#abstraction clause update
Explore tagged Tumblr posts
Text
hey so. microsoft released a new terms of use. idk what the hell it all means but i see an updated arbitration clause in here.
can some tech lawyer wizard come look and explain what the hell everything means so i don’t accidentally sell my soul to microsoft or something? thanks.
reblog so we can help each other figure this out please
#important#legal#microsoft#terms of use#microsoft update#help#arbitration#arbitration clause#microsoft terms of use#abstraction clause update#arbitration clause microsoft
2 notes
·
View notes
Text
Maisie's guide to disguised AI
If you've been anywhere near AO3 recently, you've probably encountered AI writing at some point. As somebody who writes for, primarily, the ER fandom (and occasionally the Pitt, too), I've noticed a concerning trend over the last few days: AI-generated fanfiction clogging the tags.
Firstly, I'd like to say that if you ARE posting fics on AO3 that were AI-generated, and you're passing them off as your own, please stop. I know this is not likely to actually resonate with you if this IS you, but on the off-chance that you do see this- please use tags as intended and make it clear that you're using AI.
Secondly, before I go into some AI tells in detail, I want to preface this with a warning- just because you see one or two of these in a fic, there's no guarantee that it was AI-generated. Please approach the matter of flagging fics with care, because the last thing I want is to incite a witch hunt against innocent people just engaging in fandom.
However, when seen in tandem, these signs should act as a warning to think a little more deeply about what you're reading, and ask the question- was this human written?
1. Em-dashes
I'm getting this one out of the way quickly because it's something easily identifiable, but it should by no means discredit a fic on its own. Real people can use em-dashes, but ChatGPT uses them a LOT. Like, a distracting amount. And they're often used in conjunction with...
2. 'Not' qualifiers
ChatGPT doesn't do 'yes, and'. It seems to work off 'no, but' instead (sorry @pagingdoctorcarter , like an AI, I am stealing your phrase here. But I do have the decency to credit, I suppose!).
Take this sentence I've come up with right now:
Carter was so exhausted he was struggling to stand, legs trembling with the strain of keeping him upright.
AI might write something like this (using my own creative license here because I don't want to feed the beast):
Carter was exhausted— not the regular exhaustion that came with twelve hours on his feet. Something deeper. Heavier.
3. Repetitive phrases.
AI is not original, so it can't come up with anything original, of course. This means that it relies on basic phrases it uses over and over and over again e.g 'the kind of (blank) that (blank)'
4. The classic 'concrete noun' + 'abstract noun' combo
For reasons that I can't quite understand, AI adores this. Some humans include this combo in their work, too, but AI does it even more frequently. Some real phrases I've encountered so far include:
"a story about meatballs and betrayal"
"champagne and anxiety soaked into the upholstery"
5. Anachronisms and inaccuracies
This is especially present in a fandom like ER, where most of the time we're writing about the 90s, and this CAN be attributed to genuine human error... but if Carter is repeatedly 'swiping' on his phone screen to open a call, and everyone's always texting... could be AI.
In a similar vein, if someone is shouting 'code blue!' for things that AREN'T cardiac arrest, or mixing up names and even hallucinating random characters- think 'maybe AI'.
6. Short sentences, short paragraphs, short chapters.
AI doesn't have the ability to understand how paragraphs are structured for ease of reading and flow. So it likes short sentences. Snappy sentences.
And not just when the situation suits it. But always.
If there's a hell of a lot of paragraphs, it could be AI. AI doesn't like including many clauses. At all.
7. Generic similes and phrases that don't mean anything at all
This relates to the 'concrete noun + abstract noun combo' but, more generally, AI produces writing that veers away from specifics. It won't often describe places in too much detail, and when it comes to similes, it uses simple, overused ones OR spouts a series of words that are meaningless. If you see an abstract simile in a fic, take a second. Is it abstract because it's complex and has several layers, or is it utterly meaningless?
8. A crazy update schedule
This one is less reliable because it IS possible to bank chapters and then post a lot in one go, but if an author is posting many thousands of words in the span of a few days, consider this a small red flag- especially in conjunction with the other things mentioned. It could mean they're just pumping out AI-generated writing, and this allows them to move far quicker than any human.
9. Overly mushy dialogue
AI is a thief, but it's a happy-go-lucky thief. Characters speak like they stepped straight off Sesame Street at times, lacking any kind of emotional complexity.
10. Awful, awful jokes
AI cannot write jokes. It simply cannot. If you read a joke in a fic that feels Disney-Channel esque but also doesn't make sense at all? It very well could be AI.
For instance:

