#best cyber security services companies
Explore tagged Tumblr posts
Text

Cyber security is important to the digital infrastructure of any company. There have been a lot of cyber-attacks lately with many cases being made public. The good news is that many cyber security services can help protect you from these threats. The best Cyber Security Services Companies are those that understand the importance of protecting their customers and offer a variety of services to help them do so.
#aiops platforms#aiops consulting#Cyber Security and Compliance Services#Best Cyber Security Services Companies#Best AIOps Platforms Software#AIOps Digital Transformation Solutions
0 notes
Text
The Impact of 5G on Web Development: What to Expect
A web development firm is one of the numerous companies that stand to benefit greatly from the introduction of 5G technology. 5G, the fifth generation of wireless technology, promises far higher data rates, less latency, and more simultaneous device connections. These developments will significantly alter how websites are created, used, and maintained.
1. Faster Load Times and Improved User Experience
Instantaneous Load Times: Websites, even those with rich media content like movies, high-resolution photos, and intricate animations, will load nearly instantaneously thanks to 5G's data rates, which are up to 100 times faster than 4G.
Improved User Experience: Developers can now construct more dynamic and aesthetically attractive websites without worrying about the lag times that plagued websites during the 4G era. The quick load times will also result in lower bounce rates and higher user engagement.
2. Enhanced Mobile-First Development
5G will accelerate the trend toward mobile-first development as mobile devices take over as the major mode of internet access. Due to 5G networks' increasing speed and dependability, mobile consumers will anticipate the same caliber of performance as PC users. To ensure that websites are not just responsive but also properly optimized for mobile users, this would incentivize developers to give mobile optimization top priority in their designs. Mobile devices will be able to support features like virtual reality (VR) and augmented reality (AR), which demand a lot of data and processing power but provide a more immersive user experience.
3. The Rise of Real-Time Applications
Due to 5G's reduced latency—which is sometimes as low as 1 millisecond—real-time applications will be more feasible. This covers anything from IoT (Internet of Things) connections to real-time collaboration tools and games. This means that web developers will need to focus more on building apps that process data in real-time and provide consumers feedback right away. Additionally, this could facilitate the creation of more advanced web-based tools and apps that were previously constrained by 4G's latency and speed limitations.
4. Increased Use of Cloud-Based Solutions
The use of cloud-based solutions in web development will increase due to 5G's faster and more dependable speeds. More processing and storage responsibilities may be transferred to the cloud by developers, negating the need for robust client hardware. This will make it possible to create increasingly intricate and resource-demanding apps that function flawlessly on any device, regardless of its hardware specifications. Furthermore, cloud-based development platforms will proliferate as they enable real-time collaboration among developers from any place.
5. New Challenges and Opportunities in Security
Although 5G has many advantages, it also brings with it new difficulties, especially in the area of security. As the number of linked devices and data transferred rises, so does the potential attack surface for cyber-attacks. More than ever, web developers must put security first. To safeguard user data, they must utilize strong encryption, safe authentication procedures, and constant monitoring. 5G does, however, also provide prospects for improved security measures, such as AI and machine learning-powered real-time threat detection and response.
Conclusion:
The web development company, including ARP Tech, is expected to change significantly with the introduction of 5G. 5G will give developers new opportunities in a variety of areas, including quicker load times, improved mobile experiences, the emergence of real-time apps, and cloud-based solutions. It also presents new difficulties, mainly in the area of security, which need to be resolved. Web developers will have to adjust when 5G is implemented globally to provide websites and services that satisfy consumers' changing requirements and expectations in this new era of connection.
#website development company#web design services#web design company#Cybersecurity Consulting Services#DevOps Support Services#Best Data Analytics Company#cyber security consultant
0 notes
Text

Spictera, a premier cybersecurity company, delivers top-notch protection against cyber threats. Specializing in advanced threat detection and response, Spictera provides tailored solutions to safeguard your digital assets. Trust Spictera for comprehensive cybersecurity services that ensure the integrity and security of your business operations.
0 notes
Text
Why enterprises are going hybrid and returning to colo! - CyberTalk
New Post has been published on https://thedigitalinsider.com/why-enterprises-are-going-hybrid-and-returning-to-colo-cybertalk/
Why enterprises are going hybrid and returning to colo! - CyberTalk


