#Web Accessibility Statistics
Explore tagged Tumblr posts
Text
#Web accessibility#Digital Landscape#WCAG#Screen Readers#Disabilities#Section 508#ADA Compliance#AODA Requirements#User Testing#Digital Accessibility#Web Accessibility Statistics#Visual Impairments#Content Accessible#Hearing Loss#Accessibility Barriers#Digital Content Accessibility#Assistive Technology#Accessibility Crucial#Inclusive Design#Accessibility Guidelines#Web Accessibility Guidelines#Web Content#accessibility lawsuits#Website Accessibility#AEL Data
0 notes
Text
come on someone post a dr who link already, you guys don't think i'm actually gonna sign up for disney plus just because they ditched bbc america?
#to be fair i havent had a chance to look hard yet bc i've been busy#but given this webbed site's hatred for megacorps i really thought they'd be much more numerous in reaction to the disney move#i cant be the only one who lost access instead of gaining it that's statistically impossible
6 notes
·
View notes
Text
Yeah you're right about Alice finding Bonzo as having a high W value, instead of Fredi recommending Bonzo! What I meant was that I don't think that W needs to be upped for the balance. We know that Bonzo scores high on W, and we've heard quite a bit of Bonzo. If what we've heard is representative of the total caseload (which is absolutely not a given!) then we must already be high on W (although I admit I haven't actually run any numbers yet, which I suppose wouldn't be difficult to do, so I might do that later). Then Fredi might be pushing for more W to break the balance, by lying to Gwen about which values are low.
The following got way longer than I intended, oops!
I believe I've read in another of your posts some theories on what DWPH might stand for. My current (entirely ungrounded) theory is that whatever W stands for is more aligned with the Fears from tma than the other values. This would hook into my other theory, so I'll expand on that first:
I think that whatever the fuck is going on in tmagp is indeed its own thing, separate from tma, BUT that the tma finale has let the Fears into this universe. The oiar cases don't show that very clearly, because their system is built for their own paranormal stuff, not for the Fears, so they are trying to see the stuff from the Fears through their own lens. And to be fair, their own lens is good enough for their own paranormal stuff, which was already happening since forever, and hasn't stopped since the Fears got added to the mix. So we're not just figuring out a new paranormal system, we're also figuring out how it's newly interacting with the Fears. For instance, Ink5oul seems to have their own powers centered around transformation through their tattoos, but I remember them saying something along the lines of later coming to enjoy the fear in their clients as they are tattooed. I think that when the Fears got into this universe, they immediately felt the amount of fear Ink5oul inspired in their clients and other people, and made them an avatar. If you want a specific Fear, I'd say a mix of the Corruption and the Spiral, but we should remember that those are just categories. Becoming an avatar would be the moment that Ink5oul started enjoying the fear of their clients.
Within that framework, I think it would make sense that the Eye latched onto the OIAR. Like, come on, an organisation spying on literally everything and being able to get cases of people experiencing massive amounts of fear, even if classified as top secret? That's like catnip to something called the Beholding that feeds on fear. So the Eye threw its own avatars into the computer there (bc it needed to do something with them, I guess), and bam! it has a new headquarters. Whatever reason caused it to be unable to access digital systems is apparently not hindering it here (my bet is on the reason in tma being that the Web did something to make digital stuff inaccessible, so the Eye would instead use the tapes, which of course weren't really of the Eye, but of the Web. In tmagp the Web is also new in this world, so it hasn't been able to set up such precautions while technology was developing). With the Eye in the computer systems, that would also explain how we got the podcast. In tma we were listening through the tape recorders: we, the audience, were the Beholding. Now in tmagp we're listening through security cameras and computers. So if the Fears have come to this universe, I don't think anything's changed. We're still the Eye, but we're finally able to use better microphones (not to mention, microphones on devices that are a lot more common than tape recorders).
With the Eye in the computer system (and thus in Fredi), I can imagine that it's trying again to cause some kind of apocalypse. With all of the information available to it, it's probably already figured out what needs to happen: the quaternity needs to be out of balance. Getting back to the W value, I think that since the Fears have arrived and caused additional incidents, W has risen, and the Eye is using that by telling Gwen that more W is needed. In a horror podcast, paranormal always means scary, but I think that the kind of fear that the Fears embody might be more W than D, P or H. This would mean that not only are we seeing how alchemy paranormal stuff interacts with the Fears, we are also seeing the achemy getting directly imbalanced because of the Fears.
What even is the OIAR
This is not really a theory, more like a series of questions, gut feelings and ramblings of a madwoman.
I feel like we are led to believe that the OIAR, like all official government agencies, are doing some sort of service to the people, albeit with dark undertones. Occasional civilian sacrifice to keep the horrors at bay, and all that. It seems to track with everything we know about keeping a balance, about sending a Bonzo out to brutalize some party-goers, and about Colin's ramblings about what too much sulphur or mercury might lead to. But I have to wonder.
Why did Colin bring up Stasi? If the OIAR is a British government agency, why was he concerned with the East German secret police that doesn't even exist anymore? I have to assume that Fr3-d1 (or its prototype?) was created in the DDR, and for some reason the system along with the operations were moved to the UK. But why? If the OIAR is concerned with keeping a universal balance, surely it would take much more than one British organisation using their limited local externals. Does every government have their own branch? Or is there something deeper hidden in their history?
What rubs me the wrong way is the symbology in the logo, which at this point I've overanalysed to death. We have the symbol for the Philosopher's Stone (inverted, which could mean something or not), the laurels that were used to symbolise the completion of the Great Work, and the motto "Non vacillabimus", which conveys the idea of not faltering/hesitating/wavering. These do not feel like symbols of stability or balance, they feel like symbols of conviction towards a goal. The Philosopher's Stone is not created by merely keeping things balanced, it's the end goal of repeated, transformative processes.
This is where I'm going off the rails a bit, but I have to entertain the possibility that the OIAR was never meant to be a government agency to begin with. As has been pointed out, the logo does bear a striking resemblance to the royal coat of arms (with the lion and unicorn and all that), which is why no one would even think to question it. But the lion and the unicorn are also common symbols for the sun and moon, which must be brought together in union to make the Stone. And the quaternity (or circle divided in four) in the middle is similarly a common symbol found everywhere in alchemy. Additionally, the emblem doesn't even say "Office of Incident Assessment and Response", it says "O. I. A. R." Do we know for sure that's what it even stands for? It could just as well be an Order of some kind, and god knows there wasn't a lack of those in Germany.
The OIAR could have been established in Germany as another type of organisation, such as an alchemical fraternity of some kind, and then repurposed into a British government agency. Why? I have no clue. I just have this nagging feeling that all is not what it seems. And it doesn't help that they hid a major plot twist in the Magnus Archives logo and I didn't notice it until way after I'd finished listening. TMAGP being about alchemy, which is specifically the art of hiding secrets in plain sight, makes me more paranoid than ever.
No conclusions, local madwoman out.
