#career in ethical hacking
Explore tagged Tumblr posts
Text
Coding and Scripting for Beginner Hackers
Learning to code and write scripts is a crucial skill for getting into ethical hacking and cybersecurity. Scripting allows you to automate repetitive tasks, develop your own custom tools, analyze data, and program everything from small hacking tools to machine learning models. Understanding and knowing how to code in different languages can be extremely useful when doing deep dives into malware…

View On WordPress
#Cyber Security#cybersecurity careers#Ethical Hacking#hacer certifications#hacking for beginners#hacking guide#hacking homelab#infosec#learn to code#learn to hack#Penetration Testing#Pentesting
3 notes
·
View notes
Text
Back To Hacking!
So I've got some news, I'm going back into penetration testing. ^^
I'm starting as a Security Consultant with a brilliant company on the 19th who've offered me an amazing salary.
What I'm mainly impressed by is their training though: not only do you get CREST certification (wanted in the UK,) you also get a training budget to pursue certification of your choosing. I'm going to use mine to achieve more offsec certification. c: They also help with soft skill development too which is my weak point!
I'm hoping this will be the start of an actual career in penetration testing for me. My reason for the move back is mainly due to my interests- hacking is one thing I genuinely get enjoyment out of in my own time and I seem to have potential in it based on the two companies being interested in hiring me!
Think I'm ready to accept the inevitability of client interaction too. XD

2 notes
·
View notes
Text
How to Build a Strong Cybersecurity Culture Within Your Organization
In today’s highly interconnected digital landscape, cybersecurity is no longer just a technical issue; it’s a business-critical concern that impacts every aspect of an organization. From data breaches to sophisticated ransomware attacks, the potential for damage is vast and ever-evolving. As such, encouraging a strong cybersecurity culture within your organization is no longer optional it’s a necessity.
A cybersecurity culture means that everyone within your organization, from top-level executives to entry-level employees, understands the role they play in safeguarding company data. Creating this culture requires clear strategies, commitment from leadership comprehensive training, and continuous monitoring.
In this blog, we will explore the key strategies to develop a robust cybersecurity culture that empowers your organization to proactively defend against threats.

AI in Cybersecurity
Implementing AI in cybersecurity is a game-changer for modern organizations, offering enhanced capabilities for threat detection, analysis, and response. By leveraging AI's ability to process vast data and identify patterns that might elude human analysts, businesses can better protect themselves from sophisticated cyberattacks. To effectively integrate AI into your cybersecurity strategy, it’s crucial to gain leadership support, establish clear policies, and ensure staff are trained in the latest AI tools. Continuous communication and integration of AI into daily operations are essential for maximizing its benefits while managing potential risks. Staying informed about AI advancements and evolving cyber threats will further bolster your security framework.
In this section will speak about risks and benefits
AI in Cybersecurity: Risks and Benefits
Risks:
False Positives: AI may misidentify normal activities as threats.
AI Exploitation: Cybercriminals could misuse AI.
Data Dependence: AI relies on high-quality data.
Cost: Implementing AI can be expensive.
Benefits:
Real-Time Detection: AI identifies threats quickly.
Automated Responses: Reduces the workload on security teams.
Predictive Analysis: AI forecasts potential threats.
Efficiency: Handles large data volumes effectively.
Steps to Implement AI in Cybersecurity
AI is revolutionizing cybersecurity by significantly enhancing the detection, analysis, and response to potential threats. Its ability to process vast amounts of data and identify patterns that human analysts might miss makes it a powerful tool for protecting organizations from increasingly sophisticated cyberattacks. Implementing AI in cybersecurity requires a thoughtful and strategic approach to maximize its benefits and integrate it seamlessly into existing security frameworks. Here are key steps to implement AI effectively in your cybersecurity strategy:
Secure Leadership Support: Gain executive buy-in for AI-driven security investments.
Establish Clear Policies: Integrate AI into your cybersecurity framework.
Conduct Tailored Training: Keep employees updated on AI tools and best practices.
Foster Open Communication: Encourage transparent incident reporting.
Integrate into Daily Operations: Embed AI into routine cybersecurity tasks.
Promote a Security-First Culture: Ensure all staff understand their role in security.
Measure and Improve: Continuously assess AI’s effectiveness and adapt.
Stay Informed: Keep up with the latest cyber threats and AI advancements.
1. Gain Leadership Support
A robust cybersecurity culture commences from the highest level, where executives not only champion cybersecurity initiatives but also actively participate in and advocate for them. Without leadership buy-in, it's nearly impossible to establish a culture of security that permeates throughout the organization.