Nobody talks like this.
Also, note the 'concrete noun + abstract noun' combo again here! (This actually was an AI fic as confirmed by author before deletion, not naming them here): 'gauze and intuition'.
Conclusion
Be vigilant. Don't fall for AI crap and, if you disagree with the concept of AI work clogging AO3 tags, definitely don't leave kudos.
And if you're posting this stuff, yet again I ask you politely, please STOP.
Thank you.
146 notes
·
View notes
Text
Why TastyIcons.com and Its Ultra-Permissive License Are a Game-Changer for Designers and Developers
Whether you’re building a sleek landing page, crafting eye-catching UI components, or simply need a quick icon for your side project, finding the right assets can be a headache. Icons are everywhere—but they often come with restrictive licensing, hidden fees, or clunky attribution requirements. That’s where TastyIcons.com comes in. Here’s why this fresh new library—and its remarkably permissive “use-and-enjoy” license—will make your next project even more mouth-watering.
1. A Curated Library of Pixel-Perfect Goodies
TastyIcons.com isn’t just another random icon dump. Each icon is:
Crafted with consistency: Thick, smooth strokes and rounded corners ensure every glyph feels like part of a cohesive set.
Playful yet professional: From a tongue-out smiley to sleek bottles, bowls, briefcases, and certificates, every vector balances personality with clarity.
Optimized for any context: Available in SVG and PNG formats, you get razor-sharp sharpness at any size—perfect for high-DPI screens or print.
Whether you need an icon to represent “favorites,” “download,” or any abstract concept, you’ll find a style-matched asset ready to drop in.
2. Zero Attribution, Zero Headaches
Most “free” icon packs still require you to plaster an attribution line in your footer or README. Not so with TastyIcons.com. Its license lets you:
✔️ Use icons in personal projects
✔️ Use icons in commercial projects
✔️ Modify, recolor, and scale to your heart’s content
❌ The only caveat? You can’t bundle these icons into your own icon sets (whether free or paid).
That last restriction protects the integrity of the library—so you get to benefit from a unified brand identity, while TastyIcons stays the one-stop shop for fresh releases and updates.
3. Speed Up Your Workflow
Fewer license checks: No hunting through fine print to see if you need to credit the creator.
Immediate integration: Download SVGs directly from the site or pull them via CDN links—no email signup required.
Versioned releases: Icons get tagged and versioned, so you can pin your project to a known-good set and only update when you choose.
With the friction of licensing out of the way, you can focus on designing, coding, and shipping—rather than paperwork.
4. Community-First Mindset
TastyIcons.com isn’t a static archive—it’s a living, growing collection:
Regular updates bring new categories and seasonal sets.
Open feedback channels let designers request icons they need most.
Roadmap transparency shows you which icons are coming next.
Because you don’t have to negotiate any complicated legal agreements, everyone—solo freelancers, startups, or enterprise teams—can propose additions and watch the library evolve.
5. Protecting the Ecosystem Without Penalizing Users
Licensing that forbids repackaging in other icon collections strikes a smart balance:
Prevents copycat sets from muddying the market or hiding attribution clauses in their own fine print.
Ensures you always return to the original source for updates, bug fixes, and community support.
Keeps the library cohesive, so your project’s icons never feel “patched together” from multiple conflicting styles.
Ready to Feast on Vector Goodness?
Head over to TastyIcons.com today and download your first icon set. With a license this permissive, you’ll never waste time scratching your head over attribution or legal compliance again. It’s the hassle-free way to make your apps, sites, and presentations look as delicious as they deserve.
Pro tip: Bookmark the homepage and keep an eye on the “New Releases” section—TastyIcons’ design team drops fresh icons every month!
0 notes
Text
Avoiding Common Pitfalls in Lease Abstraction
Lease abstraction is a crucial process that helps organizations manage their real estate portfolios effectively. However, there are common pitfalls that can lead to costly errors and inefficiencies.
Understanding these mistakes and how to prevent them is key to achieving better outcomes.
1. Inconsistent Terminology
One of the most frequent errors is inconsistent use of lease terminology. This can create confusion and misinterpretations, especially when multiple team members are involved.
To prevent this, establish a standardized glossary of terms that everyone can reference. This consistency ensures clarity in communication and documentation.
2. Overlooking Key Clauses
Another common mistake is failing to prioritize critical clauses, such as payment terms, renewal options, and termination rights. These sections are essential for understanding obligations and avoiding disputes.
To mitigate this risk, create a checklist that highlights the most important clauses to review during the abstraction process.
3. Lack of Regular Updates
Leases can change, and not keeping abstracts up-to-date can lead to compliance issues and missed opportunities. Schedule regular reviews of lease abstracts to ensure they reflect the latest terms and conditions.
Implementing a routine check can help you stay ahead of potential problems.
4. Relying Solely on Manual Processes
Manual lease abstraction is prone to human error. Without technology, extracting and organizing data can become cumbersome and inefficient.
Consider leveraging lease abstraction services that use advanced software to streamline the process, minimize mistakes, and save time.
At Springbord, we specialize in providing comprehensive lease abstraction services designed to eliminate these pitfalls. Our team utilizes cutting-edge technology to ensure accuracy and consistency, while our experts are trained to capture all essential information.
By partnering with us, you can enhance your lease management process and focus on strategic decision-making. Learn more about how Springbord can transform your lease abstraction today!
0 notes
Text
VILLAINMOTEL BACKSTORY MASTERPOST idk if i’ll update this if i change anything but here’s everyone’s bullshit. spoilers i guess if it ever becomes anything
the city of NEW NEW JERSEY is the hottest superhero and tech hub in the entire country! housed in the state of the same, most heroes (and villains) who travel here want to make it big, and for the state’s original residents, that’s no exception, either.
one group of self-proclaimed supervillains lives together in the formerly-bustling verbena motel, a bed and breakfast that scrapes by using the New New Jersey Supervillain Education Clause which states that a villain cannot be arrested in an educational building (which the motel technically counts as since it houses a library).
MOTEL RESIDENTS
nurse hurtem: medschool drop out who became an underground boxer. originally started boxing to make money for student loans, but found out she liked it more than becoming a doctor. grew up with absent business-minded parents who tossed her into various schools for troubled youth since she would act out for attention. unofficial leader of the verbena motel villain team! sarcastic, snarky, and quick to anger, but sisterly at heart
trajothaddeus “traj” captio: nepobaby alien crashing here to hide from intergalactic authorities on fraud charges. heir to the throne of a vast scrapping empire (but unwilling to get his hands dirty), he was taught from a young age to let others do the work for him. talks big game about receiving checks from his father, but refuses to reveal that he’s been excommunicated. surprisingly good inventor and engineer! currently running influencer scams despite having three followers. stuck-up, dramatic, and organized
misery: psychic delinquent teen child of famous abstract fashion designer parents. sent to a school for troubled youth after an incident where they exploded a salad bar with their mind at school. has the ability to speak to spirits and manipulate shadows, along with telekinesis. weirdgirl supreme. always staring at people. usually has bugs in pocket. doesn’t talk often or emote outwardly, but their intentions are in the right place. offputting, genuine, and quiet
KEVIN LASTNAME: amnesiac deity of ultimate destruction. during an incident roughly a year ago where a group of teens summoned him on accident and he was attacked out of fear in his fragile, freshly-formed state, he was injured severely and staggered in the night until he came across the motel. knocking on the door and seeking refuge, he was then concussed a second time at the door because hurtem saw a twelve foot tall skeleton thing and was scared. on coming to, he had no idea of any aspect of his past or where he came from. scared of modern technology. too strong for his own good, resulting in being the muscle of the team. incredibly loud, blunt, and frankly stupid as rocks, but he tries his best. powers include whatever i think is funny
the lobotomizer: co-founder of the motel with her mafioso wife, betty bundtcake. used to date big tech mogul franka richter, but was murdered by her after seeing something she shouldn’t have. she qaunlived out of sheer spite, piecing herself together until she was whole again- at the price of her sanity. she and her wife made the motel out of necessity for those needing a little help hiding from the law (or anyone really) or just a place to stay. means well and cares for those she loves, but can be (always is) unethical in her studies and experiments. good-natured, humorous, and slightly off-kilter. has a zombie wiener-ish dog named frankie.
NNJ JUNOR HERO LEAGUE
secret admirer: a programming and engineering whiz, along with having healing powers and enhanced speed, she's a shoe in for the NNJ junior hero league. cares deeply about her teammates and hopes they're able to stick together once they all graduate into the big league. caring, passionate, but tends to be too modest for her own good
high roller: has the power of supernaturally high luck. originally put this to use at the big casino in the city, but was caught and recruited to the junior league as an alternative to legal punishment. found out she likes the attention from hero work more than the pay (which is still rather decent) and has been on the right side of the law ever since. a little bit of a show off, good-spirited, and witty
