#VPN Tunnel
Explore tagged Tumblr posts
Text
QNAP + WireGuard: Einrichtung eines VPN-Servers mit QVPN Service
In diesem Artikel konfigurieren wir einen WireGuard VPN-Server auf Netzwerkspeicher von QNAP mit dem QTS und QuTS hero Betriebssystemen. Dafür installieren wir die Anwendung QVPN aus dem AppCenter. Alternativ bietet es sich auch an, WireGuard auf klassische Weise unter Linux zu installieren, z. B. über die Virtualization Station oder als Container mit der Container Station...[Weiterlesen]
0 notes
Text
markiplier was such a wet cat on that new tv show… peak cinema to me
#the edge of sleep#teos#markiplier#tip for non USians#the tunnel bear app is free and lets you watch teos if you connect to a us network#if ur on iphone turn off the vpn setting in settings app and you have gotten through prime videos stupid ass anti vpn block
40 notes
·
View notes
Text
writing informative posts for tumblr is always trying to find the exact right line between staying blandly informative, without being too authoritative on things I'm not an expert on, while wanting to get the word out, without relying on panic-inducing language, but also not wanting people to underestimate the problem, and also not blame people inadvertently for things that actually aren't their fault....
#trying to nail the tone on this shadowban termination vpn post is driving me nuts#also multiple people besides myself confirmed using proton's VPN so if you're using them start split tunneling tumblr like now#honestly if you're using a VPN at all probably split tunnel if you want to retain your blog#but it seems that proton users are who is getting hit now#person who is shadowbanned I've seen your ghost notifications#I don't know who you are because fucking shadowbanned but think twice about using a VPN if you have been#so many websites have trouble with VPNs I don't get why tumblr didn't just do an IP level block instead of nuking blogs
5 notes
·
View notes
Text
Leeeoooo <33 <- theyre gonna figure out your move Leo you do the same one every time Leo please
#DUCKS WIN!!#scuttling over to victory+ tunnelling my way to California with my vpn… time to go clip the game and have it sit in my clips folder <33#ducks lb
6 notes
·
View notes
Note
silly little ask but do you know anywhere that you can stream ‘undercovers’? i’ve been trying to find it for months and i can’t find it anywhere :(
Not silly at all! If you have a VPN (there’s plenty of free apps) it’s on Tubi and 7plus in Australia. It’s out there in places, I promise. We may or may not have a watch party in the discord soon 🤐
#also there’s always#🏴☠️🏴☠️🏴☠️#i use tunnel bear for a vpn#lmk if you need help#also hmu if you want to join our bscu community discord#message me for an invite
5 notes
·
View notes
Note
Why is IP tracking not illegal?
Why is IP tracking not illegal?
IP tracking is used for a multitude of reasons. It will never be illegal to track (unless the information is being gathered for criminal reasons). If you would like to protect yourself from your IP being used by tumblrs to track their perceived enemies in the fandom you can download a VPN. A virtual private network (VPN) is an encrypted connection over the Internet from a device to a network. It prevents sites from seeing your real IP.
Free VPNs
If you would like to protect yourself in the fandom, these VPN serices are free to download and easy to use. They will disguise your true IP and you can get around those pesky YouTube "this is not available in your region" notices.
3 notes
·
View notes
Link
#configuration#encryption#firewall#IPmasking#Linux#networking#OpenVPN#Performance#PiVPN#Privacy#RaspberryPi#remoteaccess#Security#self-hosted#Server#Setup#simplest#systemadministration#tunneling#VPN#WireGuard
0 notes
Text
0 notes
Text
1 note
·
View note
Text
cheap used PC tower with adequate specs (i5 quad core, 1TB SSD, optical drive for ripping) -> migrate media library -> setup jellyfin server -> setup qbittorrent & sonarr/radarr -> enable remote desktop & put the thing itself in a closet -> profit
0 notes
Text
me, seeing a ghost notification: hey it's my invisible friend (shadowbanned blogger)!