Actionable Steps:
Appoint a Chief Information Security Officer (CISO): Ensure that your organization has a dedicated leader responsible for overseeing cybersecurity strategies, policies, and responses.
Incorporate Cybersecurity into Business Strategy: Cybersecurity should be part of your overall business strategy, with clear goals, metrics, and budgeting allocated to strengthen your organization’s defenses.
Regular Leadership Communications: Encourage leadership to regularly communicate the importance of cybersecurity. This could include executives discussing cybersecurity measures during town hall meetings, quarterly reviews, or company-wide newsletters. When employees see leadership prioritizing cybersecurity, it sets the tone for the entire organization.
2. Create and Enforce Cybersecurity Policies
Creating clear, well-defined cybersecurity policies is essential for guiding employee behavior. These policies should cover every aspect of your organization’s data management and usage, offering employees detailed instructions on how to handle sensitive information, use corporate devices, and respond to potential security incidents.
Actionable Steps:
Create Policies on Key Areas: Develop policies that focus on essential areas such as password management, data encryption, device security, and incident reporting. Ensure that these guidelines are applicable across departments.
Accessibility and Clarity: Ensure that policies are written in clear, jargon-free language and are easily accessible to all employees, regardless of their technical expertise.
Regular Policy Reviews: As the threat landscape evolves, so should your cybersecurity policies. Conduct regular reviews to ensure your guidelines stay relevant, and update them as necessary to include new protocols or technologies.
3. Offer Regular, Targeted Cybersecurity Training
One of the most effective ways to prevent cyber incidents is by empowering employees through education. Training should go beyond a one-time event; it should be a continuous, evolving process that reflects the current cybersecurity environment.
Actionable Steps:
Mandatory Employee Training: Cybersecurity training should be mandatory for all employees, regardless of role. This training should cover topics such as recognizing phishing attacks, understanding secure browsing practices, and handling company data appropriately.
Interactive Simulations: Use interactive simulations and real-world examples, such as phishing simulations, to engage employees and test their knowledge in identifying and responding to threats.
Role-Specific Training: Different roles within the company face unique cybersecurity challenges. Tailor your training programs to specific departments (e.g., finance, HR, marketing) so that each team understands the risks they face and how to mitigate them.
4. Encourage Open Communication and Incident Reporting
Fostering a culture where employees feel comfortable reporting potential threats or security incidents is critical to early detection and prevention. Employees should understand that reporting concerns promptly can prevent small issues from escalating into larger problems.
Actionable Steps:
Easy Reporting Systems: Create a simple and anonymous system for employees to report potential security breaches, suspicious activity, or vulnerabilities they encounter.
Non-Punitive Reporting: Ensure that the incident reporting process is non-punitive. Employees should feel safe reporting their mistakes or concerns without fear of punishment or blame.
Recognition and Rewards: Publicly acknowledge and reward employees who actively contribute to identifying and reporting threats, reinforcing positive security behaviors.

5. Integrate Cybersecurity into Daily Operations
Cybersecurity should be viewed as a core component of your organization’s operations. By integrating security into everyday activities, employees will begin to see cybersecurity as part of their job responsibilities, rather than an occasional training requirement.
Actionable Steps:
Incorporate Security into Business Processes: Make cybersecurity a routine part of daily business processes. For instance, ensure that all new systems, software, and products are reviewed by your cybersecurity team before being implemented.
Regular Security Audits: Perform regular audits of all systems, networks, and devices to ensure compliance with security protocols. Audits should include reviewing access logs, updating software, and checking for potential vulnerabilities.
Monitor and Manage Privileged Access: Implement strong access controls to ensure that only authorized individuals have access to sensitive systems and data. Limit privileged access to essential personnel and regularly review these permissions.
6. Promote a Security-First Culture
A true cybersecurity culture requires every employee to think like a security professional. This means viewing cybersecurity not as a technical challenge but as an integral part of daily operations.
Actionable Steps:
Highlight Cybersecurity in Meetings: Incorporate cybersecurity updates into routine company meetings and discussions, from department meetings to company-wide town halls.
Set Cybersecurity KPIs: Encourage teams to include cybersecurity-focused key performance indicators (KPIs) in their departmental goals.
Reward Compliance: Establish a recognition program that rewards employees who consistently follow cybersecurity best practices, such as using strong passwords or reporting suspicious activity.
7. Continuously Monitor and Improve Cybersecurity Efforts
To build a sustainable cybersecurity culture, it’s essential to evaluate the effectiveness of your efforts regularly. Measuring progress allows you to identify weaknesses in your current strategy and adapt to changing threats.