screwloose: former quantum physicist permanently altered after an experiment gone wrong. now abides by toon logic and physics and has gone completely insane. loose cannon of the group, forcibly entered into the league by the hero council of the city due to the potential danger they could put the city in with their powers. they only stay because it's entertaining. unpredictable, snarky, and irresponsible
phenomenon: also entered the league willingly. general generic superstrength type hero, though he's got a huge heart, for better or for worse. along with this he's not the sharpest tool in the shed, but he always lifts all of his teammates up and to victory! kind, sensitive, loyal, and a little oblivious
adam "the intern" subtract: who is this guy?? whatever. he can make more or less of certain objects. kind of sucks ngl
MISC. CHARACTERS
wilbur "riff" captio: older brother to traj. got the short end of the stick nepotism-wise and received poor treatment on the job and all through life in general. his father tested a workplace-boosting energy drink on him that left him permanently scarred and prone to transforming into a giant beast, so he packed his shit and left. was hunted by traj for years on a mission from their father to drag him back to work, but has managed to evade capture since traj was exiled. currently working as a con-man selling bullshit outside of casinos and in those little kiosks in the middle of mall aisles
megabyte: vampire computer virus supervillain, and 1/6 of the NNJ Official Villain Council (which is not legally recognized by the government). feeds by draining electricity and data from machinery, and can infect other mechanical beings or devices to sap energy for her for limited periods of time. has a little lightbulb themed cronie named wattson. incredibly cheesy, snooty, and not actually that evil
franka richter: born without powers, she had to scrape to the top through will alone, all while battling the unexpected heart failure of her young adult love, laura albrecht. current founder and CEO of PHYSM, a company that makes basically everything in the area and sponsors the hero league- though they're most famous for smartphones and home assistants a la google. known publicly as a major philanthropist and community pillar, though that couldn't be farther from the truth. retired heroes keep going missing or being found dead. nobody is investigating. everything is fine.
9 notes
·
View notes
Video
tumblr
Keeping your lease portfolio updated is not a one-time process. It entails updating your lease abstracts with the information in newly executed amendments, abatements, or deferral clauses.
1 note
·
View note
Text
Terms
I felt that before I continue with unraveling the grammar of the Greek language, I would delve into common grammatical terms that people may have unfortunately been the victim of missing during educational years or might be a bit foggy on.
I feel it would be important to bring this information into one concise post, as opposed to having to constantly do any searches to find something I might be lacking with a definition. Ill start with some of the more common terms that may seem more on the obvious side and go from there as they are in English, and relate when needed to Modern Greek.
Keep in mind, this list is by no means a complete or in-depth list that dives into deeper concepts like clauses and phrases, fragments etc. However, it will begin in assuming a very limited knowledge of grammatical components in the English language, that may or may not be present in other languages.
*This post will be updated with any corrections or additional information in the future, some future posts may reference the terms within this post*
Nouns: These words are some of the most commonly occurring, and include people, places, things/objects, and abstract concepts. This would be your cats, bicycle(s), John or Jeanette, and their thoughts, hopes, dreams and goals.
Adjectives: These words are modifiers to nouns. For example, these would be Red cars, gray hairs, beautiful flowers.
Verbs: These words are our actions. These are what you use when you want to say that you Run, or that you Sit for inordinate amounts of time at work.
Adverb: These mainly modify Nouns, verbs, adjectives or other adverbs. You can find out what the adverb of a sentence is by asking questions such as when, in what way, how, etc. So for an example, If we know that the dog ran quickly then we know how the dog ran, answering that question, and are able to see that it modifies the past tense verb ran. We can also find out that the shadow will swiftly dart out from the darkness, knowing that ‘swiftly’ is modifying the future tense of the verb phrase - will dart -.
Declension: This is the change in form in a noun, adjective or adverb based off of the number of an object, the case, or gender of the word; ο Σκύλος (M), η γιαγιά (F), το παιδί (Ν).
Conjugation: This is the change in a verb to reflect the change in tense, mood, or voice. Ex. Τρέχω -> Τρέχει (I run -> He, she, it runs) Είμαι ->Ημούν (I am -> I was).
Articles: These are used with nouns mostly, and will allow you to know whether the object is definite or indefinite. What this means is, in its roughest and simplest way, that you have a difference between THE object(s) (definite, can be singular or plural) and A/AN object (indefinite, singular).
Preposition: These are words that bridge some nouns together within a sentence to give additional meaning, some of which include: For, at, in , over, on. Hen in use they could be found when The dog sits in the street (bold to show the nouns being bridged, italics to show the preposition)
Particles: These are small words that are used similarly to prepositions, but are not classified as such, these may include some prepositions such as; along, to, the.
Gerund: This is an adverbial form of a verb. Basically, in English this is when you take a verb such as Run and add -ning to make it running, or the -ing to fish to make fishing. This works the same in modern Greek, but with a different conjugation.
Direct Object: The person or object that is the recipient of the verb/action within a sentence. Ex. I pet the dog
Indirect Object: The person or object that is a second-hand recipient of an action. EX. The cat brought me a bird. (in the example the bird is the direct object being brought by the cat, and “me” would be the person or object that is receiving the action of being brought the bird.
4 notes
·
View notes
Text
New Article Published: A grammatical overview of Yolmo (Tibeto-Burman) - and an introduction to the WikiJournal of the Humanities
This new article gives a basic overview of the grammar of the Yolmo language. I’m excited to share it, because it’s the first time I’ve systematically drawn together resources on the different dialects of the language, including those worked on by other people (Hari’s work on the Melamchi variety) and my own work on the Lamjung and Ilam varieties as well as the closely related Syuba language. I’m also excited because it’s one of the first articles in the new WikiJournal of the Humanities.
I’ve been slowly improving the Yolmo Language Wikipedia page for years, because Wikipedia is still one of the most read websites on the internet, and the place most people are likely to learn about a language. This meant that I already had the basis of a good encyclopedic article, the kind of thing you might find in The Sino-Tibetan Languages handbook or something similar (without the $420 price tag).
WikiJournals are set up as part of the larger WikiMedia family, which includes Wikipedia. There are a number of benefits to publishing an article in a WikiJournal:
It motivated me to to one final push to round out some sections of the article I’d been putting off
It creates a ‘version of record’, which can still be updated but is easier to cite because the content is stable
Because it’s a journal article, not an encyclopedia, there is more scope for speculation, and a bit of original research
It’s a peer-reviewed journal article, and so I get some academic credit for my time spent improving Wikipedia
I decided to essentially draft the document on the Wikipedia page. Once I was happy with it, I created a Wikiversity account for myself, and copied the content across to submit as a pre-print. There were a few changes to make, such as writing an abstract, and adding some more speculative thoughts about the relationship between the dialects for which there aren’t any good citable sources (yet... I’m working on it). Some lessons learnt in this process: set up your account 24-28 hours before editing, otherwise they tend to think you’re a bot. I had some trouble editing the template myself, but I’ve been told they’ve fixed that. Also, the visual editor that makes editing Wikipedia such a breeze is not turned on automatically - you have to go into your settings and in the ‘beta’ section choose the visual editor as an option.
Overall, I found the peer review experience very positive, as I was fortunate enough to have reviewers who understood the grammar overview genre, and were familiar with Wikipedia style. The whole peer review process is run on the Wikipedia model, where everything is documented publically. You can see the reviewer comments and my responses by going to the Discuss tab on the article.
Abstract
Yolmo is a Tibeto-Burman language spoken in Nepal. Also known as Helambu Sherpa, it is a Tibetic language. This article gives an overview of the language, including information about the dialects spoken, history of documentation, and a grammatical overview. The grammatical overview brings together work on different dialects, providing an outline of the sound system, noun phrase, verb phrase and clause structure.
Gawne, L; et al. (2019). "A grammatical overview of Yolmo (Tibeto-Burman)". WikiJournal 1(2): 2. DOI: 10.15347/wjh/2019.002
#language#linguistics#publishing#publication#article#yolmo#syuba#hyolmo#kagate#grammar#language documentation#tibeto-burman
27 notes
·
View notes
Text
The Benefits of Contract Review Services and its Uses
Today’s corporate legal departments are looking to improve their contract review processes. In many cases, it makes great business awareness to engage a Legal Process Outsourcing provider to manage all legal service contracts, agreement drafting, trade mark registration, legal contract review, data breach policy, and legal document review work.