By Ervin Suarez, Security Engineer for Cable and Colocation Accounts, Check Point Software Technologies.
I’ve been closely observing a fascinating shift in the IT landscape and wanted to share some insights with all of you, especially given how these changes could impact our industry.
Lately, there’s been a noticeable shift among enterprises back towards colocation (colo) services, while they’ve simultaneously embraced hybrid cloud models. This trend is intriguing and speaks volumes about the evolving needs and strategies of businesses when it comes to managing IT infrastructure.
Why the shift, you might ask?
Cost efficiency: The reality is, while cloud services offer unmatched scalability, they can also escalate costs for specific workloads or data-intensive operations. Colocation offers a more predictable expense model, which is especially appealing for operations with stable demand.
Enhanced control and security: With colocation, businesses gain direct control over their physical servers, a non-negotiable for industries under tight regulatory scrutiny. This control translates into superior compliance and security, aligned with stringent industry standards.
Optimized performance: By strategically choosing colo sites, enterprises can drastically reduce latency for critical applications, ensuring high-performance outputs that cloud environments can sometimes struggle to match.
Flexibility and scalability: The hybrid model shines by offering the best of both worlds – colo for critical, stable workloads and cloud services for scalable, flexible needs. This balance is crucial for businesses that aim to maintain agility without compromising on reliability.
Robust business continuity: Distributing resources between colo and cloud environments enhances disaster recovery strategies, leveraging colo’s inherent infrastructure resilience and reliability.
Compliance with data sovereignty: In an era where data privacy reigns supreme, colocation facilities offer a strategic advantage by allowing businesses to physically host data within required jurisdictions, meeting stringent regulatory demands head-on.
What does this mean for us?
The resurgence in colocation interest, alongside a robust adoption of hybrid cloud strategies, indicates a balanced, pragmatic approach to digital infrastructure management. Businesses are seeking to optimize costs without sacrificing control, performance, or compliance.
We’re also seeing increasing collaborations between cloud and colo providers, simplifying the transition to hybrid models for enterprises. This partnership ecosystem paves the way for innovative solutions, making hybrid strategies more accessible and effective.
Innovations in networking and connectivity continue to blur the lines between colo and cloud, enabling more seamless management of distributed IT resources.
As we navigate these changes, it’s clear that flexibility, strategic planning, and an eye for optimization are key to leveraging the best of both colo and cloud worlds. The move towards hybrid infrastructures isn’t just a trend; it’s a strategic realignment of IT resources to better meet the demands of modern business operations.
This shift is supported by several trends and developments in the industry:
1. Resurgence of colocation: Colocation is becoming crucial again as companies become increasingly dependent on robust IT infrastructure to manage the growing volume of data. Traditional colocation provides reliable and secure options for IT infrastructure, which is critical given the rising importance of data privacy and security. Colocation solutions offer businesses a way to protect their data, ensure high availability, and achieve resilience while saving on capital expenditure and operational costs. This is because colocation allows businesses to leverage existing, well-maintained infrastructures which would otherwise require significant upfront investment (Datacenters).
2. Hybrid cloud flexibility: Hybrid cloud models are being recognized for their ability to provide agility and flexibility in the technology stack. This model allows enterprises to not only meet their current technological needs but also prepare for future demands. The hybrid cloud’s capacity to integrate edge computing with cloud architectures enables more businesses to adopt this technology. It effectively lowers latency, reduces bandwidth requirements, and enhances resiliency against network outages. This adoption is visible across various sectors, including telecommunications, retail, manufacturing, and energy, indicating a broad-based validation of the hybrid cloud’s value (The Enterprisers Project).
3. Multi-cloud and vendor-neutral environments: Enterprises are also moving towards a more vendor-neutral approach in their cloud and colocation strategies. This shift is partly due to the need to avoid vendor lock-in, which can limit flexibility and control. The hybrid and multi-cloud architectures, comprised of combinations of public clouds, private clouds, and colocation data centers, allow enterprises to tailor their IT infrastructure to meet specific needs while ensuring that they can manage and integrate various cloud services effectively (PacketFabric).
In summary, the trends towards colocation and hybrid cloud are driven by a need for cost efficiency, control, security, flexibility, and strategic deployment of IT resources. These models not only help with optimizing current operations, but also assist with scaling future technologies and infrastructure needs. Enterprises are increasingly aware of these benefits and are adjusting their IT strategies to leverage colocation and hybrid cloud solutions as part of their broader digital transformation initiatives.
I’m keen to hear your thoughts and experiences on this shift. How do you see the hybrid model shaping the future of IT infrastructure in your field?
Managed firewall as a service – How secure is your data center?
As we navigate through the evolving landscape of IT infrastructure, with a noticeable shift towards colocation services and hybrid cloud models, I’m thrilled to share a bit about how Check Point Software is leading the way in enhancing security within these environments.
We’ve recently launched an innovative offering, Firewall as a Service (FWaaS), specifically designed to bolster the security posture of businesses leveraging colocation facilities.
Why Check Point’s FWaaS?
In the world of colocation, where businesses seek the perfect balance between control, cost, and flexibility, Check Point’s Managed Firewall as a Service stands out as a beacon of security excellence.
We understand the complexities of managing IT infrastructure across colo and cloud environments. That’s why we’ve introduced a solution that simplifies data center workflow orchestration and scales security on-demand, akin to spinning up servers in the cloud.
Our Managed FWaaS is not just a product, but a comprehensive security ecosystem. It’s designed to integrate seamlessly with your existing security infrastructure, protecting both private and public network services from a plethora of threats that can undermine your business.
With a 98.8% catch rate, our service ensures unparalleled protection against cyber security threats, providing peace of mind in an era where security breaches are all too common.
What sets Check Point apart?
Ease of integration: Customers within a colocation facility can effortlessly connect to Check Point’s infrastructure, gaining access to a managed security cluster that’s fully maintained by our team of experts.
Comprehensive security: Our service covers all bases, from Firewall, VPN, IPS, application control, content awareness, URL filtering, anti-bot, anti-virus, anti-spam, threat emulation, to threat extraction. We manage and monitor everything, alerting you to high and critical events, ensuring your infrastructure remains secure against evolving threats.
Fully managed solution: Let our MSS experts take the wheel. We handle everything from initial setup, weekly operational changes, to yearly upgrades, allowing you to focus on core business functions without the hassle of managing security infrastructure.
Cyber insurance partnership: Recognizing the importance of comprehensive protection, we’ve partnered with Cysurance to offer cyber insurance, providing an extra layer of security and assurance for businesses in need.
Empower your security with Check Point’s FWaaS
Check Point’s Managed Firewall as a Service leverages our deep expertise to maintain your security assets, ensuring your business operates smoothly and securely, without the operational overhead. This allows organizations to scale up their security measures on-demand, mirroring the flexibility of public clouds but with the added benefit of Check Point’s industry-leading threat prevention and management.
In an era where businesses are increasingly leveraging colocation for its cost efficiency, flexibility, and enhanced control, Check Point provides a security solution that aligns perfectly with these needs. Our FWaaS offering ensures that businesses can enjoy the benefits of colocation and hybrid cloud models, with the confidence that their security is in the hands of the experts.
I’m excited about the possibilities this brings to our industry and am eager to discuss how we can support your business’s security needs in this changing landscape. Let’s embrace this shift together, with Check Point ensuring that our journey is secure.
#Accounts#applications#approach#as a service#assets#awareness#bases#Best Of#blur#bot#Business#business continuity#Check Point#Check Point Software#Cloud#cloud services#cloud solutions#clouds#cluster#Colocation#Companies#compliance#comprehensive#computing#connectivity#content#cyber#cyber insurance#cyber security#cybersecurity
0 notes
Text
#mobile app development company#mobile app security best practices#cyber threats#emerging mobile app security risks#cross-platform app development#mobile app development services
0 notes
Text
Website Security: Best Practices For Protecting Your Site From Cyber Threats