#I'm so sorry this got so much longer than i intended it to be#i haven't fully written this theory out i think#at least not as coherently as this#the whole “fears entering the universe where alchemy is already going on” thing is only slightly related to your post#sorry for that but at least it's written out now#hope you don't mind#I'm also thinking about what cases were read by which voice#I wouldn't be surprised if there's very obvious correlations there#for instance norris's cases being about Martin's emotions towards jon and augustus's cases being about research and history of alchemy#- where jonah magnus is figuring out how this system works and how to use it to his advantage#or maybe chester's and norris's cases actively trying to keep the balance while augustus's cases push the balance out?#now that last one would be a very complicated statistics problem with way too little samples right now#especially bc you can keep adding additional things to look for#anyway poor gwen. she had the fright of her life when she was sent to bonzo -#- and now she's finally figuring out how the oiar works and why they employ the externals (to have them up a value to keep them balanced)#- and now she's told that to keep the balance she needs to give an order to. of all externals. Bonzo!#and she can't even tell alice why that's a problem bc alice still thinks it's just a matter of finding those cases and handling them first#but gwen knows better: she needs to make sure the incidents happen in the first place#tmagp#tmagp spoilers#additional thoughts: if the web did indeed do something to the technology in the world of tma as it was developed so the eye can't access i#- and if we the audience are indeed directly the eye listening in#- then it makes complete sense that we can hear through both the computers and the occasional tape recorder in the tmagp universe#- but still only through tape recorders in the universe where sam ended up (which i fully believe to directly be the tma universe)#the magnus protocol#tmagp theories#tmagp theory
68 notes
·
View notes
Text
been reflecting on the lack of web-weaving/poetry/other forms of 'high quality' posts about women's sports here on tumblr and i personally think a big factor that contributes to that is the scarcity of high-quality journalism about women's sports. the athletic isn't posting articles about rivalries in women's sport, they're posting about "growth" - indexed by eye-glazing statistics about salaries, attendances and viewing numbers. it feels like women's sports are engaged first as a "women's sport" (and the connotations that has) rather than simply as sports which happen to have female athletes, who have their own desires, histories and motivations just like male athletes. people make highly intricate web-weaving posts about f1 drivers and hockey players because there is a wealth of texts for them to draw upon, whereas that simply isn't the case for women's sports or if there is, it's much less accessible.
90 notes
·
View notes
Text
That Time When I Tried To Bring A Foot Long Knife In My Cabin Bag On An International Flight
You know flights. For at least a few generations already we have had a privilege of travelling through air, which is statistically one of the safest means of transportation, but when shit goes wrong, it goes wrong in a particularly spectacular manner and being the dumb fucks we humans are, spectacular failures (such as acts of terror) register as more plausible ones in our stupid monkey brains. This is a digression, but, as the title of the post suggests, not an untangential one.
In any case, there used to be a time in my life when international flying was just a regular thing for me, getting on a plane and immediatelly getting some monday-morning shut-eye even before the take-off to teleport a few thousand kilometers away was just a fact of life. Two of my russian-speaking (but also fluent in my mother tongue) team mates doing some contract backend web development for a foreign fintech startup with me as a "team lead" (in quotes, because we have always been egalitarian) were as accustomed to flying as I was. Security checkpoint, it seemed at that time, was something we knew intimately, not necessarily to the point when we referred to the agents by their first names, but rather we knew which shoes are going to have to come off and the exact amount of change to trigger the metal detector. It was, as we all understood it, a dog-and-pony show in a post 9/11 security theater where water in your belly was qualitatively different from the water in an unopened bottle, which is technically true, but it never even made anyone feel safer as a passenger or less safe as a potential criminal (like my white ass getting "randomly checked" five times in a row for "traces of explosives"); it usually went as a well-choreographed routine of retrieving a laptop from an easily-accessible part of your backpack, unbuckling your belt, taking off your coat, putting clothes, backpack and electronics into separate trays and proceeding to waltz through the SCARY GATE in a steady pace all the while smiling in a friendly manner to the agents, maintaining Just Enough eye contact to establish connection but not come off as challenging and refraining yourself from making any meta commentary throughout the whole ordeal.
Easy.
Imagine yourself in my shoes when my backpack comes out of the x-ray about 1.25 seconds later than usual. There's a warning light going off silently at the back of my head as I wait for my belt to come back to me so my pant's don't slip off my fat white ass as much, getting brigher and turning into a bangbang double exclamation mark emoji and starting to emit avionic warning sound as the security agent pulls the tray with my backpack aside.
"Sir is this your bag?"
"Yes, it is"
"It seems you have a knife in there"
At this point I am more amused than perplexed.
"Yes, that is true," - I say smiling incredulously - "but it never caused any trouble anywhere."
I'm thinking about my trusty pocket victorinox (with scissors that are incredibly good for trimming my nails on the go) attached to my RSA OTP generator.
"Oh." - the female agent replies dryly, putting the vynil gloves on - "may I please open your bag, sir?"
"Sure!" - "May I retrieve The Object, sir?" - "Please go ahead".
And I watch, with increasing horror, my eyes widening, as I see the very remotely familiar handle that stirs something in the depths of my memory, the blade emerging in slow motion and going oh-so-slowly to what seems like forever until the whole footlong thing is out, pinched between two fingers of the agent who looks at me as memories of a town several hundred kilometers away rush back to me: the hunger, the yearning, the NEED for a simple kielbasa-and-bun sandwitch, both kielbasa and a freshly baked bun in my hands in a middle of a shop with no way to cut neither kielbasa nor the bun and the footlong steel monstrocity being the only possible option of instruments capable of cutting. Did I unpack my bag or I simply throw it aside when I got home is a question with an answer so obvious it immediately unasks itself.
"Sir?" - a female voice brings me back to here-now. - "I said, shall I discard of it, sir?"
I struggle for a moment to regain control of my motor function and nod. I think my mouth is slightly agape and I have no control of my vocal cords. A single elongated vowel escapes my throat.
"Thank you" - she says, handing my backpack over to me. My colleagues also stand frozen, their eyes wide in disbelief. - "You may proceed, sir"
"T-thank you" - I stutter as I shuffle away with my backpack in one hand and my belt which I retrieved just prior to the whole incident in another, pretty sure I've gotten damn lucky once again.
I never bought another trio of bun, kielbasa and a big fuckoff knife abroad again.
34 notes
·
View notes
Text
In early 2020, deepfake expert Henry Ajder uncovered one of the first Telegram bots built to “undress” photos of women using artificial intelligence. At the time, Ajder recalls, the bot had been used to generate more than 100,000 explicit photos—including those of children—and its development marked a “watershed” moment for the horrors deepfakes could create. Since then, deepfakes have become more prevalent, more damaging, and easier to produce.
Now, a WIRED review of Telegram communities involved with the explicit nonconsensual content has identified at least 50 bots that claim to create explicit photos or videos of people with only a couple of clicks. The bots vary in capabilities, with many suggesting they can “remove clothes” from photos while others claim to create images depicting people in various sexual acts.