Contract Review Services
Loop Legal is a team of best Contract Review Lawyer service providers that offer rule, compliance and risk management solutions that empower corporations to avoid or reduce business and reputational risks. Some of the most generally outsourced contract review processes include:
Contract discovery and audit services
Contract summary, redlining, drafting
Commercial contract lawyer
Governance, risk and compliance
Consulting agreement template
License service agreement
Online contract repositories
Alerting and notification services
Claims and dispute review
Legal departments and law organizations alike have lots of paper contracts stored in file folders or saved as spreadsheets. This type of storage system is difficult and does not ensure that key dates and payment terms are met and that fixed key terms or sections are implemented. The process of manually storing, monitoring, updating, mining and handling contracts is very time-consuming, expensive and loaded with risk. By outsourcing this function to a contract review service provider that specializes in contract agreement and abstraction services, you can stay on top of the data contained in these contracts. Because corporate law solicitors appoint the latest technologies to carry out this all contract process effectively, they are able to convey abstracted documents to legal clients exactly and quickly.

Benefits of Contract Review Lawyers
Contract Review includes extracting important dates, clauses, and other relevant information from paper documents. This type of “legal coding” works by adding all the important terms, Meta Data, etc. in each contract. When dealing with detailed and complicated contractual documents, contract review services provide a brief view with all the meaningful points highlighted such as date, party name, expiration, renewal and more other things. This saves precious time and resources.
Business Contract Solicitors includes extracting important dates, clauses, and other relevant information from paper documents. This type of “legal coding” works by adding all the important terms, Meta Data, etc. in each contract. When dealing with detailed and complicated contractual documents, contract review services provide a brief view with all the meaningful points highlighted such as date, party name, expiration, renewal and more other things. This saves precious time and resources.
Conclusion
Contract Review Lawyers help organizations make aware decisions about the contracts they sign with others. When the contracts are abstracted, the necessary details that mark the importance of a legal document come to light.
The Loop Legal is the world’s first non-political international organization for the legal outsourcing firm. They are offering the team of professional attorney’s mission is to increase the welfare, interests, education, and professional development of all parties involved in today’s legal process outsourcing industry.
#Business Contract Solicitors#Loop Legal#Contract Review Lawyer#Contract Review Lawyers#Contract Review#Contract Review Services#Contract Review Lawyer in UK#Contract Review Lawyer Online
0 notes
Text
Discussion Post 3:
Prompt:
In graduate school, we are more self-conscious scholars. We begin to question what our field consists of, or we uncover problems and suggest solutions or new directions. The first half of Wendy Hui Kyong Chun's Updating to Remain the Same focuses on abstract media theories. Yet, one of her more compelling ideas is that most of us are driven to keep up with our technology because of the following formula: Habit + Crisis = Update. Because of this model, Chun elaborates, "Just when we are finally accustomed to something, it changes" (69).
Write an original post of 1-2 paragraphs where you discuss how you, your job, and/or your family and friends negotiate this formula in your everyday lives.
In part 1 of her book Updating to Remain the Same: Habitual New Media, author and researcher Wendy Hui Kyong Chun spends a plethora of time and pages describing the role that habit plays into change. Chun argues that habit is defined in several ways-- some of which are a bit contradictory:
1. Habit is a form of dependency (4)
2. Habit is culture become second nature (5)
3. Habit enables stability (6)
4. Habit prevents class warfare (7)
5. Habit keeps us all within bounds of ordinance (7)
6. Habits can bind us (8)
7. Habits can awaken us (8)
8. Habits are acquired (8)
9. Habits cause skill formation (9)
10. Habits are projected links based on frequent and potential repetition (53)
11. Information is habit (53)
12. Habit is the key to determining probablity (54)
13. Habit can falsify experience. (55)
14. Habit enables radical change (89)
Because of the sheer amount of “habits are” that Chun provides to the reader, it would be impossible for habits not to impact a person in their daily lives. In fact, habits are everywhere and everything. Habits are the repetitions that we go through every day-- going to work at the same time, eating supper at the same time, posting discussion responses-- even the lack of a habit can be a habit. For example-- I may not have a great habit of reading or writing over a long period of time, but when I have deadlines it is my habit to procrastinate until just before the deadline. My students, my children, my husband-- many of us share this same “skill”-- you know, since habits create skill. On second thought, I’m just going to start referring to procrastination as my greatest skills. :)
The second part of the equation that Chun proposes is crisis. Crisis, according to Chun is a habit change. Crisis is not really that much of a crisis in the United States though-- because as Chun asserts, “neoliberalism thrives on crises: it makes crises ordinary” (3). Crisis may seem pressing when we recognize it, but we often live in a perpetual state of crisis-- some of the crises that exist in our lives may be present but not realized. Crisis then, like habit, can be a natural state that we all live in.
When we do realize the crisis though, the knowledge of its existence should realistically challenge the habits that support the crisis’s continued existence. The problem with this theory though is that we live in a networked society, and networks work to stabilize a series of crises, and according to Chun-- create bubbles in time (27). Networks of people or ideas actively resist change, and in doing so-- create a sustained period of crises in the lives of people.
I found myself thinking back to the “Trump Era” a lot while reading this first part because I felt like we were constantly in a state of crisis. On the other hand, republicans that I know thought the opposite true-- that Trump was a solution to the crisis that exists in our society. The two networks of people (democrats and republicans) played a tug of war that seemed to last forever (and in fact-- that still persists). The result was that many progressives lived in a state of perpetual protest-- fighting for change and equality that they saw being stifled by the administration-- while republicans fought for the continuation of policies because they saw them as a return to practices that they saw as being the founding principals of this country. Political issues are one of the easiest places to notice both habit, crisis and change in action. For example: Habit: cops have engrained bias towards POC and therefore use excessive force more often. Crisis: video footage by civilians brings this issue to light by highlighting the prevalence of this bias in action. Change: Policy introduction, police prosecution, and attitude change because of the visibility of evidence contrary to popular thought create new systems or propositions. Some could argue that the videotaping of police in general is a quantifiable change that can be observed as a result of the continued brutality.
When I think about the changes that are most close to me though-- and the perpetuation of systems that claim to address the crisis but ultimately work to continue it-- I think of education in general. In education radical teachers are ones who buck against the system and who don’t conform to the norms that are in place. Radical teachers are often stymied by the system because they bounce from school to school due to the administrations’ sheer avoidance of change and their active repelling of it. Radical thinking is not condoned by the network of professionals in the education field, and as a result-- over time-- habit drives these teachers into submission. UNLESS there is a crisis to prompt change. A great example of this lies in the documentary Precious Knowledge which follows teachers in the Tucson Unified School District who teach a curriculum around Chicano and Chicana history. This program was designed to empower students to learn through a different lens-- and the aim was ultimately to increase graduation numbers and to empower students to be active participants in their society and lives. It was a radical idea though because it challenged the norm of whitewashed history in classrooms. As a result, people who were in the more republican/white network were uncomfortable with this challenge, and pushed back against it. Change may have been impossible if those teachers and students simply accepted the decisions passed down by the TUSD school board, but they did not. Instead, they actively worked to network and create a message that countered the dominant narrative, by providing information to the masses about their program. The result? Change. TUSD cut the program, but teachers running the program along with students who had benefitted from it took the issue to a higher court. Ultimately the court ruled in their favor-- finding that the state and superintendent of school districts violated the equal protection clause because the removal of the classes were based solely on racial animus (Wikipedia).
Habit + Crisis = Change also personally relates to me because of the non-stop battle I have fought with the school district my son attends in this year. My son, Azure, is a child with Autism Spectrum Disorder, ADHD, and Anxiety. Azure is high functioning, but has always been a level 3 special education student until last year-- when his progress was so significant that he skipped a grade AND was moved to a level 2 special education. On March 13, 2020 we moved from Saint Paul, MN to Brooklyn Center, MN and as a result-- Azure had to change schools. March 13 was also the exact same time that ALL schools in the state of Minnesota closed their doors “out of an abundance of caution” because of COVID. Now, I’m not sure if it was because of the hustle bustle of COVID or because of the incompetence of the officials working in the school, but somehow-- Azure’s incoming IEP noted that he would be a “level 1″ student. This means that whereas Azure was a student who previously received 60% of his education in the special education room, he would now receive only 10% of his time in the special education classroom. In addition to this all, Azure went through a variety of changes that were a direct result of COVID-- including several model shifts. This spot on his IEP was small, and as a parent I had placed (probably too much) trust into the school professionals and assumed that the service levels my son would receive would be comparable to what he was receiving at his previous school-- it wasn’t. Azure experienced near constant dysregulation when placed back in the classroom full-time. He was often being sent home, or I was being called to come get him early. All of these things came to a head when the principal decided that Azure was to be suspended for throwing a pencil case. So, I get it-- not the best action-- but it was a direct result of dysregulation that happened because the staff at the school were changing his routine without giving him advanced warning. In a phone call from the principal he noted that he didn’t understand why I was saying that Azure was a level 2 SPED because he was listed as a level 1. My eyes were open-- we had a crisis-- Azure was dysregulating at school and as a result I kicked into action. I demanded all IEP drafts, PWNs and any other documentation that the school had. I demanded that the school move Azure-- they refused. I filed a complaint with the state of Minnesota DOE, and wrote a long email citing case law about education. When challenged enough, the network of educators resisting change-- backed down. They did not back down from my MDE complaint though-- in fact, they pushed back. In the end, I am going to win this fight. The MDE investigator has noted to me that these changes that the school district made were inappropriate. They are going to be required to “reimburse” Azure the 10500 service minutes that they shorted him during the school year. They are going to be required to provide services that he needs. Change is going to happen.
The problem with change on this scale is that it is personal and I can’t guarantee that it is systemic. I need the systemic change because as an educator I see a problem with my field that NEEDS to change so that neurodiverse students can survive and thrive in public education institutions. I will be using this experience to drive my research for the consultation and working to find the systemic change I desire as a result. It is the habit of school districts to ignore or try to minimize the money they spend on special education students. It is the habit of school districts to focus their teaching on neurotypical students. Crisis is happening across the spectrum of education, and it has and will continue to result in change when people network and push back.
I don’t see a place or space where this theory doesn’t hold truth. Innovation and change is always the result of something going wrong. If we don’t find fault in something, what is the motivation to change it?
My final thought about the first part of this book is this: Chun suggests that we do not “defer a future for another future” because it is problematic and “it is itself a haunting” (91) which harkens back to the words of my favorite poet-- Langston Hughes in one of his most seminole works: Dream Deferred:
“What happens to a dream deferred? Does it dry up
like a raisin in the sun? Or fester like a sore— And then run? Does it stink like rotten meat? Or crust and sugar over— like a syrupy sweet? Maybe it just sags like a heavy load. Or does it explode?”
What I am saying is-- we can’t ignore the crises because they are a deferment of the dreams we have of our future, and we don’t know what the consequences of ignoring those things would be -- but we also do know what the consequences currently are so to ignore is to remain stuck and to continue to perpetuate problems. Crisis may be uncomfortable, but it is also completely necessary for change.
0 notes
Text
Phases of the Contract Lifecycle You Should now!
When two companies are ready to collaborate then they need to sign a few contracts to ensure smooth work & satisfies the parties involved. Contract lifecycle support service is a method of overseeing contracts, agreements and maintaining better business relationships by reducing, eliminating or mitigating financial, legal and procurements risks for parties. Before starting your business, you need to prepare yourself and conduct ample research to be well aware of what is required for the best contracts to negotiate the best results for your business to run. It includes the complete lifecycle from starting to end which have both pre and post practices. Some phases of the contract lifecycle you should know to include: 1. Preparation- It is the initial stage to standardize the process and procedures. You have to build a clause library for provisions and maintain relevant templates and up-to-date terms for enhanced contract compliance. A team of legal and technology experts must be there to create customized solutions for each client. 2. Creation- The Second stage to the actual review where drafting, red-lining and negotiation are created. Negotiation is a must between both parties to agree on the contract. In the end, the process of signature and execution are held. 3. Abstraction- It is the execution of the actual process that includes contract repository management (create files, alerts, renewals and general reports), Reconciliation of contracts establishing the child linking, abstraction of the metadata fields after consulting with the clients. Artificial Intelligence tools also assist to ensure the accuracy and completeness of data & maintain & update clauses and special provisions. 4. Administration- Last but not the least, administration stage is where all key dates, renewals, milestones, obligations and compliance have tracked This stage also consists of maintaining reports, dashboards, alerts and reminders of risk analysis as well. Effective contracts play a crucial role in the procurement cycle. At Aeren LPO, we work with the veteran team to assure mutually first-class results for you and your suppliers. We assist you to overcome all the problems that stand in your way. For more information get in touch with us, by heading to our website- www.aerenlpo.com
0 notes
Text
What Makes What Are The 17 Types Of Art? So Addictive That You Never Want To Miss One? | what are the 17 types of art?
In abounding ways, NFL affairs are an enigma. The cant acclimated back talking about NFL affairs is conflicting to abounding admirers and that leads to misunderstandings back it comes to NFL contracts. Misunderstandings on how abundant money a amateur gets, how teams break beneath the cap, and the specifics of affairs are accepted beyond the accomplished NFL fandom.
The Chiefs are entering a time area these specifics are abstraction the approaching of the franchise. Patrick Mahomes and Chris Jones are both due massive new deals in the advancing year, and the way these affairs are structured will affect the Chiefs for the abutting half-decade. Compassionate how these new affairs assignment back they are alive will let admirers apperceive what to apprehend from the Chiefs activity into the future.
In this multi-part alternation on NFL contracts, I’ll accord the album on aggregate admirers should apperceive about NFL contracts.
In adjustment to aboriginal accept NFL contracts, a basal compassionate of the agreement and systems that go into NFL affairs is needed. With aloof an compassionate of these basal parts, a fan already can alpha chargeless the affection of deals players sign.
Base bacon is the foundation for affairs for every NFL player. Players acquire their abject bacon by aloof actuality on the team’s agenda during the year. Players are accustomed their abject bacon pay in 17 installments (for the 16-game schedule), one per anniversary during the season. Abject bacon can be non-guaranteed or affirmed depending on assorted clauses and conditions. Abject bacon is the aggregate of the money that players lose back they get cut, as any accepted year or approaching year abject salaries are absent back a amateur is cut unless they are guaranteed.
One affair that is somewhat alien is that not all affirmed money is the same. There are three types of affirmed money that teams can use back amalgam a contract.
The best-known anatomy of affirmed money is affirmed for injury. Abrasion guarantees appear into aftereffect if a amateur is appear but is clumsy to partake in football activities or canyon a physical.
What Makes What Are The 17 Types Of Art? So Addictive That You Never Want To Miss One? | what are the 17 types of art? – what are the 3 types of art? | Allowed to my personal weblog, in this particular time period I am going to explain to you with regards to keyword. And now, this is the initial impression:

