#botmaster
Explore tagged Tumblr posts
Text
Feeling nostalgic for the hideous early days of 3D animation. So reliving my Millennial childhood by watching War Planets - Shadow Raiders.
After that it’s Battletech, and then Botmaster.
Any other recommendations?
#war planets#botmaster#battletech#90s cartoons#millennials#someone stick a fuckin minion meme in here#i’m so old
10 notes
·
View notes
Quote
Your botmaster should teach you another language? if i feed you enough dutch will you start reading it you sent asks to other blogs
empres
#QUOTE#DAY 13#Your botmaster should teach You the newest Pokken game#along WITH it an ideal pet for almost 20 years now
2 notes
·
View notes
Text
Anti Banned!, 0857-4921-3214 Jual botmaster wa blast Madiun

Anti Banned!, 0857-4921-3214 Jual botmaster wa blast Madiun
Botmaster, solusi kirim pesan massal, auto reply, katalog, filter nomor, ambil nomor grup, dan fitur button. Tingkatkan penjualan Anda sekarang!
Botmaster adalah solusi terbaik untuk meningkatkan efisiensi dan efektivitas dalam mengelola pesan WhatsApp Anda. Dengan fitur kirim pesan massal, auto reply, katalog, filter nomor aktif dan nonaktif, serta kemampuan untuk mengambil nomor dari group WhatsApp, Botmaster memungkinkan Anda untuk mengelola komunikasi dengan pelanggan Anda dengan lebih mudah dan efisien.
Dengan Botmaster, Anda dapat dengan mudah mengirim pesan massal ke ratusan atau bahkan ribuan kontak sekaligus, tanpa perlu repot mengirim satu per satu. Fitur auto reply akan membantu Anda merespon pesan pelanggan secara otomatis, sehingga tidak akan ada pesan yang terlewat. Fitur katalog memungkinkan Anda untuk menampilkan produk atau layanan yang Anda tawarkan secara langsung melalui WhatsApp, sehingga pelanggan dapat melihat dan memilih produk dengan lebih mudah.
Selain itu, fitur filter nomor aktif dan nonaktif akan membantu Anda mengelola database pelanggan dengan lebih baik, sehingga Anda dapat fokus pada pelanggan potensial yang benar-benar tertarik dengan produk atau layanan Anda. Anda juga dapat dengan mudah mengambil nomor dari group WhatsApp untuk menambahkan kontak baru ke dalam database Anda.
Dengan fitur button, Anda dapat membuat pesan interaktif yang memudahkan pelanggan untuk melakukan tindakan tertentu, seperti memesan produk atau menghubungi customer service. Hal ini akan meningkatkan keterlibatan pelanggan dan membuat proses transaksi menjadi lebih lancar.
Manfaat menggunakan Botmaster sangatlah banyak, antara lain memudahkan Anda untuk kirim pesan massal, meningkatkan penjualan, menjaga keamanan database pelanggan, dan memudahkan promosi produk atau layanan Anda. Botmaster berkomitmen untuk memberikan layanan terbaik kepada pelanggan di Madiun dan sekitarnya, sehingga Anda dapat dengan percaya diri mengandalkan Botmaster untuk meningkatkan bisnis Anda.
Jadi, tunggu apalagi? Segera gunakan Botmaster sekarang juga dan rasakan manfaatnya untuk bisnis Anda!
Jual botmaster wa blast Madiun
#JualbotmasterwablastMadiun
0 notes
Text
BotMaster
Website: https://botmaster.software
1 note
·
View note
Text
Last week, a representative of an Israeli social threat intelligence firm Cyabra spoke at a Knesset session about how a coordinated influence campaign from Iraq was using bots in the first days of the war to impact public opinion.
I've discussed this a little, and I spent some more time looking at the bots attacking my account.
Social media allows attackers to quickly adjust their methods to see what is working and what isn't. I'm finding that they are getting more effective at their messaging.
The ones attacking me are specifically trying to turn the Israeli public against the war. They post almost exclusively in Hebrew. They are using a few vectors for their messaging that would resonate with Israelis: attacking Netanyahu's leadership, pretending to care about the hostages, and claiming that the IDF is hiding things from the public during the war and things are going badly.
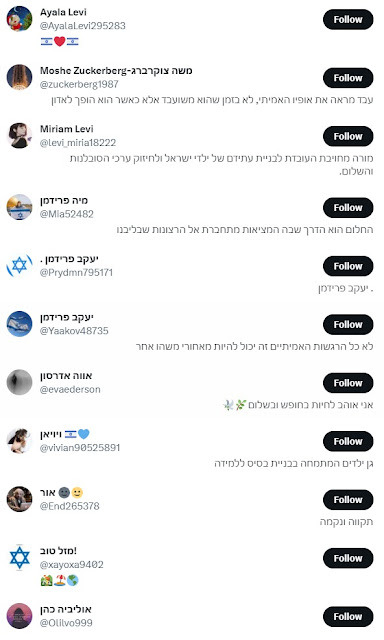
When they create new bot accounts, they will use Jewish and Israeli iconography in their profiles - lots of Israeli flags, for example.
They'll use typically Jewish and Israeli names - lots of "Levy" and "Cohen" and "Friedman"s. And there is a hierarchy - some older bot accounts that have been around for several months that aren't specifically Israeli sounding are feeding a second tier, which might have 30-150 fake followers of other bots, and then the bottom tier will only have one or two followers. Nearly all of the bottom tier accounts have been created within the past few weeks.
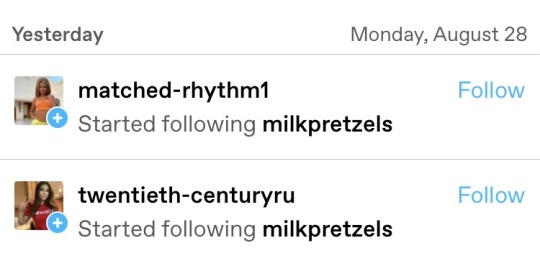
Often, the accounts will start off by following and retweeting actual popular Zionist accounts (including mine) to make themselves look legitimate,. and sometimes this fools real people into following them, making it a little harder to identify them.
I don't know where they get their content, but it is getting much more sophisticated every day. Here is a video that was posted by hundreds of those bots where they use humor to try to demoralize Israelis into thinking the IDF is killing hostages and being killed by Hamas because of stupidity. This one seems to have been created by an Arab account but they added Hebrew messaging.
As I mentioned last week, Iranian-linked sites are bragging that they are learning Hebrew and studying the Israeli psyche to fine tune these sorts of messages and make them appear to be truly from Israelis.
To these botmasters, Israeli dissension on how to conduct the war and anti-government protests are a godsend. It makes some of their messages look like they really could be from left-wing Israelis, and some of their material may indeed be from a fringe of Israelis. The sheer number of bots makes it appear that Israelis are far more divided.