#I don't know who you are but I know your pain#ALSO IF YOU'RE USING A VPN SPLIT TUNNEL TUMBLR BEFORE YOUR BLOG GETS NUKED FOR NO REASON
1 note
·
View note
Text
VPN – The Next-Generation

One of the most rapidly evolving technologies in the field of data security online privacy is the Virtual Private Network (VPN). VPNs have been in existence for many years but are now entering what can be considered their next generation of solutions. These innovative advancements are designed to enhance the capabilities and functionality of VPNs, making them even more secure and effective in protecting user data.
Next-generation VPN solutions build upon the traditional concept of VPNs by incorporating new technologies to further improve privacy, speed, and accessibility. These solutions are being developed to address the increasing need for protection against sophisticated cyber threats and growing concerns surrounding data privacy.
One major development in next-generation VPN solutions is the integration of advanced encryption protocols. Traditional VPNs rely on protocols like Point-to-Point Tunneling Protocol (PPTP) and Layer 2 Forwarding Protocol (L2TP) to establish secure connections. However, next-generation solutions are shifting towards more robust protocols like OpenVPN and IPsec, which offer superior encryption and authentication mechanisms. These protocols ensure that user data remains encrypted and protected from unauthorized access while in transit.

Another crucial aspect of next-generation VPNs is the inclusion of advanced security features. These features often include multi-factor authentication, intrusion detection systems, and malware protection. By implementing these additional layers of security, next-generation VPN solutions provide users with an added level of assurance that their online activities are safeguarded against potential threats.
Next-generation VPNs also aim to address concerns related to speed and performance. Traditionally, VPNs have been associated with reduced internet speeds due to the encryption and routing processes involved. However, new technologies such as Split Tunneling and WireGuard are being integrated into VPN solutions to mitigate these issues. Split Tunneling allows users to selectively route internet traffic through the VPN, enabling faster browsing speeds for non-sensitive activities. WireGuard, on the other hand, is a lightweight encryption protocol that offers faster connectivity and improved performance.
Moreover, next-generation VPN solutions are focusing on increased accessibility and ease of use. This means developing intuitive and user-friendly software interfaces that make setting up and managing VPN connections simpler for individuals with limited technical expertise. Additionally, the proliferation of VPN apps for various devices and operating systems ensures that users can access VPN services across a wide range of platforms, including desktops, laptops, smartphones, and tablets.

In conclusion, next-generation VPN solutions are integrating new technologies to provide enhanced privacy, security, speed, and accessibility.
With advanced encryption protocols, improved security features, and innovative performance enhancements, these next-gen VPNs are poised to offer users a superior level of data protection in an increasingly interconnected world. As cyber threats evolve, the constant evolution of VPN technology remains crucial in ensuring the privacy and security of online communications.