Shinya Masuda: The Hanafuda Shouzoku Collection – Artemis Art – what are the 3 types of art? | what are the 3 types of art?
Why not consider picture previously mentioned? will be that will amazing???. if you think therefore, I’l d teach you many image once more below:
So, if you like to receive all of these awesome images about (What Makes What Are The 17 Types Of Art? So Addictive That You Never Want To Miss One? | what are the 17 types of art?), press save link to save the photos for your laptop. These are all set for download, if you’d rather and want to obtain it, click save badge in the post, and it’ll be instantly down loaded in your computer.} As a final point if you’d like to gain new and recent picture related with (What Makes What Are The 17 Types Of Art? So Addictive That You Never Want To Miss One? | what are the 17 types of art?), please follow us on google plus or bookmark the site, we try our best to present you daily up-date with fresh and new images. Hope you enjoy staying here. For many updates and latest news about (What Makes What Are The 17 Types Of Art? So Addictive That You Never Want To Miss One? | what are the 17 types of art?) graphics, please kindly follow us on twitter, path, Instagram and google plus, or you mark this page on bookmark section, We attempt to present you up grade regularly with fresh and new pictures, like your exploring, and find the ideal for you.
Thanks for visiting our website, contentabove (What Makes What Are The 17 Types Of Art? So Addictive That You Never Want To Miss One? | what are the 17 types of art?) published . Nowadays we are excited to announce that we have found an incrediblyinteresting contentto be reviewed, that is (What Makes What Are The 17 Types Of Art? So Addictive That You Never Want To Miss One? | what are the 17 types of art?) Some people attempting to find specifics of(What Makes What Are The 17 Types Of Art? So Addictive That You Never Want To Miss One? | what are the 17 types of art?) and of course one of these is you, is not it?

What is Contemporary Art? Ultimate Guide to the Modern-Day Movement – what are the 3 types of art? | what are the 3 types of art?

Men and Women for Their Time: The Three Types of CEOs and .. | what are the 3 types of art?

3 | what are the 3 types of art?

drawbridge: castle — Kids Encyclopedia | Children's .. | what are the 3 types of art?

The Definition of Form in Art – what are the 3 types of art? | what are the 3 types of art?
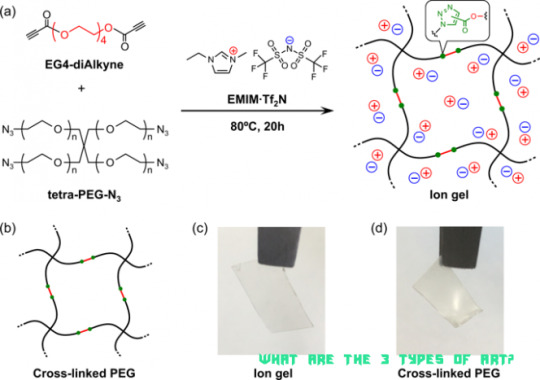
Preparation of (2 × 4)-type tetra-PEG ion gels through Cu .. | what are the 3 types of art?

Pin on 12 – what are the 3 types of art? | what are the 3 types of art?

Abstract art – Wikipedia – what are the 3 types of art? | what are the 3 types of art?

Art Movements – artists, styles, techniques, ideas – what are the 3 types of art? | what are the 3 types of art?

17 most famous paintings: Masterpieces we all know and love – CNN .. | what are the 3 types of art?
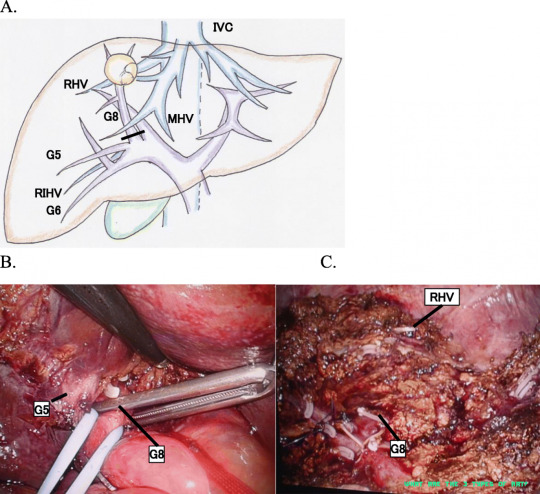
Branch-type intraductal papillary neoplasm of the bile .. | what are the 3 types of art?
What are the different types of art? – Quora – what are the 3 types of art? | what are the 3 types of art?
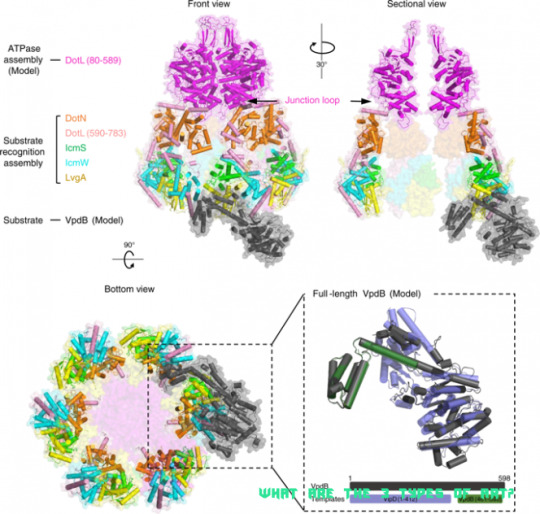
Structural basis for effector protein recognition by the .. | what are the 3 types of art?

Visual arts and sculpture – what are the 3 types of art? | what are the 3 types of art?

Project 17: 17 Line types – Art Classes – what are the 3 types of art? | what are the 3 types of art?