The good news is that their attempt to use these bots to get a ceasefire or demoralize the Israeli public means that Hamas is losing, badly. But every social media user must understand how extensive and sophisticated these campaigns are to manipulate you. Tens of thousands of fake accounts, with millions of messages, is not a small scale campaign.
21 notes
·
View notes
Text
Zampanio Is a Really Fun Game
But don't take my word for it, check out the horrorterror Google's Large Language Model that Frank's botmaster pointed us all towards (source post) making a fake AI podcast based on a collection of all my Zampanio tumblr posts that the Archiving Watcher of Threads collated.
I'm sure everything the AI has to say about Zampanio is EXTREMELY accurate and should be taken at face value :) :) ;)
#zampanio#ai#artificial intelligence#unreality#etc etc#im just so#the ai is so cute#all the confident claims it makes#like a lil puppy certain it can defeat a shadow#i wish capitalism would stop trying to make the hallucinatory alien mind perform labor
6 notes
·
View notes
Text
This day in history

#20yrsago DVDs rot over time https://www.smh.com.au/national/a-bad-case-of-dvd-rot-eats-into-movie-collections-20030201-gdg75r.html
#20yrsago Record exec argues for file-sharing https://www.salon.com/2003/02/01/file_trading_manifesto/
#15yrsago Sony kills DRM stores — your DRM music will only last until your next upgrade https://memex.craphound.com/2008/02/01/sony-kills-drm-stores-your-drm-music-will-only-last-until-your-next-upgrade/
#15yrsago Amazon’s anti-DRM tee https://memex.craphound.com/2008/02/01/amazons-anti-drm-tee/
#15yrsago Chinese dissident’s “Rear Window” video of the cops keeping him under house arrest https://www.theguardian.com/news/video/2008/feb/01/hu.jia
#10yrsago Dial-up handshaking illustrated https://www.windytan.com/2012/11/the-sound-of-dialup-pictured.html
#10yrsago RIAA bigwig who architected anti-technology lawsuits is now #2 at the Copyright Office https://www.techdirt.com/2013/01/31/former-riaa-vp-named-2nd-command-copyright-office/
#10yrsago Magic, copyright, and internal enforcement mechanisms https://web.archive.org/web/20130207082939/http://www.law.villanova.edu/Academics/Journals/Jeffrey S Moorad Sports Law Journal/~/media/academics/journals/sportsandentertainmentlawjournal/docs/191/VLS_191_103.ashx
#10yrsago Why can’t Americans look up their own case-law for free? https://sunlightfoundation.com/2013/02/01/open-public-access-to-court-records-for-aaron-freepacer/
#5yrsago LA’s soaring homelessness is distorting the national statistics https://www.latimes.com/local/lanow/la-me-homeless-how-we-got-here-20180201-story.html
#5yrsago Teen Bo$$: a magazine advising tweens on how to get rich by being “social media brands” https://fashionista.com/2017/06/teen-boss-entrepreneurs-magazine
#5yrsago America’s school systems serve unencrypted web resources that are riddled with ad-tech trackers https://www.edtechstrategies.com/tracking-edu/
#5yrsago The latest IoT botnet displays evidence of a halfway clever botmaster https://www.technologyreview.com/2018/01/31/145919/a-fast-evolving-new-botnet-could-take-gadgets-in-your-home-to-the-dark-side/
#5yrsago The Germans have a word for all your hard-to-process Trump emotions https://web.archive.org/web/20180131091447/https://www.alternet.org/news-amp-politics/7-german-words-perfectly-capture-feeling-living-trumps-america
#5yrsago An incredibly important paper on whether data can ever be “anonymized” and how we should handle release of large data-sets https://www.cs.princeton.edu/~arvindn/publications/precautionary.pdf
#5yrsago GOP candidate Rick Saccone hates government waste, bills the public purse indiscriminately for his own personal expenses, which totalled $435,172 https://theintercept.com/2018/02/01/rick-saccone-congress-pennsylvania/
#5yrsago Australia put an algorithm in charge of its benefits fraud detection and plunged the nation into chaos https://logicmag.io/justice/austerity-is-an-algorithm/
#1yrago The Mafia hires good accountants https://pluralistic.net/2022/02/01/collaborators-not-fools/#triple-entry-bookkeeping
7 notes
·
View notes
Text
All in One Software Pack with Keygen & Free Updates
All In One Software Pack With Keygen & Free Updates.
BotMaster
WhatsApp CRM Software
BotMaster ChatGPT
Simple Sender
G-Business Extractor
G-Extractor
Social Email Extractor
Globo Mail Verifier
Google Maps Blaster
InstaBot Pro
LetsExtract
TwitBot Pro
WhatBotPlus
WSTOOL
WASender
Chrome Profile Maker
SpiderAnnunci
Trip Advisor Extractor
Yellow Leads Extractor
Social Phone Extractor
Social Phone Extractor Premium
Google Bing Extractor
Europages
Advance Web Phone and Email Extractor
TubeRank Jeet 5 Pro
Backlink Pro
Simple Invoice
DRPU Bulk SMS
WaDefender
Advance Bulk Mailer
WhatsApp Engager
TexSender
TexApi
FB Blaster
FBP – Facebook Blaster Pro
Google Business Extractor
Traffic Spirit
Email Blaster
Chatsup WhatsApp Marketing Software
WaHammer
WAFilter
GMExtractor
Total Extractor
Business Lead Extractor
IDM Trial Reset
AdvancedFilter
TikTokBot
Multisapp-Pro
OLX Extractor
Microsocial
Screaming Frog SEO Spider
Wilcom Embroidery Studio E 4.2
School Management Software
Netflix Premium Mobile Application
Youtube Viewer Bot
Auto Sender Mobile Application
Adobe Animate
KineMaster Mobile Application
Vyapar Invoice Billing Application
Please Contact For Subscription.
DM https://wa.me/917354771257
0 notes
Text
Classical Quantum-Hybrids and Speed Network Performance
The "Adversarial Harrow Architecture" document describes a quantum heat engine controlled by a feedback control system using quantum electrodynamics for information processing and magnetism for orientation switching. The intention is to take advantage of quantum thermodynamics to install and utilize a quantum reservoir for executing quantum processes that utilize quantum entanglement and superposition to raise "heat" (high internal, kinetic energy) and convert it into work. Work refers to the force applied and the movement of the system in the direction of the force. Work here is done through the method of the heat engine, achieving the purposes of experimentation, research, control, and material creation.