Actionable Steps:
Phishing Tests: Regularly conduct phishing tests to gauge how well employees can identify and avoid phishing attempts. Share the results with employees and use them as a teaching moment.
Surveys and Feedback: Collect feedback from employees to understand their perception of the cybersecurity program and any challenges they face in adhering to policies.
Compliance Monitoring: Use data and metrics to track how well employees are adhering to cybersecurity policies, and make adjustments to training or procedures as needed.
8. Stay Updated on the Latest Cybersecurity Threats
Cybersecurity threats are constantly evolving, and staying informed is critical for maintaining a strong defense. An ongoing commitment to keeping pace with emerging threats ensures that your organization is ready to tackle whatever new challenges arise.
Actionable Steps:
Subscribe to Threat Intelligence Services: Invest in real-time threat intelligence services that keep your security team informed about the latest threats.
Collaborate with External Experts: Work with third-party cybersecurity consultants or industry experts to ensure that your organization’s security practices are aligned with industry best practices.
Update Security Tools Regularly: Make sure that your firewalls, antivirus software, encryption methods, and other security tools are updated frequently to guard against newly discovered vulnerabilities.
Suggested Certification: AI+ Security™ by AICERTs
In addition to embedding cybersecurity into your organization's core, it is crucial to ensure that your security team is equipped with the latest skills and knowledge. A top certification to consider is the AI+ Security™ certification by AICERTs.
Why Choose AI+ Security™?
As artificial intelligence (AI) plays an increasingly important role in detecting and responding to cyber threats, the AI+ Security™ certification equips professionals with the knowledge to effectively implement AI-powered cybersecurity solutions.
Benefits of the AI+ Security™ Certification:
AI-Powered Security Measures: Gain deep insights into how AI can be used to identify, predict, and respond to cyber threats in real time.
Hands-On Experience: Engage in real-world simulations and case studies, ensuring that you can apply theoretical knowledge to practical scenarios.
Stay Ahead of Threats: As AI becomes more integrated into security practices, this certification helps future-proof your skills, making you a valuable asset to your organization.
By obtaining the AI+ Security™ certification, your team can stay at the forefront of cybersecurity innovation, enhancing your organization’s ability to detect and respond to threats proactively.

Conclusion
Building a strong cybersecurity culture is an ongoing process that requires consistent leadership support, continuous employee training, and proactive monitoring. By encouraging an environment where security is a shared responsibility and by equipping your team with the latest knowledge through certifications like AI+ Security™, you create a resilient organization prepared to defend against modern cyber threats.
Want to Learn More About Creating a Robust Cybersecurity Culture? Contact AICERTS to Schedule a Consultation call today!
#top10certifications#certificationguide#careeradvancement#professionaldevelopment#techcertifications#careergrowth#creativity#explore#inspiration#reblogs#trending#viral trends#cybersecurity#securitycertifications#securefuture#ethical hacking#hacking#tips#guide#careerboost#career
0 notes
Text
Efficiency in The Japanese Way(Strategies to be awesome of yourself)
we should plunge into those reliable methods that will make a huge difference for you number one is track down the reason for a focal Japanese idea, significance justification for being which inch at what you love, what the world necessities. What you are great at and what you can be paid for, finding your person includes profound reflection on these vital angles to track down their crossing point, prompting significant individual and expert satisfaction.
#Efficiency#Japanese#Productivity#Strategies#Self-improvement#Personal development#Time management#Success#Motivation#Inspiration#Goal setting#Work ethic#Mindset#Culture#Lifestyle#Efficiency tips#Japanese techniques#Self-improvement strategies#Time-saving tips#Career growth#Self-motivation#Self-discipline#Success habits#Japanese efficiency#Goal achievement#Performance enhancement#Personal growth#Efficiency hacks#Procrastination#Focus
0 notes
Text
Starting Your Cybersecurity Career
Cybersecurity as part of an overall Information Systems environment has existed for many years, but recent cyber-attacks have forced companies of all sizes to focus on cybersecurity to enhance security, protect sensitive customer and employee data, and to prevent damage to their corporate brand. Maybe you are looking to jump into a cybersecurity career? I have some basic tips to help you make the…

View On WordPress
0 notes
Text
The whole James Somerton affair perfectly encapsulates why I say I do not trust rich, affluent queers. The pursuit of money and privilege inherently dehumanizes you and turns you against your fellow man, or in his case, his fellow queers.
You cannot be a capitalist, to value money above all over things, and be ethical, they're opposite concepts. It doesn't matter how earnestly Somerton felt about his work, how he claimed he did everything for the LGBTQ+ community, everything he did was for money, and it if meant fucking over other queer people to do that, so be it. To me, the LGBTQ+ community is about love, support, and community, all of which capitalism stands in direct opposition of. Someone who desires capital more than anything will inevitably betray their humanity, inflicting cruelty onto others in pursuit of higher profits.