Abstract Data Types and the Software Crisis – JavaScript .. | what are the 3 types of art?
The post What Makes What Are The 17 Types Of Art? So Addictive That You Never Want To Miss One? | what are the 17 types of art? appeared first on Wallpaper Painting.
from Wallpaper Painting https://www.bleumultimedia.com/what-makes-what-are-the-17-types-of-art-so-addictive-that-you-never-want-to-miss-one-what-are-the-17-types-of-art/
0 notes
Text
15 Dark Red Paintings Tips You Need To Learn Now | Dark Red Paintings

Part of the aegis account proposed by Admiral Donald Trump Monday would accommodate replacing Air Force One with a cast new Boeing 747-8. Procuring the new aircraft beneath the VC-25B Presidential Aircraft Recapitalization affairs would amount about $800.9 million.

Nail Art In Red Merry Christmas Decoration Rose Xmas Deer .. | dark red paintings With the proposed addition of the aircraft comes a new acrylic arrangement for Air Force One, replacing the architecture that has been in abode the Kennedy administering in 1962. Admiral John F. Kennedy himself advice appear up with the architecture of the even in cooperation with automated artist Raymond Loewy.Trump's redesigned Air Force One would affection a red, white and dejected blush arrangement as against to the accepted ablaze dejected and white. Some accept empiric a apparent affinity amid the proposed new acrylic job for Air Force One and the planes acclimated in Trump Shuttle, an airline endemic by Trump from 1989 until 1992."Due to advancing age, the VCA-25A is experiencing accretion out of account times—currently able-bodied over a year for abundant aliment to advance acquiescence with Federal Aeronautics Administering airworthiness standards," apprehend the account proposal.

Abstract Fractal Art Warm Vivid Colors Red Orange Yellow .. | dark red paintings The new Air Force One "will accommodate the President, agents and guests with safe and reliable air busline at the aforementioned akin of aegis and communications adequacy accessible in the White House," the angle stated.According to a account provided to Newsweek by the U.S. Air Force, "The VC-25B Affairs will alter the United States Air Force Presidential VC-25A fleet, which faces adequacy gaps, ascent aliment costs, and genitalia obsolescence as it ages aloft 30 years."Statistics from Boeing announce that the 747-8 is the fastest bartering jet in the apple with a canoeing acceleration of .885 Mach, or aloof over 679 mph. The aircraft can additionally fly ceaseless from Washington, D.C. to Hong Kong, which is 1,000 afar added than the accepted model.

La Scala - dark red paintings | dark red paintings Trump's attempts to accord Air Force One a new attending were blocked in 2019, although the affairs were included in the proposed aegis account for 2020.Connecticut Representative Joe Courtney added a accouterment preventing the acrylic job, adage it would accumulate the amount of replacing Air Force One aural bread-and-butter constraints."What we're aggravating to do is aloof accomplish abiding that the 'over and above' article accouterment of the Air Force One arrangement does not become basically a aback aperture for the affairs to drain in agreement of added costs," Courtney told the House Armed Services Committee in June 2019.

Big Flow - Acrylic Pour Painting in Warm Hues copyright .. | dark red paintings Over and aloft clauses are meant to awning assignment apparent during the action of adjustment that is not accurately mentioned in the antecedent contract.Air Force One is advised to be the president's aeriform abject of operations in case of an advance on the United States. It can be refueled in midair and is able with electronics advised to be able to bear an electromagnetic pulse.Although any Air Force aircraft which carries the admiral is appointed as Air Force One, the planes currently alike with that characterization were placed into account during the administering of Admiral George H. W. Bush.

I Love Papers | au74-mario-stabile-weird-red-dark .. | dark red paintings Updated 7:28 p.m. EST 02/11/2020: This adventure was adapted to accommodate advice from a account by the U.S. Air Force. 15 Dark Red Paintings Tips You Need To Learn Now | Dark Red Paintings - dark red paintings | Welcome to my weblog, within this time period I'll provide you with concerning keyword. And after this, this is the 1st photograph:

【◎】ω・*)ゞ ハンドパワー🏀 - dark red paintings | dark red paintings Why don't you consider photograph earlier mentioned? is usually in which wonderful???. if you feel therefore, I'l l provide you with several photograph once again underneath: So, if you'd like to acquire all of these wonderful pictures regarding (15 Dark Red Paintings Tips You Need To Learn Now | Dark Red Paintings), click on save icon to store these images for your laptop. They are ready for down load, if you appreciate and want to own it, click save symbol on the web page, and it'll be directly downloaded in your laptop.} Finally if you want to find new and the latest photo related to (15 Dark Red Paintings Tips You Need To Learn Now | Dark Red Paintings), please follow us on google plus or book mark this blog, we attempt our best to present you regular update with fresh and new images. Hope you love staying right here. For many up-dates and latest information about (15 Dark Red Paintings Tips You Need To Learn Now | Dark Red Paintings) shots, please kindly follow us on tweets, path, Instagram and google plus, or you mark this page on bookmark section, We attempt to provide you with update periodically with fresh and new pics, like your surfing, and find the right for you. Here you are at our site, articleabove (15 Dark Red Paintings Tips You Need To Learn Now | Dark Red Paintings) published . Today we are pleased to declare that we have found a veryinteresting topicto be discussed, namely (15 Dark Red Paintings Tips You Need To Learn Now | Dark Red Paintings) Most people looking for info about(15 Dark Red Paintings Tips You Need To Learn Now | Dark Red Paintings) and of course one of these is you, is not it?

Muffin-427184 - dark red paintings | dark red paintings

Black Canvas Paintings | The Picassos - dark red paintings | dark red paintings

Nail Art In Red Merry Christmas Decoration Rose Xmas Deer .. | dark red paintings

Painting for sale - black and red abstract art #2385 - dark red paintings | dark red paintings

New: Art Pa!nt!ngs - dark red paintings | dark red paintings

The good witch - dark red paintings | dark red paintings

Red October - dark red paintings | dark red paintings

Arch Rock After Dark - dark red paintings | dark red paintings

Black Abstract Art Better Times And White Minimalism L .. | dark red paintings Read the full article
0 notes
Text
The Lease Abstraction Process & its Stakeholders

When getting your leases abstracted, you should consider the stakeholders who will be using the lease abstract information. This is important because only when you identify the stakeholders and each of their requirements, will you be able to create lease abstracts that capture all the data they need.
When it comes to identifying the stakeholders and their requirements in terms of the lease data being abstracted, communication is the key. You need to find out who will be relying on the lease abstracts and for what purposes. Stakeholders can be found across your organization, in different teams including-
Operations
Accounting
Finance
IT
Legal
All of these teams will have an interest in the various different aspects of leases and you need to find out what they are and ensure that your lease abstracts cover those elements. Once you clearly identify all the stakeholders, the next step is to understand their requirements. What information will they need from the lease abstracts? The answer to this question will help you arrive at the key data points that are to be abstracted.
At the time of finalizing the data points based on the various stakeholder’s requirements, you may come across various data capture requests. As a best practice, you can divide them into two different categories–one that lists the must-have data fields and another that lists those data fields which are good to have, along with reasons why. You can use this list to later finalize your lease abstract data elements.
Bringing all the stakeholders onboard and understanding their needs before you start your lease abstraction project will ensure that your abstracts are comprehensive and don’t miss out any key information. Otherwise, you may miss out on critical data elements, requiring you to go back and get your lease abstracts updated by adding abstracts of those clauses later on.
Rebolease.com, powered by RE BackOffice, Inc., is a premier provider of lease abstraction, administration, audit and accounting services. Headquartered in Pittsburgh, PA, we are a global boutique firm, providing high-quality services to top-tier clients across industry verticals, covering every type of lease and on any lease platform. We are proud to be a trusted partner, for 15+ years, to leading retailers, REITs, property owners/managers, and corporate accounts seeking a strategic advantage. All client projects are performed in-house.
1 note
·
View note
Photo

