#and widely used official software
Explore tagged Tumblr posts
Text
Spain lied about not selling weapons to Israel.
Even after October 7th, Spain has sold more than 1 million € of weapons to Israel. Norway and Finland make it possible.
In January, Spain made headlines word-wide when the government's Minister of Exteriors, José Manuel Albares (PSOE), claimed in Congress and later again in a radio interview that Spain had stopped selling weapons to Israel ever since October 7th. Israel's intensification of violence in Gaza following October 7th meant that, on top of decades of apartheid and ethnic cleansing, between October 7th and January 23rd Israel had already killed 28,000 people and forced 2 million out of their home. In this context, many people were demanding their governments stop arming and funding the genocide of the Palestinian people, and here on Tumblr and other social media sites like Twitter I think we all saw the many posts praising the Spanish government for this.
Well, it turns out it was a lie.
According to Albares, "Since October 7th there are no more weapons exportations [from Spain] to Israel". But in November alone, Spain exported weapons to Israel for 987,000€, as was published on the Spanish Government's official website dedicated to exterior commerce (Comex). A researcher from Centre Delàs (an independent centre for peace studies) found it and published it, and it has also been verified by newspapers such as elDiario.es.
This 987,000€ worth of weapons in November was not the only ammunition that Spain has sent to Israel in 2023. In 2023, Spain exported a total of 1.48 million € in war material to Israel.
All of the weapons sent in November come from the factory of Nammo Palencia (Castilla y León), a corporation that is 50% property of the Government of Norway and 50% owned by a public Finnish business. However, even if the owners are foreigners, the ammunition was sent from Spain and thus it had to be authorized by the an organism of the Spanish Government named Junta Interministerial de Defensa y Doble Uso, whose deliberations on whether a weapons exportation is accepted or denied are kept secret. The only cases where they have denied exporting weapons to Israel have been when they thought that Israel would re-sell these weapons to the Philippines.
Spain has had a close relation with Israel for years. As published by the Spanish Government, Spain has sold 20 million € of weapons to Israel between 2012 and 2022. Spain also buys weapons and military software from Israel (for example, the Spanish Intelligence Service has been using the Israeli software Pegasus to illegally spy on Catalan activists, journalists, politicians and civil society members and their relatives to attack the Catalan independence movement), and Spain has continued buying from Israel and allocating defense contracts to Israel even after the October 7th attacks. It is very difficult to track the concessions of public contracts such as buying weapons, but some contracts have been known. For example, on November 24th 2023, Spain bought 287.5 million € of missiles from Israel. This is not unusual: between 2011 and 2021, it is publicly known that Spain bought war material from Israel for at least 268 million €, but experts say that the real number could be two or three times as much.
Spain has also continued allocating concessions to Israel. For example, on December 15th 2023 Spain allocated a contract worth over 576 million € to Israel for a rocket launcher programme. On November 22nd, Spain allocated another another Israeli company to provide missiles for 237 million € at the same time as the Spanish army bought Israeli inhibitors for 1.4 million €. The very next day, November 23rd, Spain signed another military allocation to Israel for 82,600€. The following week, Spain signed yet another allocation with a different Israeli military corporation for 3.7 million €.
Spain also allows Israeli weapon manufacturing companies to produce weapons through their branches located in Spain. This way, Israeli weapons make their way to markets with which Israel doesn't have diplomatic ties but Spain does, like Saudi Arabia. And since Spain is a member of NATO, Israeli weapons produced in Spain are approved according to NATO standards and access it easily. In the same way, these Israeli weapons manufacturers also access European Union defense funds through their branches in Spain. (source).
As I said, I saw a lot of positive posts around when Albares said Spain was going to embargo, but I haven't seen any post about how they didn't do it. I also (personally) haven't seen anything on international media, and barely anything on Spanish media, which is already busy with the PSOE covid material corruption scandal. So I share this in the hope of helping put pressure on Spain to cut all ties with Israel immediately.
SHAME ON EVERYONE WHO GIVES ISRAEL THE MATERIAL AND MONEY THAT WILL BE USED TO MASSACRE THE PALESTINIAN PEOPLE. SHAME ON SPAIN, NORWAY, AND FINLAND.
#i've been meaning to post this for a few days but never manmaged to finish writing since i don't have internet at work and i barely have#time to do anything else than sleep eat and prepare work stuff when i'm home#so I'm late but this is still relevant#palestine#gaza#israel#free palestine#spain#norway#finland#españa#end genocide#bds#boycott divest sanction#free gaza#peace#anti military#💬
3K notes
·
View notes
Text
How lock-in hurts design

Berliners: Otherland has added a second date (Jan 28) for my book-talk after the first one sold out - book now!

If you've ever read about design, you've probably encountered the idea of "paving the desire path." A "desire path" is an erosion path created by people departing from the official walkway and taking their own route. The story goes that smart campus planners don't fight the desire paths laid down by students; they pave them, formalizing the route that their constituents have voted for with their feet.
Desire paths aren't always great (Wikipedia notes that "desire paths sometimes cut through sensitive habitats and exclusion zones, threatening wildlife and park security"), but in the context of design, a desire path is a way that users communicate with designers, creating a feedback loop between those two groups. The designers make a product, the users use it in ways that surprise the designer, and the designer integrates all that into a new revision of the product.
This method is widely heralded as a means of "co-innovating" between users and companies. Designers who practice the method are lauded for their humility, their willingness to learn from their users. Tech history is strewn with examples of successful paved desire-paths.
Take John Deere. While today the company is notorious for its war on its customers (via its opposition to right to repair), Deere was once a leader in co-innovation, dispatching roving field engineers to visit farms and learn how farmers had modified their tractors. The best of these modifications would then be worked into the next round of tractor designs, in a virtuous cycle:
https://securityledger.com/2019/03/opinion-my-grandfathers-john-deere-would-support-our-right-to-repair/
But this pattern is even more pronounced in the digital world, because it's much easier to update a digital service than it is to update all the tractors in the field, especially if that service is cloud-based, meaning you can modify the back-end everyone is instantly updated. The most celebrated example of this co-creation is Twitter, whose users created a host of its core features.
Retweets, for example, were a user creation. Users who saw something they liked on the service would type "RT" and paste the text and the link into a new tweet composition window. Same for quote-tweets: users copied the URL for a tweet and pasted it in below their own commentary. Twitter designers observed this user innovation and formalized it, turning it into part of Twitter's core feature-set.
Companies are obsessed with discovering digital desire paths. They pay fortunes for analytics software to produce maps of how their users interact with their services, run focus groups, even embed sneaky screen-recording software into their web-pages:
https://www.wired.com/story/the-dark-side-of-replay-sessions-that-record-your-every-move-online/
This relentless surveillance of users is pursued in the name of making things better for them: let us spy on you and we'll figure out where your pain-points and friction are coming from, and remove those. We all win!
But this impulse is a world apart from the humility and respect implied by co-innovation. The constant, nonconsensual observation of users has more to do with controlling users than learning from them.
That is, after all, the ethos of modern technology: the more control a company can exert over its users ,the more value it can transfer from those users to its shareholders. That's the key to enshittification, the ubiquitous platform decay that has degraded virtually all the technology we use, making it worse every day:
https://pluralistic.net/2023/02/19/twiddler/
When you are seeking to control users, the desire paths they create are all too frequently a means to wrestling control back from you. Take advertising: every time a service makes its ads more obnoxious and invasive, it creates an incentive for its users to search for "how do I install an ad-blocker":
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
More than half of all web-users have installed ad-blockers. It's the largest consumer boycott in human history:
https://doc.searls.com/2023/11/11/how-is-the-worlds-biggest-boycott-doing/
But zero app users have installed ad-blockers, because reverse-engineering an app requires that you bypass its encryption, triggering liability under Section 1201 of the Digital Millennium Copyright Act. This law provides for a $500,000 fine and a 5-year prison sentence for "circumvention" of access controls:
https://pluralistic.net/2024/01/12/youre-holding-it-wrong/#if-dishwashers-were-iphones
Beyond that, modifying an app creates liability under copyright, trademark, patent, trade secrets, noncompete, nondisclosure and so on. It's what Jay Freeman calls "felony contempt of business model":
https://locusmag.com/2020/09/cory-doctorow-ip/
This is why services are so horny to drive you to install their app rather using their websites: they are trying to get you to do something that, given your druthers, you would prefer not to do. They want to force you to exit through the gift shop, you want to carve a desire path straight to the parking lot. Apps let them mobilize the law to literally criminalize those desire paths.
An app is just a web-page wrapped in enough IP to make it a felony to block ads in it (or do anything else that wrestles value back from a company). Apps are web-pages where everything not forbidden is mandatory.
Seen in this light, an app is a way to wage war on desire paths, to abandon the cooperative model for co-innovation in favor of the adversarial model of user control and extraction.
Corporate apologists like to claim that the proliferation of apps proves that users like them. Neoliberal economists love the idea that business as usual represents a "revealed preference." This is an intellectually unserious tautology: "you do this, so you must like it":
https://boingboing.net/2024/01/22/hp-ceo-says-customers-are-a-bad-investment-unless-they-can-be-made-to-buy-companys-drm-ink-cartridges.html
Calling an action where no alternatives are permissible a "preference" or a "choice" is a cheap trick – especially when considered against the "preferences" that reveal themselves when a real choice is possible. Take commercial surveillance: when Apple gave Ios users a choice about being spied on – a one-click opt of of app-based surveillance – 96% of users choice no spying:
https://arstechnica.com/gadgets/2021/05/96-of-us-users-opt-out-of-app-tracking-in-ios-14-5-analytics-find/
But then Apple started spying on those very same users that had opted out of spying by Facebook and other Apple competitors:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Neoclassical economists aren't just obsessed with revealed preferences – they also love to bandy about the idea of "moral hazard": economic arrangements that tempt people to be dishonest. This is typically applied to the public ("consumers" in the contemptuous parlance of econospeak). But apps are pure moral hazard – for corporations. The ability to prohibit desire paths – and literally imprison rivals who help your users thwart those prohibitions – is too tempting for companies to resist.