Welcome to the digital age, where websites have become the virtual front doors of businesses around the world. However, with this unparalleled convenience comes a lurking danger – cyber threats. In today’s interconnected world, no website is safe from potential breaches and attacks which can wreak havoc on your online presence.
But fear not! In this blog post, we will unveil a treasure trove of best practices that you can implement to fortify your website’s defenses and safeguard it against any malevolent forces out there. So tighten your seatbelts and get ready to navigate through the maze of website security – because protecting your site has never been more crucial than now!
INTRODUCTION TO WEBSITE SECURITY AND CYBER THREATS
In today’s digital age, websites have become essential tools for businesses, organizations, and individuals to connect with their audiences. However, with the increased reliance on websites comes an increased risk of cyber threats. Cyber threats are malicious activities that can compromise the security of a website and its users’ sensitive information.
As technology advances, cybercriminals also evolve their tactics and techniques. It is no longer enough to rely on basic security measures; website owners must be proactive in safeguarding their sites against potential attacks. This section will provide an overview of website security and the various cyber threats that it faces so that you can better understand how to protect your site from these risks.
What is Website Security?
Website security refers to the protection of a website from cyber attacks or unauthorized access to its data or services. A secure website ensures that any information exchanged between the site and its users remains confidential, accurate, and available when needed.
The Importance of Website Security
According to a report by Verizon, 43% of cyber-attacks target small businesses. Many assume that only large companies are at risk; however, this is far from the truth. Hackers often target smaller websites as they have fewer resources dedicated to cybersecurity compared to larger organizations. The consequences of a cyber attack on a website can be severe. It can lead to financial loss, damage to the site’s reputation, and loss of customer trust. In some cases, a data breach can also result in legal action and fines.
Types of Cyber Threats
1. Malware: Short for “malicious software,” malware is any type of software designed to harm a computer system or steal sensitive information. It includes viruses, spyware, ransomware, and Trojan horses. Malware can infect a website through vulnerabilities in its code or by tricking users into downloading malicious files.
2. Phishing: Phishing is an attempt by cybercriminals to obtain sensitive information from users by posing as a legitimate source, such as a bank or reputable company. This usually involves sending fake emails or creating fake websites that look similar to the real ones.
3. DDoS Attacks: A Distributed Denial of Service (DDoS) attack floods a website with excessive traffic, overwhelming its servers and making it inaccessible to legitimate users.
UNDERSTANDING THE IMPORTANCE OF WEBSITE SECURITY
Understanding the importance of website security is crucial in today’s digital age, where cyber threats are becoming more sophisticated and prevalent. As a website owner, it is your responsibility to ensure that your site is properly protected from potential breaches or attacks.
Website security refers to the measures and protocols put in place to protect a website from malicious attacks, unauthorized access, and data theft. It encompasses all aspects of web development, including code integrity, server-side security, user authentication, and network security.
Here are some reasons why understanding the importance of website security is essential for any business or individual with an online presence:
1. Protects Sensitive Data: One of the primary reasons for implementing robust website security is to protect sensitive data such as personal information, financial details, and login credentials. Failure to secure this data can lead to identity theft, financial frauds or legal consequences.
2. Maintains User Trust: In today’s digital landscape where customers share personal information on websites regularly, having proper security measures in place can help build trust with your users. They will feel confident that their information is safe and will be more likely to continue using your services.
3. Prevents Malware Infections: Cybercriminals often use malware – malicious software designed to infect systems -to gain access to sensitive data or take control of a website. A well-secured website makes it difficult for hackers to inject malware into the system and prevents any potential damage.
TYPES OF CYBER THREATS: MALWARE, PHISHING, DDOS ATTACKS, ETC.
As technology continues to advance, so do the methods used by malicious actors to target websites. With cyber threats becoming increasingly sophisticated and prevalent, it is crucial for website owners to understand the different types of threats in order to effectively protect their sites. In this section, we will discuss some of the most common types of cyber threats – malware, phishing, and DDoS attacks.
1. Malware: Malware stands for malicious software and refers to any type of software that is designed with malicious intent. This can include viruses, worms, trojans, spyware, adware, and other harmful programs. Malware can be installed on a website through various means such as infected email attachments or compromised plugins/ themes. Once installed on a website, malware can steal sensitive information from users or even take over the site completely. Some examples of malware attacks include ransomware where hackers lock down a site until a ransom is paid and crypto-mining where they use a site’s resources to mine cryptocurrency.
2. Phishing: Phishing is a type of social engineering attack where cybercriminals trick individuals into sharing sensitive information such as login credentials or financial details through fake emails or websites that imitate legitimate ones. These emails or websites usually create a sense of urgency or fear in order to prompt users into taking immediate action without properly verifying the source or authenticity of the request. Phishing attacks are often used as an entry point for larger-scale attacks like data breaches.
3. DDoS Attacks: DD oS stands for Distributed Denial of Service and is a type of cyber attack where multiple compromised systems (often infected with malware) are used to flood a website with traffic, causing it to crash or become unavailable. These attacks aim to disrupt the normal functioning of a website and can result in significant financial losses for businesses. DDoS attacks are often carried out by hackers seeking ransom payments or by competitors trying to take down a rival’s website.
BEST PRACTICES FOR PROTECTING YOUR WEBSITE
In today’s digital age, website security is of utmost importance. With cyber attacks becoming more sophisticated and prevalent, it has become crucial for businesses to prioritize the protection of their website. A single breach can not only compromise sensitive data but also damage a company’s reputation and trust with its customers.
To ensure your website is secure from cyber threats, here are some best practices that you need to implement:
1. Keep Your Software Up-to-Date: One of the most basic yet effective practices for protecting your website is to regularly update all software used on your site, including content management systems (CMS), plugins, themes, and scripts. These updates often include security patches that address known vulnerabilities in the software.
2. Use Strong Passwords: Password protection is the first line of defense against hackers. Make sure to use strong passwords that include a combination of uppercase and lowercase letters, numbers, and special characters. It’s also important to change passwords at regular intervals and avoid using the same password for multiple accounts.
3. Implement HTTPS: HTTPS stands for Hypertext Transfer Protocol Secure, which encrypts communication between a user’s browser and your website server. This added layer of encryption makes it difficult for hackers to intercept sensitive information such as login credentials or financial details.
– REGULARLY UPDATE SOFTWARE AND PLUGINS
Keeping your website’s software and plugins up to date is crucial in protecting your site from cyber threats. Outdated software and plugins are often the prime targets for hackers, as they can exploit vulnerabilities to gain access to your website.
Therefore, it is essential to regularly update all software and plugins used on your website. This includes the content management system (CMS) you use, such as WordPress or Drupal, as well as any additional plugins or themes installed.
Here are some best practices for maintaining up-to-date software and plugins:
1. Stay Informed: Keep yourself informed about the latest updates and security patches released by the CMS providers and plugin developers. Sign up for their newsletters or follow them on social media to stay updated on any security issues that may arise.
2. Prioritize Updates: When a new update is released, make sure to prioritize updating critical components such as CMS core files and security-related plugins first before moving onto less important ones.
3. Set Up Automatic Updates: Many CMS platforms have an option to enable automatic updates for core files, themes, and plugins. This can be helpful when you do not have much time to manually go through each update.
4. Use Reliable Sources: Only download themes and plugins from reputable sources such as official marketplaces or developer websites. Avoid downloading free versions of premium themes or plugins from unknown sources, as these may contain malicious code that could compromise your site’s security.
– IMPLEMENT STRONG PASSWORDS AND USER AUTHENTICATION PROCESSES
One of the most effective ways to protect your website from cyber threats is to implement strong passwords and user authentication processes. Weak passwords are one of the easiest ways for hackers to gain access to your website, putting all of your sensitive information at risk. By ensuring that all users have a secure password and implementing two-factor authentication, you can greatly reduce the chances of a successful hacking attempt.
Here are some best practices for implementing strong passwords and user authentication processes:
1. Use Complex Passwords: A strong password should be complex, meaning it should include a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable information such as pet names or birthdates in your password.
2. Set Minimum Length Requirements: The longer the password, the stronger it is. Make sure to set minimum length requirements so that users cannot create short or weak passwords.
3. Enforce Regular Password Changes: It’s important to regularly change passwords to prevent them from becoming compromised over time. Consider setting a mandatory password change every 90 days for added security.
4. Implement Two-Factor Authentication: This additional layer of security requires users to enter a unique code sent to their mobile device in addition to their password when logging in. This ensures that even if someone has stolen their password, they won’t be able to gain access without physical possession of their phone.
– USE HTTPS ENCRYPTION
HTTPS (Hyper Text Transfer Protocol Secure) is an online communication protocol that ensures the secure transfer of data between a website and its users. It utilizes encryption to protect sensitive information, such as passwords, credit card details, and personal information, from being intercepted and accessed by unauthorized parties.
In recent years, HTTPS has become increasingly important for website security due to the rise in cyber threats and attacks. As a website owner, it is crucial to understand the importance of using HTTPS encryption and how it can help protect your site from these threats.
How Does HTTPS Encryption Work?
HTTPS works by encrypting data sent between a user’s browser and a website’s server. This is achieved through Transport Layer Security (TLS) or Secure Sockets Layer (SSL) protocols. These protocols use cryptographic keys to encrypt the data transferred back and forth, making it unreadable for anyone trying to intercept it.
When a user visits a website using HTTPS, their browser will initiate a handshake process with the site’s server. During this process, they exchange cryptographic keys to establish an encrypted connection. Once this connection is established, all data transmitted between the user and the server will be protected.
TOP TOOLS FOR WEBSITE SECURITY
Ensuring the security of your website is crucial in today’s digital landscape. With Cyber threats constantly evolving, it is important to stay ahead and protect your site from potential attacks. Fortunately, there are several tools available that can help enhance your website’s security and minimize the risk of cyber attacks.
1) SSL Certificates: Secure Sockets Layer (SSL) certificates are a must-have for any website. These certificates provide an encrypted connection between your server and the user’s browser, ensuring that sensitive information such as credit card details or login credentials cannot be intercepted by hackers.
2) Web Application Firewall (WAF): A WAF acts as a protective shield against malicious traffic by filtering out potentially harmful requests before they reach your web application. It monitors all incoming traffic and blocks suspicious activity, keeping your site safe from common vulnerabilities like SQL injections and cross-site scripting attacks.
3) Two-Factor Authentication (2FA): 2FA adds an extra layer of security to your website by requiring users to provide two forms of identification before accessing their account. This could include a password and a unique code sent to their phone or email. It reduces the risk of unauthorized access even if a hacker manages to obtain login credentials.
4) Anti-malware/ Antivirus Software: Keeping your server clean from malware is essential for maintaining website security. Investing in reliable anti-malware/ antivirus software will detect any malicious files on your server and remove them before they cause harm.
CONCLUSION
In today’s digital age, website security is more important than ever. With cyber threats constantly evolving, it is crucial for website owners to implement best practices in order to protect their site and its visitors from potential attacks.
In this blog article, we discussed the various ways in which you can strengthen your website security. By following these best practices, you can significantly reduce the risk of your site being compromised by cyber threats.
#Website Security: Best Practices For Protecting Your Site From Cyber Threats#webdesign#web development#digital marketing#multimedia / flash animation services#digital marketing agency canada#web devlopment#app development#web design agency in toronto canada#web design company in mississauga
0 notes
Text
Cybersecurity services | Cybersecurity Service provider company
In an increasingly digital world, cybersecurity has become a critical concern for individuals, organizations, and governments. Cybersecurity services refer to the practice of protecting computer systems, networks, and data from unauthorized access, theft, damage, or disruption. With cyber threats becoming more sophisticated, understanding the fundamentals of cybersecurity has never been more critical. This article aims to provide an overview of cybersecurity services providers, their key components, common threats, and best practices to ensure the security and integrity of digital systems.

