#WE BOTH DISCOVERED IOT AT THE SAME TIME
Explore tagged Tumblr posts
Note
PHANTOM PHANTOM THE FNAF TRAILER IS OUTTTT AAAAAA
LUA I LITERALLY JSUT SAW IT I JUST SAW IT!!!!!!! YOOOOOOOOO I WAS JUST ABOTU TO TELL YOU
#WE BOTH DISCOVERED IOT AT THE SAME TIME#THATS REALLY FUNN YTHO#YOOOOOOOOOOOO#the animatronic designs suck a bit more than in game but its FINE#I will be fine about it#but it looks so cool im very excited#lua tag#asks#mutuals#rambling#phever dreams with phantom
4 notes
·
View notes
Text
Key Trends That Will Shape the Future of SCCM
In today's rapidly evolving technological landscape, businesses are constantly searching for ways to streamline their operations and enhance efficiency. One tool that has proven to be invaluable in this regard is SCCM (System Center Configuration Manager). SCCM is a comprehensive management solution that allows IT departments to automate tasks, deploy software, secure devices, and monitor system health. As we look ahead to the future, there are several key trends that will shape the landscape of SCCM and drive its continued evolution and adoption.
What is SCCM?
SCCM is a popular IT tool used to manage computers for businesses; discover how best to utilize it! Microsoft System Centre provides a comprehensive suite of products to manage IT systems across an organisation, such as software distribution, operating system deployment, patch management, network access protection and hardware/software inventory management.
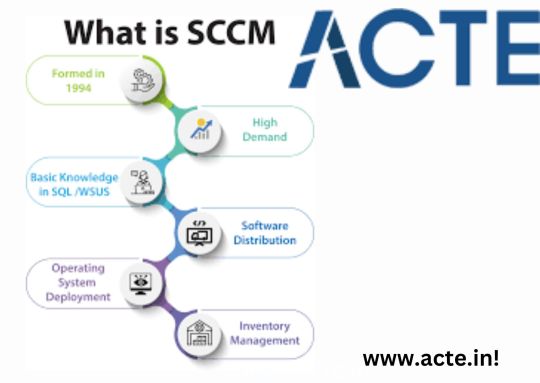
IT managers rely on SCCM for managing vast arrays of systems – including virtual machines (VMs).
Benefits of SCCM:
Consolidated Management:
SCCM ensures all company PCs use identical software and rules, enabling IT managers to control all machines from a unified interface, saving time. Furthermore, updates to software or security rules across multiple machines become much simpler with SCCM’s instant implementation feature.
Automated Deployment:
SCCM automates software, hardware and security policy deployment to save manual effort and guarantee all machines run the same software and rules. This reduces manual intervention while ensuring consistency across machines.
Automatic Patch Management:
SCCM allows IT personnel to quickly and efficiently patch systems without manually checking for fixes, which helps reduce patching time as well as potential system compromise due to unpatched vulnerabilities. This minimizes both system downtime and vulnerability exposure from unreported flaws.
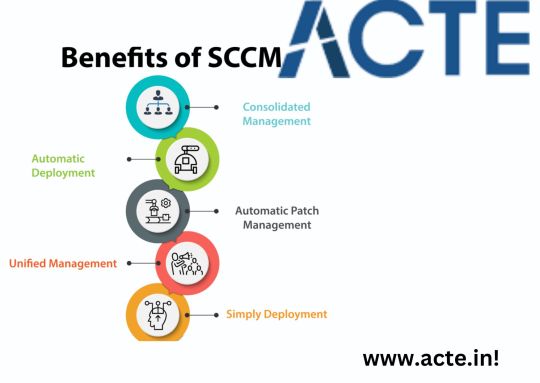
Simplify deployment:
SCCM allows administrators to quickly and easily create a package that can quickly deploy multiple PCs according to environment or organisation needs.
Advantages of SCCM
SCCM provides several advantages that make it an attractive solution for network and system management tasks.
Lower Costs:
It helps reduce network management expenses. Its single network license also minimizes software licensing expenses.
Strengthened Security: SCCM’s integrated security solution provides comprehensive protection for all company systems. It assists administrators in managing security patches, updates and configuration settings across all computers, monitoring system health indicators, and recognizing threats.
Enhance Visibility: Provides IT infrastructure visibility, allowing companies to monitor and manage IT assets with ease.
Achieve Delivery Speed and Efficiency: It gives administrators the speed to quickly deploy applications and updates across all systems with ease.
FUTURE TRENDS AND CHALLENGES OF SCCM
Cloud Integration:
Cloud computing is becoming increasingly important in IT management. SCCM is likely to continue integrating with cloud services like Microsoft Azure and AWS to enhance scalability, reliability, and global accessibility.
Endpoint Diversity:
The proliferation of different endpoint devices, including smartphones, tablets, and IoT devices, means SCCM will need to support a wider range of device types and operating systems.
Security and Compliance:
With the growing threat landscape, SCCM will play a vital role in ensuring endpoint security and compliance with regulations like GDPR and HIPAA. Expect to see enhanced security features and automation for patch management and threat detection.
Automation and AI:
SCCM will leverage automation and artificial intelligence to streamline routine tasks, optimize resource allocation, and improve troubleshooting. This can include predictive maintenance, self-healing capabilities, and intelligent insights.
Remote Work Support:
The rise of remote work has made it essential for SCCM to manage and secure devices outside traditional corporate networks. Expect more features related to remote device management and security.
Zero Trust Security Model:
SCCM will align with the zero trust security model, ensuring that trust is never assumed, and devices are continuously verified and authenticated before granting access to resources.

Containerization and Microservices:
Embracing containerization and microservices architecture can make SCCM more agile and scalable, allowing for easier updates and customization.
User-Centric Management:
SCCM will shift towards a more user-centric approach, focusing on delivering a personalized and seamless experience for end-users, regardless of the device they use.
AI-Driven Analytics:
SCCM will increasingly use AI-driven analytics to gather insights about device performance, user behavior, and software usage patterns to make data-driven decisions and optimizations.
Edge Computing:
As edge computing gains prominence, SCCM will need to extend its capabilities to manage and secure devices at the edge, which may have limited connectivity to central data centers.
Compliance as Code:
Compliance requirements will become more automated, allowing organizations to define compliance rules as code and apply them consistently across their environments using SCCM
Hybrid Environments:
Many organizations will maintain hybrid environments with on-premises and cloud-based resources. SCCM will need to seamlessly manage devices in these hybrid environments.
Sustainability and Green IOT:
There will be a growing focus on sustainability, and SCCM may incorporate features to help organizations manage and reduce their carbon footprint through efficient resource allocation and power management.
Multi-Tenancy:
For managed service providers and large organizations, SCCM may evolve to support multi-tenancy, allowing them to manage multiple customer environments from a single console securely.
User Education and Training:
As threats evolve, user education and training will be crucial. SCCM may offer features to facilitate cybersecurity training and awareness campaigns for end-users.
As the future unfolds, SCCM will continue to adapt and evolve to meet the ever-changing needs of businesses. The key trends such as - cloud integration, intelligent automation, enhanced security measures, and unified endpoint management - will shape the future of SCCM, driving its adoption and cementing its role as a critical tool for IT departments. By staying at the forefront of these trends, organizations can leverage SCCM to optimize their operations, enhance productivity, and achieve their business objectives with confidence.
Please keep in mind that the SCCM takes in the future may vary depending on market dynamics, customer demands, and technological advancements. To get the most up-to-date information on SCCM's future technologies and strategies.
I recommend visiting SCCM's official website or the ACTE Institute training programs covering all aspects of SCCM, providing valuable support for individuals aspiring to become SCCM Developer.
I highly recommend that you contact ACTE Institution because they offer certifications and job placement opportunities. Experienced teachers can help you learn better. You can find these services both online and offline. Take things step by step and consider enrolling in a course if you’re interested.
For More Update Just Follow My Account
1 note
·
View note
Text
Pluralistic, your daily link-dose: 26 Feb 2020
Today’s links
Brave autolinks 404s to the Wayback Machine: The internet’s time-traveling, privacy respecting, ad-busting browser.
Clarence Thomas admits he blew it on Brand X: A very safe mea culpa from the man who helped kill Net Neutrality.
Medicare for All would be the biggest take-home pay increase in a generation: Even if my taxes went up by six figures (!), I’d still save money.
The Smithsonian publishes 2.8m hi-rez images into the public domain: Tired: “It belongs in a museum!” Wired: “It belongs to the world!”
McMansion Hell visits 1971: Before “lawyer foyers” there were “paralegal foyers.”
This day in history: 2005, 2015, 2019
Colophon: Recent publications, current writing projects, upcoming appearances, current reading
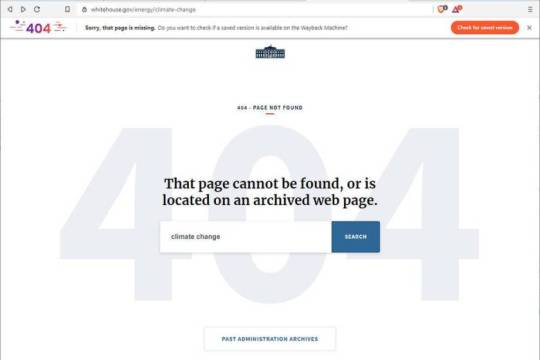
Brave autolinks 404s to the Wayback Machine (permalink)
A new feature in Brave’s excellent, privacy-centric browser: when you visit a dead page, it automagically checks to see if there’s a cached copy in the Internet Archive and directs you to that instead.
The Archive is crushing it. Working with Wikimedia, they’ve linked every book citation in Wikipedia to the relevant passage in a scanned book in their library section.
Brave’s plugin works on 404 (page not found) errors, and also for 408, 410, 451, 500, 502, 503, 504, 509, 520, 521, 523, 524, 525, and 526 errors (451 is “page censored!”).
https://www.theverge.com/2020/2/26/21154096/brave-browser-wayback-machine-404-internet-archive-lost-pages

Clarence Thomas admits he blew it on Brand X (permalink)
In 2005, Clarence Thomas wrote the majority opinion in Brand X, a case that ratified GW Bush’s FCC’s power to interpret both the statutes and jurisprudence of telcoms law however it wants, overriding judges.
https://www.law.cornell.edu/supct/html/04-277.ZS.html
That decision meant that GWB’s FCC could arrange telcoms rules to suit the Big Cable donors GWB relied on. It meant that Obama’s FCC could reverse those rules and impose net neutrality. It meant Trump’s FCC could reverse Obama’s FCC and kill net neutrality.
Now, Thomas has written a dissent in Baldwin, a new case published Monday, in which he admits that he blew it in Brand X, by giving political appointees from the administrative branch the power to overrule both Congress and the courts.
https://www.supremecourt.gov/opinions/19pdf/19-402_o75p.pdf
When the Ajit Pai decision to kill net neutrality was brought before a circuit judge, she called it “unhinged.” Then she upheld it, because Brand X tied her hands.
Unfortunately, Thomas is the sole dissent in Baldwin, whose appeal SCOTUS will not to hear, leaving Brand X unchallenged. Given Thomas’s historic cowardice when it comes to challenging the establishment, this is a nice safe way to mea culpa without risking wrath of plutes.
“Although I authored Brand X, it is never too late to ‘surrende[r] former views to a better considered position.’ Brand X appears to be inconsistent with the Constitution, the Administrative Procedure Act (APA), and traditional tools of statutory interpretation. Because I would revisit Brand X, I respectfully dissent from the denial of certiorari.” -C. Thomas.
https://arstechnica.com/tech-policy/2020/02/clarence-thomas-regrets-ruling-that-ajit-pai-used-to-kill-net-neutrality/

Medicare for All would be the biggest take-home pay increase in a generation (permalink)
UC Berkeley economist Gabriel Zucman: “Because this is my lot in life, I will note again that Medicare for All would lead to the biggest take-home pay increase in a generation for working families, because it would replace private health insurance premiums (a huge privatized head tax) by taxes based on ability to pay.”
https://twitter.com/gabriel_zucman/status/1232295342185558018
We pay more than $2000/mo for gold-plated healthcare from Cigna through my wife’s blue-chip employer, where she is an exec. When my daughter broke a bone, our ER visit to the preferred hospital (across the street from corporate HQ) cost $2700 in excesses.
The kid didn’t even see a doc. $2700 in out-of-pockets was for a Tylenol, an X-ray, and a one-minute consult with a physician’s assistant, who referred us to an orthopedist. The ortho and ER initially refused to treat my daughter unless I signed a binding arbitration waiver.
Cigna also just declined a pain therapy course recommended by my specialist, head of a prominent university’s pain clinic whose papers on the therapy are the most-cited in the field: “It’s experimental.” It will cost me $52,000 in out of pockets if I want to proceed.
So, keeping track: we’re currently spending $24k/yr on health care, and about the same in out-of-pockets, and our care is being rationed. If I want the care the top specialist in the region recommends, that’s another $52k.
Our inadequate private care, literally the best we can buy, would cost us $100k this year if we got the care our doctors recommended; $50k if we decided to ignore their advice and not get that care.
That is to say: if Medicare For All raised our taxes by ONE HUNDRED THOUSAND DOLLARS, we’d be breaking even. And getting better care. I grew up with Canadian healthcare, then 13 years of NHS UK care. The US system, at the very highest tier, is so much worse than either.