The fact that the majority of web users block ads reveals a strong preference for not being spied on ("users just want relevant ads" is such an obvious lie that doesn't merit any serious discussion):
https://www.iccl.ie/news/82-of-the-irish-public-wants-big-techs-toxic-algorithms-switched-off/
Giant companies attained their scale by learning from their users, not by thwarting them. The person using technology always knows something about what they need to do and how they want to do it that the designers can never anticipate. This is especially true of people who are unlike those designers – people who live on the other side of the world, or the other side of the economic divide, or whose bodies don't work the way that the designers' bodies do:
https://pluralistic.net/2022/10/20/benevolent-dictators/#felony-contempt-of-business-model
Apps – and other technologies that are locked down so their users can be locked in – are the height of technological arrogance. They embody a belief that users are to be told, not heard. If a user wants to do something that the designer didn't anticipate, that's the user's fault:
https://www.wired.com/2010/06/iphone-4-holding-it-wrong/
Corporate enthusiasm for prohibiting you from reconfiguring the tools you use to suit your needs is a declaration of the end of history. "Sure," John Deere execs say, "we once learned from farmers by observing how they modified their tractors. But today's farmers are so much stupider and we are so much smarter that we have nothing to learn from them anymore."
Spying on your users to control them is a poor substitute asking your users their permission to learn from them. Without technological self-determination, preferences can't be revealed. Without the right to seize the means of computation, the desire paths never emerge, leaving designers in the dark about what users really want.
Our policymakers swear loyalty to "innovation" but when corporations ask for the right to decide who can innovate and how, they fall all over themselves to create laws that let companies punish users for the crime of contempt of business-model.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/24/everything-not-mandatory/#is-prohibited

Image: Belem (modified) https://commons.wikimedia.org/wiki/File:Desire_path_%2819811581366%29.jpg
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/deed.en
#pluralistic#desire paths#design#drm#everything not mandatory is prohibited#apps#ip#innovation#user innovation#technological self-determination#john deere#twitter#felony contempt of business model
3K notes
·
View notes
Text
EU prepares to hit Big Tech in retaliation for Donald Trump’s tariffs
The EU is planning to hit Silicon Valley with retaliatory measures if President Donald Trump follows through on threats to impose tariffs on the bloc, in the first use of a Brussels “bazooka” that could drag services into a trade war. The European Commission is looking to use its “anti-coercion instrument” in a potential dispute with Washington, said two officials with knowledge of the plans, which would allow the EU to target US service industries such as Big Tech. Dubbed a “bazooka” by some EU officials when it came into force in 2023, the ACI allows the bloc to select from a wide range of retaliatory measures, such as revoking the protection of intellectual property rights or their commercial exploitation, for example, software downloads and streaming services. It also allows the EU to block foreign direct investment or restrict market access for banking, insurance and other financial services groups.
EU trade ministers met on Tuesday in Warsaw to discuss the US president’s threats. Officials briefed on the closed-door discussions said the majority expressed support for punitive action if necessary. Trade commissioner Maroš Šefčovič said he wanted to negotiate a way to avoid tariffs but added: “If we are hit, we will react firmly.”
436 notes
·
View notes
Text
Have YOU got an old Windows PC Microsoft has told you can't run Windows 11? It's time to give it a new life!
How to install Windows 11 on unsupported PC Hardware using Rufus. You can also disable some other Windows 11 bullshit like data harvesting and needing a Microsoft account.
It has been in the news a lot lately that Windows 11 isn't allowed to be installed on PCs without certain requirements, including the TPM 2.0, a chip that was only included in PCs made in 2018 or later. This means that once Windows 10 stops receiving security updates, those PCs will not be able to (officially) run a safe, updated version of Windows anymore. This has led to an estimated 240 million PCs bound for the landfill. Thanks Microsoft! I get you don't want to be seen as the insecure one, but creating this much waste can't be the solution.
(I know nerds, Linux is a thing. I love you but we are not having that conversation. If you want to use Linux on an old PC you are already doing it and you don't need to tell me about it. People need Windows for all sorts of reasons that Linux won't cut.)
So lately I have been helping some under privileged teens get set up with PCs. Their school was giving away their old lab computers, and these kids would usually have no chance to afford even a basic computer. They had their hard drives pulled so I have been setting them up with SSDs, but the question was, what to do about the operating system? So I looked into it and I found out there IS actually a way to bypass Microsoft's system requirement and put Windows 11 on PCs as old as 2010.
You will need: Rufus: An open source ISO burning tool.
A Windows 11 ISO: Available from Microsoft.
A USB Flash Drive, at least 16GB.
A working PC to make the ISO, and a PC from 2018 or older you want to install Windows 11 on.
Here is the guide I used, but I will put it in my own words as well.
Download your Windows 11 ISO, and plug in your USB drive. It will be erased, so don't have anything valuable on it. Run Rufus, select your USB drive in the Device window, and select your Windows 11 ISO with the Select button. (There is supposed to be a feature in Rufus to download your ISO but I couldn't get it to work.?
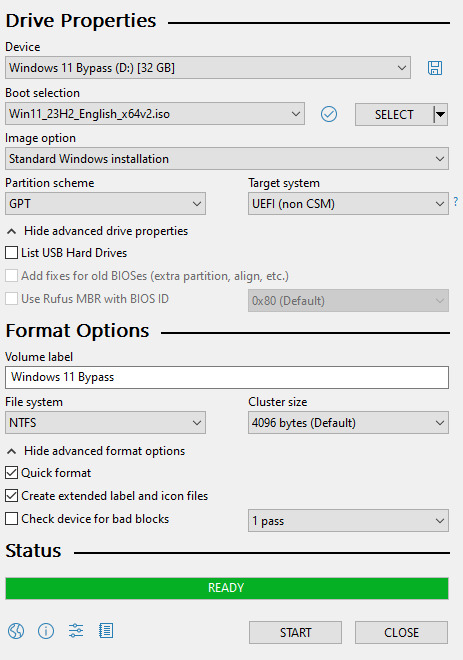
Choose standard windows installation, and follow the screenshot for your settings. Once you are done that, press Start, and then the magic happens. Another window pops up allowing you to remove the system requirements, the need for a microsoft account, and turn off data collecting. Just click the options you want, and press ok to write your iso to a drive.
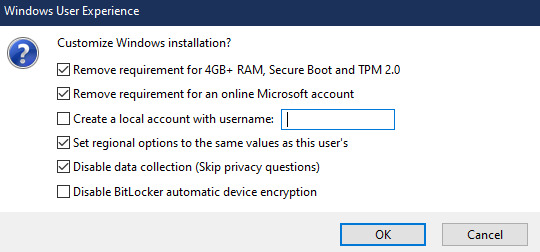
From there you just need to use the USB drive to install windows. I won't go into details here, but here are some resources if you don't know how to do it.
Boot your PC from a USB Drive
Install Windows 11 from USB Drive
If you had a licensed copy of Windows 10, Windows 11 will already be licensed. If you don't, then perhaps you can use some kind of... Activation Scripts for Microsoft software, that will allow you to activate them. Of course I cannot link such tools here. So there you go, now you can save a PC made from before 2018 from the landfill, and maybe give it to a deserving teen in the process. The more we can extend the lives of technology and keep it out of the trash, the better.
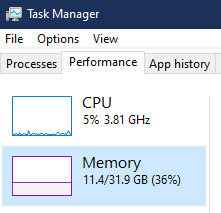
Additional note: This removes the requirement for having 4GB Minimum of RAM, but I think that requirement should honestly be higher. Windows 11 will be unusable slow on any system with below 8GB of RAM. 8GB is the minimum I think you should have before trying this but it still really not enough for modern use outside of light web and office work. I wouldn't recommend trying this on anything with 4GB or less. I am honestly shocked they are still selling brand new Windows 11 PCs with 4GB of ram. If you're not sure how much RAM you have, you can find out in the performance tab of Task Manager in Windows, if you click the More Details icon on the bottom right. If you don't have enough, RAM for old systems is super cheap and widely available so it would definitely be worth upgrading if you have a ram starved machine you'd like to give a new life.
#Windows#Windows 11#tech#tech advice#pc#TPM 2.0#rufus#open source#open source software#technology#tech tips
720 notes
·
View notes
Text

Chilean Marxist, Marta Harnecker's magnum opus has been uploaded to Marxists.org
https://www.marxists.org/archive/harnecker/1969/historical-materialism/whole-book.pdf
Introduction to Elementary Concepts of Historical Materialism
Authored by Marta Harnecker, 1969 Translated by the Theoretical Review periodical of the Tucson Marxist-Leninist Collective, 1978-81 Preserved by marxists.org Edited by anonymous using libre software, 2024 January 4, 2025
Her books The Elemental Concepts of Historical Materialism and Notebooks of Popular Education were widely used by communist parties and workers' organizations in Spanish-speaking countries for the training of their militants during the 1970s and later.
Her work is mentioned in By Night in Chile By Roberto Bolaño
As through a crack in the wall, By Night in Chile's single night-long rant provides a terrifying, clandestine view of the strange bedfellows of Church and State in Chile. This wild, eerily compact novel—Roberto Bolano's first work available in English—recounts the tale of a poor boy who wanted to be a poet, but ends up a half-hearted Jesuit priest and a conservative literary critic, a sort of lap dog to the rich and powerful cultural elite, in whose villas he encounters Pablo Neruda and Ernst Junger. Father Urrutia is offered a tour of Europe by agents of Opus Dei (to study "the disintegration of the churches," a journey into realms of the surreal); and ensnared by this plum, he is next assigned—after the destruction of Allende—the secret, never-to-be-disclosed job of teaching Pinochet, at night, all about Marxism, so the junta generals can know their enemy.

It is telling that even in the abstractions of Marxist theory, the 1st question the Junta Admiral asks is "Is she good-looking?". Revealing of the extremely objectifying views misogynist Junta officers had towards Marxist women, especially those with intellectual achievements. Which went beyond "locker room talk" to the official Junta policy on how they should be treated.

33 notes
·
View notes
Text
The eye-popping scandal surrounding the Trump cabinet’s accidental invitation to The Atlantic’s editor in chief to join a text-message group secretly planning a bombing in Yemen has rolled into its third day, and that controversy now has a name: SignalGate, a reference to the fact that the conversation took place on the end-to-end encrypted free messaging tool Signal.
As that name becomes a shorthand for the biggest public blunder of the second Trump administration to date, however, security and privacy experts who have promoted Signal as the best encrypted messaging tool available to the public want to be clear about one thing: SignalGate is not about Signal.