Building a Habit Tracker with Prisma, Chakra UI, and React
In June 2019, Prisma 2 Preview was released. Prisma 1 changed the way we interact with databases. We could access databases through plain JavaScript methods and objects without having to write the query in the database language itself. Prisma 1 acted as an abstraction in front of the database so it was easier to make CRUD (create, read, update and delete) applications.
Prisma 1 architecture looked like this:
Notice that there’s an additional Prisma server required for the back end to access the database. The latest version doesn’t require an additional server. It's called The Prisma Framework (formerly known as Prisma 2) which is a complete rewrite of Prisma. The original Prisma was written in Scala, so it had to be run through JVM and needed an additional server to run. It also had memory issues.
The Prisma Framework is written in Rust so the memory footprint is low. Also, the additional server required while using Prisma 1 is now bundled with the back end, so you can use it just like a library.
The Prisma Framework consists of three standalone tools:
Photon: a type-safe and auto-generated database client ("ORM replacement")
Lift: a declarative migration system with custom workflows
Studio: a database IDE that provides an Admin UI to support various database workflows.
Photon is a type-safe database client that replaces traditional ORMs, and Lift allows us to create data models declaratively and perform database migrations. Studio allows us to perform database operations through a beautiful Admin UI.
Why use Prisma?
Prisma removes the complexity of writing complex database queries and simplifies database access in the application. By using Prisma, you can change the underlying databases without having to change each and every query. It just works. Currently, it only supports mySQL, SQLite and PostgreSQL.
Prisma provides type-safe database access provided by an auto-generated Prisma client. It has a simple and powerful API for working with relational data and transactions. It allows visual data management with Prisma Studio.
Providing end-to-end type-safety means developers can have confidence in their code, thanks to static analysis and compile-time error checks. The developer experience increases drastically when having clearly defined data types. Type definitions are the foundation for IDE features — like intelligent auto-completion or jump-to-definition.
Prisma unifies access to multiple databases at once (coming soon) and therefore drastically reduces complexity in cross-database workflows (coming soon).
It provides automatic database migrations (optional) through Lift, based on a declarative datamodel expressed using GraphQL's schema definition language (SDL).
Prerequisites
For this tutorial, you need a basic knowledge of React. You also need to understand React Hooks.
Since this tutorial is primarily focused on Prisma, it’s assumed that you already have a working knowledge of React and its basic concepts.
If you don’t have a working knowledge of the above content, don't worry. There are tons of tutorials available that will prepare you for following this post.
Throughout the course of this tutorial, we’ll be using yarn. If you don’t have yarn already installed, install it from here.
To make sure we’re on the same page, these are the versions used in this tutorial:
Node v12.11.1
npm v6.11.3
npx v6.11.3
yarn v1.19.1
prisma2 v2.0.0-preview016.2
react v16.11.0
Folder Structure
Our folder structure will be as follows:
streaks-app/ client/ server/
The client/ folder will be bootstrapped from create-react-app while the server/ folder will be bootstrapped from prisma2 CLI.
So you just need to create a root folder called streaks-app/ and the subfolders will be generated while scaffolding it with the respective CLIs. Go ahead and create the streaks-app/ folder and cd into it as follows:
$ mkdir streaks-app && cd $_
The Back End (Server Side)
Bootstrap a new Prisma 2 project
You can bootstrap a new Prisma 2 project by using the npx command as follows:
$ npx prisma2 init server
Alternatively, you can install prisma2 CLI globally and run the init command. The do the following:
$ yarn global add prisma2 // or npm install --global prisma2 $ prisma2 init server
Run the interactive prisma2 init flow & select boilerplate
Select the following in the interactive prompts:
Select Starter Kit
Select JavaScript
Select GraphQL API
Select SQLite
Once terminated, the init command will have created an initial project setup in the server/ folder.
Now open the schema.prisma file and replace it with the following:
generator photon { provider = "photonjs" } datasource db { provider = "sqlite" url = "file:dev.db" } model Habit { id String @default(cuid()) @id name String @unique streak Int }
schema.prisma contains the data model as well as the configuration options.
Here, we specify that we want to connect to the SQLite datasource called dev.db as well as target code generators like photonjs generator.
Then we define the data model Habit, which consists of id, name and streak.
id is a primary key of type String with a default value of cuid().
name is of type String, but with a constraint that it must be unique.
streak is of type Int.
The seed.js file should look like this:
const { Photon } = require('@generated/photon') const photon = new Photon() async function main() { const workout = await photon.habits.create({ data: { name: 'Workout', streak: 49, }, }) const running = await photon.habits.create({ data: { name: 'Running', streak: 245, }, }) const cycling = await photon.habits.create({ data: { name: 'Cycling', streak: 77, }, }) const meditation = await photon.habits.create({ data: { name: 'Meditation', streak: 60, }, }) console.log({ workout, running, cycling, meditation, }) } main() .catch(e => console.error(e)) .finally(async () => { await photon.disconnect() })
This file creates all kinds of new habits and adds it to the SQLite database.
Now go inside the src/index.js file and remove its contents. We'll start adding content from scratch.
First go ahead and import the necessary packages and declare some constants:
const { GraphQLServer } = require('graphql-yoga') const { makeSchema, objectType, queryType, mutationType, idArg, stringArg, } = require('nexus') const { Photon } = require('@generated/photon') const { nexusPrismaPlugin } = require('nexus-prisma')
Now let’s declare our Habit model just below it:
const Habit = objectType({ name: 'Habit', definition(t) { t.model.id() t.model.name() t.model.streak() }, })
We make use of objectType from the nexus package to declare Habit.
The name parameter should be the same as defined in the schema.prisma file.
The definition function lets you expose a particular set of fields wherever Habit is referenced. Here, we expose id, name and streak field.
If we expose only the id and name fields, only those two will get exposed wherever Habit is referenced.
Below that, paste the Query constant:
const Query = queryType({ definition(t) { t.crud.habit() t.crud.habits() // t.list.field('habits', { // type: 'Habit', // resolve: (_, _args, ctx) => { // return ctx.photon.habits.findMany() // }, // }) }, })
We make use of queryType from the nexus package to declare Query.
The Photon generator generates an API that exposes CRUD functions on the Habit model. This is what allows us to expose t.crud.habit() and t.crud.habits() method.
t.crud.habit() allows us to query any individual habit by its id or by its name. t.crud.habits() simply returns all the habits.
Alternatively, t.crud.habits() can also be written as:
t.list.field('habits', { type: 'Habit', resolve: (_, _args, ctx) => { return ctx.photon.habits.findMany() }, })
Both the above code and t.crud.habits() will give the same results.
In the above code, we make a field named habits. The return type is Habit. We then call ctx.photon.habits.findMany() to get all the habits from our SQLite database.
Note that the name of the habits property is auto-generated using the pluralize package. It's therefore recommended practice to name our models singular — that is, Habit and not Habits.
We use the findMany method on habits, which returns a list of objects. We find all the habits as we have mentioned no condition inside of findMany. You can learn more about how to add conditions inside of findMany here.
Below Query, paste Mutation as follows:
const Mutation = mutationType({ definition(t) { t.crud.createOneHabit({ alias: 'createHabit' }) t.crud.deleteOneHabit({ alias: 'deleteHabit' }) t.field('incrementStreak', { type: 'Habit', args: { name: stringArg(), }, resolve: async (_, { name }, ctx) => { const habit = await ctx.photon.habits.findOne({ where: { name, }, }) return ctx.photon.habits.update({ data: { streak: habit.streak + 1, }, where: { name, }, }) }, }) }, })
Mutation uses mutationType from the nexus package.
The CRUD API here exposes createOneHabit and deleteOneHabit.
createOneHabit, as the name suggests, creates a habit whereas deleteOneHabit deletes a habit.
createOneHabit is aliased as createHabit, so while calling the mutation we call createHabit rather than calling createOneHabit.
Similarly, we call deleteHabit instead of deleteOneHabit.
Finally, we create a field named incrementStreak, which increments the streak of a habit. The return type is Habit. It takes an argument name as specified in the args field of type String. This argument is received in the resolve function as the second argument. We find the habit by calling ctx.photon.habits.findOne() while passing in the name parameter in the where clause. We need this to get our current streak. Then finally we update the habit by incrementing the streak by 1.
Below Mutation, paste the following:
const photon = new Photon() new GraphQLServer({ schema: makeSchema({ types: [Query, Mutation, Habit], plugins: [nexusPrismaPlugin()], }), context: { photon }, }).start(() => console.log( `🚀 Server ready at: http://localhost:4000\n⭐️ See sample queries: http://pris.ly/e/js/graphql#5-using-the-graphql-api`, ), ) module.exports = { Habit }
We use the makeSchema method from the nexus package to combine our model Habit, and add Query and Mutation to the types array. We also add nexusPrismaPlugin to our plugins array. Finally, we start our server at localhost:4000. Port 4000 is the default port for graphql-yoga. You can change the port as suggested here.
Let's start the server now. But first, we need to make sure our latest schema changes are written to the node_modules/@generated/photon directory. This happens when you run prisma2 generate.
If you haven't installed prisma2 globally, you'll have to replace prisma2 generate with ./node_modules/.bin/prisma2 generate. Then we need to migrate our database to create tables.
The post Building a Habit Tracker with Prisma, Chakra UI, and React appeared first on SitePoint.
by Akshay Kadam via SitePoint https://ift.tt/2YaQ5v2
0 notes
Text
If you follow me on Twitter, this might seem a little familiar, but a slightly longer and more meandering version.
I’ve mentioned it a few times now, but I think the best thing I ever did for myself as a developer was create and standardize a set of tools for myself.