The Smithsonian publishes 2.8m hi-rez images into the public domain (permalink)
The Smithsonian has released 2.8 million hi-rez images into the public domain!
https://www.smithsonianmag.com/smithsonian-institution/smithsonian-releases-28-million-images-public-domain-180974263/
The images include reproductions of both 2D and 3D artifacts in the Smithsonian’s collection, from all 19 Smithsonian museums, hosted on an open access platform:
https://www.si.edu/openaccess
200,000 more images are slated for inclusion in 2020, and the scope of the whole project is to digitize all 155,000,000 images in the Smithsonian’s collections and dedicate them to the public domain for any use, including commercial use. It’s part of a “digital first” strategy that eschews hypothetical licensing revenue from art books and penny-postcards in favor of serving the public mission of a museum.
Here’s a crib from a keynote I gave about this to the first Museums and the Web Europe conference in Florence — museums have both an ethical and practical duty to serve the public rather than relying on plutes and licensing.
https://mwf2014.museumsandtheweb.com/paper/glam-and-the-free-world/
Tldr: the public will support you and demand your preservation when austerity-crazed governments want to de-fund you. Plutes won’t — they’ll just offer to buy your collection for their mansions.
Anyway, this is amazeballs. The possibilities for remix, fine art, new work, and computational historical research are endless. This is the Smithsonian we pay our taxes for. It’s a brave, principled move. Go, Smithsonian go!

McMansion Hell visits 1971 (permalink)
The luckiest people in the world have never heard of McMansion Hell because they get to discover Kate Wagner’s superb dunks on architectural excess, cynicism and ill-founded optimism for the very first time!
Lately, Wagner’s been doing a “Yearbook,” revisiting proto-McMansions from 1971 to trace the primitive ancestors of today’s hulking atrocities. The latest installment is a $1.2m, 5000sqft titan in Morris County, New Jersey.
https://mcmansionhell.com/post/610960530721636352/the-mcmansion-hell-yearbook-1971
This beast predates the modern “lawyer foyer” and instead sports a “paralegal foyer,” which ” lacks the transom window above the door that enables the entryway to be seen from the street.”

I could listen to Wagner riff on bad kitchen design ALL DAY.

The realtor’s just rendered a bunch of virtual furnishings into this empty room! Wagner: “Personally I’d love to have a copy of the software that lets you 3D decorate random real estate listings – it’s like the Sims but for realtors.”

Wagner signs off with a promise of a “Brutalism Post.” Swoon!

This day in history (permalink)
#15yrsago: Dismantling fear, uncertainty, and doubt, aimed at Wikipedia and other free knowledge resources https://web.archive.org/web/20050301003539/http://www.freesoftwaremagazine.com/free_issues/issue_02/fud_based_encyclopedia/
#15yrsago: HOWTO break HP printer cartridge DRM https://constitutionalcode.blogspot.com/2005/02/cartridge-expiration-date-workarounds.html
#15yrsago: @Aaronsw asks why Stanford professors include so few astrologers http://www.aaronsw.com/weblog/001588
#15yrsago: Why John Gilmore won’t show his ID at airports http://old.post-gazette.com/pg/05058/462446.stm
#5yrsago: World War 3 Illustrated: prescient outrage from the dawn of the Piketty apocalypse https://boingboing.net/2015/02/26/world-war-3-illustrated-presc.html
#1yrago: Youtube ignored repeated reports about explicit suicide instructions spliced into cartoons on Youtube Kids https://pedimom.com/youtube-kids-scare/
#1yrago: New Orleans reduced homelessness by 90% (and saved a fortune) by giving homeless people homes https://www.wbur.org/hereandnow/2019/02/19/new-orleans-reducing-homeless-hurricane-katrina
#1yrago: Trump made history: introducing tax cuts made him LESS popular https://www.nakedcapitalism.com/2019/02/trump-choose-unpopular-president.html
#1yrago: How the payday loan industry laundered policy by paying academics to write papers that supported its positions https://www.washingtonpost.com/business/2019/02/25/how-payday-lending-industry-insider-tilted-academic-research-its-favor/?utm_term=.92930478ab59

Colophon (permalink)
Today’s top sources: Naked Capitalism (https://nakedcapitalism.com/”), Glenn Fleishman (https://twitter.com/glennf).
Hugo nominators! My story “Unauthorized Bread” is eligible in the Novella category and you can read it free on Ars Technica: https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
Upcoming appearances:
Canada Reads Kelowna: March 5, 6PM, Kelowna Library, 1380 Ellis Street, with CBC’s Sarah Penton https://www.eventbrite.ca/e/cbc-radio-presents-in-conversation-with-cory-doctorow-tickets-96154415445
Currently writing: I just finished a short story, “The Canadian Miracle,” for MIT Tech Review. It’s a story set in the world of my next novel, “The Lost Cause,” a post-GND novel about truth and reconciliation. I’m getting geared up to start work on the novel now, though the timing is going to depend on another pending commission (I’ve been solicited by an NGO) to write a short story set in the world’s prehistory.
Currently reading: Just started Lauren Beukes’s forthcoming Afterland: it’s Y the Last Man plus plus, and two chapters in, it’s amazeballs. Last week, I finished Andrea Bernstein’s “American Oligarchs” this week; it’s a magnificent history of the Kushner and Trump families, showing how they cheated, stole and lied their way into power. I’m getting really into Anna Weiner’s memoir about tech, “Uncanny Valley.” I just loaded Matt Stoller’s “Goliath” onto my underwater MP3 player and I’m listening to it as I swim laps.
Latest podcast: Gopher: When Adversarial Interoperability Burrowed Under the Gatekeepers’ Fortresses: https://craphound.com/podcast/2020/02/24/gopher-when-adversarial-interoperability-burrowed-under-the-gatekeepers-fortresses/
Upcoming books: “Poesy the Monster Slayer” (Jul 2020), a picture book about monsters, bedtime, gender, and kicking ass. Pre-order here: https://us.macmillan.com/books/9781626723627?utm_source=socialmedia&utm_medium=socialpost&utm_term=na-poesycorypreorder&utm_content=na-preorder-buynow&utm_campaign=9781626723627
(we’re having a launch for it in Burbank on July 11 at Dark Delicacies and you can get me AND Poesy to sign it and Dark Del will ship it to the monster kids in your life in time for the release date).
“Attack Surface”: The third Little Brother book, Oct 20, 2020.
“Little Brother/Homeland”: A reissue omnibus edition with a very special, s00per s33kr1t intro.
15 notes
·
View notes
Text
What Does the Bitcoin Blockchain Record?

Blockchain is a shared, immutable ledger for recording transactions, tracking assets and building trust. Discover why businesses worldwide are switching to blockchain technology.
First Blockchain overview
Definition of Blockchain: Blockchain is a shared, immutable ledger that facilitates the process of recording transactions and tracking assets in a business network. Assets can be tangible (house, car, cash, land) or intangible (intellectual property, patents, copyrights, brand). Almost anything of value can be tracked and transacted on a blockchain network, reducing risk and reducing all costs involved in the business. Blockchain importance: Business runs on information. The faster and more accurately information is received, the better. Blockchain is ideal for presenting information as it provides instantaneous, shared, and completely transparent information stored in a non-modifiable ledger that can only be accessed by authorized network members. A blockchain network can track orders, payments, accounts, production and much more. You can see all the details of a transaction from start to finish as members share a single view of the truth; so you get more confidence as well as new efficiencies and opportunities.