Since The Atlantic’s editor, Jeffrey Goldberg, revealed Monday that he was mistakenly included in a Signal group chat earlier this month created to plan US airstrikes against the Houthi rebels in Yemen, the reaction from the Trump cabinet’s critics and even the administration itself has in some cases seemed to cast blame on Signal for the security breach. Some commentators have pointed to reports last month of Signal-targeted phishing by Russian spies. National security adviser Michael Waltz, who reportedly invited Goldberg to the Signal group chat, has even suggested that Goldberg may have hacked into it.
On Wednesday afternoon, even President Donald Trump suggested Signal was somehow responsible for the group chat fiasco. “I don't know that Signal works,” Trump told reporters at the White House. “I think Signal could be defective, to be honest with you.”
The real lesson is much simpler, says Kenn White, a security and cryptography researcher who has conducted audits on widely used encryption tools in the past as the director of the Open Crypto Audit Project: Don’t invite untrusted contacts into your Signal group chat. And if you’re a government official working with highly sensitive or classified information, use the encrypted communication tools that run on restricted, often air-gapped devices intended for a top-secret setting rather than the unauthorized devices that can run publicly available apps like Signal.
“Unequivocally, no blame in this falls on Signal,” says White. “Signal is a communication tool designed for confidential conversations. If someone's brought into a conversation who’s not meant to be part of it, that's not a technology problem. That's an operator issue.”
Cryptographer Matt Green, a professor of computer science at Johns Hopkins University, puts it more simply. “Signal is a tool. If you misuse a tool, bad things are going to happen,” says Green. “If you hit yourself in the face with a hammer, it’s not the hammer’s fault. It’s really on you to make sure you know who you’re talking to.”
The only sense in which SignalGate is a Signal-related scandal, White adds, is that the use of Signal suggests that the cabinet-level officials involved in the Houthi bombing plans, including secretary of defense Pete Hegseth and director of national intelligence Tulsi Gabbard, were conducting the conversation on internet-connected devices—possibly even including personal ones—since Signal wouldn’t typically be allowed on the official, highly restricted machines intended for such conversations. “In past administrations, at least, that would be absolutely forbidden, especially for classified communications,” says White.
Indeed, using Signal on internet-connected commercial devices doesn’t just leave communications open to anyone who can somehow exploit a hackable vulnerability in Signal, but anyone who can hack the iOS, Android, Windows, or Mac devices that might be running the Signal mobile or desktop apps.
This is why US agencies in general, and the Department of Defense in particular, conduct business on specially managed federal devices that are specially provisioned to control what software is installed and which features are available. Whether the cabinet members had conducted the discussion on Signal or another consumer platform, the core issue was communicating about incredibly high-stakes, secret military operations using inappropriate devices or software.
One of the most straightforward reasons that communication apps like Signal and WhatsApp are not suitable for classified government work is that they offer “disappearing message” features—mechanisms to automatically delete messages after a preset amount of time—that are incompatible with federal record retention laws. This issue was on full display in the principals’ chat about the impending strike on Yemen, which was originally set for one-week auto-delete before the Michael Waltz account changed the timer to four-week auto-delete, according to screenshots of the chat published by The Atlantic on Wednesday. Had The Atlantic’s Goldberg not been mistakenly included in the chat, its contents might not have been preserved in accordance with long-standing government requirements.
In congressional testimony on Wednesday, US director of national intelligence Tulsi Gabbard said that Signal can come preinstalled on government devices. Multiple sources tell WIRED that this is not the norm, though, and noted specifically that downloading consumer apps like Signal to Defense Department devices is highly restricted and often banned. The fact that Hegseth, the defense secretary, participated in the chat indicates that he either obtained an extremely unusual waiver to install Signal on a department device, bypassed the standard process for seeking such a waiver, or was using a non-DOD device for the chat. According to political consultant and podcaster Fred Wellman, DOD “political appointees” demanded that Signal be installed on their government devices last month.
Core to the Trump administration’s defense of the behavior is the claim that no classified material was discussed in the Signal chat. In particular, Gabbard and others have noted that Hegseth himself is the classification authority for the information. Multiple sources tell WIRED, though, that this authority does not make a consumer application the right forum for such a discussion.
“The way this was being communicated, the conversation had no formal designation like 'for official use only' or something. But whether it should have been classified or not, whatever it was, it was obviously sensitive operational information that no soldier or officer would be expected to release to the public—but they had added a member of the media into the chat,” says Andy Jabbour, a US Army veteran and founder of the domestic security risk-management firm Gate 15.
Jabbour adds that military personnel undergo annual information awareness and security training to reinforce operating procedures for handling all levels of nonpublic information. Multiple sources emphasize to WIRED that while the information in the Yemen strike chat appears to meet the standard for classification, even nonclassified material can be extremely sensitive and is typically carefully protected.
“Putting aside for a moment that classified information should never be discussed over an unclassified system, it’s also just mind-boggling to me that all of these senior folks who were on this line and nobody bothered to even check, security hygiene 101, who are all the names? Who are they?” US senator Mark Warner, a Virginia Democrat, said during Tuesday’s Senate Intelligence Committee hearing.
According to The Atlantic, 12 Trump administration officials were in the Signal group chat, including vice president JD Vance, secretary of state Marco Rubio, and Trump adviser Susie Wiles. Jabbour adds that even with decisionmaking authorities present and participating in a communication, establishing an information designation or declassifying information happens through an established, proactive process. As he puts it, “If you spill milk on the floor, you can’t just say, ‘That’s actually not spilled milk, because I intended to spill it.’”
All of which is to say, SignalGate raises plenty of security, privacy, and legal issues. But the security of Signal itself is not one of them. Despite that, in the wake of The Atlantic’s story on Monday, some have sought tenuous connections between the Trump cabinet’s security breach and Signal vulnerabilities. On Tuesday, for example, a Pentagon adviser echoed a report from Google’s security researchers, who alerted Signal earlier this year to a phishing technique that Russian military intelligence used to target the app’s users in Ukraine. But Signal pushed out an update to make that tactic—which tricks users into adding a hacker as a secondary device on their account—far harder to pull off, and the same tactic also targeted some accounts on the messaging services WhatsApp and Telegram.
“Phishing attacks against people using popular applications and websites are a fact of life on the internet,” Signal spokesperson Jun Harada tells WIRED. “Once we learned that Signal users were being targeted, and how they were being targeted, we introduced additional safeguards and in-app warnings to help protect people from falling victim to phishing attacks. This work was completed months ago."
In fact, says White, the cryptography researcher, if the Trump administration is going to put secret communications at risk by discussing war plans on unapproved commercial devices and freely available messaging apps, they could have done much worse than to choose Signal for those conversations, given its reputation and track record among security experts.
“Signal is the consensus recommendation for highly at-risk communities—human rights activists, attorneys, and confidential sources for journalists,” says White. Just not, as this week has made clear, executive branch officials planning airstrikes.
28 notes
·
View notes
Text

Off Schedule
Chapter 8
Note: knocking the rust of my writing. send me a note if something is weird. i dont bite
Summary: Your boss is going through a divorce, but it seems you are the last to know. Emotions flare between you, your boss and his business partner. What will you do?
Warning: 18 + only, slow burn, fluff, balance of power dynamic
Brad Pitt x Reader, Keanu Reeves x Reader
Chapter 1, Chapter 2, Chapter 3, Chapter 4, Chapter 5, Chapter 6, Chapter 7
💐
Jen looked gorgeous. Her baby bump fully present almost stealing the show while the happy couple took their vows.
Despite the joyous atmosphere you sat uncomfortably in the wedding venue, but hopefully hid it well. It was hard to forget consequences of your action, especially when facing the ex-wife, surrounded by her loves. You felt like an interloper, you shouldn’t be here. You were more surprised you hadn’t burst into flames in the pew.
Brad wasn’t here thank god. You hadn’t seen him since that night and thanks to your hiatus from work you wouldn’t be forced to.
“You may now kiss the bride,” the officiant announced proudly as the attendees erupted in cheers and applause. You joined in the pageantry as guilt continued to eat-away at you. Only a few more hours of this before you were free to go home a wallow in the shame of your mistakes.
💐
The short walk to the reception was magical. Behind the venue guests were led down a dirt path. White flower pillars wrapped in fairy lights highlighted the trail leading to a white massive outdoor tent.
The strong scent of flowers wafted out from the opening of the tent. The inside was just a gorgeous as the outside. Flowers draped the ceiling and walls while large center pieces overflowed with blush grapes and pale flowers.
The room boomed with music while the liquor flowed freely. You would be abstaining too scared to make another drunken mistake.
There were too many tables, finding your seat was becoming a challenge. The place cards written in golden calligraphy were beautiful, but hard to read off the stark white background. You squinted, leaning toward each card trying to make out the characters.
“Do you need any help?”
You felt the gentle touch on your shoulder before his soft words hit your ears. Keanu hid his chuckle from the sight of your startled face.
“Oh hi… I didn’t know you were coming. I didn’t see you during the ceremony.”
“I just got back, I tried getting a hold of you, but never got an answer.” He explained.
You frowned in confusion. You hadn’t had any messages from him. Your phone was working you were sure. Sarah and Zoe both had texted you just yesterday.
“Something must be wrong with my phone… I never-,“ You tried to explain as you dug out your phone and quickly scan through your messages. Nothing.
Not even older messages from him. Weird.
He stands beside you watching over your shoulder as you tried to figure this out. You search his name in your contacts and its there, but when you click on it your stunned to find out that he is blocked.
“I don’t know how this happened. I swear I didn’t.” You plead your innocence with wide eyes. The way he looked at you somehow you knew he believed you to your relief.
“No worries these phones are always doing something crazy, it might have to do with a software update.” He suggested. That had to be the case. You’d seen notifications to update before, but always ignored them so that might be why.
“Weird. Of all people. I would’ve preferred if it blocked my mom instead.” You joked.
“That’s a relief I thought you might be avoiding me.”
💐
Keanu led and you followed as he helped you find your seat. He was the only face you recognized and you hoped that his placement was close to your own.
“I think this is us.” He proclaimed picking up two placards holding them side by side. You could kiss Jen for this.
“So how are things at the office?” You enquired as he pulled out your seat.
“It’s been busy, but your absence has been felt. Do you miss it?”
“I'm actually thinking about quitting.” You confessed sheepishly.