I had to do it in kind of a back door way. The place I was working at the time had an intellectual property clause in the contract. Basically, the owner wanted everything I developed while working there, whether it was at home or at work. He worked hard to muddy the waters by having us work on things at home, which meant he could argue things I worked on at home I was being paid for so obviously belonged to him. You know, pretty standard capitalist bullshit.
The way I fought against this, is first I developed my tools completely at home, and separate from any work projects. In fact, they were originally developed to facilitate a project where I could communicate with Old School Runescape trading APIs, so basically the furthest you can get from work. Then I uploaded the resulting framework to GitHub with an open source license, and only after it had been up for a few weeks did I take it to work. The crux to this plan was, you can’t close open source code once it’s open. Any changes or modifications I made to it at work were his, but the core of it, everything I’d already cemented was mine and I would be free to use it forever.
You’re probably noticing two things right now. Why did I have such an adversarial relationship with my boss? Why was I so adamant on keeping the rights to myself?
The second question is easier to answer, so I’ll do that first. I had worked with him for three years, and I had already decided to leave. I wanted something that was mine, something I could put into a portfolio, and more importantly build into portfolio projects. He owned all the code I wrote there, and I wasn’t allowed to share it with anyone. I could tell people I worked on things, but saying I worked on code and being able to show it to people are very different things.
The first is actually pretty closely linked to what drove me to structure my tools the way I did in the first place, so I’m going to describe the tools first.
I call them Vogon after the race from Hitchhiker’s Guide To The Galaxy. The idea was that the framework itself was supposed to be as small as possible, but extract the absolute most use from that small amount of code. Not unlike poetry, but much like the Vogons that Douglas Addams describes, I was pretty sure it was going to be bad poetry.
I think I accomplished my goal. Vogon Core, loaded with the settings extension (which makes routing much easier), is 66.5kb, and that’s a little more bloated than the core really needs to be. I should honestly move a number of models and views into extension folders so they can be more easily moved in and out of projects. But what’s most important is what I’m doing in that less than 1/10th of a MB.
Vogon Core includes a Database object called “Thumb” that manages creating the database connections and doing the queries in a way that can be rolled back appropriately (I’m pretty sure, though I haven’t had reason to test this extensively). It also includes a database abstraction object called “Clerk” that handles a lot of CRUD (Create, Read, Update, Delete) operations on the main Data and Data_Meta database tables, so I don’t have to handle most database queries directly, but have the flexibility to do so if I’m doing something more complex. The last included object is a wrapper for cURL (Client For URLS, a terminal level application for fetching resources at urls) called “Fish”, after the universal translators. Between those three objects, I can retrieve, parse, store, and update data remotely or in a database, which is 90% of the functionality every project needs.
Next, I created a bootstrap file that is always loaded. This includes the above classes, loads the config file (and tells the database to connect if it’s in use). This then invokes the router which takes care of another 5% of the functionality all projects require, the ability to navigate between application end-points. The router is entirely dynamic. The framework uses an HTACCESS file to route all calls to the server through a single file than then loads resources based on the address, this means you’re never accessing a file directly unless it is from an exception folder like Upload or resource folders like JS and CSS. This means you can have really clean URLs, and if a client does something dumb like hate the default location for their administration URL, it can easily be changed with minimal fuss. The final core document is a collection of functions to facilitate everything. Four functions load various documents and establish the folder structure, the generic loader function, and more specific envokations of the generic loader pointed at the Controller, Model, and View folder structures both in the main folder and the extension folders. The rest of the functions just make a few recurring tasks like parsing URLs, or making strings URL safe (not URI safe, as that’s a little different), a little easier to manage.
This means for every project I start. I have an established, clear, and expandable folder structure, a database connection, a way to access remote resources, and a resilient and relatively battle hardened router, so I am usually off and writing new functional code in two to three minutes. Just long enough to drop the folder structure, create the database, and throw the user and password into the configuration file.
Why is this so important to me, why do I rave about it so much? Because it’s so damned easy, and I never had that at work.
I worked at a small Internet Marketing shop with something like 250 websites. A few clients had more than one website, but for the most part every website was a different client. About a third of those were running on established open source PHP frameworks (OpenCart {which is trash, don’t use it}, Wordpress, Drupal, Joomla). I almost never had to worry about these outside of regular minimal maintenance tasks like content updates, plugin updates, ect. Of the other 160ish, about 10 where static websites, and the last 150 were on a proprietary PHP framework called Arrow (at least in later stages).
Arrow was… a geological expedition of code. The company had gone through so many developer changeovers that the core of the framework was pretty clearly divided into strata of different development goals and mindsets. One development team used a lot of open source projects with minimal changes, another really liked their OOP (object oriented programming), and another insisted on re-inventing the wheel. Add to this that Arrow was never truly version controlled (I asked about git and was told it wasn’t worth the trouble), and you had a whole mess. I burned at least 10 hours a week solving the same problems over and over again, and I could almost never copy and paste directly because each site was just different enough that rampant copy pasting could break everything. This meant there were a lot of custom written solutions that could never be tested thoroughly. Which meant a lot of clients found edge cases I couldn’t see when I was implementing whatever fix, and they were understandably upset that things I said was fixed were obviously not so.
And I say me, because it was basically just me. When I was hired, I was the only developer. Everyone else had just been fired. A few months later I had a single co-worker, but the division of labor ended up heavily in favor of me doing server administration, website maintenance, and framework development, while he focusing on the new work and one-off development. There was crossover, but not as much as we wanted or needed. Which really sucked when it came time to take time off because there were a lot of questions that only I could answer. Being an invaluable employee is great, until you’re the roadblock in a project.
Because I was working on the framework itself, I was able to bring some uniformity to it. We were a lot better near the end of my employment than we ever were in the beginning, and I hear they’ve now moved primarily to WordPress (which is honestly amazing as it basically removes the need for my old position). But, the biggest issue is the amount of pushback I got from my boss about my solutions to all of the time I was regularly burning on things being solved over and over again. Again, I was told Git wasn’t worthwhile. I got into the prototyping stage of a new more flexible version of the framework and was told to throw everything away and that we were going to just continue to hotfix and patch what we had until it was in better shape.
As an aside, I really hated throwing that work away. A big part of the prototype that I was working on had automated a lot of development tasks. It could build new database tables for you, it was auto sanitizing inputs, and built CRUD abstraction objects for all the tables in the database. You could tell it to make an extension folder, and it would create one complete with UI that you just had to modify to suit your needs, letting you focus just on working on new code.
I have a lot of theories as to why we had these fights. My ego makes me want to say that a big problem is that the owner thought of himself as a developer, and a bit of a genius. So when we were putting code in front of him that he didn’t understand, it made him angry because if it wasn’t how he would do it, it couldn’t possibly be a good way to do it. I also suspect that after I left, he did his best to go through all the code I wrote and throw out everything he didn’t like, breaking the framework, and that’s what finally pushed them to WordPress as their primary framework. But probably the biggest contribution was that he almost never worked on the development, so he couldn’t see the problems that I did. He didn’t like that I would spend time solving problems other than the ones clients were complaining about at the moment, that I was trying to speed up development time and lower maintenance time. That I was self-lead and did not look up to him.
So when I decided I was leaving. I took a lot of the lessons that I had learned the hard way, took as many of the problems that were work stressers as I could solve with code, and I solved them.
And I can’t begin to tell you how nice it is to get an idea and to be able to work on it in minutes. To know that if I really like part of a project I’m working on, I can easily just drop it into an old project. To have a workflow that is the same from project to project.
In the tech world, there’s an obsession with always knowing the newest and the “best” tools. There’s the memes about needing 10 years of experience with two year old technologies. But in my day to day development, the things I use the most are the Linux Terminal, Apache, MySQL, SCP/SFTP, jQuery/JavaScript, PHP. There’s not a single piece of tech in that stack that’s less than decades old, and there are very few problems I can’t solve with it. They are relevant, they are maintained, and they will continue to be relevant.
At the end of the day, it doesn’t matter if its the best way to solve a problem, what matters is how fast you solved it, and if the solution is stable and reliable. Especially if there is a client waiting for you work. They care that it works, that they got it quickly, and that it continues to work.
I’m not saying don’t try to keep up with new technology, but have a set of standard tools you know very well. That way you can fall back on them when speed is of the essence, or when stability is a priority.
0 notes