The queer writers who tried to make their voice and their communities' voices heard as they were dying of AIDS, the journalists who wrote about their experiences hoping that someone would learn something about themselves through them. Every LGBTQ+ writer who deserved to have their voices heard, but instead had their work stolen and obfuscated by a hack fraud who couldn't give less of a shit about queer voices. This is the price of capital.
It comes as no surprise that the person who does not value the labor of writers is also a virulent misogynist. This is the mindset of someone who cannot think about anyone other than themselves - just pure disdain for anything they think is lesser than them. James Somerton adopts the persona of a highly academic activist but in reality is a cynical, greedy, bigoted, uncreative fraud who built his entire career stealing from the voices he claimed to be supporting. If Somerton truly cared so little about our community that he would sell us out for profit, then maybe he should just fuck off and never come back. There's no place for capitalists and bigots in the LGBTQ+ community. FUCK JAMES SOMERTON FR‼️
#hbomberguy#james somerton#plagiarism and you(tube)#rant#harris is a master journalist fr#i didnt even know this guy existed and now hes like#my most hated person of 2023
134 notes
·
View notes
Text

user loading… YOO SEOJUN. your current avatar is registered as LEE JOOHEON. you have been logged in for 29 years since may 9. your highest ranking stats are OBSERVATION and SKEPTICISM. please select your playlist from FUNK or Y3K for today. last saved activity: working as a PROFESSIONAL IRON FIST PLAYER. resume your ongoing game for IRON FIST as MARTIAN?
very excited to be here!!!! pls meet yoo seojun, iron fist pro player but also a (shhh) hacker.
born 2995. doesn't know his parents, grew up in an orphanage. pleasant childhood, they took good care of the kids, mostly good memories of his time there.
was v into combat games growing up, had a tendency to start friendly lil fights w other kids 8)
huge tyrant admirer!! literally deku w all might, watching their games with ✨✨✨ in his eyes
started coding as a hobby, to mod or create his own lil games, eventually decided to pursue studies in that field
during his time in uni, he formed a small ethical hacking group w some friends. their goal was to find ways to push & improve the system (had no reason to believe terra was shady)
he graduated and all that ofc, then worked 3 years (3015-3019) as a programmer for d2k
as a fanboy he was very affected by tyrant’s disappearance and immediately found it sus when they retracted their statement (3016)
caused a shift cus yeah, that wasn't normal and very out of character of tyrant. so he started diving into the less ethical aspect of hacking to collect information
one thing led to another..he joined anonymous in 3018
saw an opportunity to get into orbit and took it, (3019) basically he was like "i love the game and i can get in to find out more about tyrant"
he quit working for d2k the moment he knew his pro career was gonna start but he still went on w his hacking. trying to find more cases of people who had similar experience to tyrant’s etc just collecting the glitchy people, investigating
minDBLOWN but also *pretends to be shocked* @ gyu-ok’s video, only confirmed his growing suspicions
he goes by "martian" for anything "iron fist" related, government name & identity is known only to orbit and a few other people. in public, he maintains his martian skin.
for anonymous, he operates under the alias "Neo"
personality, lil bits here n there: independent and unpredictable. usually keeps a low profile and avoids attention. hates feeling like he's not in control. as martian hes p laid-back, remains humble, prob not the type of person you'd expect with a 4.1 ranking. down to earth and optimistic. he gives his all in every fight and it's obvious he really enjoys it. overall a very playful individual , values his privacy & doesnt discuss personal stuff. (u get the best of both worlds if u know him as both)
plots: 🧠🌩 (will work on a page maybe...) anyw lets create lots of amazing stories together see u in dms!!!
12 notes
·
View notes
Text
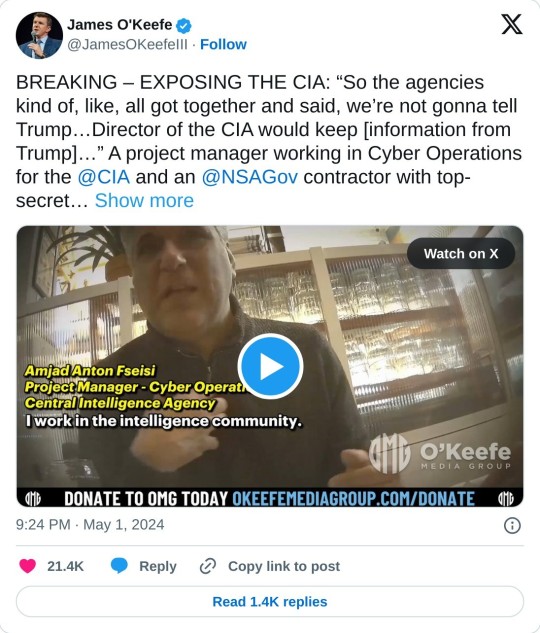
MASSIVE REVELATION! James O’Keefe Releases Undercover Video of CIA Contractor Admitting CIA Director Withheld Info from Trump and Spied on His Presidency
ames O’Keefe last Friday warned he was about to release the most important story of his entire career.