The 50 bots list more than 4 million “monthly users” combined, according to WIRED's review of the statistics presented by each bot. Two bots listed more than 400,000 monthly users each, while another 14 listed more than 100,000 members each. The findings illustrate how widespread explicit deepfake creation tools have become and reinforce Telegram’s place as one of the most prominent locations where they can be found. However, the snapshot, which largely encompasses English-language bots, is likely a small portion of the overall deepfake bots on Telegram.
“We’re talking about a significant, orders-of-magnitude increase in the number of people who are clearly actively using and creating this kind of content,” Ajder says of the Telegram bots. “It is really concerning that these tools—which are really ruining lives and creating a very nightmarish scenario primarily for young girls and for women—are still so easy to access and to find on the surface web, on one of the biggest apps in the world.”
Explicit nonconsensual deepfake content, which is often referred to as nonconsensual intimate image abuse (NCII), has exploded since it first emerged at the end of 2017, with generative AI advancements helping fuel recent growth. Across the internet, a slurry of “nudify” and “undress” websites sit alongside more sophisticated tools and Telegram bots, and are being used to target thousands of women and girls around the world—from Italy’s prime minister to school girls in South Korea. In one recent survey, a reported 40 percent of US students were aware of deepfakes linked to their K-12 schools in the last year.
The Telegram bots identified by WIRED are supported by at least 25 associated Telegram channels—where people can subscribe to newsfeed-style updates—that have more than 3 million combined members. The Telegram channels alert people about new features provided by the bots and special offers on “tokens” that can be purchased to operate them, and often act as places where people using the bots can find links to new ones if they are removed by Telegram.
After WIRED contacted Telegram with questions about whether it allows explicit deepfake content creation on its platform, the company deleted the 75 bots and channels WIRED identified. The company did not respond to a series of questions or comment on why it had removed the channels.
Additional nonconsensual deepfake Telegram channels and bots later identified by WIRED show the scale of the problem. Several channel owners posted that their bots had been taken down, with one saying, “We will make another bot tomorrow.” Those accounts were also later deleted.
Hiding in Plain Sight
Telegram bots are, essentially, small apps that run inside of Telegram. They sit alongside the app’s channels, which can broadcast messages to an unlimited number of subscribers; groups where up to 200,000 people can interact; and one-to-one messages. Developers have created bots where people take trivia quizzes, translate messages, create alerts, or start Zoom meetings. They’ve also been co-opted for creating abusive deepfakes.
Due to the harmful nature of the deepfake tools, WIRED did not test the Telegram bots and is not naming specific bots or channels. While the bots had millions of monthly users, according to Telegram’s statistics, it is unclear how many images the bots may have been used to create. Some users, who could be in multiple channels and bots, may have created zero images; others could have created hundreds.
Many of the deepfake bots viewed by WIRED are clear about what they have been created to do. The bots’ names and descriptions refer to nudity and removing women’s clothes. “I can do anything you want about the face or clothes of the photo you give me,” the creators’ of one bot wrote. “Experience the shock brought by AI,” another says. Telegram can also show “similar channels” in its recommendation tool, helping potential users bounce between channels and bots.
Almost all of the bots require people to buy “tokens” to create images, and it is unclear if they operate in the ways they claim. As the ecosystem around deepfake generation has flourished in recent years, it has become a potentially lucrative source of income for those who create websites, apps, and bots. So many people are trying to use “nudify” websites that Russian cybercriminals, as reported by 404Media, have started creating fake websites to infect people with malware.
While the first Telegram bots, identified several years ago, were relatively rudimentary, the technology needed to create more realistic AI-generated images has improved—and some of the bots are hiding in plain sight.
One bot with more than 300,000 monthly users did not reference any explicit material in its name or landing page. However, once a user clicks to use the bot, it claims it has more than 40 options for images, many of which are highly sexual in nature. That same bot has a user guide, hosted on the web outside of Telegram, describing how to create the highest-quality images. Bot developers can require users to accept terms of service, which may forbid users from uploading images without the consent of the person depicted or images of children, but there appears to be little or no enforcement of these rules.
Another bot, which had more than 38,000 users, claimed people could send six images of the same man or woman—it is one of a small number that claims to create images of men—to “train” an AI model, which could then create new deepfake images of that individual. Once users joined one bot, it would present a menu of 11 “other bots” from the creators, likely to keep systems online and try to avoid removals.
“These types of fake images can harm a person’s health and well-being by causing psychological trauma and feelings of humiliation, fear, embarrassment, and shame,” says Emma Pickering, the head of technology-facilitated abuse and economic empowerment at Refuge, the UK’s largest domestic abuse organization. “While this form of abuse is common, perpetrators are rarely held to account, and we know this type of abuse is becoming increasingly common in intimate partner relationships.”
As explicit deepfakes have become easier to create and more prevalent, lawmakers and tech companies have been slow to stem the tide. Across the US, 23 states have passed laws to address nonconsensual deepfakes, and tech companies have bolstered some policies. However, apps that can create explicit deepfakes have been found in Apple and Google’s app stores, explicit deepfakes of Taylor Swift were widely shared on X in January, and Big Tech sign-in infrastructure has allowed people to easily create accounts on deepfake websites.
Kate Ruane, director of the Center for Democracy and Technology’s free expression project, says most major technology platforms now have policies prohibiting nonconsensual distribution of intimate images, with many of the biggest agreeing to principles to tackle deepfakes. “I would say that it’s actually not clear whether nonconsensual intimate image creation or distribution is prohibited on the platform,” Ruane says of Telegram’s terms of service, which are less detailed than other major tech platforms.
Telegram’s approach to removing harmful content has long been criticized by civil society groups, with the platform historically hosting scammers, extreme right-wing groups, and terrorism-related content. Since Telegram CEO and founder Pavel Durov was arrested and charged in France in August relating to a range of potential offenses, Telegram has started to make some changes to its terms of service and provide data to law enforcement agencies. The company did not respond to WIRED’s questions about whether it specifically prohibits explicit deepfakes.
Execute the Harm
Ajder, the researcher who discovered deepfake Telegram bots four years ago, says the app is almost uniquely positioned for deepfake abuse. “Telegram provides you with the search functionality, so it allows you to identify communities, chats, and bots,” Ajder says. “It provides the bot-hosting functionality, so it's somewhere that provides the tooling in effect. Then it’s also the place where you can share it and actually execute the harm in terms of the end result.”
In late September, several deepfake channels started posting that Telegram had removed their bots. It is unclear what prompted the removals. On September 30, a channel with 295,000 subscribers posted that Telegram had “banned” its bots, but it posted a new bot link for users to use. (The channel was removed after WIRED sent questions to Telegram.)
“One of the things that’s really concerning about apps like Telegram is that it is so difficult to track and monitor, particularly from the perspective of survivors,” says Elena Michael, the cofounder and director of #NotYourPorn, a campaign group working to protect people from image-based sexual abuse.
Michael says Telegram has been “notoriously difficult” to discuss safety issues with, but notes there has been some progress from the company in recent years. However, she says the company should be more proactive in moderating and filtering out content itself.