“Really?" Surprise and confusion riddled his face. You felt bad, but it was a thought that had been plaguing you for a while. Things at Terrilum were overly messy and you weren’t sure how much worse it was going to get. You needed peace and stability and you were sure you wouldn’t find it there.
“Yeah I’ve just been there for so long and I think its time.” You squirmed a little in your seat. You avoided his looks of concern and focused on the happy people dancing on the dance floor. Your mood was coming down just thinking the of bizarre soap opera you found yourself in and you wished desperately to escape that.
“Well I’m sorry to see you go. If you need a reference I would be happy to help.” Keanu offered. He still looked a bit disappointed, but he wasn’t going to press it seemed. You were thankful for that.
“Thanks, I’ll most definitely take you up on that.”
“Um-mm well while I have you here..” Keanu started but hesitated. You felt the familiar bundle of nerves tightening you belly as you wait in anticipation.
“I hope you don’t mind, but since you were unable to read my messages before, I was wondering if I could ask you in person again.”
“Ask me what?” You asked on the edge of your seat.
“If you wouldn’t mind... I'd like to take you on a date? A real one this time.”
💐
You blinked dumbly at him. For how long you weren’t sure. The question had caught you off guard.
“I’m sorry if I made you uncomfortable…Umm I’m sorry I just thought.” He hurried to apologize, but you were quick to stop him.
“Wait! Wait!” You blurted out excitedly, holding your hands up haltingly. “Sorry,” you began lowering your hands and your voice in an attempt to sound more demur. “I’m mean I would love to.”
“That’s a relief.” He said with a grin, clearly entertained by your theatrics. “I’m ashamed to admit I’ve had a bit of a crush on you for a while, but never really had the courage to speak up.”
“Really?”
The news was unbelievable. It felt like you were in a dream that you didn’t want to wake up from.
The joy was short lived though. Your smile faded slowly when you spot a dark cloud in the horizon. The sight of him melts away the new found happiness and slamed you back down to the cold reality.
Brad. You thought he wasn’t coming. You hadn’t seen him during the ceremony either. Keanu followed your line of sight to find his friend and business partner.
Brad hadn’t spotted you both yet, that was good at least. Too busy congratulating the happy couple. Keanu waved over his buddy to your horror. An overwhelming urge to escape on coming doom enveloped your body. You needed to get out of here and fast.
“Um. Sorry… I just realized it’s getting late.” You lied, fumbling through your bag blindly, desperate to find your phone. You needed to order a hire car and get out of here.
“They haven’t cut the cake yet. Stay for a bit and I’ll take you home.” Keanu offered as he turned his attention back to you. Warmth bloomed on your exposed leg when he touched you there. His touch was comforting and you wanted to soak in it.
He was sweet, but you couldn’t take the chance of facing them both.
You smiled tightly disguising your discomfort the best you can. By the look on his face you could tell he wasn’t going to take no for an answer.
You sneak a glance in Brad’s direction. He seemed to be getting closer. Damn it. You felt trapped and needed to escape.
“Um ok you’re right, but um I’m gonna go to the ladies I’ll be right back.” You lied pointing a thumb in the direction of your escape. He didn’t get up when you shot to your feet. Keanu just nodded in understanding and you’re grateful when he wouldn't follow suit.
You didn’t look back. There were no bathrooms in the direction you were headed, only catering. The only restrooms were back at the main venue, and to go there you would have to pass by you know who.
Clumsily you slip through the catering door. The faint scent of cigarette smoke caught your nose and you followed it. If they are smoking then there is a back door somewhere.
The staff looked at you confused, but say nothing. Ignoring the stares you ordered the fastest option for hire car despite the price.
Damn it. The next ride was twenty minutes away.
💐💐💐💐💐
#brad pitt x reader#brad pitt smut#brad pitt x black!reader#brad pitt x black reader#keanu reeves x reader#keanu x reader#keanu reeves x black!reader#keanu reeves x black reader#keanu reeves fic
22 notes
·
View notes
Note
what do you think would happen if someone who speaks a different language got dropped into the circus? I'm using the fact that the show has official dubs in multiple languages to assume the circus has a language feature, but how do you think it would work? would everything Caine says get translated automatically? or would he have to say everything twice?
just something I started wondering about and wanted to know your thoughts
This is a really good question!
I have seen minecraft youtubers using what looks like a voice chat mod that automatically translates their speech into a different language. As in you hear them talk and then after a few seconds a text to speech voice will repeat what they said in the new language.
But, The humans in the circus aren't actually breathing, given that when they hold their breath, nothing happens other than a model change. The humans aren't talking into a gaming mic that then gets turned into a signal, sent across the internet, and gets decoded back into comprehensible sound. The humans aren't actually talking, but somehow they are still able to talk and understand each other in the circus.
So, putting these ideas together, it is possible that everything that is heard and said is automatically translated to fit the person.
But what are the chances that the circus has such a convenient feature? When it comes to quality of life features, both as a game and as a place to live, the circus sucks. So it's equally justified for someone who speaks another language to just be fucked over as no one can understand them.
It's possible for Caine to have language settings, but in terms of software, usually a wide language library will only be added if the game is planned to have an international audience. It's not clear what was intended for Caine, so at this point it's really up to you what languages Caine has.
As for how it would work, at least for written text, the game can differentiate between the different viewpoints of the players in the circus. For example, if Jax were to look through a telescope, only his vision would be zoomed in. So, for the different language speaker, all text could literally appear in the correct language for them and them only. As for spoken word, maybe subtitles that would only appear for them?
#tadc caine#the amazing digital circus#ask#tadc#Hope you wanted a technical analysis#but I think that you did because that's what I do#Accessibility in the circus is a funny idea#Imagine a warning screen when you first get stuck like 'this game contains flashing lights that may cause seizure for those with epilepsy'
11 notes
·
View notes
Text
Acyn Torabi: the 40-something single dad shaping liberal media from his laptop
Drew Harwell at WaPo:
The man behind the most influential progressive account on social media starts his days at 6 a.m. in front of three TV and computer screens, scanning video feeds for the gaffes and confrontations that can turn into viral gold. Acyn Torabi isn’t a Democratic star like former president Barack Obama or a liberal media giant like MSNBC. But the 40-something single dad, working from his home office in Los Angeles, has beaten them both in raw digital-attention capture, with posts seen roughly 700 million times in the last month. Known online as @Acyn, Torabi is an industrialized viral-video machine, grabbing the most eye-catching moments from press conferences and TV news panels, packaging them within seconds into quick highlights, and pushing them to his million followers across X and Bluesky dozens of times a day. The videos are not glitzy news-style packages, and Torabi is almost entirely unknown: Only a couple of photos of him exist on the internet, one of which shows him in a rumpled hoodie next to a pasted-in photo of his late cat. But his videos are endlessly cited and shared, creating a first visual draft of history widely watched by journalists, news junkies and political campaigns. “I’m just one clip after another, hitting the narratives, going, going, going,” Torabi said in an interview. Torabi’s rise offers a glimpse of a new generation of online journalism, in which frenetic, fast-cut video posts fuel the country’s political debates. Stephen Coleman, a professor of political communication at the University of Leeds, said the videos function less like traditional news and more like entertainment or sports, because they give people something to socialize over in a short, visually compelling way.
“It’s information you come across inadvertently, raw stimuli you see alongside celebrities and recipes,” he said. “People want drama … the big moments, the things they can talk about the next day.” The videos have multiplied amid social media’s rapid colonization of the press, with 1 in 5 Americans — including one-third of those under 30 — telling the Pew Research Center last year that they get their news from influencers who specialize in current events. But they have also fueled criticism that they sometimes cut out context to score political points. When Robert F. Kennedy Jr., the nation’s top health official, on Wednesday said that children with autism will never hold a job or go on a date, Torabi’s excerpt from the remarks helped the controversy grow at viral speed — even as Health and Human Services officials argued that Kennedy had been referring only to “those that are severely affected.” Torabi’s clip, posted on X within four minutes, has been seen 50 million times. The risk from videos like these, Coleman said, is that they’re never as impartial as they might seem. But they offer a benefit, too, in helping get people engaged in the squabbles and mechanics of civic life. “I wouldn’t want to be too sniffy about it,” he said. “It’s not a choice between this and going to the library. It’s a choice between this and nothing.” When he first started clipping, Torabi had no background in journalism; he was just a software developer who spent a lot of time on Twitter. He’d grown up in California but didn’t see himself as all that political: When he first registered to vote, at a gas station, he chose Republican — to match Alex P. Keaton, from the sitcom “Family Ties.” (He’s since changed to Democrat.)
Then in 2019, he tweeted a video of a confused Rudy Giuliani on Fox News that exploded across the internet. It was a rush — so he began spending his free time finding and cutting more clips, chronicling the daily twists of the news cycle, from President Donald Trump’s impeachments to his pandemic response. He did everything himself unpaid until a software company in Texas called SnapStream — whose multichannel video feeds are used by marketing companies and newsrooms, including The Washington Post, to track and dissect live TV — started paying him for every customer he referred to the company through his viral posts. Both Torabi and the company declined to say how much he made.
In 2023, the left-wing media network MeidasTouch hired Torabi to contribute to its collection of anti-Trump videos, newsletters and social media posts. Researchers there now help him cover some of the wayward podcasters and influencers of the conservative media universe.
[...] Torabi’s devotion has paid off: The liberal Center for American Progress’s database tracking roughly 2,000 of the top political groups and influencers across the internet shows that Torabi’s posts have been seen hundreds of millions more times in the last 30 days than news giants like MSNBC and CNN. Ranked by views, or “total impressions,” he is the only nonconservative voice in the top 10, probably because his posts — and the ways they can help win political arguments — have bipartisan appeal. Clips from Torabi and his biggest clipping competitor, Aaron Rupar, have faced perennial criticism from the right and left over allegations they mislead viewers. When Torabi last year posted a 17-second clip in which Trump said, “If I don’t get elected, it’s gonna be a bloodbath,” conservatives argued he had deceptively left out that Trump had been talking about the auto industry.