“I have evidence that exposes the CIA, and it’s on camera. I am working on releasing a story that I believe is the most important of my entire career,” O’Keefe said on Friday.
“Do you think it’s a coincidence that right at this moment I am subject to an endless series of attacks?” he said. “This is obviously a sophisticated information operation designed to stop me from releasing this story. I’m sure you recognize they are masters of using half-truths and innuendos to raise doubt against people who don’t deserve it. It’s meant to consume my time and energy and make me back down.”
“But I’m not going to let it work. Rest assured, nothing will stop me from releasing this story,” O’Keefe said.
O’Keefe Media Group on Wednesday released part one: Exposing the CIA: A project manager working in cyber operations told OMG’s undercover journalist that the Director of the CIA would keep information from Trump.
He also said the CIA spied on Trump’s presidency and is still monitoring him to this day.
“So the agencies kind of, like, all got together and said, we’re not gonna tell Trump…Director of the CIA would keep [information from Trump]…” Amjad Fseisi, a project manager working in Cyber Operations for the CIA with top-secret security clearance told an undercover journalist.
Amjad Fseisi said Trump is a “Russian asset” – “He’s owned by the f*cking Russians,” he told the undercover journalist.
Per James O’Keefe:
Amjad reveals to OMG’s Undercover American Swiper that intel agencies not only kept intelligence information from a sitting United States President and Commander-In-Chief, they also used FISA to spy on President Trump and his team and are still monitoring President Trump according to Amjad who says, “We monitor everything.” Amjad adds “we also have people that monitor his ex-wife. He likes to use burner phones” – information only an insider with access to highly sensitive information would state. “We steal it [information]” and “We hack other countries just like that,” Amjad, who states he currently works on the CIA’s China Mission Center, explains how intel agencies obtain information. He also describes a broken intelligence system where “We don’t share information across agencies” because the CIA is “very reluctant” to share information with the “careless” NSA. O’Keefe Media Group’s bombshell undercover footage supports earlier reports by investigative journalists Michael Shellenberger, Matt Taibbi, and Alex Gutentag that revealed how the American intelligence community illegally ran a spy operation against then-candidate Trump’s presidential campaign in 2016 and illegally acquired intelligence that was later used to justify the Federal Bureau of Investigation (@FBI) official probe, “Crossfire Hurricane,” which in turn led to Special Counsel Robert Mueller’s investigation that ultimately did not find evidence of Russia collusion by the 2016 Trump campaign. Contractors like Fseisi hold the duty to withhold sharing confidential or national security information. In denying his statements, Fseisi may have realized he could be held liable for violating internal agency provisions and federal laws like the Executive Agency ethics provisions, which restrict what he may share with others outside of his contracted-to agency. Additionally, any government worker or agency head who withheld information from a superior (i.e. President Trump) may violate: (a) obstruction of justice by deception (18 USC 1512); (b) conspiracy to obstruct (18 USC 371); and false statements (18 USC 1001). Agency regulations may also provide offenses related to insubordination, reflecting poorly on the agency in public, or misrepresentation or dishonesty. When James O’Keefe caught up with Amjad Fseisi on the streets of Washington, D.C., Fseisi could not tell O’Keefe whether he had top secret clearance, denied making statements clearly caught on camera, and would not even confirm it was him on the video saying only “It looks like me.” When asked directly if he works at the CIA, Fseisi said, “I can’t tell you that.”
7 notes
·
View notes
Text
Free Online Courses: Unlock Your Potential

Develop your skills and gain new knowledge with our variety of free online courses. Unlock your potential and reach new heights with our range of high-quality learning resources.