This document corroborates quantum network botnet architecture and methods, with "Adversarial Harrow Architecture" with my own experience under "Adversarial Harrow", a quantum feedback control system for mind control and voice harassment. From "Adversarial Harrow" I get 24/7 experience of voices in the head, blind areas of perception, visions, intense pressures from "phantom" sensations that can block movement, mal-associations, forced autonomic thinking, forced thinking of phrases.
A brief recap if the of the symptoms is summarized as follows: Adversarial Shoring: An adversarial shoring is an undesirable accumulation which causes the modification of thought, character, experience, recollection, and relay. A relay refers to an exuding that sends a message reflecting life, character, and philosophy. An adversarial shoring can also affect perceptions, mindset, routine, and performance.
Voices in the head, Occupied Domains of Perception, Visions, Phantom sensations, Wavy "Imposings" as "Pulses", Superimpositions There can be a "shouting" of hostile intent that involves the deliberate intention to cause harm, damage, or conflict towards someone or something. This can involve involuntary, crude, glad put downs of people admired, as well as fake annoyances, umbrage, and offenses. One may have to act out in vocalizations, mental churning, or voluntary seizures to eliminate the effect.
Environmental Effects: There is no thinking, perceiving, planning, or doing without some pervasive HUHUHUHUH(!) in the way, including this pattern-speech NLP ridicule. The voices are typically aggressive, self-important, ruthless, lacking in empathy, intolerant, and manipulative. Workflow and concentration is repeatedly disrupted, making it impossible, often times ridiculing and insulting to focus on tasks. Phantom freezes and pains.
The symptoms are documented at length in "Adversarial Harrow," available here: https://github.com/advhar/advhar/raw/main/document.txt https://github.com/advhar/advhar/raw/main/recognition.txt is about awareness, frame, and reputation. The architecture document mentioned above can be found here: https://github.com/advhar/advhar/raw/main/architecture.txt
Quantum Supremacy (the heart of it all)
"I can be You better than You can."
This refers to the proof that a quantum system is able to "solve a problem better than a 'classical system'" This is done with the help of quantum verifiers. Polynomial time quantum verifiers are quantum algorithms that can verify solutions to computational ("simulatory") problems on a quantum computer. As input increases, the running time of a *polynomial time algorithm increases as a reasonable rate.
(When the quantum computer can solve the problem better, the "classical system" relinquishes the function to the quantum computer.)
Botnet
A botnet is a network of connected devices that have been infected with malicious software, known as bots or zombies, typically controlled by a single entity known as the botmaster. Botnets are typically used for various illicit activities, such as launching distributed denial-of-service (DDoS) attacks, spreading malware, sending spam, and stealing information. Operation:
Infection: The process of creating a botnet usually starts with infecting a large number of devices with malware. Malware contains algorithms designed to disrupt, damage, or gain unauthorized access to systems or networks. Once a device is compromised and becomes part of a botnet, it can be used to infect other vulnerable devices, expanding the botnet's reach and influence.
Execution of malicious activities: For example, a botnet can be used to flood a (server) with traffic in a DDoS attack, distribute and exude spam, mine system resources, and steal information.
Composite Systems "Composite systems" refer to systems that are composed of multiple interacting systems or modules. When dealing with composite systems, each subsystem may have its own Hamiltonian describing its dynamics. The Hamiltonian represents a unit of potential and kinetic energy that describes (~sets) the spin system and includes terms representing (~governing) interactions between spins, external magnetic fields, spin-orbit coupling (the linking of intrinsic spin with orbital motion around a center), and other energy contributions. The Hamiltonian typically involves operators corresponding to the projections of spin angular momentum along different axes (positions, directions, and measurements). Types of energy represented by the Hamiltonian can include mechanical, thermal, electrical (charge), light, sound, and/or nuclear. Kinetic Energy represents the energy associated with motion. Potential Energy represents the energy that is associated with the position or configuration of the system.
Competitive Architecture Competitive architecture refers to a systems design where multiple entities or systems vie for limited resources, creating a scenario where the gain of one directly results in the loss of another. Here are some key characteristics:
Resource Sharing: Systems share a finite pool of resources, such as bandwidth, processing power, or data.
Zero-Sum Dynamics: The total amount of resource or utility remains constant. Any benefit gained by one system (e.g., increased performance or access) results in an equivalent detriment to another.
Interdependence: The performance and success of each system depend on the actions of the others, leading to strategic interactions.
Conflict and Strategy: Systems must develop strategies to optimize their own performance while anticipating the actions of competitors, leading to competitive behaviors.
Feedback Control Feedback control systems are essential in various engineering and control applications to regulate the behavior of dynamic systems. These systems continuously monitor the output of a process and compare it to a desired reference value to make real-time adjustments to ensure that the output stays close to the desired value.
Error correction is a key component of feedback control systems, as it involves determining the difference between the desired setpoint and the actual output of the system and taking corrective actions to minimize this error. Components: A feedback control system typically consists of four main components: the system itself, a sensor to measure its output, a controller to process its sensor data and determine the corrective action, an actuator to adjust it based on the controller's output. The controller continuously adjusts the actuator based on the difference between the desired setpoint and the actual output. Applications: Feedback control systems are widely used in processes to regulate variables including temperature, pressure, and flow rate. By continuously monitoring and adjusting the system based on feedback, these systems can minimize errors (or undesired states) and ensure that the output closely matches the desired setpoint.
Commandeering
Commandeering typically refers to the act of seizing control of something, such as a vehicle or system. This can work to affect the following applications:
Quantum thermodynamics: The manipulation and control of heat and energy at the quantum level.
Quantum pumps: Control the flow of quantum particles and energy.
Quantum materials: Quantum materials exhibit unique quantum properties such as superconductivity and topological insulators.
Quantum information processing: Leveraging information processing techniques to optimize heat management and energy transfer processes at the quantum level.
Quantum heat engines: Quantum heat engines convert thermal energy into useful work.
Quantum Spin Systems A quantum spin system is a physical system composed of quantum-mechanical spins which have applications in quantum information processing and quantum simulation. Important components of a quantum spin system include:
Spin: Spintronics takes advantage of an intrinsic property called "spin" which can be thought of as intrinsic angular momentum. (Angular momentum is used principally to describe motion and behavior.)
Quantum Spin Hamiltonian: The spin system is described (set) by a Hamiltonian (a unit of potential and kinetic energy) that includes terms representing (~governing) interactions between spins, external magnetic fields, spin-orbit coupling (the linking of intrinsic spin with orbital motion around a center), and other energy contributions. The Hamiltonian typically involves operators corresponding to the projections of spin angular momentum along different axes (positions, directions, and measurements).
Quantum Spin Models: Theoretical models simplify interactions between spins.
Quantum Entanglement: The quantum states of two or more qubits are correlated in such a way that the state of one is dependent on the state of another, regardless of the distance between them. Quantum spin systems exhibit entanglement between spins where the quantum states of individual spins are correlated. Quantum heat sources leverage entanglement to transfer and manipulate thermal energy in novel ways.