- All network participants have access to the distributed ledger and unmodifiable transaction records. With this shared ledger, transactions are recorded only once, eliminating duplication of the same transaction common in traditional business networks. - Once a transaction is recorded in the shared ledger, it cannot be modified or tampered with by any participant. If a log contains an error, a new transaction must be added to reverse the error and both transactions will be visible. - To speed up transactions, a set of rules called smart contracts are stored on the blockchain and these are executed automatically. A smart contract can define terms for corporate bond transfers, conditions for travel insurance payable, and more. What needs to change: Operations teams often put effort into repetitive record keeping and third-party verification. Record keeping systems can be vulnerable to fraud and cyberattacks. Limited transparency can slow data validation. Also, with the advent of the IoT, there is a huge explosion in transaction volumes. All of this slows business down, lowers profitability and means we need a better way. This is where blockchain comes into play. So how does Blockchain work? - These operations indicate the movement of a tangible (product) or intangible (ideal) entity. The burst can record the information you choose: who, what, when, where, how much and even what condition (like the temperature of a food shipment). - As an asset moves from one place to another or changes ownership, these blocks form a data chain. Blocks verify the exact time and order of transactions. The blocks are securely connected to each other to prevent any block being changed or another block being inserted between two existing blocks. - Each additional block strengthens the verification of the previous block and thus the entire blockchain. This provides a fundamental strength of immutability, giving the blockchain a tamper-evident structure. This creates a transaction ledger that you and other network members can trust, eliminating the possibility of a malicious user's interference.
What is the unity between the Bitcoin blockchain?
The Bitcoin blockchain is basically a tremendous, shared, encoded rundown of all tends to that hold Bitcoin adjusts. Each new square addresses the furthest down the line update to account adjusts. A square essentially alludes to a bunch of Bitcoin exchanges that are connected in light of the fact that they occurred inside a similar time span. New squares are made get-togethers mining happens or an exchange happens where Bitcoin is traded. Along these lines, it works similar as a public record, representing monetary exchanges and giving an approach to confirm that all Bitcoin clients have been outfitted with a similar data. Everybody can download a duplicate of the blockchain and use it to follow the way of Bitcoins starting with one Bitcoin exchange then onto the next. (It ought to be noticed that despite the fact that there is a record of each Bitcoin exchange at any point made, they are connected to a particular Bitcoin address, instead of a specifically recognizing name or email. Therefore, Bitcoin is considered pseudonymous.) The objective of a blockchain is to permit computerized data to be recorded and conveyed to each member, yet never altered. While a blockchain can be utilized to store quite a few information focuses (votes in a political decision, item inventories, state recognizable pieces of proof, deeds to homes, and so forth), Bitcoin simply utilizes blockchain as a way to straightforwardly record a record of installments. In a blockchain, every hub has a full record of the information that has been put away on the blockchain since its origin. For Bitcoin, this information incorporates the whole history of all Bitcoin exchanges. On the off chance that one hub has a mistake in its information, it can utilize the huge number of different hubs as a source of perspective highlight right itself. Blockchains comprise of a progression of individual squares, orchestrated in sequential request dependent on the request for exchanges. There are two sections to the data contained in a square. The initial segment comprises of the header components: data about the area and different information identified with the exchanges contained inside that square. For instance, a hash inside the header focuses to the past block. There are no hashes for beginning squares in light of the fact that these squares have no archetype. A merkle tree—an information structure utilized in software engineering to record exchanges—is utilized to show the succession of exchanges contained inside the square. Another hash inside the square contains timestamp data, the nonce, and the trouble level. Here is a concise clarification of every one of these parts: - Timestamp data: shows the time and date of the square's creation - Nonce: the number that is needed to be settled by diggers - Trouble level: means the trouble of the issue being settled. The subsequent part is the identifier data. Once more, this is a cryptographic hash work. It is produced by hashing the header components twice in succession. Blockchain More Anonymous Than a Bank Statement One of the supposed advantages (or dangers, contingent upon your standpoint) of Bitcoin is its exceptional obscurity. Those executing in Bitcoins should be attached to a particular Bitcoin address, as opposed to a specifically distinguishing name or email. However namelessness is fairly compromised due to the blockchain data ledger.1 Since each exchange is openly logged, one single penetrate of proprietorship character could prompt the disclosure of numerous different proprietors by basically following back the exchanges. The blockchain is even more mysterious than a bank articulation, however it's anything but an invulnerable smoke screen, as certain defenders of Bitcoin innovation like to state. What is Blockchain.com? Blockchain.com is a cryptocurrency blockchain explorer service as well as a cryptocurrency wallet and cryptocurrency exchange that supports Bitcoin, Bitcoin Cash and Ethereum. They also provide Bitcoin data charts, statistics and market information. Read the full article
0 notes
Text
If you did not already know
ClusterNet Clustering using neural networks has recently demonstrated promising performance in machine learning and computer vision applications. However, the performance of current approaches is limited either by unsupervised learning or their dependence on large set of labeled data samples. In this paper, we propose ClusterNet that uses pairwise semantic constraints from very few labeled data samples (< 5% of total data) and exploits the abundant unlabeled data to drive the clustering approach. We define a new loss function that uses pairwise semantic similarity between objects combined with constrained k-means clus- tering to efficiently utilize both labeled and unlabeled data in the same framework. The proposed network uses convolution autoencoder to learn a latent representation that groups data into k specified clusters, while also learning the cluster centers simultaneously. We evaluate and com- pare the performance of ClusterNet on several datasets and state of the art deep clustering approaches. … AutoKGE Knowledge graph embedding (KGE) aims to find low dimensional vector representations of entities and relations so that their similarities can be quantized. Scoring functions (SFs), which are used to build a model to measure the similarity between entities based on a given relation, have developed as the crux of KGE. Humans have designed lots of SFs in the literature, and the evolving of SF has become the primary power source of boosting KGE’s performance. However, such improvements gradually get marginal. Besides, with so many SFs, how to make a proper choice among existing SFs already becomes a non-trivial problem. Inspired by the recent success of automated machine learning (AutoML), in this paper, we propose automated KGE (AutoKGE), to design and discover distinct SFs for KGE automatically. We first identify a unified representation over popularly used SFs, which helps to set up a search space for AutoKGE. Then, we propose a greedy algorithm, which is enhanced by a predictor to estimate the final performance without model training, to search through the space. Extensive experiments on benchmark datasets demonstrate the effectiveness and efficiency of our AutoKGE. Finally, the SFs, searched by our method, are KG dependent, new to the literature, and outperform existing state-of-the-arts SFs designed by humans. … SOD SOD is an embedded, modern cross-platform computer vision and machine learning software library that expose a set of APIs for deep-learning, advanced media analysis & processing including real-time, multi-class object detection and model training on embedded systems with limited computational resource and IoT devices. SOD was built to provide a common infrastructure for computer vision applications and to accelerate the use of machine perception in open source as well commercial products. Designed for computational efficiency and with a strong focus on real-time applications. SOD includes a comprehensive set of both classic and state-of-the-art deep-neural networks with their pre-trained models. … Leave-One-Out Least Square Monte Carlo (LOOLSM) The least square Monte Carlo (LSM) algorithm proposed by Longstaff and Schwartz [2001] is the most widely used method for pricing options with early exercise features. The LSM estimator contains look-ahead bias, and the conventional technique of removing it necessitates an independent set of simulations. This study proposes a new approach for efficiently eliminating look-ahead bias by using the leave-one-out method, a well-known cross-validation technique for machine learning applications. The leave-one-out LSM (LOOLSM) method is illustrated with examples, including multi-asset options whose LSM price is biased high. The asymptotic behavior of look-ahead bias is also discussed with the LOOLSM approach. … https://analytixon.com/2022/09/02/if-you-did-not-already-know-1818/?utm_source=dlvr.it&utm_medium=tumblr
0 notes
Text
Why Edge Computing is gaining popularity

Why Edge Computing is gaining popularity
Edge Computing
Edge Computing brings computation and data storage closer to the devices where it’s being gathered, rather than relying on a central location that can be thousands of miles away. This is done so that data, especially real-time data, does not suffer latency issues that can affect an application’s performance. In addition, companies can save money by having the processing done locally, reducing the amount of data that needs to be processed in a centralized or cloud-based location.
Gartner defines edge computing as “a part of a distributed computing topology in which information processing is located close to the edge — where things and people produce or consume that information.”
Ubiquitous Computing
Ubiquitous computing is a concept in software engineering and computer science where computing is made to appear anytime and everywhere. In contrast to desktop computing, ubiquitous computing can occur using any device, in any location, and across any format.
And we are probably seeing this in our own everyday life. For example, at home, we might be using an Alexa device from Amazon or we might be using Google home. We might even have an intelligent fridge or a car we can talk to.
As companies increasingly leverage ubiquitous computing to support multiple types of applications and systems, a massive amount of data is generated for decision making. However, sending all the data to the cloud can result in latency. Edge computing can drive sub-second responses by moving both computing and data closer to the user. This will reduce latency, minimize data threats, and boost bandwidth. Here are some interesting use cases across industries:
Evolution of Computing
To understand Edge Computing, we need to travel back a few decades and see how Computing has evolved in the past 50 years. The below picture provides a quick recap of the evolution of Computing.

How Edge Computing works
Edge computing was developed due to the exponential growth of IoT devices, which connect to the internet for either receiving information from the cloud or delivering data back to the cloud. And many IoT devices generate enormous amounts of data during the course of their operations.

Think about devices that monitor manufacturing equipment on a factory floor or an internet-connected video camera that sends live footage from a remote office. While a single device producing data can transmit it across a network quite easily, problems arise when the number of devices transmitting data at the same time grows. Instead of one video camera transmits live footage, multiply that by hundreds or thousands of devices. Not only will quality suffer due to latency, but the costs in bandwidth can be tremendous.
Edge-computing hardware and services help solve this problem by being a local source of processing and storage for many of these systems. An edge gateway, for example, can process data from an edge device and then send only the relevant data back through the cloud, reducing bandwidth needs. Or it can send data back to the edge device in the case of real-time application needs.
These edge devices can include many different things, such as an IoT sensor, an employee’s notebook computer, their latest smartphone, the security camera, or even the internet-connected microwave oven in the office break room. Edge gateways themselves are considered edge devices within an edge-computing infrastructure.
Why does Edge Computing matter
For many companies, the cost savings alone can be a driver towards deploying an edge-computing architecture. Companies that embraced the cloud for many of their applications may have discovered that the costs in bandwidth were higher than they expected.
Increasingly, though, the biggest benefit of edge computing is the ability to process and store data faster, enabling more efficient real-time applications that are critical to companies. Before edge computing, a smartphone scanning a person’s face for facial recognition would need to run the facial recognition algorithm through a cloud-based service, which would take a lot of time to process. With an edge computing model, the algorithm could run locally on an edge server or gateway, or even on the smartphone itself, given the increasing power of smartphones. Applications such as virtual and augmented reality, self-driving cars, smart cities, even building-automation systems require fast processing and response.
Computing as close as possible to the point of use has always been important for applications requiring low-latency data transmission, very high bandwidth, or powerful local processing capabilities — particularly for machine learning (ML) and other analytics.
Here are some interesting use cases across industries:
Use Case (a) Autonomous vehicles
One of the leading current uses is for autonomous vehicles, which need data from the cloud. If access to the cloud is denied or slowed, they must continue to perform; there is no room for latency. The amount of data produced by all sensors on a vehicle is prodigious and must not only be processed locally, but anything sent up to the cloud must be compressed and transmitted on an as-needed basis to avoid overwhelming available bandwidth and taking precious time. IoT applications in general are important drivers of edge computing because they share a similar profile.
Use Case (b) In-hospital patient monitoring
Healthcare contains several edge opportunities. Currently, monitoring devices (e.g. glucose monitors, health tools, and other sensors) are either not connected, or where they are, large amounts of unprocessed data from devices would need to be stored on a 3rd party cloud. This presents security concerns for healthcare providers.
An edge on the hospital site could process data locally to maintain data privacy. Edge also enables right-time notifications to practitioners of unusual patient trends or behaviours (through analytics/AI), and the creation of 360-degree view patient dashboards for full visibility.
Use Case © Remote monitoring of assets in the oil and gas industry
Oil and gas failures can be disastrous. Their assets, therefore need to be carefully monitored.
However, oil and gas plants are often in remote locations. Edge computing enables real-time analytics with processing much closer to the asset, meaning there is less reliance on good quality connectivity to a centralized cloud.

Privacy and Security
However, as is the case with many new technologies, solving one problem can create others. From a security standpoint, data at the edge can be troublesome, especially when it’s being handled by different devices that might not be as secure as a centralized or cloud-based system. As the number of IoT devices grows, it’s imperative that IT understand the potential security issues around these devices, and make sure those systems can be secured. This includes making sure that data is encrypted, and that the correct access-control methods are implemented.
What about 5G
Around the world, carriers are deploying 5G wireless technologies, which promise the benefits of high bandwidth and low latency for applications, enabling companies to go from a garden hose to a firehose with their data bandwidth. Instead of just offering faster speeds and telling companies to continue processing data in the cloud, many carriers are working edge-computing strategies into their 5G deployments to offer faster real-time processing, especially for mobile devices, connected cars, and self-driving cars.

The Future of Edge Computing
Shifting data processing to the edge of the network can help companies take advantage of the growing number of IoT edge devices, improve network speeds, and enhance customer experiences. The scalable nature of edge computing also makes it an ideal solution for fast-growing, agile companies, especially if they are already making use of colocation data centers and cloud infrastructure.
By harnessing the power of edge computing, companies can optimize their networks to provide flexible and reliable service that bolsters their brand and keeps customers happy.
Edge computing offers several advantages over traditional forms of network architecture and will surely continue to play an important role for companies going forward. With more and more internet-connected devices hitting the market, innovative organizations have likely only scratched the surface of what’s possible with edge computing.
1 note
·
View note
Text
Smart Hotel - Is It Worth Investing In?