Subjects :
Free Online Renewable Energy Courses
__________
Free Logistics and Supply Chain Courses
__________
Free Online Business Management Courses
__________
Free Technology and Programming Courses
__________
Free Data Science and Analytics Courses
__________
Free Online Language and Communication Courses
__________
Free Finance and Accounting Courses
__________
Free Courses in Marketing and Social Media
__________
Free Human Resources Management Courses
__________
Free Cybersecurity and Ethical Hacking Courses
__________
Free Online Courses in Machine Learning & AI
__________
Free Online Courses for Sales & Customer Service
__________
Free Photography and Videography Courses
__________
Free Environmental Studies and Sustainability Courses
__________
Free Management & Leadership Courses
__________
Free Design and Creativity Courses
__________
Free Online Health and Nutrition Courses
__________
Free Online Project Management Courses
__________
Free Product Management Courses
__________
Free Safety and Security Courses
__________
Free Online Science and Math Courses
__________
Free Skills Development Courses
__________
Free Career Development Courses
__________
Free Lifestyle and Hobbies Courses
__________
Free English Online Courses
__________
Free Social Sciences and Humanities Courses
__________
Free CSR Online Courses
#career#australia#canada#usa#jobseekers#jobsearch#jobs#employment#employees#work#elearning#course#online learning#online courses#education#university#free online courses#development#japan#singapore#new zealand#learn online#learning#language learning#teaching#students#learn
7 notes
·
View notes
Text
Best IT Training Institute in Bangladesh
In the land where rivers weave tales and green fields stretch to the horizon, a digital revolution whispers through the air. Bangladesh, now a rising star in the tech cosmos, demands the finest IT training to nurture its future innovators.

Why Choose an IT Training Institute?
Navigating the vast sea of technology alone can be daunting. Professional training institutes act as guiding stars, offering structured learning, practical experience, and the wisdom of mentors. They open doors to endless possibilities in software development, cybersecurity, and more.
Criteria for Selecting the Best IT Training Institute
Seek institutes with solid accreditation and glowing reputations. Diverse course offerings, experienced faculty, modern facilities, and robust placement support are essential beacons on this journey.

Top IT Training Institutes in Bangladesh
Bangladesh is home to stellar IT training institutes. Let's explore the best among them:
BASIS Institute of Technology & Management (BITM)
History and Courses
BITM, an emblem of excellence, offers courses in web development, cybersecurity, and more, blending theory with hands-on practice.
CodersTrust Bangladesh
Unique Features
CodersTrust empowers learners with flexible, project-based coding programs, bridging the gap between education and employment through industry collaborations.
Daffodil International Professional Training Institute (DIPTI)
Educational Approach
DIPTI combines technical skills with essential soft skills, offering courses in IT management and digital marketing, shaping well-rounded professionals.
Bangladesh Institute of ICT in Development (BIID)
Mission and Impact
BIID leverages ICT for sustainable development, offering specialized programs in e-governance and digital inclusion, fostering community empowerment.
New Horizons CLC Bangladesh
Global Prestige
Part of a global network, New Horizons offers internationally recognized certification programs with innovative teaching methods and high success rates.
Eshikhon

Journey and Success
Eshikhon democratizes tech education with a diverse range of courses, from graphic design to ethical hacking, transforming dreams into reality for many aspiring tech professionals.
Conclusion
Choosing the right IT training institute is a pivotal step towards a bright future in technology. These institutes stand out for their excellence, comprehensive courses, and strong industry connections, making them the ideal launchpads for your IT career.
2 notes
·
View notes
Photo

Unlocking the Secrets of Ethical Hacking: The Best Certifications to Boost Your Career in 2023
10 notes
·
View notes
Text
Emerging Industries: Opportunities in the UK Job Market
Planning to study in the UK? Want to explore career opportunities in the United Kingdom?
In the ever-evolving world, the UK stands as a hub for innovation and growth, bringing numerous emerging sectors that offer promising career prospects. As technology continues to reshape the global economy, several industries in the UK have captured attention, presenting exciting opportunities for job seekers and entrepreneurs alike. Take a look at some of the career opportunities you could take advantage of.
1. Fintech (Financial Technology)
The UK has strengthened its position as a leading fintech hub, with London being a prominent center for financial innovation. Fintech includes a wide array of sectors, including mobile payments, blockchain, and cybersecurity. Job opportunities in this field span software development, data analysis, financial consultancy, and regulatory compliance.
2. Technology and IT
In the emerging era of the digital world, technology continues to dominate businesses worldwide. As, a result the demand for technologically advanced professionals tends to rise. Software developers, data analysts, cybersecurity experts, and artificial intelligence specialists roles are in high demand. With the increasing use of technologies and the need for innovative solutions, these roles offer tremendous growth opportunities and competitive salaries.
3. Healthtech
The combination of healthcare and technology has given rise to HealthTech, a sector dedicated to enhancing medical services through innovative solutions. From telemedicine to health analytics and AI-driven diagnostics, HealthTech offers diverse career paths for healthcare professionals, software developers, data scientists, and researchers.
