#aircraft transponder tracking
Explore tagged Tumblr posts
Text

F-14 flying alongside SR-71 during refueling (Image via Haburats SR-71 on X/Twitter)
The F-15 wasn’t the only top-tier fighter in the U.S. arsenal at the time, and the truth is, the Navy’s famed F-14 Tomcat of Top Gun fame was actually better equipped for these sorts of high-speed intercepts.
While the Eagle’s AN/APG-63 was a highly capable radar, it fell well short of the massive power output and multi-targeting capability of the Tomcat’s AN/AWG-9 radar and fire control system. With around double the detection range of the Eagle’s radar and the ability to track 24 targets simultaneously, the F-14 could guide six separate missiles into six separate targets at the same time. Despite being based on a fairly dated design, there wouldn’t be a more powerful radar installed in a fighter until the F-22 Raptor entered service.
But perhaps even more important was the Tomcat’s armament, because the F-14 came equipped with the now-legendary AIM-54 Phoenix missile – the longest-ranged air-to-air missile on the planet at the time that flew with a combination of a semi-active seeker to take cues from the F-14’s radar and an active radar-homing seeker for terminal guidance. In other words, once the Phoenix was close enough to a target, it could rely on its own onboard radar to close in, rather than needing the launching pilot to maintain a lock until impact.
Training intercepts that pitted the F-14 against the SR-71 were known by insiders as Tomcat Chase sorties, and were usually carried out over the Pacific, rather than the Nevada desert, thanks to the presence of F-14-hauling aircraft carriers at sea. As with the F-15, Habu drivers did their best to give the F-14 a fighting chance, flying along straight, predetermined flight paths at lower altitudes and speeds than they would normally do. They also maintained open radio communications, allowing the SR-71 pilots to guide the F-14s into their relative positions so they’d have a chance to fire their notional AIM-54s.
The Blackbird flew with its transponder on, and again, without its defensive electronic countermeasures engaged. But, again, even in these very favorable conditions, Tomcats struggled to find their mark.
“The 14s could find us but they couldn’t do anything until we modified and gave them times, route of flight, speed, and altitude beforehand so they could have a pre-planned setup,” Pilot Dave Peters recalled. “The 15s didn’t do that well for quite some time.” Tough as it was to spot the Blackbird zooming past, once the Tomcats did, the Phoenix missile was capable enough to pose some real problems for the Blackbird. With a top speed in excess of Mach 4 (except when put into a ballistic flight path into the ground, where it could exceed Mach 5), the AIM-54 had the speed and the range required to close with an airborne Habu, and thanks to its onboard radar seeker, it would be tougher to shake than the Eagle’s Sparrows.
However, there remains some debate about whether or not even the Phoenix could have found its mark in the Blackbird’s high-altitude domain.
“Another factor in our favor was the small guidance fins on their missiles,” Graham wrote. “They are optimized in size for guiding a missile to its target in the thicker air from the ground up and around forty thousand feet. At eighty thousand feet the air is so thin that full deflection of the missile’s guidance fins can barely turn it.”
Sandbox News.
@Habubrats71 via X
25 notes
·
View notes
Text
Assad releases his first statement since fleeing Syria
The departure of ousted Syrian President Bashar al-Assad from the country was unplanned, according to a statement released Monday by the Syrian presidency’s Telegram account and purportedly coming from Assad.
The statement from the Syrian Presidency account on Telegram said:
“My departure from Syria was neither planned nor did it occur during the final hours of the battles, as some have claimed. On the contrary, I remained in Damascus, carrying out my duties until the early hours of Sunday December 8th 2024.”
When Assad arrived at the Latakia base, he said “it was clear that our forces had been completely withdrawn from all fighting positions and that the last positions of the army had fallen and the situation continued to deteriorate.” The former Syrian president stressed that Moscow then offered to organise an immediate evacuation to Russia. He also added:
This happened the day after the fall of Damascus, after the fall of the last military positions and the consequent paralysis of all remaining state institutions.
The former president added that during these events he “never once thought of resigning or seeking asylum.”
Assad emphasised in the statement that during the rebel offensive,”‘terrorism spread throughout Syria and eventually reached Damascus on the evening of Saturday the 7th.”
This was followed by “questions about the fate and whereabouts of the president,” which came “amid a flood of disinformation and stories that are far from the truth.”
The president’s statement should have been published even earlier, he added. But “the circumstances prevailing at the time, including a complete shutdown of communications for security reasons, led to a delay in the publication of this statement. Moscow and the date of December 16 are listed there as the place of publication of the statement.
The statement also said:
“When the state falls into the hands of terrorism and the ability to make a meaningful contribution is lost, any position becomes void of purpose, rendering its occupation meaningless.”
Bashar al-Assad’s escape from the country was organised with the help of Russian intelligence officers, Bloomberg quoted sources as saying. They took him out via a Russian airbase in Syria.
During Assad’s departure, the transponder of the aircraft was switched off so that it would not be tracked. At the same time, before leaving, Russia convinced the former Syrian president that he would lose the fight against armed rebels, the agency claimed.
Syria’s central bank under Bashar al-Assad ‘s presidency sent several planes to Moscow with millions of dollars and euros in cash, Financial Times previously reported, citing confidential documents.
Assad kept his plans to leave the country secret and before his escape allegedly assured officers that Russia would help, Reuters reported earlier, citing sources.
“Hours before his escape to Moscow, Assad assured at a meeting with about 30 army and security chiefs at the defence ministry on Saturday that Russian military support was on the way and urged ground forces to hold on,” the agency quoted the interlocutors as saying.
The authors of the materials also stress that Assad hid his plans to flee for so long that he did not even inform his younger brother Maher Assad, the commander of the elite 4th Armoured Division.
Read more HERE

#world news#news#world politics#middle east#syria#syria news#syria civil war#syria crisis#syria conflict#syria coup#assad regime#aleppo#damascus#syrian civil war#syrian rebels#bashar al assad#assad
1 note
·
View note
Text
WIP Wednesday: Custos Custodium
In which the heist pays off, and big feelings are had by all. Come for the fancy VTOL, stay for the angst.
Malik set down in an empty parking lot at a scenic overlook to investigate her prize, her enthusiasm only growing as she poked and prodded at its systems. To Jensen’s disgust, the first thing she did was get Pritchard on the line to make sure the computer system couldn’t be remotely hijacked. This entailed physically disabling some of the transmitters, including the one that—according to the logs—had alerted the DeBeers nephew personally when the hatch had opened. Others required only software changes. Soon, Pritchard announced himself confident that no one could get into the craft’s systems from outside, not even him, although he recommended she bring it by for an in-person look as well.
Reassured the VTOL wouldn’t turn on her in midair, Malik dove back into the interface, issuing a running commentary that Jensen tried sporadically to follow. All the flight-essential capabilities mapped to the buttons on the sticks or the console, but the other functions ran through the touch-sensitive wraparound cockpit screen. And there were a lot of functions: HUD readouts, climate controls, radar, comms, and more that he lost track of.
Eventually, she turned to disguise. The craft spoofed a transponder code with ease, but a physical registration number seemed more difficult until Malik sat bolt upright and said, “Hey. Does this interface look like what I think it looks like?”
He roused from his exhausted, brooding slump in the copilot seat and inspected it. “Smart paint? I bet so.”
She fiddled with it for a minute, then dragged him outside to see the results. It gave him a chance for a better look at the chunk of machinery for which he’d almost gotten himself killed. Bigger than the Bumblebee, yet smaller than Chikane’s and the other Task Force’s aircraft, it bore an even sharper and more aggressive profile. The nose hooked down slightly, giving the impression of a raptor’s beak, and the narrow fuselage pinched in and upwards at the rear before fanning out into a pair of absurdly wide tail surfaces angled gently down to the sides. A sleek stub of rudder jutted up between them.
The root of the wings ran most of the length of the fuselage, from which point they tapered gradually before sweeping back to sharp points. A pair of engines, each in its own nacelle, sat at the crook of each wing. The craft looked like it wanted to leap from its perch and stoop upon some unsuspecting prey. As indeed it just had, he supposed. He couldn’t see the cannon, but of course it would retract, for discretion and aerodynamics both.
Chromatically, the aircraft had become unrecognizable, white above and olive below all along the fuselage. The phony registration number appeared in black on the white tailplanes, in white on the olive sides. He walked around to the left flank, following Malik slowly on his wobbly right leg. Gunmetal streaks showed where bullets had smeared across the smart paint, but only a close look betrayed them as anything more suspicious than grime.
Malik stood hipshot, hand on her waist, and jerked a thumb at the transformed VTOL. “This thing is sweet! Man, it’s a vigilante agent’s dream come true. We are gonna get in so much trouble—and get out of it again, more importantly. Speaking of which, how are you holding up?”
“Bled on your upholstery, I’m afraid.”
“DeBeers sprang for the good stuff. It looks stain-resistant—shouldn’t be a problem. You got pretty chewed up, though. Let me see your back.”
“It’s fine.”
“Bullshit.” She grabbed his shoulder and craned her neck to look behind him. “Omigod your neck! What happened? Looks like a… a ring?”
“I bet. After I broke the gun, that exo trooper used the barrel like a cattle prod.”
“Jeez. And your whole back. Ouch. Hmm—uh, yeah, that looks nasty. It’s stopped bleeding, but I bet you could use some protein, huh? Liquids, too. Maybe a beef smoothie.”
He gagged, only partly in jest.
1 note
·
View note
Text