In the last several years, smart home technology has completely altered the way we live at home. Internet-connected equipment has made it possible to control our home's lights, heating, entertainment system, and even security system from our smartphones. Smart advancements like these have now entered the hospitality business, so it's no surprise.
Most businesses strive to provide the same level of ease and comfort that their customers enjoy at home, and hotels are no exception. To learn more about the impact of smart technology on hospitality software solutions, check out our most recent blog post.
Smart Guest Experiences
As a result, hoteliers should expect to witness a growing influence of hospitality software development on guests' expectations and experiences. With occupancy sensors, guest data may be used to automate guest interactions, lowering both friction points and labour expenses, while also enhancing the guest experience. As a result of advances in smart technology, hotels will be able to anticipate and tailor a variety of visitor services based on previous visits and an assortment of guest data.
Smart Reserved Parking
Nowadays, hotels can employ smart sensors to let guests request parking spots ahead of time and have their space allotted upon arrival. This will save hotels time and money by eliminating the need to manually manage parking spaces, and it will improve the guest experience from the moment they pull in.
Big Data Protection
There are many advantages to smart technology in travel software solutions, but one of the most important is the way it aggregates and makes usable data. Big data comes with a lot of responsibility, however.
The best use of big data is when you can utilise it to take action if that's entering a new market segment or altering your rate plans to compete with your rivals.
Predictive Maintenance
Like smart EMSs, predictive maintenance lets hotels use sensor data to discover inefficient or hazardous trends and to inform maintenance employees before a given issue evolves into a far more costly one. Instead of waiting for a component to fail, IoT technologies in hospitality software solutions are allowing engineers to predict maintenance requirements based on system usage, preempting system breakdowns and lowering the costs of operating a malfunctioning system.
Smart Room Keys
More hotels are now allowing visitors to enter their rooms via their mobile apps. Plastic keycards are environmentally hazardous, and managing a keycard inventory that is susceptible to loss and demagnetization is a time-consuming and labour-intensive task.
Smart Room Service
Additionally, sophisticated occupancy sensors will allow hotels to send out menu notifications to customers' smartphones when they are most likely to be in their rooms. Personalized suggestions based on previous orders can be included in these alerts. As a matter of fact, several meal delivery apps provide push notifications to loyal customers at their chosen ordering times and on their favoured days.
Smart Energy Management
Occupancy sensors and smart thermostats have the capability of responding to changes in occupancy. As an example, smart energy management systems use advanced machine learning algorithms to continuously monitor previous thermodynamics, local weather patterns, and peak demand loads to optimise energy use in real-time, all year long. Efficiencies in reducing energy consumption aren't the only theories. Hotels can save up to 20% on their energy bills by implementing smart energy management systems into travel software development.
Online Reputation Management
It is possible to estimate future bookings based on a hotel's web evaluations, but they can also provide useful information about how well a resort met visitor expectations. Because of this, hotels and other lodging establishments will continue to invest in technologies that enable them to monitor online evaluations, manage their online reputation, and utilise that feedback to enhance both their operational and guest service standards. In fact, online reviews affect a property's bottom line as well as serve as a source of direct input from guests.
Are you ready for the smart hotel business?
#hospitality software solutions#hospitality software development#travel software solutions#travel software development
0 notes
Text
Video Analytics: What Does it Mean and How Does it Actually Work?
Over the past few years, video analytics has gained interest from various industries and businesses worldwide. Video analytics, also known as video content analytics, helps automate tasks that were previously entirely dependent on humans. As a result, it leaves a lot of room for businesses to employ their workforce in other crucial jobs, which helps improve productivity and the overall operations of a business. Along with this, video analytics can also support organizations in keeping track of their hygiene, safety, and security.
We now understand what video analytics can do, but how does it actually work and benefit your businesses?
In this blog, you will discover the basic concepts of video analytics, how it works, and how it is used in the real world.
What is video analytics?
Video analytics refers to using Artificial Intelligence to analyze real-time videos to detect anomalies according to pre-fed data. This technology detects and tracks objects, activities, and people and helps in improving day-to-day operations. In addition, it analyses historical and real-time footage to learn from mistakes and applies it to develop solutions and make essential decisions beyond human capabilities.
How does video analytics work?
You might have got an idea of what video analytics means. But how does it work and produce desired results?
1. Feeding the system
There is a saying, “You are what you consume.” It’s perfectly accurate in the case of AI. The quality of the decision made by Artificial Intelligence is as good as the data it is fed. No matter how advanced the model is, the decision would be substandard if its data is not good. So, feeding the system with the right and extensive historical data will help the AI be in its prime while making important decisions. It is necessary to provide a considerable amount of real-time images, videos and recorded footage to the video analytics software to accurately analyze a video and come up with a decision.
Relevant data comes mainly from CCTV cameras. First, there must have a clear view of the entire territory from different angles. This step enables the software to capture the same visual event from a different perspective so the analysis could be accurate. Gathering more data is good if the system can process it efficiently.
2. Cloud Computing vs. Edge Computing
In a world where data is precious than oil, a large volume of data is captured every passing second. Hence, it needs to be processed for its analysis to happen. There are two modern technologies for this process:
o Cloud Computing
Cloud computing is the availability of computer system resources remotely and on-demand without direct active management by a user. As the name suggests, enormous amounts of data are stored in servers, in a cloud or virtual space, instead of hard disks or proprietary local disks. This data can be accessed remotely from anywhere in the world through the internet. Furthermore, once you connect to the web, you can access large amounts of data without being present nearby the database. This lets you access your required data on demand from the comfort of your home.
Cloud computing technology aims to make users capable of using cloud storage without deep knowledge about them. It aims at cost-cutting and lets users focus on core business instead of hindrance by IT drudgery. It mainly works on virtualization technology, separating a computing device into different virtual devices to efficiently manage and perform complex tasks. Virtualization enables the users to speed up their IT operations efficiently and at a low cost.
o Edge Computing It’s a paradigm involving a distributed network of computers whose components are located on different computer networks which operate on the same communication protocols by passing messages to one another. It brings data storage and computation closer to the work area to improve response time, latency, and bandwidth. Its main applications lie in “instant data” or real-time data processing where all work is outside the cloud.
Edge computing aims to move computation to the edge of networks, far from data centers, utilizing smart objects and network gateways to provide better services and perform tasks efficiently on behalf of the cloud. By moving computation to the edge, it’s easier to dispense content caching, persistent data storage, and better IoT management, which results in better transfer rates and response times.
Video analytics software can either run on cloud servers known as central processing or implanted in cameras themselves, called edge processing. While both processes are good, a cloud solution is preferable for processing real-time camera feeds and complex analytic functionalities for non-critical tasks. In addition, in cloud-based video analytics, there is less upfront investment on hardware, is easy to deploy, and has zero infrastructure cost.
Furthermore, using cloud technology, we can now configure the software to send only actionable data to the servers to reduce network traffic and more storage requirements.
3. Defining scenarios and training models
Once your physical architecture is set up, we must define the relevant scenarios we want our software to focus on and then train our models to detect and track target events. Let’s take an example of a manufacturing company and how the hardhat, which is commonly used on the site, is recognized with the help of video intelligence.
o Image Classification
In image classification, the technology identifies what are easily recognizable images or objects using unique colors, pattern, and format. In our example, hardhat can be easily recognized while monitoring operations. This process is known as image classification in layman’s terms.
o Localization
Now let’s take an example of hardhat placing along with the safety jacket of the same color. Now there are multiple objects and the technology could find challenges to identify it. That’s where localization comes to rescue. It trains the camera to differentiate between multiple objects and provides correct results.
o Object Detection
However, to attempt localization there needs to be some training involved. That’s where object detection is helpful. It trains the algorithm in a way that it can differentiate between multiple objects and helps us give the right results by identifying key differentiators.
We also need to train our models from scratch, which requires a tremendous amount of effort. But we have some resources available which make this a less tedious task. For example, image datasets such as ImageNet or Microsoft Common Objects in Context (COCO) play a crucial role while training new models. Recently, open-source projects are being published which deal with building a custom video analysis system.
4. Human Review
Finally, a human is needed to review all the alerts sent by the video analytics software and act upon them. With the help of such advanced systems, operators can now detect main events which may be overlooked or would take several hours to see manually.
Conclusion
Many sectors like manufacturing, retail, food services, hospitality, drive-thrus, and QSRs can benefit from this technology. Let us learn how.
1. QSRs and Drive-thrus: Drive-thrus can use video analytics to count vehicles, study the wait-time of the vehicles, and also for automatic number plate recognition (ANPR) based on customer identification.
2. Hospitality: As guest experience is the driving force behind the hospitality industry, video analytics can help assure guests have the best experience by ensuring concierge availability, clean surroundings, and secure premises.
3. Food Services: Restaurants can benefit significantly from AI-powered video analytics by automating the monitoring of various hygiene, cleanliness, and safety practices such as PPE usage, mopping, handwashing, and many more.
4. Retail: Video analytics can help retailers understand the traffic areas in their store, manage queue length and footfall.
5. Manufacturing: From use cases ranging from accident safety to safety gear to assembly line productivity, manufacturers can use intelligent video analytics to improve workplace safety and productivity.
With intelligent video analytics, we can perform tasks more effectively and less tediously, which is also less expensive. Organizations can leverage it to automate tedious and monotonous processes, gain valuable insights and make better business decisions.
About wobot.ai
Wobot.ai is a Video Analytics platform equipped with 100+ AI-powered checklists. These checklists span across industries such as QSRs, Drive-thrus, Cloud Kitchens, Restaurants, Hotels, Retail, and Manufacturing. In addition, the platform is compatible with all types of CCTV cameras and supports quick viewing, multi-device access, and robust remote assistance. With Wobot.ai, businesses can gain continuous feedback on processes, focus on areas of improvement, and highlight role models within organizations.
To use Wobot’s Video Analytics for your business, visit
https://app.wobot.ai/signup
.
0 notes
Text
Should you be worried about your passwords getting hacked?