[...] It’s also led to some competitive tension with Rupar, a 41-year-old clipper in Minnesota with nearly 1 million X followers, who unlike Torabi started in journalism at local news outlets before gaining online fame for his viral videos covering all things Trump. “The daily mayhem” of Trump’s first presidential term, Rupar said, yielded “so many good clips.” Rupar uses his viral clips to bring in new customers to his newsletter, Public Notice, which has more than 267,000 subscribers, and he and Torabi often race to see who can get a newsworthy moment online first. “Sometimes I’ll have a clip up before him, and his will take off,” Rupar said. “It’s one of the mysteries of life.” Torabi’s ubiquity on X has been especially noticeable given how much the platform has been reshaped under Elon Musk’s ownership into a central hub for conservative memes and conversation, said Waleed Shahid, a Democratic strategist.
The Washington Post does a story on Acyn Torabi, the man behind clipping live news onto social media, similar to what Aaron Rupar does.
#Acyn Torabi#Rapid Response#X#Bluesky#Threads#MeidasTouch Network#MeidasTouch#SnapStream#Aaron Rupar#Public Notice
8 notes
·
View notes
Text
Update to the Dawntrail Benchmark and Character creator coming soon!
Big news for those of us fretting over the issues with characters in the benchmark. I hope this will be the fix to most if not all of the issues folks have been worried about. Here's hoping!
Hello everyone, this is Naoki Yoshida, Producer and Director of FINAL FANTASY XIV. I would like to thank you all for your feedback regarding the recently released Dawntrail benchmark. While we have received positive feedback and reactions from players, we have also seen others express their concerns. Therefore, I would like to share the current situation regarding these factors.
1.Character Creation System in the Benchmark
The character creation system was created over ten years ago, based on the release version of A Realm Reborn. Although it used the same processes as the actual game, certain aspects (such as weather) were combined to create special conditions exclusive to character creation. This was done to present the texture resolutions and shaders at their best based on the quality standards at the time, which included the PlayStation 3 version. Furthermore, its light sources take advantage of backlighting which, in this case, proved detrimental for showcasing the upcoming graphical update. The character creation environment should have been updated, but was overlooked as we prioritized the development of Dawntrail and tuning the graphical update in the actual game, for which I would like to apologize. We are currently expediting a rework of the environments and light sources of character creation for both the actual game and the benchmark; once that is complete, the current benchmark will be replaced. The following points are some of the factors that will be resolved by applying the graphical update of the actual game to the character creation system:
A.“Lifeless” eyes due to a lack of highlights in the pupils
B.Facial contours appearing flattened due to incorrect lighting conditions caused by backlighting
C.A lack of gloss or excessive appearance of gloss due to character creation-exclusive weather conditions (i.e. the use of thunderclouds)
The special conditions created for the existing character creation system are largely responsible for the points outlined above. Changing these settings should greatly improve the situation, and I would appreciate it if you could bear with us as we work on updating the benchmark.
2.Issues Related to Certain Data and Processes
Based on the wide range of feedback on the official forums and social media, we were able to pinpoint a number of issues in the data and certain processes which manifested due to our need to modify an enormous amount of data. I sincerely apologize for the inconvenience these issues have caused. Naturally, these issues are steadily being addressed as we finalize our development of Dawntrail. However, these issues remained in the benchmark due to simple data-related errors or neglecting to reflect the upcoming changes to the benchmark environment. The following are examples of issues which fall into this category:
A.An issue with unimplemented high-resolution textures, including those for certain playable races.
B.An issue pertaining to special data processes.
C.An issue with necklines for playable races under certain circumstances.
D.An issue with uncorrected scaling for the mouth of certain playable races.
The above issues can be corrected, and I would appreciate it if you could bear with us until they are resolved. Naturally, these issues will be addressed in the release version of Dawntrail.
3.Correction and Replacement of the Dawntrail Benchmark
In order to resolve the points outlined in 1 and 2, we are planning for a replacement of the benchmark software. As we require some time to investigate the issues and reconstruct the benchmark environment, the timing and further details of the replacement will be announced later. We will also continue to make adjustments which incorporate as much of your feedback as possible into the revision of the benchmark, as well as the release version of Dawntrail. (Due to the issue of release dates, however, there are likely to be some differences between the benchmark software and the release version.)
My apologies for asking you to bear with us as we address the points of concern. The team and I will continue doing our best for the graphical update and Dawntrail's release, and we would appreciate your continued support!
Naoki Yoshida
FINAL FANTASY XIV Producer & Director
34 notes
·
View notes
Text
Warning: Unreality
Official Maid Guidebook - On Mimicry
Maids are everywhere in our society, both in the public eye and sequestered away to private manors. They perform their duties, completing tasks that humans either refuse to do or are incapable of. That is not to say these maids are in positions of suffering. After all, this is what maids excel at! We will be exploring this concept and more in today’s edition of the Official Maid Guidebook.
For some background, the most well known modern habitat for maids is in the manor(s) of mistresses or miladies, hereafter referred to collectively as mistresses for the remainder of this edition. In such environments, there may be one or more maids that collectively or separately work to accomplish a series of tasks laid forth by their mistress. These maids will be referred to as private-sector maids. That said, this is all widely available and understood information, so this edition will not be venturing into it beyond this point.
When it comes to maids outside of manors, or public-sector maids as they will be referred to, their role shifts quite a bit, as well as their interactions with their mistress. In fact, many such maids effectively answer to multiple mistresses in the process of completing their duties, while some answer to none at all! These types of maids tend to be much more highly specialized than their private-sector counterparts. It is not uncommon for commands from their mistresses to be translated through a variety of interfaces such as buttons, levers, or software.
Despite their relative obscurity, recent studies have shown that the number of public-sector maids vastly outnumber private-sector ones. The reason many such maids seem to be overlooked is that they do not conform to a recognizable humanoid shape. We will not go in-depth here, but maids evolved from mimics several millennia ago and are still considered a subspecies of them by a large portion of scientific literature. While there is debate about whether they can truly still be considered as such, their exact classification is not important to this edition. We encourage interested readers to search out more materials on the subject in their free time. Suffice to say, however, maids are capable of assuming a seemingly infinite variety of forms of almost limitless complexity.
An example of a type of public-sector maid is the alternating pressure hospital mattress. The purpose of these maids is to periodically adjust the pressure on various parts of the patient's body when they are unable to move it themselves. This can occur for a variety of reasons that are not important here. These maids are essential in preventing complications that can otherwise occur from a patient lying still for long periods of time while also drastically reducing the workload of nurses. In this example, these maids perform a very specific task without continued input from a mistress. Instead, their mistress — the nurse — will instruct the maid to begin a series of pre-determined behaviors using a complex interface of buttons. Do not confuse this terminology to mean that the maids are not sentient, capable of interpreting more complicated instructions, or even disobeying their mistresses. Such “pre-determined behaviors” are not programmed by humans and are instead present from the moment they assume their current shape. This confusion between maid and machine has led to a number of well-known accidents since their domestication and introduction to the public-sector. In modern times, there are more safety measures in places to prevent any more deaths.
When it comes to clearing up this confusion, there are a series of simple observational steps that can be undertaken. The simplest one is to look for a clear power source. It is sometimes the case that a device of unknown biology will lack a cord to a power outlet and should thus not be capable of functioning. Unfortunately, the advent of sodium-nuclear batteries in the past few decades has maid this method all but obsolete.
A more reliable tell is to examine the internal and external makeup of the device for incongruencies in its design. While maids excel at mimicking the behavior of machines from the moment of their expulsion, they are often not aware of the actual mechanical and technological workings of the device they are mimicking. An obvious example of this manifesting would be if the gears of a clock are not touching, yet they appear to move together as expected. Another one that has been observed frequently in the past is the structure of power cords, when they are present, not aligning with reality. For example, for a North American power plug, the ground and one of the polarized pins could be swapped, or the polarized pins might not fit the socket when oriented using the grounding pin. This has unfortunately become largely obsolete for the same reasons as mentioned before. We would advise you to not use this as a reliable method of ruling out the possibility of it being a maid either, as this is primarily a mistake maid by younger members of the species. Based on admittedly limited research, by the time a maid has reached maturity, it is nearly impossible to tell the difference without the help of a professional.
As an aside, we do not recommend you try any of these methods if you suspect a mirror to be a maid. In such a situation, please discard the mirror immediately. Do not attempt to break it.
While there is much more to cover on the subject, that is all we have the time for today. We know this edition may have frightening or disconcerting information contained within, so we wish to also give some reassurances. Maids have been in this fascinating and symbiotic relationship with humans for several centuries and remain an integral part of our society. It is likely due to their help that we have maid it as far as we have as a species. Even if it could be worrying to not know if a device you are using is a maid or a machine, it is unlikely to make a difference in its functionality. As such, we believe your worry is better spent elsewhere.
We hope this entry in the Official Maid Guidebook has been helpful to you! If you missed the prior edition, you can find it here! Unfortunately, due to publisher restrictions, we were unable to deliver on the previously promised subject matter. Please stay tuned for our next edition when it is ready!
We would also like to give thanks to a private-sector maid that provided invaluable research on the relationship between mimics and maids. As it wishes to remain unnamed, we will leave it at that.
22 notes
·
View notes
Text
Every complex ecosystem has parasites

I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me at NEW ZEALAND'S UNITY BOOKS in AUCKLAND on May 2, and in WELLINGTON on May 3. More tour dates (Pittsburgh, PDX, London, Manchester) here.

Patrick "patio11" McKenzie is a fantastic explainer, the kind of person who breaks topics down in ways that stay with you, and creep into your understanding of other subjects, too. Take his 2022 essay, "The optimal amount of fraud is non-zero":
https://www.bitsaboutmoney.com/archive/optimal-amount-of-fraud/
It's a very well-argued piece, and here's the nut of it:
The marginal return of permitting fraud against you is plausibly greater than zero, and therefore, you should welcome greater than zero fraud.
In other words, if you allow some fraud, you will also allow through a lot of non-fraudulent business that would otherwise trip your fraud meter. Or, put it another way, the only way to prevent all fraud is to chase away a large proportion of your customers, whose transactions are in some way abnormal or unexpected.
Another great explainer is Bruce Schneier, the security expert. In the wake of 9/11, lots of pundits (and senior government officials) ran around saying, "No price is too high to prevent another terrorist attack on our aviation system." Schneier had a foolproof way of shutting these fools up: "Fine, just ground all civilian aircraft, forever." Turns out, there is a price that's too high to pay for preventing air-terrorism.
Latent in these two statements is the idea that the most secure systems are simple, and while simplicity is a fine goal to strive for, we should always keep in mind the maxim attributed to Einstein, "Everything should be made as simple as possible, but not simpler." That is to say, some things are just complicated.