ADS-B Receiver from Digilogic Systems
Automatic Dependant Surveillance-Broadcast (ADS-B) Receiver is a JSS 55555-approved ruggedized product developed by Digilogic Systems, that decodes signals from ADS-B aircraft transponders to determine various information like Latitude, Longitude, Altitude, etc, adhering to ICAO standards.
Leveraging NI Hardware and Digilogic’s expertise in ruggedization and algorithm implementation, this ADS-B receiver kit stands out as a unique product. The kit includes an antenna, RF frontend, and an ADS-B receiver equipped with a licensed application.
Digilogic's ADS-B Receiver offers dual redundant receivers, real-time flight data, built-in GPS connectivity, remote receiver configuration, and easy LAN connectivity for live tracking, making it a standalone unit for network data retrieval.
For any queries (or) to request a quote, please contact us. Phone: Hyderabad: (+91) 40 4547 4601 Bengaluru: (+91) 80 4975 6034 Website: https://www.digilogicsystems.com/ Email: [email protected]
Stay connected with us on our social media channels for the latest updates! Facebook: https://www.facebook.com/digilogicsystems/ LinkedIn: https://www.linkedin.com/company/digilogicsystems/ YouTube: https://www.youtube.com/@digilogicsystems/ Instagram: https://www.instagram.com/digilogic_systems/ Twitter: https://twitter.com/DigilogicSystem
#adsbreceiver#ADSB#Aviation#aerospace#aviationproducts#avionics#digilogicsystems#testingequipment#testmeasurement#testautomation#digilogic#innovativesolutions#GPS#defence#makeinindia
0 notes
Text
what is remote id in vpn configuration
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is remote id in vpn configuration
Remote ID Definition
Remote ID, or Remote Identification, refers to a crucial aspect of modern technological systems, particularly in the realm of drones and unmanned aerial vehicles (UAVs). In essence, Remote ID serves as a digital license plate for drones, enabling authorities and other parties to identify and track these devices while they are in flight.
The primary purpose of Remote ID is to enhance safety and security in the skies. By providing real-time information about a drone's location, its operator, and other pertinent details, Remote ID enables authorities to quickly respond to any potential incidents or violations of airspace regulations. This capability is especially important as the number of drones in operation continues to rise, leading to concerns about airspace congestion and the potential for unauthorized or malicious drone activities.
Remote ID technology typically involves the use of transponders or broadcast modules installed on drones, which continuously transmit identification and location data to nearby receivers or to centralized monitoring systems. This information can then be accessed by authorized parties, such as law enforcement agencies, air traffic controllers, or other drone operators sharing the same airspace.
In addition to its safety and security benefits, Remote ID also plays a crucial role in enabling the integration of drones into the national airspace system. Regulatory bodies, such as the Federal Aviation Administration (FAA) in the United States, have proposed rules mandating Remote ID for all drones operating in controlled airspace, as a means of ensuring accountability and facilitating the safe coexistence of manned and unmanned aircraft.
Overall, Remote ID represents a fundamental component of drone regulation and airspace management, helping to unlock the full potential of drones while mitigating associated risks and concerns. By providing transparency and accountability in drone operations, Remote ID paves the way for the widespread adoption and responsible use of this transformative technology.
VPN Configuration Process
Virtual Private Network (VPN) configuration process ensures a secure and encrypted connection for users to browse the internet privately. Setting up a VPN involves a few key steps to ensure smooth operation and maximum security.
Firstly, choose a reliable VPN service provider that offers strong encryption protocols and a no-logs policy to protect your data and privacy. Sign up for a subscription plan that suits your needs and download the VPN client software on your device.
Once installed, launch the VPN application and log in using your credentials provided by the service provider. From the settings menu, you can select your desired server location to mask your real IP address and enhance your online anonymity. Some VPNs also offer additional features like kill switch and split tunneling for added security and flexibility.
After selecting the server, you can connect to the VPN by simply clicking the connect button. Wait for the connection to establish, and you will notice a VPN icon in the taskbar indicating that you are now securely connected.
It's important to periodically update your VPN client software to ensure you have the latest security patches and bug fixes. Additionally, regularly checking your VPN connection for any leaks using online tools can help verify the effectiveness of your configuration.
By following these steps and staying informed about the latest VPN trends, you can enjoy a secure and private internet browsing experience with peace of mind.
Remote ID Importance
Title: Understanding the Significance of Remote ID in Modern Times
In the rapidly evolving landscape of unmanned aerial vehicles (UAVs), commonly known as drones, the implementation of Remote ID (RID) stands as a pivotal advancement. Remote ID refers to a system that enables identifying and tracking drones while they are in flight. This technology holds paramount importance in various sectors, including aviation, public safety, and privacy regulation.
One of the primary reasons for the growing emphasis on Remote ID is its role in enhancing airspace safety. With the proliferation of drones for commercial, recreational, and governmental purposes, airspace congestion has become a significant concern. Remote ID enables authorities to monitor drone activity in real-time, thus reducing the risk of collisions and ensuring the safe integration of drones into airspace shared with manned aircraft.
Moreover, Remote ID serves as a crucial tool for law enforcement agencies and emergency responders. By providing instant access to information about drone operators and their flight paths, RID facilitates rapid response to incidents such as unauthorized drone flights near airports, critical infrastructure, or disaster zones. This capability enhances public safety and enables timely intervention to mitigate potential risks.
Additionally, Remote ID plays a vital role in addressing privacy concerns associated with drone operations. By requiring drones to broadcast identification and location information, RID promotes transparency and accountability among operators. This transparency helps alleviate fears regarding unauthorized surveillance or intrusions into private property, fostering greater public acceptance of drone technology.
Furthermore, the implementation of Remote ID regulations is essential for the continued growth and innovation of the drone industry. Clear and standardized RID requirements provide clarity for manufacturers, operators, and policymakers, thereby fostering a conducive environment for investment and development in drone-related technologies.
In conclusion, Remote ID is not merely a technical requirement but a foundational element in shaping the future of drone operations. Its multifaceted benefits extend beyond safety and security to encompass privacy protection and industry growth. As drones become increasingly integrated into our daily lives, the significance of Remote ID cannot be overstated in ensuring responsible and sustainable UAV operations.
VPN Security Measures
VPN Security Measures: Safeguarding Your Online Privacy
In an age where online privacy is increasingly under threat, virtual private networks (VPNs) have emerged as essential tools for safeguarding sensitive information and maintaining anonymity on the internet. However, not all VPNs are created equal, and it's crucial to understand the security measures that reputable providers employ to ensure your data remains protected.
Encryption stands as the cornerstone of VPN security. Leading VPN services utilize robust encryption protocols such as AES-256, which encrypts data as it travels between your device and the VPN server. This encryption renders intercepted data indecipherable to unauthorized parties, thwarting potential eavesdroppers and hackers.
Furthermore, VPNs employ secure tunneling protocols to establish a protected pathway for data transmission. Protocols like OpenVPN, IPSec, and WireGuard create encrypted tunnels that shield your online activities from prying eyes, even on unsecured networks such as public Wi-Fi hotspots.
Another critical aspect of VPN security is a strict no-logs policy. Reputable VPN providers refrain from logging user activity, ensuring that no identifiable information is stored. This commitment to privacy means that even if compelled by authorities to disclose information, VPN companies have nothing to provide, safeguarding user anonymity.
In addition to these core security features, advanced VPNs offer features like kill switches and split tunneling. Kill switches automatically disconnect your device from the internet if the VPN connection drops, preventing data leaks. Split tunneling allows users to route only specific traffic through the VPN while accessing local resources directly, enhancing efficiency without compromising security.
Ultimately, while VPNs provide invaluable protection against online threats, it's essential to choose a trusted provider that prioritizes security and privacy. By understanding the key security measures employed by VPN services, users can confidently navigate the digital landscape while safeguarding their sensitive information.
Remote ID Implementation
Title: Navigating the Landscape: Remote ID Implementation in Today's Digital Age
In the ever-evolving landscape of technology and aviation, the implementation of Remote ID (Identification) marks a pivotal moment. Remote ID serves as a crucial mechanism for tracking and identifying drones in flight, enabling safer skies and facilitating the integration of unmanned aircraft systems (UAS) into the national airspace.
Remote ID entails equipping drones with technology that broadcasts identification and location information to authorities and other airspace users in real-time. This information includes the drone's serial number, location, altitude, and the location of its control station. Such transparency enhances accountability, mitigates security risks, and promotes responsible drone operation.
The Federal Aviation Administration (FAA) in the United States has been at the forefront of establishing Remote ID regulations to enhance safety and security in the skies. The FAA's Remote ID rule, which came into effect in April 2021, mandates that almost all drones operating in U.S. airspace, including recreational and commercial drones, comply with Remote ID requirements.
Implementation of Remote ID presents both challenges and opportunities for stakeholders in the drone industry. Drone manufacturers must integrate Remote ID technology into their products, ensuring compliance with regulatory standards. Meanwhile, operators need to familiarize themselves with Remote ID requirements and adopt appropriate measures for compliance.
While some may perceive Remote ID as a regulatory burden, its implementation ultimately fosters a safer and more efficient drone ecosystem. By enabling authorities to identify and track drones in real-time, Remote ID enhances airspace security, facilitates law enforcement activities, and promotes responsible drone operation.
As technology continues to advance, Remote ID implementation will likely evolve, ushering in new possibilities for enhanced safety, security, and innovation in the burgeoning field of unmanned aviation. Embracing Remote ID is not just about compliance; it's about shaping a future where drones can coexist harmoniously with manned aircraft, unlocking the full potential of this transformative technology.
0 notes
Text
Good morning TUMBLR - March 11th - 2024
''Mr. Plant has owed me a shoe since July 5, 1971."
Ch. XII.8 - Morocco - 1989 - 1991
AIRPORT TESTING PHASE The airport project entered the decisive phase in October. The time came for the testing of all the aeronautical systems: the tests were carried out by a special ''laboratory plane''. An ATR 42 of ICAO, the body that oversees all civil international aviation activities, was sent to new airport for this pourpose . All the normal interiors of an airplane – seats, overhead bins etc – had been removed and replaced by large computers and data-tracking and recording equipment. I met the two pilots, guys with great experience and unique friendliness. The tests lasted almost two weeks and essentially consisted of flights lasting around 2 hours in the morning and 2 hours in the afternoon (weather permitting) during which the pilots tested and recorded the correct functioning of the radio aids, the ILS (instrument landing system) and the landing strip and so called ''thresholds'' of the runaway. (i.e. whether the runaway coordinates communicated to ICAO were actually correct) PAPI (Precision Approach Pente Indicator the ground instrument that communicates with the aircraft's transponder and indicates to the pilot if he is following the right glide path) was also checked and found precise. The MARKER BEACONS (outer – middle – inner) which indicate to the pilot the precise position of the plane in the air. They were interesting days, especially for me they were a source of daily discoveries. One day the pilot made me sit next to him in the cockpit – at a certain point suddenly, smiling and putting his hands behind his head, he told me: Well, now the most interesting phase: let's see if this old cart is capable of landing while I keep my eyes closed! I looked at him in horror, but I tried to maintain an attitude as if it were an everyday thing for me to be in the cockpit of a turboprop plane, while is landing on autopilot…… We were flying at about 5,000 feet and 10km from the runway threshold - the plane was stalled, all the alarms were blaring, but the pilot was smiling and didn't seem worried at all. The plane began its descent shakily, with continuous attitude corrections. I thought ''but who made me get on this bulls****t today…'' The radio communications with the control tower intensified as we got closer to the runway. The plane descended steadily and I stared partly at the ground and partly at the pilot who continued to keep his hands behind his head, while the steering moved continuously. Now a few hundred meters from the runway, the pilot took the control steering again, giving the engine full throttle and raising the plane again! We returned to the air without touching the asphalt, and the pilot laughed heartily as he told me:
''Nah…that's not right…we would have crashed…too early and too low…now let's take a lap and try again…'' Pfuuuuuu……I breathed a sigh of relief! We made a wide circle, arriving to fly over Taroudant, about 80 km from Agadir. Then a big turn and we headed back West, all the way to the Atlantic. A new turn put us back on the runway axis. The pilot released the controls once again and the plane in automatic flight mode began its descent again. This time everything went perfectly, the landing was soft without jolts, and we touched the asphalt on the intermediate white signal of the runway threshold. I congratulated the pilot, and then got off the plane, happy to be back ''down to earth''.
BROKEN FIBER OPTIC CABLE The tests had all been successful, there was very little left until the of the inauguration day of the New International Agadir Airport. Opening an airport to national and international traffic is a rather complicated matter. Once the date and time of entry into service has been communicated to ICAO, it becomes extremely difficult to backtrack. The entire aeronautical world had been informed that from midnight on 22 December 1991 the old Agadir airport was beeing abandoned, and that all aircraft heading to Agadir had to reprogram their on-board computers for the new destination, entering the new coordinates. But an incredible accident put airport inauguration in doubt until the last hours, with the associated serious embarrassment for the entire air transport system of Morocco Kingdom in case the opening date and time could not be respected. The ''unthinkable event'' had occurred: an excavator engaged in landscaping work along the airport fence had severed the large fiber optic cable that connected the new airport with the entire world!!! And here I must break a spear in favor of M. Amine El Aouri: in the darkest moment for the entire project of the new airport, after an emergency meeting had been called in the offices of the Project Management, he uttered a sentence that calling it ''historical'' is perhaps not enough: ''Sourtout il ne faut pas panique' '' !!! (Above all, let's not panic!)
And then Mr. El Aouri added that it was not the time to search for the culprits, the trial was postponed until after the problem had been resolved. A problem that was currently has no solution. The replacement of the entire cable, from the cabin inside the airport to the first junction cabin - approximately 11 kilometers - was immediately discarded. It must be said that repairing an optical fiber cable through welding is an extremely delicate operation, and the result remains in doubt until the acceptance tests on the continuity of the fibers are carried out. But considering the imminence of the opening date of the airport - there were now 6 days to go - there was no other alternative. The decision was taken unanimously: to immediately contact the Finnish company that possessed the know-how and the special welding machine to carry out the repair. And so it was, once the economic agreement was reached, the technicians with the equipment arrived in Agadir two days later. They were put in a position to work 24 hours a day, and the weldings were completed within 48 hours. Another 6 hours of testing - with the entire Works Management holding their breath, aware that their career, in case of failure, was over - and than the cable was declared suitable for the transmission of data and signals.!!!!
THE INAUGURATION'S NIGHT And the long-awaited opening night arrived! It had been decided by the management of the old airport - namely the Director M. El Zakri - that the entry into service of the new airport should take place at midnight on 22 December. The reason was easy to explain: at that time, and for the next 6 hours, no landing was scheduled, and therefore the staff of the old airport - control tower workers, clerks, security workers, police, customs, firefighters , handlers etc would have had plenty of time to move to the new airport and become familiar with their new service environnment. We - the construction people - suddenly we witenessed the airport coming alive with all that human staff that makes an airport ''in service'': not only the technicians, but even the sales women in the new shops, the duty free, the 'newsstand, the cafeterias came into life in those frantic 6 hours. But an unpleasant surprise awaited us: after having roamed freely throughout the airport areas for months, suddenly the police and security barred our way! The airport that had been ''ours'' with the arrival of these ''invaders'' had become ''theirs''......And we, its builders, had become like any traveler or visitor to any airport - we could access only the common areas, we could not enter either the departures or the arrivals. It was forbidden to go up to the terrace, where a splendid ''khaima'' (tent) of laminated wood had been installed. Having made our concerns to M. El Zakri, in the end we were allowed, in a completely exceptional way, to go up to the terrace to witness the inaugural landing. And so it was that from the panoramic terrace we first saw all the runway lights lighting up, and than someone suddenly shouted ''L'AVION L'AVION!!!'' (THE PLANE!!! THE PLANE!!) Yes it was true, the first plane of the first landing on the new runway of the airport ''Al Massira el Qadra'' (it was decided to call it that in honor of the famous Green March) was landing ! And than a screech was heard in the cool Moroccan morning, the wheels of the Air France Airbus had touched the asphalt of the runway!!! Than the braking and the deafening noise of the turbines sent in reverse, and finally the plane approaching the terminal, with the flags of Morocco and France hoisted on the sides of the cockpit. A long round of applause erupted from the small crowd allowed to witness the landing, and the reception committee approached the plane with bouquets of flowers. The pilots and hostesses got out, kisses and hugs and it was truly a great emotion for everyone to see that everything had worked properly!