Understanding Cybersecurity
Cybersecurity services company encompasses a range of practices and technologies designed to safeguard computer systems and networks from cyber threats. It involves the protection of electronic data, software, and hardware from unauthorized access, theft, or damage. The primary goal of cybersecurity is to prevent the compromise of sensitive information and maintain the confidentiality, integrity, and availability of digital assets.
Key Components of Cybersecurity
Effective cybersecurity involves multiple layers of defence, each serving a specific purpose. These components include:
Network security:
It focuses on securing computer networks and preventing unauthorized access by implementing firewalls, intrusion detection systems, and virtual private networks (VPNs).
Data security:
It involves protecting sensitive data through encryption, access controls, and regular cybersecurity service provider company backups, ensuring that information remains confidential and available only to authorized individuals.
Application security:
This component focuses on securing software and applications from vulnerabilities that cybercriminals can exploit. It includes secure coding practices, patch management, and regular software updates.
Common Cyber Threats
The digital landscape is teeming with various cyber threats, and staying informed about them is crucial. Here are some common threats:
Malware:
Malicious software such as viruses, worms, and ransomware that can infiltrate systems and cause damage or steal sensitive information.
Phishing:
The use of deceptive emails, messages, or websites to trick individuals into revealing sensitive information, such as passwords or credit card details.
Denial of Service (DoS) attacks:
Overwhelming a system or network with traffic to disrupt its normal functioning, rendering it inaccessible to legitimate users.
Social engineering:
Manipulating individuals into divulging confidential information through psychological manipulation or deception.
Best Practices for Cybersecurity
To enhance cybersecurity services company and protect against threats, adopting best practices is essential. These include:
Strong passwords:
Using unique, complex passwords and enabling two-factor authentication (2FA) for an extra layer of security.
Regular software updates:
Keeping all software and applications up to date to address security vulnerabilities and protect against exploits.
Employee education:
Conducting cybersecurity awareness training for individuals to recognize and mitigate common threats like phishing attacks.
Data backups:
Regularly backing up critical data to prevent loss in case of a cyber incident or system failure.
Conclusion
Cybersecurity services company is a crucial discipline in today's interconnected world. By understanding its key components, common threats, and best practices, individuals and organizations can better protect their digital systems and data, reducing the risk of cyberattacks and safeguarding their online presence. Stay vigilant and prioritize cybersecurity to stay one step ahead of cybercriminals.
#cyber security service#cyber security services#cyber security service provider company#best cyber security company
0 notes
Text
Leading Cyber Security Development Company | Webtrills
Secure your digital assets with the expertise of Webtrills, a trusted cyber security development company. They provide advanced solutions to protect your online presence from threats and vulnerabilities. With cutting-edge technologies and experienced professionals, comprehensive security measures are tailored to your needs. Protect your business and customer data today with Webtrills, your reliable partner in cyber security development.