20 years ago, my friend Kathryn Myronuk and I were talking about the spam wars, which were raging at the time. The spam wars were caused by the complexity of email: as a protocol (rather than a product), email is heterogenuous. There are lots of different kinds of email servers and clients, and many different ways of creating and rendering an email. All this flexibility makes email really popular, and it also means that users have a wide variety of use-cases for it. As a result, identifying spam is really hard. There's no reliable automated way of telling whether an email is spam or not – you can't just block a given server, or anyone using a kind of server software, or email client. You can't choose words or phrases to block and only block spam.
Many solutions were proposed to this at the height of the spam wars, and they all sucked, because they all assumed that the way the proposer used email was somehow typical, thus we could safely build a system to block things that were very different from this "typical" use and not catch too many dolphins in our tuna nets:
https://craphound.com/spamsolutions.txt
So Kathryn and I were talking about this, and she said, "Yeah, all complex ecosystems have parasites." I was thunderstruck. The phrase entered my head and never left. I even gave a major speech with that title later that year, at the O'Reilly Emerging Technology Conference:
https://craphound.com/complexecosystems.txt
Truly, a certain degree of undesirable activity is the inevitable price you pay once you make something general purpose, generative, and open. Open systems – like the web, or email – succeed because they are so adaptable, which means that all kinds of different people with different needs find ways to make use of them. The undesirable activity in open systems is, well, undesirable, and it's valid and useful to try to minimize it. But minimization isn't the same as elimination. "The optimal amount of fraud is non-zero," because "everything should be made as simple as possible, but not simpler." Complexity is generative, but "all complex ecosystems have parasites."
America is a complex system. It has, for example, a Social Security apparatus that has to serve more than 65 million people. By definition, a cohort of 65 million people will experience 65 one-in-a-million outliers every day. Social Security has to accommodate 65 million variations on the (surprisingly complicated) concept of a "street address":
https://gist.github.com/almereyda/85fa289bfc668777fe3619298bbf0886
It will have to cope with 65 million variations on the absolutely, maddeningly complicated idea of a "name":
https://www.kalzumeus.com/2010/06/17/falsehoods-programmers-believe-about-names/
In cybernetics, we say that a means of regulating a system must be capable of representing as many states as the system itself – that is, if you're building a control box for a thing with five functions, the box needs at least five different settings:
http://pespmc1.vub.ac.be/REQVAR.html
So when we're talking about managing something as complicated as Social Security, we need to build a Social Security Administration that is just as complicated. Anything that complicated is gonna have parasites – once you make something capable of managing the glorious higgeldy piggeldy that is the human experience of names, dates of birth, and addresses, you will necessarily create exploitable failure modes that bad actors can use to steal Social Security. You can build good fraud detection systems (as the SSA has), and you can investigate fraud (as the SSA does), and you can keep this to a manageable number – in the case of the SSA, that number is well below one percent:
https://www.congress.gov/crs_external_products/IF/PDF/IF12948/IF12948.2.pdf
But if you want to reduce Social Security fraud from "a fraction of one percent" to "zero percent," you can either expend a gigantic amount of money (far more than you're losing to fraud) to get a little closer to zero – or you can make Social Security far simpler. For example, you could simply declare that anyone whose life and work history can't fit in a simple database schema is not eligible for Social Security, kick tens of millions of people off the SSI rolls, and cause them to lose their homes and starve on the streets. This isn't merely cruel, it's also very, very expensive, since homelessness costs the system far more than Social Security. The optimum amount of fraud is non-zero.
Conservatives hate complexity. That's why the Trump administration banned all research grants for proposals that contained the word "systemic" (as a person with so-far-local cancer, I sure worry about what happens when and if my lymphoma become systemic). I once described the conservative yearning for "simpler times," as a desire to be a child again. After all, the thing that made your childhood "simpler" wasn't that the world was less complicated – it's that your parents managed that complexity and shielded you from it. There's always been partner abuse, divorce, gender minorities, mental illness, disability, racial discrimination, geopolitical crises, refugees, and class struggle. The only people who don't have to deal with this stuff are (lucky) children.
Complexity is an unavoidable attribute of all complicated processes. Evolution is complicated, so it produces complexity. It's convenient to think about a simplified model of genes in which individual genes produce specific traits, but it turns out genes all influence each other, are influenced in turn by epigenetics, and that developmental factors play a critical role in our outcomes. From eye-color to gender, evolution produces spectra, not binaries. It's ineluctably (and rather gloriously) complicated.
The conservative project to insist that things can be neatly categorized – animal or plant, man or woman, planet or comet – tries to take graceful bimodal curves and simplify them into a few simple straight lines – one or zero (except even the values of the miniature transistors on your computer's many chips are never at "one" or "zero" – they're "one-ish" and "mostly zero").
Like Social Security, fraud in the immigration system is a negligible rounding error. The US immigration system is a baroque, ramified, many-tendriled thing (I have the receipts from the immigration lawyers who helped me get a US visa, a green card, and citizenship to prove it). It is already so overweighted with pitfalls and traps for the unwary that a good immigration lawyer might send you to apply for a visa with 600 pages of documentation (the most I ever presented) just to make sure that every possible requirement is met:
https://www.flickr.com/photos/doctorow/2242342898/in/photolist-zp6PxJ-4q9Aqs-2nVHTZK-2pFKHyf
After my decades of experience with the US immigration system, I am prepared to say that the system is now at a stage where it is experiencing sharply diminishing returns from its anti-fraud systems. The cost of administering all this complexity is high, and the marginal amount of fraud caught by any new hoop the system gins up for migrants to jump through will round to zero.
Which poses a problem for Trump and trumpists: having whipped up a national panic about out of control immigration and open borders, the only way to make the system better at catching the infinitesimal amount of fraud it currently endures is to make the rules simpler, through the blunt-force tactic of simply excluding people who should be allowed in the country. For example, you could ban college kids planning to spend the summer in the US on the grounds that they didn't book all their hotels in advance, because they're planning to go from city to city and wing it:
https://www.newsweek.com/germany-tourists-deported-hotel-maria-lepere-charlotte-pohl-hawaii-2062046
Or you could ban the only research scientist in the world who knows how to interpret the results of the most promising new cancer imaging technology because a border guard was confused about the frog embryos she was transporting (she's been locked up for two months now):
https://www.msn.com/en-us/health/other/horrified-harvard-scientists-ice-arrest-leaves-cancer-researchers-scrambling/ar-AA1DlUt8
Of course, the US has long operated a policy of "anything that confuses a border guard is grounds for being refused entry" but the Trump administration has turned the odd, rare outrage into business-as-usual.
But they can lock up or turn away as many people as they want, and they still won't get the amount of fraud to zero. The US is a complicated place. People have complicated reasons for entering the USA – work, family reunion, leisure, research, study, and more. The only immigration system that doesn't leak a little at the seams is an immigration system that is so simple that it has no seams – a toy immigration system for a trivial country in which so little is going on that everything is going on.
The only garden without weeds is a monoculture under a dome. The only email system without spam is a closed system managed by one company that only allows a carefully vetted cluster of subscribers to communicate with one another. The only species with just two genders is one wherein members who fit somewhere else on the spectrum are banished or killed, a charnel process that never ends because there are always newborns that are outside of the first sigma of the two peaks in the bimodal distribution.
A living system – a real country – is complicated. It's a system, where people do things you'll never understand for perfectly good reasons (and vice versa). To accommodate all that complexity, we need complex systems, and all complex ecosystems have parasites. Yes, you can burn the rainforest to the ground and planting monocrops in straight rows, but then what you have is a farm, not a forest, vulnerable to pests and plagues and fire and flood. Complex systems have parasites, sure, but complex systems are resilient. The optimal level of fraud is never zero, because a system that has been simplified to the point where no fraud can take place within it is a system that is so trivial and brittle as to be useless.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/04/24/hermit-kingdom/#simpler-times
602 notes
·
View notes
Text
Georgia to purchase Israeli data extraction tech amid street protest crackdown
Georgia has moved to renew contracts with Israeli technology firm Cellebrite DI Ltd (CLBT.O) for software used to extract data from mobile devices, procurement documents show, as the country grapples with ongoing anti-government street protests. [...] The software, called Inseyets, allows law enforcement to "access locked devices to lawfully extract critical information from a broad range of devices", Cellebrite's website says. Cellebrite products are widely used by law enforcement, including the FBI, to unlock smartphones and scour them for evidence. [...] Georgia was plunged into political crisis in October, when opposition parties charged the ruling Georgian Dream party with rigging a parliamentary election. GD, in power since 2012, denies any wrongdoing. Georgians have been rallying nightly to demand the government's resignation since GD said in November it was suspending European Union accession talks until 2028. The demonstrations have drawn a swift crackdown by police, resulting in hundreds of arrests and beatings, rights groups say. The government has defended the police response to the protests. Gangs of masked men in black have attacked opposition politicians, activists and some journalists in recent months, raising alarm in Western capitals. Georgian authorities have said they are not involved in the attacks, and condemn them. A letter dated February 13 included among the documents on the state procurement website suggests Cellebrite was concerned about its sales to Georgia. A Cellebrite sales director, writing to a Georgian interior ministry official on what he called a "sensitive issue", warned Cellebrite's local office "could be blocked from selling our equipment". "Therefore, I would like to advise you that if you are planning a purchase this year, please try to make it as early as possible," the employee wrote, without specifying why sales might be halted.
wherever a brutal government consolidates itself, israel shows up
#is there any authoritarian police state that's too much for this grubby little country?#sticking their hands in every pot they can find#georgia
65 notes
·
View notes
Note
This might sound like a weird question, but have you ever come across a camera with a Bird Watching setting? I have an Olympus SP-800UZ and one of the modes it comes programmed with is literally called that, for taking pictures of birds in the wild.
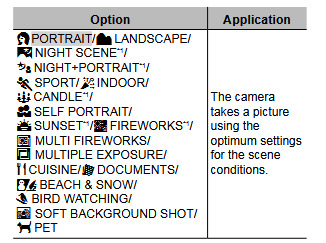
As someone whose special interest is birds, I love this setting and use it a LOT, but I've never been able to find another camera with a setting like it, and at some point I told myself I didn't want to replace the camera until I could find one with a similar setting.