Most IT security specialists define passwords as "the keys to our Digital Home": that's a pretty good metaphore, especially considering that our "digital home" is getting bigger as the time passes (and the technology advances). In the latest few decades we learned how to protect our precious devices (computers and, most recently, mobile devices) to prevent unauthorized access to them and their data... But, with the advent of the Internet and Internet of Things, the house became an infinite amount of different rooms: from online banking to food delivery services, from cloud-based repositories to remotely accessible Virtual Private Networks, we were literaly stormed by those "keys". At the same time, since technology runs faster than our ability to assimilate it, most internet users - as well as business companies - still use passwords in a totally insecure way today: to continue with our initial metaphore, nobody would leave the key on the door, or feel comfortable using the same key to open multiple doors, or use a weak lock & key combination, right? However, when using passwords, most of us often do just that. In the initial part of this post we'll try to summarize the most common mistakes that people do in choosing a password; then we'll briefly review the most common ways used by hackers to stole passwords; last but not least, we'll share some suggestions and best practices to secure our passwords and improve our account's security.
Common Password Mistakes
The typical password mistakes can be split into three main categories: choosing a weak password, using the same password among different web sites, and insecurely storing passwords. In the following sections we'll deal with each one of them. Choosing a weak Password A weak password, as the name implies, is a password too easy to guess or to discover using automated hacking techniques (brute-force, rainbow tables, and so on). Those who thinks that this is issue is a thing of the past because nowadays the majority of IT users have been educated enough to avoid choosing trivial passwords should check the SplashData's Most Used (and Worst) Password of 2017 infographics, which could easily change their mind. Here a list of the top 10: - 123456 (proudly keeping the first place since 2013) - password - 12345678 - qwerty - 12345 - 123456789 - letmein - 1234567 - football - iloveyou Luckily enough, such situation has been mitigated by enforcing a password security policy that is already adopted by most websites - and that is mandatory for all online services that deal with money or personal data, at least in most countries. Such policies not only require a minimum length and the presence of different character types (uppercase and lowercase letters, numbers, special characters) to make them harder to guess, but also force the users to periodically change them (often every 90 or 180 days). However, choosing a weak password is still critical for those devices where such policies are not enforced yet - such as most IoT devices. Using the same Password In addition to using passwords objectively too weak, users (and company officers) often also make the mistake of using the same password for different web sites or services. The so-called "password reuse" is probably the most serious mistake we can make nowadays: if a hacker manages to hack into a website's servers (this is happened for Yahoo, LinkedIn, Sony, and countless "minor" websites) and steal the users passwords, it will definitely try to use those retrieved passwords to gain access to other services. The only thing we can do to stop such common hacking practice is to ensure that each and every account that we have has its own password. A great example of such bad practice was given during the LinkedIn data breach (2012), through which Mark Zuckerberg's LinkedIn, Twitter and Pinterest accounts were all hacked because he used the same password for all of them. Such verification process can be automated using dedicated tools, such as Shard - a open-source command line tool that was developed to allow users to test whether a password they use for a site is used to access some of the more popular services, including Facebook. LinkedIn, Reddit, Twitter or Instagram. Insecurely storing Passwords The need to use strong passwords and a different password for each website or service inevitably brings another big requirement: the need to have a "secure" mechanism for storing these passwords, since human memory won't definitely be able to keep up. And this is where the most serious security problems often occur, not only for home users yet also for most companies. Who among us has never seen those dreadful MS Excel files (or text files!) containing a huge list of passwords? And the worst thing is that those unsecure repositories are often shared among different users (family members, co-workers, and so on), meaning that they aren't protected even with the basic user authentication mechanism provided by the OS.
How passwords are hacked
The techniques used by hackers for discovering our passwords are more than one, sometimes really trivial: as we can easily see by looking at the list below, most of them leverage or exploit the bad practices that we've talked about early on. - Social Engineering: e.g. Phishing, Password Sniffing. In practice, it is we who allow ourselves to be deceived by social engineering techniques and give passwords to those who ask for them through for example messages, emails, fake sites that disguise a well-known site. - Guessing passwords: Using personal information such as name, date of birth or pet names. When this happens, sometimes the "hacker" happens to be kind of close to the "victim": a friend, neighbor, co-worker or someone that knows enough info to perform such guesses. However, thanks to the modern approach to social networks, everyone might easily know a lot of stuff about anyone else. - Brute Force Attack: Automatically testing a large number of passwords until the right one is found. There are special programs to do this (a widely used one, John the Ripper, is open source, meaning that anyone can use it). Brute-force attacks are quite expensive to pull off, which requires time and computing power, but can easily achieve the result if the password is weak enough. - Intercepting a password, for example while it is being transmitted over a network. The bad habit of communicating passwords via email is frequent: there are even sites that, as soon as we register, send us a polite welcome message containing username and password displayed "in clear". Too bad that email is not a safe tool. - Shoulder surfing: a social engineering variant. It basically means "observing someone from behind" (i.e. "shoulder") while typing the password. - Using a KeyLogger. Keyloggers are malware programs that record everything typed on the keyboard, then transmit this data to the hacker who installed the keylogger. There are also hardware-based keyloggers that require direct access to the victim's computer. - Passwords stored in an insecure way, like handwritten on a piece of paper, or saved on a word file (see above). - By compromising a database containing a large number of user passwords, then using this information to attack other systems where users have reused the same passwords ("credential stuffing"). How to secure our Password Securing our passwords in order to avoid most - if not all - of the hacking attemps listed above is not impossible and is a goal that can be achieved by anyone. In a nushell, all we need to do is to apply two best practices: - Write strong and unique Password - Securely store your Passwords Both of them are equally important and must be followed for each and every password, without exceptions. How to write a strong Password A strong password is characterized by the following elements: length and character types used. - Regarding the length, it is strongly recommended to use at least 12 characters. - As for the character types, just let the math guide you: we have 10 numeric types (0-9), 52 letter types (26 lowercase + 26 uppercase), and more or less 33 special character types easy to type because they're directly accessible from a typical keyboard (such as #, &, %, ?, ^, and so on). To summarize all that, in total we have 95 character types available: with that in mind, we can say that a good password should have at least one character coming from each one of these types, because by increasing the types of characters, the number of possible combinations grows exponentially, thus making harder (and time-consuming) to "brute-force" the resulting password. How to store your Passwords As we aready said early on, using a different password for each website or service means that we can't rely to our memory to remember them all: at the same time, using insecure data stores such as MS Excel files or text files is definitely not an option. The best way to tackle (and fix) this problem is to use a Password Manager tool: a dedicated software that acts as a vault where you can securely store all your passwords, as well as your usernames and/or credential info, with the big advantage of having them in a single place. This basically means that you'll only need to remember the password required to access it, which is often very strong and can be further protected by other authentication factors (fingerprint, SMS, OTP, mobile tokens, and so on). The most advanced Password Managers also provide a good level of integration with the Operating System and browsers, meaning that they can even “automatically” (yet securely) fill in your credentials whenever you log in to a site (or an app) using your desktop or mobile device. IMPORTANT: Password Manager apps shouldn't be confused in any way with the "password storage" features offered by most modern browsers, such as Google Chrome, Mozilla Firefox, and MS Edge, that prompts you to store your credentials and fill out the forms for you, unless they are part of a bigger product that grants the fundamental features that a good Password Manager needs to have: centralized and distribuited repository, access from multiple devices, data encryption of the whole vault, 2-factor authentication support, and so on.
Conclusion
That's it, at least for now: we hope that this post will help most users and companies to increase their online security by securely choosing and storing their password. Read the full article
1 note
·
View note
Text
Teknomaks’a bir global lider daha: Teltonika Networks
Technews blogta yeni bir yazı var: https://www.technews.com.tr/genel/roportaj/teknomaksa-bir-global-lider-daha-teltonika-networks.html
Teknomaks’a bir global lider daha: Teltonika Networks
Geçtiğimiz ay Endüstriyel Hücresel IoT Yönlendirici ve Ağ Geçidi ürün gamı ile dünyanın önde gelen ilk 5 üreticisinden biri olan Litvanya merkezli Teltonika Networks ile Teknomaks, Yetkili Distribütörlük anlaşması imzaladı. Biz de kendilerini daha yakından tanımak için hem Teltonika Networks’u, hem de Türkiye’de pazarı hakkında görüşlerini sorduk.
Can you talk about Teltonika? Teltonika’dan biraz bahseder misiniz?
Teltonika Networks is a rapidly growing technology company, manufacturing professional network connectivity equipment for international markets. Through long-term experience and research and development of industrial network devices for IoT and M2M communication, we have developed a wide portfolio of products for the most complex areas of Industry 4.0, Smart City, and Green Energy. Teltonika Networks controls every stage of the product development cycle, which enables us to respond quickly and flexibly to market needs and changes while ensuring reliability, security, and ease of use. As a part of Teltonika IoT Group, all our products are manufactured and assembled in a modern factory in Lithuania which allows us to ensure highest quality standards.
Teltonika Networks, uluslararası pazarlar için profesyonel ağ bağlantı ekipmanları üreten, hızla büyüyen bir teknoloji şirketidir. IoT ve M2M iletişimi için endüstriyel ağ cihazlarının uzun vadeli deneyimi ve araştırma-geliştirmesiyle, Endüstri 4.0, Akıllı Şehir ve Yeşil Enerji’nin en karmaşık alanları için geniş bir ürün portföyü geliştirdik. Teltonika Networks, ürün geliştirme döngüsünün her aşamasını kontrol eder, bu da güvenilirlik, güvenlik ve kullanım kolaylığı sağlarken pazar ihtiyaçlarına ve değişikliklerine hızlı ve esnek bir şekilde yanıt vermemizi sağlar. Teltonika IoT Group’un bir parçası olarak tüm ürünlerimiz, en yüksek kalite standartlarını sağlamamıza olanak tanıyan Litvanya’daki modern yapıdaki fabrikamızda üretilmekte ve monte edilmektedir.
Which criterias are you taking into account when designing your products? Ürünlerinizi tasarlarken hangi kriterleri dikkate alıyorsunuz?
The most important source of inspiration when we design our products is our partner feedback. We aim, to be close to our partners with numerous and often local sales teams able to give more attention to each and single project. As a result, we are able to not only fulfil a demand and advise on business and technical details, but to also understand the solution our clients are working on and the real-life problem they are trying to solve. We must emphasize that this close connection is essential to have an efficient feedback loop that influences our RnD decisions greatly. Our partners dictate, what product they need to grow their business and attract more opportunities. We reinforce these demands with our own research and look for the most valuable set of product design parameters to achieve a popular product, which in turn helps us to offer it at a disruptive price point without sacrificing quality.
Ürünlerimizi tasarlarken en önemli ilham kaynağı iş ortağımızın geri bildirimidir. Her bir projeye çok daha fazla ilgi gösterebilen çok sayıda ve genellikle yerel çalışan satış ortaklarımıza yakın olmayı hedefliyoruz. Sonuç olarak, sadece iş ve teknik detaylarla ilgili bir talebi ve tavsiyeyi yerine getirmekle kalmıyor, aynı zamanda müşterilerimizin üzerinde çalıştığı çözümü ve çözmeye çalıştıkları gerçek hayattaki sorunu da anlıyoruz. Bu yakın bağlantının, Ar-Ge kararlarımızı büyük ölçüde etkileyen verimli bir geri bildirim döngüsüne sahip olmak için gerekli olduğunu vurgulamalıyız. İşlerini büyütmek ve daha fazla fırsat çekmek için hangi ürüne ihtiyaç duyduklarını ortaklarımız belirler. Bu talepleri kendi araştırmalarımızla pekiştiriyoruz ve popüler bir ürün elde etmek için en değerli ürün tasarım parametreleri setini arıyoruz ve bu da kaliteden ödün vermeden onu vurucu bir fiyat noktasında sunmamıza yardımcı oluyor.
How do you foresee the future to be shaped? And what is your plan to answer the needs in the future? Geleceğin nasıl şekilleneceğini öngörüyorsunuz? Ve gelecekte ihtiyaçlara cevap vermek için planınız nedir?
Year by year, connected IoT solutions are getting more and more attention and demand all over the world. At the same time, we see that different markets are in very different development stages, which dictates what connectivity hardware they demand. We ship our devices to more than 140 countries all over the world and we can strongly say that there is no single recipe for success. However, few components are present everywhere: value – determined by the functionality, reliability and equipment cost and finding the right tool for each task. Naturally, 5G is already changing the landscape of connectivity and challenging conventional wired connectivity methods, however emerging LPWAN connectivity options like NB-IoT and LTE Cat-M1 are also finding their place under the sun. In short – we are going to even more diversify our portfolio adapting to different specifics of each market which is both challenging and rewarding. However, we must remember, that with these connectivity methods, 4G LTE isn’t going anywhere, a lot of projects do not require extremely power efficient devices or speeds/latency associated with 5G. Therefore, 4G LTE is here to stay and be the backbone of the majority of connected IoT solutions.