“Imagine if you were a survivor who’s having to do that themselves, surely the burden shouldn't be on an individual,” Michael says. “Surely the burden should be on the company to put something in place that's proactive rather than reactive.”
56 notes
·
View notes
Text
Paramite

Image © deviantArt user Snugglestab, accessed at their gallery here
[Sponsored by @martyslittleusedblog, another creature from the Oddworld games. The series' interest in ecology helps when converting its monsters to give me something to pull from with regards to flavor text. So I'm not just making this up!]
Paramite CR 3 N Magical Beast This eyeless creature’s head is shaped like a hand, with three clawed appendages above its mouth, one on each side, and one below. It walks on four legs, its forelimbs larger and more muscular than its hind limbs, each tipped with a single claw.
Paramites are forest dwelling carnivores found on alien planets. Their ecology is somewhere between that of a giant spider and a hyena—they are social ambush predators that typically hunt in groups. A single paramite is usually a scout for a larger group, and may attempt to lead curious passerby closer to the nest or to an ambush site where more paramites are waiting. Paramites are excellent climbers and fight three-dimensionally, attempting to surround prey from the trees. Their facial appendages are their primary weapon, being used to slash, jab and grab prey in order to crush and tear it apart. They have no teeth in their mouths, instead shredding their victims with their facial appendages before ingesting them.
Paramites are sapient, albeit not very smart. They have their own language, a series of grunts, squeals and clicks, produced both vocally and through rubbing and snapping their fingers together. Paramites lair in the canopies of large trees or in the upper reaches of forest caves. There, they build nests out of webbing; their webs are not sticky, but sturdy and weatherproof, and last long enough to sometimes be utilized by other creatures once the paramites have moved on or died. Paramites do not collect treasure intentionally, but some useful or valuable items may be left as debris in their nests.
Paramite CR 3 XP 800 N Medium magical beast Init +2; Senses blind, blindsight 30 ft., Perception +6
Defense AC 15, touch 12, flat-footed 13 (+2 Dex, +3 natural) hp 26 (4d10+4) Fort +5, Ref +6, Will +3
Offense Speed 30 ft., climb 30 ft. Melee claw +6 (1d6+3 plus grab) Special Attacks constrict (1d6+3)
Statistics Str 14, Dex 15, Con 13, Int 4, Wis15, Cha 6 Base Atk +4; CMB +6 (+10 grapple); CMD 18 (22 vs. trip) Feats Power Attack, Precise Strike (B), Stealthy Skills Climb +22, Escape Artist +5, Perception +6, Stealth +8 (+12 in forests); Racial Modifiers +16 Climb, +4 Stealth in forests Languages Paramite SQ expert climber, webbing
Ecology Environment warm or temperate forests or underground Organization solitary, pair, pack (3-6) or nest (7-24) Treasure incidental
Special Abilities Blindsight (Ex) A paramite’s blindsight is based on hearing and scent. If it is deafened or in an area of silence, or if it cannot smell, it is treated as having blindsense. If both are true, it is considered to be blind. Expert Climber (Ex) A paramite’s racial bonus to Climb checks is doubled to +16. It can climb on vertical surfaces or ceilings as if under the effects of a spider climb spell. Webbing (Ex) Although a paramite’s webs are not sticky, they can be used to build structures. In addition, as long as a paramite starts a fall from a solid surface, it is treated as being under the effects of a non-magical feather fall spell, as it uses a tether to lower itself to the ground.
110 notes
·
View notes
Text







Monty Jaggers McGraw:
I am writing new BASIC programs to demo at my VCF Southwest 2025 exhibit of my 1979 Tektronix 4054A color vector graphics computer.
One of the programs I am writing is a 1978-1979 Battlestar Galactica TV demo. That TV show had $500,000 of Tektronix vector graphics computers and test equipment and many screenshots of their green vector storage CRT displays - some stills - some animated. These computer graphics were generated on both 1975 4051 and 1976 4081 vector graphics computers - predecessors to my 4052 and 4054A computers (see first photo attached).
Miami Herald TV 1978 magazine interview with the Battlestar Galactica set designer indicated extras on the set stationed in front of the 4051 computers were playing games during filming to increase realism and were so absorbed they kept playing after the cut! (article page attached).
The 4051 and second generation 4052 were the same physical size and used the same CRT and same Display board, but the 4052 and 4054 computers replaced the 800KHz Motorola 6800 CPU with a custom four AMD2901 bit-slice CPU to create a 16-bit address and data bus ALU which emulated the 6800 opcodes and added hardware floating point opcodes to speed up these computers 10x over the Motorola 6800, doubled the BASIC ROM space to 64KB and doubled the RAM space to 64KB!
I created these vector bitmap graphics using a "3D CAD" picture I found on the web of the Battlestar Galactica (last attachment).
As far as I know - there was never any 4050 BASIC program to view bitmap pictures on any of the 4050 computers. The 1979 4014 vector graphics terminal had a grayscale bitmap mode in the Extended Graphics option board, but I have only found a couple of bitmap 4014 images on a single Tektronix demo tape cartridge.
My 4050 BASIC program to display bitmaps works on all 4050 series computers - with an optional Tektronix 4050R12 Fast Graphics/Graphics Enhancement ROM Pack. This ROM Pack speeds up displaying vector images (including vector dot images) 10x over using BASIC MOVE and DRAW commands.
The Battlestar Galactica bitmap image in R12 binary format is 332234 bytes - slightly larger than would fit on a DC300 quarter-inch tape cartridge in the internal tape drive of all three 4050 computers, but would have fit on a 3M DC600 tape cartridge with a capacity of 600KB - it would have been very slow to load.
I designed an Arduino board to emulate the Tektronix 4924 GPIB tape drive - with the help of my software developer. My GPIB Flash Drive board contains a MicroSD card with gigabytes of storage and the Flash Drive emulates a GPIB tape changer, storing all the files of a "tape" in a single directory. I have also attached to this post a photo of my GPIB Flash Drive.
I have recovered almost 100 Tektronix 4050 Tapes and posted the ones I think are the most interesting at this time on my github repository for Tektronix 4051/4052/4054 computers: https://github.com/mmcgraw74/Tektronix-4051-4052-4054-Program-Files I included Tektronix published MATH volumes 1, 2, and 3 and Electrical Engineering, but I don't think they have a lot of use today. I have in my collection but not recovered tapes on Project Management, Statistics, and over 100 more tapes from the very active user group, which Tektronix made collections and published abstracts in their newsletter and the newletter customer got the tape for free. Commercial software like CAD programs were likely encrypted to eliminate copying - since Tektronix 4050 BASIC included a SECRET command which would then encrypt the program file as it was recorded to tape and add a SECRET flag in the tape header that would signal to BASIC ROM when that file was accessed to decrypt the program when it was loaded into memory. One big limiter to the size of the program was RAM in the 4051 was limited to 32KB and the 4052 and 4054 were limited to 64KB of RAM, although Tek BASIC did include commands to allow program "chunks" to be overlayed as necessary. Tektronix used those commands in their 4050 System Tape which was shipped with every system and included a tutorial on many of their BASIC commands. The tutorial ran on the original 4051 with 8KB of memory, and if the program detected 16KB of memory it would APPEND larger program files to speed up the tutorial.