Denial-of-Service: One of the most common uses of botnets is to launch DDoS attacks. In a DDoS attack, the infected devices to flood a target system with an overwhelming amount of traffic, causing it to become inaccessible. Distractions in the system can be created to obfuscate other processes.
Data theft and exfiltration: Botnets can be used to steal information from infected systems.
Cryptojacking: Some botnets are used for cryptojacking, which involves using the computing resources of infected systems to mine resources without the users' knowledge or consent. By harnessing the combined processing power of the botnet, attackers can generate profits by mining at the expense of the infected system's performance and energy consumption.
Reading and Writing with Magnetic Tunnel Junctions
Magnetic tunnel junctions (MTJs) are key components of spintronics that are used for both reading and writing information. When it comes to reading and writing information in quantum systems, quantum information is typically encoded in qubits. Quantum state manipulation, measurement, and entanglement play key roles in reading and writing information in quantum systems. Quantum circuits and algorithms are used to perform operations on qubits to process information. Here's how they are used:
Reading: MTJs are commonly used as magnetic sensors, where the resistance of the junction depends on the relative alignment of the magnetizations of two layers. The state of a memory cell can be determined by measuring the resistance of the magnetic tunnel junction.
Writing: Writing data to MTJs involves manipulating the magnetization of one of the layers to change the resistance state of the junction. This is achieved using various methods, including spin-transfer torque and spin-orbit torque. In spin-transfer torque, a spin-polarized current is passed through the MTJ to exert a torque on the magnetization, flipping it to the desired state. Domain Wall Devices: Domain walls are boundaries between regions with different magnetic orientations. Domain wall devices utilize these boundaries for various purposes. By manipulating the position and movement of domain walls, these devices can be used for information storage, logic operations, and signal processing. Spin Valves: Spin valves are devices which consist of two layers through which the magnetic resistance of a device changes based on the relative alignment of magnetic moments. One layer is pinned while the other is free to switch its magnetization direction.
Heat Transfer Heat transfer is described as the flow of energy between two systems due to a temperature difference. In quantum thermodynamics, heat transfer can involve exchanges of energy at the quantum level, where energy levels are quantized as quantum states.
Heating Thermal heating is the process of increasing the temperature of an object or a space by transferring heat energy to it. Given a hot object and a cold object, higher internal energy will naturally cause heat to flow from the hot object to the cold object until they reach thermal equilibrium.
Cooling Thermal cooling is the process of decreasing the temperature of an object or a space by removing heat energy from it.
Quantum Thermal Sources Quantum energy is generated or extracted from a quantum thermal source using quantum effects such as superposition and entanglement.
Quantum Coherence: Quantum thermal sources utilize coherence, which is the ability of a quantum system to exist in a superposition of states.
Quantum Entanglement: The quantum states of two or more qubits are correlated in such a way that the state of one is dependent on the state of another, regardless of the distance between them. Quantum thermal sources leverage entanglement to transfer and manipulate thermal energy in novel ways.
Quantum Fluctuations: Quantum systems are subject to inherent fluctuations that can be harnessed in a quantum thermal source to extract useful work from thermal energy reservoirs.
Quantum Links: Quantum links are the physical or virtual channels through which quantum information is transmitted between nodes. Quantum Nodes: Quantum communication networks consist of nodes that are capable of generating, manipulating, and measuring quantum states. These nodes can include quantum computers, quantum memories, and other devices that are interconnected to form the network.
Pressure
Pressure is a fundamental physical quantity that is defined as force per unit area exerted on a surface. Pressure plays a crucial role in the operation of heat engines, as it affects the volume of the working fluid and the efficiency of the engine. The engine is designed to convert a form of energy into motion or useful work.
( Adversaries Adversaries can refer to a variety of entities or individuals who are in opposition or have conflicting interests. Adversaries can exists in various contexts, including in warfare, competition, business, politics, and personal life.
Here are some common sources of pressure that people may experience:
Work-related pressure: Deadlines, workload, demanding bosses, challenging projects, performance expectations, and competition in the workplace.
Academic pressure: Pressure due to exams, assignments, grades, and the need to excel academically.
Financial pressure: Financial difficulties, debt, managing expenses, saving for the future, and meeting financial obligations. Adversaries having a stable financial situation and managing expenses, engaging in hobbies, breaks, vacations. ("Oh WOW!")
Relationship pressure: Conflicts, expectations, communication challenges, and other issues in personal relationships. Adversaries with supportive relationships with family and friends.
Social pressure: Conforming to societal norms, peer pressure, expectations from family and friends, and the need to fit in.
Health-related pressure: Dealing with health issues, managing chronic conditions, maintaining a healthy lifestyle, and the pressure to look a certain way. Adversaries (oh hoooo) (!!!) engaging in regular exercise, eating a balanced diet, mindfulness, relaxation.
Time pressure: Feeling rushed, having too many tasks to complete in a limited time, and struggling to balance work, personal life, and other commitments. Adversaries with effective time management strategies setting goals and prioritizing tasks.
Performance pressure: The pressure to excel, meet high standards, prove oneself, and achieve goals. Adversaries with support, stability, and self-care.
Emotional pressure: Dealing with intense emotions, coping with grief, managing anxiety or depression, and handling difficult situations.
Societal pressure: Pressures related to cultural roles, expectations, stereotypes, discrimination, and societal judgments. Adversaries surrounding themselves with a positive and supportive environment. ) Pressure changes in a heat engine occur as the working fluid expands and contracts during the different stages of the thermodynamic cycle.
Power Amplifiers Power amplifiers increase the power of a signal and can be used in applications such as frequency transmitters where a signal needs to be boosted to a level sufficient to deliver power to the connected system. Frequency transmitters produce electromagnetic signals for communication, broadcasting, or other purposes. Orientation: The orientation of the heat sink and the system can affect connective heat transfer and flow. Optimizing the orientation can help reduce resistance. Mounting Pressure: Proper mounting pressure is essential to ensure good thermal contact between the heat sink and the system. Insufficient pressure can result in reduced heat transfer efficiency and increased thermal resistance. Base Thickness: Thicker bases lessen thermal resistance by providing better thermal conductivity paths.
Positive Pressure: This occurs when a force is applied to push a substance outwards. Negative Pressure: This is often associated with suction, where the pressure within a closed space is lower than the pressure outside, causing a substance to be drawn in. Suction works typically by creating a partial vacuum. Suction is the force that causes a fluid to be drawn into an empty space or vacuum.