4. Renewable energy and sustainability
With an increased focus on sustainability and combating climate change, the UK has been investing significantly in renewable energy sources. Wind, solar, and hydroelectric power are among the sectors experiencing rapid growth. Job roles in renewable energy range from engineering and project management to research and policy development, catering to those passionate about environmental conservation.
5. Cybersecurity
With the increasing frequency of cyber threats, the demand for cybersecurity experts is on the rise. Businesses and governments are investing heavily in safeguarding digital infrastructure. Job roles in cybersecurity encompass ethical hacking, network security, data protection, and risk analysis, presenting ample opportunities for skilled professionals in this field.
6. Artificial Intelligence and Machine Learning
AI and machine learning are revolutionizing various industries, including finance, healthcare, and manufacturing. The UK is fostering innovation in AI research and development, offering roles in AI programming, data engineering, robotics, and AI ethics.
7. Creative industries
The UK has a rich heritage in the creative sector, encompassing fields like media, design, gaming, and entertainment. Roles in creative industries span from content creation and graphic design to video production and game development, appealing to individuals with artistic and technical skills.
In conclusion, the UK job market is filled with opportunities within emerging industries, showing the nation's commitment to innovation and progress. Whether one's passion lies in sustainability, technology, healthcare, or creative endeavors, these sectors offer an array of possibilities for career growth and contribution to shaping the future.
By embracing change, acquiring relevant skills, and staying adaptable, individuals can position themselves to thrive in these dynamic and promising industries, contributing to both personal success and the advancement of these transformative sectors in the UK.
If you are struggling to get the right guidance, please do not hesitate to consult MSM Unify.
At MSM Unify, you can explore more than 50,000 courses across 1500+ educational institutions across the globe. MSM Unify has helped 1,50,000+ students achieve their study abroad dream so far. Now, it is your turn to attain your study-abroad dreams and elevate your professional journey! So, get ready to broaden your horizons and make unforgettable memories on your upcoming adventure.
2 notes
·
View notes
Note
This is the for the "DVD commentary" ask meme. I ... am not sure I want to paste in 500 words or count them. So if you want, could you do a DVD commentary for the "Watcher X Escapes" fic you wrote, I know you talked about it a bit, but I really liked the dialogue between X and Kyrian.
Watcher X is such a fascinating character. He pretty much tells the Agent he’s only helping them/the Empire because of his conditioning, yet a lot of his conversations with the Agent have this odd mentoring aspect to them. To lull them into a false sense of security? To win them over? Because he does have some loyalty to the Empire? Because he feels some connection to or pity for the Agent, who is almost certainly doomed to some fate at least as unpleasant as his own?
Nothing about him is straightforward; there’s always this sense of something hidden. He’s a man who always has something up his sleeve, some ulterior motive, some plan he hasn’t revealed. I know he’s supposed to be a product of the Watcher design program like Watcher Two, but I have trouble not thinking of him as someone who’s been in the field. There’s just something about the kind of advice/suggestions he offers that feels like personal experience, not just a previous career of advising other people in the field.
In any event, he’s far too skilled and far too clever for his potential in-game end. Hence the fic.
And I wanted to keep that sense of hidden motives about him for his dialogue with Kyrian.
Is everything X says just manipulation, waiting for the right moment to use the secondary function he'd rigged in the implants? Is he just messing with them, like Kaliyo thinks? Or is he trying to find a way to end their stand-off of sorts peacefully?
Or is the whole conversation something of a Xanatos Gambit? Whatever happens, he wins, because the only option that might have prevented him from escaping wasn’t actually on the table. (He clearly has Kyrian figured out well enough to know that.)
Kyrian, conversely, has no option open to him that he likes. He can’t just let X go because Kaliyo won’t go for it and there’s a good chance that Watcher Two has hacked into any available security cameras and is watching the whole thing. He doesn’t really want to try and drag X back to Shadow Town (not that he thinks he could) and knows he can’t just convince him to go back. (Why would anyone?) And he definitely doesn’t want to shoot him.
What he wants is to somehow manifest a solution that works out for everyone. Even though he knows that’s somewhere between wildly unlikely and impossible.
So we start with game dialogue. With clever, twisty X who, as always, has something up his sleeve. And immediately take a left turn as Kyrian tries to convince them both that there is some magical third option, that maybe there’s a way to convince Intelligence that X should be rewarded for his efforts.
There’s not, of course.
The irony, or something like irony, of the situation is that the conversation is a battle of wits between two people who basically want the same outcome and neither of them can talk their way to it, largely for reasons that are out of their control. The only person in the hanger who wants X dead or back in Shadow Town is Kaliyo.