15 notes
·
View notes
Note
How do I stop web pages on mobile from redirecting me to the app? Specifically tumblr. I want to access my blog statistics but they're not available here on the app. Is there any way to do this besides uninstalling and reinstalling tumblr?
-
8 notes
·
View notes
Text
Working with Technology Deities
{My post is Cross Posted from The Cobalt Athenaeum aka my original post}
This is all largely UPG and SPG based.
Technology deities are a type of egregore, you can call them a pop culture deity if that feels better. They are the embodiment of the tech domain itself. A primordial being, at least in the way I work with them. They have no faces, names or gender to me. They just are their domain and energy itself. Incredibly powerful in their own right. They can be found the same way a pop culture deity can be, you can see more in our Sister Server Westruun (the blue one) aka The Cobalt Athenaeum.
How Do I Work With a Tech Deity?
You can work with them like any other deity, the largest difference is incorporating them into your tech magic. Are you a streamer? A YouTuber? Or even a blogger? Perhaps work with the Algorithm god. They rule over (in my personal experience) the Algorithm, wisdom, confidence, perception, and change. They can help you boost your numbers, your presence, boost confidence and much more. Incorporating them into your life would surely aid you in your goals.
Make a space for them, build a relationship, make offerings and petition them. You will not regret it.
Tech Deity Examples and Correspondences
I’ve worked with a deity of a social media site and the deities listed below. I will not be posting everything and everyone's correspondences I have worked with, I believe it is important to base your own correspondences and this will be a sample but you can get a general idea from here. These are all my correspondences from working with them. You can use the same ones listed or feel out your own when you meet them.
Algorithm Deity God Of: The Algorithm, wisdom, perception, change, confidence Plants & Trees: Basil, Clary Sage, Maples Elements: Air Celestial Body/Planet: Mercury Scents and Incense: Clary Sage, Ginger, Peppermint Stones & Gems: Tigers eye, Lapis Lazuli Tarot card: The Fool Colours: Light blue, grey, red Candle Colour: Bold Red Offerings: Coffee, caffeinated teas, water, sugar (quick rush), carbs (energy), omega 3s (brain food) Things to use to work with them: analytical data, statistical data, copy of information for social platform, goals. How you can work with them: To grow your social media presence, and data studies, to learn how to be less resistant to change as well as to be, look and appear more confident.
Cloud Deity God Of: All known, unknown and held information on the internet, knowledge, memory, balance (both destructive and non-destructive knowledge) Plants & Trees: Rosemary, Thyme, Cacti, Cedar, Ferns Elements: Water Celestial Body/Planet: Saturn Scents and Incense: Rosemary, Jasmine, cedarwood Stones & Gems: Turquoise, Red Jasper, Sapphires Tarot card: Magician Colours: purple and pink Candle Colour: Purple Offerings: Herbal teas, water, omega 3s (brain power), savoury, spicy Things to use to work with them: Memory stick, notes, notebook, photos, computer, phone, books, camera How you can work with them: Memory recall, sourcing information, retaining information, studying, school, balance in your life
Web Deity God Of: The internet, duality (positive and negative), change, expression Plants & Trees: Fungai, Palm Trees, marigolds Elements: Fire Celestial Body/Planet: Sun Scents and Incense: Orange, Rosemary, Cinnamon Stones & Gems: Amber, Obsidian, fluorite Tarot card: The World Colours: Yellow, Orange, Green Candle Colour: Orange Offerings: Alcohol, water, sweet, spicy, carbs, any junk food Things to use to work with them: Electronics that can access web pages How you can work with them: Finding duality in the world, working with them via searches and teachings, how to stop resisting change, self-expression
Conductor Deity God Of: Electricity, power, energy, action, travel, courage & fear Plants & Trees: Oak Trees, sugarcane, lemon trees, Lemon balm Elements: Electricity Celestial Body/Planet: Venus Scents and Incense: Orange, lemon, Ginger Stones & Gems: Quartz, Citrine, sunstone Tarot card: Swords Colours: Yellow, white, gold Candle Colour: Yellow or Gold Offerings: Coffee, alcohol, water, soups, fruits and veggies, carbs, protein Things to use to work with them: Battery, anything electronic, metals How you can work with them: Powering wards, spellwork and yourself. Action-based plans and spellwork, exercise and general movement, travel, working on self-courage and fears.
This is a highly controversial topic and quite frankly I will not have any arguing on this post. If you simply do not believe in this? Move on. If it's not harming anything or anyone why do you care? The answer is you don't. I will block you from my page if I see anything. General discussion is fine, but being nasty? No.
Would you be interested in the rest of my posts? Check out the Masterpost.
Blessings,
Juniper
12 notes
·
View notes
Text
Researching stuff.
Adding links here to methods for finding out things, because on the modern internet, actually finding out accurate information is now uniformly obfuscated by the relentless enshitification of search functions, proliferation of search engine optimised content mills, nation state level intentional misinformation and propaganda programs, and of course, these days, all the crap sources above are endlessly enriched by the output of generic Large Language Model plagiarism statistical bullshit engines, both image and text (And video and Bot and so forth).
Finding academic and peer reviewed Journal Articles - they haven't quite fucked google scholar yet, so it's better than the enshittified google or bing or <insert enshittified search bar embed here> whatever.
So I generally hit up Google Scholar for whatever subject, author name, paper title or similar that I've gleaned from whatever article or mention or wikpedia page sparked my interest. Often that gets me what I want, as there's often a link to a pdf of what I need within those search results. Yay.
If that doesn't work, then I start escalating, usually via the methodology here described at Logic of Science's blog:
They wrote it down so I don't have to. Excellent. Although some of the links in there have degraded. So the main ones I'll put here:
And then there's the pirate nuclear option, Sci Hub. Because it makes the big publishers and corporates really angry, don't use sci hub from a work or academic 'net access environment. Also it necessarily moves around a lot, so I generally search up where is sci hub now, to avoid going to a link that's expired or may now be a honeypot/trap:
Also, look out for content mill generated fake journals. I usually check here:
The other thing that's getting harder is finding out whether an image is misattributed or just plain fake. So right click and save the image, and then go to images dot google dot com, which is nowhere near as good as it used to be, but still not entirely enshittified, and click on the wee camera icon to the right and upload the image, and look through the results. What you find is _All_ the places that have posted that image, page after page of them. Scroll through - click on the ones that seem to be the oldest, check who's posting them. What you often find with viral outrage images is that they are _not_ what you think, especially if the image is a bit old, a bit bitrotted, or there's something else wrong - the clothing isn't right for the country/culture/time being outraged about, or something like that. Sometimes you find out that it's true, but most of the time you find out that it's wrong, that someone has just done a quick search for an image that roughly matches the outrage or the politics they want to push, added some outragey comments, and shared it, and enjoyed their flamey fire. I've been doing this for decades, ever since I started using a browser capable of image searching, mainly because I was outraged at people posting fake geology memes. But it works just as well on finding anything else.