0 notes
Text
#web design company#application development#web development services#website designing company#mobile game development#application development company#top app development companies#ios app development company#vapt companies#vapt testing companies#game development company#video game companies#mobile game companies#best game development companies#mobile game development company#top cybersecurity companies#cyber security company#best cyber security companies#cyber crime and cyber security company
0 notes
Text
Duck Comic Reading Club Week 7: Paperinik New Adventures: Earthquake

Ok, let's get to the point, this issue is the best one yet. An amazing story and a gorgeous art combined.
Oh God, the art. The Francesco Guerrini work here is astonishing. The use of the colors is masterful. Brilliant in every aspect.
This week story start with an earthquake on Duckburg. No major disaster occurred, except for good old uncle Scrooge.

Why do you insurance your oil rig with your own insurance company?
I mean, I got that he didn't have to pay himself the quota for the service, but now you have to pay for the damages. So, stop complaining you crazy old bird.

But One found out something fishy about the earthquakes, and is up to Donald to investigate this. Is so funny that Duckburg is Paperopoli in italian. Is better than Patolandia tho.
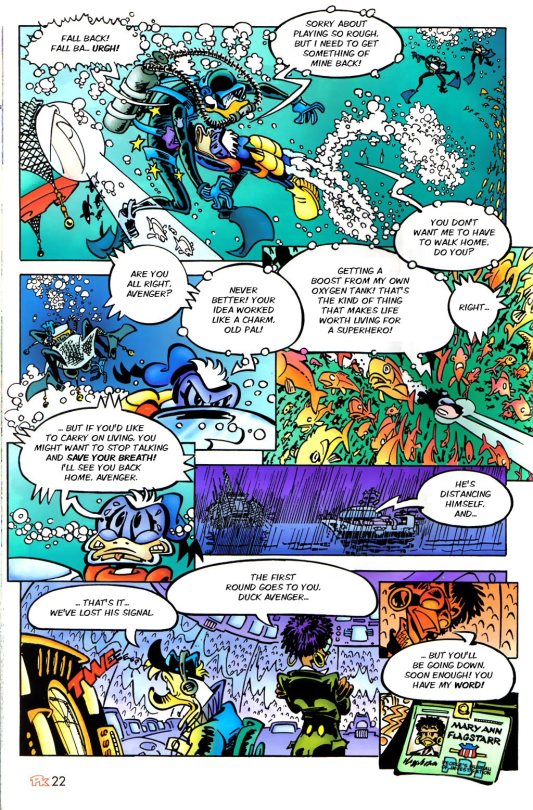
PK took one of the many vehicles at the Tower, and went for a ride, super hero style.
This page is a piece of beauty.

We got a new character, Mary Ann Flagstarr, a PBI agent. Tough lady.

PK had had encounters with the police, but now, he faced federal agents. My boy is not making any friends.
But, you know? A vigilante, a superhero, can't work with the authority. So, yeah, go get them PK.
Another new character, Professor Morgan Fairfax. What a nice fella, I'm sure he has never done anything wrong in his life.
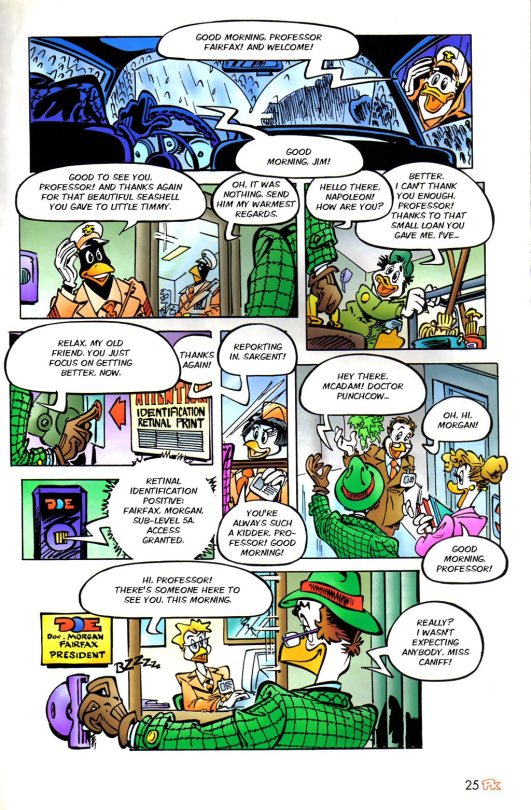
One knows something is not right, they need to keep investigating. But now, is time to go back to the world of cyber space.
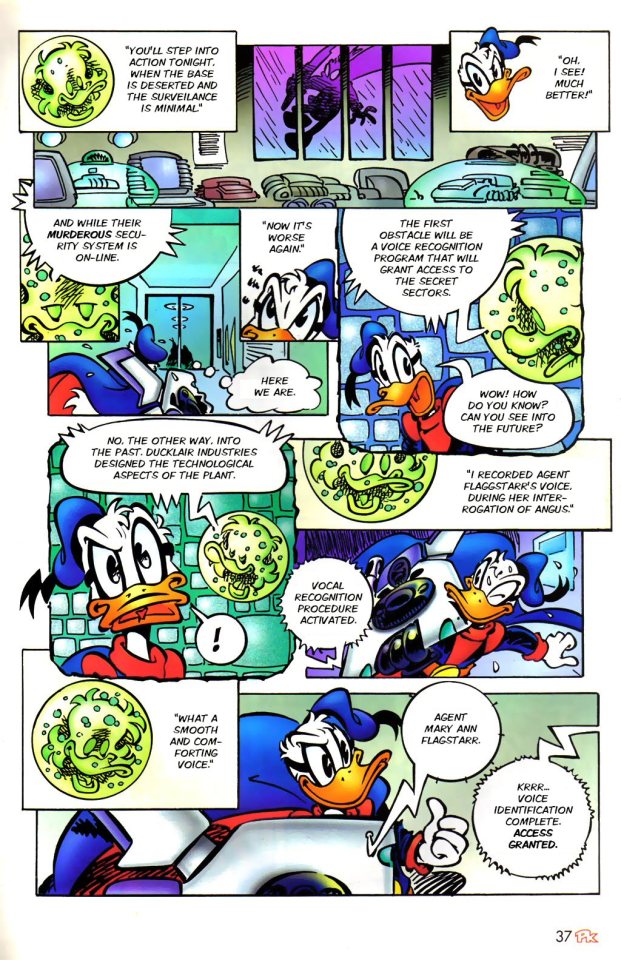
Another beautiful page, this issue can't miss.