After just under half an hour a second plane - from German company CONDOR - landed, but it did not cause the same emotion, the effect of the ''first time'' had already disappeared.
RETURN TO ITALY The sad time to say good by to Agadir was arrived...... But before leaving I had a not easy problem to solve.
My Range Rover had remained in Moroccan territory for more than two years without ever leaving it, and that's was not permitted by local law. In theory, not having completed the documents for the temporary importation of the vehicle, every 90 days I would have had to leave Moroccan territory, even for one day only. After which I could easily return with the car for a new period of 90 days. This maneuver would have cost me time and money because, excluding Mauritania to the South and Algeria to the east from the start, I only had the alternative to reach Ceuta (Spanish territory) to the North. This meant over 1,000+1,000 km of state roads every three months! I had given up on this possibility since the beginning of my stay, postponing the solution til the problemat at the project. My friendship with the airport director, M. El Zakri, made it easier for me. I went to his office one morning, and over a mint tea and a pastry I explained the problem to him. He immediately told me not to worry, he knew the Directors of the Tangier airport who knew the Directors of the port of Tangier!!
Attend, on l'appelle tout de suite....(Wait.....we'll call him immediately) IMr. Al Zakri called M. le Directeur de l'aeroport de Tanger on the phone, and explained to him my ''headache'', describing to him how important my contribution had been in the construction of the new Agadir airport, so that now I deserved to be helped to re-export my car without incurring sanctions that could lead to the seizure of the vehicle. It was sufficient for him, M. le Directeur de l'aeroport de Tanger, to make a phone call to his friend M. le Directeur du port de Tanger, telling him that at such day and time, such and such vehicle, driven by M. L'Ingegneur Conseil de le Nouveau Aeroport d'Agadir would have boarded the ferry to Algeciras: very simple no?? I heartily thanked M. El Zakri, promising to visit him if I were to return to Agadir in the future. The Director was the prototype of this kind of Moroccan who ''makes'' his country work. Very competent, a lot of self-sacrifice, no arrogance, always available to listen to the employees. A truly excellent person!
That very same day, I took the Range Rover for a quick check - oil, water etc - and than upon returning home I began to fill the SUV with all the items accumulated over 2 years of stay. That's, without forgetting the turtle that I had found one day lost in the area of the worksite. I left Agadir at dawn on a splendid day, I chose to take the N8 state road to Marrakesh, a truly spectacular road, given that it crosses the Anti Atlas chain from South East to North West. The route is dotted with small Berber villages, descendants of those Berbers with whom the French occupiers had to come to terms, given their skill and tenacity in the art of war and guerrilla warfare. After a brief stop in the ''Ochre City of Marrakech'' I continued to Casablanca (at the time there was no motorway, but a simple state road). Than, with only stops just to rest a bit, I drove to Tangier. A full night at the old Les Almohad made up for the hours I spent driving. The next morning, as agreed with M. El Zakri, I went to Tangier airport, just outside the city. I asked for M. le Directeur, who received me almost immediately. I was offered some excellent green tea, and than le Directeur, a portly man in his 60s called M. le Directeur du Port de Tanger. Who said that there was no problem, he would immediately inform M. le Directeur de la Douane that early the same day an Italian with a Range Rover would board the ferry to Algeciras and above all ''that there was no need to carry out any type of inspection of the documents and the vehicle''. Heartened, I expressed my heartfelt thanks to M. le Directeur de l'Aeroport de Tanger, and set off for the port of Tangier. Upon boarding the ferry everything went as expected, with the border police and customs officers sneering and making a last futile attempt to get something out of the matter.
CROSSING THE STRAIT AND JOURNEY TO ITALY. I crossed the Strait of Gibraltar for the umpteenth time, the same 13 km wide strait that rapresent for too many an obstacle to a better life. Unfortunately, for too many others, after realizing the dream of arriving in Europe, is only the beginning of new and different nightmares. In winter there were few passengers on ferries, almost all truck drivers who travel between Spain and Morocco and vice versa. Fish, fruit and vegetables are the most exported goods from South to North. Once in Algerciras the disembarkation operations took little time, compared to the hours of waiting during the summer, when tourists and Moroccans returning home to spent summer holidays in their native country. I then took the state road towards the North, I intended to stay as much as possible on the coast because I had a problem with the car's heating system: after 2 years in Morocco, it simply wasn't working, and the temperatures at the beginning of January in Europe were certainly not those of Agadir.
The journey continued without any problems, the turtle was walking around on the floor in front of the passenger seat, every now and then I passed it half a tomato, which it was greedy for. Soon, having passed Almeria and Cartagena, I arrived in Orihuela Costa, the only place in Europe where bananas are grown. I proceeded slowly, admiring the plantations on the side of the highway. So when the traffic light at the intersection turned red, and I pressed the brake pedal, it was a big surprise for me to notice the car didn't slow down! I coundn't do anything but ran through the red light and luckily, given the time - it was just after 6.00 in the morning, no vehicle came from the other side!! I stopped at the first lay-by to try to understand why the brake hadn't worked, and with my great amazement I saw the turtle exactly under the brake pedal!! Distracted by the sight of the banana plants, I hadn't noticed that the turtle had managed to climb onto the Range Rover's gearbox tunnel, was also made easier by the carpet covering on which turtle's nails had an easy grip, and it had slipped right there, where it should never have gone!! So I was forced to put the turtle on the floor of the rear seats, I didn't want to risk an accident at the next intersection. The rest of the journey was quite boring, although the cold got more pungent as I progressin to North. During the crossing of Southern France and along the Ligurian Riviera everything was fine, but the Genoa – Alessandria stretch was covered in snow, and I was forced to cover my legs with a blanket.
I arrived home quite ''frozen'' but very happy.

Orihuela plantation - Spain
1 note
·
View note
Text
Three Lincoln Laboratory inventions named IEEE Milestones
New Post has been published on https://sunalei.org/news/three-lincoln-laboratory-inventions-named-ieee-milestones/
Three Lincoln Laboratory inventions named IEEE Milestones

The Institute of Electrical and Electronics Engineers (IEEE) designated three historical MIT Lincoln Laboratory technologies as IEEE Milestones. The technologies are the Mode S air traffic control (ATC) radar beacon system, 193-nanometer (nm) photolithography, and the semiconductor laser. The latter recognition is shared by Lincoln Laboratory, General Electric, and IBM.
As the world’s largest technical professional organization, the IEEE’s mission is to “advance technology for the benefit of humanity.” The Milestone program commemorates innovations developed at least 25 years ago that have done just that.
All three technologies are integral to everyday life. Anyone who has flown on commercial aircraft has benefited from Mode S, the system that air traffic controllers use to track planes. The integrated circuits that power modern computing and communication devices were manufactured using 193 nm photolithography. Perhaps most ubiquitous of all is the semiconductor laser — a micrometer-sized light-emitting device that has made possible high-speed internet, among many other technologies underpinning today’s information society.
“MIT Lincoln Laboratory has been a leader in fostering innovations that were previously only considered possible in science fiction. The three IEEE Milestones presented are a testament to those accomplishments and a celebration of the diversity of ingenuity and teamwork that created these game-changing technologies,” says Karen Panetta, vice chair of IEEE Boston Section, which presented the awards to Lincoln Laboratory at a ceremony on Feb. 2.
Lincoln Laboratory holds three previous IEEE Milestones for pioneering the use of packet networks for speech communications, for developing the nation’s first air defense system, and for creating the Whirlwind high-speed digital computer in collaboration with MIT campus.
Tracking aircraft globally
The Mode S ATC radar beacon system was developed to address the challenges posed to the existing ATC beacon-radar system used in the late 1960s. Commercial air traffic was growing quickly, causing interference between beacon replies and interrogations from ATC ground radars. This interference threatened to disrupt aircraft surveillance in high-density airspace.
Under Federal Aviation Administration (FAA) sponsorship, Lincoln Laboratory led the technology developments necessary to address this safety issue. The advanced communication architecture of Mode S allowed radars to select a specific aircraft to interrogate. To selectively communicate, the system design included improved aircraft transponders, each assigned a unique address code. Upgrades to radar antennas and signal processing also allowed Mode S to accurately determine airplane position with far fewer air-to-ground messages than required by prior systems. Mode S also provided a datalink capability that enabled other key safety systems, such as the Traffic Alert and Collision Avoidance System.
Today, Mode S is a worldwide industry standard. An estimated 100,000 aircraft are equipped with Mode S transponders, and more than 900 Mode S radars are deployed across the globe. The technology is also the foundation for the FAA’s newest ATC surveillance system, which allows continuous flight tracking independent of ground radars by using aircraft-broadcast position and velocity information.
“This technology touches everybody who flies, every time they fly, for the entire duration of their flight,” says Wesley Olson, a group leader in the laboratory’s Homeland Protection and Air Traffic Control Division, where Mode S was first envisioned. “If it wasn’t for Mode S, we would have a very different air transportation system today, one that would be far less efficient and far less safe.”
Powering the microelectronics industry
The 193 nm projection photolithography technique has enabled the fabrication of every chip in every laptop, smartphone, military system, and data center for the past 20 years.
Photolithography uses light to print tiny patterns onto a silicon chip. The patterns are projected over a silicon wafer, which is coated with a chemical that changes its solubility when exposed to light. The soluble parts are etched out, leaving behind tiny structures that become the transistors and other devices on the chip.
Shorter wavelengths of light allow for printing smaller features, enabling more densely packed chips. By the 1980s, the accepted wisdom in the industry was that 248 nm was the shortest wavelength possible for photolithography.
Despite widespread skepticism and technical obstacles, Lincoln Laboratory pioneered photolithography at the 193 nm wavelength, fabricating the world’s first microelectronic devices using the technique. The first-ever 193 nm projection system was installed at the laboratory in 1993. Soon after, the laboratory opened its doors to industrial partners to guide 193 nm semiconductor manufacturing and pave the way toward its widespread adoption. Today, it is the industry’s mainstream technique and has enabled increasingly powerful integrated circuits.
“Photolithography at 193 nm has enabled the microelectronics industry to continue its path of miniaturization as charted by Moore’s law, thus impacting every aspect of our increasingly digital lives. It is also a prime example of the impact that close collaborations between Lincoln Laboratory and industrial partners have had on society,” says Mordechai Rothschild, who was one of the key developers of the 193 nm technique and today is a principal staff member in the Advanced Technology Division.
Lighting up a world of new technologies
In fall 1962, General Electric, IBM, and Lincoln Laboratory each independently reported the first demonstrations of the semiconductor laser. In the 62 years since, it has become the most widespread laser in the world and a foundational element in a vast range of technologies: DVDs, CDs, computer mice, laser pointers, barcode scanners, medical imagers, and printers, to name a few. However, its greatest impact is arguably in communications. Every second, a semiconductor laser encodes information onto light that is transmitted through fiber-optic cables across oceans and into many homes, forming the backbone of the internet.
While lasers were invented a few years earlier in 1960, the semiconductor type was exceptional because it realized all laser elements — light generation and amplification, lenses, and mirrors — within a piece of semiconducting material no bigger than a grain of rice. When injected with electrical current, the material is extremely efficient at converting the electrical energy to light. These attributes attracted the imagination of scientists and engineers worldwide.
“I’m pretty sure that we wouldn’t be streaming movies to our homes or searching for the best restaurants from our phones without the low cost and manufacturability of semiconductor lasers,” says Paul Juodawlkis, an expert in photonic devices and integrated circuits, and leader of the laboratory’s Quantum Information and Integrated Nanosystems Group. “It’s great to know that Lincoln Laboratory has played an important role in advancing this technology for government and commercial applications for the past 60-plus years and is poised to continue doing so in the future.”
Honoring inventors and their legacy
The 2024 IEEE President-elect Kathleen Kramer presented the three awards to Lincoln Laboratory Director Eric Evans during the dedication ceremony. The ceremony was held in the auditorium at Lincoln Laboratory in Lexington, Massachusetts. Evans was joined on stage by inventors or their descendants to receive each plaque. Many Lincoln Laboratory staff and retirees who contributed to these innovations were also in attendance.
Vincent Orlando, who devoted his 50-year career at the laboratory to developing Mode S technology, joined Evans to accept that award. Mordechai Rothschild and David Shaver unveiled the 193 nm photolithography plaque. Both were lead developers of that technology.
For some, the ceremony was a touching celebration of their parent’s legacy, and a return to fond memories. Richard Rediker, a son of semiconductor laser inventor Robert Rediker, recalled playing in a lab as a child with his father more than 60 years ago, the last time he visited Lincoln Laboratory. He accepted the semiconductor plaque alongside Susan Zeiger and Robert Lax, children of co-inventors Herbert Zeiger and Benjamin Lax respectively.
“It was so rewarding to meet the other children of my father’s colleagues and to fully appreciate what the inventions of our fathers mean to society today. Although my father passed away five years ago, this ceremony brought him back to life for an afternoon,” says Rediker, adding that it was an experience he will never forget.
Likewise, these technologies have left an indelible mark on the world.
“By celebrating the pride and prestige of our profession’s contributions to history, we demonstrate how engineers, scientists, and technologists have contributed not only to our local communities, but also to our global community,” Kramer said, before presenting the plaques. “It is my pleasure to recognize these pioneering events and people behind them. They serve as landmarks in the progress of technology and civilization.”
0 notes
Text
Three Lincoln Laboratory inventions named IEEE Milestones
New Post has been published on https://thedigitalinsider.com/three-lincoln-laboratory-inventions-named-ieee-milestones/
Three Lincoln Laboratory inventions named IEEE Milestones