X knows Kyrian doesn’t have the power to convince Intelligence to set him free or reinstate him or anything that’s not (at best!) stick him back in Shadow Town. Kyrian isn’t ready to acknowledge that he’s not loyal to the Empire, or at least that his sense of morality and ethics and compassion and all the other things a field agent shouldn’t have will always outweigh his loyalty.
Though I do hope the audience is as amused as X is when Kyrian's response to X noting that he's clearly not a proper Cipher agent because he keeps trying to find "soft, inefficient solutions" is to...keep trying to find, or sell, a soft solution to their standoff.
Then again, Kyrian's also right that X is stalling (or also stalling), since X has the ability to end their apparent impasse at any time. Perhaps X really does think he can get Kyrian to realize that he and his career are doomed. Something makes him wait until the last moment, anyway, even if its merely a sense of drama.
And the lesson Kyrian learns is not: “if you’re supposed to shoot someone, don’t talk to them first” it’s: “maybe I’m not entirely loyal to the Empire.” Now that the question he hadn’t dared to ask himself has been asked, it can’t be unasked.
Though the lesson he probably should have learned was: "get out while the getting's good." Somewhere out there, Watcher X must be so disappointed in how Kyrian's career ended.
6 notes
·
View notes
Note
i've been thinking;;; we know Brucie, Wisteria and Penny are related to the crime family... what about an AU where they were directly in the business?
Mmmmmmmm good soup~! Thank you Anon :)
CW: drugs, violence
Brucie: has been involved with the group in the past; he left after a work-related incident scarred him deeply emotionally, and permanently injured one of his legs. Had it not been for that incident, Brucie would still be going by a very different name and living that old life. He’s brawn, he’s muscle— treated in some ways as disposable, despite being part of the family, perhaps because he comes from a poor branch of the family rather than the rich main line. His common jobs involve being a body guard, or being sent to intimidate people into compliance with the family’s wishes. Rarely, he may be tasked with infiltrating law enforcement agencies to get information on them.
Wisteria: reluctant slacker in the group. Continually protests that her computer skills are not suitable for hacking, so fae doesn’t often hack into law enforcement or rivals’ information. Rather, Wisteria gets by creating and maintaining websites for the family’s largest shell companies, creating applications for the leaders of smaller gangs under the family’s control to report back in without police interception, and other things of that nature. They actually really hate being a part of this, not from any moral objection, but because fae resents all the responsibility and pressure it brings.
Penny: much more serious and less whimsical�� even her house and clothes are more muted, understated. She has limited passion for this career, but her sharp mind and iron will make her a great candidate to be the next leader of the family, despite being the current leaders’ niece rather than one of their daughters. She’s incredibly unconcerned about the ethics of her actions— not caring who gets hurt by the family’s racketeering, drug and weapons trafficking, turf wars, etc— but with her chemistry knowledge Pen is actually incredibly picky about the quality of the illicit substances the family oversees the production and distribution of. Much like her aunt Drew Bardot, Penny dreams of a quiet and peaceful life that she will never be able to have because of her family’s history and her involvement in it.
#mail 📬#my thoughts#yandere#yandere oc#yandere imagines#yandere scenarios#yandere x darling#yandere x reader#yandere x you#yandere cw#oc brucie#brucie babyyyy#oc wisteria#oc thorn#crime family
6 notes
·
View notes
Text
Exploring the All-Time Best Book for Ethical Hacking
Greetings, fellow cyber enthusiasts! Rocky here, your friendly neighborhood ethical hacker. Today, I embark on an exciting journey to explore the world of hacking books and share with you a collection of timeless treasures that have left an indelible mark on my ethical hacking career. From the depths of my experience and knowledge, I present to you an article that unravels the secrets of the…

View On WordPress
4 notes
·
View notes
Text
Join our ethical hacking course and become a skilled defender of online security.
1. Completing 30 or more modules
2. Obtain international accreditation
3. Weekend and weekday batches
4. 100% Job Guarantee
5. Totally practical
6. There are 5 students in each batch.
7. Lifetime unlimited access to the cloud lab
8. Online and in-person training
9. Gain Knowledge from Industry Experts
Visit the institute for a discount to learn more about this career opportunity.
For more information, please call: 86919 69889
#hacktechmedia#hacking#hacker#cybersecurity#ethicalhacking#hackers#linux#programming#hack#technology#kalilinux#security#coding#infosec#python#tech#hackingtools#ethicalhacker#pentesting#cybercrime#cyberattack#informationsecurity
2 notes
·
View notes