Her geçen yıl, bağlantılı IoT çözümleri tüm dünyada giderek daha fazla ilgi ve talep görüyor. Aynı zamanda, farklı pazarların, talep ettikleri bağlantı donanımını belirleyen çok farklı gelişme aşamalarında olduğunu görüyoruz. Cihazlarımızı tüm dünyada 140’tan fazla ülkeye gönderiyoruz ve başarının tek bir tarifi olmadığını kuvvetle söyleyebiliriz. Bununla birlikte, her yerde birkaç bileşen bulunur: değer – işlevsellik, güvenilirlik ve ekipman maliyeti ile belirlenir ve her görev için doğru aletin bulunması. Doğal olarak, 5G zaten bağlantı ortamını değiştiriyor ve geleneksel kablolu bağlantı yöntemlerine meydan okuyor, ancak NB-IoT ve LTE Cat-M1 gibi yeni ortaya çıkan LPWAN bağlantı seçenekleri de güneşin altında yerlerini buluyor. Kısacası – hem zorlu hem de ödüllendirici olan her pazarın farklı özelliklerine uyum sağlayarak portföyümüzü daha da çeşitlendireceğiz. Ancak, bu bağlantı yöntemleriyle 4G LTE’nin hiçbir yere kaybolmadığını, birçok projenin son derece düşük güçte çalışan cihazları veya 5G deki yüksek hızıve çok düşük gecikme süresini gerektirmediğini unutmamalıyız. Bu nedenle 4G LTE, IoT çözümlerinin çoğunluğunda belkemiği olarak kalmak durumunda.
What direction is your research and development activities moving on? Araştırma ve geliştirme çalışmalarınız hangi yönde ilerliyor?
This year, we have introduced our new Ethernet & Wireless product division, with a goal to address the growing demand in industrial networking space that does not require cellular connectivity component. We are strongly committed to move towards this space and apply the same value-based mentality to capture the market. However, we will not sacrifice our cellular product division development, as we are constantly growing our RnD team to keep innovating our current portfolio, create new products and discover new technologies that can be applied. One thing to note, all our RnD decisions are based on our product philosophy which is to offer devices that are secure, reliable and easy to use.
Bu yıl, hücresel bağlantı bileşeni gerektirmeyen endüstriyel ağ alanında artan talebi karşılamak amacıyla yeni Ethernet ve Kablosuz ürün grubumuzu tanıttık. Bu alana doğru ilerlemeye ve pazarı ele geçirmek için aynı değere dayalı zihniyeti uygulamaya son derece kararlıyız. Ancak, mevcut portföyümüzü yenilemeye devam etmek, yeni ürünler yaratmak ve uygulanabilecek yeni teknolojileri keşfetmek için Ar-Ge ekibimizi sürekli olarak büyüttüğümüz için hücresel ürün bölümü geliştirmemizden ödün vermeyeceğiz. Unutulmaması gereken bir nokta, tüm Ar-Ge kararlarımız güvenli, güvenilir ve kullanımı kolay cihazlar sunmak olan ürün felsefemize dayanmaktadır.
What is your marketplace worldwide? Dünya çapında pazar yeriniz nedir?
We have a truly global footprint, as mentioned we are currently shipping devices to more than 140 countries worldwide. Regardless of our strong footprint in Europe, close to our origin, we have sales, support and logistics offices in 19 countries to fulfil our commitment to be close to our partners. Global ambition has as much challenges as it offers opportunities. We must constantly work to certify our products in different markets, to offer different price level and specification devices, to develop our Remote Management System that can solve problems specific to each region.
Gerçekten küresel bir ayak izimiz var, belirtildiği gibi şu anda dünya çapında 140’tan fazla ülkeye cihaz gönderiyoruz. Avrupa’daki güçlü ayak izimiz ne olursa olsun, menşemize yakın, ortaklarımıza yakın olma taahhüdümüzü yerine getirmek için 19 ülkede satış, destek ve lojistik ofislerimiz var. Küresel hırs fırsatlar sunduğu kadar zorluklara da sahiptir. Ürünlerimizi farklı pazarlarda sertifikalandırmak, farklı fiyat ve özellikte cihazlar sunmak, her bölgeye özgü sorunları çözebilen Uzaktan Yönetim Sistemimizi geliştirmek için sürekli çalışmalıyız.
What is your coverage in Turkey? Türkiye’deki kapsama alanınız nedir?
One of our key elements in creating strong and reliable partnerships is to be closer to our partners, our customers. Therefore, we already invested and we are providing technical support locally. At Teltonika Networks we see a huge potential in Turkey IoT business and that a partnership with Teknomaks will show to the market why our devices and IoT platform is very popular Globally. Turkish people are very innovative and we see big potential for our networking devices in different type of projects: smart city, energy sector, industry and automation, retails and transportation.
Güçlü ve güvenilir ortaklıklar oluşturmanın kilit unsurlarından biri de iş ortaklarımıza ve müşterilerimize daha yakın olmaktır. Zaten bu sebeple yatırım yaptık ve yerel Teknik Destek sağlıyoruz. Teltonika Networks için Türkiye IoT işinde büyük bir potansiyel görüyoruz ve Teknomaks ile ortaklığımızın pazara, cihazlarımızın ve IoT platformumuzun neden küresel olarak popular olduğunu göstereceğini görüyoruz. Türk halkı çok yenilikçi. Bu sebeple akıllı şehir, enerji sektörü, sanayi ve otomasyon, perakende ve ulaşım gibi farklı türdeki projelerde ağ cihazlarımız için büyük bir potansiyel görüyoruz.
What make you different from others? Sizi diğerlerinden farklı kılan nedir?
To use a famous slogan – we think differently, we take our original ideas, we apply our courage and effort and we measure how successful it is. Most importantly we do not fear change or ambitious goals – we embrace them and we are happy that this recipe so far is showing results that we can be proud of!
Ünlü bir slogan kullanmak için – farklı düşünüyoruz, orijinal fikirlerimizi alıyoruz, cesaretimizi ve çabamızı uyguluyoruz ve ne kadar başarılı olduğunu ölçüyoruz. En önemlisi, değişimden veya iddialı hedeflerden korkmuyoruz – onları benimsiyoruz ve bu tarifin şu ana kadar gurur duyabileceğimiz sonuçlar vermesi bizi mutlu ediyor!
Teltonika ürünleri ve ağ bağlantıları ekipmanları hakkında daha fazla bilgi almak için şimdi Teknomaks‘ı ziyaret edin!
0 notes
Text
Internet of Things Market is Expanding Significantly with Growing Adoption of Smart US$ 1.88 trillion by 2022
Mar 05, 2021: Synopsis:
The global Internet of Things (IoT) Market scope was projected at US$ 605.69 billion in 2014. It is expected to reach US$ 1.88 trillion by 2022 with a CAGR of 15.2% during the completion of the prediction period. The idea of IoT has transformed the manner, organizations through business verticals. It assists organizations in growing working efficiency and enhancing business results.
The whole lot of business verticals are experiencing a vast alteration in a proposal to deliver reachable, excellent, and reasonable services to their clienteles. New-fangled uses, an outcome of innovative technology, are being developed to discourse altering necessities of the business. IoT, in grouping with big data and cloud computing, is making profitable openings for the organizations. The growing number of connected devices and the propagation of smartphones have funded considerably to the growth of IoT.
Download sample Copy of This Report at: https://www.millioninsights.com/industry-reports/internet-of-things-iot-market/request-sample
Manufacturing sector inherently concentrating to growing their efficiency of business procedure and the productivity by way of optimal use of source. One of the important issue motivating the manufacturing sector in the direction of IoT empowered placements is having standardized and reliable united vision of the data and procedures for smooth admittance for maximum of the shareholders. The vendors of Industrial IoT have been attaining control above numerous varied industrial procedures by way of incorporating cutting-edge IoT platforms and resolutions to systematize industrialized processes.
IoT technology has been empowering retailers all over the world, to link to both - people and businesses. This permits retailers to increase understandings regarding the performance of the product and discover new-fangled methods of client engagement.
Read Complete Report With TOC @ https://www.millioninsights.com/industry-reports/internet-of-things-iot-market
Classification:
The global Internet of Things market can be classified by Application Area, Platform, Service, Software Solution and Region. By Application Area, it can be classified as Smart mobility and transportation, Connected logistics, Smart energy and utilities, Smart retail, Smart manufacturing, Building and home automation, Banking and Financial Institutions (BFSI).By Platform, it can be classified as Network management, Device management, and Application management.
By Service, it can be classified as Managed service, Support and maintenance, Professional service, Consulting service, Deployment and integration. By Software Solution, it can be classified as Network bandwidth management, Data management, Real- time Streaming Analytics, Remote monitoring system, and Security solution.
Regional Lookout:
By Region the global Internet of Things (IoT) industry can be classified as North America, Europe, Asia Pacific, Latin America, and Middle East & Africa. North America griped the biggest share of market during the past year. The issues accountable for this development consist of technical progressions, speedy digitalization through business verticals, and growing acceptance of smart connected apparatuses that have additionally powered the development in this province. It has got enormous uses, everywhere in diverse businesses. For example, a storage and warehouse company, Lineage Logistics (U.S.A.) work together with Monnit Corporation for IoT empowered sensors. Monnit Corporation delivered Lineage Logistics vibration and temperature sensors.
Increasing demand for smart devices in the U.S.A and Canada pushes the market in North America. The province is expected to top the global market during the period of forecast. Large scale implementation of technologies for example Artificial Intelligence (AI) and Cloud computing in this area adds to the development of the IoT market.
A number of mergers & acquisitions (M&A) amongst foremost companies and IT companies in North America is additional reason motivating the market. On top of North America, additional provinces for example Europe and Asia Pacific are expected to develop substantially during the period of forecast.
Get in touch
At Million Insights, we work with the aim to reach the highest levels of customer satisfaction. Our representatives strive to understand diverse client requirements and cater to the same with the most innovative and functional solutions.
Contact Person:
Ryan Manuel
Research Support Specialist, USA
Email: [email protected]
Global Headquarters
Million Insights
Felton Office Plaza 6265 Highway 9 Felton, California 95018, United States
Phone: 1-408-610-2300
Email: [email protected]
Asia Pacific
Million Insights
Office No. 302, 3rd Floor, Manikchand Galleria, Model Colony, Shivaji Nagar, Pune, MH, 411016 India
Phone: 91-20-65300184
0 notes
Text
Angel
Strap in. This one’s gonna be a doozy. #7 - Also on AO3
It takes them another hour or so of envisioning their future before they reach the edge of the Aeroport, the final destination in their journey. After a quick inspection of the area, the pairs’ Ghosts suggest taking an entrance on the west side of the building in order to have the best chance of finding a ship or two. They find such an entrance in the form of a gaping hole in three stories of glass, and make their way inside.
It’s a minor maze initially, following signs through the old passenger area and towards the central hangar, but eventually they find their way. The walls begin to show signs of rot, and there’s a hard gunky buildup on the floor as they close in on their target.
Both Hunters suddenly get the feeling that this won’t be an easy “grab and go” mission. They pull down their masks, pull up their hoods, and ready their weapons.
“I have... a very bad feeling about this place.” Seraph comments as the weight of Darkness falls upon their shoulders. The pairs’ Ghosts light the way as they continue their trek into the old Aeroport, sticking closer than usual as a precaution.
Myss is looking down the scope of her scout, waiting to pop any head that enters her vision. While concentrating, she almost misses the guttural clicking sounds that begin to surround them, and the squishing noises their footsteps now make. She spots three glowing eyes ahead, pops a bullet into them without thinking, and hears screaming.
{[Hive!]} Casper and Lumo exclaim at the same time.
Seeing the large number of oncoming foes, Myss fires her Shadowshot at the horde’s feet, tethers them all, and makes easy targets of them. The two Hunters fight them - Thralls, they learn - rather well, the pair almost in sync as they threw blow after blow at them. There’s no time to revel in their abilities however, as they’re greeted by several larger Hive, and a floating one as they enter the next room.
The pair waste no time in attacking the larger Hive, but they don’t manage well. Trading blows just means they get hit twice as hard, and the brawl eventually leads to Seraph falling to a Knight’s blade.
[Guardian down!]
When her partner’s not back after a few seconds, Myss begins to panic, and dodges away from the Acolyte she was currently engaged with to assist her. After the dodge, she finds the Hive are all mildly confused for a moment, which gives her just enough time to revive Seraph, who thanks her before returning to combat. They fight for another several minutes, each falling two or three times, and each helps the other up every time.
“I don’t - I don’t know if we can do this, Seraph!” Myss shouts, dodging away from a Knight’s swing. “We should leave, and find another entrance.”
As soon as she suggests that, a toxic fog blocks their exit.
Seraph manages to knock down the last of the Knights on her side, and fires on the one Myss is left with. “We can do this.” She states confidently, standing firm beside her partner.
The floating Hive - the Wizard - releases a deafening screech, prompting another wave of Hive, as well as a floating ball in a conical cage - a Shrieker - that reminds Myss of what her Super looks like.
The pair exhales sternly in unison, doubts forming as they steel themselves for the next wave.
The pair die a few more times - revival always aided by the other - before Seraph decides that enough is enough and pops her Super, taking aim at the Wizard. She fires once, which its enough to break its shield, but misses the other two shots as it manages to move out of the way just in time.
“Dammit!” Seraph knows she won’t have another chance like this again. Myss used her own Super when they entered, and she probably doesn’t have it back yet. Every time they eliminate a wave, another comes rushing in, and they can’t avoid them for long enough to be able to focus on putting a dent in the Wizard. They’re out of options.
She can tell Lumo’s reaching his limit, which means Casper probably is too. They need to do something crazy, and Seraph has just the idea for that. She’s not sure if it’ll work, and there’s only one way to find out.
But there’s something she has to do first, just in case.