But is hard to step into a federal database without anyone noticing, so they got caught. Thankfully, One was one step ahead and got himself a great scapegoat.

Oh, now you don't like spread misinformation, right jerk?
He didn't face any charge, and, to be fair, he was innocent. But, if being ugly was a crime, he would get the chair.
Back to the Professor, and he's making some really evil looking smirks. Could it be that he's not the nice guy that we though?
Also, another banger page.

PK infiltrates in the building, using some advance tech. One is a cheat code, and here's being used at his fullness.

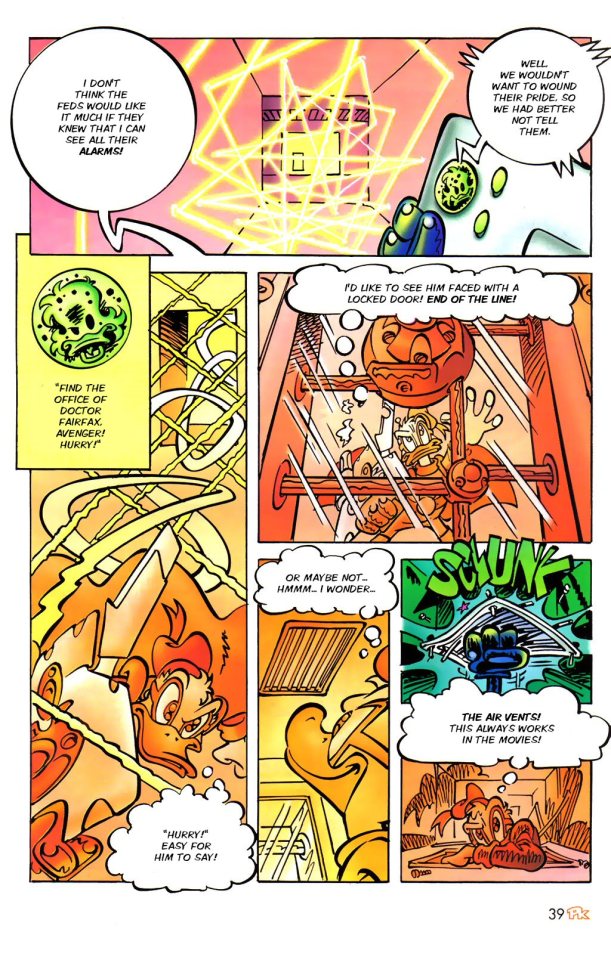
PK had a weird Donald moment, when he stuck in the vent, fall to the ground, and got face to face with the worst security guard ever.

Hey, masked vigilante sneaked in this government facility that I supposed to be looking after. I'm gonna make some lame jokes, and then I'm gonna miss the shots less than a meter away.
Don't come in the morning pal.
You know? I'm starting to think that this guy Fairfax is not that nice.

Yeah, yeah, he's the bad guy. Trying to burn PK alive is in my Being Bad Bingo.
And yet another absolutely gorgeous page. Is amazing.

Thankfully, One and his infinite tech come to the rescue. PK also save the guard, because he's a hero.

Now, this one part was kinda weird. Agent Flagstarr has been shown trough the issue as tough, focus agent, that wants to get the job done. But, a few words of Fairfax and a gift are enough to make her dismiss orders.
Also, that face… you can't trust someone with that face…

Now we found about Fairfax plan. He wants to create a earthquake strong enough that the whole planet would change, and new land would appear.
At the cost of the entire west coast being destroyed.

The worst part? One agrees with him. What the hell man? Not cool One, not cool.

PK got in the plane and try to stop Fairfax, but Flagstarr was in his way. The agent was conflicted on what to do. Madam, help the guy who doesn't want to destroy the whole west coast. Is not that hard.
Man, the art on this issue is out of control.

PK is so cool.