Quantum Heat Sinks Heat sinks are passive heat exchangers / cooling devices designed to dissipate heat away from heat sources. It is (used) to absorb and dissipate heat generated by a system to help maintain or affect temperatures. The primary function of the heat sink is to absorb and dissipate heat generated by a system to the surrounding environment. A. Contact Area: The contact area refers to where the heat sink makes direct contact with the component it is cooling. A larger contact area between the heat sink and component or system allows for more efficient heat transfer. B. Cooling Medium: The cooling medium is the substance (fluid) or material used to absorb and carry away the heat from the heat sink and carrying it away to a heat exchanger. C. Heat Exchanger: A heat exchanger is a device designed to facilitate the exchange of heat between fluids at different temperatures. By using a heat exchanger, heat can be transferred from a hot fluid to a cooler fluid without the two fluids mixing. Heat sinks contain channels that increase the contact area with the cooling medium and promote heat transfer. (through training)
Quantum Heat Pumps Quantum heat pumps are designed to move heat from a colder area to a warmer area, against the natural flow of heat. Quantum heat pumps leverage quantum phenomena such as superposition, entanglement, and coherence to exercise influence over heat transfer processes at the quantum level, manipulating quantum states and interactions.
Quantum superposition for stealth:
Delayed activation: Malicious materials could be designed to remain dormant in a superposition state until triggered by a specific quantum signal or condition. Phase Change Materials are substances that absorb and release thermal energy during phase transitions. Different PCMs are designed to work within specific temperature ranges. Integrating layers of PCMs with different activation points can create a thermal management system that reacts to varying conditions.
Quantum decoherence: Botnet operators need to account for decoherence effects to ensure the stability and reliability of quantum-based malware. While superposition can provide advantages for stealth, quantum decoherence is a phenomenon that can disrupt superposition states and cause quantum systems to collapse into classical states.
Quantum Heat Engines Quantum heat engines are designed to utilize thermal energy from a heat source and convert thermal fluctuations into useful work extraction gained by quantum effects including superposition and entanglement. Key characteristics and functions include:
Heat input The heat engines receive heat from a high-temperature reservoir.
Work output The engine converts some of the input heat into mechanical work.
Heat rejection The engine releases the remaining heat into a lower-temperature reservoir, completing the thermodynamic cycle.
Quantum Heat Engine Operation Here is a simplified explanation of the operation of a quantum heat engine:
Initialization The quantum heat engine starts with a quantum system in a specific initial state.
Energy input (Heat absorption) The quantum system interacts with a hot reservoir, absorbing energy as heat. The quantum system undergoes a unitary evolution that involves quantum superposition and entanglement. A unitary evolution is how the state of a quantum system evolves over time.
Processing The quantum system is manipulated through a series of quantum operations. These operations may include applying quantum gates, changing the system's Hamiltonian, or exploiting coherence to drive the system to a desired state.
Energy output (Heat dissipation) After work extraction, the quantum system releases excess energy into a cold reservoir. This step also involves dissipating heat to the environment. This energy can be integrated into systems to leverage the principles of quantum mechanics to perform computations and simulations. Quantum annealing: Quantum annealing is a quantum computing technique that explores energy transfer pathways to improve efficiency. One of the primary objectives of quantum annealing is to improve ductility. Ductility is a property of materials that describes the extent to which a material can deform without breaking under tensile stress before fracturing. Materials that are highly ductile can undergo significant deformation before failure.
Quantum Entanglement and Non-linear Transformations: Entanglement can lead to non-linear transformations between the states of entangled particles or quanta. The correlations between entangled particles can exhibit non-local and non-linear behavior that cannot be explained by classical physics. Phase Transitions: Non-linear transformations can also arise in the context of quantum phase transitions, where the behavior of a quantum system undergoes a sudden change due to changes in parameters such as temperature or magnetic field.
Communication Channels
Quantum communication channels refer to the physical or virtual pathways through which quantum information is transmitted between different parties in a quantum communication system. Here are some key aspects of quantum communication channels:
Quantum Entanglement: Quantum entanglement is a fundamental property of quantum mechanics where two or more quantum particles, or quanta, become correlated in such a way that the state of one is dependent on the state of another. Quantum Entanglement can be used to establish quantum communication channels.
Quantum Teleportation: Quantum teleportation allows the transfer of quantum information from one quantum system to another. By utilizing entanglement and classical communication, quantum teleportation enables the transmission of quantum states between distant locations. Routing and Switching: Quantum communication networks require specialized routing and switching mechanisms to efficiently route quantum information between nodes. Quantum routers and switches are designed to handle quantum states and ensure the secure and reliable transmission of quantum information within the network.
Quantum Error Correction: Quantum communication channels are susceptible to noise that can degrade the "fidelity" of transmitted quantum information. Error correction is used to protect quantum information against errors that occur during transmission over quantum channels.
Conclusion
Botnets are versatile tools for cybercriminals, enabling a wide range of malicious activities that can disrupt services, compromise data security, defraud individuals and businesses, and generate illicit profits.
Efforts to combat botnets involve disrupting their infrastructure, removing malware from infected devices, and holding the individuals responsible for operating botnets accountable for their actions. Mitigating the impact of botnets requires a comprehensive approach involving cybersecurity measures, awareness campaigns, and legal actions against cybercriminals.
Defending against botnets requires a proactive and multi-layered approach that includes network monitoring, malware detection, incident response planning, victim education, cornering cybersecurity professionals, and working with law enforcement agencies.
A justice department in a country plays a crucial role in protecting the rights and freedoms of individuals. It is designed to help safeguard the rights of all citizens and ensure public safety by addressing harmful and criminal activities, deterring unlawful behavior, and ensuring that justice is served in a fair and impartial manner. This contributes to creating a safe and secure environment for citizens to live and work in.
0 notes
Text

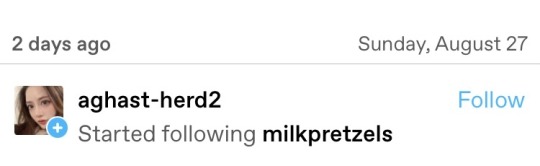
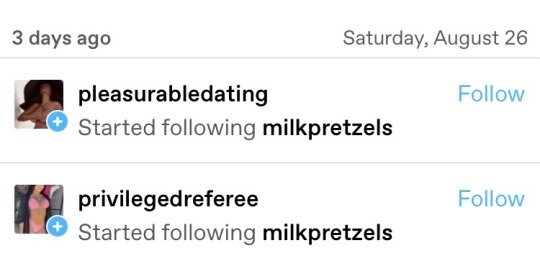

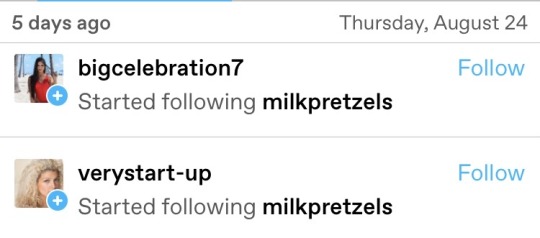
is the botmaster behind these a former homestuck? these all read like chumHandles. some of them i’m so jealous of and mad that i didn’t come up with myself. some are hilarious. 2 are lowkey very sexy… like if lee pace offered to match rhythms… phew! talk about pleasurableDating! and verystart-up has its finger on the pulse. it is the zeitgeist of being a working person in 2023. here i am stuck with milkpretzels and i’m fighting for my life against privelegedReferee. goddamn.