In the brief calm before the next wave, Seraph pulls Myss aside. She drapes her own cloak over her partner, rips their helmets off, and smiles at the other’s puzzled expression. Wasting no time, she pulls herself up to press her lips against the taller Hunter’s. Myss is shocked and confused, but melts into the kiss immediately.
And then it’s over.
“Get ready to run.” Seraph orders, putting their helmets back in place.
“What?!” Myss yells, grabbing onto the other’s shoulder. “No! I’m not leaving you!”
“You’re not. I’ll be right behind you.” Seraph assures Myss, wanting so desperately to believe that it will be true.
After a breath, Myss moves her hand from Seraph’s shoulder to the top of her head, bringing their helmet-clad heads together with a light thud.
“You better be.” She orders, then releases her partner.
Myss trusts Seraph with whatever crazy idea she has to get them out of this hell, believing that she’ll come out unscathed.
Seraph runs towards the center of the horde, and ultimately towards the Wizard. Myss hangs back by the door, but still fairly inside the room. She’s ready to run like hell once Seraph gets clear, but is also ready to help if she’s needed.
“Myss! Get out of here!” Seraph yells when she notices her partner lingering inside the room. “I’ll hold them off!” She gets to the Wizard’s side and, just as she’s about to attack, Lumo’s pained shrieks ring out through the room, causing the two Guardians to freeze in panic.
{It-It’s got me! Seraph!} Lumo cries as he’s pulled from Seraph and towards the Wizard, the Light visibly draining from his optic. {Seraph! R-Run... Go! I can’t...}
“NO!” Seraph wails as her Ghost is sapped of his Light, catching his empty shell as it fell. “No! Lumo!” Tears stream down her face as she clutches his body to her chest.
Myss is frozen in place, and can feel that Casper is too, having never imagined they would see something so painful in their entire existence. She quickly realizes what this means for Seraph’s fate, and tears begin welling in her eyes. She has to save her partner from that Wizard before it kills her, so she begins running towards them.
“No!” Seraph points at Myss. Bright, pained orange eyes meet her own, melting with her tears. “Get to the City!” She orders, voice breaking. “Live!” The Wizard’s making hand motions again, similar to the ones it made when it took Lumo, and she knows this is the end for her. “I l-”
But those last words never get out, and are instead replaced with her screams as the Wizard performs its ritual.
Myss’ face drops in absolute horror and disbelief as she watches her partner transform - murdered - before her.
“Seraph...?” She quietly calls in desperation, her tears now flowing violently.
“Seraph!” She tries again, her eyes refusing to believe what they saw.
“Seraph, no...” She weeps, falling to her knees as a purple crystal takes her partner’s place, beginning to glow bright with her stolen Light.
“NO!”
The Hunter releases one last angry defiance before hopping up and firing her Shadowshot directly at the Wizard, who disintegrates into violent violet energy with a scream. The remaining ball tethers to the horde of Hive that surrounded its victim, trapping them all where they stood.
The Wizard’s death somehow destroyed the structural stability of the crystal, and Seraph’s stolen Light - Void Light - is exposed and tangible. Myss knows what she has to do.
Wasting no time, she rushes up to where her partner fell, grabs Lumo’s empty shell, tucks Seraph’s Light under her arm, and makes for the exit. Thankfully, the fog on the door has dissipated - likely also controlled by the Wizard - and she’s able to run out the way she came.
Like when she discovered her Super, Myss allows her instincts to guide her out of the Hive-infested Aeroport, as she’s currently incapable of coherent thought. She makes it out after a few minutes, not stopping until her legs give out.
Whether it's the sheer devastation, or the effort it took to summon that small amount of extra Light to call upon her Super, she collapses when she reaches the forest.
Myss never releases the ball of Light that once belonged to Seraph, keeping it tight against her chest. She lets her despair ring out through the forest, wailing in grief for several minutes, rocking back and forth as she holds on to the ball as if her life depended on it.
“S-S-Seraph...” Myss whispers with an extreme shake in her voice. “Y-you id-iot-t-t... W-we.. We we-r-re sup-p-p-osed to...” She can’t bring herself to finish the statement.
“Th-th-thank you-u-u.” She finally resorts to saying, pushing any regret to the back of her mind. Holding the ball against her chest burns, but she ignores it. “Thank you f-f-for s-saving m-m-me one-one last t-time.”
“I l-” She starts, though is unable to complete the heavy statement on the first try. “I lo- I-I l-l-love... l-love you t-t-too. S-so m-much. I-I’ll miss-s-s-s you-u-u.”
Myss knows it’s not the same, but - in lieu of more stuttered words - she places her lips on the ball of Seraph’s Light. It burns, but she welcomes it.
Over the next few moments, the Hunter can feel the size of the ball slowly shrinking, but it never feels like it’s gone. Seraph’s Light still feels the same, though the burning is increasing and concentrated over her chest, directly above where her jewel pendant rested on her breast.
“W-what’s hap-p-pening?” She asks her Ghost, who appears in front of her.
He has to shake off the shock in order to answer his Guardian. [I-I think...] Casper begins, chirping in disbelief. [I think you’re absorbing her Light, Myss - her Void Light.]
“What? H-how...? How is that... am I d-doing that?!” Myss asks as she watches the ball continually shrink.
[I’m not... not sure.] Casper begins a scan of his Guardian, floating a step backwards in confusion. [I... I feel more Light within you than usual, more than what I gave you.] He blinks, his back half spinning as he thought. [I think... The only thing I can think of is that Seraph’s Light must have known it was being held by you, and knew it was safe - that it’d be safe with you and your Light.]
Myss’ tears, though they never stopped, now flow with a new vigor. The Hunter is blinded by the ocean of grief that floods her eyes, but now it’s overwhelmingly mixed with joy, pride, euphoria, and love. Her arms wrap tightly around her torso as the last of Seraph’s light is merged with hers, and the ball disappears. The burn from the process remains in the now glowing crystal that rests on her breast, which she clutches in her hands.
“Thank you, Seraph.” Myss sniffles. “For staying with me.”
A moment passes in which the Hunter breathes deeply to centre herself, but instead she feels a new fire within her, one she hasn’t felt before. She gets to her feet and lifts her head, cocking it in a motion that beckons her Ghost to return to her backpack.
Casper doesn’t question his Guardian, knowing her nerves have steeled and that her mind is clear as they head back towards the Aeroport. She’s determined to succeed, and she will.
Myss returns to the dreaded room calmly and quietly, and is greeted with a chorus of screeches and wails. She can feel a smaller energy - a much hotter burn - form in her palm, and she pitches it towards the oncoming horde, which bursts into bright orange flames on contact.
She relishes in their pained screams and, a few moments later, the horde is dealt with. The Wizard fell at her hands earlier, which means now the Shrieker is the only obstacle she has between her and a ship.
Her Light is making her fingertips burn, and she smiles knowingly. Myss thrusts her arm to the sky, and a brilliant, familiar, flaming pistol forms in her hand.
Her first Golden Gun.
Without missing a beat, Myss aims all shots at the Shrieker’s cracked eye, and it disintegrates into millions of burning embers.
With all the Hive in the room cleared out, Myss can clearly see the entirety of it, and spots a couple ships in the very back of the room - behind where the Shrieker was floating.
They were so close.
Myss clutches her necklace, and approaches the ships.
[This one’s in the best shape.] Casper states of an angular ship after scanning the lot. [Let’s go home.]
The Hunter takes a moment to return to the empty husk that once held Seraph’s transformed frame, and brushes a hand gently along it. She removes her own gray cloak and places it on the shell, her vision going blurry. Myss allows the second wave of grief to take her, wrapping her arms around herself as her tears flow fresh.
Several minutes pass with the Hunter crying quietly next to her partner’s remains, which Casper lets Myss have. He wouldn’t say she’s earned it, but the pair deserved to have a proper goodbye.
The Hunter’s sobs soon morph into a broken, melodic tune, one that Casper was familiar with.
“You’d wink... You'd stare... You’d stop my heart cold. You’d make me feel young, and we’re only days old...” A sniffle, her voice turning thick. “There were so many things we planned to be... And all of you, was loved by me...”
If a Ghost could cry, Casper would. He could feel how heartbroken and devastated his Guardian was, and he wished there was a way he could cheer her up. He knew there wasn’t, at least not right now, but he would try his best with the memories he’d collected over the past few weeks.
But he’d try that another time. The Hunter appears to be calming down, and his highest priority now is getting her safely to the City.
Just by looking at her, by seeing the extra Light she now possessed, he knew Myss now had an angel to watch over her as long as she lived. Well, other than him, of course.
Myss stands a few seconds later, holding Seraph’s gifted cloak tightly, and turns towards her Ghost.
“Let’s go home.”
#destiny#destiny the game#destiny fic#destiny fanfiction#guardian oc#character death#[fic]#[meta]#[taleofmyss]
11 notes
·
View notes
Text
Internet of Things Market 2025 Report by Global Size, Key Companies, Trends, Growth and Regional Forecasts
Internet of Things Market scope was projected at US$ 605.69 billion in 2014. It is expected to reach US$ 1.88 trillion by 2022 with a CAGR of 15.2% during the completion of the prediction period. The idea of IoT has transformed the manner, organizations through business verticals. It assists organizations in growing working efficiency and enhancing business results.
Request a Sample PDF Copy of This Report @ https://www.millioninsights.com/industry-reports/internet-of-things-iot-market/request-sample
Market Synopsis of Internet of Things Market:
The whole lot of business verticals are experiencing a vast alteration in a proposal to deliver reachable, excellent, and reasonable services to their clienteles. New-fangled uses, an outcome of innovative technology, are being developed to discourse altering necessities of the business. IoT, in grouping with big data and cloud computing, is making profitable openings for the organizations. The growing number of connected devices and the propagation of smartphones have funded considerably to the growth of IoT.
Manufacturing sector inherently concentrating to growing their efficiency of business procedure and the productivity by way of optimal use of source. One of the important issue motivating the manufacturing sector in the direction of IoT empowered placements is having standardized and reliable united vision of the data and procedures for smooth admittance for maximum of the shareholders. The vendors of Industrial IoT have been attaining control above numerous varied industrial procedures by way of incorporating cutting-edge IoT platforms and resolutions to systematize industrialized processes.
IoT technology has been empowering retailers all over the world, to link to both - people and businesses. This permits retailers to increase understandings regarding the performance of the product and discover new-fangled methods of client engagement.
Classification:
The global Internet of Things market can be classified by Application Area, Platform, Service, Software Solution and Region. By Application Area, it can be classified as Smart mobility and transportation, Connected logistics, Smart energy and utilities, Smart retail, Smart manufacturing, Building and home automation, Banking and Financial Institutions (BFSI).By Platform, it can be classified as Network management, Device management, and Application management.
By Service, it can be classified as Managed service, Support and maintenance, Professional service, Consulting service, Deployment and integration. By Software Solution, it can be classified as Network bandwidth management, Data management, Real- time Streaming Analytics, Remote monitoring system, and Security solution.
View Full Table of Contents of This Report @ https://www.millioninsights.com/industry-reports/internet-of-things-iot-market
Table of Contents:-
Chapter 1 Methodology and Scope
Chapter 2 Executive Summary
Chapter 3 Internet of Things: Market Variables, Trends & Scope
Chapter 4 Internet of Things: Product Estimates & Trend Analysis
Chapter 5 Internet of Things: Application Estimates & Trend Analysis
Chapter 6 Internet of Things: End-use Estimates & Trend Analysis
Chapter 7 Internet of Things: Industrial End-use Estimates & Trend Analysis
Chapter 8 Internet of Things: Regional Estimates & Trend Analysis
Chapter 9 Competitive Landscape
Chapter 10 Internet of Things: Manufacturers Company Profiles
Get in touch
At Million Insights, we work with the aim to reach the highest levels of customer satisfaction. Our representatives strive to understand diverse client requirements and cater to the same with the most innovative and functional solutions.
0 notes
Text
Artificial Intelligence- When Intelligence, is not natural
Introduction In 1955 John McCarthy announced Artificial Intelligence for the first time. The term, ‘Artificial Intelligence’ is derived from two words, artificial- a thing which is not natural, and intelligence- a capacity to understand and collect information about events, a particular group, etc.
After combining these two words into a single frame, ‘Artificial Intelligence’ means a computer programming code in a machine like a computer exhibiting traits of human beings like learning, problem-solving, scanning, storing information like memory, thinking, etc. Just like mimicking someone, a system of Artificial Intelligence does the same as human beings perceive things by performing various tasks from their environment.
The system is very quick in recognizing the impulses, and with advanced deep learning, it processes the tasks using natural language processing (NLP) technology. Being a natural branch of artificial intelligence, NLP fulfills the gap of communication between a machine and a human being through many principles and disciplines like computer science, and computational linguistics. NLL helps the machine to understand the human language by turning into their language. The technology saves valuable time and energy by performing its operation in less time than expected.NLP assists artificial intelligence to do multiple tasks like reading a text, following the instructions given in the text, checking records simultaneously, etc. In short, artificial intelligence enables the machine to learn languages to perform tasks. Now,