Finally, One got a change of heart, if you can said that, and helped PK to stop this madness. I knew One wasn't a psychopath.
But that last image of the device at the bottom of the sea is quite unsettling.
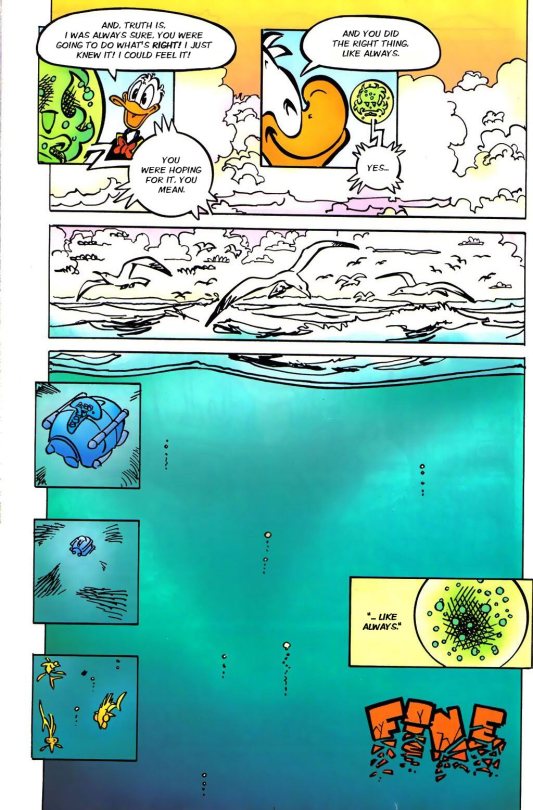
What can I said? This was awesome. I love all the detective PK stuff, the danger was palpable, One almost got Duckburg destroy. The art was magnificent, the colors were vibrant, it looked beautiful in general.
Hands down, the best one yet.
#dcrc paperinik#dcrc#donald duck#duckverse#pkna#dcrc week 7#paperinik#duck avenger#one#uno#mary ann flagstarr#professor morgan fairfax#comic review
43 notes
·
View notes
Text
AO3 is Down
As many of you probably noticed, AO3 has been down a majority of Monday and will likely be down today as well. They are currently suffering from what's called a DDoS attack and given my tech background, wanted to give some insight on that.
What is a DDoS attack?
A DDoS attack (or a distributed denial-of-service attack) is where a company and/or website is targeted and sent a massive load of access requests, overwhelming servers and basically bringing the site down. Typically no data is compromised during these attacks, their basic aim is to make it so that a site is not accessible.
Who's responsible for the attack?
A group called Anonymous Sudan is claiming responsibility for the attack, claiming religious and political reasons for doing so, however, the folks at AO3 have consulted cyber security experts on this and they have strong reasons to believe that these reasons are fabricated. More likely than not, and I've seen this in the past, is they're quite literally being trolls.
What can you do to help?
The best thing to do in this situation, as much as it sucks, is to not access the site right now until AO3's staff say it's ok to do so. The less access requests to the site and their servers, the better, that way their volunteer IT personnel can work on getting the site back up as quickly as possible. You can keep track of updates here.
With that said, a massive shoutout to the folks at AO3 for their clear communication and their dedication to getting their site back up. Please consider donating once they come back up because, as someone who works in the IT field, I know how stressful a situation like this is and appreciate everything they do to make it so that we have a place to post and read whatever we want without fear of our stuff taken down or of judgement.
102 notes
·
View notes
Text

Cybersecurity and compliance services along with endpoint device security are now becoming a specialized offering from companies. Read this blog to know more.
#cyber security#Best Cyber Security Services Companies#Cyber Security and Compliance Services#Cyber Security Mdr Services#aiops artificial intelligence for it operations#aiops digital transformation solutions#best aiops platforms software#ai devops automation service tools
0 notes
Text

Did you know that all companies behind the above mentioned services are part of the so-called Surveillance Capitalism? In a nutshell, this term describes an economic system centered around technology monopolies which harvest private user data to maximize profit.
Don't see any issues with that? Well, Surveillance Capitalism actually threatens the very core of our societies. It gives rise to mass surveillance, polarizes the political debate, interferes with electoral processes, drives uniformity of thought, facilitates censorship and promotes planned obsolescence. Tackling those issues requires comprehensive changes to our legal systems and social conventions.
70 notes
·
View notes
Text
Understanding Data Encryption and Classification for Effective Data Rights Management
Introduction:
Nowadays, data security has become a top priority. As the data is generated and shared more exponentially, the safeguarding of sensitive information has become more challenging while being crucial. Data encryption and classification are the two major aspects of data rights, and they play a leading part in protecting information from involuntary or Best geofence storage service and in compliance with privacy laws.

What is Data Encryption?
Data encryption is like putting your information in a safe, but it is a digital safe. This process entails encoding the plain text into an illegible text referred to as ciphertext with a specific algorithm and key. This procedure makes sure that even if somebody who's not authorized is granted access to the data, they will still not be able to decrypt it without the corresponding decryption key.
Imagine that you want to send a secret message to your friend. Instead of writing the message clearly, you mix it up using some secret code that only you and your friend know. Without the key, any interposition would only yield nonsensical letters.
What is Data Classification?
Data classification is grouping the data according to its level of sensitivity and significance. It also allows organizations to categorize their data holdings and decide which data needs to be protected at what level. Classification is usually done by tagging data with a label that identifies its security requirements or handling process.
Data classification is like putting your stuff into different boxes. All your important documents might go into a folder, another for pictures and one for miscellaneous notes. Every folder is labelled to indicate what paperwork is inside of it and how you should handle it.
Effective Data Rights Management
Encrypting and classifying data are crucial in the context of the formulation of advice on the management of data rights with the objective of attaining maximum data protection and regulatory compliance. Here's how they work together, Here's how they work together:
Data Identification:
This high classification facilitates to define the sensitive data that needs to be encrypted conveniently. By splitting the data into groups according to the application of encryption technologies, information systems can address the shortage of encryption means and distribute the resources in a reasonable way.
Access Control:
Encryption is a safeguard against unpermitted access, and people with classification rights choose who to give access to encoded information. The access controls can build on data classification labels so that only the laid-out clearance users, possessing the proper clearance can unscramble the cipher and access sensitive information.