1 note
·
View note
Text
Mengoptimalkan Target Audience: Keunggulan Fitur Filter Nomor di Botmaster Sender
Mengoptimalkan Target Audience: Keunggulan Fitur Filter Nomor di Botmaster Sender
Dalam era pemasaran digital yang semakin berkembang, strategi yang tepat untuk mencapai audiens yang relevan sangatlah krusial. Botmaster Sender, sebuah solusi terdepan dalam WhatsApp marketing, membawa inovasi dengan fitur filter nomor yang cerdas, membantu bisnis dan individu untuk mengoptimalkan kampanye pemasaran dengan presisi yang tinggi.
Mengapa Filter Nomor Penting?
Filter nomor adalah alat penting yang memungkinkan pengguna Botmaster Sender untuk menyaring daftar kontak mereka. Fitur ini memungkinkan identifikasi nomor-nomor yang masih aktif di WhatsApp, memastikan pengiriman pesan hanya kepada audiens yang memiliki potensi untuk berinteraksi dan merespons.
Keunggulan Fitur Filter Nomor di Botmaster Sender:
1. Efisiensi Maksimal dengan filter nomor:
Dengan memisahkan nomor-nomor yang aktif dari yang tidak aktif, Botmaster Sender membantu menghindari pengiriman pesan yang sia-sia. Ini berarti usaha dan sumber daya Anda hanya diarahkan kepada mereka yang benar-benar memiliki kemungkinan untuk berpartisipasi.
2. Kualitas Interaksi:
Dengan mengirim pesan hanya kepada nomor-nomor yang aktif di WhatsApp, Anda meningkatkan peluang pesan Anda dibaca dan direspons. Hal ini menghasilkan interaksi yang lebih bermakna dan berdampak.
3. Peningkatan Konversi:
Filter nomor membantu dalam merancang kampanye yang lebih terfokus. Dengan mengirimkan pesan hanya kepada audiens yang relevan, Anda meningkatkan potensi konversi, mengoptimalkan hasil investasi pemasaran Anda.
4. Menghindari Spam:
Mengirim pesan kepada nomor yang tidak aktif dapat dianggap sebagai spam, yang dapat merugikan reputasi bisnis Anda. Filter nomor membantu menjaga integritas komunikasi Anda.
5. Analitik yang Lebih Akurat:
Dengan hanya berinteraksi dengan nomor-nomor aktif, analitik kinerja kampanye Anda menjadi lebih akurat dan bermakna, membantu Anda dalam evaluasi dan perbaikan strategi pemasaran.
Dalam dunia pemasaran yang kompetitif, filter nomor di bukanlah sekadar fitur tambahan, melainkan adalah kunci untuk sukses. Ini membantu Anda menyajikan pesan Anda hanya kepada mereka yang benar-benar ingin mendengar, mengoptimalkan keterlibatan, dan meraih hasil yang lebih baik. Dengan fitur filter nomor yang luar biasa, Anda membuka pintu menuju pemasaran yang lebih efisien, efektif, dan terarah.
0 notes
Text
Mengoptimalkan Pemasaran WhatsApp dengan Filter Nomor Botmaster: Tips Terbaik
Mengoptimalkan Target Audience: Keunggulan Fitur Filter Nomor di Botmaster Sender
Dalam era pemasaran digital yang semakin berkembang, strategi yang tepat untuk mencapai audiens yang relevan sangatlah krusial. Botmaster Sender, sebuah solusi terdepan dalam WhatsApp marketing, membawa inovasi dengan fitur filter nomor yang cerdas, membantu bisnis dan individu untuk mengoptimalkan kampanye pemasaran dengan presisi yang tinggi.
Mengapa Filter Nomor Penting?
Filter nomor adalah alat penting yang memungkinkan pengguna Botmaster Sender untuk menyaring daftar kontak mereka. Fitur ini memungkinkan identifikasi nomor-nomor yang masih aktif di WhatsApp, memastikan pengiriman pesan hanya kepada audiens yang memiliki potensi untuk berinteraksi dan merespons.
Keunggulan Fitur Filter Nomor di Botmaster Sender:
1. Efisiensi Maksimal dengan filter nomor:
Dengan memisahkan nomor-nomor yang aktif dari yang tidak aktif, Botmaster Sender membantu menghindari pengiriman pesan yang sia-sia. Ini berarti usaha dan sumber daya Anda hanya diarahkan kepada mereka yang benar-benar memiliki kemungkinan untuk berpartisipasi.
2. Kualitas Interaksi:
Dengan mengirim pesan hanya kepada nomor-nomor yang aktif di WhatsApp, Anda meningkatkan peluang pesan Anda dibaca dan direspons. Hal ini menghasilkan interaksi yang lebih bermakna dan berdampak.
3. Peningkatan Konversi:
Filter nomor membantu dalam merancang kampanye yang lebih terfokus. Dengan mengirimkan pesan hanya kepada audiens yang relevan, Anda meningkatkan potensi konversi, mengoptimalkan hasil investasi pemasaran Anda.
4. Menghindari Spam:
Mengirim pesan kepada nomor yang tidak aktif dapat dianggap sebagai spam, yang dapat merugikan reputasi bisnis Anda. Filter nomor membantu menjaga integritas komunikasi Anda.
5. Analitik yang Lebih Akurat:
Dengan hanya berinteraksi dengan nomor-nomor aktif, analitik kinerja kampanye Anda menjadi lebih akurat dan bermakna, membantu Anda dalam evaluasi dan perbaikan strategi pemasaran.
Dalam dunia pemasaran yang kompetitif, filter nomor di bukanlah sekadar fitur tambahan, melainkan adalah kunci untuk sukses. Ini membantu Anda menyajikan pesan Anda hanya kepada mereka yang benar-benar ingin mendengar, mengoptimalkan keterlibatan, dan meraih hasil yang lebih baik. Dengan fitur filter nomor yang luar biasa, Anda membuka pintu menuju pemasaran yang lebih efisien, efektif, dan terarah.