The Institute of Electrical and Electronics Engineers (IEEE) designated three historical MIT Lincoln Laboratory technologies as IEEE Milestones. The technologies are the Mode S air traffic control (ATC) radar beacon system, 193-nanometer (nm) photolithography, and the semiconductor laser. The latter recognition is shared by Lincoln Laboratory, General Electric, and IBM.
As the world’s largest technical professional organization, the IEEE’s mission is to “advance technology for the benefit of humanity.” The Milestone program commemorates innovations developed at least 25 years ago that have done just that.
All three technologies are integral to everyday life. Anyone who has flown on commercial aircraft has benefited from Mode S, the system that air traffic controllers use to track planes. The integrated circuits that power modern computing and communication devices were manufactured using 193 nm photolithography. Perhaps most ubiquitous of all is the semiconductor laser — a micrometer-sized light-emitting device that has made possible high-speed internet, among many other technologies underpinning today’s information society.
“MIT Lincoln Laboratory has been a leader in fostering innovations that were previously only considered possible in science fiction. The three IEEE Milestones presented are a testament to those accomplishments and a celebration of the diversity of ingenuity and teamwork that created these game-changing technologies,” says Karen Panetta, vice chair of IEEE Boston Section, which presented the awards to Lincoln Laboratory at a ceremony on Feb. 2.
Lincoln Laboratory holds three previous IEEE Milestones for pioneering the use of packet networks for speech communications, for developing the nation’s first air defense system, and for creating the Whirlwind high-speed digital computer in collaboration with MIT campus.
Tracking aircraft globally
The Mode S ATC radar beacon system was developed to address the challenges posed to the existing ATC beacon-radar system used in the late 1960s. Commercial air traffic was growing quickly, causing interference between beacon replies and interrogations from ATC ground radars. This interference threatened to disrupt aircraft surveillance in high-density airspace.
Under Federal Aviation Administration (FAA) sponsorship, Lincoln Laboratory led the technology developments necessary to address this safety issue. The advanced communication architecture of Mode S allowed radars to select a specific aircraft to interrogate. To selectively communicate, the system design included improved aircraft transponders, each assigned a unique address code. Upgrades to radar antennas and signal processing also allowed Mode S to accurately determine airplane position with far fewer air-to-ground messages than required by prior systems. Mode S also provided a datalink capability that enabled other key safety systems, such as the Traffic Alert and Collision Avoidance System.
Today, Mode S is a worldwide industry standard. An estimated 100,000 aircraft are equipped with Mode S transponders, and more than 900 Mode S radars are deployed across the globe. The technology is also the foundation for the FAA’s newest ATC surveillance system, which allows continuous flight tracking independent of ground radars by using aircraft-broadcast position and velocity information.
“This technology touches everybody who flies, every time they fly, for the entire duration of their flight,” says Wesley Olson, a group leader in the laboratory’s Homeland Protection and Air Traffic Control Division, where Mode S was first envisioned. “If it wasn’t for Mode S, we would have a very different air transportation system today, one that would be far less efficient and far less safe.”
Powering the microelectronics industry
The 193 nm projection photolithography technique has enabled the fabrication of every chip in every laptop, smartphone, military system, and data center for the past 20 years.
Photolithography uses light to print tiny patterns onto a silicon chip. The patterns are projected over a silicon wafer, which is coated with a chemical that changes its solubility when exposed to light. The soluble parts are etched out, leaving behind tiny structures that become the transistors and other devices on the chip.
Shorter wavelengths of light allow for printing smaller features, enabling more densely packed chips. By the 1980s, the accepted wisdom in the industry was that 248 nm was the shortest wavelength possible for photolithography.
Despite widespread skepticism and technical obstacles, Lincoln Laboratory pioneered photolithography at the 193 nm wavelength, fabricating the world’s first microelectronic devices using the technique. The first-ever 193 nm projection system was installed at the laboratory in 1993. Soon after, the laboratory opened its doors to industrial partners to guide 193 nm semiconductor manufacturing and pave the way toward its widespread adoption. Today, it is the industry’s mainstream technique and has enabled increasingly powerful integrated circuits.
“Photolithography at 193 nm has enabled the microelectronics industry to continue its path of miniaturization as charted by Moore’s law, thus impacting every aspect of our increasingly digital lives. It is also a prime example of the impact that close collaborations between Lincoln Laboratory and industrial partners have had on society,” says Mordechai Rothschild, who was one of the key developers of the 193 nm technique and today is a principal staff member in the Advanced Technology Division.
Lighting up a world of new technologies
In fall 1962, General Electric, IBM, and Lincoln Laboratory each independently reported the first demonstrations of the semiconductor laser. In the 62 years since, it has become the most widespread laser in the world and a foundational element in a vast range of technologies: DVDs, CDs, computer mice, laser pointers, barcode scanners, medical imagers, and printers, to name a few. However, its greatest impact is arguably in communications. Every second, a semiconductor laser encodes information onto light that is transmitted through fiber-optic cables across oceans and into many homes, forming the backbone of the internet.
While lasers were invented a few years earlier in 1960, the semiconductor type was exceptional because it realized all laser elements — light generation and amplification, lenses, and mirrors — within a piece of semiconducting material no bigger than a grain of rice. When injected with electrical current, the material is extremely efficient at converting the electrical energy to light. These attributes attracted the imagination of scientists and engineers worldwide.
“I’m pretty sure that we wouldn’t be streaming movies to our homes or searching for the best restaurants from our phones without the low cost and manufacturability of semiconductor lasers,” says Paul Juodawlkis, an expert in photonic devices and integrated circuits, and leader of the laboratory’s Quantum Information and Integrated Nanosystems Group. “It’s great to know that Lincoln Laboratory has played an important role in advancing this technology for government and commercial applications for the past 60-plus years and is poised to continue doing so in the future.”
Honoring inventors and their legacy
The 2024 IEEE President-elect Kathleen Kramer presented the three awards to Lincoln Laboratory Director Eric Evans during the dedication ceremony. The ceremony was held in the auditorium at Lincoln Laboratory in Lexington, Massachusetts. Evans was joined on stage by inventors or their descendants to receive each plaque. Many Lincoln Laboratory staff and retirees who contributed to these innovations were also in attendance.
Vincent Orlando, who devoted his 50-year career at the laboratory to developing Mode S technology, joined Evans to accept that award. Mordechai Rothschild and David Shaver unveiled the 193 nm photolithography plaque. Both were lead developers of that technology.
For some, the ceremony was a touching celebration of their parent’s legacy, and a return to fond memories. Richard Rediker, a son of semiconductor laser inventor Robert Rediker, recalled playing in a lab as a child with his father more than 60 years ago, the last time he visited Lincoln Laboratory. He accepted the semiconductor plaque alongside Susan Zeiger and Robert Lax, children of co-inventors Herbert Zeiger and Benjamin Lax respectively.
“It was so rewarding to meet the other children of my father’s colleagues and to fully appreciate what the inventions of our fathers mean to society today. Although my father passed away five years ago, this ceremony brought him back to life for an afternoon,” says Rediker, adding that it was an experience he will never forget.
Likewise, these technologies have left an indelible mark on the world.
“By celebrating the pride and prestige of our profession’s contributions to history, we demonstrate how engineers, scientists, and technologists have contributed not only to our local communities, but also to our global community,” Kramer said, before presenting the plaques. “It is my pleasure to recognize these pioneering events and people behind them. They serve as landmarks in the progress of technology and civilization.”
#000#1980s#2024#Administration#air#air defense#Air traffic#aircraft#applications#architecture#aviation#Awards#honors and fellowships#cables#career#chemical#Children#chips#code#Collaboration#communication#communications#Community#computer#computing#continuous#data#Data Center#defense#Design
0 notes
Text
How to Track a Flight in Real Time

Ever wondered how to track a flight? Here’s what you need to know, including nine flight tracker apps and websites to check out
If you've ever looked up at a plane flying by and wondered where it's coming from and where it's going, it's actually rather easy to find out. Thanks to flight tracking programs, all the information about any given flight is just a click (or tap) away. These days, many flight trackers provide real-time updates about a plane's location, altitude, and speed, and they can be used to monitor nearly all commercial and cargo flights, and even some private and military flights, too. So if you're curious about where your inbound flight is, or if you'd like to track the arrival of someone you're picking up at the airport, you can use a flight tracker to keep tabs on the plane.
How does flight tracking work?
Radar is technically still the global standard for tracking flights, but it has many limitations — numerous areas don't have radar coverage, like the majority of the ocean. Today, flight tracking is shifting to a surveillance system called Automatic Dependent Surveillance–Broadcast, or ADS-B. "Most aircraft today (and virtually all commercial aircraft) are now equipped with an ADS-B transponder which shares every second its detailed position, altitude, and speed parameters with other aircraft and with air traffic control. This is a much more efficient system than the previous system relying on radar," Kathleen Bangs, a spokesperson for flight tracking company Flight Aware, tells Travel + Leisure. Companies that track flights can use global networks of ADS-B receivers to determine the positions of flights all around the world.
How to Track a Flight
While the specifics vary depending on your tracker of choice, generally speaking, you can input any flight number into a flight tracking app or website and see all the key data about that flight, from its ETA to its altitude to its ground speed. Some flight trackers are less sophisticated and might only provide limited information, like departure and arrival times.
Best Flight Tracker Apps and Websites
Flight Aware
"FlightAware operates the world's largest flight tracking and data platform," says Bangs. "We receive data from our terrestrial network of over 35,000 ADS-B receivers in 195 countries, air traffic control systems in over 45 countries, Flight Aware-Aireon global space-based ADS-B, and datalink (satellite/VHF) via every major provider including ARINC, SITA, Satcom Direct, Garmin, and Honeywell Go Direct." On both the desktop website and the mobile app, you can input specific flights to track, or you can look at a global map to see what planes are nearby. We particularly like that you can add a weather radar overlay to the map.
Flightradar24
"Flight tracking on Flightradar24 is powered by a network of ADS-B receivers, the largest such independent network in the world. Individuals apply to host an ADS-B receiver, and once installed, this receives signals from aircraft," Chris Lomas, a Flightradar24 aviation content specialist, tells T+L. "Thousands of aircraft are tracked by our network each day." Like Flight Aware, it has a global map for you to peruse current flights. But one of the most fun tools on the Flightradar24 app, specifically, is the AR feature. When you use it, it opens up your camera, and any plane within the image will be tagged with details like its flight number, departure point, and destination…
read full article
How to Track a Flight in Real Time
Ever wondered how to track a flight? Here’s what you need to know, including nine flight tracker apps and websites to check out.
This article is sponsored by
Loading Offer..
Auto-Redirect failed, Please Click Here to continue.
1 note
·
View note
Text
Mystery Solved: Missing F-35 Fighter Jet Found in South Carolina