Conclusion:
The use of data encryption and classification forms part of comprehensive data rights management plans. Encryption works to make Best Database Backup Services only accessible to authorized people. While at the same time, sensitivity labels can be used to classify easy-to-reach data from data that requires more protection. Organizations can provide an appropriate environment for data if they combine these approaches. They can take care of risks, protect confidential information, and be consistent with data privacy regulations.
#Best object storage software#Best Database backup Services#IT Security services#Cyber security company
0 notes
Note
Okay okay so here are questions for your bastard children au.
1. How does Ghost find out that Cam is a half brother? How did that conversation go? What did Cam react to realizing Simon Riley isn't dead and actually a scary mf in the 141? And how did Simon react to learning that his basterd father was more of a basterd than he thought?
2. Will the other siblings learn about Giles = Simon? Or is it a secret between Cam and Simon? I cant imagine it would be safe to tell all these people he barely knows. But also, they are family...
Probably more questions to come, but these are the main ones for now 💕💕
So there are several ways I'm playing with the reveal going! But basically it boils down to Cam is not ashamed of Simon, he is proudly open about who his older brother is and what he means to him. He doesn't go around announcing it, but when talking about why they wanted to join the military, he just very clearly goes "My older brother, Simon Riley, was in the service, and I want to be like him and make him proud of me. Yes, that Simon Riley, no, I don't think he's guilty. I never met him, but everyone said he was sweet, if grim, and he was very protective of his family, even and especially after he came back on leave. I don't believe he could've done it - killed the American? yes. killed his brother and mother and baby nephew? absolutely not."
Cam also talks to "Simon" out loud sometimes. Like a mission will go well, and he'll sigh and look up at the sky or into thin air and go "We did it, Simon. We made it through." (And Ghost will nearly break his own neck doing a double take if they were paired together for it.)
Cam is just glad Simon's alive and glad that he and all the other siblings were right and he was innocent. Though, he is a little sad he can't tell the others, especially Jambo. I forgot to say in the last ask, but Jambo is a computer nerd obsessed with proving Simon's innocence. He has maybe gotten in trouble for hacking government records (mostly because he's bad at it). Not even he thinks Simon's still alive, though.
Ghost is scared as fuck for Cam and the others. He's lost all his family before, he's almost certain it'll happen again. Cam gets in his face about it when the avoidance gets extreme though and is like "I chose this life, too. You only get to dictate the risks I take in my professional life, as my mentor and superior officer, not in my personal life as my brother. We are both adults." After that, things get smoother, and he agrees to be added to the groupchat with the best cyber security Laswell can set up on his end.
As far as learning about his half-siblings' existence... he's disappointed in his dad but not surprised. Or surprised that his dad is a disappointment. 🤷♀️
Keegan for sure finds out eventually, when the Ghosts and 141 finally team up. I think the others will start to suspect after a while, but they're not saying nothing. If Giles is Simon, they don't want to get him in trouble with the authorities, and if he's not, they don't want to upset him by treating him like someone he's not. So they all know but they're not talking and they don't Know. Not even Jambo. And this is 100% to keep them safe, Cam and Keegan and Simon all chose to enlist, the others did not. And Kitty is roughly the same age Joseph was when he died, which makes the feelings More Complicated for Simon. He got PTSD up the wazoo.
One thing that is related to it being family, though, is that Ghost's maternal grandmother - his Mamó Caoimhe (pronounced sort of like Mamaw Keeva), who he was super close to - is still alive. The Bastard Children in Manchester all take turns checking in on her and bringing her food and giving her company. They've never said they're her son-in-law's offspring, but she definitely suspects. But Ghost cut off all contact with her for the same safety reasons and supposed to be dead reasons after the massacre, and it gives him peace to know she has people looking after her. Specifically, being able to get regular updates on how she's doing without putting her in danger by showing up himself or straight up hiring a stalker - or begging Laswell - does his mental health a world of good.
I think that answered all your questions? 😅 Let me know if I missed any!
#/incoherent noises/#call of duty#call of duty modern warfare#simon ghost riley#simon riley#cod ghost#call of duty ghosts#keegan russ#the bastard children of bones riley#ocs#cod ocs#my ocs#asked and answered
4 notes
·
View notes
Text
How Is The Demand For Web Development In The Future?
In our fast-paced digital era, the demand for web development services is poised for substantial growth, driven by the continuous evolution of technology and the expanding influence of the internet across industries. As we look towards the future, several key factors contribute to the increasing demand for web development expertise.
1. Digital Transformation Across Industries:
Businesses, regardless of their size or sector, are undergoing digital transformation. This shift is not only a trend but a necessity to stay competitive in the modern marketplace. Web development plays a central role in enabling this transformation, as companies seek to establish and enhance their online presence.
2. E-Commerce Expansion:
The rise of e-commerce continues to be a major driver for web development demand. With more consumers preferring online shopping, businesses are investing in robust and user-friendly websites to facilitate seamless transactions. This trend is likely to persist, further fueling the need for skilled web developers.
3. Mobile-First Approach:
The increasing use of smartphones has led to a paradigm shift towards a mobile-first approach in web development. Responsive design and mobile optimization are becoming standard practices, ensuring websites deliver a consistent and engaging experience across various devices. Web developers proficient in mobile technologies will be in high demand.
4. Integration of AI and Machine Learning:
Artificial Intelligence (AI) and Machine Learning (ML) are becoming integral components of web development. From chatbots for customer support to personalized content recommendations, AI and ML enhance user experiences. As businesses strive for more intelligent and interactive websites, the demand for developers skilled in these technologies is set to rise.
5. Progressive Web Applications (PWAs):
Progressive Web Applications represent the future of web development by combining the best of web and mobile applications. PWAs offer faster loading times, offline capabilities, and an app-like experience on the web. The adoption of PWAs is expected to grow, necessitating web developers to adapt to this emerging paradigm.
6. Blockchain Integration:
Blockchain technology is not limited to cryptocurrencies; it's making inroads into web development. Decentralized applications (DApps) and smart contracts are examples of how blockchain can be incorporated. As businesses explore these innovative solutions, developers with blockchain expertise will be in demand.
7. Cybersecurity Concerns:
With the increasing frequency of cyber threats, cybersecurity is a top priority for businesses. Web developers will play a crucial role in implementing secure coding practices and ensuring websites are resilient to cyber-attacks. The demand for developers with a focus on cybersecurity will likely see a significant uptick.
8. Cross-Browser Compatibility:
As new web browsers emerge and existing ones update, ensuring cross-browser compatibility becomes imperative. Web developers need to create websites that function seamlessly across different browsers and platforms, ensuring a consistent experience for users. This attention to compatibility will be a continuous demand in the future.
9. Continued Growth of Content Management Systems (CMS):
The popularity of Content Management Systems, such as WordPress, Drupal, and Joomla, is expected to persist. These systems empower businesses to manage their web content effectively. Web developers specializing in CMS customization and optimization will remain in demand as companies seek tailored solutions.
In conclusion, the future of web development is promising, characterized by constant innovation and a growing reliance on digital solutions. Web development services in Faridabad play a vital role in meeting the evolving requirements of the digital landscape, ensuring businesses stay competitive and relevant.
2 notes
·
View notes