threats and safe practices.
Perform Routine Assessments: Schedule regular security assessments to identify gaps and address them promptly.
Document Policies: Maintain clear and accessible cybersecurity policies, including acceptable use, data protection, and incident response protocols.
Engage Experts: Partner with cybersecurity professionals to audit and enhance cyber hygiene practices.
The Future of Cyber Hygiene

As digital transformation accelerates, the importance of cyber hygiene will only grow. Emerging technologies like artificial intelligence (AI) and machine learning (ML) offer promising solutions for automating and enhancing cybersecurity practices. However, they also introduce new challenges, such as ensuring these systems are secure and free from bias.
Organizations must view cyber hygiene as an ongoing commitment rather than a one-time effort. By embedding cybersecurity into their culture and operations, they can better navigate the complexities of the digital age.
Conclusion
Cyber hygiene is a cornerstone of effective cybersecurity. It not only minimizes risks but also ensures that security assessments are more precise and actionable. By adopting proactive measures and staying vigilant, organizations can protect their assets, maintain compliance, and build resilience against future threats. In today’s interconnected world, robust cyber hygiene is not just a best practice—it’s a necessity. Read other related post: How to Align Security Assessments with Business Goals
#cloud and security#cybersecurity#it msp services#managed it services#data security#it#it management
1 note
·
View note
Text
Some random doodles!


These are if my favorite characters through the years met lol
This isn’t all of them but it’s the ones that I REALLY like(d) growing up and recently :)
#fnaf#fnaf security breach#fnaf gregory#fnaf glamrock freddy#glamrock freddy#jack skellington#nightmare before christmas#coraline#little nightmares#little nightmare mono#little nightmares six#chicken little#cult of the lamb#lambert#final fantasy vii#cloud strife#mlp#fluttershy#discord mlp#fluttercord#toriel#undertale#winnie the pooh
2K notes
·
View notes
Text

fateful encounter
#one of my favorite things about ffvii's story is that every tiny event comes with a million new What Ifs.#what if tifa didn't recognize cloud at the train station? what if she chose not to help him and instead just minded her own business?#what if cloud didn't have that sword? would tifa have even noticed him? or would she have assumed that he was just another mako junkie?#what if someone else had found him first? what if someone called public security and shinra came to 'investigate?'#why was cloud in sector 7 anyway? what if he'd been in sector 5 instead? would aerith have discovered him?#was he trying to catch a train up to the shinra building in order to follow the reunion? since jenova's body was up there?#every answer creates a bunch of new questions. the story writes itself in your own head. uuUUAAHHGHH i love this game#ffvii#cloud strife#tifa lockhart#my art <3#.............what if cloud had stumbled onto the tracks and gotten run over
493 notes
·
View notes
Text




Part 29 ✨ 🍅
Previous - next - first
colors brought to you once again thanks to @cloudwhisper23 🎨 🖌️ bless you fren 💕
#my art#cloud#ok couple fun facts there’s a sailor moon background there I just even used the same colors nfjfjfnjfjfnfjnf I’m gonna start doing that more#and i was gonna hide a Rickroll in those speech bubbles or CC’s name but turns out people still can read it so :v had to calm down#fnaf#five night’s at freddy’s#security breach#fnaf 2#fnaf au#into the ballpit au#michael afton#Glamrock Freddy#jeremy fitzgerald#Gregory#crying child#evan afton#fazbear frights#into the pit#uhhhhh ummm#ye that’s all
2K notes
·
View notes
Text

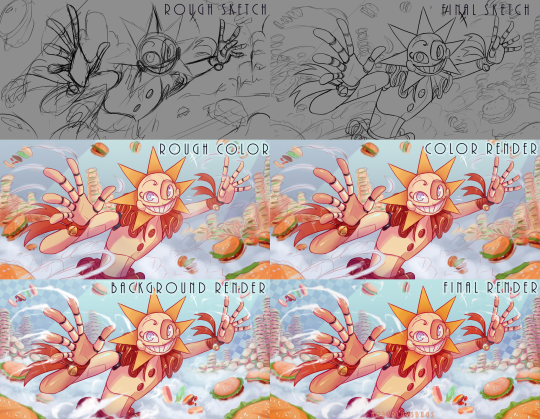
Whopper
This stupid meme lives in my head rent free and I can never seem to escape it. Whopper sun belongs to @just-a-drawing-bean
Process is down below
1K notes
·
View notes
Text
The cloud is just someone else's computer, and they probably don't back it up as often as you'd like. Better keep those important files on a disk locally at two different locations, just in case. 😉
54 notes
·
View notes
Text

Introducing my fnaf oc... Cloud!! I've been doodling him for a while but I wanted to introduce him with a full piece, so here's my baby boy! Oh, and Moon.
#my art#art#fan art#fnaf#fnaf daycare attendant#fnaf security breach#daycare attendent#dca fnaf#fnaf moon#fnaf fanart#fnaf dca#moon dca#dca fandom#dca fanart#dca moon#dca oc#dca#moondrop#moon#cloud#raindrop#fnaf oc#fnaf original character#daycare attendant moon
272 notes
·
View notes
Text




☁🌟Miss Starry Cloud☁🌟
My new character is called Miss Starry Cloud☄☁, she is the theater assistant, as a replacement for the daycare assistant. Scheduled to be entertainment at certain times when children can visit the theater. I will give more details later, I will only say that its programming is based on the Mimic-1
Digital art//Fan art by S.Cartoon
Sundrop//Moondrop by FNAF SB
Reblog and love..please and thanks👍
#five nighst at freddy's security breach#five nights at freddy's#fnaf#fnaf sb#fnaf daycare attendant#daycare attendant#fnaf sundrop#sundrop#fnaf moondrop#moondrop#fnaf sun#fnaf moon#miss starry cloud#digital art#fan art#my art#artist on tumblr#tumblr
45 notes
·
View notes
Text