And of course, if it's to a website, see if the wayback machine still has it cached:
29 notes
·
View notes
Text
Google Analytics
Google Analytics (GA) is a free web and app analytics service from google that tracks how users interact with your website or mobile app. It Collects data like visitor numbers, page views,session duration, bounce rate, and user demografics, and user demographics,and presents it in easy to understand reports.By analyzing traffic from Search engines , advertising platforms, and social media , you can evaluate the impact of your marketing efforts.

Key Features
Visitor Statistics: Measure overall site traffic and Segment it into new users versus returning users.
Behaviour Tracking: Find out which of your Pages draw the most attention, see how long Visitors Stay on each, and map out their paths through yor Site.
Acquisation Insights: Discover where your User Come from- organic Search, paid ads, referals, or Social media.
Conversion & Goals: Track Specific actions you define as goals.
Real-time Reporting: It display data on active Visitors and their actions during the last 30 minutes , updating live- usually within seconds to a few minutes.
Why It's Useful
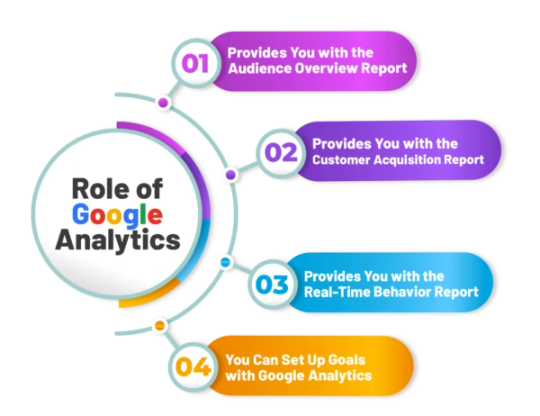
Optimize your Website: Find exact Pages where users are leaving, and refine their content and design to reduce dropout.
Improve marketing ROI: Track which campaigns drive the most Conversions.
Understand your audience: Segment users by demographics,interests and device type.
Make informed decisions: Utilize data to guide content,design,and business Strategy.
Use Cases Across Industries
Whether you run an e-commerce store, a B2B company, a news website, or a nonprofit organization, Google Analytics enables you to:
Monitor sales funnels
Identify high-performing pages and drop-off points
Segment users by behavior or source
A/B test content and features
Refine marketing strategy using real-time and historical data
Conclusion
Google analytics is a powerful and accessible tool for understanding your Website's audience and performance. It uses AI-powered insights, real time reporting , and predictive metrics -like purchase Probability and Churn risk- to help businesses understand User behaviour deeply and act on it quickly. It helps you make smarter decisions-from marketing to Site design-based on real user behaviour and trends.
To know More: Google analytics
2 notes
·
View notes
Text
WhatMatters
Your guide to California policy and politics

By Lynn La
May 28, 2025
Presented by CA Primary Care Association, The Nature Conservancy, TURN – The Utility Reform Network and San Jose Spotlight

Good morning, California.
CA continues fight with other states over reproductive care

A Planned Parenthood physician inside a consultation room at the health center in Sacramento on Feb. 1, 2022. Photo by Carlos Barria, Reuters
After the U.S. Supreme Court overturned federal abortion protections in 2022, California lawmakers moved quickly to make the state a “safe haven” for reproductive health care. But while California has some of the strongest laws ensuring abortion rights, other states’ restrictions can make performing or seeking the procedure from California doctors more complicated.
On Tuesday California Attorney General Rob Bonta, along with 19 other attorneys general, urged the American Medical Association to do more about protecting prospective OB-GYNs seeking certification. To become board certified, OB-GYN candidates must travel to Dallas, where the American Board of Obstetrics and Gynecology is headquartered, to complete their in-person certifying exam.
Under Senate Bill 8, Texas has a near-total ban on abortions and penalizes abortion providers. Because of this, the attorneys general argue that the in-person requirements lead some candidates from their states to fear for their legal and physical safety in Texas.
Though California struggles to provide wide access to maternity care, there are over 3,000 OB-GYNs employed in California — the highest number of any state — according to the most recent data available from the U.S. Bureau of Labor Statistics.
Attorneys’ general testimony to the AMA: “The web of confusing and punitive state-based restrictions creates a legal minefield for medical providers. … Indeed, at least one anti-choice group has publicly announced that it is actively recruiting individuals, including disgruntled ex-boyfriends, to bring cases under SB8’s bounty hunter provision.”
The attorneys general suggest either relocating the testing sites to states where abortion is not restricted; pivoting to remote testing; or granting some exemptions to the in-person exam.
Bonta’s call to the medical association comes as the state Senate is considering a bill that aims to protect California abortion providers beyond state lines.
Last week the Assembly advanced the measure, which would help shield California pharmacists, doctors and hospitals from penalties for dispensing the abortion pill mifepristone to out-of-state patients. The proposal would also strengthen privacy protections, such as removing prescriber names from abortion medication labels.
Focus on Inland Empire: Each Wednesday, CalMatters Inland Empire reporter Deborah Brennan surveys the big stories from that part of California. Read her newsletter and sign up here to receive it.
Other Stories You Should Know
CA port workers feel tariff squeeze

Dock cranes at the Port of Long Beach on May 5, 2025. Photo by David Swanson, Reuters
Since their inconsistent April rollout, President Donald Trump’s tariff policies have had the potential to upend California’s businesses, public pensions and budget. But the tariffs are also disrupting workers laboring at the state’s biggest ports, writes CalMatters’ Levi Sumagaysay.
Across California, port executives and spokespeople have reported notable signs of slowdown:
At the Port of Long Beach, cancellations are beginning to exceed levels seen during the pandemic.
At the Port of Los Angeles, 80 ships were expected to arrive in May, but 17 have been canceled and 10 have been canceled for June. (In May of last year, there were a total of 12 cancellations.)
At the Port of Oakland, April saw a significant 15% month-over-month drop in container activity.
With fewer goods coming in and out of the state, there is less work to go around: Union representatives report that part-time port workers aren’t getting any hours, and port security workers are struggling to carry out their jobs with few workers to look after. Truck drivers also say they are seeing less work.
Eric Tate, secretary-treasurer of Teamsters Local 848, which represents Southern California truck drivers: “We’re trying to gear up and quickly move stuff around. We’re trying to save Christmas.”
Read more here.
CA tech department finds zero high-risk systems

Illustration by Adriana Heldiz, CalMatters; iStock
By law, the California Department of Technology must submit a report every year on whether state agencies and entities are using high-risk automated systems that can affect people’s lives.
In its most recent findings, the department said that none of the nearly 200 state entities it surveyed uses high-risk automated systems — despite a handful of legislative analyses concluding that California must spend millions of dollars a year to monitor the state’s use of high-risk algorithms.