In an intriguing turn of events, the debris from a missing F-35 stealth fighter jet has been discovered in Williamsburg County, South Carolina, after a day of perplexing searches and social media commotion. The disappearance of this $80 million aircraft had left many scratching their heads, but now we have some answers. The Debris Discovery On Monday, the US military confirmed the discovery of the F-35's debris field in Williamsburg County, located approximately two hours northeast of Joint Base Charleston (JBC). The announcement was made through a statement posted on X, the platform formerly known as Twitter. The statement also urged members of the community to avoid the area as a recovery team worked to secure the debris field. This discovery came after Joint Base Charleston had issued a plea on social media for information regarding the missing aircraft when it vanished over South Carolina on Sunday. Flight tracking sites showed multiple search aircraft converging on a wooded and farmland area near Stuckey in Williamsburg County. The F-35: A Coveted Asset The F-35 Lightning II jet, known for its distinctive shape and radar-evading features, is highly coveted by US allies worldwide, particularly Ukraine. Its advanced capabilities have made it a prized asset, especially in regions facing security challenges. The pilot of the missing F-35 ejected for reasons still unknown, safely parachuting into a North Charleston neighborhood on Sunday. This left the aircraft flying seemingly autonomously, a situation that some have likened to a "zombie state." Interestingly, this incident is not entirely unprecedented. In 1989, a malfunctioning Soviet MiG-23 pilot ejected over Poland, leaving the jet to fly on autopilot until it eventually crashed in Belgium, over 900 kilometers away. The Public's Reaction The curious case of the vanishing F-35 sparked incredulous reactions online. Some questioned how such a high-tech aircraft could be lost without a tracking device. Congressman Nancy Mace, representing the Charleston area, expressed her disbelief and concern, while others resorted to humor, posting manipulated photos of lost signs on trees with rewards for finding the missing jet. In a humorous twist, one post even featured Ukraine President Volodymyr Zelensky posing with an F-35, playfully suggesting that he might have taken it. Zelensky has been actively seeking advanced US jets for Ukraine's air force since Russia's invasion last year, with the US initiating training for Ukrainian pilots on F-16s. The F-35B and Its Stealth Capabilities The missing aircraft, an F-35B variant, is operated by the Marines and boasts short takeoff and vertical landing capabilities. Its unique airframe design, including angled stabilizers at the back, and the use of special materials make it challenging for conventional radar systems to detect. A spokesperson from Joint Base Charleston mentioned that the aircraft's transponder was not functioning, adding to the difficulty of tracking it. The stealth capabilities of the F-35, designed to evade radar detection, further compounded the situation. What happened to the missing F-35 fighter jet?The F-35 fighter jet went missing after the pilot ejected for unknown reasons. The debris field from the aircraft was later discovered in Williamsburg County, South Carolina.Why is the F-35 jet so coveted by US allies, particularly Ukraine?The F-35 is highly coveted due to its advanced capabilities and distinctive design, which shields it from radar detection. Ukraine has been seeking advanced US jets to bolster its air force since Russia's invasion.What is the F-35B variant, and how does it differ from other F-35 models?The F-35B is a variant of the F-35 operated by the Marines. It has short takeoff and vertical landing capabilities, making it suitable for various operational scenarios.Why was it difficult to track the missing F-35 jet?The F-35's transponder was not functioning, and its stealth capabilities, designed to evade radar detection, added to the challenges of tracking it. Read the full article
0 notes
Text
Janet Flight Schedule
A fleet of six Boeing 737s provide commuter service between Las Vegas International Airport, Area 51, TTR, Palmdale Plant 42 and sometimes other destinations as needed. The airline uses the callsign Janet and the planes are known as Janets. There are also seven smaller Beech Executive aircraft that operate out of the same terminal in Las Vegas. They are also known as Janets and use this callsign. Further down on this page you will find more information on the Beech Janets.
The six 737s make about 14 round-trip flights to Area 51 and about 10 to TTR every weekday. Some flights listed below do not operate every day. There may also be occasional flights as needed that are not listed below. There are usually no 737 Janet flights on weekends. The tables below show the flight schedule as of 06/01/2021.
Janets from Las Vegas to Area 51 or TTR usually turn off their Mode-S transponder (the device that allows aircraft tracking websites to display the aircraft's position) when entering the NTTR air space. So, how do we know which flights are going to Area 51 and which are going to TTR? Very simple: The altitude in the visible part of the flight path from Las Vegas to Area 51 is 14,000ft. and 15,000ft. for the return flight. For flights to/from TTR, the flight altitude is FL200/FL190. In addition, flights to Area 51 usually enter the ranges around Indian Springs or Mercury while TTR-bound flights usually follow US-95 towards Tonopah or head north-west from Mercury inside the ranges.
Las Vegas - Area 51 round trip
Las Vegas -> Area 51 (14,000 ft.)
Callsign Time Notes
Janet 11 03:40am - 04:05am
Janet 33 04:05am - 04:30am
Janet 77 05:05am - 05:30am
Janet 43 06:05am - 06:30am
Janet 87 07:10am - 07:35am
Janet 17 08:20am - 08:45am
Janet 41 09:05am - 09:30am
Janet 53 09:05am - 09:30am Norm. to TTR, if to Area 51 cont. to TTR as Janet 89
Janet 46 11:10am - 11:35am
Janet 27 01:30pm - 01:55pm
Janet 51 02:15pm - 02:40pm
Janet 15 04:10pm - 04:35pm
Janet 61 05:00pm - 05:25pm
Janet 25 06:35pm - 07:00pm
Area 51 -> Las Vegas (15,000 ft.)
Callsign Time Notes
Janet 22 04:25am - 04:50am
Janet 44 04:55am - 05:20am
Janet 88 06:05am - 06:30am
Janet 54 08:00am - 08:25am
Janet 18 08:05am - 08:30am
Janet 42 10:05am - 10:30am
Janet 86 12:45pm - 01:10pm
Janet 82 01:30pm - 01:55pm
Janet 34 01:45pm - 02:10pm
Janet 16 02:45pm - 03:10pm
Janet 62 03:25pm - 03:50pm
Janet 26 05:35pm - 06:00pm
Janet 72 06:20pm - 06:45pm
Janet 36 08:15pm - 08:40pm
Las Vegas - Tonopah Test Range round trip
Las Vegas -> Tonopah Test Range (FL 200)
Callsign Time Notes
Janet 55 04:35am - 05:10am
Janet 65 05:25am - 06:00am
Janet 31 05:55am - 06:30am
Janet 75 08:00am - 08:35am
Janet 53 09:15am - 09:50am +/- 1 hr; occasionally to Area 51, see Janet 89
Janet 47 12:55pm - 01:30pm
Janet 39 02:45pm - 03:20pm
Janet 73 03:25pm - 04:00pm
Janet 37 03:55pm - 04:30pm
Janet 83 06:15pm - 06:50pm
Tonopah Test Range (TTR) -> Las Vegas (FL 190)
Callsign Time Notes
Janet 24 06:10am - 06:45am
Janet 76 06:40am - 07:15am
Janet 30 06:50am - 07:25am
Janet 12 09:10am - 09:45am
Janet 64 11:30am - 12:05pm
Janet 74 02:30pm - 03:05pm
Janet 48 04:00pm - 04:35pm
Janet 84 05:00pm - 05:35pm
Janet 68 05:15pm - 05:50pm
Janet 14 07:30pm - 08:05pm
Tonopah Test Range (TTR) - Area 51 Flight
Callsign Time Notes
Janet 50 08:50am - 09:20am Tue-Thu; usually via Hwy 95; some days direct, then landing at 9:05am
This direct flight from TTR to Area 51 usually operates Tuesday thru Thursday. Most days it flies down the US-95 corridor like the Janets from TTR to Vegas at FL190. At waypoint JAYSN south of Mercury it turns north and descends to 14,000ft for the Area 51 approach. Occasionally, if R-4807A is cold it flies direct at 14,000ft.
Area 51 - TTR Flight
Callsign Time Notes
Janet 89/20 03:15pm - 03:40pm Only on days when Janet 53 lands at Area 51 instead of TTR; seems to go direct, across the R-4807A air space
Palmdale round trip flights
Two weekly round trip flights transport workers from USAF Plant 42 in Palmdale, CA to Area 51 on Monday mornings and back on Friday nights (Thursdays before a holiday weekend). Plant 42 is home to the Lockheed ("Skunkworks") and Northrop black projects development division. The workers stay at Area 51 during the week.
Area51/TTR -> Palmdale -> Area51/TTR (Mondays)
Callsign From To Time Notes
Janet 19 Area51/TTR Palmdale 07:05am - 07:50am Origin seems to alternate weekly between Area 51 and TTR
Janet 29 Palmdale Area51/TTR 08:30am - 09:10am Destination seems to alternate weekly between Area 51 and TTR
Las Vegas - Area 51 -> Palmdale -> Las Vegas (Fridays)
Janet 60/90 Las Vegas Area 51 06:40pm - 07:05pm Sometimes flies as Janet 60, other times as Janet 90
Janet 92 Area 51 Palmdale 07:40pm - 08:25pm
Janet 93 Palmdale Las Vegas 08:50pm - 09:30pm
Other Janet Flights
JANET99 - Mostly to Kansas City International Airport, MO for overhaul/maintenance
Beech Executive Aircraft "Janet" Flights
The seven Beech "King Air" Executive Aircraft are registered to the same owner as the 737 Janets and operate from the same Las Vegas terminal. Since 02/2021 they also use the Janet call sign, but with a single digit flight number (e.g. "Janet 4" in radio traffic and "JANET04" on flight tracking web sites). The number is the last digit of the aircraft registration (tail number). See our list of Janet Tail Numbers. The exceptions are N20RA, which goes by "Janet 5" and N910CB, which goes by "Janet 10".
The King Airs make somewhat regular round trip flights to the destinations listed below as needed. There is usually at least one such trip every weekday, including some of the destinations listed. Most of the round trips originate from and end in Las Vegas. However, since the Las Vegas Janet terminal only has room for four of the seven jets some of them are always at Area 51 or TTR over night and occasionally make round trips from there.
Sometimes one of the King Airs provides support for tests inside the ranges. In June of 2020 N654BA was stationed at TTR and flew test missions over the Tolicha Peak Electronic Combat Range (TPECR) and over the Nevada National Security Site (NNSS) using the callsign Greyhound 1. N661BA has also been spotted supporting an Area 51 mission using the Area 51 call sign Sabre 45.
Other Destinations
Recent destinations
LAS - Las Vegas International Airport, NV (home base)
XTA - Area 51, NV
TNX - Tonopah Test Range, NV (TTR)
9L2 - Edwards AFB North Base, CA
PMD - Palmdale Regional Airport, CA (USAF Plant 42)
IYK - Inyokern Airport, CA (NAWS China Lake)
NTD - NAS Point Mugu, CA
OXR - Oxnard Airport, CA (NAS Point Mugu)
CMA - Camarillo Airport, CA (NAS Point Mugu)
LSV - Nellis AFB, NV
DVT - Phoenix Deer Valley Airport, AZ
IWA - Phoenix Mesa Gateway Airport, AZ
VBG - Vandenberg AFB, CA
COS - Colorado Springs Airport, CO (Peterson AFB, Space Force)
FAT - Fresno Yosemite International Airport (Fresno Air National Guard Base)
PAE - Paine Field, WA (Boeing)
MCI - Kansas City International Airport, MO (Overhaul Facility, callsign mostly JANET99)
OGD - Ogden-Hinckley Airport, UT (Near Hill AFB)
HIF - Hill AFB, UT
Older destinations seen in the past
HND - Henderson Executive Airport, NV
NSI - San Nicolas Island, CA
ALM - Alamogordo-White Sands Regional Airport, NM
SLC - Salt Lake City International Airport, UT
Destination Codes
During clearance delivery the destination of a Janet flight is given. However, instead of actual names, the following codes are used:
Destination Code
Palmdale Regional Airport/USAF Plant 42 (KPMD) Station 1
Groom Lake (KXTA/KTNX) Station 3
Basecamp? Station 6
TTR (KTNX) Station 7
Las Vegas Janet Terminal (KLAS) Station 9
#janet#janetairline#janetairlines#janetairways#airliner#topsecret#lasvegas#vegas#KLAS#kxta#area51#GroomLake#KTNX#Tonopah#tonopahtestrange#nv#Nevada#beoing737#area52#alien#blackproject#boeing#conspiracytheories#conspiracytheory#homeyairport
1 note
·
View note
Text

I flew the most secret MiG fighter in the world for the US Air Force: Red Eagle pilot gives the low-down on America’s MiG-21 ‘Fishbed’
Hush KitMarch 16, 2021
Name: Brian McCoy
Rank: Captain
Service: United States Air Force
How did the MiG-21 differ from the F-5E?
The biggest difference for the pilot would have to be familiarity. The F-5E is essentially a beefed-up, fighter version of the Northrop T-38 Talon … an aircraft every USAF pilot had experience in during basic flight training.
First Impressions?
Small airplane! Small cockpit, archaic instrument panel, high canopy rails.
How would you rate the cockpit for the following:
a. Ergonomics?
Ergonomics wasn’t yet a thing when the ‘Fishbed’ was designed.
b. Pilot’s view?
Outward visibility contends for the worst single problem encountered by the Fishbed pilot during air combat manoeuvring. Fighting the MiG-21 required deliberate manoeuvring simply to keep the adversary in sight … regardless of the tactical advisability of such manoeuvring.
The blind zone behind the pilot (due to the ejection seat and structural members behind the seat) extends at least 40 degrees either side of the tail. The wings are not visible to the pilot – neither is the vertical tail.
The blind zone under the high canopy rails extends about 70 degrees either side as measured from the pilot’s butt centerline (aircraft structure).
The blind zone out front is about 10 degrees either side of the nose (tall instrument panel; poorly-placed gun camera; combining glass supports; thick, translucent Pexiglass sheet placed in front of pilot as protection from B-52 tail gunner).
c. Comfort
i. While not really a concern for the designers, it’s not any more uncomfortable than other fighter designs from the era. And they did paint the instrument panel a soothing shade of green specifically to calm the pilot.
d. Instrumentation
i. Primarily the instruments we used were factory-installed … with Cyrillic characters and metric system measures and graduations – neither of which were familiar to the average American fighter pilot. Luckily our outstanding maintenance professionals placed green arcs for normal operating ranges and red radials for system limits. At some point, numbers are numbers.

Our jets had American altimeters, airspeed indicators, radios, transponders, oxygen regulators and drag chutes (for the Soviet jets … F-7 jets came from the factory with drag chutes).
Yes, the ejection system was factory installed. For the older Soviet jets, that meant a 57mm mortar shell fired to propel the ejection seat (and pilot) from the aircraft. It also brought along the forward-hinged canopy which attached to the headrest of the pilot’s seat and then folded down in front of the pilot as a shield from windblast. (The canopy and related support members probably weighed 250 – 400 pounds!) The later F-7 jets featured a rocket-propelled seat that had nearly 0/0 capability (the pilot was on his own against the breeze). The fabulous ACES-II ejection seat installed in the F-15 and F-16 aircraft (among others) used similar rocket tubes that fired sequentially to keep the G-loading associated with riding the seat during ejection down to a maximum of about 16 G’s. The F-7 rocket tubes fired all at once … giving the ejectee a spine-compressing 21 G “boost” from the aircraft.
Against the F-16?
a. In WVR: Which aircraft would have the advantage and why?
i. The F-16 holds every advantage: Higher thrust-to-weight ratio, vastly better outward visibility, higher instantaneous turn rate, much higher sustained turn rate, better weapons, much better cannon and gunsight, better man/machine interface, better acceleration … the only potential advantage the ‘Fishbed’ pilot might enjoy is if the speeds in the fight slow below 250 KIAS – well below. The slower the fight gets, the more the advantage swings to the MiG.
b. Which set-ups and altitudes would the MiG-21 favour?
i. Offensive perch at 1,000 foot range in solid gun tracking solution … LOL.
ii. Side-by-side, line-abreast 500’ spread, 150 KIAS (or less), 20,000 feet MSL.
c. How should the MiG-21 pilot fight?
i. Call for help, stay close to the Viper, get slow (and hope the Viper follows suit), keep pointing the nose at the Viper to threaten him, call for help, look for any opportunity to leave the fight, consider pre-emptive ejection, call for help!”
d. Who would you put your money on?
i. It might be obvious that I’m leaning toward the F-16.
ii. But this question opens a line of consideration I’ve encountered several times on related FB posts … the idea that the superior aircraft always – and almost automatically – wins. For nearly eight years I flew nothing but air-to-air in engagements ranging from 1v1’s to Red/Green/Maple Flag exercises. I’ve led small missions and those Flag exercises. Debriefed both using high technology or chalkboards in as much detail as the situation required to illustrate the learning points involved. I estimate I’ve been in 4,500 engagements during those years. As I learned more and more about air combat and experienced varied tactics, aircraft capabilities (or lack thereof) and the occasional imposition of simple luck … the more I came to realise the skill, daring and bravado of the pilot in that other airplane was far more important in determining an engagement’s outcome than the type aircraft he was strapped into.
iii. But I’d rather be in the F-16 for such a fight.