.... My point still stands Too many good fictions....
Solar Lunacy - @bamsara Moon
Enthralling you, Enthralling me - @justfangirlstuffs Vampire Sun and Moon
Clouds and Nebulas - @chimkin-samich Sun and Moon
Part1 / Part2 (welcome!) / Part3 / Part4 / Part5 / Part6 Without white text:

#myart#fnaf daycare attendant#fnaf security breach#fnaf sb#fnaf moon#moondrop#fnaf sun#sundrop#sketch#fnaf#gift art#fanart#fnaf fanart#fnaf fandom#daycare attendant#fnaf dca#solar lunacy#bamsara#enthralling you enthralling me#justfangirlstuffs#clouds#nebulas#chimkin-samich#scarredlove#fnaf au#sketches#art dump
1K notes
·
View notes
Text

Just a lil Sun I colored from a panel from Clouds
#arts#clouds#sundrop x self insert#sundrop fnaf#sundrop x y/n#sun and moon x y/n#sun and moon x reader#sundrop#sundrop security breach#daycare attendant fnaf
501 notes
·
View notes
Text

IM CRYING WHY
#fnaf#fnaf au#fnaf fanart#fnaf fandom#fnaf movie#fnaf oc#fnaf security breach#five nights at freddy's#fnaf oc art#fnaf 1 fanart#puffy clouds#salamander#anti proship#dni proship#i’m crying#shitpost#depressing shit#twitter
44 notes
·
View notes
Text
Yippeeeee I finished my Y/N self insert character and I like this one a lot better!
Here’s with and without the color overlay-



Plus have a doodle of Moon about to put you to sleep, he’s so caring! :)
#fnaf sb#fnaf self insert#fnaf sb y/n#fnaf moon#moondrop#fnaf security breach#my art#self insert#oc#cloud y/n#moon x reader#moon x y/n#fnaf moon x y/n#fnaf moondrop#moondrop x y/n#yeah decided to go a bit more towards self insert#but I will be using this for general reader content too!#they are non-binary#I decided to make them a tech at the pizzaplex#mostly does small p&s work#fixing arcades and charging stations#yippeeee
440 notes
·
View notes
Note
What are your Headcanons ideas what if Zack and Cloud are childhood friends? 🤔
UHHHHH i haven't thought about this one too much to be honest lmao
I think they would be enemies at first actually. Two kids with opposite personalities who can't stand each other's guts. Zack hates how quiet and funless Cloud is, and Cloud can't tolerate Zack's rowdy chatty nature. They get into petty fights over little things and are happy to never have to interact again after they grow up.
Many years later, they crash back into each other's lives somehow. Now that they're past their asshole teenager years, they learn to set their differences aside, and maybe even make up for their respective weaknesses...!
#idk the childhood friends to lovers trope just doesn't work for me with zakkura i guess#the reason i love zakkura so much is because of how short and brutal their time together was.#it's about how they never even got the chance to realize that it was love at all.#zack too busy in SOLDIER. cloud too caught up in public security. by the time an opportunity shows itself#it's too late.#and just when things look like they'll eventually work out#they don't. they can't. it's over.#:')#ANYWAY!#ffvii#zack fair#cloud strife#zakkura#asks
32 notes
·
View notes
Text



A rare shiny page brought to you thanks to the power of friendship! Thank you for coloring it so beautiful @cloudwhisper23
Page 27
Previous - next- first
#my art#fnaf#five nights at freddy's#security breach#michael afton#glamrock freddy#Jeremy Fitzgerald#Gregory#evan afton#crying child#fnaf au#fazbear frights#into the ballpit au#cloud#I better not be missing any tags
1K notes
·
View notes
Text

'Sleuth Jesters' Eclipse
In the shock of it all, the gunfire had suddenly ceased and all that was left was plumes of smoke. Heavy, harsh, and yet strict waves of thick blur and ash on your field of vision. Muffling the quiet surroundings.
All except for distinct and sharp footsteps.
Something- no, someone approaches you in the haze. Before long a dreaded shadowy figure pierces through the mist with dusty ease.
"My my, what do we have here?"
Your breath hitches and your eyes widen at the voice. Everything seems to be in slow motion as you stare in fear and in dread.
You knew exactly who that deep voice belongs to.
The smoke seeped through his chaises and his sleazy formal wear as if breathing in and forming his familiar figure and colors through the mist. It dragging behind on his back, his rays, and fingertips toward you. His intricate digits burned with embers and blended the smoke as it follows him, Almost as if he was in control of the hell unleashed. The hold of his cigar evident in his hand even though it can never be smoked through that stagnant wicked grin.
"Hello, Sweetheart." ____________________________________________ Took inspiration with @just-a-drawing-bean's design of Eclipse. Sleuth Jesters belongs to @naffeclipse
Process is down below

1K notes
·
View notes
Note
I hope this isn't too much but can I request a sun and moon fnaf sb stimboard with plushies, drawing (colorful or kid like if possible?) And any other soft thing you see fit? Thank you!










Sun and Moon (FNAF, Security Breach) with plushies and drawing!
🧸|🖋️|🧸 🖋️|🧸|🖋️ 🧸|🖋️|🧸
#weheartstims#stimboard#fnaf sun#sun fnaf#fnaf daycare attendant#moon fnaf#fnaf moon#fnaf security breach#fnaf sb#plushies#drawing#hands#yellow#blue#glitter#coloring#care bears#elephant#sun#cloud#moon#crescent moon
54 notes
·
View notes