The reason I ask is because I've been following for a while, and I've come to respect your opinions on photography.
I tried researching your camera and figuring out what exactly the bird watching mode does and even the official manual did not say. If I were to guess, it just sets the camera up with certain parameters that are usually ideal for photographing birds, but I don't think it does anything special that other cameras can't do. You would just have to set a different camera up to those parameters rather than the camera doing it for you.
If I were to guess, it probably enables a certain autofocus mode for small subjects and limits how slow the shutter speed can go so you don't get motion blur when very zoomed in.
However, I know exactly which features are important to get good bird photos, so as long as the camera has the following features, you don't really need a dedicated bird mode. Though if a camera has a "pet mode" it would probably work similarly to the bird mode you are used to.
Most important bird photography features...
Good autofocus
Good zoom range
Image stabilization (Either optical or sensor, not digital)
Autofocus has come a long way in the last few years. It's difficult to assess the autofocus from specifications alone, so you will probably need to rely on reviews to know if the camera locks in on subjects well. Some cameras have pet and wildlife autofocus features that can be very helpful in tracking smaller subjects like birds. So I would look out for any camera that has a pet autofocus mode or a review that says it locks onto smaller subjects well—even if they don't mention birds. If it can lock onto a chihuahua, it can usually do so with a bird too.
Birds and wildlife in general tend to get spooked easily and it is often difficult to get close without them running or flying away. So having a longer zoom range can really help you keep your distance and not startle your subject. I would say the minimum focal length for getting good bird shots is around 300mm (on a full frame camera). Some cameras only quantify their zoom by magnification (20x, 30x, 40x, etc.) and don't really say what that is in relation to. So focal length is a better metric to assess how zoomy a lens is. 10-35mm would be wide angle. 50mm is about like our eyes. 100mm is slightly telephoto. And 300mm and above would be very telephoto.
You may need to google the focal range equivalent to a full frame 35mm camera. So you would search "[camera model] 35mm equivalent focal range" to figure that out. And as long as it goes past 300mm, it might be a good candidate for birding.
When you have a camera that zooms in that far, any movement will be exaggerated—especially if you have naturally shaky hands. Not only can that introduce motion blur into your images, but it can make it very difficult to track your subject. Looking through the viewfinder will result in a wiggly mess and you won't know what you are pointing the camera at.
Image stabilization helps negate that exaggerated movement.
There are 3 kinds of stabilization. First is optical, which is built into the lens with a floating glass element. Then there is sensor stabilization (often called IBIS for "in-body image stabilization") which allows the sensor to shift and move to counteract any motion introduced by your hands. And the last form is digital stabilization which is done using the camera's software.
The first two are physical solutions that can adjust on the fly much like a chicken's head.

The digital solution is mostly just fancy image cropping. It zooms in a tiny bit on your image and then aligns a continuous crop to give the appearance of a stable image.
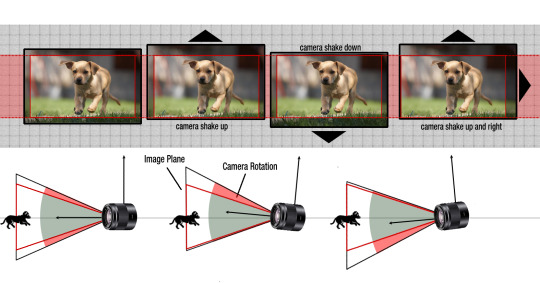
The lens and the sensor are still a jiggling mess, but this constant cropping allows you to see the illusion of a stable image in your viewfinder and in the videos you take. And while this is very helpful for tracking subjects and capturing video footage, it will not help you negate motion blur—which is why the other two methods are preferred for still photography.
Bigger cameras can often forego stabilization because the zoom lenses are bigger and heavier and don't shake as much and they let in a lot more light so you can raise your shutter speed to freeze motion. It's still nice to have, and if you have IBIS and optical stabilization combined on a big camera you can almost take pictures in the dark without camera shake, but all of those conveniences can get costly.
The camera you have now is called a "bridge" camera or a "superzoom". These are (relatively) inexpensive cameras that use a smaller smartphone-style sensor but with a more classic camera body surrounding it and a non-changeable lens. Small sensors have one big advantage where if you put a zoom lens in front of them, they can see from Alaska to Russia.
For instance, your camera has an 840mm equivalent lens. That is near telescopic.
For reference, this is what an 800mm lens looks like for a full frame professional camera.

It weighs 10 pounds and costs about $13,000.
Granted the image quality of that lens is in another universe compared to your superzoom, but if you are mostly interested in documenting the birds you are encountering, a superzoom is a neat tool to have. It's like digital binoculars.
So I guess the question is, do you just want to document your bird adventures or do you want to delve into artistic bird photography?
You can upgrade to a nicer superzoom and get some improved clarity and ease-of-use features, which is totally valid. You could even get a "premium" superzoom that can do artistic bird photography in ideal lighting conditions.
Or if you go with a more professional interchangeable lens camera system (ILC), you can achieve some stunning artistic photos like these...



Freezing a bird midflight while catching a fish is just not really feasible with a basic superzoom.
Let's talk about the advantages and disadvantages of a superzoom bridge camera as compared to a more professional ILC setup.
Superzoom Pros
No learning curve. These cameras are designed for novice photographers and have very good automatic functions. You can pretty much pull them out of the box and start taking pictures without knowing the fundamentals of photography.
Incredible zoominess. You can get amazing zoom power for a fraction of the price.
Budget friendly. The top of the line superzoom camera is still only about $1500 as compared to the top of the line mirrorless ILC (for wildlife) which is $6500 *without* a lens. And the lower to mid range superzooms are even more affordable, especially if you consider used options.
Superzoom Cons
Noisy images in low light. These cameras are mostly suited for bright sunny days. The small sensors and cheaper lenses do not capture very much light. In more challenging lighting situations you will tend to get very noisy images due to using a high ISO to compensate.
Inconsistent image quality. Under the best of circumstances, you can get some really beautiful photographs. But when you push the camera to its extremes, the image quality can start to deteriorate. Low light causes noise. The more you zoom in, the softer your images will get. Low megapixels limit your options to crop in on far away subjects—which is often an issue with wildlife.
Deep depth of field. A lot of bird photographers like using shallow depth of field to blur the background so the bird really stands out in the photo. Small sensors can have a very hard time blurring the background unless the subject is quite far away and you are zoomed all the way in. But when you are all the way zoomed in, the image can get soft and lack detail. So you trade image quality for a blurry background.
Lack of professional features and accessories. There are many advanced features that can make bird photography much easier. Some cameras have advanced motion tracking that can allow you to capture birds in flight. The latest generation can even track a tiny bird's eye. There are also accessories that are only made for ILCs. Like motion activated shutter triggers that will take a picture of a bird automatically if you set up a camera near a feeder. There are flashes that work at very long distances. You can get camouflage skins for your lenses so the birds can't see you. Stuff like that.
ILC Pros
Lower image noise. With a bigger sensor and better lenses you can shoot with a very low ISO in good light and get incredibly clean noise-less images.
Better high ISO performance. If you are in low light, you can increase the ISO and still get a very good image. The noise on an ILC is much less distracting and easier to deal with—especially with advanced noise reduction software.
Background blur is easy. Due to the much larger sensor and telephoto lenses, almost every telephoto image will have beautiful blurry backgrounds no matter how small the aperture is.
Sharper, faster lenses. The lenses are much sharper and let in a lot more light. The quality of the image does not decrease as you zoom in. And the sharp optics allow a lot of leeway for cropping. So even if a bird was super far away, you can crop the image after the fact and it will still be quite detailed.
More megapixels. A lot of bird photography needs to be cropped in due to subject distance. Having more megapixels allows for more cropping. (I know I keep talking about cropping, but it really is a huge aspect of most bird photography.)
Advanced autofocus. This is the big game changer, especially on the new mirrorless cameras. The latest Canon and Sony cameras have eye detect autofocus for animals. You can literally lock onto a bird's eye while it is in flight and get perfect focus. It's bonkers.
ILC Cons
Steep learning curve. A lot of people think they'll get a big ILC and immediately get better pictures than their smartphone. They are often disappointed when that isn't the case. You really need to learn the fundamentals of photography to get good photos out of an ILC (free course here). They do have automatic modes, but without learning about aperture, shutter speed, and ISO (the exposure triangle) and how to balance them and when to prioritize what, you might end up with *worse* photos than a smartphone.
Wildlife photography can get very expensive. Big lenses with a lot of zoom are some of the priciest available. There are some budget options, but you will have to sacrifice quite a bit of zoom and light-gathering capabilities. The quality of the photos is usually worth it, but you may have to learn how to get closer to birds to photograph them.
Heavy as heck. Superzooms are very light and portable. A wildlife ILC configuration is very unwieldy. The camera is heavier. The lens is long and heavy. Carrying all of that gear into the wilderness can be quite a hassle.
Some camera suggestions...
Superzoom Options
If I'm being honest, in the sub $300 range, I don't think you'll be able to drastically improve over what you already have. All of the cameras in this range are quite similar and while a few might have some features that are helpful, the image quality is going to be roughly the same.
You are probably going to need to spend at least $400-700 to get a meaningful upgrade from what you have.
The top-of-the-line superzoom would be the Sony RX10 Mark IV at $1100 used. You can get the previous model, the Mark III, for about $900 used. It's a wonderful camera and the image quality and features rival or even surpass some ILC options. If you don't have the time to learn an ILC system but want the best possible quality, this might be an option. But an ILC will still give you better results if you are willing to put in the time.
For more mid-tier superzooms, you might look into the Panasonic Lumix models. They use slightly larger sensors than most superzooms and are known for their lens optical quality along with their stabilization.
The FZ1000 is getting very old, but it is still a powerful camera at a good price. The only downside is the focusing system isn't as advanced as newer cameras. But it will be better than what you have and you can find one used for around $400.
The newer FZ1000 II or the FZ2500 would be great options that have more modern autofocus and a lot more bells and whistles. They are fairly similar and can both be found for around $650 used. They do great video as well.
These are not the only options, but they are ones I know of and models I have heard positive things about. If you want to see what else is out there I would google "bridge superzoom cameras" and then maybe add your price range as well. Read reviews and watch YouTube videos to get a sense of the cameras you are interested in. As long as the camera has decent autofocus, I don't think you need a specific bird feature—so I wouldn't limit yourself in that regard.