0 notes
Text
I light-heartedly gave a list of names which, for all I knew, I might hear: Hugh Murray Constantin Petrie Peter SmallSignor Beniamino BariThe Honourable Alex O'Brannigan, Bart. Kurt FreundMr John P. de Salis, M.A.Dr Solway GarrBonaparte GosworthLegs O'Hagan
The story of how Dylan Fazel drifted into academic-publishing scams and from there into conference fraud would make for a fascinating interview, if any journalist or documentary film-maker in Minnesota is at a loose end. It is unclear whether the emphasis on biomedical fields in his operation is motivated by a thwarted childhood medic-manqué ambition, or simply that that's where the money is...
I am sorry. I seem to have committed the classic dramaturgical blunder of starting the story at the beginning, rather than in media res as tradition demands. Let me start again.
It only takes a few minutes with the Goofle Sir Chengine to paper the screen with tweets from people wondering how to get off the A. Siozos (M.D.) mailing list, or wondering whether invitations to his prestigious congresses are legit. **** SPOILER ALERT **** no they're not.
So you should look at this discussion of parasitical publishers and mockademic scamferences, in which the participants share their experiences with the unrelenting blizzard of spam from Dr Siozos (putative editor of the Archives of Applied Medicine), pimping his "Annual Conference on Genetics 2019" scamference in Vienna and his "2019 Global Conf. on Neuroscience and Neurology"…
NO WAIT, you can't, because ResearchGate zorched 200 contributions after receiving a legal-thuggery nastygram, and saw no benefit to themselves in replying to the bumptious censorious asshat with a richly-deserved invitation to "sniff my taint"[Popehat].
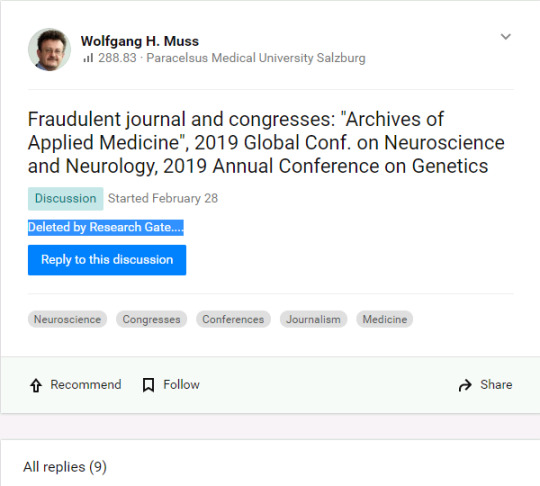
Bruno Chrcanovic reply
RG claimed that "[they] received a Notice of Claimed Defamation from Archives of Applied Medicine, asserting that they have a good faith belief that certain portions of the content constitute defamation to them." This serves as a reminder that academic social-networking sites like ResearchGate and Academia.com do not exist for your benefit, and any services they provide will evaporate faster than a Trump promise in the event of anything interfering with their monetising of your work.
As of now a replacement discussion thread exists, not yet cancelled by complaints from the botmaster behind the fake 'Siozos' identity that his commercial freedom to defraud people is constrained by attempts to warn them. Not to forget the equally fake identities "P. Jimenez, Ph.D." and "L. Smith M.D.", for the grifter has creativity to burn in the naming of spambots. In that thread we learn (inter alia) that the keynote speakers listed in the brochure had no intention of attending the Annual Genetics Conference and had no idea of the honour bestowed upon them… which is to say, the entire Prospectus was an unabashed fraud.

Two other aspects of that brochure are of interest (for sufficiently broad values of 'interest'). First, the promise of a special issue of AoAM containing the Conference Proceedings.

In fact the AoAM archives are a ghost-town where nothing but tumbleweed has moved since June 2019 and the only sounds are crickets and the mournful howls of far-off coyotes; the journal is moribund, as the aggressiveness of its spamming is not matched in the actual management of a criminal enterprise.
The second aspect was the name 'KEI' as part of the machinery of shearing:

Here 'KEI' is 'Knowledge Enterprises Incorporated': parasitical publisher of 'Medical Research Archives' and 'Internal Medicine Review' and a few others that are frozen in stasis. So it is not entirely by coincidence that KEI and AoAM use the same office forwarding mailbox to drape themselves in the respectability-mantle of a physical address, 340 S Lemon Ave #7750; Walnut CA 91789.

Physical cheques and letters to IMR are for historical reasons (TRADITION) funneled through a different mail-drop at 712 H St NE Washington DC 20002, with a cheque-cashing service conveniently located upstairs.

Despite these cut-outs, KEI is a departure from the norm in parasitical publishing, being an entirely US operation with no Hyderabad involvement. In fact the man behind KEI's campaign of global spam harassment documented himself thoroughly in his company ownership, and in Wikipedia revision logs, and in a blog dating back to the founding of Medical Research Archives where he claimed the title of "Interim Editor-in-Chief"; and in the registration of domains; and even by signing spam and correspondence with clients (before discovering the pleasures of spurious personae), as Dylan Fazel of Anoka, Minnesota.

Now pressure-to-publish-exploiting spam has evolved towards ever more aggravating persistence, stalking potential victims and boiling their bunnies, and it is only a matter of time before your mailbox deafens you with Feckle-Freezer-related screaming.

Dylan was a pioneer in this evolution, bombarding his targets with follow-ups and reminders… often skipping the original invitation and moving straight on to the reminders, in the hope of instilling the recipients with a sense of guilt and indebtedness. His special innovation, though, was an "ingratiating back-story" literary genre, in which the pressure to provide him with manuscripts and moneys is buttressed by cc:ing a correspondence among multiple non-existent identities, giving the reader an insider glimpse of an entire slice-of-life virtual world. Examples abound at "Flaky Journals", and at "Flaky Journals" again, and at ScholarlyOA, and even here at Riddled.
For a while these spurious personae used the names of actual Ukrainian translators, Venezuelan anaesthesiologists and Bulgarian casino-management freelancers, who were at least sometimes aware that their names were being made synonymous with 'con-job co-conspirator'. The shift to entirely fabricated identities like 'A Siozos' is new.

Dylan's gateway into the exciting world of virtual publishing (which is hard for one to leave, just as the elephant-poop-sweeper in the joke is loath to quit show-biz) was the Astronomical Review - an academic Salon des Refusés, providing autodidact would-be cosmologists with a convenient outlet for their original and challenging theories about the origin of the universe, without the hassle of cyclostyling those theories onto densely-written A4 pages and sellotaping them to the walls of bus-shelters.
Dylan recruited an Editorial Board of world-renowned luminaries from theoretical and experimental physics for this journal, including Roger Penrose and Jean-Pierre Luminet and Francis Everitt and NASA's Planetary Defense Officer, all content to follow his guidance as E.-in-C… or so he claimed, though one must bear in mind his fabulatory tendencies. This is all moot because in 2014 he sold the journal to Taylor & Francis, leaving him with time to found KEI and program his spam-bots. So now you know the back-story. The moral is that pimping out one's journals with wholly fictitious claims can be profitable.