As CalMatters’ Khari Johnson explains, high-risk algorithms are systems that can assist or replace human decision making. In the winter of 2020, the California Employment Development Department paused unemployment benefits for 1.1 million people after it used artificial intelligence tools to mistakenly flag thousands of legitimate unemployment applicants as fraudulent.
The California Department of Corrections and Rehabilitation also uses automated systems to assign recidivism scores to inmates, including one system that has a documented history of racial bias.
But the technology department’s assessment is based on self reports, and it’s up to each agency to determine whether they are using a high-risk system. Critics of the report argue agencies should expand their definition of high-risk systems to include algorithms such as the ones that the employment and corrections departments are using.
Read more here.
And lastly: CA’s ‘science of reading’ bill

Sixth-grade students read at Stege Elementary School in Richmond on Feb. 6, 2023. Photo by Shelby Knowles for CalMatters
California lawmakers reworked a bill that now seeks to provide funding for phonics-based instruction in K-12 public schools, but stops short of requiring the teaching method. CalMatters’ Carolyn Jones and video strategy director Robert Meeks have a video segment on the bill as part of our partnership with PBS SoCal. Watch it here.
SoCalMatters airs at 5:58 p.m. weekdays on PBS SoCal.
California Voices
CalMatters columnist Dan Walters: The state Senate shunted a bill last week that would have made building housing easier, undermining the Legislature’s own goal of increasing housing production.
Other things worth your time:
Some stories may require a subscription to read.
Trump threatens to strip federal funds to CA over transgender youth athletes // Los Angeles Times
New CA rule for trans athletes faces criticism from all side // San Francisco Chronicle
CA schools see 9% surge in homeless students as funds decrease // EdSource
US officials visit Alcatraz amid Trump’s plan to reopen island prison // The Guardian
Undercover ICE agents begin making arrests at SF immigration vourt // The San Francisco Standard
Stanford scientists detect new COVID variant in CA as US moves to tighten vaccine access // San Francisco Chronicle
Bakersfield girl facing deportation could die within days of losing medical care // Los Angeles Times
Anaheim to decide how first $15M from Disney for affordable housing should be used // The Orange County Register
FAA didn't issue key notice about malfunctioning airport weather observation system before deadly San Diego crash // KPBS
CA’s pelicans are once again starving. This year, it’s the babies // KQED
See you next time!
Tips, insight or feedback? Email [email protected]. Subscribe to CalMatters newsletters here. Follow CalMatters on Facebook and Twitter.
About Us· How We're Funded· Subscribe· Donate
CalMatters 1017 L Street #261 Sacramento, CA 95814 United States
2 notes
·
View notes
Text
Commonwealth Scholarship Results: Tips for Future Applicants
The Commonwealth Scholarship Commission (CSC) within the UK annually awards scholarships to individuals from Commonwealth nations, enabling them to pursue postgraduate studies inside the UK. These scholarships aim to help proficient individuals who've the ability to make sizeable contributions to their domestic nations. The choice technique is rigorous, involving a couple of degrees, and the effects are eagerly awaited by using applicants global.

When Will Common Wealth Scholarship Result Come Out
Ministry of Education
+eight
Study UK Homepage eight
GOV.UK
+eight
Commonwealth Scholarships
Understanding the Commonwealth Scholarship Results
The assertion of the Commonwealth Scholarship consequences is a end result of a comprehensive choice technique. Applicants are evaluated based on academic merit, the potential impact of their work at the improvement in their home international locations, and their leadership abilities. The consequences are usually published at the reliable CSC internet site and communicated to the nominees via their respective nominating corporations.
Accessing the Results
To get admission to the scholarship consequences, applicants must go to the legit Commonwealth Scholarship Commission website's "Scholarships Results" web page. This page affords certain statistics approximately the results of various scholarship applications. Additionally, applicants are advised to live in contact with their nominating organizations or relevant educational our bodies of their home countries, as those groups frequently receive the effects at once and might provide personalised guidance.
GOV.UK
+9
Commonwealth Scholarships
+nine
Commonwealth Scholarships
+9
Post-Result Procedures
For people who are offered the scholarship, the following steps involve formal attractiveness, visa packages, and preparations for analyzing in the UK. It's critical for a hit applicants to adhere to the timelines and recommendations supplied by means of the CSC and their chosen universities to make sure a smooth transition.
For Applicants from India
Indian candidates can discuss with the Ministry of Education's legitimate announcements for information on the very last effects and similarly commands. The Ministry often publishes public notices regarding the Commonwealth Scholarships, which can be accessed thru their authentic internet site.
#When Will Common Wealth Scholarship Result Come Out#class 12th passed students#college pass students apply
2 notes
·
View notes
Text
Why Tableau is Essential in Data Science: Transforming Raw Data into Insights

Data science is all about turning raw data into valuable insights. But numbers and statistics alone don’t tell the full story—they need to be visualized to make sense. That’s where Tableau comes in.
Tableau is a powerful tool that helps data scientists, analysts, and businesses see and understand data better. It simplifies complex datasets, making them interactive and easy to interpret. But with so many tools available, why is Tableau a must-have for data science? Let’s explore.
1. The Importance of Data Visualization in Data Science
Imagine you’re working with millions of data points from customer purchases, social media interactions, or financial transactions. Analyzing raw numbers manually would be overwhelming.
That’s why visualization is crucial in data science:
Identifies trends and patterns – Instead of sifting through spreadsheets, you can quickly spot trends in a visual format.
Makes complex data understandable – Graphs, heatmaps, and dashboards simplify the interpretation of large datasets.
Enhances decision-making – Stakeholders can easily grasp insights and make data-driven decisions faster.
Saves time and effort – Instead of writing lengthy reports, an interactive dashboard tells the story in seconds.
Without tools like Tableau, data science would be limited to experts who can code and run statistical models. With Tableau, insights become accessible to everyone—from data scientists to business executives.
2. Why Tableau Stands Out in Data Science
A. User-Friendly and Requires No Coding
One of the biggest advantages of Tableau is its drag-and-drop interface. Unlike Python or R, which require programming skills, Tableau allows users to create visualizations without writing a single line of code.
Even if you’re a beginner, you can:
✅ Upload data from multiple sources
✅ Create interactive dashboards in minutes
✅ Share insights with teams easily
This no-code approach makes Tableau ideal for both technical and non-technical professionals in data science.
B. Handles Large Datasets Efficiently
Data scientists often work with massive datasets—whether it’s financial transactions, customer behavior, or healthcare records. Traditional tools like Excel struggle with large volumes of data.
Tableau, on the other hand:
Can process millions of rows without slowing down
Optimizes performance using advanced data engine technology
Supports real-time data streaming for up-to-date analysis
This makes it a go-to tool for businesses that need fast, data-driven insights.