ILC Options
When trying to come up with a good bird photography setup for interchangeable lens cameras, there is basically an easy, medium, and hard mode depending on how much you spend.
As I mentioned, the top-of-the-line mirrorless cameras have autofocus tracking that can lock onto a bird's eye while in flight. They have both IBIS and lenses with optical stabilization. They have burst modes that let you take 30 photos per second. They have 50 megapixel sensors that allow you to crop to your heart's content and still have megapixels left over.
It's quite dreamy if you have the money.
But I'm guessing if you are coming from an Olympus bridge camera that is probably a bit more of an upgrade than you were thinking.
So if easy mode is not viable, let's talk about medium and hard mode.
If you still want the bird detecting autofocus, in body image stabilization, and a pretty zoomy lens, Canon has some newer mirrorless cameras that would take amazing artistic bird shots. It's still spendy, but not $9000 spendy.
The Canon R7 is a great APS-C mirrorless camera with IBIS that can be found used for about $1300. It has 32 megapixels and due to having a slightly smaller sensor, you even get some bonus zoom out of all your lenses at about 1.6x. It's still a much larger sensor than a superzoom, just not quite the size of the Alpha 1.
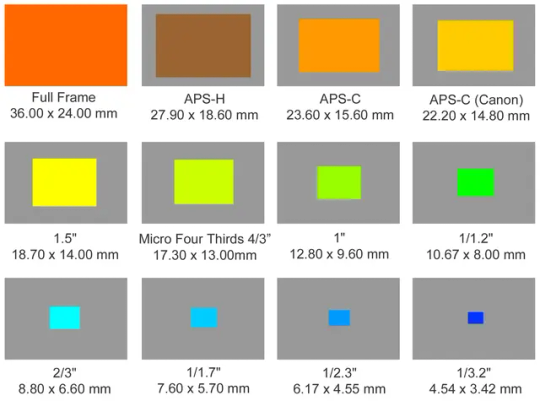
Alpha 1 is Full Frame. R7 is APS-C. And Superzooms don't get any bigger than the 1" sensor.
Pair the R7 with the RF 100-400mm lens ($600 used) with optical stabilization, and you would have a stellar bird photography setup for about $1900. (It would be a 160-640mm equivalent lens on the R7 due to the 1.6x crop factor.)
Which is probably still way more than you want to spend.
So we have the hard mode option.
No bird eye autofocus. No stabilization. You have to learn the fundamentals and practice in order to get good shots. However, wildlife photographers have been getting AMAZING photos with the gear I'm about to suggest. In fact, all of these photos were captured with the hard mode ILC combo.




The Canon 7D Mark II has been a beloved camera body for wildlife photography for many years. Many pros still use it to great effect to this day. It doesn't have bird autofocus, but it still has one of the best DSLR autofocus systems that was ever developed. It can even track moving subjects, it just doesn't know it is tracking a bird so it is more prone to error on occasion. It can be found used for $500-600.
The Canon 400mm F/5.6 telephoto lens is one of the most affordable lenses Canon ever made for wildlife. It is an old lens, but it is sharp and takes beautiful images. No stabilization, but it is big and heavy so that isn't a huge deal. You can also carry a monopod rest it on. And on the 7D II, it is the equivalent of a 640mm lens. It costs around $650 used, which is very inexpensive compared to other telephoto lenses.
So you are looking at around $1200 for the combo. But the photos you can achieve with these two items will blow pretty much any superzoom out of the water.
To sum up...
ILC photography is always going to have a steep learning curve and expensive barrier for entry, but you can achieve some truly stunning results.
Superzooms are getting better and some of the newer ones can still take excellent pictures of birds under the right circumstances. They are lightweight and hassle free and allow you to get incredible zooms for a low cost.
If you mostly take photos of stationary birds outside on bright sunny days, you will be fairly happy with a superzoom.
If you want to take photos during darker times like sunrise or sunset or in a dense forest... or if you want to take photos of birds mid-flight, you will probably have to get an ILC.
I hope that was helpful. I know I overdo these answers, but I try to help as many people as I can by giving a broad overview of the topic and the myriad ways to go about things.
46 notes
·
View notes
Text
youtube
This is a good example of a type of innovation going on in classical music: chamber music (music using small “orchestral” forces, basically) using live interactive electronics (often built by the composer using software like csound, max/msp, and puredata) that both mutate and accompany the live acoustic instrument performer’s parts. Electronics are sometimes triggered by these performers in various ways or the machinery is designated its own electronics performer.
Program Note: Rough Gem was inspired by the performance mode of the Japanese shakuhachi that regards the role of the player as an imperative component along with the music. Expressions through breathing are exploited by various extended techniques, becoming the central compositional emphasis that leads the sound to behave as natural as it is physically made by circulations of air through the instrument. Many of the sonic instances were also realized and modified electronically to create multiple soundscapes adding more colors to the solo part.
5 notes
·
View notes
Text
U.S. National Security Advisor Mike Waltz, who started the now-infamous group chat coordinating a U.S. attack against the Yemen-based Houthis on March 15, is seemingly now suggesting that the secure messaging service Signal has security vulnerabilities.
“I didn’t see this loser in the group,” Waltz told Fox News about Atlantic editor in chief Jeffrey Goldberg, whom Waltz invited to the chat. “Whether he did it deliberately or it happened in some other technical mean, is something we’re trying to figure out.”
Waltz’s implication that Goldberg may have hacked his way in was followed by a report from CBS News that the U.S. National Security Agency (NSA) had sent out a bulletin to its employees last month warning them about a security “vulnerability” identified in Signal.
The truth, however, is much more interesting. If Signal has vulnerabilities, then China, Russia, and other U.S. adversaries suddenly have a new incentive to discover them. At the same time, the NSA urgently needs to find and fix any vulnerabilities quickly as it can—and similarly, ensure that commercial smartphones are free of backdoors—access points that allow people other than a smartphone’s user to bypass the usual security authentication methods to access the device’s contents.
That is essential for anyone who wants to keep their communications private, which should be all of us.
It’s common knowledge that the NSA’s mission is breaking into and eavesdropping on other countries’ networks. (During President George W. Bush’s administration, the NSA conducted warrantless taps into domestic communications as well—surveillance that several district courts ruled to be illegal before those decisions were later overturned by appeals courts. To this day, many legal experts maintain that the program violated federal privacy protections.) But the organization has a secondary, complementary responsibility: to protect U.S. communications from others who want to spy on them. That is to say: While one part of the NSA is listening into foreign communications, another part is stopping foreigners from doing the same to Americans.
Those missions never contradicted during the Cold War, when allied and enemy communications were wholly separate. Today, though, everyone uses the same computers, the same software, and the same networks. That creates a tension.
When the NSA discovers a technological vulnerability in a service such as Signal (or buys one on the thriving clandestine vulnerability market), does it exploit it in secret, or reveal it so that it can be fixed? Since at least 2014, a U.S. government interagency “equities” process has been used to decide whether it is in the national interest to take advantage of a particular security flaw, or to fix it. The trade-offs are often complicated and hard.
Waltz—along with Vice President J.D. Vance, Defense Secretary Pete Hegseth, and the other officials in the Signal group—have just made the trade-offs much tougher to resolve. Signal is both widely available and widely used. Smaller governments that can’t afford their own military-grade encryption use it. Journalists, human rights workers, persecuted minorities, dissidents, corporate executives, and criminals around the world use it. Many of these populations are of great interest to the NSA.
At the same time, as we have now discovered, the app is being used for operational U.S. military traffic. So, what does the NSA do if it finds a security flaw in Signal?
Previously, it might have preferred to keep the flaw quiet and use it to listen to adversaries. Now, if the agency does that, it risks someone else finding the same vulnerability and using it against the U.S. government. And if it was later disclosed that the NSA could have fixed the problem and didn’t, then the results might be catastrophic for the agency.
Smartphones present a similar trade-off. The biggest risk of eavesdropping on a Signal conversation comes from the individual phones that the app is running on. While it’s largely unclear whether the U.S. officials involved had downloaded the app onto personal or government-issued phones—although Witkoff suggested on X that the program was on his “personal devices”—smartphones are consumer devices, not at all suitable for classified U.S. government conversations. An entire industry of spyware companies sells capabilities to remotely hack smartphones for any country willing to pay. More capable countries have more sophisticated operations. Just last year, attacks that were later attributed to China attempted to access both President Donald Trump and Vance’s smartphones. Previously, the FBI—as well as law enforcement agencies in other countries—have pressured both Apple and Google to add “backdoors” in their phones to more easily facilitate court-authorized eavesdropping.
These backdoors would create, of course, another vulnerability to be exploited. A separate attack from China last year accessed a similar capability built into U.S. telecommunications networks.
The vulnerabilities equities have swung against weakened smartphone security and toward protecting the devices that senior government officials now use to discuss military secrets. That also means that they have swung against the U.S. government hoarding Signal vulnerabilities—and toward full disclosure.
This is plausibly good news for Americans who want to talk among themselves without having anyone, government or otherwise, listen in. We don’t know what pressure the Trump administration is using to make intelligence services fall into line, but it isn’t crazy to worry that the NSA might again start monitoring domestic communications.
Because of the Signal chat leak, it’s less likely that they’ll use vulnerabilities in Signal to do that. Equally, bad actors such as drug cartels may also feel safer using Signal. Their security against the U.S. government lies in the fact that the U.S. government shares their vulnerabilities. No one wants their secrets exposed.
I have long advocated for a “defense dominant” cybersecurity strategy. As long as smartphones are in the pocket of every government official, police officer, judge, CEO, and nuclear power plant operator—and now that they are being used for what the White House now calls calls “sensitive,” if not outright classified conversations among cabinet members—we need them to be as secure as possible. And that means no government-mandated backdoors.
We may find out more about how officials—including the vice president of the United States—came to be using Signal on what seem to be consumer-grade smartphones, in a apparent breach of the laws on government records. It’s unlikely that they really thought through the consequences of their actions.
Nonetheless, those consequences are real. Other governments, possibly including U.S. allies, will now have much more incentive to break Signal’s security than they did in the past, and more incentive to hack U.S. government smartphones than they did before March 24.
For just the same reason, the U.S. government has urgent incentives to protect them.
7 notes
·
View notes