#vpn#next-gen VPNs#VPN#cyber threats#cyber security#VPN solutions#next-generation VPN solutions#multi-factor authentication#Tunneling Protocol#Layer 2#(L2TP)
0 notes
Text
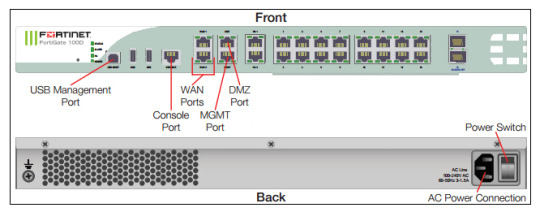
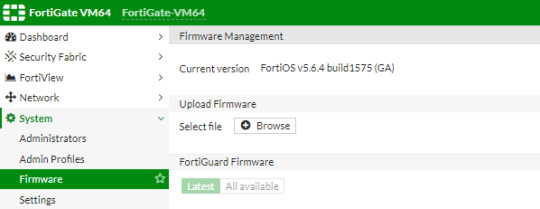
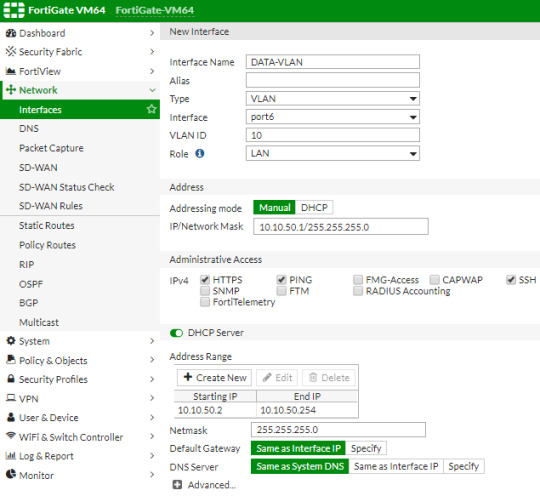
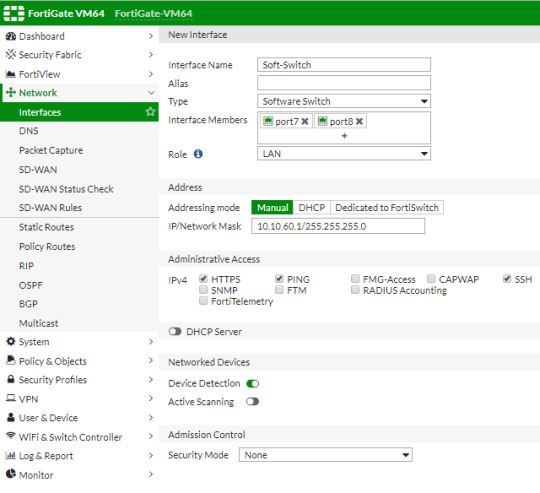
Fortify your cybersecurity arsenal with #Fortigate training. Learn to design, deploy, and manage robust security solutions. Become the guardian of your network's integrity. https://www.dclessons.com/category/courses/fortigate
#fortigate#introduction#firewall#datacenter#practicelabs#training#install#setup#routing#transparentmode#vdom#configure#network#vpn#tunneling#ipsec#tunnel#device#forticare#port#fortiexplorer#nat#mode
0 notes
Text
This post got me thinking and doing a bit of searching. WiFi has been around since the 90s at least, but it's another question whether or not it would have been available at a school in 2003, and he was able to connect to the Internet when he wasn't on school grounds too. I generally assumed his laptop could be using a satellite connection, but I didn't give it much serious thought.
So I asked my parents and they said if you had an always-connected laptop in 2003, it was probably using a SIM card to connect through the mobile phone network! You can even still find laptops with SIM slots today, since not everyone has the option of hooking their place of residence up to an ISP. So I have learnt something today, thank you! 👍
jeremie belpois was out here opening his laptop anywhere, did the guy carry a hot spot on him 24/7, insta-connect to nearest internet? what was his skill? how’d he pull that off? did the xana alert not require internet connection even though it was his laptop?
#code lyoko reblog#hi computer networking is one of my interests and I like learning about the history of it#I'd also guess that any illegal activity performed on his pc or laptop would be done via the supercomputer#using a vpn to take advantage of the supercomputer's superior processing power and network access capabilities#and making it harder to trace back to his personal devices#(note vpns aren't exactly what yt sponsors sell them as. think of it as a tunnel that lets him do stuff on the sc remotely)#but once again I find myself wondering how jeremie pays for stuff. data wasn't as cheap then as it is today#and as someone in the notes said: his laptop had remarkably long battery life
116 notes
·
View notes
Text
Please for the love of all that is holy STOP USING FREE VPNS. You know that adage about how, "If a service is free, you're the product?" It's extremely true, particularly when it comes to free VPNs.
A 2016 study of Android VPNs found that:
75% of free VPNs use 3rd-party tracking software
38% of free VPNs contain code flagged as malware
19% tunnel your data through FULLY UNENCRYPTED CONNECTIONS
84% of all VPNs were leaking IPv6 traffic
66% of all VPNs were leaking DNS traffic
4 of the VPNs tested were ACTIVELY DOING TLS INJECTIONS
You are straight up better off trusting your ISP with your traffic data than some random VPN you found and downloaded from the internet. Using no VPN is far far safer than using a free VPN whose whole profit model is built off selling your information.
59 notes
·
View notes