C. Connects with Multiple Data Sources
A major challenge in data science is bringing together data from different platforms. Tableau seamlessly integrates with a variety of sources, including:
Databases: MySQL, PostgreSQL, Microsoft SQL Server
Cloud platforms: AWS, Google BigQuery, Snowflake
Spreadsheets and APIs: Excel, Google Sheets, web-based data sources
This flexibility allows data scientists to combine datasets from multiple sources without needing complex SQL queries or scripts.
D. Real-Time Data Analysis
Industries like finance, healthcare, and e-commerce rely on real-time data to make quick decisions. Tableau’s live data connection allows users to:
Track stock market trends as they happen
Monitor website traffic and customer interactions in real time
Detect fraudulent transactions instantly
Instead of waiting for reports to be generated manually, Tableau delivers insights as events unfold.
E. Advanced Analytics Without Complexity
While Tableau is known for its visualizations, it also supports advanced analytics. You can:
Forecast trends based on historical data
Perform clustering and segmentation to identify patterns
Integrate with Python and R for machine learning and predictive modeling
This means data scientists can combine deep analytics with intuitive visualization, making Tableau a versatile tool.
3. How Tableau Helps Data Scientists in Real Life
Tableau has been adopted by the majority of industries to make data science more impactful and accessible. This is applied in the following real-life scenarios:
A. Analytics for Health Care
Tableau is deployed by hospitals and research institutions for the following purposes:
Monitor patient recovery rates and predict outbreaks of diseases
Analyze hospital occupancy and resource allocation
Identify trends in patient demographics and treatment results
B. Finance and Banking
Banks and investment firms rely on Tableau for the following purposes:
✅ Detect fraud by analyzing transaction patterns
✅ Track stock market fluctuations and make informed investment decisions
✅ Assess credit risk and loan performance
C. Marketing and Customer Insights
Companies use Tableau to:
✅ Track customer buying behavior and personalize recommendations
✅ Analyze social media engagement and campaign effectiveness
✅ Optimize ad spend by identifying high-performing channels
D. Retail and Supply Chain Management
Retailers leverage Tableau to:
✅ Forecast product demand and adjust inventory levels
✅ Identify regional sales trends and adjust marketing strategies
✅ Optimize supply chain logistics and reduce delivery delays
These applications show why Tableau is a must-have for data-driven decision-making.
4. Tableau vs. Other Data Visualization Tools
There are many visualization tools available, but Tableau consistently ranks as one of the best. Here’s why:
Tableau vs. Excel – Excel struggles with big data and lacks interactivity; Tableau handles large datasets effortlessly.
Tableau vs. Power BI – Power BI is great for Microsoft users, but Tableau offers more flexibility across different data sources.
Tableau vs. Python (Matplotlib, Seaborn) – Python libraries require coding skills, while Tableau simplifies visualization for all users.
This makes Tableau the go-to tool for both beginners and experienced professionals in data science.
5. Conclusion
Tableau has become an essential tool in data science because it simplifies data visualization, handles large datasets, and integrates seamlessly with various data sources. It enables professionals to analyze, interpret, and present data interactively, making insights accessible to everyone—from data scientists to business leaders.
If you’re looking to build a strong foundation in data science, learning Tableau is a smart career move. Many data science courses now include Tableau as a key skill, as companies increasingly demand professionals who can transform raw data into meaningful insights.
In a world where data is the driving force behind decision-making, Tableau ensures that the insights you uncover are not just accurate—but also clear, impactful, and easy to act upon.
#data science course#top data science course online#top data science institute online#artificial intelligence course#deepseek#tableau
3 notes
·
View notes
Text
The Rise of the 66 Lottery: Why More Players Are Joining the Game
In the dynamic world of lottery games, the 66 lottery has emerged as a unique and popular option for both casual and serious players. Its combination of simplicity, frequent draws, and easy access has made it a go-to choice in several countries, particularly across Asia. Whether you're new to lottery gaming or a long-time enthusiast, the 66 lottery offers a fresh and exciting experience.
What Is the 66 Lottery?
The 66 lottery is a number-based game where participants select digits in the hope of matching those drawn by the official system. Unlike large national or international lotteries that offer huge jackpots but lower odds, the 66 lottery focuses on smaller, more frequent wins. The name “66” may vary in meaning depending on the country or platform, but it generally refers to the format or the local branding of the game.
Most versions of the 66 lottery are based on 2-digit or 3-digit number draws, where players choose combinations from 00 to 99 or 000 to 999. Draws usually occur once or multiple times daily, and results are quickly announced via apps, websites, or even local betting agents.
Why Is the 66 Lottery So Popular?
There are several reasons behind the growing popularity of the 66 lottery:
Quick Results One of the biggest advantages of the 66 lottery is the speed at which results are announced. Many games are drawn daily, and some platforms even host multiple rounds per day. This appeals to players who prefer immediate outcomes over waiting for a weekly draw.
Low Entry Barrier Players can often place bets with small amounts of money, making the game accessible to a wide range of people. Whether you're a student, a working professional, or someone just looking for light entertainment, the 66 lottery doesn’t require a large investment.
Simple Rules The rules of the 66 lottery are easy to understand. There’s no need for advanced strategies or deep statistical knowledge. Simply choose your numbers, place a bet, and wait for the draw.
Cultural Influence In some cultures, the number 66 is considered lucky or symbolic. It’s associated with prosperity, double fortune, or harmony, adding a layer of cultural meaning to the game that makes it even more attractive.
Online Accessibility With many platforms offering mobile and web-based lottery services, the 66 lottery is now just a few taps away. This convenience has made it especially appealing in regions with high mobile usage.
How to Play the 66 Lottery
To participate in the 66 lottery, follow these basic steps:
Register on a trusted lottery website or app.
Choose your numbers – typically two or three digits depending on the format.
Select your bet amount – higher bets often lead to higher payouts.
Confirm your ticket and wait for the draw.
Check the results on the platform or receive notifications if you win.
Is the 66 Lottery Safe?
Like any gambling-related activity, safety depends on where and how you play. Many legitimate online platforms host the 66 lottery and operate under local or regional licenses. However, there are also scams and unregulated operators to watch out for.
To ensure safety:
Use only licensed platforms with good reputations.
Avoid sharing sensitive personal or financial information with unverified sources.
Read user reviews and check for customer support availability.
Tips for Playing the 66 Lottery
Although lotteries are based on chance, here are a few smart tips to enhance your experience:
Stick to a budget: Set a limit and avoid chasing losses.
Use a mix of numbers: Some players choose a mix of odd and even numbers or switch combinations regularly.
Play in groups: Lottery pools or group play can improve your chances without increasing costs.
Track past results: Some players believe in following number trends, though outcomes are always random.
Conclusion
The 66 lottery has become a favorite among lottery players for its simplicity, affordability, and fast-paced nature. Its daily draws, easy-to-understand mechanics, and online availability make it a fun and convenient option for anyone looking to test their luck. However, like any form of gambling, it’s important to play responsibly and always use verified platforms.
Whether you play for fun, cultural significance, or the thrill of a potential win, the 66 lottery offers a unique lottery experience that continues to attract thousands of new players every day.
1 note
·
View note