About 60 – 70% of our ‘adversaries’ paid attention in our pre-mission briefings and avoided fighting in such a way as to maximise our limited list of potential advantages. They kept their energy up, kept their distance, threatened us enough to force us to bleed energy and then killed us quickly and cleanly. We lost nearly all of these sorts of engagements – just as intended!
The Hush-Kit Book of Warplanes will feature the finest cuts from Hush-Kit along with exclusive new articles, explosive photography and gorgeous bespoke illustrations. Pre-order our Hush-Kit Book of Warplanes here. Until Tuesday 6th April we are running a bank holiday weekend promo code. The code is CRACKING20 and is valid for 20% off pledges and pre-orders on The Hush-Kit Book of Warplanes
20 – 25% of our adversaries either ignored our briefings or intentionally sought to see what happens when they ‘stepped into the phone booth’ with us. We’d win well over half of such fights … pretty good considering we almost always started out defensively.
The rest either had a bad day, didn’t have a plan, or were so overcome by the situation that they forgot what to do. We knew what to do.
iii. We normally started on the DEFENSIVE perch, allowing frontline pilots the opportunity to watch the threat aircraft do it’s thing while they were looking out their front windows … much easier than assessing performance while looking over their shoulders.
iv. I had memorable engagements against F-15’s, F-16’s, A-4M’s … but perhaps especially against the original F/A-18.
Best thing about the MiG-21?
a. Simplicity
Worst thing about the MiG-21?
a. Toss-up between abysmal outward visibility, incredible susceptibility to battle damage and astounding energy bleed-off during heavy manoeuvring.
How would you rate the MiG-21 in the following areas:
a. Instantaneous turn rate
i. Totally dependent on airspeed. Nothing special until below 250 KIAS – then it became startling. The rate did not increase at the lower speeds … it simply did not fall off as much as expected.
b. Sustained turn rate
i. Woeful. A 4+G level turn in full AB bled a bit over 1 knot per degree of heading change. Impossible to assess a “sustained turn rate” with bleed off like that.
c. Weapons platform
i. Keep in mind we flew very early export model ‘Fishbeds’ – MiG-21 F-13’s and F-7’s. Not the most advanced Fishbeds built.
ii. We simulated carriage of the IR-guided AA-2 Atoll … a direct copy of the AIM-9B Sidewinder. Not an impressive missile. Fishbeds also carry the AA-8 Aphid IR missile … a short range missile with impressive cornering capability.
iii. As a gun platform the Fishbed suffers from an incredibly unstable gunsight … useless above 2.5-3 G’s. The gun itself suffered from poor rate of fire and low muzzle velocity … but at least it didn’t carry many rounds.
d. Acceleration
i. Acceleration of the early-model Fishbed was actually quite good. Less than late- model F-16’s but on par with F-15C’s.
e. Top Speed
i. We lived with a self-imposed limit of 600 KIAS … enough for perhaps Mach 1.3 at altitude. It’s reportedly a Mach 2 capable airframe. I see no reason to doubt that capability.
Read what fighting these MiGs was like from an F-15 pilot here
f. Take-off characteristics
i. Tonopah Test Range Airfield sits at about 5,600 feet above sea level – enough altitude to seriously reduce takeoff performance. We never flew the Bandits from a lower field elevation.
ii. Temperature varied considerably at TNX – also effecting flight performance drastically.
iii. Taking the runway, I’d lock the nosewheel in the straight-ahead position and select nosewheel braking to aid in any abort situation. Once cleared for takeoff (except for that ONE time!), I’d run the power up to MILITARY while holding the brakes. When prepared to launch, I’d simply release brakes and note the acceleration sensation at the small of my back. After perhaps 2 seconds of acceleration at just MIL, I’d thumb the release and select MAXIMUM power. The afterburner lightoff process took a few seconds (and featured a very good opportunity for the engine to cease operating altogether), caused several expected engine instrument fluctuations and normally resulted in much higher thrust output. (Sensing the differing acceleration rates of the two power settings gave me another check for normal engine operation.) Once lit, the afterburner made things happen much more quickly.
iv. The MiG-21 typically rolled about 3,500 to 5,000 feet before attaining takeoff speed at about 150 KIAS. Climbout was always in full afterburner until reaching 10,000 feet MSL. (This was to get us as quickly as possible out of the more dangerous low altitude ejection envelope.) We typically climbed out at 300 KIAS with a very steep climb angle.
v. The aircraft was designed to takeoff from even unprepared fields, climb quickly to high altitude, accelerate to supersonic speed … and run down attacking B-52 bombers. I never took off from a plowed field, so I can’t verify that specific capability – but the airplane’s delta wing made it very capable of quick climbs and rapid acceleration.
g. Landing characteristics
i. Oh, boy! Do we have to do this?
ii. First of all, refer back to the section where I discussed the limited forward visibility. Nowhere is that more relevant than during each mission’s landing phase.
Pilots had to fly the overhead traffic pattern looking obliquely forward during the final turn. This is completely natural and how every final turn is flown in every fighter jet.

When rolled out on final, that same oblique viewpoint (out both sides now) has to be used to fine-tune runway alignment … and it works okay. But the normal down-the-runway cues most guys use for rounding out and flaring to land are hidden, so peripheral vision has to substitute perceived sink rate to help ‘feel’ for the runway. This skillset needed some development. (It wasn’t as bad as the wall in front of Charles Lindbergh in the ‘Spirit of St. Louis’ … but it wasn’t as good as looking through your car’s windshield, either.)
iii. The engine’s extremely slow windup makes the landing pattern the most dangerous phase of flight for the unwary or careless ‘Fishbed’ pilot.
Idle to MILITARY power took as much as 13 seconds … almost a quarter of a minute!! Imagine a ‘Fishbed’ pilot allowing the engine’s rpm to decay all the way to idle while at low altitude, low airspeed and high sink rates – as normally occur during any routine traffic pattern.
One of the signs of low thrust availability came anytime engine rpm dropped below 80% N1.
a. The extended windup time was less than the 13-second Idle to MIL marathon … but even 5 or 6 seconds waiting for useable thrust could be critical.
b. The exhaust nozzle opened fully right around that 80% N1 reading, dropping the effective thrust to nearly nothing. That was the true danger of allowing the engine rpm to decay.
c. Instructor pilots flying chase aircraft (AT-38B’s) could visually monitor the exhaust nozzle during traffic patterns with new pilots so as to provide warning and guidance in case of decayed engine rpm … or other issues with transitioning pilots’ traffic pattern work.

An AT-38B Talon aircraft flies over the plains during a 479th Tactical Training Wing Lead-In Fighter Training (LIFT) flight near Holloman Air Force Base. Training on the Talon, LIFT pilots and weapons systems officers become familiar with fighter tactics and maneuvers which they will eventually use tactics and maneuvers which they will eventually use when flying more technologically advanced aircraft.
d. While potentially dangerous, this condition was easily avoided by simply not allowing the engine rpm to slow below the 80% N1 level. As a result, we flew wimpy wide traffic patterns with very gradual turns and descents.
iv. The Fishbed was actually easy to fly through it’s landing pattern … so long as the pilot was aware of and prepared for the unusual and potentially dangerous pitfalls unique to the aircraft.
v. Being a single-engine aircraft, we spent a lot of time thinking about and training for flameout recoveries. Our glide profile was flown at 250 KIAS … the same speed we used for other emergency recoveries.
vi. While TNX was our prime recovery field, flight conditions at the time of the emergency could make landing there impossible due to distance. There were several contingency landing possibilities in the area – like old, inactive runways or dry lake beds. (Necessity is the mother of invention.)
vii. We used drag chutes on every landing to extend brake and tire life.
Read what fighting these MiGs was like from an F-15 pilot here
h. Climb rate
i. The aircraft could climb rapidly and steeply to whatever altitude was required. Once level, the Fishbed could quickly accelerate to supersonic speed.
i. Range
i. This is an astonishingly short-ranged aircraft … even for a fighter. I’ve taken off from TNX, climbed to meet an adversary almost directly overhead the runway, fought three engagements and left the range with need to land immediately due to fuel considerations … ten minutes after takeoff!
ii. I flew 287 ‘Fishbed’ sorties in my Constant Peg career – logging 134.5 hours … a bit under 0.47 hours per sortie. We weren’t trying for long sorties and made liberal use of afterburner, so your results may vary.
iii. We never flew the Bandit jets with external fuel tanks or in a cross-country fuel-efficient mode … at least not while I was there.
j. Sensors
i. Mark-1 eyeballs were our best set of sensors – by far! Our best-in-the-business GCI controllers were a close second.
ii. There was no onboard Airborne Intercept search-and-track radar.
iii. There was no IRSTS.
iv. There was a range-only radar system that displayed information on a meter equipped with lights to indicate “In Range.” It was a pathetic system useful only when I pointed the jet straight down to get altitude verification. I suppose it may have been effective against relatively cooperative, bomber-sized targets.