Difference between Artificial Intelligence and Machine Learning Artificial Intelligence simulates and trains the machine to mimic human actions like speaking a particular dialect, recognizing colors, shapes, etc. whereas machine learning is a subset of artificial intelligence that are developed to interpret human actions. Machine learning searches for data and tries to reach to a conclusion just like us using certain algorithms. Like a car has a laser-like device on its top, giving signals for the in-between objects while parking in a parking area, and also informing about all the cars that are surrounding it. But both need large volumes of data, granular data, and extremely diversified data.
Current Scenarios In today’s world, since its inception, Artificial Intelligence has become an integral part of every person’s life due to this, our life has become very fast. AI has led to cut short time and multitasking at once. Artificial Intelligence repetitively learns and discovers through diversified data. Without human involvement, it clarifies high volume of data without fatigue and analyses deep data, hidden into deep layers of neural networks. It is capable of identifying and performing human tasks, deep neural networks achieve incredible accuracy by interacting with humans like a person who uses Google Search, Alexa, Siri, MacBook, Tablets etc.,
How does it work? Before learning the working structure of artificial intelligence, we need to research and have deep knowledge about its basic components. Here they are:
Machine Learning: The machine needs algorithms, statistics, the guidance of neural networks, operation research, and physics to analyze and perform any task.
Computer Vision: Being an integral part of artificial intelligence, computer vision is a technique that assists to identify, process, and interpret the visual data of an image like graphs, tables, pictures in a video, etc. It is done under the light of deep learning.
Natural Language Processing (NPL): NPL makes sure to interact with human language and speech. It connects machines to humans for interpreting, recognizing human contexts and producing responses. Example: It is applied to a Skype translator.
Cognitive Computing: The component cognitive computing improves the relationship between humans and computers by making inferences from the context i.e. simulating human processes with machines like speech and image reorganization.
A Neural Network: It is a type of machine learning that interconnects units (like neurons) with the human brain. Before analyzing the final data, it associates the units with previously undefined data. For example, out of 1,000 photos, to recognize the final photo of a cat.
Deep Learning: This is the most important element of artificial intelligence. For example, a voice assistant, Siri answers the ’What is my name?’ Deep Learning implies many layers of artificial neural networks determining a single result from many inputs.
Uses: Artificial intelligence has made our life error-free with superb advanced high-technology. From self-driving and parking vehicles, to digital assistance thanks to Artificial Intelligence in assisting our homes, offices, our objects like mobile phones, washing machines, etc. installing biometric machines in offices, has made it easy to track the attendance of employees. Google assistant, Siri, and Alexa to speech and face recognition have made our gadgets safe and secure. Even applications like Uber, RedBus, Ola use artificial intelligence that allows us to share route details along with the driver and cab information to our dear ones. Many high-profile industries demand Artificial Intelligence for security, risk recognition, legal assistance, etc. For example, such as health care industry need AI for X-rays and diagnosis treatment of patients. The retail sector uses AI in collecting and possessing multiple customer data online, and offline and also in online shopping and multiple payment options like COD, internet banking, debit, or credit cards. The manufacturing industry also needs AI to analyses IoT (Internet of Things), and for calculating demand and supply of the products in the market. The banking sector uses AI to identify any fraudulent activity, risk measurement, fast and smooth transactions, credit scoring, etc.
What are the future perspectives of Artificial Intelligence? The future of Artificial Intelligence will be vast and more extensive than the present time. From deep learning, the networking system to driverless cars, it will make the world a digital place. It is influencing everyone’s life making it very simple, optimized, and fulfilling the purpose of life and understanding the mechanics behind Artificial Intelligence. Hence, humans will successfully merge with it completely to do autonomous work.
School of Engineering & Technology Jain (Deemed-to-be- University) is a pioneering school of engineering that offers wide variety of new- age courses. The institute offers both B.Tech and M.Tech programs in Artificial Intelligence that opens a wide gateway for job opportunities for the students even at a global platform. The course gives hands on experience and make the students ready to face the industry demands, with advance knowledge of artificial intelligence.
0 notes
Link
Cybersecurity multinationals Fortinet, Trend Micro and McAfee Labs predict a rise in the use of machine learning and AI methods to create more effective attacks, including against cloud systems, as well as in business process compromise scams, denial of services and ransomware attacks. Threat actors will leverage machine learning and blockchain technologies to expand their evasion techniques, says Trend Micro research and development centre TrendLabs in its ‘Paradigm Shifts’ 2018 predictions report. Cyberattackers will use more machine learning to create attacks, experiment with combinations of machine learning and AI, and expand their efforts to discover and disrupt the machine learning models used by defenders, McAfee Labs predicts in its ‘Adversarial machine learning arms race revs up’ November 2017 report. “During the year, we expect researchers will show that an attack was driven by some form of machine learning. We already see black-box attacks that search for vulnerabili- ties and do not follow any previous model, making them difficult to detect.” For example, machine learning could help improve the effectiveness of social engineering and make phishing attacks more difficult to identify by harvesting and synthesising more data than a human can. It can also increase the effectiveness of using weak or stolen credentials on the growing number of connected devices and help attackers scan for vulnerabilities, which will boost the speed of attacks and shorten the time from discovery to exploitation.
SKILLS & RESOURCES
Skills and resources are the key elements in any cyberattacker’s arsenal. All attacks require a vulnerability in the network – whether in the form of technology or people, TrendLabs reports. Cyberattackers are expected to analyse machine learning models through a combination of probing from the outside to map the model, reading published research and public domain material and trying to exploit an insider. “The goal is evasion or poisoning. Once the attackers think they have a reasonable recreation of a model, they will work to get past it, or to damage the model so that either their malware gets through or nothing gets through and the model is worthless.” However, combined human-machine teams show great potential to swing the advantage back to the defenders, states McAfee Labs. Machine learning is already making significant contributions to security, helping to detect and correct vulnerabilities, identify suspicious behaviour and contain zero-day attacks. Human-machine teaming is becoming an essential part of cybersecurity, augmenting human judgment and decision- making with machine speed and pattern recognition. “Combining machine learning, AI and game theory to probe for vulnerabilities in our software and the systems is the next step beyond penetration testing and uses the capacity and unique insights of machines to seek bugs and other exploitable weaknesses.” Further, because adversaries will attack the models, defenders will respond with layers of models, each operating independently, at the end point such as in the cloud and in the data centre. Each model has access to different inputs and is trained on different data sets, providing overlapping protections, McAfee Labs adds. Machine learning, however, can only be as good and accurate as the context it gets from its sources. “We have found that certain ransomware use loaders that certain machine learning solutions are unable to detect because the malware is packaged not to look malicious. This is especially problematic for software that employs pre-execution machine learning, which analyses files without any execution or emulation,” according to the TrendLabs report. While machine learning helps improve protection, it should not take over security mechanisms and should be considered an additional security layer incorporated into an in-depth defence strategy. Local information technology security services firm Galix MD Simeon Tassev highlights that South African businesses must put in place tools such as AI and analytics to identify, collect and analyse data quickly and address issues, but they face a cybersecurity skills shortage, in line with global norms. A lack of awareness or understanding can lead to insufficient security measures or the wrong decisions. Companies need the right skills – whether these are in-house or hired – to cross-check and validate their responses to changing cybersecurity risks and vulnerabilities, he emphasises.
RANSOMWARE ATTACKS
Cybersecurity multinationals forecast the continuing proliferation of ransomware attacks, which will increasingly target industrial and utility systems and industrial Internet of Things (IoT) networks, as well as cloud systems and service providers. Although the magnitude of ransomware has already grown 35-fold over the last year with ransomworms and other types of attacks, there is more to come. The ransom of commercial services is big business, highlights Fortinet global security strategist Derek Manky. In 2018, digital extortion will be at the core of most cybercriminals’ business model and will propel them into other schemes that will get their hands on potentially hefty payouts, TrendLabs avers in its report. Further extortion and fraud attacks can be anticipated in 2018, even as other types of digital extortion become more prevalent. “Ransomware is evolving and is being deployed with more regularity. While targets, attack groups and tactics may change, there is growing concern that ransomware could easily be combined with nation-state- developed exploits to spread through networks at an alarming rate,” highlights Trend Micro Southern Africa manager Anvee Alderton. “What we are learning from these attacks is that it is vital to patch any known vulner- abilities the moment a fix is available. Simul- taneously, it is important that we understand how security can be undermined and to research the exploits that are available for popular software.” One of the biggest challenges to create machine learning models is gathering data that is relevant and representative of the rapidly changing malware environment, adds McAfee Labs. Further, researchers have already demonstrated the possibilities of using machine learning to monitor traffic and identify possible zero-day exploits and have also proved machine learning models have blind spots that adversaries can probe for exploitation. Cybercriminals will use these same capabilities to find zero-day exploits. Cybercrime organisations will use more machine learning to modify code based on how and what has been detected by penetration- and detection-testing services – offered by cybercrime organisations – to make their penetration tools less detectable, says Manky. “Machine learning allows cybercriminals to quickly refine their technology to better circumvent security devices used by the targeted company or government agency. To perform such sophisticated scanning and analysis, however, criminal service providers have had to create computing clusters leveraging hijacked compute resources.” Coinhive, a recent example, is distributed through browser plug-ins that infect end-user machines and hijack their compute power to mine for virtual currency. This computing botnet process is shortening the time from concept to delivery of new malware that is both more malicious and more difficult to detect and stop. “Once true AI is integrated into this process, the time between a breach and the time it is detected or protected will be reduced to a matter of milliseconds, rather than the hours or days [as is the case] today,” emphasises Manky.
CRITICAL INFRASTRUCTURE
Cybercriminals will begin to combine AI technologies with multivector attacks to scan for, detect and exploit weaknesses in a cloud provider’s environment, predicts Manky. FortiGuard Labs recorded 62-million malware detections in one quarter in 2017. Out of these, nearly 17 000 malware variants were detected from over 2 500 different malware families. “Increased automation of malware will only make this situation more urgent in the coming year,” he says. Further, cybercriminals will turn to IoT devices to create proxies to obfuscate their location and Web traffic, especially considering that law enforcement usually refers to intellectual property addresses and logs for criminal investigation and postinfection forensics, TrendLabs highlights. “A large network of anonymised devices, running on default credentials and with virtually no logs, could serve as jumping-off points for cybercriminals to surreptitiously facilitate their activities within the compromised network.” The next big target for ransomware is likely to be the ransom of commercial services such as cloud service providers. The financial opportunities are clear, as cloud computing is expected to grow to $162-billion by 2020. Cloud services present a huge potential attack surface, adds Manky. Government entities, critical infrastructure, law enforcement, healthcare and a wide range of industries of all sizes use the cloud. Healthcare and critical infrastructure providers are at greatest risk from the effects of an attack and the advances in cyberattack techniques. “Most critical infrastructure and operational technology networks are notoriously fragile and originally designed to be air-gapped and isolated. Applying security as an afterthought once a network designed to operate in isolation is connected to the digital world is rarely very effective,” warns Manky. Because of the high value of these net- works, and the potential for devastating results should they be compromised or knocked offline, critical infrastructure and healthcare providers will need modern cyberdefence. “The security these systems currently have in place will not be enough. It is imperative that organisations migrate to advanced security systems built around quality intelligence and an integrated security fabric that can see across the distributed network and counter the sophisticated attack systems being developed and deployed by attackers, as well as easily integrate advances in collaboration platforms and AI systems into the fabric,” states Manky. Tassev concurs and adds that, to partici- pate in the global digital economy, South African businesses must demonstrate their ability to secure their systems and their customers’ data. “Ensuring access to up-to-date security skills is going to be as important as actively participating in developing security skills in South Africa. This will become increasingly important as AI, virtual reality and other new technologies continue to emerge,” he concludes.
1 note
·
View note