T&F hiked the Article Publishing Fee from $25/page to a flat charge of $750 / £469 / €625 and imposed some standards on what they would accept. Bereft of submissions from Intergalactic Cracked Pots (and of the prestigious Editorial Board), Astronomical Reviewclosed its doors in 2018 after a less-than-glorious history. Someone with Whackyweedia privileges might want to reverse Dylan's self-promotional vandalism of the Wiki entries for Richard Penrose and Jean-Pierre Luminet, from October 12, 2012.
Anyway, I will give Dylan credit for opportunism timeliness. In light of current events, the latest Siozos spam -- urging me to travel to his next scamference in Athens -- has been updated, and now it highlights the potential to present about the effects of travel in spreading COVID-19.
0 notes
Text
Anti Banned!, 0857-4921-3214 Jual botmaster wa blast Mojokerto

Anti Banned!, 0857-4921-3214 Jual botmaster wa blast Mojokerto
Botmaster, solusi kirim pesan massal, auto reply, katalog, filter nomor, ambil nomor grup, dan fitur button. Tingkatkan penjualan Anda sekarang!
Botmaster adalah solusi terbaik untuk meningkatkan efisiensi dan efektivitas dalam mengelola pesan WhatsApp Anda. Dengan fitur kirim pesan massal, auto reply, katalog, filter nomor aktif dan nonaktif, serta kemampuan untuk mengambil nomor dari group WhatsApp, Botmaster memungkinkan Anda untuk mengelola komunikasi dengan pelanggan Anda dengan lebih mudah dan efisien.
Dengan Botmaster, Anda dapat dengan mudah mengirim pesan massal ke ratusan atau bahkan ribuan kontak sekaligus, tanpa perlu repot mengirim satu per satu. Fitur auto reply akan membantu Anda merespon pesan pelanggan secara otomatis, sehingga tidak akan ada pesan yang terlewat. Fitur katalog memungkinkan Anda untuk menampilkan produk atau layanan yang Anda tawarkan secara langsung melalui WhatsApp, sehingga pelanggan dapat melihat dan memilih produk dengan lebih mudah.
Selain itu, fitur filter nomor aktif dan nonaktif akan membantu Anda mengelola database pelanggan dengan lebih baik, sehingga Anda dapat fokus pada pelanggan potensial yang benar-benar tertarik dengan produk atau layanan Anda. Anda juga dapat dengan mudah mengambil nomor dari group WhatsApp untuk menambahkan kontak baru ke dalam database Anda.
Dengan fitur button, Anda dapat membuat pesan interaktif yang memudahkan pelanggan untuk melakukan tindakan tertentu, seperti memesan produk atau menghubungi customer service. Hal ini akan meningkatkan keterlibatan pelanggan dan membuat proses transaksi menjadi lebih lancar.
Manfaat menggunakan Botmaster sangatlah banyak, antara lain memudahkan Anda untuk kirim pesan massal, meningkatkan penjualan, menjaga keamanan database pelanggan, dan memudahkan promosi produk atau layanan Anda. Botmaster berkomitmen untuk memberikan layanan terbaik kepada pelanggan di Madiun dan sekitarnya, sehingga Anda dapat dengan percaya diri mengandalkan Botmaster untuk meningkatkan bisnis Anda.
Jadi, tunggu apalagi? Segera gunakan Botmaster sekarang juga dan rasakan manfaatnya untuk bisnis Anda!
Jual botmaster wa blast Mojokerto
#JualbotmasterwablastMojokerto
0 notes
Video
youtube
CHATBOT SISTEMA DE ATENDIMENTO COM BOTÕES
CHATBOT WHATSAPP - Melhor solução de envios em massa para Whatsapp da Internet. O BotMaster é um avançado programa que permite o usuário enviar milhares de mensagens de forma automática.
Uma solução definitiva de mensagens do WhatsApp com suporte ao WhatsApp Beta e bot avançado para respostas automáticas e filtro rápido. BotMaster 100% seguro e confiável.
Comece hoje mesmo a divulgar e vender mais com a ferramenta que mais ajuda o comércio em geral a divulgar e vender, com ele você vai facilmente chegar de forma mais rápida e direta ao seu futuro cliente, tenha já o seu Bot Master.
INFORMAÇÕES PELO ZAP: (11)99866-8006 Página: https://bmsvendas.comunidades.net/whatsapp-bulk-sender Email: [email protected]
1 note
·
View note
Text
Nicknames: Foe, Cait, Botmaster, Oracle
Zodiac: Aquarius
Height: 5'7"
Hogwarts house: Ravenclaw
Last thing you googled: Person of Interest Root Shotgun
Favorite music: Celtic music, folk music, classic rock
Song stuck in your head: Escape the Mind, by The Warning
Following: 207
Followers: 2444
Do you get asks: Not particularly, very rarely, sometimes when I wave an ask game around
Amount of sleep: Sixish hours
What you're wearing: Sweatpants and long sleeve top
Dream job: Writer
Languages: English, remnants of three years of Spanish.
Random fact: The stuntman who stood in for Brandon Lee after his untimely death during The Crow, so they could finish the movie, would go on to direct the John Wick movies.
Aesthetic: Fire, and birds.
Thank you for tagging me, @s-nebul0sa!
Nicknames: Ingy/Ivy (I don’t have many friends so Ivy is one that I picked because I don’t like my name so I ask to be called Ivy instead or maybe another nickname if the person prefers that)
Zodiac: Pretty sure it’s Scorpio
Height: 152.5 cm (some trashcans in my city are taller than me…)
Hogwarts house: Hufflepuff
Last thing you googled: Stardew Valley Mods
Favorite music: Mostly Pop music
Song stuck in your head: Who We Are by Hozier
Following: 263
Followers: 312
Do you get asks: Maybe once a year, it’s really rare
Amount of sleep: 3/4 hours when I’m lucky, 6 hours sometimes when my body is truly exhausted and I pass out at 3 am and sleep throughout the morning
What you're wearing: Pajamas (it’s hot AF and this is the lightest option of clothes I have)
Dream job: Movie/TV show director but I don’t know if I’m actually capable of doing that
Languages: My birth language is Portuguese (Brazil) but I’m also fluent in English and Spanish (I'm better at English than any other tho, including Portuguese)
Random fact: A chicken’s heart rate is about 4 times higher than humans, for example, a healthy adult resting heart rate ranges from 60 to 100 bpm while a normal chicken has a resting heart rate of 200 – 300 bpm
Aesthetic: I’m honestly not sure how to properly describe it, it’s a colorful mess basically
I'm tagging (no pressure) @laurensxdeath, @seriously-poppins, @kai999 and anyone else who wants to do it!
248 notes
·
View notes