Biggest myth about the MiG-21?
a. That it is not an effective combat machine. With well over 11,000 copies built over a very long production run, it remained deadly due to sheer numbers for decades.
What should I have asked you?
a. How many times did the MiG-21 try to kill you? [Tried hard only once]
b. Would you willingly fly the MiG-21 into combat? [No.]
c. Was the MiG-21 easy to taxi? [Not Day One … or Day Two]
Describe you most memorable exercise in the MiG-21?
a. Describe a typical MiG-21 fight
b. How did the Soviets fight and where did this knowledge about their tactics come from?
i. I’m unsure of the remaining classification status of some aspects of this sort of information and not comfortable discussing it. It’s probably now unclassified since the USSR is out of business but I’d prefer to leave this topic alone.
c. Which model of MiG-21 was it and where did it come from?
i. We flew the MiG-21 F-13 (an early export model best known for combat operations versus United States aircraft in Southeast Asia.) We also flew later license-built (?) F-7 aircraft. Where these aircraft came from is frankly more than I personally know or am willing to discuss.
d. What was life like between missions? How did the desire for secrecy change things in your life?
i. We left Nellis AFB every morning via MAC-owned/operated C-12 executive transport aircraft (Beechcraft King Airs). We returned almost every evening after the day’s flight operations were complete. This travel was required to enable face-to-face debriefings with our adversary aircrews. Non-pilot personnel typically traveled to Tonopah on Monday mornings and returned to Nellis Friday afternoons. There were adequate dormitory, mess hall and recreational facilities to accommodate all assigned personnel. Pilots each had a full-time dorm room in case they needed to remain overnight.
ii. Details of our squadron’s operations were classified – but the fact that something special was going on was not a closely-guarded secret. We were treated with something like lofty respect by the Nellis fighter community – and granted unquestioned ‘expert’ status in matters regarding adversary aircraft.
iii. I could not share specific information with my family. If I’d been killed while flying a MIG – my family would have been told a cover story.
iv. One night at home my heart nearly stopped during a local news broadcast clearly showing a MiG-21 taking off at Tonopah! I couldn’t say a word about what I’d seen on the TV … thankfully my young family couldn’t tell a MiG-21 from a B-29 … but my jaw dropping to the floor might have drawn attention.
Tell me something I don’t know about the MiG-21
a. It accelerates right with the MiG-27 … knot for knot!
Describe the MiG-21 in three words
a. Surprisingly nimble $hitheap!
Quickest way to lose a fight with a MiG-21?
a. Failure to pick him up visually before he’s in firing position. With a wingspan under 24’ … it’s very hard to see!
b. Slowing down with him (assuming he’s willing and able to fight at very slow speed)
Against the F-15
a. How does the MiG-21 compare to the F-15 in WVR?
i. Each of the advantages enjoyed by the F-16 in the previous discussion also apply to the F-15’s advantages (except that acceleration is basically a draw) – with the additional factor that the Eagle is even better than the ‘Fishbed’ at slow speeds. The MiG is considerably smaller and much harder to see and perhaps keep track of in a visual fight.
b. What was your most challenging opponent in BFM/DACT and why?
i. Not really a definitive single answer to this question – owing to the pilot skill factor brought up above.
ii. Need to mention that most Constant Peg engagements went according to plan.
In a 1v1 between an F-5E and a MiG-21 which aircraft would you rather be in and why?
a. If life and death is not on the line, I’d prefer to be in the MiG-21. Knowing what I know, I can control the fight, bring it to a situation I can completely control and confidently maneuver to win the fight … decisively.
b. If life and death is on the line … give me the F-5E. (Damn few ‘Fishbed’ pilots realise they can fight that jet down to 30 KIAS. The better survivability of the F-5E can’t be denied.)
What was Constant Peg and how did it work?
a. Constant Peg was a flight program utilising actual threat aircraft to expose frontline American fighter crews to the sight of an aircraft they’d expect to kill. There was some exposure to fighting that aircraft – with the expectation that they would not encounter more skilled pilots anywhere else.
b. Normally selected units deploying to Nellis for Red Flag exercises were given the opportunity to spend part of their time with us.
i. They would operate out of Nellis – just as they did for Red Flag.
ii. We’d inbrief them into our program – usually on a Saturday.
During this inbrief each pilot would sign a sheet informing them of the penalties for divulging information about our program.
We’d also brief them about the aircraft they’d be flying against. (This was when we’d tell them not to go into the phone booth with the ‘Fishbed’!)
iii. We would wait on the ground until GCI told us our adversaries were inbound to our operating areas at the extreme northwest corner of the vast Nellis airspace complex. Our flight time was extremely limited, so saving fuel was a primary … and constant! … concern.
iv. Immediately after takeoff (we most often took off in pairs), we’d run a Soviet-style tactic for our adversaries to practice their radar work. They’d also run a stern-conversion on us to get us quickly together to get on with the meat of our mission.
v. Participating pilots had to first experience a Performance Profile mission with one of our pilots. This was a sophisticated ‘show and tell’ mission where the Red Eagle pilot described identifying features of his aircraft (without actually naming the aircraft … never know who’s listening!), coordinated a drag race to compare acceleration capabilities and led an advanced-handling demonstration.
vi. Once completing a PP with a ‘Fishbed’ pilot, our adversaries normally got a second PP with a Flogger pilot.
vii. After flying a PP with both aircraft, they were cleared to fly BFM missions with us.
BFM missions with the ‘Fishbed’ were full-up fights. We’d normally begin out front in the defensive position … allowing our adversary to watch us do our thing out their front window. Most of the time we’d start at about 20,000 feet, with about 400-450 knots on both jets and the adversary about 9,000 feet behind at the MiG’s 4:30 or 7:30 position. We’d usually get two long or three short engagements before the ‘Fishbed’ was out of fuel.
Who would win Eurofighter Typhoon versus Dassault Rafale? Analysis here
BFM missions with the Flogger were not very challenging for our adversaries … the Flogger couldn’t turn well at all. But seeing that in person was an important thing to learn.
viii. Once completing BFM missions with both aircraft, adversary pilots moved on to DACT missions – normally against one ‘Fishbed’ and one ‘Flogger’. (We rarely flew DACT sorties since so much emphasis was put on the BFM missions.)
c. We also participated in actual Red Flag missions – either with the Bandit aircraft or our AT-38B’s … or sometimes with both! (Our participation limited the Red Flag scenario to American participants only – due to the classification of our program.)
Why were you chosen for this effort and how would you describe the other individuals in your team?
a. I sometimes wonder why I was selected for this program. I volunteered, had built a solid reputation within the USAF fighter community and had appropriate experience that allowed me to be considered. Only Aggressors, Fighter Weapon School graduates and former Topgun Instructors were considered to become Bandits! I was an Aggressor. Bottom line? I got lucky!!
i. Even with those prerequisites, a prospective Red Eagle had to pass muster with the current Red Eagles. One vote, “No” … and you were out.
ii. Three personal interviews took place: two with individual General Officers – in their offices. Not intimidating at all! The third … and most important … was with the Red Eagle Operations Officer. Fail that one – and the outcome of the other interviews didn’t matter.
iii. Needed a security clearance a notch above Top Secret to play. Not routine.
b. Everyone that wore a Red Eagle patch was absolutely top-notch! The pilots I flew with – USAF, USN and USMC – were extremely skilled aviators. I’d go to war with any one of them … or all of them! Red Eagle GCI controllers were the absolute best. Our maintenance folks were beyond comparison … best in the business! They could build an airplane from spare parts without any problems – or they could fashion parts if none existed! We pilots routinely placed our lives in their hands without batting an eye. We also entrusted our lives to the Life Support technicians that worked directly for me (I was the Squadron Life Support Officer) but needed no direction from me. (There were two ejections while I was there … both pilots survived without meaningful injuries – thanks in part to the efforts of my guys.) We had dedicated professionals manning the firetrucks, security posts, refueling trucks, cooking our meals, cleaning our rooms, filling out our paperwork … at every level of effort – amazing, hand-picked personnel volunteered to pull classified duty at a classified location for several days each week away from home. I’m still impressed by the numbers of highly-qualified people that supported our unique mission. And kept it all secret until the program was declassified in 2006!
13 notes
·
View notes
Text
RFID The New Technology - The origins of RFID tags

Leon Theremin is thought to be the very first user or the inventor of this device. It was the logical element of a spy kit for The Russian Government from 1945. It is not a true source: the gadget created by Theremin was a covert passive listening device, is not an identification tool. The technology used to RFID is actually in use since the 1920s. The IFF transponder, which is a more pertinent technology, was invented in 1939. The British employed it during the Second World War to detect aircrafts if they were friendly or enemies.
Is RFID a thing? RFID is a broad term for technology that utilize radio waves to identify objects or individuals automatically. After storing a serial code or other information about identification on the chip that is connected via an antenna the user is able to detect radio waves coming from the chip and transform this signal to digital data that can then be transferred onto computers and used by. The technology is ideally suited for use in access control, and asset tracking. For example the logistics clothing rfid tags makes use of it when delivering massive cargoes.
RFID technology is widely in use in all technologies and areas like radio, television, cellular phones, radar and automated identification systems. RFID (Radio Frequency Identification) allows for the automatic identification of objects using the radiofrequency signals. RFID is utilized in a variety of applications such as the collection of tolls (electronic) railway car identification and tracking intermodal container identification tracking and identification of assets inventory management for healthcare, retail and logistics applications across the nation, access control animal identification, loyalty programs for fuel dispensing programs, immobilizing vehicles and more.
Radio Frequency (RF) refers to of electromagnetic waves that have an appropriate wavelength for use in radio communications. The frequency of these waves is categorized by the frequency. radio waves are described in megahertz, kilohertz or gigahertz. Radio frequencies vary from extremely low frequencies (VLF) that has an interval between 10 and 30 kHz, up to extreme high frequency (EHF) that has between 30 and 300 GHz.
RFID An Outline - RFID is the most reliable and most reliable technology for automatic operation due to its resiliency. It has advantages not offered in other technologies for identification. RFID is able to function in a variety of circumstances and provide an excellent level of integrity of data. Furthermore, because RFID is hard to duplicate, it offers an high levels of security. In essence, RFID is essentially the same as bar codes. Bar code makes use of an electronic reader and codes which are attached to the item and RFID uses a reader and specific RFID devices that can be attached to the item. In order to transfer information from the label to a readers the Bar code system utilizes optical signals, whereas RFID employs RF signals to accomplish the identical.
Radio waves transmit information between the item that the RFID device is attached , and the RFID reader. The reader can contain information about the object, like what the item's name is and the time it spends to move through the area, and even a number of parameters, such as temperature. Practicallyspeaking, RFID devices like tags and labels are able to be linked to anything such as a car to pallets of items. RFID technology operates in the 50 kHz range up to 2.5 GHz. The RFID system comprises the these components:
. A tool that can be used to store information about the object.
. An antenna that transmits information from RF signal between the reader as well as the RFID.
. A transceiver for RFID that produces an RF signals.
. A reader that receives RF signals from an RFID device and transmits the information to an host system to process.
Additionally the RFID system also includes software for specific applications.
Different types of RFID tags - RFID tags come in two varieties either passive or active. Passive RFID tags are deficient in terms of power source on their own, whereas active RFID tags have a energy source, and can be able to cover a wider range and larger memories than passive tags . Additionally, they are able to accommodate additional data transmitted via transceiver. Today, you can find some of the slimmest active tags the size of one coin.
Passive RFID tags are increasingly used because their production costs are lower and they don't rely on batteries. Beyond cost benefits There is nothing unique in passive Tags as well as the precision and dependability of Active Tags allow the usage of Active Tags widespread in the present. They are classified by their radio frequency there are four kinds of tags that are in use, namely. high frequency, low frequency, UHF, and Microwave tags.
The advantages of RFID for Bar Coding - According to the research team, RFID tag has the capability to store more information including serial numbers, individual information about the product, and any other information manufacturers would like to add. In contrast to Barcode systems, RFID scrutinizes each product separately and does not reveal the type of product. RFID technology assists us to identify any item within a specified distance. However, we aren't obliged to observe the physical presence of the product. The plastic-based passive tags are stronger and more durable. They can be reused.
. Low-frequency RFID tags are in widespread application for identification of animals, beer kegs and auto key-and-lock anti-theft systems.
. High-frequency RFID tags are used in bookstores and libraries for trackers, the pallet tracking access control in buildings as well as airline baggage tracking and tracking of clothing items. High-frequency tags are used extensively to identify badges as well as to replace magnetic stripe cards.
. UHF is typically used for the tracking of containers and pallets in trade and in trackers of trucks and trailers in warehouses.
. Microwave RFID tags are utilized in access control systems for long-range vehicles.
. RFID transceivers are used in the measurement of seismic sensors, making it easier to perform collecting data from remote locations.
. RFID transponders are able to be embedded in tyres to track tyres RFID chips are also useful in the form of cards that function for electronic money.
. This technology has a brand new application in the form of Smart Key; the key fob has an active RFID circuit that can detect the key's presence at a distance of 3 inches from the the sensor. The driver is then able to unlock the doors and start the engine, even if the key is in the pockets or purses of the driver. Inventions for marking animals RFID chips, embeddable RFID chips are employed as brooding devices for human beings too.
Possible uses - It is anticipated that RFID tags could substitute for UPC or EAN barcodes since they have many advantages over barcodes. Barcodes, however, offer their own advantages, such as the lower cost of RFID, and this will help keep barcodes on the market. Current UPC codes are limited to one code, however RFID codes sit on the opposite side, i.e. they're so long that they come with a distinct codes. The unbeatable attributes of RFID tags suggest that a product could be independently tracked while it travels from place to place, and finally arrives in the hands of the customer. The system aids companies to combat theft as well as other loss of product.
RFID in textiles Rental - The principal usage of RFID in rental of textiles has, to date focused on the automation of the garment handling process, which includes check-in, sorting and payment. RFID systems for textile rental can reduce the need for manual labor, producing a typical ROI of less than two years. In addition, RFID systems are extremely precise and can result in significant increases in satisfaction of customers.
. The check-in of soiled clothes can be carried out inside the bags that are delivered to customers, reducing time and improving precision.
. Clean clothes can be easily or semi-automatically sorting, saving substantial cost of labor.
. RFID can automate garment collectors on customer premises and dispensers, allowing further reduction in the cost of the end-customer and a rise in the margins of textile services.
Numerous Fashion Apparel & Textile companies that have many stores - are in the process of making strides to streamline their supply chain, and optimizing sales forecasts as well as distribution. They are seeking ways to increase the market share and revenues by adopting new methods of managing their inventory and stores. RFID is now the central element in their strategy decision-making.
This technology can determine the total amount spent on products in awkward situations in a way that is automatic. This reduces cost of manoeuvring, speed up the inspection process, reduces down the number of errors in the registers, increases customer satisfaction , and lowers pilfering. Retailers with RFID can gain excellent insight into store operations, such as the information about back room stock including stock outs, stock levels and places of inventory within the store. This improves the customer service lead and initiatives to ensure the safety of commodities.
Since all of the products come with RFID sensors of RFID, merchants can have physical evidence of inventory counts daily or as needed. When inventory counts are made it is possible to complete them in just a few minutes, without human involvement. Retailers can save in the form of millions of dollars each year, by reducing physical counts.
Additional security for goods and improved visibility and reduction in cost of mobile products can be achieved through RFID tags. They are perfect for sending correct commodities to the right location in a timely manner. The efficiency Supply Chain's effectiveness Supply Chain not only reduces workforce, but also boosts sales.
Products can be identified and tracked with RFID tags. For instance, tracking assets generally leads to better commodity management in retail stores. RFID can identify the source of change and manufacturing and help in stopping pilfering.
RFID is not a new concept. The problem was always to figure out the appropriate time to implement the technology in your specific supply chain model.
The technology itself gives the possibility of scanning many objects simultaneously since it doesn't require a separate lines of view for every item. For example, a pallet at a warehouse with 10 cases can be scanned at once and reads all the cases simultaneously, which includes those in the middle of the pallet that are hidden from view by humans. Furthermore, the capability to save more data on a tag rather than an ordinary bar code permits the use to the electronic product number (EPC) in order to label the item by their unique identifiers.
Numerous opportunities in the areas of batch management, inventory management, and logistics are available. One potential benefit of RFID is the automation of basic tracking of goods. The current manual processes require workers to record and scan information as objects move. RFID can assist in this. For example when an entire pallet of yarn is marked with an RFID tag and your forklift comes with an RFID reader installed, your driver is immediately aware of the contents of that pallet once he gets close enough to allow the reader to talk to the RFID tag. In this way information, he can determine where the pallet is. When it's time to add a knitter yarn RFID assists in locating the particular pallet that is stored in the warehouse. It also identifies the location it was relocated, and informs the driver of the present location.
Another benefit comes related to control of the batch and control. In particular, the chance mixing many yarns on a knitting machine can be minimized, since you can now match a specific amount of yarn to the knitting machine as well as the production order. The knitting machine will inform the user if the yarn that is being inserted into its perimeter isn't correct.
The data carrier and the communication device are not required to be connected physically. A common retailer is delighted to realize that instead of walking along every lane of the warehouse or in the store in order to look over inventory employees can do the work within the same place and calculate inventory in a matter of minutes. Read/write capabilities can be performed in one assembly line, or remote across continents.
Mobile-tracking devices can be used again or destroyed, based on the specifications in RFID operation. In comparison to the barcode system which has a between 2 and 3 percent fail rate RFID has the ability to get 100% scanning in the event that an item is initially scanned. Many tags are read simultaneously. "Cluster Reading", as the process is referred to can improve the process of data piling significantly.
RFID enhances the ability of retailers to scan through all kinds of weather, and also through different environments such as metals or bodies of water, as well as dirt. This capability of RFID easily surpasses barcode scanning, which typically isn't able to do so. The total costs of scanning processes are cut down by RFID and because RFID increases the accuracy and availability of data, these less expenses can be converted into savings in time and cash.
Additionally, the benefit of logistics comes from the automation of the manifest while the container is loaded. When a fabric roll is transported through the dock door with RFID into the container, it will be added automatically in the manifest. If the truck go through another canopy on its exit from the yard, you could be able to match the contents of the truck to the manifest.
0 notes
Text
youtube
ADS-B Receiver - Digilogic Systems
Automatic Dependant Surveillance-Broadcast (ADS-B) Receiver is a JSS 55555-approved ruggedized product developed by Digilogic Systems, that decodes signals from ADS-B aircraft transponders to determine various information like Latitude, Longitude, Altitude, etc, adhering to ICAO standards.
Leveraging NI Hardware and Digilogic’s expertise in ruggedization and algorithm implementation, this ADS-B receiver kit stands out as a unique product. The kit includes an antenna, RF frontend, and an ADS-B receiver equipped with a licensed application.
Digilogic's ADS-B Receiver offers dual redundant receivers, real-time flight data, built-in GPS connectivity, remote receiver configuration, and easy LAN connectivity for live tracking, making it a standalone unit for network data retrieval.
In summary, the ADS-B receiver from Digilogic Systems is a rugged, reliable solution specifically designed for defense and civil aviation. Compliant with international standards, Digilogic's ADS-B receiver enhances situational awareness and plays a critical role in aviation safety and operational efficiency. Additionally, the product offers advanced connectivity, synchronization, real-time data capabilities, and remote configuration.
For any queries (or) to request a quote, please contact us. Phone: Hyderabad: (+91) 40 4547 4601 Bengaluru: (+91) 80 4975 6034 Website: https://www.digilogicsystems.com/ Email: [email protected]
Stay connected with us on our social media channels for the latest updates! LinkedIn: https://www.linkedin.com/company/digilogicsystems/ Facebook: https://www.facebook.com/digilogicsystems Instagram: https://www.instagram.com/digilogic_systems/ Twitter: https://x.com/DigilogicSystem Youtube: https://www.youtube.com/@digilogicsystems
"Experience Seamless Air Traffic Management with Digilogic's ADS-B Receiver"
#adsbreceiver#aviation#aviationproducts#avionics#digilogicsystems#testmeasurement#testautomation#digilogic#innovativesolutions#Youtube
0 notes
Text
Spy Planes & UAV’s Above Europe
✈️🌍 A Helpful Guide 🌎🛩
-
🛩Forte : RQ-4 Global Hawk

An UAV that has been a constant figure over the Black Sea and Eastern Ukraine since long before the war. People have been watching it consistently for at least a year. Nothing is certain in life, except death and Forte.
The RQ-4 Global Hawk is a high altitude and long endurance UAV that collects imagery intelligence (IMINT). (That means it takes pics📸).
It can fly for up to 30 hours in a single go and usually launches out of Sicily in the Mediterranean. Sometimes elsewhere.
-
🛩 Yank : The Guardrails

The Guardrails collect signals intelligence (SIGINT).📡 They usually fly in Lithuania just north of Kaliningrad and Belarus. They are modified Beechcraft.
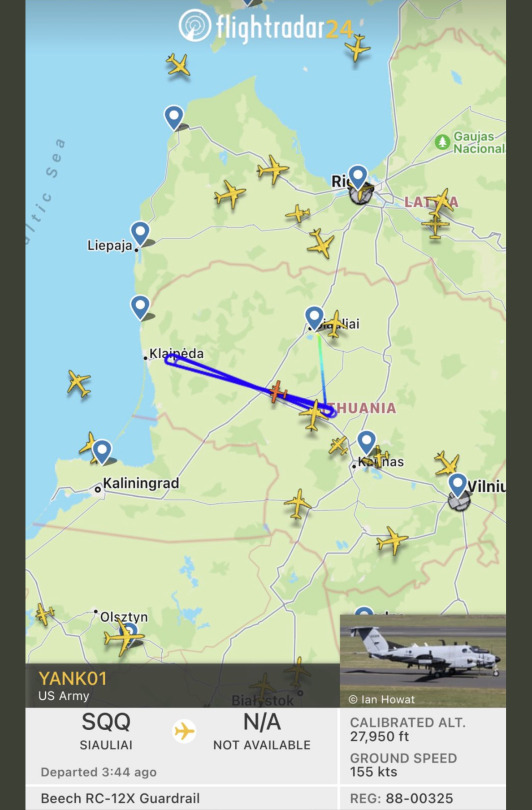
Kinda goofy looking, but an endearing little spy plane nonetheless.
-
🛩 Jake/Homer (Occasionally Different Names) : The Rivet Joints

Unlike Forte and the Yankies, the Jakes and Homers pop up in a lot of places around Europe. It usually launches out of Mildenhall and I’ve seen it checking out Kaliningrad, Murmansk, and the Black Sea. One time Russia even released a missile at/near it, which made headlines.
When the Jakes and Homers check out Murmansk, they usually take a stratotanker with it. It also usually turns its transponder off when it gets up there.
Rivet Joints do a lot of things related to intelligence. Per Wikipedia: sensor suite allows the mission crew to detect, identify and geolocate signals throughout the electromagnetic spectrum.
The Jakes and Homers have a lot of diverse adventures, basically. And sometimes they’re not even called “Jake” or “Homer” at all!
-
🛩The Bombardier Challenger: aka Totally Not a Spyplane (It Is)
This is a sneaky one that can look like normal traffic unless you click on it and see its weird path. It usually stays near Moldova over Romania. Sometimes it does mix it up a bit and heads towards Belarus and Kaliningrad.
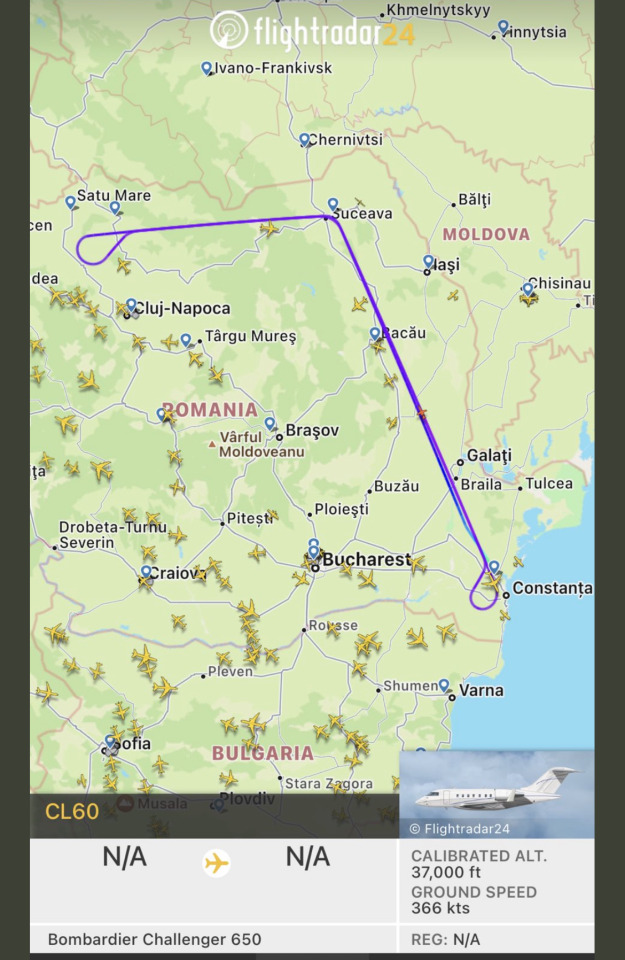
This is likely the one that has Aerial Reconnaissance and Targeting Exploitation Multi-Mission Intelligence System (ARTEMIS). But it’s mysterious so 🤷🏼
-
🛩NATO: The Sentry.
She has the best loops in the business!

The Sentry is an AWACS (Airborne Warning and Control System). It does… everything. Weather surveillance, command, control, and communications, and so on. 📡
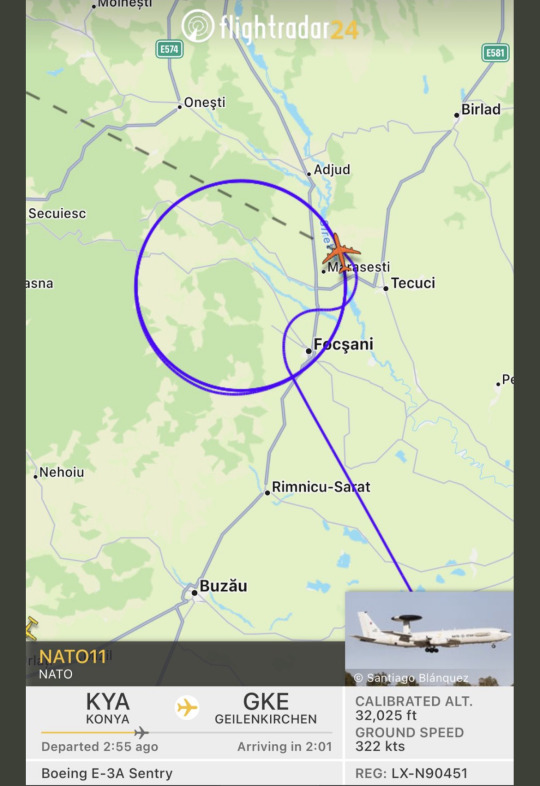
It usually circles over Romania coming from Konya. It does sometimes circle elsewhere.
-
🛩The Swedish Air Force Gulf Streams
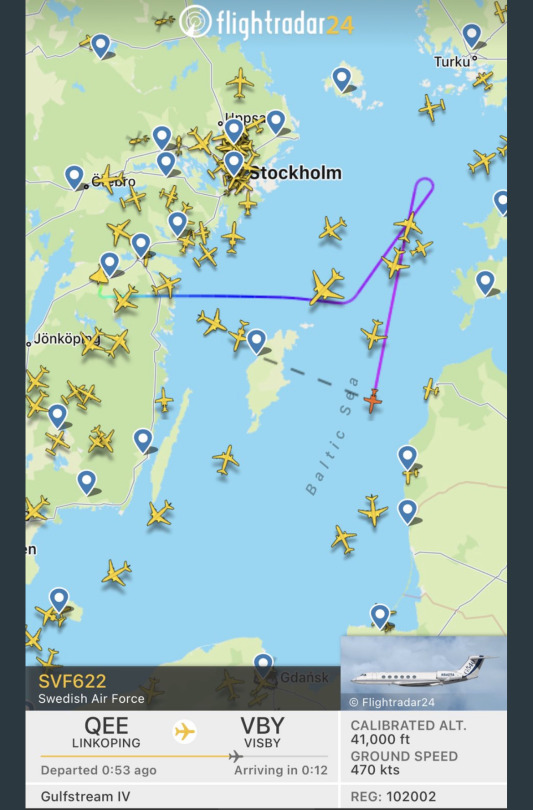
Another modified passenger aircraft that tends to hang out up in the Baltic Sea checking in on Kaliningrad. Sometimes these could just be passenger planes, but these tracks can be sus! And these planes can be easily modified.
-
🛩Northrop Grumman E-8 Joint Surveillance Target Attack Radar System (Joint STARS)
It also does a lot of things. Per wiki: it tracks ground vehicles and some aircraft, collects imagery, and relays tactical pictures to ground and air theater commanders.
-
🛩 Saab 340 AEWCS

Swedish AEWCS plane. Funky lookin little dude. Similar to the Sentry, but with some limitations.
6 notes
·
View notes
Audio
Circuit des Yeux | Vanishing
I cannot believe The vanishing is happening!
The goodbye point The goodbye light Goodbye to our arsenite Goodbye hands touching where it hurts Goodbye laugh tracks of ancient works Goodbye dog Goodbye thought Goodbye to this memory spot
Goodbye to the evidence you saw It wasn't fiction even though the rememberance is small Goodbye to a mother's call at dinner time Goodbye to the sun's participating shine Goodbye passive transponder in the night Goodbye to the aircraft taking flight Goodbye to the puddle in the ground We didn't know each other well But you were my mirrored sky
Fading! Falling! Melting! Sinking! Disappear! Zero axiom is our hero!
#circuit des yeux#vanishing#-io#classic#it's about climate change i think#it slaps#best voice in the game#idk which game but
11 notes
·
View notes